A Systematic Review of Using Machine Learning and Natural Language Processing in Smart Policing
Abstract
:1. Introduction
2. Background
3. Methodology
3.1. Research Questions
- RQ1: What methods in ML and NLP have been proposed to process crime data and predictive policing?
- RQ2: What are the strengths and limitations of the current proposed methods, and how can they be addressed?
3.2. Research Process
- IC1: Provides/lists the ML methods or frameworks used in smart policing;
- IC2: States the challenges of using AI in smart policing and how to address them.
4. Findings
4.1. Addressing RQ1
4.1.1. Mapping Techniques
4.1.2. Machine Learning
| Reference | ML Algorithm | Description | Result |
|---|---|---|---|
| [50] | K-means | The resulting clusters plotted on a geospatial plot show the possible crime patterns | |
| [51] | KNN, RF, SVM, NB, CNN, long short-term memory (LSTM) | Presents a comprehensive comparison of ML algorithms for crime hotspot prediction based on historical data of a large city in Southeast China from 2015 to 2018; they also used built environment data such as road network density and points of interest | LSTM performed better than other models as it extracted the patterns and regularity from historical crime data more accurately; built environment data improved the performance as well |
| [52] | LR, DT, RF, multilayer perceptron (MLP), NB, SVM, XGBoost, KNN, LSTM, ARIMA | Performs a comparison between ML algorithms to predict crime hotspots based on historical data and time-series analysis in Chicago and Los Angeles | XGBoost performed better than other algorithms, with 94% and 88% accuracy on the two datasets. LSTM classified crime over different periods, showing that Chicago’s crime rate had more variations compared with Los Angeles. The ARIMA model was implemented to analyze the five-year trends of crime rates and hotspots, suggesting moderate variations for Chicago and a decline for Los Angeles |
| [53] | ARIMA, smoothing exponential methods with SES and HES | An ARIMA time-series model is employed to perform short-term property crime prediction for a city in China based on 50 weeks of property crime data and compared with SES and HES methods | The ARIMA model has higher fitting and prediction accuracy than exponential smoothing |
| [54] | K-means and NB | Proposed a predictive policing system model focusing on street crime in the Karachi region. | The busiest parts of the cities have the highest rates of crime |
| [55] | NB and backpropagation (BP) neural network | Explores classification techniques to predict crime categories based on crime datasets collected from socioeconomic and law enforcement data of various states in the USA | NB outperformed the BP algorithm, achieving an accuracy of 90.22% for one group and 94.08% for another |
| [56] | Linear discriminant analysis (LDA) and KNN | Introduces a new model for crime hotspot prediction that incorporates area-specific heat levels, temporal distances of holidays, and neighborhood attributes to create spatiotemporal characteristics; LDA is used for dimensionality reduction, and KNN is used for prediction | The proposed model performs optimally when analyzing weekly crime statistics |
| [57] | LASSO feature selection with naïve Bayes and ARIMA model | Proposes a model to predict future crime occurrences at a future time and predict which type of crime may be happening in a given area; it also analyzes crime features including date, time, and geographical factors like latitude and longitude, and employs LASSO feature selection and classification models such as naïve Bayes and SVM to extract insights from the data | The proposed model outperforms SVM, KDE, and deep neural networks in terms of accuracy; however, SVM has the best precision value |
| [58] | Negative binomial, Poisson regression, and regression models | Crime data of Salinas, California, USA | All three models have similar performance |
| [59] | SVM, multilayer neural network, LR | Conducts research on how SVM can provide a framework to predict the probability of reincarceration and preforms a comparison among SVM, LR, and neural networks based on a recidivism dataset | SVM can be a reliable method for recidivism prediction, but a combined prediction utilizing all three methods obtains the most flexibility, with enhanced accuracy and effectiveness of crime forecasting |
| [60] | DT, NB | Predicting crime categories in different states of the USA | DT outperformed NB |
| [61] | DT J48, NB, SVM, multilayer perceptron | Predicting crime categories | DT outperformed other algorithms |
| [62] | DT J48 | Suggests a crime prediction prototype model using a decision tree (J48) based on the UCI dataset of “Crime and Communities” | Experimental results indicate that the J48 algorithm achieves an accuracy of 94.25% in predicting crime categories |
| [63] | DT, NB | Suggests crime category prediction in specific geographical areas using ML algorithms based on historical incident data sourced from the Chicago Police Department’s CLEAR system; both algorithms were applied to the top 9 selected features from the dataset | DT outperformed the NB algorithm in terms of predictive accuracy |
| [64] | Neural network, NB, RF | Predicting future drug-related crime hotspots | Neural network has a better performance |
| [45] | NB, DT | Extract rules for classification and prediction of crime and criminality | NB is more reliable |
| [65] | Linear regression, additive regression, and decision stump | Presents a comparison between the violent crime patterns from the Communities and Crime Dataset provided by the University of California—Irvine repository and actual crime statistical data for the state of Mississippi that were provided by neighborhoodscout.com | Linear regression performs the best |
| [66] | RF | Long-term crime forecasts for robberies in Dallas in 200 by 200 foot grid cells that allow spatially varying associations of crime generators and demographic factors | RF outperforms risk terrain models and kernel density estimation in terms of forecasting future crimes using different measures of predictive accuracy, but it only slightly outperforms using prior counts of crime |
| [67] | SVM, KDE, deep neural network (DNN) | Introduces a feature-level data fusion method with environmental context based on a deep neural network that consists of spatial, temporal, environmental context, and joint feature representation layers | Evaluated the performance of SVM, KDE, and their proposed method using accuracy, precision, recall, and area under the curve (AUC). Their DNN-based multimodal data fusion method is a more appropriate method for predicting crime occurrence. The limitation of this model is that it will not work when sufficient data are not provided |
| [68] | Simple logistic, LR, NB, Bayes net, SVM, DT with C4.5, MLP | Examines the machine learning algorithms and data mining tools in crime analysis in the process of crime prediction and prevention | DT showed promising results, with an accuracy rate of 76% |
| [69] | Feedforward network, CNN, RNN, recurrent convolutional network | Uses neural network techniques and combines RNN and CNN to predict crime types on different datasets | Evaluated the performance of neural networks, with the following results: feedforward with 71.3% accuracy, CNN with 72.7%, and RNN with 74.1%, and the combination of CNN and RNN with 75.6%. |
| [70] | Apriori, NB, DT | Applied Apriori to detect frequent crime patterns and NB, and DT to predict the potential crime types | Achieved a prediction accuracy rate of 51% on Denver’s crime dataset and 54% on Los Angeles’ dataset, and provided an analysis study based on the results for each city |
| [71] | SVM, NB, KNN | The authors apply ML algorithms to identify hate speech in the context of spiritual belief, emphasizing the importance of monitoring cybercrimes | SVM outperforms NB and KNN in terms of F-score, precision, and recall for sentiment classification and religion classification |
