Internet of Things Meets Vehicles: Sheltering In-Vehicle Network through Lightweight Machine Learning
Abstract
:1. Introduction
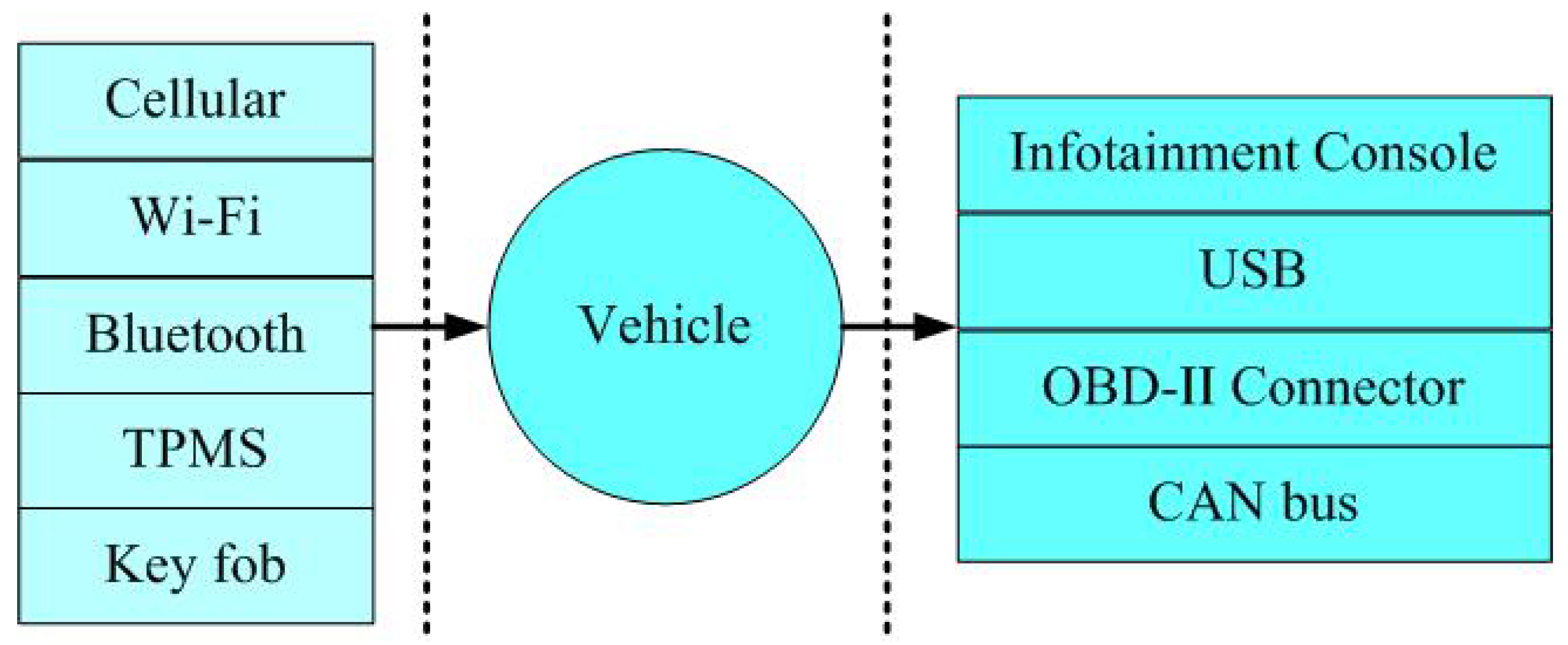
1.1. Internet of Things Meets Vehicles
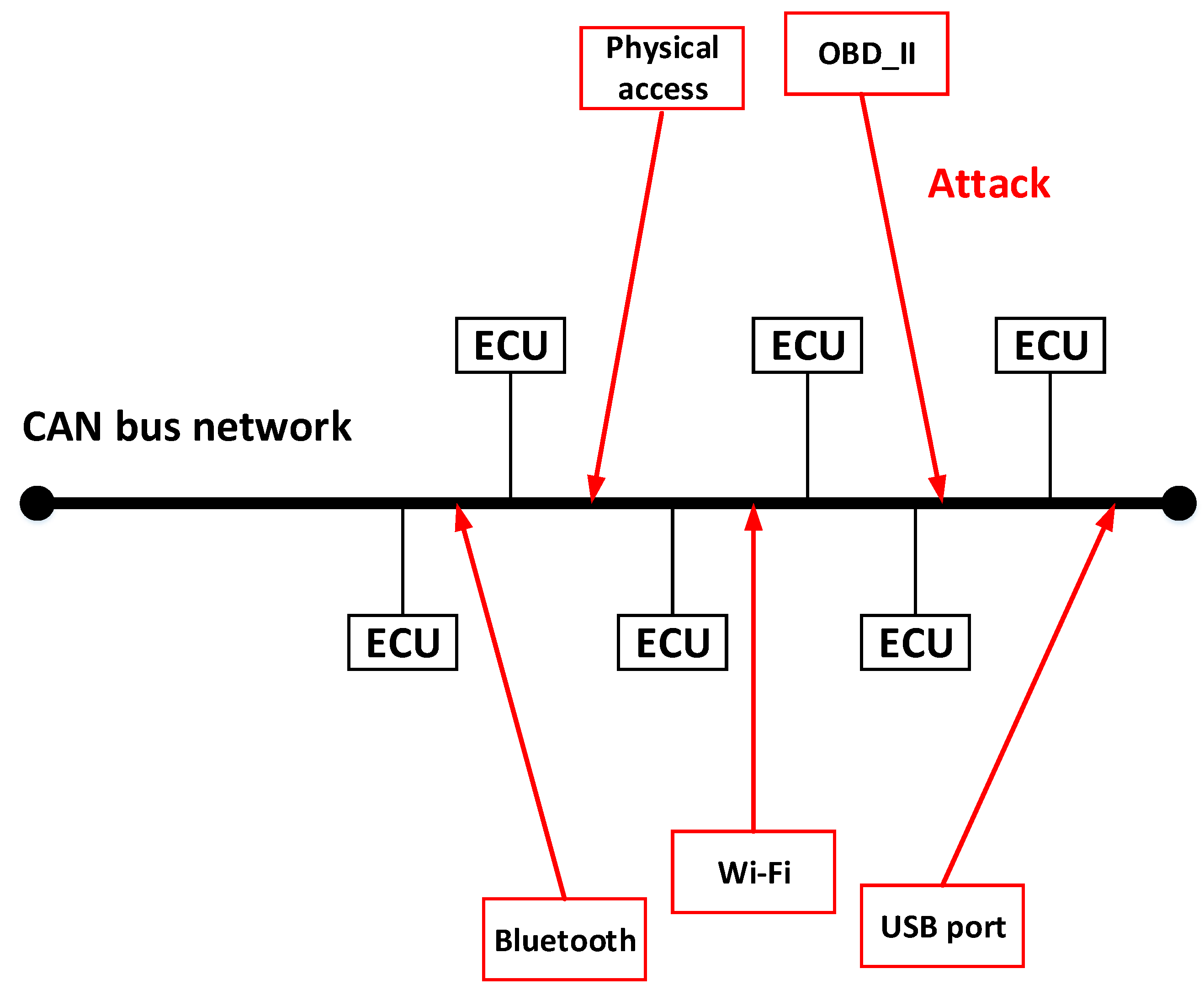
1.2. Attack Surfaces
1.3. Can Bus
1.4. Our Contributions
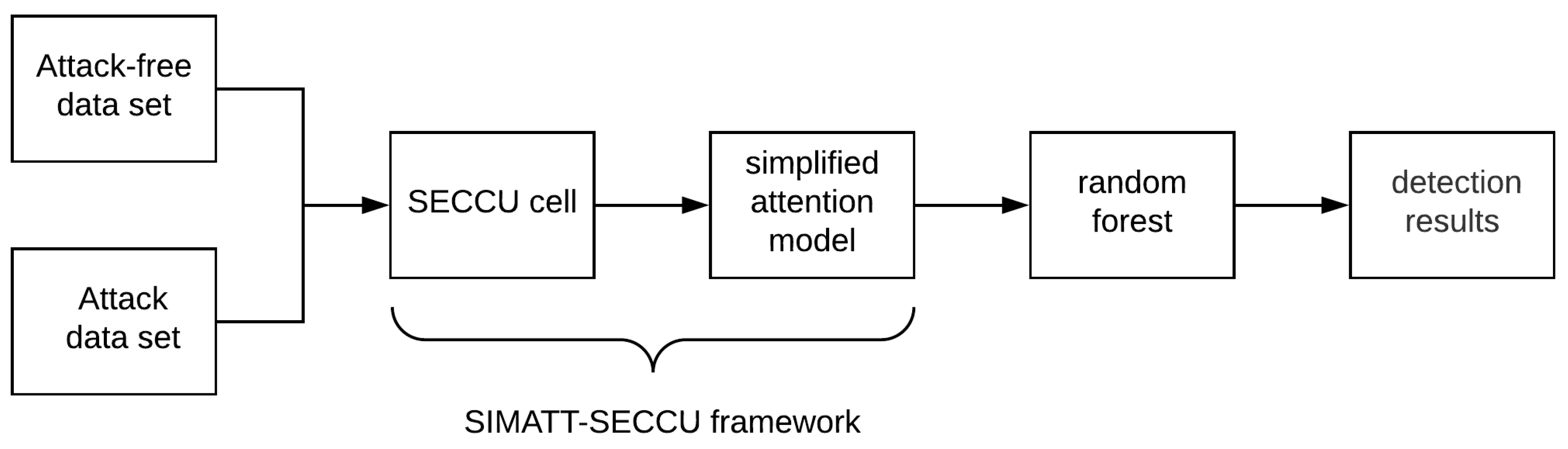
- To suit the actual situation of an in-vehicle network, we present a new recurrent neural network (RNN) model named SECCU.
