Abstract
A three-party Authenticated Key Agreement (AKA) protocol in the distributed computing environment is a client that requests services from an application server through an authentication server. The authentication server is responsible for authenticating the participating entities and helping them to construct a common session key. Adopting the Key Transfer Authentication Protocol (KTAP) in such an environment, the authentication server is able to monitor the communication messages to prevent and trace network crime. However, the session key in the KTAP setting is created only by the authentication server and is vulnerable to the resilience of key control. On the other hand, with the rapid growth of network technologies, mobile devices are widely used by people to access servers in the Internet. Many AKA protocols for mobile devices have been proposed, however, most protocols are vulnerable to Ephemeral Secret Leakage (ESL) attacks which compromise the private keys of clients and the session key by an adversary from eavesdropped messages. This paper proposes a novel ESL-secure ID-based three-party AKA protocol for mobile distributed computing environments based on ESL-secure ID-based Authenticated Key Exchange (ID-AKE) protocol. The proposed protocol solves the key control problem in KTAP while retaining the advantages of preventing and tracing network crime in KTAP and also resists ESL attacks. The AVISPA tool simulation results confirm the correctness of the protocol security analysis. Furthermore, we present a parallel version of the proposed ESL-secure ID-based three-party AKA protocol that is communication-efficient.
1. Introduction
With the rapid growth of network technologies, portable mobile devices (e.g., mobile phone, notebook and tablet) are widely used by people to access remote servers on the Internet. Due to the limited computing capability and power energy of mobile devices, many Authenticated Key Agreement (AKA) protocols are based on the traditional public key cryptography system [1,2,3] and the ID-based AKA (ID-AKA) protocols [4,5,6] for mobile devices. Imbalanced computation is used to shift the computational burden to a powerful server using an online/offline computation technique to further reduce the mobile device computational load. If an AKA protocol adopted an online/offline computation technique, the ephemeral secrets are generally generated by an external source that may be controlled by an adversary. The ephemeral secrets are also involved in the offline pre-computation and stored in the insecure memory of mobile devices. If ephemeral secrets are compromised, an adversary can reveal the private keys of clients and the session key would turn out to be known from the eavesdropped messages. This phenomenon is called Ephemeral Secret Leakage (ESL) attacks [7]. To solve this security vulnerability, Tseng et al. [7] proposed the first ESL-secure ID-based Authenticated Key Exchange (ID-AKE) protocol for mobile client-server environments.
In 1976, Diffie and Hellman [8] proposed the first Public Key Cryptography (PKC) concept, and proposed the first key agreement protocol that allows two participants to construct a common session key over a public network. Unfortunately, Diffie and Hellman’s protocol does not authenticate the communication participants and is vulnerable to the man-in-the-middle attacks. Different approaches have been proposed by cryptographic researchers to defeat the weakness in terms of improving protocol security and efficiency. An AKA protocol should provide implicit key authentication for participants. Each participant is ensured that no other participants or adversaries can learn or determine the value of a common session key in a protocol run. The common session key is used to ensure information integrity, confidentiality and availability between participants using symmetric encryptions.
In traditional public key cryptography systems, the users have to access and verify other user’s certificate before using its public key through the Certificate Authority (CA). The CA requires high computational cost and storage efforts to manage the certificates and also increases the computational cost for the client side [9]. Shamir [10] proposed the first ID-based cryptosystem to simplify the certificate management procedures. In Shamir’s ID-based cryptosystem setting, the user’s public key is an easy calculated function of the user’s known identity information such as identity numbers, E-mail address and so forth. The corresponding private key can be calculated and issued to the user via a secure channel by a trusted party referred to as Private Key Generator (PKG). In this way, the users do not need to verify other user’s certificates before using the public key and thus can substantially reduce the computational burden of the CA. However, Shamir’s ID-based cryptosystem is not easy to be realized in practice due to lack of efficient encryption and decryption algorithms and thus restricts its development. Boneh and Franklin [11] proposed the first secure and efficient practical ID-based encryption scheme based on the Weil pairing defined on elliptic curves. Subsequently, the ID-based cryptographic schemes based on bilinear pairings have received much attention from cryptographic researchers and a large number of ID-based cryptographic systems using bilinear pairings have been published in the literatures [12,13,14].
Joux [15] proposed the first three-party key agreement protocol based on bilinear pairings. Joux’s key agreement protocol is the first key agreement protocol based on bilinear pairings and also the first one-round three-party key agreement protocol. However, like the basic Diffie-Hellman key agreement protocol, Joux’s protocol without authentication is also insecure against the man-in-the-middle attacks. To solve this problem, Al-Riyami and Paterson [16] proposed several three-party AKA protocols that use bilinear pairings. Al-Riyami and Paterson’s protocols overcome the security flaw in Joux’s protocol. However, Al-Riyami and Paterson’s protocols still need certificates issued by the CA to ensure the authenticity and a user also needs to verify the certificates before using other users’ public keys. Afterwards, many ID-based three-party AKA protocols using bilinear pairings have rapidly emerged and been well-studied as well [17,18,19].
Up to now, most of the literature on ID-based three-party AKA protocols using bilinear pairings focused on the environment in which PKG computes the public key and corresponding private key from a user’s identity information, and issuing the public/private key pair to the user via a secure channel. The participants can authenticate each other using the public/private key pair and construct a common session key. In 2004, Yeh et al. [20] pointed out that another common communication environment exists, referred to as the distributed computing environment, discussed in Kerberos [21]. In this open distributed computing environment, if the users would like to access services on application servers distributed throughout the network, a centralized authentication server is provided rather than building an elaborate authentication protocol at each server. The authentication server is responsible for participating entities’ authentication and helps the user and the application server construct a common session key. In the centralized authentication server model an inspection mechanism is provided to prevent and trace network crime, permitting users to access the services provided by the application servers legally. The Key Transfer Authentication Protocol (KTAP) is adopted in this system [22]. In a KTAP setting the session key is created by the authentication server and secretly transmitted to the user and the application server. The authentication server can therefore monitor the transferred messages [23,24,25,26]. However, the disadvantage of KTAP is that the session key is only created by the authentication server and the client and the application servers are unable to participate in constructing the common session key. KTAP is therefore vulnerable to key control resilience attacks [27].
