A Distributed Deadlock-Free Task Offloading Algorithm for Integrated Communication–Sensing–Computing Satellites with Data-Dependent Constraints
Abstract
1. Introduction
- We establish a mixed-integer linear programming (MILP) model for the task offloading problem in ICSC satellites, considering data dependence constraints among sub-tasks.
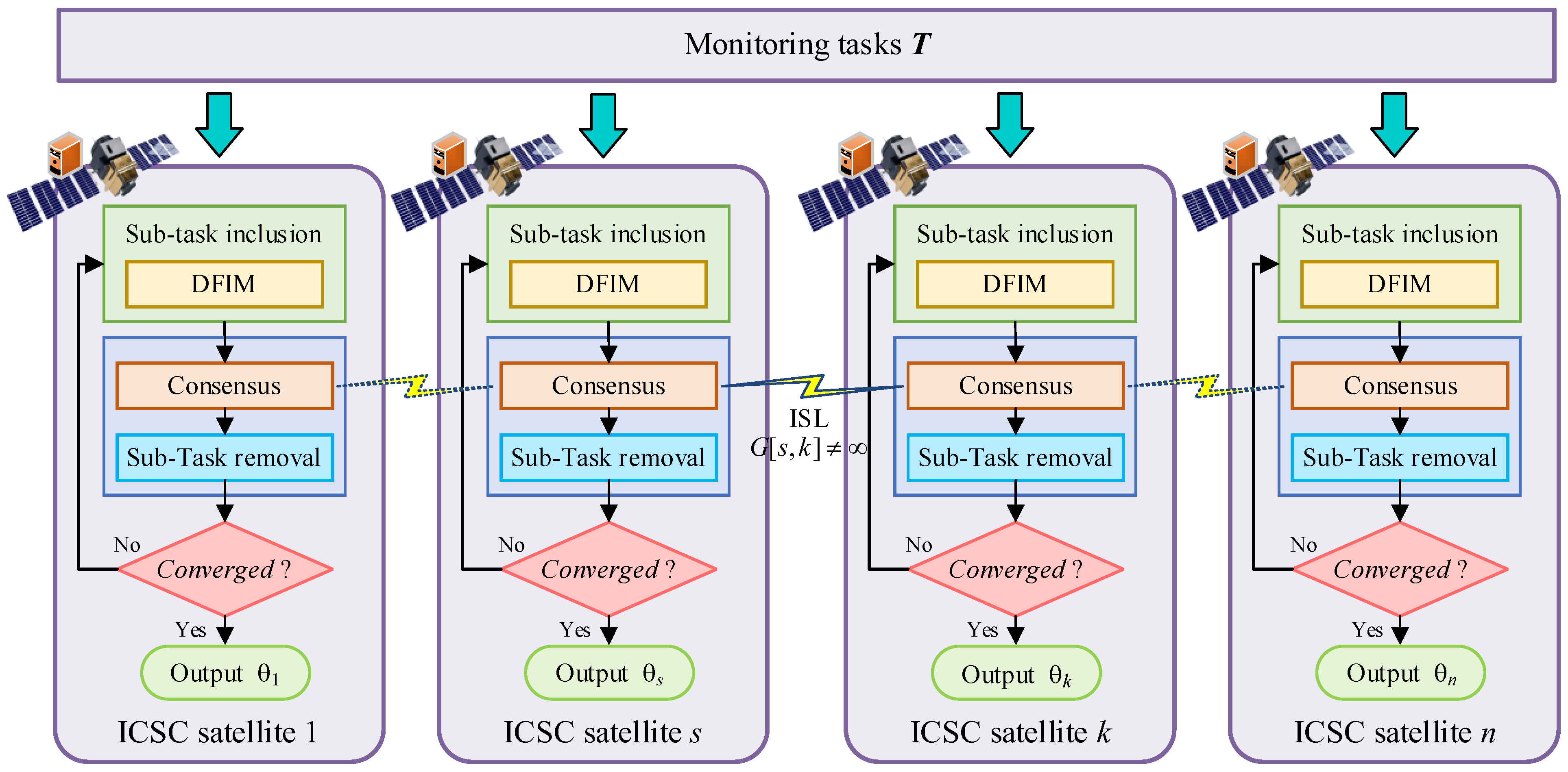
- To address this problem, we introduce a decentralized PI framework. Our method, the distributed deadlock-free task offloading (DDFTO) algorithm, operates on each satellite in parallel, utilizing local communication via ISLs. It alternates between stages of sub-task inclusion and consensus and sub-task removal on each satellite, continuing until all ICSC satellites converge on a common offloading assignment.
- To resolve undesired deadlocks in offloading assignments, a deadlock-free insertion mechanism (DFIM) is integrated into DDFTO. We demonstrate its effectiveness and computational complexity in resolving deadlocks.
2. Related Works
3. Problem Description and Formulation
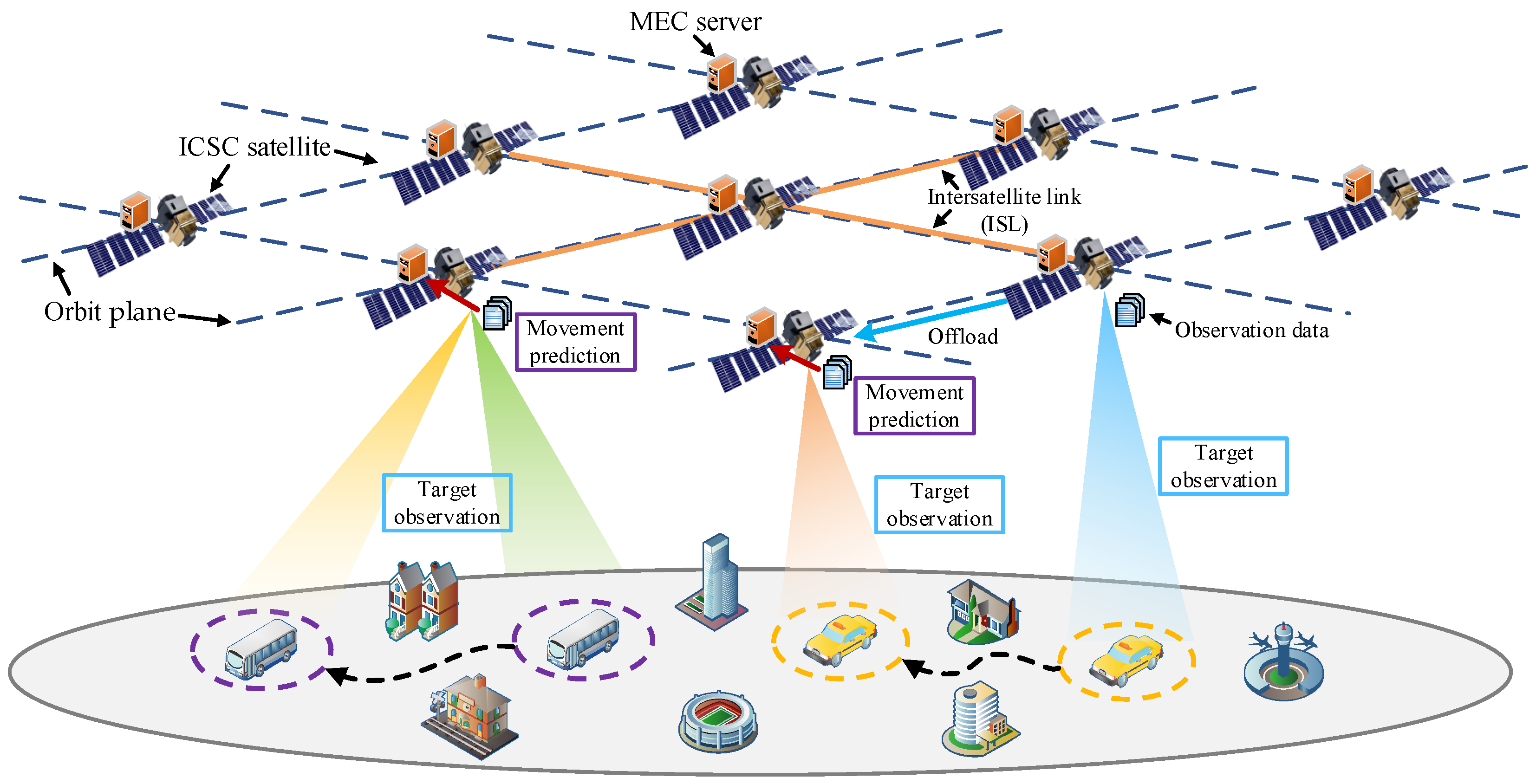
3.1. ICSC Satellites
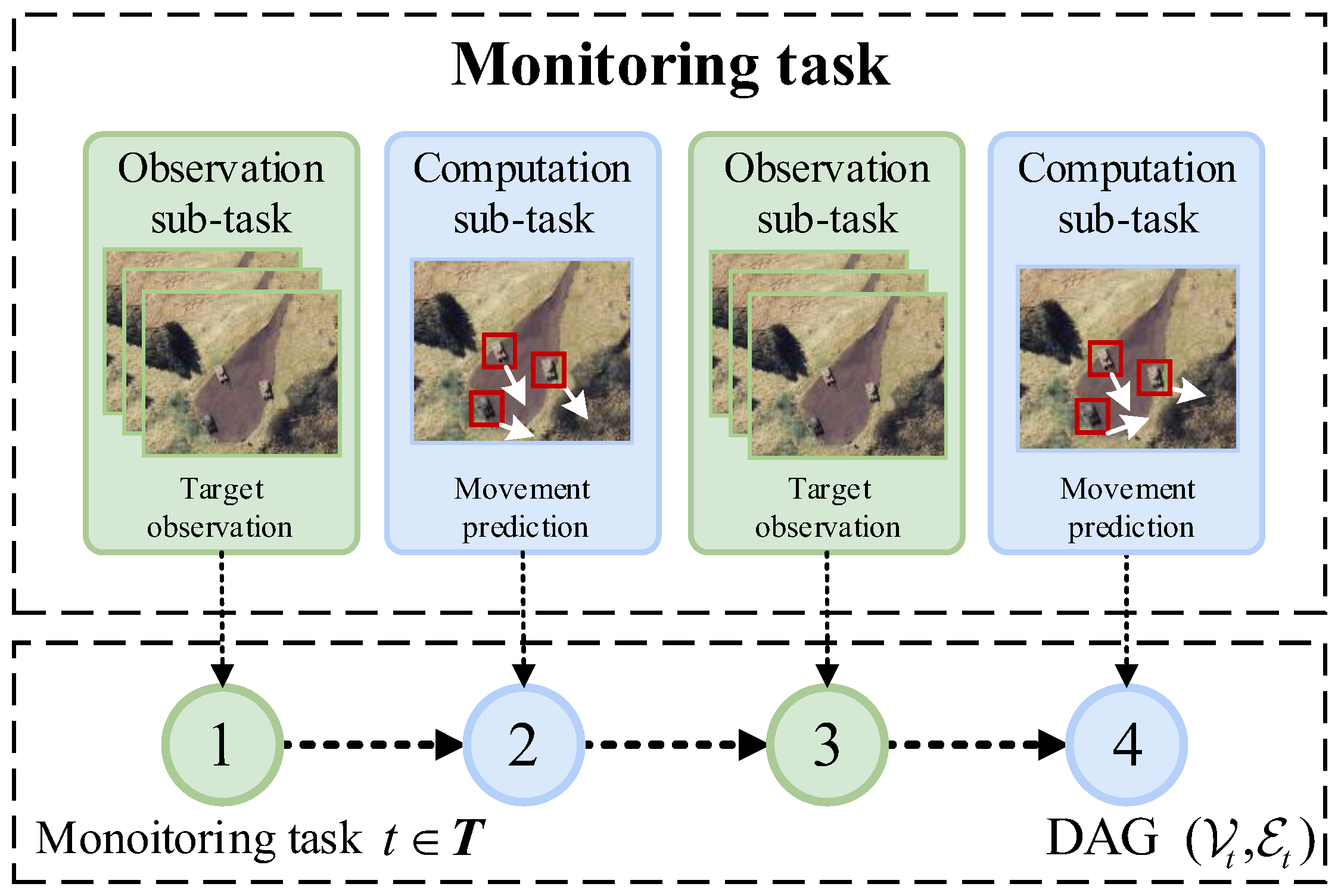
3.2. Monitoring Tasks and Sub-Tasks
3.3. Basic Constraints
3.4. Latency Model
- (1)
- vR: The time when all results of predecessors v are received by the assigned satellite of v.
