Abstract
Protecting the integrity of images has become a growing concern due to the ease of manipulation and unauthorized dissemination of visual content. This article presents a comprehensive approach to safeguarding images’ authenticity and reliability through watermarking techniques. The main goal is to develop effective strategies that preserve the visual quality of images and are resistant to various attacks. The work focuses on developing a watermarking algorithm in Python, implemented with embedding in the spatial domain, transformation in the frequency domain, and pixel modification techniques. A thorough evaluation of efficiency, accuracy, and robustness is performed using numerical metrics and visual assessment to validate the embedded watermarks. The results demonstrate the algorithm’s effectiveness in protecting the integrity of the images, although some attacks may cause visible degradation. Likewise, a comparison with related works is made to highlight the relevance and effectiveness of the proposed techniques. It is concluded that watermarks are presented as an additional layer of protection in applications where the authenticity and integrity of the image are essential. In addition, the importance of future research that addresses perspectives for improvement and new applications to strengthen the protection of the goodness of pictures and other digital media is highlighted.
1. Introduction
In the digital age, managing media files has become more accessible and widespread. The images are widely shared and distributed through online platforms, social networks, and instant messaging applications. However, this ease of access and sharing carries significant copyright, privacy, and mishandling risks. One of the main dangers we face is copyright infringement [1]. Original images can easily be copied, downloaded, and used without the rightful owner’s consent. This leads to losing control over the authorship and use of images, which can have severe repercussions for content owners and creators.
In addition, the unauthorized manipulation and alteration of images is another growing problem in the digital environment. Image editing tools and software are widely available, making it easy to modify visual content fraudulently [2]. This can result in the spread of false information, misleading images, or even impersonation. The integrity and authenticity of the images are also at risk due to the ease with which they can be manipulated. Advanced digital editing allows for creating fake images or modifying existing images convincingly, making it difficult to distinguish between the real and the fake. This poses significant challenges regarding the reliability of the images and their use in some areas, such as digital forensics, content verification, and evidence authentication [3].
Current robust image watermarking techniques have proven effective in many cases. Still, they also present specific vulnerabilities that attackers can exploit to remove or modify watermarks, thereby compromising the authenticity and integrity of protected images. These vulnerabilities include sensitivity to compression, filtering, and region deletion attacks, which can lead to watermark degradation and eventual deletion. These limitations can undermine confidence in using watermarks to protect intellectual property and image authorship in the digital environment.
Given this situation, it is essential to have effective mechanisms to protect the authenticity and integrity of images in digital environments. Watermarking has established itself as a standard solution to address these challenges, as it makes it possible to identify and trace the authorship of images and detect unauthorized tampering [4,5]. This work addresses these critical points by developing a robust watermark resistant to common attacks, such as compression, filtering, and region removal. We have thoroughly evaluated its resistance and resilience after subjecting it to various attacks, thus, demonstrating the effectiveness of our comprehensive approach. By highlighting these performance flaws of current techniques and presenting how our proposed algorithm overcomes these limitations, we seek to provide greater understanding and confidence in the effectiveness of our approach to image protection in digital environments. Our contribution is focused on addressing these vulnerabilities and offering a practical and reliable solution to ensure the authenticity and integrity of images in the digital world.
This proposal is based on developing an algorithm in Python that allows the insertion of watermarks in multimedia files. The following variables have been defined to guarantee a comprehensive analysis, efficiency, precision, and robustness. Efficiency is a crucial aspect of any image processing algorithm. This is achieved by measuring the execution time of the algorithm using specific Python libraries, such as “time”, to determine how quickly the watermark insertion process can be applied [6]. In addition, system resources, such as CPU and memory, are monitored using tools, such as “psutil”, to optimize the algorithm’s performance.
Accuracy is critical to ensure that the watermark is legible, visible, and does not significantly distort the original image. For this, the resulting watermarked images are visually evaluated to verify their quality and readability. In addition, numerical metrics, such as the root mean square error (RMS) or the structural similarity index (SSIM), are used to calculate the difference between the original and watermarked images. The smaller the difference, the higher the accuracy of the algorithm [7]. For its part, robustness refers to the ability of the algorithm to resist attacks and preserve the integrity of the watermark. Therefore, the system can be tested with specific attacks, such as removing image regions, image compression or filtering, and intentionally shifting watermark pixels. The ability of the watermark to recover after attacks is analyzed, and its resistance is evaluated [8].
With the development of an efficient and precise algorithm for inserting watermarks in multimedia files, the comprehensive approach under which this work is presented allows us to evaluate the algorithm’s efficiency in execution time and use of resources and to guarantee the precision of the inserted watermarks through visual evaluations and numerical metrics [9,10]. In addition, the algorithm’s robustness is demonstrated by subjecting it to various attacks and evaluating its recovery and resistance capacity.
The results obtained in the work allowed us to establish that this proposal seeks to offer a comprehensive approach to protecting images in digital environments [11]. In addition, the system developed with its watermark insertion module and exhaustive analysis of efficiency, precision, and robustness aims to provide a reliable and effective solution to protect and preserve the authenticity of images in the digital world.
This work is divided into the following sections, which are considered vital to achieve the proposed objectives. Section 2 defines the materials and method; Section 3 presents the results obtained from the analysis; Section 4 presents the discussion of the results obtained with the proposal to improve the use of watermarks in images with AI; Section 5 presents the conclusions found in the development of the work.
