1. Introduction
Service Function Chaining (SFC) is a fundamental technology in the context of Network Function Virtualization (NFV) and Software-Defined Networking (SDN) [
1]. By dynamically orchestrating Virtual Network Functions (VNFs), SFC enables the flexible deployment and on-demand scaling of network services [
2]. SDN enhances network programmability by decoupling the control and data planes, while NFV improves resource utilization by separating network functions from underlying hardware. However, as network environments become increasingly dynamic, challenges such as resource fluctuations, user mobility, and unexpected failures occur more frequently. To maintain service continuity and optimize resource usage, SFC migration becomes necessary—imposing stricter demands on network performance and service quality.
Despite significant progress in SFC migration research, several critical challenges remain. Key issues such as service interruption during migration, VNF state consistency, and security and privacy risks are yet to be fully addressed. Traditional algorithms—such as genetic and greedy algorithms—often struggle in large-scale, dynamic network environments due to high computational complexity and a tendency to converge on local optima. While machine learning approaches have enhanced adaptability, their reliance on large datasets, limited real-time performance, and lack of interpretability hinder their practical deployment. Additionally, factors like communication overhead in distributed scenarios, adaptation to heterogeneous nodes, and privacy protection further complicate migration strategy design. These challenges underscore the urgent need for more efficient, scalable, and robust solutions to enable reliable SFC migration in complex and evolving network environments.
This paper provides a comprehensive review of the current state of research on SFC migration, analyzing it across key dimensions including migration motivations, strategy optimization, core challenges, and proposed solutions. It distinguishes between passive and active migration mechanisms, highlights the trade-offs among various optimization objectives, and examines the integration of emerging technologies such as machine learning and cross-domain collaboration. Furthermore, it explores the potential of SFC migration in future-oriented scenarios such as 6G. The goals are to offer researchers a thorough technical foundation, promote deeper integration of SFC migration theory and practice, and support the development of an intelligent, resilient, and high-performance network service ecosystem.
2. Service Function Chaining
Before delving into an in-depth discussion of SDN and NFV, it is essential to clarify the profound impact they bring to SFC when combined. This converged architecture serves as a core driving force in the evolution of modern network technologies, fundamentally revolutionizing the way network services are provisioned.
As thoroughly explained in the literature [
3], the synergistic operation of SDN and NFV holds significant implications for practical network service delivery. The centralized control capability of SDN is pivotal within this framework. With its powerful functionalities, the SDN controller can obtain a global view of the network, accurately capturing critical information such as network topology, link states, and traffic distribution. Based on this comprehensive insight, the SDN controller can scientifically orchestrate the Virtual Network Functions (VNFs) provided by NFV according to the specific requirements of different services.
Through the close collaboration of SDN and NFV, network services are no longer constrained by the limitations of traditional architectures. They can now adapt more flexibly and efficiently to the diverse needs of users and application scenarios. Whether it is latency-sensitive applications like online gaming and telemedicine, or bandwidth-intensive tasks such as file transfer and cloud computing services, this converged architecture can construct customized service chains that meet specific quality-of-service (QoS) requirements, thereby providing a solid foundation for the thriving development of various network applications.
2.1. SDN
Software-Defined Networking (SDN) introduces an innovative separation between the network’s control and data planes. This architectural shift significantly enhances network programmability and scalability, enabling more efficient management and faster deployment of network applications. Centralized software-based control offers several key advantages. First, underlying hardware devices are relieved from complex routing configurations and are instead responsible only for basic switching and forwarding tasks. This not only increases the versatility of the hardware but also improves operational efficiency [
4,
5]. Second, the centralized control layer maintains a global view of the network, allowing administrators to plan and allocate resources more intelligently and effectively [
6]. The SDN network architecture is illustrated in
Figure 1.
