Abstract
With the rapid popularization of the Internet of Things (IoT) in our daily lives, the communication security and identity privacy of IoT devices must be ensured. However, traditional authentication mechanisms utilized in IoT cannot completely ensure a user’s privacy when his/her messages are routed via an untrusted intermediate device. Strong designated-verifier proxy re-signature (SDVPRS) is a new cryptographic technology that combines the advantages of strong designated verifier signature and proxy re-signature. Therefore, SDVPRS is considered to be a better approach to maintain data integrity and protect the identity privacy of the signer in a resource-limited IoT device. Nevertheless, designing a secure SDVPRS scheme without random oracles is still a challenging task. In this paper, we mainly focus on such a construction by providing a new method. We first provide the formal definition of SDVPRS and its security model. Then, we present the first SDVPRS scheme, which is bidirectional, multi-use and non-transferable, and we prove its security under the standard complexity assumptions in the standard model. The analysis results show that our SDVPRS scheme can not only protect the privacy of the signer’s identity, but also provide non-delegatability for signature verification. We present an example of potential application to environmental monitoring systems using our SDVPRS scheme.
1. Introduction
The Internet of Things (IoT) is rapidly entering all aspects of our daily lives. IoT uses sensors, radio frequency identification (RFID), wireless data communications and other technologies to construct a network that covers all things in the world to make the interactions between people and things and between things and things more intelligent and convenient [1]. IoT devices equipped with sensors have the ability to sense and process information, and they are used to collect, transmit and disseminate data from the field to a server or other IoT devices. IoT has been deployed in many environments, such as smart transportation, smart cities, environmental surveillance, smart homes, military target tracking, biomedical health monitoring and industrial automation [2].
IoT is everywhere in our daily lives and offers great benefits for human life. However, IoT data are transmitted over public networks, and ensuring a user’s privacy and data security is of particular importance [3]. In an IoT environment, most IoT devices have limitations in terms of energy capacity, storage capacity and computing power. Therefore, conventional cryptosystems cannot be implemented in resource-constrained IoT devices. Digital signature technology guarantees the integrity of the data during transmission and also authenticates the identity of the sender. Based on various digital signature techniques, such as identity-based signature and certificateless signature, researchers have proposed several schemes [2,3,4,5,6] to ensure the integrity and authenticity of IoT data transmitted over public channels. However, anyone can use the signer’s public key to verify the validity of the signature, so these schemes [2,3,4,5,6] reveal some private information of the signer (such as the identity of the signer). Strong designated verifier proxy re-signature (SDVPRS) can provide a better solution to solve these problems. Due to the combination of the features of strong designated verifier signature (SDVS) and proxy re-signature (PRS), SDVPRS not only maintains the integrity of IoT data during transmission, but also protects the identity privacy of the IoT device that signs IoT data. In an SDVPRS scheme, only the designated verifier can verify the validity of a signature. Specifically, SDVPRS allows a signer to designate a verifier, and a semi-trusted proxy is allowed to convert the signer or the designated verifier into a signature. However, how to design an SDVPRS scheme without random oracles is still challenging. Hence, we focus on constructing an SDVPRS scheme in the standard model that can be applied to IoT devices.
PRS, which allows a proxy to transform the signature of a message generated by Alice into Bob’s signature of the same message, is an important cryptosystem in cryptography [7]. However, the proxy by itself is unable to create arbitrary signatures on behalf of Alice or Bob. If the proxy can not only convert Alice’s signature into Bob’s signature, but also convert Bob’s signature into Alice’s signature, then we say that a PRS scheme is bidirectional. Additionally, if the transformed signatures can be further transformed by the proxy, then we say that a PRS scheme is multi-use. Since PRS can convert signatures, it has been applied to key management, cross-domain identity authentication and other fields [7,8,9].
To designate a verifier to verify the validity of a signature, the designated verifier signature (DVS) was presented by Jakobsson et al. [10]. A DVS scheme ensures that only the designated verifier can verify signatures generated by the signer. However, the designated verifier is able to produce simulated signatures that are computationally indistinguishable from the real signatures on the same messages created by the signer. Consequently, a DVS scheme provides the authentication of signatures, but it does not satisfy the non-repudiation of ordinary signatures since only the designated verifier is able to ensure that signatures are generated by a real signer. Specifically, in a DVS scheme, both the signer and the designated verifier can generate a valid signature of the message. To avoid man-in-the-middle attacks, Jakobsson et al. [10] further proposed the concept of the strong designated verifier signature (SDVS), which requires the secret key of the designated verifier during signature verification. Since the attacker does not know the verifier’s secrete key, the validity of the intercepted signature cannot be verified. SDVS has stronger security and many special applications such as voting and deniable authentication [11,12,13].
Based on the concepts of PRS and DVS, designated verifier proxy re-signature (DVPRS) was introduced by Wei et al. [14]. In a DVPRS scheme, a semi-trusted proxy can change the signer or the verifier in a DVS. Consequently, DVPRS has the properties of both PRS and DVS. DVPRS is a useful technique in deniable or anonymous authentication, and it can be applied to fields such as wireless communication networks [15,16,17].
To enhance the privacy of the signer’s identity, we introduce the concept of SDVPRS in this paper, which is a variant of DVPRS. In SDVPRS, the designated verifier’s secret key is required in the signature verification; thus, the validity of the signature can only be checked by the signer or the designated verifier. This approach ensures that an adversary who captures a signature only knows that either the signer or the designated verifier created the signature, but the adversary cannot infer which one of them is the real signature generator. No third party other than the designated verifier knows the true identity of the signer; thus, SDVPRS can protect the privacy of the signer’s identity. Because SDVPRS combines the advantages of SDVS and PRS, most of the significant security requirements, such as integrity, unforgeability and non-transferability, and the signer’s identity privacy protection can be guaranteed in a single logic step.
The security concepts of DVPRS were presented by Wei et al. [14], but the formal definition of SDVPRS was not taken into account in [14]. In addition, Wei et al. [14] designed a DVPRS scheme in the random oracle model, which is also the only publicly available DVPRS scheme. Unfortunately, the random oracle model might not ensure the security of the scheme if the random oracles are instantiated with concrete hash functions [18]. In fact, Wei et al.’s proposal [14] is an SDVPRS scheme since the verification of the signature requires the designated verifier’s secret key. Therefore, constructing a secure (S)DVPRS scheme without random oracles in the standard model is an unsolved problem.