With the rapid growth of network technologies, portable mobile devices (e.g., mobile phone, notebook and tablet) are widely used by people to access remote servers on the Internet. Due to the limited computing capability and power energy of mobile devices, many AKA protocols are based on the traditional public key cryptography system [1,2,3] and the ID-based AKA (ID-AKA) protocols [4,5,6] for mobile devices. Imbalanced computation is used to shift the computational burden to a powerful server using an online/offline computation technique to further reduce the mobile device computational load. If an AKA protocol adopted an online/offline computation technique, the ephemeral secrets are generally generated by an external source that may be controlled by an adversary. The ephemeral secrets are also involved in the offline pre-computation and stored in the insecure memory of mobile devices. If ephemeral secrets are compromised, an adversary can reveal the private keys of clients and the session key would turn out to be known from the eavesdropped messages. This phenomenon is called Ephemeral Secret Leakage (ESL) attacks. To solve this security vulnerability, Tseng et al. [7] proposed the first ESL-secure ID-based Authenticated Key Exchange (ID-AKE) protocol for mobile client-server environments.
Most KTAPs [20,23,24,25] are password-based authentication protocols. In these protocols the users need to share their own passwords with the authentication server and employ the authentication server public keys to ensure the identities of the participants. These protocols also use symmetric cryptosystems to encrypt the transferred messages. For password-based authentication protocol security a strong password should consist of letters (uppercase letters, lowercase letters), numbers and special punctuations to resist various attacks, such as password guessing attacks and dictionary attacks, etc. However, most mobile devices do not employ standard QWERTY keyboards for users to conveniently enter strong passwords. Instead, these mobile devices often use numeric passwords for user authentication, which is called Personal Identification Number based (PIN-based) authentication. The PIN-based authentication provides a small password space size and thus is vulnerable to various attacks [28]. Otherwise, using the authentication server public keys and the symmetric cryptosystems for the user authentication requires expensive computation, which is not applicable to mobile devices with limited computing capability.
This paper improved Tseng et al.’s scheme [7], to propose an ESL-secure ID-based three-party AKA protocol which is more suitable for mobile distributed computing environments. The proposed protocol adopts imbalanced computation to shift the computational burden to the powerful server and an online/offline computation technique to further reduce the computational cost required for mobile devices. The offline pre-computation is executed prior to protocol execution to achieve better performance. The proposed protocol keeps all of the merits of KTAP regarding security including the authentication server is able to monitor the communication messages to prevent and trace network crime and solves the session key problem, which is only created by the authentication server. All participants can contribute information to derive the common session key. In the security analysis, the proposed protocol resists ESL attacks and also satisfies the security attributes required for AKA protocols: known-key security, partial forward secrecy, key-compromise impersonation resilience, unknown key-share resilience and key control resilience [29]. Furthermore, the proposed protocol is validated by Automated Validation of Internet Security Protocols and Applications (AVISPA) [30] formal validation tool to show its security against various active and passive attacks. In addition, a parallel version of the proposed protocol is proposed to enhance the protocol run performance.
This paper is organized as follows. Section 2 gives a brief review of the basic bilinear pairing concept, the related mathematical assumptions and the security attributes required for AKA protocols and notions used in the proposed protocol. The proposed ESL-secure ID-based three-party AKA protocol is presented in Section 3. In Section 4 the proposed protocol security and performance analyses are conducted. Conclusions are given in Section 5.
2. Preliminaries
In this Section the basic bilinear pairings concept, the related mathematical assumptions, the security attributes required for AKA protocols, and the notations used in the proposed protocol are briefly introduced.
2.1. Bilinear Pairings
Let denote a generator of , where is an additive cyclic group of large prime order and let be a multiplicative group of the same large prime order . is a subgroup of the group of points on an elliptic curve defined over a finite field. is a subgroup of the group of the multiplicative cyclic group defined over a finite field. A bilinear pairing is defined as a map: . The map is called an admissible bilinear map if it satisfies the following properties.
- Bilinearity: Let , we have:
- (1)
- .
- (2)
- .
- (3)
- .
- Non-degeneracy: There exist such that .
- Computable: For , there exists an efficient algorithm to compute .
2.2. Computational Problems
The security of the proposed protocol is based on the following two computational problems. There is no polynomial time algorithm to solve these computational problems with non-negligible probability:
- Discrete Logarithm Problem (DLP): Give ; find an integer such that whenever such integer exists.
- Computational Diffie-Hellman Problem (CDHP): Given for unknown , the CDHP is to compute the value .
2.3. Security Attributes
Here, , and are going to agree upon a common session key and communicate to each other securely. An AKA protocol should provide implicit key authentication for , and , so there are additional security attributes defined for AKA protocols.
- Known-Key Security. A unique session key should be constructed in each round of an AKA protocol. An adversary cannot derive other previous session keys if knowledge of the previous session keys has been compromised. The main purpose of known-key security is to ensure that the compromising of one session key will not compromise other or future session keys.
- Forward Secrecy. If the long-term private keys of one or more of the participants are compromised, the secrecy of previously established session keys will not be obtained by an adversary. The main purpose of forward secrecy is to provide complete protection for the previous transferred messages. If all long-term private keys of the participants are compromised without compromising previous established session keys, that means an AKA protocol still provides protection for the previously transferred messages. We say that the AKA protocol offers perfect forward secrecy.