The SDN network consists of three layers: the application layer, the control layer, and the data layer [
7]. The application layer is at the top of the architecture and is composed of customized applications developed by developers using the APIs provided by the control layer. It communicates with the control layer through the northbound interface. The control layer, as the core of the architecture, consists of multiple controllers and their functional modules. It receives instructions from the application layer through the northbound interface, sends configuration commands to the data layer through the southbound interface, and regularly collects device information from the data layer to achieve centralized network management and control [
8,
9]. The data layer is at the bottom of the architecture and is mainly responsible for executing the instructions issued by the southbound interface, regularly updating the flow table entry rules, and reporting faults to the control layer in a timely manner when abnormalities occur in the underlying network, so that the control layer can re-configure the network according to preset strategies [
10]. Currently, although the SDN southbound interface protocol has not been unified, the OpenFlow protocol has become the de facto standard due to its wide application.
The OpenFlow protocol enables collaborative interaction between the controller and the switch through three core message types [
11]: Controller-to-Switch, Asynchronous, and Symmetric. Controller-to-Switch messages are initiated by the controller to update flow table entries, query status, and configure switch parameters. Asynchronous messages are sent by the switch to notify the controller of events such as state changes, enabling real-time decision making. Symmetric messages facilitate bidirectional communication, supporting tasks like protocol version negotiation, link maintenance, and message integrity checks to ensure reliable and consistent interaction [
12].
In OpenFlow-enabled switches, data processing and forwarding rely on structured tables, primarily including flow tables, group tables, and meter tables [
13]. A flow table consists of entries, each containing a match field, a counter, and an action. When a packet arrives, it is sequentially matched against these entries. If a match is found, the associated action is executed; otherwise, matching continues until a default entry—typically at the end of the table—is used. The counter tracks the number of packets matched by that entry. The group table defines reusable sets of actions, supporting multicast and load-balancing scenarios. The meter table enables traffic metering and rate limiting, aiding in security enforcement. By configuring thresholds, the switch can detect potential attacks and apply interception or redirection strategies to improve network security and reliability [
14].
2.2. NFV
Network Function Virtualization (NFV) is an innovative architectural concept that decouples network functions from dedicated hardware, enabling them to run as software on general-purpose servers. Leveraging virtualization technologies, NFV defines network functions in software and deploys them as Virtual Network Functions (VNFs), allowing for flexible deployment, rapid upgrades, and on-demand scalability. This shift significantly enhances network flexibility and agility, enabling dynamic adjustments to network functions based on real-time requirements and effectively meeting evolving business demands.
Virtualization and cloud computing are foundational technologies that support the implementation of NFV [
15]. Virtualization abstracts physical resources—such as servers, storage, and networking devices—into virtual resource pools for computing, storage, and networking. This abstraction allows NFV to instantiate multiple virtual machines (VMs) on general-purpose hardware, with each VM being capable of independently running various network function software applications (e.g., virtual routers and virtual firewalls). Virtualization not only enhances resource utilization but also provides the flexibility and scalability needed for the dynamic deployment and adjustment of network functions in response to business demands.
Cloud computing complements NFV by offering robust computing and storage capabilities. Cloud platforms enable dynamic resource allocation and elastic scaling through the centralized management of virtualized resource pools. NFV can leverage the Infrastructure-as-a-Service (IaaS) layer of cloud computing to software-define and deploy network functions within virtual machines on the cloud. This enables rapid adaptation to changing service requirements and efficient, load-responsive resource allocation. Additionally, the Platform-as-a-Service (PaaS) layer provides development tools and runtime environments that simplify the design, deployment, and management of NFV services [
16].
