Design of a Symmetry Protocol for the Efficient Operation of IP Cameras in the IoT Environment
Abstract
1. Introduction
2. Related Works
2.1. Internet of Things
2.2. IP Camera Trends
2.3. IP Camera Market Trends
2.4. Cases of IP Camera Security
2.5. Network Attack Methods
2.5.1. DDoS
2.5.2. Sniffing and Spoofing
2.6. DVR and NVR
3. Contents of the Proposed System
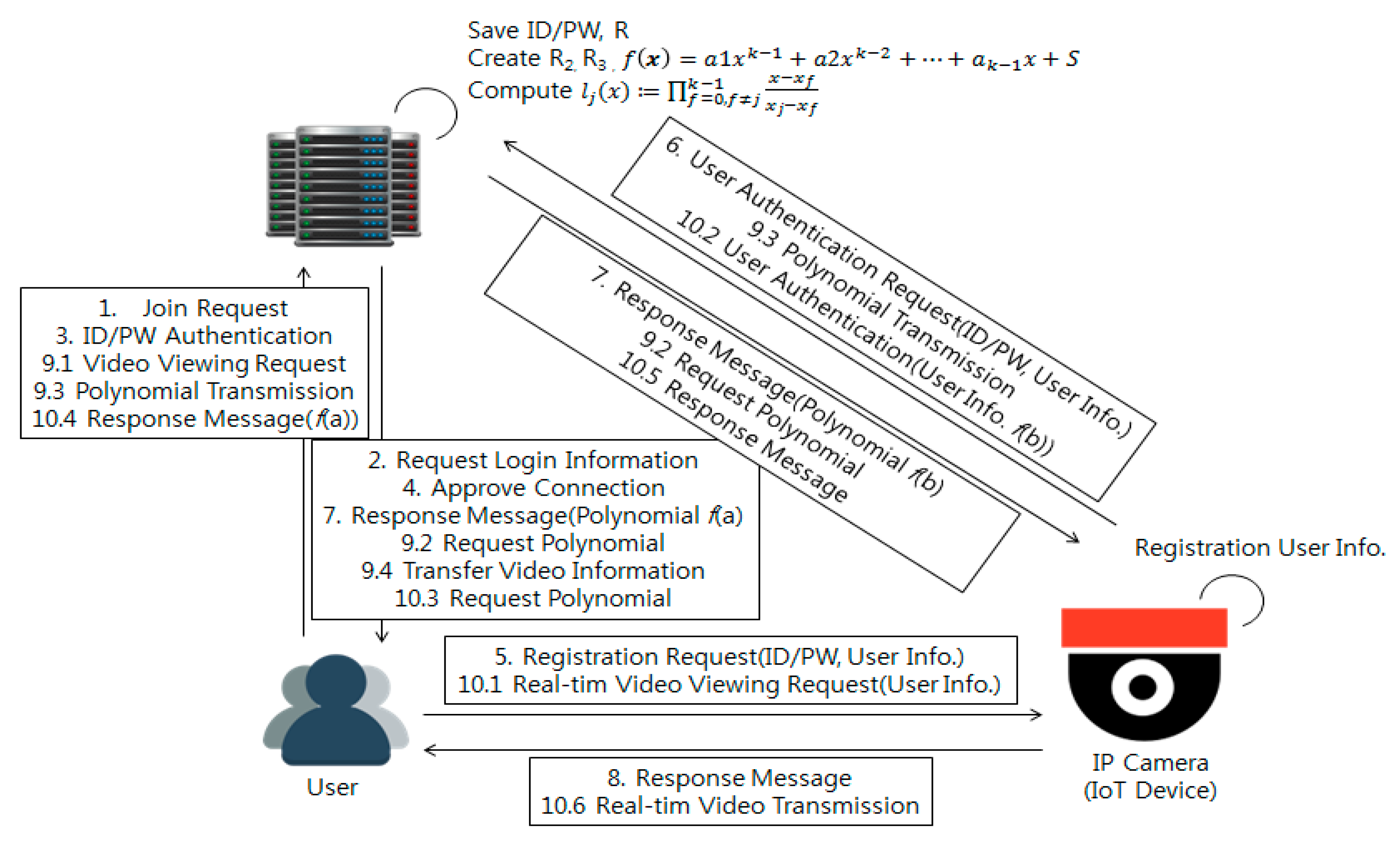
3.1. Internal Connection Protocol
3.2. Registration Procedure
- The user sends a joint request for registration to the control center.
