Abstract
We consider the problem of sharing the cost of connecting a large number of atomless agents in a network. The centralized agency elicits the target nodes that agents want to connect, and charges agents based on their demands. We look for a cost-sharing mechanism that satisfies three desirable properties: efficiency which charges agents based on the minimum total cost of connecting them in a network, stand-alone core stability which requires charging agents not more than the cost of connecting by themselves directly, and limit routing-proofness which prevents agents from profitable reporting as several agents connecting from A to C to B instead of A to B. We show that these three properties are not always compatible for any set of cost functions and demands. However, when these properties are compatible, a new egalitarian mechanism is shown to satisfy them. When the properties are not compatible, we find a rule that meets stand-alone core stability, limit routing-proofness and minimizes the budget deficit.
1. Introduction
Congestion is a form of negative externality to the networks of any size. These networks can include but are not limited to road networks, internet networks, telecommunication networks as well as utility power grid networks and other networks [1,2,3,4,5,6]. The emergence of congestion can be attributed to the instance in which a large number of selfish agents, each wishing to route traffic via one’s preferred links (or edges), without taking into account the actions of other agents in the network [7]. Such selfish routing behavior generates discrepancy between the socially optimal traffic pattern (minimizing overall delay or cost) and the selfish-routing behavioral outcome (also known as the non-cooperative Nash equilibrium). [8,9] suggest that the non-cooperative Nash equilibrium need not in general optimize the social welfare (minimizing overall delay or cost in this context). Indeed, the non-cooperative Nash equilibrium could generate a loss substantially higher than the social optimum. This implies that the discrepancy could cause some unwanted direct or indirect consequences such as network congestion, traffic paralysis as well as social welfare loss.
An earlier work by Roughgarden [8] investigates and quantifies the efficiency loss of the network performance due to the self-interested agents. The degradation is calculated by the worst-possible ratio between the Nash equilibrium and the social optimal traffic and is called the price of anarchy (POA) [8]. The closer the POA is to one, the less efficiency loss it generates between the Nash equilibrium and social optimum. Roughgarden shows that if the cost (latency) functions on the links in the network are linear, then the POA is equal to ; if the cost functions are cubic, then the POA is approximately 1.896; and if the cost functions are polynomials of degree where , then POA is a asymptotically equal to as 1. Finally, if the cost functions are unrestricted to any allowable class of functions (e.g., linear, quadratic, cubic, polynomials, etc.), then the POA is unbounded. These results indicate that the efficiency loss can be immensely large and the consequences generated by the selfish routing behavior can be extremely severe in the network.
In order to avoid such consequences, it is therefore important to manage the congestion of a network. In this paper, we consider a network with a set of nodes in which every node interconnects with at least one other node by a link. There is a variable congestion cost associated with each link that depends on the units of demands sent by agents. The cost may represent any maintenance cost or accessing fee of the links. Different links may have different congestion costs. There are a large number of self-interested agents who wish to route their traffic from an arbitrary node to another node using the links in the network. We assume the self-interested agents are interested in routing only via links that will incur the minimal cost or delay. In addition, we also include the possibility for a single agent performing a special type of strategic maneuver (or similarly, routing maneuver). The concept of strategic maneuver was first introduced by Dominique and Moulin [5], and followed by Moulin [10], who study mechanisms where coalition of agents in a large network can furtively create several alias and misreport themselves as several agents. Formally, that means an agent may report and route her traffic to the target node as two or more agents in hope of lowering her connection cost. To illustrate such scenario, we suppose there is an agent with initial node i and target node j. Then, she may report herself as two agents first connecting from node , then from node if she finds such strategic maneuver is less costly than connecting directly from node .
Unlike the decentralized networks such as road networks or internet networks, the networks being considered in this paper are operated in a centralized manner. We imagine there is a central authority that possesses the power to elicit the demand characteristics from all agents in the networks and is capable of computing and implementing the optimal traffic pattern at any time. Meanwhile, we imagine there is a centralized agency that will help satisfy the needs demanded by the agents at minimal total delay or cost. Since agents are self-interested, they need not have the incentive to reveal their true routing schemes. The centralized agency is therefore vulnerable to any misreports by individual units, or by a coalition of subgroup of units. Such strategic maneuver behavior will potentially distort the socially optimal traffic pattern (minimizing overall cost or delay) in the sense that links with relatively lower cost are more likely to be congested, which may in turns incurring higher total cost or delay.
Therefore, in order to prevent effectively such strategic maneuvers, thereby improving the performance of a network, there is a need to design cost-sharing mechanisms to charge on each agent in the network so that the action of strategic maneuver will make no difference in terms of lowering connection costs. Moulin calls any cost-sharing mechanisms or cost-sharing rules routing-proof if they are invulnerable to such strategic maneuvers [10]. Technically, it is not as difficult to find a routing-proof mechanism, if routing-proofness is the only constraint that we are aiming to satisfy. For instance, the simple average cost mechanism (AC) will do2. By splitting the total cost equally among all agents in the network, each agent is to pay a share of the average cost. As a result, any agent who intends to report as two or more agents will simply have to pay double or more of the average cost. Nevertheless, this mechanism may not be charging every agent or coalition fairly if the average cost exceeds the cost of a subnetwork meeting all connection needs of the group (stand-alone objections). This fairness-related constraint is known as stand-alone core stability and is the primary design constraint in the minimum cost spanning tree problem [10] and a variety of other problems.
