1. Introduction
Wireless networks have become one of the most popular types of communication networks because of the many services they provide. In addition, Wi-Fi greatly helps computers communicate and interact with each other at a speed very similar to that of a wired LAN (Local Area Network) [
1]. VLAN is a technology that helps to solve many performance problems. In addition, it provides many uses for wireless communication networks to determine both management and security policies within a company. It also enables operators to integrate any isolation level by separating hosts into different broadcast domains [
2]. There are a number of reasons to create VLANs, but the primary one is traffic control; as a LAN expands and more network devices are added, the frequency of the broadcast also grows, causing the network to become very data-congested. Finally, it may be said that dividing a network into smaller broadcast domains by using VLANs causes broadcast traffic to vanish [
3]. VLANs have restricted access to private server data by managing traffic, improving security, and reducing levels of congestion [
4]. The aim of this research was to study the performance of a VLAN in a wireless network using the Riverbed Modeler academic Edition v17.5 simulation program, since the VLAN improves bandwidth utilization and has proven to have many advantages in wireless networks. Delay, throughput and traffic dropped were examined with and without using a VLAN, showing that the VLAN improved the delay and traffic dropped parameters but reduced the throughput of the network, which is a major drawback of VLANs. Ad hoc routing algorithms, such as OLSR, DSR, and AODV, have been investigated to improve the performance of the VLAN in wireless networks in terms of delay, throughput and traffic dropped. An additional investigation into the impact of ad hoc routing protocols (OLSR, DSR, and AODV) in wireless sensor networks is also introduced in this paper.
The rest of the paper is organized as follows:
Section 2 presents related studies,
Section 3 presents basic theoretical concepts,
Section 4 presents the materials and methods,
Section 5 presents the results and discussion, and
Section 6 presents the conclusions.
2. Related Work
With the use of VLANs, the study in [
5] improved the functionality of already-existing computer networks, specifically regular LAN networks. The findings demonstrated that a VLAN network is more reliable than a LAN in terms of throughput, delay, jitter, and packet loss and the VLAN network is more dependable than LAN when there is a lot of traffic. Dlnya Abdulahad Aziz analyzed how implementing VLANs affects network performance and demonstrates how to satisfy security requirements in any field. They concluded that when the LAN grows and new network devices are added, creating VLANs is essential for data and traffic control in order to maintain the broadcast frequency’s validity [
3]. Dhurgham Abdulridha et al. evaluated the effectiveness of LAN and VLAN networks in many circumstances by measuring important performance factors such as throughput, average latency, and traffic sent and received. OPNET 17.5 Student Version was used to run the simulation. The simulation findings showed that without VLAN technology, there is more existing traffic and the average queuing delay is cut in half [
4]. Abbas Mehdizadeh et al. explains the precise definition the operation of VLAN memberships in a switched network. The use of virtual local area networks can simplify network management and improve the security of networks [
6]. Yakubu Ajiji Makeri et al. improve the performance of a business network by implementing VLAN through the simulation of an existing LAN. They utilized a virtual local area network to address the issues with the current business network to model and contrast the performance of the new (VLAN) and old (NO VLAN) enterprise networks. Additionally, standard deviation (SD) was utilized to determine the consistency of the responses and satisfaction levels. Through the use of a VLAN, network virtualization provided further advantages [
7].
All the previous studies examined the impact of VLANs in a local area network in terms of performance and security, but in this study, the impact of VLANs on the management of the wireless networks and performance improvement is examined and an investigation into routing protocols to improve the performance of the wireless network is carried out.
3. Basic Theoretical Concepts
The theoretical concepts in this study are described in terms of:
3.1. Virtual Local Area Network
Recently, the world has witnessed remarkable development in the field of wireless communication, including many different portable devices that do not have a traditional (wired) connection. Fixed stations for wireless networks have been established using mobile nodes and computers. These are called wireless roaming networks [
8]. The mobility and flexibility achieved by portable wireless networks increases connectivity. This has allowed researchers to build a mobile communications engineering computing platform that is compatible with current architectures, in addition to considering the wireless and mobility characteristics [
9].
Recently, virtual LANs have expanded from each major LAN to become an integral property of switched LAN solutions. One of the reasons for the attention now being given to VLAN features is the rapid deployment of LAN switching, which started two decades ago. A VLAN provides an alternative solution to broadcast containment routers because it makes it possible to switch to broadcast traffic. A VLAN makes it possible to split a physical network into two layers [
6].
Virtual LAN technology is used in the development of university internal networks, companies, and business networks. A VLAN is used for data link layers to create multiple networks. The Local Area Network is subdivided into different broadcast domains. The division of workstations is focused on virtually linked platforms and software teams that may or may not be physically related. A VLAN enables a network administrator to create a logical network from a physical network. By dividing a large network into smaller networks, VLAN technology improves network efficiency, management, and security [
10]. That is, when using VLAN, in addition to the possibility of configuring the physical network, the structure is logical and impeding. VLAN isolates computers with better shape and performance from WLAN networks. This can be accomplished by configuring users and switching to a VLAN so that their department networks are accessible in a shared space [
11,
12]. Therefore, logical connectivity between switch ports can be made available in VLAN. Thus, communication is performed between nodes within a similar VLAN to supply the necessary security, admission control, and to mend the overall network performance and scalability. VLANs minimize broadcast traffic and mend traffic management by providing flexibility in the IP network location and relocation of devices [
13]. There is always a need for monitoring tools to enable network administrators to maintain effective communication over a swapped infrastructure. Efficient routing algorithms must be applied to ensure effective communication paths [
14].
