A Lightweight and Provable Secured Certificateless Signcryption Approach for Crowdsourced IIoT Applications
Abstract
:1. Introduction
1.1. Motivation and Contributions
- The scheme is using the concept of identity-based cryptosystem which suffers from the key escrow problem;
- Also, they used the mathematical concepts of bilinear pairing for the proposed scheme which needs huge computational power;
- Because of bilinear pairing, the scheme needs high bandwidth;
- The scheme does not fulfill the security property of resisting against a replay attack and forward secrecy;
- They did not validate the security requirement of their proposed scheme by utilizing the formal security validation tools like AVISPA, Scyther, etc.
- The scheme has just provided the authentication of IIoT crowdsourced data;
- Also, they used the mathematical concepts of bilinear pairing for the proposed scheme which needs high computational power;
- Because of bilinear pairing, the scheme needs high bandwidth.
- The scheme does not fulfill the security property of resisting against replay attack, confidentiality, and forward secrecy;
- The authentication of the scheme is not validated through the formal security validation tools like AVISPA, Scyther, etc.
- We design certificatelesssigncryption for crowdsourced IIoT based on the hyper elliptic curve;
- We remove the key escrow problem;
- We will showthe results for proving the efficiency in term of computational cost and communication overhead;
- Our scheme will provide security services such as confidentiality, anti-replay attack, integrity, authentication, sender authentication, message authentication, and unforgeability, respectively;
- We will validate our scheme security services through a well-known simulation tool AVISPA with the help of HLPSL language.
1.2. Outlines of Paper
2. Related Work
3. Preliminary
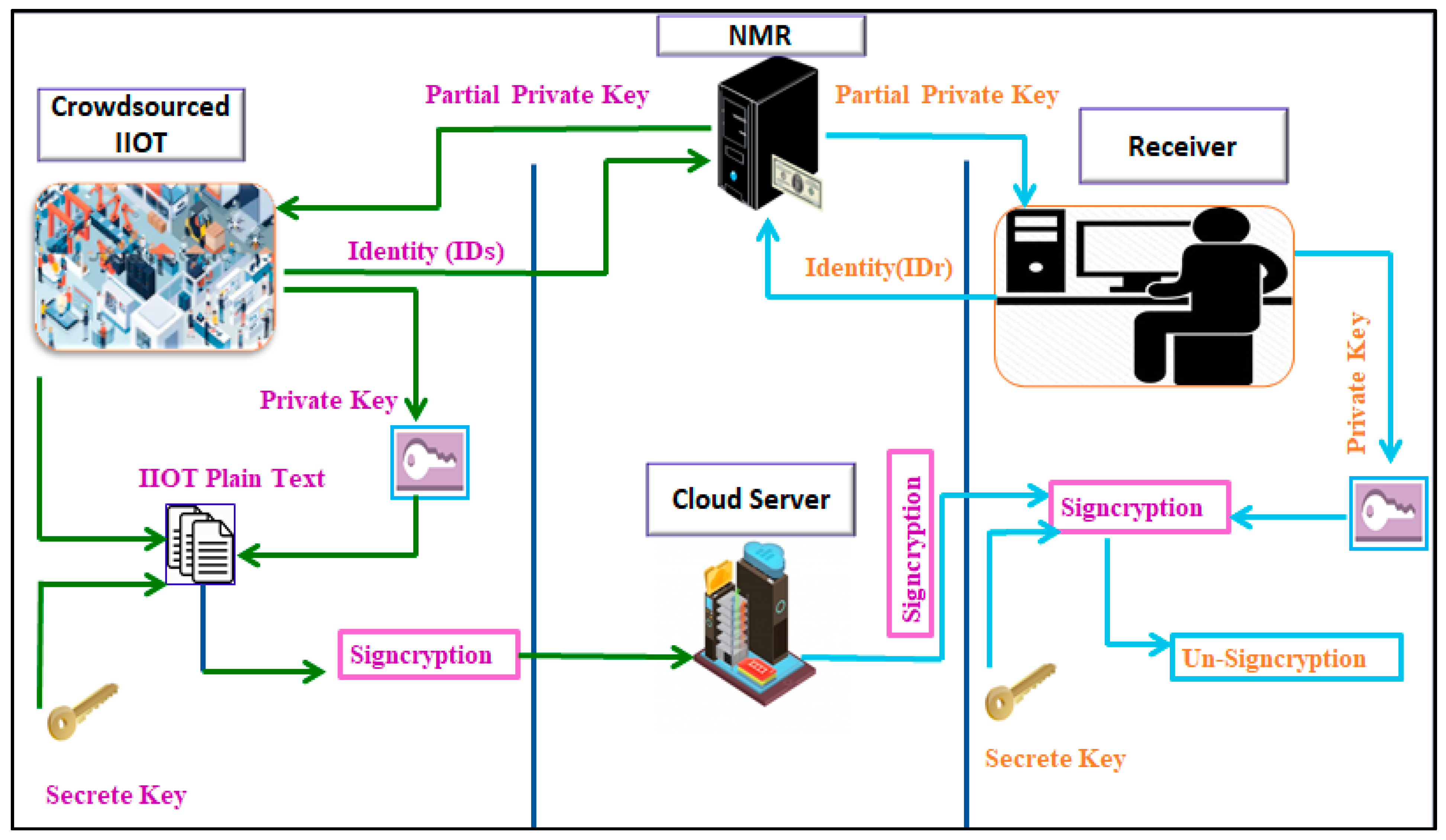
4. Proposed Model
5. Generic Model for Certificateless Signcryption
5.1. Setup (STP)
5.2. User Key Generation (UKG)
5.3. Set Partial Private Key (SPPK)
5.4. Set Private Key (SPK)
5.5. CertificatelessSigncryption (CLSN)
5.6. CL-Unsigncryption (CLUS)
6. Proposed CertificatelessSigncryption
6.1. STP
6.2. SPPK
6.3. UKG
6.4. SPK
6.5. CLSN
6.6. CLUS
7. Correctness
8. Security Analysis
8.1. Confidentiality
8.2. Replay Attack
8.3. Integrity
8.4. Authentication
8.5. Unforgeability
9. Computational Cost
- The proposed scheme reduced at the computational time from AIK [27] is 4EX + 1BP − 7HDM/ 4EX + 1BP = 22.19 − 3.36/22.19 = 0.84*100 = 84.85%.
