A Secure and Efficient Lightweight Symmetric Encryption Scheme for Transfer of Text Files between Embedded IoT Devices
Abstract
1. Introduction
2. Related Work
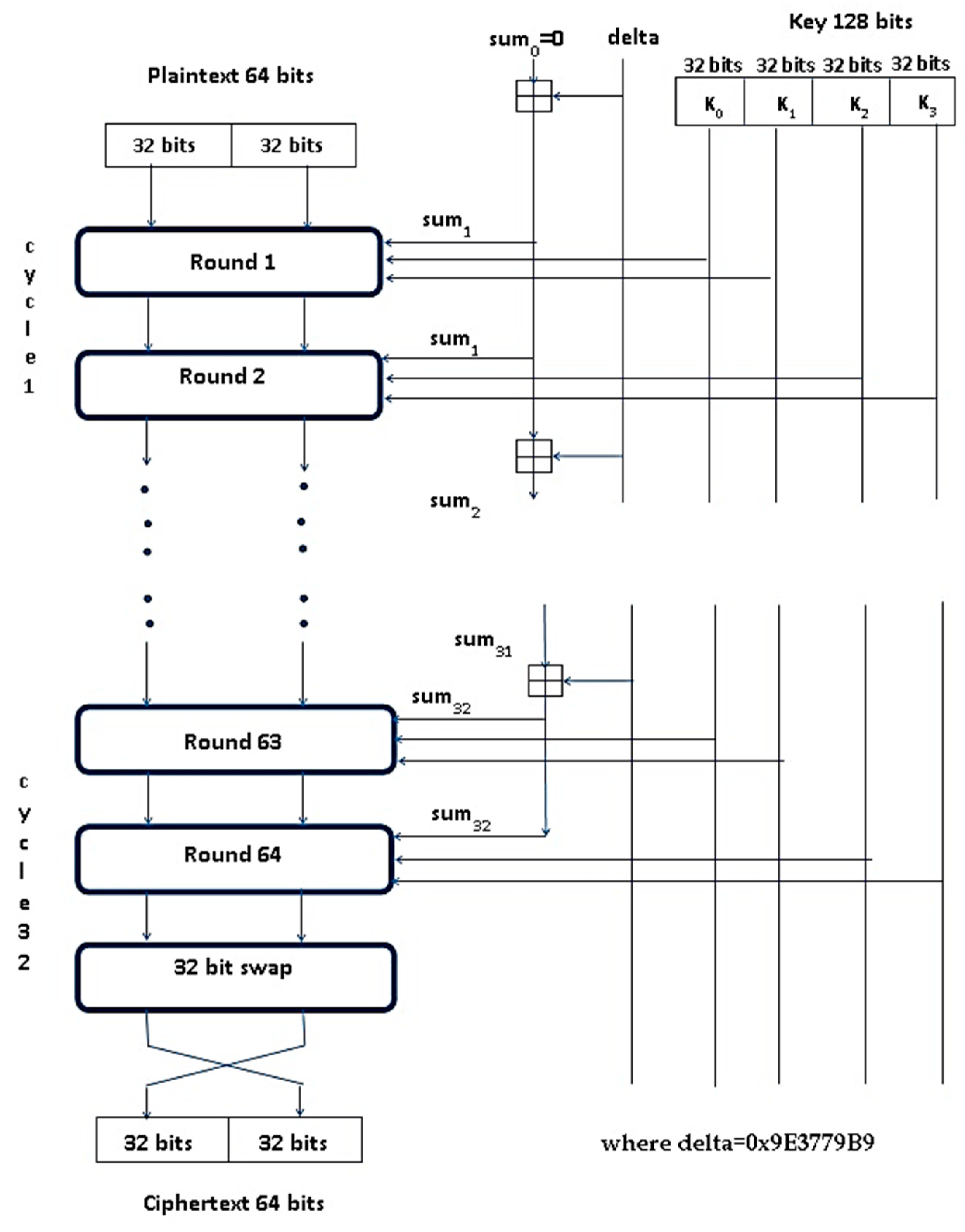
3. Novel Tiny Symmetric Encryption Algorithm (NTSA)
| Algorithm 1 Novel tiny symmetric encryption algorithm (NTSA) symmetric encryption algorithm |
| Encrypt (plaintext v, key k): |
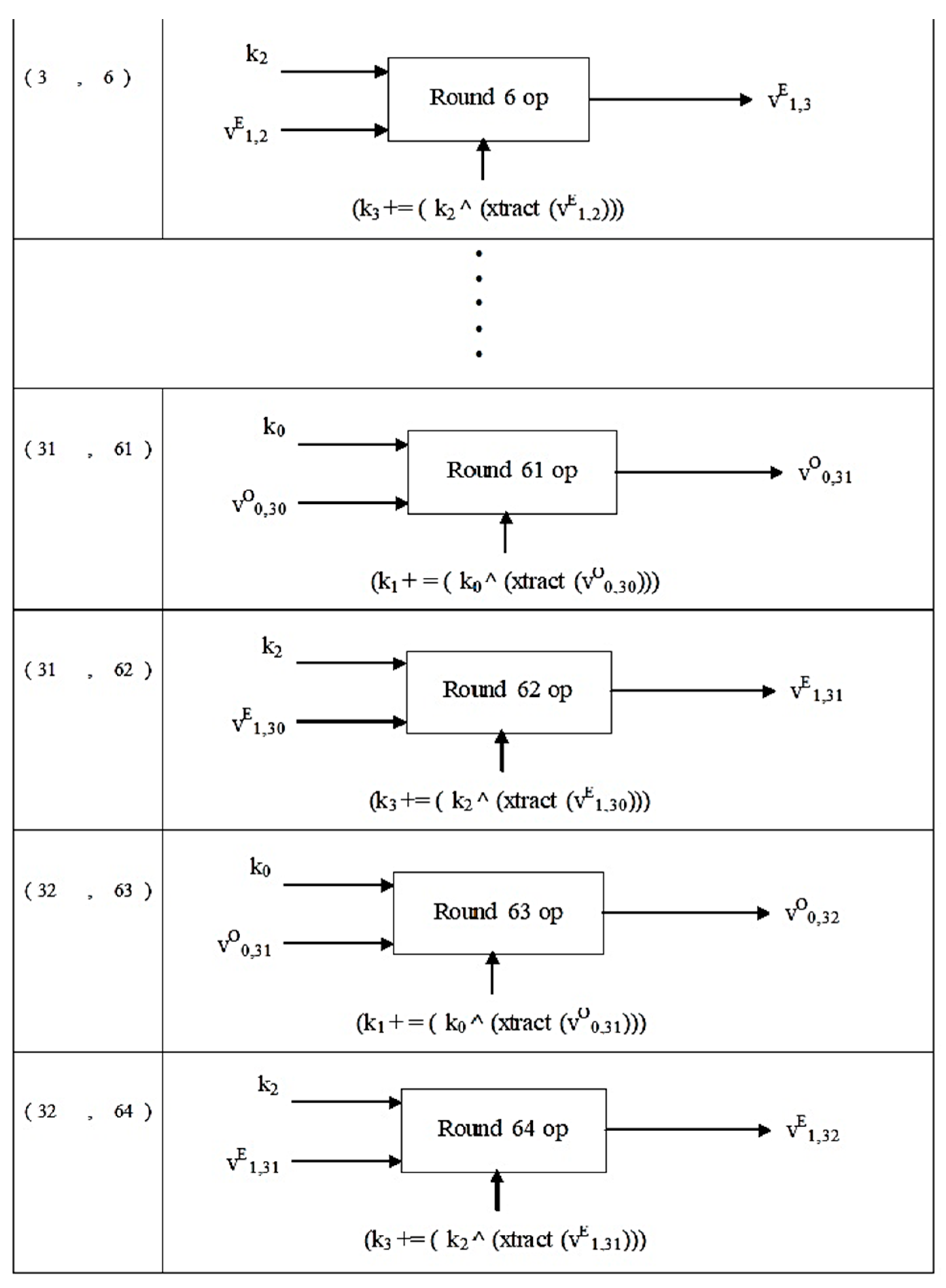
| 1: Start 2: Assign key constant kc = 0 3: Assign cycle = 0 4: kc = kc + ksc 5: 32-bit block v0 is recomputed as v0 += ((v1 LSHIFT 4) AND k0) XOR (v1 AND kc) XOR ((v1 RSHIFT 5) AND k1) 6: Partial key k1 is recomputed as k1 += (k0 XOR(xtract(v0))) where function xtract() returns value of array indexed v0. 7: 32-bit block v1 is recomputed as v1 += ((v0 LSHIFT 4) AND k2) XOR (v0 AND kc) XOR ((v0 RSHIFT 5) AND k3) 8: Partial key k3 is recomputed as k3 += (k2 XOR(xtract(v1))) where function xtract() returns value of array indexed v1. 9: Increment cycle by 1 10: Repeat step 4 through step 9 until cycle = 32 11: Assign value of k1 to newk1 and k3 to newk3 12: Return newk1 and newk3 |
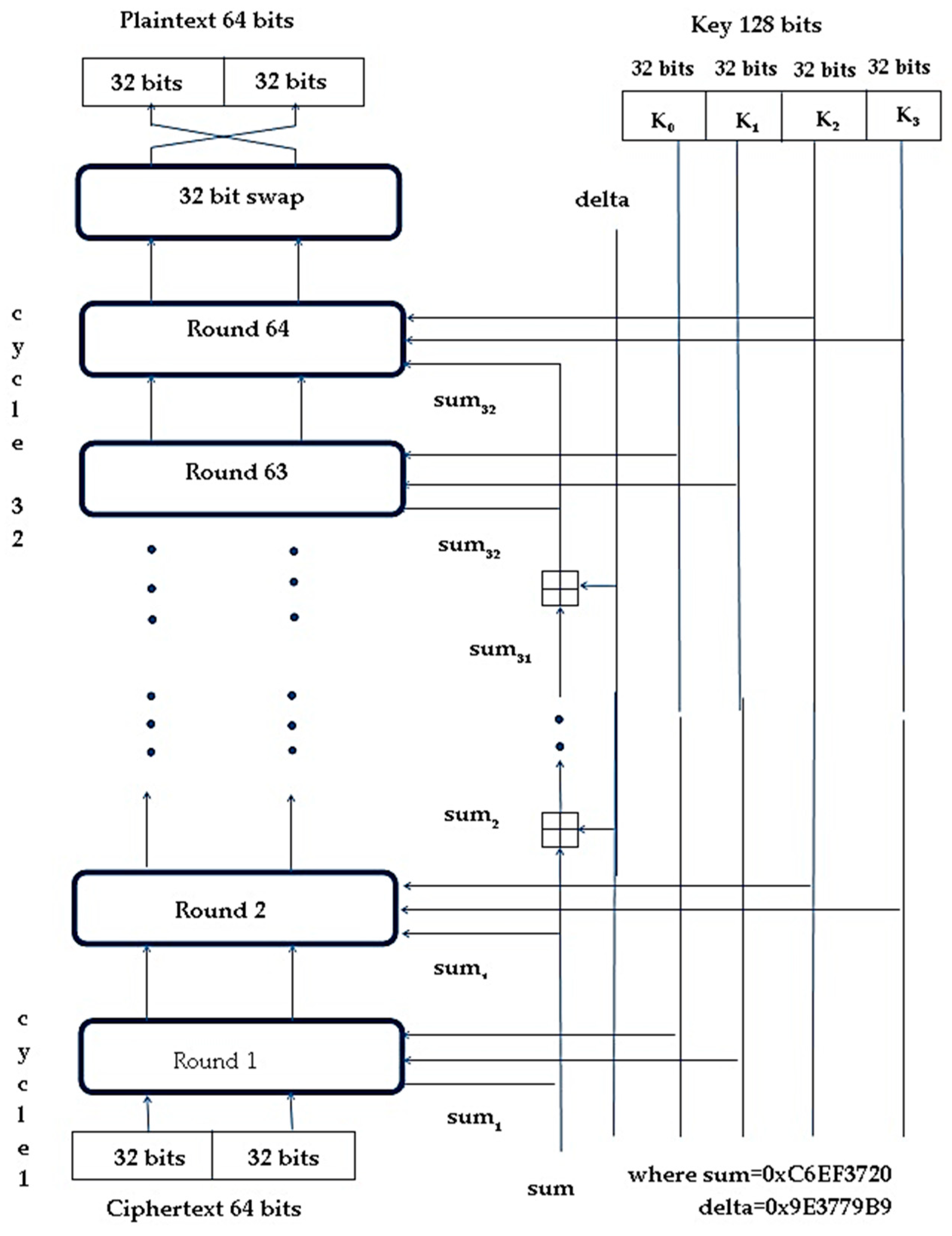
| Algorithm 2. NTSA symmetric decryption algorithm |
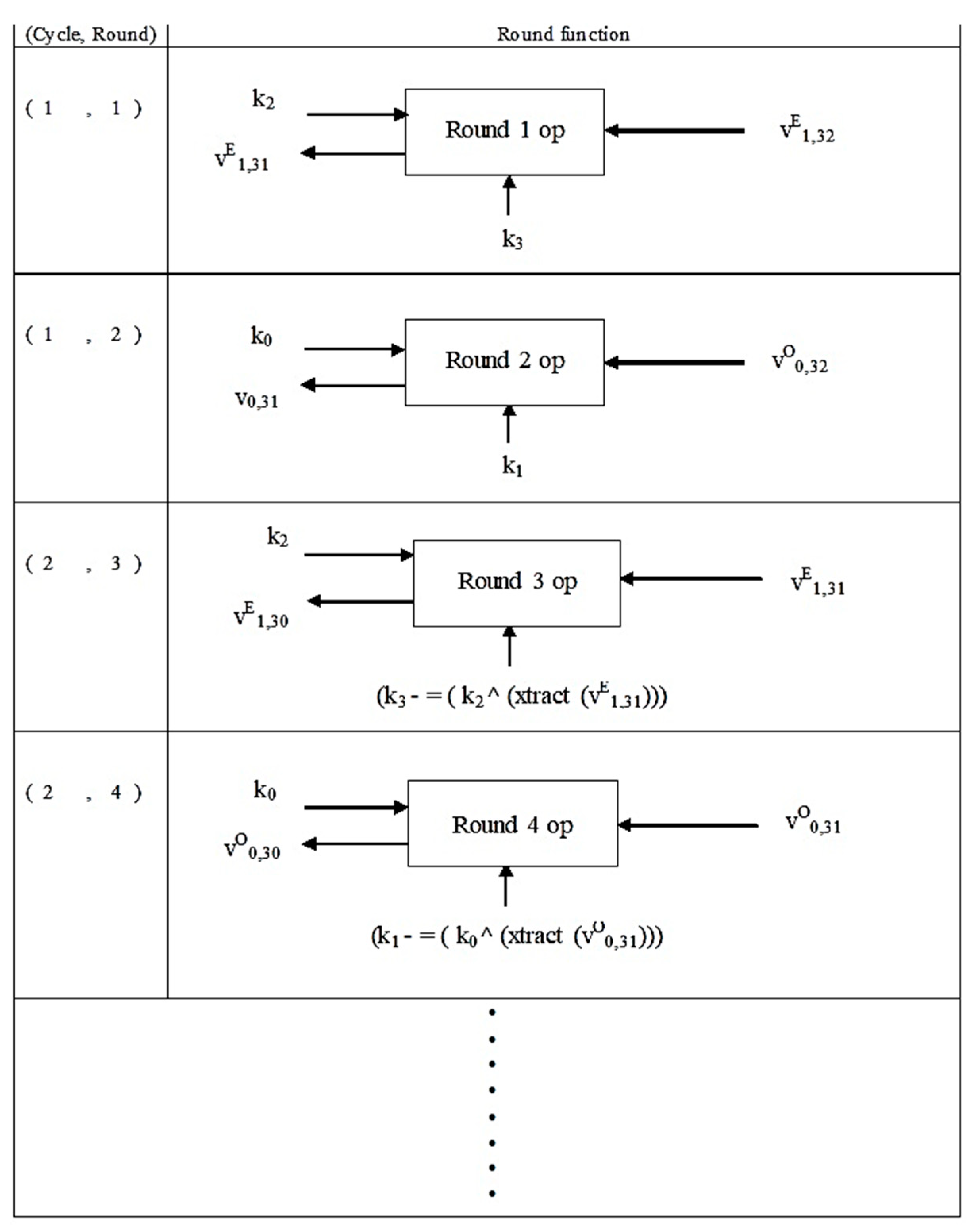
| Encrypt (plaintext v, key k): |
| 1: Start 2: Assign key constant kc = 0XC6EF3720 3: Assign k1 = newk1 and k3 = newk3 4: Assign cycle=0 5: Partial key k3 is recomputed as k3 - = (k2 XOR(xtract(v1))) where function xtract() returns value of array indexed v1. 6: 32-bit block v1 is recomputed as v1 - = ((v0 LSHIFT 4) AND k2) XOR (v0 AND kc) XOR ((v0 RSHIFT 5) AND k3) 7: Partial key k1 is recomputed as k1 - = (k0 XOR(xtract(v0))) where function xtract() returns value of array indexed v0. 8: 32-bit block v0 is recomputed as v0 - = ((v1 LSHIFT 4) AND k0) XOR (v1 AND kc) XOR ((v1 RSHIFT 5) AND k1) 9: kc = kc − ksc 10: Increment cycle by 1 11: Repeat step 5 through step 10 until cycle=32 12: Return |
4. Experimental Results and Discussion
4.1. Performance Comparison of NTSA with TEA, XTEA and XXTEA
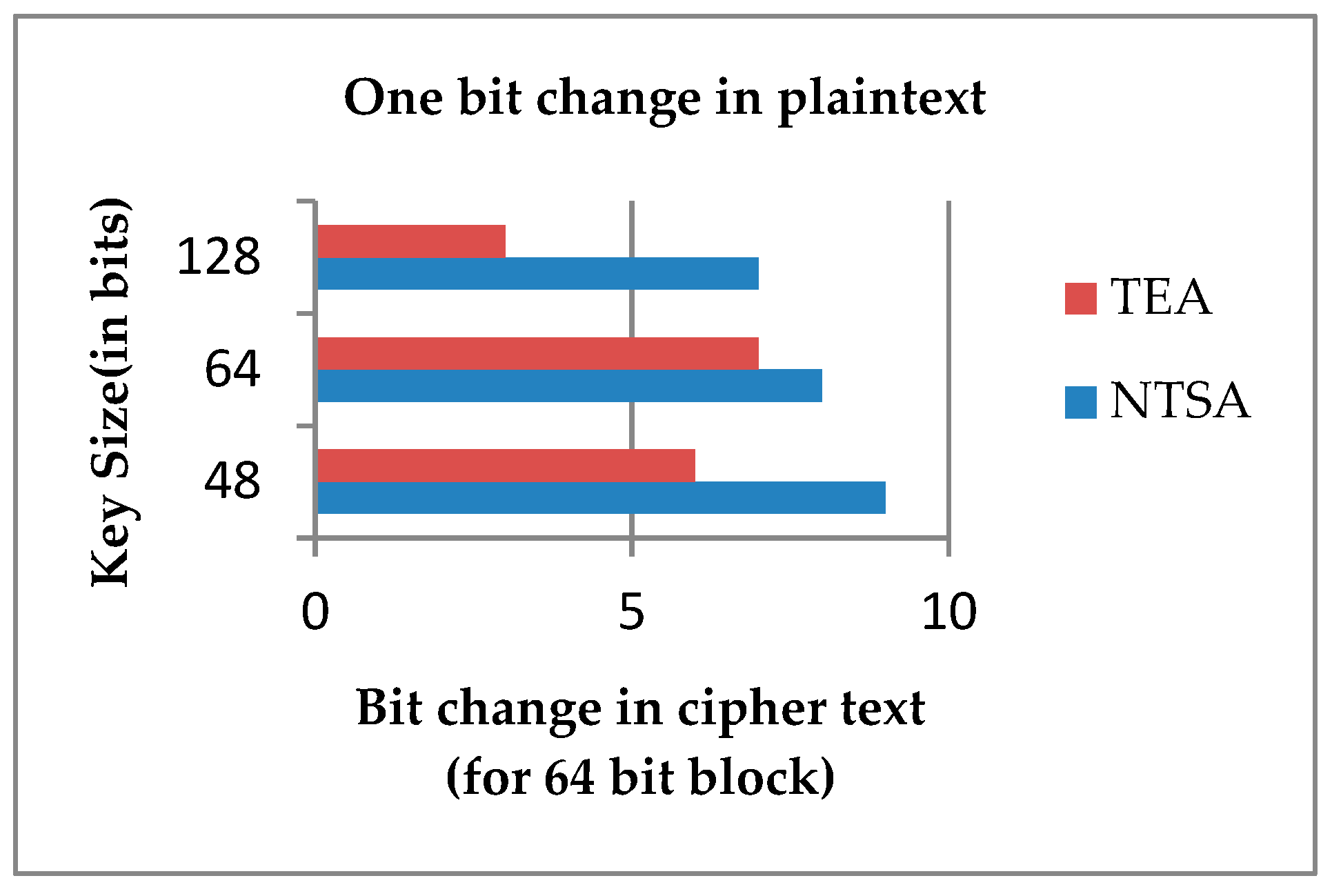
Avalanche Effect
5. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Porambage, P.; Okwuibe, J.; Liyanage, M.; Ylianttila, M.; Taleb, T. Survey on Multi-Access Edge Computing for Internet of Things Realization. IEEE Commun. Surv. Tutor. 2018, 20, 2961–2991. [Google Scholar] [CrossRef]