3.2. Routing Protocols of Wireless Networks
The main features of the nodes in WLAN are Dynamics and Robustness, which are controlled by different ad hoc routing protocols, such as OLSR, DSR, and AODV. However, the increasing demand for resources in networks leads to insufficient resources. Node mobility also results in link failure and significant routing overhead, which lowers the reliability of network communication [
15].
- (1)
Reactive routing protocols: These are often called upon to route protocols for requests. A node can only find a path for sending a packet to another node. It uses a cache path if it does not have routing tables [
16].
- (2)
Proactive (Distance Vector) routing protocols: In these protocols, information about routing is maintained periodically for each node with one route recorded [
16].
- (3)
Hybrid routing protocol: This incorporates the benefits of both reactive and constructive routing. Initially, a proactive approach is used to obtain route information, and then the route requirement is reactively handled to the required node [
16,
17]
A Performance study of the two AODV, DSR reactive routing protocols, and OLSR proactive routing protocols is presented in this paper.
AODV stores data routing in standard routing tables for wireless networks. The function of the timer in mobile node is the process of removing the routing table entry when the route has no use for a specific period and it works in two basic operations [
18,
19].
In the first process, it is necessary to locate and preserve the route. Subsequent neighbor messages are handled by the source and intermediate nodes in each flow to propagate material packets. In the route discovery stage, multimedia communication is implemented by sending an introductory message. In addition, error messages are sent when connection failure is observed. In the route maintenance process, an RREQ is sent by the root node to its neighbors and the data propagate until the destination node is reached.
DSR: In this protocol, an on-request path is provided when a transmitting node requests one, and source routing is used instead of searching the routing table at each intermediate node. The transmission of introduction messages is not required to be periodic in order to notify neighbors of its availability, which is distinguished from other on-demand routing and DSR is an interactive routing protocol. An example of this is the route search and maintenance phase, where route request packets are produced within the network to perform a route check [
19,
20]. The network with DSR is completely self-configuring and self-organizing, with no requirements for network administration [
16].
OLSR is a proactive routing protocol that is specifically designed for wireless networks. The protocol maintains one or more tables for each node. The nodes are available because of the proactive existence of this protocol. It also updates the routing information so that all the information on the nodes is announced and published within the entire network [
21].
3.3. Network Simulation
There are several difficulties in implementing wireless protocols in the real world as they include a testable environment setting and can contain thousands of portable nodes. In addition, it is difficult to build different environments. A protocol is produced that simulates these difficulties, and thus the protocol is tested in several environments to be verified once, the simulation is performed, and the protocol is implemented [
22].
Simulation: This is a simple method used to evaluate a test environment and was created to simulate reality. The size of the internet is likely to change. In addition, the statistical results of the simulation provide the ability to evaluate the network performance and the implemented algorithm parts. Design errors in the simulation world are easily corrected rather than being corrected in real models. For this research, Riverbed Modeler v17.5 was used as a tool to simulate the inspection dedicated to the virtual network WLAN and to clarify how to improve performance by routing algorithms. The Riverbed Modeler provides a framework for all proposed studies, including model design, simulation, and analysis of all data, and accurately describes packets. In the simulation editor, configuring the network components and creating parameters are simple [
23].
4. Materials and Methods
The proposed network in terms of the number of testable simulation scenarios are designed according to the simulation environment of this study. Then, the statistics were selected in terms of quality-of-service parameters to run a simulation and analyze the results. This study was implemented utilizing the Riverbed Modeler Academic Edition v17.5. The simulation setup consisted of a number of testable scenarios to test the network performance of the VLAN and the impact of the routing algorithms on the network performance. Each scenario consisted of several workstations linked to two Ethernet switches via Access Points for communication between the workstations and two servers. Two cases were considered in this study (low density and high density) with two traffics (File Transfer FTP, Web browsing HTTP and Email) to investigate the behavior of the designed VLAN network when the load (number of clients) is increased and how the ad hoc routing protocols could improve network performance in terms of the selected quality-of-service parameters. The simulation environments of each of the Riverbed scenarios are as follows:
Three access points: named (wirelessethernetslip4router);
Numbers of workstations (wlanwkstn) connected by the links to the servers;
Two Ethernet switches (Ethernet16 switch): each switch had 16 ports for configuration;
Two servers (Ethernet Servers) to represent two departments;
Links (100BaseT) to connect the access points to the switches, links connecting the switches to the servers, and a single link to connect two switches that act as trunks in VLAN scenarios;
Application definition and profile configuration: to define and assign the application and services to clients and servers in the network;
In another case, the wireless sensor network was examined as another network. WSNs consist of number of sensors sending data to the controller. These parameters were represented utilizing ZigBee (IEEE 802.15.4) standard connected to WIFI as a gateway.