- The proposed scheme computational cost reduction From ASGMPM [8] is 6EX + 2BP − 7HDM/6EX + 2BP= 40.44 − 3.36/40.44 = 0.91*100 = 91.69%.
- The proposed scheme computational cost reduction from PM [47] is 8EX + 9BP − 7HDM/8EX + 9BP = 144.73 − 3.36/144.73 = 0.97*100 = 97%.
- The proposed scheme computational cost reduction from HB [48] is 10EX − 7HDM/10EX = 19.7 − 3.36/19.7 = 0.82*100 = 82.94%.
- The proposed scheme computational cost reduction from ZC [50] is 12EX + 5BP − 7HDM /12EX + 5BP = 95.19 − 3.36/95.19 = 0.96*100 = 96.47%.
- The proposed scheme computational cost reduction from LW [51] is 12EM − 7HDM /12EM = 11.64 − 3.36/11.64 = 0.71*100 = 71.13%.
- The proposed scheme computational cost reduction from LM [52] is 7EM − 7HDM /7EM = 6.79 − 3.36/6.79 = 0.50*100 = 50.51%.
10. Communication Overhead
11. Conclusions
12. Future Work
Author Contributions
Funding
Conflicts of Interest
Appendix A. Implementation and Validation
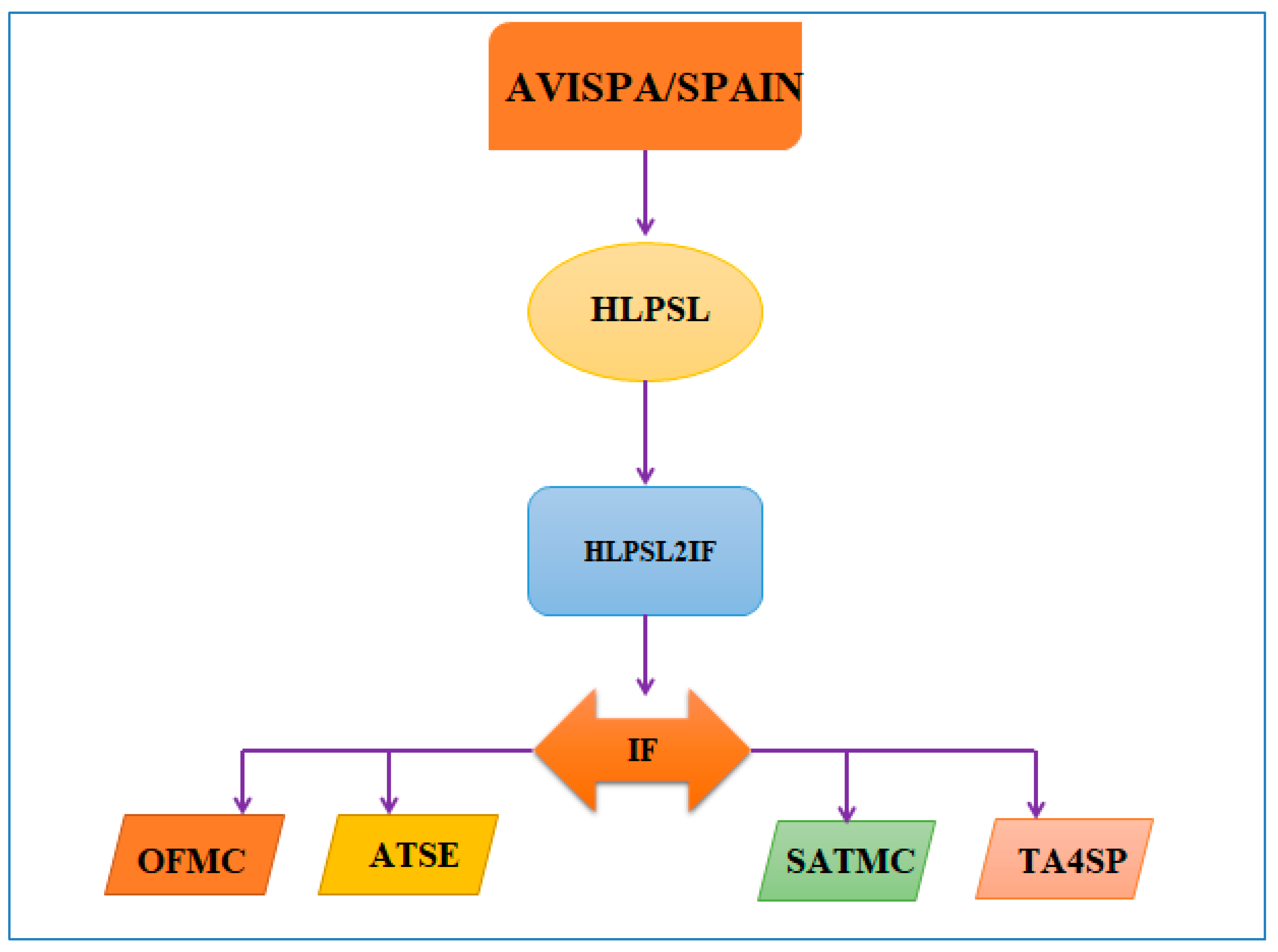
| role role_Clsn(Clsn:agent, Clus:agent,Ys:public_key, Yr:public_key, SND,RCV:channel(dy)) played_byClsn def= local State:nat,Nc:text,H:text,Y:text, M:text,En:hash_func,K:symmetric_key init State := 0 transition 1. State=0 /\ RCV(start) =|> State’:=1 /\ SND(Clsn.Clus) 2. State=1 /\ RCV(Clus.{Nc’}_Yr) =|> State’:=2 /\ Y’:=new() /\ H’:=new() /\ K’:=new() /\ M’:=new() /\ secret(M’,sec_2,{Clsn}) /\ witness(Clsn,Clus,auth_1,M’) /\ SND(Clsn.{En(M’)}_K’.{H’.Y’}_inv(Ys)) end role |
| role role_Clus(Clsn:agent,Clus:agent, Ys:public_key,Yr:public_key, SND,RCV:channel(dy)) played_byClus def= local State:nat,Nc:text,H:text,Y:text,M:text, En:hash_func,K:symmetric_key init State := 0 transition 1. State=0 /\ RCV(Clsn.Clus) =|> State’:=1 /\ Nc’:=new() /\ SND(Clus.{Nc’}_Yr) 6. State=1 /\ RCV(Clsn.{En(M’)}_K’.{H’.Y’}_inv(Ys)) =|> State’:=2 /\ request(Clus,Clsn,auth_1,M’) /\ secret(M’,sec_2,{Clsn}) end role |
| role session1(Clsn:agent,Clus:agent, Ys:public_key,Yr:public_key) def= local SND2,RCV2,SND1,RCV1:channel(dy) composition role_Clus(Clsn,Clus,Ys,Yr,SND2,RCV2) /\ role_Clsn(Clsn,Clus,Ys,Yr,SND1,RCV1) end role role session2(Clsn:agent,Clus:agent, Ys:public_key,Yr:public_key) def= local SND1,RCV1:channel(dy) composition role_Clsn(Clsn,Clus,Ys,Yr,SND1,RCV1) end role |
| role environment() def= const hash_0:hash_func,ys:public_key,alice:agent,bob:agent,yr:public_key,const_1:agent,const_2:public_key,const_3:public_key,auth_1:protocol_id,sec_2:protocol_id intruder_knowledge = {alice,bob} composition session2(i,const_1,const_2,const_3) /\ session1(alice,bob,ys,yr) end role |