- (2)
- vC: The time when the assigned satellite has completed the previous sub-task v.
- (3)
- vA: The time the assigned satellite turns to the required angle if v is an observation sub-task.
- (4)
- vE: The time when sub-task v is executed.
- (5)
- vF: The finish time of sub-task v.
3.5. Problem Formulation
4. The Distributed Deadlock-Free Task Offloading Algorithm
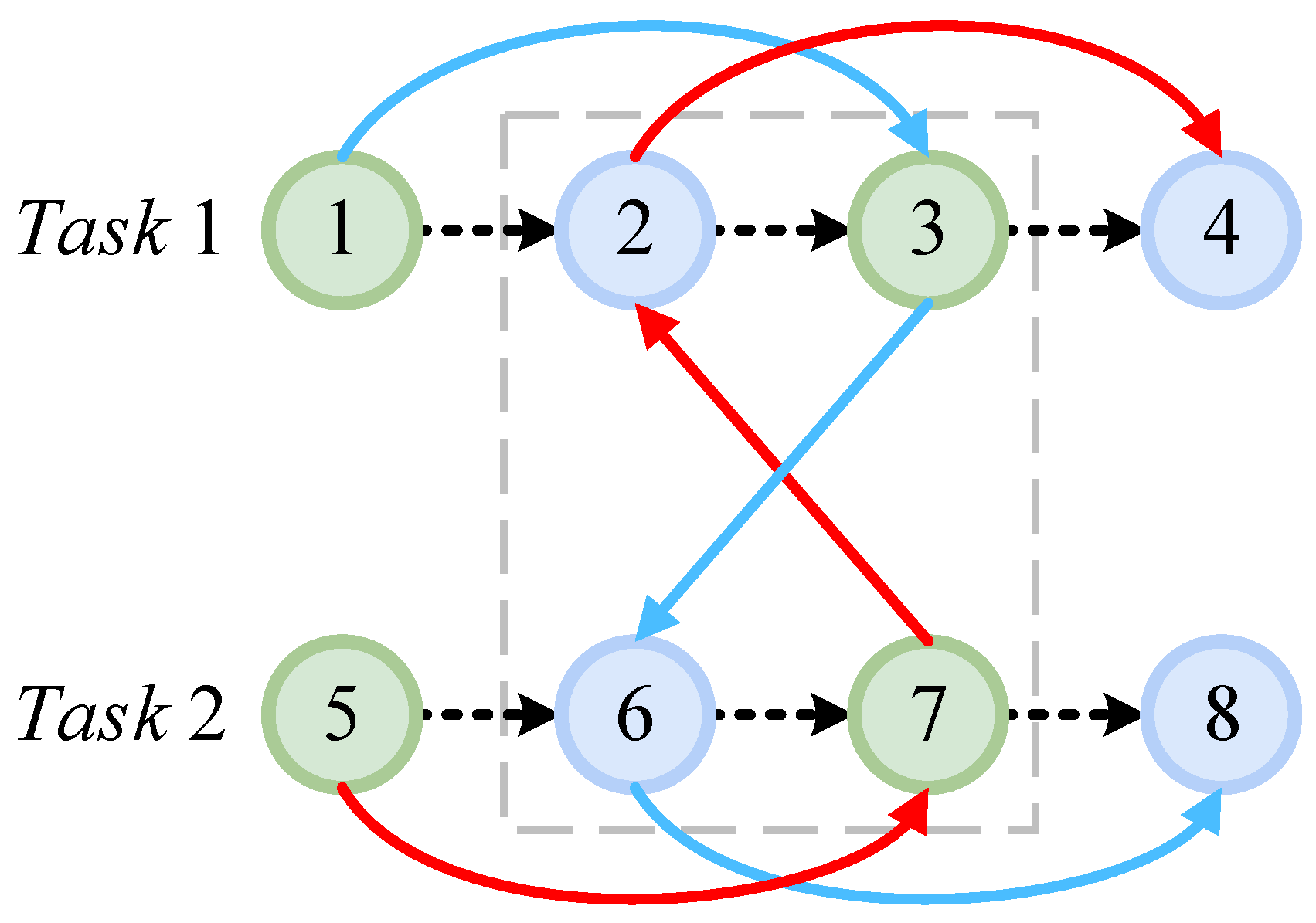
4.1. Basic Concept
- (1)
- Removal impact: for sub-task v ∈ θs, the removal impact (θ ⊖s v) indicates the variation of F(θ) after removing v from θs, and then we have the following:where θ ⊖s v represents the removal of sub-task v from θs ∈ θ. For any v ∉ θs, we let (θ ⊖s v) = ∞.
- (2)
- Inclusion impact: for sub-task v ∉ θs, the inclusion impact (θ ⊕s v) represents the minimum variation of F(θ) after inserting t into θs, and then we have the following:where θ ⊕s,p v indicates the inclusion of sub-task v into p-th position of θs. Similarly, we set (θ ⊕s v) = ∞ when sub-task v already exists in θs.
- (1)
- Rs = [Rs1, Rs2, …, Rs|V|]T records the latest removal impacts for sub-tasks in V. Initially, Rsv is set to (θ ⊖s v) for ∀ v ∈ θs, and Rsv = ∞ otherwise.
- (2)
- As = [As1, As2, …, As|V|]T records the assigned satellite of sub-tasks in V as believed by s. Initially, Asv = v for ∀ v ∈ θs, and Asv = ∅ otherwise.
- (3)
- Es = [Es1, Es2, …, Es|V|]T tracks the time when sub-tasks are executed by the assigned satellites as believed by s. Initially, Esv = for ∀ v ∈ θs, and Esv = ∅ otherwise.
- (4)
- Ps = [Ps1, Ps2, …, Psn]T is a vector where entry Psk is the timestamp that satellite s believes it received the latest information from satellite k. Initially, Psk = 0 for ∀ k ∈ S. During communication, Psk ∈ Ps is updated by the following rules:where sk is the time when s received information from k via ISL.
4.2. Sub-Task Inclusion
| Algorithm 1: Local Assignment Construction |
| Input: Sub-task sequence θs, vectors As = [As1, As2, …, As|V|]T and Es = [Es1, Es2, …, Es|V|]T. Output: Local assignment θ∗.
