Developing Secure IoT Services: A Security-Oriented Review of IoT Platforms
Abstract
1. Introduction
- Lack of exhaustive documentation of the existing frameworks
- Multiple programming languages to control the devices
- Hardware heterogeneity of the devices
- Resource constraints inherent to the IoT nodes
- Several communication protocols used by the devices
2. Related Works
3. Security Criteria for Comparison
- Authentication: The authentication process provides a way of identifying an entity within the system. In the context of IoT, the produced data are massive, causing several security and privacy issues, especially regarding the authentication among the devices, the users and the system itself [26]. To address this limitation, various authentication schema have been proposed [27,28]. Thus, we considered the following three sub-criteria:
- Authentication protocol between IoT devices and IoT platform
- Authentication protocol between the IoT platform and users (both end-users or administrators)
- Authentication protocol among the components of the IoT platform
- Encrypted information management: The encryption process takes care of encoding a message or an information so that only authorized entities can access it [29]. Due to the amount of information and the resource-constrained nature of the IoT devices, the encryption assumes a fundamental role. In this case, we analyzed the encryption at two levels:
- Encryption for data at rest (i.e., data physically stored and inactive)
- Encryption for data in transit (i.e., data transmitted among the entities)
- Authorization: Once a user has been successfully authenticated in the system, the authorization process determines whether the user has the rights to access a given resource or to execute an activity. As in the case of authentication, authorization strategies represent a strong requisite in the IoT ecosystem, since unauthorized intruders can perform malevolent actions, such as compromising the integrity of the system by maliciously modifying its data [30]. We detailed this feature in two sub-criteria, as follows:
- User authorization to perform operations within the IoT platform
- Authorization of the IoT devices to perform operations among the components of the IoT platform
- Accounting: It measures the amount of resources a specific user consumes during their access. Examples of resources include the session time or the data which the user has sent and/or received during a session [31]. Given the huge number of performed operations within the IoT platform, this parameter is also crucial from a security perspective. In addition, in this case, we extracted the following sub-criteria:
- Accounting for operations that users perform over the data and IoT devices (e.g., read, write, aggregation, etc.)
- Accounting for operations created for IoT services components on data and IoT devices (e.g., accounting, disassociation, update, etc.)
- Anomaly detection: It refers to the ability of the system to spot anomalies among the normal activities, which may indicate the presence of a security incident [32]. In this context, this criterion is related to the IoT platform capability to detect anomalies in IoT service’s state or in the normal operation of its components [33]. We consider this characteristic of primary importance in a full-fledged IoT framework, so that the security incidents can be reported in a timely fashion, and possible countermeasures can be undertaken [16].
4. IoT Platforms Overview
4.1. Samsung Artik
4.2. Amazon IoT (AWS IoT)
4.3. IBM Watson IoT
4.4. Oracle IoT
4.5. Evrythng
4.6. Dweet
4.7. Node-Red
4.8. Nimbits
4.9. The Thing System
4.10. Sitewhere
5. IoT Platforms Analysis
5.1. Samsung Artik
5.1.1. Authentication
5.1.2. Encryption
5.1.3. Authorization
- Authorization code: Once the user signs using an authentication method, she is redirected to the IoT application with an authorization code which at the same time allows the application to ask for an application token used to make API calls.
- Implicit method: Once the user signs using an authentication method, she is redirected to the application server along with a token that is used by the application to make API calls. Only an application with a token can make API calls. Artik also permits sharing devices through an invitation sent by email, which allows the user to see the device data and send actions on the device.