Our work, therefore, has the objective to design or propose a cost-sharing mechanism satisfying the following three properties:
- Efficiency: the minimum total cost of connecting all agents to their target nodes;
- Stand-alone core stability: no groups of agents pay more than the cost of a subnetwork meeting all connection needs of the group;
- Routing-proofness: no agent can lower its cost by reporting as several agents along an alternative path connecting her target nodes.
1.1. Innovation of the Paper and Overview of the Results
While efficiency and stand-alone core stability are standard properties in the literature (see related literature section), the main innovation of this paper comes from studying the three properties together in a large economy with congestion. Previous work by Moulin [10] studied these properties in a model without congestion cost, where the cost associated with each link is fixed and the costs are independent of the units of traffic sent by agents. This assumption, while convenient, is not realistic in a variety of networks such as traffic, telecommunication and other large and complex networks (e.g., the internet). Our paper extends the model introduced by Moulin [10] to the case with variable congestion costs that depend on the units of traffic being connected in our network. The adoption of variable congestion costs substantially increases the difficulty of computing the efficiency of a general network. In particular, computing the social optimum (efficiency) of a general network is Non-deterministic Polynomial-time-hard (NP-hard) [12], unless the cost functions satisfy certain conditions (e.g., linearity or all cost functions are identical in the network [12]). Thus, our work is sharply different from [10] where the minimum cost (efficiency) can easily be computed by applying a simple greedy algorithm [13].
The second innovation of the paper comes from studying the case where there are a large number of self-interested agents in the network such that each of them only controls a negligible fraction of the overall traffic (i.e., agents have zero mass). These types of assumptions are critical for the internet and other large an complex networks, where even if an agent reroutes in the network, then because the amount of traffic each agent controls is infinitesimally small relative to the overall traffic, the costs charged to agents should not be too sensitive and changing significantly. This assumption is also relevant for rerouting in airline networks, where agents wishing to fly from A to B, can instead buy two one-way tickets, from A to C and C to B, if proven cheaper than a direct ticket from A to B. One agent manipulating the airline system will have no effect on prices and a substantially large amount of population is needed for changes in prices to take effect. Furthermore, in practice, it is relatively hard to coordinate a large group of agents that change prices in a network. In order to address this feature, we introduce a new axiom, the limit routing-proofness, that adapts Moulin’s concept of routing-proofness to the case where agents are extremely small relative to the overall traffic. We study the limitation of such an axiom in a congestion-prone network. In particular, we provide the necessary and sufficient conditions for the existence of rules that satisfy limit routing-proofness along with efficiency and stand-alone core stability (Theorem 1).
A third innovation of the paper comes from actually introducing a mechanism that satisfies these three properties when they are compatible. Our mechanism builds on perhaps the most studied mechanism in the cost-sharing literature, the uniform rule [14,15], and adapt it to our network setting with congestion in a way that Limit routing-proofness is satisfied. In order to compute the outcome of the mechanism, we actually provide an algorithm to compute the prices that agents pay, and show that such prices coincide with the cost-shares of our new mechanism (Proposition 1).
1.2. Related Literature
The stand-alone core stability and efficiency are two traditional properties in the network literature [4,10,16,17]; while routing-proofness is a relatively more recent idea [5,10,18]. The predecessor of routing-proofness was first coined the axiom of no transit originated by Hanriet and Moulin in [5]. In [5], Hanriet and Moulin suggest two cost-allocation methods: private-cost and external cost methods that satisfy the axiom of additivity, sustainability and no transit. These methods work only for the case without congestion.
The closest paper to our work is Moulin [10], who studies a congestion-free network cost-sharing problem and where the no transit axiom is renamed as routing-proofness. The paper constructs two core stable and routing-proof cost-sharing rules: weighted Shapley value (WSH) and weighted spanning rule (WSP) together satisfying the stand-alone core stability and routing-proofness. The first family of the rules requires only that the connecting costs to be zero or one, whereas the second family allows for arbitrary costs but requires a spanning traffic. As such, neither of these rules work in our general congestion-prone setting.
Another related paper is a real-world application of routing-proofness by Dong, Guo and Wang [18]. In there, a highway toll pricing method is proposed to assign the toll charges to different types of agents in a linear network. The proposed method satisfies the stand-alone test for vehicles, cost recovery (for road sections with no cross-subsidizing) and a version of routing-proofness in the sense that no agents can reduce the toll charges by exiting and re-entering the highway consecutively [18]. In contrast with the papers above, the model presented in [18] is a congestion-prone network rather than congestion-free, but the proposed method only works in a linear network, whereas our networks would typically have cycles, and that is where the strength of our routing-proofness property comes from.
Related work also comes from the cost-sharing literature on the implementation of efficient costs. Juarez and Kumar [2] discuss the appropriateness on the implementation of various efficient cost-sharing mechanisms when agents choose their paths strategically as if they are in a routing game. A comparison of different classes of mechanisms such as the average cost mechanism, proportional to stand-alone mechanism, (weighted) egalitarian mechanism and the Shapley mechanism is done. It is important to note that the paper does not deal with routing-proofness issues, and as such, all the mechanisms studied there fail to meet our test.
Other implementation work include Hougaard and Tvede [19,20], who characterize cost-minimizing networks at the equilibrium of games by changing the announcement rule. The sequential sharing of costs and profits is studied axiomatically in Juarez et al. [11]. Kumar [21] also investigates secure implementation in cost-sharing models without congestion, while Hougaard et al. [22] study the sharing of profits in trees and Moulin et al. [23] study the division of the costs/profits of non-redundant items. In contrast with this literature, our work is the first to address from an axiomatic view the division of costs in congestion-prone networks by atomless agents.