|
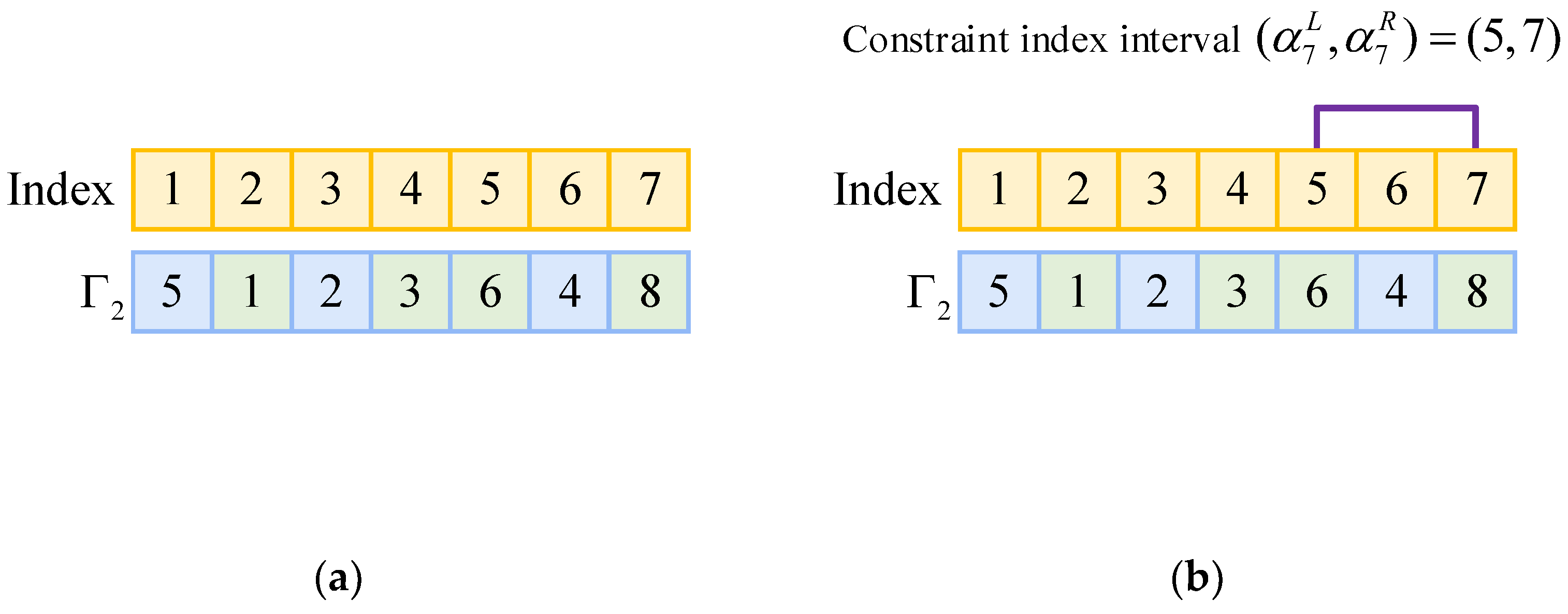
4.3. Deadlock-Free Insertion Mechanism
| Algorithm 2: Deadlock-Free Insertion Mechanism (DFIM) |
| Input: Sub-task sequence θs, vectors Es, candidate sub-task v. Output: Candidate insertion positions Φs,v.
|
| Algorithm 3: Sub-task inclusion |
| Input: Sub-task set V, sequence θs, vectors Rs, As, and Es. Output: New sequence θs′, new vectors Rs′, As′, and Es′.
|
4.4. Consensus and Sub-Task Removal
4.4.1. Consensus
- (1)
- Update: Set Rsv = Rkv, Asv = Akv, and Esv = Ekv.
- (2)
- Maintain: Set Rsv = Rsv, Asv = Asv, and Esv = Esv.
- (3)
- Reset: Swr Rsv = ∞, Asv = ∅, and Esv = ∅.
4.4.2. Sub-Task Removal
| Algorithm 4: Sub-task removal |
| Input: sequence θs, vectors Rs, As, and Es. Output: new sequence θs′, new vectors Rs′, As′, and Es′.
|
4.5. Framework of DDFTO
| Algorithm 5: Distributed Deadlock-Free Task Offloading (DDFTO) |
| Input: satellites S, monitoring tasks T, network topology matrix G. Output: task assignment θ.
|
4.6. Convergence and Complexity Analysis
5. Computational Experiments
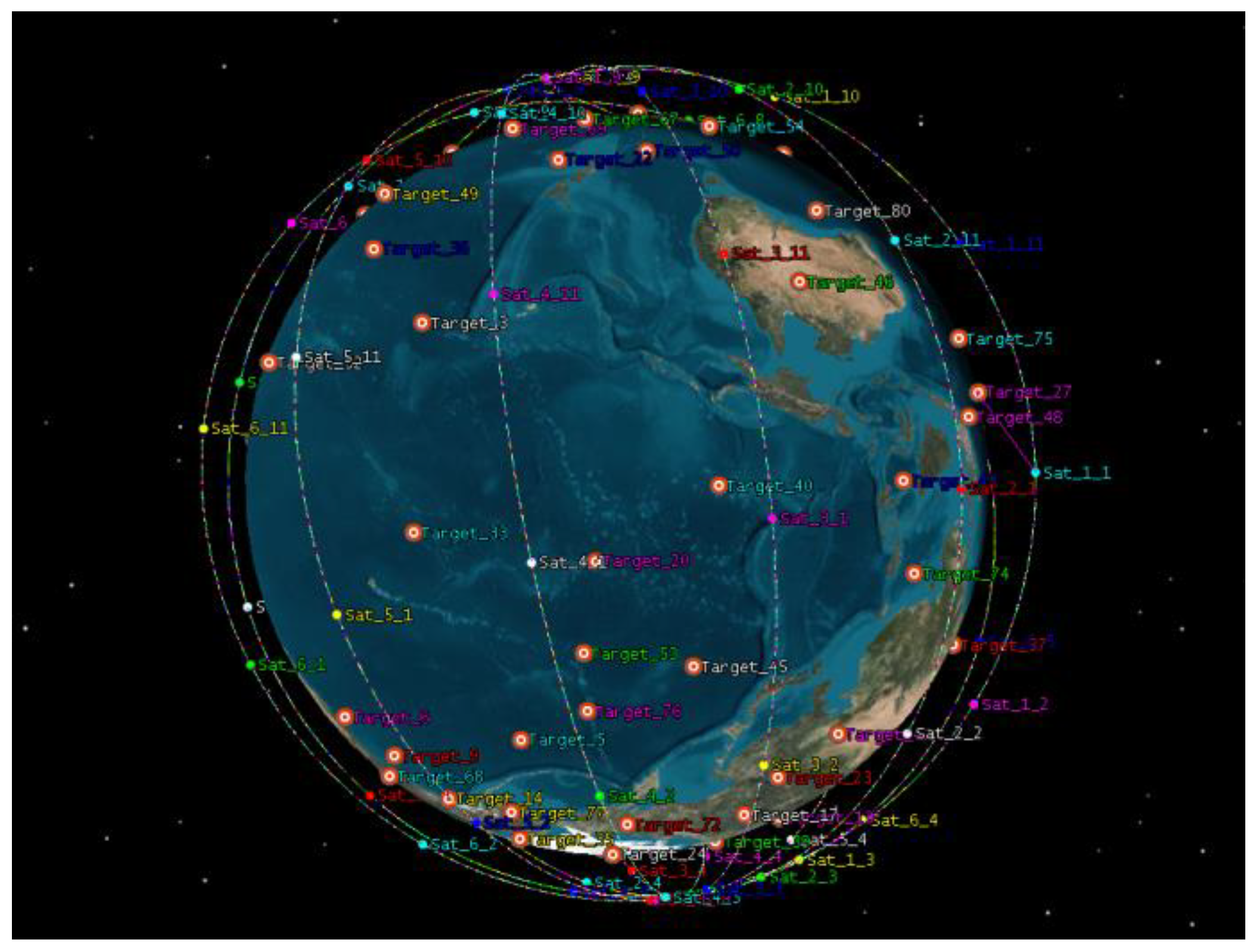
5.1. Experimental Setup
- (1)
- DALEOS [21]: A distributed algorithm that uses heuristics to select a controller satellite for each monitoring task and a flooding mechanism to assign satellites for each sub-task. This competitor retains its original design but adopts DFIM to handle deadlocks.
- (2)
- Local Execution: Each monitoring task is performed by the nearest visible ICSC satellite without any inter-satellite coordination.
- (3)
- Random Offloading: Sub-tasks are sorted based on their data dependencies, and ICSC satellites are randomly selected for them.
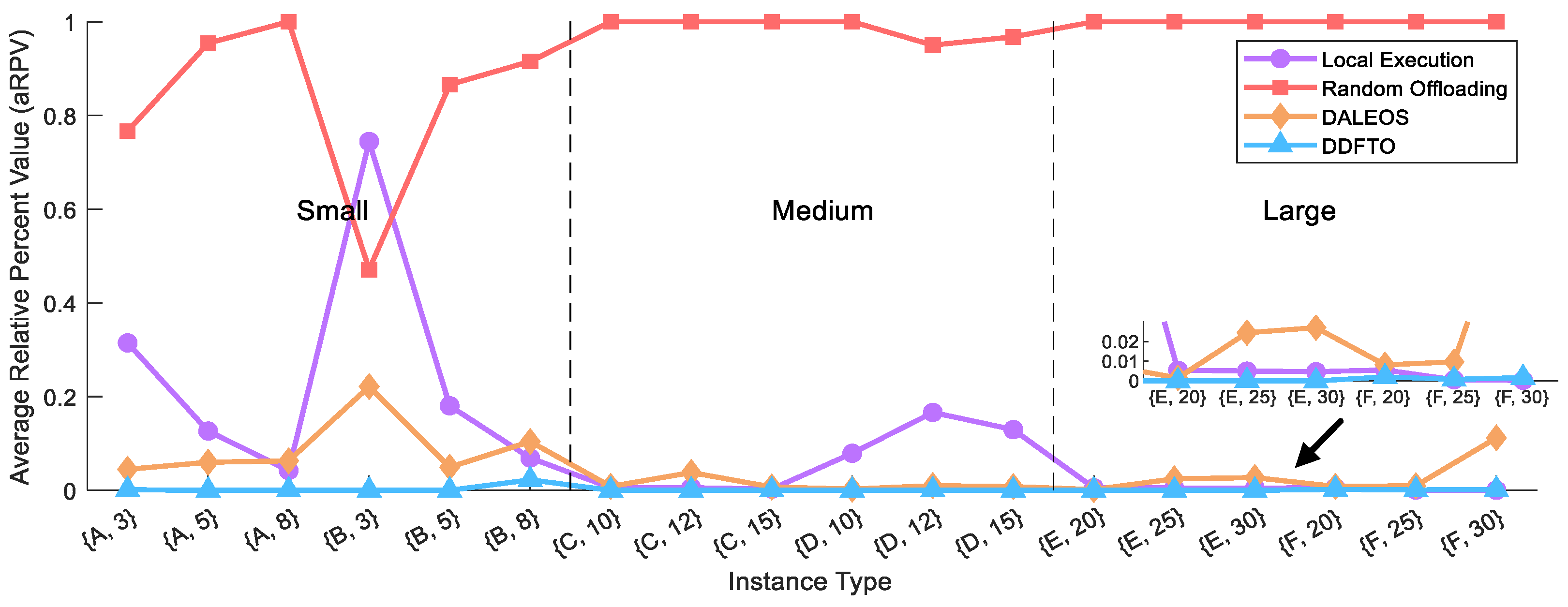
- Relative Percent Value (RPV): This measures the relative percentage value of F(θ) compared to other algorithms.Here, F(θ) is the fitness of an algorithm for a test instance, while Fworst and Fbest are the worst and best fitness values obtained using all algorithms for the same instance. A lower RPV indicates better performance, eliminating the influence of different test instances.