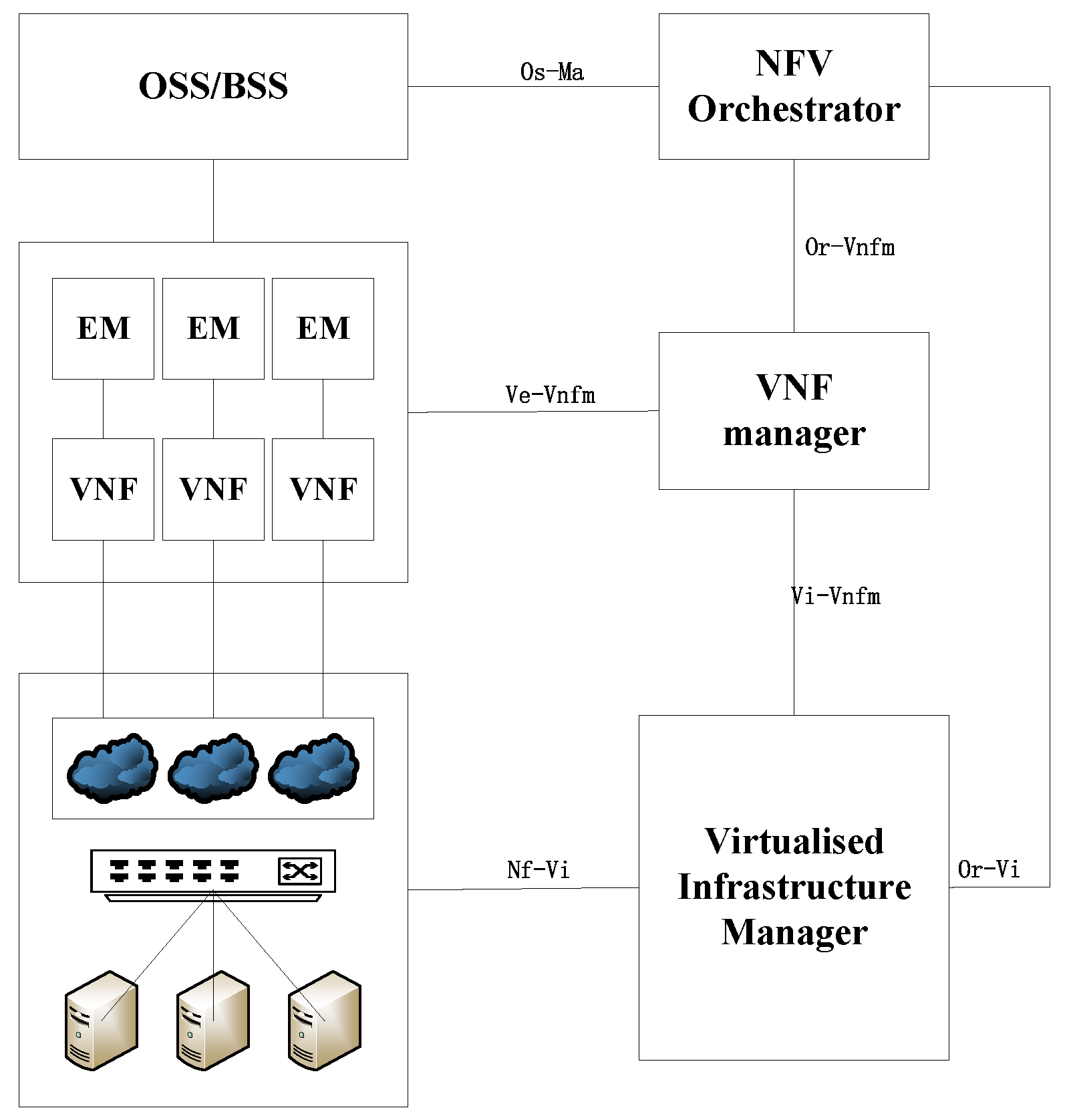
The NFV architecture comprises three core components: NFV Infrastructure (NFVI), Virtual Network Functions (VNFs), and Management and Orchestration (MANO) [
17]. The NFVI provides the underlying virtualized computing, storage, and networking environment for VNFs. VNFs are the software implementations of network functions (e.g., virtual firewalls and virtual load balancers) running on the NFVI. The MANO framework manages and orchestrates the entire NFV environment and includes three functional blocks: Virtual Infrastructure Manager (VIM), VNF Manager (VNFM), and NFV Orchestrator (NFVO). Together, they enable the automated deployment, scaling, and lifecycle management of VNFs, enhancing operational efficiency and network agility [
18].
Figure 2 illustrates the overall NFV architecture.
NFV has a wide range of application scenarios, covering various network environments from data centers to Wide Area Networks (WANs) [
17]. In data centers, NFV can achieve the rapid deployment and flexible expansion of network functions, improving resource utilization and operation efficiency. In WANs, NFV can reduce the number of physical devices, lower deployment costs and complexity, and at the same time improve network flexibility and scalability. In addition, NFV is combined with edge computing to place computing resources close to end-users, reducing latency and improving the response speed of network services. This distributed NFV architecture not only improves network scalability and availability but also reduces dependence on large-scale data centers [
19].
