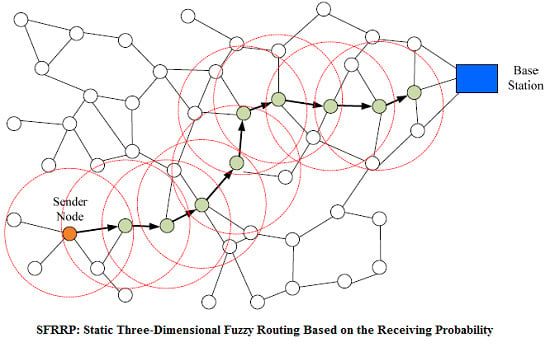
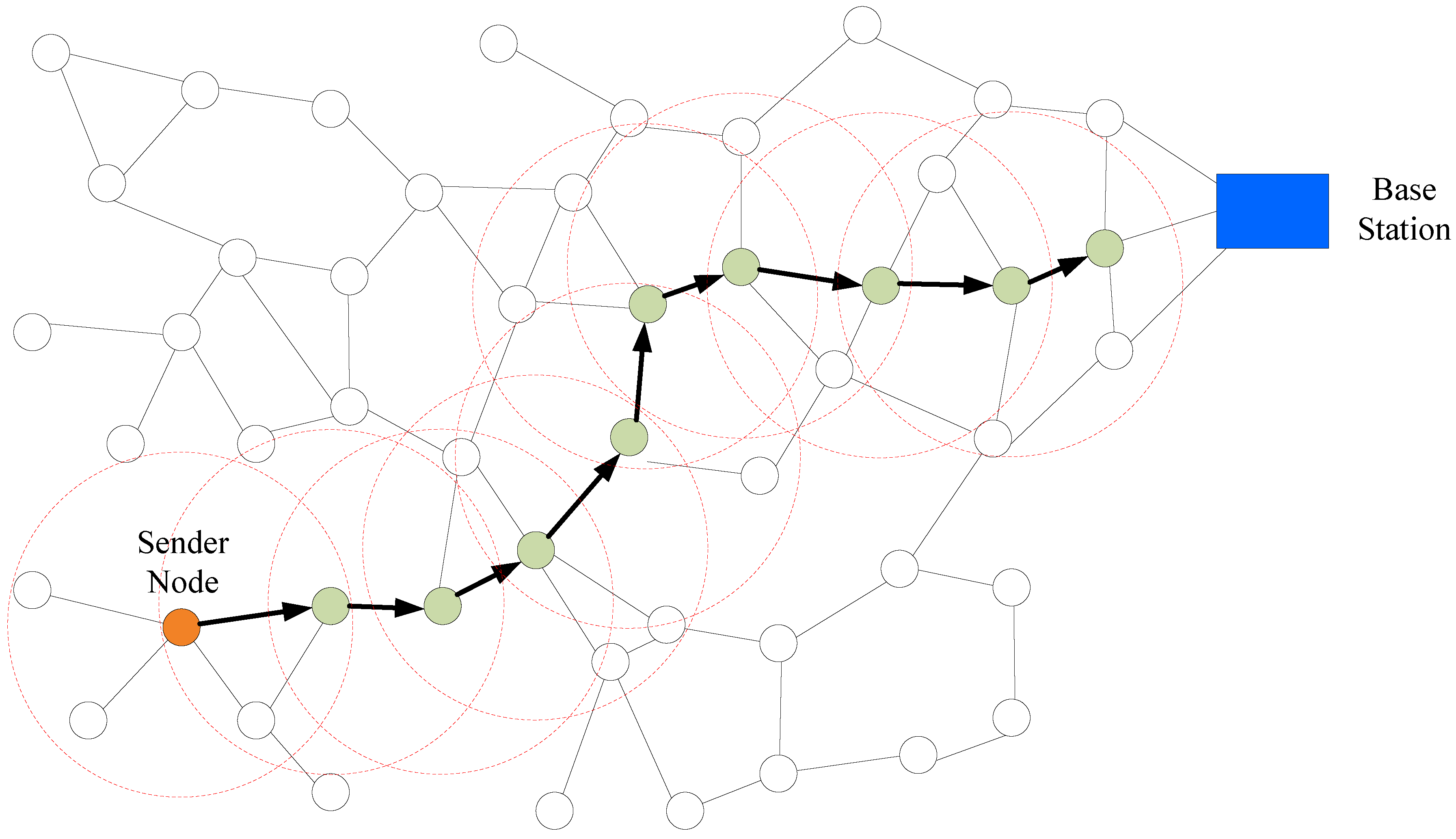
Static Three-Dimensional Fuzzy Routing Based on the Receiving Probability in Wireless Sensor Networks
Abstract
:1. Introduction
2. Related Works
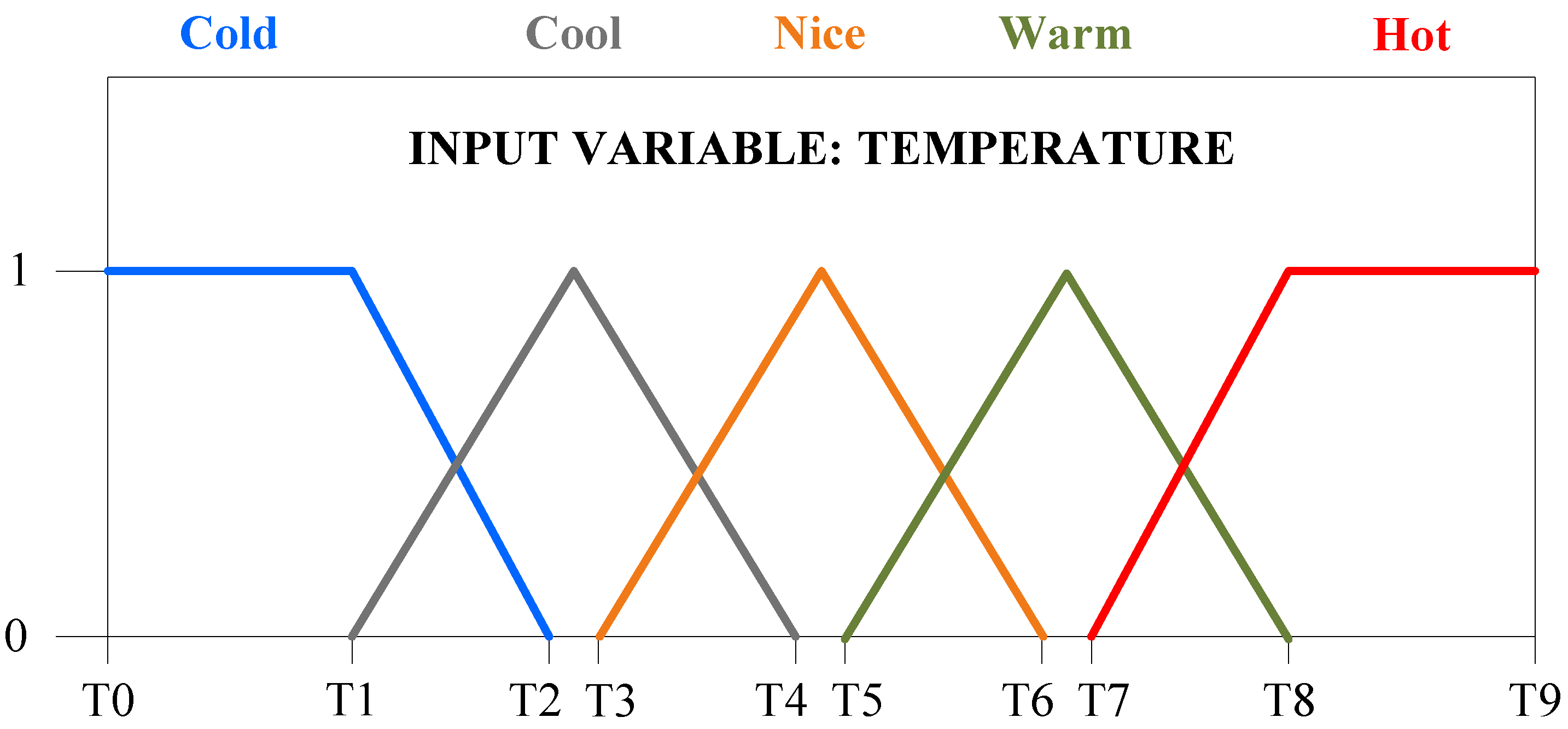
3. Fuzzy Logic Applications
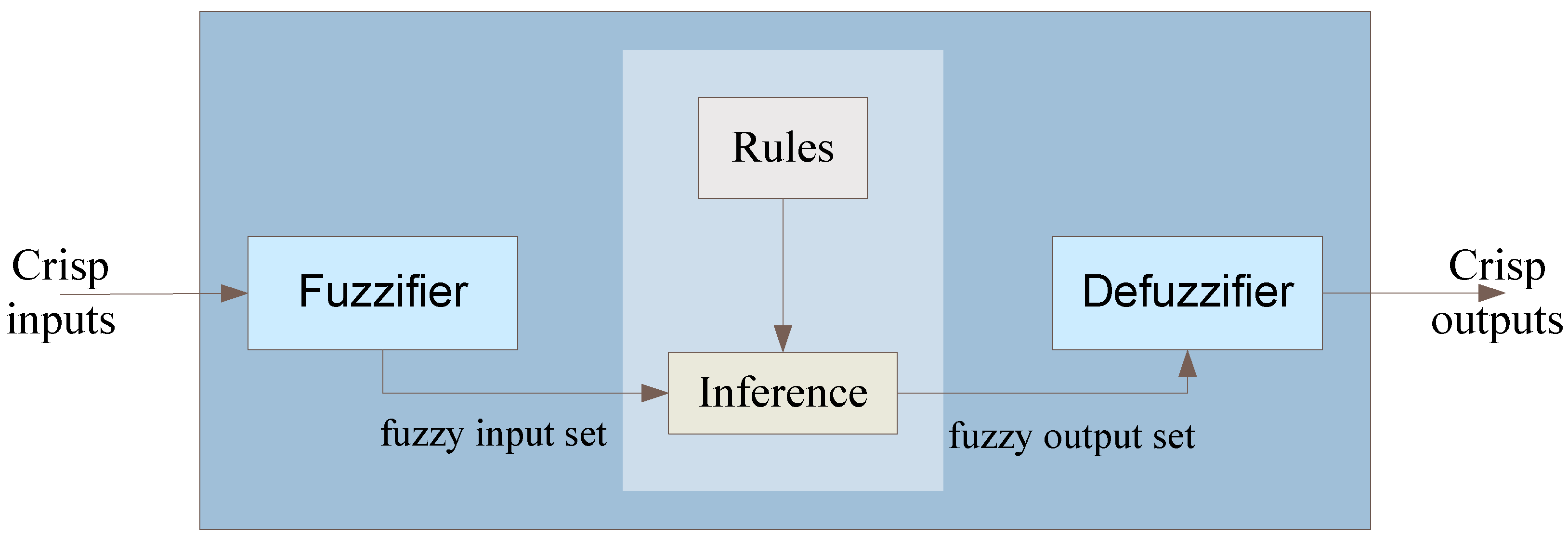
| 1. | Appoint the linguistic variables and terms (initialization) |
| 2. | Create the membership functions (initialization) |
| 3. | Create the rule base (initialization) |
| 4. | Convert crisp input data to fuzzy values based on the membership functions (FUZZIFICATION) |
| 5. | Evaluate the rules in the rule base (inference) |
| 6. | Combine the results of the rules (aggregation) |
| 7. | Convert the output data to non-fuzzy value (DEFUZZIFICATION) |
| Fuzzy Rules | |
|---|---|
| 1. | IF (temperature is cold OR cool) AND (target is warm) THEN command is heat |
| 2. | IF (temperature is warm OR hot) AND (target is warm) THEN command is cool |
| 3. | IF (temperature is warm) AND (target is warm) THEN command is no-change |