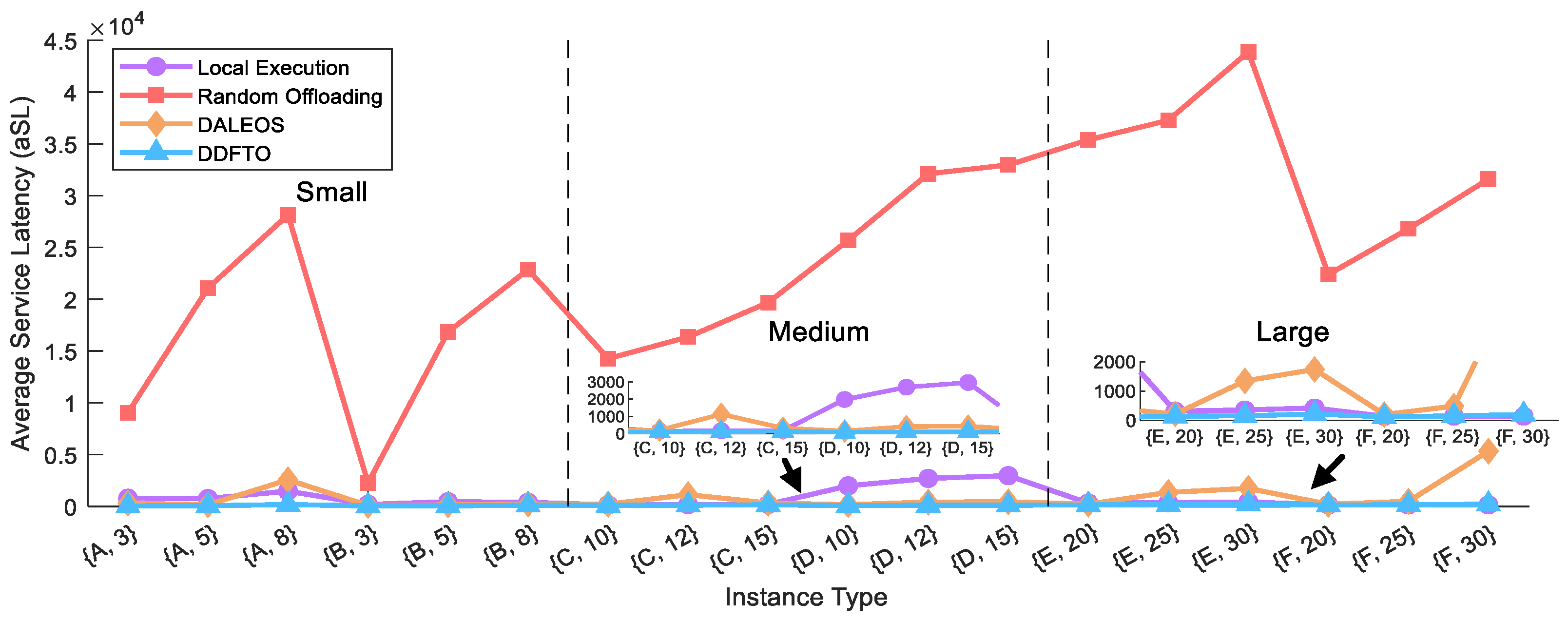
- Service Latency (SL): This refers to the performance index F1, which is the maximum completion time for all tasks and is calculated using Formula (12).
- Energy Consumption (EC): This refers to the performance index F2, which is the energy consumption for performing all sub-tasks and is calculated using Equation (13).
5.2. Deadlock Statistics
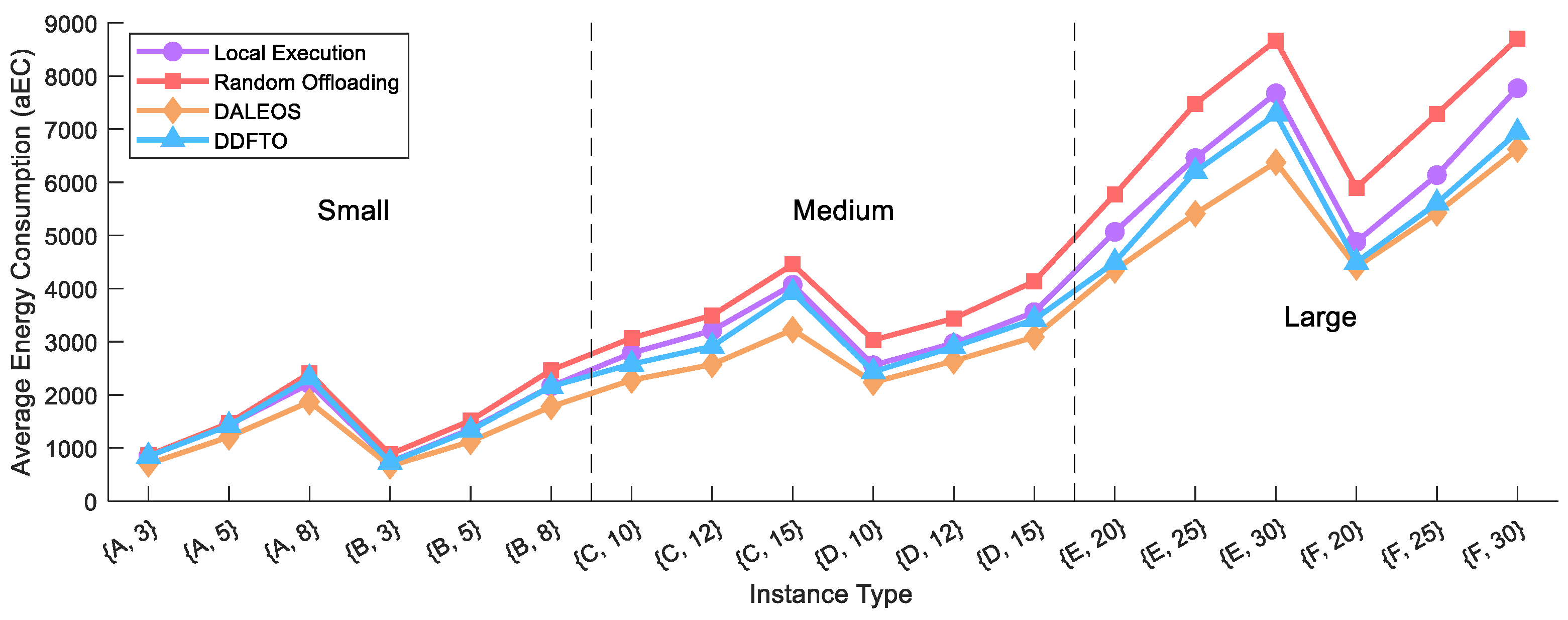
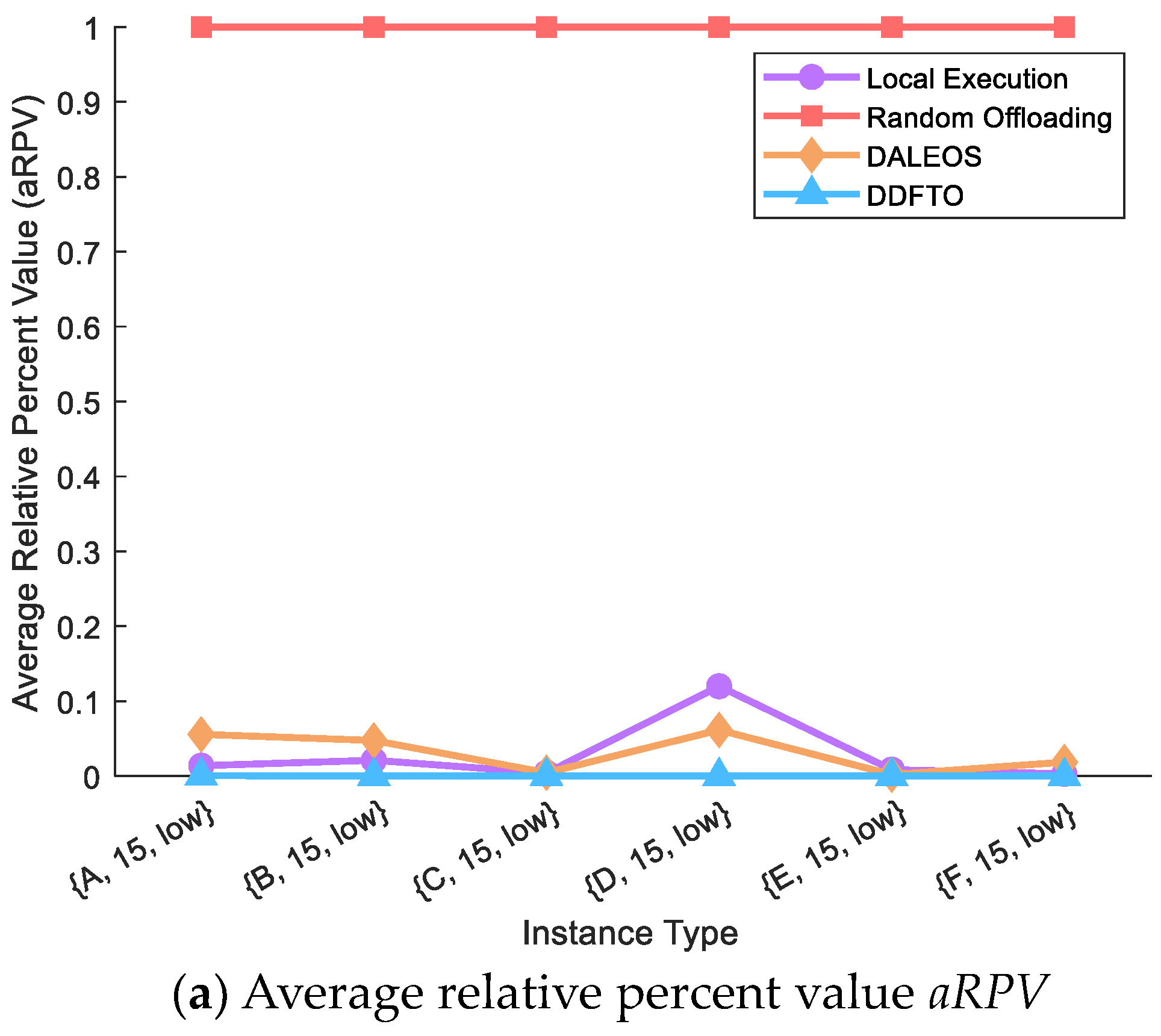
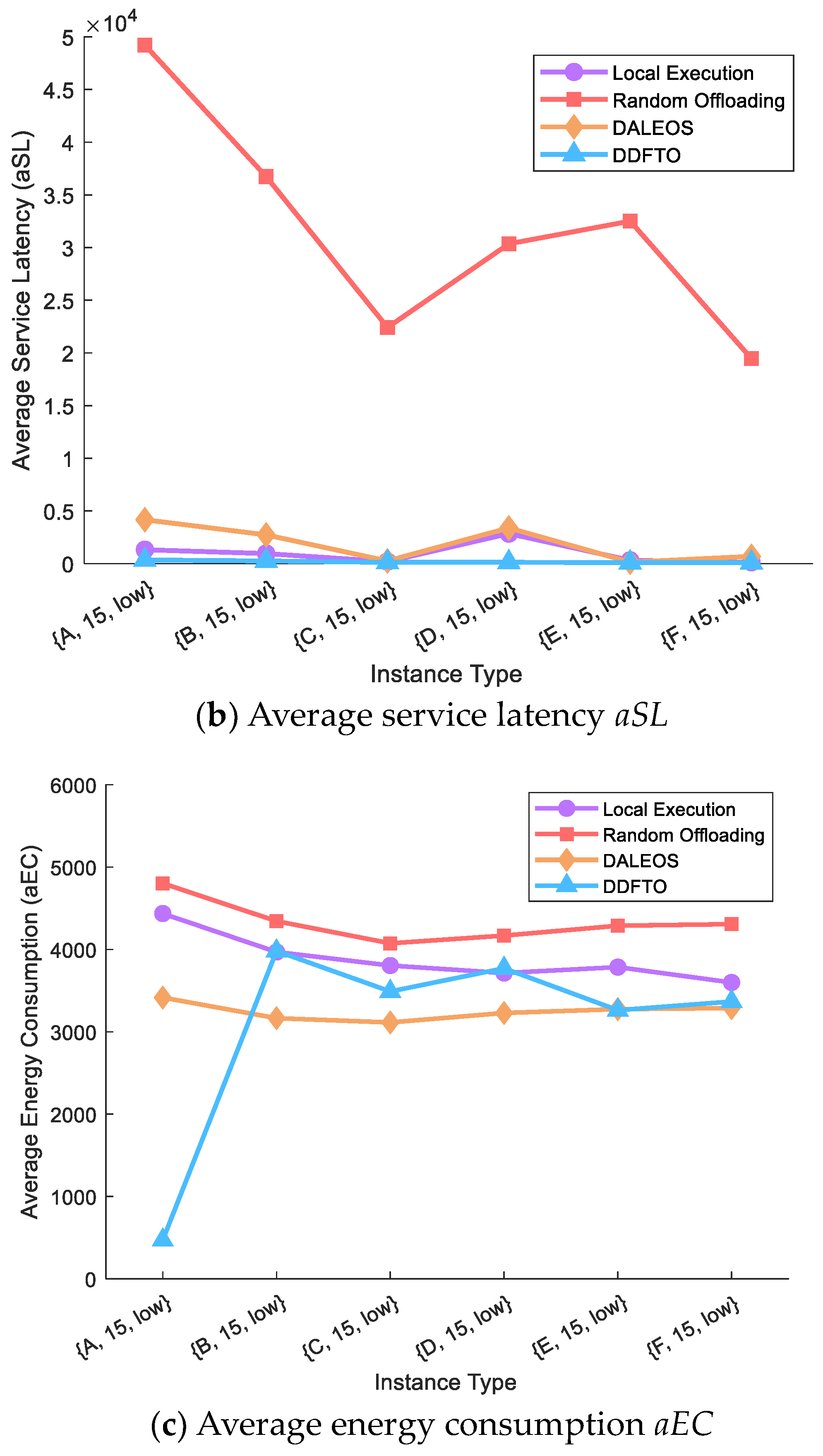
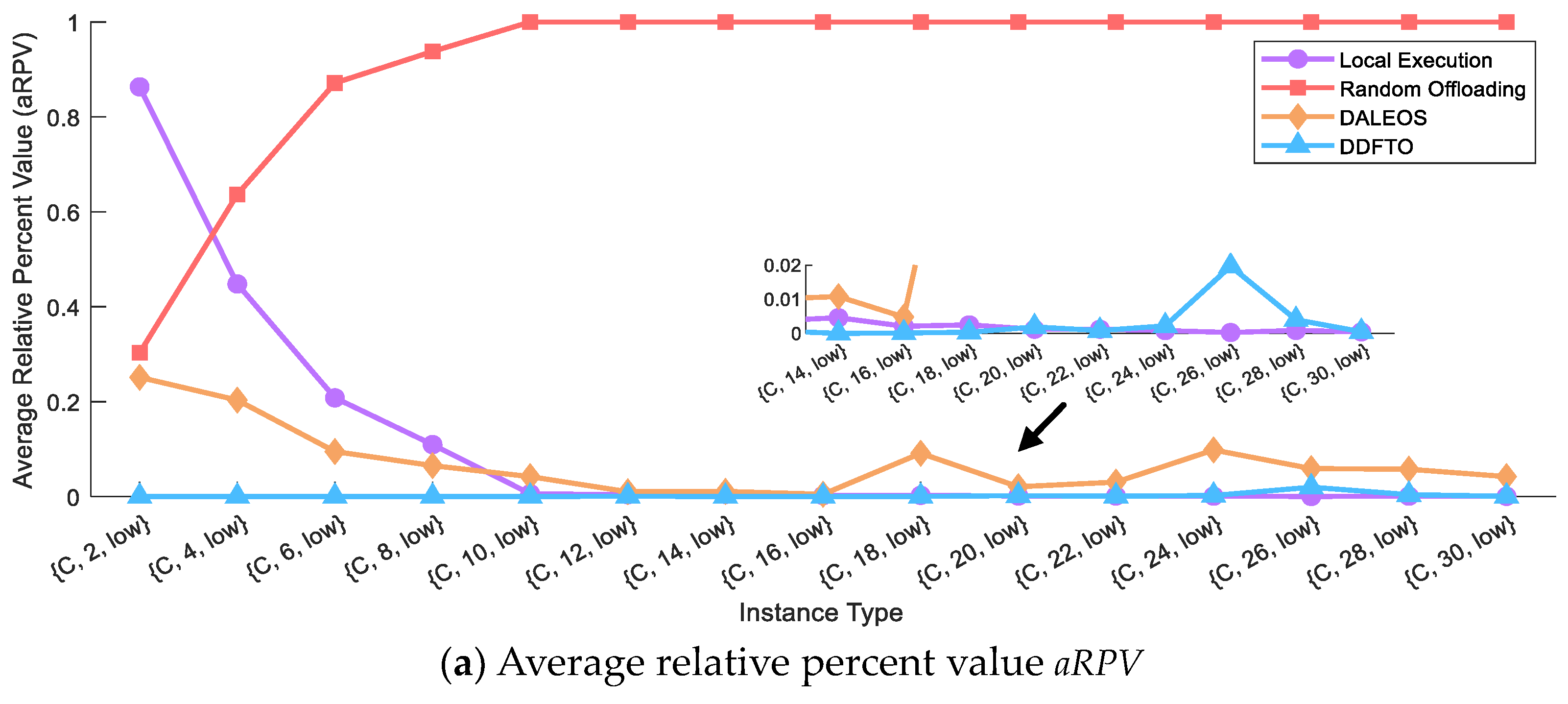
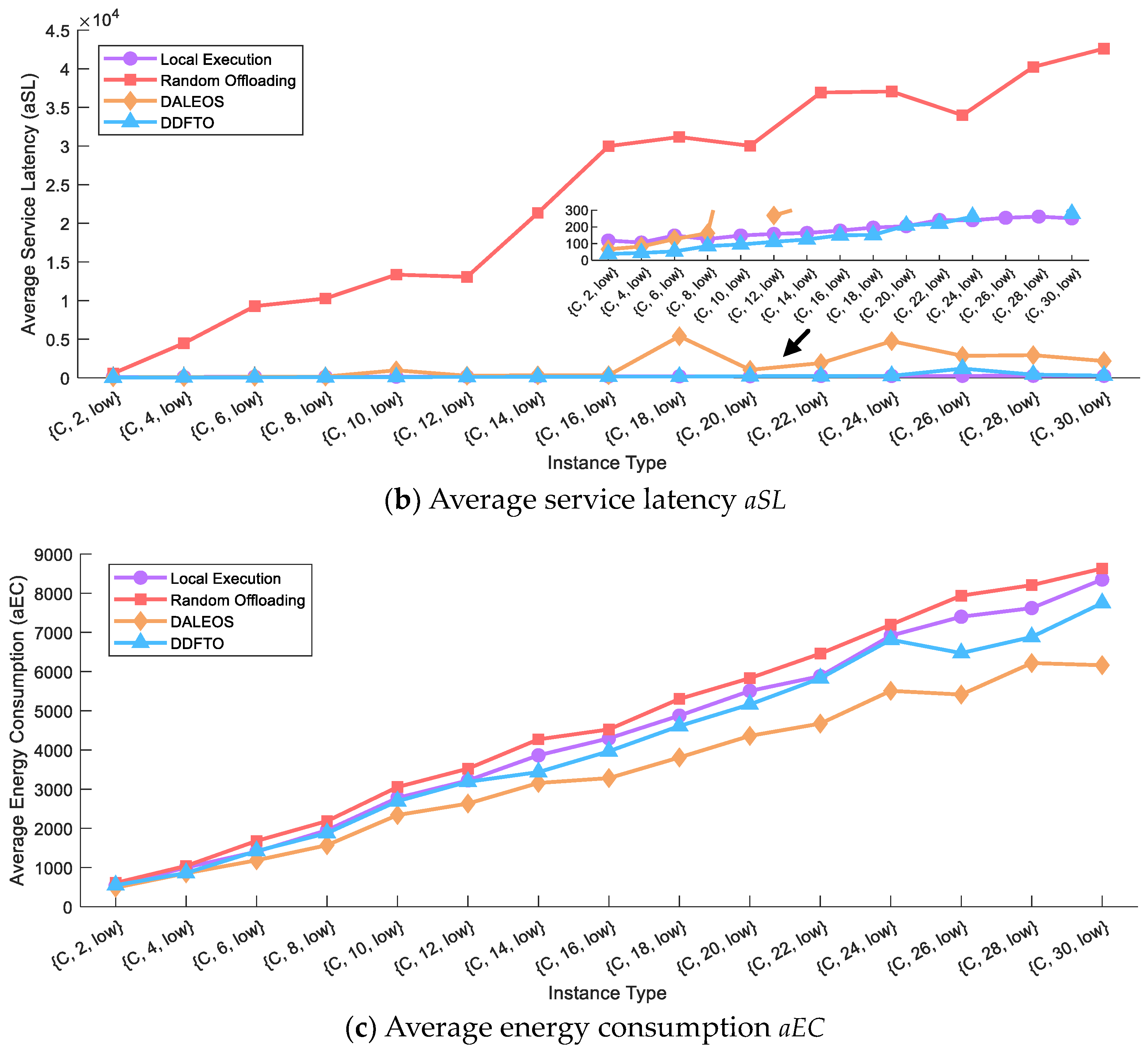
5.3. Comparison with Existing Algorithms
6. Discussion
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Zhao, Q.; Yu, L.; Du, Z.; Peng, D.; Hao, P.; Zhang, Y.; Gong, P. An overview of the applications of earth observation satellite data: Impacts and future trends. Remote Sens. 2022, 14, 1863. [Google Scholar] [CrossRef]
- Ramapriyan, H.K. The role and evolution of NASA’s Earth science data systems. In Proceedings of the Institute of Electrical and Electronic Engineers (IEEE) EDS/CAS Chapter Meeting, Camarillo, CA, USA, 19 August 2015. No. GSFC-E-DAA-TN24713. [Google Scholar]
- Çelikbilek, K.; Saleem, Z.; Ferre, R.M.; Praks, J.; Lohan, E.S. Survey on optimization methods for LEO-satellite-based networks with applications in future autonomous transportation. Sensors 2022, 22, 1421. [Google Scholar] [CrossRef] [PubMed]
- Ji, S.; Zhou, D.; Sheng, M.; Li, J. Mega satellite constellation system optimization: From a network control structure perspective. IEEE Trans. Wirel. Commun. 2021, 21, 913–927. [Google Scholar] [CrossRef]
- Leyva-Mayorga, I.; Martinez-Gost, M.; Moretti, M.; Pérez-Neira, A.; Vázquez, M.; Popovski, P.; Soret, B. Satellite edge computing for real-time and very-high resolution earth observation. IEEE Trans. Commun. 2023, 71, 6180–6194. [Google Scholar] [CrossRef]
- Xiang, S.; Liang, Q.; Tang, P. Task-Oriented Compression Framework for Remote Sensing Satellite Data Transmission. IEEE Trans. Ind. Inform. 2024, 20, 3487–3496. [Google Scholar] [CrossRef]
- Mamun, A.; Jia, X.; Ryan, M. Adaptive data compression for efficient sequential transmission and change updating of remote sensing images. In Proceedings of the 2009 IEEE International Geoscience and Remote Sensing Symposium, Cape Town, South Africa, 12–17 July 2009; Volume 4, pp. IV–498. [Google Scholar]
- Mateo-Garcia, G.; Veitch-Michaelis, J.; Smith, L.; Oprea, S.V.; Schumann, G.; Gal, Y.; Baydin, A.G.; Backes, D. Towards global flood mapping onboard low cost satellites with machine learning. Sci. Rep. 2021, 11, 7249. [Google Scholar] [CrossRef] [PubMed]
- Qi, Q.; Chen, X.; Khalili, A.; Zhong, C.; Zhang, Z.; Ng, D.W.K. Integrating sensing, computing, and communication in 6G wireless networks: Design and optimization. IEEE Trans. Commun. 2022, 70, 6212–6227. [Google Scholar] [CrossRef]
- Zuo, Y.; Yue, M.; Yang, H.; Wu, L.; Yuan, X. Integrating Communication, Sensing and Computing in Satellite Internet of Things: Challenges and Opportunities. IEEE Wirel. Commun. 2024, 31, 332–338. [Google Scholar] [CrossRef]
- Giuffrida, G.; Fanucci, L.; Meoni, G.; Batic, M.; Buckley, L.; Dunne, A.; van Dijk, C.; Esposito, M.; Hefele, J.; Vercruyssen, N.; et al. The Φ-Sat-1 mission: The first on-board deep neural network demonstrator for satellite earth observation. IEEE Trans. Geosci. Remote Sens. 2021, 60, 1–14. [Google Scholar] [CrossRef]
- Bentoutou, Y. A real time EDAC system for applications onboard earth observation small satellites. IEEE Trans. Aerosp. Electron. Syst. 2012, 48, 648–657. [Google Scholar] [CrossRef]
- Dolce, F.; Di Domizio, D.; Bruckert, D.; Rodríguez, A.; Patrono, A. Earth observation for security and defense. In Handbook of Space Security: Policies, Applications and Programs; Springer: Berlin/Heidelberg, Germany, 2020; pp. 705–731. [Google Scholar]
- Han, X.; Yang, M.; Wang, S.; Chao, T. Continuous monitoring scheduling for moving targets by Earth observation satellites. Aerosp. Sci. Technol. 2023, 140, 108422. [Google Scholar] [CrossRef]
- Selva, D.; Krejci, D. A survey and assessment of the capabilities of Cubesats for Earth observation. Acta Astronaut. 2012, 74, 50–68. [Google Scholar] [CrossRef]
