STT-DPSA: Digital PUF-Based Secure Authentication Using STT-MRAM for the Internet of Things
Abstract
1. Introduction
- We propose a digital PUF-based secure authentication model using STT-MRAM PUF as configuration bits for the network of LUTs.
- We use two digital PUFs that have the same function as the basic building block for IoT authentication models.
- We present two versions of authentication model for different requirements on cell area: one is based on matrix multiplication and the other is based on stochastic logic.
- Through a series of attack analyses and hardware resource evaluations, we prove that our method poses lightweight overhead on participating parties and provides high security for IoT devices.
- We implement STT-DPSA on FPGA to prove the feasibility of our model.
2. Related Work
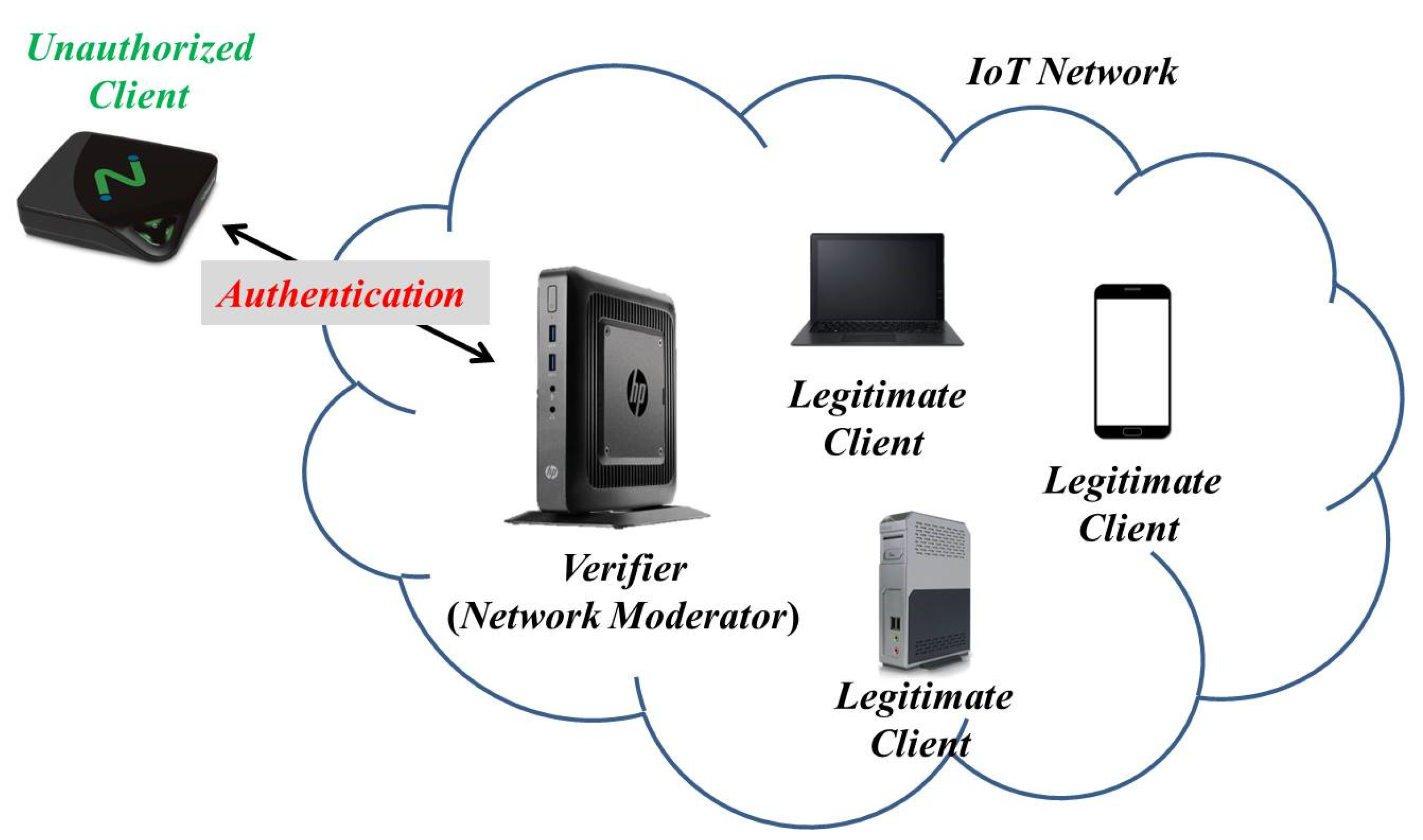
3. System and Attack Models
3.1. System Model
3.2. Attack Model
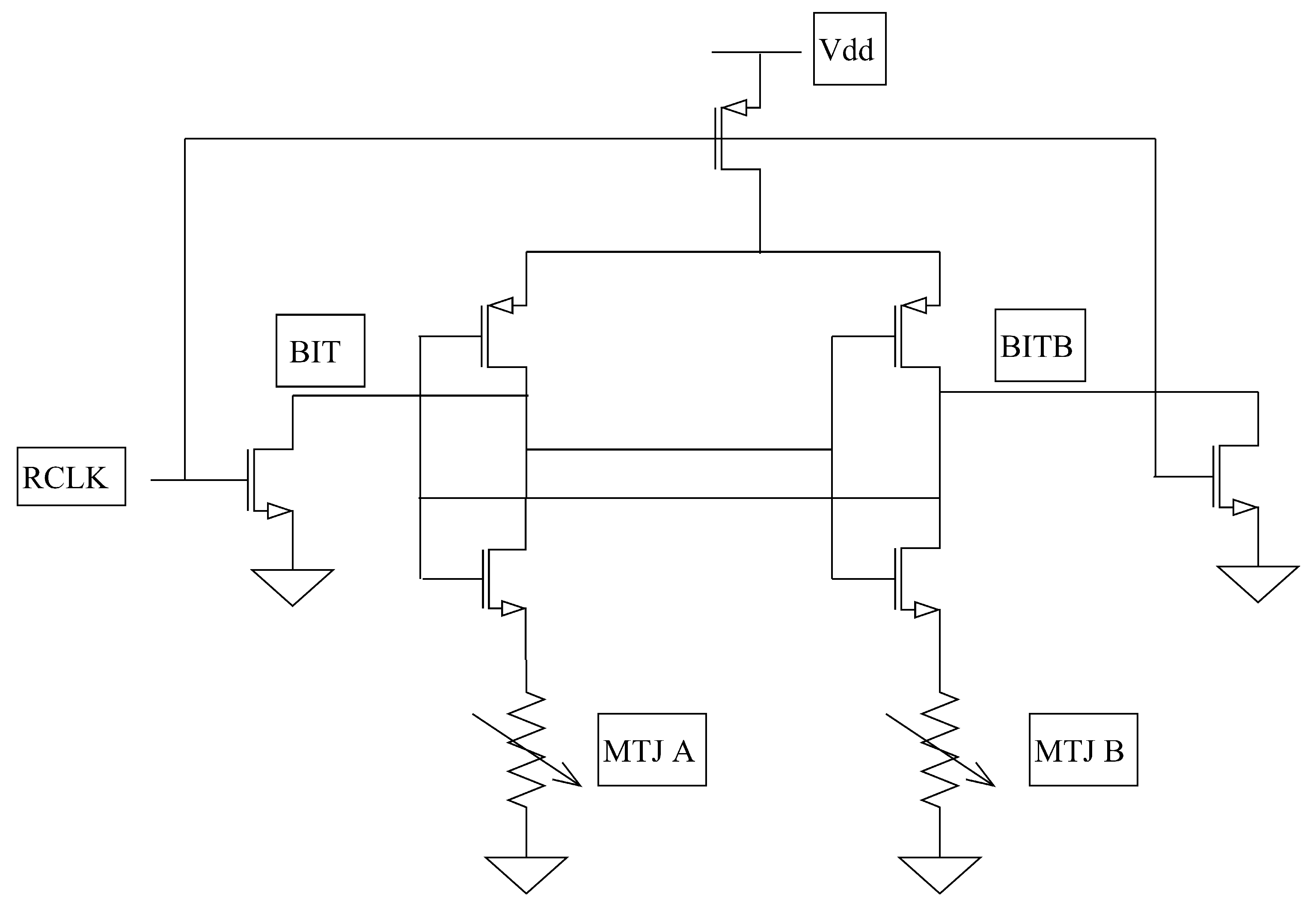
4. Design of a Strong Digital Physical Unclonable Function (PUF) Based on Spin-Transfer Torque Magnetic Random-Access Memory (STT-MRAM) PUF
5. Authentication Model
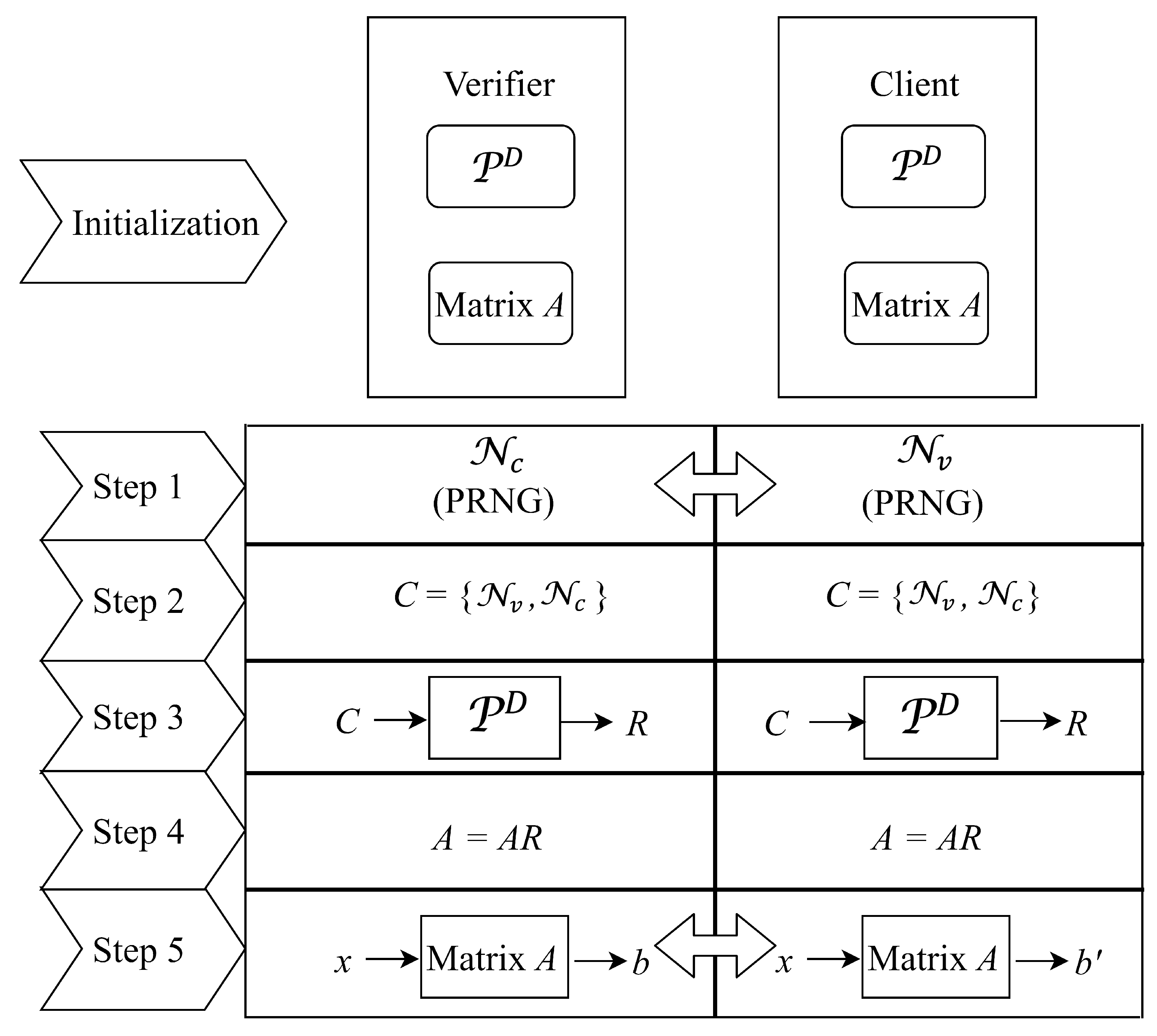
5.1. Authentication Model Based on Matrix Multiplication
- Step 1:
- The verifier ( the client) generates a random number () using pseudo-random number generator (PRNG) [12] and exchanges the random number with the client ( the verifier).
