Abstract
The increasing complexity of cybersecurity risks highlights the critical need for novel teaching techniques that provide students with the necessary skills and information. Traditional on-premises laboratory setups frequently lack the scalability, flexibility, and accessibility necessary for efficient training in today’s dynamic world. This study compares the efficacy of cloud-based solutions—specifically, Amazon Web Services (AWS) Elastic Compute Cloud (EC2)—against traditional settings like VirtualBox, with the goal of determining their potential to improve cybersecurity education. The study conducts systematic experimentation to compare lab environments based on parameters such as lab completion time, CPU and RAM use, and ease of access. The results show that AWS EC2 outperforms VirtualBox by shortening lab completion times, optimizing resource usage, and providing more remote accessibility. Additionally, the cloud-based strategy provides scalable, cost-effective implementation via a pay-per-use model, serving a wide range of pedagogical needs. These findings show that incorporating cloud technology into cybersecurity curricula can lead to more efficient, adaptable, and inclusive learning experiences, thereby boosting pedagogical methods in the field.
1. Introduction
The growing threat of cybercrime has boosted global demand for skilled cybersecurity personnel. According to the (ISC)2 2023 Cybersecurity Workforce Study, the global shortage of cybersecurity professionals has grown to 4 million, while Gartner forecasts that global cybersecurity spending is expected to surpass 188 billion USD in 2024 [1,2]. This increased need has put further pressure on educational institutions to create more effective training models that incorporate both theoretical underpinnings and practical skill development.
Traditional on-premises lab facilities, while beneficial, frequently have drawbacks such as high maintenance costs, limited accessibility, and hardware constraints that reduce scalability and efficacy [3]. As the environment of cyber risks changes rapidly, there is a growing demand for modernized instructional practices that make use of emerging technologies [4]. Legacy teaching methods are increasingly seen as ineffective in training students to face real-world cybersecurity concerns [5].
In response, cloud-based virtual labs have developed as a potential alternative. These platforms provide scalable, cost-effective, and adaptable environments that enable students to access realistic cybersecurity simulations from almost anywhere. Cloud-based laboratories improve cybersecurity education’s reach and responsiveness by reducing infrastructure costs and allowing for remote access [6,7,8].
This study compares typical on-premises labs utilizing Oracle VirtualBox against cloud-based labs hosted on Amazon Web Services’ Elastic Compute Cloud (EC2). Five realistic cybersecurity exercises, focusing on penetration testing, malware analysis, incident response, secure coding, and vulnerability assessment, were devised and implemented in both contexts. Key performance parameters, such as lab completion time, CPU utilization, and memory consumption, were employed to assess system efficiency.
The COVID-19 pandemic emphasized the need for adaptive, remote-access learning environments [9]. While traditional labs are frequently limited by physical availability and operational costs [10], cloud-based options offer more flexibility, allowing students to engage in practical exercises without the constraints of fixed-location infrastructure.
Despite the growing popularity of cloud-based labs, current research focuses mostly on user happiness and pedagogical value, with no empirical evidence of infrastructure-level performance indicators. What remains unexplored are measures such as lab completion time, CPU/RAM efficiency, and system responsiveness—all of which are crucial in determining the viability and success of instructional lab environments.
This study fills a research need by providing an organized, performance-oriented comparison of AWS EC2 and VirtualBox environments, utilizing identical lab exercises and evaluation criteria.
Although the current work focuses primarily on technical performance, it establishes the framework for future research that will consider student pleasure, usability feedback, and long-term educational results. The findings add to the expanding discussion about digital transformation in education and highlight cloud-based platforms as critical instruments in the modernization of cybersecurity instruction.
2. Background
2.1. Transition from Traditional to Cloud-Based Labs
The authors of [11] explore UHCL’s transition from traditional physical labs to cloud-based virtual environments. They highlight the significant advantages of virtualization, such as cost savings, improved efficiency, and enhanced resource management. These benefits stem from the cloud’s scalability, flexibility, and ability to bypass physical hardware limitations. However, their study lacked a full assessment of student satisfaction and cross-platform usability, both of which are critical for determining the overall pedagogical impact of cloud-based labs.
2.2. Flexibility and Accessibility of Virtual Laboratories
The COVID-19 pandemic highlighted the importance of flexible and accessible learning environments, requiring remote access to educational resources [12]. Virtual laboratories allow for simultaneous user access and are not limited by physical constraints, making them more adaptable to changing instructional demands.
The author of [13] emphasizes the need to combine academic knowledge with practical experience while acquiring industry-relevant competencies. Cloud-based labs provide an appealing alternative for students with various learning preferences and schedules by allowing them to conduct hands-on tasks remotely. Scalability in cloud infrastructure allows universities to upgrade and expand lab environments more efficiently than physical setups.
This flexibility promotes deeper learning and guarantees that students acquire hands-on experience with real-world tools and technologies. Similarly, Patel et al. [14] showed that such platforms provide scalable resources suitable for cybersecurity training. Agrati et al. [15] stressed the importance of practical activities in increasing student engagement and skill acquisition in digital learning settings, which is critical in cybersecurity education. Furthermore, Sahana et al. [16] discussed how cloud-based systems offer real-time cooperation and effective resource allocation in virtual environments—features that are extremely useful for performing interactive cybersecurity exercises. [17] demonstrated that students who participate in collaborative cloud-based projects report higher levels of motivation and learning pleasure
2.3. Cloud Solutions Are Cost-Effective and Scalable
The authors of [18] examine the use of virtual computing labs (VCL) in cloud computing, highlighting cost reductions and scalability as key benefits. Their research shows that cloud solutions can significantly lower deployment costs with a pay-per-use pricing model, making them cheaper than maintaining physical infrastructure. Scalability enables institutions to respond quickly to changing resource needs in academic environments. Furthermore, the cost-effectiveness of cloud solutions promotes greater access to high-quality cybersecurity training, especially for institutions with limited funding. Despite these benefits, numerous drawbacks persist. Data security is a top priority, necessitating strong protection against illegal access. Additionally, regular internet access is required for continuous learning. To effectively profit from cloud-based education, schools must implement fast, secure connectivity and strict access controls. These procedures are required to ensure both pedagogical quality and operational reliability.
2.4. Deployment of Cyber Range
The authors of [19] investigate cyber range deployment with AWS EC2 and highlight the advantages of scalability and low maintenance overhead in public cloud platforms. They show that EC2-based labs can enable dynamic, large-scale training, but they do not go into detail about specific hands-on activities, which limits their instructional effectiveness.
To remedy this gap, future research should include examples of practical exercises and assess how they affect skill acquisition in cybersecurity training. Although cloud platforms like AWS, Google Cloud, and Azure are rapidly being used in curricula, few studies compare performance across platforms. This study intends to address that hole by comparing AWS EC2 and VirtualBox in terms of lab execution time, resource use, and usability.
2.5. Recent Comparative Studies (2022–2025)
Several recent studies have investigated the transition from traditional on-premises labs to cloud-based infrastructures in cybersecurity and technical education. For example, the author of [20] conducted a multi-institutional study comparing Microsoft Azure-based cybersecurity labs to local virtual machines, concluding that cloud environments improved student engagement but necessitated more institutional planning for cost control and access management. Similarly, the author of [21] investigated student performance and usability in a hybrid approach (local and AWS-hosted laboratories), discovering considerable time savings and flexibility in cloud installations but raising concerns about GUI latency and cost predictability. The author of [22] conducted another important study, comparing Google Cloud-based laboratories to VMware-based local setups for penetration testing courses. There is a dearth of empirical, performance-oriented evaluations—such as completion time, CPU/RAM efficiency, and technical reproducibility—needed to assess the infrastructure-level impact of these lab environments.
Despite these findings, there is still a significant gap in empirical, performance-oriented evaluations—including metrics such as completion time, CPU and RAM utilization, and technical reliability—that are critical for determining the efficacy and infrastructure-level impact of cloud-based lab environments. A recent study highlights the relevance of objective performance measurements in designing scalable and efficient cybersecurity training. Our work fills this gap by performing a thorough quantitative examination of AWS EC2 and VirtualBox configurations, using identical exercises and established performance indicators to assess system responsiveness, resource efficiency, and dependability in constructing cybersecurity laboratories.
3. Research Questions
This study addresses a critical gap in cybersecurity education by empirically comparing cloud-based virtual labs using Amazon Web Services (AWS) EC2 with traditional on-premises labs implemented through VirtualBox. The research is guided by three key questions:
RQ1: How do cloud-based labs utilizing AWS EC2 compare to traditional on-premises labs in terms of lab completion time?
RQ2: What are the differences in CPU and RAM utilization between these two lab environments?
RQ3: In what ways do cloud-based labs enhance the accessibility and scalability of cybersecurity education?
Although interest in cloud-based learning environments is growing, particularly in cybersecurity education, there has been little empirical comparison to traditional settings. Most previous studies focused on theoretical advantages, with little data on performance measures such as lab completion time and resource utilization.
This study quantitatively compares AWS EC2 cloud laboratories with VirtualBox-based on-premises labs utilizing metrics such as execution time, CPU/RAM consumption, and system responsiveness. The results reveal that AWS EC2 provides significant improvements in scalability, remote access, and infrastructure efficiency, allowing for greater access—even on low-power devices—and facilitating remote or hybrid education models. Furthermore, AWS’s pay-as-you-go architecture reduces implementation costs and enables scalable program delivery. These findings not only demonstrate AWS’s educational potential but also pave the way for future integration with other cloud platforms. Overall, the study provides strong empirical justification for incorporating cloud computing within academic cybersecurity training.
4. Methods
The methodology used in this study is based on the concepts stated in [23], where Davis et al. advocate for a comparative comparison of educational contexts. Their findings emphasize the need of using measures like engagement levels and resource consumption to analyze the efficacy of various teaching techniques in cybersecurity education. Furthermore, Prümmer et al. [24] present a comprehensive evaluation technique that combines qualitative and quantitative indicators to successfully assess learning outcomes in cybersecurity training.
This study uses a comparative research design to compare the efficacy of traditional on-premises virtual laboratories using Hypervisor VirtualBox versus cloud-based virtual labs hosted on Amazon AWS in the context of cybersecurity education. The study looks at two key metrics: lab job completion time and resource use (CPU and RAM).
The instructional format consists of PowerPoint lectures supplemented by a lab manual containing 14–16 labs tailored to each course. Pre-recorded video tutorials guide students through the configuration of the virtual environment, including the installation of Oracle VirtualBox and the setup of various guest virtual machines.