- Coffman, E.G.; Elphick, M.; Shoshani, A. System deadlocks. ACM Comput. Surv. CSUR 1971, 3, 67–78. [Google Scholar] [CrossRef]
- He, Y.; Chen, Y.; Lu, J.; Chen, C.; Wu, G. Scheduling multiple agile earth observation satellites with an edge computing framework and a constructive heuristic algorithm. J. Syst. Archit. 2019, 95, 55–66. [Google Scholar] [CrossRef]
- Valente, F.; Eramo, V.; Lavacca, F.G. Optimal bandwidth and computing resource allocation in low earth orbit satellite constellation for earth observation applications. Comput. Netw. 2023, 232, 109849. [Google Scholar] [CrossRef]
- Zhu, X.; Wang, H.; Yang, Z.; Pham, Q.V. Time-division based integrated sensing, communication, and computing in integrated satellite-terrestrial networks. Digit. Signal Process. 2023, 143, 104262. [Google Scholar] [CrossRef]
- Gost, M.M.; Leyva-Mayorga, I.; Pérez-Neira, A.; Vázquez, M.Á.; Soret, B.; Moretti, M. Edge computing and communication for energy-efficient earth surveillance with LEO satellites. In Proceedings of the 2022 IEEE International Conference on Communications Workshops (ICC Workshops), Seoul, Republic of Korea, 16–20 May 2022; pp. 556–561. [Google Scholar]
- Biswas, S.; Paul, H.S. DALEOS: Distributed scheduling for earth observation Data Analytics in LEO Satellites. In Proceedings of the 2024 IEEE International Conference on Pervasive Computing and Communications Workshops and other Affiliated Events (PerCom Workshops), Biarritz, France, 11–15 March 2024; pp. 209–214. [Google Scholar]
- Zhu, B.; Lin, S.; Zhu, Y.; Wang, X. Collaborative Hyperspectral Image Processing Using Satellite Edge Computing. IEEE Trans. Mob. Comput. 2024, 23, 2241–2253. [Google Scholar] [CrossRef]
- Mateo-Garcia, G.; Veitch-Michaelis, J.; Purcell, C.; Longepe, N.; Reid, S.; Anlind, A.; Bruhn, F.; Parr, J.; Mathieu, P.P. In-orbit demonstration of a re-trainable machine learning payload for processing optical imagery. Sci. Rep. 2023, 13, 10391. [Google Scholar] [CrossRef]
- Furano, G.; Meoni, G.; Dunne, A.; Moloney, D.; Ferlet-Cavrois, V.; Tavoularis, A.; Byrne, J.; Buckley, L.; Psarakis, M.; Voss, K.-O.; et al. Towards the use of artificial intelligence on the edge in space systems: Challenges and opportunities. IEEE Aerosp. Electron. Syst. Mag. 2020, 35, 44–56. [Google Scholar] [CrossRef]
- Bui, T.-A.; Lee, P.-J.; Lum, K.-Y.; Loh, C.; Tan, K. Deep learning for landslide recognition in satellite architecture. IEEE Access 2020, 8, 143665–143678. [Google Scholar] [CrossRef]
- Shi, F.; Qiu, F.; Li, X.; Zhong, R.; Yang, C.; Tang, Y. Detecting and tracking moving airplanes from space based on normalized frame difference labeling and improved similarity measures. Remote Sens. 2020, 12, 3589. [Google Scholar] [CrossRef]
- Turner, J.; Meng, Q.; Schaefer, G.; Whitbrook, A.; Soltoggio, A. Distributed task rescheduling with time constraints for the optimization of total task allocations in a multirobot system. IEEE Trans. Cybern. 2017, 48, 2583–2597. [Google Scholar] [CrossRef] [PubMed]
- Zhao, W.; Meng, Q.; Chung, P.W. A heuristic distributed task allocation method for multivehicle multitask problems and its application to search and rescue scenario. IEEE Trans. Cybern. 2015, 46, 902–915. [Google Scholar] [CrossRef] [PubMed]
- Zhang, R.; Feng, Y.; Yang, Y.; Li, X.; Li, H. Dynamic Delay-Sensitive Observation-Data-Processing Task Offloading for Satellite Edge Computing: A Fully-Decentralized Approach. Remote Sens. 2024, 16, 2184. [Google Scholar] [CrossRef]
- Wu, Q.; Pan, J.; Wang, M. Dynamic Task Planning Method for Multi-Source Remote Sensing Satellite Cooperative Observation in Complex Scenarios. Remote Sens. 2024, 16, 657. [Google Scholar] [CrossRef]
- Peng, G.; Song, G.; He, Y.; Yu, J.; Xiang, S.; Xing, L.; Vansteenwegen, P. Solving the agile earth observation satellite scheduling problem with time-dependent transition times. IEEE Trans. Syst. Man Cybern. Syst. 2020, 52, 1614–1625. [Google Scholar] [CrossRef]
- Cao, X.; Li, Y.; Xiong, X.; Wang, J. Dynamic routings in satellite networks: An overview. Sensors 2022, 22, 4552. [Google Scholar] [CrossRef]