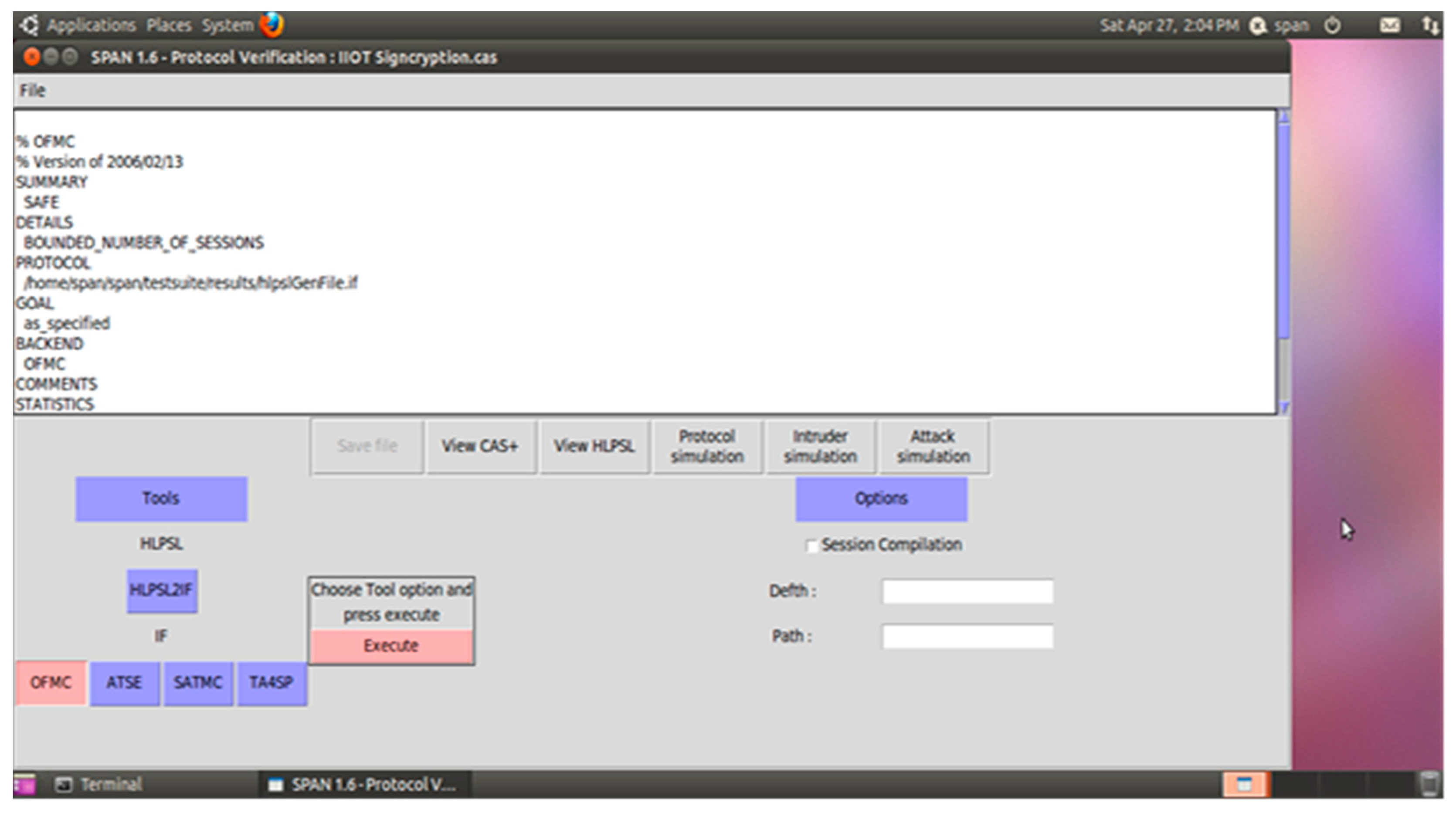
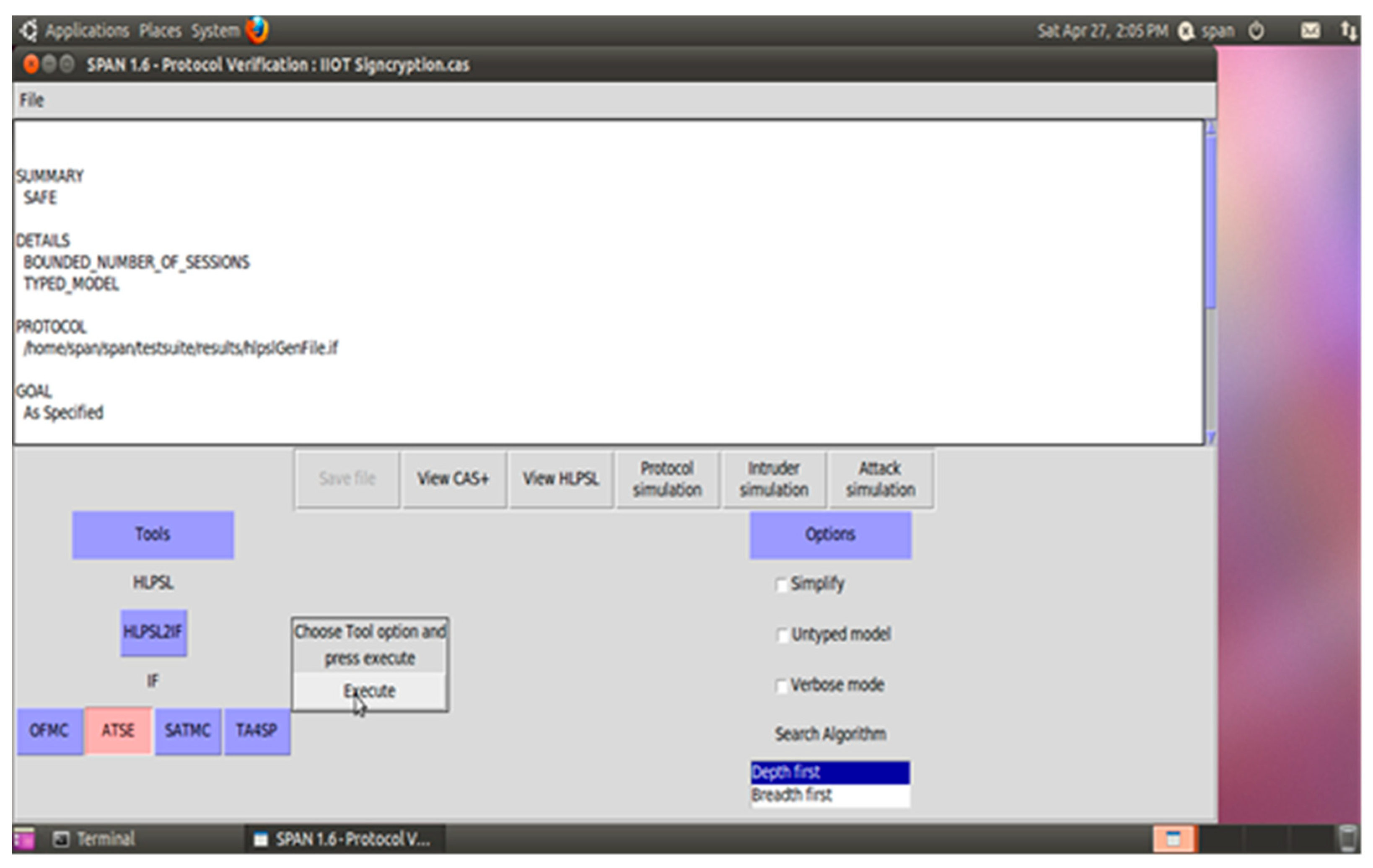
References
- Shen, L.; Ma, J.; Liu, X.; Wei, F.; Miao, M. A Secure and Efficient ID-Based Aggregate Signature Scheme for Wireless Sensor Networks. IEEE Internet Things J. 2017, 4, 546–554. [Google Scholar] [CrossRef]
- Liao, Y.; Loures, E.D.F.R.; Deschamps, F. Industrial Internet of Things: A Systematic Literature Review and Insights. IEEE Internet Things J. 2018, 5, 4515–4525. [Google Scholar] [CrossRef]
- Cohensius, G.; Ben-Porat, O.; Meir, R.; Amir, O. Efficient Crowdsourcing via Proxy Voting. arXiv 2018, arXiv:1806.06257. [Google Scholar]
- Kazai, G.; Kamps, J.; Koolen, M.; Milic-Frayling, N. Crowdsourcing for book search evaluation: Impact of hit design on comparative system ranking. In Proceedings of the 34th International ACM SIGIR Conference on Research and Development in Information Retrieval, Beijing, China, 25–29 July 2011; pp. 205–214. [Google Scholar]
- Vuurens, J.; de Vries, A.P.; Eickhoff, C. How much spam can you take? An analysis of crowdsourcing results to increase accuracy. In Proceedings of the ACM SIGIR Workshop on Crowdsourcing for Information Retrieval (CIR11), Beijing, China, 28 July 2011; pp. 21–26. [Google Scholar]
- Wais, P.; Lingamneni, S.; Cook, D.; Fennell, J.; Goldenberg, B.; Lubarov, D.; Marin, D.; Simons, H. Towards building a high-quality workforce with mechanical turk. In Proceedings of the Computational Social Science and the Wisdom of Crowds (NIPS), Whistler, BC, Canada, 10 December 2010; pp. 1–5. [Google Scholar]
- Quinn, A.J.; Bederson, B.B. Human computation: A survey and taxonomy of a growing field. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Vancouver, BC, Canada, 7–12 May 2011; pp. 1403–1412. [Google Scholar]
- Karati, A.; Islam, S.H.; Biswas, G.P.; Bhuiyan, M.Z.A.; Vijayakumar, P.; Karuppiah, M. Provably Secure Identity-Based Signcryption Scheme for Crowdsourced Industrial Internet of Things Environments. IEEE Internet Things J. 2018, 5, 2904–2914. [Google Scholar] [CrossRef]
- Zheng, Y. Digital signcryption or how to achieve cost (signature & encryption)? cost (signature)+ cost (encryption). In Advances in Cryptology-CRYPTO’97; Springer: Berlin/Heidelberg, Germany, 1997; pp. 165–179. [Google Scholar]