- The control center sends a response message to the user, and the user proceeds to the membership subscription process based on the ID/PW, generates a random value, and transmits them together.
- The control center stores the user’s subscription information in the database and finishes.
- The user sends a connection request to the IP camera through the network to register the desired IP camera.
- The IP camera requests the user’s information, and the user transmits the ID/PW and the random value generated in the control center registration procedure in response to the request.
- The IP camera sends a request to the control center for the product to confirm the validity of the user.
- The control center determines the suitability of the user (i.e., the process of requesting the user to provide the serial number of the associated IP camera and the receipt of the response to the request), and sends the polynomial to the user for authentication later. The polynomial key distribution method is presented in Section 3.2.2.
- Finalizing the registration procedure of the user and the IP camera.
3.2.1. Overview of Image Viewing
- The user transmits an image viewing request message.
- In this study, the user is allowed to view an image when more than an number of devices, user and control center information, are collected. Each device determines the suitability of the user request and then transmits the polynomial information owned by the device to the operation server if it is determined to be appropriate.
- If a certain number of polynomial key values are collected, the operation server allows access to the image.
3.2.2. Polynomial Key Distribution and Transmission Method
- The control center selects the k-1th order polynomial f(k) with the constant s.
- The control center decides the value of j and transmits f(j). In this paper, j is designated as 1 for user, 2 for control center, and 3 for IP camera, and these are encrypted using the group key transmitting.
- When the control center sends the key to the operation server, they encrypt it using the group key and transmit it.
- The control center decrypts the original key using the Lagrange polynomial if or more distribution keys are collected.
3.2.3. Exchange of Keys to Secure Safety
3.3. Video Image Monitoring
- In order to monitor a video image, the user requests to connect to the IP camera, encrypts the ID/PW and the polynomial key value using the group key, and then transmits them.
- The IP camera requests the polynomial key value of the received login information from the control center and nearby devices according to the level of security requirement.
- If the polynomial key value is confirmed to be suitable, an image is transmitted to the user in real time.
4. Performance Evaluation
4.1. Security Evaluation
4.1.1. Mutual Authentication
4.1.2. Reuse Attack