- Step 2:
- Both of the verifier and client form a string C by concatenating with .
- Step 3:
- Both of the verifier and client use the string C as a challenge of his/her and obtain a corresponding response (called R for short) in a matrix form.
- Step 4:
- Both of the verifier and client compute the matrix multiplication and replace matrix A with . If the resulted matrix A is a zero matrix, then we must re-initialize the matrix A and go back to step 1. That is because a zero matrix used in step 5 will lead to a result of zero vector that can be easily predicted by an attacker.
- Step 5:
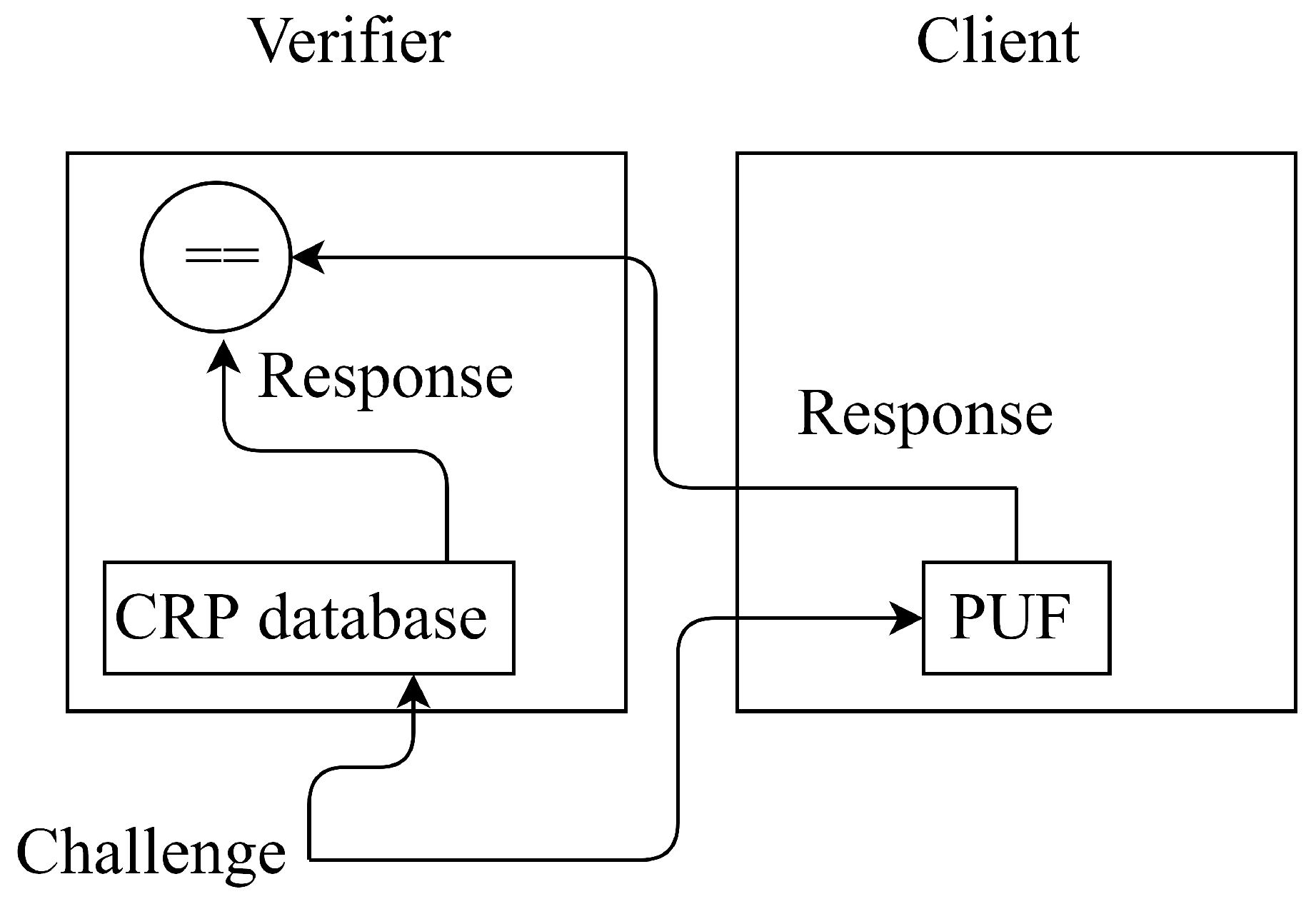
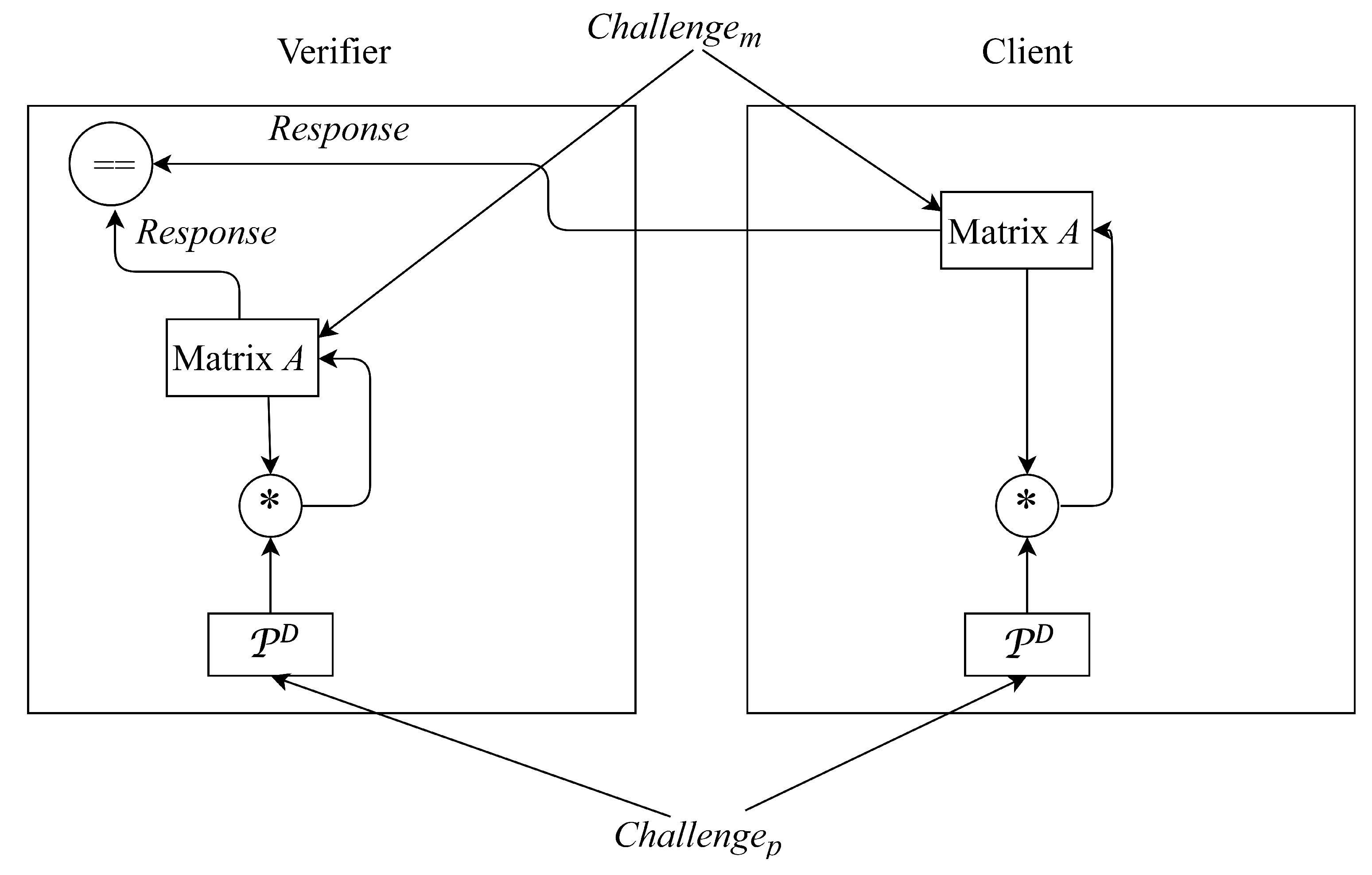
- The verifier selects a column vector x generated by PRNG as a challenge and sends x to the client. Subsequently, the verifier ( the client) computes as b (). Next, the client sends to the verifier. If , then the verifier authorizes the client as a legitimate device. Otherwise, the client fails to be authorized and viewed as an illegitimate one. We show behaviors of the verifier and client in Algorithms 1 and 2, respectively.