- We propose the simplified attention (SIMATT) model that can be computed using the computing power of vehicle electronics and improve detection accuracy.
- The experimental results demonstrate that our proposed SIMATT-SECCU symmetry framework has the best performance in comparison with many classic models.
- Our detecting model is fully data-driven and does not require any domain knowledge about the CAN protocol.
- Our proposed model focuses on a lightweight anomaly detection method for in-vehicle network based on machine learning, which solves the problem of insufficient computing power of networked vehicle electronic devices when applying machine learning algorithms.
2. Related Work
3. Recurrent Neural Network
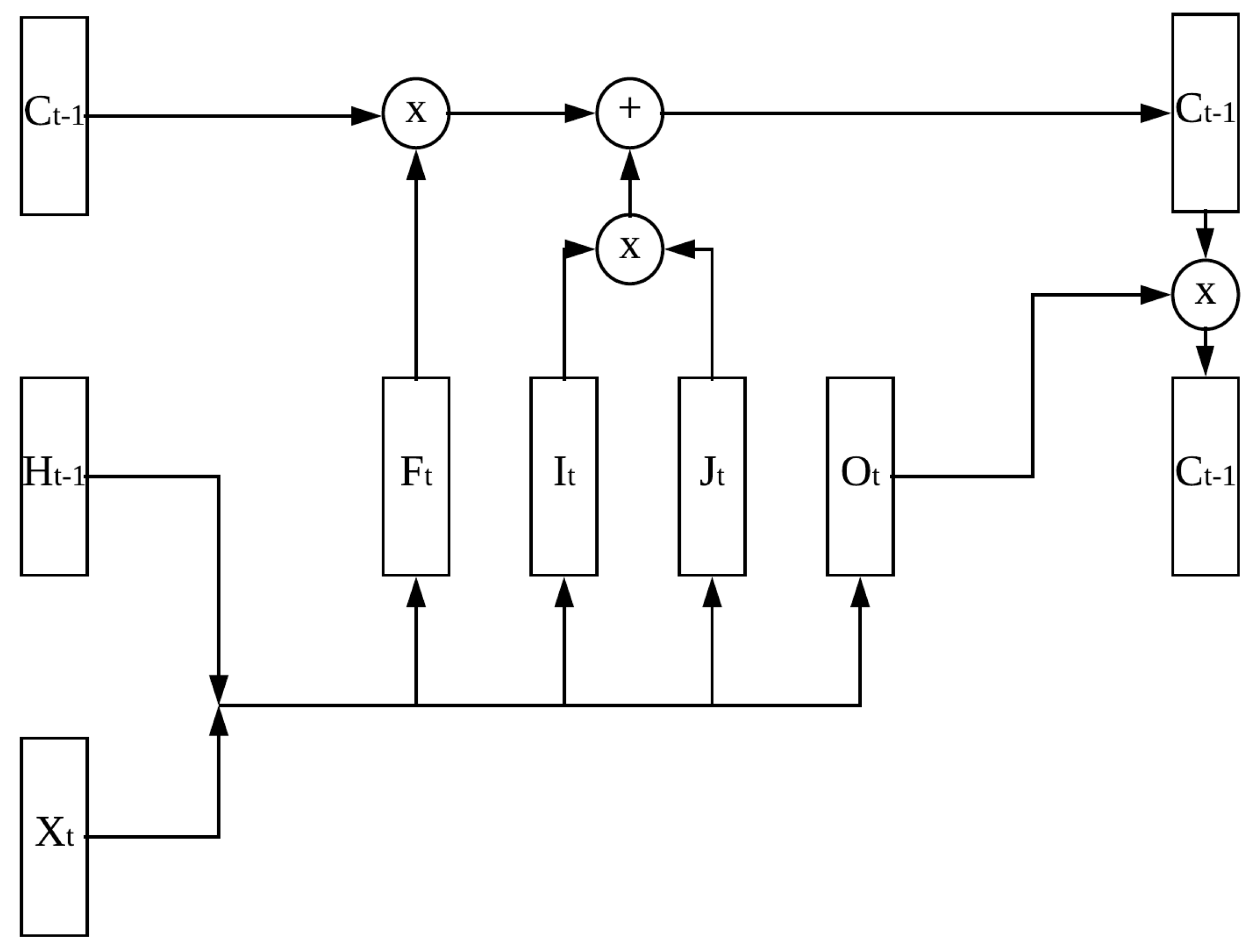
3.1. Long Short-Term Memory
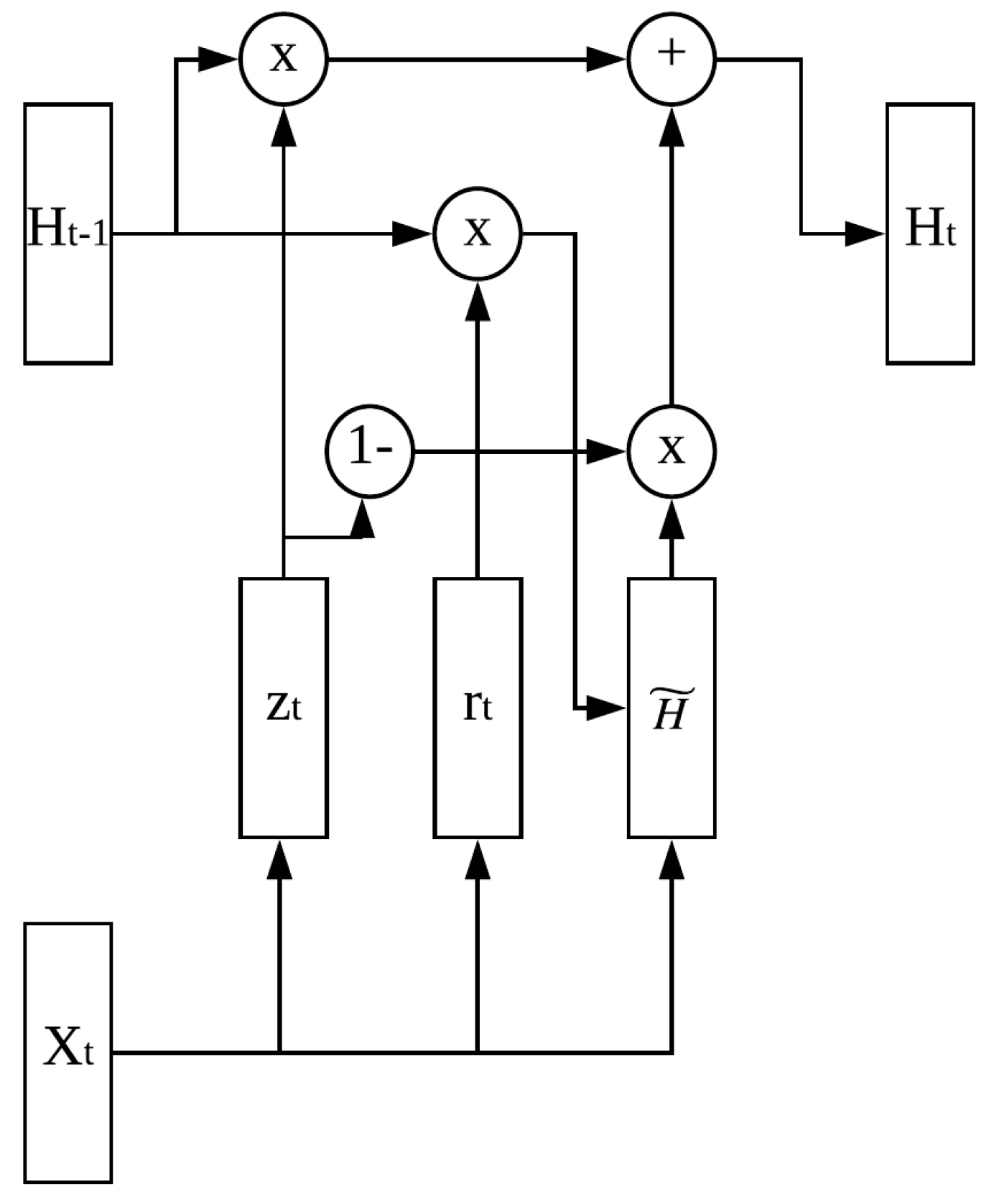
3.2. Gated Recurrent Unit
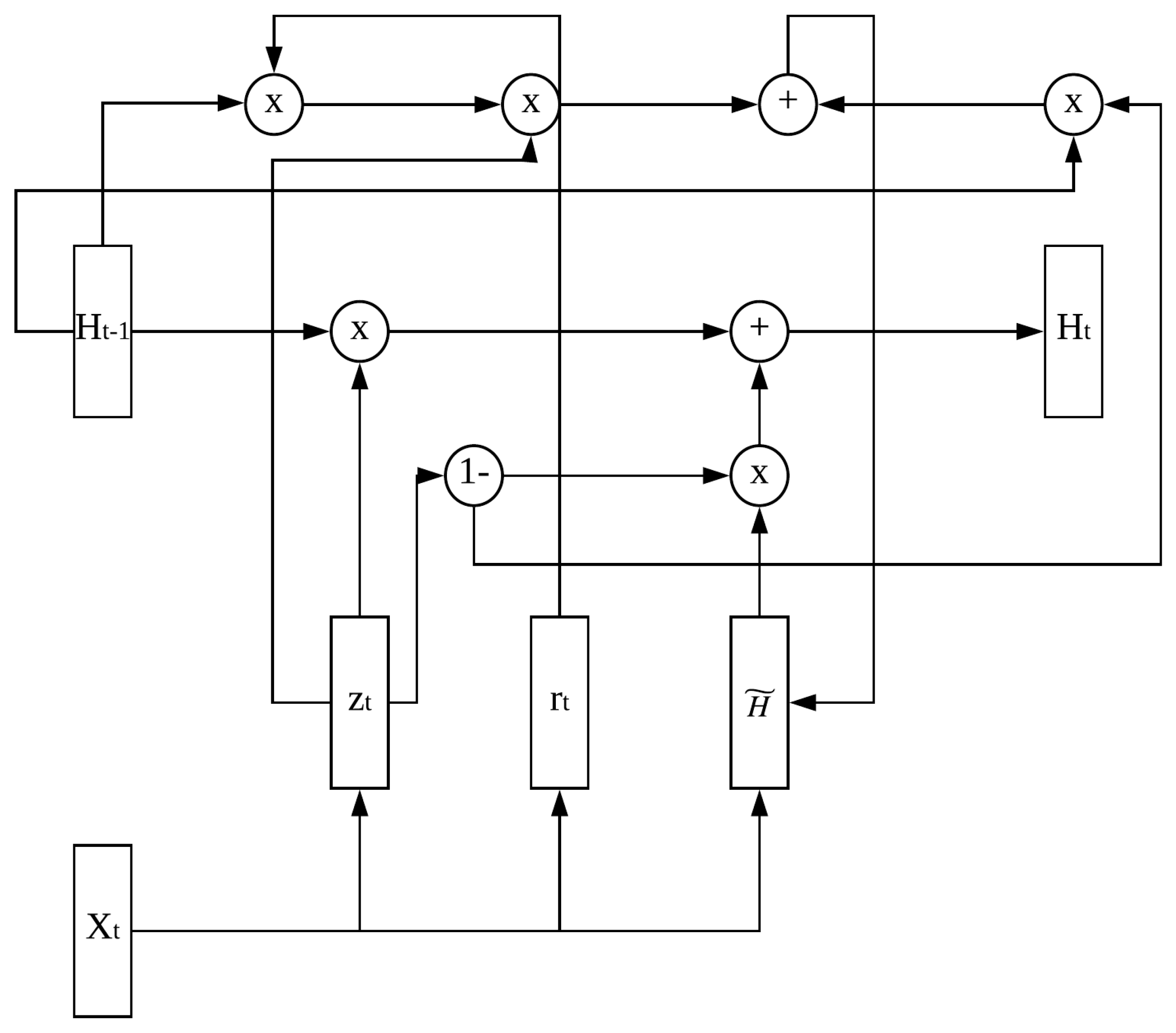