5.1.4. Accounting
5.1.5. Anomaly Detection
5.2. Amazon IoT (AWS IoT)
5.2.1. Authentication
5.2.2. Encryption
5.2.3. Authorization
5.2.4. Accounting
5.2.5. Anomaly Detection
5.3. IBM Watson IoT
5.3.1. Authentication
5.3.2. Encryption
5.3.3. Authorization
5.3.4. Accounting
5.3.5. Anomaly Detection
5.4. Oracle IoT
5.4.1. Authentication
5.4.2. Encryption
5.4.3. Authorization
5.4.4. Accounting
5.4.5. Anomaly Detection
5.5. Evrythng
5.5.1. Authentication
5.5.2. Encryption
5.5.3. Authorization
5.5.4. Accounting
5.5.5. Anomaly Detection
5.6. Dweet
5.6.1. Authentication
5.6.2. Encryption
5.6.3. Authorization
5.6.4. Accounting
5.6.5. Anomaly Detection
5.7. Node-Red
5.7.1. Authentication
5.7.2. Encryption
5.7.3. Authorization
5.7.4. Accounting
5.7.5. Anomaly Detection
5.8. Nimbits
5.8.1. Authentication
5.8.2. Encryption
5.8.3. Authorization
5.8.4. Accounting
5.8.5. Anomaly Detection
5.9. The Thing System
5.9.1. Authentication
5.9.2. Encryption
5.9.3. Authorization
5.9.4. Accounting
5.9.5. Anomaly Detection
5.10. Sitewhere
5.10.1. Authentication
5.10.2. Encryption
5.10.3. Authorization
5.10.4. Accounting
5.10.5. Anomaly Detection
5.11. Summary
6. Description of the IoT Service to Implement
- Collision management device: It measures the presence of objects within a horizontal and vertical space.
- Cabin pressure device: It measures the pressure level in the cabin.
- Altitude management device: It measures the altitude at which the airplane is located.
- Fuel level management device: It measures the fuel level of the aircraft.
- Engine temperature management device: It measures the temperature of the engine.
- Engine coolant management device: It measures the coolant level of the engine.
- Storm detection device: It has two sensors: (i) a distance sensor which calculates the distance from the aircraft to a storm; and (ii) a luminosity sensor which allows determining the severity of the storm based on its luminosity.
- Fire detection device: It is a heat sensor that determines whether there is presence of fire in the aircraft.
- Navigation system: This device has geolocation functions, and reports the aircraft latitude and longitude.
- Rule 1: An alarm must be generated when the aircraft finds objects within a horizontal space less than 9.25 km and within a vertical space less than 305 m.
- Rule 2: The airplane must auto regulate the pressure in the cabin to keep it within the range [75.3–81.2] kilo Pascal.
- Rule 3: An alarm must be generated when the aircraft is below 4 km of altitude and is at a distance from the destination or origin greater than 120 km.
- Rule 4: An alarm must be generated and sent to the nearest control tower when the aircraft is at a fuel level below 20% of the tank capacity and the distance to arrival destination is bigger than 1000 km.
- Rule 5: An alarm must be generated when the engine temperature is bigger than 200 degrees Celsius.
- Rule 6: The airplane must auto regulate the level of the engine coolant to keep it above 70%. When the liquid level is under that level, an alarm must be generated.
- Rule 7: The aircraft must generate an alarm when there is a storm at less than 50 km with a severity lower than 2 on a scale of 0–5, where 0 means no severe thunderstorm and 5 means widespread severe storms, according to the scale from the Storm Prediction Center (https://www.spc.noaa.gov/).
- Rule 8: The aircraft must detect and report the presence of fire in the engine compartment. In the case of fire, the retardant foam must be activated.
- Rule 9: The plane must constantly report its geographical position.