| Algorithm 1: The verifier Side |
| Input: , A, , and Output: Whether the authentication process succeeds // Flow chart of authentication model based on matrix multiplication for the verifier side is as shown in the left side of Figure 8.  |
| Algorithm 2: The client Side |
| Input: , A, , and x Output: // Flow chart of authentication model based on matrix multiplication for the client side is as shown in the right side of Figure 8. 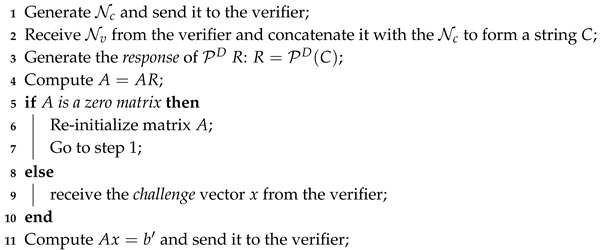 |
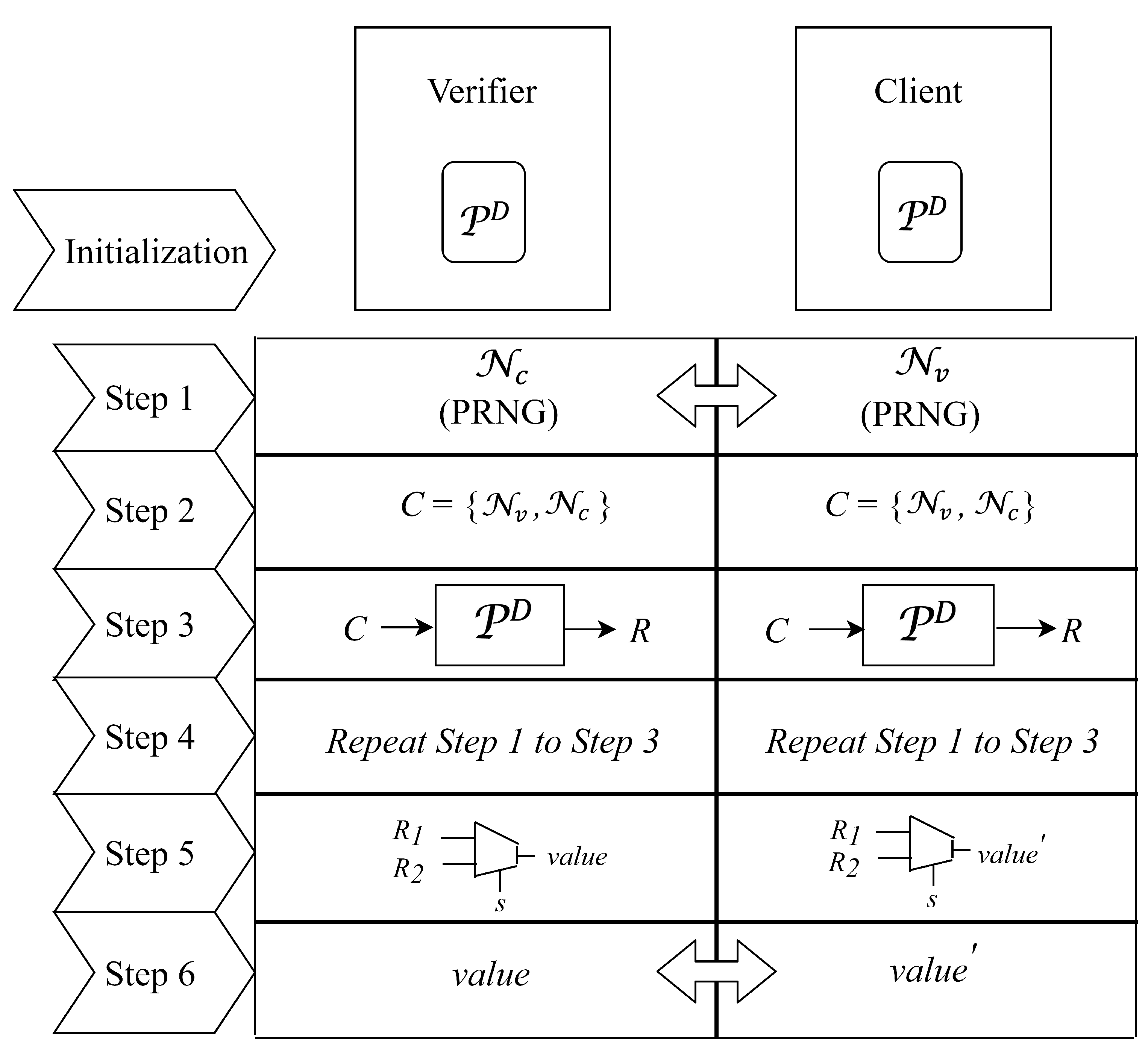
5.2. Authentication Model Based on Stochastic Logic
- Step 1:
- The verifier ( the client) generates a random number () using PRNG and exchanges the random number with the client ( the verifier).
- Step 2:
- The verifier and client form a string by concatenating with .
- Step 3:
- The verifier and client use the string as a challenge of his/her and obtain a corresponding response (called for short).
- Step 4:
- The verifier and client repeat steps and obtain a corresponding response (called for short).
- Step 5:
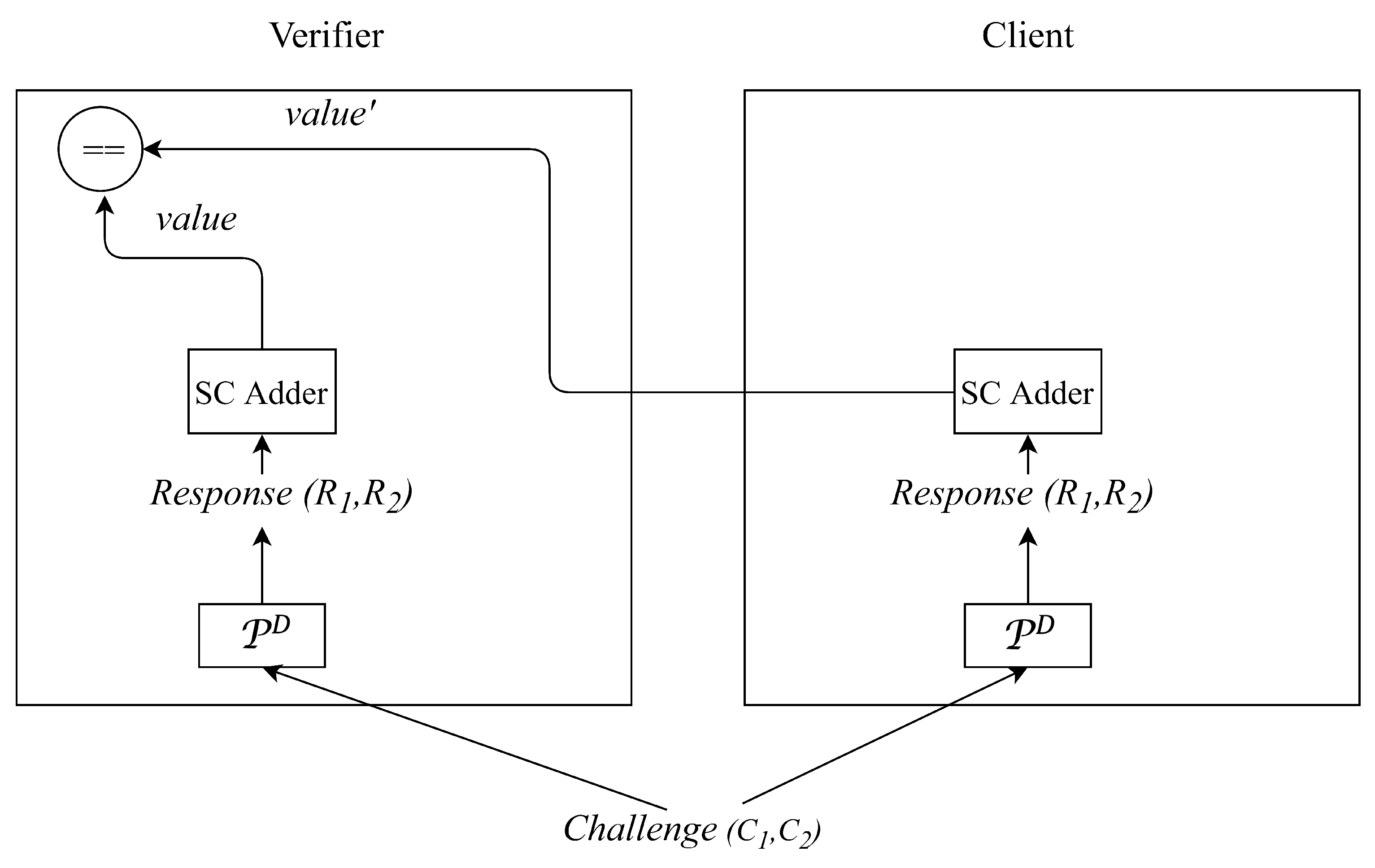
- The verifier and client treat and as bitstreams and take these two bitstreams as inputs to a stochastic logic adder for obtaining a corresponding calculation result and .