- Ploennigs, J.; Cohn, J.; Stanford-Clark, A. The Future of IoT. IEEE Internet Things Mag. 2018, 1, 28–33. [Google Scholar] [CrossRef]
- Philip, V.; Suman, V.K.; Menon, V.G.; Dhanya, K. A Review on latest Internet of Things based Healthcare Applications. Int. J. Comput. Sci. Inf. Secur. 2017, 15, 248–254. [Google Scholar]
- Deshkar, S.; Thanseeh, R.A.; Menon, V.G. A Review on IoT based m-Health Systems for Diabetes. Int. J. Comput. Sci. Telecommun. 2017, 8, 13–18. [Google Scholar]
- Vinoj, P.G.; Jacob, S.; Menon, V.G. Hybrid brainactuated muscle interface for the physically disabled. In Basic and Clinical Pharmacology and Toxicology; Wiley: Hoboken, NJ, USA, 2018; Volume 123. [Google Scholar]
- Keerthi, K.S.; Mahapatra, B.; Menon, V.G. Into the World of Underwater Swarm Robotics: Architecture, Communication, Applications and Challenges. Recent Pat. Comput. Sci. 2019, 12, 1. [Google Scholar]
- Bordel, B.; Alcarria, R.; De Andres, D.M.; You, I.; Martin, D. Securing Internet-of-Things Systems through Implicit and Explicit Reputation Models. IEEE Access 2018, 6, 47472–47488. [Google Scholar] [CrossRef]
- Menon, V.G.; Prathap, J. Vehicular Fog Computing: Challenges applications and future directions. Int. J. Veh. Telemat. Infotain. Syst. 2017, 1, 15–23. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating Critical Security Issues of the IoT World: Present and Future Challenges. IEEE Internet Things J. 2018, 5, 2483–2495. [Google Scholar] [CrossRef]
- Wang, B.; Zhan, Y.; Zhang, Z. Cryptanalysis of a Symmetric Fully Homomorphic Encryption Scheme. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1460–1467. [Google Scholar] [CrossRef]
- Maimuț, D.; Reyhanitabar, R. Authenticated Encryption: Toward Next-Generation Algorithms. IEEE Secur. Privacy 2014, 12, 70–72. [Google Scholar] [CrossRef]
- Ahmad, S.; Alam, K.M.R.; Rahman, H.; Tamura, S. A comparison between symmetric and asymmetric key encryption algorithm based decryption mixnets. In Proceedings of the 2015 International Conference on Networking Systems and Security (NSysS), Dhaka, Bangladesh, 5–7 January 2015; pp. 1–5. [Google Scholar]