Table 1 shows the simulation environment of the proposed network.
In the first case (low-density) Scenario1–Scenario5, 15 workstations were used in the designed network.
The scenarios are as follows:
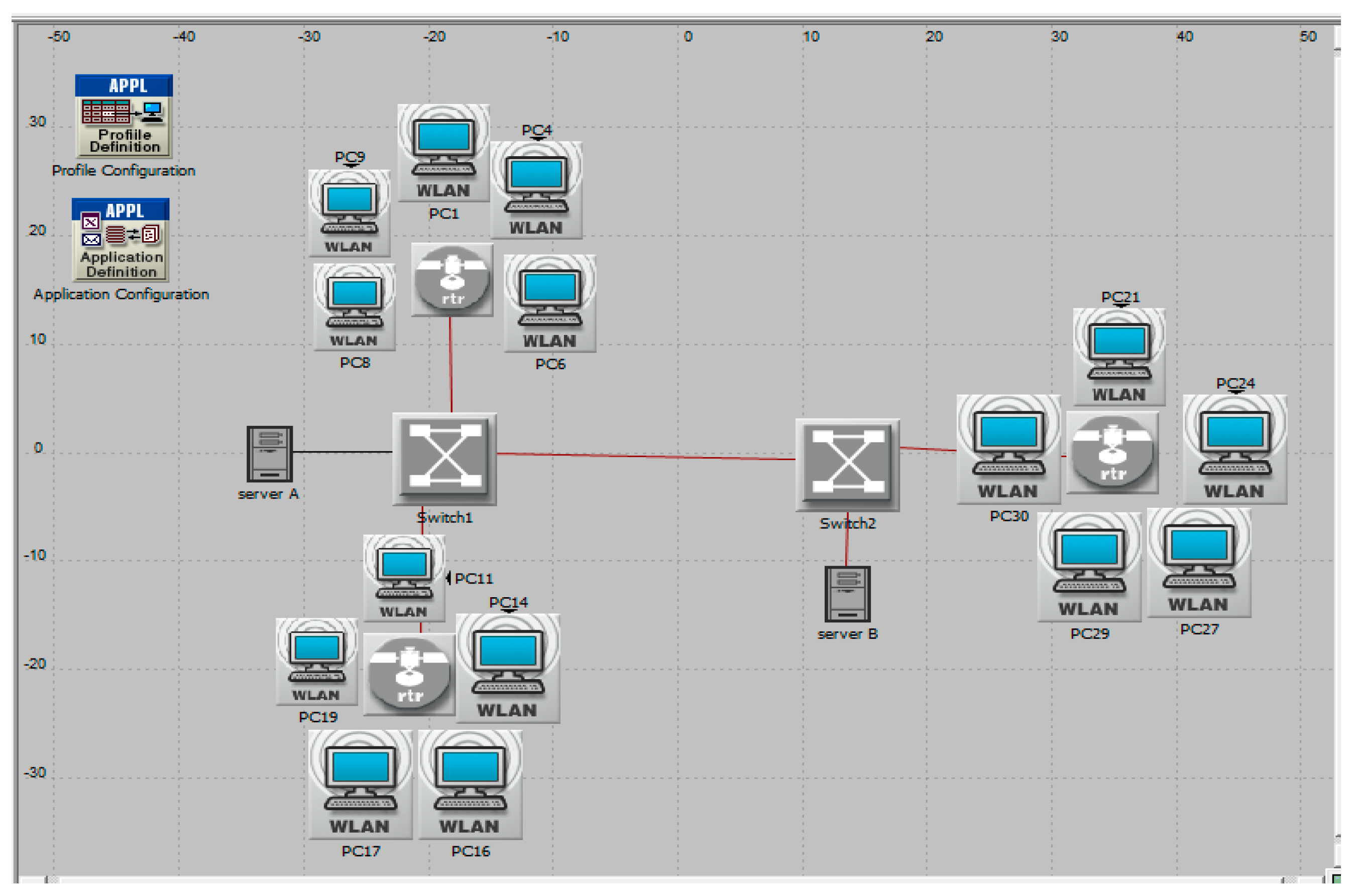
Scenario 1 (No VLAN): Wireless LANs consists of the following parameters: 15 workstations numbered (PC1-PC15) and connected to two Ethernet switches via three access points connected by a 100Base-T link. The switches were connected to two Ethernet servers. In this case, each PC could randomly select a server to send and receive data at any time. The scenario is illustrated in
Figure 1.