4. The Proposed Routing Protocol
4.1. The Network Model

4.2. Data Packet Format
| Element Name | Features |
|---|---|
| Initiator ID | Indicates the ID number of the sender node |
| Initiator Sequence Number | Illustrates the number of packets generated by the sender node |
| Partial Route | Represents nodes traveled by the packets |
| Data | Indicates the message content |
| Start Round | Round of start sending packets |
| Finish Round | Round of finish sending packets |
| Delay Time | The total time required to send packets |
4.3. The Proposed Fuzzy System
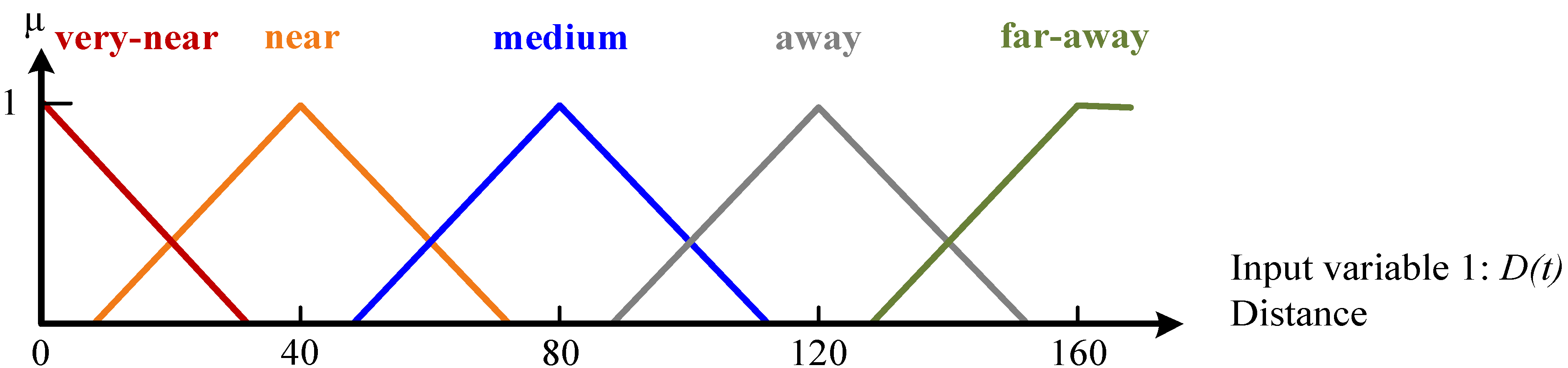
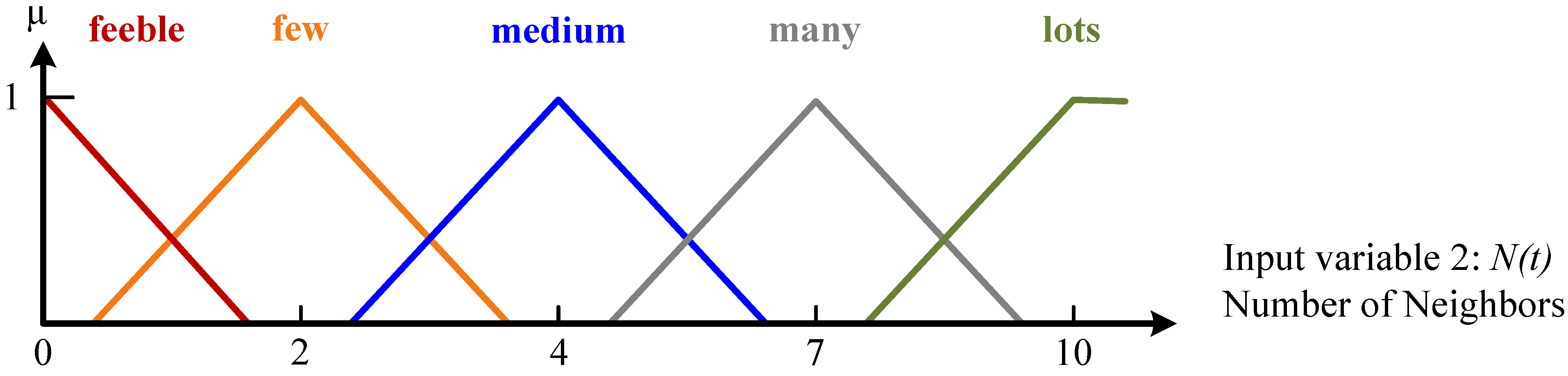

| Rule No. | Antecedent | Consequent | |
|---|---|---|---|
| Distance | Number of Neighbors | Receiving Probability | |
| 1 | very-near | feeble | very-low |
| 2 | very-near | few | low |
| 3 | very-near | medium | high |
| 4 | very-near | many | very-high |
| 5 | very-near | lots | very-high |
| 6 | near | feeble | very-low |
| 7 | near | few | low |
| 8 | near | medium | medium |
| 9 | near | many | high |