1.1. Our Contributions
In this paper, we first present the security concepts of SDVPRS. In contrast to PRS, our formal definition for SDVPRS relies on the security concepts of SDVS. Based on Waters’ technique [19], we then present a construction of an SDVPRS scheme without random oracles, which is proven to be existentially unforgeable in the standard model. Our SDVPRS scheme is bidirectional, multi-use, transparent and non-transferable. Furthermore, the security proof shows that our SDVPRS scheme can ensure the integrity and authenticity of IoT data, as well as protect the identity privacy of the IoT device. To the best of our knowledge, our proposal is the first (strong) designated verifier PRS scheme without random oracles. Our SDVPRS scheme is very useful for protecting the security of IoT data and the identity privacy of the sender.
1.2. Related Work
With the substantial development of cloud computing and IoT techniques, data privacy [20,21,22,23], access control [24,25] and message authentication [26,27,28] have become important issues and the focus of many studies. According to the diverse requirements of the authentication, various signature schemes, such as homomorphic signature schemes [29,30] and proxy signature schemes [31,32,33], have been proposed. However, most of the existing message authentication schemes do not consider the privacy of IoT devices. SDVPRS is a new cryptographic technology that has the advantages of PRS and SDVS, so we introduce SDVPRS to solve the sender’s identity privacy problem in IoT environments.
The concept of PRS was presented by Blaze et al. [7] in 1998, and the security definition of PRS was formalized by Ateniese and Hohenberge [34] in 2005. Since then, researchers have designed a large number of PRS schemes with special properties. Hu et al. [35] proposed a secure identity-based proxy re-signature scheme under the standard model, but its security relies on strong difficult problem assumptions. Tian [36] designed an identity-based proxy re-signature scheme over lattices, but the size of the signature and secret key was relatively large. Wang and Xia [37] presented an identity-based proxy re-signature scheme with the aggregate property. However, their scheme required numerous system parameters. To reduce the security risks of an individual proxy, Yang et al. [38] introduced the concept of threshold proxy re-signature, which can distribute the re-signature key to multiple proxies for management. Yang et al. [39] introduced the concept of flexible threshold proxy re-signature, which can flexibly select different thresholds according to the importance of the message to be re-signed. To improve the response time of re-signing, Yang et al. [40] proposed an on-line/off-line threshold proxy re-signature scheme, which completes most of the computational tasks of re-signing in the off-line phase. To solve the key escrow problem in identity-based proxy re-signature, some certificateless proxy re-signature schemes [41,42] have been proposed. Unfortunately, these schemes have some security flaws [43].
The first DVS scheme was presented by Jakobsson et al. [10] in 1996. Saeednia et al. [44] gave the formal definition of SDVS. Later, some SDVS schemes were presented in [45,46,47]. Hung et al. [48] designed a secure SDVS scheme in the standard model, but its security depended on the security of pseudo-random functions. Hence, their scheme has potential security risks. Based on the standard complexity assumptions, Tian et al. [49] designed two SDVS schemes without random oracles. The researchers also proposed some variants of DVS such as universal DVS [50,51] and multi-verifier DVS [52,53]. Until now, the only DVPRS scheme was that proposed by Wei et al. [14], but its security was dependent on ideal random oracles.
Data security has become an important issue in IoT. When IoT data are transmitted through open and insecure channels, they are vulnerable to various attacks, such as forgery attack, tamper attack, and so on. To ensure the communication security of IoT devices, Jia et al. [3] proposed a data authentication scheme based on a certificateless signature. Combining aggregate signature and identity-based signature, Shen et al. [2] designed a data integrity protection scheme for wireless sensor networks. Kumar et al. [4] proposed a secure data transmission scheme for a healthcare wireless sensor network using certificateless aggregation signature technology. Yeh et al. [6] proposed an efficient certificateless signature scheme to ensure the security of IoT devices. However, these schemes [2,3,4,5,6] were proven to be secure in the random oracle model, which means that these schemes might be insecure in reality. In particular, these existing schemes protect the integrity of IoT data, but at the same time, they disclose the identity privacy of IoT devices. Motivated by this scenario, we construct an SDVPRS scheme in the standard model to protect the integrity of IoT data and the privacy of the sender’s identity. The proxy converts the IoT device’s signature to a group’s signature on the same data, thereby reducing the risk of identifying the identity of the IoT device according to the signature and realizing the anonymity of data transmission. In addition to the designated verifier, no one can verify the legality of the final signature. That is, our scheme enables the integrity and authenticity of IoT data to be verified without revealing the user’s identity privacy.
2. Preliminaries
2.1. Bilinear Pairing
Assume that p is a large prime, and are two multiplicative cyclic groups of order p and g is an arbitrary generator of . A map is called a bilinear pairing if it satisfies the following conditions.
- Bilinearity: = , where .
- Non-degeneracy: , where is the identity element of .
- Computability: is efficiently computable, where .
2.2. Complexity Assumptions
Polynomial-time algorithms are unable to solve the following hard problems [34,54], which are considered to be intractable in complexity theory.
Definition 1.
Given four elements , where unknown values a, b and c are randomly selected from , the bilinear Diffie–Hellman (BDH) problem in is to calculate .
Definition 2.
Given and where unknown values a, b and c are randomly selected from , the decisional bilinear Diffie–Hellman (DBDH) problem in is to determine whether holds.
Taking as input and , the DBDH oracle outputs one if ; else, it outputs zero.
Definition 3.
Given where unknown values a, b and c are randomly selected from , the gap bilinear Diffie–Hellman (GBDH) problem in is to use the oracle to calculate .
The main difference between the BDH problem and the GBDH problem is whether the DBDH oracle is required to solve the corresponding problem.
3. Security Model and System Framework
3.1. The Syntax of SDVPRS
An SDVPRS scheme includes the following nine algorithms:
- : This algorithm takes a security parameter as input and produces system parameters .
- : Upon input of , this algorithm outputs a secret key and a corresponding public key .
- : Upon input of , a signer’s key pair and another signer’s key pair , this algorithm generates a re-signing key for the proxy.
- : Upon input of and two verifiers’ key pairs and , this algorithm generates a re-designate-verifier key .
- : This algorithm takes , a signer’s secret key , a message m and a designated verifier’s public key as input. It outputs a signature on m.
- : This algorithm takes , a re-signing key between a signer and another signer and a signature on a message m under the signer and a verifier as input. It generates a re-signature on m under and .