3. Motivations and Requirement Scenarios of SFC Migration
3.1. Dynamic Resource Adjustment and Load Balancing
One of the primary motivations for Service Function Chain (SFC) migration is to address dynamic fluctuations in network resources. In cloud and virtualized environments, the unpredictability of traffic—such as during flash sales or sudden DDoS attacks—can lead to transient overloads on physical nodes or network links. For instance, Liu et al. [
20] proposed a sliding-window-based resource prediction model that analyzes historical load data to forecast future resource demands. When a node’s CPU utilization exceeds a predefined threshold, the model triggers a migration decision. In simulation, this approach reduced the node overload probability from 18% to 6%. Additionally, a topology-aware algorithm is used to select the migration target node, ensuring that the resulting increase in end-to-end delay remains within 10%.
A representative use case of SFC migration can be found in the 5G Core Network (5GC), particularly in load balancing for the User Plane Function (UPF). The 5G network supports diverse application types—such as Enhanced Mobile Broadband (eMBB), Ultra-Reliable Low-Latency Communication (uRLLC), and Massive Machine-Type Communication (mMTC)—each with distinct performance requirements. For example, eMBB requires high bandwidth, while uRLLC emphasizes low latency. As the component responsible for processing user data traffic, the UPF must be properly load-balanced to avoid scenarios where some UPFs are overloaded while others remain underutilized. Imbalanced loads can degrade network performance and user experience. To address this, Mei et al. [
21] proposed a 5G end-to-end network slice resource allocation strategy that frames the slice embedding problem as an Integer Linear Programming (ILP) model. The strategy incorporates a coordinated algorithm for mapping virtual nodes and links to physical infrastructure, thereby balancing resource utilization and enhancing overall network reliability and efficiency.
3.2. User Mobility and Edge Service Continuity
In Mobile Edge Computing (MEC) scenarios, service continuity under user mobility is a critical factor driving Service Function Chain (SFC) migration. A typical example is the Vehicle-to-Everything (V2X) communication environment, where high-speed vehicle movement leads to frequent changes in the connected edge nodes.
In this context, the collaboration between cloud and edge services becomes crucial [
22]. Cloud services can provide powerful computing and storage resources to handle complex tasks and store large volumes of data, while edge services are capable of rapidly responding to user requests near the user side, thereby reducing transmission latency. Taking the V2X scenario as an example, when vehicles are moving at high speed, edge services are responsible for real-time data collection from vehicles and preliminary processing, such as the analysis of road condition monitoring data. Meanwhile, cloud services can perform in-depth data mining and long-term storage, providing decision support for applications like traffic management. At the same time, through efficient collaboration between cloud and edge services, seamless service continuity can be ensured when vehicles switch across different edge nodes.
Cao et al. [
23] proposed an SFC migration framework based on location prediction, employing the Extended Kalman Filter (EKF) algorithm to forecast the vehicle’s future position with an error margin within 3 m. During migration, a lightweight replica of the VNF is pre-deployed on the target edge node. By using incremental state synchronization, the framework reduces synchronization time by 72%. Simulation results from a road test scenario demonstrate a service interruption time of less than 20 milliseconds, significantly decreasing end-to-end latency.
Similarly, Guo et al. [
24] deployed a Multi-Access MEC server for LTE-V2X and introduced a collaborative timing management strategy for coordinated MEC service migration and handover. Their approach dynamically adjusts the Time to Trigger (TTT) and hysteresis factor (Hys) based on the vehicle’s speed, using fuzzy logic to optimize handover timing and mitigate the risk of ping-pong handovers. Furthermore, they integrate the Entropy Weight Method (EWM) with the Grey Relational Analysis (GRA) algorithm to make informed handover decisions, ensuring the selection of the optimal target eNodeB (eNB) and improving the handover success rate.