2. Materials and Methods
For developing the proposed system and its methodology, works related to the insertion of watermarks in multimedia files are reviewed and compared with our proposal. Our approach focuses on developing a Python algorithm for inserting watermarks using libraries, such as OpenCV, Pillow, or PyWavelets. In addition, the efficiency, precision, and robustness of the algorithm are analyzed through specific analysis variables.
2.1. Review of Related Works
The review of related works focuses on those who work on the protection of images in digital environments, in which the techniques and approaches used in said works are analyzed. This review helps us to understand the current state of research in this field and identify existing approaches’ strengths and limitations. In addition, a comparison with this proposal is established, highlighting how our comprehensive approach addresses the limitations of previous work and offers a more complete and robust solution [12].
In the paper [13], an approach based on domain transform for the insertion of watermarks into images is proposed. They use the Fourier transform to represent the image in the frequency domain and modify the frequency coefficients to embed the watermark. However, this approach has limitations regarding robustness against attacks in the spatial domain and the ability to hide the watermark. Our proposal addresses these limitations by offering a comprehensive approach that combines different watermarking techniques, including spatial domain embedding and domain transformation. This allows us to take advantage of the strengths of each technique and obtain a more robust and efficient solution.
In the work [14], the pixel modification technique embeds watermarks in images. The value of the pixels’ least significant bits (LSB) to store the watermark information is modified. Although this technique offers good stealth capabilities, it is susceptible to specific attacks designed to detect and remove the watermark. It combines pixel modification with other techniques, such as spatial domain insertion and domain transform, compared to our proposal. This allows the mitigation of the vulnerabilities of the pixel modification technique and offers greater robustness in protecting images.
Another work, [15] proposes an image protection system based on digital authentication. They use cryptographic algorithms to generate unique digital signatures for each image and verify the authenticity of images by verifying these signatures. While this approach offers high security regarding authenticity, it does not directly address protection against image tampering itself. Our proposal focuses on the comprehensive protection of images, addressing authenticity and protection against manipulation. In addition to digital authentication, we implement watermarking techniques to hide information in the image and detect any manipulation attempts. This makes it possible to offer a more complete and robust solution in digital environments.
The review of related works reveals that there are specific approaches to protecting images in digital environments [16]. Still, none of them comprehensively addresses the aspects of authenticity and protection against manipulation. Our proposal combines different watermark and digital authentication techniques to provide a comprehensive and robust solution.
2.2. Review of Concepts Used
In the development of this work, several concepts are used that serve as a theoretical basis that allows us to solve the phenomenon of study. We will focus on watermarking, which is the process of hiding information in an image in a way that is perceptible or imperceptible to users. We will implement techniques including least significant bit (LSB) or adaptive pixel modification algorithms. In addition, we will use domain transforms, such as the Fourier transform, to make specific modifications to the image.
Watermarking is the process of hiding information in an image perceptibly or imperceptibly for users [17]. This technique is used to identify the authorship of an image, protect intellectual property, and detect unauthorized manipulation. This work implements watermark insertion techniques that allow embedding data in multimedia files safely and efficiently. One of the techniques used is pixel modification. In this approach, changes are made to the image’s pixel values to hide the watermark. A typical example is LSB modification, where the least significant bits of the pixels are replaced with the watermark bits [18]. This allows for subtle concealment that is almost invisible to the human eye.
In addition to the least significant bit modification, adaptive pixel modification algorithms are used. These algorithms analyze the characteristics of the image and make targeted modifications to the pixels to hide the watermark more effectively [19]. For example, they can adjust the intensity of pixels in high-contrast areas for better concealment. Another approach employed is using domain transforms, such as the Fourier transform. These transforms allow the image to be represented in the frequency domain, allowing us to make specific modifications to the frequency components of the image [20]. This can provide greater robustness against attacks in the spatial domain and improve watermark concealment.
2.3. Method
All the stages for the development of the algorithm for inserting watermarks in multimedia files are presented in Figure 1. The approach is based on libraries and programming tools in Python, which offer a wide range of functions and capabilities for working with images.
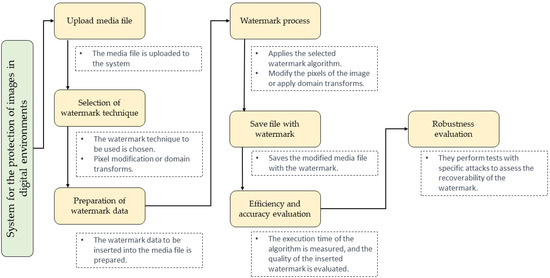
Figure 1.
Flowchart of the method of inserting watermarks in multimedia files.
The method of embedding watermarks in media files consists of the following steps. In the media file upload step, the selected media file is uploaded to the system. A library, such as OpenCV or PyWavelets, is used to upload and convert the file into a suitable format for processing. It is essential to consider the type of media file and apply the corresponding functions to load it correctly.
In the watermark technique selection step, the technique that will be used to insert the data into the media file is chosen [21,22]. Different approaches are available, and the choice will depend on the specific system requirements and goals. The options available in the system are as follows:
- Pixel modification. This technique involves directly modifying the pixel values in the image to hide the watermark. A commonly used algorithm in this technique is the LSB modification algorithm. The algorithm works as follows:
- Select the least significant bit of each color component (red, green, and blue) from the original pixel.
- Replace the least significant bit with the bits of the watermark you want to insert.
- Repeat this process for each pixel in the image.
- Domain transform. In this technique, a mathematical transform, such as the Fourier transform, is used to insert the watermark into the frequency domain of the image. The algorithm used in this technique includes the following steps:
- Apply the Fourier transform to the original image to obtain its representation in the frequency domain.