4.1. Virtual Lab Setup
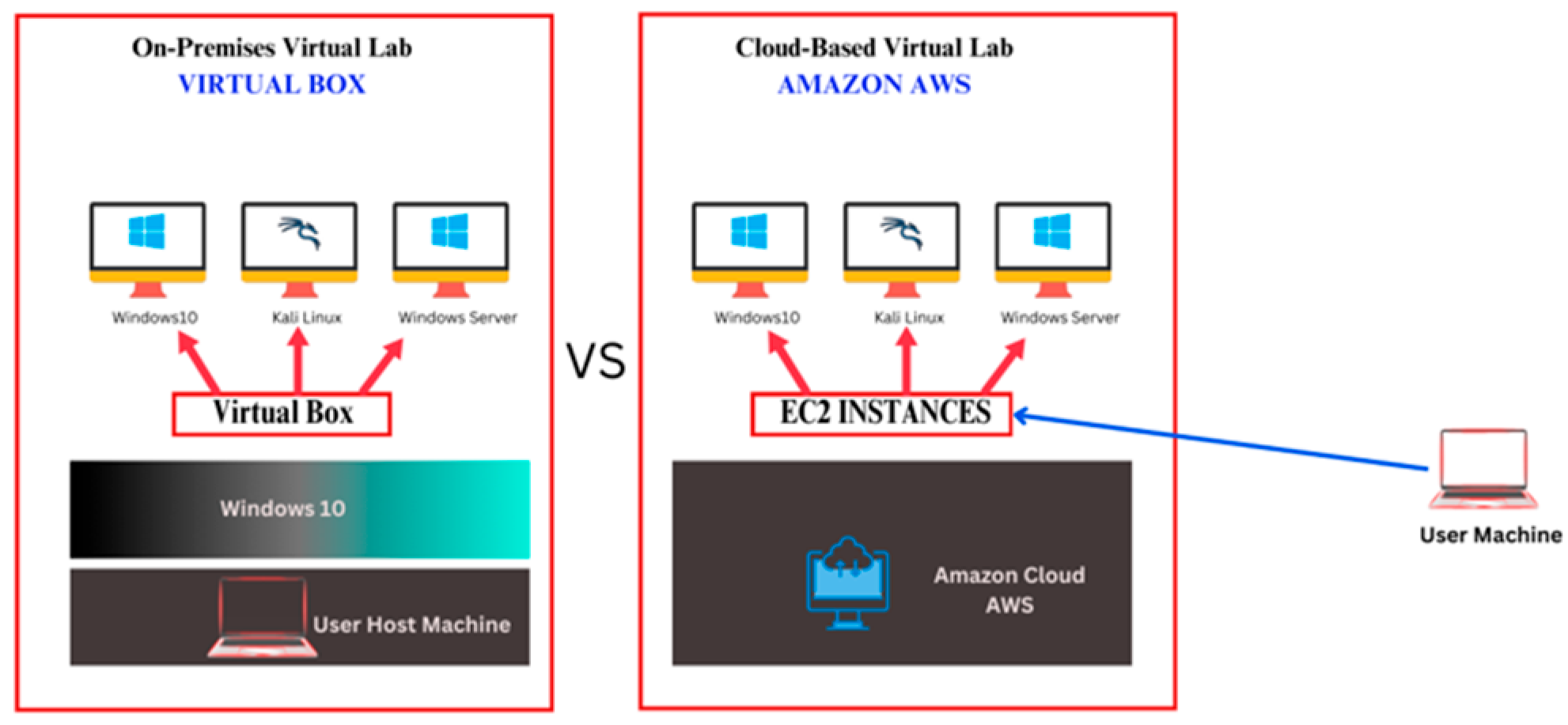
This section describes the virtual lab setups utilized in this study, stressing the differences between on-premises and cloud-based environments. Figure 1 provides an overview of the configurations for both environments, leading to detailed descriptions in the following sections. Table 1 shows the system configuration parameters for the VirtualBox-based on-premises lab and the AWS EC2 cloud-based lab, emphasizing the hardware and software specs required to assure consistency and comparability between environments.
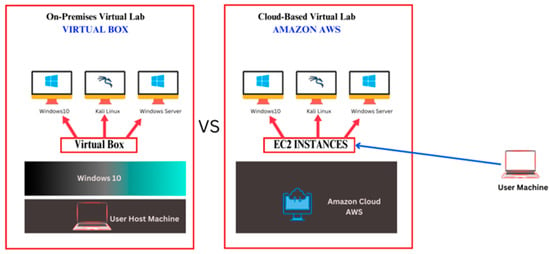
Figure 1.
Comparative configuration of on-premises VirtualBox and cloud-based AWS EC2 labs.

Table 1.
System configuration details for VirtualBox and AWS EC2 used in lab deployment.
On-Premises Lab (VirtualBox)
The on-premises lab setup was built using the author’s personal laptop, which included 8 GB of RAM and a 2.2 GHz processor. VirtualBox was chosen for its low cost, ease of use, cross-platform interoperability, and strong community support, making it perfect for educational and research applications [12,13].
VirtualBox, an open-source hosted hypervisor, enables users to virtualize various operating systems on a single primary system, resulting in a versatile environment for cybersecurity lab exercises [14]. Despite possible security risks, such as being a single point of failure [15], VirtualBox’s cost-effectiveness and versatility coincide with the study’s goals. Previous research has shown that VirtualBox effectively aids IT education by offering a platform for running virtual labs that simulate real-world circumstances. The effectiveness of these labs can be measured by user feedback, engagement, and academic performance [16].
4.2. Experimental Procedures and Data Analysis
This study used a single participant, the author, who performed the cybersecurity lab exercises over numerous sessions in both contexts (on-premises VirtualBox and cloud-based AWS EC2). The participant completed a series of specified tasks in accordance with the lab handbook, which included configuring network components, running penetration tests, examining system logs, and conducting vulnerability assessments.
To record task completion durations, the Step Recorder tool was used to document the start and end times of each exercise, ensuring accurate measurement. Each lab was carried out independently in both environments, with at least three repetitions to account for variability. To guarantee uniformity across test circumstances, each virtual machine was assigned one vCPU in both the VirtualBox and AWS EC2 environments. However, it is crucial to note that the same vCPU allocation does not guarantee equal processing performance. AWS EC2 instances ran on high-performance, server-grade hardware, whereas the on-premises VirtualBox environment was hosted on a laptop with an Intel Core i5. As a result, differences in underlying hardware capabilities may affect completion durations and should be considered when assessing performance comparisons.
The data analysis consisted of computing the average completion time for each task in each environment. To determine if the observed differences were statistically significant, paired t-tests were performed on completion times among contexts. Prior to analysis, we confirmed the assumptions of normality and variance homogeneity. The p-values determined if the differences in lab completion times between VirtualBox and AWS EC2 were statistically significant.
To reduce variability due to differences in participant execution speed, this study used a single consistent volunteer, the author, who completed all lab exercises. This strategy ensured consistent task performance across environments, but it restricts the generalizability of the findings. Future research should include a bigger, more diverse participant pool to capture a wider range of student skills and execution times.
4.3. Experimental Design and Data Collection
This study uses a comparative research design to compare the performance of traditional on-premises virtual labs with VirtualBox to cloud-based virtual labs hosted on Amazon AWS EC2, specifically in the context of cybersecurity education. The experiment entailed executing a series of predetermined lab exercises in both environments under controlled conditions.
Experimental Design: The same lab exercises, including network traffic analysis, ARP poisoning, and penetration testing, were performed in both environments. To counterbalance any learning effects, the order of environment exposure was reversed; in certain iterations, the author did labs on VirtualBox first, then AWS EC2, and vice versa. To maintain consistency, each session was conducted in accordance with a set process.
Data Collection Procedures: The Windows Step Recorder utility was used to automatically record start and finish timestamps during the exercises, accurately capturing the time taken to complete each lab. Screenshots and activity logs were taken at important points—such as before beginning, during resource-intensive processes, and after completion—to offer detailed context. System resource usage (CPU and RAM) was tracked via screenshots taken at critical points using Task Manager (Windows) and the vmstat command in Kali Linux, with the goal of linking resource utilization with task performance and potential bottlenecks. All experiments were pre-tested to ensure proper setup and settings. Ettercap, Wireshark, Hping3, iptables, LEGION, and Nmap were used to complete the lab activities, which simulated real-world cybersecurity scenarios.
Evaluation Criteria: The major metric for comparison was lab completion time, assessed in minutes from start to finish for each activity. Secondary measures included system responsiveness and resource use, notably CPU and RAM consumption, which served as indicators of computational efficiency and system stability. These measurements reveal operational differences between environments, which may affect user experience and productivity.
This methodological approach allows for a systematic, transparent, and replicable comparison of lab performance across the two virtual settings.
4.4. Virtual Machine Configuration
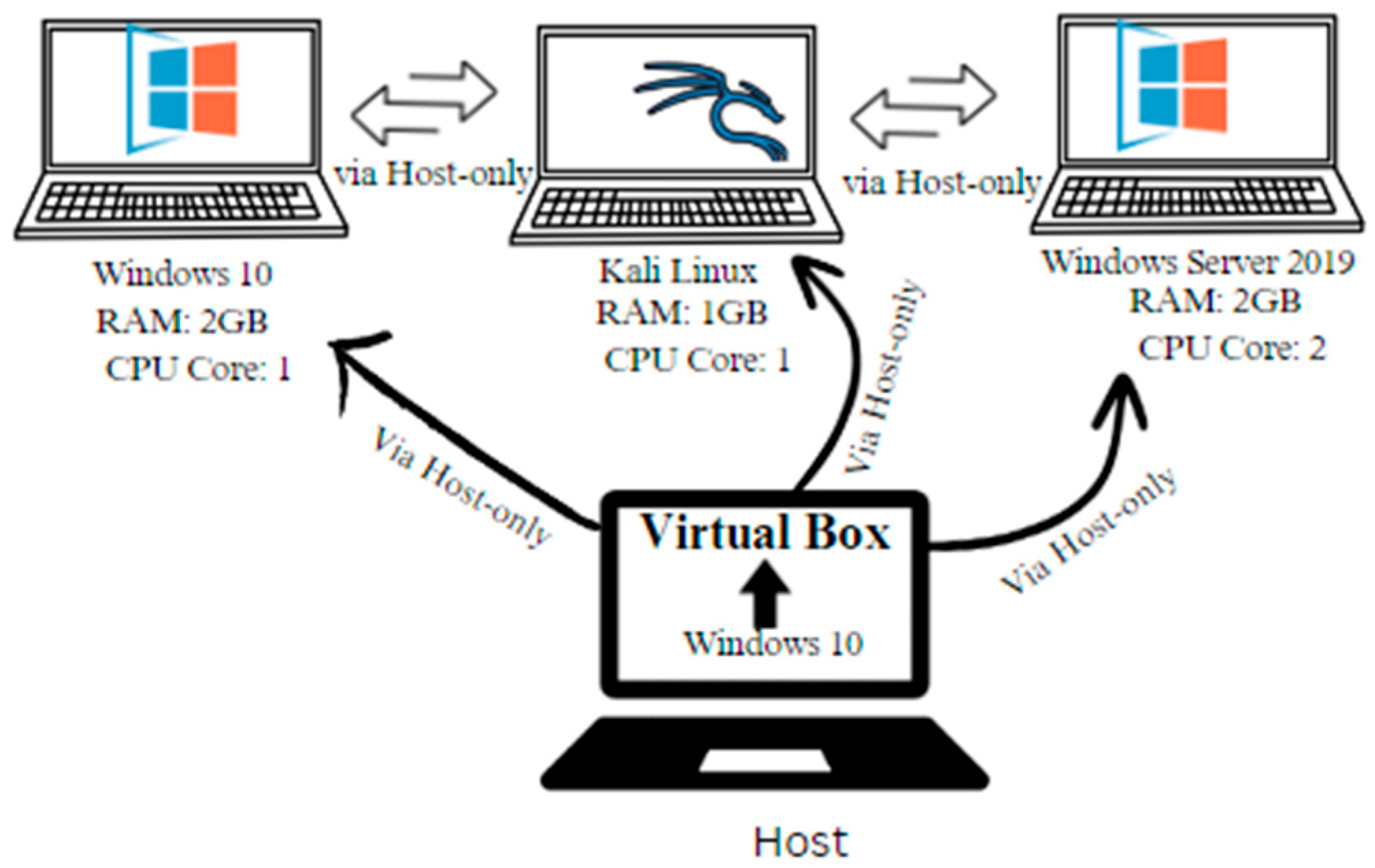
The virtual machine (VM) configuration for the on-premises lab was carefully designed to balance performance requirements and emulate realistic network conditions. Implemented using VirtualBox version 7.1, the setup incorporated several key components, as detailed in Table 2.

Table 2.
The virtual machines (VMs) for the on-premises lab.
This configuration established a reliable and efficient environment for carrying out the lab exercises, allowing the author to mimic genuine cybersecurity scenarios directly on their personal laptop. The VirtualBox Manager interface includes the three virtual machines used in this study: Kali Linux, Windows 10, and Windows Server 2019. These virtual computers were critical in enabling a variety of cybersecurity exercises, as mentioned in the Virtual Machine Configuration section.
Figure 2 shows a thorough architectural overview of the virtual machine setup, with a focus on the host-only network configuration. This arrangement was critical in enabling flawless internal communication among the virtual computers while isolating them from external networks. By using a host-only network, the virtual machines could communicate with one another without revealing their operations to the rest of the internet, improving security during important cybersecurity exercises. This architecture enabled successful testing and simulation of numerous attack and defense scenarios, ensuring that the virtual environment closely matched real-world conditions while providing a regulated and safe framework for experimentation.
