Defining Cyber Risk Scenarios to Evaluate IoT Systems
Abstract
1. Introduction
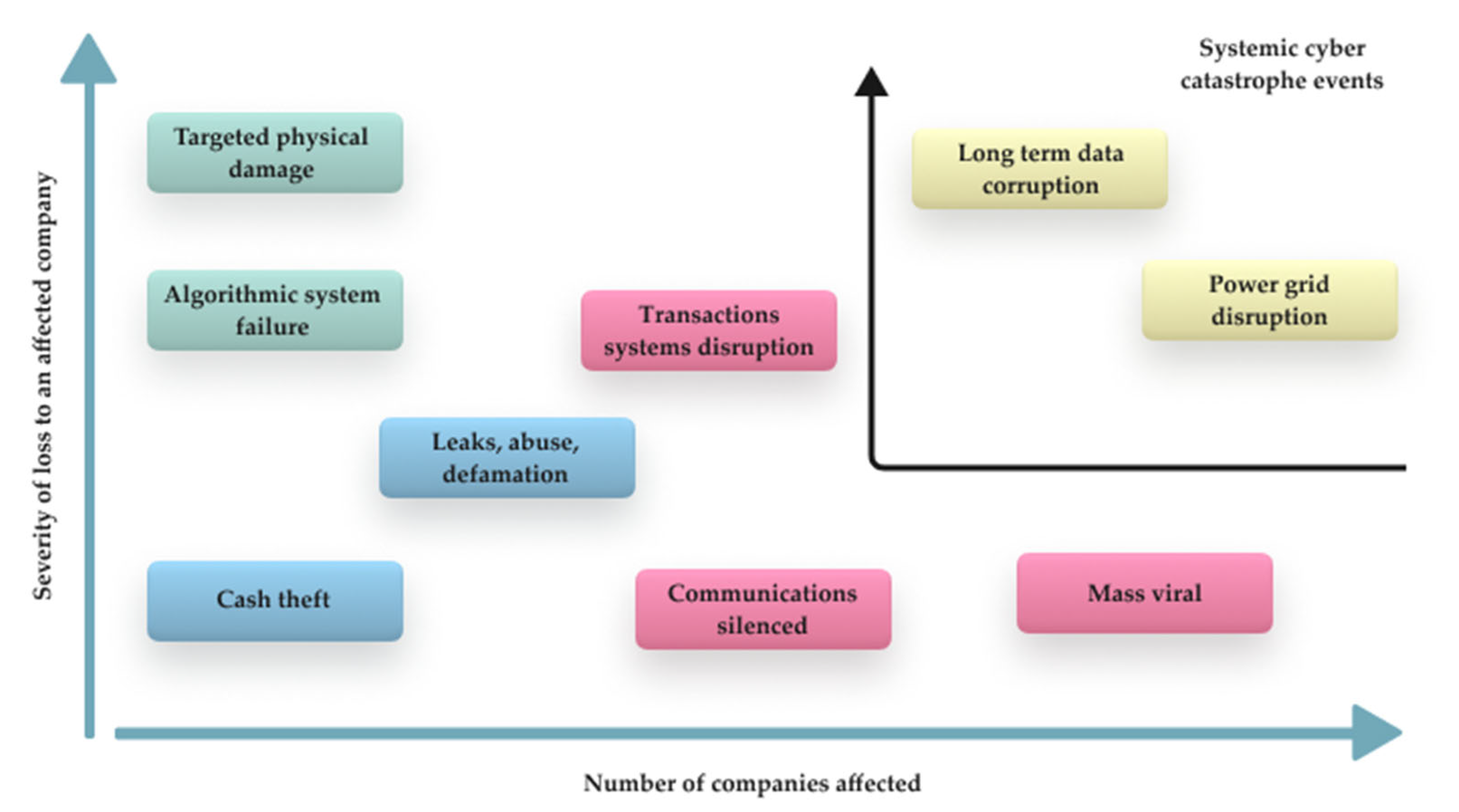
- Level 1: the pervasiveness of technology could disrupt several organizations simultaneously;
- Level 2: interdependencies between organizations, as an organization’s cybersecurity failure presents a potential risk of affecting its networking organizations;
- Level 3: cybersecurity failure, which could be systematically catastrophic to economies and societies. Multiple financial and social sectors could fail.
- Repeated attacks;
- Scattershot attacks;
- Pervasive attacks;
- Rolling attacks;
- Transitive attacks;
- Cascading attacks;
- Shared resource consumption attacks;
- Critical function attacks;
- Regional attacks;
- Service dependency attacks;
- Coordinated supply chain attacks.
- Bayesian networks allow for real-time tracking of how event probabilities change as new evidence is introduced into the model;
- Bayesian networks define how the different network nodes are linked. Additionally, they study how the probabilities change after introducing some evidence into specific nodes;
- Bayesian networks could make predictions under scenarios of limited and uncertain data.
2. Literature Review
2.1. Systematic Literature Review—Bayesian Networks Applied to Cybersecurity
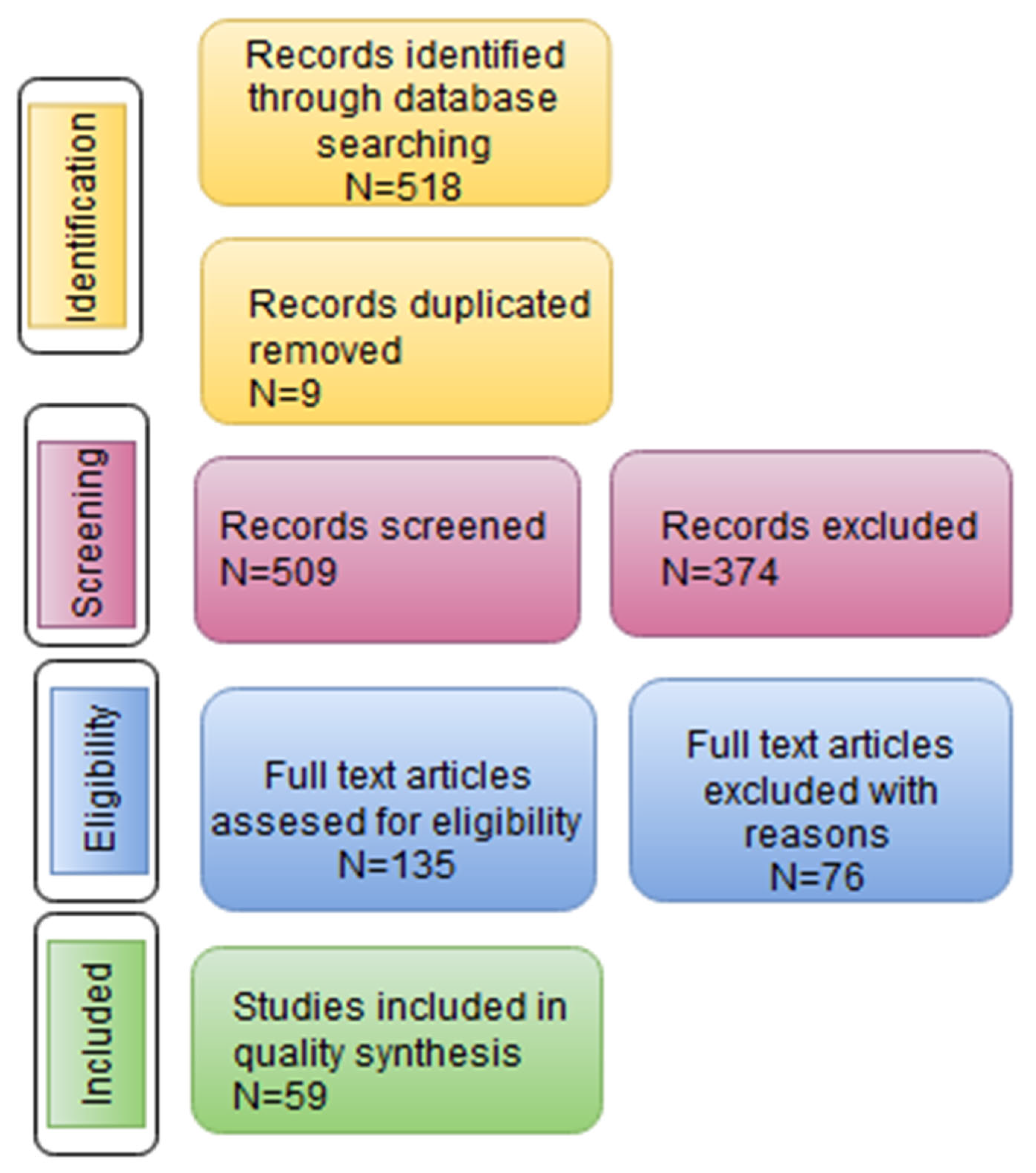
- (i)
- Identification, which is related to evaluating previous studies from scientific databases and searching the use of Bayesian networks for IoT security. The previous studies were explored according to the following keywords: (a) “Security and (Bayes Network or Bayesian Network)”, (b) “Security attacks and (Bayes Network or Bayesian Network)” and (c) “Cybersecurity attacks and (Bayes Network or Bayesian Network)”. The used scientific databases were IEEE Xplorer, Scopus, ACM and Springer. The method search was performed to find previous studies accomplished in the last six years (2016–2022).