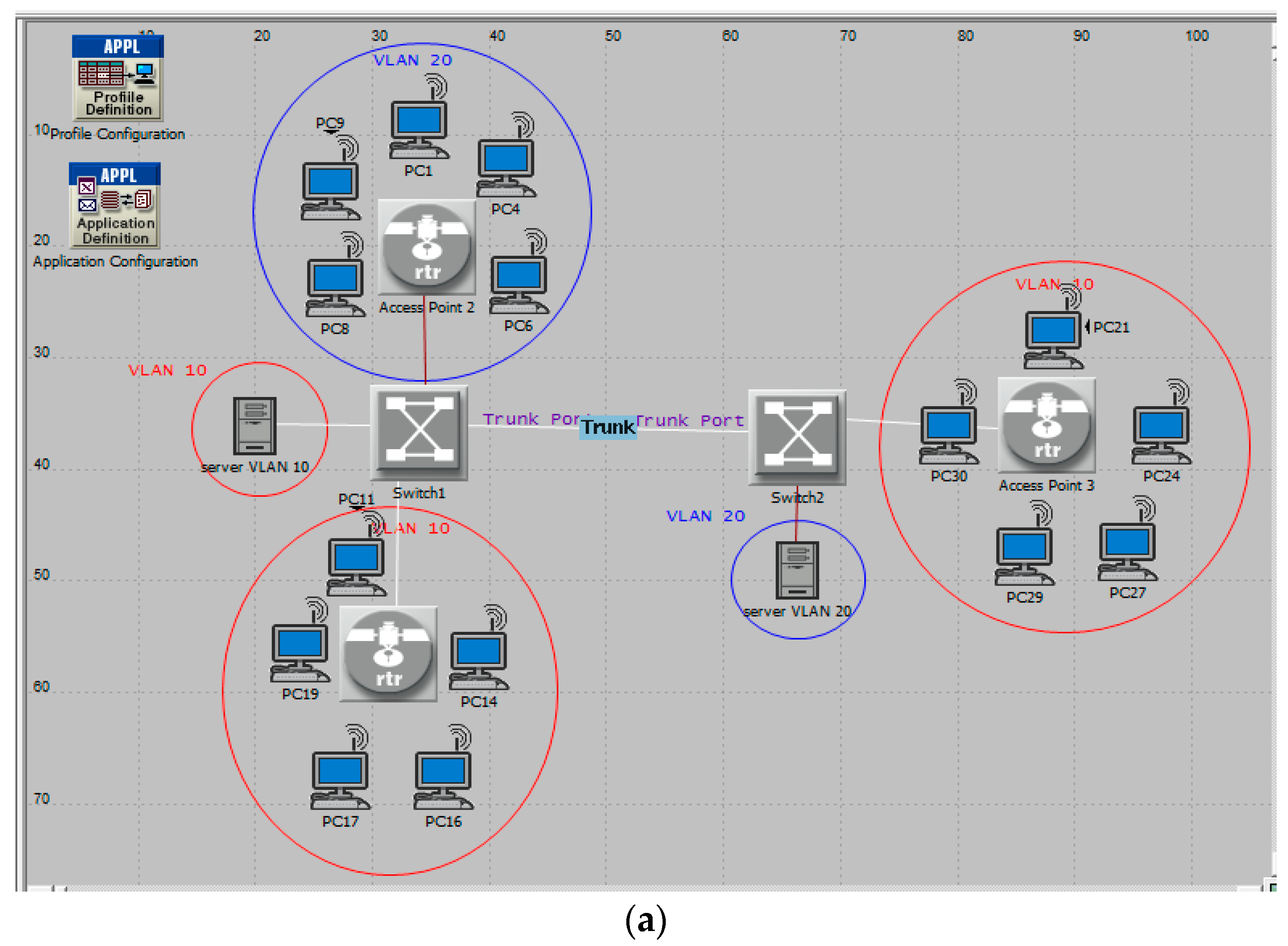
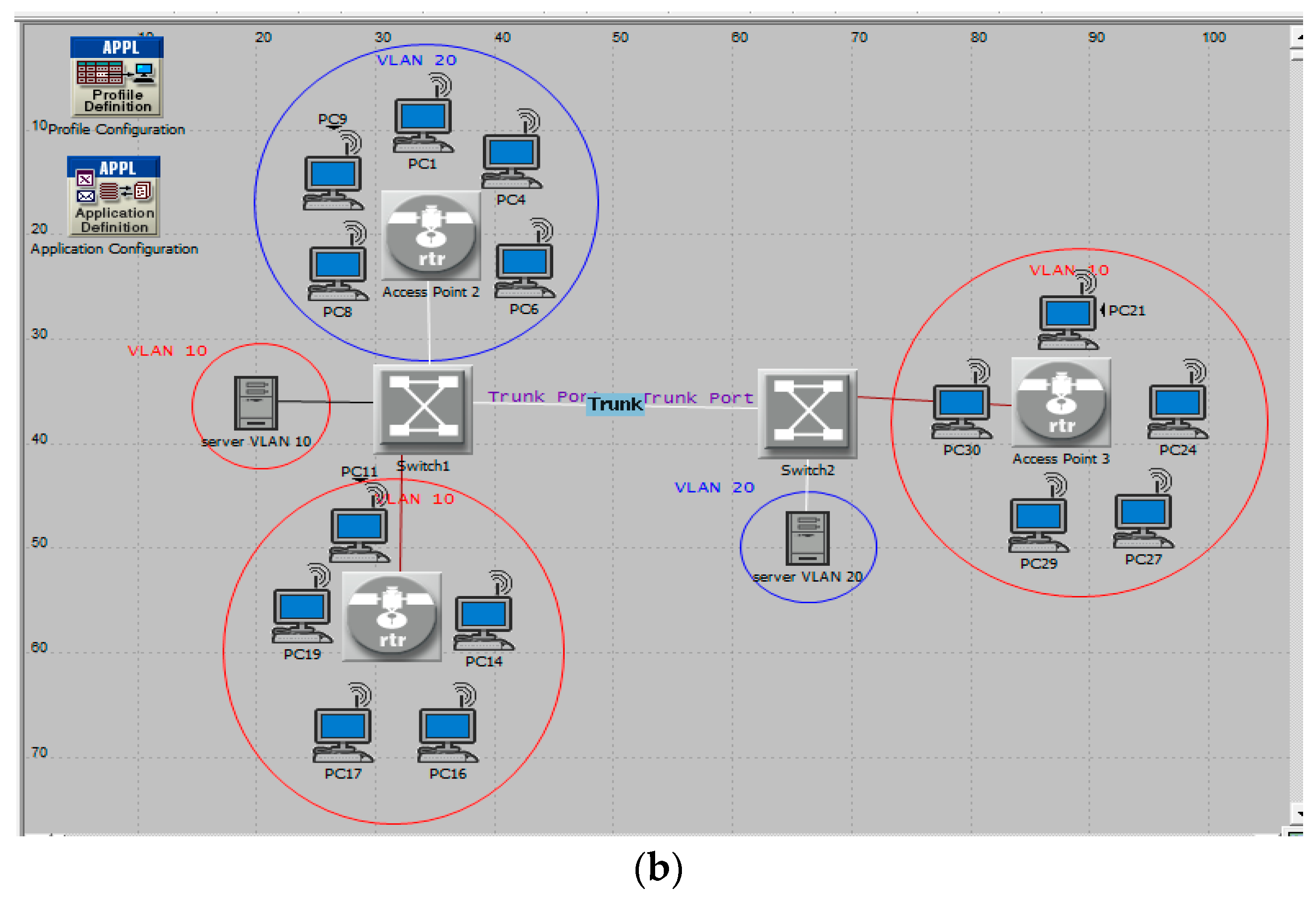
Scenario 2 (VLAN): VLANs were configured by dividing the network in two VLAN-aware switches with access ports. The VLAN association of these connected end-nodes was identified by the PVID of these ports. The switches with trunk ports were connected to each other to support both VLAN 10 and VLAN 20. VLAN 10 had ten PCs connected via two access points in wireless mode to two switches and VLAN 20 contained five PCs connected via an access point to the first switch. This scenario is shown in
Figure 2.
In this scenario, communication of any workstation cannot be carried out with any server at any time. VLAN 10 Clients selected servers randomly but their linked requests for the server of VLAN 20 were rejected by “Switch2”, so that service was obtained from the server in their VLAN, minus any problems, as shown in the “VLAN 10 Dropped Traffic” graph. In VLAN 2, clients only tried to connect to the server in their VLAN, hence VLAN 20 experienced smaller packet drops than VLAN 10. These could be illustrated as shown in
Figure 3.
Scenario 3, Scenario 4 and Scenario 5: In these scenarios, three ad hoc routing algorithms (AODV, DSR and OLSR) with 15 workstations (PCs) were applied to investigate their effect on the delay and throughput improvement performance of the VLAN, as well as the PDR or traffic dropped.
In the second case (High Density), the number of workstations was doubled to 30 PCs.
Scenario 6 and Scenario 7: These scenarios state that No VLAN and a VLAN with the number of workstations is 30 PCs.
Scenario 8, Scenario 9 and Scenario 10: In these scenarios, three ad hoc routing algorithms (AODV, DSR and OLSR) were applied to investigate their effect on the delay and throughput improvement in VLAN performance when the traffic was increased to 30 workstations.
Scenario 8, Scenario 9 and Scenario 10: In these scenarios, three ad hoc routing protocols were examined to investigate the effect of ad hoc routing protocols on wireless sensor networks, as shown in
Figure 4.
5. Results and Discussion
Individual statistics were collected, the simulation was run in two cases (low and high density) and the results were obtained to study the impact of VLAN technology.