- Modify the Fourier transform coefficients to insert the watermark data.
- Apply the inverse Fourier transform to obtain the modified image with the watermark.
- Adaptive pixel modification algorithms are based on the adaptation of the pixel modification based on the local characteristics of the image. Techniques, such as pixel modification based on the difference in values and pixel modification based on the local median, among others, are used [23]. These algorithms allow greater concealment capacity and certain robustness against attacks since they adapt to the specific characteristics of the image. However, they may also be more susceptible to specific attacks to detect these adaptive modifications.
The watermark data to be inserted into the media file are prepared in the next stage. These data can be authentication, identification, or any other type of hidden information you want to protect. The data are transformed or encoded according to the selected watermarking technique for subsequent insertion. Next, the watermark insertion in the multimedia file is carried out [24]. Depending on the selected technique, specific modifications are made to the file. For example, in the case of pixel modification, the least significant bits of the image can be modified to hide the watermark data. In the case of the domain transform, the transform coefficients can be altered to insert the watermark information. It is essential to ensure that the watermarking process is invisible to the human eye and does not significantly affect the visual or auditory quality of the media file [25].
In Figure 2, the pseudocode of the proposed algorithm for the insertion of watermarks in images is presented. In the pseudocode, the insert_watermark_function takes as its input the original image and the watermark to be inserted. The watermark is verified to be smaller than the original image to ensure it can be inserted without significantly distorting it. Then, the watermark’s insertion position in the original image’s center is calculated.
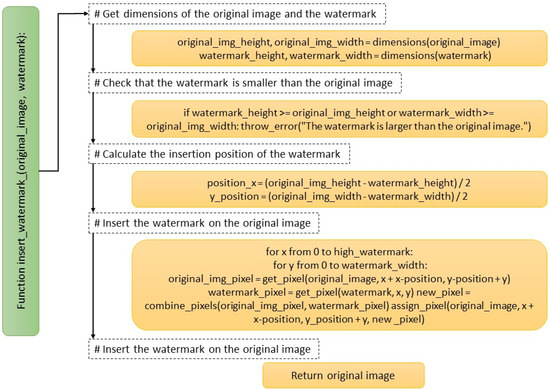
Figure 2.
Pseudocode for the image watermark insertion algorithm.
The algorithm uses two loops to loop through the watermark pixels and the original image in the embedding region. Each pixel is combined with the corresponding pixel from the original image using a combine_pixels function that mixes the values of the color channels to achieve a visible but non-intrusive watermark. Finally, the original image with the inserted watermark is returned. It should be noted that the pseudocode is presented in a simplified manner and does not include specific implementation details, such as the dimensions, get_pixel, assign_pixel, and combine_pixels functions. These functions and their detailed logic would be present in the actual algorithm implementation in Python. This improves reproducibility and allows a more accurate evaluation of its performance by providing a step-by-step guide to how the watermark is inserted into the original image.
The modified media file with the embedded watermark is saved in the next step. The corresponding library, such as OpenCV or Pillow, saves the file in the desired format. It is critical to ensure that the resulting file maintains the quality and integrity of the embedded watermark.
In the efficiency and precision evaluation stage, tests are carried out to evaluate the efficiency and precision of the implemented watermark algorithm. Different techniques and metrics are used to measure these aspects, as follows:
- Efficiency evaluation:
- Execution time, i.e., the time it takes for the algorithm to process a watermark image, is measured. This is accomplished by using the Python “time” library to calculate the elapsed time before and after the execution of the algorithm.
- Resource usage—system resource usage, such as CPU and memory usage, is monitored during the execution of the algorithm. This can be accomplished using OS-specific tools or Python libraries, such as “psutil”, to perform this trace.
- Accuracy evaluation:
- Visual assessment. A visual assessment of the resulting watermarked images is performed to verify if the watermark is legible, visible, and does not significantly distort the original image [26]. Side-by-side comparison or visualization methods are used to make this assessment.
- Numerical evaluation. If you have an original image without a watermark and an image with a watermark, you can use image quality metrics, such as the ECM or the structural similarity index (SSIM), to calculate the difference between the two images. A minor difference indicates a higher precision in the insertion of the watermark.
In the robustness evaluation stage, tests are carried out with specific attacks to evaluate the robustness of the watermark algorithm. Some examples of attacks that can be considered are as follows:
- Deletion and tampering attacks. Testing with removing regions of the image, compressing, or filtering the image, and intentionally changing the watermark pixels. This makes it possible to assess the resilience of the watermark after these attacks.
- Statistical analysis. Statistics can be analyzed on the ability to detect and correct the watermark after applying different attacks. This involves measuring the rate of detection and correction of the watermark and assessing resistance against specific attacks.
2.4. System Operation
During the implementation process, different techniques have been used to insert watermarks in multimedia files, such as images. These techniques include pixel modification, adaptive pixel modification algorithms, and domain transforms, such as the Fourier transform [27]. At the spatial domain watermark insertion stage, the Pillow library loads the image, creates a copy, and then adds the watermark text in the upper right corner using the draw function text().
In the domain transform watermark insertion stage, the Pillow library loads the image, converts it to grayscale, and applies the Fourier transform. A white watermark mask is then created and mixed with the Fourier transform of the image [28]. Finally, the inverse Fourier transform is applied to obtain the resulting image with the watermark. In inserting watermarks using pixel modification techniques, the Pillow library loads the image and the watermark. The watermark size is adjusted to match the image, and we have applied the watermark pixel by pixel, calculating new RGBA values for each pixel.