- (ii)
- Blind screening review process, which implies that the authors of this research developed this procedure to evaluate previous studies. The procedure was achieved by using the Rayyan method.
- (iii)
- Eligibility, as a full review of the documents was developed to identify relevant contributions to this study.
- (iv)
- Inclusion, as a quality analysis of selected documents from the eligibility stage was established. In Figure 2, an overview of the PRISMA methodology used for this systematic literature review is shown. Table 2 shows the distribution of previous studies, related to the Bayesian network methods in cybersecurity, found in journals, books, conferences and documents.
2.2. Risk Assessment Using Bayesian Networks
3. Risk Methodologies in Complex and Dynamic Environments
- Model complex systems;
- Manage unknown (latent) variables;
- Manage data lack;
- Use probability distributions;
- Use judgment experts;
- Direct conception of model structure.
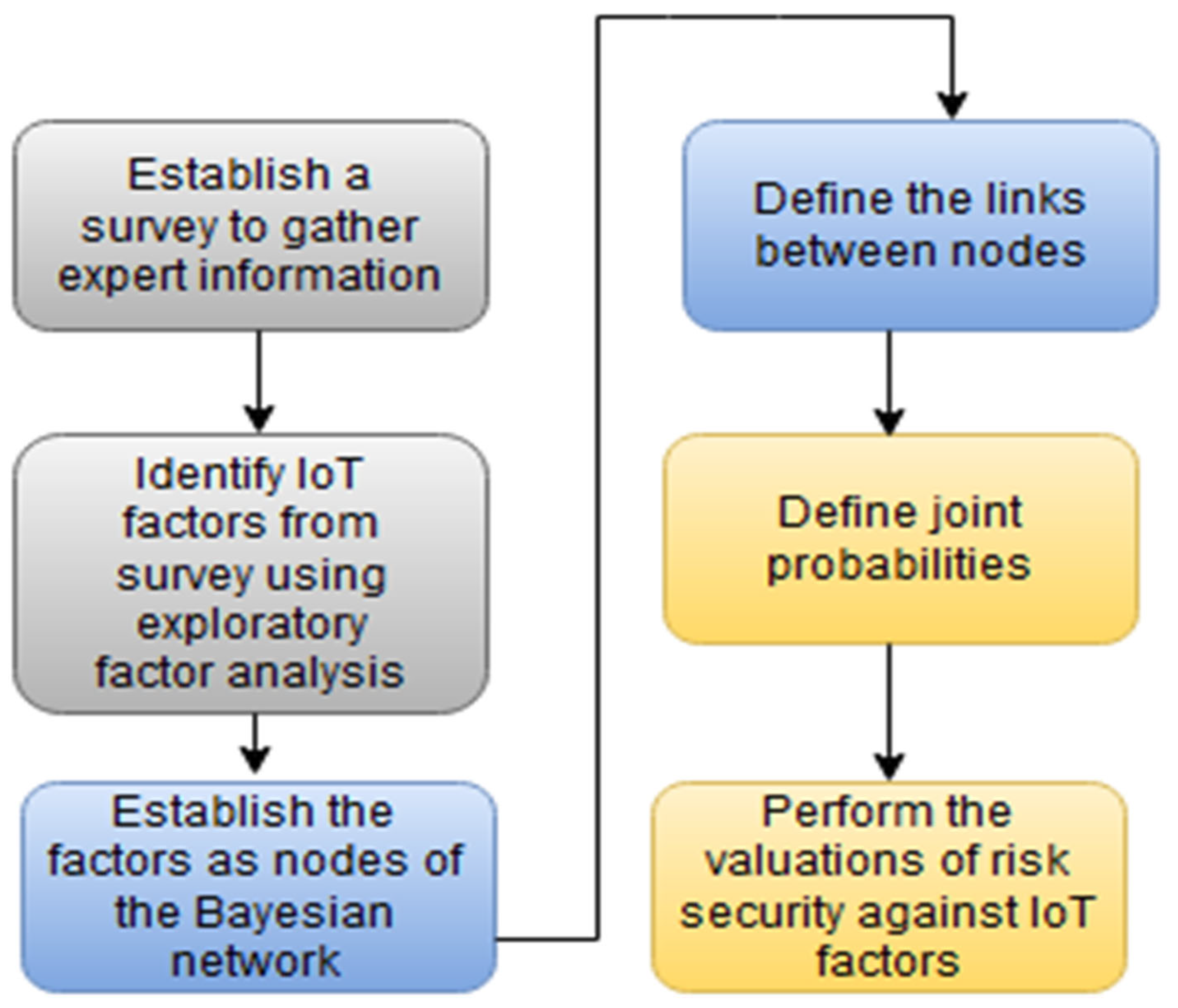
- Identification and selection of nodes (factors). In scenarios where there is a lack of data for node modeling, the suggestion is to employ previous study cases or expert judgments.
- Define the model structure; this includes the relations (links) between nodes [60]. Define the causal relationship between nodes by a set of directed edges. The direction is from the origin nodes to the destination nodes.
- Determine the conditional probabilities of all nodes. Define prior elicitation from experts and/or from selected data.
- Validation of the model structure. Assess the feasibility and accuracy of the model by expert judgment.
