A Novel RFID Authentication Protocol Based on Reconfigurable RRAM PUF
Abstract
:1. Introduction
2. Research on RFID Security Mechanism Based on PUF
3. RRAM PUF Circuit
4. Protocol Details
4.1. Registration Phase
4.2. Certification Phase
4.3. Reconfiguration Phase
5. Experimental Results Analysis
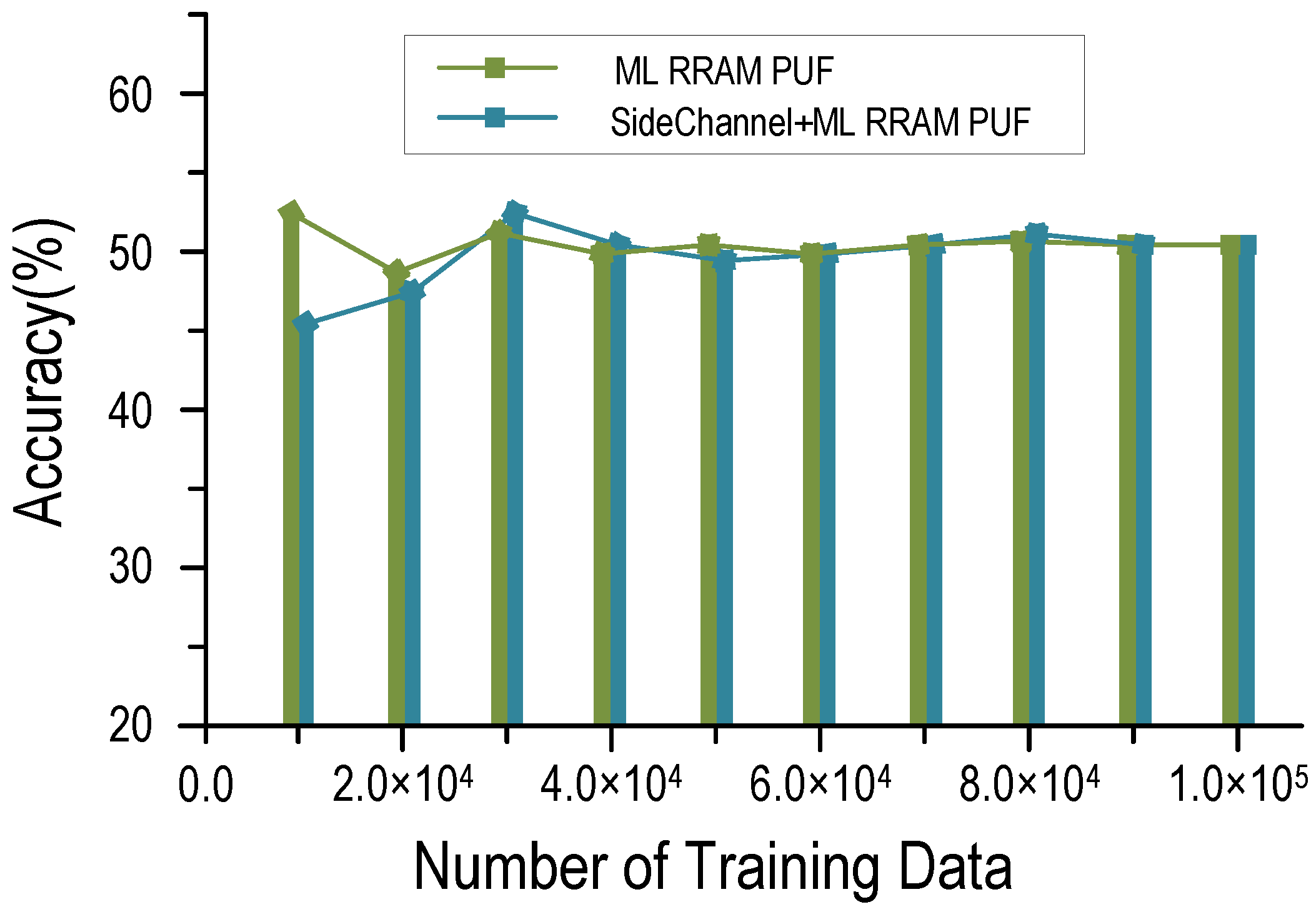
5.1. RRAM PUF Test Results
5.2. Protocol Characteristics Analysis
5.2.1. Reliability Analysis
5.2.2. Security Analysis
5.2.3. Protocol Comparative Analysis
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Gope, P.; Lee, J.; Quek, T.Q.S. Lightweight and Practical Anonymous Authentication Protocol for RFID Systems Using Physically Unclonable Functions. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2831–2843. [Google Scholar] [CrossRef]
- Gao, Y.; Al-Sarawi, S.F.; Abbott, D. Physical unclonable functions. Nat. Electron. 2020, 3, 81–91. [Google Scholar] [CrossRef]
- Suh, G.; Devadas, S. Physical unclonable functions for device authentication and secret key generation. Proceedings the of 2007 44th ACM/IEEE Design Automation Conference, San Diego, CA, USA, 4–8 June 2007. [Google Scholar]
- Zhang, L.; Fong, X.; Chang, C.-H.; Kong, Z.H.; Roy, K. Feasibility study of emerging non-volatile memory based physical unclonable functions. In Proceedings of the 6th IEEE Int. Memory Workshop (IMW), Taipei, Taiwan, 18–21 May 2014. [Google Scholar]
- Zhang, L.; Kong, Z.H.; Chang, C.-H.; Cabrini, A.; Torelli, G. Exploiting Process Variations and Programming Sensitivity of Phase Change Memory for Reconfigurable Physical Unclonable Functions. IEEE Trans. Inf. Forensics Secur. 2014, 9, 921–932. [Google Scholar] [CrossRef]
- Das, J.; Scott, K.; Rajaram, S.; Burgett, D.; Bhanja, S. MRAM PUF: A novel geometry based magnetic PUF with integrated CMOS. IEEE Trans. Nano 2015, 14, 436–443. [Google Scholar] [CrossRef]
- Rose, G.S.; Meade, C.A. Performance Analysis of a Memristive Crossbar PUF Design. In Proceedings of the 52nd Annual Design Automation Conference (DAC), San Francisco, CA, USA, 8–12 June 2015. [Google Scholar]
- Shrivastava, A.; Chen, P.; Cao, Y.; Yu, S.; Chakrabarti, C. Design of a reliable RRAM-based PUF for compact hardware security primitives. In Proceedings of the IEEE International Symposium on Circuits and Systems (ISCAS), Montreal, QC, Canada, 22–25 May 2016; pp. 2326–2329. [Google Scholar]
- Chen, A. Utilizing the variability of resistive random access memory to implement reconfigurable physical unclonable functions. IEEE Electron Device Lett. 2015, 36, 138–140. [Google Scholar] [CrossRef]