| 10 | near | lots | high |
| 11 | medium | feeble | very-low |
| 12 | medium | few | low |
| 13 | medium | medium | medium |
| 14 | medium | many | high |
| 15 | medium | lots | high |
| 16 | away | feeble | very-low |
| 17 | away | few | very-low |
| 18 | away | medium | low |
| 19 | away | many | medium |
| 20 | away | lots | medium |
| 21 | far-away | feeble | very-low |
| 22 | far-away | few | very-low |
| 23 | far-away | medium | low |
| 24 | far-away | many | low |
| 25 | far-away | lots | medium |

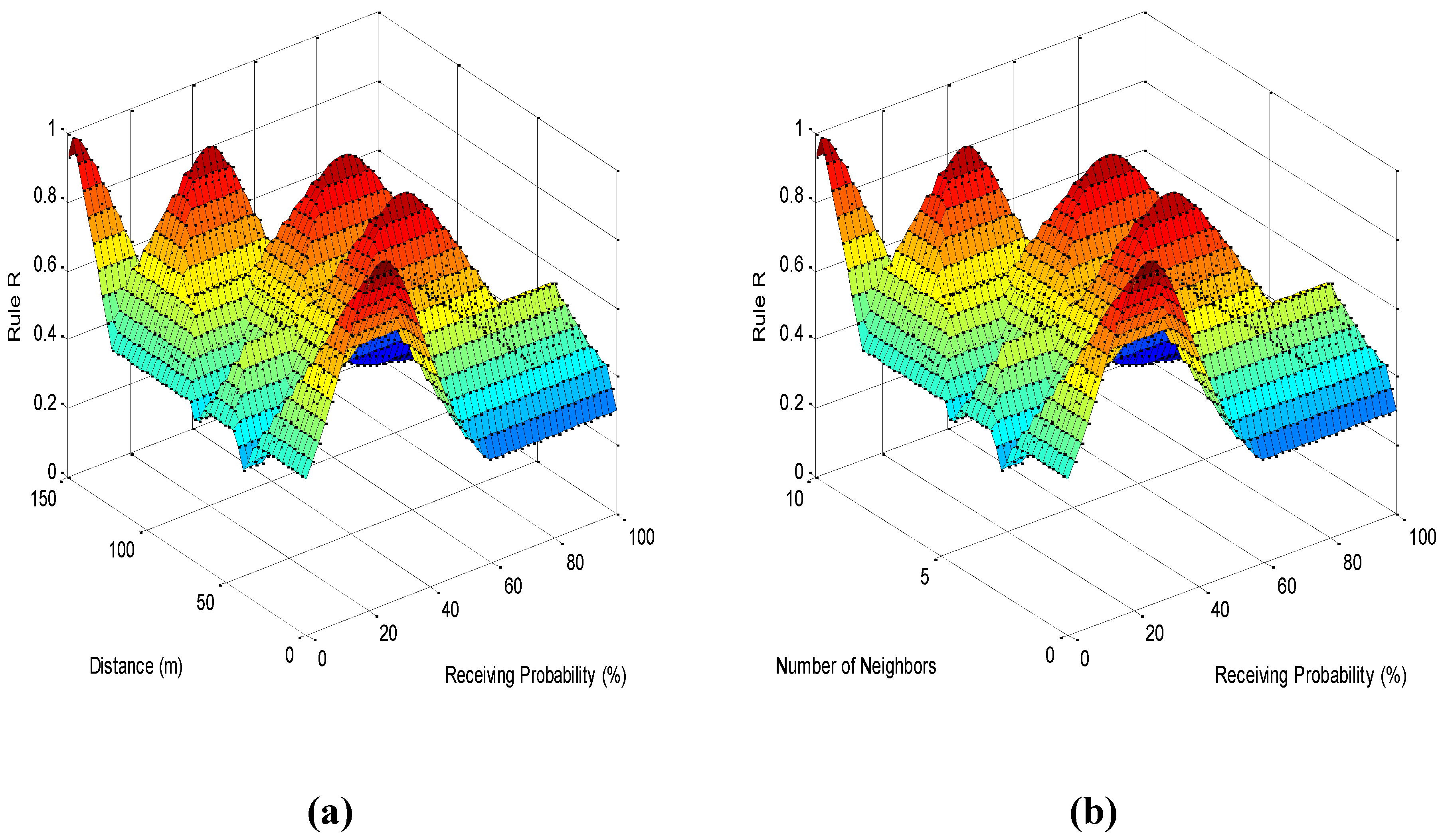
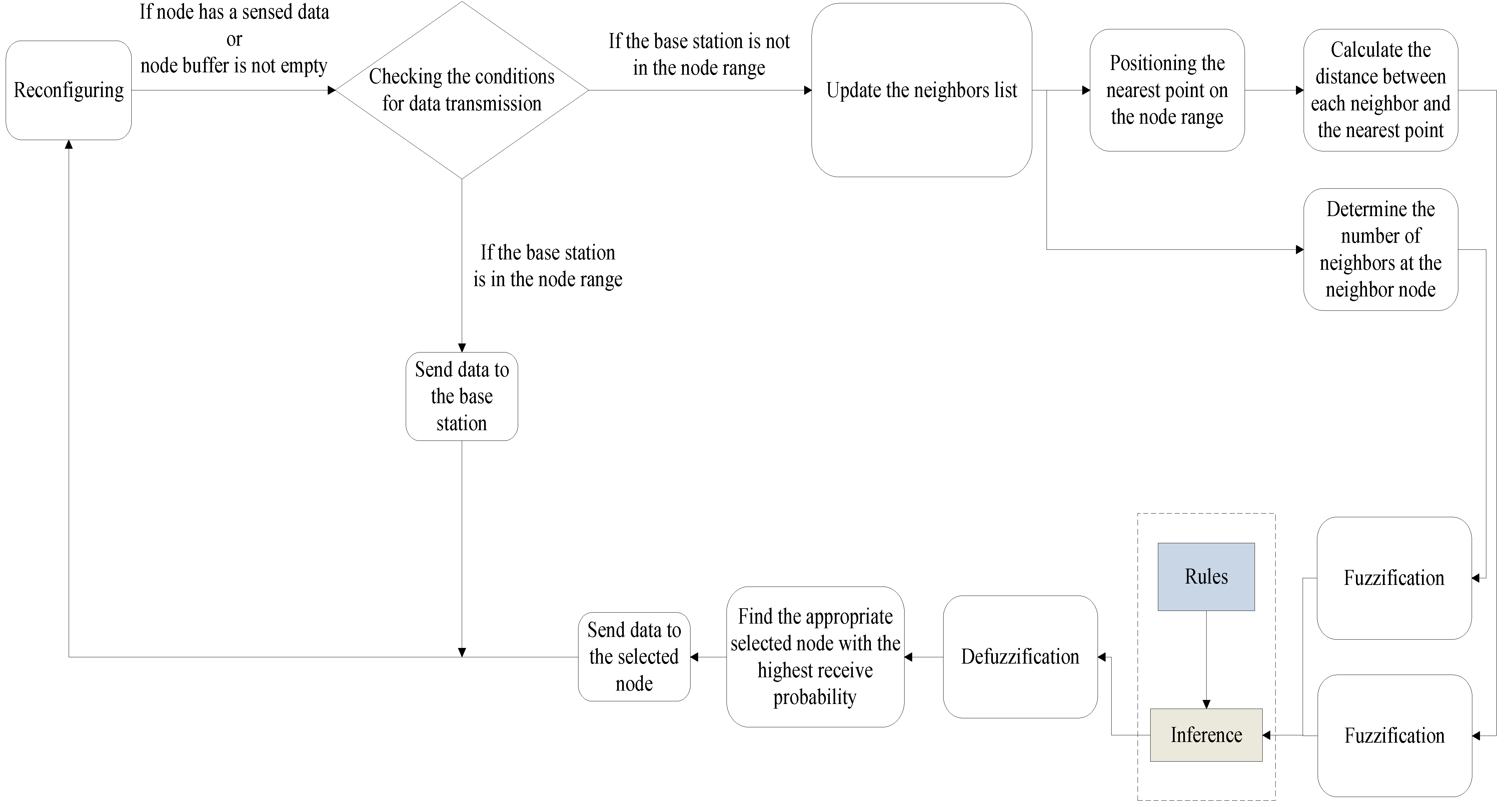
4.4. Routing Procedure in the Proposed Protocol




5. Experimental Evaluation and Analysis
5.1. Simulation Model
| Parameter | Default Value |
|---|---|
| Network size (m3) | 300 × 300 × 300 |
| Number of sensor nodes | 50 |
| Transmission range of sensor nodes (m) | 75 |
| Initial nodes energy (Joule) | 5 |
| Maximum buffer size of sensor nodes (packet) | 60 |
| Position of base station (m) | (150 , 150 , 0) |
5.2. Experimental Results
5.2.1. Impact of Data Generation Rate