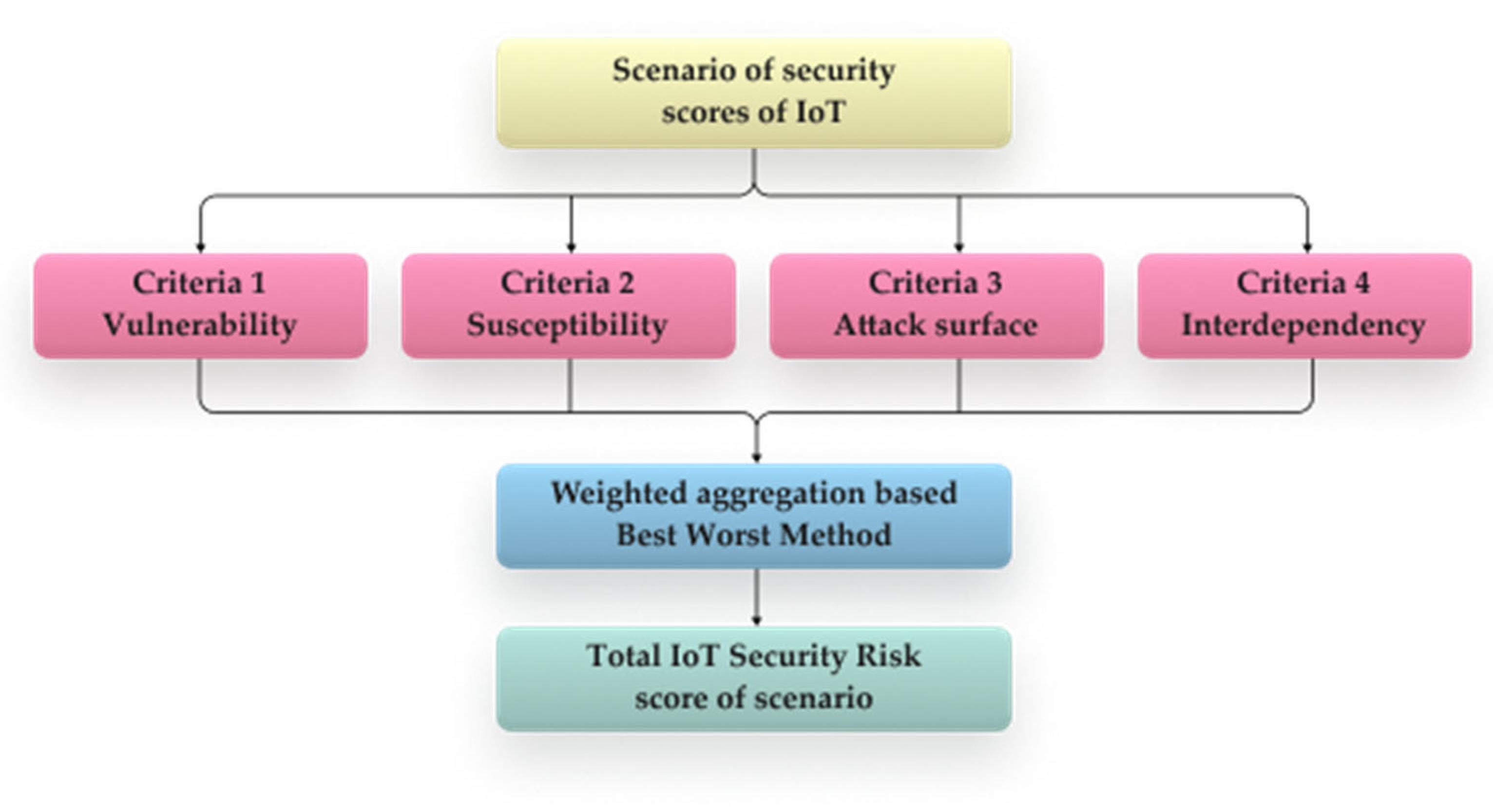
4. Bayesian Network Structure
4.1. Key Factors of IoT Devices to Evaluate Risk Security
4.2. Bayesian Network Model
4.3. Probability Distribution of Bayesian Network Nodes
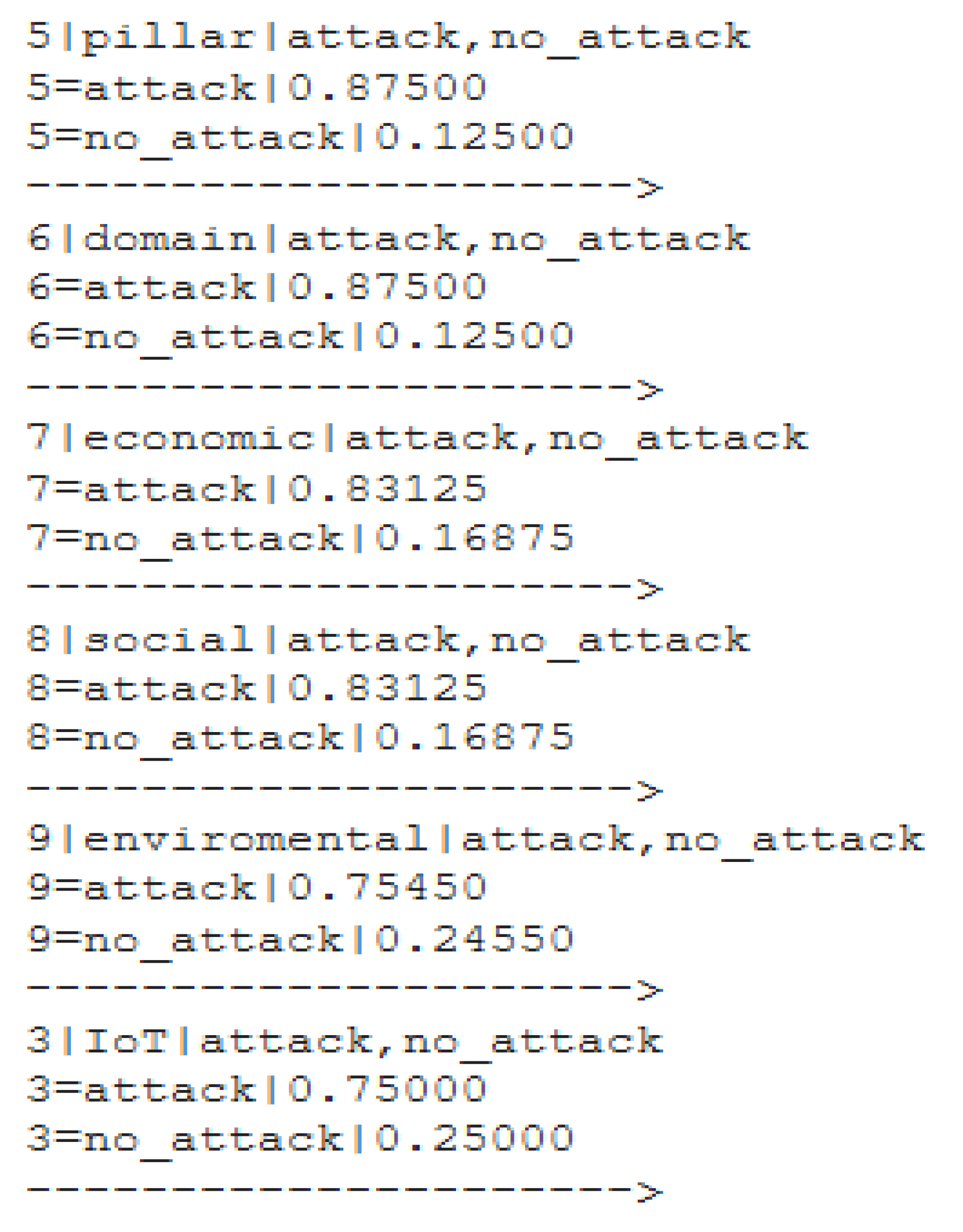
5. Results: Risk Security Using Scenario Cases and Bayesian Networks
6. Discussion and Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- World Economic Forum, Technology, Innovation and Systemic Risk. 2022. Available online: https://www.weforum.org/projects/technology-innovation-and-systemic-risk (accessed on 28 February 2022).