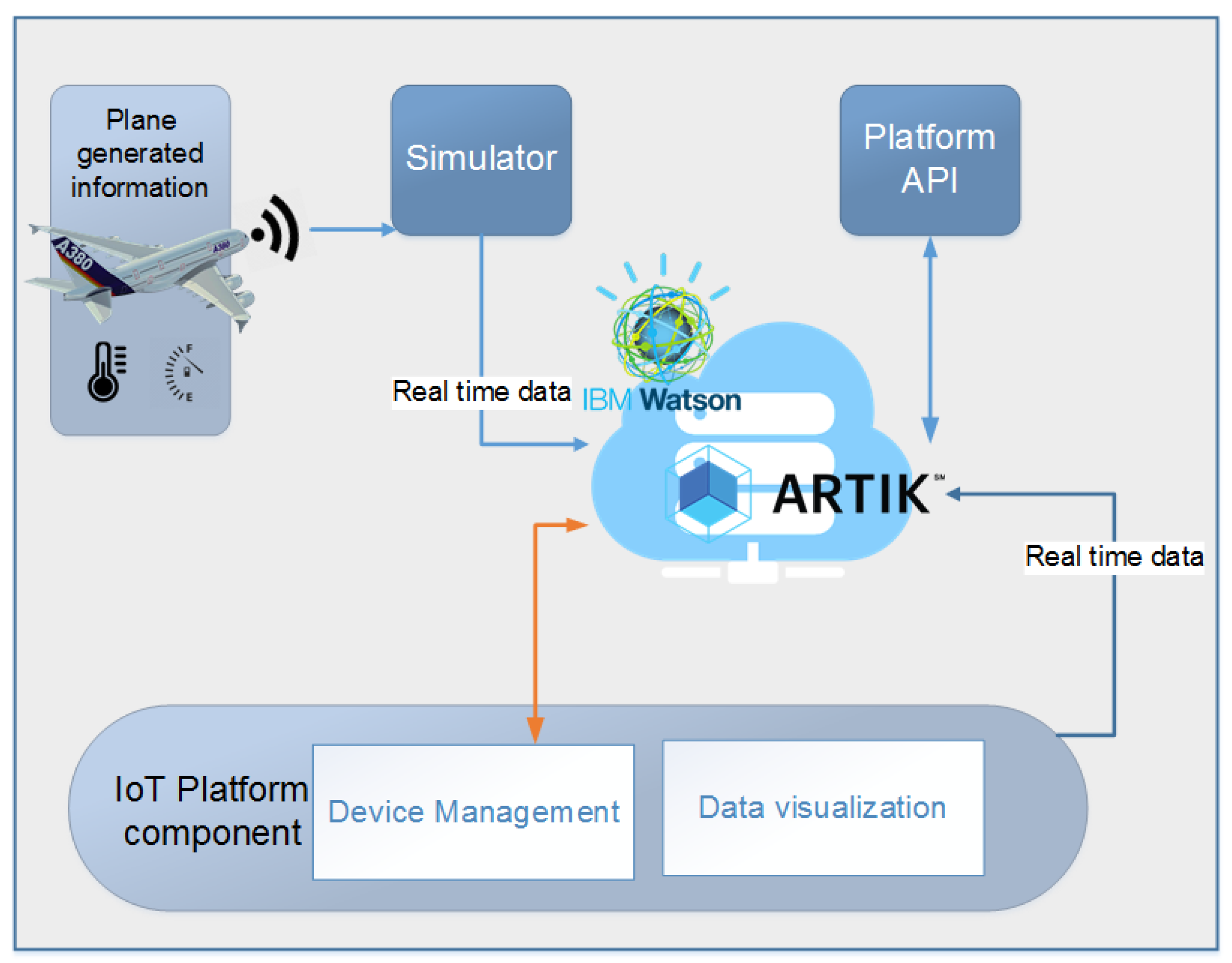
7. Implementation of the Service
7.1. IBM Watson IoT
- Access Control Permissions: It defines permissions to create, update and delete different features in the applications such as passwords, devices, members and roles.
- Blockchain Permissions: It defines permissions to manage the blockchain configuration.
- Cache Permissions: It defines permissions to manage the active data (cache).
- Connection Permissions: It defines permissions to manage the client connection status.
- Dashboard Permissions: It defines permission to create, delete, share, update and see dashboards.