| [72] | DNN, CNN, RNN | Proposes an intelligent unmanned aerial vehicle system that relies on deep learning algorithms to analyze video data and detect suspicious criminal activities | No performance evaluation is provided; some improvements are suggested for future work, such as battery power and using surveillance-specific algorithms |
| Reference | Dataset | No. of Instances | No. of Attributes | Algorithm/Technique | Accuracy (%) |
|---|---|---|---|---|---|
| [52] | Los Angeles criminal records (2010–2018) [96] | 2.6 million | 17 | Logistic regression DT RF MLP NB SVM XGBOOST KNN | 48 60 43 84 71 60 88 89 |
| [52] | Chicago criminal records (2001–November 2019) through the city of Chicago’s data portal website [97] | 7 million | 22 | Logistic regression DT RF MLP NB SVM XGBOOST KNN | 90 66 77 87 73 66 94 88 |
| [55] | Communities and Crime from the UCI Machine Learning Repository [98]: Group 1, which is classified based on race | 2000 | 128 in total, but only 4 were selected for this study to obtain optimal results | NB BP | 90.22 94.08 |
| [55] | Communities and Crime from the UCI Machine Learning Repository [98]: Group 2, which is classified based on marital status | 2000 | 128 in total, but only 4 were selected for this study to obtain optimal results | NB BP | 65.94 65.94 |
| [57] | Chicago crime records through the city of Chicago’s data portal website [97] | 6,480,461 | - | SVM KDE Deep neural network LFSNBC | 67.01 66.33 84.25 97.47 |
| [59] | Data1978 | 4618 (9327 in total, but 4709 instances were excluded due to missing information) | - | LR SVM Neural network | - |
| [59] | Data1980 | 5739 (9549 in total, but 3810 instances were excluded due to missing information) | - | LR SVM Neural network | - |
| [60] | Communities and Crime from the UCI Machine Learning Repository [98] | 1994 | 128 | DT NB | 83.9519 70.8124 |
| [61] | Communities and Crime from the UCI Machine Learning Repository [98] | 1994 | 128 | DT J48 NB MLP SVM | 100 89.6104 100 92.2078 |
| [62] | Communities and Crime from the UCI Machine Learning Repository [98] | 1994 | 12 | DT J48 | 94.2528 |
| [63] | Chicago incident reports from 2013 to 2017 [99] | 12,109 | 18 | NB DT | 83.33 91.59 |
| [65] | Communities and Crime Unnormalized Dataset | 2215 | 147 in total (4 non-predictive features, 125 predictive features, and 18 potential goal features), but 9 attributes related to violent crimes were selected for this study | Linear regressionAdditive regressionDecision stump | Not defined |
| [65] | Mississippi 2013 Crime Dataset [100] | 89,714 recorded crimes, but 8214 records were selected for this study | - | Linear regressionAdditive regressionDecision stump | Not defined |
| [66] | Crime data related to robberies reported from incident-level data and geocoded to the address level on the Dallas Open Data portal [101] | 12,613 | - | RFKDECounting prior crimes Risk terrain modeling | - |
| [67] | Chicago crime records for 2014 through the city of Chicago’s data portal website [97], American Community Survey data, weather data from Weather Underground [102], and environmental context information from image data using Google Street View [103] | 274,064 crime cases from Chicago crime records, 801 census tracts from the American Community Survey | - | SVM KDE Deep neural network | 67.01 66.33 84.25 |
| [69] | Chicago crime records through the city of Chicago’s data portal website [97], along with census data through the United States Census Bureau and weather data through the National Oceanic and Atmospheric Administration | 6 million records | - | Feedforward CNN RNN RNN + CNN | 71.3 72.7 74.1 75.6 |
| [69] | Portland crime data through the National Institution of Justice Real-Time Crime Forecasting, along with census data through the United States Census Bureau and weather data through the National Oceanic and Atmospheric Administration | - | - | Feedforward CNN RNN RNN + CNN | 62.2 62.9 63.8 65.3 |
| [70] | Denver crimes dataset (2010–2015) [104] | 333,068 | 19 | NB DT | 51 42 |
| [70] | Los Angeles crimes dataset (96% for 2014 and 4% for before 2014) [105] | 243,750 | 14 | NB DT | 54 43 |
4.1.3. Natural Language Processing
| Reference | Data Source(s) | Description | Result |
|---|---|---|---|
| [115] | Text analysis and classification using the WEKA toolkit and SVM | ||
| [116] | Twitter data in addition to 290 incident records collected from local law enforcement agencies in Charlottesville, Virginia | Explores Twitter-based prediction of criminal incidents, with a focus on hit-and-run crimes, using NLP techniques such as sentiment analysis and event extraction. A linear regression model is also used to predict if a crime will occur in the following days based on information extracted from the tweets | The model’s performance was evaluated using a receiver operating characteristic (ROC) curve. The results indicated that date from social media platforms such as Twitter could be a valuable resource for predicting criminal incidents, but there are areas for improvement and further research, especially considering the temporal aspect of event descriptions and feature selection methods |
| [118] | Portuguese narrative police reports | Presents a system that uses information retrieval techniques to extract, transform, clean, load, and find a connection between police reports collected from different sources to identify relevant entities within the extracted information | The proposed model outperformed Linguakit and RAPPORT in terms of the F-score |
| [119] | Mozenda Web Screen Scrapper tool and 4 online newspapers: Otago Daily Times, Zealand Herald, Sydney Morning Herald, and The Hindu | Proposed a crime information extraction system using NER and a conditional random fields (CRF) machine learning approach to identify locations in sentences and classify them based on online newspapers by focusing on information related to the theft crime | The model was evaluated based on four newspaper articles from three countries, resulting in accuracy of 84% to 90% for articles from New Zealand and 73% to 75% for articles from India and Australia |
| [120] | Malaysian newspapers and social media sites | Introduced an ensemble framework for crime information extraction from the web using NER and classification algorithms including NB, SVM, and KNN, along with a weighted voting ensemble method to combine them | The proposed model outperformed the baseline models, with an F-score of 89.48% for identifying crime types and 93.36% for extracting crime-related entities |
| [121] | News articles related to identity theft on the internet found by search engines and annual identity theft reports | Proposed an approach to analyze criminal behaviors and predict future trends of identity theft and fraud using NLP methods and information extraction, including NER and part-of-speech tagging based on raw text from news articles on the web. The Identity Threat Assessment and Prediction (ITAP) algorithm, designed in a modular pipeline, collects news stories, preprocesses them, extracts named entities, categorizes them, and creates identity theft records | Around 3500 identity theft news stories were collected, their text was cleaned, and named entities were extracted and categorized. These categories formed identity theft records, which were then used for various analyses, such as identifying affected groups, assessing risk for specific PII attributes, tracking occurrence frequency across different sectors and locations, evaluating potential financial impacts, and tracking changes over time |