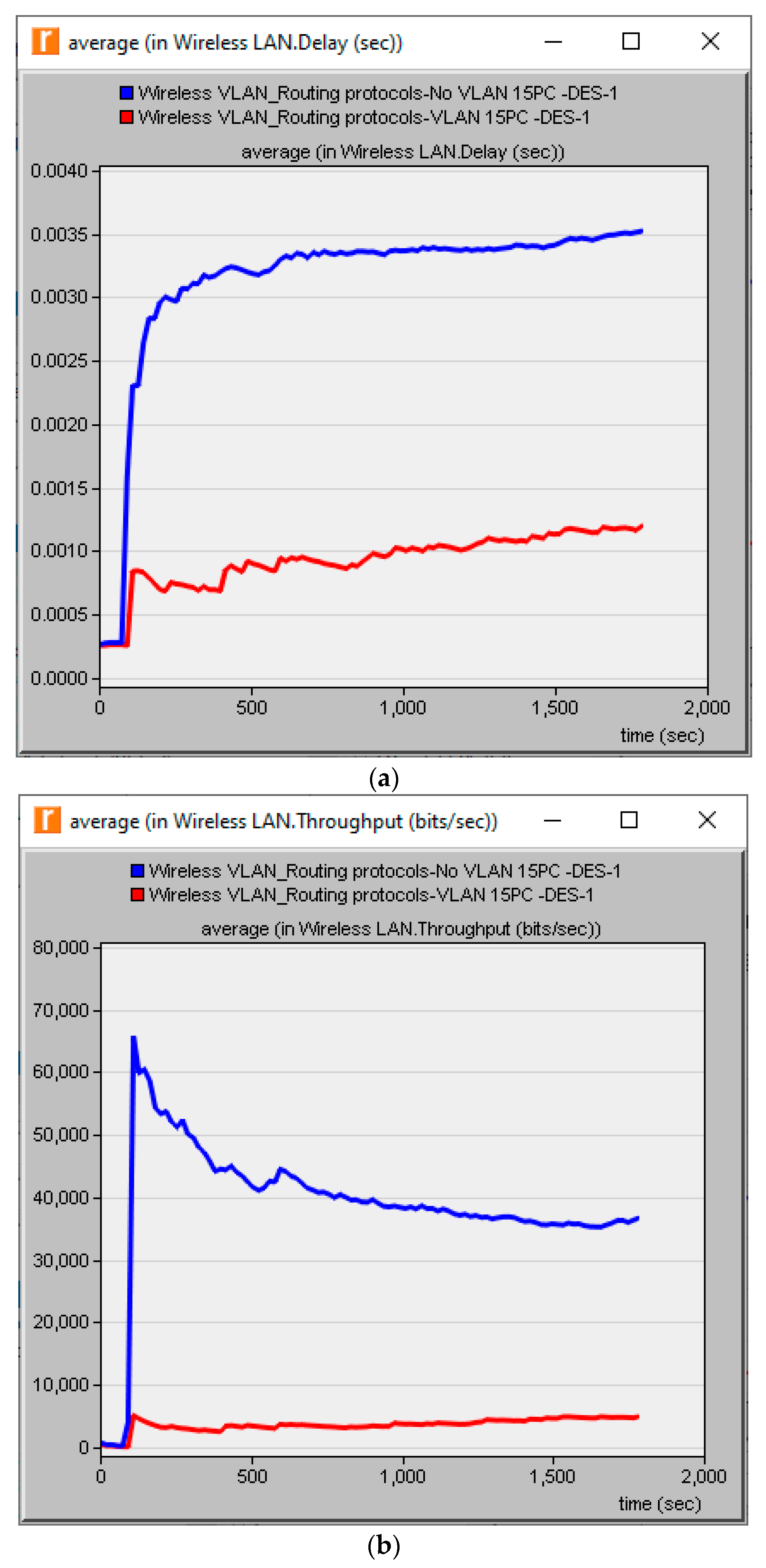
Delay and Throughput:Figure 5 showed the delay and throughput of the network with and without the VLAN and VLAN traffic dropped graph between VLAN 10 and VLAN20.
Delay and Throughput indicated how the Virtual LAN could improve the network by reducing the delay and the data dropped, but the throughput was also reduced. VLAN traffic dropped indicated how clients’ requests from VLAN 10 to the VLAN 20 server were rejected by “Switch2”, so that the service was received from the server in their VLAN without any problem, but in VLAN 20, the clients only tried to connect to the server in their VLAN, hence VLAN 20 experienced smaller packet drops than VLAN 10, as shown in
Figure 6.