7.2. Samsung Artik Cloud
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Gartner. Gartner’s 2016 Hype Cycle for Emerging Technologies Identifies Three Key Trends That Organizations Must Track to Gain Competitive Advantage; Gartner: Stamford, CT, USA, 2016. [Google Scholar]
- Li, S.; Da Xu, L.; Zhao, S. The Internet of Things: A Survey; Springer: New York, NY, USA, 2015; pp. 243–259. [Google Scholar]
- Yelamarthi, K.; Aman, M.S.; Abdelgawad, A. An application-driven modular IoT architecture. Wirel. Commun. Mob. Comput. 2017, 2017, 1350929. [Google Scholar] [CrossRef] [PubMed]
- Gomes, B.; Muniz, L.; da Silva e Silva, F.J.; Ríos, L.E.T.; Endler, M. A comprehensive cloud-based IoT software infrastructure for Ambient Assisted Living. In Proceedings of the 2015 International Conference on Cloud Technologies and Applications (CloudTech), Marrakech, Morocco, 2–4 June 2015; pp. 1–8. [Google Scholar]
- Yaqoob, I.; Ahmed, E.; Hashem, I.A.T.; Ahmed, A.I.A.; Gani, A.; Imran, M.; Guizani, M. Internet of Things Architecture: Recent Advances, Taxonomy, Requirements, and Open Challenges. IEEE Wirel. Commun. 2017, 24, 10–16. [Google Scholar] [CrossRef]
- Połap, D.; Kęsik, K.; Książek, K.; Woźniak, M. Obstacle Detection as a Safety Alert in Augmented Reality Models by the Use of Deep Learning Techniques. Sensors 2017, 17, 2803. [Google Scholar] [CrossRef] [PubMed]
- Woźniak, M.; Połap, D. Object detection and recognition via clustered features. Neurocomputing 2018, 320, 76–84. [Google Scholar] [CrossRef]
- Zarpelo, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A Survey of Intrusion Detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Abdelgawad, A.; Yelamarthi, K. Internet of things (IoT) platform for structure health monitoring. Wirel. Commun. Mob. Comput. 2017, 2017, 6560797. [Google Scholar] [CrossRef]
- Połap, D.; Winnicka, A.; Serwata, K.; Kęsik, K.; Woźniak, M. An Intelligent System for Monitoring Skin Diseases. Sensors 2018, 18, 2552. [Google Scholar] [CrossRef] [PubMed]
- Charmonman, S.; Mongkhonvanit, P. Special consideration for Big Data in IoE or Internet of Everything. In Proceedings of the 2015 13th International Conference on ICT and Knowledge Engineering (ICT Knowledge Engineering 2015), Bangkok, Thailand, 18–20 November 2015; pp. 147–150. [Google Scholar]
- Wollschlaeger, M.; Sauter, T.; Jasperneite, J. The Future of Industrial Communication: Automation Networks in the Era of the Internet of Things and Industry 4.0. IEEE Ind. Electron. Mag. 2017, 11, 17–27. [Google Scholar] [CrossRef]
- Ju, J.; Kim, M.S.; Ahn, J.H. Prototyping Business Models for IoT Service. Procedia Comput. Sci. 2016, 91, 882–890. [Google Scholar] [CrossRef]
- Gupta, H.; Vahid Dastjerdi, A.; Ghosh, S.K.; Buyya, R. iFogSim: A toolkit for modeling and simulation of resource management techniques in the Internet of Things, Edge and Fog computing environments. Softw. Pract. Exp. 2017, 47, 1275–1296. [Google Scholar] [CrossRef]
- Sarkar, S.; Chatterjee, S.; Misra, S. Assessment of the Suitability of Fog Computing in the Context of Internet of Things. IEEE Trans. Cloud Comput. 2018, 6, 46–59. [Google Scholar] [CrossRef]
- Nespoli, P.; Papamartzivanos, D.; Gómez Mármol, F.; Kambourakis, G. Optimal Countermeasures Selection against Cyber Attacks: A Comprehensive Survey on Reaction Frameworks. IEEE Commun. Surv. Tutor. 2018, 20, 1361–1396. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Xu, L.D.; He, W.; Li, S. Internet of Things in Industries: A Survey. IEEE Trans. Ind. Inform. 2014, 10, 2233–2243. [Google Scholar] [CrossRef]
- Perera, C.; Liu, C.H.; Jayawardena, S. The Emerging Internet of Things Marketplace From an Industrial Perspective: A Survey. IEEE Trans. Emerg. Top. Comput. 2015, 3, 585–598. [Google Scholar] [CrossRef]