2. The Model
A network cost-sharing problem (or simply a problem) is a triple , where is a network with finite set of nodes and a finite set of undirected links connecting such nodes. is a vector of cost functions associated to each link, where the cost function associated to link is strictly increasing and strictly convex. The vector is the traffic demand associated to each link, where representing the units of traffic demanded on link (i.e., represents the mass of the agents interested in connected the two nodes of link ). We denote by the set of all network cost-sharing problems.
For an arbitrary network cost-sharing problem , the link will be simply denoted by i if there is no confusion. Given the cost function associated to link i, we denote by the average cost associated to such link. Let be the set of all feasible paths without cycles that connect link i in the network.3
Definition 1.
(a) Given a path k and , we denote by such that if and if .
(b) Given any link and a demand for that link, a connection vector generates demand if there exists non-negative weights such that and .
(c) Given demands , a connection vector is feasible if for every link there exists a connection vector that generates demand such that .
While agents demanding link i are interested in connecting the nodes of such link, this connection can be achieved directly via link i or indirectly via alternative paths connecting link i. In particular, the demands of traffic on link i can be split into multiple alternative paths where each particular path indirectly connects link i (part (b) in definition above). A connection vector is said to be feasible if it is the sum of all these paths.
Definition 2.
The total cost (or simply a cost) of a feasible connection vector is .
With each element represents all possible amounts of traffic on link i, the total cost of connecting all agents with connection vector is the sum of each cost function evaluated at for all .
Recall that we are in a centralized setting where the planner has the ability to select the paths of some agents demanding a given link. A natural objective for the planner is to select a path that minimizes the cost. This is incorporated in the following definition.
Definition 3.
Given a set of demands , a feasible connection vector is efficient if for any other feasible connection vector , we have .
We say that a feasible connection vector of a given set of demands is efficient if there exists a feasible connection vector such that the total cost evaluated at is always less than or equal to the total cost evaluated any other connection vectors . Such connection vector will generate the least cost (also referred as efficient cost) of serving all the agents in the network.
Definition 4 (Mechanism and efficient mechanism).
(a) A cost-sharing mechanism (also called rule or solution) is a continuous function ξ that allocates a set of cost shares for the use of every link at every network cost-sharing problem. (b) A cost-sharing mechanism is efficient at problem P if it divides the efficient cost among agents:
where is the efficient cost at a problemP.
We focus on a mechanism that allocates payments based on the demands of single links. That is, the planner cannot distinguish the names of agents who demand the same link. This is a standard assumption in the cost-sharing literature. An efficient cost-sharing mechanism is a centralized mechanism that meets the demands efficiently and redistribute this cost based only on the demand of every link. Thus, the sum of the charges assigned by the mechanism, when multiplied by the demands of each link, is equal to the efficient cost at a given problem.
Definition 5 (Stand-alone core stability).
Consider a network cost-sharing problem . A cost-sharing mechanism ξ satisfies the stand-alone core stability at if for any link i, we have that .
Definition 5 ensures the absence of stand-alone objections from agents caused by overcharging from the implemented mechanism. This constraint plays an important role in terms of fairness to prevent agents from being charged more than the cost of the links they actually demanded. Moreover, it also helps to prevent agents who demand inexpensive links from subsidizing those who demand expensive links in a network.
Definition 6 (Limit routing-proofness).
Consider a network cost-sharing problem . A cost-sharing mechanism is limit routing-proof (LRP) at P if for each link i, and each path that connects link i we have that:
Limit routing-proofness prevents agents from routing their demand along alternative paths that may also meet their demand. In particular, at a problem P, by Equation (1), an agent demanding link i pays . If such an agent decides to demand an alternative path that also connects i (by posing as separate agents along path ) his charge will be , which is not smaller than under limit routing-proof (LRP).
3. Efficiency, Stand-Alone Core Stability and LRP
The trade-off between stand-alone core stability and incentive compatibility (here, interpreted as routing-proofness) for efficient mechanisms has already been identified in the literature. Indeed, in a related network model where the connection demands of agents need to be met, Juarez and Kumar [2] study two mechanisms: the average-cost mechanism (AC) that divides the cost of the efficient network equally among all the agents and the proportional to stand-alone mechanism (PR) that divides the cost of the efficient network in proportion to the cost of their demands.4 In our setting, the AC mechanism meets LRP, as any agent pays the same cost-share regardless of the link demanded, thus an agent splitting their demand in two or more links will pay twice or more their cost-share. Unfortunately, it is easy to see that AC does not meet the stand-alone core stability, as it might happen that agents demanding a very inexpensive link cross-subsidize agents demanding very expensive links. PR is an exact opposite situation, meeting stand-alone stability but failing to meet LRP. Therefore, neither of them meet our three objectives. Other traditional mechanisms, like Aumann–Shapley, also fail to meet our demanding LRP. Therefore, in addressing the compatibility between stand-alone core stability, efficiency and limit routing-proofness, new mechanisms need to be developed.
One of the most studied rules in the cost-sharing literature is the uniform rule [14,15,24], which is a variation of AC that respect stand-alone core stability. This rule can be trivially adapted to our network setting by considering the cost of each link as the demand of the agents.5 Both the uniform rule and AC divide the total cost of the network across all agents, however, their similarity begins to diverge when the charges reach the threshold of the stand-alone cost of a link (presumably the smallest stand-alone cost first). In that case, AC will disregard the stand-alone cost and continue increasing charges to agents on each link i equally without bound. In contrast, the uniform rule will stop assigning charges to agents whose links have reached their stand-alone costs. The remaining cost will then be covered by the links in which the stand-alone costs are yet to be reached. Note that this characteristic will definitely preserve the property of stand-alone core stability. Unfortunately, the uniform rule does not meet LRP. The next section provides a variation of the uniform rule that meets LRP, stand-alone core stability and efficiency, whenever possible. We call it the egalitarian mechanism.