- Mckinsey. 2022. Available online: https://www.mckinsey.com/alumni/news-and-insights/global-news/firm-news/the-accelerating-value-of-the-internet-of-things (accessed on 28 February 2022).
- Zikria, Y.B.; Ali, R.; Afzal, M.K.; Kim, S.W. Next-Generation Internet of Things (IoT): Opportunities, Challenges, and Solutions. Sensors 2021, 21, 1174. [Google Scholar] [CrossRef] [PubMed]
- Radanliev, P.; De Roure, D.C.; Nurse, J.R.C.; Montalvo, R.M.; Cannady, S.; Santos, O.; Maddox, L.; Burnap, P.; Maple, C. Future developments in standardization of cyber risk in the Internet of Things (IoT). SN Appl. Sci. 2020, 2, 169. [Google Scholar] [CrossRef]
- Nurse, J.; Creese, S.; Roure, D. Security Risk Assessment in Internet of Things Systems. IT Prof. 2017, 19, 20–26. [Google Scholar] [CrossRef]
- Kandasamy, K.; Srinivas, S.; Achuthan, K.; Rangan, V.P. IoT cyber risk: A holistic analysis of cyber risk assessment frameworks, risk vectors, and risk ranking process. EURASIP J. Info. Secur. 2020, 2020, 8. [Google Scholar] [CrossRef]
- Deleuze, G.; Bertin, H.; Dutfoy, A.; Pierlot, S.; Pourret, O. Use of Bayesian Belief Networks for risk management in energy distribution. In Probabilistic Safety Assessment and Management; Spitzer, C., Schmocker, U., Dang, V.N., Eds.; Springer: London, UK, 2004. [Google Scholar] [CrossRef]
- Szpyrka, M.; Jasiul, B.; Wrona, K.; Dziedzic, F. Telecommunications Networks Risk Assessment with Bayesian Networks. In Computer Information Systems and Industrial Management. CISIM 2013. Lecture Notes in Computer Science; Saeed, K., Chaki, R., Cortesi, A., Wierzchoń, S., Eds.; Springer: Berlin/Heidelberg, German, 2013; Volume 8104. [Google Scholar] [CrossRef]
- Hunte, J.; Neil, M.; Fenton, N. Product risk assessment: A Bayesian network approach. arXiv 2020, arXiv:2010.06698. [Google Scholar]
- Li, M.; Hong, M.; Zhang, R. Improved Bayesian Network-Based Risk Model and Its Application in Disaster Risk Assessment. Int. J. Disaster Risk Sci. 2018, 9, 237–248. [Google Scholar] [CrossRef]
- Pius, A.M.; Ogada, K.; Mwalili, T. Supervised Machine Learning Modelling of Demand for Outpatient Health-Care Services in Kenya using Artificial Neural Networks and Regression Decision Trees. In Proceedings of the 2021 22nd International Arab Conference on Information Technology (ACIT), Muscat, Oman, 21–23 December 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Dahal, S.; Schaeffer, R.; Abdelfattah, E. Performance of Different Classification Models on National Coral Reef Monitoring Dataset. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 27–30 January 2021; pp. 0662–0666. [Google Scholar] [CrossRef]
- Chela, G.M.; Flores, M.; Gualli, T.G.; Andrade, R. Methodological Proposal for the Construction of a Decision Support System (DSS) Applied to IoT. In Information and Knowledge in Internet of Things. EAI/Springer Innovations in Communication and Computing; Guarda, T., Anwar, S., Leon, M., Mota Pinto, F.J., Eds.; Springer: Cham, Switzerland, 2022. [Google Scholar] [CrossRef]
- Jantsch, A.; Anzanpour, A.; Kholerdi, H.; Azimi, I.; Siafara, L.C.; Rahmani, A.M.; TaheriNejad, N.; Liljeberg, P.; Dutt, N. Hierarchical dynamic goal management for IoT systems. In Proceedings of the 2018 19th International Symposium on Quality Electronic Design (ISQED), Santa Clara, CA, USA, 13–14 March 2018; pp. 370–375. [Google Scholar] [CrossRef]
- Hongmei, L.; Wenning, H.; Wenyan, G.; Gang, C. Survey of Probabilistic Graphical Models. In Proceedings of the 2013 10th Web Information System and Application Conference, Washington, DC, USA, 10–15 November 2013; pp. 275–280. [Google Scholar] [CrossRef]
- Rabiner, L.; Juang, B. An introduction to hidden Markov models. IEEE ASSP Mag. 1986, 3, 4–16. [Google Scholar] [CrossRef]
- Cao, Y. Study of the Bayesian networks. In Proceedings of the 2010 International Conference on E-Health Networking Digital Ecosystems and Technologies (EDT), Shenzhen, China, 17–18 April 2010; pp. 172–174. [Google Scholar] [CrossRef]
- Kumar, P.; Singh, L.K.; Kumar, C.; Verma, S.; Kumar, S. A Bayesian Belief Network Model for Early Prediction of Reliability for Computer-Based Safety-Critical Systems. In Proceedings of the 2021 2nd International Conference on Range Technology (ICORT), Balasore, India, 5–6 August 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Asvija, B.; Eswari, R.; Bijoy, M.B. Security Threat Modelling With Bayesian Networks and Sensitivity Analysis for IAAS Virtualization Stack. J. Organ. End User Comput. (JOEUC) 2021, 33, 44–69. [Google Scholar] [CrossRef]
- Guan, R.; Li, L.; Wang, T.; Qin, Y.; Xiong, W.; Liu, Q. A Bayesian Improved Defense Model for Deceptive Attack in Honeypot-Enabled Networks. In Proceedings of the 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Zhangjiajie, China, 10–12 August 2019; pp. 208–214. [Google Scholar] [CrossRef]