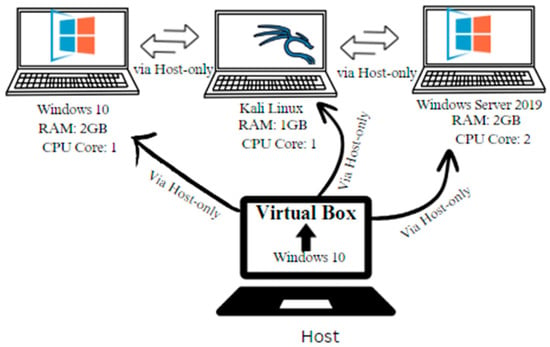
Figure 2.
VirtualBox setup architecture with host-only network (10.0.0.x).
4.5. Cloud-Based Lab (AWS)
Amazon Elastic Compute Cloud (EC2) is a virtual server service provided by Amazon Web Services (AWS) that falls under the category of infrastructure as a service (IaaS) [17]. EC2 was chosen for the cloud-based lab due to its feature-rich nature, stability, and commercial availability [18]. One of the key reasons for selecting AWS EC2 is its scalability, which allows users to easily adjust the capacity of virtual servers based on demand [19]. This scalability is facilitated through features like auto-scaling and load-balancing, ensuring that resources can be dynamically allocated as needed [25]. Additionally, EC2 offers flexibility in configuring and deploying virtual machines, enabling users to customize their computing environments according to specific requirements [20].
In addition, AWS EC2 was chosen above alternative platforms such as Microsoft Azure Lab Services and Google Colab because of its infrastructure-as-a-service (IaaS) flexibility, full OS-level control, and compatibility with advanced cybersecurity tools and network setups. Google Colab, which is geared for notebook-based data science jobs, does not allow virtual network simulations or system-level operations like ARP poisoning or firewall rule testing. While Azure Lab Services simplifies lab management, it comes at a greater operational cost and limits control over networking and virtualization layers. AWS EC2, on the other hand, enables detailed control over virtual network interfaces, security groups, and system resources, all of which are necessary for simulating realistic cybersecurity training environments.
Furthermore, AWS EC2 is known for its ease of configuration and deployment of virtual machines, making it a preferred choice for various applications. The platform is based on XEN para-virtualization technology, which provides the capability to size instances based on the EC2 Compute Unit (ECU) [24]. Moreover, EC2 instances are virtual servers that can be rented and configured by users, offering a high level of control over the computing environment [26]. The service also provides features such as virtual private clouds, elastic block stores, elastic load balancing, internet protocol (IP) addresses, route services, and high-performance computing clusters, enhancing its flexibility and usability [27].
In conclusion, AWS EC2 stands out as a robust choice for cloud-based labs due to its scalability, flexibility, and ease of configuration and deployment of virtual machines. The platform’s feature-rich environment, stability, and commercial availability make it a reliable option for various computing needs.
4.6. AWS EC2 Instance Configuration for Virtual Lab SETUP
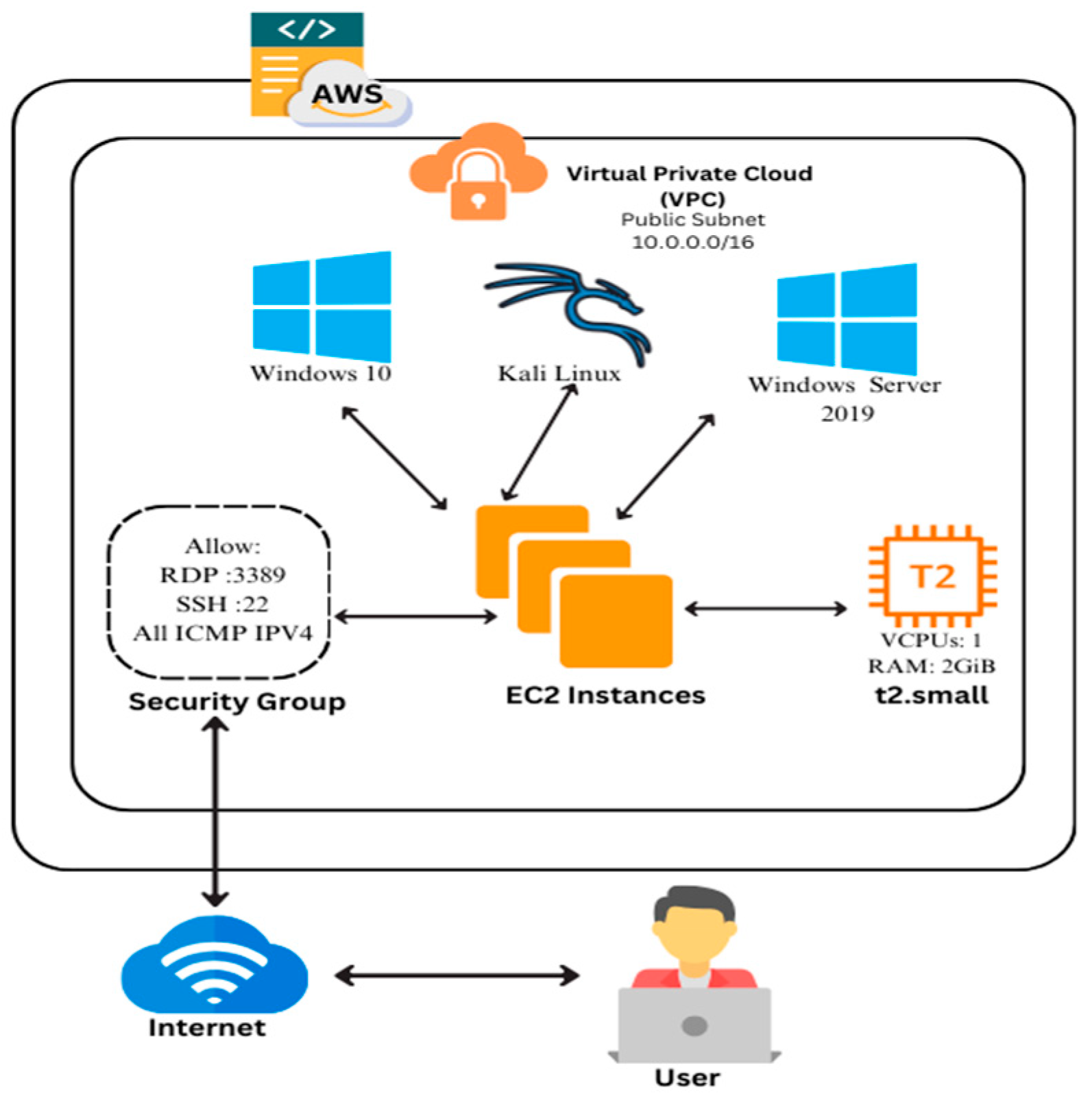
The following steps detail the configuration and deployment process of the EC2 instances, focusing on the architecture and the rationale behind the choices made. As shown in Figure 3, the VPC was configured with a public subnet of 10.0.0.0/16, allowing the EC2 instances to be accessed securely over the internet.
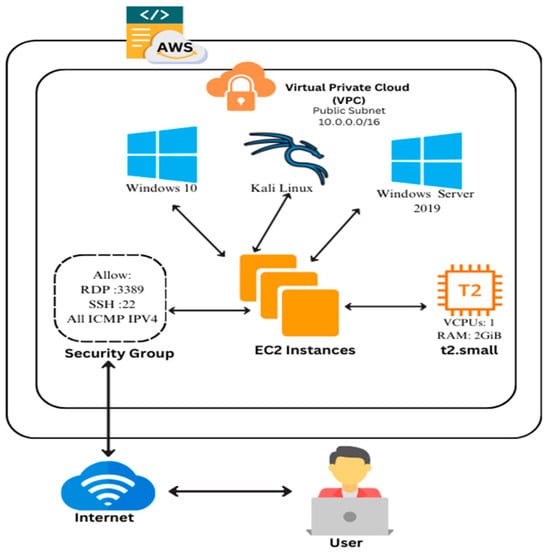
Figure 3.
AWS cloud-based lab architecture with public subnet configuration.
To establish consistency between the cloud and on-premises settings, three EC2 instances were deployed: Kali Linux, Windows Server 2019, and Windows 10. These instances were carefully configured to match the resources allocated in the VirtualBox setup, resulting in a fair comparison of performance and usability. Table 3 displays the configuration options for the AWS EC2 instances used in the cloud-based virtual lab environment, including operating systems, instance kinds, and resource allocation.

Table 3.
AWS EC2 instances configured for the cloud-based virtual lab environment, including Kali Linux, Windows Server 2019, and Windows 10.
The t2.small instance type was specifically chosen to maintain resource parity with the on-premises VirtualBox system, which assigns one vCPU and 2 GB RAM to each virtual machine. While newer instance types, such as t3.small and t3.micro, offer better performance and cost-efficiency in burstable applications, they are AWS Nitro System compatible and may create variability owing to CPU credit-based throttling. In contrast, t2.small instances are built on a well-established platform that supports a diverse set of AMIs, including the older Windows and Linux editions used in this study. Furthermore, the t2 instance type matches the educational funds available at the time of deployment, making its use more predictable. This makes t2.small the most stable and pedagogically relevant alternative for consistent testing against local hardware with predictable throttling behavior.
Each instance in our virtual lab was set up using the t2.small instance type, which includes one vCPU and two gigabytes of RAM. This configuration is identical to our on-premises VirtualBox system, where each virtual machine is allotted one core CPU and two gigabytes of RAM. Maintaining resource parity across cloud and on-premises systems is crucial for our research as it enables a fair comparison of performance metrics across both setups.
Users accessed the pre-configured EC2 instances via Remote Desktop Connection, allowing them to interact with each operating system as if using a local PC. This setup creates a flexible and adaptive environment for conducting cybersecurity lab exercises, enhancing the overall learning experience.
4.7. Virtual Private Cloud (Vpc) Configuration
The first step in setting up our virtual lab involved the creation and configuration of a virtual private cloud (VPC). The VPC was configured with a public subnet of 10.0.0.0/16, providing a private, isolated network for our lab environment. This configuration is critical for maintaining data integrity and security, as emphasized in [28], Bernardo, Malta, and Magalhães present an evaluation framework for cybersecurity maturity aligned with the NIST Cybersecurity Framework. They emphasize the importance of strong infrastructure and secure network segmentation to withstand operational challenges like natural disasters and cyber threats. The subnet was assigned to the availability zone us-east-1e, ensuring that all resources within this lab environment were located within the same geographical and logical boundary. This strategic placement reduces latency and enhances performance consistency, which is vital for applications demanding high availability and reliability.
4.8. Ec2 Instance Deployment
To ensure consistency between the cloud-based and on-premises environments, three EC2 instances were deployed: Kali Linux, Windows Server 2019, and Windows 10. These instances were carefully configured to match the resources allocated in the VirtualBox setup, ensuring a fair comparison in terms of performance and usability. Table 3 highlights the setup settings for the AWS EC2 instances utilized in the cloud-based virtual lab environment, such as operating systems, instance kinds, and resource allocation.
Each instance in our virtual lab was configured with the t2. small instance type, which has one vCPU and two gigabytes of RAM. This configuration mirrors that of our on-premises VirtualBox system, where each virtual machine is similarly assigned one core CPU and 2 GB of RAM. Maintaining resource parity between the cloud and on-premises systems is critical for our study, as it allows for a fair comparison of performance measures across both setups. Brilingaitė, Bukauskas, and Juozapavičius [29] emphasize the importance of resource allocation in cloud environments. Their frameworks for competence development and assessment in hybrid cybersecurity exercises highlight how appropriate resource allocation strategies can optimize the performance and reliability of virtual machines in private cloud data centers. This alignment ensures that our cloud-based instances effectively replicate the performance characteristics of their on-premises counterparts.
Users connected to the pre-configured EC2 instances using the Remote Desktop Connection, which allowed them to interact with each operating system as if they were working on a local PC. This arrangement provides a fluid and adaptable environment for completing cybersecurity lab exercises, hence improving the overall learning experience.