3.3. Fault Recovery and Energy Efficiency Optimization
Fault recovery is a critical requirement for SFC migration, especially in mission-critical infrastructure. Huang et al. [
25] addressed potential failures in security service chains arising from hardware faults, software bugs, or sudden traffic surges. They proposed a backup and recovery mechanism based on proportional resource reservation, adopting a proactive strategy that pre-allocates primary and backup resources across the physical network. The method constructs candidate sets of nodes and links for remapping in case of failures. When a node failure occurs, a target is selected from the candidate set, and reserved resources are allocated by using an enhanced discrete particle swarm optimization algorithm to solve the remapping problem efficiently. This approach reduces resource overhead while improving fault recovery rates. In the event of a link failure, the mechanism adjusts the traffic distribution across physical paths, redirecting traffic to alternate links within the candidate set. A dynamic path segmentation algorithm is employed to handle traffic redirection effectively, maximizing the residual value of the underlying physical network.
In parallel, energy efficiency optimization is a key enabler of sustainable network operations. With growing demands on limited energy resources, enhancing energy utilization not only lowers operational costs but also minimizes environmental impact. For instance, data centers, which house vast numbers of servers and networking devices, are significant energy consumers. Strategies such as virtual machine (VM) migration and the consolidation of underutilized servers can substantially reduce energy consumption. Yang et al. [
26] proposed a Three-Way Decision-based Virtual Machine Migration (TWD-VMM) scheduling strategy, leveraging the divide–conquer–efficiency model of three-way decision theory. The approach begins by constructing a hierarchical threshold tree to identify optimal thresholds that minimize total energy consumption. This enables the classification of hosts into high-, medium-, and low-load regions. Distinct migration strategies are then applied: for high-load hosts, the algorithm prioritizes post-migration resource balance and load reduction; for low-load hosts, the focus is on maintaining balanced resource utilization after consolidation; and for medium-load hosts, migrations are permitted only if the post-migration load still falls within acceptable thresholds. This targeted strategy improves both energy efficiency and resource utilization.
4. SFC Migration Strategies
Current research on SFC migration can be broadly classified into two main approaches: (1) passive migration and (2) active migration. Passive migration is a reactive strategy, where VNFs are relocated in response to server or link failures that disrupt service operations, with the goal of restoring normal functionality. In contrast, active migration is a proactive approach that involves dynamically adjusting VNF placements based on predicted changes in network resources, aiming to optimize performance and prevent potential disruptions before they occur.
4.1. Passive Migration Strategies
Passive migration is a failure-driven, emergency response mechanism activated by anomalies in physical nodes or links. Its primary objective is to ensure service continuity by quickly migrating affected VNFs to healthy nodes. This approach relies on real-time monitoring and threshold-based detection, making it straightforward and easy to implement. However, it comes with drawbacks, including prolonged service downtime and suboptimal resource utilization.
Tang Lun et al. [
27] proposed a passive migration scheme designed to address dynamic resource fluctuations in SFC requests. They developed a constrained Markov decision process (CMDP)-based stochastic optimization model to minimize energy consumption in server clusters. To overcome challenges like inaccurate state transition probability estimation and high-dimensional state spaces, the authors introduced an intelligent VNF migration framework utilizing reinforcement learning. The framework leverages a convolutional neural network (CNN) to approximate action-value functions, allowing for the dynamic optimization of VNF migration paths and CPU resource allocation strategies for network slices based on real-time system state parameters.
Liu et al. [
28] investigated a passive migration mechanism for SFCs triggered by node overloading. They proposed a VNF migration strategy that shifts workloads from overloaded to underutilized nodes to maintain system stability and service quality. However, they noted that migrating a shared VNF may disrupt the mapping between SFCs and the physical network, potentially increasing propagation latency and degrading quality of service (QoS), especially for delay-sensitive applications. To address this, they introduced a partial VNF migration approach that balances load while controlling SFC latency. Instead of migrating the entire VNF, their method selectively redirects traffic from a subset of SFCs to alternative VNF instances. An Integer Linear Programming (ILP) framework was formulated to model the optimization problem. Given its NP-hard nature, a dynamic, latency-aware algorithm was also proposed to efficiently mitigate overloads while maintaining low end-to-end latency. Experimental results showed that the approach reduced the average SFC latency by 12.7–21.8% and the migration cost by 12.5–48.5%, outperforming existing methods. Additionally, it achieved approximately 90% faster execution time while preserving comparable latency performance.