- Ganguly, P. Selecting the right IoT cloud platform. In Proceedings of the 2016 International Conference on Internet of Things and Applications (IOTA), Pune, India, 22–24 January 2016; pp. 316–320. [Google Scholar]
- Guth, J.; Breitenbücher, U.; Falkenthal, M.; Leymann, F.; Reinfurt, L. Comparison of IoT platform architectures: A field study based on a reference architecture. In Proceedings of the 2016 Cloudification of the Internet of Things (CIoT), Paris, France, 23–25 November 2016; pp. 1–6. [Google Scholar]
- Derhamy, H.; Eliasson, J.; Delsing, J.; Priller, P. A survey of commercial frameworks for the Internet of Things. In Proceedings of the 2015 IEEE 20th Conference on Emerging Technologies Factory Automation (ETFA), Luxembourg, 8–11 September 2015; pp. 1–8. [Google Scholar]
- Yaqoob, I.; Ahmed, E.; ur Rehman, M.H.; Ahmed, A.I.A.; Al-garadi, M.A.; Imran, M.; Guizani, M. The rise of ransomware and emerging security challenges in the Internet of Things. Comput. Netw. 2017, 129, 444–458. [Google Scholar] [CrossRef]
- Ammar, M.; Russello, G.; Crispo, B. Internet of Things: A survey on the security of IoT frameworks. J. Inf. Secur. Appl. 2018, 38, 8–27. [Google Scholar] [CrossRef]
- Díaz López, D.; Blanco Uribe, M.; Santiago Cely, C.; Vega Torres, A.; Moreno Guataquira, N.; Morón Castro, S.; Nespoli, P.; Gómez Mármol, F. Shielding IoT against cyber-attacks: An event-based approach using SIEM. Wirel. Commun. Mob. Comput. 2018, 2018, 3029638. [Google Scholar] [CrossRef]
- Beltran, V.; Skarmeta, A.; Ruiz, P. An ARM-Compliant Architecture for User Privacy in Smart Cities: SMARTIE—Quality by Design in the IoT. Wirel. Commun. Mob. Comput. 2017, 2017, 3859836. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. Authentication Protocols for Internet of Things: A Comprehensive Survey. Secur. Commun. Netw. 2017, 2017, 6562953. [Google Scholar] [CrossRef]
- Nespoli, P.; Zago, M.; Huertas Celdrán, A.; Gil Pérez, M.; Gómez Mármol, F.; García Clemente, F.J. A Dynamic Continuous Authentication Framework in IoT-Enabled Environments. In Proceedings of the Fifth International Conference on Internet of Things: Systems, Management and Security (IoTSMS 2018), Valencia, Spain, 15–18 October 2018. [Google Scholar]
- Boneh, D.; Sahai, A.; Waters, B. Functional encryption: Definitions and challenges. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); LNCS: Berlin, Germany, 2011; Volume 6597, pp. 253–273. [Google Scholar]
- Saxena, N.; Choi, B.J.; Lu, R. Authentication and Authorization Scheme for Various User Roles and Devices in Smart Grid. IEEE Trans. Inf. Forensics Secur. 2016, 11, 907–921. [Google Scholar] [CrossRef]
- Goldstein, J.; Pagan, F.; Short, J. Systems and Methods for Providing Dynamic Network Authorization Authentication and Accounting. Patent EP20000973771, 20 October 2000. [Google Scholar]
- Sforzin, A.; Gómez Mármol, F.; Conti, M.; Bohli, J.M. RPiDS: Raspberry Pi IDS—A Fruitful Intrusion Detection System for IoT. In Proceedings of the 13th IEEE International Conference on Advanced and Trusted Computing (ATC 2016), Toulouse, France, 18–21 July 2016; pp. 440–448. [Google Scholar]
- Useche Peláez, D.; Díaz López, D.; Nespoli, P.; Gómez Mármol, F. TRIS: A Three-Rings IoT Sentinel to protect against cyber-threats. In Proceedings of the Fifth International Conference on Internet of Things: Systems, Management and Security (IoTSMS 2018), Valencia, Spain, 15–18 October 2018. [Google Scholar]
- Hunke, N.; Rüßmann, M.; Schmieg, F.; Bhatia, A.; Kalra, N. Winning in IoT: It’s All about the Business Processes. Available online: https://www.bcg.com/en-co/publications/2017/hardware-software-energy-environment-winning-in-iot-all-about-winning-processes.aspx (accessed on 25 October 2018).