- Yassein, M.B.; Aljawarneh, S.; Qawasmeh, E.; Mardini, W.; Khamayseh, Y. Comprehensive study of symmetric key and asymmetric key encryption algorithms. In Proceedings of the 2017 International Conference on Engineering and Technology (ICET), Antalya, Turkey, 21–23 August 2017; pp. 1–7. [Google Scholar]
- Lamba, C.S. Design and Analysis of Stream Cipher for Network Security. In Proceedings of the 2010 Second International Conference on Communication Software and Networks, Singapore, 26–28 February 2010; pp. 562–567. [Google Scholar]
- Baker, S.I.B.; Al-Hamami, A.H. Novel Algorithm in Symmetric Encryption (NASE): Based on Feistel Cipher. In Proceedings of the 2017 International Conference on New Trends in Computing Sciences (ICTCS), Amman, Jordan, 9–11 October 2017; pp. 191–196. [Google Scholar]
- Rebeiro, C.; Nguyen, P.H.; Mukhopadhyay, D.; Poschmann, A. Formalizing the Effect of Feistel Cipher Structures on Differential Cache Attacks. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1274–1279. [Google Scholar] [CrossRef]
- Wheeler, D.; Needham, R. TEA, a tiny encryption algorithm. In Proceedings of the 1995 Fast Software En-Cryption Workshop, Leuven, Belgium, 14–16 December 1995; Springer: Berlin/Heidelberg, Germany, 1995; pp. 97–110. [Google Scholar]
- Amrutha George, A.; Riyadh, M.; Prajitha, M.V. Secure image transferring using KBRP and TEA algorithms. In Proceedings of the 2015 International Conference on Innovations in Information, Embedded and Communication Systems (ICIIECS), Coimbatore, India, 19–20 March 2015; pp. 1–5. [Google Scholar]
- Abdelhalim, M.B.; El-Mahallawy, M.; Ayyad, M.; Elhennawy, A. Implementation of a modified lightweight cryptographic TEA algorithm in RFID system. In Proceedings of the 2011 International Conference for Internet Technology and Secured Transactions, Abu Dhabi, UAE, 11–14 December 2011; pp. 509–513. [Google Scholar]
- Shepherd, S.J. The Tiny Encryption Algorithm. Cryptologia 2007, 31, 233–245. [Google Scholar] [CrossRef]
- Sima, I.; Tarmurean, D.; Greu, V.; Diaconu, A. XXTEA, an alternative replacement of KASUMI cipher algorithm in A5/3 GSM and f8, f9 UMTS data security functions. In Proceedings of the 2012 9th International Conference on Communications (COMM), Bucharest, Romania, 21–23 June 2012; pp. 323–326. [Google Scholar]