- : This algorithm takes , a re-designate-verifier key between a verifier and another verifier and a signature on a message m under a signer and the verifier as input. It generates a re-signature on m under and .
- : This algorithm takes , a signer’s public key , a designated verifier’s secret key and a signature on a message m as input. It outputs one if is a valid signature; otherwise, it outputs zero.
- : This algorithm takes , a signer’s public key , a designated verifier’s secret key and a message m as input. It generates a simulated signature that is indistinguishable from the one created by the signer.
3.2. Security Model of SDVPRS
An SDVPRS scheme consists of three entities: the signer, the proxy and the designated verifier. The security model of SDVPRS mainly considers the following four security concepts. Among them, two properties, unforgeability and non-delegatability for signature verification, ensure the integrity and authenticity of the IoT data in the communication process, and the other two properties, non-transferability and privacy of the signer’s identity (PSI), prevent any third party from obtaining the identity information of the IoT device from a signature. Similar to the security model of a bidirectional PRS scheme [34], the security model of a bidirectional SDVPRS scheme also requires that the proxy is semi-trusted and is not allowed to collude with the signer or the designated verifier.
Unforgeability means that a legal signature can only be generated by the signer or the designated verifier. We define a game between a challenger and an adversary to describe the unforgeability of an SDVPRS scheme.
- : executes the algorithms and to generate system parameters , the key pair , of the target signer and the key pair of the target verifier. Then, sends and the public keys of other users to .
- : may adaptively request the following oracles built by .
- -
- : Upon input of message , this oracle outputs a signature = on .
- -
- : Upon input of two signers’ public keys and , this oracle outputs a re-signing key = , where and are the secret keys corresponding to and , respectively.
- -
- : Upon input of two verifiers’ public keys and , this oracle outputs a re-designate-verifier key = , .
- -
- : Upon input of a message , this oracle returns a simulated signature = on .
- -
- : This oracle takes a message and a signature as input, and it outputs a decision = , , where .
- : Eventually, produces a forgery . The adversary wins if the following conditions are satisfied.
- = 1, which means that is a valid signature on .
- has never been submitted to and .
Definition 4.
If there is no polynomial-time attacker who can win in the above game with a non-negligible probability, then we say that a bidirectional SDVPRS scheme is existentially unforgeable against adaptive chosen-message attacks.
The property of non-transferability means that any third party cannot distinguish whether the real generator of a signature is the signer or the designated verifier.
Definition 5.
If the signature created by the signer and the signature simulated by the designated verifier are computationally indistinguishable, then we say that an SDVPRS scheme is non-transferable [14].
PSI ensures that no one other than the designated verifier can infer the signer’s true identity from a signature. Specifically, two signers and produce signatures for a designated verifier V. Given a signature on a message m, anyone without V’s secret key is unable to determine whether is created by or . We provide a game between a distinguisher and a challenger to describe the formal definition of PSI.
- : performs the algorithms and to generate system parameters , ’s key pair , ’s key pair and V’s key pair . Then, sends , to .
- : may adaptively issue the following oracle queries.
- -
- : Upon receiving , a message and an index , this oracle returns a signature = of .
- -
- : Upon receiving , a message and an index , this oracle returns a simulated signature = on .
- -
- : Taking , an index and a signature on a message m as input, this oracle outputs a decision = , where .
- -
- : Upon input of , a message , an index , a signature on and an index , this oracle outputs a re-signature = , on .
- : Upon receiving a challenge message submitted by , first selects a random bit and runs the algorithm to generate a signature = . Then, returns to .
- : continues to query , and defined in Phase 1, but is not allowed to submit to .
- : finally outputs a guess . The distinguisher wins the game if .
The advantage of in the game is defined as follows:
Definition 6.
If the advantage of any polynomial-time distinguisher is negligible in the above game, then we say that an SDVPRS scheme possesses the PSI property.
Non-delegatability for signature verification requires that the legality of a signature can only be correctly verified by those who know the secret key of the designated verifier. We use a game between a challenger and an adversary to define non-delegatability for signature verification.
- : executes the algorithms and to generate system parameters , the key pair of the target signer and the key pair of the target verifier. Then, sends to .
- : answers ’s signing query and simulation query in the same manner as in the formal definition of existential unforgeability in Definition 5.
- : finally produces a forgery . If the following conditions are satisfied, then we say that wins the game.
- is a valid signature on , namely , = 1.
- has never made a signature query and a simulated query on .
Definition 7.
An SDVPRS scheme is said to be non-delegatable for signature verification if there is no polynomial-time attacker who can win the above game with a non-negligible probability.
3.3. System Framework
Our system model is shown in Figure 1, which contains three entities: IoT device, proxy and data center. It focuses on the integrity and authenticity of IoT data during transmission while protecting the identity privacy of the IoT device. The proposed SDVPRS scheme is easily implemented on each IoT device as software. Our system model focuses on the integrity and authenticity of IoT data.
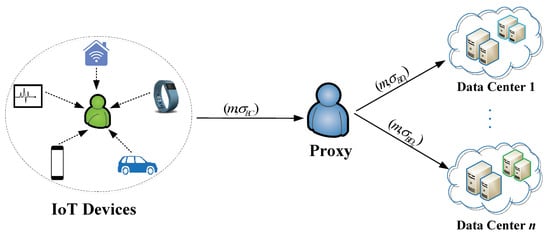
Figure 1.
System framework for IoT data authenticity.
- IoT device: This entity has very limited computing and communication capabilities. Each IoT device uses its secret key to sign the data collected from the physical world and then sends the data and its signature to the proxy.
- Proxy: This entity is usually served by a semi-trusted server with a certain computation and communication power. To ensure the security of data storage, IoT data are stored by multiple data centers for consumers of different security levels. The proxy uses the re-signing key to convert the signature generated by the IoT device into a group’s signature for the same message m, so that the data center only knows that is a valid signature on m, but cannot infer the identity of the real signer. After receiving , another proxy uses the re-designate-verifier key to convert the signature into the signature for every data center, and it sends the IoT data m and to the i-th data center, where .
- Data center: This entity has high computing and storage capacities. After verifying the validity of the received signature, the authentic IoT data are stored by each data center.
4. Our SDVPRS Scheme
In this section, we present a construction of an SDVPRS scheme based on Waters’ scheme [19]. In our proposed SDVPRS scheme, the length of a message is assumed to be n bits. For a message of arbitrary length, we use a hash function to convert the length of the message to fixed length n. Our SDVPRS scheme works as follows.