Liao et al. [
29] proposed a solution for SFC passive migration, focusing on the challenges of large-scale state transfer in resource-constrained MEC networks with fluctuating demands. They formulated the joint VNF deployment and migration problem (MTLDM) as a multi-objective optimization problem and introduced a Collaborative Filtering-based Fast Delay-aware algorithm (CFFD) to address it. The CFFD algorithm leverages preference information from previously deployed/migrated VNFs to accelerate decision making. It also incorporates a similarity-based method to reduce the complexity caused by resource heterogeneity and minimize system latency. A heuristic mechanism is further integrated to improve request acceptance rates. Simulation results show that CFFD achieves up to 22.08% improvement in delay optimization and 99% reduction in decision time compared with baseline methods. Moreover, Manhattan distance and cosine similarity are shown to outperform Pearson’s correlation in selecting suitable host nodes for VNF placement or migration.
4.2. Active Migration Strategies
Active migration is a prediction-driven resource optimization strategy that utilizes machine learning models to forecast future network load changes and preemptively adjust VNF deployments. The key advantage of this approach is its ability to proactively optimize resource allocation, reducing the risk of service interruptions and enhancing energy efficiency. Common methods combine load forecasting with global resource scheduling algorithms to achieve multi-objective optimization, balancing energy consumption, latency, and quality of service (QoS). However, these methods often face challenges such as high algorithmic complexity and continuous consumption of computational resources.
For active VNF migration, Tang Lun et al. [
30] proposed an intelligent migration framework based on deep belief network (DBN) for predicting resource demand. This framework first develops a multi-dimensional cost evaluation model integrating bandwidth consumption and migration operation costs. An online incremental learning mechanism is then used to optimize the DBN for dynamic resource demand prediction. Based on the predictions and network topology awareness, a priority-based greedy algorithm is applied to select optimal target nodes under resource constraints, while a tabu search algorithm is used to globally optimize migration paths.
Qinghai Liu [
20] introduced a novel optimization paradigm leveraging digital twin (DT) technology to address resource consumption challenges during VNF migration and SFC reconfiguration. The paradigm converts the resource consumption problem into a mathematical model, aiming to minimize energy consumption and maximize resource utilization in active migration scenarios. A distributed federated learning framework combined with a bidirectional gated recurrent unit (Bi-GRU) prediction mechanism is used to evaluate dynamic resource demands. Based on these predictions, deep reinforcement learning (DRL) algorithms optimize VNF migration decisions, forming a closed-loop control strategy.
Yang Yong et al. [
31] proposed an active service function chain (SFC) migration framework to address physical network overload caused by dynamic resource demands in NFV environments. The framework develops a quantification model for migration overhead by evaluating migration costs and link resource utilization. A radial basis function neural network, optimized by a particle swarm algorithm, predicts overloaded physical nodes hosting VNFs. During the decision-making phase, the framework prioritizes migrating VNFs with the highest resource occupancy from overloaded nodes and selects target nodes that minimize total overhead by using a global topology-aware optimization algorithm.
5. Key Issues and Challenges of SFC Migration
5.1. Service Interruption and Dynamic Resource Allocation During Migration
One of the fundamental challenges in SFC migration is minimizing service interruption time during the migration process. The migration of Virtual Network Function (VNF) instances requires the reallocation of computing resources—such as CPU and memory binding and release alongside network path reconfiguration and state data transmission. Delays in any of these stages can result in packet loss or service degradation. For instance, in virtual machine migration scenarios, traditional live migration techniques such as pre-copy and post-copy can effectively reduce downtime, but they incur additional bandwidth overhead [
32]. For SFCs that support applications with stringent real-time requirements—such as industrial control systems—even millisecond-level interruptions can have severe consequences.
Moreover, the dynamic nature of resource availability at the target node can invalidate pre-reserved resources, increasing the risk of secondary migrations. While some approaches mitigate this risk through redundant resource reservation or real-time monitoring, excessive reservation leads to inefficient resource utilization. This, in turn, may result in a vicious cycle of resource waste and frequent migrations [
33], ultimately undermining network stability and scalability.