- Lu, J. Related-key rectangle attack on 36 rounds of the XTEA block cipher. Int. J. Inf. Sec. 2009, 8, 1–11. [Google Scholar]
- Holden, J. Demitasse: A “Small” Version of the Tiny Encryption Algorithm and Its Use in a Classroom Setting. Cryptologia 2013, 37, 74–83. [Google Scholar] [CrossRef]
- De Dormale, G.M.; Bass, J.; Quisquater, J.-J. On Solving RC5 Challenges with FPGAs. In Proceedings of the 15th Annual IEEE Symposium on Field-Programmable Custom Computing Machines (FCCM 2007), Napa, CA, USA, 23–25 April 2007; pp. 281–282. [Google Scholar]
- Li, T.; Wu, H.; Wang, X.; Bao, F. SenSec Design Technical Report-TR v1.1; InfoComm Security Department, Institute for Infocomm Research: Singapore, 2005. [Google Scholar]
- Karlof, C.; Sastry, N.; Wagner, D. TinySec: A link layer security architecture for wireless sensor networks. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems (SenSys ’04), Baltimore, MD, USA, 3–5 November 2004; pp. 162–175. [Google Scholar]
- Luk, M.; Mezzour, G.; Perrig, A.; Gligor, V. MiniSec: A secure sensor network communication architecture. In Proceedings of the 6th International Symposium on Information Processing in Sensor Networks (IPSN ’07), Cambridge, MA, USA, 25–27 April 2007; pp. 479–488. [Google Scholar]
- Standaert, F.-X.; Piret, G.; Gershenfeld, N.; Quisquater, J.-J. SEA: A scalable encryption algorithm for small embedded applications. In Proceedings of the Workshop on RFIP and Light weight Crypto, Graz, Austria, 14–15 July 2005. [Google Scholar]
- Hong, D.; Sung, J.; Hong, S.; Lim, J.; Lee, S.; Koo, B.-S.; Lee, C.; Chang, D.; Lee, J.; Jeong, K.; et al. HIGHT: A new block cipher suitable for low-resource device. In Cryptographic Hardware and Embedded Systems—CHES 2006: 8th International Workshop, Yokohama, Japan, 10–13 October 2006; Volume 4249 of Lecture Notes in Computer Science; Springer: Berlin, Germany, 2006; pp. 46–59. [Google Scholar]
- Usman, M.; Ahmed, I.; Aslam, M.I.; Khan, S.; Shah, U.A. SIT: A Lightweight Encryption Algorithm for Secure Internet of Things. Int. J. Adv. Comput. Sci. Appl. 2017, 8. [Google Scholar] [CrossRef]