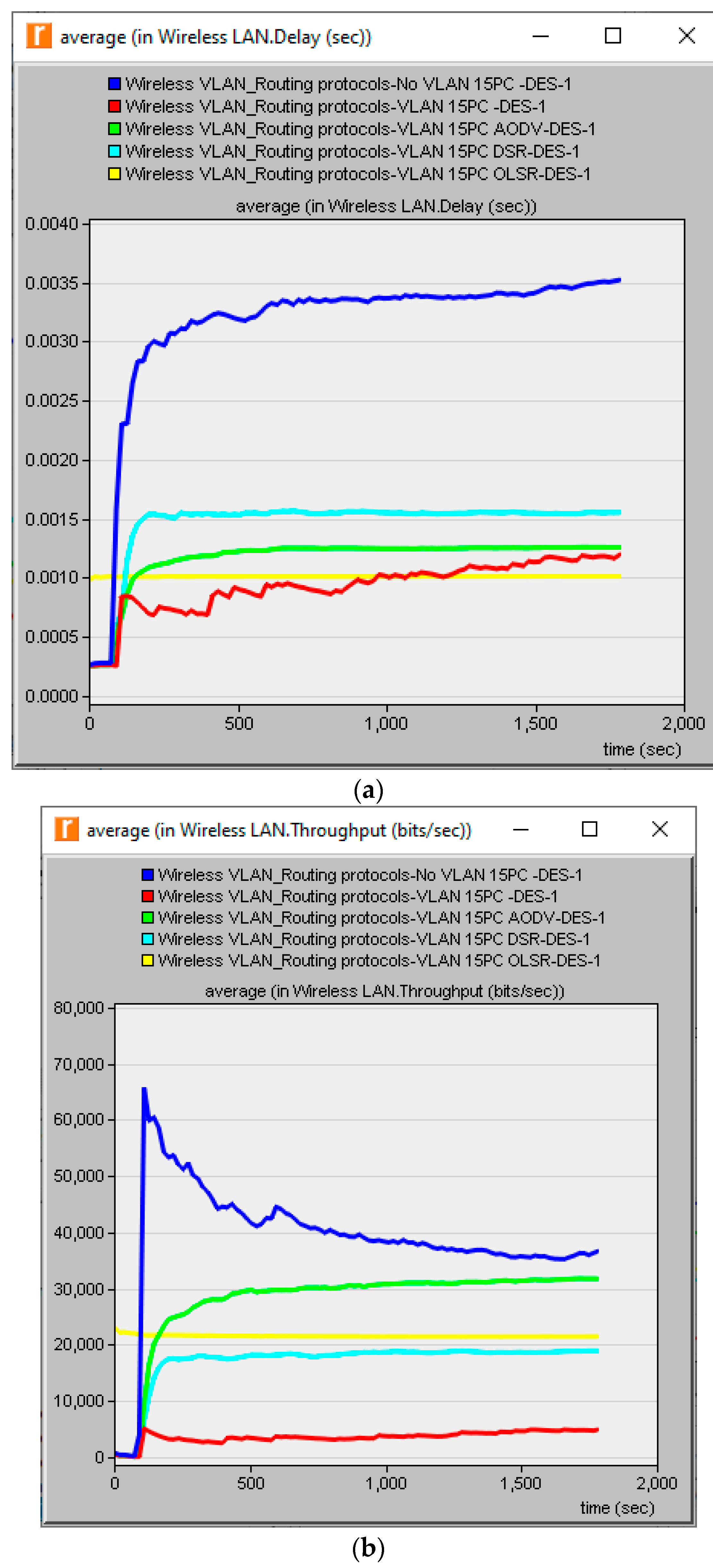
As seen above, VLAN’s primary problem was that it reduced throughput, which is one of the important QoS parameters of any network performance. In this study, the degradation in throughput was improved by using three routing protocols in a low-density network, where the number of workstations was 15 PCs.
Figure 7 shows the network delay and throughput with three routing protocols (AODV, DSR and OLSR).
Figure 7 indicates that using routing protocols could improve VLANs by reducing the delay of the WLAN and increasing throughput, thus improving the performance of the WLAN. The AODV routing protocols also improved the network by achieving the highest throughput. This study carried out an additional investigation to demonstrate the impact of routing protocols utilization in high-density cases (30 workstations). Delay and throughput in high-density scenarios are shown in
Figure 8.
At high density, all the ad hoc routing protocols reduced the delay and increased the throughput. AODV improved the delay and throughput of the network because it achieved the least delay and highest throughput.
Traffic Dropped: At low density, traffic dropped in VLAN 10 and VLAN 20 for three ad hoc routing protocols was compared with VLANs without ad hoc routing protocols to investigate the effect of ad hoc routing protocols on packets dropped, as shown in
Figure 9.
At high density, traffic dropped in VLAN 10 and VLAN 20 for three ad hoc routing protocols was compared with VLAN without ad hoc routing protocols, as shown in
Figure 10.
As shown in
Figure 8 and
Figure 9, the routing protocols reduced the VLAN traffic dropped because of the VLAN.