- : This algorithm takes a security parameter as input and produces system parameters = , where and are two cyclic groups of prime order p, g is a generator of , is a bilinear pairing and elements are randomly chosen from .
- : The signer S randomly selects , computes and and sets its secret key and the public key , . Similarly, the designated verifier V randomly selects , computes and outputs its public/secret key pair .
- : The proxy randomly selects and sends to the signer . After receiving , uses his/her secret key to compute and forwards to the signer . Then, uses his/her secret key to calculate and send to the proxy. Finally, the proxy computes the re-signing key between and :
- : To generate a re-designate-verifier key between two verifiers and , the proxy does the following:
- The proxy randomly selects and returns to the verifier .
- uses his/her secret key to compute and sends to the verifier .
- uses his/her secret key to compute . Then, returns to the proxy.
- After receiving , the proxy calculates the re-designate-verifier key as follows:
Note that and can be kept by different proxies to perform different operations, and they can also be assigned to a proxy to perform all operations. In and , a cryptographic algorithm (such as RSA or ECC) may be used to encrypt the transmitted messages to prevent the proxy from obtaining each participant’s secret key through intercepted messages in practical applications. - : Given a message and a designated verifier V’s public key , the signer S performs the following steps:
- Choose a random integer , and calculate .
- Calculate , where is the secret key of the signer S.
- Output as a signature on m.
- : For a signature on a message m with respect to a signer and a verifier , the proxy uses a re-signing key between two signers and to compute a new signature on m related to the signer and the verifier as follows:
- : Given a re-designate-verifier key between two verifiers and , a message m and a signature of m for a signer and a verifier , the proxy computes a new signature on m for and as follows:
- : Upon receiving the public key of a signer S, a message m and a corresponding signature , the designated verifier V utilizes its own secret key to check whether:holds. If it holds, output one; else, output zero.
- : For a message m and the public key of a signer S, the designated verifier V with a secret key randomly selects , computes and:then generates as a simulated signature on m with respect to S and V.
Correctness: Assume that is a signature on a message m for and , is a re-signing key between and and is a signature on m that is derived from and .
Let ; we have:
Then, we can obtain:
Similarly, we are able to check the correctness of the signature for and . Hence, we can conclude that our SDVPRS scheme is correct.
Remark 1.
For a re-signing key between and , it is easy to obtain another key between and that converts ’s signatures into ’s signatures. From a re-designate-verifier key between and , we can also obtain another key that transforms the identity of the verifier in a signature from to . Hence, our SDVPRS scheme is bidirectional.
Remark 2.
As and = , it is easy to infer that signatures created by the algorithm are computationally indistinguishable from signatures generated by the and algorithms. This shows that the proposed SDVPRS scheme possesses the multi-use property.
Remark 3.
If is a signature created by the signer S for the message m, then the designated verifier V can also output a valid signature on the same message m. Consequently, the distribution of σ is the same as that of . This result implies that signatures generated by the algorithm are indistinguishable from those simulated by the algorithm. Therefore, our SDVPRS scheme is non-transferable.
Theorem 1.
If the GBDH problem is intractable, then our proposed SDVPRS scheme is existentially unforgeable against adaptively chosen message attacks in the standard model.
Proof of Theorem 1.
Let be an attacker against the unforgeability of the proposed scheme with probability ε. is allowed to make at most signing queries, signature verification queries, simulation queries, re-signing key queries and re-designate-verifier key queries. We can build an algorithm that utilizes ’s output to solve the GBDH problem. Given an instance of the GBDH problem, ’s goal is to calculate by invoking the oracle . will act as a challenger to answer the following queries requested by .
- : sets such that . Then, chooses a random integer , random values and random elements . Furthermore, assigns and for . In addition, randomly selects and sets the public key of the signer i to be and the public key of the verifier j as for and . The public key of the target signer is set to , and the public key of the target designated verifier’s public key is set to . This implicitly indicates that is the target signer’s secret key and is the target designated verifier’s secret key, but and c are unknown to . Finally, sends , and the public keys of other users to .Given any n-bit message , we define two functions to simplify the expression: and . Consequently, we have
- : builds the following oracles to answer ’s queries.
- -
- : Upon receiving a message m, checks whether holds. If it does hold, then aborts. Otherwise, randomly selects , computes and and then returns a signature on m to .Correctness: For a signature produced by , we have:and , where .Then, we deduce that satisfies the following signature verification equation:This equation shows that the signature σ is valid. Moreover, it indicates that the signature computed by and the signature created by the signer in the real scheme are computationally indistinguishable from the adversary ’s view.
- -
- : Upon receiving two signers’ public keys and , computes and returns a re-signing key to .
- -
- : Upon input of two verifiers’ public keys and , computes and returns a corresponding re-designate-verifier key to .
- -
- : This oracle is the same as .
- -
- : Upon receiving a message m and a signature , responds by performing the following steps:
- (1)
- If , then creates another signature of m just as responds to the signing queries in the oracle . Subsequently, submits to the oracle . If outputs one, then sends one to ; otherwise, sends zero to .Correctness: If is a valid signature for message m, then σ must satisfy the following signature verification equation:Another valid signature calculated by must also satisfy the following verification equation:Thus, we can obtain:The above equation demonstrates that , , is a correct BDH tuple.
- (2)
- If , makes a query to the oracle with input , . If returns one, then sends one to ; else, sends zero to .Correctness: Assuming that is a valid signature, the following equation holds:Hence, we can obtain:This shows that is a valid BDH tuple.
- : produces a message/signature pair , , where has never been submitted to and . If , then terminates the simulation. Otherwise, can successfully obtain a solution for the given CDHinstance by calculating:
We now analyze the probability that can successfully solve the GBDH instance. If completes the entire simulation without aborting, then the following events must occur.
- : All signature, simulation and verification queries on any message satisfy .
- : .
As and random elements , implies that . In contrast, implies that . The probability of completing the entire simulation is . Since and , we have:
Since two events and are independent, we have:
Furthermore, we conclude that:
The probability of successfully solving the GBDH problem is at least . ☐
Theorem 2.
If the DBDH problem is intractable, then our SDVPRS scheme possesses the PSI property.
Proof of Theorem 2.
Let be a polynomial-time distinguisher against the PSI property in the proposed SDVPRS scheme. We can construct another algorithm that invokes to solve the DBDH problem. Upon receiving a DBDH instance , where and , the task of is to determine whether holds.