- Key-Compromise Impersonation Resilience. Suppose that ’s private key has been revealed to an adversary. The adversary only can impersonate to cheat and . It is desired that the compromise of ’s private key does not allow the adversary to impersonate or to cheat .
- Unknown Key-Share Resilience. After the session key has been established, believes the session key is shared with and , while and mistakenly believe that the session key is instead shared with an adversary. Therefore, a desirable AKA protocol should be resistant to unknown key-share attacks. None of the participants can force to establish a session key with a participant that he does not know but believes he is sharing the session key with the participants that he knows.
- Key Control Resilience. The session key should be determined jointly by all participants (e.g., , and ). None of the participants can control the session key construction procedure alone. The main purpose of key control resilience is to ensure session key construction fairness and security. It should not be possible for any participants or adversaries to predict or predetermine the session key value.
Constructing a desirable AKA protocol must conform to these desirable security attributes: known-key security, forward secrecy, key-compromise impersonation resilience, unknown key-share resilience, key control resilience. Thus, an AKA protocol is able to resist various active and passive attacks.
2.4. Notations
The system parameters, notations and functions used in the whole proposed protocol are defined as follows:
- : an additive cyclic group.
- : a multiplicative cyclic group.
- : a bilinear map, .
- : a generator of the group .
- : the private key of the authentication server, .
- : the public key of the authentication server, .
- : the identity of the authentication server.
- : the identity of the client.
- : the identity of the application server.
- : the private key of /the private key of .
- : six one-way hash functions, , where is a fixed length and .
- : two map-to-point hash functions, .
3. The Proposed Protocol
We present the proposed ESL-secure ID-based three-party AKA protocol for mobile distributed computing environments in this section. The proposed protocol consists of three phases: the system setup phase, the key extract phase and the mutual authentication and key agreement phases. We also present a parallel version of the proposed protocol to enhance the protocol run performance.
3.1. System Setup Phase
The proposed protocol system consists of an authentication server , an application server and a mobile client . The client refers to a user with handheld device and communicates with the authentication server and the application server through open channels such as wireless networks. The application server provides services or applications to the client . The authentication server is responsible for computing private keys according to the application server and the client ’ identities and distribute the private keys to them via a secure channel. The authentication server is also responsible to generate the systems parameters.
In the system setup phase the authentication server first generates two cyclic groups and of a large prime order , an admissible bilinear map , and a random generator of , where and are additive and multiplicative cyclic groups of large prime order , respectively. The authentication server then performs the following tasks:
- Randomly select a system private key .
- Compute the system public key .
- Choose two map-to-point hash functions .
- Choose six one-way hash functions , where is a fixed length and .
- Publish public parameters and functions .
3.2. Key Extract Phase
In the key extract phase client and the application server separately submit their identities and to the authentication server and receive their corresponding private keys and , respectively. The key extract phase is depicted in Figure 1. To the client as an example, the detailed procedures are presented as follows:
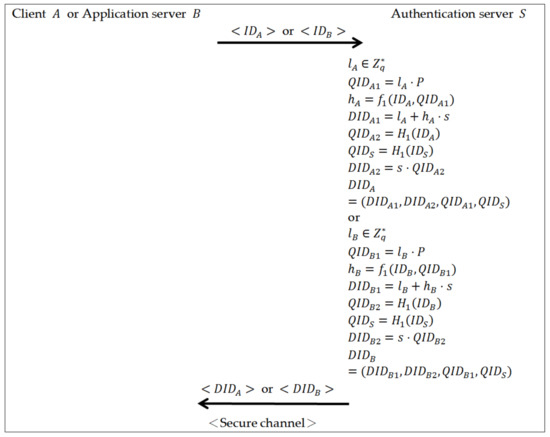
Figure 1.
The key extract phase.
- The client submits its identity to the authentication server .
- Upon receiving the client with identity , the authentication server chooses an ephemeral secret value , and compute , , , , and .
- Set as the client ’s private key and send it to the client via a secure channel.
The authentication server also set as the application server ’s private key in the same procedures.
3.3. Mutual Authentication and Key Agreement Phase
Suppose that the client would like to communicate with the authentication server and request services or applications from the application server . As depicted in Figure 2, the detailed interactions between the three participants are presented as below:


Figure 2.
The mutual authentication and key agreement phase.
Step 1. :
The client with identity performs the following off-line computations in advance:
- (1)
- Random select an ephemeral secret .
- (2)
- Compute and .
- (3)
- Compute and .
- (4)
- Send to the authentication server .
Step 2. :
Upon receiving , the authentication server authenticates the client by performing the following tasks:
- (1)
- Compute , and .
- (2)
- Check whether or not. If the equation holds, then the authentication server accepts the request. Otherwise, the authentication server terminates it.
- (3)
- Random select an ephemeral secret .
- (4)
- Compute , and .
- (5)
- Compute , and .
- (6)
- Send to the application server .
Step 3. :
Upon receiving , the application server authenticates the authentication server by performing the following tasks:
- (1)
- Compute .
- (2)
- Check whether or not. If the equation holds, then the application server accepts the request. Otherwise, the application server terminates it.
- (3)
- Random select an ephemeral secret .
- (4)
- Compute and .
- (5)
- Compute and .
- (6)
- Send to the authentication server .
Step 4. : ,
Upon receiving , the authentication server authenticates the application server by performing the following tasks:
- (1)
- Compute , and .
- (2)
- Check whether or not. If the equation holds, then the authentication server accepts the application server . Otherwise, the authentication server terminates it.
- (3)
- Compute and .
- (4)
- Acquire two nonce , .
- (5)
- Compute and .