- Chen, H.; Chen, S.; Xu, H.; Hu, B. A Security Scheme of 5G Ultradense Network Based on the Implicit Certificate. Wirel. Commun. Mob. Comput. 2018, 2018, 8562904. [Google Scholar] [CrossRef]
- Kumar, N.C.; Basit, A.; Singh, P.; Venkaiah, V.C. Lightweight Cryptography for Distributed PKI Based MANETS. arXiv 2018, arXiv:1804.06313. [Google Scholar]
- Ullah, S.; Marcenaro, L.; Rinner, B. Secure Smart Cameras by Aggregate-Signcryption with Decryption Fairness for Multi-Receiver IoT Applications. Sensors 2019, 19, 327. [Google Scholar] [CrossRef]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Proceedings of the Advances in Cryptology-CRYPTO’84, LNCS 196, Santa Barbara, CA, USA, 19–22 August 1984; pp. 47–53. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-based encryption from the weil pairing. In Proceedings of the Advances in Cryptology-CRYPTO’01, LNCS 2139, Santa Barbara, CA, USA, 19–23 August 2001; pp. 213–229. [Google Scholar]
- Malone-Lee, J. Identity Based Signcryption. In Cryptology ePrint Archive Report; IACR: Lyon, France, 2002. [Google Scholar]
- Al-Riyami, S.; Paterson, K. Certificateless Public Key Cryptography. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Berlin, Germany, 30 November–4 December 2003; pp. 452–473. [Google Scholar]
- Barbosa, M.; Farshim, P. Certificateless Signcryption. In Proceedings of the ASICC, Tokyo, Japan, 18–20 March 2008; ACM: New York, NY, USA, 2008; pp. 18–20. [Google Scholar]
- Suárez-Albela, M.; Fraga-Lamas, P.; Fernández-Caramés, T.M. A Practical Evaluation on RSA and ECC-Based Cipher Suites for IoT High-Security Energy-Efficient Fog and Mist Computing Devices. Sensors 2018, 18, 3868. [Google Scholar] [CrossRef]
- Yu1, M.; Zhang, J.; Wang, J.; Gao1, J.; Xu1, T.; Deng, R.; Zhang, Y.; Yu, R. Internet of Things security and privacy-preserving method through nodes differentiation, concrete cluster centers, multi-signature, and blockchain. Int. J. Distrib. Sens. Netw. 2018, 14, 1–15. [Google Scholar]
- Braeken, A. PUF Based Authentication Protocol for IoT. Symmetry 2018, 10, 352. [Google Scholar] [CrossRef]
- Zhou, C.; Zhao, Z.; Zhou, W.; Mei, Y. Certificateless Key-Insulated Generalized Signcryption Scheme without Bilinear Pairings. Secur. Commun. Netw. 2017, 2017, 8405879. [Google Scholar] [CrossRef]
- Kumari, S.; Karuppiah, M.; Das, A.K.; Li, X.; Wu, F.; Kumar, N. A secure authentication scheme based on elliptic curve cryptography for IoT and cloud servers. J. Supercomput. 2017, 74, 6428–6453. [Google Scholar] [CrossRef]