In addition, functions have been developed to evaluate the algorithm’s efficiency, precision, and robustness. To measure efficiency, execution time is calculated, and we have monitored the use of system resources, such as CPU and memory. Visual assessments of the resulting watermarked images are performed, and numerical metrics, such as ECM, are calculated to assess accuracy [29]. To assess robustness, we run tests against specific attacks, such as image region removal, compression, and filtering, and look at the watermark’s recoverability after attacks. A detailed guide to using the system is provided in Appendix A.
3. Results
Numerical metrics, such as root mean square error (RMS) or structural similarity index (SSIM), are widely used to measure accuracy in image comparison; visual assessment also plays an essential role in validating watermark results. Visual evaluation allows direct inspection of watermarked and unwatermarked images, allowing human evaluators to spot potential issues that numerical metrics might miss. Human perception can be more sensitive to subtle changes in image quality and watermark visibility. Furthermore, visual evaluation is an effective way to assess the legibility and aesthetic appearance of the embedded watermark, which is essential in applications where the watermark must be easily detectable and non-intrusive to the viewer.
To ensure the reliability of the visual evaluation, a group of expert evaluators with experience in image processing and watermarking was used. These evaluators were previously trained to recognize and analyze key aspects, such as the legibility, visibility, and distortion of the original image due to the insertion of the watermark. In addition, clear guidelines and criteria were provided for the evaluation, ensuring a consistent and objective methodology. While numerical metrics provide a quantitative assessment, combining visual evaluation with numerical metrics allows for a more complete picture of the accuracy and quality of the watermark insertion algorithm. Numerical metrics provide objective and quantifiable data to support the conclusions of the work, while visual evaluation complements this analysis by considering subjective aspects of human perception. This combination of approaches allows for more reliable and robust results, improving the validity and precision of evaluating the proposed algorithm.
3.1. Application of Techniques to Generate a Watermark
Table 1 shows the results obtained when executing the process of inserting the watermark in a figure. In these results, the process of inserting the watermark in the figure took an execution time of approximately 19.82 s. This value indicates the algorithm’s efficiency, being a relatively low time for the task performed. In the CPU usage at the beginning of the process, a CPU usage of 5.5% was recorded. This indicates the system workload during the execution of the watermark. At the end of the process, CPU usage increased to 14.3%. This could be due to the computational intensity required for the watermark insertion. At the start of the process, memory usage of 71.5% was recorded. This value indicates the amount of RAM used during the execution of the algorithm.

Table 1.
Results of inserting a watermark in a figure.
Regarding the ECM error, a value of 159.34 was obtained. This metric is used to assess the quality of the watermark, where a lower value indicates less difference between the original image and the watermarked image. In this case, the value obtained indicates that the introduced watermark is relatively close to the original image. The results show that inserting the watermark in the figure was completed in a reasonable amount of time and with moderate use of resources. These results may vary depending on the hardware and system load during execution.
Figure 3 shows the results obtained in the images about the actual image. Its simplicity and ease of implementation characterize the spatial domain insertion technique. It allows you to apply the watermark directly to the spatial domain of the image, making it visible to the naked eye. This advantage can be beneficial when the watermark must be easily detectable and recognizable. Furthermore, this technique has a relatively fast execution time and low resource consumption, which makes it suitable for real-time applications. However, the visibility of the watermark can be considered a disadvantage in specific scenarios where a more subtle and less noticeable insertion is sought.
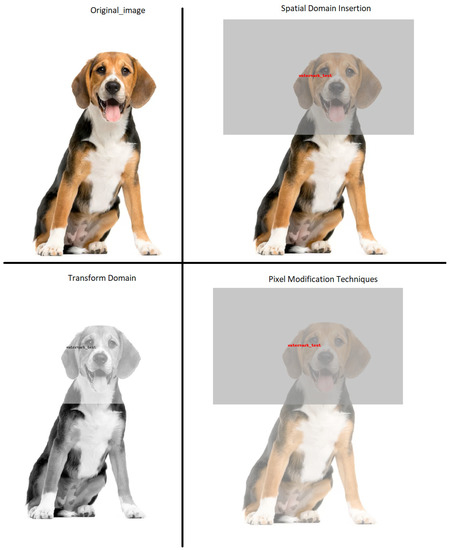
Figure 3.
Results of the watermarking techniques of all the techniques implemented versus the original image.
The domain transform technique takes advantage of the properties of image transforms, such as the Fourier Transform, to apply the watermark in the frequency or transform domain. The main advantage of this technique lies in its ability to hide the watermark in the high-frequency components of the image, making it less visible, even when the figure has been enlarged to discuss the results. This can be beneficial in applications requiring a more invisible watermark and resistance to removal attempts. However, this technique may require a longer processing time due to the transformation and the need to perform operations in the frequency domain.
Pixel modification techniques are based on modifying the image’s pixel values to embed the watermark. They may include methods, such as changing RGB values, replacing specific pixels, or applying non-linear modification algorithms. One advantage of these techniques is their versatility and ability to accommodate different types of images and watermarking requirements. In addition, they allow greater flexibility in controlling the visibility and resistance to the erasure of the watermark. However, these techniques can also be more complex to implement and may require a more detailed analysis of the effects on the quality and integrity of the original image.