3.1. A New Egalitarian Mechanism
Given a network cost-sharing problem , our ultimate objective is to find a cost-sharing mechanism such that the set of cost shares allocated by the mechanism will be efficient, limit routing-proof and core stable. In order to achieve that, we formulate the network cost-sharing problem along with the constraints into a set of system of equations.
We denote the payment charged to each agent on link i. Other variables are defined exactly the same way as the model in Section 2. represents the efficient cost of the network computed as a function of . We express efficiency in this form because computing the efficiency (social optimality) of a network is generally a NP-hard problem.6
Equation (2) requires that the sum of the charges, when multiplied by the demands over all links is exactly equal to the efficiency of the network. In particular, this constraint represents the efficiency property.
Equation (3) describes the stand-alone core stability for all agents demanding link i. Essentially, this constraint says that the amount of assigned charges to each agent on link i should never exceed the cost of connecting the target pairs by themselves via link i.
Equation (4) represents the limit routing-proofness constraint for a general network. Recall that for any link i, is the set of all feasible alternative paths that connect link i. The limit routing-proofness constraint then implies that the charge on link i must be less than or equal to the sum of for on all possible paths 7.
Equation (5) is an obvious one, which says that the cost-shares assigned to agents must be greater than or equal to zero. The systems (2)–(5) might have multiple solutions or they might not have any, is it will be shown in the following sections.
Definition 7 (Egalitarian solution at λ*).
Consider a parameter . The egalitarian solution at , denoted by , assigns at the network cost-sharing problem the set of cost-shares such that the cost share of link is determined by
This solution achieves revenue equal to .
Note that is a well defined cost-sharing solution, as there exists a unique set of values that satisfy Equation (6). They can be easily computed by starting for small values, say at , at which point the solution returns for all . As we increase the value of , the stand-alone constraint () or LRP constraints () bind. The formal computation of this rule is described in the next section.
By construction, egalitarian mechanism (EG), meets stand-alone core stability and LRP, but it may not be efficient. Indeed, the revenue generated by EG equals to which may be smaller or larger than . Clearly, is non-decreasing in , and it may be that is actually constant for a large value of . Indeed, consider two values and such that for all i. Under , the payment to the agents along link i is not larger than . Thus, any increases to will also hit the same stand-alone constraints, and the cost-shares of the agents remain unchanged.
From the analysis, the maximum revenue generated under EG occurs when . We denote by such a maximum revenue. Note that if the revenue , then by the continuity of , we can always find one such that . This will generate an allocation EG8 and it will be called the egalitarian solution (). Note also that when this egalitarian solution exists, it will be efficient, core stable and limit routing-proof.
The computation of EG above is similar to the computation of the uniform rule, except for the additional LRP constraints, , in Equation (6). Such a variation substantially changes how EG assigns cost shares to the agent in different links. In contrast with the uniform rule, the EG mechanism proposed in this paper might not exists for an arbitrary network cost-sharing problem P. The existence of EG depends on whether the last stand-alone cost being reached can cover the loss incurred by the replacement of the limit routing-proofness constraints. We see this in the next sections.
3.2. A Numerical Example of EG
In this section, we will provide a step-by-step numerical example illustrating how EG allocates charges to agents. Consider the network in Figure 1 and a demand . That is, a total of 11 units of traffic were demanded: two units are demanded on link 1; six units were demanded on link 2; and three units were demanded on link 3.
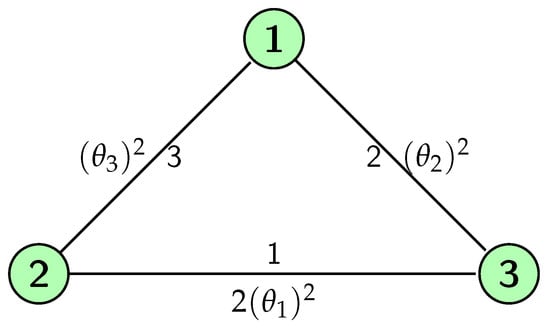
Figure 1.
A simple network with three nodes.
The computation of the efficient allocation for this network requires no re-routing of traffic, therefore providing an efficient cost equal to .
The stand-alone cost for each link is:
Under EG, we have:
Solving the above system simultaneously will give us an egalitarian solution, if there exists one. We attacked this problem by gradually increasing until the first stand-alone constraint for is reached. This happens when .
Note the fact that the stand-alone constraints of and are still non-binding implies . So by (11), suppose for all , we check if (11) is satisfied:
Obviously, does not achieve efficiency. Hence, we must continue increasing on and while leaving as its stand-alone constraint is reached.
Next, we applied the same logic and continue increasing . It is easy to see that the next stand-alone constraint being reached will be . That is, when .
We know that and the stand-alone constraint of is still non-binding when . This implies . Thus, the minimum value in (11) will never be the limit routing-proofness constraint. We check (11),
Again, efficiency is still not attained with and . Leaving and , we have by efficiency,
Recall that (12) implies
In this case, we need to be cautious about the limit routing-proofness constraint. If it happens that the minimum value is obtained from the limit routing-proofness constraint, then there will be no egalitarian solution satisfying Equation (11).