| [122] | A set of crime reports related to internet fraud on the official website of the Dutch police (each report contains 1–5 sentences and 85 tokens on average) | Evaluates the standard NER algorithm, named Frog, for the Dutch language based on a manually annotated corpus collected from 250 complaints reports from the Dutch police; it discusses confusion in entity type assignment and recall errors, and proposes ways to improve performance | The current Dutch NER algorithm performs inadequately on unedited free-entry data. The significance of this depends on the purpose of entity recognition, e.g., law enforcement seeks relevant information, while linguistics aims for named-entity identification, so different types and assignments matter, and domain-specific roles demand further processing |
| [123] | - | Proposed a method for extracting valuable information about suspects’ hard drives and social networks to discover criminal communities and analyze their relations | The method efficiently identified criminal communities and their interlinked subgroups, offering a detailed view of network structure, crucial for criminal network analysis; it also received positive feedback from a Canadian law enforcement unit’s digital forensics team |
| [117] | A set of police narrative reports provided from the Phoenix Police Department database | Presents a neural-network-based entity extractor by using NER techniques to detect valuable entities such as person names, addresses, narcotic drugs, and vehicle names in police reports | The system achieved promising precision and recall rates for person names and narcotic drugs but performed less effectively for addresses and personal properties |
| [124] | Texts on the web | Proposed a semantic NLP model to develop systems that extract crime information from unstructured text in a collaborative web environment. The framework centers around a semantic inferential model (SIM)-based NLP module | This framework’s performance was demonstrated through the creation of “WikiCrimesIE,” a tool for extracting crime-related information from text on the web, which gained an F-score of 78% for crime extraction and 70% for crime type identification |
| [125] | Chinese criminal investigation notes, online news on the internet, and litigation data | Introduces a method for criminal information analysis and relation visualization by utilizing entity extraction techniques and part-of-speech (POS) tagging based on Chinese criminal text | By forming term networks based on documents from sources like criminal investigation notes, news, and litigation data, this method enhances the visualization of detailed information and hidden relationships, enabling efficient exploration of potential criminal activities |
| [126] | 65 Arabic crime articles with a total of 13,300 words | Introduces a rule-based NER to identify and classify named entities in Arabic crime text as it applies syntactical rules such as sentence splitting, tokenization, and POS tagging | The system achieved 90% accuracy, showing effectiveness and satisfactory performance. The paper outlines plans to integrate the rule-based system with machine learning techniques and embed it within a crime analysis framework |
| [127] | Crime news articles represented in html format collected from the Malaysian National News Agency (BERNAMA | Introduces a method to extract information on nationalities from crime news in Malaysia by applying NER using gazetteers and rule-based extraction. The system is composed of three modules: direct extraction, indirect extraction, and victim–suspect reference identification | The method’s performance was evaluated based on a manual extraction system and showed an F-score of 70%. The authors also highlighted challenges with punctuation and nationality indicators causing the system to miss certain references or extract incorrectly, as well as difficulties in identifying implicit state markers for victims or suspects |
| [128] | Crime news from online sources and crime records for 2001 to 2014 provided by the National Crime Records Bureau | Presents an Android application called Reach 360, designed to offer alerts and support in dangerous situations, including features such as alerting contacts, demonstrating crime hotspots via heatmaps, and forecasting crimes based on crime news using machine learning. NLP tasks such as sentence segmentation, word tokenization, POS, and NER are used to process crime news | Multilayer perceptron performed better than logistic regression and RF in terms of accuracy for crime forecasting. The study does not provide other specific details on the performance evaluation of their application; it mainly focuses on introducing its features, the methodology behind it, and its potential to address safety concerns and forecast crimes |
| [129] | Official data of crime records from Porto’s Public Security Police between January 2016 and December 2018 | Explores the application of mapping techniques, NLP, and ML models such as SVM, LR, DT, and RF to analyze crime patterns and predict crimes. The study collected tweets related to insecurity around crime locations and performed topic modeling and sentiment analysis. Latent Dirichlet allocation (LDA) was also used to classify tweets into topics, while sentiment analysis identified positive and negative sentiments related to crime | This method identified crime patterns and crime hotspots in downtown Porto and emphasized the importance of crime trend forecasting for resource allocation. The study does not provide details on the evaluation of the used models |
| [130] | Patch Hate Crime dataset, New York Times news reports | Introduces a framework to address the problem of hate speech on social media and its connection to hate crime with a combination of event extraction through NLP, time-series analysis, and regression analysis. The event-related factors extracted using event extraction are integrated into a regression model. These factors, along with other predictive features, are used to predict hate crime trends | Various models were applied to forecast hate crime trends, and the results were compared. Regressive models outperformed the ARIMA model, with models including event-related variables performing better |
| [131] | Twitter posts by users in the United Kingdom between October 2015 and October 2016 | Presents a comprehensive study of online antagonistic content on Twitter that involved data collection from Twitter | The authors developed a supervised machine learning classifier with a bag-of-words model to identify antisemitic content, providing an analysis of the production and propagation of antagonistic content |
| [132] | A corpus of two million downloaded tweets | Introduces an intelligent system used by the Spanish National Office Against Hate Crimes to identify and monitor hate speech on Twitter. The system makes use of NLP methods including lemmatization, stop-word removal, and POS tagging for preprocessing tweets, and then classifies them using MLP and LSTM | The authors evaluated 19 different strategies, each comprising various combinations of features and classification models. Ultimately, the top-performing model, achieving an AUC of 0.828, leveraged word embeddings, emojis, and token expressions and further enhanced them through text frequency–inverse document frequency. This approach outperformed the existing models in the literature. |
| [71] | Twitter posts | Applies ML algorithms to Twitter posts for text classification and sentiment analysis to analyze hate speech and hateful sentiment in the context of spiritual belief | SVM outperformed NB and KNN in terms of F-score, precision, and recall for sentiment classification and religion classification |
4.2. Addressing RQ2
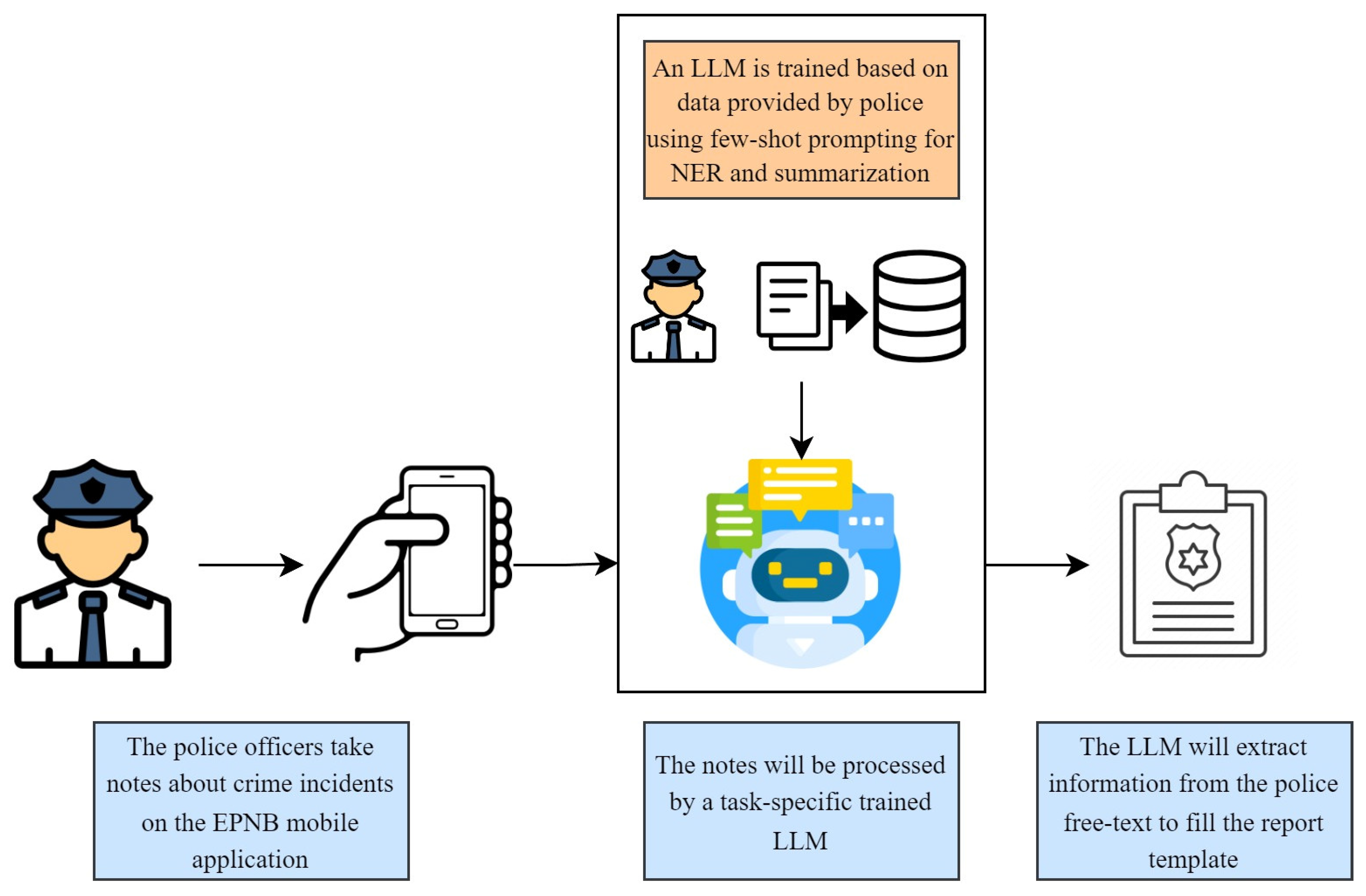
5. Next-Generation Smart Policing
- For example:
- [{
- “criminal name”: “Value1”,
- “criminal age”: “Value2”,
- “location”: “Value3”,
- # ...
- }]
- If any of this information is not defined in the report just leave it blank. You also need to summarize the narrative report and put it into “summary” in the same JSON format file.”
6. Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Camacho-Collados, M.; Liberatore, F. A decision support system for predictive police patrolling. Decis. Support Syst. 2015, 75, 25–37. [Google Scholar] [CrossRef]
- Gable Cino, J. Deploying the secret police: The use of algorithms in the criminal justice system. Ga. Stet Univ. Law Rev. 2018, 34, 1073. [Google Scholar]
- Mehrabi, N.; Morstatter, F.; Saxena, N.; Lerman, K.; Galstyan, A. A survey on bias and fairness in machine learning. ACM Comput. Surv. (CSUR) 2021, 54, 1–35. [Google Scholar] [CrossRef]
- Ferguson, A.G. Predictive policing and reasonable suspicion. Emory LJ 2012, 62, 259. [Google Scholar] [CrossRef]
- Page, M.J.; Moher, D.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. PRISMA 2020 explanation and elaboration: Updated guidance and exemplars for reporting systematic reviews. BMJ 2021, 372, n160. [Google Scholar] [CrossRef] [PubMed]
- Saravanan, P.; Selvaprabu, J.; Arun Raj, L.; Abdul Azeez Khan, A.; Javubar Sathick, K. Survey on crime analysis and prediction using data mining and machine learning techniques. In Advances in Smart Grid Technology: Select Proceedings of PECCON 2019—Volume II; Springer: Singapore, 2021; pp. 435–448. [Google Scholar]
- Carnaz, G.; Quaresma, P.; Beires Nogueira, V.; Antunes, M.; Fonseca Ferreira, N.N. A review on relations extraction in police reports. New Knowl. Inf. Syst. Technol. 2019, 1, 494–503. [Google Scholar]
- Hassani, H.; Huang, X.; Silva, E.S.; Ghodsi, M. A review of data mining applications in crime. Stat. Anal. Data Min. ASA Data Sci. J. 2016, 9, 139–154. [Google Scholar] [CrossRef]
- Mandalapu, V.; Elluri, L.; Vyas, P.; Roy, N. Crime Prediction Using Machine Learning and Deep Learning: A Systematic Review and Future Directions. IEEE Access 2023, 11, 60153–60170. [Google Scholar] [CrossRef]
- Nicholls, J.; Kuppa, A.; Le-Khac, N.-A. Financial cybercrime: A comprehensive survey of deep learning approaches to tackle the evolving financial crime landscape. IEEE Access 2021, 9, 163965–163986. [Google Scholar] [CrossRef]
- Thomas, A.; Sobhana, N. A survey on crime analysis and prediction. Mater. Today Proc. 2022, 58, 310–315. [Google Scholar] [CrossRef]
- Maliphol, S.; Hamilton, C. Smart Policing: Ethical Issues & Technology Management of Robocops. In Proceedings of the 2022 Portland International Conference on Management of Engineering and Technology (PICMET), Portland, OR, USA, 7–11 August 2022; pp. 1–15. [Google Scholar]
- Raaijmakers, S. Artificial intelligence for law enforcement: Challenges and opportunities. IEEE Secur. Priv. 2019, 17, 74–77. [Google Scholar] [CrossRef]
- Baek, M.-S.; Park, W.; Park, J.; Jang, K.-H.; Lee, Y.-T. Smart policing technique with crime type and risk score prediction based on machine learning for early awareness of risk situation. IEEE Access 2021, 9, 131906–131915. [Google Scholar] [CrossRef]
- Elluri, L.; Mandalapu, V.; Roy, N. Developing machine learning based predictive models for smart policing. In Proceedings of the 2019 IEEE International Conference on Smart Computing (SMARTCOMP), Washington, DC, USA, 12–15 June 2019; pp. 198–204. [Google Scholar]
- Joh, E.E. Artificial intelligence and policing: First questions. Seattle UL Rev. 2017, 41, 1139. [Google Scholar]
- Yang, F. Predictive policing. In Oxford Research Encyclopedia of Criminology and Criminal Justice; Oxford University Press: Oxford, UK, 2019. [Google Scholar]
- Matsueda, R.L.; Kreager, D.A.; Huizinga, D. Deterring delinquents: A rational choice model of theft and violence. Am. Sociol. Rev. 2006, 71, 95–122. [Google Scholar] [CrossRef]
- Brayne, S.; Rosenblat, A.; Boyd, D. Predictive Policing. Data Civ. Rights New Era Polic. Justice 2015. Available online: https://datacivilrights.org/pubs/2015-1027/Predictive_Policing.pdf (accessed on 1 October 2023).
- Willis, J.J.; Mastrofski, S.D.; Weisburd, D. Making sense of COMPSTAT: A theory-based analysis of organizational change in three police departments. Law Soc. Rev. 2007, 41, 147–188. [Google Scholar] [CrossRef]
- Cardon, D. Deconstructing the Algorithm: Four Types of Digital Information Calculations; Routledge: London, UK, 2016. [Google Scholar]
- Dourish, P. Algorithms and their others: Algorithmic culture in context. Big Data Soc. 2016, 3, 2053951716665128. [Google Scholar] [CrossRef]
- Kitchenham, B.; Brereton, O.P.; Budgen, D.; Turner, M.; Bailey, J.; Linkman, S. Systematic literature reviews in software engineering—A systematic literature review. Inf. Softw. Technol. 2009, 51, 7–15. [Google Scholar] [CrossRef]
- Rajaei, M.J.; Mahmoud, Q.H. A Survey on Pump and Dump Detection in the Cryptocurrency Market Using Machine Learning. Future Internet 2023, 15, 267. [Google Scholar] [CrossRef]
- Bertovskiy, L.V.; Novogonskaya, M.S.; Fedorov, A.R. Predictive Policing: High-tech Modeling as a Method to Identify Serial Killers. Kutafin Law Rev. 2022, 9, 329–342. [Google Scholar] [CrossRef]
- Shapiro, A. Reform predictive policing. Nature 2017, 541, 458–460. [Google Scholar] [CrossRef]
- Chainey, S.; Tompson, L.; Uhlig, S. The utility of hotspot mapping for predicting spatial patterns of crime. Secur. J. 2008, 21, 4–28. [Google Scholar] [CrossRef]
- Block, R.; Perry, S. STAC News. Ill. Crim. Justice 1993, 1, 4–28. [Google Scholar]
- Eck, J.; Chainey, S.; Cameron, J.; Wilson, R. Mapping Crime: Understanding Hotspots; National Institute of Justice: Washington, DC, USA, 2005. [Google Scholar]
- Ratcliffe, J.; McCullagh, M. Crime, repeat victimisation and GIS. Mapp. Anal. Crime Data 2001, 61–92. [Google Scholar] [CrossRef]
- Williamson, D.; McLafferty, S.; McGuire, P.; Ross, T.; Mollenkopf, J.; Goldsmith, V.; Quinn, S. Tools in the spatial analysis of crime. Mapping and analysing crime data. A. Hirschfield K. Bowers. Lond. New York Taylor Fr. 2001, 1, 187. [Google Scholar]
- Rosenblatt, M. Remarks on some nonparametric estimates of a density function. Ann. Math. Stat. 1956, 1, 832–837. [Google Scholar] [CrossRef]
- de Queiroz Neto, J.F.; dos Santos, E.M.; Vidal, C.A. Mskde-using marching squares to quickly make high quality crime hotspot maps. In Proceedings of the 29th SIBGRAPI Conference on Graphics, Patterns and Images (SIBGRAPI), Sao Paulo, Brazil, 4–7 October 2016; pp. 305–312. [Google Scholar]
- Benbouzid, B. Values and Consequences in Predictive Machine Evaluation. A Sociology of Predictive Policing. Sci. Technol. Stud. 2018, 31. Available online: https://ssrn.com/abstract=3123315 (accessed on 1 October 2023).
- Mohler, G.; Short, M.; Brantingham, P.; Schoenberg, F.; Tita, G. Self-Exciting Point Process Modeling of Crime. J. Am. Stat. Assoc. 2011, 106, 100–108. [Google Scholar] [CrossRef]
- PredPol. The Science & Testing of Predictive Policing, The Predictive Policing Company. Available online: https://cdn2.hubspot.net/hubfs/3362003/White%20Paper%20Science%20&%20Testing%20of%20Predictive%20Policing.pdf (accessed on 5 December 2023).