4.1.3. Message Forgery Attack
4.1.4. Sniffing
4.1.5. Spoofing
4.1.6. Side-Channel Attack
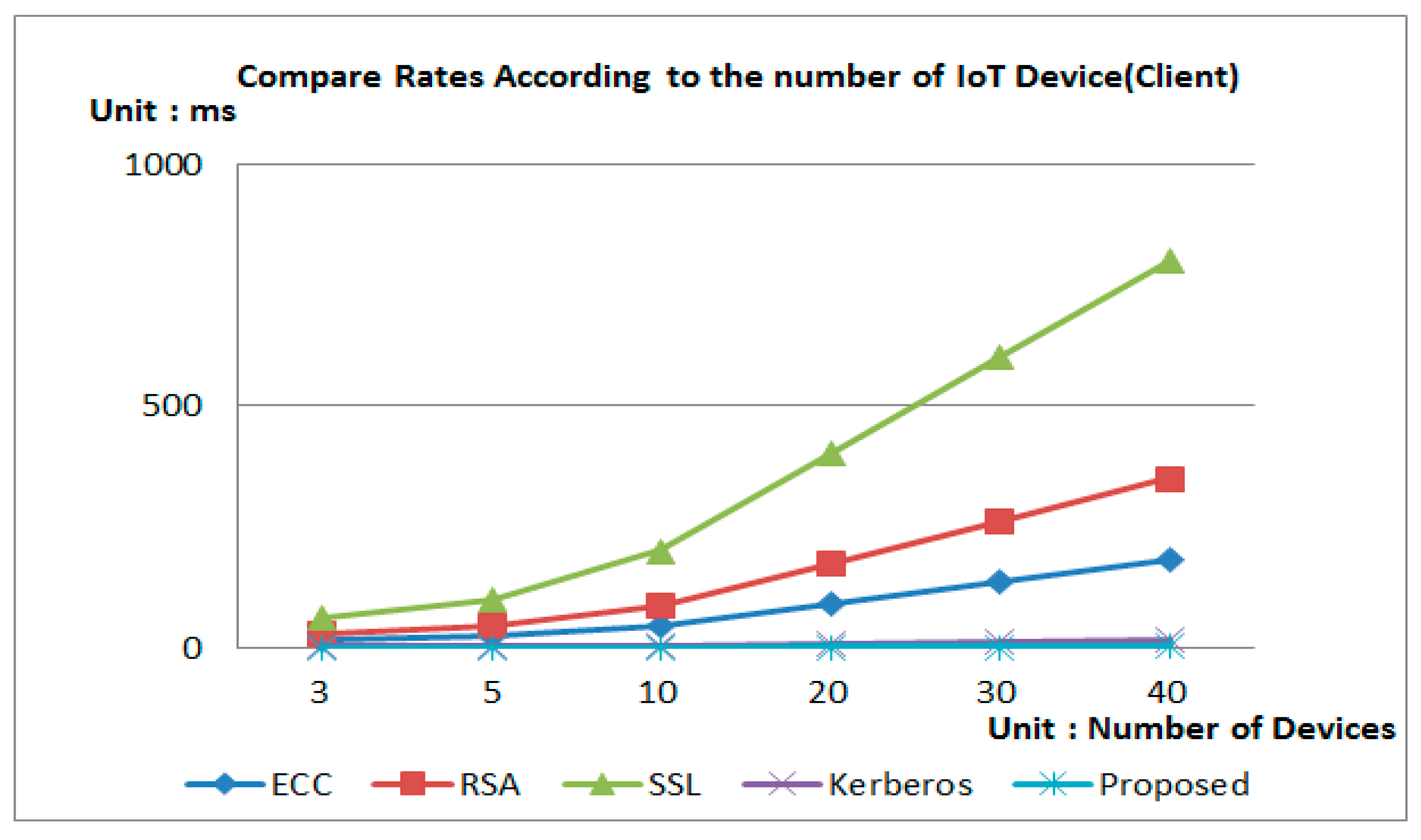
4.2. Performance Evaluation
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A survey on security and privacy issues in internet-of-things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Williams, C. Today the Web Was Broken by Countless Hacked Devices—Your 60-Second Summary. Available online: www.theregister.co.uk/2016/10/21/dyn_dns_ddos_explained (accessed on 21 October 2016).
- Imperva Breaking Down Mirai: An IoT DDoS Botnet Analysis. Available online: https://www.incapsula.com/blog/malware-analysis-mirai-ddos-botnet.html (accessed on 26 October 2016).
- Brass, I.; Tanczer, L.; Carr, M.; Blackstock, J. Regulating IoT: Enabling or Disabling the Capacity of the Internet of Things? Risk Regul. 2017, 33, 12–15. [Google Scholar]
- Burke, D. Preventing DDOS Attacks against IoT Devices. Ph.D. Thesis, Utica College, Utica, NY, USA, 2018. [Google Scholar]
- Frank, C.; Nance, C.; Jarocki, S.; Pauli, W.E. Protecting IoT from Mirai botnets; IoT device hardening. In Proceedings of the Conference on Information Systems Applied Research, Austin, TX, USA, 5 November 2017; p. 1508. [Google Scholar]
- Popovic, G.; Arsic, N.; Jaksic, B.; Gara, B.; Petrovic, M. Overview, characteristics and advantages of IP Camera video surveillance systems compared to systems with other kinds of camera. Int. J. Eng. Sci. Innov. Technol. 2013, 2, 356–362. [Google Scholar]
- Kang, J.; Han, J.; Park, J.H. Design of IP camera access control protocol by utilizing hierarchical group key. Symmetry 2015, 7, 1567–1586. [Google Scholar] [CrossRef]
- Fularz, M.; Kraft, M.; Schmidt, A.; Kasiński, A. The architecture of an embedded smart camera for intelligent inspection and surveillance. In Progress in Automation, Robotics and Measuring Techniques; Springer: Cham, Switzerland, 2015; pp. 43–52. [Google Scholar]
- Tekeoglu, A.; Tosun, A.S. Investigating security and privacy of a cloud-based wireless IP camera: NetCam. In Proceedings of the 2015 24th International Conference on Computer Communication and Networks (ICCCN), Las Vegas, NV, USA, 3–6 August 2015; pp. 1–6. [Google Scholar]
- Bangali, J.; Shaligram, A. Design and Implementation of Security Systems for Smart Home based on GSM technology. Int. J. Smart Home 2013, 7, 201–208. [Google Scholar] [CrossRef]
- Baran, R.; Ruść, T.; Rychlik, M. A smart camera for traffic surveillance. In International Conference on Multimedia Communications, Services and Security; Springer: Cham, Switzerland, 2014; pp. 1–15. [Google Scholar]
- Krebs on Security. Researchers Find Fresh Fodder for IoT Attack Cannons. Available online: https://krebsonsecurity.com/2016/12/researchers-find-fresh-fodder-for-iot-attack-cannons/ Krebs on Security (accessed on 16 December 2016).