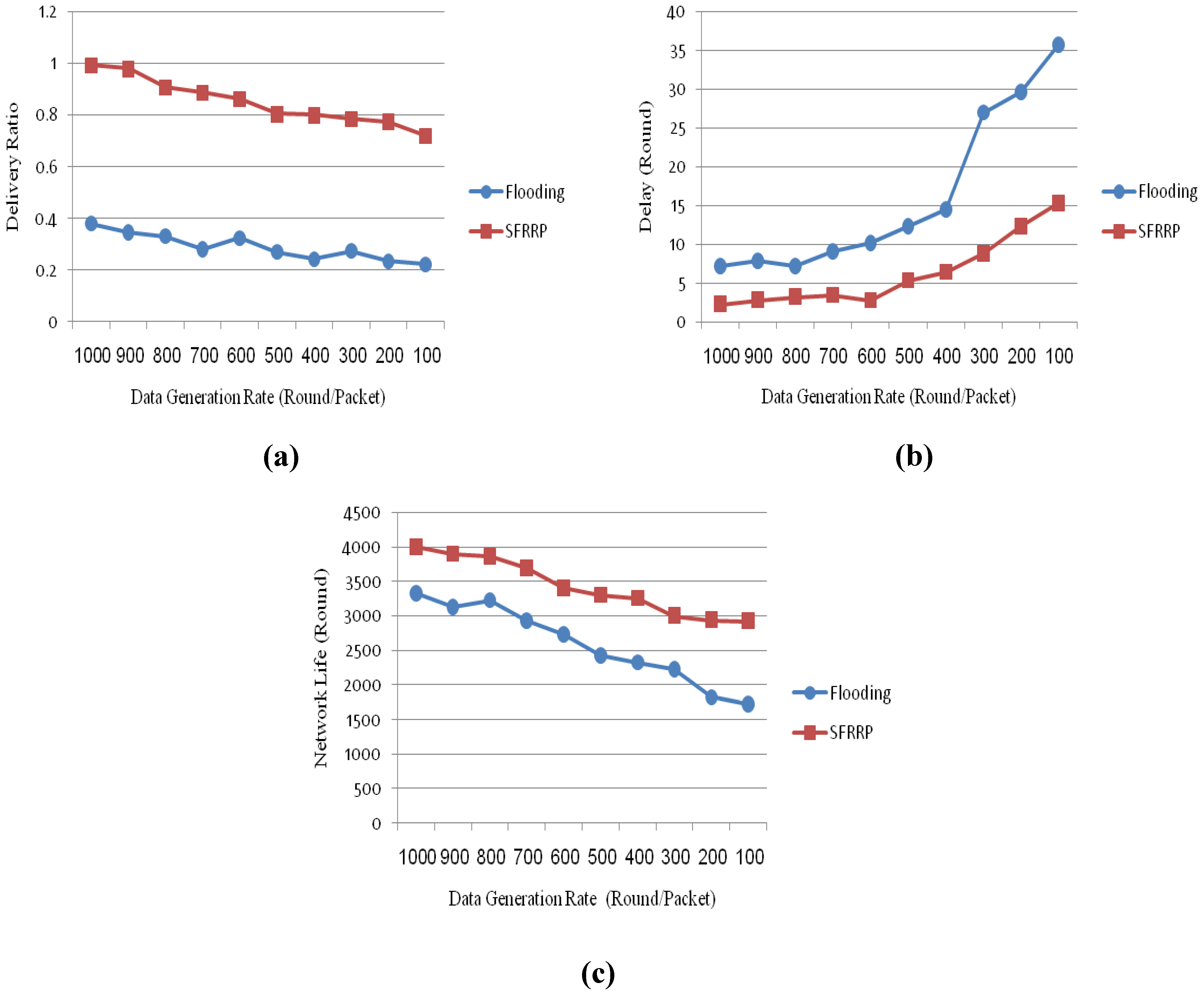
5.2.2. Impact of Buffer Size

5.2.3. Impact of Node Initial Energy

5.2.4. Total Energy Consumption of Nodes
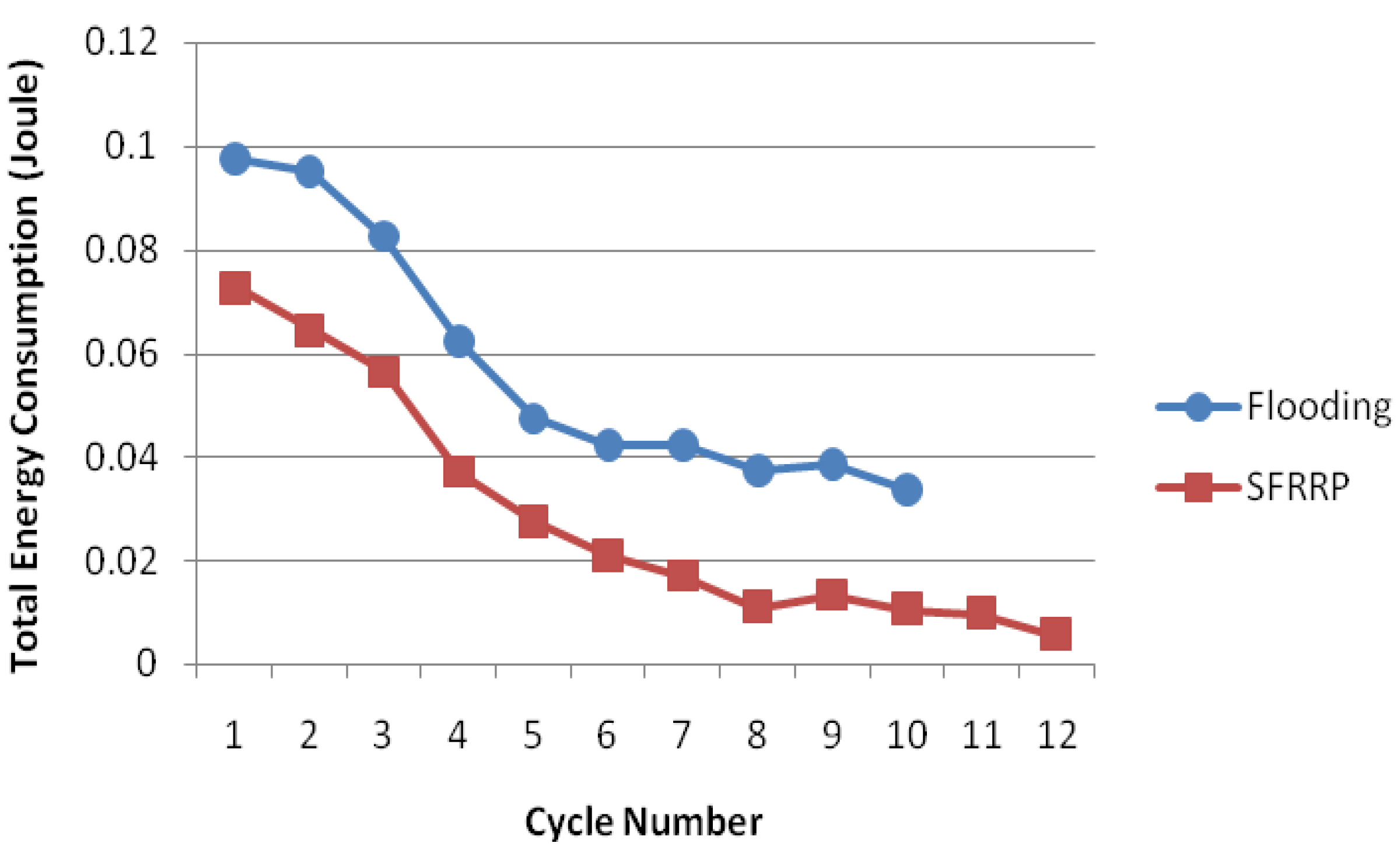
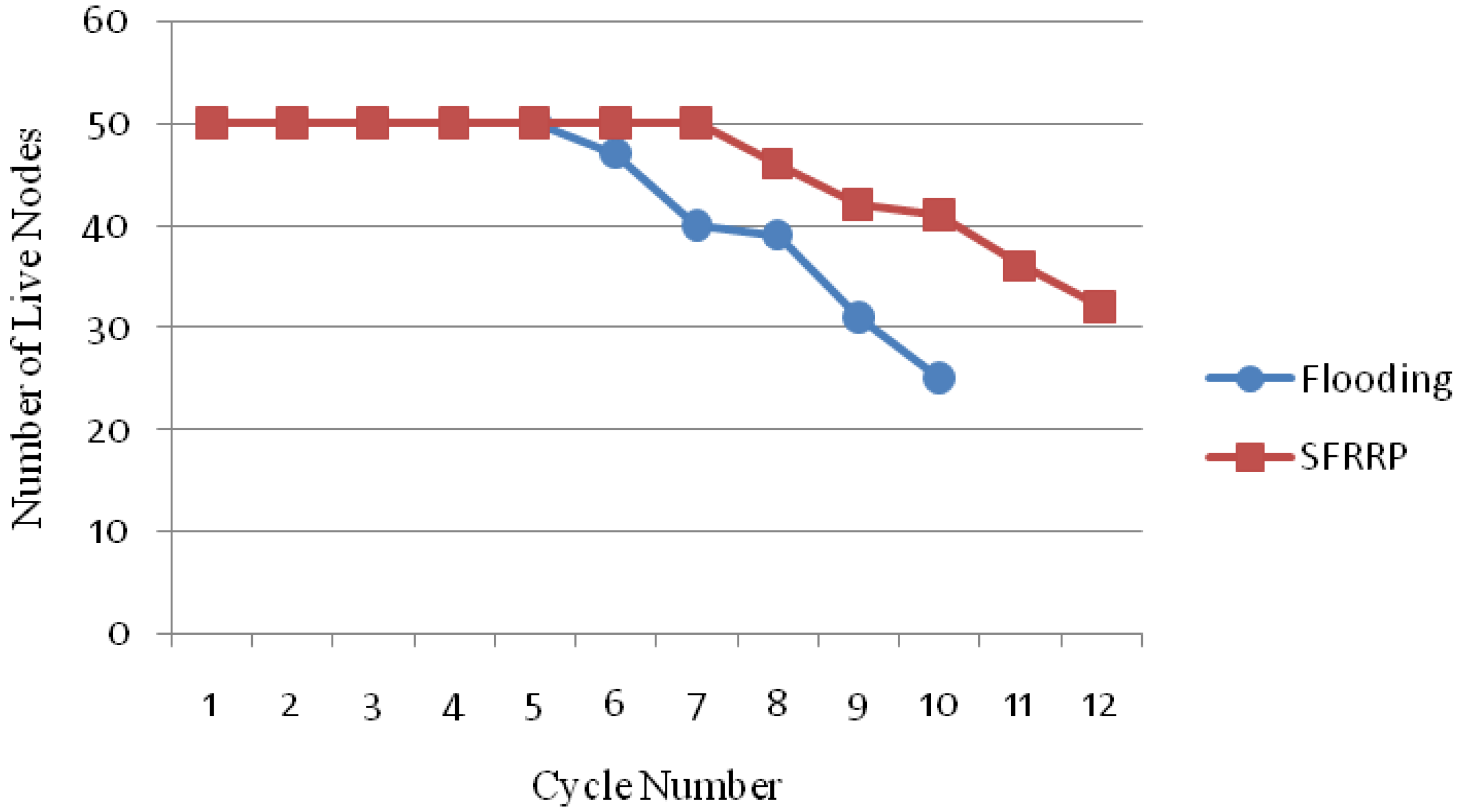
5.2.5. Number of Live Nodes
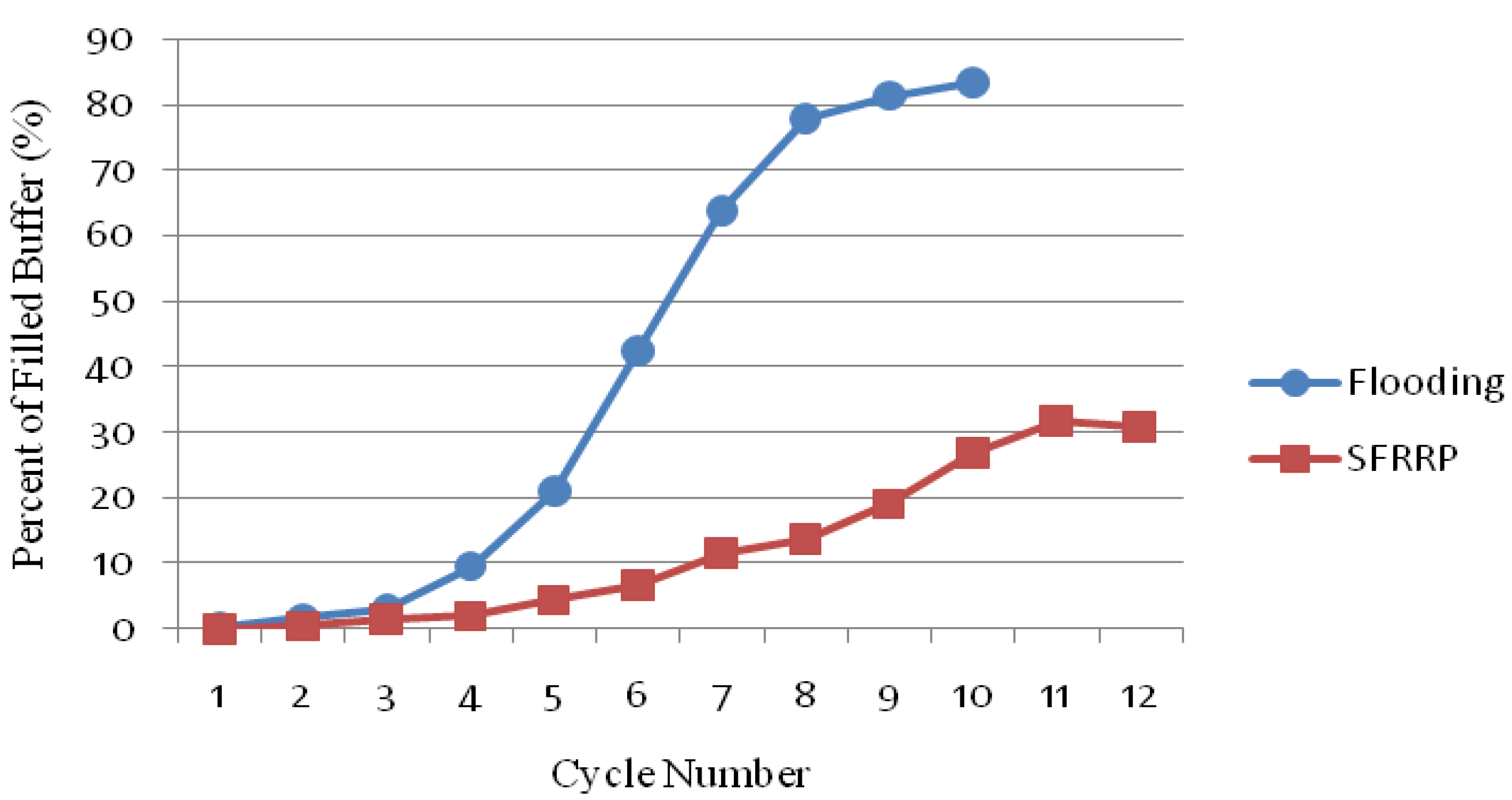
5.2.6. Percent of Filled Node Buffer
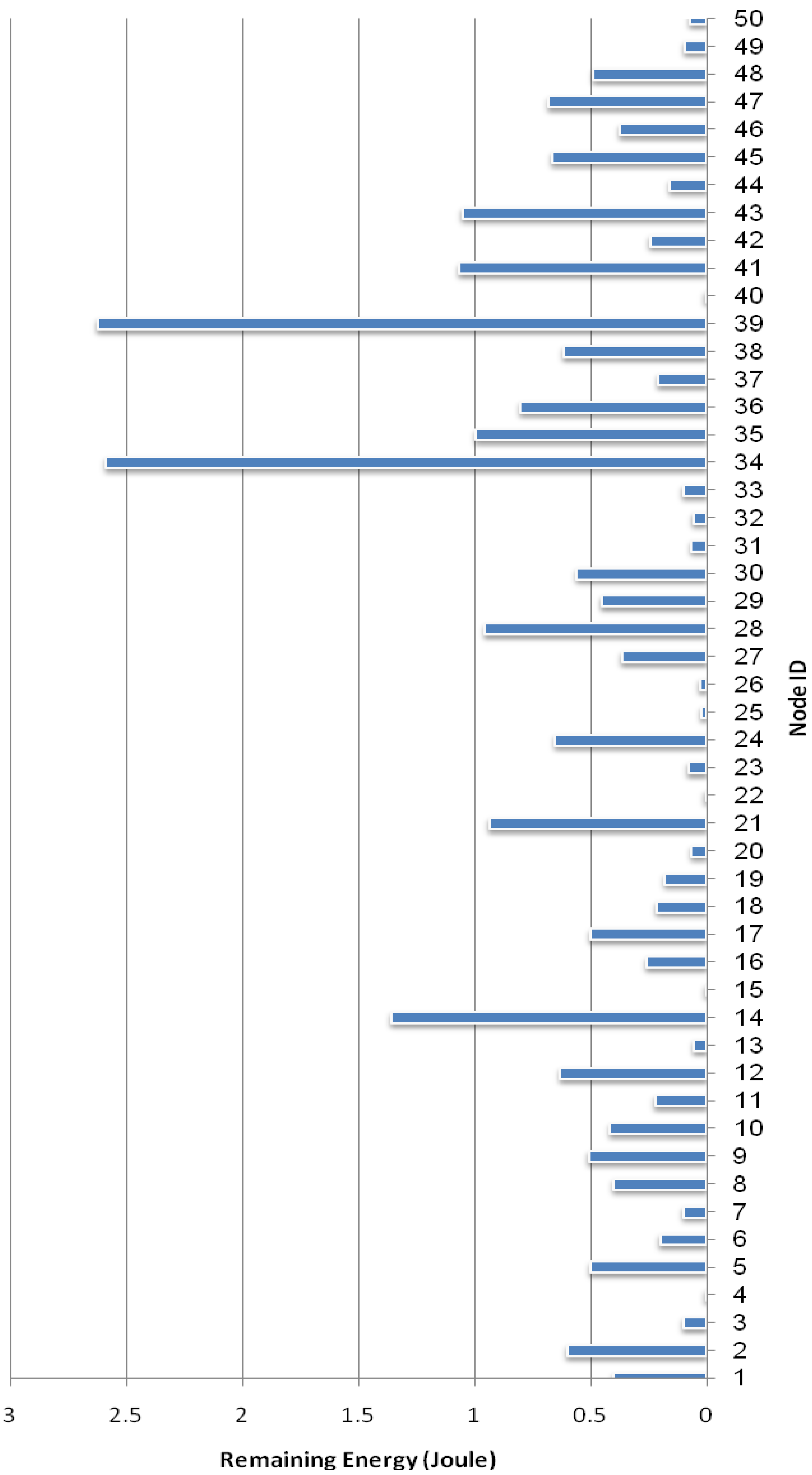
6. Conclusions
7. Future Work
Conflicts of Interest
References
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Khalil, E.A.; Attea, B.A. Energy-aware evolutionary routing protocol for dynamic clustering of wireless sensor networks. Swarm Evol. Comput. 2011, 1, 195–203. [Google Scholar] [CrossRef]
- Fortino, G.; Guerrieri, A.; O'Hare, G.; Ruzzelli, A. A flexible building management framework based on wireless sensor and actuator networks. J. Netw. Comput. Appl. 2012, 35, 1934–1952. [Google Scholar] [CrossRef]
- Shokrzadeh, H.; Khorsandi, S.; Toroghi Haghighat, A. Optimized query-driven appointment routing based on Expectation-Maximization in wireless sensor networks. J. Netw. Comput. Appl. 2012, 35, 1749–1761. [Google Scholar] [CrossRef]