Table 2 shows the values obtained in each technique; we can perform a comparative analysis of the different watermark techniques based on the results. Technique 1 has a longer execution time, with a value of 19.82 s, indicating that it may require more computational resources. However, it performs well in decreasing the root mean square error, with a value of 159.34. Technique 2 shows a faster execution time of 8.67 s, which implies a lower computational load. In addition, it significantly reduces the root mean square error to 75.21, indicating a good quality of the resulting image. Technique 3 presents an intermediate execution time of 12.45 s and a mean square error value of 98.75, which suggests an acceptable quality in the resulting image.

Table 2.
Comparative results of watermark techniques.
Regarding resource usage, Technique 2 shows the lowest CPU usage at the start and end, while Technique 1 has the highest memory usage at the start. In general, each technique has advantages and considerations regarding execution time, resource usage, and resulting image quality. The choice of the most suitable technique will depend on the project’s specific requirements and the user’s preferences.
3.2. Generation of Attacks
In Figure 4, the resulting image for each attack carried out is described, highlighting the specific characteristics of each one. In the case of the “Remove Regions” attack, the resulting image no longer bears the watermark. However, it is noted that the regions where the watermark was located have been removed and replaced by black pixels. This causes a drastic change in the image’s appearance, as the removed areas become entirely black. In the “Compression” attack, the image has been resized due to the compression process. This means that the resulting image may be smaller in dimension compared to the original image. This size change can alter the image’s visual perception and affect the quality of the details. In the case of the “Filtered” attack, the resulting image is slightly blurred. Although the blurring is subtle, a loss of detail and decreased sharpness of edges can be observed. This blurriness results from the filtering process applied to the image, which softens the pixels and reduces the definition of the details.
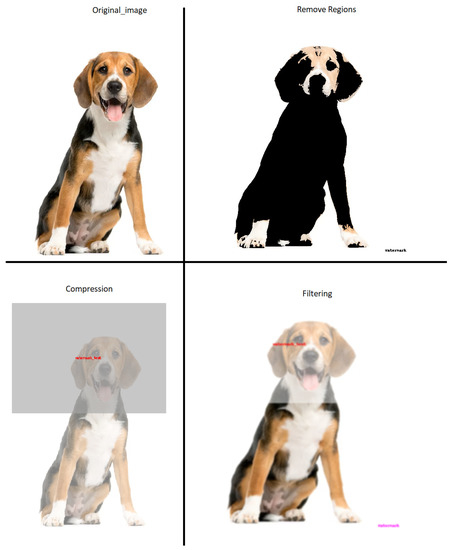
Figure 4.
Result of the application of attacks on the watermarked image versus the original image.
Table 3 shows the results obtained for each attack carried out. The ECM and SSIM are used as image quality metrics to assess image disruption due to each attack. In the case of the “Delete Regions” attack, an ECM of 159.34 and an SSIM of 0.83 were obtained. These values indicate a moderate alteration in the image, with reasonably high structural similarity between the original and attached images. In the case of the “Compression” attack, an ECM of 450.75 and an SSIM of 0.65 are observed. These values reveal a high alteration in the image due to the change in the size and the compression quality.

Table 3.
Results of image attacks with quality metrics.
Furthermore, the structural similarity decreases considerably, indicating a significant loss of detail and structure in the attached image. As for the “Filtered” attack, an ECM of 76.92 and an SSIM of 0.92 are obtained. These values suggest a more subtle alteration in the image, with high structural similarity. Although the image may have some blurring due to filtering, the structural similarity remains relatively high compared to the other attacks. The ECM and SSIM values objectively measure image disruption due to each attack. The compression attack shows a noticeable change in the size and quality of the image, while the filtering attack produces a more subtle alteration but with some blurring.
4. Discussion
This study addresses the issue of protecting the integrity of images through the insertion of watermarks and evaluating the robustness of these marks against different attack techniques. As image sharing has become increasingly common in the digital environment, it has become crucial to implement security mechanisms to ensure the authenticity and protection of images from malicious manipulation. In this sense, watermarks have emerged as an effective solution to provide an additional layer of security and preserve the integrity of images [30,31]. During the development of this study, various watermarking techniques have been used to insert unique information into the images. Spatial domain embedding, domain transform, and pixel modification techniques have been applied to ensure high visual quality and natural-looking images [32]. The results obtained have demonstrated the effectiveness of these techniques in successfully inserting watermarks without significantly affecting the quality of the images. This is essential to guarantee users’ acceptance and visual perception of the images, since an apparent alteration or degradation in quality could negatively affect the viewer’s experience [33].
Regarding the evaluation of the robustness of the watermarks, three primary attacks have been carried out: “Remove Regions”, “Compression”, and “Filtering”. These attacks represent realistic scenarios in which images may be exposed to malicious tampering or standard compression processes [34]. Each of these attacks has revealed valuable information about the ability of watermarks to resist different types of tampering and preserve their integrity. In the case of the “Delete Regions” attack, the watermark was removed from the image. However, noticeable changes were observed in the colors of the removed areas, which were replaced entirely with black. This indicates that tamper detection is precise, and the presence of image disturbances can be determined. Although the loss of visual information is significant, the ability to detect tampering is still practical.
In the case of the “Compression” attack, compression was applied to the watermarked images [35,36]. This process resulted in decreased visual quality and a change in image size. Artifacts and loss of fine detail were evident due to compression, affecting image fidelity. However, the watermark remained visible, and modifications could be identified. Importantly, tampering detection through compression is expected, as images are often compressed for storage or transmission on various media, such as websites or social media. In the case of the “Filtering” attack, a filter was used to smooth the image. Although there was some slight blurring in the resulting image, it was subtle and did not significantly affect the visibility of the watermark [37]. Despite the degradation in visual quality, manipulation was detected, highlighting the proposed watermarks’ ability to resist this type of alteration.