- : selects , at random and sets and . Then, assigns the signer ’s public key , the signer ’s public key and the public key of the designated verifier V. sets the common secret key between and V as . Additionally, sets the common secret key between and V as . Finally, sends , to .Given any n-bit message , we define a function . Thus, we have:
- : adaptively issues queries to the following oracles.
- -
- : Upon receiving an index and a message m, selects at random and uses the common secret key to compute:and . Then, sends a signature of m to .
- -
- : This oracle is the same as .
- -
- : When issues a verification query on a signature of a message m and an index , computes and uses to check whether the following equation is true:If this equation holds, then sends one to ; else, sends zero to .Correctness: For a signature associated with the signer and the verifier V, we have:This shows that can correctly verify the legality of the signature submitted by .
- -
- : Upon input of a message , an index , a signature on and an index , first performs a verification query with input to obtain a corresponding decision . If , then returns ⊥; otherwise, obtains a signature related to and V by querying the oracle with input . Then, sends to as a re-signature on .
- : After receiving a challenge message submitted by , first randomly selects a bit and queries the oracle on input to obtain a corresponding signature of . Then, sends to .Note that if , then ; otherwise, is a random element in .
- : handles the subsequent queries submitted by as in Phase 1, and is not allowed to query with input , where .
- : eventually produces a guess . outputs one if and zero otherwise.
If can correctly guess such that , then we have:
Therefore, can successfully solve a DBDH instance with at least probability. ☐
Theorem 3.
If the BDH problem is intractable, then our SDVPRS scheme is non-delegatable for signature verification.
Proof of Theorem 3.
Let be a polynomial-time attacker against the property of non-delegatability for signature verification. Given a BDH tuple , we can construct another algorithm that utilizes ’s forgery to calculate .
- : sets system parameters , the signer’s public key and the designated verifier’s public key in the same way as in the proof of Theorem 1.
- : answers ’s signing and simulation queries in the same manner as in the proof of Theorem 1.
- : Eventually, produces a message/signature pair . If , then terminates the simulation. Otherwise, evaluates and outputs the BDH value:
The probabilistic analysis of successfully solving the BDH problem is similar to the probability analysis of Theorem 1. ☐
5. Performance Evaluation
This section discusses the performance comparison between our SDVPRS scheme and Wei et al.’s [14] DVPRS scheme with respect to the security model, the size of the secret key, the signature length and the computational overhead. The corresponding comparison results are shown in Table 1 and Table 2. We use the PBClibrary to evaluate the time cost of cryptographic operations. We select the curve a.param of Type A in the PBC-0.47-VC library to perform bilinear pairing, and p is a 512-bit prime. The simulated environment is set up on a laptop with the Windows 10 operating system, with an Intel(R) Core(TM) i7-6500 CPU @2.59 GHz and 8 GB of RAM. Since the computational overhead of other cryptographic operations is relatively small, we mainly consider time-consuming exponentiation and bilinear pairing. To simplify the description, let E denote an exponentiation computation that takes 7.46 ms. P represents a bilinear pairing operation, which takes 14.13 ms. represents the length of an element in , which is 20 bits. represents the length of an element in , which is 128 bits. In Table 1, KeySize and SigSize are used to represent the size of a secret key and a signature, respectively.

Table 1.
Comparison of communication overhead. SigSize, signature size; SDVPRS, strong designated-verifier proxy re-signature.

Table 2.
Comparison of computational overhead.
Table 1 presents the comparisons of the communication overhead based on the size of the secret key and signature. In both our SDVPRS scheme and Wei et al.’s scheme [14], the size of the secret key is (40 bits). In our SDVPRS scheme, the length of a signature is (256 bits). The length of a signature in Wei et al.’s scheme [14] is (128 bits), but this scheme has been proven to be secure in the random oracle model.
Table 2 presents the comparisons between our SDVPRS scheme and Wei et al.’s DVPRS scheme [14] in terms of the computational overheads of the , , and algorithms. It should be noted that and can be pre-computed in our scheme. To generate a signature, our scheme needs two exponentiations and one bilinear pairing operation (29.05 ms), while Wei et al.’s scheme [14] needs one exponentiation and one bilinear pairing operation (21.59 ms). As for the computation cost of signature conversion, our scheme requires two exponentiations (14.92 ms), while Wei et al.’s scheme [14] requires one exponentiation (7.46 ms). For the signature verification process, our scheme needs one exponentiation and one bilinear pairing operation (21.59 ms), while Wei et al.’s scheme [14] requires one exponentiation and two bilinear pairing operations (35.72 ms).
From the above analysis, we have observed that our scheme is comparable in computational performance to that of Wei et al.’s scheme [14]. However, our SDVPRS scheme provides higher security because the security of our scheme does not depend on ideal random oracles.
6. Application for Environmental Monitoring System
We describe an environmental monitoring data transmission system using our proposed SDVPRS scheme. This system, as shown in Figure 2, consists of three entities: IoT device, a server node and a set of n data centers that store IoT data.
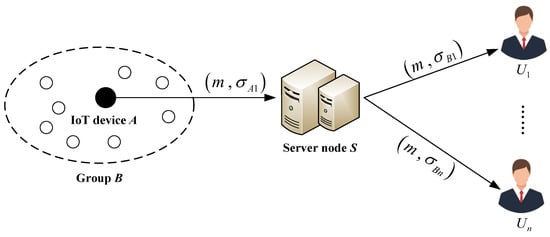
Figure 2.
Environmental monitoring data transmission based on IoT.
The IoT device A belonging to a group B is mainly responsible for collecting environmental data and generating signatures of these data. Each data center has powerful computing and storage capabilities to store or analyze environmental data sent by IoT devices. For example, data centers receiving environmental data are usually government agencies, universities, research institutes or various types of environmental companies. The server node S acts as a proxy with a certain computing power and communication capabilities. It can convert the signature of IoT device A into the signature of group B, where the IoT device is located, and send the environmental monitoring data and corresponding signature anonymously to a subset of some designated data centers (denoted by ). The system consists of four phases: system setup, data acquisition, data transmission and data storage. The environmental monitoring data transmission system is described as follows.
- System setup:The system parameters = are generated by the algorithm in Section 4. Each entity in the system generates its public/secret key pair by running the algorithm in Section 4.
- The IoT device A sets its secret key and public key , . Similarly, the group B in which the IoT device A is located sets the secret key and public key , .
- Each data center sets its public/secret key pair , .