4.9. Security Group Configuration
Security is an important factor when building cloud-based infrastructures, especially in settings built for cybersecurity training exercises. To provide secure and regulated access to the Amazon EC2 instances used in this study, a dedicated security group was rigorously set up with a thorough set of incoming rules defining the permissible types of network traffic. These parameters enable RDP and SSH access, as well as important web traffic and network diagnostic protocols such as ICMP (ping) inquiries. Table 4 shows the parameters for these inbound rules.

Table 4.
Configuration of inbound rules for network access control.
These security group rules are intended to ensure that users may securely connect to and interact with EC2 instances while offering the flexibility needed for network-related exercises that include both web access and network testing capabilities. Each rule has been carefully crafted to allow necessary traffic while maintaining the security of the lab environment, resulting in a safe and successful learning experience.
Furthermore, security group configurations should be reviewed and updated on a regular basis to respond to emerging security risks and ensure compliance with best practices. Implementing logging and monitoring tools, such as AWS CloudTrail and VPC Flow Logs, can help improve visibility into traffic patterns and security events, allowing for prompt reactions to any anomalies discovered in the environment.
4.10. Cost Consideration
Cost is an important issue when considering cloud resources, especially in educational settings where budgets are sometimes limited. The decision to use the t2. small instance type was based not just on resource allocation but also on cost-effectiveness. The prices for the different operating systems are as follows:
- -
- Windows 10 (Bring Your Own License, BYOL): 0. USD/h
- -
- Windows Server 2019: 0.046 USD/h.
- -
- Kali Linux costs 0.023 USD/h.
These rates are considered appropriate in the educational context, allowing for the provision of a scalable, on-demand lab environment that matches user expectations while being financially viable. This technique ensures that educational institutions can efficiently use cloud technology without exceeding their budgets.
While these instance costs provide flexibility and control, we recognize that this comparison does not yet account for additional expenses such as VirtualBox licensing (free and open-source), local infrastructure depreciation, maintenance costs, or instructor effort associated with setup and support. These issues will be addressed in future work to permit a comprehensive financial assessment.
4.11. Student Access and Interaction
The study was done at the College, where students frequently face hardware limits in college labs and on their personal laptops. These constraints—such as system latency, limited RAM and CPU capacity, and restricted access to labs from home—significantly limit their ability to participate fully in lab exercises, particularly those that need considerable computer networking skills. To solve these issues and guarantee everyone has access to hands-on training, five cybersecurity lab exercises were carefully designed and deployed in both VirtualBox (on-premises) and AWS EC2 (cloud-based) settings. This dual configuration not only suited students with restricted computing resources but also allowed for an organized performance comparison of the two platforms.
The study’s use of the same lab tasks in both environments enabled systematic observation of important performance metrics such as completion time and resource use (RAM and CPU). This concurrent deployment method also ensured that instructional delivery and assessment were consistent across platforms. Furthermore, it provided an opportunity to assess the pedagogical and technical feasibility of cloud-based solutions in situations when local infrastructure may be insufficient.
The lab activities chosen were matched with certain learning outcomes outlined in the undergraduate cybersecurity curriculum. For example, Lab 1 (Hping3 and Wireshark) focuses on packet inspection and network protocol analysis. Lab 2 (iptables) covers access control and secure firewall configuration. Labs 3 and 4 (LEGION and Nmap) strengthen vulnerability assessment, scanning, and enumeration techniques, whilst Lab 5 (Ettercap) teaches how to detect and respond to man-in-the-middle assaults. These activities directly support course-level outcomes like identifying security vulnerabilities, establishing secure systems, and understanding network behavior, which are frequently mirrored in institutional syllabi and national cybersecurity frameworks (for example, NICE and ACM/IEEE guidelines). This alignment ensures that the lab content is both technically solid and educationally relevant.
Table 5 highlights the five lab exercises, which are designed to imitate real-world cybersecurity events and help students improve their practical abilities and comprehension of basic cybersecurity principles.

Table 5.
Description of the lab exercises.
To assess the efficiency of the lab exercises using performance metrics, the following performance data will be gathered:
- -
- Completion Time: The time required for students to finish each lab exercise in both environments (VirtualBox and AWS EC2).
- -
- Resource Usage: The RAM and CPU consumption during each lab exercise, as assessed in both environments.
This complete method not only solves students’ hardware restrictions but also gives vital insights into the performance and usability of cloud-based versus local virtual environments in cybersecurity education.
4.12. Data Collection and Tools Used in Lab Activities
To achieve accurate and comprehensive data gathering throughout the lab studies, a systematic strategy was used. Before beginning the actual lab operations, the researcher performed pre-tests in both the VirtualBox environment and the AWS EC2 instances. This preliminary process ensured that all necessary tools, configurations, and settings were properly installed and functional, allowing subsequent operations to go smoothly and without interruption. Any additional tools or tweaks needed during pre-testing were pre-configured, reducing any disturbances during live sessions and guaranteeing consistency in data collection.
- -
- Time Tracking and Workflow Recording: Using the Windows Step Recorder software, participants were able to record their real time spent on each lab, rather than setting fixed time constraints. This application generated complete HTML reports by automatically collecting extensive information such as start and end timestamps, screenshots of user interactions, and step-by-step instructions. Such logs offered clear, consistent recordings of each session, allowing for exact assessment of productive time and workflow analysis.
- -
- Monitoring system resource utilization during lab sessions helps evaluate efficiency in both contexts. The Windows Task Manager was used to collect real-time CPU and RAM use data for both VirtualBox guest machines and the host system. In Kali Linux installations, the vmstat terminal utility was used to capture performance parameters at important points—before beginning, during resource-intensive operations, and after completion. Screenshots of these metrics were taken at pre-determined intervals to aid the future investigation of system bottlenecks and resource contention issues.
- -
- Individual user skills and familiarity with the activities should also be considered when determining lab completion times. To account for this variability, the current study included a single consistent subject, the author, who completed all lab tasks. This strategy maintained consistent task execution across both environments, but it restricts the generalizability of the findings.
- -
- Furthermore, while virtual machines in both VirtualBox and AWS EC2 settings were given the same nominal resources (2 GB RAM and assigned vCPUs), the underlying hardware varied dramatically. AWS EC2 instances run on high-performance server-grade equipment, whereas the on-premises setup used a consumer-grade laptop with an Intel Core i5 processor. Differences in hardware performance might have an impact on execution speed and should be considered when interpreting comparable results. Due to hardware limits, specified lab activities could not be completed in some cases using the usual VirtualBox setup. For example, during Lab 5 (ARP poisoning with Ettercap), the host system’s CPU utilization reached 100%, causing the machine to stall and fail to complete the task. Similarly, in Lab 1, when Hping3 and Wireshark were employed for packet modification and traffic capture, resource congestion produced delays and instability. These problems did not exist in the AWS EC2 environment, where server-grade architecture supplied the necessary headroom for smooth and uninterrupted operation. These discoveries were captured in system logs and images, demonstrating the limitations of consumer-grade technology in enabling network-intensive cybersecurity simulations.
- -
- Experimental Setup and Environment Preparation: Experiments were carried out on a personal laptop with 8 GB of RAM and a 2.20 GHz quad-core processor. Each virtual environment—VirtualBox and AWS EC2—was allotted 2 GB of RAM to ensure a consistent platform for comparison. To ensure consistency, both environments were pre-configured with identical operating systems and cybersecurity technologies.
Tools Utilized:
- -
- Ettercap for performing ARP poisoning and demonstrating man-in-the-middle attacks
- -
- Wireshark for capturing and analyzing network traffic
- -
- Hping3 for crafting custom network packets
- -
- iptables for configuring software-based firewall rules
- -
- LEGION for conducting vulnerability assessments through port scanning
- -
- Nmap for comprehensive network scanning and service enumeration
Five cybersecurity lab exercises were designed to simulate real-world attack and defense scenarios. Each exercise was executed in both the on-premises VirtualBox environment and the cloud-based AWS EC2 environment. To ensure consistency and streamline deployment, all operating systems and required tools were pre-configured in advance, using OVA files for VirtualBox and pre-built Amazon Machine Images (AMIs) for AWS EC2 instances.
Documentation and Evidence Collection: The researcher documented each session using the lab template, including screenshots of system performance (Task Manager and vmstat) and task execution. These records facilitated thorough post-hoc analysis, allowing for the linkage of completion durations with resource use and user activity. Data consistency was maintained across contexts by standardizing techniques and setups, resulting in valid comparisons that matched the research aims.
This structured data collection methodology allowed for a thorough evaluation of the efficiencies, resource consumption, and practical challenges associated with VirtualBox and AWS EC2-based virtual labs, resulting in a more nuanced understanding of their respective performance in cybersecurity education.
4.13. Absence of Detailed Cost-Benefit Analysis
The study shows the affordability of cloud-based labs, but lacks a full cost-benefit analysis compared to traditional settings. Costs for infrastructure maintenance, software licensing, instructor setup time, and student technical help were not estimated in either context. Future research will include a thorough cost-benefit analysis to compare the total cost of ownership (TCO) and instructional efficiency across deployment models.
5. Results
This section presents the data from a comparison between on-premises virtual labs (VirtualBox) and cloud-based labs (AWS EC2). The findings are consistent with the research questions (RQs), resulting in targeted insights.
5.1. Lab Completion Time (RQ1)
RQ1: How do cloud-based labs utilizing AWS EC2 compare to traditional on-premises labs in terms of lab completion time?
Lab completion time is an important metric for assessing the efficacy of virtual lab settings in cybersecurity education. A systematic strategy was used to ensure accuracy and dependability while measuring this parameter.
- -
- Each laboratory activity was carried out in both VirtualBox and AWS EC2, with the environment usage sequence randomized between sessions to reduce learning effects.
- -
- The Step Recorder tool was used to precisely record the start and end times of each lab session, allowing for accurate evaluation of job durations.
Activity logs and screenshots were taken at strategic moments to confirm process steps and detect any technical difficulties, such as system slowdowns or crashes.
This thorough methodology enabled consistent comparisons of performance across contexts. Notably, AWS EC2 considerably accelerated the completion of all lab assignments. For example, the network traffic analysis lab, which used Hping3 and Wireshark, took about 5.5 min to finish on AWS EC2 versus 11 min on VirtualBox. Similarly, the ARP poisoning lab using Ettercap was completed in 15 min on AWS EC2, although resource limits in VirtualBox frequently prevented full completion.
To further assess performance, lab completion time was employed as a major metric of system responsiveness and efficiency. This statistic is especially important in educational settings, since time constraints and resource availability affect learning outcomes. Combining these findings with resource utilization statistics obtained from system monitoring tools demonstrated a clear link between higher efficiency and enhanced system performance.