- Huang, H.; Hartman, J.H.; Hurst, T.N. Data-centric routing in sensor networks using biased walk, Sensor and Ad Hoc Communications and Networks, 2006. SECON'06. 2006 3rd Annual IEEE Communications Society on, Hyatt Regency, Reston, VA, USA, September 2006; IEEE: Hyatt Regency, Reston, VA, USA, September 2006; pp. 1–9.
- Othman, M.F.; Shazali, K. Wireless Sensor Network Applications: A Study in Environment Monitoring System. Procedia Eng. 2012, 41, 1204–1210. [Google Scholar] [CrossRef]
- Ali, K.A.; Mouftah, H.T. Wireless personal area networks architecture and protocols for multimedia applications. Ad Hoc Netw. 2011, 9, 675–686. [Google Scholar] [CrossRef]
- Boukerche, A.; Turgut, B.; Aydin, N.; Ahmad, M.Z.; Bölöni, L.; Turgut, D. Routing protocols in ad hoc networks: A survey. Comput. Netw. 2011, 55, 3032–3080. [Google Scholar] [CrossRef]
- Muñoz, J.L.; Esparza, O.; Aguilar, M.; Carrascal, V.; Forné, J. Rdsr-v. reliable dynamic source routing for video-streaming over mobile ad hoc networks. Comput. Netw. 2010, 54, 79–96. [Google Scholar] [CrossRef]