3.3. Security Control Unit
4. Attention Model
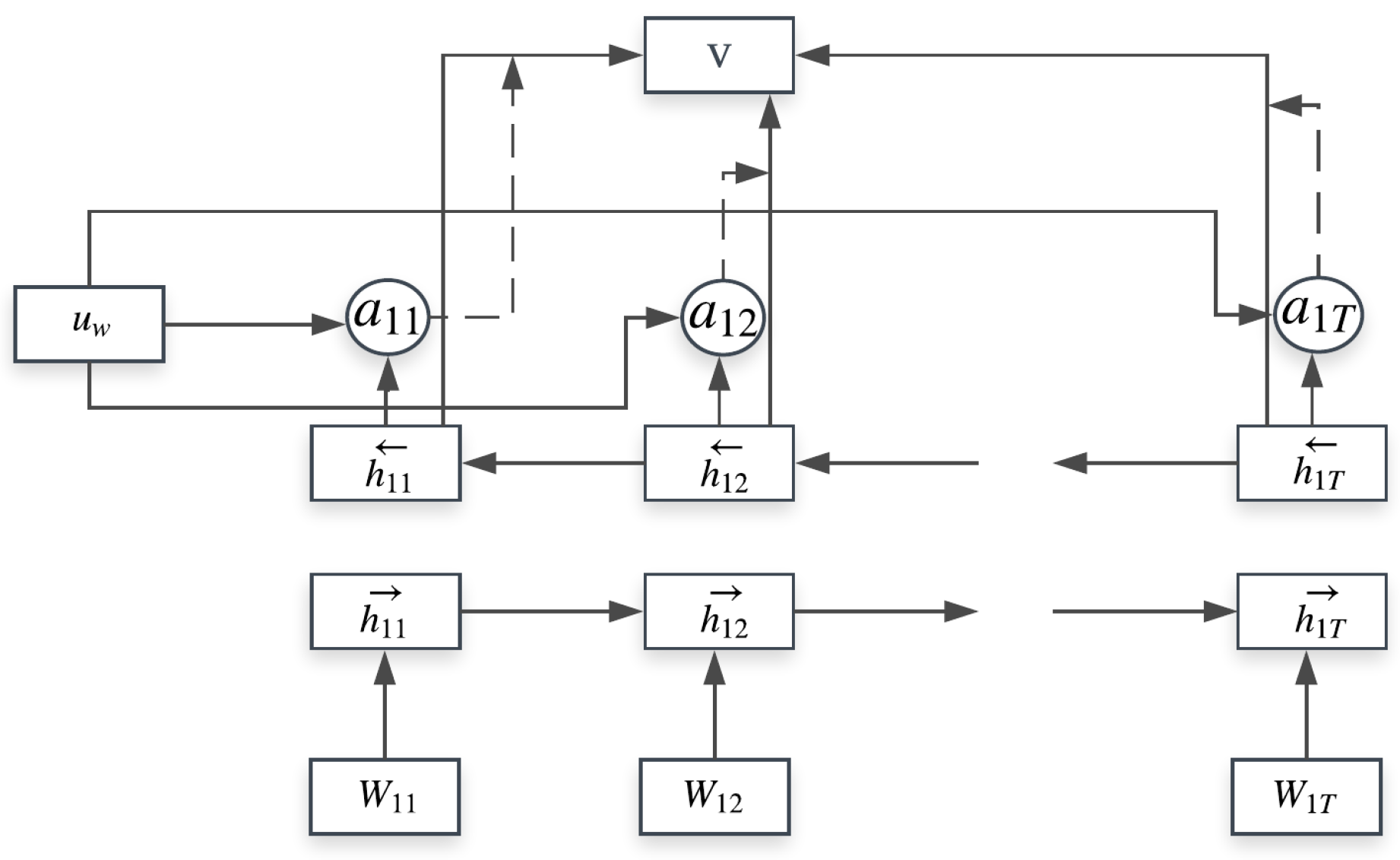
4.1. Hierarchical Attention Model
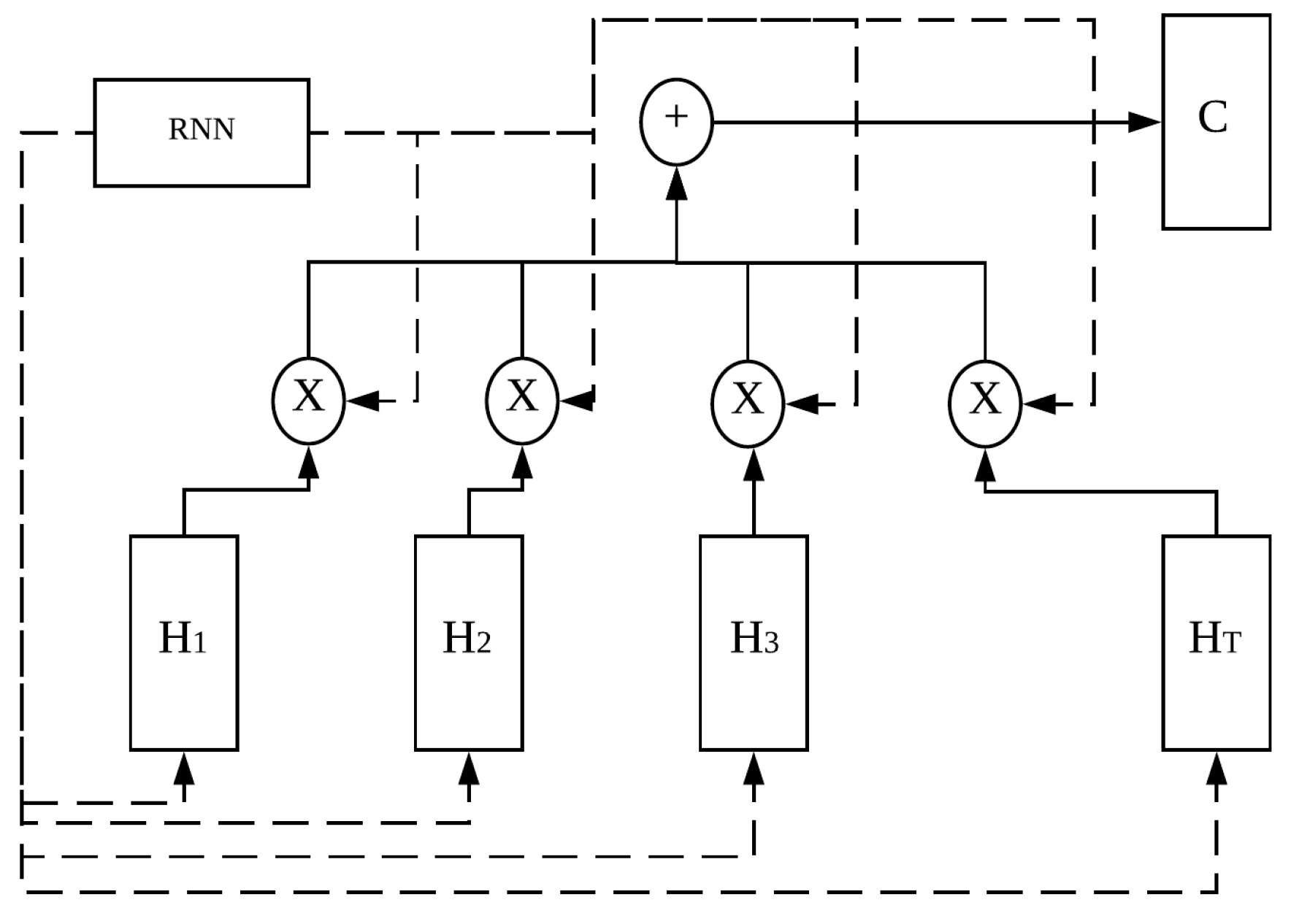
4.2. Simplified Attention Model
5. Can Bus and Dataset
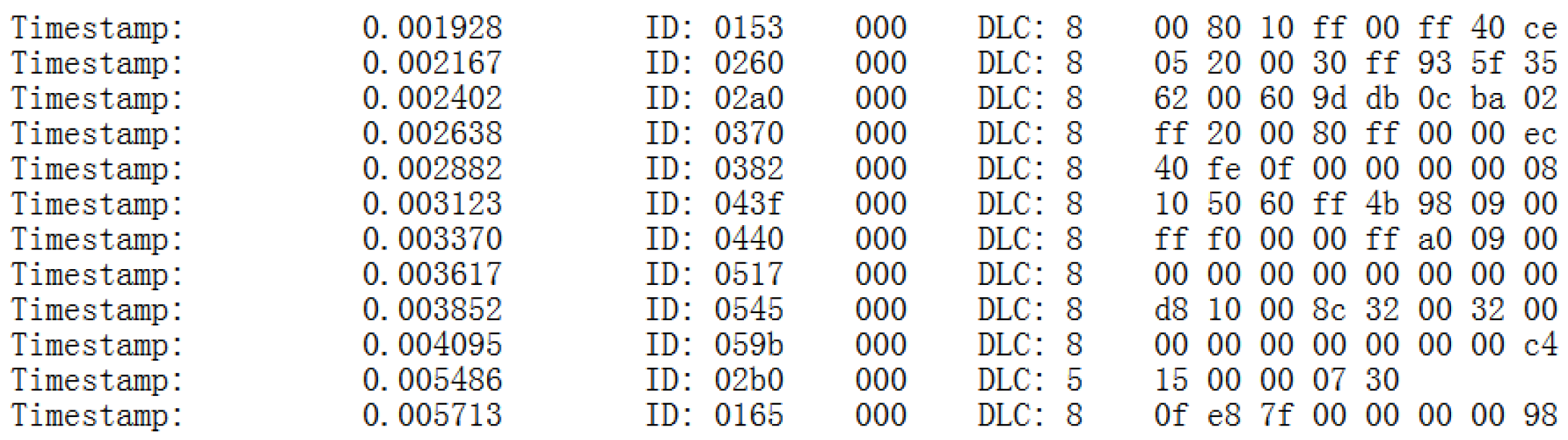
5.1. Can Bus
5.2. Can Bus Dataset
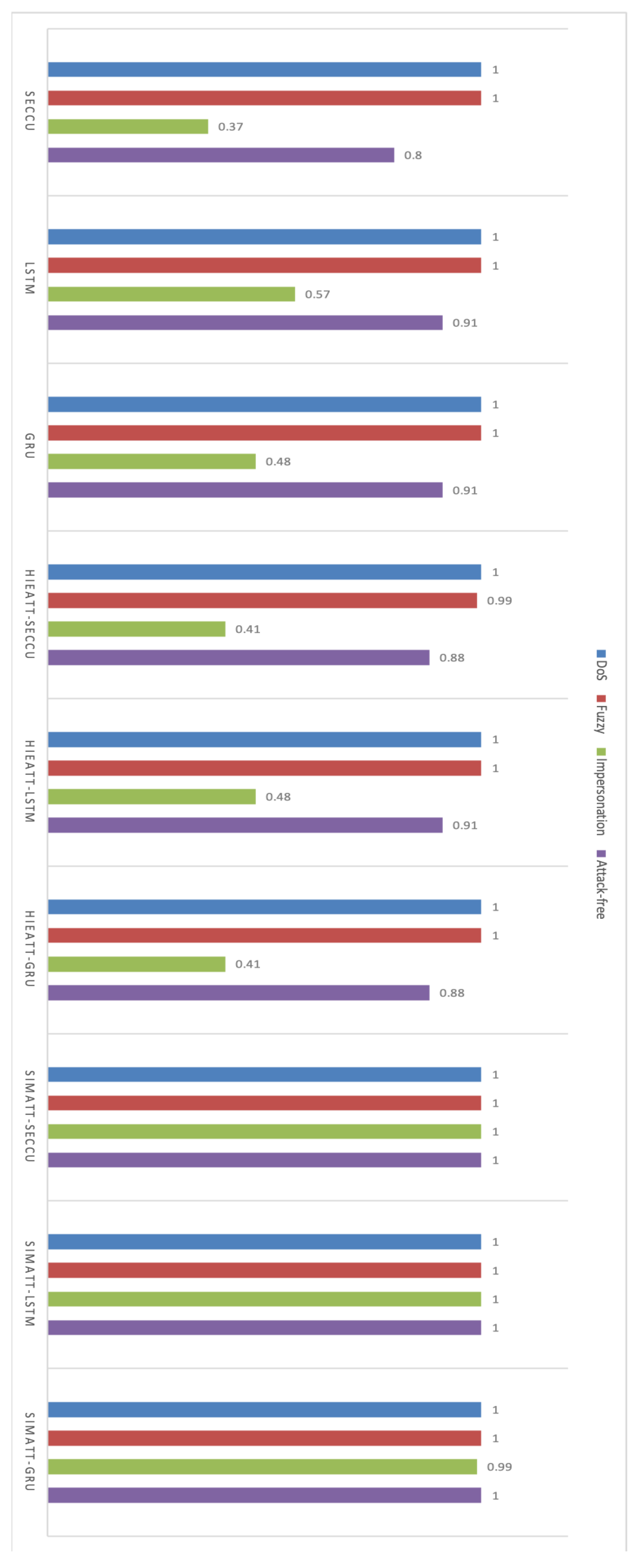
- Attack-free: This data set consists of CAN data generated under normal conditions after the vehicle has been started.