Comparing the results with related works in image and watermark security, it can be stated that our watermarks have proven to be robust against common attacks. Most previous studies have shown the effectiveness of watermarks in detecting tampering, but it is essential to consider that each watermarking technique has its strengths and weaknesses [38]. In this sense, our watermarking techniques have shown high visual quality and good resistance against attacks. It is essential to highlight that our proposal is distinguished by its multidisciplinary approach and the combination of various watermark techniques [39,40]. We have achieved a balance between visual quality and watermark robustness by employing spatial domain embedding, domain transform, and pixel modification techniques. This allows our watermarks to be highly effective in detecting tampering while preserving the natural appearance of images.
5. Conclusions
This study has comprehensively addressed the issue of image integrity protection through the insertion of watermarks and the evaluation of its robustness against different attack techniques. Our watermarking techniques have demonstrated high visual quality and resistance to common attacks, such as region removal, compression, and filtering. The results support our approach’s relevance to image security and highlight the importance of using watermarks as an additional layer of protection in sensitive applications. In future work, new watermarking techniques can be explored, and their robustness against more advanced attacks can be evaluated to continue improving the security of images in the digital environment.
First, various watermarking techniques have been applied to insert unique information into images. Spatial domain embedding, domain transform, and pixel modification techniques effectively embed watermarks without significantly affecting the visual quality of images. This is essential to ensure users’ acceptance and visual perception of the images, as an apparent alteration or degradation in quality could negatively affect the viewer’s experience. Additionally, we have found that our watermarking techniques have maintained a balance between visual quality and robustness, making them suitable for sensitive applications where image authenticity and integrity are paramount.
Secondly, we have evaluated the robustness of watermarks against different attack techniques. Our results have shown that our watermarks can withstand common attacks, such as region stripping, compression, and filtering. Although some of these attacks have caused some degradation in the visual quality of the images, our watermarks have managed to maintain their visibility and detect tampering. This indicates that our watermarking techniques effectively preserve the integrity of images and provide an additional layer of security.
One of the future research prospects is the exploration of advanced machine learning and image processing techniques to further improve the robustness and security of the proposed watermarking algorithm. More sophisticated deep learning models can be investigated, such as generative adversarial networks (GANs), which make it possible to generate watermarks that are more resistant to attacks and difficult to remove without significantly affecting the quality of the original image. In addition, the implementation of deep learning techniques in the watermark detection process could be explored, allowing faster and more accurate identification of fraudulent or unauthorized watermarks in large image databases.
Another perspective is the application of the developed watermarking algorithm on other types of media files, such as videos and audio. Protecting these formats’ authenticity and integrity is also paramount in today’s digital environment. Therefore, extending the reach of the algorithm to encompass other digital media could significantly impact the security and reliability of information online.
In addition, strategies will be deepened to improve the resistance of the watermark against specific attacks, such as filtering and compression, which are common in the processing and transmission of images online. Exploring watermark coding and encryption techniques could be a promising direction to ensure its integrity even after being subjected to various attacks.
Author Contributions
Conceptualization, W.V.-C.; methodology, W.V.-C.; software, J.G.; validation, J.G.-O.; formal analysis, W.V.-C.; investigation, J.G.; data curation, W.V.-C. and J.G.-O.; writing—original draft preparation, J.G.-O.; writing—review and editing, J.G.; visualization, J.G.-O.; supervision, W.V.-C. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The code for this project is available on GitHub at the following repository: https://github.com/wvillegas01/Watermarks.git. You can access and download the code from the repository. Please feel free to use, modify, and contribute to the project as per the terms of the [MIT License] (LICENSE).
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. System Usage Guide
The developed system offers an efficient and robust solution for inserting watermarks in multimedia files. Here is a step-by-step guide on how to use the system:
- Installation of the necessary libraries:
- Install the following Python libraries: Pillow, numpy, scikit-learn, cv2, matplotlib, tkinter, and psutil. You can install them using the pip package manager with the following command: pip install pillow numpy scikit-learn opencv-python matplotlib tkinter psutil.
- Preparation of the original image:
- Before applying the watermark, ensure you have an original image in a suitable format (for example, JPEG or PNG) that you want to protect with a watermark.
- Selection of watermark technique:
- Run the system, and a user interface will open.
- Select the watermark technique you want to use from the available options: “Spatial Domain Insertion”, “Domain Transform”, or “Pixel Modification Techniques”. Each technique offers different approaches to inserting the watermark into the image.
- Loading the original image:
- Click the “Upload Image” button to select the original image from your file system. Select a valid image compatible with the format supported by the system.
- Watermark Settings:
- If you have selected the spatial domain watermark technique, you can enter the watermark text in the corresponding field. Be sure to provide relevant and meaningful text for the watermark.
- If you have selected the domain transform watermark technique, you do not need to configure additional parameters.
- Application of the watermark:
- Click the “Apply Watermark” button to start inserting the watermark on the image.
- The system will apply the selected technique and generate the resulting image with the watermark.
- The resulting image will be displayed in a popup window, and you can save it to your file system using the “Save” button.
- Evaluation of efficiency and precision:
- While inserting the watermark, the system will record the execution time and the use of system resources, such as the percentage of CPU and memory usage.
- Once the watermark has been applied, the root mean square error (RMS) between the original and watermarked images will be calculated. This value indicates the precision of the watermark insertion.