We proceed to check if satisfies all the constraints given by Equations (7)–(13).
Hence, we have found an egalitarian solution EG such that efficiency, stand-alone core stability and limit routing-proofness are simultaneously satisfied. Interestingly, since the demands and are precisely the optimal allocations that generates the total minimum cost, the stand-alone core stability and efficiency force the egalitarian solution for all .
3.3. An Example for Problem Where EG does not Exists
Consider the network in Figure 2 and . That is, where one unit of traffic demand link 2 ↔ 3, one unit of traffic demand link 1 ↔ 3; and four units of traffic demand link 1 ↔ 2.
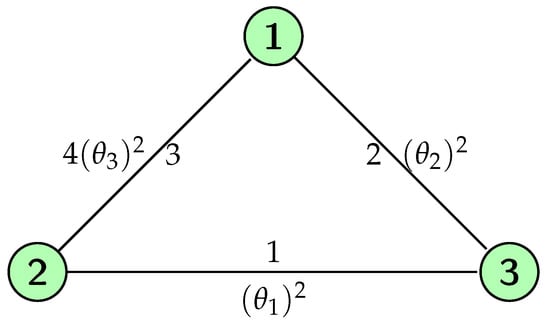
Figure 2.
A simple network with three nodes and three links.
Efficiency requires units of traffic demanding link 1 ↔ 2 to be routed along the alternative route on links 1 ↔ 3 and 3 ↔ 2. This will generate an efficient cost equal to
In order to compute the stand-alone cost note that
Thus, if the central authority decides to impose a personalized charge to every agent, then it can impose at most a total amount of $1 to each agent on link 1 and 2; $16 to each agent on link 3.
For EG to exists, it needs to recoup the efficient cost . As we increase , the stand-alone constraints of link 1 and 2 are reached immediately followed by link 3. That is, = 1 for .
Hence, by efficiency, we have that
Thus, the charges assigned to each agent under EG are . Note that this solution satisfies stand-alone core stability and efficiency but it fails to meet the limit routing-proofness constraint, as the agents demanding link 3 would prefer to pose as two agents demanding links 1 and 2.
4. The RP Algorithm
We now turn our focus on investigating the necessary and sufficient conditions for the existence of an efficient, core stable and limit routing-proof egalitarian solution. To derive those conditions, we introduce an algorithm called the RP algorithm.
Definition 8 (The RP algorithm).
Given a problem P, the RP algorithm assigns at any step a price to every link in the network. This price can be of two types: temporary or permanent. We define a semi-cycle to be a cycle of links such that all but one of the links have assigned permanent prices.
- Step 0. We start from a network N and assign temporary prices to every link i in the network. Continue to step 1.
- Step 1. The algorithm ends when all the assigned prices are permanent. For a given set of prices, replace the smallest temporary price with a permanent price of the same value. The rest of the prices are unchanged. If the new prices generate a semi-cycle, then we continue to step 2. Otherwise, we repeat step 1 with the new prices.
- Step 2. For every semi-cycle with link i that has attached a temporary price , we replace their temporary price with a new temporary price Moreover, if every path is a semi-cycle, then becomes permanent. We continue to step 1 with the new set of prices.
The algorithm finishes in at most steps, where s is the number of links in the network, since every time that step 1 runs, a price moves from temporary to permanent.
By assigning temporary prices at the average cost in step 1, the RP algorithm ensures for stand-alone core stability. On the other hand, replacing a new temporary price either with the minimum of the average cost, or the sum of the prices on the alternative paths of a semi-cycle respects the LRP property.9
Note that the construction of the RP algorithm and EG are similar, but their objectives and operations are slightly different. To be precise, the RP algorithm always finds the feasible and maximal prices that it can charge the agents in order to meet the LRP constraint. This is in contrast with EG where it always allocates the minimal prices to agents subject to their stand-alone costs. Such discrepancy is due to the nature of the operation of EG and the RP algorithm. The RP algorithm always starts from the maximal prices possible (e.g., starts from the stand-alone prices) and solves the problem backwards, whereas EG attacks the problem from the lowest prices possible while gradually increasing it and stops when efficiency is reached.
Example of RP Algorithm
We provide a numerical example showing how prices are computed under the RP algorithm.
Consider an arbitrary network with the links numbered as in Figure 3a. Without loss of generality, suppose the average costs are given as in Figure 3b. By the RP algorithm, we start assigning a temporary price—average cost to each link until every link has a temporary price. For instance, we assign to link 1 and to link 2, etc. Starting from the smallest temporary price, , will be replaced with a permanent price followed by the second, third smallest temporary prices and so forth at every point in time until the first semi-cycle is formed.
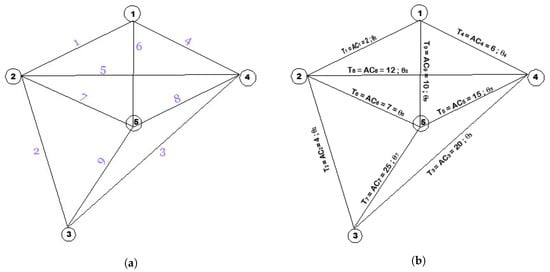
Figure 3.
Step 1 of RP algorithm. (a) A general network with 5 nodes and 9 links numbered as shown; (b) A network with assigned temporary prices.
