Effectiveness Evaluation Method for Hybrid Defense of Moving Target Defense and Cyber Deception
Abstract
1. Introduction
- We propose a hybrid defense framework that combines MTD and cyber deception effectiveness evaluation models based on queuing theory, aiming to achieve an optimal balance among security, reliability, and defense costs by defining defense resource cost indicators.
- We develop an evolutionary game model to assess the impact of various combinations of MTD and cyber deception strategies on system security, resource overhead, and reliability. By treating MTD and cyber deception as competitive strategies regarding reliability and defense costs, the model aims to enhance system security while maintaining reliability and controlling defense costs.
- Validation of the analytic model through simulation and experimentation demonstrates that the method can accurately evaluate the effectiveness of the hybrid defense framework, which combines MTD and cyber deception.
2. Related Work
2.1. Mobile Target Defense(MTD) and Cyber Deception Hybrid Defense Framework
2.2. Methods for Evaluating the Effectiveness of MTD Techniques
2.3. Efficiency Evaluation of Hybrid MTD Technology
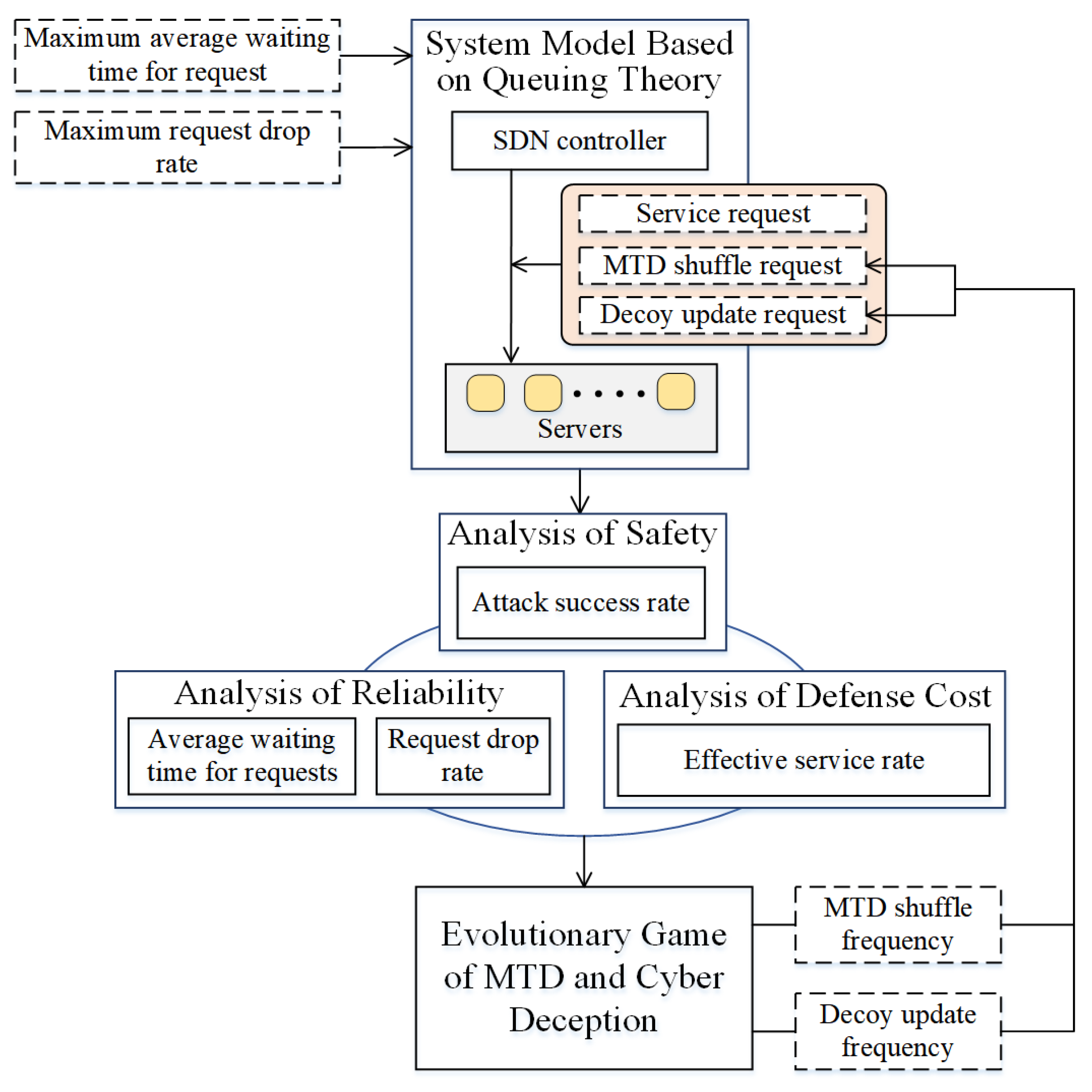
3. Hybrid Defense Evaluation Model
3.1. The Quantitative Model of MTD and Cyber Deception
3.1.1. MTD Shuffle Model
3.1.2. Cyber Deception Model
3.2. System Model Based on Queuing Theory
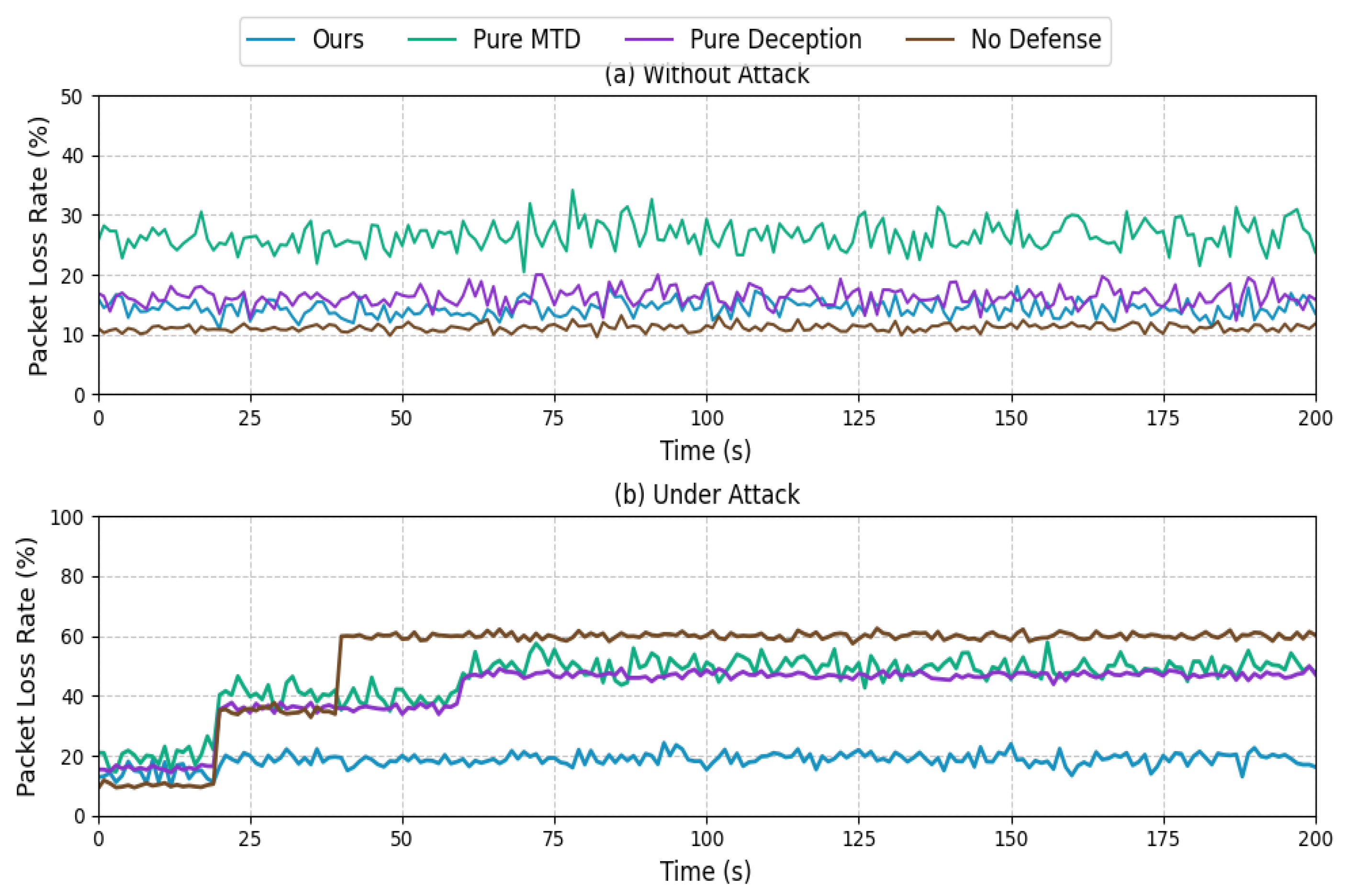
- Requests queued at the server will be discarded after waiting for .
- When the packet loss rate of the system reaches , we consider the system unusable.
- After performing MTD shuffle on the server, the connection will be interrupted, making the server temporarily unavailable and requiring waiting for time to restore the connection.
- The average processing time for service requests by the server is .
3.2.1. Effective Shuffle Interval
3.2.2. Effective Decoy Update Frequency
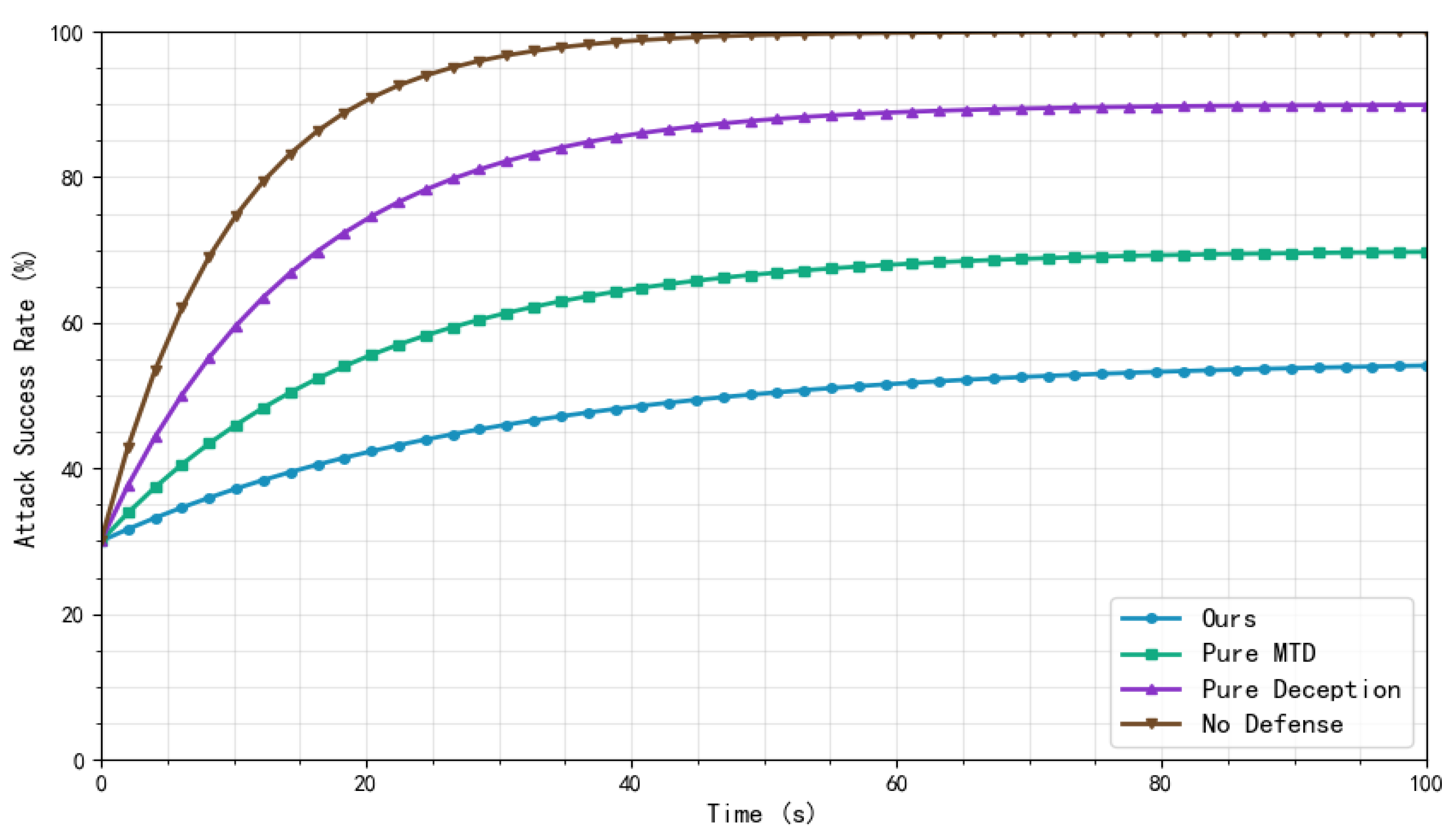
3.3. Analysis of Safety
- Static strategy attacks: In this attack type, the attacker continuously attacks until all targets are compromised. The base attack success rate increases linearly over time [30].