- Eterno, J.A.; Silverman, E.B. The New York City police department’s Compstat: Dream or nightmare? Int. J. Police Sci. Manag. 2006, 8, 218–231. [Google Scholar] [CrossRef]
- Azavea. HunchLab: Under the Hood. 2015. Available online: https://blog.pilpul.me/files/2015/09/HunchLab-Under-the-Hood.pdf, (accessed on 5 December 2023).
- Barrett, L. Reasonably suspicious algorithms: Predictive policing at the United States border. NYU Rev. L. Soc. Chang. 2017, 41, 327. [Google Scholar]
- Ferguson, A.G. Policing predictive policing. Wash. UL Rev. 2016, 94, 1109. [Google Scholar]
- Saunders, J.; Hunt, P.; Hollywood, J.S. Predictions put into practice: A quasi-experimental evaluation of Chicago’s predictive policing pilot. J. Exp. Criminol. 2016, 12, 347–371. [Google Scholar] [CrossRef]
- Hoggard, C. Fresno Police Scanning Social Media to Asses Threat. abc30 Action News. 2015. Available online: https://abc30.com/fresno-police-social-media-big-brother-software/525999/ (accessed on 5 December 2023).
- Robinson, D. Buyer Beware: A Hard Look at Police ‘Threat Scores’. 2016. Available online: https://medium.com/equal-future/buyer-beware-a-hard-look-at-police-threat-scores-961f73b88b10/ (accessed on 5 December 2023).
- Levine, E.S.; Tisch, J.; Tasso, A.; Joy, M. The New York City police department’s domain awareness system. Interfaces 2017, 47, 70–84. [Google Scholar] [CrossRef]
- Saeed, U.; Sarim, M.; Usmani, A.; Mukhtar, A.; Shaikh, A.B.; Raffat, S.K. Application of machine learning algorithms in crime classification and classification rule mining. Res. J. Recent Sci. ISSN 2015, 2277, 2502. [Google Scholar]
- Chen, H.; Schroeder, J.; Hauck, R.V.; Ridgeway, L.; Atabakhsh, H.; Gupta, H.; Boarman, C.; Rasmussen, K.; Clements, A.W. COPLINK Connect: Information and knowledge management for law enforcement. Decis. Support Syst. 2003, 34, 271–285. [Google Scholar] [CrossRef]
- Egbert, S. Predictive policing and the platformization of police work. Surveill. Soc. 2019, 17, 83–88. [Google Scholar] [CrossRef]
- De’ath, G.; Fabricius, K.E. Classification and regression trees: A powerful yet simple technique for ecological data analysis. Ecology 2000, 81, 3178–3192. [Google Scholar] [CrossRef]
- Breiman, L. Random forests. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef]
- Nath, S.V. Crime pattern detection using data mining. In Proceedings of the 2006 IEEE/WIC/ACM International Conference on Web Intelligence and Intelligent Agent Technology Workshops, Hong Kong, China, 18–22 December 2006; pp. 41–44. [Google Scholar]
- Zhang, X.; Liu, L.; Xiao, L.; Ji, J. Comparison of machine learning algorithms for predicting crime hotspots. IEEE Access 2020, 8, 181302–181310. [Google Scholar] [CrossRef]
- Safat, W.; Asghar, S.; Gillani, S.A. Empirical analysis for crime prediction and forecasting using machine learning and deep learning techniques. IEEE Access 2021, 9, 70080–70094. [Google Scholar] [CrossRef]
- Chen, P.; Yuan, H.; Shu, X. Forecasting crime using the arima model. In Proceedings of the 2008 Fifth International Conference on Fuzzy Systems and Knowledge Discovery, Jinan, China, 18–20 October 2008; pp. 627–630. [Google Scholar]
- Khan, J.R.; Saeed, M.; Siddiqui, F.A.; Mahmood, N.; Arifeen, Q.U. PREDICTIVE POLICING: A Machine Learning Approach to Predict and Control Crimes in Metropolitan Cities. Univ. Sindh J. Inf. Commun. Technol. 2019, 3, 17–26. [Google Scholar]
- Babakura, A.; Sulaiman, M.N.; Yusuf, M.A. Improved method of classification algorithms for crime prediction. In Proceedings of the 2014 International Symposium on Biometrics and Security Technologies (ISBAST), Kuala Lumpur, Malaysia, 26–27 August 2014; pp. 250–255. [Google Scholar]
- Zhang, Q.; Yuan, P.; Zhou, Q.; Yang, Z. Mixed spatial-temporal characteristics based crime hot spots prediction. In Proceedings of the 2016 IEEE 20th International Conference on Computer Supported Cooperative Work in Design (CSCWD), Nanchang, China, 4–6 May 2016; pp. 97–101. [Google Scholar]
- Nitta, G.R.; Rao, B.Y.; Sravani, T.; Ramakrishiah, N.; Balaanand, M. LASSO-based feature selection and naïve Bayes classifier for crime prediction and its type. Serv. Oriented Comput. Appl. 2019, 13, 187–197. [Google Scholar] [CrossRef]
- Shingleton, J.S. Crime Trend Prediction Using Regression Models for Salinas, California; Naval Postgraduate School: Monterey, CA, USA, 2012. [Google Scholar]
- Wang, P.; Mathieu, R.; Ke, J.; Cai, H. Predicting criminal recidivism with support vector machine. In Proceedings of the 2010 International Conference on Management and Service Science, Wuhan, China, 24–26 August 2010; pp. 1–9. [Google Scholar]
- Iqbal, R.; Murad, M.A.A.; Mustapha, A.; Panahy, P.H.S.; Khanahmadliravi, N. An Experimental Study of Classification Algorithms for Crime Prediction. Indian J. Sci. Technol. 2013, 6, 1–7. [Google Scholar] [CrossRef]
- Ivan, N.; Ahishakiye, E.; Omulo, E.O.; Wario, R. A performance analysis of business intelligence techniques on crime prediction. Int. J. Comput. Inf. Technol. 2017, 4, 84–90. [Google Scholar]
- Ahishakiye, E.; Taremwa, D.; Omulo, E.O.; Niyonzima, I. Crime prediction using decision tree (J48) classification algorithm. Int. J. Comput. Inf. Technol. 2017, 6, 188–195. [Google Scholar]
- Aldossari, B.S.; Alqahtani, F.M.; Alshahrani, N.S.; Alhammam, M.M.; Alzamanan, R.M.; Aslam, N.; Irfanullah. A Comparative Study of Decision Tree and Naive Bayes Machine Learning Model for Crime Category Prediction in Chicago. In Proceedings of the 2020 6th International Conference on Computing and Data Engineering, Sanya, China, 4–6 January 2020; pp. 34–38. [Google Scholar]
- Lin, Y.-L.; Chen, T.-Y.; Yu, L.-C. Using machine learning to assist crime prevention. In Proceedings of the 2017 6th IIAI International Congress on Advanced Applied Informatics (IIAI-AAI), Hamamatsu, Japan, 9–13 July 2017; pp. 1029–1030. [Google Scholar]
- McClendon, L.; Meghanathan, N. Using machine learning algorithms to analyze crime data. Mach. Learn. Appl. Int. J. (MLAIJ) 2015, 2, 1–12. [Google Scholar] [CrossRef]
- Wheeler, A.P.; Steenbeek, W. Mapping the risk terrain for crime using machine learning. J. Quant. Criminol. 2021, 37, 445–480. [Google Scholar] [CrossRef]
- Kang, H.-W.; Kang, H.-B. Prediction of crime occurrence from multi-modal data using deep learning. PLoS ONE 2017, 12, 176–244. [Google Scholar] [CrossRef]
- Llaha, O. Crime analysis and prediction using machine learning. In Proceedings of the 43rd International Convention on Information, Communication and Electronic Technology (MIPRO), Opatija, Croatia, 28 September–2 October 2020; pp. 496–501. [Google Scholar]
- Stec, A.; Klabjan, D. Forecasting crime with deep learning. arXiv 2018, arXiv:1806.01486. [Google Scholar]