- Lucero, S. IoT Platforms: Enabling the Internet of Things; IHS Technology: Phoenix, AZ, USA, 2016. [Google Scholar]
- Wootton, C. Samsung ARTIK Reference: The Definitive Developers Guide; Apress: New York, NY, USA, 2016; p. 409. [Google Scholar]
- Wootton, C. Beginning Samsung ARTIK—A Guide to Developers; Apress: New York, NY, USA, 2016; p. 396. [Google Scholar]
- Kurniawan, A. Learning AWS IoT: Effectively Manage Connected Devices on the AWS Cloud Using Services Such as AWS Greengrass, AWS Button, Predictive Analytics and Machine Learning; Packt Publishing Ltd.: Birmingham, UK, 2018; p. 278. [Google Scholar]
- Tarneberb, W.; Chandrasekaran, V.; Humpherey, M. Experiences Creating a Framework for Smart Traffic Control using AWS IoT. In Proceedings of the 2016 ACM 9th International Conference on Utility and Cloud Computing, Shanghai, China, 6–9 December 2016; pp. 63–69. [Google Scholar]
- Azraq, A.; Chughtai, S.; Mashhour, A.; V Nguyen, D.; Dos Santos, R.M. Enhancing the IBM Power Systems Platform with IBM Watson Services; IBM Redbooks: New York, NY, USA, 2018; p. 218. [Google Scholar]
- Ravulavaru, A. Enterprise Internet of Things Handbook: Build End-to-End IoT Solutions Using Popular IoT Platforms; Packt Publishing: Birmingham, UK, 2018. [Google Scholar]
- PratimRay, P. A survey of IoT cloud platforms. Future Comput. Inform. J. 2016, 1, 35–46. [Google Scholar]
- Vossen, G.; Schonthaler, F.; Dillon, S. The Web at Graduation and Beyond: Business Impacts and Developments; Springer: New York, NY, USA, 2016. [Google Scholar]
- EVRYTHNG IoT Smart Products Platform. Available online: https://evrythng.com/ (accessed on 12 July 2018).
- Guinard, D.; Trifa, V. Building the Web of Things; Manning Publications Co.: Greenwich, CT, USA, 2016. [Google Scholar]
- Dweet—Data Sharing for IoT. Available online: https://dweet.io/ (accessed on 12 September 2018).
- Freeboard—Dashboards for the Internet of Things. Available online: https://freeboard.io/ (accessed on 1 September 2018).