- Zhang, H.; Liu, R.; Kaushik, A.; Gao, X. Satellite edge computing with collaborative computation offloading: An intelligent deep deterministic policy gradient approach. IEEE Internet Things J. 2023, 10, 9092–9107. [Google Scholar] [CrossRef]
- Choi, H.L.; Brunet, L.; How, J.P. Consensus-based decentralized auctions for robust task allocation. IEEE Trans. Robot. 2009, 25, 912–926. [Google Scholar] [CrossRef]
- Cui, G.; Duan, P.; Xu, L.; Wang, W. Latency optimization for hybrid GEO–LEO satellite-assisted IoT networks. IEEE Internet Things J. 2022, 10, 6286–6297. [Google Scholar] [CrossRef]
- Chai, F.; Zhang, Q.; Yao, H.; Xin, X.; Gao, R.; Guizani, M. Joint multi-task offloading and resource allocation for mobile edge computing systems in satellite IoT. IEEE Trans. Veh. Technol. 2023, 72, 7783–7795. [Google Scholar] [CrossRef]
- Zhang, Y.; Chen, C.; Liu, L.; Lan, D.; Jiang, H.; Wan, S. Aerial edge computing on orbit: A task offloading and allocation scheme. IEEE Trans. Netw. Sci. Eng. 2022, 10, 275–285. [Google Scholar] [CrossRef]
- Chen, X.; Zhang, P.; Du, G.; Li, F. A distributed method for dynamic multi-robot task allocation problems with critical time constraints. Robot. Auton. Syst. 2019, 118, 31–46. [Google Scholar] [CrossRef]


| Notation | Description |
|---|---|
| n | Number of ICSC satellites. |
| m | Number of monitoring tasks. |
| S | Set of ICSC satellites. |
| T | Set of monitoring tasks. |
| V | Set of sub-tasks. |
| Cs | Computing capacity of ICSC satellites. |
| G | Network topology matrix. |
| (t, t) | Directed acyclic graph of monitoring task t, where t collects sub-tasks in t, and t denotes dependencies among them. |
| v | Predecessors of sub-task v. |
| v | Successors of sub-task v. |
| <ξv, ρv, dvI, dvO> | Parameter tuple characterizing each sub-task v, where ξv refers to the workload of v, ρv represents the imaging time of v, dvI refers to the input data of v, and dvO represents the output. |
| TWvs | Visible time windows for observation sub-task v and satellite s. |
| θ = {θ1, θ2, …, θn} | Offloading assignment for ICSC satellites. |
| (θ ⊖s v) | Removal impact, indicating the variation of F(θ) after removing v from θs. |
| (θ ⊕s v) | Inclusion impact, indicating the minimum variation of F(θ) after inserting t into θs. |
| Rs = [Rs1, Rs2, …, Rs|V|]T | Vector of removal impacts for sub-tasks on satellite s. |
| As = [As1, As2, …, As|V|]T | Vector of considered assigned satellite for sub-tasks on satellite s. |
| Es = [Es1, Es2, …, Es|V|]T | Vector tracking the time when sub-tasks are executed believed by satellite s. |
| Ps = [Ps1, Ps2, …, Psn]T | Vector indicating the latest timestamp of satellite s. |
| Γs | Pending removal tasks on satellite s. |
| Φs,v | Candidate insertion positions for sub-task v on satellite s. |
| Value of Akv in Sending Satellite k | Value of Asv in Receiving Satellite s | Actions Adopted by s |
|---|---|---|
| k | s | if Rkv < Rsv → Update |
| k | Update | |
| a ∉ {k, s} | if Pka > Psa or Rkv < Rsv → Update | |
| ∅ | Update | |
| s | s | Maintain |
| k | Reset | |
| a ∉ {k, s} | if Pka > Psa → Reset | |
| ∅ | Maintain | |
| a ∉ {k, s} | s | if Pka > Psa and Rkv < Rsv → Update |
| k | if Pka > Psa → Update else → Reset | |
| a | Pka > Psa → Update | |
| b ∉ {k, s, a} | if Pka > Psa and Pkb > Psb → Update if Pka > Psa and Rkv < Rsv → Update if Pkb > Psb and Pka < Psa → Reset | |
| ∅ | if Pka > Psa → Update | |
| ∅ | s | Maintain |
| k | Update | |
| a ∉ {k, s} | if Pka > Psa → Update | |
| ∅ | Maintain |
| Constellation | Altitude (km) | Inclination (deg) | Planes | Satellites (n) |
|---|---|---|---|---|
| A | 5000 | 138.58 | 2 | 6 |
| B | 5000 | 138.58 | 3 | 9 |
| C | 3000 | 112.42 | 4 | 16 |
| D | 480 | 97.33 | 3 | 24 |
| E | 550 | 97.59 | 6 | 36 |
| F | 780 | 98.52 | 6 | 66 |
| Instance Type | Constellations | Target Number | Target Density | Combination Number |
|---|---|---|---|---|
| Small | A, B | 3, 5, 8 | high, low | 2 × 3 × 2 = 12 |
| Medium | C, D | 10, 12, 15 | high, low | 2 × 3 × 2 = 12 |
| Large | E, F | 20, 25, 30 | high, low | 2 × 3 × 2 = 12 |
| Parameters | Default Values |
|---|---|
| Computing capacity of satellites Cs | 3~5 GHz |