- Almanie, T.; Mirza, R.; Lor, E. Crime prediction based on crime types and using spatial and temporal criminal hotspots. arXiv 2015, arXiv:1508.02050. [Google Scholar] [CrossRef]
- Zia, T.a.A.; Shehbaz, M.; Nawaz, M.S.; Shahzad, B.; Abdullatif, A.; Mustafa, R.; Lali, M.I. Identification of hatred speeches on Twitter. In Proceedings of the 52nd The IRES International Conference, Kuala Lumpur, Malaysia, 5–6 November 2016; pp. 27–32. [Google Scholar]
- Gayathri, M.; Meghana, M.; Trivedh, M.; Manju, D. Suspicious Activity Detection and Tracking through Unmanned Aerial Vehicle Using Deep Learning Techniques. Int. J. Adv. Trends Comput. Sci. Eng. 2020, 9, 2812–2816. [Google Scholar] [CrossRef]
- Stalidis, P.; Semertzidis, T.; Daras, P. Examining deep learning architectures for crime classification and prediction. Forecasting 2021, 3, 46. [Google Scholar] [CrossRef]
- Rajapakshe, C.; Balasooriya, S.; Dayarathna, H.; Ranaweera, N.; Walgampaya, N.; Pemadasa, N. Using cnns rnns and machine learning algorithms for real-time crime prediction. In Proceedings of the 2019 International Conference on Advancements in Computing (ICAC), Malabe, Sri Lanka, 5–7 December 2019; pp. 310–316. [Google Scholar]
- Wang, B.; Yin, P.; Bertozzi, A.L.; Brantingham, P.J.; Osher, S.J.; Xin, J. Deep learning for real-time crime forecasting and its ternarization. Chin. Ann. Math. Ser. B 2019, 40, 949–966. [Google Scholar] [CrossRef]
- Berk, R.A. Artificial intelligence, predictive policing, and risk assessment for law enforcement. Annu. Rev. Criminol. 2021, 4, 209–237. [Google Scholar] [CrossRef]
- Singh, A.; Anand, T.; Sharma, S.; Singh, P. IoT based weapons detection system for surveillance and security using YOLOV4. In Proceedings of the 2021 6th International Conference on Communication and Electronics Systems (ICCES), Coimbatre, India, 8–10 July 2021; pp. 488–493. [Google Scholar]
- Velastin, S.A.; Boghossian, B.A.; Vicencio-Silva, M.A. A motion-based image processing system for detecting potentially dangerous situations in underground railway stations. Transp. Res. Part C Emerg. Technol. 2006, 14, 96–113. [Google Scholar] [CrossRef]
- Bhatti, M.T.; Khan, M.G.; Aslam, M.; Fiaz, M.J. Weapon detection in real-time cctv videos using deep learning. IEEE Access 2021, 9, 34366–34382. [Google Scholar] [CrossRef]
- Ahmed, S.; Bhatti, M.T.; Khan, M.G.; Lövström, B.; Shahid, M. Development and optimization of deep learning models for weapon detection in surveillance videos. Appl. Sci. 2022, 12, 5772. [Google Scholar] [CrossRef]
- Kaya, V.; Tuncer, S.; Baran, A. Detection and classification of different weapon types using deep learning. Appl. Sci. 2021, 11, 7535. [Google Scholar] [CrossRef]
- Ruiz-Santaquiteria, J.; Velasco-Mata, A.; Vallez, N.; Bueno, G.; Alvarez-Garcia, J.A.; Deniz, O. Handgun detection using combined human pose and weapon appearance. IEEE Access 2021, 9, 123815–123826. [Google Scholar] [CrossRef]
- Hashmi, T.S.S.; Haq, N.U.; Fraz, M.M.; Shahzad, M. Application of deep learning for weapons detection in surveillance videos. In Proceedings of the 2021 International Conference on Digital Futures and Transformative Technologies (ICoDT2), Islamabad, Pakistan, 20–21 May 2021; pp. 1–6. [Google Scholar]
- Narejo, S.; Pandey, B.; Esenarro Vargas, D.; Rodriguez, C.; Anjum, M.R. Weapon detection using YOLO V3 for smart surveillance system. Math. Probl. Eng. 2021, 2021, 9975700. [Google Scholar] [CrossRef]
- Verma, G.K.; Dhillon, A. A handheld gun detection using faster r-cnn deep learning. In Proceedings of the 7th International Conference on Computer and Communication Technology, Nagpur, India, 11–13 November 2017; pp. 84–88. [Google Scholar]
- Ingle, P.Y.; Kim, Y.-G. Real-time abnormal object detection for video surveillance in smart cities. Sensors 2022, 22, 3862. [Google Scholar] [CrossRef] [PubMed]
- Velasco-Mata, A.; Ruiz-Santaquiteria, J.; Vallez, N.; Deniz, O. Using human pose information for handgun detection. Neural Comput. Appl. 2021, 33, 17273–17286. [Google Scholar] [CrossRef]
- Simonyan, K.; Zisserman, A. Very deep convolutional networks for large-scale image recognition In: Proceedings of International Conference on Learning Representations. arXiv 2015, arXiv:1409.1556. [Google Scholar]
- Redmon, J.; Divvala, S.; Girshick, R.; Farhadi, A. You only look once: Unified, real-time object detection. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Las Vegas, NV, USA, 27–30 June 2016; pp. 779–788. [Google Scholar]
- Redmon, J.; Farhadi, A. YOLO9000: Better, faster, stronger. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Honolulu, HI, USA, 21–26 July 2017; pp. 7263–7271. [Google Scholar]
- Redmon, J.; Farhadi, A. Yolov3: An incremental improvement. arXiv 2018, arXiv:1804.02767. [Google Scholar]
- Bochkovskiy, A.; Wang, C.-Y.; Liao, H.-Y.M. Yolov4: Optimal speed and accuracy of object detection. arXiv 2020, arXiv:2004.10934. [Google Scholar]
- Sajjad, M.; Nasir, M.; Muhammad, K.; Khan, S.; Jan, Z.; Sangaiah, A.K.; Elhoseny, M.; Baik, S.W. Raspberry Pi assisted face recognition framework for enhanced law-enforcement services in smart cities. Future Gener. Comput. Syst. 2020, 108, 995–1007. [Google Scholar] [CrossRef]
- Sermanet, P.; Eigen, D.; Zhang, X.; Mathieu, M.; Fergus, R.; LeCun, Y. Overfeat: Integrated recognition, localization and detection using convolutional networks. arXiv 2013, arXiv:1312.6229. [Google Scholar]
- Zhang, H.; Berg, A.C.; Maire, M.; Malik, J. SVM-KNN: Discriminative nearest neighbor classification for visual category recognition. In Proceedings of the 2006 IEEE Computer Society Conference on Computer Vision and Pattern Recognition (CVPR’06), New York, NY, USA, 17–22 June 2006; pp. 2126–2136. [Google Scholar]
- County of Los Angeles Enterprise GIS. Available online: https://egis-lacounty.hub.arcgis.com/ (accessed on 27 September 2023).
- Chicago Data Portal. Available online: https://data.cityofchicago.org/stories/s/5cd6-ry5g (accessed on 26 September 2023).
- Communities and Crime. Available online: https://archive.ics.uci.edu/dataset/183/communities+and+crime (accessed on 27 September 2023).
- Chicago Crime. Available online: https://www.kaggle.com/datasets/chicago/chicago-crime (accessed on 26 September 2023).
- Mississippi Crime Rates and Statistics—NeighborhoodScout. Available online: https://www.neighborhoodscout.com/ms/crime (accessed on 27 September 2023).
- City of Dallas Open Data. Available online: https://www.dallasopendata.com/ (accessed on 27 September 2023).
- Weather Underground. Available online: https://www.wunderground.com/ (accessed on 27 September 2023).
- Google. Google Street View. Available online: https://developers.google.com/maps/documentation/streetview/ (accessed on 27 September 2023).