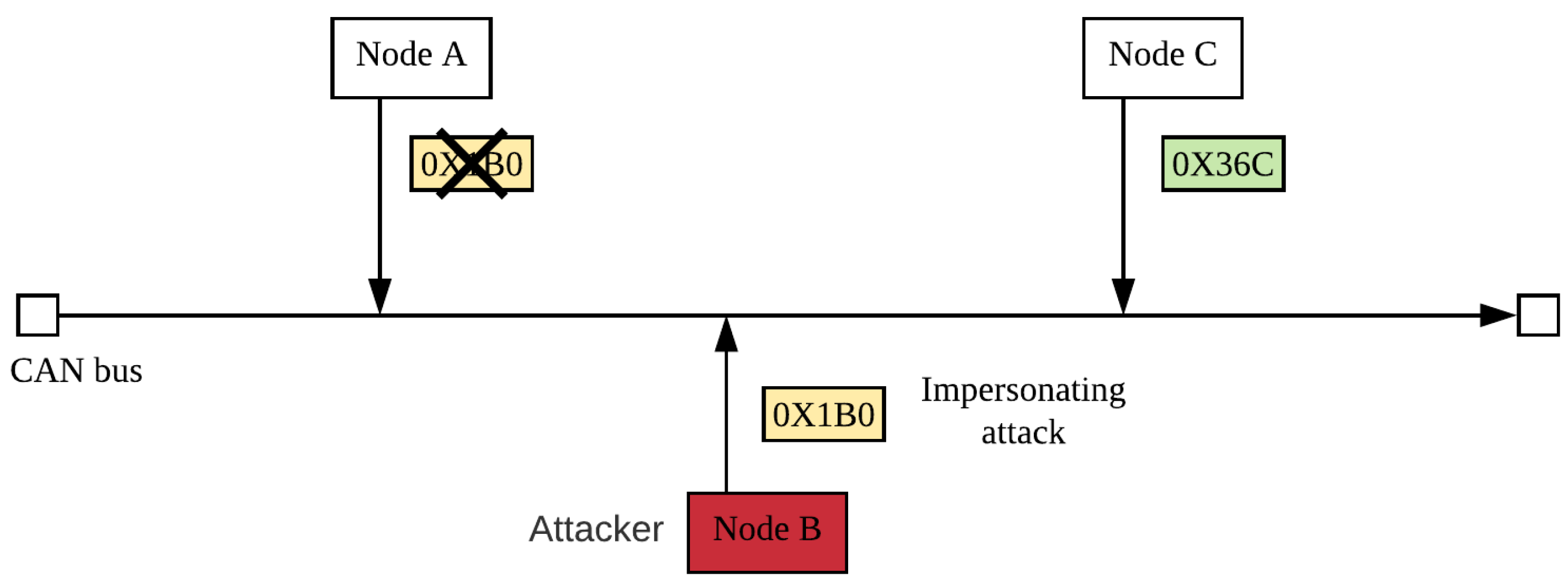
- Impersonation attack: After an attacker has attacked an ECU and disabled it, the attacker inserts his/her ECU for a specific purpose. The inserted ECU is disguised as the disabled ECU, and it can periodically reply to request from other ECU [31,32]. Impersonation attack does not change the original frequency of CAN messages, so IDSs based on frequency characteristics cannot detect this attack. If the attacker does not change the contents of the CAN messages, the inserted ECU looks like a legitimate ECU, and the attacker can then launch other types of attacks. We refer the reader to [31] for further details about the construction and distribution characteristics of the impersonation attack data set. This attack mode is shown in Figure 11.
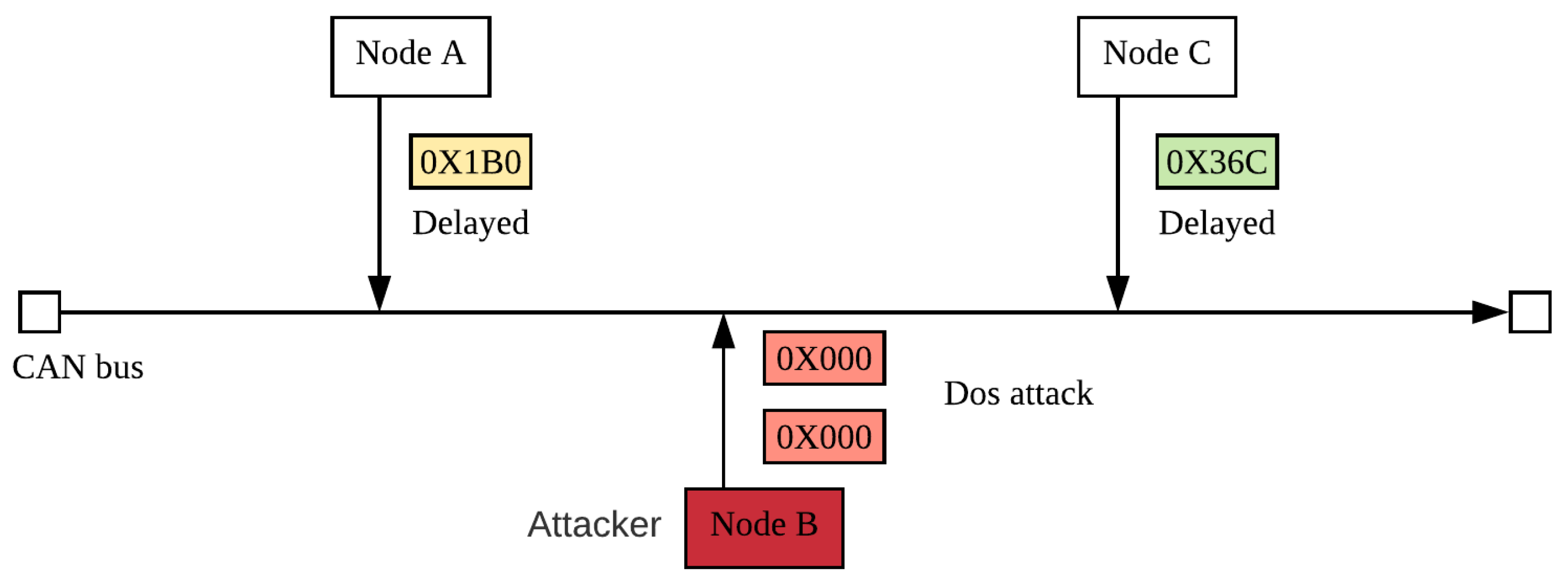
- DoS attack: This dataset consists of data generated while an attacker periodically injected high-priority CAN instructions so that legitimate instructions are not sent in time. In this data set, the attacker injected the highest priority instruction (ID 0000). This attack mode is shown in Figure 12.
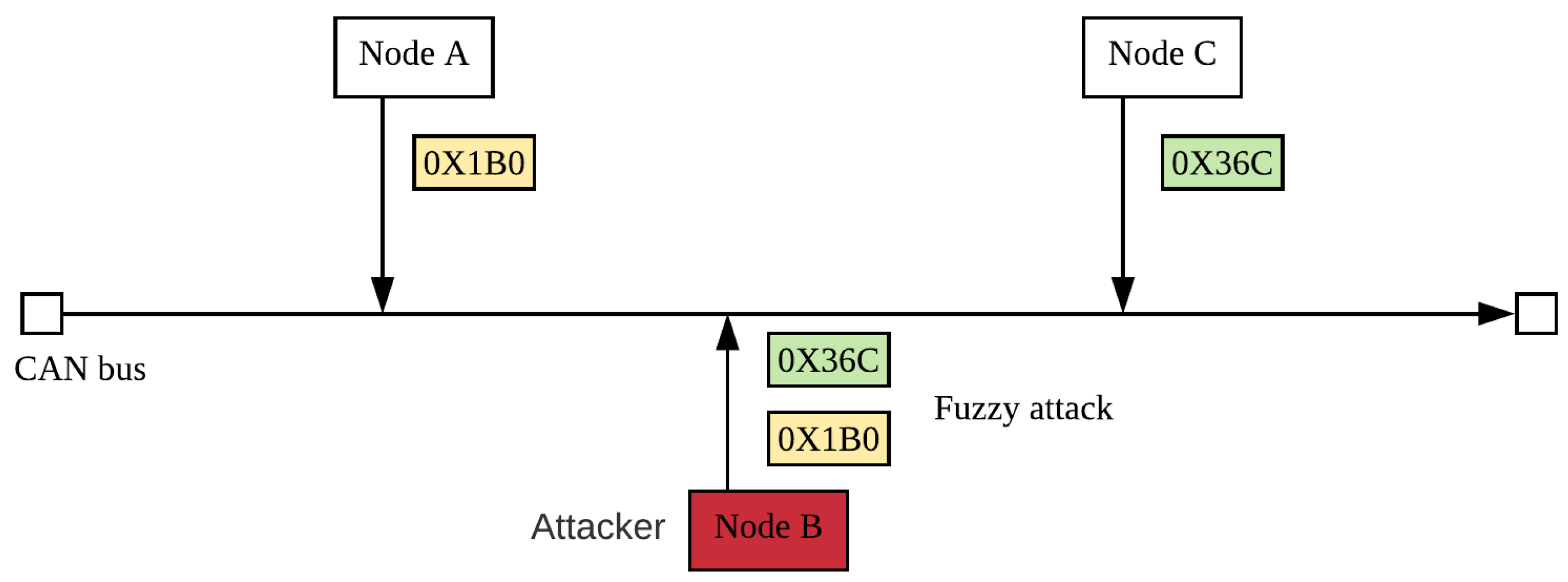
- Fuzzy attack: This dataset consists of data generated while an attacker randomly sends instructions to cause the vehicle to perform unexpectedly. To implement a fuzzy attack, the attacker needs to collect detailed information about the target vehicle. For example, instruction ID that can produce unexpected behavior. It is different from DoS attack by occupancy bus to delay normal information transmission. The Fuzzy attack caused the vehicle function to be unavailable. This attack mode is shown in Figure 13.
6. Experiment Procedure and Results
6.1. Experiment Procedure
- We take the first 80% of the instruction sequences in all data sets and divide them into 10 equal parts.
- Each part is treated as a test set, and the remaining nine parts are used as a training set. A total of 10 test results are obtained.
- The SIMATT model was removed and the SECCU cell was replaced with an LSTM cell or a GRU cell to compare the proposed model with the LSTM and GRU models, respectively. Only the SIMATT model was removed to obtain the SECCU-based model.
- The SIMATT model was replaced by the HIEATT model, and the SECCU cell was replaced by an LSTM cell or a GRU cell to obtain the HIEATT-LSTM and HIEATT-GRU models, respectively. The HIEATT-SECCU model was obtained by replacing the SIMATT model with the HIEATT model.