- Liang, C.; Ye, N.; Malekian, R.; Wang, R. The hybrid encryption algorithm of lightweight data in cloud storage. In Proceedings of the 2016 2nd International Symposium on Agent, Multi-Agent Systems, and Robotics (ISAMSR), Bangi, Malaysia, 23–24 August 2016; pp. 160–166. [Google Scholar]
- Gao, C.; Lv, S.; Wei, Y.; Wang, Z.; Liu, Z.; Cheng, X. M-SSE: An Effective Searchable Symmetric Encryption with Enhanced Security for Mobile Devices. IEEE Access 2018, 6, 38860–38869. [Google Scholar] [CrossRef]
- Schneier, B. The IDEA Encryption Algorithm. Dr. Dobb’s J. 1990, 18, 50–56. [Google Scholar]
- Burwick, C.; Coppersmith, D.; D’Avignon, E.; Gennaro, R.; Halevi, S.; Jutla, C.; Matyas, S.M.; O’Connor, L.; Peyravian, M.; Safford, D.; et al. MARS—A candidate cipher for AES. 1998. Available online: http://www.research.ibm.com/security/mars.html (accessed on 29 April 2018).
- Abdelhalim, M.B.; El-Mahallawy, M.; Elhennawy, M.A.A. Design and Implementation of an Encryption Algorithm for use in RFID System. Int. J. RFID Secur. Cryptogr. 2013, 2. [Google Scholar] [CrossRef]
- Zhdanov, O.N.; Sokolov, A.V. Block Symmetric Cryptographic Algorithm based on Principles of variable block length and many-valued logic. Far East J. Electron. Commun. 2016, 16, 573–589. [Google Scholar] [CrossRef]
- Korea Telecommunication Technology Association. 128 Bit Light Weight Block Cipher LEA, Information Telecommunication Organization Standard (Korean Standard). 2013.
- Park, J.H. 128 bit block cipher LEA. TTA J. 2015, 157. [Google Scholar]
- Abdullah, D.; Rahim, R.; Siahaan, A.P.U.; Ulva, A.F.; Fitri, Z.; Malahayati, M.; Harun, H. Super-Encryption Cryptography with IDEA and WAKE Algorithm. J. Phys. Conf. Ser. 2018, 1019, 012039. [Google Scholar] [CrossRef]
- Anderson, R.; Biham, E.; Knudsen, L. Serpent: A Proposal for the Advanced Encryption Standard. In Proceedings of the First Advanced Encryption Standard (AES) Conference, Ventura, CA, USA, 20–22 August 1998. [Google Scholar]
- Ren, W.; Miao, Z. A Hybrid Encryption Algorithm Based on DES and RSA in Bluetooth Communication. In Proceedings of the 2010 Second International Conference on Modeling, Simulation and Visualization Methods, Sanya, China, 15–16 May 2010; pp. 221–225. [Google Scholar]
- Wheeler, D.; Needham, R. TEA, A Tiny Encryption Algorithm. Available online: http://www.cix.co.uk/~klockstone/tea.pdf (accessed on 22 April 2018).