- Omala, A.; Mbandu, A.; Mutiria, K.; Jin, C.; Li, F. Provably Secure Heterogeneous Access Control Scheme for Wireless Body Area Network. J. Med Syst. 2018, 42. [Google Scholar] [CrossRef] [PubMed]
- Tamizhselvan, C.; Vijayalakshmi, V. An Energy Efficient Secure Distributed Naming Service for IoT. Int. J. Adv. Stud. Sci. Res. 2019, 3. [Google Scholar]
- Naresh, V.; Sivaranjani, R.; Murthy, N.V.E.S. Provable secure lightweight hyper elliptic curve-based communication system for wireless sensor networks. Int. J. Commun. Syst. 2018, 31, e3763. [Google Scholar] [CrossRef]
- Rahman, A.; Ullah, I.; Naeem, M.; Anwar, R.; Khattak, H.; Ullah, S. A Lightweight Multi-Message and Multi-Receiver Heterogeneous Hybrid Signcryption Scheme based on Hyper Elliptic Curve. Int. J. Adv. Comput. Sci. Appl. 2018, 9. [Google Scholar] [CrossRef] [Green Version]
- Karati, A.; Islam, S.H.; Karuppiah, M. Provably Secure and Lightweight Certificateless Signature Scheme for IIoT Environments. IEEE Trans. Ind. Inform. 2018, 14, 3701–3711. [Google Scholar] [CrossRef]
- Mehmood, A.; Noor-Ul-Amin, I.; Umar, A.I. Public Verifiable Generalized Authenticated Encryption based on Hyper Elliptic Curve. J. Appl. Environ. Biol. Sci. 2017, 7, 194–200. [Google Scholar]
- Ming, Y.; Wang, Y. Cryptanalysis of an identity based signcryption scheme in the standard model. Int. J. Netw. Secur. Appl. 2016, 18, 165–171. [Google Scholar]
- Nayak, B. A secure ID-based signcryption scheme based on elliptic curve cryptography. Int. J. Comput. Intell. Stud. 2017, 6, 150. [Google Scholar] [CrossRef]
- Ashibani, Y.; Mahmoud, Q.H. An efficient and secure scheme for smart home communication using identity-based signcryption. In Proceedings of the IEEE 36th International Performance Computing and Communications Conference (IPCCC), Phoenix, AZ, USA, 10–12 December 2017. [Google Scholar]
- Huang, Y.; Yang, J. A Novel Identity-Based Signcryption Scheme in the Standard Model. Information 2017, 8, 58. [Google Scholar] [CrossRef]
- Tsai, T.-T.; Huang, S.-S.; Tseng, Y.-M. SIBSC: Separable Identity-Based Signcryption for Resource-Constrained Devices. Informatica 2017, 28, 193–214. [Google Scholar] [CrossRef] [Green Version]
- Yu, H.; Wang, Z.; Li, J.; Gao, X. Identity-Based Proxy Signcryption Protocol with Universal Composability. Secur. Commun. Netw. 2018, 2018, 9531784. [Google Scholar] [CrossRef]