- Blackstock, M.; Lea, R. Toward a Distributed Data Flow Platform for the Web of Things (Distributed Node-RED). In Proceedings of the 5th International Workshop on Web of Things (WoT ’14), Cambridge, MA, USA, 8 October 2014; pp. 34–39. [Google Scholar]
- Yasumoto, K.; Yamaguchi, H.; Shigeno, H. Survey of Real-Time Processing Technologies of IoT Data Streems. J. Inf. Process. 2016, 24, 195–202. [Google Scholar]
- Kamal, R. Internet of Thinks: Architecture and Design Principles; McGraw Hill Education: New York, NY, USA, 2017. [Google Scholar]
- Kocovic, P.; Behringer, R.; Ramachandran, M.; Mihajlovic, R. Emerging Trends and Applications of the Internet of Things; IGI Global: Hershey, PA, USA, 2017. [Google Scholar]
- Minerauda, J.; Mazhelisb, O.; Suc, X.; Tarkomaa, S. A gap analysis of Internet-of-Things platforms. Comput. Commun. 2016, 89–90, 5–16. [Google Scholar] [CrossRef]
- Mavromoustakis, C.X.; Mastorakis, G.; Dobre, C. Advances in Mobile Cloud Computing and Big Data in the 5G Era; Springer: New York, NY, USA, 2016. [Google Scholar]
- Martino, B.D.; Li, K.C.; Yang, L.T.; Esposito, A. Internet of Everything: Algorithms, Methodologies, Technologies and Perspectives; Springer: New York, NY, USA, 2017. [Google Scholar]
- Geng, H. Internet of Things and Data Analytics Handbook; John Wiley & Sons: New York, NY, USA, 2017. [Google Scholar]
- Spitzer, C.; Ferrell, U.; Ferrell, T. Digital Avionics Handbook, 3rd ed.; CRC Press: Boca Raton, FL, USA, 2017. [Google Scholar]
- Soro, A.; Ambe, A.H.; Brereton, M. Minding the Gap: Reconciling Human and Technical Perspectives on the IoT for Healthy Ageing. Wirel. Commun. Mob. Comput. 2017, 2017, 7439361. [Google Scholar] [CrossRef]
- Cao, T.D.; Hoang, H.H.; Huynh, H.X.; Nguyen, B.M.; Pham, T.V.; Tran-Minh, Q.; Tran, V.T.; Truong, H.L. Iot services for solving critical problems in vietnam: A research landscape and directions. IEEE Internet Comput. 2016, 20, 76–81. [Google Scholar] [CrossRef]
- Thacker, S.; Pant, R.; Hall, J.W. System-of-systems formulation and disruption analysis for multi-scale critical national infrastructures. Reliab. Eng. Syst. Saf. 2017, 167, 30–41. [Google Scholar] [CrossRef]










| Platform | Authentication System | Encrypted Information | Authorization System | Accounting System | Anomaly Detection |
|---|---|---|---|---|---|
| Samsung Artik [36] | Devices IoT to cloud: OAuth2 | Data at move: DTLS, socket | Operations over IoT platform: tokens | Users to the data or the IoT devices: record data timestamp | Change Detection: Anodot |
| Users and the cloud: client credentials | Data at rest: encryption keys | Operations between components of the IoT platform: cloud apps | Components to the data or the IoT devices: N/A | ||
| Cloud components: tokens to execute API calls | |||||
| Amazon IoT [38] | Devices IoT to cloud: device credentials | Data at move: TLS | Operations over IoT platform: polices | Users to the data or IoT devices: CloudWatch, CloudTrail | Change Detection: AWS Lambda |
| Users and the cloud: user credentials | Data at rest: AES-256, digital certificates | Operations between components of the IoT platform: N/A | Components to the data or the IoT devices: N/A | ||
| Cloud components: N/A | |||||
| IBM Watson IoT [40] | Devices IoT to cloud: API keys | Data at move: MQTT and TLS, SSL or IPSec, AES, RSA | Operations over IoT platform: polices, blacklists and white-lists | Users to the data or the IoT devices: logs | Change Detection: Nessus |
| Users and the cloud: ID/password, OAuth tokens and certificates | Data at rest: SSL certificates and proprietary solutions | Operations between components of the IoT platform: spaces for authenticated clients | Components to the data or the IoT devices: logs | ||
| Cloud components: LDAP, IBM web identity | |||||
| Oracle IoT [42] | Devices IoT to cloud: OAuth | Data at move: HTTPS and JSON Web Token, RSA | Operations over IoT platform: roles and policies | Users to the data or the IoT devices: N/A | Change Detection: N/A |