- (6)
- Compute and .
- (7)
- Send and to the client .
Step 5. :
Upon receiving and , the client authenticates the authentication server by performing the following tasks:
- (1)
- Compute .
- (2)
- Check whether or not. If the equation holds, then the client accepts the authentication server . Otherwise, the client terminates it.
- (3)
- Compute and .
- (4)
- Send to the application server .
Step 6. :
Upon receiving , the application server authenticates the client and the authentication server by performing the following tasks:
- (1)
- Compute .
- (2)
- Check whether or not. If the equation holds, then the application server accepts the authentication server . Otherwise, the application server terminates it.
- (3)
- Compute .
- (4)
- Check whether or not. If the equation holds, then the application server can be sure that the client has the ability to compute the session key. Otherwise, the application server notifies the authentication server that the authentication has been failed and terminates it.
- (5)
- Compute .
- (6)
- Compute the session key .
- (7)
- Send to the client .
On the other side, upon receiving , the client checks whether or not. If the equation holds, the client can be sure that the application server has the ability to compute the session key, then the client computes the session key . Otherwise, the client notifies the authentication server that the authentication has been failed and terminates it. After transferring the messages in the above six steps, the client and the application server can authenticate each other via the authentication server and agree upon the session key. The authentication server also can compute or to compute the session key which is shared with the client and the application server . The session key is created by the three participants and not created by the authentication server alone. Therefore, the proposed protocol can solve the problem in the resilience of key control of the KTAP while the authentication server still can monitor the communication messages to prevent and trace network crime.
In Steps 2 and 4, the correctness of the equations that the authentication server uses to authenticate the client and the application server can be proved by the bilinear pairings feature operation. To the client as an example, the correctness of in Step 2 is presented as follows:
In Step 3, the correctness of the equation that the application server uses to verify the message sent from the authentication server . The correctness of is presented as follows:
In Steps 5 and 6, the equations and that the client and the application server use to authenticate the authentication server , respectively. If and , we say that and are valid, the equations hold because of and .
In Step 6, if , we say that and are valid. The client , the application server and the authentication server have established a common session key . The correctness of is presented as follows:
3.4. The Parallel Version
Chen et al. [31] pointed out that to enhance the performance and reduce latency of an AKA protocol, the communication steps in the protocol should be as parallel as possible. To enhance the proposed protocol performance, a parallel version of the protocol is presented. We reordered the steps in the proposed protocol as shown in Figure 3. It can be obviously seen that the steps are reordered but the message exchange contents are the same as those in the preceding protocol. In the parallel version of the proposed protocol, the protocol can be executed in four rounds.

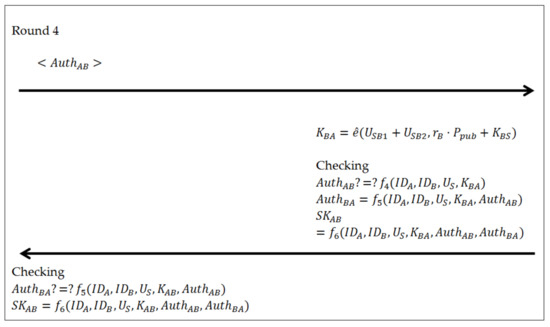
Figure 3.
The parallel version of Ephemeral Secret Leakage (ESL)-secure ID-based three-party Authenticated Key Agreement (AKA) protocol.
3.5. Preventing and Tracing Network Crime
In a distributed computing environment preventing and tracing network crime often consists of mechanisms to prevent, detect and deter security violations that involve the transmission of messages. Authentication, Authorization, Accounting (AAA) services are the commonly used mechanisms to protect the security of networks in distributed computing environments [32,33,34]. The authentication service is the first inspection mechanism that prevents and traces network crime. The authorization service is based on the security primitives of the authentication service. The authentication service and the authorization service are usually performed together to ensure that a client requesting access to the services is in fact the client to whom entry is authorized. It is able to prevent services access by a client that is not authorized and trace which services were accessed by which client. After authentication and authorization, a common session key is constructed using symmetric encryptions. These are most effective techniques to protect transferred messages from being intercepted, disclosed and forged by an adversary. The AAA services also provide accounting services that are used to collect resources usage information for billing. In the generic AAA services, the authentication, authorization and accounting services are provided by an authentication server referred to as AAA server.
The proposed protocol is an ID-based three-party AKA protocol that provides mutual authentication and establishes a common session key between three participants. The authentication server in the proposed protocol is responsible for the authentication of participating entities and restricts access to authorized clients. Both clients and the application servers must send their identities to the authentication server and retrieve the private keys computed by the authentication server in the key extract phase. A client or an adversary without the private key is unable to request and access the services provided by an application server. An application server without the private key is unable to be accepted by the authentication server and the clients. The authentication server needs to authenticate the clients and the application servers but also needs to be authenticated by the clients and the application servers. The proposed protocol is able to prevent unauthorized access and detect, deter an adversary who constructs a forged identity as the real authentication server or application server to acquire useful information from the clients.
The proposed protocol allows three participants to establish a common session key to protect the transferred messages and also ensures the authenticity. The common session key of the proposed protocol is derived from the authentication server, the client and the application server’s private keys and their ephemeral secrets in the mutual authentication and key agreement phase. The three participants are able to ensure that no other participants or adversaries can learn or determine the value of the common session key and the authentication server could use the common session key to monitor the transferred messages. The common session key of the proposed protocol is able to protect and guarantee the authenticity of the transferred messages and also trace which client has accessed the services provided by which application server. None of the clients are able to deny that the client has requested and accessed the services provided by the application server.