| Number of sub-tasks |Vt| | 2~4 |
| Workload of sub-tasks ξv | 1~1.5 Kcycle/bit |
| Imaging time of sub-tasks ρv | 10~20 s |
| Input data size of sub-tasks dvI | 50~100 Mbit |
| Output data size of sub-tasks dvO | 50~100 Mbit |
| Rate of ISL RISL | 100 Mbps |
| Transition power ηx | 1 w |
| Angle transition power ηa | 0.2 w |
| Observation power ηo | 1 w |
| Effective capacitance coefficient κ | 10−28 |
| Instance Type | Total Assignment Number | Deadlock-Free Assignments | Deadlock Rate | Deadlock-Free Assignments (Using DFIM) | Deadlock Rate (Using DFIM) |
|---|---|---|---|---|---|
| {A, 3, high} | 10,000 | 4363 | 56.37% | 10,000 | 0% |
| {A, 3, low} | 10,000 | 5464 | 45.36% | 10,000 | 0% |
| {A, 5, high} | 10,000 | 2544 | 74.56% | 10,000 | 0% |
| {A, 5, low} | 10,000 | 2108 | 78.92% | 10,000 | 0% |
| {A, 8, high} | 10,000 | 510 | 94.90% | 10,000 | 0% |
| {A, 8, low} | 10,000 | 786 | 92.14% | 10,000 | 0% |
| {B, 3, high} | 10,000 | 6488 | 35.12% | 10,000 | 0% |
| {B, 3, low} | 10,000 | 6431 | 35.69% | 10,000 | 0% |
| {B, 5, high} | 10,000 | 4656 | 53.44% | 10,000 | 0% |
| {B, 5, low} | 10,000 | 3660 | 63.40% | 10,000 | 0% |
| {B, 8, high} | 10,000 | 1995 | 80.05% | 10,000 | 0% |
| {B, 8, low} | 10,000 | 1760 | 82.40% | 10,000 | 0% |
| Instance Type | Total Assignment Number | Deadlock-Free Assignments | Deadlock Rate | Deadlock-Free Assignments (Using DFIM) | Deadlock Rate (Using DFIM) |
|---|---|---|---|---|---|
| {C, 10, high} | 10,000 | 2248 | 77.52% | 10,000 | 0% |
| {C, 10, low} | 10,000 | 2782 | 72.18% | 10,000 | 0% |
| {C, 12, high} | 10,000 | 1780 | 82.20% | 10,000 | 0% |
| {C, 12, low} | 10,000 | 1887 | 81.13% | 10,000 | 0% |
| {C, 15, high} | 10,000 | 1117 | 88.83% | 10,000 | 0% |
| {C, 15, low} | 10,000 | 1244 | 87.56% | 10,000 | 0% |
| {D, 10, high} | 10,000 | 4703 | 52.97% | 10,000 | 0% |
| {D, 10, low} | 10,000 | 4489 | 55.11% | 10,000 | 0% |
| {D, 12, high} | 10,000 | 3738 | 62.62% | 10,000 | 0% |
| {D, 12, low} | 10,000 | 3768 | 62.32% | 10,000 | 0% |
| {D, 15, high} | 10,000 | 2680 | 73.20% | 10,000 | 0% |
| {D, 15, low} | 10,000 | 3000 | 70.00% | 10,000 | 0% |
| Instance Type | Total Assignment Number | Deadlock-Free Assignments | Deadlock Rate | Deadlock-Free Assignments (Using DFIM) | Deadlock Rate (Using DFIM) |
|---|---|---|---|---|---|
| {E, 20, high} | 10,000 | 3009 | 69.91% | 10,000 | 0% |
| {E, 20, low} | 10,000 | 2340 | 76.60% | 10,000 | 0% |
| {E, 25, high} | 10,000 | 1866 | 81.34% | 10,000 | 0% |
| {E, 25, low} | 10,000 | 1753 | 82.47% | 10,000 | 0% |
| {E, 30, high} | 10,000 | 816 | 91.84% | 10,000 | 0% |
| {E, 30, low} | 10,000 | 659 | 93.41% | 10,000 | 0% |
| {F, 20, high} | 10,000 | 5616 | 43.84% | 10,000 | 0% |
| {F, 20, low} | 10,000 | 5385 | 46.15% | 10,000 | 0% |
| {F, 25, high} | 10,000 | 4902 | 50.98% | 10,000 | 0% |
| {F, 25, low} | 10,000 | 4940 | 50.60% | 10,000 | 0% |
| {F, 30, high} | 10,000 | 3803 | 61.97% | 10,000 | 0% |
| {F, 30, low} | 10,000 | 3853 | 61.47% | 10,000 | 0% |
| Instance Type | Local Execution | Random Offloading | DALEOS | DDFTO | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| aRPV | aSL | aEC | aRPV | aSL | aEC | aRPV | aSL | aEC | aRPV | aSL | aEC | |
| {A, 3, high} | 0.4282 | 435.53 | 888.45 | 0.6311 | 8924.26 | 938.27 | 0.0662 | 101.23 | 767.55 | 0.0025 | 44.75 | 932.11 |
| {A, 3, low} | 0.2010 | 1146.07 | 819.03 | 0.9022 | 9147.02 | 788.91 | 0.0235 | 517.16 | 632.49 | 0.0000 | 45.16 | 756.99 |
| {A, 5, high} | 0.1660 | 1071.96 | 1461.31 | 0.9083 | 16,785.53 | 1482.37 | 0.1040 | 145.40 | 1194.32 | 0.0000 | 66.24 | 1414.82 |
| {A, 5, low} | 0.0870 | 433.65 | 1400.80 | 1.0000 | 25,363.96 | 1452.15 | 0.0158 | 159.80 | 1220.32 | 0.0000 | 64.13 | 1427.90 |
| {A, 8, high} | 0.0486 | 2061.53 | 2219.58 | 1.0000 | 34,354.58 | 2361.44 | 0.1075 | 4550.04 | 1903.00 | 8.1 × 10−4 | 232.85 | 2283.35 |
| {A, 8, low} | 0.0360 | 892.74 | 2201.61 | 1.0000 | 21,941.94 | 2453.22 | 0.0185 | 579.46 | 1836.03 | 0.0000 | 117.04 | 2348.60 |
| {B, 3, high} | 0.6890 | 198.44 | 680.42 | 0.5524 | 3956.77 | 866.58 | 0.1950 | 93.53 | 625.64 | 0.0000 | 48.76 | 704.52 |
| {B, 3, low} | 0.7997 | 176.54 | 787.17 | 0.3899 | 565.41 | 897.56 | 0.2479 | 81.41 | 692.39 | 0.0000 | 46.87 | 753.15 |