Note that the first semi-cycle is formed by links 1, 2 and 4. Thus, the temporary price on link 3 is replaced by a new temporary price = 12. This new temporary price will become a permanent price only if all the ascending smaller prices are replaced with permanent prices. Once the price is replaced, we continue to replace the next smallest price, which is price of link 7 in this case. In there a second semi-cycle is formed by links 2 and 7 and we replace the temporary price with .10
Continue replacing in this fashion and ensuring all the semi-cycles are extracted until each temporary price becomes permanent price as shown in Figure 4b.
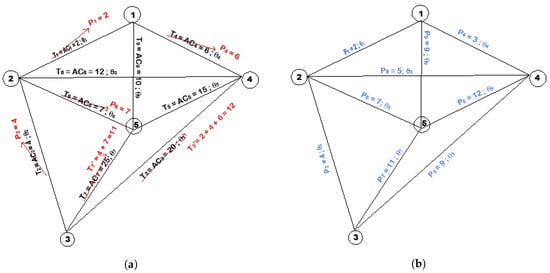
Figure 4.
Step 2–4 of RP algorithm. (a) In the process of replacing temporary prices to permanent prices; (b) The RP algorithm ends when all links have permanent prices.
5. Main Results
We now turn to the main results of this paper. As mentioned in the previous section, our results will rely heavily on the application of RP algorithm.
Proposition 1.
For any network cost-sharing problem the prices given by the RP algorithm coincide with EG.
The proof is in Appendix A.
The RP algorithm takes the permanent price for all i. If the minimum temporary price is for some , then the RP algorithm will never replace any permanent prices less than that. Therefore, the revenue generated under these prices and demands is going to be maximal. That is, RP merely searches for the maximal prices that it can achieve while satisfying together the stand-alone core stability and limit routing-proofness.
On the other hand, EG also allocates charges to agents with respect to the stand-alone core stability and limit routing-proofness. It chooses, or controls the parameter where the revenue target (this might include efficiency) is just achieved and stops. Hence, if the revenue target is precisely the maximal revenue that is achievable by the RP algorithm, then the allocation EG coincides with the price vector simply because EG and RP algorithm are constructed in an identical way. Indeed, since the RP algorithm always searches for the maximal revenue that it can achieve in a network, the total charge (resp. total revenue) allocated (resp. collected) by EG can do no better than that maximal revenue. Thus, the maximal revenue provided by the RP algorithm is an upper bound for which EG can achieve in a network.
Theorem 1.
Consider an arbitrary network cost-sharing problem.
- a.
- Let agent j* be the last agent in the RP algorithm. A stand-alone core stable, efficient and limit routing-proof price vector exists if and only if one of following conditions is satisfied:
- i
- , where is the set of all feasible alternative paths of ;
- ii
- b.
- The egalitarian solution exists if and only if either condition (i) or (ii) is satisfied.
The proof is in Appendix A. Theorem 1a states the necessary and sufficient conditions for which the price vector is core stable, efficient and limit routing-proof. Note that condition (ii) is implied by condition (i), but added as a reference. On the other hand, part (b) tells us that the egalitarian solution is guaranteed to exist if either condition (i) or (ii) hold.
Corollary 1.
Given a general network, suppose that the average cost satisfies the (generalized)11 triangle inequality, that is,
for any demand of link i, then the egalitarian solution exists.
The proof is in Appendix A. Note that this condition is sufficient but not necessary for the existence of egalitarian solution. To see this, consider the following network.
In Figure 5a, the average costs are given by $3, $10 and $5 for link 1, 2, 3 respectively. Clearly, the triangle inequality is not satisfied since $5 + $3 = $8 < $10. Under the RP algorithm, is replaced with a new permanent price taken from the sum of $5 + $3 = $8. We see that there exists an egalitarian solution whenever . In other words, no solution will be found if . Hence, (10) is a sufficient condition rather than a necessary condition.
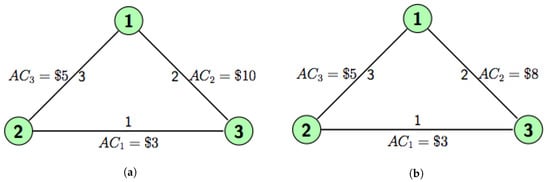
Figure 5.
An example illustrating the existence of egalitarian solution. (a) A network with assigned average costs. (b) The prices under routing-proof (RP) algorithm.
6. Conclusions and Open Questions
We have introduced the study of routing-proof mechanisms for network cost-sharing models in the presence of atomless agents for an arbitrary set of cost-functions. We have shown that two canonical properties in the cost-sharing literature, efficiency and stand-alone core stability, may be compatible with limit routing-proofness. In order to do so, we have introduced a new mechanisms, the egalitarian mechanism, as a natural selection when these three properties are compatible.
We find three critical open questions. The first pertaining to the study of mechanisms when agents are not atomless. Our work only provides a glimpse of the restrictions needed on the cost-functions to achieve efficiency, stand-alone core stability and a more general routing-proofness constraint where the payment allocated to agents may change depending on the mass rerouted.
The second question pertains to the demands of agents. Our work has focused on agents demanding single links between any pair of nodes. However, by extending the model into demanding multiple links should enhance the applicability of EG and related mechanisms.
Finally, our work has only shown the existence of a mechanism meeting efficiency, stand-alone core stability and limit routing-proofness, but has not provided a full characterization of a mechanism. More work is needed to develop a characterization using axioms in the spirit of limit routing-proofness.
Author Contributions
R.J. and M.W. conceptualized the paper, found the results and wrote them. They contributed equally to the study.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. Proofs
Appendix A.1. Proof of Proposition 1
Proof.