- Sergiou, C.; Vassiliou, V.; Paphitis, A. Hierarchical Tree Alternative Path (HTAP) algorithm for congestion control in wireless sensor networks. Ad Hoc Netw. 2013, 11, 257–272. [Google Scholar] [CrossRef]
- Can, Z.; Demirbas, M. A survey on in-network querying and tracking services for wireless sensor networks. Ad Hoc Netw. 2013, 11, 596–610. [Google Scholar] [CrossRef]
- Nayebi, A.; Karlsson, G.; Sarbazi-Azad, H. Evaluation and design of beaconing in mobile wireless networks. Ad Hoc Netw. 2011, 9, 368–386. [Google Scholar] [CrossRef]
- Chang, D.; Cho, K.; Choi, N.; Kwon, T.; Choi, Y. A probabilistic and opportunistic flooding algorithm in wireless sensor networks. Comput. Commun. 2012, 35, 500–506. [Google Scholar] [CrossRef]
- Heinzelman, W.R.; Kulik, J.; Balakrishnan, H. Adaptive protocols for information dissemination in wireless sensor networks, Proceedings of the 5th annual ACM/IEEE international conference on Mobile computing and networking, Seattle, WA, USA, August 1999; pp. 174–185.
- Kulik, J.; Heinzelman, W.; Balakrishnan, H. Negotiation-based protocols for disseminating information in wireless sensor networks. Wirel. Netw. 2002, 8, 169–185. [Google Scholar] [CrossRef]
- El-Basioni, B.M.M.; El-kader, S.M.A.; Eissa, H.S. Designing a local path repair algorithm for directed diffusion protocol. Egypt. Inform. J. 2012, 13, 155–169. [Google Scholar] [CrossRef]
- Liu, A.; Ren, J.; Li, X.; Chen, Z.; Shen, X.S. Design principles and improvement of cost function based energy aware routing algorithms for wireless sensor networks. Comput. Netw. 2012, 56, 1951–1967. [Google Scholar] [CrossRef]
- Geetha, V.; Kallapur, P.; Tellajeera, S. Clustering in Wireless Sensor Networks: Performance Comparison of LEACH & LEACH-C Protocols Using NS2. Procedia Technol. 2012, 4, 163–170. [Google Scholar]
- Manjeshwar, A.; Agrawal, D.P. TEEN: a routing protocol for enhanced efficiency in wireless sensor networks, Proceedings of the 15th International Parallel & Distributed Processing Symposium, Washington, DC, USA, 2001; pp. 2009–2015.