In the proposed protocol the authentication server provides authentication service, authorization service and uses the common session key to prevent and trace network crime. However, the authentication server does not provide accounting services. The most important aspect in the AAA services is the authentication service and the purpose of the accounting service is to collect information on resource usage for billing, auditing and trend analysis [35,36,37,38]. Hence, the proposed protocol is suitable for various communication systems in the distributed computing environments in terms of protecting the security of network, preventing and tracing network crime.
4. Security and Performance Analysis
In this Section we discuss the security analysis of the proposed protocol. The simulation results were performed using the AVISPA tool. The methodology used in our performance analysis and the metrics utilized to evaluate the results of the proposed protocol.
4.1. Security Analysis
In this Section we present the security analysis of the proposed protocol to show the security attributes required for AKA protocols are satisfied and the simulation results by the AVISPA tool.
- Mutual authentication and Ephemeral-Secret-Leakage Resistance. The proposed protocol adopted Tseng et al.’s ESL-secure ID-AKE protocol [7] to achieve the client-to-server authentication. The authentication server authenticates the client and the application server by checking whether and or not. To the client as an example, the message , where , and can be viewed as a signature on a message in Tseng et al.’s ESL-secure ID-AKE protocol. According to the security analysis by Tseng et al., if an adversary could have obtained the ephemeral secret using ESL attacks, the adversary still needs to solve the computational Diffie-Hellman problem to violate the client-to-server authentication.The application server authenticates the authentication server by checking whether or not. The message , where , and , can be viewed as a signature on a message . Without knowledge of the authentication server ’s private key , none of the participants or adversaries can forge the message and compute a valid signature. To forge a valid message , an adversary must have obtained the authentication server ’s private key from , where . It is a discrete logarithm problem to the adversary.The proposed protocol provides the server-to-client authentication that is also based on Tseng et al.’s ESL-secure ID-AKE protocol. The client and the application server authenticate the authentication server by checking whether and or not. Even though an adversary could obtain the client ’s ephemeral secret by the ESL attacks. Since and are derived from and respectively. To violate the server-to-client authentication, the adversary has to solve the computational Diffie-Hellman problem to obtain and the discrete logarithm problem to compute the application server ’s ephemeral secret and the computational Diffie-Hellman problem to obtain from the transferred messages. Otherwise, the adversary only can compute the authentication server ’s private key from , in which the adversary needs to solve the discrete logarithm problem.The application server can be sure that the client has obtained the session key by checking whether or not. The client checks whether or not to be sure that the application server also has obtained the session key and both of them with the authentication server can agree upon the common session key . For computing a valid message or , we assume that the client ’s ephemeral secret has been compromised by an adversary. Since the messages and are derived from , where and , the adversary must solve the computational Diffie-Hellman problem to compute or the discrete logarithm problem to compute and the computational Diffie-Hellman problem to compute from transferred messages. Otherwise, the adversary only can compute the authentication server ’s private key from , in which the adversary needs to solve the discrete logarithm problem.Without knowledge of the private key of a participant (e.g., the client ’s private key ). An adversary cannot impersonate the participant since the adversary is unable to forge a valid signature. The proposed protocol employs the signature to authenticate the participants’ identities and one way hash function to protect the integrity of the transferred messages. Even though the ephemeral secret of the client has been compromised, each participant can be sure that none of the adversaries can impersonate other participants to violate the verification procedures and corrupt the participants’ private keys and the session key.
- Known Key Security. Suppose that an adversary can eavesdrop on the transmitted messages to learn the previous session keys. However, the session key of the proposed protocol is unique and dependent of each participant’s ephemeral secrets , and and private keys , and . Therefore, knowledge of the previous session keys does not enable the adversary to derive other session keys and does not give the adversary any information that the adversary could use to derive other session keys. Even though the client ’s ephemeral secret has been compromised. If an adversary would like to compute , where from the transferred messages, the adversary needs to solve the computational Diffie-Hellman problem to compute the client ’s private key or the discrete logarithm problem from , where to obtain the authentication server ’s private key . Otherwise, the adversary only can solve the discrete logarithm problem and the computational Diffie-Hellman problem to compute the application server ’s corresponding ephemeral secret and private key . In the proposed protocol, even if one of the session key has been compromised, the security of the other or future session keys is not endangered.
- Partial Forward Secrecy. The proposed protocol session key is dependent on each participant’s private key and corresponding ephemeral secret. In the proposed protocol, if the private key of client or the application server has been compromised, an adversary also needs to obtain the corresponding ephemeral secrets to compute the session key. Suppose that the adversary would like to compute the corresponding ephemeral secrets from the transferred messages, the adversary needs to solve the discrete logarithm problem. However, if the adversary corrupts the private key of the authentication server , it is obvious that all of the previous session keys can be recovered from the transferred messages. Since the adversary is indeed able to compute , or , and . The proposed protocol offers partial forward secrecy.
- Key-Compromise Impersonation Resilience. To discuss the key-compromise impersonation resilience property, we assume that client ’s private key is compromised to an adversary who tries to impersonate the application server to cheat the client and the authentication server . When the client requests service from the application server , the adversary only can choose and from the previous sessions and send them to the authentication server and the client , respectively. Since the adversary cannot derive the application server ’s private key and the corresponding ephemeral secret from the transferred messages to compute , where . The adversary only can violate the verification procedures of the authentication server . If the adversary tries to derive the ephemeral secret and the private key from the transferred messages to compute and construct the session key, the adversary needs to solve the discrete logarithm problem and the computational Diffie-Hellman problem.
- Unknown Key-Share Resilience. To implement such an attack, the adversary is required to obtain the private key of client or the application server . In the proposed protocol, both of the client and the application server have to be authenticated by the authentication server . Only the participant that has the private key distributed from the authentication server could compute the valid signature and thus pass the verification procedures and compute the session key. To the client as an example, the client with its private key and the ephemeral secret can compute and to pass the verification procedures of the authentication server and the application server . The ephemeral secret with are able to compute the session key . Hence, the proposed protocol can withstand an unknown key-shared attack.