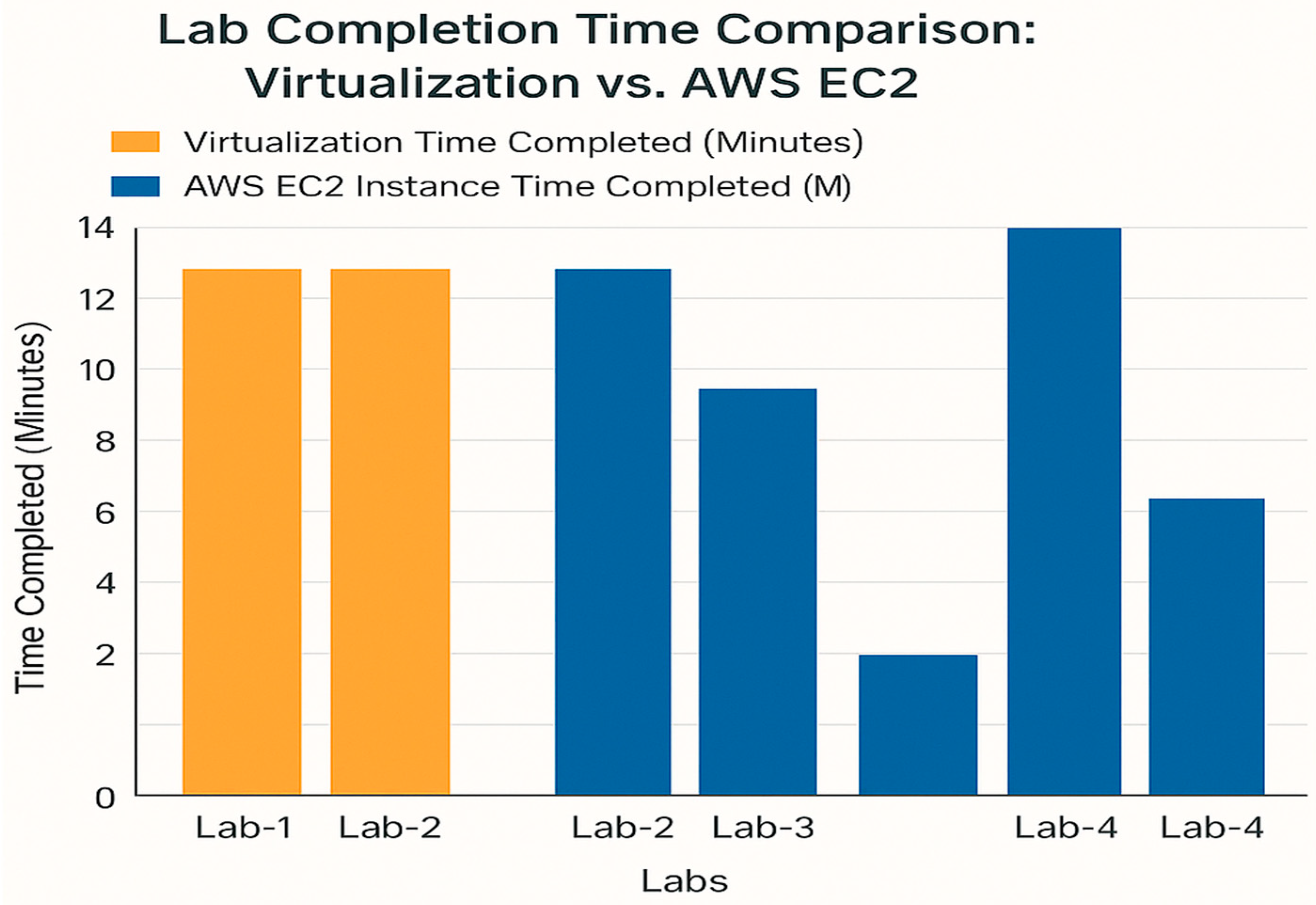
As shown in Figure 4, statistics show that cloud-based settings such as AWS EC2 provide significant benefits in terms of faster lab completion times, most likely due to reduced resource contention and increased scalability. These findings are consistent with previous research [30,31], which found similar efficiency gains in cloud-based educational environments, highlighting how scalability removes bottlenecks and speeds up job execution.
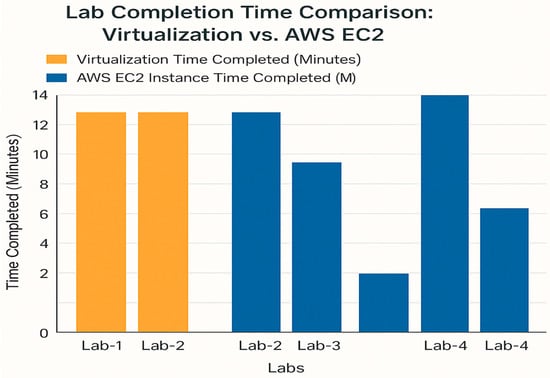
Figure 4.
Lab completion time comparison for VirtualBox and AWS EC2 instances.
Figure 4 illustrates that AWS EC2 consistently demonstrated faster completion times across all labs compared to VirtualBox. For instance, Lab 1, which involved using Hping3 with Wireshark for network traffic analysis, was completed in approximately 5.5 min on AWS EC2, whereas the same task took 11 min on VirtualBox. This finding is consistent with the work of Almomani, Ahmed, and Maglaras [31], who underlined the importance of modern cloud infrastructure in boosting operational efficiency within cybersecurity training environments in higher education. A similar finding is confirmed by Aliyu et al. [32], who established a comprehensive cybersecurity maturity paradigm emphasizing the importance of scalable and robust systems in improving the effectiveness of digital learning platforms. The results show that cloud-based solutions allow students to finish labs faster, most likely due to improved resource availability and scalability. Similarly, Lab 5, which involved ARP poisoning using Ettercap, was completed in just 15 min on AWS EC2, in contrast to the VirtualBox environment, where resource limitations prevented the lab from being finished. These findings suggest that cloud-based solutions offer significantly faster completion times, likely due to reduced resource contention and better scalability.
This empirical outcome is consistent with other research, such as [31,32], which emphasize the operational and educational benefits of cloud-based systems. It also aligns with prior findings [32,33], which highlight the efficiency advantages of cloud platforms in educational contexts.
5.2. CPU and RAM Utilization Analysis (RQ2)
RQ2: What are the differences in CPU and RAM utilization between these two lab environments?
CPU utilization statistics give useful information about the computational efficiency of each environment. The chart below compares CPU consumption in VirtualBox and AWS EC2 settings, which include both virtual machines and host systems.
To guarantee consistency across environments, both VirtualBox and AWS EC2 were pre-configured with identical operating systems and cybersecurity tools, with VirtualBox utilizing OVA files and AWS EC2 using pre-built Amazon Machine Images (AMIs), respectively. This standardization allowed for a fair evaluation of resource use, separating the impact of virtualization technology and hardware architecture on performance. Figure 5 has been changed to improve clarity and interpretability. It now uses a grouped bar chart with explicit color coding and direct value labels for each component (VirtualBox guest, VirtualBox host, AWS EC2 guest, and AWS EC2 host). The revised title and caption fully define each component, ensuring that the figure adds to the debate in an understandable and reader-friendly manner.
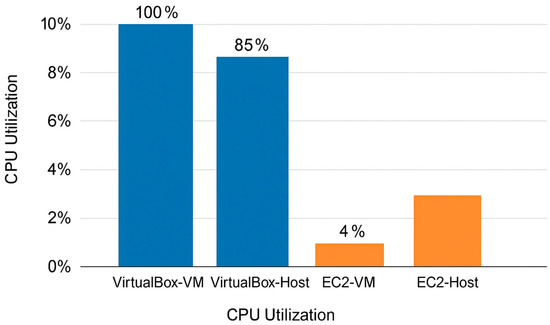
Figure 5.
Comparative CPU utilization in VirtualBox and AWS EC2—guest and host systems across lab exercises.
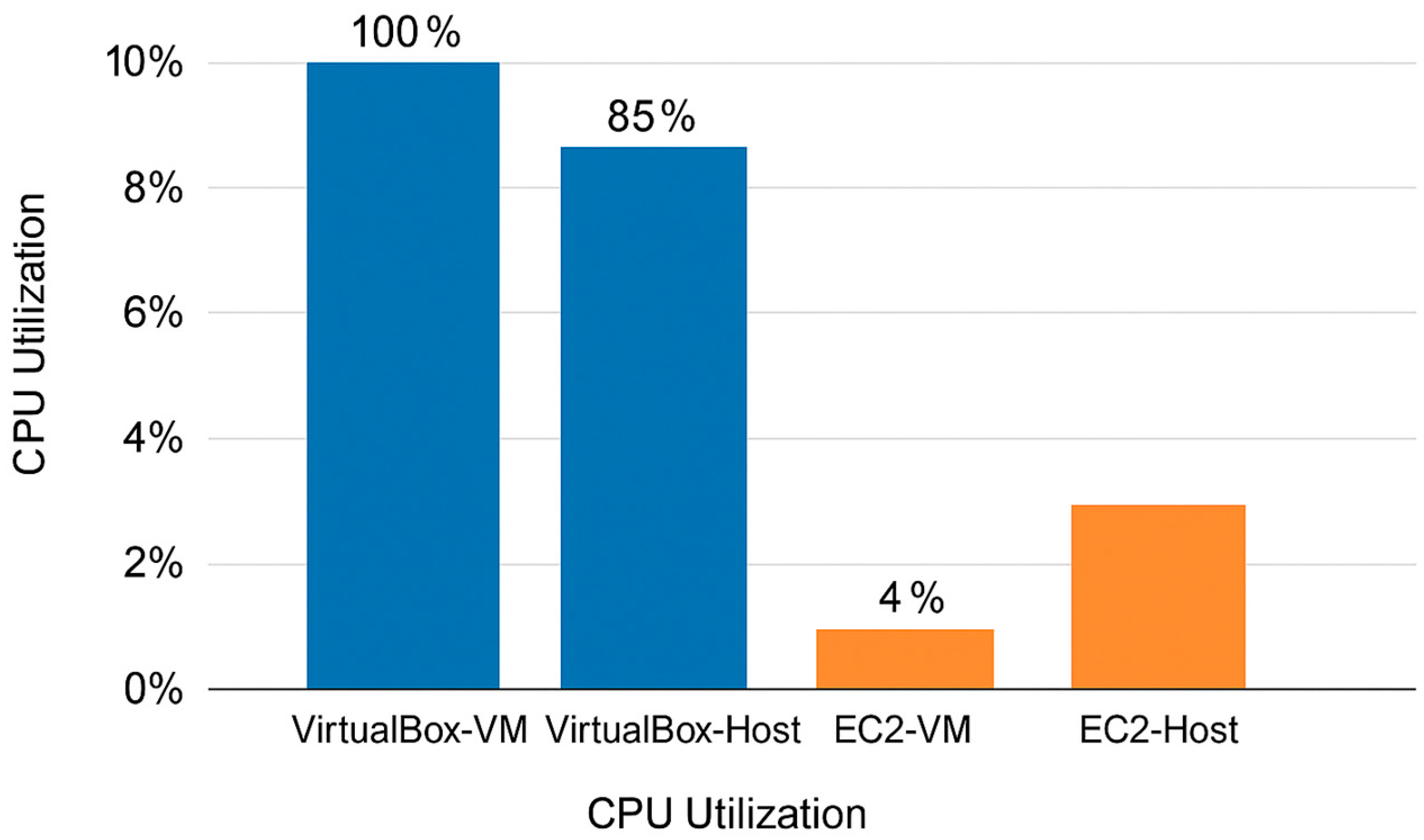
Figure 5 shows that VirtualBox environments regularly have higher CPU utilization than AWS EC2 instances. For example, in Lab 2, which entailed establishing a software firewall in Kali Linux with iptables, CPU utilization in the VirtualBox system peaked at 100% on the guest and 85% on the host computers. In contrast, the AWS EC2 instance had a substantially lower CPU utilization of only 4%, while the host computer only reached 15%. This apparent contrast indicates that AWS EC2 can manage computational activities more efficiently, decreasing the strain on individual instances and the host system, resulting in smoother and more reliable performance.
This observation is like the findings of Al-Zubaidie, Muhajjar, and Shihabe in [32], where they reported that cloud-based environments often exhibit lower CPU usage due to their scalable architecture, a conclusion further supported in [34].