- Changing strategy attacks: In this case, the attacker constantly gathers information and adjusts the attack strategy to target specific vulnerabilities more precisely. The base attack success rate grows exponentially [31].
3.4. Analysis of Defense Cost
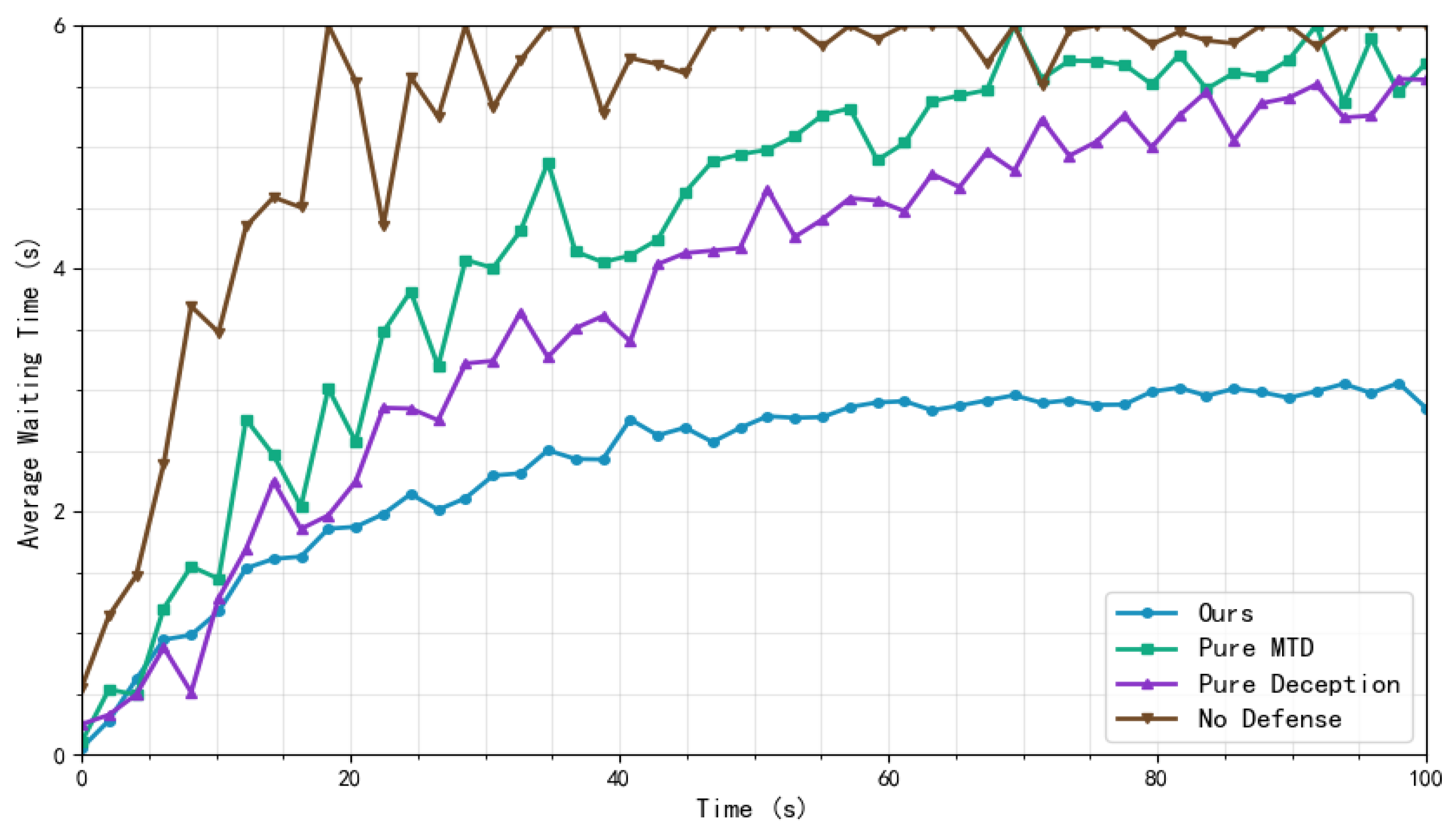
3.5. Analysis of Reliability
3.6. Evolutionary Game of MTD and Cyber Deception
3.7. Optimization Problem
3.8. MTD and Cyber Deception Collaborative Optimization Selection Algorithm
| Algorithm 1 MTD and Cyber Deception Collaborative Optimization Selection Algorithm |
| Input: Constraint thresholds (max drop rate), (max waiting time); system parameters ; strategy sets and |
| Output: (optimal MTD transform frequency), (optimal deception update frequency) |
| 1: Step 1: Initialize system parameters and strategy space 2: Initialize system parameters: ; 3: Initialize define strategy spaces: , ; |
| 4: Step 2: Calculate system state and attack success probability 5: For each strategy pair : 6: Compute parameters 7: |
|
8: Step 3: Construct payoff matrix 9: For each strategy pair : 10: . 11: if and then 12: . 13: else 14: . 15: end if 16: . 17: . 18: . |
|
19: Step 4: Replicator dynamics on 20: function REPLICATORDYNAMICS(Q, A) 21: . 22: For each strategy pair : 23: . 24: return 25: end function |
|
26: Step 5: Evolution to equilibrium and selection 27: Initialize with and ; set , and . 28: repeat 29: . 30: . 31: . 32: Project to simplex: set each , then renormalize so . 33: . 34: ; . 35: until or 36: Find indices such that is maximal. 37: return , . |
4. Experiment
4.1. Experimental Setup
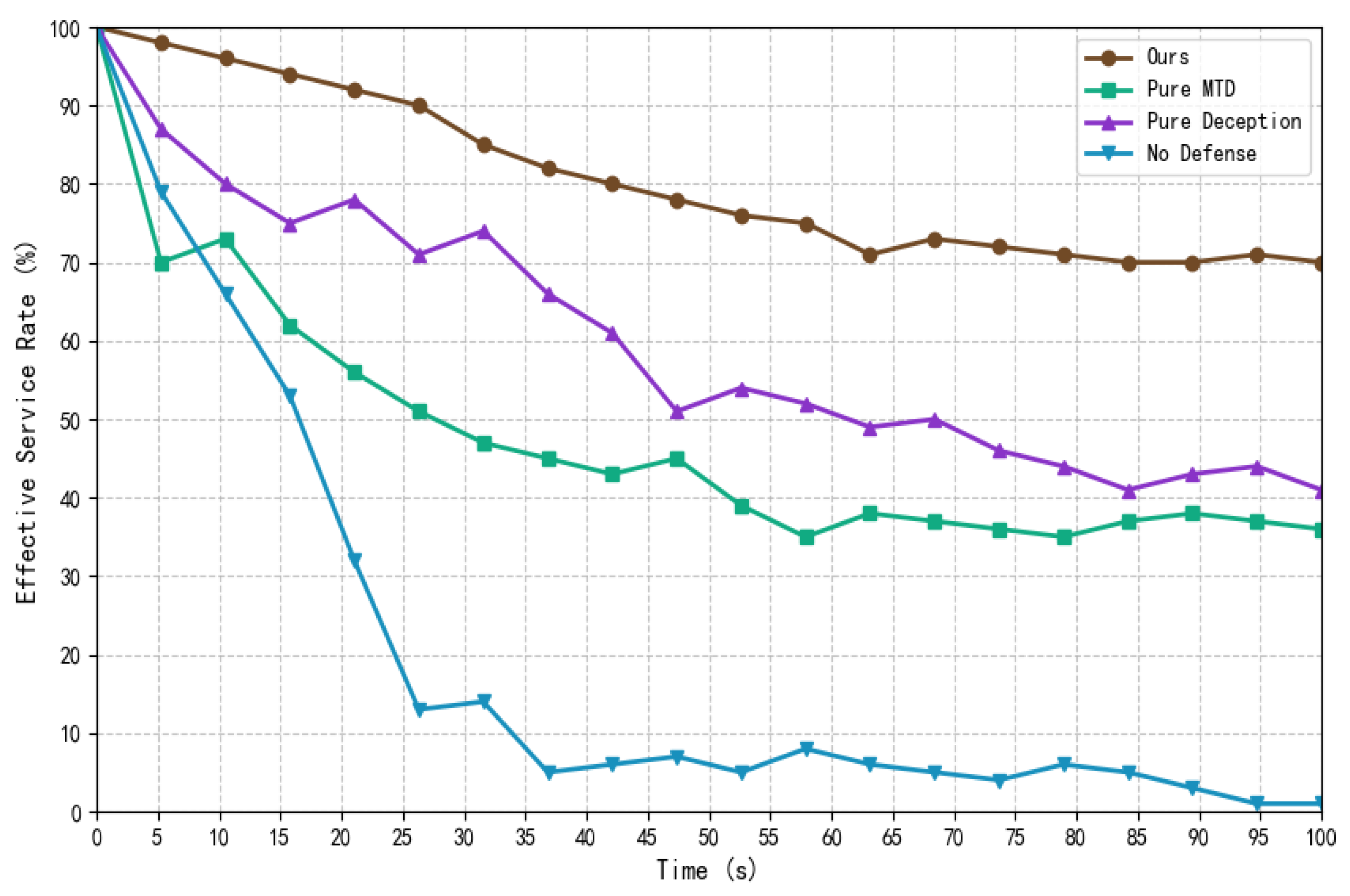
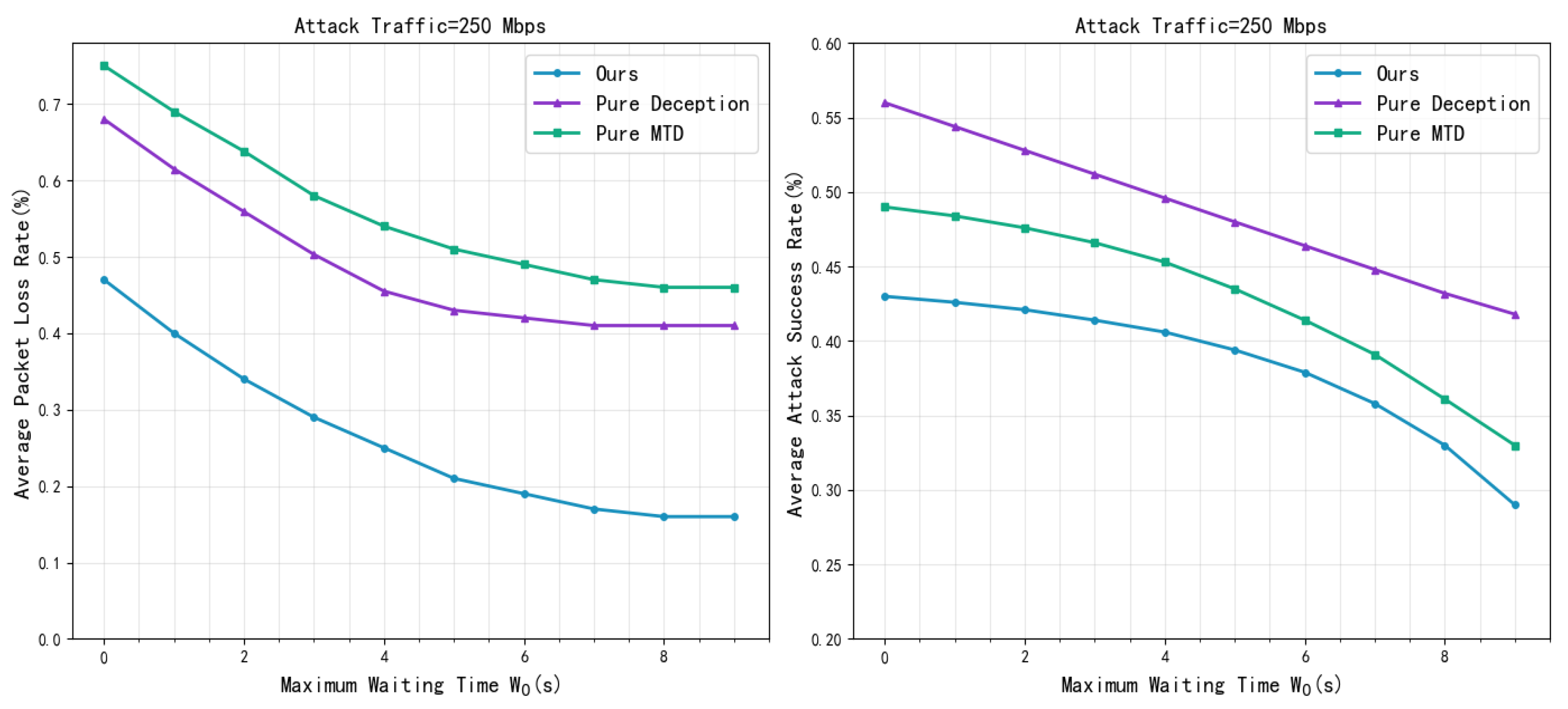
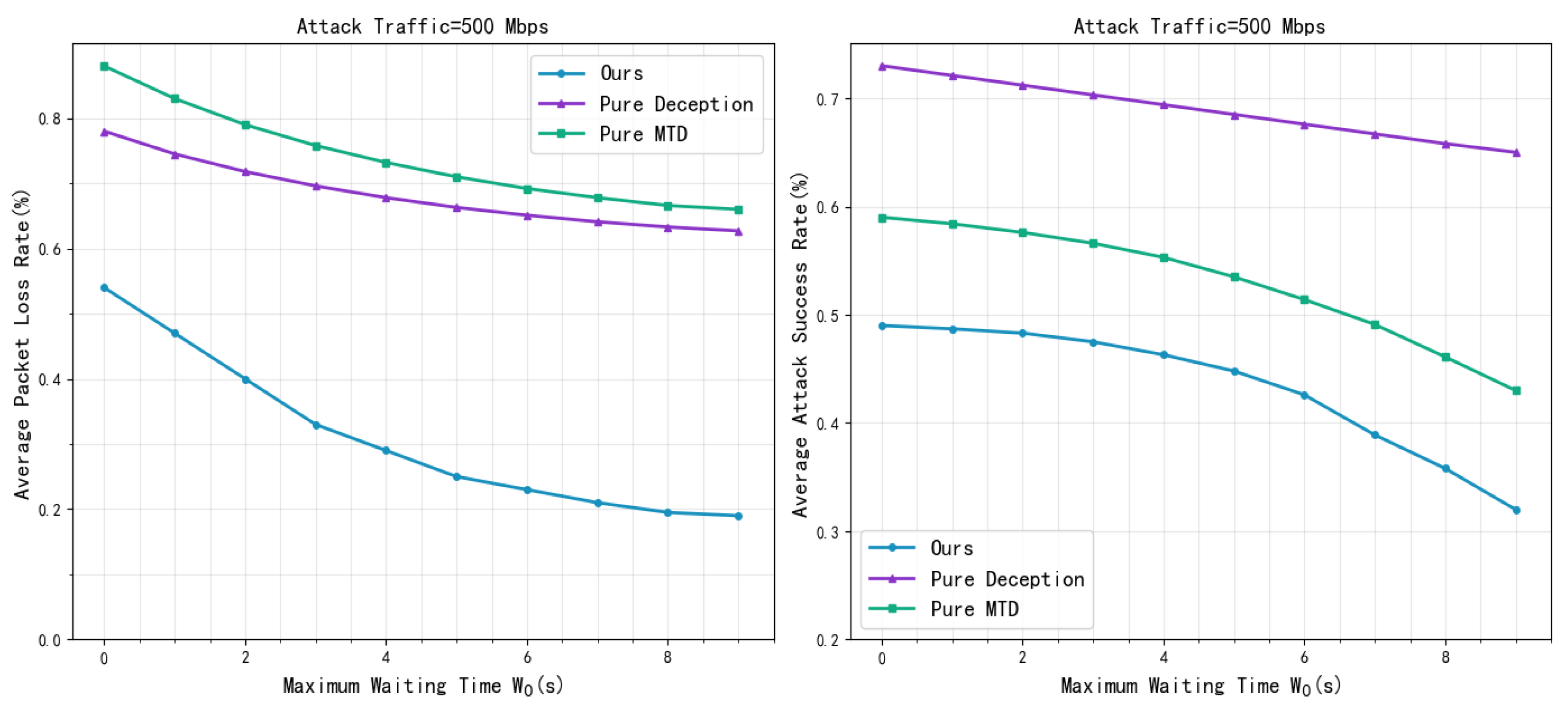
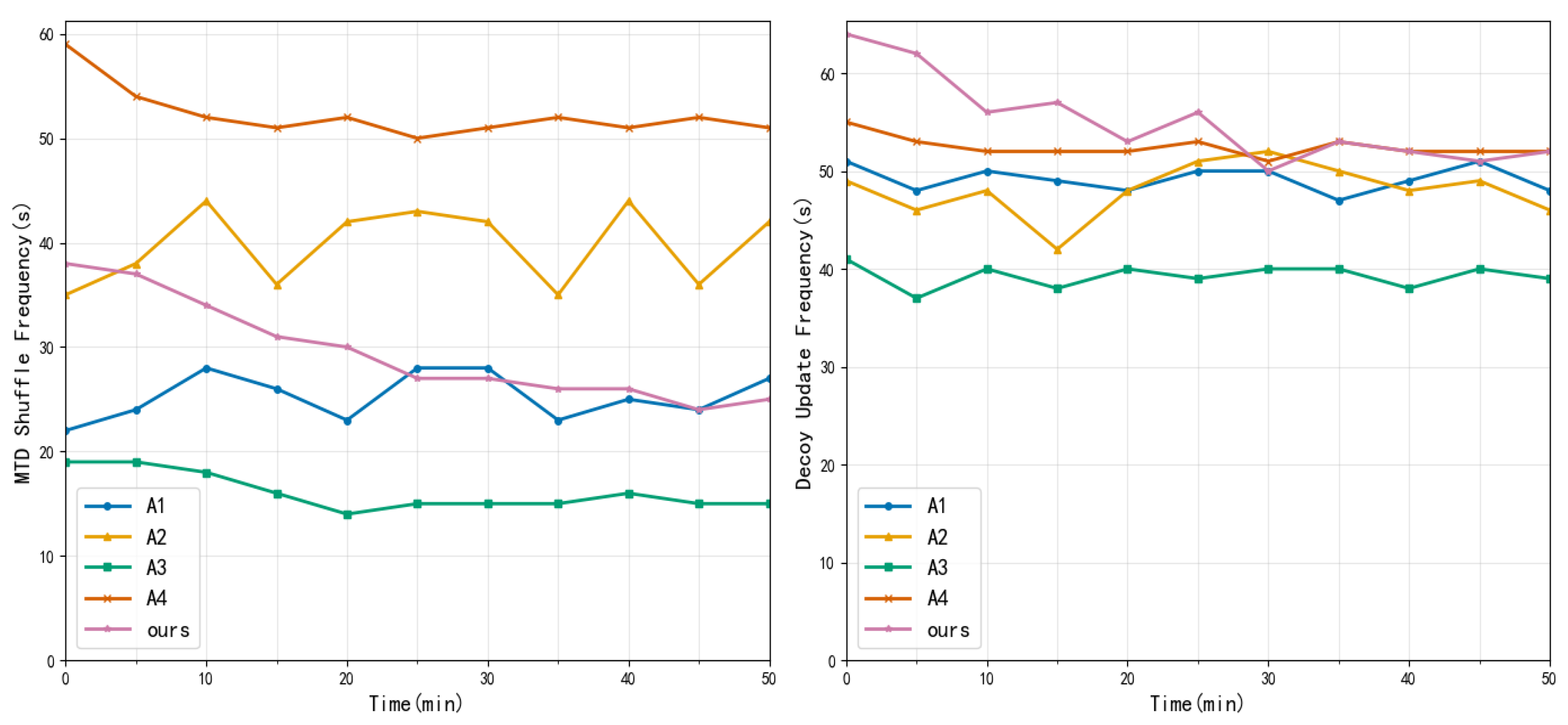
4.2. Experimental Results
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Griffioen, P.; Weerakkody, S.; Sinopoli, B. A Moving Target Defense for Securing Cyber-Physical Systems. IEEE Trans. Autom. Control 2021, 66, 2016–2031. [Google Scholar] [CrossRef]