5.2. Assurance of VNF State Consistency
Most network functions—such as Network Address Translation (NAT) and firewalls—maintain internal states, such as session tables. During migration, it is essential to ensure the accurate and timely synchronization of state data between the source and target nodes to maintain service continuity. Existing state synchronization approaches can be broadly categorized into two types: Checkpointing and Log Replay. The Checkpoint mechanism periodically captures and transfers the VNF state to the target node. While simple and widely used, it can incur frequent I/O operations, leading to increased migration latency [
34]. On the other hand, Log Replay records a sequence of state-changing operations and replays them at the target node to reconstruct the state. Although it offers finer-grained control, it requires strict event ordering, imposing stringent clock synchronization requirements in distributed environments.
Furthermore, in the context of large-scale SFC migrations, interdependencies among VNFs introduce state coupling, which may result in cascading synchronization issues. These dependencies significantly increase the complexity of ensuring consistency across the service chain, making scalable and efficient state migration a persistent research challenge.
5.3. Security and Privacy Risks
During the migration process, VNF instances and their state data may be exposed to untrusted network paths or target nodes, introducing risks such as data leakage and man-in-the-middle attacks. For instance, when migrating to an edge node, the absence of hardware-level security protection on the edge device could expose sensitive state information to malicious actors. Additionally, the migration decision itself may become a target, as forged migration trigger signals could induce frequent SFC migrations, leading to resource consumption and creating potential service vulnerabilities [
35,
36].
Existing solutions primarily focus on transmission encryption and integrity verification to safeguard the migration process. However, the integration of these security measures often results in increased migration delay, presenting a trade-off between security and performance.
6. Limitations of Existing Research
Despite the innovative approaches proposed in the field of SFC migration, several critical limitations remain, directly affecting the practical deployment and performance optimization of these technologies.
6.1. Limitations of Traditional Algorithms
The applicability of traditional optimization algorithms in complex and dynamic environments is constrained by several factors. First, high computational complexity remains a major challenge. For instance, genetic algorithms, which rely on population iteration to search for global optima, suffer from the exponential growth of computational overhead in large-scale networks. Experiments in ref. [
37] demonstrate that when the number of nodes exceeds 100, the convergence time of genetic algorithms is over 10 times longer than traditional greedy algorithms, rendering them unsuitable for real-time scenarios with strict latency requirements.
Second, local optimum problems become especially pronounced in dynamic environments. While greedy algorithms quickly generate approximate solutions, they are often influenced by local states, failing to globally optimize multi-objective constraints. Simulation results in ref. [
38] indicate that in resource-fluctuating scenarios, the chain migration success rate of greedy algorithms is more than 20% lower than that of reinforcement learning methods. Moreover, scalability limitations hinder the use of traditional algorithms in heterogeneous networks. In cases where cloud, edge, and IoT nodes coexist, traditional algorithms struggle to adjust migration strategies dynamically to accommodate the varying computational capabilities of different nodes, leading to inefficient resource allocation.
6.2. Limitations of Machine Learning Methods
While machine learning significantly enhances the dynamic adaptability of migration strategies, its performance is constrained by data dependency and real-time bottlenecks. First, the scarcity and bias of training data pose critical challenges. For example, the deep reinforcement learning-based migration framework in ref. [
30] relies heavily on extensive historical traffic data and migration logs to train Q-networks. However, in real-world networks, data samples for sudden traffic surges or anomalies are often scarce, resulting in poor model generalization under extreme conditions. Experiments in ref. [
39] show that when input traffic fluctuations exceed 30% of the training data distribution, the delay prediction error rate of DQN models can increase by up to 40%.
Second, real-time decision-making delays limit their effectiveness in highly dynamic environments. Reinforcement learning’s Markov decision process (MDP) requires frequent updates to both state and action spaces, resulting in increased computational latency. For instance, the PPO algorithm in ref. [
40] incurs decision delays of more than 10 s when handling sudden resource overload events, which exceeds the millisecond-level response required by carrier networks.
Additionally, poor model interpretability hinders industrial adoption. Federated learning frameworks, which aggregate data from multiple nodes, lack traceable decision logic, making it challenging for operators to trust and act on migration decisions.
6.3. Challenges in Distributed Scenarios
Implementing migration strategies in distributed networks introduces challenges related to communication overhead, privacy protection, and node heterogeneity. First, high communication costs are a significant issue in the integration of federated learning with edge computing [
41].