- Data acquisition:The IoT device A that assembles the sensor(s) collects environmental monitoring data (e.g., atmosphere, water, soil, plants, etc.). Then, A randomly selects and calculates and , where is the public key of the data center . Finally, A sends m and the corresponding signature to the server node S.
- Data transmission:After receiving the message m and signature sent by A, the server node S performs the following steps.
- S calculates the signature using the re-signature key . That is, the server node S converts the signature of the IoT device into the signature on m of the group B.
- S uses the re-designate-verifier key to convert the signature to , where and for .
- S sends m and the corresponding signature to the designated data center , .
- Data storage:After receiving the environmental monitoring data and the corresponding signature , each data center uses its own private key and the public key of group B to check whether the following equation holds:If the above equation does not hold, it means that m is not authentic environmental monitoring data, and aborts and stops. Otherwise, m is securely stored by the data center so that other authorized users can access and analyze the collected environmental data.
In the above system, only the data center can verify the validity of the signature on the environmental monitoring data m. The server node S converts the signature of the IoT device A into the signature of the group B, so that each data center cannot infer the true identity of the IoT device from the received signature. Therefore, our system can verify the authenticity and integrity of environmental monitoring data, while protecting the identity privacy of IoT devices.
Here, we experimentally evaluate the performance of the proposed system. The experimental environment is the same as the simulation environment in Section 5. In the data acquisition phase, the following values can be precomputed:
For environmental monitoring data , IoT device A generates a signature on m as:
where is the public key of data center . Figure 3 shows that when the length of the data is 100 bits, 300 bits, 500 bits, 700 bits and 900 bits, the time overhead of the IoT device is up to 20 ms, 27 ms, 35 ms, 42 ms and 50 ms, respectively.
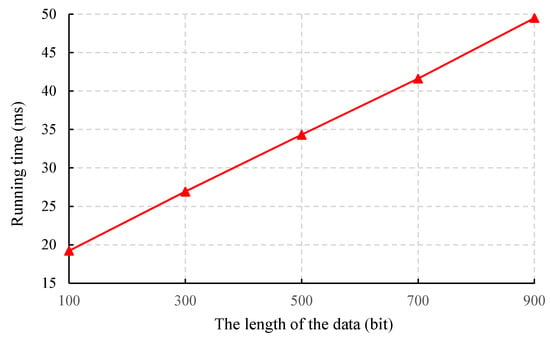
Figure 3.
Time cost of the IoT device.
In the data transmission phase, the server node needs two exponentiations to convert the signature of the IoT device into the signature of its group. In addition, the server node needs two exponentiations to change the data center in to the data center . Figure 4 shows that when the total number of data centers is 2, 4, 6, 8 and 10, the computational overhead required by the server node is approximately 29 ms, 60 ms, 92 ms, 125 ms and 156 ms, respectively.
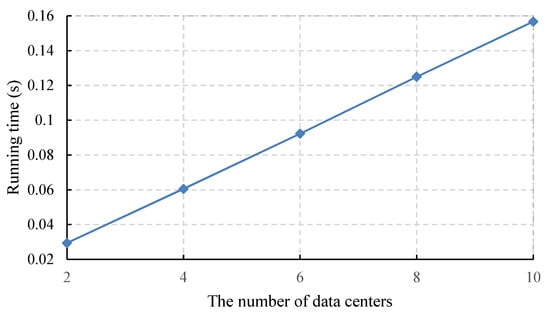
Figure 4.
Time cost of the server node.
For the data storage phase, the signature verification equation of the data is:
where can be pre-computed. When the length of the data is 100 bits, 300 bits, 500 bits, 700 bits and 900 bits, the time overhead required for each data center is as shown in Figure 5. Because the server nodes and data centers have strong computing power, our proposal has practical application.
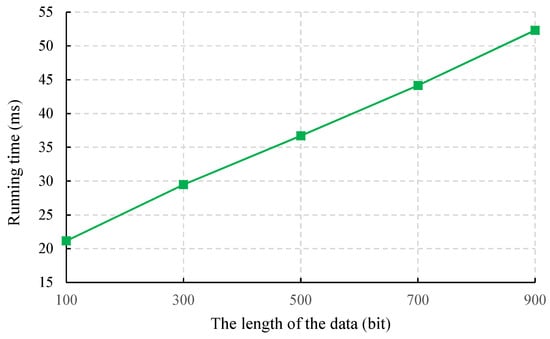
Figure 5.
Time cost for verifying signature validity in each data center.
7. Conclusions
Data authenticity and identity privacy are still critical issues for IoT devices. To secure IoT devices, a new SDVPRS technique applied to the IoT environment is presented in this paper. First, we present the security concepts of SDVPRS, and then, we propose the first construction of an SDVPRS scheme without random oracles. Furthermore, we prove that the proposed scheme is secure in the standard model based on the BDH, GBDH and DBDH problems. The security proofs demonstrate that our SDVPRS scheme can protect the identity privacy of IoT devices while ensuring the authenticity and integrity of IoT data. Our SDVPRS scheme is very useful for IoT-based data transmission systems.
Author Contributions
For the research paper, X.-D.Y. and L.-K.X. proposed and designed the SDVPRS scheme. C.-L.C. presented the background about SDVPRS. C.-F.W. did the performance analysis. The four authors cooperatively proved the security of the proposed scheme.
Funding
This research was funded by the National Natural Science Foundation of China Grant Numbers 61662069, 61672020 and 61472433; the China Postdoctoral Science Foundation Grant Number 2017M610817; the Science and Technology Project of Lanzhou City of China Grant Number 2013-4-22; and the Foundation for Excellent Young Teachers by Northwest Normal University Grant Number NWNU-LKQN-14-7.