- Zhang, T.; Xu, C.; Shen, J.; Kuang, X.; Grieco, L.A. How to Disturb Network Reconnaissance: A Moving Target Defense Approach Based on Deep Reinforcement Learning. IEEE Trans. Inf. Forensics Secur. 2023, 18, 5735–5748. [Google Scholar] [CrossRef]
- Zhang, T.; Kong, F.; Deng, D.; Tang, X.; Wu, X.; Xu, C.; Zhu, L.; Liu, J.; Ai, B.; Han, Z.; et al. Moving Target Defense Meets Artificial-Intelligence-Driven Network: A Comprehensive Survey. IEEE Internet Things J. 2025, 12, 13384–13397. [Google Scholar] [CrossRef]
- Qin, X.; Jiang, F.; Dong, C.; Doss, R. A hybrid cyber defense framework for reconnaissance attack in industrial control systems. Comput. Secur. 2024, 136, 103506. [Google Scholar] [CrossRef]
- Pagnotta, G.; De Gaspari, F.; Hitaj, D.; Andreolini, M.; Colajanni, M.; Mancini, L.V. DOLOS: A Novel Architecture for Moving Target Defense. IEEE Trans. Inf. Forensics Secur. 2023, 18, 5890–5905. [Google Scholar] [CrossRef]
- Rehman, Z.; Gondal, I.; Ge, M.; Dong, H.; Gregory, M.; Tari, Z. Proactive defense mechanism: Enhancing IoT security through diversity-based moving target defense and cyber deception. Comput. Secur. 2024, 139, 103685. [Google Scholar] [CrossRef]
- Yan, J.; Zhou, Y.; Wang, T. A Port-Hopping Technology against Remote Attacks and Its Effectiveness Evaluation. Electronics 2023, 12, 2477. [Google Scholar] [CrossRef]
- Connell, W.; Menascé, D.A.; Albanese, M. Performance Modeling of Moving Target Defenses with Reconfiguration Limits. IEEE Trans. Dependable Secur. Comput. 2021, 18, 205–219. [Google Scholar] [CrossRef]
- Masud, M.T.; Keshk, M.; Moustafa, N.; Turnbull, B.; Susilo, W. Vulnerability defence using hybrid moving target defence in Internet of Things systems. Comput. Secur. 2025, 153, 104380. [Google Scholar] [CrossRef]
- Sharma, D.P. Evaluating Moving Target Defense Methods Using Time to Compromise and Security Risk Metrics in IoT Networks. Electronics 2025, 14, 2205. [Google Scholar] [CrossRef]