- Key control Resilience. In the proposed protocol, the session key , where is determined by all participants’ private keys and corresponding ephemeral secrets. None of the participants can force a session key to be predetermined or predict the value and control the outcome of the session key. Hence, the proposed protocol ability to prevent the session key is created only by the authentication server or other two participants.
4.2. Formal Analysis Using AVISPA
Besides the above analysis we also provide a formal analysis of the proposed protocol using AVISPA. AVISPA is a push-button tool which is one of the commonly used automated security validation tools for Internet security-sensitive protocols and applications [19]. AVISPA was developed based on the Dolev-Yao intruder model [35]. In this model, the intruder has full control over the network and the intruder can intercept, inject, analyze and modify messages in transit. In addition, the intruder can play the role of a legitimate participant and gain knowledge of the compromised participant, but he is not allowed to crack the underlying cryptography. The first step in using AVISPA is to implement the analyzed protocol in High-Level Protocol Specification Language (HLPSL) that is an expressive, modular, role-based formal language for security protocol description and specifying their security properties. The HLPSL presentation of the analyzed protocol is translated into a lower level language called Intermediate Format (IF) using HLPSL2IF. IF the analyzed protocol is used as an input to different back-ends, the current version of AVISPA tool comprises four back-ends that implement a variety of automatic analysis techniques, namely, On-the-fly Model-Checker (OFMC), Constraint-Logic-based Attack Searcher (CL-AtSe), SAT-based Model-Checker (SATMC), and Tree Automata based on Automatic Approximations for the Analysis of Security Protocols (TA4SP) [30]. The four back-ends perform the analysis and output the results in precisely defined output format stating whether problems exist in the protocol or not. Thus, AVISPA is appropriate for the analysis of large-scale security protocols and applications.
To evaluate the proposed protocol security using AVISPA, we implemented the proposed protocol using the HLPSL and the role specifications of the client, the application server and the authentication server are given in Appendix A. We simulated the proposed protocol using the AVISPA web tool [36]. The proposed protocol is analyzed in the OFMC and CL-AtSe back-ends. Both of the two back-ends are helpful for the verification of the proposed protocol and detection of attacks. Note that intruder knowledge of the proposed protocol comprises the ephemeral secret of the client. After executing the code in AVISPA web tool, both OFMC and CL-AtSe back-ends outputs were generated and shown in Figure 4 and Figure 5. From the simulated results, there are no major attacks to the protocol and the simulated results also confirm the correctness of the protocol security analysis. The security goals of the proposed protocol are achieved and thus the proposed protocol confirms security against various active and passive attacks.
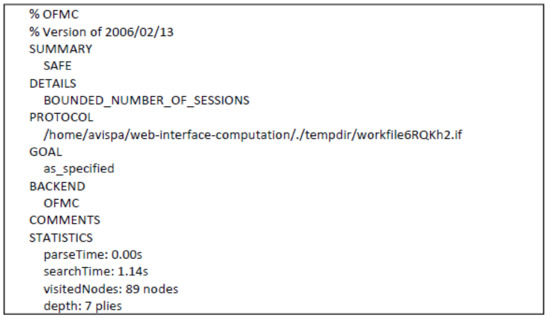
Figure 4.
Simulation result of the proposed protocol on On-the-fly Model-Checker (OFMC) model checker.

Figure 5.
Simulation result of the proposed protocol on Constraint-Logic-based Attack Searcher (CL-AsSe) model checker.
4.3. Performance Analysis
In this section, the performance and the simulation results of the proposed protocol are analyzed. For convenience, the following notations are used to analyze the computational cost:
- : the execution time for a bilinear pairing operation .
- : the execution time for points in multiplication operation.
- : the execution time for a modular exponential operation in .
- : the execution time for a map-to-point hash function in .
- : the execution time for an addition operation of points in or a multiplication operation in .
- : the execution time for a one-way hash function.
The total computational cost for the client side in this proposed protocol is . However, the computation in Step 1 of the mutual authentication and key agreement phase for the client side can be pre-computed using offline computation. The total cost for on-line computation on the client side is . The total computational cost for the application server side is . On the other hand, the authentication server side performs Steps 2 and 4 to authenticate the client, the application server and constructs the session key. The total computational cost for the authentication server side is .
Note that compared with and , , , and are more time-consuming [31]. The proposed protocol adopts an imbalanced computation technique and an online/offline computation technique to reduce the computational load for the client side. From the analysis result mentioned above, the computational burdens are major on the authentication server and the application server which are powerful servers and the offline pre-computation reduces the computational cost required for the client side. Although, bilinear pairing operations are still required for the client side, the proposed protocol captures all basic desirable security attributes including the ESL resistance and the authentication server is able to monitor the transferred messages to prevent and trace network crime. The required computation cost of the proposed protocol is also reasonable.
4.4. Software Performance
Scott et al. [37] and Oliveira et al. [38] implemented the related pairing-based operations for low-power computing devices (i.e., smartcards and sensor nodes) in 2006 and 2011, respectively. Scott et al. used the processor on the Philips HiPersmart card offers the maximum clock speed of 36 MHz for related pairing-based operations. Scott et al. pointed out that for the security level of the Ate pairing system, a popular and valid choice would be to use a supersingular curve or non-supersingular curve over a finite field , with bits and a large prime order bits. The simulations are performed with a simulator implemented in Android system. We used the Jpair library to execute the simulations, which is a Java implementation of bilinear pairings to implement the software and a mobile device (Android 5.0 and 2.3 GHz Intel Atom with 4 GB of RAM) for the client side. Since the Weil pairing evaluation is more time-consuming than the Tate pairing [39], simulations are provided based on the Tate pairing on a supersingular elliptic curve. In the proposed protocol security level, the parameters will be the same as Scott et al.’s experimental data mentioned above. Table 1 lists the simulations data for related pairing-based operations on the client side. The execution time results for the client side have an average of 1000 simulations. Table 2 lists the computational cost and the execution time (in seconds) on the client side, where the execution time is measured using Table 1. The proposed protocol adopts an online/offline computation technique in which the online execution time on the client side requires 0.553 s. Although, the bilinear pairing operations are still required for the client side, the proposed protocol is still efficient and suitable for mobile distributed computing environments.