- Step 6:
- The client sends to the verifier. Finally, if , then the verifier authorizes the client as a legitimate device. Otherwise, the client fails to be authorized and viewed as an illegitimate one. We show the behaviors of the verifier and client in Algorithms 3 and 4, respectively.
| Algorithm 3: Verifier Side |
| Input: , , , and Output: Whether the authentication process succeeds // Flow chart of the authentication model based on stochastic logic for the verifier side is as shown in the left side of Figure 10.
|
| Algorithm 4: Client Side |
| Input: , and Output: // Flow chart of the authentication model based on stochastic logic for the client side is as shown in the right side of Figure 10.
|
6. System Analysis
6.1. System Complexity
6.2. System Security
6.2.1. Modeling Attacks
6.2.2. Modeling Attack to the Matrix A of Matrix Multiplication Authentication Model
6.2.3. Brute-Force Attacks to
6.2.4. Brute-Force Attacks to the Matrix A of Matrix Multiplication Authentication Model
6.2.5. Brute-Force Attacks to the Response of the Matrix A of Matrix Multiplication Authentication Model
6.2.6. The Modeling Attacks to Stochastic Logic Authentication Model
6.2.7. Resistance against Machine-Learning Attacks
7. Evaluation
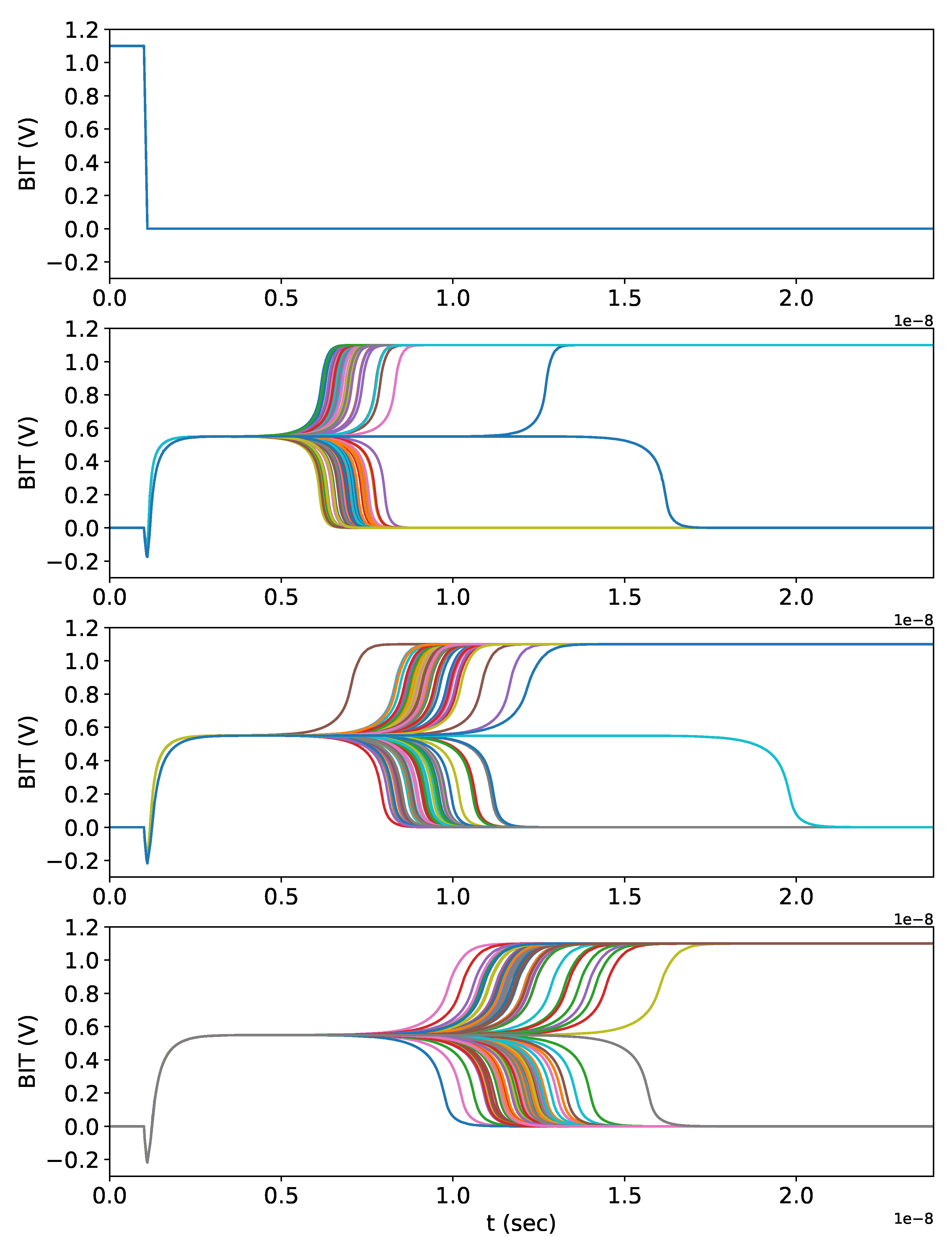
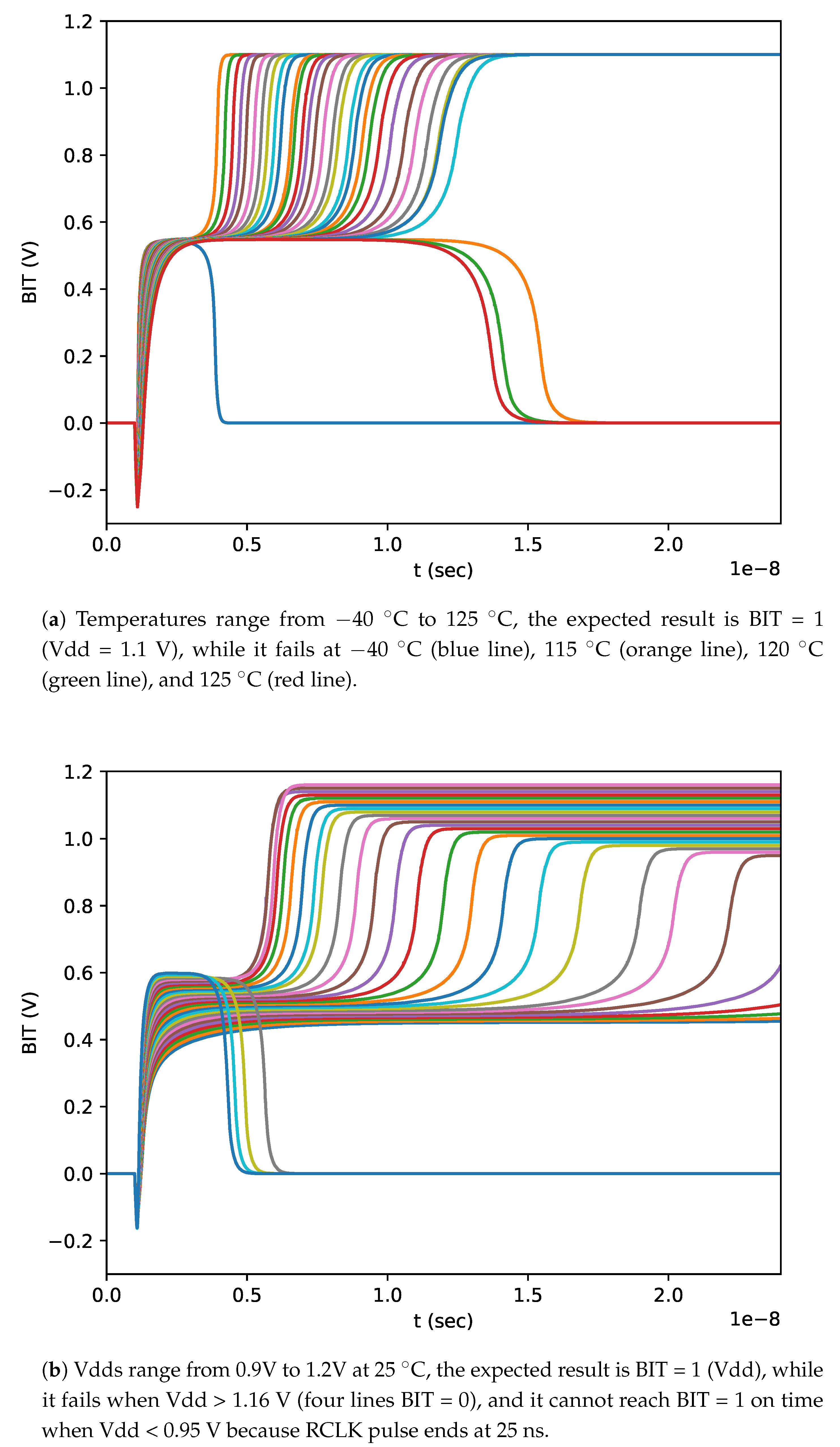
7.1. Unpredictability Validation of
7.2. Reliability Validation of
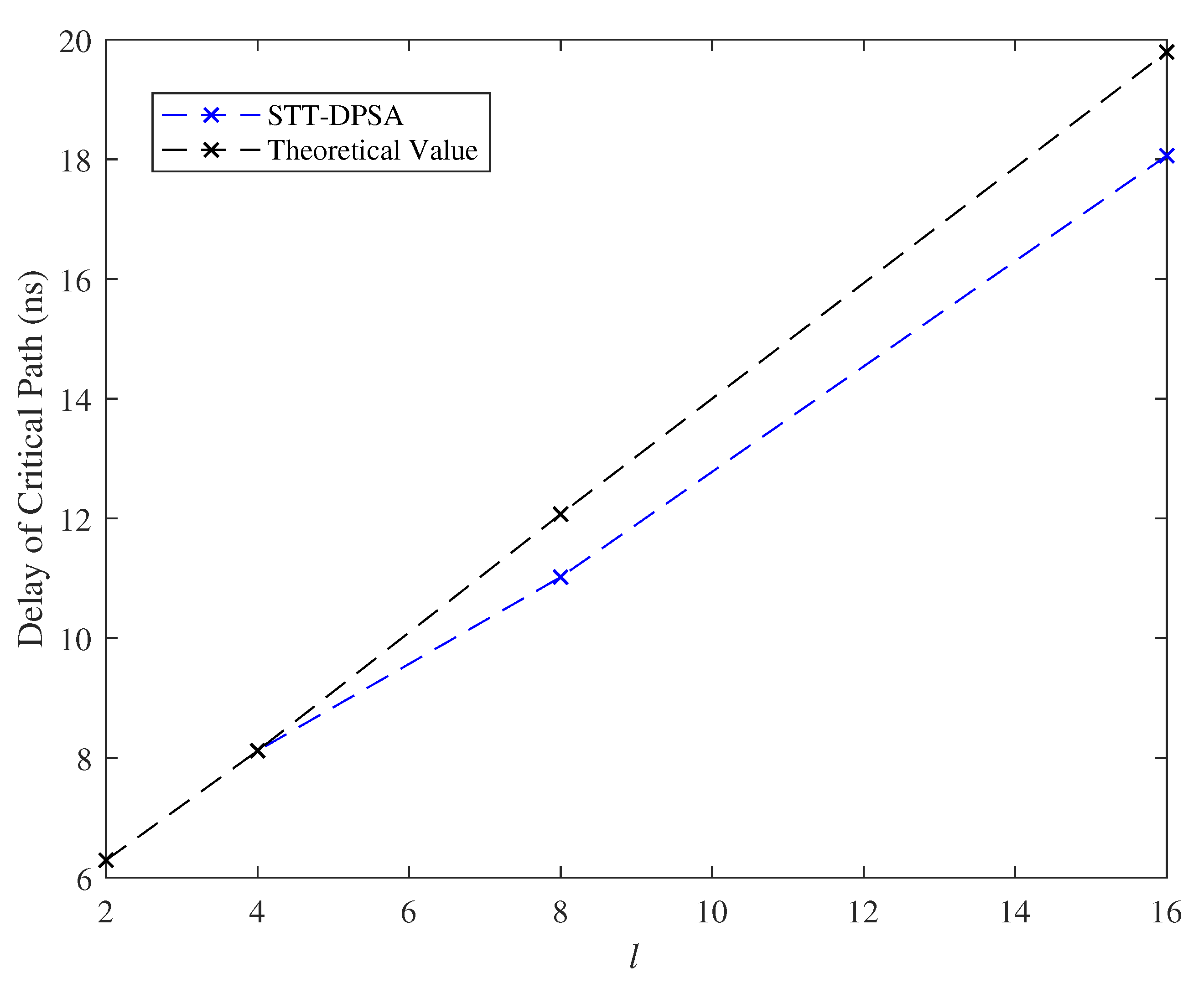
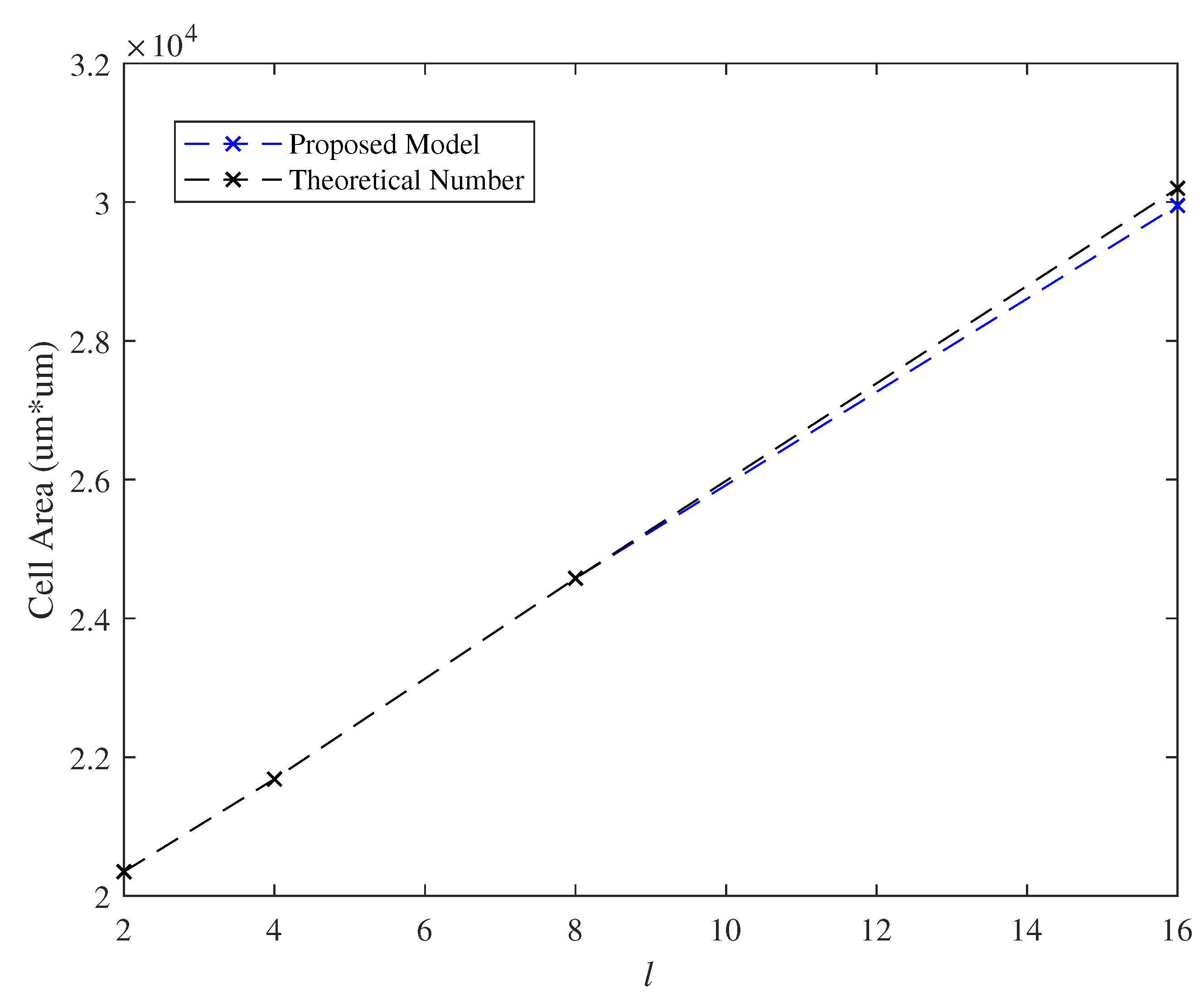
7.3. Effect of the Parameter l
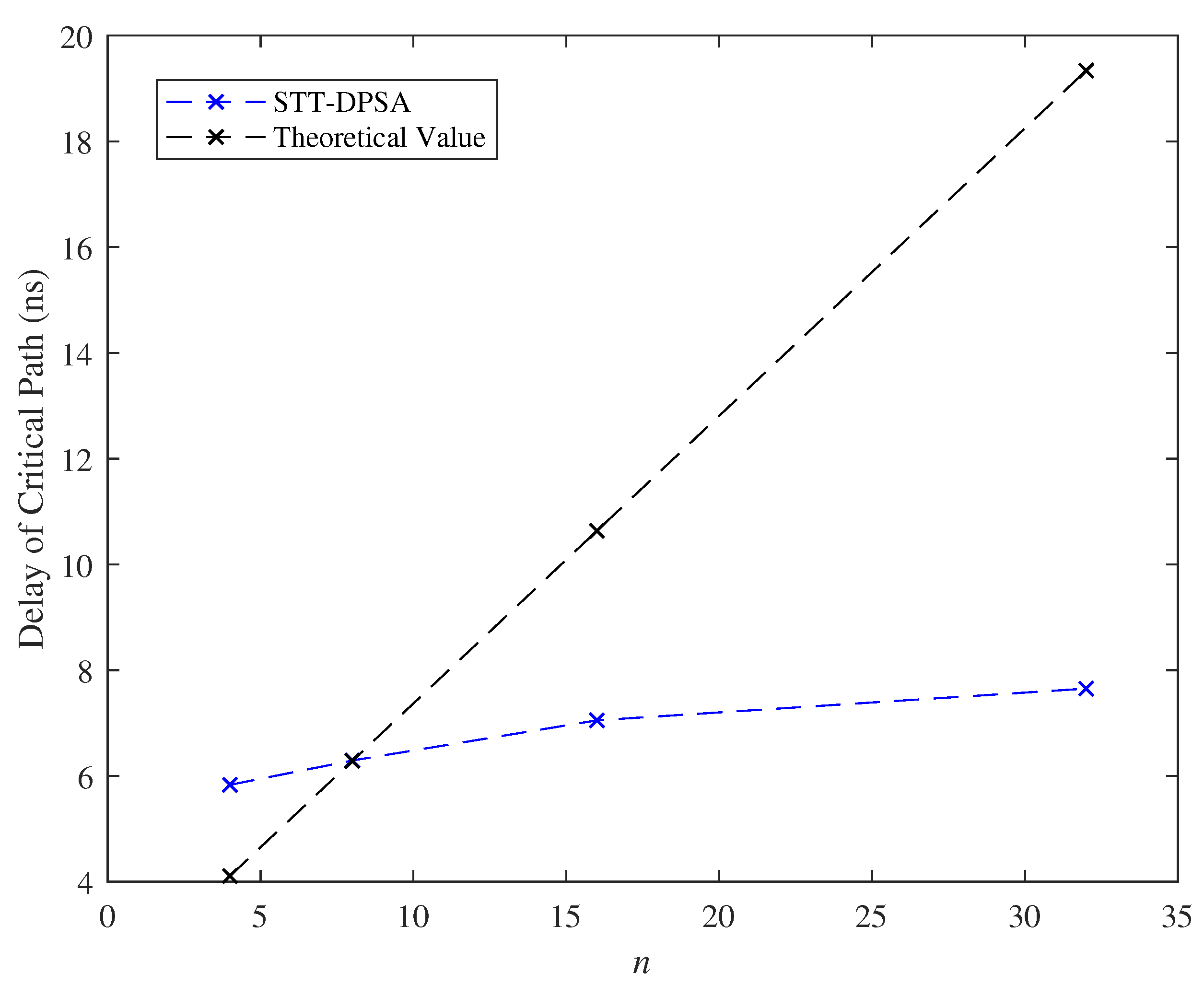
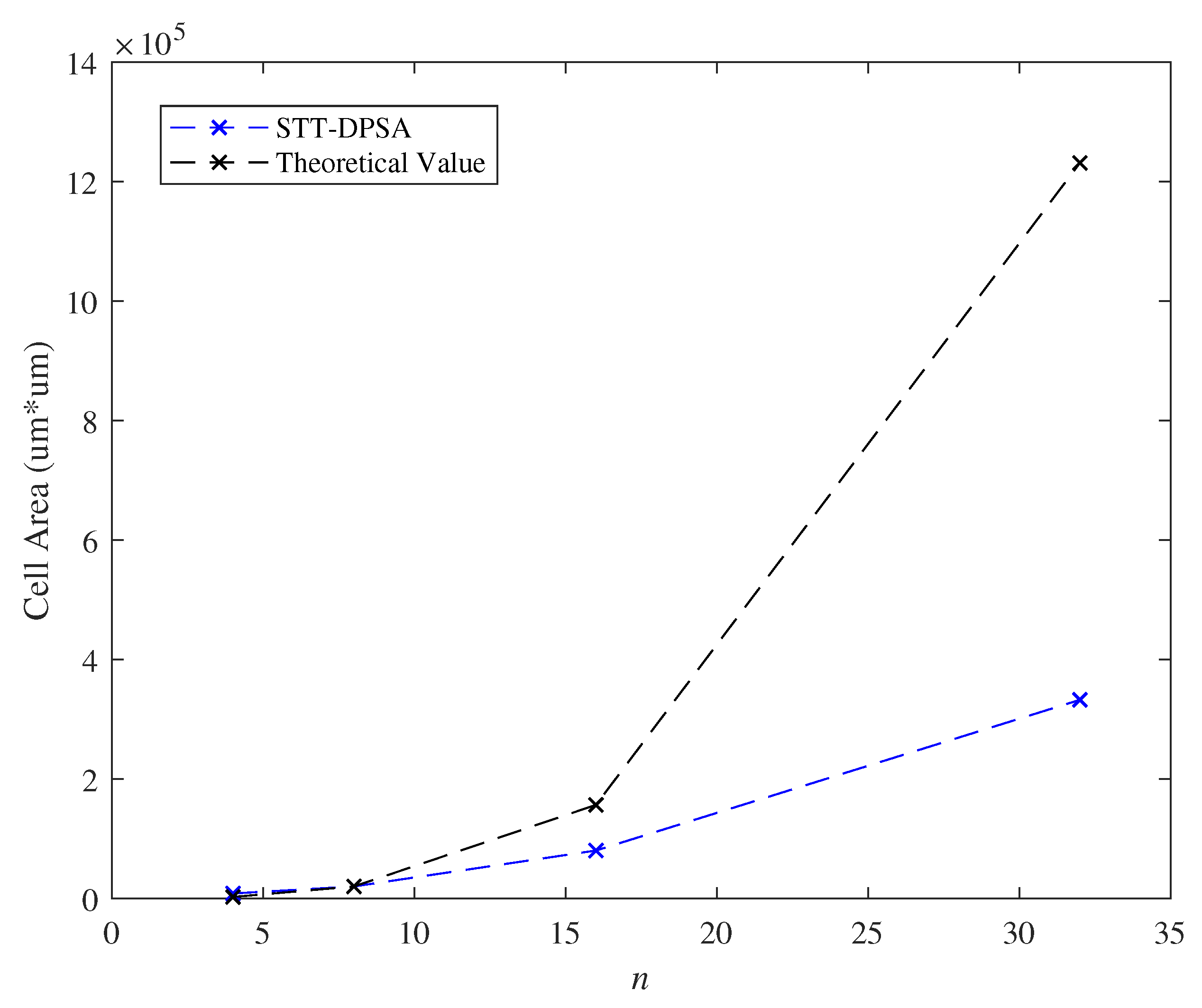
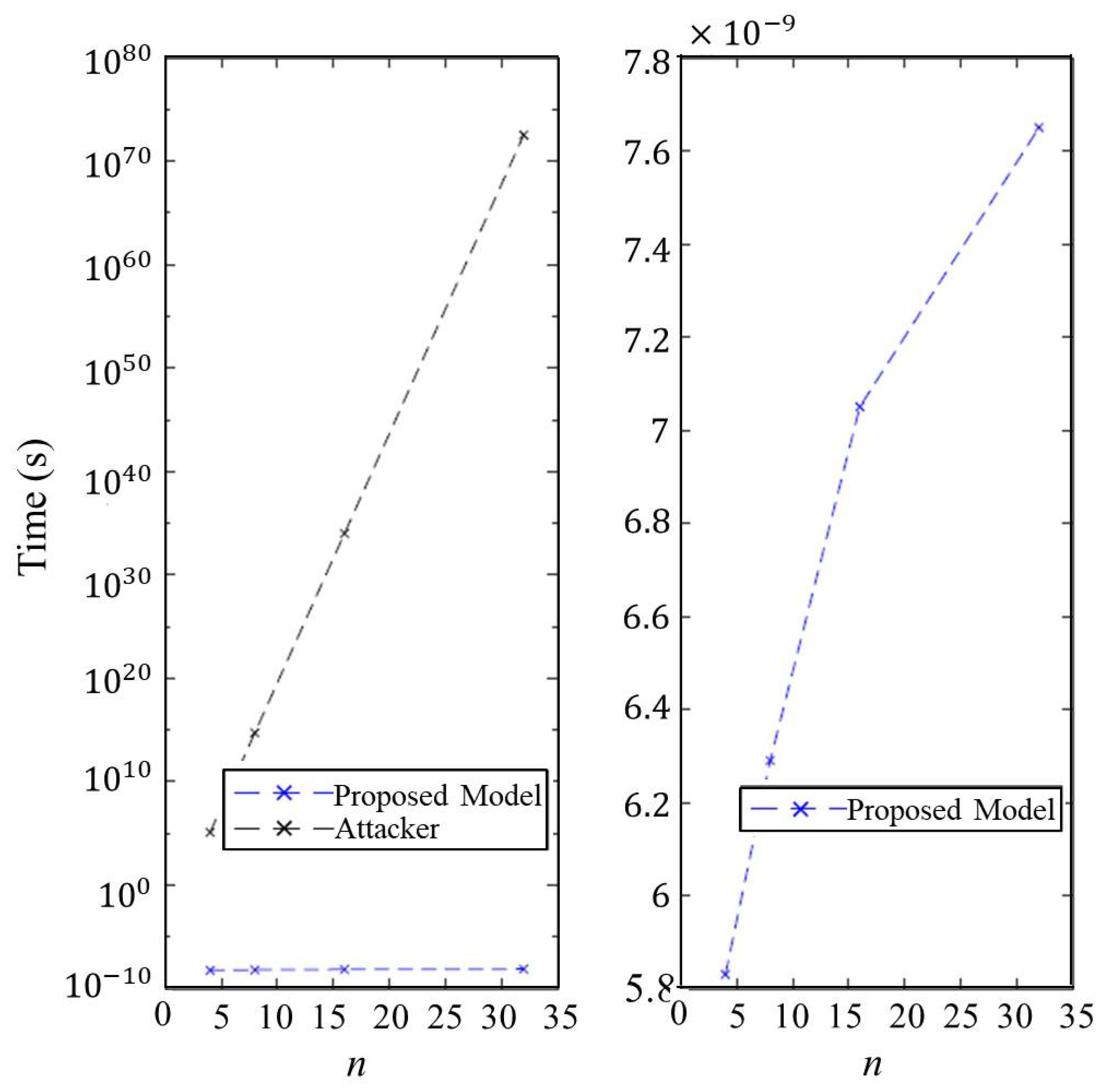
7.4. Effect of the Parameter n
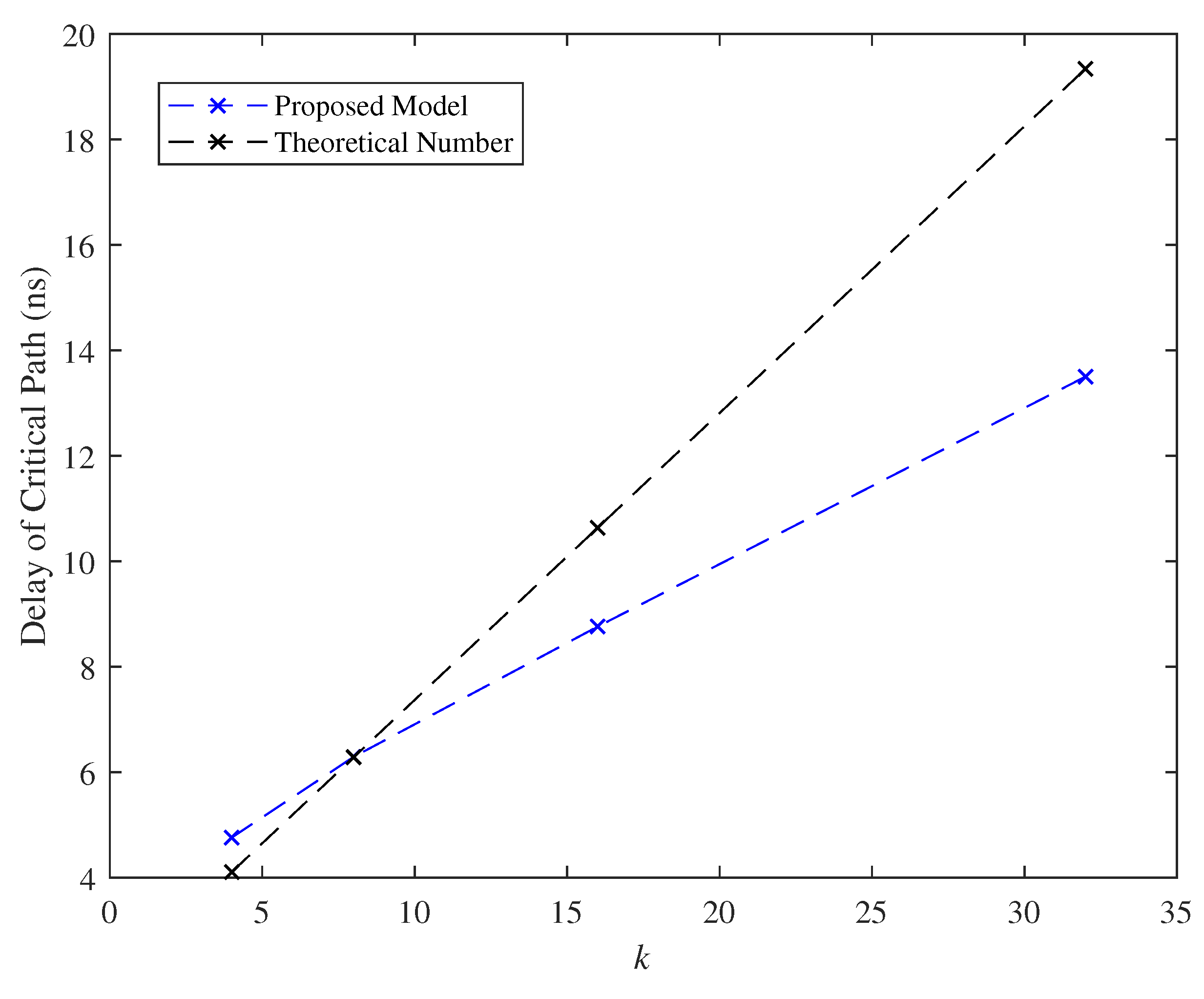
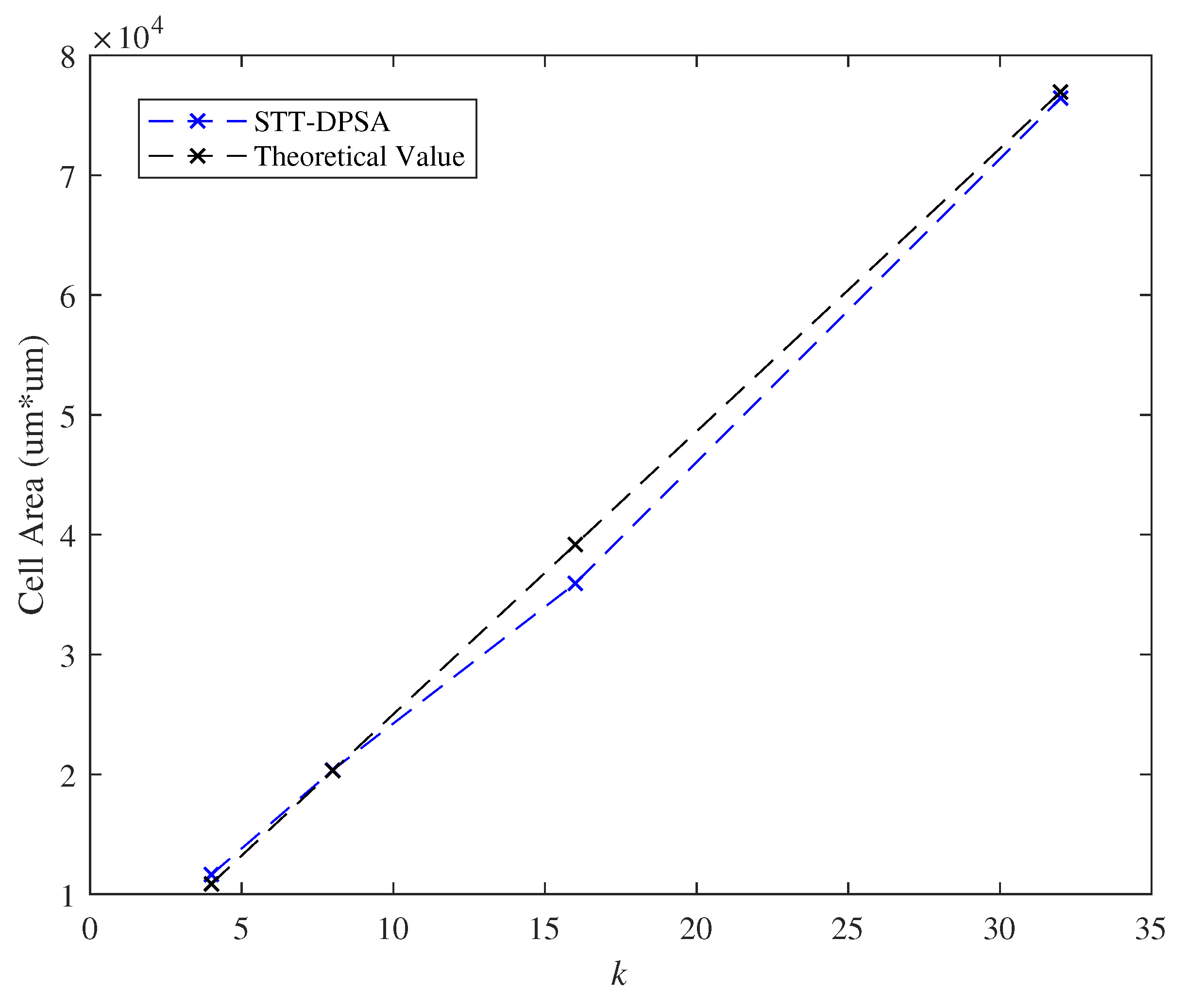
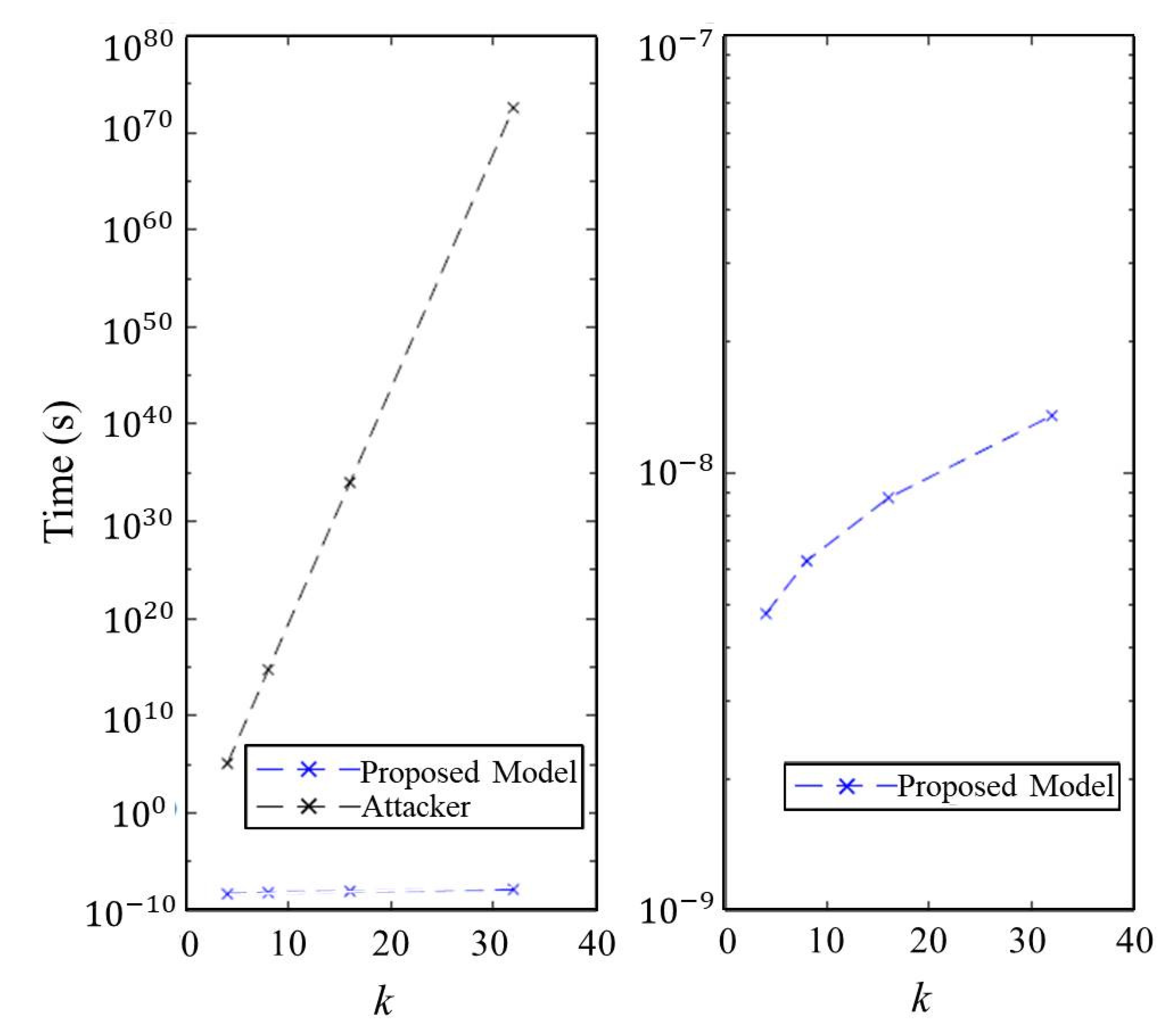
7.5. Effect of the Parameter k
7.6. Execution Time of Authentication
7.7. Evaluation of Stochastic Logic Authentication Model
7.8. Comparisons
7.9. Implementation of STT-DPSA
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Suh, G.E.; Devadas, S. Physical Unclonable Functions for Device Authentication and Secret Key Generation. In Proceedings of the 44th ACM/IEEE Design Automation Conference, San Diego, CA, USA, 4–8 June 2007; pp. 9–14. [Google Scholar]