- Ma, D.; Tang, Z.; Sun, X.; Guo, L.; Wang, L.; Chen, K. Game Theory Approaches for Evaluating the Deception-based Moving Target Defense. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 7 November 2022. [Google Scholar] [CrossRef]
- Menasce, D. Security performance. IEEE Internet Comput. 2003, 7, 84–87. [Google Scholar] [CrossRef]
- Torquato, M.; Maciel, P.; Vieira, M. PyMTDEvaluator: A Tool for Time-Based Moving Target Defense Evaluation: Tool description paper. In Proceedings of the 2021 IEEE 32nd International Symposium on Software Reliability Engineering (ISSRE), Wuhan, China, 25–28 October 2021; pp. 357–366. [Google Scholar] [CrossRef]
- Jalowski, Ł.; Zmuda, M.; Rawski, M. A Survey on Moving Target Defense for Networks: A Practical View. Electronics 2022, 11, 2886. [Google Scholar] [CrossRef]
- Zambianco, M.; Facchinetti, C.; Doriguzzi-Corin, R.; Siracusa, D. Resource-Aware Cyber Deception for Microservice-Based Applications. IEEE Trans. Serv. Comput. 2024, 17, 4211–4224. [Google Scholar] [CrossRef]
- Nguyen, T.A.; Kim, M.; Lee, J.; Min, D.; Lee, J.W.; Kim, D. Performability evaluation of switch-over Moving Target Defence mechanisms in a Software Defined Networking using stochastic reward nets. J. Netw. Comput. Appl. 2022, 199, 103267. [Google Scholar] [CrossRef]
- Alavizadeh, H.; Hong, J.B.; Kim, D.S.; Jang-Jaccard, J. Evaluating the effectiveness of shuffle and redundancy MTD techniques in the cloud. Comput. Secur. 2021, 102, 102091. [Google Scholar] [CrossRef]
- Moghaddam, T.; Kim, M.; Cho, J.H.; Lim, H.; Moore, T.J.; Nelson, F.F.; Kim, D.D. A Practical Security Evaluation of a Moving Target Defence against Multi-Phase Cyberattacks. In Proceedings of the 2022 52nd Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshops (DSN-W), Baltimore, MD, USA, 27–30 June 2022; pp. 103–110. [Google Scholar] [CrossRef]
- Kim, M.; Cho, J.H.; Lim, H.; Moore, T.J.; Nelson, F.F.; Ko, R.K.L.; Dongseong Kim, D. Evaluating Performance and Security of a Hybrid Moving Target Defense in SDN Environments. In Proceedings of the 2022 IEEE 22nd International Conference on Software Quality, Reliability and Security (QRS), Guangzhou, China, 5–9 December 2022; pp. 276–286. [Google Scholar] [CrossRef]