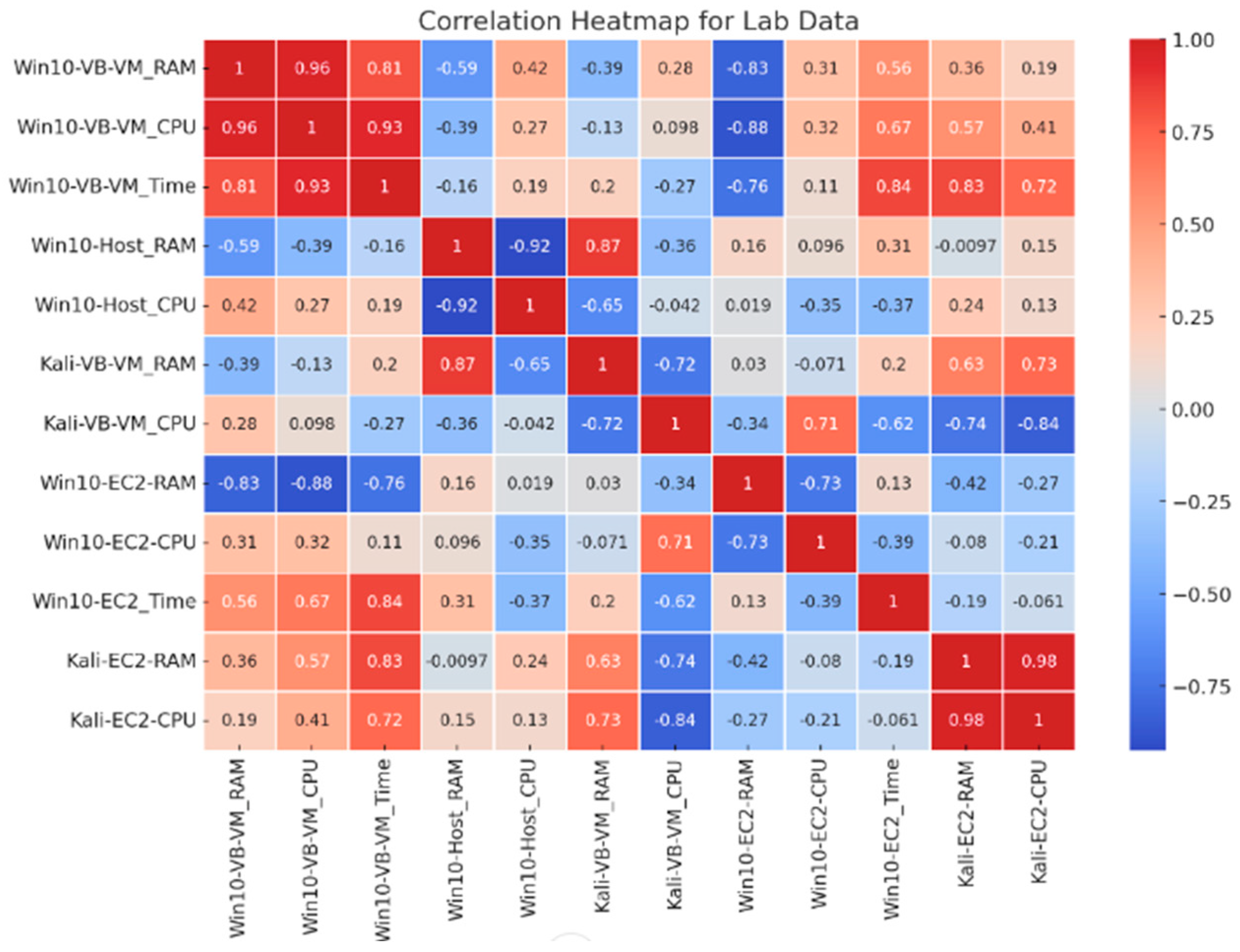
Figure 6 shows the correlation heatmap of CPU consumption, RAM usage, and lab completion times. It shows a significant positive relationship between VirtualBox CPU consumption and RAM exhaustion, as well as a lower correlation between AWS EC2 resource usage and task completion times, indicating more efficient resource use in cloud environments. The hues range from red (strong positive correlation) to blue (strong negative correlation), making it possible to visually examine the degree and direction of correlations between each pair of variables. For example, there is a significant positive correlation (0.96) between Win10-VB-VM_RAM and Win10-VB-VM_CPU. A high negative correlation (−0.88) exists between Win10-VB-VM_CPU and Win10-EC2-RAM.
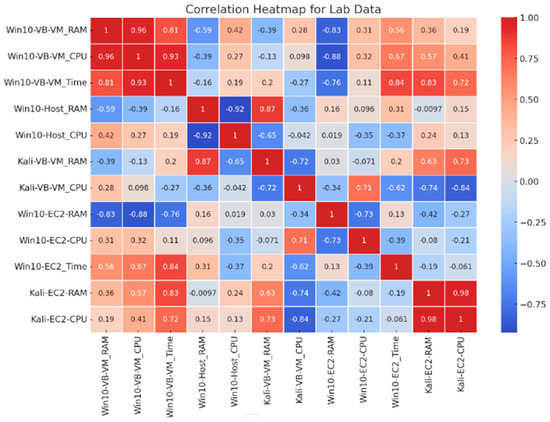
Figure 6.
Correlation heatmap showing relationships between RAM, CPU, and lab completion time.
Overall, these findings illustrate the benefits of cloud platforms such as AWS EC2 in terms of performance efficiency and resource management, providing a nuanced perspective that complements current literature while pointing out some limits of traditional virtualization methodologies.
5.3. Ram Utilization (RQ2)
RQ2: What are the differences in CPU and RAM utilization between cloud-based labs and on-premises labs?
RAM utilization is another critical factor influencing the performance of virtual lab environments. Figure 6 shows the RAM usage for both VirtualBox and AWS EC2 environments, considering both the guest machines and host systems.
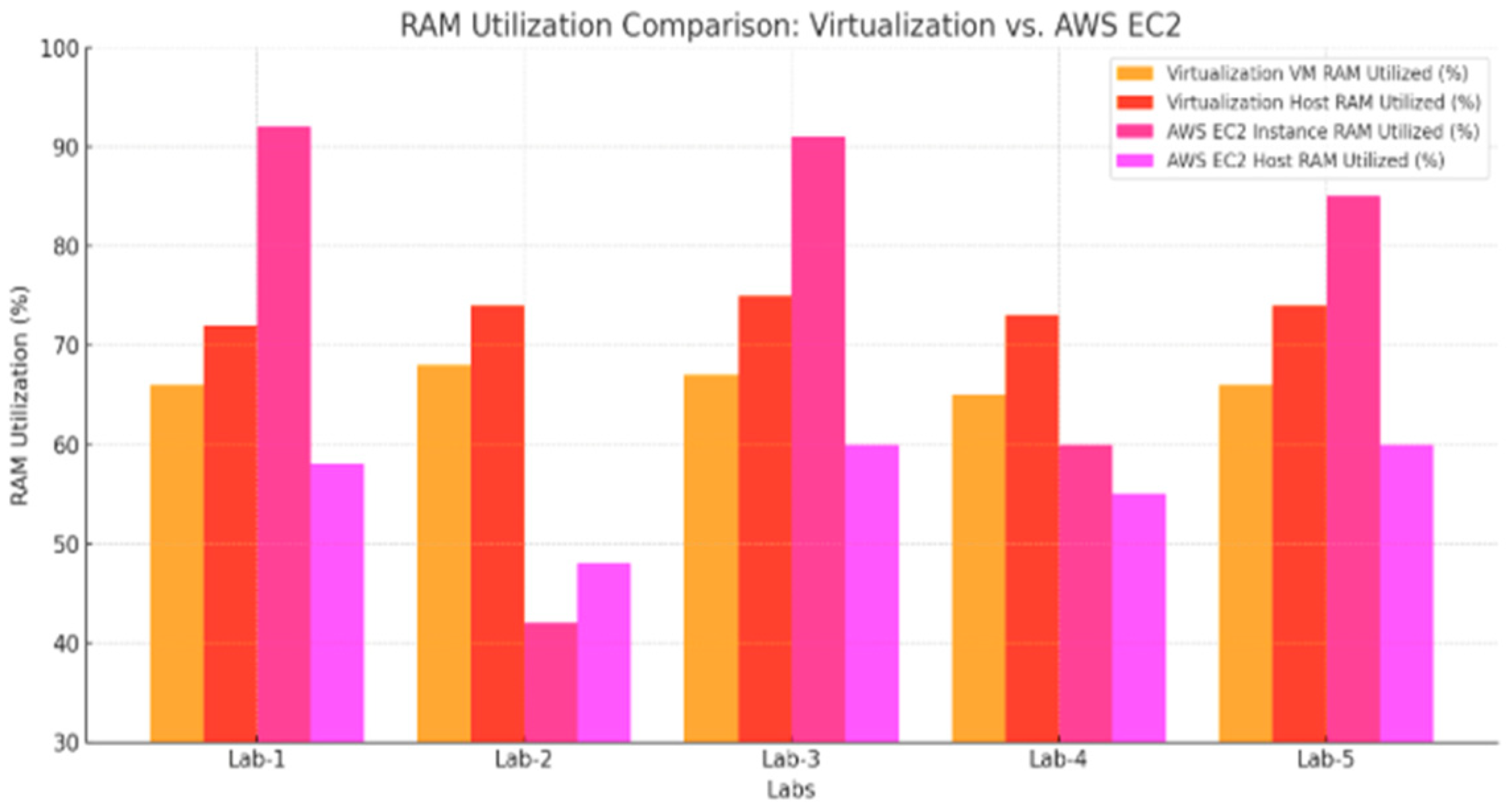
As depicted in Figure 7, AWS EC2 consistently demonstrated lower and more consistent RAM utilization across all labs. For example, in Lab 3, which involved exploring network ports using LEGION, the AWS EC2 instance recorded a maximum RAM usage of 56%, whereas the VirtualBox guest machine peaked at 62%, with the host machine’s RAM usage soaring to 89%. This data suggests that the cloud-based environment of AWS EC2 offers a more balanced and optimized use of memory resources, minimizing the impact on the host system and reducing the likelihood of resource exhaustion.
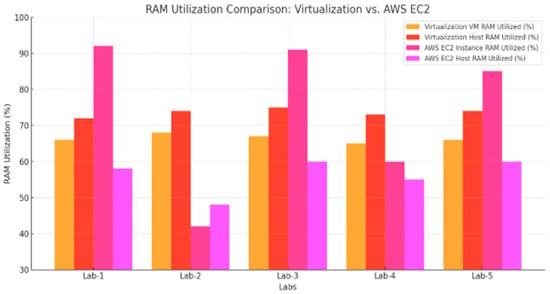
Figure 7.
RAM utilization comparison for VirtualBox and AWS EC2 instances including the host machine.
5.4. Summary of Findings (RQ3)
RQ3: In what ways do cloud-based labs enhance the accessibility and scalability of cybersecurity education?
One of the primary benefits of cloud-based labs is their capacity to expand accessibility dramatically. Unlike traditional techniques, which rely on physical hardware and infrastructure, cloud solutions allow students to access instructional resources from anywhere with an internet connection. This is particularly important in cybersecurity education, where hands-on, practical experience is required. For example, remote laboratories developed for cybersecurity training have been found to improve student interest and skill acquisition by providing a modular platform capable of supporting a wide range of modules from fundamental protocol analysis to sophisticated threat management [28]. Such accessibility enables students to complete courses at their own pace and convenience, enhancing their entire learning experience.
Students’ qualitative evaluation reinforces these advantages. Participants felt that the remote access environment really improved their learning. For example, students reported that:
Student A: “The remote access provided by the AWS EC2 environment made it easier for me to practice cybersecurity tasks outside of scheduled lab hours, which helped me reinforce my learning.”
Student B: “Using the cloud-based labs significantly improved my understanding of complex network concepts because I could access the environment anytime and from anywhere.”
Student C: “The convenience of remotely accessing the labs reduced setup time and allowed me to focus more on learning the material rather than configuring systems.”
These responses demonstrate how the flexibility and accessibility of cloud-based labs actively contribute to enhanced learner engagement and self-directed learning.
Another significant advantage of cloud-based labs is their ability to scale. Traditional systems, such as those that use VirtualBox, are limited by the physical capabilities of host machines, which might limit the number of concurrent users and the intricacy of exercises. In contrast, cloud technologies such as AWS EC2 provide on-demand scalability, allowing institutions to distribute resources flexibly based on current educational demands. This adaptability enables educators to quickly respond to changing class sizes and activity needs. Furthermore, speedy VM deployment allows students to focus on gaining practical skills without being hampered by hardware limitations.