- Rio Kellyan, Tech Desk Editor. The Video of the Home Security Camera Was Hacked. Available online: https://www.bbc.com/korean/news-44962424 (accessed on 7 July 2018).
- Korea Internet & Security Agency. 2016 Mirai Malicious Code Trends. Available online: https://www.krcert.or.kr/data/reportView.do?bulletin_writing_sequence=24864&queryString=cGFnZT0xJnNvcnRfY29kZT0mc2VhcmNoX3NvcnQ9dGl0bGVfbmFtZSZzZWFyY2hfd29yZD1taXJhaSZ4PTAmeT0w (accessed on 12 December 2016).
- Peng, T.; Leckie, C.; Ramamohanarao, K. Survey of network-based defense mechanisms countering the DoS and DDoS problems. ACM Comput. Surv. (CSUR) 2007, 39, 3. [Google Scholar] [CrossRef]
- Mirkovic, J.; Reiher, P. A taxonomy of DDoS attack and DDoS defense mechanisms. ACM SIGCOMM Comput. Commun. Rev. 2004, 34, 39–53. [Google Scholar] [CrossRef]
- Jeon, W.; Kim, J.; Lee, Y.; Won, D. A practical analysis of smartphone security. In Symposium on Human Interface; Springer: Berlin/Heidelberg, Germany, 2011; pp. 311–320. [Google Scholar]
- Ramachandran, V.; Nandi, S. Detecting ARP spoofing: An active technique. In Proceedings of the International Conference on Information Systems Security, Kolkata, India, 19–21 December 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 239–250. [Google Scholar]
- Chomsiri, T. Sniffing packets on LAN without ARP spoofing. In Proceedings of the Third 2008 International Conference on Convergence and Hybrid Information Technology, Busan, Korea, 11–13 November 2008; pp. 472–477. [Google Scholar]
- Lin, C.F.; Yuan, S.M.; Leu, M.C.; Tsai, C.T. A framework for scalable cloud video recorder system in surveillance environment. In Proceedings of the 2012 9th international conference on Ubiquitous Intelligence & Computing and 9th International Conference on Autonomic & Trusted Computing (UIC/ATC), Fukuoka, Japan, 4–7 September 2012; pp. 655–660. [Google Scholar]
- Lipton, A.J.; Clark, J.I.; Zhang, Z.; Venetianer, P.L.; Strat, T.; Allmen, M.; Severson, W.; Haering, N.; Chosak, A.; Frazier, M.; et al. Video Analytic Rule Detection System and Method. U.S. Patent 8,564,661, 22 October 2013. [Google Scholar]
- Liu, H.; Chen, S.; Kubota, N. Intelligent Video Systems and Analytics: A Survey. IEEE Trans. Ind. Inform. 2013, 9, 1222–1233. [Google Scholar]
- Lindsey, S.L.; Call, S.J. Devices, Systems, and Methods for Remote Video Retrieval. U.S. Patent Application No 14/451,067, 4 February 2016. [Google Scholar]
- Liu, J.K.; Au, M.H.; Susilo, W.; Liang, K.; Lu, R.; Srinivasan, B. Secure sharing and searching for real-time video data in mobile cloud. IEEE Netw. 2015, 29, 46–50. [Google Scholar] [CrossRef]