- Andem, V.R. A Cryptanalysis of the Tiny Encryption Algorithm; The University of Alabama: Tuscaloosa, AL, USA, 2003. [Google Scholar]
- Rachmawati, D.; Sharif, A.; Jaysilen; Budiman, M.A. Hybrid Cryptosystem Using Tiny Encryption Algorithm and LUC Algorithm. IOP Conf. Ser. Mater. Sci. Eng. 2018, 300, 012042. [Google Scholar] [CrossRef]
- Novelan, M.S.; Husein, A.M.; Harahap, M.; Aisyah, S. SMS Security System on Mobile Devices Using Tiny Encryption Algorithm. IOP Conf. Ser. J. Phys. Conf. Ser. 2018, 1007, 012037. [Google Scholar] [CrossRef]
- Needham, R.M.; Wheeler, D.J. TEA Extensions; Technical Report; Computer Laboratory, University of Cambridge: Cambridge, MA, USA, 1997. [Google Scholar]
- Kaps, J.-P. Chai-tea, Cryptographic Hardware Implementations of XTEA. In Proceedings of the INDOCRYPT 08 Proceedings of the 9th International Conference on Cryptology in India: Progress in Cryptology, Kharagpur, India, 14–17 December 2008. [Google Scholar]
- Wheeler, D.; Needham, R. XXTEA: Correction to XTEA; Technical report; Computer Laboratory, University of Cambridge: Cambridge, MA, USA, 1998. [Google Scholar]
- Coppersmith, D.; Johnson, D.B.; Matyas, S.M. A proposed mode for triple-DES encryption. IBM J. Res. Dev. 1996, 40, 253–262. [Google Scholar] [CrossRef]
- Milad, A.A.; Muda, H.Z.; Noh, Z.A.; Algaet, M.A. Comparative Study of Performance in Cryptography Algorithms (Blowfish and Skipjack). J. Comput. Sci. 2012, 8, 1191–1197. [Google Scholar]
- Wu, F.; Wu, T.; Yuce, M.R. An Internet-of-Things (IoT) Network System for Connected Safety and Health Monitoring Applications. Sensors 2019, 19, 21. [Google Scholar] [CrossRef] [PubMed]
- Menon, V.G.; Prathap, J.; Priya, J. Ensuring reliable communication in disaster recovery operations with reliable routing technique. Mobile Inf. Syst. 2016, 2016, 9141329. [Google Scholar] [CrossRef]
- Menon, V.G.; Prathap, J. Comparative analysis of opportunistic routing protocols for underwater acoustic sensor networks. In Proceedings of the 2016 International Conference on Emerging Technological Trends (ICETT), Kollam, India, 21–22 October 2016. [Google Scholar]
- Menon, V. Optimized Opportunistic Routing in Highly Dynamic Ad hoc Networks. Preprints 2019, 2019, 020130. [Google Scholar]
- Menon, V.G.; Prathap, J. Performance of various Routing Protocols in Mobile Ad Hoc Networks-A Survey. Res. J. Appl. Sci. Eng. Technol. 2013, 6, 4181–4185. [Google Scholar] [CrossRef]
- Menon, V.G.; Prathap, J. Analyzing the behavior and performance of opportunistic routing protocols in highly mobile wireless ad hoc networks. Int. J. Eng. Technol. 2016, 8, 1916–1924. [Google Scholar] [CrossRef]
- Menon, V.G.; Prathap, P.M.J. Opportunistic routing with virtual coordinates to handle communication voids in mobile ad hoc networks. In Advances in Signal Processing and Intelligent Recognition Systems; Springer: Cham, Switzerland, 2016; pp. 323–334. [Google Scholar]



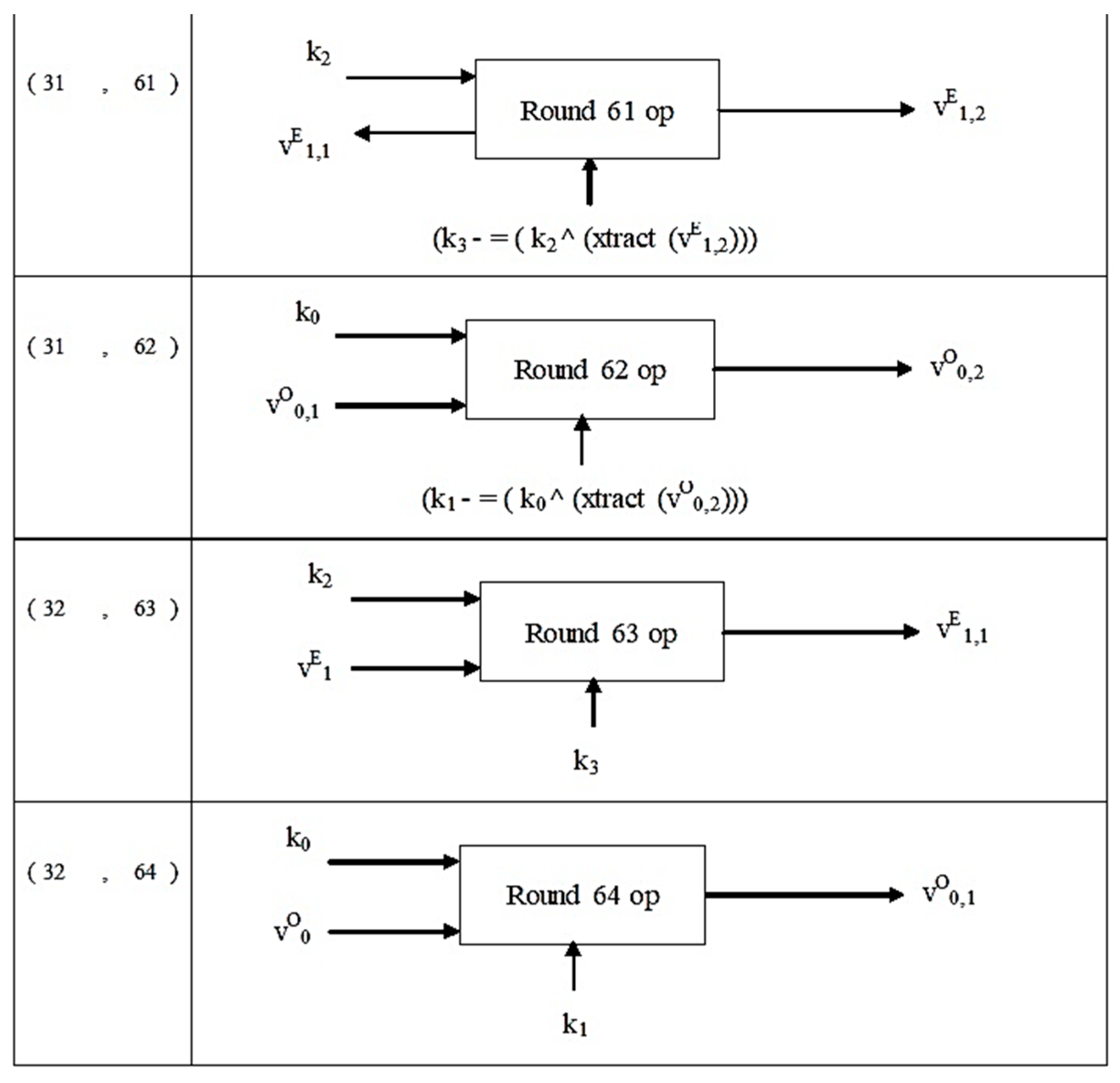

| Algorithm | Developer | Block/Stream Cipher | Key Size | Attack | Algorithm Structure |
|---|---|---|---|---|---|
| DES [41] | IBM | Block cipher (64 bits) | 56 bits | Brute Force Attack | 16 rounds Feistel Structure |
| 3DES [49] | IBM | Block cipher (64 bits) | 112 or 168 bits | chosen-plaintext attack | 48 rounds Feistel Structure |
| IDEA [33] | Lai and James | Block cipher (64 bits) | 128 bits | weak keys | 8 rounds Feistel Structure |