- Gassend, B.; Clarke, D.; van Dijk, M.; Devadas, S. Silicon Physical Random Functions. In Proceedings of the 9th ACM Conference Computer and Communication Security, Washington, DC, USA, 18–22 November 2002; pp. 148–160. [Google Scholar]
- Herder, C.; Yu, M.; Koushanfar, F.; Devadas, S. Physical Unclonable Functions and Applications: A Tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- Perrig, A.; Szewczyk, R.; Tygar, J.D.; Wen, V.; Culler, D.E. SPINS: Security Protocols for Sensor Networks. Wirel. Netw. 2002, 8, 521–534. [Google Scholar] [CrossRef]
- Karlof, C.; Sastry, N.; Wagner, D. TinySec: A Link Layer Security Architecture for Wireless Sensor Networks. In Proceedings of the ACM 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, MD, USA, 3–5 November 2004; pp. 162–175. [Google Scholar]
- Zhu, S.; Setia, S.; Jajodia, S. LEAP+: Efficient Security Mechanisms for Large-Scale Distributed Sensor Networks. ACM Trans. Sens. Netw. 2006, 2, 500–528. [Google Scholar] [CrossRef]
- Tsou, Y.-T.; Lu, C.-S.; Kuo, S.-Y. SER: Secure and Efficient Retrieval for Anonymous Range Query in Wireless Sensor Networks. Comput. Commun. 2017, 108, 1–16. [Google Scholar] [CrossRef]
- Liu, A.; Ning, P. TinyECC: A Configurable Library for Elliptic Curve Cryptography in Wireless Sensor Networks. In Proceedings of the ACM/IEEE International Conference on Information Processing in Sensor Networks, St. Louis, MO, USA, 22–24 April 2008; pp. 245–256. [Google Scholar]
- Oliveira, L.B.; Aranha, D.F.; Gouvêa, C.P.; Scott, M.; Caâmara, D.F.; López, J.; Dahab, R. TinyPBC: Pairings for Authenticated Identitybased Non-Interactive Key Distribution in Sensor Networks. Comput. Commun. 2011, 34, 485–493. [Google Scholar] [CrossRef]
- Li, S.; Xu, H.; Li, M.; Zhou, X. A Group-Based NTRU-Like Public-Key Cryptosystem for IoT. IEEE Access 2019, 7, 75732–75740. [Google Scholar]
- Layman, P.; Chaudhry, S.; Norman, J.; Thomson, J. Electronic Fingerprinting of Semiconductor Integrated Circuits. U.S. Patent 6 738 294, 30 September 2002. [Google Scholar]
- Weste, N.; Harris, D. Integrated Circuit Design, 4th ed.; Pearson Education: London, UK, 2011; pp. 377–424. [Google Scholar]
- Meguerdichian, S.; Potkonjak, M. Matched Public PUF: Ultra Low Energy Security Platform. In Proceedings of the IEEE/ACM International Symposium on Low-Power Electronics and Design, Fukuoka, Japan, 1–3 August 2011; pp. 45–50. [Google Scholar]