- Costin, A. Security of CCTV and video surveillance systems: Threats, vulnerabilities, attacks, and mitigations. In Proceedings of the 6th International Workshop on Trustworthy Embedded Devices, Vienna, Austria, 28 October 2016; pp. 45–54. [Google Scholar]



| Notation | Meaning |
|---|---|
| Ek(plaintext) | Encrypt a using key k |
| Dk(ciphertext) | Encrypt ciphertext using key k |
| R | Random Number |
| ID | Identification for authentication |
| PW | Password for authentication |
| f(k) | Polynomial for secret sharing |
| SN | Serial Number |
| lj(x) | Formula for secret combinations |
| Simulation Initial Settings | |
|---|---|
| Number of Device | 3~40 |
| Placement Area | 45 m × 45 m |
| Control Center Location | X = 60 m, y = 30 |
| Device Initial Energy | 1.0 |
| ETX, ERX | 50 nanoJ |
| Packet Size | 6000 bit |
| Sortation | Client | Server |
|---|---|---|
| Process | ARM1176JZF-S 700 MHz Single Core | 3.5 GHz Intel Core i5-4690 |
| Memory | 512 MB | 16 GB |
| storage medium | Micro SD Card, 8 GB | SSD 512 GB |
| Number | ECC | RSA | SSL | Kerberos | Proposed |
|---|---|---|---|---|---|
| 3 | 18.74498 | 30.77373 | 59.15496 | 0.09947 | 26.85049 |
| 5 | 31.24164 | 51.28955 | 98.59160 | 0.165781 | 44.75081 |
| 10 | 68.731608 | 112.83701 | 216.90153 | 0.364719 | 98.451782 |
| 20 | 137.46322 | 225.67402 | 433.80306 | 0.72944 | 196.90356 |
| 30 | 203.69549 | 334.40787 | 642.81727 | 1.08089 | 291.77528 |
| 40 | 281.17476 | 461.60595 | 887.32445 | 1.49203 | 402.75729 |
| Number | ECC | RSA | SSL | Kerberos | Proposed |
|---|---|---|---|---|---|
| 3 | 12.99786 | 25.59363 | 59.44896 | 1.17664 | 0.09490 |
| 5 | 21.66311 | 42.65605 | 99.08161 | 1.96106 | 0.15816 |
| 10 | 48.95862 | 96.40267 | 223.92443 | 4.43201 | 0.35744 |
| 20 | 93.58461 | 184.27414 | 428.03254 | 8.47179 | 0.68325 |
| 30 | 134.31125 | 264.46751 | 614.30596 | 12.15859 | 0.98059 |
| 40 | 181.97008 | 358.31082 | 832.28549 | 16.47293 | 1.32854 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, J.; Kang, J.; Jun, M.-s.; Han, J. Design of a Symmetry Protocol for the Efficient Operation of IP Cameras in the IoT Environment. Symmetry 2019, 11, 361. https://doi.org/10.3390/sym11030361
Lee J, Kang J, Jun M-s, Han J. Design of a Symmetry Protocol for the Efficient Operation of IP Cameras in the IoT Environment. Symmetry. 2019; 11(3):361. https://doi.org/10.3390/sym11030361
Chicago/Turabian StyleLee, Jaeseung, Jungho Kang, Moon-seog Jun, and Jaekyung Han. 2019. "Design of a Symmetry Protocol for the Efficient Operation of IP Cameras in the IoT Environment" Symmetry 11, no. 3: 361. https://doi.org/10.3390/sym11030361
APA StyleLee, J., Kang, J., Jun, M.-s., & Han, J. (2019). Design of a Symmetry Protocol for the Efficient Operation of IP Cameras in the IoT Environment. Symmetry, 11(3), 361. https://doi.org/10.3390/sym11030361