- Zhou, C.; Zhou, W.; Dong, X. Provable certificateless generalized signcryption scheme. Des. Codes Cryptogr. 2012, 71, 331–346. [Google Scholar] [CrossRef]
- Shi, W.; Kumar, N.; Gong, P.; Zhang, Z. Cryptanalysis and improvement of a certificateless signcryption scheme without bilinear pairing. Front. Comput. Sci. 2014, 8, 656–666. [Google Scholar] [CrossRef]
- Liu, Z.; Hu, Y.; Zhang, X.; Ma, H. Certificateless signcryption scheme in the standard model. Inf. Sci. 2010, 180, 452–464. [Google Scholar] [CrossRef]
- Selvi, S.S.D.; Vivek, S.S.; Rangan, C.P. Security weaknesses in two certificateless signcryption schemes. In IACR Cryptology ePrint Archive; IACR: Lyon, France, 2010. [Google Scholar]
- Jin, Z.P.; Wen, Q.Y.; Zhang, H. A supplement to Liu et al.’s certificateless signcryption scheme in the standard model. In IACR ePrint Archive; IACR: Lyon, France, 2010. [Google Scholar]
- Weng, J.; Yao, G.; Deng, R.H.; Chen, M.-R.; Li, X. Cryptanalysis of a certificateless signcryption scheme in the standard model. Inf. Sci. 2011, 181, 661–667. [Google Scholar] [CrossRef]
- Miao, S.; Zhang, F.; Li, S.; Mu, Y. On security of a certificateless signcryption scheme. Inf. Sci. 2013, 232, 475–481. [Google Scholar] [CrossRef] [Green Version]
- Xiong, H. Toward certificateless signcryption scheme without random oracle. In IACR ePrint Archive; IACR: Lyon, France, 2014. [Google Scholar]
- Cheng, L.; Wen, Q.Y. An improved certificateless signcryption in the standard model. Int. J. Netw. Secur. 2015, 17, 597–606. [Google Scholar]
- Wahid, A.; Mambo, M. Implementation of Certificateless Signcryption based on Elliptic Curve Using Javascript. Int. J. Comput. Inform. (IJCANDI) 2016, 1, 90–100. [Google Scholar]
- Zhou, C.; Gao, G.; Cui, Z. Certificateless Signcryption in the Standard Model. Wirel. Pers. Commun. 2016, 92, 495–513. [Google Scholar] [CrossRef]
- Rastegari, P.; Berenjkoub, M. An Efficient Certificateless Signcryption Scheme in the Standard Model. ISC Int. J. Inf. Secur. 2017, 9, 3–16. [Google Scholar] [CrossRef]
- Yu, H.; Yang, B. Pairing-Free and Secure Certificateless Signcryption Scheme. Comput. J. 2017, 60, 1187–1196. [Google Scholar] [CrossRef]
- Lin, X.-J.; Sun, L.; Qu, H.; Liu, D. Cryptanalysis of A Pairing-Free Certificateless Signcryption Scheme. Comput. J. 2017, 61, 539–544. [Google Scholar] [CrossRef]
- Zhou, C. Certificateless Signcryption Scheme without Random Oracles. Chin. J. Electron. 2018, 27, 1002–1008. [Google Scholar] [CrossRef]