Let be the prices given by the RP algorithm and let be the EG solution. Fix a problem P and let be the maximal revenue target achieved by EG and the RP algorithm, we will show that . Without loss of generality, suppose that the average cost functions satisfy .
Solving by RP algorithm: we assign temporary prices on each link i. At each point in time, the smallest temporary price is replaced by a permanent price, i.e., until any semi-cycle is formed. Let j be the last link that completes the semi-cycle. We replace by .
Case 1: if , then we have:
Subcase 1: if is the next smallest , then becomes .
Subcase 2: if is not the next smallest , then we continue replacing other temporary prices with until either becomes the smallest or another semi-cycle forms.
Note that if is the smallest price, then becomes .
Case 2: if , then we have:
Subcase 1: if is the next smallest price, then becomes .
Subcase 2: if is not the next smallest price, then we continue replacing other temporary prices with until becomes the smallest price or another semi-cycle forms.
Together, this implies that and or .
(Remark: If another semi-cycle forms before becomes the smallest price at some point in time, then we can follow the same proof as described above.)
Now, we solve P by EG. From Equation (6), we know that . As , is reached, followed by until a semi-cycle is formed. Then, for all i before a semi-cycle is reached. Suppose link j is the last link that completes the semi-cycle. Then we have,
Case 1: If , then .
Case 2: If , then .
Hence, we have that before any semi-cycle forms. Since EG is constructed as the same way as the RP algorithm, i.e., . Hence, ; on the other hand, . Thus, since for all . □
Appendix A.2. Proof of Theorem 1
Proof.
Part (a): ⇒) We first prove the sufficiency part, i.e., suppose a stand-alone core stable, efficient and limit routing-proof solution exists, then we have .
Step 1: to prove the sufficient part, we need to show the following first. Let be some prices on a limit routing-proof and core stable allocation. Then for any , we have .
Note that the temporary price by the stand-alone property. We see that at any point in time, the RP algorithm will replace a permanent price on link i. First, note that prior to the formation of a semi-cycle, and then it becomes a permanent price . Once a semi-cycle is formed, we replace with a new temporary price and for all l in the path . Now, we need to show that for all i.
Note that since and . Since , we have:
Case 1: If .
Case 2: If . where the last inequality holds by limit routing-proofness. Together case 1 and case 2 imply . Continue checking in this fashion for all , we have that , as required.
Step 2: suppose a solution satisfies limit routing-proofness, stand-alone core stability and efficiency, then by step 1, we have .
.
Since for all where the last inequality holds by limit routing-proofness. By the stand-alone core stability, . Together, this implies , as required.
⇐) Now, we proceed to prove the necessity part. Note that by the construction of the RP algorithm, the allocation is core stable and limit routing-proof. By Proposition 1, we know that the prices given by the RP algorithm will coincide with EG, that is, . Thus, the only thing left to show is the efficiency. If we can show that , then egalitarian solution will be a solution that satisfies efficiency, stand-alone core stability and limit routing-proofness. By assumption, . By definition, . Hence, we have,
as desired.
Part (b): Suppose the egalitarian solution EG exists, then it is efficient, core stable and limit routing-proof. By Proposition 1, we know that the maximal revenue given by the RP algorithm is always an upper bound for which EG can achieve. Moreover, the RP algorithm respects stand-alone core stability and limit routing-proofness. Thus, if the egalitarian exists, then there must exist a price vector that is also efficient, core stable and limit routing-proof. Hence, by Theorem 1a, condition (i) or condition (ii) is satisfied.
Firstly, note that condition (i) clearly implies condition (ii). Secondly, if condition (ii) is satisfied, then we have that by Theorem 1. Hence, by proposition 1 and continuity, there exists such that when we slowly decrease the revenue target from to . This will generate exactly the egalitarian solution EG. □
Appendix A.3. Proof of Corollary 1
Proof.
Suppose without loss of generality that agents demand link i, EG starts charging to all agents. At any point in time, the stand-alone constraint of every link will be reached.
Without loss of generality, suppose the stand-alone constraint of link i is reached first, i.e., . By assumption,
This implies that agents on link i are charged at the lowest cost among all feasible alternative paths that connect link i, so agents will not have an incentive to reroute. Limit routing-proofness is trivially satisfied by the assumption. Note that satisfies the stand-alone core stability since . It also satisfies efficiency since agents on link i are being charged at the lowest cost.