| RC5 [24] | Ron Rivest | Block cipher (32,64,128 bits) | 0–2040 bits | differential attack | (12 round suggested) Feistel Structure |
| TEA [45] | Wheeler and Needham | Block cipher (64 bits) | 128 bits | equivalent key attack | Variable round Feistel Structure |
| XTEA [46] | Wheeler and Needham | Block cipher (64 bits) | 128 bits | related key differential attack | Variable round nested Feistel Structure |
| XXTEA [47] | Wheeler and Needham | Block cipher (64 bits) | 128 bits | chosen-plaintext attack | unbalanced Feistel Network |
| SKIPJACK [50] | National Security Agency (NSA) | Block cipher (64 bits) | 80 bits | slide attack | 32 rounds, unbalanced Feistel Structure |
| AES [40] | Daemen and Rijmen | Block cipher (128 bits) | 128, 192, 256 bits | known plaintext | 20 rounds Feistel Structure |
| MARS [34] | IBM | Block cipher (128 bits) | 128, 192, 256 bits | meet-in-the-middle | 32 rounds Feistel Structure |
| HIGHT [29] | Hong et al. | Block cipher (64 bits) | 128 bits | Impossible Differential attack | light weight block algorithm, effective in hardware |
| FILE SIZE | ENCRYPTION TIME (in milliseconds) | |||
|---|---|---|---|---|
| (IN KILO BYTES) | TEA | XTEA | BLOCK TEA (XXTEA) | NTSA |
| 0.37 | 0.059 | 0.174 | 0.083 | 0.041 |
| 0.95 | 0.125 | 0.244 | 0.155 | 0.112 |
| 1.6 | 0.214 | 0.451 | 0.271 | 0.201 |
| 2.6 | 0.351 | 0.683 | 0.429 | 0.289 |
| 6.8 | 0.771 | 1.384 | 1.768 | 0.551 |
| 8.6 | 0.817 | 2.120 | 1.192 | 0.801 |
| 12.2 | 0.916 | 2.306 | 1.379 | 0.857 |
| 16.2 | 1.544 | 3.744 | 1.981 | 1.211 |
| 26.7 | 1.802 | 4.176 | 2.712 | 1.603 |
| FILE SIZE | DECRYPTION TIME (in milliseconds) | |||
|---|---|---|---|---|
| (IN KILO BYTES) | TEA | XTEA | BLOCK TEA (XXTEA) | NTSA |
| 0.37 | 0.058 | 0.136 | 0.068 | 0.055 |
| 0.95 | 0.123 | 0.289 | 0.156 | 0.112 |
| 1.6 | 0.209 | 0.474 | 0.254 | 0.201 |
| 2.6 | 0.332 | 0.691 | 0.371 | 0.323 |
| 6.8 | 0.753 | 1.369 | 1.73 | 0.655 |
| 8.6 | 0.806 | 2.095 | 1.16 | 0.789 |
| 12.2 | 0.903 | 2.228 | 1.365 | 0.890 |
| 16.2 | 1.537 | 3.698 | 1.959 | 1.234 |
| 26.7 | 1.78 | 4.241 | 2.799 | 1.645 |
| FILE SIZE | ENCRYPTION TIME (in milliseconds) | |||
|---|---|---|---|---|
| (IN KILO BYTES) | TEA | XTEA | BLOCK TEA (XXTEA) | NTSA |
| 0.37 | 0.059 | 0.125 | 0.068 | 0.51 |
| 0.95 | 0.126 | 0.264 | 0.158 | 0.109 |
| 1.6 | 0.198 | 0.423 | 0.232 | 0.189 |
| 2.6 | 0.332 | 0.686 | 0.384 | 0.221 |
| 6.8 | 0.696 | 1.584 | 0.743 | 0.548 |
| 8.6 | 0.948 | 1.669 | 1.171 | 0.899 |
| 12.2 | 1.277 | 2.807 | 1.535 | 1.02 |
| 16.2 | 1.12 | 3.263 | 1.864 | 1.10 |
| 26.7 | 2.209 | 5.207 | 2.224 | 1.983 |
| FILE SIZE | DECRYPTION TIME (in milliseconds) | |||
|---|---|---|---|---|
| (IN KILO BYTES) | TEA | XTEA | BLOCK TEA (XXTEA) | NTSA |
| 0.37 | 0.058 | 0.143 | 0.068 | 0.49 |
| 0.95 | 0.125 | 0.276 | 0.179 | 0.101 |
| 1.6 | 0.195 | 0.43 | 0.233 | 0.174 |
| 2.6 | 0.324 | 0.673 | 0.388 | 0.311 |
| 6.8 | 0.678 | 1.57 | 0.75 | 0.556 |
| 8.6 | 0.936 | 1.641 | 1.21 | 0.889 |
| 12.2 | 1.241 | 2.764 | 1.538 | 1.03 |
| 16.2 | 1.111 | 3.184 | 1.956 | 1.10 |
| 26.7 | 2.179 | 5.178 | 2.193 | 1.989 |
| KEY SIZE | ENCRYPTION TIME (in milliseconds) | |||
|---|---|---|---|---|
| (IN BITS) | TEA | XTEA | BLOCK TEA (XXTEA) | NTSA |
| 32 | 0.125 | 0.287 | 0.145 | 0.07 |
| 48 | 0.125 | 0.264 | 0.162 | 0.083 |
| 64 | 0.125 | 0.246 | 0.17 | 0.088 |
| 96 | 0.126 | 0.265 | 0.158 | 0.093 |
| 128 | 0.126 | 0.264 | 0.158 | 0.097 |