- The SECCU cell was replaced with an LSTM cell or GRU cell to obtain the SIMATT-LSTM and SIMATT-GRU models, respectively.
6.2. Introduction to Experimental Evaluation Indicators
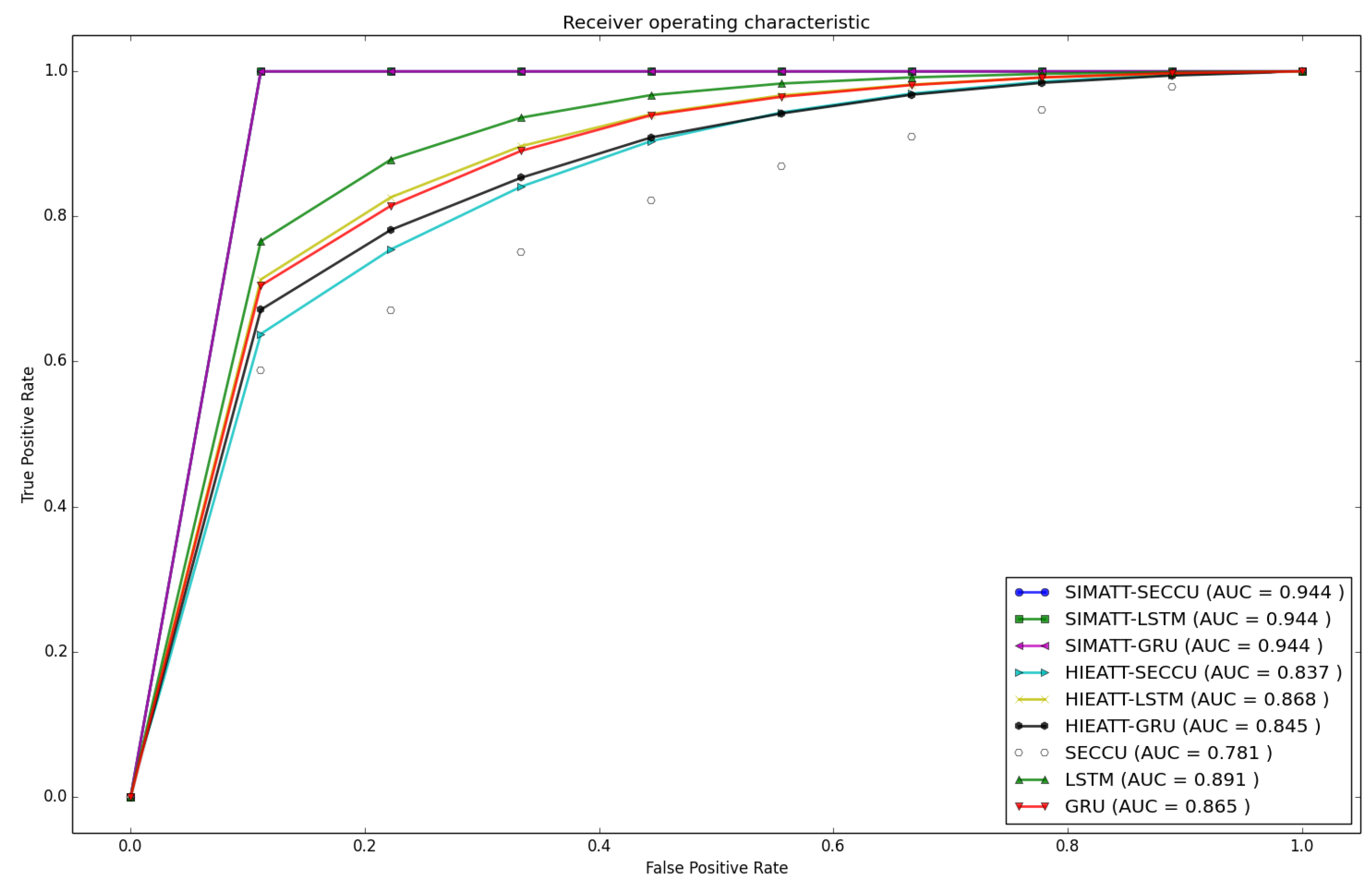
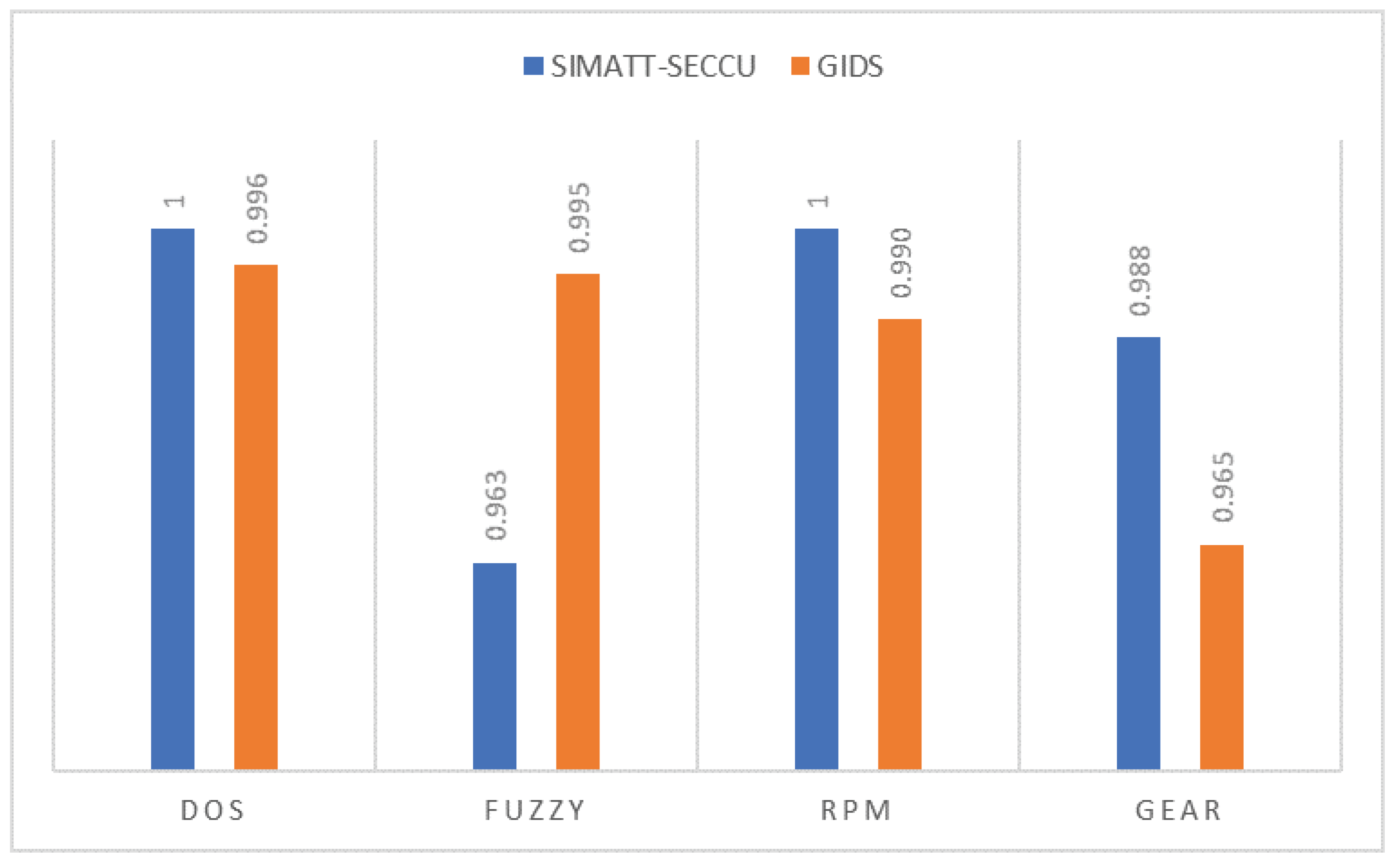
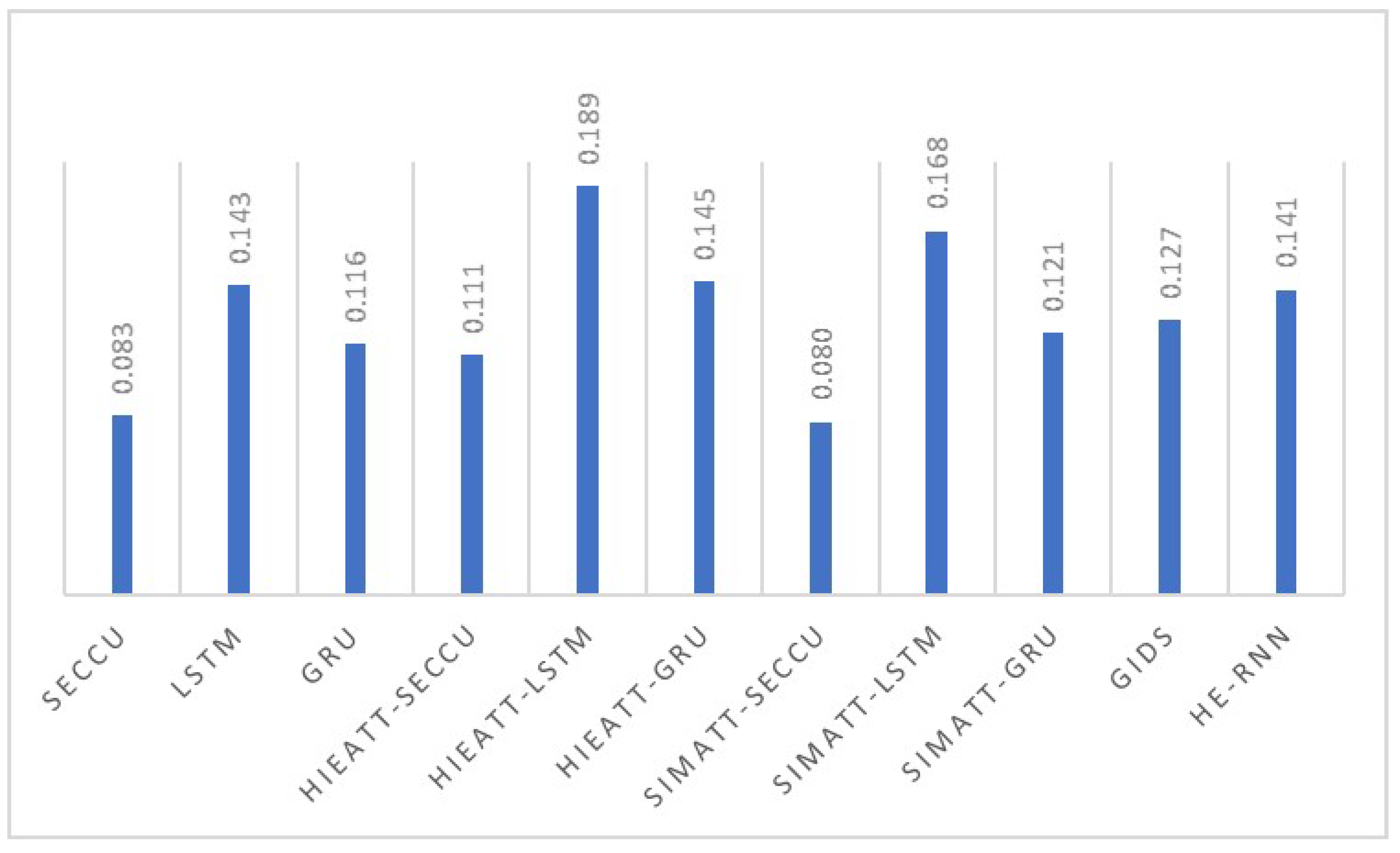
6.3. Model Performance Analysis
7. Conclusions
- To suit the actual situation of an in-vehicle network, we present a new recurrent neural network (RNN) model named SECCU.
- We propose the simplified attention (SIMATT) model that can be computed using the computing power of vehicle electronics and improve detection accuracy.
- The experimental results demonstrate that our proposed SIMATT-SECCU symmetry framework has the best performance in comparison with many classic models.
- Our detecting model is fully data-driven and does not require any domain knowledge about the CAN protocol.
- Our proposed model focuses on a lightweight anomaly detecting for in-vehicle network based on machine learning, which solves the problem of insufficient computing power of networked vehicle electronic devices when applying machine learning algorithms.
Author Contributions
Funding
Conflicts of Interest
References
- Woo, S.; Jo, H.J.; Lee, D.H. A practical wireless attack on the connected car and security protocol for in-vehicle CAN. IEEE Trans. Intell. Transp. Syst. 2015, 16, 993–1006. [Google Scholar] [CrossRef]
- Foster, I.; Prudhomme, A.; Koscher, K.; Savage, S. Fast and vulnerable: A story of telematic failures. In Proceedings of the USENIX Workshop on Offensive Technologies, Washington, DC, USA, 10–11 August 2015. [Google Scholar]
- Golde, N.; Redon, K.; Borgaonkar, R. Weaponizing femtocells: The effect of rogue devices on mobile telecommunications. In Proceedings of the NDSS Symposium, San Diego, CA, USA, 5–8 Feburary 2012. [Google Scholar]
- Kim, J.H.; Seo, S.-H.; Hai, N.T.; Cheon, B.M.; Lee, Y.S.; Jeon, J.W. Gateway framework for in-vehicle networks based on CAN, FlexRay, and Ethernet. IEEE Trans. Veh. Technol. 2015, 64, 4472–4486. [Google Scholar] [CrossRef]
- Park, T.J.; Han, C.S.; Lee, S.H. Development of the electronic control unit for the rack-actuating steer-by-wire using the hardware-in-the-loop simulation system. Mechatronics 2005, 15, 899–918. [Google Scholar] [CrossRef]
- Tuohy, S.; Glavin, M.; Ciarán, H. Intra-vehicle networks: A review. IEEE Trans. Intell. Transp. Syst. 2015, 16, 534–545. [Google Scholar] [CrossRef]
- Biswas, S.; Tatchikou, R.; Dion, F. Vehicle-to-vehicle wireless communication protocols for enhancing highway traffic safety. IEEE Commun. Mag. 2006, 44, 74–82. [Google Scholar] [CrossRef]
- Farsi, M.; Ratcliff, K.; Barbosa, M. An overview of controller area network. Comp. Control Eng. J. 1999, 10, 113–120. [Google Scholar] [CrossRef]
- Li, X.; Yu, Y.; Sun, G.; Guannan, S.; Kefei, C. Connected vehicles’ security from the perspective of the In-vehicle network. IEEE Netw. 2018, 32, 58–63. [Google Scholar] [CrossRef]
- Tang, T.; Shi, W.; Shang, H.; Wang, Y. A new car-following model with consideration of inter-vehicle communication. Nonlinear Dyn. 2014, 76, 2017–2023. [Google Scholar] [CrossRef]
- Groza, B.; Murvay, S. Efficient protocols for secure broadcast in controller area networks. IEEE Trans. Ind. Inform. 2013, 9, 2034–2042. [Google Scholar] [CrossRef]
- Woo, S.; Jo, H.J.; Kim, I.S.; Lee, D.H. A practical security architecture for in-vehicle CAN-FD. IEEE Trans. Intell. Transp. Syst. 2016, 17, 2248–2261. [Google Scholar] [CrossRef]
- Muter, M.; Asaj, N. Entropy-based anomaly detection for in- vehicle networks. In Proceedings of the 2011 IEEE Intelligent Vehicles Symposium (IV), Baden-Baden, Germany, 5–9 June 2011; pp. 1110–1115. [Google Scholar]
- Lan, H.M.; Kwak, B.I.; Kim, H.K. Anomaly intrusion detection method for vehicular networks based on survival analysis. Veh. Commun. 2018, 14, 52–63. [Google Scholar]
- Song, H.M.; Kim, H.K. Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network. In Proceedings of the International Conference on Information Networking (ICOIN), Kota Kinabalu, Malaysia, 13–15 January 2016. [Google Scholar]
- Seo, E.; Song, H.M.; Kim, H.K. GIDS: GAN based intrusion detection system for in-vehicle network. In Proceedings of the 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, UK, 28–30 August 2018. [Google Scholar]