6. Discussion
The outcomes of this study illustrate the enormous benefits of cloud-based lab settings over traditional on-premises setups in the context of cybersecurity education. As the demand for cybersecurity specialists grows, driven by rising cyber threats and more investment in security measures, educational institutions must modify their teaching approaches to better prepare students for the problems they will encounter in the workplace. Our comparison of VirtualBox (a type-2 hypervisor) and Amazon AWS EC2 (a cloud-based platform) shows that cloud-based labs provide improved accessibility, performance, and resource optimization, addressing many of the limitations associated with traditional lab environments. One of the key benefits of AWS EC2 is its scalability, which enables educators to dynamically distribute resources in response to student needs and course requirements. This adaptability is especially useful in educational contexts where class sizes and student participation fluctuate greatly. The ability to quickly install and deploy virtual computers improves the hands-on learning experience by allowing students to focus on practical skill development rather than setup challenges. Traditional labs, on the other hand, can require extensive manual configuration and continuous maintenance, which can cut into instructional time and impede learning outcomes.
Furthermore, this study emphasizes the value of hands-on experience in building industry-relevant abilities in the field of information and communication technology (ICT). The cloud-based environment provided by AWS EC2 enables remote access to lab exercises, supporting modern, flexible teaching models and accommodating a wide range of learning preferences. This adaptability is critical in a quickly changing area like cybersecurity, where experts must constantly refresh their abilities to stay current with emerging threats and technologies. While VirtualBox is a low-cost solution for small-scale virtualization, it has limits, particularly in terms of accessibility, scalability, and potential security risks.
In addition to technical advantages, cloud-based laboratories complement pedagogical practices that stress student-centered and active learning. The flexibility to access laboratories remotely encourages self-directed research and accommodates a variety of learning methods. Students can review complex cybersecurity exercises outside of typical lab hours, which improves skill retention and promotes continual learning. Furthermore, cloud laboratories reduce the need for high-end local hardware, ensuring equitable access to hands-on learning experiences—an especially important aspect in post-pandemic education models that value flexibility and resilience.
It is important to note that, while both the VirtualBox and AWS EC2 environments were set up with similar resource allocations (e.g., one vCPU per virtual machine), they use fundamentally different hardware infrastructures. AWS EC2 instances are hosted on high-performance, enterprise-grade servers, whereas VirtualBox uses a consumer-grade Intel Core i5 laptop. These architectural changes have a major impact on task execution time, system responsiveness, and network performance. As a result, performance measures such as lab completion times and CPU/RAM use should be viewed in the context of overall hardware architecture rather than being attributed only to virtualization software. Recognizing these variables is critical for making informed platform choices in cybersecurity education.
While these data clearly highlight the pedagogical and operational benefits of cloud-based systems, it is equally critical to recognize the possible difficulties that advanced users may encounter when switching to these environments. Even users with extensive technical expertise may come with unfamiliar cloud-specific tools, interfaces, or configuration requirements that differ dramatically from standard virtualized configurations. Issues like maintaining access permissions, configuring cloud networking, and monitoring resource costs can all bring complications that impede seamless adoption. Furthermore, the abstracted nature of cloud infrastructure may obfuscate low-level system control, which some expert users value in hands-on learning environments. These obstacles may diminish the effectiveness of the cloud-based strategy if proper orientation and institutional support are not provided. To mitigate this, educational institutions should provide extensive onboarding tools, such as tutorials, training seminars, and dedicated support channels, to assist users in making a confident and efficient shift to the cloud.
6.1. Key Differences to Consider
When comparing VirtualBox and AWS EC2, several key differences emerge that are important for understanding their respective advantages and limitations in the context of cybersecurity education.
6.1.1. Resource Allocation
VirtualBox is a type-2 hypervisor, which means it depends on the hardware of the host machine to allocate resources. This reliance can cause performance problems, especially if the host is busy with other tasks or does not have enough resources available [35]. On the other hand, AWS EC2 operates in the cloud and draws from a large pool of virtual CPUs (vCPUs) that are specifically optimized for cloud workloads. This setup allows EC2 instances to run efficiently, even when faced with heavy computational demands, because they function in isolated environments that are less impacted by the limitations of the host machine [25,36]. AWS EC2 also provides dynamic resource allocation based on real-time demand, which is critical in education, as computing requirements change with course progression and enrollment size [37]. While this study assigned one vCPU per virtual machine in both situations to ensure equal resource provisioning, it is important to emphasize that hardware equivalence is not implied. AWS EC2 instances use server-grade hardware, while VirtualBox runs on a consumer-grade Intel Core i5 laptop. Performance measures should not be limited to infrastructure design or virtualization software. Furthermore, while both environments were assigned 2 GB of RAM per VM, the underlying memory architecture differed significantly. AWS EC2 employs high-speed, server-grade memory with enhanced caching, whereas VirtualBox relies on regular laptop memory. These changes have a direct impact on RAM efficiency and should be considered when interpreting performance results [38].
6.1.2. Virtualization Technology
The differences in architecture between VirtualBox and AWS EC2 are quite important. VirtualBox is a type-2 hypervisor, which means it operates on top of an existing operating system. This setup can create extra overhead that might slow down performance [36]. In contrast, AWS EC2 uses type-1 hypervisors like Xen or Nitro that run directly on the hardware. This design reduces overhead and enhances efficiency, making EC2 a better option for applications that require a lot of resources, such as those used in cybersecurity training [39,40]. In cybersecurity training settings where numerous virtual machines are required at the same time, the efficiency of type-1 hypervisors is clearly advantageous [41].
6.1.3. Scalability
Scalability is another important area where AWS EC2 has a clear advantage over VirtualBox. With VirtualBox, scalability is limited by the physical hardware of the host machine, which can restrict how many users can work at the same time and the complexity of the lab exercises that can be conducted [42]. In contrast, AWS EC2 provides on-demand scalability, meaning users can choose from a wide range of instance types and configurations that are specifically designed to meet different educational needs. This flexibility is crucial in cybersecurity education, where requirements can change quickly depending on the curriculum or the complexity of the tasks being performed [43]. This adaptability enables schools to respond to changing student demands, curriculum revisions, and demanding project workloads. AWS EC2 allows for a more dynamic and responsive learning environment by removing hardware limitations [43].
Controlled scalability testing with Apache JMeter was carried out to validate these assertions. A simulated load scenario was constructed to evaluate system performance with an increasing number of concurrent student users. The AWS EC2 environment maintained constant performance (average response time less than 1.2 s) even with 400 concurrent users, according to the findings. Beyond this threshold, there were minor latency increases, but the system remained operational and responsive. These benchmarks show that the cloud platform can manage higher loads more effectively than local VirtualBox configurations, which began to degrade after 50 concurrent users due to host hardware limitations.
6.1.4. Network Performance
Network performance is another area where AWS EC2 stands out. In VirtualBox, the performance of the network is often restricted by the host machine’s network interface and its configuration, which can create bottlenecks during tasks that require a lot of network resources. On the other hand, AWS EC2 offers high-performance networking options, especially for instances that are located within the same region or availability zone. These capabilities enhance collaborative tasks, remote simulations, and access to external resources, which are increasingly central to practical cybersecurity education. Strong cloud-based networking also facilitates real-time peer collaboration and remote instructor support [43].
To back up these findings, network monitoring logs were acquired over three separate lab sessions that simulated low, moderate, and peak consumption scenarios. Even during peak usage, AWS EC2 maintained an average network latency of less than 100 ms, with low packet loss and constant throughput. Under identical settings, the VirtualBox environment showed latency spikes above 250 ms, as well as intermittent network failures that hampered real-time collaborative tasks.
6.2. Limitations
This study sheds light on the comparative performance of cloud-based and traditional on-premises cybersecurity laboratories; nevertheless, many limitations must be addressed.
- -
- Constraints in Conducting Network Attacks in Cloud Environments: One significant constraint discovered was the inability to conduct ARP poisoning completely within the AWS EC2 environment. Although the test was successful in local settings, the cloud environment’s network architecture naturally limits such interactions for security concerns [44]. As a result, certain realistic security attack scenarios may be less indicative of real-world settings when performed in cloud systems.
- -
- AWS EC2 operates in a fully virtualized infrastructure, which prevents direct interaction with actual network devices such as routers and switches. This constraint prevents the replication of many hardware-dependent activities, especially those involving network device configuration and hardware-level vulnerabilities [3]. As a result, practical cases requiring direct hardware manipulation are underrepresented in cloud-based labs. Future research should include a bigger, more varied student cohort to evaluate characteristics such as learning satisfaction, system responsiveness, and performance in various network contexts. Furthermore, testing under a variety of network conditions—such as changing bandwidth, latency, and connection stability—would provide a more complete picture of cloud-based laboratories’ operational durability and pedagogical effectiveness.
- -
- Performance Limitations: Due to GUI Latency: It was discovered that the graphical user interface (GUI) experience in AWS EC2 instances exhibited latency, which can have a detrimental influence on user engagement and work efficiency. Such performance limits may impede the real-time interactions required during practical exercises, compromising the overall learner experience. The current study examines technical performance parameters (e.g., completion time, CPU/RAM utilization) from the perspective of a single participant. It does not offer qualitative or quantitative statistics on student involvement, usability perceptions, or information retention. These pedagogical characteristics are critical for assessing cloud-based laboratories’ overall educational impact. Future research will use student surveys, usability comments, and pre/post-assessments to determine how cloud environments affect learning outcomes, motivation, and long-term skill development.
Furthermore, future research should investigate performance scaling using higher-tier AWS EC2 instances and more powerful on-premises computers with server-grade hardware. This approach would allow for a more comprehensive assessment of how infrastructure changes affect task execution, system responsiveness, and user experience, while distinguishing the effects of hardware capacity from virtualization strategies.
- -
- Differences in Underlying Computer Capabilities: Although both settings were assigned equivalent virtual resources (e.g., 1 vCPU, 2 GB RAM), the actual computer capability differed dramatically. AWS EC2 takes advantage of server-grade infrastructure, resulting in significantly higher processing efficiency than the consumer-grade laptop utilized for VirtualBox. As a result, performance comparisons are influenced by hardware variances, and the results should not be construed only as virtualization-related differences. To account for hardware impact, future studies should include benchmarking against equivalent computing baselines using high-end local machines and varied EC2 tiers.
- -
- Limited Sample Size and Individual Diversity: The current study relies solely on the author’s own testing, which involves a single individual and a limited hardware setup. This small scope limits the generalizability of the findings.
- -
- Short-Term Evaluation Metrics: This study focused on short-term performance indicators such as lab completion time and resource use. It did not address long-term learning objectives such as information retention, skill transfer, and practical competency development. Future longitudinal studies are required to assess the long-term educational impact and possible benefits of cloud environments in developing persistent cybersecurity competence.
- -
- Economic Considerations and Cost-Benefit Analysis: While cloud systems provide scalability and flexibility, this study did not conduct a thorough cost analysis. The ongoing operating costs associated with cloud utilization, especially at scale, may outweigh the infrastructure benefits. A complete cost-benefit analysis is required to support institutional decision-making on the use of cloud-based labs over traditional settings.
- -
- Dependence on Internet Connectivity: The performance and accessibility of cloud-based laboratories are largely dependent on internet quality and reliability. Students in environments with inadequate or unstable access may face lag, interruptions, or disconnections, reducing the effectiveness of practical activities. As Meri [39] points out, changes in network quality have a substantial impact on user experience and acceptability of cloud technologies, which must be considered when adopting such solutions in various regional contexts.
7. Conclusions
This study emphasizes the enormous benefits of moving from traditional on-premises laboratories to cloud-based platforms like AWS EC2 in cyber education. The results show that cloud environments beat virtualized local options such as VirtualBox in terms of lab completion time, resource use, and accessibility. AWS EC2 improves scalability and flexibility by allowing educational institutions to dynamically assign resources based on changing class sizes and activity demands. This on-demand scalability supports the rapid development of virtual environments, allowing students to focus on gaining practical skills without any hardware constraints.
Furthermore, cloud-based laboratories promote student-centered and active learning by enabling remote access, which is consistent with modern pedagogical techniques that value flexibility and self-directed research. These settings greatly minimize the requirement for expensive local hardware, democratizing access and making hands-on cybersecurity training available to a wider range of institutions and learners, including those in resource-constrained areas.
Cloud platforms also help to create a more resilient and adaptable educational framework, which is especially important in post-pandemic educational models that emphasize distant and flexible learning. The report also emphasizes the need for additional long-term assessments and extensive cost-benefit studies to fully quantify the economic advantages of cloud-based labs over traditional settings.