- Kalnoor, G.; Gowrishankar, S. A model for intrusion detection system using hidden Markov and variational Bayesian model for IoT based wireless sensor network. Int. J. Inf. Tecnol. 2021, 14, 2021–2033. [Google Scholar] [CrossRef]
- Toğaçar, M. Detecting attacks on IoT devices with probabilistic Bayesian neural networks and hunger games search optimization approaches. Trans. Emerg. Telecommun. Technol. 2022, 33. [Google Scholar] [CrossRef]
- Kalnoor, G.; Gowrishankar, S. A Framework Using Markov-Bayes’ Model for Intrusion Detection in Wireless Sensor Network. In ICDSMLA 2020; Lecture Notes in Electrical, Engineering; Kumar, A., Senatore, S., Gunjan, V.K., Eds.; Springer: Singapore, 2022; Volume 783. [Google Scholar] [CrossRef]
- Wisanwanichthan, T.; Thammawichai, M. A Double-Layered Hybrid Approach for Network Intrusion Detection System Using Combined Naive Bayes and SVM. IEEE Access 2021, 9, 138432–138450. [Google Scholar] [CrossRef]
- Liu, Q.; Keller, H.B.; Hagenmeyer, V. A Bayesian Rule Learning Based Intrusion Detection System for the MQTT Communication Protocol. In Proceedings of the 16th International Conference on Availability, Reliability and Security (ARES 2021), Vienna, Austria, 17–20 August 2021; Association for Computing Machinery: New York, NY, USA, 2021; Volume 81, pp. 1–10. [Google Scholar] [CrossRef]
- Sahu, A.; Davis, K. Structural Learning Techniques for Bayesian Attack Graphs in Cyber Physical Power Systems. In Proceedings of the 2021 IEEE Texas Power and Energy Conference (TPEC), College Station, TX, USA, 2–5 February 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Klassen, M.; Yang, N. Anomaly based intrusion detection in wireless networks using Bayesian classifier. In Proceedings of the 2012 IEEE Fifth International Conference on Advanced Computational Intelligence (ICACI), Nanjing, China, 18–20 October 2012; pp. 257–264. [Google Scholar] [CrossRef]
- Berguig, Y.; Laassiri, I.; Hanaoui, S. DoS Detection Based on Mobile Agent and Naïve Bayes Filter. In Proceedings of the 2018 International Symposium on Advanced Electrical and Communication Technologies (ISAECT), Kenitra, Morocco, 21–23 November 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Fu, Y.; He, Z. Bayesian-Inference-Based Sliding Window Trust Model Against Probabilistic SSDF Attack in Cognitive Radio Networks. IEEE Syst. J. 2020, 14, 1764–1775. [Google Scholar] [CrossRef]
- Muñoz-González, L.; Sgandurra, D.; Barrère, M.; Lupu, E.C. Exact Inference Techniques for the Analysis of Bayesian Attack Graphs. IEEE Trans. Dependable Secur. Comput. 2019, 16, 231–244. [Google Scholar] [CrossRef]
- Vaddi, P.K.; Pietrykowski, M.C.; Kar, D.; Diao, X.; Zhao, Y.; Mabry, T.; Ray, I.; Smidts, C. Dynamic bayesian networks based abnormal event classifier for nuclear power plants in case of cyber security threats. Prog. Nucl. Energy 2020, 128, 103479. [Google Scholar] [CrossRef]
- Lin, P.; Chen, Y. Dynamic Network Security Situation Prediction based on Bayesian Attack Graph and Big Data. In Proceedings of the 2018 IEEE 4th Information Technology and Mechatronics Engineering Conference (ITOEC), Chongqing, China, 14–16 December 2018; pp. 992–998. [Google Scholar] [CrossRef]
- Zhang, Y.; Malacaria, P. Bayesian Stackelberg games for cyber-security decision support. Decis. Support Syst. 2021, 148, 113599. [Google Scholar] [CrossRef]
- Durgadevi, V.; Ganeshkumar, P. Fuzzy integrated Bayesian Dempster-Shafer Theory to defend cross-layer heterogeneity attacks in Communication Network of Smart Grid. Inf. Sci. 2018, 479, 542–566. [Google Scholar] [CrossRef]
- Alhakami, W.; Lharbi, A.A.; Bourouis, S.; Alroobaea, R.; Bouguila, N. Network Anomaly Intrusion Detection Using a Nonparametric Bayesian Approach and Feature Selection. IEEE Access 2019, 7, 52181–52190. [Google Scholar] [CrossRef]
- Pirbhulal, S.; Gkioulos, V.; Katsikas, S. Towards Integration of Security and Safety Measures for Critical Infrastructures Based on Bayesian Networks and Graph Theory: A Systematic Literature Review. Signals 2021, 2, 771–802. [Google Scholar] [CrossRef]
- Forti, N.; Battistelli, G.; Chisci, L.; Sinopoli, B. A Bayesian approach to joint attack detection and resilient state estimation. In Proceedings of the 2016 IEEE 55th Conference on Decision and Control (CDC), Las Vegas, NV, USA, 12–14 December 2016; pp. 1192–1198. [Google Scholar] [CrossRef]
- Li, Y.; Liu, T.; Zhu, J.; Wang, X. IoT Security Situational Awareness Based on Q-Learning and Bayesian Game; Springer: Singapore, 2021; pp. 190–203. ISBN 978-981-16-5943-0. [Google Scholar]