Now, it remains to check the cases . Note that the assumption
holds for all , hence by the same reasoning, we can deduce that are also core stable, limit routing-proof and efficient. Now, without loss of generality, suppose the stand-alone cost of link s is reached last, then by efficiency,
The triangle inequality constraint assumed implies that,
Thus, each agent who demands link s is paying at , which essentially is the lowest cost among all other feasible paths. Hence, is also routing-proof, core stable and efficient. Therefore, EG has a solution such that every for all is limit routing-proof, core stable and efficient. □
References
- Han, L.; Juarez, R. Free intermediation in resource transmission. Games Econ. Behav. 2018, 111, 75–84. [Google Scholar] [CrossRef]
- Juarez, R.; Kumar, R. Implementing efficient graphs in connection networks. Econ. Theory 2013, 54, 359–403. [Google Scholar] [CrossRef]
- Frederick, H.; Gerald, L. Introduction to Operations Research; McGraw-Hill: Columbus, OH, USA, 2009. [Google Scholar]
- Moulin, H. Cost sharing in networks: Some open questions. Int. Game Theory Rev. 2013, 15, 1340001. [Google Scholar] [CrossRef]
- Dominique, H.; Moulin, H. Traffic-based cost allocation in a network. RAND J. Econ. 1996, 27, 332–345. [Google Scholar]
- Juarez, R. Group strategyproof cost sharing: The role of indifferences. Games Econ. Behav. 2013, 82, 218–239. [Google Scholar] [CrossRef]
- Melo, E. Congestion pricing and learning in traffic network games. J. Public Econ. Theory 2011, 13, 351–367. [Google Scholar] [CrossRef]
- Roughgarden, T. The Price of anarchy is independent of the network topology. J. Comput. Syst. Sci. 2003, 67, 341–364. [Google Scholar] [CrossRef]
- Fotakis, D.; Spirakis, P. Cost-balancing tolls for atomic network congestion games. In Proceedings of the 3rd International Conference on Internet and Network Economics (WINE’07), San Diego, CA, USA, 12–14 December 2007; pp. 179–190. [Google Scholar]
- Moulin, H. Pricing traffic in a spanning network. In Proceedings of the 10th ACM Conference on Electronic Commerce (EC09), Stanford, CA, USA, 6–10 July 2009. [Google Scholar]
- Juarez, R.; Ko, C.Y.; Xue, J. Sharing sequential values in a network. J. Econ. Theory 2018, 77, 734–779. [Google Scholar] [CrossRef]
- Chakrabarty, D.; Mehta, A.; Nagarajan, V. Fairness and optimality in congestion games. In Proceedings of the 6th ACM Conference on Electronic Commerce (EC ’05), Vancouver, BC, Canada, 5–8 June 2005; pp. 52–57. [Google Scholar]
- Joel, S. Linear Programming Note X Integer Programming; Mimeo University of California: San Diego, CA, USA, 2007. [Google Scholar]
- Sprumont, Y. The division problem with single-peaked preferences: A characterization of the uniform allocation rule. Econ. J. Econ. Soc. 1991, 59, 509–519. [Google Scholar] [CrossRef]
- Benassy, J.P. The Economics of Market Disequilibrium (No. 330.1/B45e); Academic Press: Cambridge, MA, USA, 1982. [Google Scholar]
- Bogomolnaia, A.; Holzman, R.; Moulin, H. Sharing the cost of a capacity network. Math. Oper. Res. 2010, 35, 173–192. [Google Scholar] [CrossRef]
- Dutta, B.; Mishra, D. Minimum cost arborescences. Games Econ. Behav. 2011, 74, 120–143. [Google Scholar] [CrossRef]
- Dong, B.; Guo, G.; Wang, Y. Highway toll pricing. Eur. J. Oper. Res. 2012, 220, 744–751. [Google Scholar] [CrossRef]
- Hougaard, J.L.; Tvede, M. Truth-telling and nash equilibria in minimum cost spanning tree models. Eur. J. Oper. Res. 2012, 222, 566–570. [Google Scholar] [CrossRef]
- Hougaard, J.L.; Tvede, M. Minimum cost connection networks: Truth-telling and implementation. J. Econ. Theory 2015, 157, 76–99. [Google Scholar] [CrossRef]
- Kumar, R. Secure implementation in production economies. Math. Soc. Sci. 2013, 66, 372–378. [Google Scholar] [CrossRef]
- Hougaard, J.L.; Moreno-Ternero, J.D.; Tvede, M.; sterdal, L.P. Sharing the proceeds from a hierarchical venture. Games Econ. Behav. 2017, 102, 98–110. [Google Scholar] [CrossRef]
- Moulin, H.; Laigret, F. Equal-need sharing of a network under connectivity constraints. Games Econ. Behav. 2011, 72, 314–320. [Google Scholar] [CrossRef]
- Juarez, R.; You, J.S. Optimality of the uniform rule under single-peaked preferences. Econ. Theory Bull. 2018, 1–10. [Google Scholar] [CrossRef]
- Hougaard, J.L. An Introduction to Allocation Rules; Springer: Heidelberg/Berlin, Germany, 2009. [Google Scholar]
| 1. | See [8] for more POAs of different classes of functions such as the quadratic, M/M/1 delay functions and M/G/1 delay functions. |
| 2. | The average cost mechanism has been used successfully in a variety of network problems, e.g., [2,11]. |
| 3. | A path is a sequence of consecutive nodes in the network. We say that a path has no cycles if the nodes do not repeat. We say that a path connects link i if the path starts in one of the nodes of link i and ends in the other. When there is no confusion, we also refer to a path by its links instead of its nodes. |
| 4. | For brevity, we do not repeat the formal definition of these mechanisms already discussed in Juarez and Kumar [2]. |
| 5. | See [2,25] for the application of the Uniform rules to network problems. |
| 6. | Moulin [4] suggests that if no simple algorithm can characterize the cost minimization outcomes, then we will have no choice but to drop the cost minimization requirement and turn to the exogenously given suboptimalities. |
| 7. | Note that if a simple triangular network is analyzed here, then the routing-proofness constraint is just a set of triangle inequalities. |
| 8. | If it happens that is the maximum revenue that EG can achieve, then and the allocation EG coincides with EG. |
| 9. | Similar to EG, the RP algorithm might not satisfy the efficiency property, but for any revenue (regardless of whether efficiency is achievable), it always generates prices that maximize the possible revenue. |
| 10. | Depending on the configuration of the networks, a temporary price may be replaced more than once before it finally becomes a permanent price. |
| 11. | Note that this does not necessary have to be a triangle, it can be a “n-cycle” inequality where n is the number of links in the cycle. |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).