- Data.denvergov.org. Denver Open Data Catalog: Crime. Available online: https://denvergov.org/opendata (accessed on 27 September 2023).
- US City Open Data Census—Datasets. Available online: https://us-cities.survey.okfn.org/ (accessed on 27 September 2023).
- Dixon, A.; Birks, D. Improving policing with natural language processing. In Proceedings of the 1st Workshop on NLP for Positive Impact, Online, 5 August 2021; pp. 115–124. [Google Scholar]
- Chowdhary, K.; Chowdhary, K.R. Natural language processing. Fundam. Artif. Intell. 2020, 603–649. [Google Scholar]
- Campedelli, G.M. Where are we? Using Scopus to map the literature at the intersection between artificial intelligence and research on crime. J. Comput. Soc. Sci. 2021, 4, 503–530. [Google Scholar] [CrossRef]
- Birks, D.; Coleman, A.; Jackson, D. Unsupervised identification of crime problems from police free-text data. Crime Sci. 2020, 9, 18. [Google Scholar] [CrossRef]
- Kuang, D.; Brantingham, P.J.; Bertozzi, A.L. Crime topic modeling. Crime Sci. 2017, 6, 12. [Google Scholar] [CrossRef]
- Basilio, M.P.; Brum, G.S.; Pereira, V. A model of policing strategy choice: The integration of the Latent Dirichlet Allocation (LDA) method with ELECTRE I. J. Model. Manag. 2020, 15, 849–891. [Google Scholar] [CrossRef]
- Basilio, M.P.; Pereira, V.; Brum, G. Identification of operational demand in law enforcement agencies: An application based on a probabilistic model of topics. Data Technol. Appl. 2019, 53, 333–372. [Google Scholar] [CrossRef]
- Karystianis, G.; Adily, A.; Schofield, P.; Knight, L.; Galdon, C.; Greenberg, D.; Jorm, L.; Nenadic, G.; Butler, T. Automatic extraction of mental health disorders from domestic violence police narratives: Text mining study. J. Med. Internet Res. 2018, 20, e11548. [Google Scholar] [CrossRef]
- Karystianis, G.; Adily, A.; Schofield, P.W.; Greenberg, D.; Jorm, L.; Nenadic, G.; Butler, T. Automated analysis of domestic violence police reports to explore abuse types and victim injuries: Text mining study. J. Med. Internet Res. 2019, 21, e13067. [Google Scholar] [CrossRef] [PubMed]
- Almehmadi, A.; Joudaki, Z.; Jalali, R. Language usage on Twitter predicts crime rates. In Proceedings of the 10th International Conference on Security of Information and Networks 2017, Hong Kong, China, 29 November–2 December 2017; pp. 307–310. [Google Scholar]
- Wang, X.; Gerber, M.S.; Brown, D.E. Automatic crime prediction using events extracted from twitter posts. In International Conference on Social Computing, Behavioral-Cultural Modeling, and Prediction; Springer: Berlin/Heidelberg, Germany, 2012; pp. 231–238. [Google Scholar]
- Chau, M.; Xu, J.J.; Chen, H. Extracting meaningful entities from police narrative reports. In the UA Campus Libraries at The University of Arizona. 2002. Available online: http://hdl.handle.net/10150/105786/ (accessed on 5 December 2023).
- Carnaz, G.; Beires Nogueira, V.; Antunes, M.; Ferreira, N. An automated system for criminal police reports analysis. In Tenth International Conference on Soft Computing and Pattern Recognition (SoCPaR 2018) 10; Springer International Publishing: Berlin/Heidelberg, Germany, 2020; pp. 360–369. [Google Scholar] [CrossRef]
- Arulanandam, R.; Savarimuthu, B.T.R.; Purvis, M. Extracting crime information from online newspaper articles. In Proceedings of the Second Australasian Web Conference, Auckland, New Zealand, 20–23 January 2014; pp. 31–38. [Google Scholar]
- Shabat, H.A.; Omar, N. Named entity recognition in crime news documents using classifiers combination. Middle-East J. Sci. Res. 2015, 23, 1215–1221. [Google Scholar]
- Yang, Y.; Manoharan, M.; Barber, K.S. Modelling and analysis of identity threat behaviors through text mining of identity theft stories. In Proceedings of the 2014 IEEE Joint Intelligence and Security Informatics Conference, The Hague, The Netherlands, 24–26 September 2014; pp. 184–191. [Google Scholar]
- Schraagen, M.; Brinkhuis, M.; Bex, F. Evaluation of Named Entity Recognition in Dutch online criminal complaints. Comput. Linguist. Neth. J. 2017, 7, 3–16. [Google Scholar]
- Al-Zaidy, R.; Fung, B.C.; Youssef, A.M. Towards discovering criminal communities from textual data. In Proceedings of Proceedings of the 2011 ACM Symposium on Applied Computing, TaiChung, Taiwan, 21–24 March 2011; pp. 172–177. [Google Scholar]
- Pinheiro, V.; Furtado, V.; Pequeno, T.; Nogueira, D. Natural language processing based on semantic inferentialism for extracting crime information from text. In Proceedings of the IEEE International Conference on Intelligence and Security Informatics, Vancouver, BC, Canada, 23–26 May 2010; pp. 19–24. [Google Scholar]
- Yang, K.-S.; Chen, C.-C.; Tseng, Y.-H.; Ho, Z.-P. Name entity extraction based on POS tagging for criminal information analysis and relation visualization. In Proceedings of the 6th International Conference on New Trends in Information Science, Service Science and Data Mining (ISSDM2012), Taipei, Taiwan, 23–25 October 2012; pp. 785–789. [Google Scholar]
- Asharef, M.; Omar, N.; Albared, M.; Minhui, Z.; Weiming, W.; Jingjing, Z. Arabic named entity recognition in crime documents. J. Theor. Appl. Inf. Technol. 2012, 44, 1–6. [Google Scholar]
- Alkaff, A.; Mohd, M. Extraction of Nationality from Crime News. J. Theor. Appl. Inf. Technol. 2013, 54, 304–312. [Google Scholar]
- Pandey, S.; Jain, N.; Bhardwaj, A.; Kaur, G. Leveraging Machine Learning and Natural Language Processing for Predicting the Crime Rate: Reach 360. In Proceedings of the 3rd International Conference on Internet of Things and Connected Technologies (ICIoTCT), Jaipur, India, 26–27 March 2018; pp. 26–27. [Google Scholar]
- Saraiva, M.; Matijosaitiene, I.; Mishra, S.; Amante, A. Crime prediction and monitoring in porto, portugal, using machine learning, spatial and text analytics. ISPRS Int. J. Geo-Inf. 2022, 11, 400. [Google Scholar] [CrossRef]
- Han, S.; Huang, H.; Liu, J.; Xiao, S. American hate crime trends prediction with event extraction. arXiv 2021, arXiv:2111.04951. [Google Scholar]
- Ozalp, S.; Williams, M.L.; Burnap, P.; Liu, H.; Mostafa, M. Antisemitism on Twitter: Collective efficacy and the role of community organisations in challenging online hate speech. Soc. Media + Soc. 2020, 6, 2056305120916850. [Google Scholar] [CrossRef]
- Pereira-Kohatsu, J.C.; Quijano-Sánchezz, L.; Liberatore, F.; Camacho-Collados, M. Detecting and monitoring hate speech in Twitter. Sensors 2019, 19, 4654. [Google Scholar] [CrossRef]
- Ku, C.H.; Iriberri, A.; Leroy, G. Crime information extraction from police and witness narrative reports. In Proceedings of the IEEE Conference on Technologies for Homeland Security, Waltham, MA, USA, 12–13 May 2008; pp. 193–198. [Google Scholar]
- Ku, C.H.; Iriberri, A.; Leroy, G. Natural language processing and e-government: Crime information extraction from heterogeneous data sources. In Proceedings of the 2008 International Conference on Digital Government Research, Melbourne, Australia, 23–24 October 2008; pp. 162–170. [Google Scholar]
- Anderson, N.; Belavy, D.L.; Perle, S.M.; Hendricks, S.; Hespanhol, L.; Verhagen, E.; Memon, A.R. AI did not write this manuscript, or did it? Can we trick the AI text detector into generated texts? The potential future of ChatGPT and AI in Sports & Exercise Medicine manuscript generation. BMJ Open Sport Exerc. Med. 2023, 9, e001568. [Google Scholar] [PubMed]
- Hayward, K.J.; Maas, M.M. Artificial intelligence and crime: A primer for criminologists. Crime Media Cult. 2021, 17, 209–233. [Google Scholar] [CrossRef]
- Cooke, D.J.; Michie, C. Violence risk assessment: From prediction to understanding—Or from what? To why? In Managing Clinical Risk; Routledge: Oxford, UK, 2012; pp. 3–25. [Google Scholar]
- Oswald, M.; Grace, J.; Urwin, S.; Barnes, G.C. Algorithmic risk assessment policing models: Lessons from the Durham HART model and ‘Experimental’proportionality. Inf. Commun. Technol. Law 2018, 27, 223–250. [Google Scholar] [CrossRef]
- Babuta, A.; Oswald, M.; Rinik, C. Machine Learning Algorithms and Police Decision-Making: LEGAL, Ethical and Regulatory Challenges. 2018. Available online: https://nrl.northumbria.ac.uk/id/eprint/40579/ (accessed on 5 December 2023).