- Xu, T.; Wendt, J.; Potkonjak, M. Digital Bimodal Function: An Ultra-Low Energy Security Primitive. In Proceedings of the IEEE Symposium on Low Power Electronics and Design, Beijing, China, 4–6 September 2013; pp. 292–296. [Google Scholar]
- Xu, T.; Potkonjak, M. Robust and Flexible FPGA-based Digital PUF. In Proceedings of the IEEE International Conference on Field Programmable Logic and Applications, Munich, Germany, 2–4 September 2014; pp. 1–6. [Google Scholar]
- Tanaka, Y.; Bian, S.; Hiromoto, M.; Sato, T. Coin Flipping PUF: A Novel PUF With Improved Resistance Against Machine Learning Attacks. IEEE Trans. Circuits Syst. II Express Br. 2018, 65, 602–606. [Google Scholar] [CrossRef]
- Yu, W.; Wen, Y.; Köse, S.; Chen, J. Exploiting Multi-Phase On-Chip Voltage Regulators as Strong PUF Primitives for Securing IoT. J. Electron. Test. Theory Appl. (Springer) 2018, 34, 587–598. [Google Scholar] [CrossRef]
- Rahman, M.; Hosey, A.; Guo, Z.; Carroll, J.; Forte, D.; Tehranipoor, M. Systematic correlation and cell neighborhood analysis of SRAM PUF for robust and unique key generation. J. Hardw. Syst. Secur. 2017, 1, 137–155. [Google Scholar] [CrossRef]
- Yu, W.; Chen, J. Masked AES PUF: A new PUF against hybrid SCA/MLAs. IET Electron. Lett. 2018, 54, 618–620. [Google Scholar] [CrossRef]
- Govindaraj, R.; Ghosh, S.; Katkoori, S. Design, Analysis and Application of Embedded Resistive RAM based Strong Arbiter PUF. IEEE Trans. Dependable Secure Comput. 2018. [Google Scholar] [CrossRef]
- Xu, T.; Potkonjak, M. Digital PUF using Intentional Faults. In Proceedings of the IEEE International Symposium on Quality Electronic Design, Santa Clara, CA, USA, 2–4 March 2015; pp. 448–451. [Google Scholar]
- Miao, J.; Li, M.; Roy, S.; Ma, Y.; Yu, B. SD-PUF: Spliced Digital Physical Unclonable Function. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2018, 37, 927–940. [Google Scholar] [CrossRef]
- Beckmann, N.; Potkonjak, M. Hardware-Based Public-Key Cryptography with Public Physically Unclonable Functions. In International Workshop on Information Hiding; Springer: Berlin/Heidelberg, Germany, 2009; pp. 206–220. [Google Scholar]
- Park, S.; Lim, S.; Jeong, D.; Lee, J.; Yang, J.; Lee, H. PUFSec: Device Fingerprint-based Security Architecture for Internet of Things. In Proceedings of the IEEE Conference on Computer Communications, Atlanta, GA, USA, 1–4 May 2017; pp. 1–9. [Google Scholar]