- Chen, P.-Y.; Fang, R.; Liu, R.; Chakrabarti, C.; Cao, Y.; Yu, S. Exploiting Resistive Cross-point Array for Compact Design of PhysicalUnclonable Function. In Proceedings of the IEEE International Hardware Oriented Securiry and Trust (HOST), Washington, DC, USA, 5–7 May 2015; pp. 26–31. [Google Scholar]
- Liu, R.; Wu, H.; Pang, Y.; Qian, H.; Yu, S. A highly reliable and tamper-resistant RRAM PUF: Design and experimental validation. In Proceedings of the IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 3–5 May 2016; pp. 13–18. [Google Scholar]
- Chen, A. Comprehensive assessment of RRAM-based PUF for hardware security applications. In Proceedings of the IEEE International Electron Devices Meeting (IEDM), Washington, DC, USA, 7–9 December 2015; pp. 1071–1074. [Google Scholar]
- Hajri, B.; Mansour, M.M.; Chehab, A.; Aziza, H. A Lightweight Reconfigurable RRAM-based PUF for Highly Secure Applications. In Proceedings of the IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems (DFT), Frascati, Italy, 19–21 October 2020; pp. 1–4. [Google Scholar]
- Pappu, R.; Recht, B.; Taylorand, J.; Gershenfeld, N. PhysicalOne Way Functions. Science 2002, 297, 2026–2030. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Akgun, M.; Caglayan, M.U. Providing destructive privacy and scalability in RFID systems using PUFs. Ad Hoc Netw. 2015, 32, 32–42. [Google Scholar] [CrossRef]
- Aysu, A.; Gulcan, E.; Moriyama, D.; Schaumont, P.; Yung, M. End-to-end design of a puf-based privacy preserving authentication protocol. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2015; pp. 556–576. [Google Scholar]
- Pandey, S.; Deyati, S.; Singh, A.; Chatterjee, A. Noise-resilient SRAM physically unclonable function design for security. In Proceedings of the IEEE 25th Asian Test Symposium (ATS), Hiroshima, Japan, 21–24 November 2016; pp. 55–60. [Google Scholar]
- Delvaux, J.; Gu, D.; Verbauwhede, I.; Hiller, M.; Yu, M.-D. Efficient fuzzy extraction of puf-induced secrets: Theory and applications. In International Conference on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2016; pp. 412–431. [Google Scholar]
- Huth, C.; Aysu, A.; Guajardo, J.; Duplys, P.; Güneysu, T. Secure and private, yet lightweight, authentication for the IoT via PUF and CBKA. In International Conference on Information Security and Cryptology; Springer: Berlin/Heidelberg, Germany, 2017; pp. 28–48. [Google Scholar]