- Generation of attacks (optional):
- To evaluate the algorithm’s robustness against specific attacks, click the “Generate Attack” button.
- A drop-down menu will be displayed with available attack options, such as “Remove Regions”, “Compression”, and “Filtering”. Select the type of attack you wish to perform.
- The system will apply the selected attack to the watermarked image and generate an attacked version. The attached image will be displayed in a popup window.
- Saving and analysis of results:
- The resulting watermarked image and the attached image (if any attack was generated) can be saved to your file system using the “Save” button.
- You can analyze the results obtained, including execution time, resource usage, ECM, and the watermarked and attached images’ visual appearance.
References
- Rakhmawati, L.; Wirawan, W.; Suwadi, S. A Recent Survey of Self-Embedding Fragile Watermarking Scheme for Image Authentication with Recovery Capability. EURASIP J. Image Video Process. 2019, 2019, 61. [Google Scholar] [CrossRef]
- Khalifa, F.M.; Saeed, M.G. Image Watermarking Using All Phase Discrete Cosine Biorthogonal Transform in Selected Pixel Blocks. Polytech. J. 2020, 10, 68–73. [Google Scholar] [CrossRef]
- Kumar, L.; Singh, K.U. Color Ultrasound Image Watermarking Scheme Using FRT and Hessenberg Decomposition for Telemedicine Applications. J. Univers. Comput. Sci. 2022, 28, 882–897. [Google Scholar] [CrossRef]
- Huang, J.C.; Jeng, F.G.; Chen, T.H. A New Buyer-Seller Watermarking Protocol without Multiple Watermarks Insertion. Multimed Tools Appl. 2017, 76, 9667–9679. [Google Scholar] [CrossRef]
- Khadam, U.; Iqbal, M.M.; Saeed, S.; Dar, S.H.; Ahmad, A.; Ahmad, M. Advanced Security and Privacy Technique for Digital Text in Smart Grid Communications. Comput. Electr. Eng. 2021, 93, 107205. [Google Scholar] [CrossRef]
- Ali, Z.; Fazal-E-amin; Hussain, M. A Novel Fragile Zero-Watermarking Algorithm for Digital Medical Images. Electronics 2022, 11, 710. [Google Scholar] [CrossRef]
- Sinhal, R.; Jain, D.K.; Ansari, I.A. Machine Learning Based Blind Color Image Watermarking Scheme for Copyright Protection. Pattern Recognit. Lett. 2021, 145, 171–177. [Google Scholar] [CrossRef]
- Chou, C.H.; Liu, K.C. A Perceptually Tuned Watermarking Scheme for Color Images. IEEE Trans. Image Process. 2010, 19, 2966–2982. [Google Scholar] [CrossRef]
- Cox, I.J.; Miller, M.L. Facilitating Watermark Insertion by Preprocessing Media. EURASIP J. Adv. Signal Process. 2004, 2004, 979753. [Google Scholar] [CrossRef]
- Siledar, S.; Tamane, S. REVERSIBLE DATABASE WATERMARKING WITH DISTORTION CONTROL. Indian J. Comput. Sci. Eng. 2021, 12, 1503–1509. [Google Scholar] [CrossRef]
- Lei, B.; Zhao, X.; Lei, H.; Ni, D.; Chen, S.; Zhou, F.; Wang, T. Multipurpose Watermarking Scheme via Intelligent Method and Chaotic Map. Multimed. Tools Appl. 2019, 78, 27085–27107. [Google Scholar] [CrossRef]
- Kracht, D.; Schober, S. Insertion and Deletion Correcting DNA Barcodes Based on Watermarks. BMC Bioinform. 2015, 16, 50. [Google Scholar] [CrossRef] [PubMed]
- Kumar, S.; Singh, B.K. DWT Based Color Image Watermarking Using Maximum Entropy. Multimed. Tools Appl. 2021, 80, 15487–15510. [Google Scholar] [CrossRef]
- Rinki, K.; Verma, P.; Singh, R.K. A Novel Matrix Multiplication Based LSB Substitution Mechanism for Data Security and Authentication. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 5510–5524. [Google Scholar] [CrossRef]
- Chen, J.; Cao, J.; Liang, Z.; Cui, X.; Yu, L.; Li, W. STPD: Defending against ℓ0-Norm Attacks with Space Transformation. Future Gener. Comput. Syst. 2022, 126, 225–236. [Google Scholar] [CrossRef]
- Khadam, U.; Iqbal, M.M.; Azam, M.A.; Khalid, S.; Rho, S.; Chilamkurti, N. Digital Watermarking Technique for Text Document Protection Using Data Mining Analysis. IEEE Access 2019, 7, 64955–64965. [Google Scholar] [CrossRef]
- Sinha Roy, S.; Basu, A.; Chattopadhyay, A. On the Implementation of a Copyright Protection Scheme Using Digital Image Watermarking. Multimed. Tools Appl. 2020, 79, 13125–13138. [Google Scholar] [CrossRef]
- Moghaddam, M.E.; Nemati, N. A Robust Color Image Watermarking Technique Using Modified Imperialist Competitive Algorithm. Forensic Sci. Int. 2013, 233, 193–200. [Google Scholar] [CrossRef]