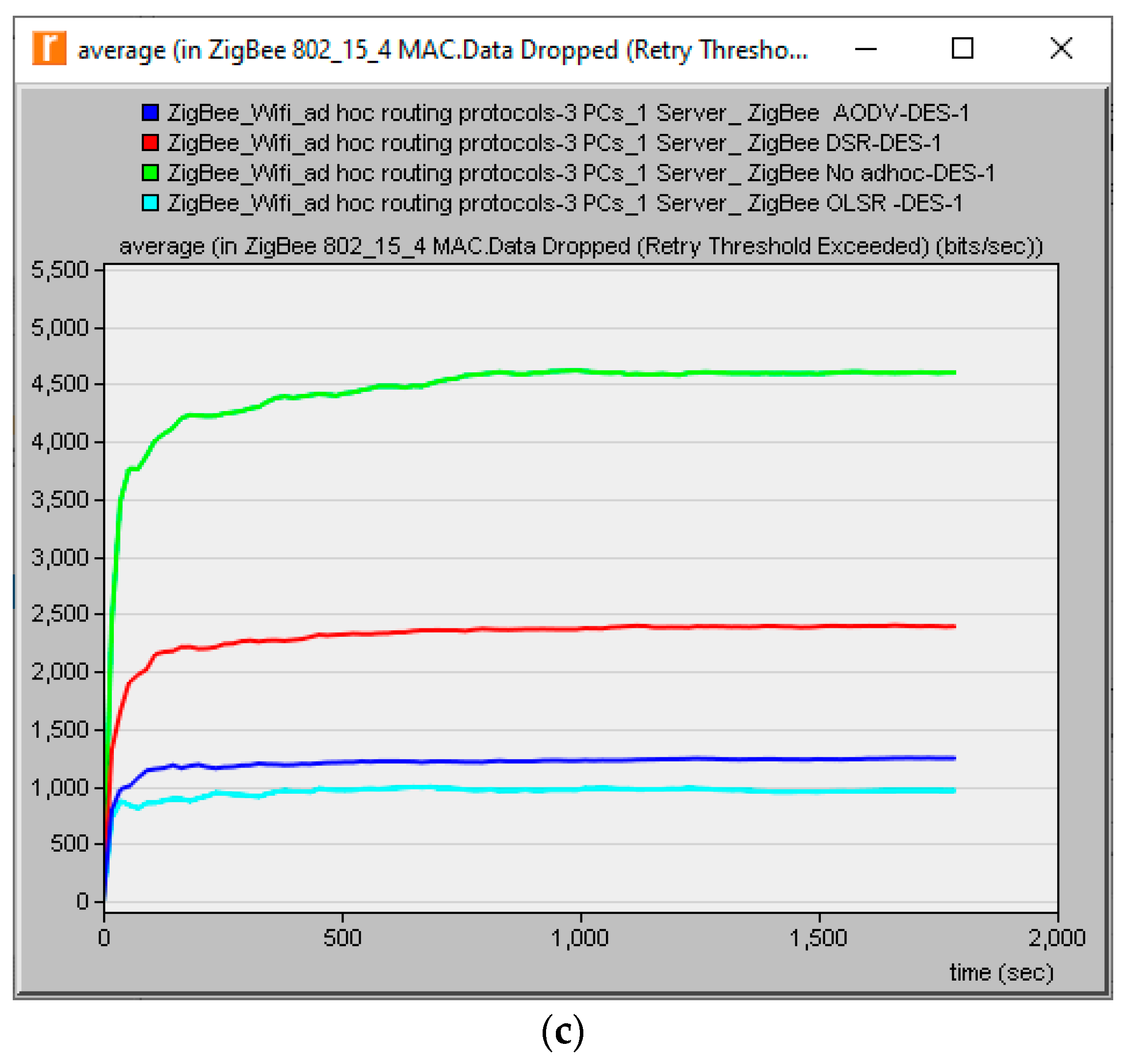
The same three ad hoc routing protocols (AODV, DSR and OLSR) were utilized to examine how these protocols improved the throughput, delay and data dropped of the WSN, as shown in
Figure 11.
As seen in the Figure above, these routing protocols improved the delay, throughput and data dropped QoS parameters of the Wireless Sensor Networks. AODV achieved the least delay and the highest throughput and AODV also improved the traffic dropped of the network.
6. Conclusions
This study investigated the impact of dividing the networks in WLAN by introducing virtual LAN and how this could improve the performance of networks in terms of metrics such as delay, throughput and PDR. Riverbed academic Edition v17.5 was used as a simulation tool for our investigation. This study consisted of 15 testable scenarios in two cases for a low-density network and a high-density network. Two important traffics (File Transfer FTP, Web browsing HTTP and Email) were applied in all scenarios. The use of the VLAN improved the network by reducing the delay and data dropped of the wireless network; however, the throughput was reduced, which is a major drawback of VLANs. Therefore, this throughput could be improved using the routing protocols examined in this study. The aim of this paper is to improve the VLAN for the wireless network by utilizing three ad hoc routing protocols such as AODV, DSR and OLSR for low and high traffic density in a number of different scenarios, using Riverbed Modeler Simulation program in terms of the number of quality-of-service parameters. The results showed that ad hoc routing protocols improve the delay, throughput and traffic dropped performance of the VLAN, as shown in
Figure 7. As the number of workstations was increased, AODV achieved higher improvement in throughput for low density and high density, but its delay was increased when the number of workstations was increased. OLSR achieved better delay improvement, even when the traffic increased, as shown in
Figure 8. Traffic dropped was also an improvement in this network performance for the low-density and high-density cases, as shown in
Figure 9 and
Figure 10, respectively. The utilization of these routing protocols reduced the traffic dropped in the VLAN, which represented an extra improvement to the VLAN network in wireless communication so that the better selection of the ad hoc routing protocol played an important role in delay or throughput improvement. In this paper, the three ad hoc routing protocols also improved the performance of the Wireless Sensor Network in terms of delay, throughput and traffic dropped, as shown in
Figure 11. Consequently, this study recommends the use of a smart device to determine the type of routing used in terms of the delay or throughput requirements.