- Cao, L.; Ge, W. Analysis of Certificateless Signcryption Schemes and Construction of a Secure and Efficient Pairing-free one based on ECC. Ksii Trans. Internet Inf. Syst. 2018, 12, 4527–4547. [Google Scholar]
- Luo, W.; Ma, W. Secure and Efficient Data Sharing Scheme Based on Certificateless Hybrid Signcryption for Cloud Storage. Electronics 2019, 8, 590. [Google Scholar] [CrossRef]
- Koblitz, N. Hyper elliptic crypto systems. J. Cryptol. 1989, 1, 139–150. [Google Scholar] [CrossRef]
- Wollinger, T.; Pelzl, J.; Paar, C. Cantor versus Harley: Optimization and analysis of explicit formulae for hyperelliptic curve cryptosystems. IEEE Trans. Comput. 2005, 54, 861–872. [Google Scholar] [CrossRef]
- Wollinger, T.; Pelzl, J.; Wittelsberger, V.; Paar, C.; Saldamli, G.; Koç, Ç. Elliptic and hyperelliptic curves on embedded μP. Acm Trans. Embed. Comput. Syst. 2004, 3, 509–533. [Google Scholar] [CrossRef]
- Fan, X.; Wollinger, T.; Gong, G. Efficient explicit formulae for genus 3 hyperelliptic curve cryptosystems over binary fields. IET Inf. Secur. 2007, 1, 65. [Google Scholar] [CrossRef]
- Zhou, C. An improved lightweight certificateless generalized signcryption scheme for mobile-health system. Int. J. Distrib. Sensor Netw. 2019, 15, 1–16. [Google Scholar] [CrossRef]
- Ullah, I.; Amin, N.U.-A.; Naeem, M.; Khattak, H.; Khattak, S.J.; Ali, H. A Novel Provable Secured Signcryption Scheme PSSS: A Hyper-Elliptic Curve-Based Approach. Mathematics 2019, 7, 686. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Lee, K.; Park, K.; Park, Y. Secure Authentication Protocol for Wireless Sensor Networks in Vehicular Communications. Sensors 2018, 18, 3191. [Google Scholar] [CrossRef]
- Qiu, S.; Xu, G.; Ahmad, H.; Guo, Y. An enhanced password authentication scheme for session initiation protocol with perfect forward secrecy. PLoS ONE 2018, 13, e0194072. [Google Scholar] [CrossRef]
- Ali, R.; Pal, A.K. Three-Factor-Based Confidentiality-Preserving Remote User Authentication Scheme in Multi-server Environment. Arab. J. Sci. Eng. 2017, 42, 3655–3672. [Google Scholar] [CrossRef]
- Jung, J.; Kang, D.; Lee, D.; Won, D. An Improved and Secure Anonymous Biometric-Based User Authentication with Key Agreement Scheme for the Integrated EPR Information System. PLoS ONE 2017, 12, e0169414. [Google Scholar] [CrossRef]
| No | Notation | Description |
|---|---|---|