Acknowledgments
The authors would like to appreciate the anonymous referees for their valuable comments and constructive suggestions.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A survey on security and privacy issues in internet-of-things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Shen, L.; Ma, J.; Liu, X.; Wei, F.; Miao, M. A secure and efficient id-based aggregate signature scheme for wireless sensor networks. IEEE Internet Things J. 2017, 4, 546–554. [Google Scholar] [CrossRef]
- Jia, X.; He, D.; Liu, Q.; Choo, K.K.R. An efficient provably-secure certificateless signature scheme for Internet-of-Things deployment. Ad Hoc Netw. 2018, 71, 78–87. [Google Scholar] [CrossRef]
- Kumar, P.; Kumari, S.; Sharma, V.; Sangaiah, A.K.; Wei, J.; Li, X. A certificateless aggregate signature scheme for healthcare wireless sensor network. Sustain. Comput. Inform. Syst. 2018, 18, 80–89. [Google Scholar] [CrossRef]
- Wang, L.; Chen, K.; Long, Y.; Wang, H. An efficient pairing-free certificateless signature scheme for resource-limited systems. Sci. China Inf. Sci. 2017, 60, 119102. [Google Scholar] [CrossRef]
- Yeh, K.H.; Su, C.; Choo, K.K.R.; Chiu, W. A novel certificateless signature scheme for smart objects in the Internet-of-Things. Sensors 2017, 17, 1001. [Google Scholar] [CrossRef] [PubMed]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible protocols and atomic proxy cryptography. In Proceedings of the Theory and Applications of Cryptographic Techniques (EUROCRYPT’98), Espoo, Finland, 31 May–4 June 1998; Springer: Berlin/Heidelberg, Germany, 1996; LNCS Volume 1403, pp. 127–144. [Google Scholar]
- Yang, X.; Chen, C.; Ma, T.; Wang, J.; Wang, C. Revocable identity-based proxy re-signature against signing key exposure. PLoS ONE 2018, 13, e0194783. [Google Scholar] [CrossRef] [PubMed]
- Shao, J.; Cao, Z.; Wang, L.; Liang, X. Proxy re-signature schemes without random oracles. In Proceedings of the Cryptology in India (INDOCRYPT), Chennai, India, 9–13 December 2007; Springer: Berlin/Heidelberg, Germany, 2007; LNCS Volume 4859, pp. 197–209. [Google Scholar]
- Jakobsson, M.; Sako, K.; Impagliazzo, R. Designated verifier proofs and their applications. In Proceedings of the Theory and Applications of Cryptographic Techniques (EUROCRYPT’96), Saragossa, Spain, 12–16 May 1996; Springer: Berlin/Heidelberg, Germany, 1996; LNCS Volume 1070, pp. 143–154. [Google Scholar]
- Zhao, W.; Peng, Y.; Xie, F.; Dai, Z.; Gao, H.; Gao, Y. Designated verifier signature scheme over circulant matrices. In Proceedings of the Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), Piraeus, Greece, 18–20 July 2012; IEEE Press: Piscataway, NJ, USA, 2012; pp. 420–423. [Google Scholar]
- Li, M.; Fang, T. Provably secure and efficient id-based strong designated verifier signature scheme with message recovery. In Proceedings of the Network-Based Information Systems (NBiS), Salerno, Italy, 10–12 September 2014; IEEE Press: Piscataway, NJ, USA, 2014; pp. 287–293. [Google Scholar]
- Tso, R.; Nieto, J.M.G.; Okamoto, T.; Boyd, C.; Okamoto, E. Verifier-key-flexible universal designated-verifier signatures. In Proceedings of the Cryptography and Coding, Cirencester, UK, 18–20 December 2007; Springer: Berlin/Heidelberg, Germany, 2007; LNCS Volume 4887, pp. 403–421. [Google Scholar]
- Wei, J.; Yang, G.; Mu, Y. Designated verifier proxy re-signature for deniable and anonymous wireless communications. Wirel. Pers. Commun. 2017, 97, 3017–3030. [Google Scholar] [CrossRef]
- Yang, X.; Yang, M.; An, F.; Leng, Q. A payment mechanism with multi-authority and privacy protection in mobile social networks. In Proceedings of the Wavelet Active Media Technology and Information Processing (ICCWAMTIP), Chengdu, China, 15–17 December 2017; IEEE Press: Piscataway, NJ, USA, 2017; pp. 258–262. [Google Scholar]
- Zhou, C.X. Identity based generalized proxy signcryption scheme. Inf. Technol. Control 2016, 45, 13–26. [Google Scholar]
- Hu, X.; Tan, W.; Xu, H.; Wang, J. Short and provably secure designated verifier proxy signature scheme. IET Inf. Secur. 2016, 10, 69–79. [Google Scholar] [CrossRef]
- Canetti, R.; Goldreich, O.; Halevi, S. The random oracle methodology, revisited. J. ACM (JACM) 2004, 51, 557–594. [Google Scholar] [CrossRef]
- Waters, B. Efficient identity-based encryption without random oracles. In Proceedings of the Theory and Applications of Cryptographic Techniques (EUROCRYPT 2005), Aarhus, Denmark, 22–26 May 2005; LNCS Volume 3494, pp. 114–127. [Google Scholar]
- Gao, C.Z.; Cheng, Q.; He, P.; Susilo, W.; Li, J. Privacy-preserving Naive Bayes classifiers secure against the substitution-then-comparison attack. Inf. Sci. 2018, 444, 72–88. [Google Scholar] [CrossRef]
- Li, T.; Li, J.; Liu, Z.; Li, P.; Jia, C. Differentially private naive bayes learning over multiple data sources. Inf. Sci. 2018, 444, 89–104. [Google Scholar] [CrossRef]
- Zhang, X.; Tan, Y.; Liang, C.; Li, Y.; Li, J. A covert channel over volte via adjusting silence periods. IEEE Access 2018, 6, 9292–9302. [Google Scholar] [CrossRef]
- Huang, Z.; Liu, S.; Mao, X.; Chen, K.; Li, J. Insight of the protection for data security under selective opening attacks. Inf. Sci. 2017, 412, 223–241. [Google Scholar] [CrossRef]
- Li, J.; Chen, X.; Chow, S.S.; Huang, Q.; Wong, D.S.; Liu, Z. Multi-authority fine-grained access control with accountability and its application in cloud. J. Netw. Comput. Appl. 2018, 112, 89–96. [Google Scholar] [CrossRef]
- Castiglione, A.; De Santis, A.; Masucci, B.; Palmieri, F.; Castiglione, A.; Li, J.; Huang, X. Hierarchical and shared access control. IEEE Trans. Inf. Forensics Secur. 2016, 11, 850–865. [Google Scholar] [CrossRef]