- Aysu, A.; Wang, Y.; Schaumont, P.; Orshansky, M. New maskless debiasing method for lightweight physical unclonable function. In Proceedings of the IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Mclean, VA, USA, 1–5 May 2017; pp. 134–139. [Google Scholar]
- Suzuki, M.; Ueno, R.; Homma, N.; Aoki, T. Multiple-valued debiasing for physically unclonable functions and its application to fuzzy extractors. In International Workshop on Constructive Side-Channel Analysis and Secure Design; Springer: Berlin/Heidelberg, Germany, 2017; pp. 248–263. [Google Scholar]
- Zhu, F. New lightweight two-way RFID authentication protocol: PUF-LMAP. Microcomput. Appl. 2016, 35, 1–4. [Google Scholar]
- Wang, C.; Qin, X.; Liu, Y. Heuristic Attack Strategy Against Improved LMAP Protocol. Comput. Sci. 2014, 41, 143–149. [Google Scholar]
- Xie, S.; Liang, W.; Xu, J.; Tang, M.; Weng, T.-H.; Li, K.C. A novel bidirectional RFID identity authentication protocol. In Proceedings of the 2018 IEEE Smart World, Ubiquitous Intelligence & Computing, Advanced & Trusted Computing, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation, Guangzhou, China, 8–12 October 2018; pp. 301–307. [Google Scholar]
- Zheng, X.; Xie, S.; Xie, C.; Zhu, W. An RFID Lightweight Authentication Technology Based on PUF-RFID Structure Model. In Blockchain and Trustworthy Systems; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Sun, Z.; Wei, M. PUF-based Anonymous RFID system Ownership Transfer Protocol. In Proceedings of the Chinese Control Conference (CCC), Guangzhou, China, 27–30 July 2019; pp. 6367–6373. [Google Scholar]
- Ye, Q.; Sun, Z. Lightweight RFID Authentication Protocol for Cloud Services using PUF Encryption. In Proceedings of the 33rd Chinese Control and Decision Conference (CCDC), Kunming, China, 22–24 May 2021; pp. 5629–5634. [Google Scholar]
- Choi, Y.; Karpinskyy, B.; Ahn, K.; Kim, Y.; Kwon, S.; Park, J.; Lee, Y.; Noh, M. Physically unclonable function in 28nm fdsoi technology achieving high reliability for aec-q 100 grade 1 and iso 26262 asilb. In Proceedings of the 2020 IEEE International Solid-State Circuits Conference—(ISSCC), San Francisco, CA, USA, 16–20 February 2020; pp. 426–428. [Google Scholar]
- Li, D.; Yang, K. 25.1 a 562F2 physically unclonable function with a zero-overhead stabilization scheme. In Proceedings of the 2019 IEEE International Solid- State Circuits Conference—(ISSCC), San Francisco, CA, USA, 17–21 February 2019; pp. 400–402. [Google Scholar]
- Taneja, S.; Alvarez, A.B.; Alioto, M. Fully synthesizable PUF featuring hysteresis and temperature compensation for 3.2% native BER and 1.02 fJ/b in 40 nm. IEEE J. Solid-State Circuits 2018, 39, 2828–2839. [Google Scholar] [CrossRef]