- Cao, Y.; Guo, Y.; Liu, B.; Ge, W.; Zhu, M.; Chang, C. A Fully Digital Physical Unclonable Function Based Temperature Sensor for Secure Remote Sensing. In Proceedings of the 27th International Conference on Computer Communication and Networks (ICCCN), Hangzhou, China, 30 July–2 August 2018; pp. 1–8. [Google Scholar]
- Gu, T.; Mohapatra, P. BF-IoT: Securing the IoT Networks via Fingerprinting-Based Device Authentication. In Proceedings of the IEEE 15th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Chengdu, China, 9–12 October 2018; pp. 254–262. [Google Scholar]
- Das, J.; Scott, K.; Bhanja, S. MRAM PUF: Using Geometric and Resistive Variations in MRAM Cells. ACM J. Emerg. Technol. Comput. Syst. (JETC) 2016, 13, 1–15. [Google Scholar] [CrossRef]
- Maiti, A.; Gunreddy, V.; Schaumont, P. A Systematic Method to Evaluate and Compare the Performance of Physical Unclonable Functions. In Embedded Systems Design with FPGAs; Springer: New York, NY, USA, 2012; pp. 245–267. [Google Scholar]
- Alaghi, A.; Qian, W.; Hayes, J.P. The Promise and Challenge of Stochastic Computing. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2018, 37, 1515–1531. [Google Scholar] [CrossRef]
- Alaghi, A.; Li, C.; Hayes, J.P. Stochastic Circuits for Real-Time Image-Processing Applications. In Proceedings of the 50th ACM/IEEE Design Automation Conference, Austin, TX, USA, 29 May–7 June 2013; pp. 1–6. [Google Scholar]
- Rührmair, U.; Sehnke, F.; Sölter, J.; Dror, G.; Devadas, S.; Schmidhuber, J. Modeling Attacks on Physical Unclonable Functions. In Proceedings of the ACM Conference on Computer and Communications Security, Chicago IL, USA, 4–8 October 2010; pp. 237–249. [Google Scholar]
- Tsou, Y.-T.; Zhen, H.; Kuo, S.-Y.; Chang, C.-R.; Fukushima, A.; Rong, B.-D. SPARR: Spintronics-based Private Aggregatable Randomized Response for Crowdsourced Data Collection and Analysis. Comput. Commun. 2020, 152, 8–18. [Google Scholar] [CrossRef]
- Fukushima, A.; Seki, T.; Yakushiji, K.; Kubota, H.; Imamura, H.; Yuasa, S.; Ando, K. Spindice: A Scalable Truly Random Number Generator Based on Spintronics. J. Appl. Phys. Express 2014, 7, 083001. [Google Scholar] [CrossRef]
- NanGate FreePDK45 Open Cell Library. Available online: http://projects.si2.org/openeda.si2.org/projects/nangatelib (accessed on 10 February 2020).