| Users and the cloud: credentials | Data at rest: Trusted Assets Manager, cipher algorithms | Operations between components of the IoT platform: OAuth2 access token | Components to the data or the IoT devices: activity logs | ||
| Cloud components: Certificates, OAuth tokens | |||||
| Evrythng [45] | Devices IoT to cloud: API key | Data at move: TLS and AES | Operations over IoT platform: access, manage and sharing rules | Users to the data or the IoT devices: logs | Change Detection: IDS |
| Users and the cloud: 2FA, TOTP and social media authentication. | Data at rest: key management infrastructure | Operations between components of the IoT platform: manage and sharing rules | Components to the data or the IoT devices: logs | ||
| Cloud components: Public Key Infrastructure | |||||
| Dweet [46] | Devices IoT to cloud: tokens | Data at move: HTTPS and web sockets | Operations over IoT platform: roles | Users to the data or the IoT devices: N/A | Change Detection: SMS or e-mail notification |
| Users and the cloud: ID/password | Data at rest: N/A | Operations between components of the IoT platform: N/A | Components to the data or the IoT devices: N/A | ||
| Cloud components: N/A | |||||
| Node-Red [48] | Devices IoT to cloud: API keys or serials | Data at move: AES-256 | Operations over IoT platform: user permissions | Users to the data or the IoT devices: logs | Change Detection: anomaly detection, Bluemix |
| Users and the cloud: username and password | Data at rest: cryptographic libraries | Operations between components of the IoT platform: username and password | Components to the data or the IoT devices: logs | ||
| Cloud components: basic authentication | |||||
| Nimbits [50] | Devices IoT to cloud: Authentication Header | Data at move: NO | Operations over IoT platform: roles | Users to the data or the IoT devices: Slf4j log schema | Change Detection: detection rules |
| Users and the cloud: email and password, or Google Accounts | Data at rest: cyphering mySQL database | Operations between components of the IoT platform: permission for load balancing | Components to the data or the IoT devices: N/A | ||
| Cloud components: SQL user/password | |||||
| The Thing System [52] | Devices IoT to cloud: UUID | Data at move: HTTPS and Simple Thing Protocol | Operations over IoT platform: roles | Users to the data or the IoT devices: logs | Change Detection: detection rules |
| Users and the cloud: username, password and OTP Cloud components: N/A | Data at rest: N/A | Operations between components of the IoT platform: N/A | Components to the data or the IoT devices: syslog | ||
| Sitewhere [54] | Devices IoT to cloud: hardware ID and tokens. | Data at move: N/A | Operations over IoT platform: granted authorities | Users to the data or IoT devices: tracking user operations | Change Detection: zoneToken |
| Users and the cloud: username and password | Data at rest: N/A | Operations between components of the IoT platform: N/A | Components to the data or the IoT devices: N/A | ||
| Cloud components: N/A |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Díaz López, D.; Blanco Uribe, M.; Santiago Cely, C.; Tarquino Murgueitio, D.; Garcia Garcia, E.; Nespoli, P.; Gómez Mármol, F. Developing Secure IoT Services: A Security-Oriented Review of IoT Platforms. Symmetry 2018, 10, 669. https://doi.org/10.3390/sym10120669
Díaz López D, Blanco Uribe M, Santiago Cely C, Tarquino Murgueitio D, Garcia Garcia E, Nespoli P, Gómez Mármol F. Developing Secure IoT Services: A Security-Oriented Review of IoT Platforms. Symmetry. 2018; 10(12):669. https://doi.org/10.3390/sym10120669
Chicago/Turabian StyleDíaz López, Daniel, María Blanco Uribe, Claudia Santiago Cely, Daniel Tarquino Murgueitio, Edwin Garcia Garcia, Pantaleone Nespoli, and Félix Gómez Mármol. 2018. "Developing Secure IoT Services: A Security-Oriented Review of IoT Platforms" Symmetry 10, no. 12: 669. https://doi.org/10.3390/sym10120669
APA StyleDíaz López, D., Blanco Uribe, M., Santiago Cely, C., Tarquino Murgueitio, D., Garcia Garcia, E., Nespoli, P., & Gómez Mármol, F. (2018). Developing Secure IoT Services: A Security-Oriented Review of IoT Platforms. Symmetry, 10(12), 669. https://doi.org/10.3390/sym10120669