- Rachmawanti, E.H.; Santoso, H.A. A Non-Blind Robust and Impercept Watermarking Using Discrete Cosine Transform and Discrete Wavelet Transform. Kinet. Game Technol. Inf. Syst. Comput. Netw. Comput. Electron. Control 2021, 6, 69–76. [Google Scholar] [CrossRef]
- Mukherjee, D.P.; Maitra, S.; Acton, S.T. Spatial Domain Digital Watermarking of Multimedia Objects for Buyer Authentication. IEEE Trans Multimed. 2004, 6, 1–15. [Google Scholar] [CrossRef]
- Venkateswarlu, L. A Robust Dual Watermarking Technique for Medical Images in EHealthcare Records. HELIX 2018, 8, 3206–3214. [Google Scholar] [CrossRef]
- Podilchuk, C.I.; Zeng, W. Image-Adaptive Watermarking Using Visual Models. IEEE J. Sel. Areas Commun. 1998, 16, 525–539. [Google Scholar] [CrossRef]
- Kutter, M.; Winkler, S. A Vision-Based Masking Model for Spread-Spectrum Image Watermarking. IEEE Trans. Image Process. 2002, 11, 16–25. [Google Scholar] [CrossRef] [PubMed]
- Gautier, M.; Noguet, D. Signal Detection Using Watermark Insertion. In Proceedings of the 2013 IEEE 77th IEEE Vehicular Technology Conference, Dresden, Germany, 2–5 June 2013. [Google Scholar]
- El Zein, O.M.; El Bakrawy, L.M.; Ghali, N.I. A Non-Blind Robust Watermarking Approach for 3D Mesh Models. J. Theor. Appl. Inf. Technol. 2016, 83, 353. [Google Scholar]
- Islam, M.; Laskar, R.H. Geometric Distortion Correction Based Robust Watermarking Scheme in LWT-SVD Domain with Digital Watermark Extraction Using SVM. Multimed. Tools Appl. 2018, 77, 14407–14434. [Google Scholar] [CrossRef]
- Lubis, R.R.A.; Hardi, S.M.; Zarlis, M.; Jaya, I.; Tarigan, J.T. Analysis on Combination of Watermarking Algorithm: Modified Least Significant Bit Algorithm with Least Significant Bit+1. Proc. J. Phys. Conf. Ser. 2019, 1235, 012081. [Google Scholar] [CrossRef]
- Gong, X.; Rodrigues, M.; Kiyavash, N. Invisible Flow Watermarks for Channels with Dependent Substitution, Deletion, and Bursty Insertion Errors. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1850–1859. [Google Scholar] [CrossRef]
- Goljan, M. Cryptanalysis of the Yeung–Mintzer Fragile Watermarking Technique. J. Electron. Imaging 2002, 11, 262. [Google Scholar] [CrossRef]
- Kuraparthi, S.; Kollati, M.; Kora, P. Robust Optimized Discrete Wavelet Transform-Singular Value Decomposition Based Video Watermarking. Trait. Du Signal 2019, 36, 565–573. [Google Scholar] [CrossRef]
- Wong, P.W.; Memon, N. Secret and Public Key Image Watermarking Schemes for Image Authentication and Ownership Verification. IEEE Trans. Image Process. 2001, 10, 1593–1601. [Google Scholar] [CrossRef]
- Mansouri, A.; Aznaveh, A.M.; Torkamani-Azar, F.; Kurugollu, F. A Low Complexity Video Watermarking in H.264 Compressed Domain. IEEE Trans. Inf. Forensics Secur. 2010, 5, 649–657. [Google Scholar] [CrossRef]
- Wójtowicz, W.; Ogiela, M.R. Digital Images Authentication Scheme Based on Bimodal Biometric Watermarking in an Independent Domain. J. Vis. Commun. Image Represent. 2016, 38, 1–10. [Google Scholar] [CrossRef]
- Coatrieux, G.; Pan, W.; Cuppens-Boulahia, N.; Cuppens, F.; Roux, C. Reversible Watermarking Based on Invariant Image Classification and Dynamic Histogram Shifting. IEEE Trans. Inf. Forensics Secur. 2013, 8, 111–120. [Google Scholar] [CrossRef]
- Laouamer, L.; AlShaikh, M.; Nana, L.; Pascu, A.C. Robust Watermarking Scheme and Tamper Detection Based on Threshold versus Intensity. J. Innov. Digit. Ecosyst. 2015, 2, 1–12. [Google Scholar] [CrossRef]
- Kadian, P.; Arora, N.; Arora, S.M. A Highly Secure and Robust Copyright Protection Method for Grayscale Images Using DWT-SVD. Int. J. Recent Technol. Eng. 2019, 8, 7284–7288. [Google Scholar] [CrossRef]
- Younus, Z.S.; Hussain, M.K. Image Steganography Using Exploiting Modification Direction for Compressed Encrypted Data. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 2951–2963. [Google Scholar] [CrossRef]
- Aziz, F.; Ahmad, T.; Malik, A.H.; Uddin, M.I.; Ahmad, S.; Sharaf, M. Reversible Data Hiding Techniques with High Message Embedding Capacity in Images. PLoS ONE 2020, 15, e0231602. [Google Scholar] [CrossRef]
- Srivastava, R.; Tomar, R.; Gupta, M.; Yadav, A.K.; Park, J. Image Watermarking Approach Using a Hybrid Domain Based on Performance Parameter Analysis. Information 2021, 12, 310. [Google Scholar] [CrossRef]
- Wang, Z.; Zhang, Y.; Mosalam, K.M.; Gao, Y.; Huang, S.L. Deep Semantic Segmentation for Visual Understanding on Construction Sites. Comput.-Aided Civ. Infrastruct. Eng. 2022, 37, 145–162. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).