| 1 | Hℇ | Hyper elliptic curve |
| 2 | Divisor of hyper elliptic curve | |
| 3 | Means genus on a hyper elliptic curve | |
| 4 | 𝒽 | Irreversible hash function |
| 5 | IDs | Identity of the IIoT data owner/ CLSR |
| 6 | IDr | Identity of the data consumer/ CLUR |
| 7 | s,r | The public keys of data owner/ CLSR and data consumer/ CLUR |
| 8 | 𝘗s = (s,δs) | The private key pair of IIoT data owner/ CLSR |
| 9 | 𝘗r = (r,δr) | The private key pair of data consumer/ CLUR |
| 10 | It is the largest prime number of Hℇ and = 280 | |
| 11 | Nc | It is the nonce |
| 12 | 𝓂, | Represents the plaintext and cipher text |
| 13 | K | Shared secret key |
| 14 | EK, DK | Means encryption and decryption |
| 15 | S | Means digital signature |
| 16 | Ω | Means signcryption tuple |
| Schemes | Signature/Signcryption | Verification/Un-Signcryption | Total |
|---|---|---|---|
| AIK [27] | 2EX | 2EPX + 1BP | 4EX + 1BP |
| ASGMPM [8] | 4EX | 2EX + 2BP | 6EX + 2BP |
| PM [47] | 7EX + 2BP | 1EX + 7BP | 8EX + 9BP |
| HB [48] | 5EX | 5EX | 10EX |
| ZC [50] | 7EX + 1BP | 5EX + 4BP | 12EX + 5BP |
| LW [51] | 7EM | 5EM | 12EM |
| LM [52] | 4 EM | 3 EM | 7 EM |
| Proposed Scheme | 4HDM | 3HDM | 7HDM |
| Schemes | Signature/Signcryption (ms) | Verification/ Un-Signcryption (ms) | Total (ms) |
|---|---|---|---|
| AIK [27] | 3.94 | 18.25 | 22.19 |
| ASGMPM [8] | 7.88 | 32.56 | 40.44 |
| PM [47] | 42.59 | 102.14 | 144.73 |
| HB [48] | 9.85) | 9.85 | 19.7 |
| ZC [50] | 28.1 | 67.09 | 95.19 |
| LW [51] | 6.79 | 4.85 | 11.64 |
| LM [52] | 3.88 | 2.91 | 6.79 |
| Proposed Scheme | 1.92 | 1.44 | 3.36 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ullah, I.; Ul Amin, N.; Zareei, M.; Zeb, A.; Khattak, H.; Khan, A.; Goudarzi, S. A Lightweight and Provable Secured Certificateless Signcryption Approach for Crowdsourced IIoT Applications. Symmetry 2019, 11, 1386. https://doi.org/10.3390/sym11111386
Ullah I, Ul Amin N, Zareei M, Zeb A, Khattak H, Khan A, Goudarzi S. A Lightweight and Provable Secured Certificateless Signcryption Approach for Crowdsourced IIoT Applications. Symmetry. 2019; 11(11):1386. https://doi.org/10.3390/sym11111386
Chicago/Turabian StyleUllah, Insaf, Noor Ul Amin, Mahdi Zareei, Asim Zeb, Hizbullah Khattak, Ajab Khan, and Shidrokh Goudarzi. 2019. "A Lightweight and Provable Secured Certificateless Signcryption Approach for Crowdsourced IIoT Applications" Symmetry 11, no. 11: 1386. https://doi.org/10.3390/sym11111386