- UMN MTJ SPICE Model. Available online: http://mtj.umn.edu (accessed on 10 February 2020).



| Methods | Computationa Complexity | Computational Complexity | Susceptibility | Initialization Time | Resource Complexity |
|---|---|---|---|---|---|
| (Verifier Side) | (Client Side) | ||||
| PUFSec [24] | Exponential | Exponential | Yes | Linear | Exponential |
| Matched PPUF [13] | Linear | Linear | Yes | No | Constant |
| DBF [14] | Polynomial | Linear | No | Exponential | Exponential |
| DBF with Arbiter PUF [15] | Polynomial | Linear | Exponential | Yes | Exponential |
| STT-DPSA (our method) | Linear | Linear | No | Linear | Polynomial |
| Cell Area (m*m) | Delay of Critical Path (ns) | |
|---|---|---|
| Matrix Multiplication Version | 20,349 | 31.45 |
| Stochastic Logic Version | 4953 | 17.25 |
| Method | Cell Area (m*m) | Execution Time (s) | Memory Usage (bits) |
|---|---|---|---|
| STT-DPSA | 20,349 | 0 | |
| DBF [14] | 835 | ||
| DBF with Arbiter PUF [15] | 930 | ||
| PUFSec [24] | 2245 | ||
| Matched PUF [13] | 5376 | 0 |
| Parameter Settings | , , , and |
|---|---|
| FPGA Device | Intel Cyclone IV E EP4CE115F29C7 |
| Total Logic Elements | 68108/114480 (59%) |
| Total Registers | 3080 |
| Clock Frequency | Hz |
| Supply Voltage (V) | Cell Area (um) | Power @ 50 MHz (mW) |
|---|---|---|
| 1.8 | 20,349 | 1.2278 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chien, W.-C.; Chang, Y.-C.; Tsou, Y.-T.; Kuo, S.-Y.; Chang, C.-R. STT-DPSA: Digital PUF-Based Secure Authentication Using STT-MRAM for the Internet of Things. Micromachines 2020, 11, 502. https://doi.org/10.3390/mi11050502
Chien W-C, Chang Y-C, Tsou Y-T, Kuo S-Y, Chang C-R. STT-DPSA: Digital PUF-Based Secure Authentication Using STT-MRAM for the Internet of Things. Micromachines. 2020; 11(5):502. https://doi.org/10.3390/mi11050502
Chicago/Turabian StyleChien, Wei-Chen, Yu-Chian Chang, Yao-Tung Tsou, Sy-Yen Kuo, and Ching-Ray Chang. 2020. "STT-DPSA: Digital PUF-Based Secure Authentication Using STT-MRAM for the Internet of Things" Micromachines 11, no. 5: 502. https://doi.org/10.3390/mi11050502
APA StyleChien, W.-C., Chang, Y.-C., Tsou, Y.-T., Kuo, S.-Y., & Chang, C.-R. (2020). STT-DPSA: Digital PUF-Based Secure Authentication Using STT-MRAM for the Internet of Things. Micromachines, 11(5), 502. https://doi.org/10.3390/mi11050502