| 160 | 0.114 | 0.271 | 0.154 | 0.100 |
| 192 | 0.125 | 0.279 | 0.144 | 0.100 |
| 240 | 0.125 | 0.279 | 0.145 | 0.113 |
| KEY SIZE | DECRYPTION TIME (in milliseconds) | |||
|---|---|---|---|---|
| (IN BITS) | TEA | XTEA | BLOCK TEA (XXTEA) | NTSA |
| 32 | 0.124 | 0.281 | 0.146 | 0.068 |
| 48 | 0.136 | 0.257 | 0.15 | 0.087 |
| 64 | 0.123 | 0.214 | 0.152 | 0.088 |
| 96 | 0.123 | 0.259 | 0.158 | 0.091 |
| 128 | 0.125 | 0.276 | 0.179 | 0.090 |
| 160 | 0.113 | 0.267 | 0.155 | 0.101 |
| 192 | 0.126 | 0.26 | 0.159 | 0.119 |
| 240 | 0.123 | 0.259 | 0.157 | 0.119 |
| KEY SIZE | ENCRYPTION TIME (in milliseconds) | |||
|---|---|---|---|---|
| (IN BITS) | TEA | XTEA | BLOCK TEA (XXTEA) | NTSA |
| 32 | 1.173 | 2.287 | 1.649 | 1.009 |
| 48 | 1.178 | 2.572 | 1.393 | 1.010 |
| 64 | 1.248 | 2.089 | 1.178 | 1.006 |
| 96 | 1.208 | 2.32 | 1.502 | 1.10 |
| 128 | 1.067 | 2.301 | 1.534 | 1.04 |
| 160 | 1.137 | 2.608 | 1.076 | 1.03 |
| 192 | 1.39 | 2.327 | 1.148 | 1.11 |
| 240 | 1.439 | 2.866 | 1.413 | 1.2 |
| KEY SIZE | DECRYPTION TIME (in milliseconds) | |||
|---|---|---|---|---|
| (IN BITS) | TEA | XTEA | BLOCK TEA (XXTEA) | NTSA |
| 32 | 1.127 | 2.249 | 1.641 | 1.08 |
| 48 | 1.195 | 2.572 | 1.396 | 1.083 |
| 64 | 1.241 | 2.084 | 1.179 | 1.112 |
| 96 | 1.226 | 2.299 | 1.477 | 1.117 |
| 128 | 1.029 | 2.265 | 1.583 | 1.020 |
| 160 | 1.093 | 2.645 | 1.074 | 1.025 |
| 192 | 1.363 | 2.278 | 1.163 | 1.155 |
| 240 | 1.402 | 2.827 | 1.414 | 1.388 |
| KEY SIZE | ENCRYPTION TIME (in milliseconds) | |||
|---|---|---|---|---|
| (IN BITS) | TEA | XTEA | BLOCK TEA (XXTEA) | NTSA |
| 32 | 2.253 | 4.459 | 2.339 | 1.772 |
| 48 | 1.883 | 3.734 | 2.111 | 1.789 |
| 64 | 1.933 | 3.349 | 2.485 | 1.812 |
| 96 | 2.812 | 4.856 | 2.246 | 1.856 |
| 128 | 2.209 | 5.207 | 2.224 | 1.825 |
| 160 | 2.925 | 3.687 | 2.731 | 1.887 |
| 192 | 1.869 | 4.562 | 1.958 | 1.662 |
| 240 | 1.989 | 4.213 | 2.43 | 1.912 |
| KEY SIZE | DECRYPTION TIME (in milliseconds) | |||
|---|---|---|---|---|
| (IN BITS) | TEA | XTEA | BLOCK TEA (XXTEA) | NTSA |
| 32 | 2.212 | 4.422 | 2.387 | 1.701 |
| 48 | 1.854 | 3.713 | 2.136 | 1.746 |
| 64 | 1.888 | 3.307 | 2.516 | 1.777 |
| 96 | 2.726 | 4.892 | 2.289 | 1.834 |
| 128 | 2.179 | 5.178 | 2.193 | 1.820 |
| 160 | 2.883 | 3.668 | 2.711 | 1.811 |
| 192 | 1.853 | 4.498 | 1.935 | 1.812 |
| 240 | 1.934 | 4.073 | 2.456 | 1.936 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rajesh, S.; Paul, V.; Menon, V.G.; Khosravi, M.R. A Secure and Efficient Lightweight Symmetric Encryption Scheme for Transfer of Text Files between Embedded IoT Devices. Symmetry 2019, 11, 293. https://doi.org/10.3390/sym11020293
Rajesh S, Paul V, Menon VG, Khosravi MR. A Secure and Efficient Lightweight Symmetric Encryption Scheme for Transfer of Text Files between Embedded IoT Devices. Symmetry. 2019; 11(2):293. https://doi.org/10.3390/sym11020293
Chicago/Turabian StyleRajesh, Sreeja, Varghese Paul, Varun G. Menon, and Mohammad R. Khosravi. 2019. "A Secure and Efficient Lightweight Symmetric Encryption Scheme for Transfer of Text Files between Embedded IoT Devices" Symmetry 11, no. 2: 293. https://doi.org/10.3390/sym11020293
APA StyleRajesh, S., Paul, V., Menon, V. G., & Khosravi, M. R. (2019). A Secure and Efficient Lightweight Symmetric Encryption Scheme for Transfer of Text Files between Embedded IoT Devices. Symmetry, 11(2), 293. https://doi.org/10.3390/sym11020293