- Manjeshwar, A.; Agrawal, D.P. APTEEN: A hybrid protocol for efficient routing and comprehensive information retrieval in wireless sensor networks, Proceedings of the 16th International Parallel and Distributed Processing Symposium, Ft. Lauderdale, FL, USA, April 2001.
- Rodoplu, V.; Meng, T.H. Minimum energy mobile wireless networks. IEEE J. Sel. Area. Comm. 1999, 17, 1333–1344. [Google Scholar] [CrossRef]
- Zhang, J.; Lee, H.-N. Energy-efficient utility maximization for wireless networks with/without multipath routing. AEU Int. J. Electron. C 2010, 64, 99–111. [Google Scholar] [CrossRef]
- Li, L.; Halpern, J.Y. Minimum-energy mobile wireless networks revisited, Communications, 2001. ICC 2001. IEEE International Conference on, Helsinki, Finland, June 2001; IEEE: Helsinki, Finland, June 2001; pp. 278–283.
- Subramanian, L.; Katz, R.H. An architecture for building self-configurable systems, Mobile and Ad Hoc Networking and Computing, 2000. MobiHOC. 2000 First Annual Workshop on, Boston Massachusetts, USA, August 2000; IEEE, 2000; pp. 63–73.
- Talebi, M.S.; Khonsari, A.; Mohtasham, A.; Abbasi, A. Cost-aware monitoring of network-wide aggregates in wireless sensor networks. Comput. Netw. 2011, 55, 1276–1290. [Google Scholar] [CrossRef]
- Li, Q.; Aslam, J.; Rus, D. Hierarchical power-aware routing in sensor networks, Proceedings of the DIMACS workshop on pervasive networking, 2001; Citeseer, 2001.
- Xu, Y.; Heidemann, J.; Estrin, D. Geography-informed energy conservation for ad hoc routing, Geography-informed energy conservation for ad hoc routing, Proceedings of the 7th annual international, New York, NY, USA, 2001; ACM, 2001; pp. 70–84.
- Yu, Y.; Govindan, R.; Estrin, D. Geographical and energy aware routing: A recursive data dissemination protocol for wireless sensor networks; Citeseer, 2001. [Google Scholar]
- Chen, B.; Jamieson, K.; Balakrishnan, H.; Morris, R. Span: An energy-efficient coordination algorithm for topology maintenance in ad hoc wireless networks, Proceedings of the 7th annual international conference on Mobile computing and networking, Hingham, MA, USA, September 2002; ACM, 2002; pp. 481–494.
- Kuhn, F.; Wattenhofer, R.; Zollinger, A. Worst-case optimal and average-case efficient geometric ad-hoc routing, Proceedings of the 4th ACM international symposium on Mobile ad hoc networking & computing, New York, NY, USA, 2003; ACM, 2003; pp. 267–278.
- Zhang, X.; Wu, Z.D. The balance of routing energy consumption in wireless sensor networks. J. Parallel Distr. Comput. 2011, 71, 1024–1033. [Google Scholar] [CrossRef]
- Bassi, G.; Galarza, C.G. High throughput and low power consumption on a wireless sensor network. Digit. Singal Process. 2012, 22, 263–268. [Google Scholar] [CrossRef]
- Abadeh, M.S.; Habibi, J.; Lucas, C. Intrusion detection using a fuzzy genetics-based learning algorithm. J. Netw. Comput. Appl. 2007, 30, 414–428. [Google Scholar] [CrossRef]
- Kong, X.; Lin, C.; Jiang, Y.; Yan, W.; Chu, X. Efficient dynamic task scheduling in virtualized data centers with fuzzy prediction. J. Netw. Comput. Appl. 2011, 34, 1068–1077. [Google Scholar] [CrossRef]
- Abbas Khan, S.; Daachi, B.; Djouani, K. Application of fuzzy inference systems to detection of faults in wireless sensor networks. Neurocomputing 2012, 94, 111–120. [Google Scholar] [CrossRef]
- Kruglov, V.M. A characterization of the Poisson distribution. Stat. Probabil. Lett. 2010, 80, 2032–2034. [Google Scholar] [CrossRef]
- Acilar, A.M.; Arslan, A. Optimization of multiple input–output fuzzy membership functions using clonal selection algorithm. Expert Syst. Appl. 2011, 38, 1374–1381. [Google Scholar] [CrossRef]
- Gostev, V.; Skurtov, S.; Nevolko, V. Designing of an fuzzy controller at identical triangular membership functions, Modern Problems of Radio Engineering, Telecommunications and Computer Science (TCSET), 2010 International Conference on, Slavs'ke, Lviv Oblast, Ukraine, February 2010; IEEE, 2010; pp. 289–289.
- Wong, M.L.; Yam, Y.; Baranyi, P. Representing membership functions as elements in function space, American Control Conference, Arlington, VA, USA, June 2001; Proceedings of the 2001. IEEE, 2001; pp. 1922–1927.
- Runkler, T.A. Selection of appropriate defuzzification methods using application specific properties. IEEE Trans. Fuzzy Syst. 1997, 5, 72–79. [Google Scholar] [CrossRef]
- Monkman, S.; Schagaev, I. Redundancy + Reconfigurability = Recoverability. Electronics 2013, 2, 212–233. [Google Scholar] [CrossRef]
- Sand, H.; Zimmermann, B.; Wabakken, P.; Andrèn, H.; Pedersen, H.C. Using GPS technology and GIS cluster analyses to estimate kill rates in wolf‐ungulate ecosystems. Wildlife Soc. B. 2005, 33, 914–925. [Google Scholar] [CrossRef]
© 2013 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Samadi Gharajeh, M.; Khanmohammadi, S. Static Three-Dimensional Fuzzy Routing Based on the Receiving Probability in Wireless Sensor Networks. Computers 2013, 2, 152-175. https://doi.org/10.3390/computers2040152
Samadi Gharajeh M, Khanmohammadi S. Static Three-Dimensional Fuzzy Routing Based on the Receiving Probability in Wireless Sensor Networks. Computers. 2013; 2(4):152-175. https://doi.org/10.3390/computers2040152
Chicago/Turabian StyleSamadi Gharajeh, Mohammad, and Sohrab Khanmohammadi. 2013. "Static Three-Dimensional Fuzzy Routing Based on the Receiving Probability in Wireless Sensor Networks" Computers 2, no. 4: 152-175. https://doi.org/10.3390/computers2040152
APA StyleSamadi Gharajeh, M., & Khanmohammadi, S. (2013). Static Three-Dimensional Fuzzy Routing Based on the Receiving Probability in Wireless Sensor Networks. Computers, 2(4), 152-175. https://doi.org/10.3390/computers2040152