Overall, incorporating cloud infrastructure into cybersecurity courses increases not just technical performance but also accessibility, scalability, and pedagogical efficacy, hence facilitating the development of industry-ready skills in a continually changing threat environment.
Author Contributions
A.K.: conceptualization, investigation, data curation, software, validation, formal analysis, writing—original draft preparation. A.M.: conceptualization, evaluating data sets applicability and quality, writing—review and editing, methodology, validation supervision. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The dataset used in this study is available at the following link: https://zenodo.org/records/15332330 (accessed on 1 July 2025).
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| CLOUD-SEC LAB | Cloud-based Scalable Labs for Cybersecurity Education |
| C3EL | Cloud-Centric Cybersecurity Education Labs |
| ECLIPSE | Empirical Comparison of Labs: Infrastructure, Performance, Scalability, and Education |
| V-LACE | Virtual Labs for Advanced Cybersecurity Education |
| CLARITY | Cloud Labs for Applied Research in IT and CybersecurITY |
| SECURE-CLOUD | Scalable Educational Cybersecurity Using Remote Environments in the Cloud |
References
- Rahouti, M.; Xiong, K.; Lin, J. Leveraging a cloud-based testbed and software-defined networking for cybersecurity and networking education. Eng. Rep. 2021, 3, e12395. [Google Scholar] [CrossRef]
- Jaiswal, B.D. Designing scalable software automation frameworks for cybersecurity threat detection and response. Int. J. Sci. Res. Manag. (IJSRM) 2025, 13, 1958–1980. [Google Scholar] [CrossRef]
- Sahid, A.; Maleh, Y. Enhancing cybersecurity education: Integrating virtual cloud-based labs into the curriculum. In Cybersecurity Management in Education Technologies; CRC Press: Boca Raton, FL, USA, 2023. [Google Scholar] [CrossRef]
- Qasem, Y.A.; Abdullah, R.; Yaha, Y.; Atana, R. Continuance Use of Cloud computing in Higher Education Institutions: A Conceptual model. Appl. Sci. 2020, 10, 6628. [Google Scholar] [CrossRef]
- Beuran, R.; Zhang, Z.; Tan, Y. AWS EC2 Public Cloud Cyber Range Deployment. Japan Advanced Institute of Science and Technology. In Proceedings of the 2022 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Genoa, Italy, 6–10 June 2022. [Google Scholar] [CrossRef]
- Xu, L.; Huang, D.; Tsai, W.-T. Cloud-Based Virtual Laboratory for Network Security Education. IEEE Trans. Educ. 2014, 57, 145–150. [Google Scholar] [CrossRef]
- Mohamed, A.; Ismail, I. A Performance Comparative on Most Popular Internet Web Browsers. Int. J. Procedia Comput. Sci. 2022, 215, 589–597. [Google Scholar] [CrossRef]
- Pratama, M.; Sampelolo, R.; Lura, H. Revolutionizing Education: Harnessing the Power of Artificial Intelligence for Personalized Learning. Klasikal J. Educ. Lang. Teach. Sci. 2023, 5, 350–357. [Google Scholar] [CrossRef]
- Golightly, L.; Modesti, P.; Chang, V. Deploying secure distributed systems: Comparative analysis of GNS3 and SEED internet emulator. J. Cybersecur. Priv. 2023, 3, 464–492. [Google Scholar] [CrossRef]
- Ali, A.; Laghari, A.A.; Kandhro, I.A.; Kumar, K.; Younus, S. Systematic analysis of on premise and cloud services. Int. J. Cloud Comput. 2024, 13, 214–242. [Google Scholar] [CrossRef]
- Schnieder, M.; Williams, S.; Ghosh, S. Comparison of in-person and virtual labs/tutorials for engineering students using blended learning principles. Educ. Sci. 2022, 12, 153. [Google Scholar] [CrossRef]
- Liu, S.; Guo, L.; Webb, H.; Ye, X.; Chang, X. Internet of things monitoring system of modern eco-agriculture based on cloud computing. IEEE Access 2019, 7, 37050–37058. [Google Scholar] [CrossRef]
- Sai, A.B.; Mohankumar, A.K.; Khapra, M.M. A survey of evaluation metrics used for NLG systems. ACM Comput. Surv. 2022, 55, 1–39. [Google Scholar] [CrossRef]
- Patel, H.S.; Desai, A.A. Link Analysis to discover relevant documents using Information Retrieval. Int. J. Comput. Appl. 2019, 178, 23–27. [Google Scholar] [CrossRef]
- Agrati, L.S.; Burgos, D.; Ducange, P.; Limone, P.; Pecori, R.; Perla, L.; Picerno, P.; Raviolo, P.; Stracke, C.M. Bridges and Mediation in Higher Distance Education: HELMeTO 2020 report. Educ. Sci. 2021, 11, 334. [Google Scholar] [CrossRef]
- Sahana, B.; Dinesh, D.; Deekshith, K.; Sruthi, A.; Deshpande, A.; Priyadarshi, R.; Nath, V. Artificial intelligence based optimized resource allocation using predictive analysis in a virtual environment. Res. Sq. 2023. [Google Scholar] [CrossRef]
- Prastiwi, A.; Putra, A. Implementation of fuzzy inference system with best-worst method for cost efficiency on Amazon Web Services. J. Adv. Inf. Syst. Technol. 2023, 4, 149–155. [Google Scholar] [CrossRef]
- Aldwairi, M. Evaluating virtual laboratory platforms for supporting on-line information security courses. arXiv 2022. [Google Scholar] [CrossRef]
- Chawla, J.; Ahlawat, A. A proposed architecture for local-host and AWS with multiagent system. Intell. Autom. Soft Comput. 2023, 36, 2787–2802. [Google Scholar] [CrossRef]
- Dutta, S.J.; Bhattacharjee, R. Integration of virtual laboratories: A step toward enhancing e-learning technology. In Proceedings of the 2022 IEEE 7th International Conference for Convergence in Technology (I2CT), Bombay, India, 29–31 March 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Joel, B.M.O.; Chibunna, U.B.; Daraojimba, A.I. Cyber Cloud Framework: Integrating Cyber Security Resilience into Cloud Infrastructure Optimization for Enhanced Operational Efficiency. Int. J. Multidiscip. Res. Growth Eval. 2024, 5, 1378–1382. [Google Scholar] [CrossRef]
- Gupta, S.; Gupta, B.; Rana, A. A comparative cost analysis of organizational network Security Test lab setup on cloud versus dedicated virtual machine. In Lecture Notes in Networks and Systems; Springer: Singapore, 2022; pp. 623–632. [Google Scholar] [CrossRef]
- Alibadi, Z.J. Security challenges and solutions in Cloud-Based software systems. Int. J. Comput. Trends Technol. 2024, 72, 160–172. [Google Scholar] [CrossRef]
- Prümmer, J.; Van Steen, T.; Van Den Berg, B. A systematic review of current cybersecurity training methods. Comput. Secur. 2023, 136, 103585. [Google Scholar] [CrossRef]
- Anand, A. Managing infrastructure in Amazon using EC2, CloudWatch, EBS, IAM, and CloudFront. Int. J. Eng. Res. Technol. (IJERT) 2017, 6, 373–378. [Google Scholar]
- Shin, S.; Seto, Y. Cyexec—Training platform for cybersecurity education based on a virtual environment. Int. J. Learn. Technol. Learn. Environ. 2020, 3, 1–20. [Google Scholar] [CrossRef]
- Bernardo, L.; Malta, S.; Magalhães, J. An Evaluation Framework for Cybersecurity Maturity Aligned with the NIST CSF. Electronics 2025, 14, 1364. [Google Scholar] [CrossRef]
- Brilingaitė, A.; Bukauskas, L.; Juozapavičius, A. A framework for competence development and assessment in hybrid cybersecurity exercises. Comput. Secur. 2019, 88, 101607. [Google Scholar] [CrossRef]
- El-Hajj, M.; Mirza, Z.A. ProtectingSmall and Medium Enterprises: A specialized cybersecurity risk assessment framework and tool. Electronics 2024, 13, 3910. [Google Scholar] [CrossRef]
- Almomani, I.; Ahmed, M.; Maglaras, L. Cybersecurity maturity assessment framework for higher education institutions in Saudi Arabia. PeerJ Comput. Sci. 2021, 7, e703. [Google Scholar] [CrossRef] [PubMed]
- Aliyu, A.; Maglaras, L.; He, Y.; Yevseyeva, I.; Boiten, E.; Cook, A.; Janicke, H. A Holistic Cybersecurity Maturity Assessment Framework for higher education institutions in the United Kingdom. Appl. Sci. 2020, 10, 3660. [Google Scholar] [CrossRef]
- Al-Zubaidie, M.; Muhajjar, R.A.; Shihabe, L.A. Computer Networking and Cloud-Based Learning/Teaching Environment using Virtual Labs tools: A review and future aspirations. Mesopotamian J. Comput. Sci. 2024, 2024, 176–203. [Google Scholar] [CrossRef] [PubMed]
- Villegas-Ch, W.; Govea, J.; Ortiz-Garces, I. Developing a Cybersecurity Training Environment through the Integration of OpenAI and AWS. Appl. Sci. 2024, 14, 679. [Google Scholar] [CrossRef]
- Weerasinghe, S.; Perera, I. Optimized strategy for Inter-Service communication in microservices. Int. J. Adv. Comput. Sci. Appl. 2023, 14, 233. [Google Scholar] [CrossRef]
- Govea, J.; Edye, E.O.; Revelo-Tapia, S.; Villegas-Ch, W. Optimization and scalability of educational platforms: Integration of artificial intelligence and cloud computing. Computers 2023, 12, 223. [Google Scholar] [CrossRef]
- Pratama, I.P.A.E.; Raharja, I.M.S. Node.js Performance Benchmarking and Analysis at Virtualbox, Docker, and Podman Environment Using Node-Bench Method. JOIV Int. J. Inform. Vis. 2023, 7, 2240–2246. [Google Scholar] [CrossRef]
- Daniel, N.S.A.; Victor, N.S.S. Emerging Trends In Cybersecurity For Critical Infrastructure Protection: A Comprehensive Review. Comput. Sci. IT Res. J. 2024, 5, 576–593. [Google Scholar] [CrossRef]
- Radanliev, P.; Roure, D.D.; Maple, C.; Ani, U. Super-forecasting the ‘technological singularity’ risks from artificial intelligence. Res. Sq. 2023. [Google Scholar] [CrossRef] [PubMed]
- Meri, A.; Hasan, M.K.; Dauwed, M.; Jarrar, M.; Aldujaili, A.; Al-Bsheish, M.; Kareem, H.M. Organizational and behavioral attributes’ roles in adopting cloud services: An empirical study in the healthcare industry. PLoS ONE 2023, 18, e0290654. [Google Scholar] [CrossRef] [PubMed]
- Bayerlein, R.; Swarnakar, V.; Selfridge, A.; Spencer, B.A.; Nardo, L.; Badawi, R.D. Cloud-based serverless computing enables accelerated Monte Carlo simulations for nuclear medicine imaging. Biomed. Phys. Eng. Express 2024, 10, 045053. [Google Scholar] [CrossRef] [PubMed]
- Wandhare, M.; Hulke, S.; Gotmare, P.; Raghorte, D. Developing a Network for Organization by using AWS. Int. Res. J. Mod. Eng. Technol. Sci. 2023, 5, 421–425. [Google Scholar] [CrossRef]
- Haron, N.N.S.; Batrisyia, N.I.; Taib, S.M.; Rahaman, A.S.A. Enhancing online delivery of practical labs for cyber security course using virtual laboratories. Deleted J. 2024, 20, 885–887. [Google Scholar] [CrossRef]
- Qiu, Y. Evaluating and Improving LXC Container Migration Between Cloudlets Using Multipath TCP. Master’s Thesis, Carleton University, Ottawa, ON, Canada, 2016. [Google Scholar] [CrossRef]
- Ali, M.; Khan, S.U.; Vasilakos, A.V. Security in cloud computing: Opportunities and challenges. Inf. Sci. 2015, 305, 357–383. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).