- Chen, Y.; Zhang, C.; Zhang, T. Spatial-Temporal Decisions for Moving Target Defense Game Subject to Quality of Service Constraints. In Proceedings of the 2023 4th International Conference on Computer Engineering and Intelligent Control (ICCEIC), Guangzhou, China, 20–22 October 2023; pp. 210–215. [Google Scholar] [CrossRef]
- Torquato, M.; Maciel, P.; Vieira, M. Evaluation of time-based virtual machine migration as moving target defense against host-based attacks. J. Syst. Softw. 2025, 219, 112222. [Google Scholar] [CrossRef]
- Rashid, A.; Such, J. Effectiveness of Moving Target Defenses for Adversarial Attacks in ML-Based Malware Detection. IEEE Trans. Dependable Secur. Comput. 2025, 22, 3885–3900. [Google Scholar] [CrossRef]
- Ge, M.; Cho, J.H.; Kim, D.; Dixit, G.; Chen, I.R. Proactive Defense for Internet-of-things: Moving Target Defense with Cyberdeception. ACM Trans. Internet Technol. 2021, 22, 1–31. [Google Scholar] [CrossRef]
- Seo, S.; Moon, H.; Lee, S.; Kim, D.; Lee, J.; Kim, B.; Lee, W.; Kim, D. D3GF: A Study on Optimal Defense Performance Evaluation of Drone-Type Moving Target Defense Through Game Theory. IEEE Access 2023, 11, 59575–59598. [Google Scholar] [CrossRef]
- Gao, C.; Wang, Y.; Xiong, X.; Zhao, W. MTDCD: An MTD Enhanced Cyber Deception Defense System. In Proceedings of the 2021 IEEE 4th Advanced Information Management, Communicates, Electronic and Automation Control Conference (IMCEC), Chongqing, China, 18–20 June 2021; Volume 4, pp. 1412–1417. [Google Scholar] [CrossRef]
- Etxezarreta, X.; Garitano, I.; Iturbe, M.; Zurutuza, U. Low delay network attributes randomization to proactively mitigate reconnaissance attacks in industrial control systems. Wirel. Netw. 2024, 30, 5077–5091. [Google Scholar] [CrossRef]
- Li, H.; Guo, Y.; Sun, P.; Wang, Y.; Huo, S. An optimal defensive deception framework for the container-based cloud with deep reinforcement learning. IET Inf. Secur. 2022, 16, 178–192. [Google Scholar] [CrossRef]