- Liu, J.; Zhu, Y.; Chan, C.; Martins, R.P. A 0.04% BER Strong PUF with Cell-Bias-Based CRPs Filtering and Background Offset Calibration. IEEE Trans. Circuits Syst. I Regul. Pap. (TCAS-I) 2020, 67, 3853–3865. [Google Scholar] [CrossRef]
- Zhang, Z.; Guo, Y. Survey of physical unclonable function. Comput. Appl. 2007, 32, 3115–3120. [Google Scholar] [CrossRef]





| Test | p-Value | Result |
|---|---|---|
| Frequency | 0.834 | Pass |
| Frequency within a Block | 0.676 | Pass |
| Runs Test | 0.547 | Pass |
| Longest Run of Ones in a Block | 0.435 | Pass |
| Binary Matrix Rank | 0.541 | Pass |
| Discrete Fourier Transform | 0.427 | Pass |
| Non-overlapping Template Matching | 0.851 | Pass |
| Overlapping Template Matching | 0.744 | Pass |
| Maurer’s Universal Statistical | 0.472 | Pass |
| Linear Complexity | 0.624 | Pass |
| Serial | 0.784 | Pass |
| Approximate Entropy | 0.842 | Pass |
| Cumulative Sums | 0.745 | Pass |
| Random Excursion | 0.524 | Pass |
| Random Excursion Variants | 0.481 | Pass |
| This Work | ISSCC’20 [28] | ISSCC’19 [29] | JSSC’18 [30] | TCAS-I’20 [31] | |
|---|---|---|---|---|---|
| Type | RRAM | CMOS | CMOS | CMOS | CMOS |
| Bit Error Rate | 0.089% | 0.30% | 3.2% | 0.04% | |
| Inter HD | 0.5001 | 0.4978 | 0.4998 | 0.4907 | 0.5032 |
| Intra HD | 0 | - | - | 0.0049 | 0.097 |
| Performance | Xie [24] | Zheng [25] | Sun [26] | Ye [27] | This Protocol |
|---|---|---|---|---|---|
| Physical attack | √ | × | √ | × | √ |
| Eavesdropping attack | √ | × | × | √ | √ |
| Forgery attack | √ | √ | √ | √ | √ |
| Middleman attack | √ | × | × | × | √ |
| Replay attack | × | √ | √ | √ | √ |
| Nonsynchronous | √ | × | √ | √ | √ |
| Tracking attack | √ | √ | √ | √ | √ |
| Machine learning | √ | √ | × | × | √ |
| Reliability | O | × | O | O | √ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ren, Q.; Fu, X.; Wu, H.; Yang, K.; Lei, D.; Xing, G.; Zhang, F. A Novel RFID Authentication Protocol Based on Reconfigurable RRAM PUF. Micromachines 2021, 12, 1560. https://doi.org/10.3390/mi12121560
Ren Q, Fu X, Wu H, Yang K, Lei D, Xing G, Zhang F. A Novel RFID Authentication Protocol Based on Reconfigurable RRAM PUF. Micromachines. 2021; 12(12):1560. https://doi.org/10.3390/mi12121560
Chicago/Turabian StyleRen, Qirui, Xiangqu Fu, Hao Wu, Kaiqi Yang, Dengyun Lei, Guozhong Xing, and Feng Zhang. 2021. "A Novel RFID Authentication Protocol Based on Reconfigurable RRAM PUF" Micromachines 12, no. 12: 1560. https://doi.org/10.3390/mi12121560