Second, SFC migration in dynamic edge environments raises privacy risks. While federated learning offers privacy through parameter sharing, metadata exchanges during cross-domain migration can reveal sensitive information, such as SFC topology characteristics and user behavior patterns. Malicious actors may exploit this to reverse-engineer information such as model gradients and routing data—which is especially concerning in sensitive areas like healthcare and finance. Solutions like homomorphic encryption or differential privacy significantly increase computational latency, creating a trade-off between migration timeliness and privacy protection.
Additionally, edge node heterogeneity presents significant adaptability challenges. Variations in hardware architectures across vendors lead to instruction set incompatibilities in computing units, and differences in network interface protocols introduce protocol conversion overhead during VNF migration. More critically, energy supply heterogeneity in IoT devices, such as the coexistence of fixed-power and battery-driven devices, requires migration strategies with multi-dimensional resource awareness. Current static scheduling algorithms based on resource reservation struggle to adapt to such dynamic heterogeneous environments, highlighting the need for elastic migration frameworks with online learning capabilities. These frameworks must be able to dynamically adjust decisions based on the real-time monitoring of CPU microarchitecture features, network protocol stack configurations, and energy states [
42].
7. Future Research Directions
Future research should focus on developing simpler and more practical methods to enhance the migration capabilities of Service Function Chains (SFCs). At the technical level, the practical application of intelligent algorithms should be prioritized. For instance, machine learning can be leveraged to automatically analyze network states—such as server load and traffic fluctuations—to dynamically determine the optimal time and method for migration, minimizing the need for complex manual configurations. Additionally, addressing resource coordination issues is crucial, particularly in hybrid cloud and edge computing environments. Balancing computational, storage, and bandwidth resources is essential to ensuring that migrations do not compromise service quality or incur excessive costs.
Furthermore, system design should prioritize security and stability. Exploring lightweight security verification methods, such as automated security checks at each stage of migration, can help prevent data breaches or tampering. For energy efficiency, migration strategies could be tailored based on server load, such as migrating during low-traffic periods or preferring nodes powered by green energy. Moreover, testing migration solutions in emerging environments like 5G and the IoT is critical to assessing their performance in diverse network scenarios, such as real-time industrial control or the rapid-response needs of Vehicle-to-Everything (V2X) networks.
Finally, future research should align with real-world applications. Tools that facilitate testing and deployment, such as simulation environments based on open-source cloud platforms (e.g., Kubernetes), are essential to validating the reliability of migration strategies. In addition, establishing universal standards to ensure interoperability among devices and services from different vendors will help reduce compatibility issues. Tailoring migration solutions for specific scenarios, such as industrial automation or smart cities, will ensure that the technology addresses industry-specific challenges, rather than remaining purely theoretical.
8. Conclusions
This paper presents a comprehensive review of research on SFC migration, analyzing its importance and the challenges it faces in dynamic network environments. As a core achievement of the integration of NFV and SDN, SFC enables the dynamic orchestration of VNFs, making it possible to support diverse service requirements. However, in response to challenges such as resource fluctuations, user mobility, and fault recovery, the need to ensure service continuity and optimize resource utilization has driven the exploration of efficient migration mechanisms.
Although both passive and active migration strategies have demonstrated potential to varying degrees—particularly with advancements in reinforcement learning-based dynamic scheduling and digital twin technology for resource prediction—several critical issues remain unresolved. These include but are not limited to service interruption control, state consistency maintenance, reduction in algorithmic complexity, and enhanced security and privacy protection. Furthermore, traditional optimization algorithms often exhibit low computational efficiency and poor scalability when handling large-scale heterogeneous networks, while machine learning approaches, although improving adaptability, face challenges related to real-time performance and high data dependency.
Future research should focus on deeply integrating intelligent algorithms with cross-domain collaborative technologies, developing lightweight and secure migration frameworks, and exploring energy-efficient solutions. With the emergence of new application scenarios such as 6G and edge computing, coordinated innovation between theory and practice becomes increasingly important. This will not only help overcome current technical bottlenecks but also pave the way for building a highly reliable, intelligent, and sustainable network service ecosystem.