- Yesi, K.; Siti, N.; Deris, S.; Bhakti, Y. Improving Classification Attacks in IOT Intrusion Detection System using Bayesian Hyperparameter Optimization. In Proceedings of the 2020 3rd International Seminar on Research of Information Technology and Intelligent Systems (ISRITI), Yogyakarta, Indonesia, 10 December 2020; pp. 146–151. [Google Scholar] [CrossRef]
- Wang, J.; Guo, M. Vulnerability categorization using Bayesian networks. In Proceedings of the Sixth Annual Workshop on Cyber Security and Information Intelligence Research (CSIIRW ′10), Oak Ridge, TN, USA, 21–23 April 2010; Association for Computing Machinery: New York, NY, USA, 2010; Volume 29, pp. 1–4. [Google Scholar] [CrossRef]
- Priscilla, G.; Vadakkapaikkadu, R. Evolution of Safety and Security Risk Assessment methodologies to use of Bayesian Networks in Process Industries. Process Saf. Environ. Prot. 2021, 149, 758–775. [Google Scholar] [CrossRef]
- Hui, B.-F.; Ma, Y.-L. Information Security Defense Evaluation Based on Bayesian Network. In Proceedings of the International Conference on Artificial Intelligence for Communications and Networks, Xining, China, 23–24 October 2021; Springer: Cham, Switzerland, 2021; pp. 3–7, ISBN 978-3-030-90199-8. [Google Scholar]
- Wang, J.; Fan, K.; Mo, W.; Xu, D. A Method for Information Security Risk Assessment Based on the Dynamic Bayesian Network. In Proceedings of the 2016 International Conference on Networking and Network Applications (NaNA), Hakodate City, Japan, 23–25 July 2016; pp. 279–283. [Google Scholar] [CrossRef]
- Behfarnia, A.; Eslami, A. Risk Assessment of Autonomous Vehicles Using Bayesian Defense Graphs. In Proceedings of the 2018 IEEE 88th Vehicular Technology Conference (VTC-Fall), Chicago, IL, USA, 27–30 August 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Isaac, M.; Sadegh, S.; Aad, M. Stochastic Simulation Techniques for Inference and Sensitivity Analysis of Bayesian Attack Graphs. In Proceedings of the International Conference on Science of Cyber Security, Shanghai, China, 13–15 August 2021; Springer: Cham, Switzerland, 2021. [Google Scholar]
- Zhang, Q.; Zhou, C.; Tian, Y.-C.; Xiong, N.; Qin, Y.; Hu, B. A Fuzzy Probability Bayesian Network Approach for Dynamic Cybersecurity Risk Assessment in Industrial Control Systems. IEEE Trans. Ind. Inform. 2018, 14, 2497–2506. [Google Scholar] [CrossRef]
- Halabi, T.; Wahab, O.A.; Al Mallah, R.; Zulkernine, M. Protecting the Internet of Vehicles Against Advanced Persistent Threats: A Bayesian Stackelberg Game. IEEE Trans. Reliab. 2021, 70, 970–985. [Google Scholar] [CrossRef]
- Thakkar, A.; Badsha, S.; Sengupta, S. Game theoretic approach applied in cybersecurity information exchange framework. In Proceedings of the 2020 IEEE 17th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2020; pp. 1–7. [Google Scholar] [CrossRef]
- Wall, A.; Agrafiotis, I. A Bayesian approach to insider threat detection. J. Wirel. Mob. Netw. Ubiquitous Comput. Dependable Appl. 2021, 12, 48–84. [Google Scholar]
- Wahab, O.A.; Bentahar, J.; Otrok, H.; Mourad, A. Resource-Aware Detection and Defense System against Multi-Type Attacks in the Cloud: Repeated Bayesian Stackelberg Game. IEEE Trans. Dependable Secur. Comput. 2021, 18, 605–622. [Google Scholar] [CrossRef]
- Hu, Z.; Yu, X.; Shi, J.; Ye, L. Abnormal Event Correlation and Detection Based on Network Big Data Analysis. Comput. Mater. Contin. 2021, 69, 695–711. [Google Scholar] [CrossRef]
- Yang, C.; Shi, Z.; Zhang, H.; Wu, J.; Shi, X. Multiple Attacks Detection in Cyber-Physical Systems Using Random Finite Set Theory. IEEE Trans. Cybern. 2020, 50, 4066–4075. [Google Scholar] [CrossRef] [PubMed]
- Peng, Q. Bayesian Networks for Data Prediction. In Proceedings of the 2009 International Forum on Computer Science-Technology and Applications, ChongQing, China, 25–27 December 2009; pp. 101–102. [Google Scholar] [CrossRef]
- Radanliev, P.; de Roure, D.; Cannady, S.; Montalvo, R.M.; Nicolescu, R.; Huth, M. Economic impact of IoT cyber risk—Analysing past and present to predict the future developments in IoT risk analysis and IoT cyber insurance. In Living in the Internet of Things: Cybersecurity of the IoT-2018; Institution of Engineering and Technology: London, UK, 2018; pp. 1–9. [Google Scholar] [CrossRef]
- Bahizad, S. Risks of Increase in the IoT Devices. In Proceedings of the 2020 7th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2020 6th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), New York, NY, USA, 1–3 August 2020; pp. 178–181. [Google Scholar] [CrossRef]
- Wangyal, S.; Dechen, T.; Tanimoto, S.; Sato, H.; Kanai, A. A Study of Multi-viewpoint Risk Assessment of Internet of Things (IoT). In Proceedings of the 2020 9th International Congress on Advanced Applied Informatics (IIAI-AAI), Kitakyushu, Japan, 1–15 September 2020; pp. 639–644. [Google Scholar] [CrossRef]