- Babuta, A.; Oswald, M. Machine Learning Predictive Algorithms and the Policing of Future Crimes: Governance and Oversight. Available online: https://ssrn.com/abstract=3479081 (accessed on 1 October 2023).
- Mittelstadt, B. Automation, algorithms, and politics|auditing for transparency in content personalization systems. Int. J. Commun. 2016, 10, 12. [Google Scholar]
- Alikhademi, K.; Drobina, E.; Prioleau, D.; Richardson, B.; Purves, D.; Gilbert, J.E. A review of predictive policing from the perspective of fairness. Artif. Intell. Law 2022, 30, 1–17. [Google Scholar] [CrossRef]
- Joh, E.E. Feeding the Machine: Policing, Crime Data, & Algorithms. William Mary Bill Rights J. 2017, 26, 287. [Google Scholar]
- Goldenfein, J. Algorithmic Transparency and Decision-Making Accountability: Thoughts for Buying Machine Learning Algorithms; Office of the Victorian Information Commissioner: Melbourne, Australia, 2019; Closer to the Machine: Technical, Social, and Legal Aspects of AI; Available online: https://ssrn.com/abstract=3445873 (accessed on 1 October 2023).
- Blodgett, S.L.; Barocas, S.; Daume III, H.; Wallach, H. Language (technology) is power: A critical survey of” bias” in nlp. arXiv 2020, arXiv:2005.14050. [Google Scholar]
- Lum, K.; Isaac, W. Predictive policing reinforces police bias. Hum. Rights Data Anal. Group 2016, 10. [Google Scholar]
- Kusner, M.J.; Loftus, J.; Russell, C.; Silva, R. Counterfactual Fairness. In Proceedings of the Advances in Neural Information Processing Systems, Long Beach, CA, USA, 4–9 December 2017; pp. 4066–4076. [Google Scholar]
- Dwork, C.; Hardt, M.; Pitassi, T.; Reingold, O.; Zemel, R. Fairness through awareness. In Proceedings of the 3rd Innovations in Theoretical Computer Science Conference 2012, Cambridge, MA, USA, 8–10 January 2012; pp. 214–226. [Google Scholar]
- Corbett-Davies, S.; Pierson, E.; Feller, A.; Goel, S.; Huq, A. Algorithmic decision making and the cost of fairness. In Proceedings of the 23rd Acm Sigkdd International Conference on Knowledge Discovery and Data Mining, Halifax, NS, Canada, 13–17 August 2017; pp. 797–806. [Google Scholar]
- Hardt, M.; Price, E.; Srebro, N. Equality of opportunity in supervised learning. arXiv 2016, arXiv:1610.02413. [Google Scholar]
- Grgic-Hlaca, N.; Zafar, M.B.; Gummadi, K.P.; Weller, A. The case for process fairness in learning: Feature selection for fair decision making. NIPS Symp. Mach. Learn. Law 2016, 1, 11. [Google Scholar]
- Verma, S.; Rubin, J. Fairness Definitions Explained. In Proceedings of the International Workshop on Software Fairness, Gothenburg, Sweden, 29 May 2018; pp. 1–7. [Google Scholar]
- Asaro, P.M. AI ethics in predictive policing: From models of threat to an ethics of care. IEEE Technol. Soc. Mag. 2019, 38, 40–53. [Google Scholar] [CrossRef]
| Tool | Reference | Description and Application | Type | Other Technologies in Use | Agencies That Use the Tool |
|---|---|---|---|---|---|
| CompStat | [20,37] | Crime data analysis to identify crime trends and patterns within specific districts and guide police departments in addressing crime and allocating resources more efficiently | Location-based | Geographic information system (GIS) | New York Police Department (NYPD) |
| PredPol | [34,35] | An ML algorithm trained on past crime data alongside hotspot mapping to predict crime risks | Based on crime type, location, and time | Google Maps, GPS, and AVL | More than 60 police departments, including the Los Angeles Police Department and the Atlanta Police Department |
| HunchLab | [19,38,39] | Uses ML to find crime trends and reflects community needs by giving weight to different types of crimes | Location-based | GIS | Philadelphia Police Department |
| Palantir | [17] | Makes predictions about crime perpetrators who fit the queries that officers input to the system | Location-based | - | Salt Lake City Police Department |
| Strategic Subject List | [40,41] | Scoring algorithm to predict risks of offending and involvement in criminal activities based on empirical data, considering factors like the person’s criminal record and violence within their criminal network | Person-based | - | Chicago Police Department (CPD) |
| Beware | [39,42,43] | Individualized risk assessments of potential offenders to inform of potential criminal activities; the risk assessment is based on public arrest records, social media posts, and information compiled by commercial data brokers | Person-based | - | Fresno Police Department |
| Domain Awareness System | [44] | An urban network consisting of sensors, databases, devices, software, and infrastructure designed to provide insights and information to officers via smartphones and precinct computers to make them aware of possible criminal activities | A combination of location-based and person-based strategies | Surveillance systems like cameras | New York Police Department (NYPD) |
| COPLINK | [45,46] | Consists of two components: COPLINK Connect for information sharing between police officers and law enforcement agencies, and COPLINK Detect, which uses AI to find crime patterns | Both location-based and person-based | - | Phoenix Police Department |
| PRECOBS | [47] | Pre-crime observation system that predicts crimes by mainly consulting the near-repeat hypothesis and a rational-choice-framed conception of offenders that can be translated into algorithms for classifying and evaluating crime risk in geographic areas | Location-based | - | Police departments in Switzerland and Germany |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sarzaeim, P.; Mahmoud, Q.H.; Azim, A.; Bauer, G.; Bowles, I. A Systematic Review of Using Machine Learning and Natural Language Processing in Smart Policing. Computers 2023, 12, 255. https://doi.org/10.3390/computers12120255
Sarzaeim P, Mahmoud QH, Azim A, Bauer G, Bowles I. A Systematic Review of Using Machine Learning and Natural Language Processing in Smart Policing. Computers. 2023; 12(12):255. https://doi.org/10.3390/computers12120255
Chicago/Turabian StyleSarzaeim, Paria, Qusay H. Mahmoud, Akramul Azim, Gary Bauer, and Ian Bowles. 2023. "A Systematic Review of Using Machine Learning and Natural Language Processing in Smart Policing" Computers 12, no. 12: 255. https://doi.org/10.3390/computers12120255
APA StyleSarzaeim, P., Mahmoud, Q. H., Azim, A., Bauer, G., & Bowles, I. (2023). A Systematic Review of Using Machine Learning and Natural Language Processing in Smart Policing. Computers, 12(12), 255. https://doi.org/10.3390/computers12120255