- Javadpour, A.; Ja’fari, F.; Taleb, T.; Shojafar, M.; Benza?d, C. A comprehensive survey on cyber deception techniques to improve honeypot performance. Comput. Secur. 2024, 140, 103792. [Google Scholar] [CrossRef]
- Li, Z.; Jin, H.; Zou, D.; Yuan, B. Exploring New Opportunities to Defeat Low-Rate DDoS Attack in Container-Based Cloud Environment. IEEE Trans. Parallel Distrib. Syst. 2020, 31, 695–706. [Google Scholar] [CrossRef]
- Li, Q.; Huang, H.; Li, R.; Lv, J.; Yuan, Z.; Ma, L.; Han, Y.; Jiang, Y. A comprehensive survey on DDoS defense systems: New trends and challenges. Comput. Netw. 2023, 233, 109895. [Google Scholar] [CrossRef]
- Roy, S.; Sharmin, N.; Acosta, J.C.; Kiekintveld, C.; Laszka, A. Survey and Taxonomy of Adversarial Reconnaissance Techniques. Acm Comput. Surv. 2022, 55, 1–38. [Google Scholar] [CrossRef]
- Zhang, Z.; Tian, Y.; Deng, R.; Ma, J. A Double-Benefit Moving Target Defense Against Cyber-Physical Attacks in Smart Grid. IEEE Internet Things J. 2022, 9, 17912–17925. [Google Scholar] [CrossRef]
| Year | Literature | Study Areas | |||
|---|---|---|---|---|---|
| S | D | R | Hybrid | ||
| 2021 | Evaluating the effectiveness of shuffle and redundancy MTD techniques in the cloud [17] | ✓ | ✓ | ||
| 2022 | A Practical Security Evaluation of a Moving Target Defence against Multi-Phase Cyberattacks [18] | ✓ | |||
| 2022 | Evaluating Performance and Security of a Hybrid Moving Target Defense in SDN Environments [19] | ✓ | |||
| 2022 | Performability evaluation of switch-over Moving Target Defence mechanisms in a Software Defined Networking using stochastic reward nets [16] | ✓ | |||
| 2023 | Spatial-Temporal Decisions for Moving Target Defense Game Subject to Quality of Service Constraints [20] | ✓ | |||
| 2024 | Proactive defense mechanism: Enhancing IoT security through diversity-based MTD and cyber deception [6] | ✓ | ✓ | ✓ | |
| 2025 | Evaluation of time-based virtual machine migration as moving target defense against host-based attacks [21] | ✓ | |||