Table 1.
Computational cost on the client side.

Table 2.
Execution time on the client side.
5. Conclusions
We proposed an ESL-secure ID-based three-party AKA protocol for mobile distributed computing environments. The proposed protocol employs Tseng et al.’s ESL-secure ID-AKE protocol [7] against ESL attacks. The proposed protocol keeps all of the merits of KTAP regarding security including the authentication server is able to monitor the communication messages to prevent and trace network crime and solves the problems of KTAP in which the session key is only created by the authentication server. Each participant can contribute information to derive the common session key. In the security analysis, the proposed protocol resists ESL attacks and also satisfies the security attributes required for AKA protocols: known-key security, partial forward secrecy, key-compromise impersonation resilience, unknown key-share resilience and key control resilience. In addition, the formal validation of the proposed protocol is performed using an automated validation tool AVISPA. The simulations results show that the proposed protocol is secure against active and passive adversaries. In the performance analysis, the proposed protocol adopted an imbalanced computation technique to shift the computational burden to the powerful servers. The software performance simulation result shows that the mobile client could perform offline pre-computation to reduce the online computation cost. Furthermore, a parallel version of the proposed protocol is proposed to enhance the protocol run performance.
In the future, we will implement the proposed in the “To Say” APP. The “To Say” APP allows users store the last words (text, image, audio, and video) in the application server and send the last words to the designated receivers in a secure channel. The authentication server is responsible for authenticate the users and helps them to construct a common session key with the receivers. When the APP detects the users are not active, the server will automatically send the last words to the designated receivers.
Acknowledgments
This study was supported by the National Science Council of Taiwan under grant MOST 106-2221-E-018-001 and MOST 106-2622-E-018-002-CC3.
Author Contributions
The authors contributed equally to this work.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
The HLPSL code of the proposed protocol.
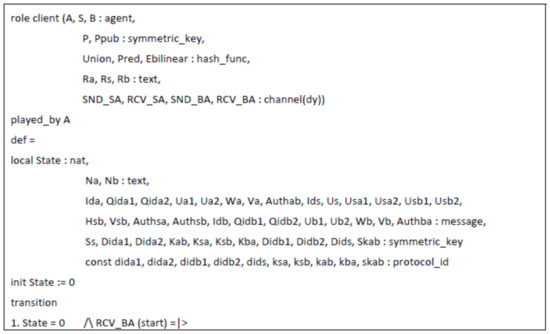
Figure A1.
Role specification of the client in HLPSL.


Figure A2.
Role specification of the authentication server in HLPSL.


Figure A3.
Role specification of the application server in HLPSL.
References
- Wen, H.A.; Lin, C.L.; Hwang, T. Provably secure authenticated key exchange protocols for low power computing clients. Comput. Secur. 2006, 25, 106–113. [Google Scholar] [CrossRef]
- Wong, D.S.; Chan, A.H. Efficient and mutually authenticated key exchange for low power computing devices. In Proceedings of the 14th International Conference on the Theory and Application of Cryptology and Information Security, Melbourne, Australia, 9–13 December 2008; pp. 272–289. [Google Scholar]
- Jakobsson, M.; Pointcheval, D. Mutual Authentication for Low-Power Mobile Devices. Financ. Cryptogr. 2002, 2339, 178–195. [Google Scholar]
- Choi, K.; Hwang, J.; Lee, D.; Seo, I. ID-based Authenticated Key Agreement for Low-Power Mobile Devices. Inf. Sec. Priv. 2005, 3574, 494–505. [Google Scholar]
- Chuang, Y.H.; Tseng, Y.M. Towards generalized ID-based user authentication for mobile multi-server. Int. J. Commun. Syst. 2012, 25, 447–460. [Google Scholar] [CrossRef]
- Wu, T.Y.; Tseng, Y.M. An efficient user authentication and key exchange protocol for mobile client–server environment. Comput. Netw. 2010, 53, 1062–1070. [Google Scholar] [CrossRef]
- Tseng, Y.M.; Tseng, L. Ephemeral-Secret-Leakage Secure ID-Based Authenticated Key Exchange Protocol for Mobile Client-Server Environments. In Proceedings of the 24th Cryptology and Information Security Conference, Putrajaya, Malaysia, 24–26 June 2014. [Google Scholar]
- Diffie, W.; Hellman, M.E. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Tsai, C.S.; Lee, C.C.; Hwang, M.S. Password Authentication Schemes: Current Status and Key Issues. IJINS 2006, 3, 101–115. [Google Scholar]
- Shamir, A. Identity-Based Cryptosystems and Signature Schemes. Adv. Cryptol. 1985, 5, 47–53. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-Based Encryption from the Weil Pairing. In Proceedings of the 21st Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; pp. 213–229. [Google Scholar]
- Boneh, D.; Boyen, X. Secure Identity Based Encryption without Random Oracles. In Proceedings of the 24th Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 2004; pp. 443–459. [Google Scholar]
- Waters, B. Efficient Identity-Based Encryption without Random Oracles. In Proceedings of the 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; pp. 114–127. [Google Scholar]