- Shen, H.; Gao, C.; He, D.; Wu, L. New biometrics-based authentication scheme for multi-server environment in critical systems. J. Ambient Intell. Humaniz. Comput. 2015, 6, 825–834. [Google Scholar] [CrossRef]
- Cai, Z.; Yan, H.; Li, P.; Huang, Z.A.; Gao, C. Towards secure and flexible EHR sharing in mobile health cloud under static assumptions. Clust. Comput. 2017, 20, 2415–2422. [Google Scholar] [CrossRef]
- Shen, J.; Zhou, T.; Chen, X.; Li, J.; Susilo, W. Anonymous and traceable group data sharing in cloud computing. IEEE Trans. Inf. Forensics Secur. 2018, 13, 912–925. [Google Scholar] [CrossRef]
- Lin, Q.; Yan, H.; Huang, Z.; Chen, W.; Shen, J.; Tang, Y. An ID-based linearly homomorphic signature scheme and its application in blockchain. IEEE Access 2018, 6, 20632–20640. [Google Scholar] [CrossRef]
- Chen, W.; Lei, H.; Qi, K. Lattice-based linearly homomorphic signatures in the standard model. Theor. Comput. Sci. 2016, 634, 47–54. [Google Scholar] [CrossRef]
- Lin, Q.; Li, J.; Huang, Z.; Chen, W.; Shen, J. A short linearly homomorphic proxy signature scheme. IEEE Access 2018, 6, 12966–12972. [Google Scholar] [CrossRef]
- Tian, H.; Li, J. A short non-delegatable strong designated verifier signature. Front. Comput. Sci. 2014, 8, 490–502. [Google Scholar] [CrossRef]
- Chen, W.; Chen, Z.; Samatova, N.F.; Peng, L.; Wang, J.; Tang, M. Solving the maximum duo-preservation string mapping problem with linear programming. Theor. Comput. Sci. 2014, 530, 1–11. [Google Scholar] [CrossRef]
- Ateniese, G.; Hohenberger, S. Proxy re-signatures: New definitions, algorithms, and applications. In Proceedings of the Computer and Communications Security (CCS), Alexandria, VA, USA, 7–11 November 2005; ACM Press: New York, NY, USA, 2005; pp. 310–319. [Google Scholar]
- Hu, X.; Zhang, Z.; Yang, Y. Identity based proxy re-signature schemes without random oracle. In Proceedings of the Computational Intelligence and Security (CIS), Beijing, China, 11–14 December 2009; IEEE Press: Piscataway, NJ, USA, 2009; pp. 256–259. [Google Scholar]
- Tian, M. Identity-based proxy re-signatures from lattices. Inf. Process. Lett. 2015, 115, 462–467. [Google Scholar] [CrossRef]
- Wang, Z.W.; Xia, A.D. ID-based proxy re-signature with aggregate property. J. Inf. Sci. Eng. 2015, 31, 1199–1211. [Google Scholar]
- Yang, P.; Cao, Z.; Dong, X. Threshold proxy re-signature. J. Syst. Sci. Complex. 2011, 24, 816–824. [Google Scholar] [CrossRef]
- Yang, X.D.; Wang, C.F.; Lan, C.H.; Wang, B. Flexible threshold proxy re-signature schemes. Chin. J. Electron. 2011, 20, 691–696. [Google Scholar]
- Yang, X.; Wang, C.; Zhang, L.; Qiu, J. On-line/off-line threshold proxy re-signatures. Chin. J. Electron. 2014, 23, 248–253. [Google Scholar]
- Guo, D.; Wei, P.; Yu, D.; Yang, X. A certificateless proxy re-signature scheme. In Proceedings of the Computer Science and Information Technology (ICCSIT), Chengdu, China, 9–11 July 2010; IEEE Press: Piscataway, NJ, USA, 2010; pp. 157–161. [Google Scholar]
- Xiao, H.; Zhang, M. Provably-secure certificateless proxy re-signature scheme. In Proceedings of the Intelligent Networking and Collaborative Systems (INCoS), Xi’an, China, 9–11 September 2013; IEEE Press: Piscataway, NJ, USA, 2013; pp. 591–594. [Google Scholar]
- Hu, X.; Liu, Y.; Xu, H.; Wang, J.; Zhang, X. Analysis and improvement of certificateless signature and proxy re-signature schemes. In Proceedings of the Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, 19–20 December 2015; IEEE Press: Piscataway, NJ, USA, 2015; pp. 166–170. [Google Scholar]
- Saeednia, S.; Kremer, S.; Markowitch, O. An efficient strong designated verifier signature scheme. In Proceedings of the International Conference on Information Security and Cryptology (ICISC), Seoul, Korea, 27–28 November 2003; Springer: Berlin/Heidelberg, Germany, 2003; LNCS Volume 2971, pp. 40–54. [Google Scholar]
- Noh, G.; Jeong, I.R. Strong designated verifier signature scheme from lattices in the standard model. Secur. Commun. Netw. 2015, 18, 6202–6214. [Google Scholar] [CrossRef]
- Chen, Y.; Zhao, Y.; Xiong, H.; Yue, F. A certificateless strong designated verifier signature scheme with non-delegatability. IJ Netw. Secur. 2017, 19, 573–582. [Google Scholar]
- Khan, A.U.; Ratha, B.K. A secure strong designated verifier signature scheme. IJ Netw. Secur. 2017, 19, 599–604. [Google Scholar]
- Huang, Q.; Yang, G.; Wong, D.S.; Susilo, W. Efficient strong designated verifier signature schemes without random oracles or delegatability. Int. J. Inf. Secur. 2009, 10, 373–385. [Google Scholar] [CrossRef]
- Tian, H.; Jiang, Z.; Liu, Y.; Wei, B. A systematic method to design strong designated verifier signature without random oracles. Clust. Comput. 2013, 16, 817–827. [Google Scholar] [CrossRef]
- Lin, H.Y. Secure universal designated verifier signature and its variant for privacy protection. Inf. Technol. Control 2013, 42, 268–276. [Google Scholar]
- Lin, C.; Wu, W.; Huang, X.; Xu, L. A new universal designated verifier transitive signature scheme for big graph data. J. Comput. Syst. Sci. 2017, 83, 73–83. [Google Scholar] [CrossRef]
- Laguillaumie, F.; Vergnaud, D. Multi-designated verifiers signatures: Anonymity without encryption. Inf. Process. Lett. 2007, 102, 127–132. [Google Scholar] [CrossRef]
- Ming, Y.; Wang, Y. Universal designated multi verifier signature scheme without random oracles. Wuhan Univ. J. Nat. Sci. 2008, 13, 685–691. [Google Scholar] [CrossRef]
- Huang, Q.; Yang, G.; Wong, D.S.; Susilo, W. Efficient strong designated verifier signature schemes without random oracle or with non-delegatability. Int. J. Inf. Secur. 2011, 10, 373–385. [Google Scholar] [CrossRef]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).