| 2025 | Evaluating Moving Target Defense Methods Using Time-to-Compromise and Security Risk Metrics in IoT Networks [10] | ✓ | |||
| 2025 | Effectiveness of Moving Target Defenses for Adversarial Attacks in ML-Based Malware Detection [22] | ✓ | ✓ | ||
| 2025 | Vulnerability defence using hybrid moving target defence in Internet of Things systems [9] | ✓ | |||
| Metric | |||||||
|---|---|---|---|---|---|---|---|
| 20% | 25% | 30% | 3 s | 4 s | 5 s | 6 s | |
| MTD shuffle frequency | 41.5 s | 33.4 s | 25 s | 41.5 s | 33.4 s | 28.7 s | 25 s |
| Decoy update frequency | 68 s | 51.7 s | 42.6 s | 68 s | 60.5 s | 54 s | 42.6 s |
| Attack Success Rate | Average Packet Loss Rate (%) | Average Waiting Time ( s) | Average Effective Service Rate | |
|---|---|---|---|---|
| A1 | 37.61% | 26.42% | 3.06 s | 55.67% |
| A2 | 35.56% | 58.16% | 4.04 s | 71.36% |
| A3 | 29.07% | 69.70% | 4.52 s | 48.31% |
| A4 | 43.55% | 53.12% | 3.97 s | 72.43% |
| Ours | 38.20% | 22.01% | 2.97 s | 79.66% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hou, F.; Hou, F.; Zang, X.; Hua, Z.; Liu, Z.; Wu, Z. Effectiveness Evaluation Method for Hybrid Defense of Moving Target Defense and Cyber Deception. Computers 2025, 14, 513. https://doi.org/10.3390/computers14120513
Hou F, Hou F, Zang X, Hua Z, Liu Z, Wu Z. Effectiveness Evaluation Method for Hybrid Defense of Moving Target Defense and Cyber Deception. Computers. 2025; 14(12):513. https://doi.org/10.3390/computers14120513
Chicago/Turabian StyleHou, Fangbo, Fangrun Hou, Xiaodong Zang, Ziyang Hua, Zhang Liu, and Zhe Wu. 2025. "Effectiveness Evaluation Method for Hybrid Defense of Moving Target Defense and Cyber Deception" Computers 14, no. 12: 513. https://doi.org/10.3390/computers14120513
APA StyleHou, F., Hou, F., Zang, X., Hua, Z., Liu, Z., & Wu, Z. (2025). Effectiveness Evaluation Method for Hybrid Defense of Moving Target Defense and Cyber Deception. Computers, 14(12), 513. https://doi.org/10.3390/computers14120513