- Tariq, S.; Lee, S.; Kim, H.K.; Woo, S.S. Detecting In-vehicle CAN message attacks using heuristics and RNNs. In Proceedings of the International Workshop on Information and Operational Technology Security Systems, Heraklion, Greece, 13 September 2018. [Google Scholar]
- Larson, U.E.; Nilsson, D.K.; Jonsson, E. An approach to specification-based attack detection for in-vehicle networks. In Proceedings of the IEEE Intelligent Vehicles Symposium, Eindhoven, The Netherlands, 4–6 June 2008; pp. 220–225. [Google Scholar]
- Wang, C.; Zhao, Z.; Gong, L.; Zhu, l.; Cheng, X. A distributed anomaly detection system for in-vehicle network using HTM. IEEE Access 2018, 6, 9091–9098. [Google Scholar] [CrossRef]
- Hu, W.; Liao, Y.; Vemuri, V.R. Robust anomaly detection using support vector machines. In Proceedings of the International Conference on Machine Learning, Washington, DC, USA, 21–24 August 2003; pp. 282–289. [Google Scholar]
- Li, H.; Wang, Y.; Qin, H.; Xinkai, W. Investigating the effects of attack detection for in-vehicle networks based on clock drift of ECUs. IEEE Access 2018, 6, 49375–49384. [Google Scholar]
- Xiao, J.; Wu, H.; Li, X. Robust and Self-Evolving IDS for In-Vehicle Network by Enabling Spatiotemporal Information. In Proceedings of the IEEE 21st International Conference on High Performance Computing and Communications, Zhangjiajie, China, 10–12 August 2019. [Google Scholar]
- Sutskever, I.; Vinyals, O.; Le, Q.V. Sequence to sequence learning with neural networks. arXiv 2014, arXiv:1409.3215. [Google Scholar]
- Cho, K.; van Merrienboer, B.; Gulcehre, C.; Bahdanau, D.; Bougares, F.; Schwenk, H.; Bengio, Y. Phrase representations using RNN encoder-decoder for statistical machine translation. arXiv 2014, arXiv:1406.1078. [Google Scholar]
- Chung, J.; Gulcehre, C.; Cho, K.; Bengio, Y. Gated feedback recurrent neural networks. arXiv 2015, arXiv:1502.02367. [Google Scholar]
- Jozefowicz, R.; Zaremba, W.; Sutskever, I. An empirical exploration of recurrent network architectures. In Proceedings of the International Conference on Machine Learning, Lille, France, 6–11 July 2015. [Google Scholar]
- Greff, K.; Srivastava, R.K.; Koutník, J.; Steunebrink, B.R.; Schmidhuber, J. LSTM: A search space odyssey. IEEE Trans. Neural Netw. Learning Syst. 2017, 28, 2222–2232. [Google Scholar] [CrossRef]
- Parikh, A.P.; Täckström, O.; Das, D.; Uszkoreit, J. A decomposable attention model for natural language inference. arXiv 2016, arXiv:1606.01933. [Google Scholar]
- Pappas, N.; Popescu-Belis, A. Multilingual hierarchical attention networks for document classification. arXiv 2017, arXiv:1707.00896. [Google Scholar]
- Sukhbaatar, S.; Szlam, A.; Weston, J.; Fergus, R. End-to-end memory networks. arXiv 2015, arXiv:1503.08895. [Google Scholar]
- Lee, H.; Jeong, S.H.; Kim, H.K. OTIDS: A novel intrusion detection system for in-vehicle network by using remote frame. In Proceedings of the 15th Annual Conference on Privacy, Security and Trust, PST, Calgary, AB, Canada, 27–29 August 2017. [Google Scholar]
- Cho, K.-T.; Shin, K.G. Fingerprinting electronic control units for vehicle intrusion detection. In Proceedings of the USENIX Security Symposium, Austin, TX, USA, 10–12 August 2016. [Google Scholar]
- Breiman, L. Random Forests. Mach. Learning 2001, 45, 5–32. [Google Scholar] [CrossRef] [Green Version]
- Zhang, H.; Yang, S.; Guo, L.; Zhao, Y.; Shao, F.; Chen, F. Comparisons of isomir patterns and classification performance using the rank-based manova and 10-fold cross-validation. Gene 2017, 569, 21–26. [Google Scholar] [CrossRef] [PubMed]
- Meijer, R.J.; Goeman, J.J. Efficient approximate k-fold and leave-one-out cross-validation for ridge regression. Biom. J. 2013, 55, 141–155. [Google Scholar] [CrossRef] [PubMed]


| CAN | Controller Area Network |
| SECCU | Security Control Unit |
| LSTM | Long Short-Term Memory |
| GRU | Gated Recurrent Unit |
| HIEATT | HIErarchical ATTention model |
| SIMATT | SIMplified ention Model |
| GIDS | GAN Based Intrusion Detection System |
| RNN | Recurrent Neural Network |
| HE-RNN | HEuristics and RNNs |
| IOV | Internet of Vehicles |
| IOT | Internet of Things |
| OBD-II | OnBoard Diagnostics II |