- Al Mousa, A.; al Qomri, M.; al Hajri, S.; Zagrouba, R.; Chaabani, S. Environment Based IoT Security Risks and Vulnerabilities Management. In Proceedings of the 2020 International Conference on Computing and Information Technology (ICCIT-1441), Tabuk, Saudi Arabia, 9–10 September 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Kononenko, I.; Kukar, M. Chapter 3—Machine Learning Basics. In Machine Learning and Data Mining; Igor, K., Matjaž, K., Eds.; Woodhead Publishing: Sawston, Cambridge, 2007; pp. 59–105. ISBN 9781904275213. [Google Scholar] [CrossRef]
- Scanagatta, M.; Salmerón, A.; Stella, F. A survey on Bayesian network structure learning from data. Prog. Artif. Intell. 2019, 8, 425–439. [Google Scholar] [CrossRef]
- Piccininni, M.; Konigorski, S.; Rohmann, J.L.; Kurth, T. Directed acyclic graphs and causal thinking in clinical risk prediction modeling. BMC Med. Res. Methodol. 2020, 20, 179. [Google Scholar] [CrossRef]
- Devore, J.L.; Berk, K.N.; Carlton, M.A. Joint Probability Distributions and Their Applications. In Modern Mathematical Statistics with Applications. Springer Texts in Statistics; Springer: Cham, Switzerland, 2021. [Google Scholar] [CrossRef]
- Mikkola, P.; Martin, O.; Chandramouli, S.; Hartmann, M.; Pla, O.; Thomas, O.; Pesonen, H.; Corander, J.; Vehtari, A.; Kaski, S.; et al. Prior knowledge elicitation: The past, present, and future. arXiv 2021, arXiv:2112.01380. [Google Scholar]
- Xu, S.; Jia, B.; Liang, F. Learning Moral Graphs in Construction of High-Dimensional Bayesian Networks for Mixed Data. Neural Comput. 2019, 31, 1183–1214. [Google Scholar] [CrossRef]
| Regression | Classification | Neuronal Networks | Probabilistic Graphical Models |
|---|---|---|---|
| Decision tree regression (CART) | Logistic regression | Autoencoders | Bayesian belief net work |
| Random forest regression | Adaptive boosting (AdaBoost) | Conventional neural networks | Hidden Markov model |
| K-nearest neighbors regression (KNN) | Naïve Bayes | Recurrent neural net works | |
| Multivariate adaptive regression splines (MARS) | Support vector machine (SVM) | ||
| Support vector regression (SVR) |
| Type of Manuscripts | Number of Works | Topics Related to Bayesian Networks |
|---|---|---|
| Journal | 348 | |
| Conference | 210 | |
| Book | 3 | |
| Chapters | 92 |
| Application Areas | Number of Papers | Focus On |
|---|---|---|
| IoT | 47 | Detecting attacks [37]. Situational awareness [38]. Classification of attacks [39]. Classification of vulnerabilities [40]. |
| Risk management/assessment | 34 | Industrial process [41]. Information security [42]. Network systems [43]. Cyber–physical systems [22]. Autonomous vehicles [24]. Attack graphs [44]. Cybersecurity protection [45]. |
| Awareness | 5 | IoT security situational awareness [38]. Information attack in vehicular ad hoc network [24]. |
| Defense mechanism | 4 | Advanced persistent threats [46]. Game theoretical approach [47]. |
| Detection of attacks | 158 | Insider threat detection [48]. Resource-aware detection [49]. Detection in a cloud environment [50]. Abnormal event correlation [51]. Multiple attacks detection [52]. |
| Factors | Description |
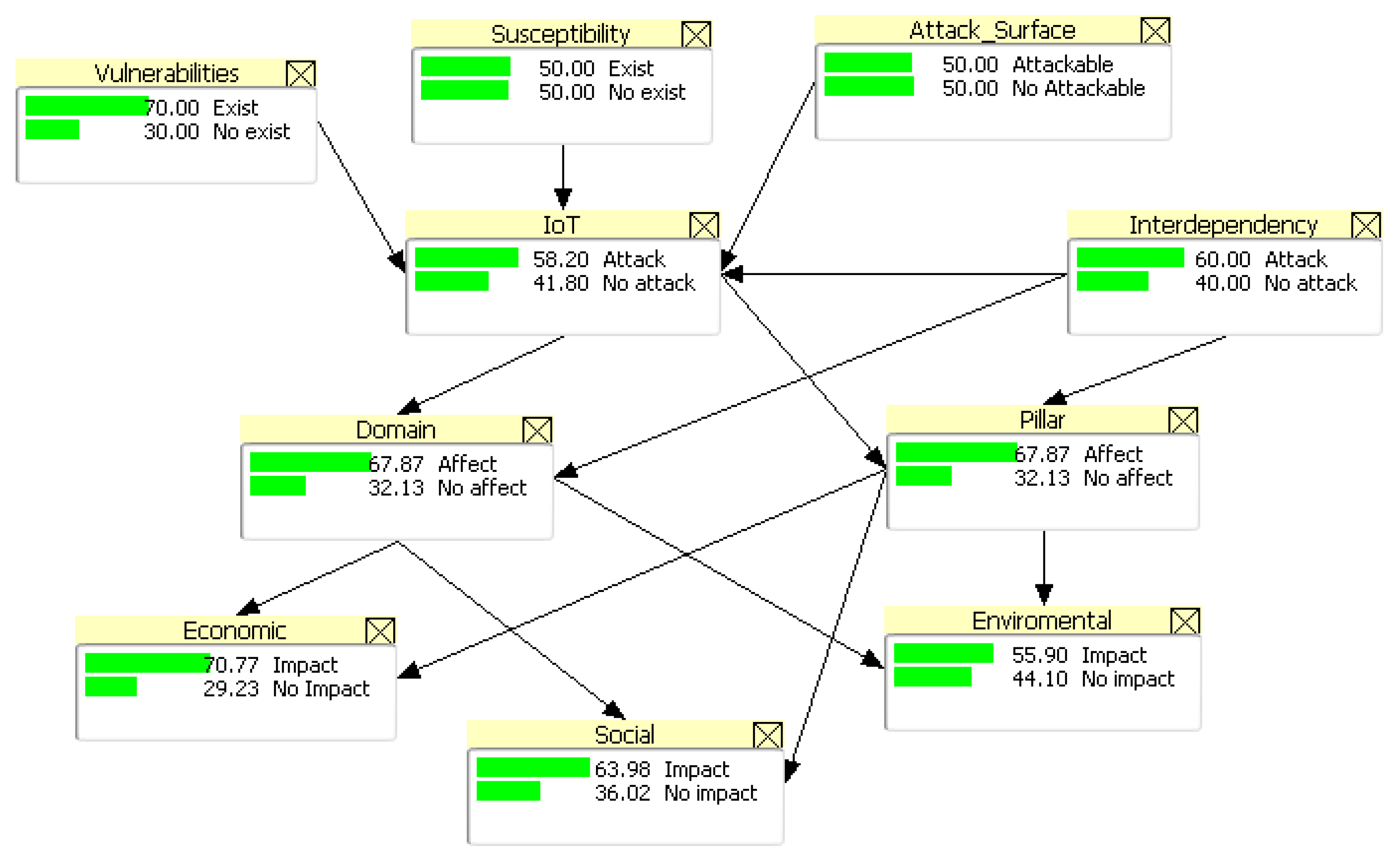
|---|---|
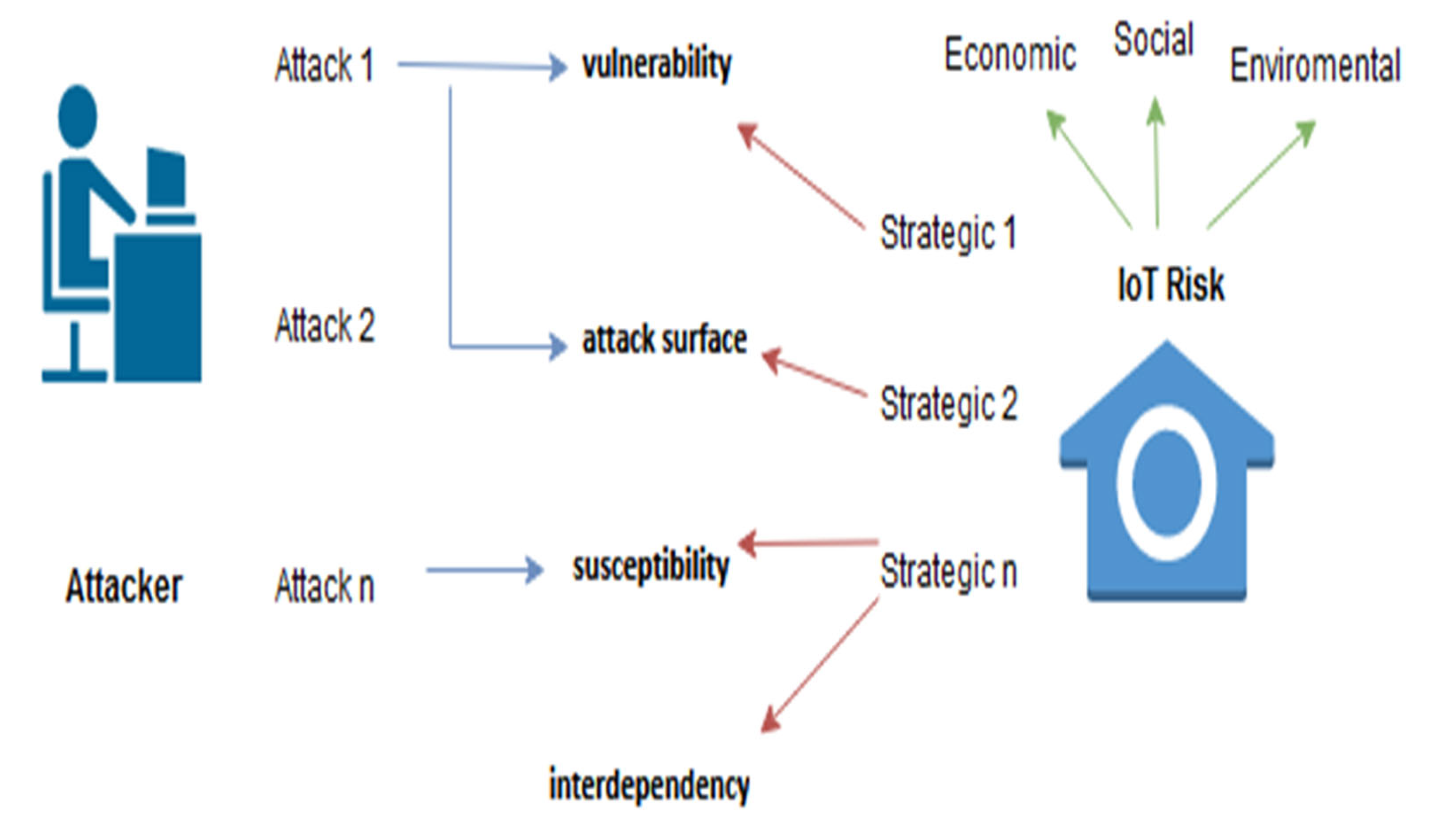
| Vulnerabilities | The IoT device may have vulnerabilities in its layers (three on the ITU model). Therefore, the vulnerability value of an IoT model represents the overall value of all contributions in each layer. |
| Type of attack | Different types of attacks can compromise the confidentiality, availability and integrity of IoT devices. |
| Attack surface | The attack surface will be conditioned by the inherent organization characteristics in which the IoT solution has been implemented. The attack surface includes entry/exit points, transmission channels, protocols and data used in the IoT model layers (three layers in the ITU case). The number of used IoT devices can also increase the attack surface due to the growing number of entry/exit points, channels, protocols and data. |
| Interdependency | The IoT device interacts with different layers’ protocols and technologies employed on the IoT system. The IoT device serves to build solutions that have a social, economic and environmental impact on the organization’s domain or pillar. Interdependency is driven with other IT/OT systems or IoT systems to implement the required functionalities. This interdependency between domains and systems increases the attack’s surface. |