- Gentry, C. Practical Identity-Based Encryption without Random Oracles. In Proceedings of the 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, St. Petersburg, Russia, 28 May–1 June 2006; pp. 445–464. [Google Scholar]
- Joux, A. A One Round Protocol for Tripartite Diffie–Hellman. Algorithm. Number Theory 2000, 1838, 385–393. [Google Scholar]
- Al-Riyami, S.; Paterson, K. Tripartite Authenticated Key Agreement Protocols from Pairings. In Proceedings of the 9th IMA International Conference, Cirencester, UK, 16–18 December 2003; pp. 332–359. [Google Scholar]
- Lim, M.H.; Lee, S.; Moon, S. Cryptanalysis of Tso et al.’s ID-Based Tripartite Authenticated Key Agreement Protocol. Inf. Syst. Secur. 2007, 4812, 64–76. [Google Scholar]
- Hölbl, M.; Welzer, T.; Brumen, B. Two proposed identity-based three-party authenticated key agreement protocols from pairings. Comput. Secur. 2010, 29, 244–252. [Google Scholar] [CrossRef]
- Xiong, H.; Chen, Z.; Li, F. New identity-based three-party authenticated key agreement protocol with provable security. JNCA 2013, 36, 927–932. [Google Scholar] [CrossRef]
- Yeh, H.T.; Sun, H.M. Password-based user authentication and key distribution protocols for client–server applications. J. Syst. Softw. 2004, 72, 97–103. [Google Scholar] [CrossRef]
- Kohl, J.T.; Neuman, B.C.; Tso, T.Y. The evolution of the Kerberos authentication system. In Distributed Open System; IEEE Computer Society Press: Washington, DC, USA, 1991; pp. 78–94. [Google Scholar]
- Yeh, H.T.; Sun, H.M. Password authenticated key exchange protocols among diverse network domains. Comput. Electr. Eng. 2005, 31, 175–189. [Google Scholar] [CrossRef]
- Li, G. Optimal authentication protocols resistant to password guessing attacks. In Proceedings of the Eighth IEEE Computer Security Foundations Workshop, Kerry, Ireland, 13–15 June 1995; pp. 24–29. [Google Scholar]
- Kwon, T.; Kang, M.; Jung, S.; Song, J. An Improvement of the Password-Based Authentication Protocol (K1P) on Security against Replay Attacks. IEICE Trans. Commun. 1999, 82, 991–997. [Google Scholar]
- Kwon, T.; Song, J. Authenticated key exchange protocols resistant to password guessing attacks. Commun. IEE Proc. 1998, 145, 304–308. [Google Scholar] [CrossRef]
- Chang, T.Y.; Hwang, M.S.; Yang, W.P. A communication-efficient three-party password authenticated key exchange protocol. Inf. Sci. 2011, 181, 217–226. [Google Scholar] [CrossRef]
- Ni, L.; Chen, G.; Li, J. Escrowable identity-based authenticated key agreement protocol with strong security. Comput. Math. Appl. 2013, 65, 1339–1349. [Google Scholar] [CrossRef]
- Chang, T.Y.; Tsai, C.J.; Lin, J.H. A graphical-based password keystroke dynamic authentication system for touch screen handheld mobile devices. J. Syst. Softw. 2012, 85, 1157–1165. [Google Scholar] [CrossRef]
- Blake-Wilson, S.; Menezes, A. Authenticated Diffe-Hellman Key Agreement Protocols. In Proceedings of the Selected Areas in Cryptography, Kingston, Ontario, Canada, 17–18 August 1999; pp. 339–361. [Google Scholar]
- AVISPA v1.1 User Manual. 2006. Available online: http://www.avispa-project.org/ (accessed on 24 January 2018).
- Chen, T.H.; Lee, W.B.; Chen, H.B. A round- and computation-efficient three-party authenticated key exchange protocol. J. Syst. Softw. 2008, 81, 1581–1590. [Google Scholar] [CrossRef]
- Metz, C. AAA protocols: Authentication, authorization, and accounting for the Internet. IEEE Int. Comput. 1999, 3, 75–79. [Google Scholar] [CrossRef]
- Rensing, C.; Karsten, M.; Stiller, B. AAA: A survey and a policy-based architecture and framework. IEEE Netw. 2002, 16, 22–27. [Google Scholar] [CrossRef]
- Decugis, S. Towards a Global AAA Framework for Internet. In Proceedings of the 2009 Ninth Annual International Symposium on Applications and the Internet, Bellevue, WA, USA, 20–24 July 2009; pp. 227–230. [Google Scholar]
- Dolev, D.; Yao, A.Y. On the Security of Public Key Protocols. IEEE Inf. Theory Soc. 1983, 29, 198–208. [Google Scholar] [CrossRef]
- AVISPA Web tool. Automated Validation of Internet Security Protocols and Applications. Available online: http://www.avispa-project.org/web-interface (accessed on 24 January 2018).
- Scott, M.; Costigan, N.; Abdulwahab, W. Implementing Cryptographic Pairings on Smartcards. In Proceedings of the 8th International Workshop, Yokohama, Japan, 10–13 October 2006; pp. 134–147. [Google Scholar]
- Oliveira, L.B.; Aranha, D.F.; Gouvêa, C.P.L.; Scott, M.; Câmara, D.F.; López, J. TinyPBC: Pairings for authenticated identity-based non-interactive key distribution in sensor networks. Comput. Commun. 2011, 34, 485–493. [Google Scholar] [CrossRef]
- Hu, L.; Dong, J.W.; Pei, D.Y. Implementation of Cryptosystem Based on Tate Pairing. J. Comput. Sci. Technol. 2005, 20, 264–269. [Google Scholar] [CrossRef]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).