| ECU | Electronics Control Unit |
| V2V | Vehicle-to-Vehicle |
| V2I | Vehicle-to-Infrastructure |
| Key References | Detection Strategy | Method |
|---|---|---|
| Müter et al. [13] | Anomaly-based | Statistical-based (entropy-based) |
| Han et al. [14] | Anomaly-based | Survival |
| Song et al. [15] | Signature-based | Frequency-based |
| Seo et al. [16] | Anomaly-based | Generative adversarial networks |
| Tariq et al. [17] | Anomaly-based | Heuristic algorithm and RNN |
| Larson et al. [18] | Security rules | Object dictionary of the CANopen protocol |
| Wang et al. [19] | Anomaly-based | Time series prediction model |
| Hu et al. [20] | Anomaly-based | Support vector machine |
| Ji et al. [21] | Anomaly-based | Clock drift |
| Xiao et al. [22] | Anomaly-based | Time series prediction model |
| true positives(TP) | Positive class is judged as positive class |
| false negatives(FN) | Positive class is judged as negative class |
| false positives(FP) | Negative class is judged as positive class |
| true negatives(TN) | Negative class is judged as negative class |
| Model | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | Mean |
|---|---|---|---|---|---|---|---|---|---|---|---|
| SECCU | 0.916 | 0.900 | 0.876 | 0.898 | 0.864 | 0.684 | 0.587 | 0.521 | 0.540 | 0.593 | 0.738 |
| LSTM | 0.964 | 0.922 | 0.909 | 0.922 | 0.921 | 0.817 | 0.711 | 0.787 | 0.752 | 0.729 | 0.843 |
| GRU | 0.960 | 0.922 | 0.904 | 0.926 | 0.903 | 0.774 | 0.675 | 0.702 | 0.673 | 0.686 | 0.813 |
| HIEATT-SECCU | 0.929 | 0.887 | 0.867 | 0.883 | 0.863 | 0.738 | 0.648 | 0.686 | 0.632 | 0.656 | 0.779 |
| HIEATT-LSTM | 0.958 | 0.924 | 0.906 | 0.925 | 0.903 | 0.796 | 0.677 | 0.723 | 0.664 | 0.687 | 0.816 |
| HIEATT-GRU | 0.946 | 0.909 | 0.901 | 0.914 | 0.899 | 0.763 | 0.626 | 0.678 | 0.628 | 0.635 | 0.790 |
| SIMATT-SECCU | 1.000 | 1.000 | 0.993 | 1.000 | 1.000 | 1.000 | 0.993 | 1.000 | 1.000 | 0.993 | 0.997 |
| SIMATT-LSTM | 1.000 | 1.000 | 1.000 | 0.993 | 1.000 | 0.993 | 0.958 | 1.000 | 1.000 | 0.993 | 0.993 |
| SIMATT-GRU | 1.000 | 1.000 | 0.979 | 0.993 | 0.993 | 0.986 | 0.938 | 1.000 | 0.993 | 0.972 | 0.985 |
| Model | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | Mean |
|---|---|---|---|---|---|---|---|---|---|---|---|
| SECCU | 0.840 | 0.798 | 0.760 | 0.803 | 0.740 | 0.663 | 0.858 | 0.852 | 0.823 | 0.872 | 0.801 |
| LSTM | 0.936 | 0.853 | 0.820 | 0.851 | 0.840 | 0.863 | 0.915 | 0.937 | 0.938 | 0.943 | 0.890 |
| GRU | 0.936 | 0.846 | 0.821 | 0.853 | 0.815 | 0.834 | 0.927 | 0.928 | 0.915 | 0.943 | 0.882 |
| HIEATT-SECCU | 0.862 | 0.787 | 0.745 | 0.799 | 0.751 | 0.765 | 0.877 | 0.884 | 0.869 | 0.898 | 0.824 |
| HIEATT-LSTM | 0.921 | 0.852 | 0.809 | 0.857 | 0.831 | 0.861 | 0.928 | 0.917 | 0.915 | 0.925 | 0.882 |
| HIEATT-GRU | 0.892 | 0.834 | 0.819 | 0.832 | 0.804 | 0.826 | 0.905 | 0.906 | 0.895 | 0.909 | 0.862 |
| SIMATT-SECCU | 1.000 | 1.000 | 1.000 | 1.000 | 1.000 | 1.000 | 1.000 | 1.000 | 1.000 | 1.000 | 1.000 |
| SIMATT-LSTM | 1.000 | 1.000 | 1.000 | 1.000 | 1.000 | 0.986 | 0.986 | 1.000 | 1.000 | 1.000 | 0.997 |
| SIMATT-GRU | 1.000 | 1.000 | 0.986 | 0.973 | 0.986 | 1.000 | 1.000 | 1.000 | 0.986 | 1.000 | 0.993 |
| Attack | Precision | Recall | F1 |
|---|---|---|---|
| DoS | 0.9930 | 0.9927 | 0.9929 |
| Fuzzy | 0.9901 | 0.9935 | 0.9918 |
| Attack | Precision | Recall | F1 |
|---|---|---|---|
| DoS | 1.0000 | 1.0000 | 1.0000 |
| Fuzzy | 1.0000 | 1.0000 | 1.0000 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xiao, J.; Wu, H.; Li, X. Internet of Things Meets Vehicles: Sheltering In-Vehicle Network through Lightweight Machine Learning. Symmetry 2019, 11, 1388. https://doi.org/10.3390/sym11111388
Xiao J, Wu H, Li X. Internet of Things Meets Vehicles: Sheltering In-Vehicle Network through Lightweight Machine Learning. Symmetry. 2019; 11(11):1388. https://doi.org/10.3390/sym11111388
Chicago/Turabian StyleXiao, Junchao, Hao Wu, and Xiangxue Li. 2019. "Internet of Things Meets Vehicles: Sheltering In-Vehicle Network through Lightweight Machine Learning" Symmetry 11, no. 11: 1388. https://doi.org/10.3390/sym11111388
APA StyleXiao, J., Wu, H., & Li, X. (2019). Internet of Things Meets Vehicles: Sheltering In-Vehicle Network through Lightweight Machine Learning. Symmetry, 11(11), 1388. https://doi.org/10.3390/sym11111388