| Severity | The severity will depend on the confidentiality, availability and integrity impact of the operations and information handled by the IoT device. The severity and security components impact (CIA) will depend on the target and type of attack. For example, an MITM attack will be focused on confidentiality, while a DoS attack will be focused on availability. The IoT device security protection–CIA will depend on the security requirements arising from the inherent characteristics of the domain or pillar. The vulnerability’s presence can increase the likelihood of a significant impact on security components during an attack. |
| Application domain | The attack on IoT devices could affect economic, social and environmental operations. The domain or pillar requires certain security configurations, and it may have inherent vulnerabilities. The characteristics of the domain or location may increase the attacked IoT device’s susceptibility. |
| Scalability | The behavior of the security attack may be conditioned by the IoT device’s dependency on other IT/OT systems. The attack could come from IT/OT to the IoT, or vice versa. This could increase the attack’s scalability. A higher number of devices could also increase attack scalability. Previous episodes could generate higher-impact attacks. |
| Susceptibility | The attack susceptibility is linked to the IoT device’s susceptibility. The IoT device may have components in different layers (according to the ITU model: three layers), which could increase the attack susceptibility due to extra entry and exit points. The systems’ interdependence could also affect the susceptibility. Exposure to a higher number of attacks and a shorter time between them can negatively affect equipment susceptibility. |
| Uncertainty | The security attack’s effect on IoT systems can have a random behavior depending on different variables, such as attack transmission through IoT devices. There is a non-deterministic behavior to the attack because it is not possible to precisely establish the security condition of the IoT device or IT/OT system at the time of the attack. |
| Nodes | Nodes Status |
|---|---|
| Vulnerabilities |
|
| Attack surface |
|
| Interdependency |
|
| Application domain |
|
| Susceptibility |
|
| Nodes of Application Domain | Nodes Status |
|---|---|
| Domain | (1) impact; (2) no impact |
| Pillar | (1) impact; (2) no impact |
| Economic | (1) impact; (2) no impact |
| Environmental | (1) impact; (2) no impact |
| Social | (1) impact; (2) no impact |
| Number Nodes | Computational Time (Seconds) |
|---|---|
| 1 | 12 s |
| 2 | 12 s |
| 3 | 12.5 s |
| 4 | 15 s |
| Case | Nodes | Description |
|---|---|---|
| VS | vulnerability; susceptibility | vulnerability = exist; susceptibility = exist |
| VI | vulnerability; interdependency | vulnerability = exist; interdependency = exist |
| VIAs | vulnerability; interdependency; attack surface | vulnerability = exist; interdependency = exist; attack surface = hackable |
| VSAsI | vulnerability; susceptibility; attack surface; interdependency | vulnerability = exist; susceptibility = exist; attack surface = hackable; interdependency = exist |
| VSI | vulnerability; susceptibility; interdependency | vulnerability = exist; susceptibility = exist; interdependency = exist |
| IoT Factors (Input Variables) | Impact (Output Variables) | |||||
|---|---|---|---|---|---|---|
| Vulnerability | Susceptibility | Attack Surface | Interdependency | Economic | Social | Environmental |
| 70% | 50% | 60% | 60% | 70.77% | 63.98% | 55.90% |
| 100% | 50% | 50% | 60% | 73.12% | 66.04% | 57.66% |
| 100% | 100% | 50% | 60% | 76.56% | 69.08% | 60.26% |
| 100% | 100% | 100% | 60% | 77.91% | 70.25% | 61.26% |
| 100% | 100% | 100% | 100% | 86.05% | 77.15% | 67.28% |
| 70% | 100% | 50% | 60% | 73.40% | 66.30% | 57.88% |
| 70% | 50% | 50% | 100% | 84.86% | 76.22% | 66.43% |
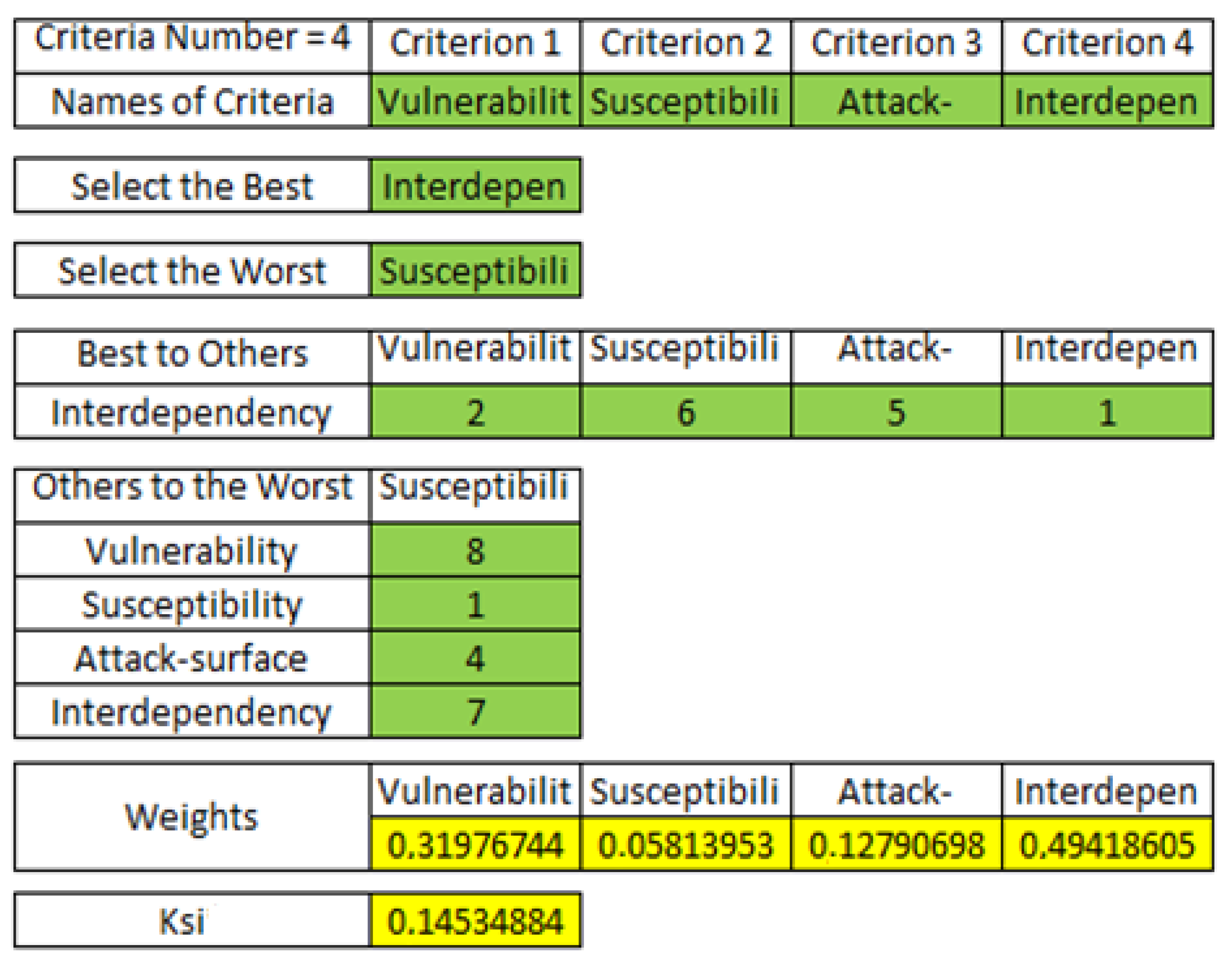
| Factors | Vulnerability | Attack Surface | Susceptibility | Interdependency | IoT Risk Security |
|---|---|---|---|---|---|
| Weights | 0.32 | 0.06 | 0.13 | 0.49 | 6.19 |
| Values | 8 | 5 | 3 | 6 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Andrade, R.; Ortiz, I.; Cazares, M.; Navas, G.; Sánchez-Pazmiño, M.I. Defining Cyber Risk Scenarios to Evaluate IoT Systems. Games 2023, 14, 1. https://doi.org/10.3390/g14010001
Andrade R, Ortiz I, Cazares M, Navas G, Sánchez-Pazmiño MI. Defining Cyber Risk Scenarios to Evaluate IoT Systems. Games. 2023; 14(1):1. https://doi.org/10.3390/g14010001
Chicago/Turabian StyleAndrade, Roberto, Iván Ortiz, María Cazares, Gustavo Navas, and María Isabel Sánchez-Pazmiño. 2023. "Defining Cyber Risk Scenarios to Evaluate IoT Systems" Games 14, no. 1: 1. https://doi.org/10.3390/g14010001
APA StyleAndrade, R., Ortiz, I., Cazares, M., Navas, G., & Sánchez-Pazmiño, M. I. (2023). Defining Cyber Risk Scenarios to Evaluate IoT Systems. Games, 14(1), 1. https://doi.org/10.3390/g14010001