| {B, 5, high} | 0.2380 | 392.66 | 1332.97 | 0.8181 | 14,630.02 | 1524.08 | 0.0905 | 155.81 | 1120.63 | 0.0000 | 64.01 | 1349.24 |
| {B, 5, low} | 0.1228 | 505.25 | 1377.86 | 0.9132 | 19,065.12 | 1507.31 | 0.0082 | 147.77 | 1121.28 | 0.0000 | 62.97 | 1313.57 |
| {B, 8, high} | 0.0192 | 435.63 | 2090.45 | 1.0000 | 27,635.11 | 2491.37 | 0.0035 | 212.63 | 1762.70 | 0.0000 | 117.98 | 2143.24 |
| {B, 8, low} | 0.1189 | 349.83 | 2234.25 | 0.8306 | 18,097.47 | 2436.95 | 0.2047 | 225.83 | 1795.80 | 0.0448 | 93.68 | 2175.48 |
| OVAR | 0% | 0% | 0% | 0% | 0% | 0% | 0% | 0% | 100% | 100% | 100% | 0% |
| Instance Type | Local Execution | Random Offloading | DALEOS | DDFTO | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| aRPV | aSL | aEC | aRPV | aSL | aEC | aRPV | aSL | aEC | aRPV | aSL | aEC | |
| {C, 10, high} | 0.0076 | 160.70 | 2866.59 | 1.0000 | 13,253.09 | 3145.13 | 0.0100 | 231.07 | 2311.41 | 0.0000 | 97.37 | 2658.69 |
| {C, 10, low} | 0.0037 | 138.73 | 2707.94 | 1.0000 | 15,278.85 | 2993.54 | 0.0065 | 190.14 | 2242.34 | 0.0000 | 104.50 | 2496.39 |
| {C, 12, high} | 0.0054 | 180.89 | 3352.48 | 1.0000 | 17,310.71 | 3599.32 | 0.0631 | 1968.20 | 2685.99 | 0.0000 | 119.96 | 3039.99 |
| {C, 12, low} | 0.0057 | 171.26 | 3068.45 | 1.0000 | 15,403.01 | 3393.81 | 0.0129 | 293.63 | 2456.52 | 1.3 × 10−4 | 116.07 | 2785.90 |
| {C, 15, high} | 0.0025 | 168.08 | 4125.30 | 1.0000 | 21,064.08 | 4473.35 | 0.0085 | 356.05 | 3211.75 | 7.5 × 10−4 | 151.28 | 4059.67 |
| {C, 15, low} | 0.0027 | 202.87 | 4017.56 | 1.0000 | 18,305.66 | 4436.20 | 0.0057 | 295.03 | 3242.79 | 1.4 × 10−5 | 147.95 | 3793.53 |
| {D, 10, high} | 0.0894 | 2167.18 | 2386.86 | 1.0000 | 24,468.14 | 2921.72 | 0.0021 | 149.65 | 2185.80 | 0.0000 | 88.99 | 2240.79 |
| {D, 10, low} | 0.0687 | 1804.67 | 2728.45 | 1.0000 | 26,929.55 | 3141.48 | 0.0030 | 171.68 | 2285.22 | 0.0000 | 72.20 | 2625.68 |
| {D, 12, high} | 0.1266 | 2395.76 | 3061.00 | 1.0000 | 33,719.68 | 3408.30 | 0.0035 | 178.00 | 2647.14 | 0.0000 | 95.45 | 2919.24 |
| {D, 12, low} | 0.2057 | 2999.81 | 2886.58 | 0.9000 | 30,512.77 | 3469.72 | 0.0164 | 651.31 | 2629.05 | 0.0010 | 111.54 | 2887.50 |
| {D, 15, high} | 0.0782 | 3096.26 | 3642.95 | 1.0000 | 38,568.15 | 4123.19 | 0.0115 | 659.70 | 3188.66 | 0.0000 | 111.95 | 3375.34 |
| {D, 15, low} | 0.1809 | 2845.50 | 3469.26 | 0.9353 | 27,362.24 | 4148.23 | 0.0042 | 218.99 | 2989.42 | 0.0000 | 116.30 | 3461.84 |
| OVAR | 0% | 0% | 0% | 0% | 0% | 0% | 0% | 0% | 100% | 100% | 100% | 0% |
| Instance Type | Local Execution | Random Offloading | DALEOS | DDFTO | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| aRPV | aSL | aEC | aRPV | aSL | aEC | aRPV | aSL | aEC | aRPV | aSL | aEC | |
| {E, 20, high} | 0.0050 | 318.10 | 5006.04 | 1.0000 | 36,845.37 | 5539.21 | 0.0013 | 213.55 | 4341.25 | 0.0000 | 147.74 | 4351.55 |
| {E, 20, low} | 0.0060 | 318.60 | 5128.57 | 1.0000 | 33,922.07 | 6008.57 | 0.0018 | 230.05 | 4355.02 | 0.0000 | 142.95 | 4642.19 |
| {E, 25, high} | 0.0055 | 379.18 | 6477.22 | 1.0000 | 38,514.60 | 7572.58 | 0.0134 | 743.56 | 5324.09 | 0.0000 | 146.19 | 6060.81 |
| {E, 25, low} | 0.0047 | 342.66 | 6439.91 | 1.0000 | 36,048.58 | 7386.28 | 0.0357 | 1953.49 | 5495.79 | 2.7 × 10−4 | 177.61 | 6345.95 |
| {E, 30, high} | 0.0050 | 414.72 | 7626.81 | 1.0000 | 40,356.60 | 8644.88 | 0.0411 | 2181.07 | 6340.72 | 0.0000 | 214.89 | 7198.28 |
| {E, 30, low} | 0.0045 | 435.62 | 7726.61 | 1.0000 | 47,409.99 | 8695.02 | 0.0132 | 1296.27 | 6416.82 | 0.0000 | 226.90 | 7361.69 |
| {F, 20, high} | 0.0098 | 154.74 | 4957.87 | 1.0000 | 25,687.84 | 5922.47 | 0.0052 | 186.22 | 4507.42 | 9.5 × 10−6 | 111.55 | 4479.23 |
| {F, 20, low} | 0.0014 | 131.13 | 4802.05 | 1.0000 | 19,089.41 | 5877.35 | 0.0112 | 221.64 | 4301.81 | 0.0042 | 140.55 | 4510.62 |
| {F, 25, high} | 5.3 × 10−4 | 141.83 | 6319.60 | 1.0000 | 31,898.81 | 7375.91 | 0.0159 | 742.02 | 5516.96 | 2.6 × 10−4 | 153.17 | 5668.86 |
| {F, 25, low} | 7.8 × 10−4 | 143.23 | 5953.34 | 1.0000 | 21,702.09 | 7201.70 | 0.0036 | 236.78 | 5331.03 | 0.0014 | 162.01 | 5549.13 |
| {F, 30, high} | 1.5 × 10−4 | 130.86 | 7986.29 | 1.0000 | 29,388.36 | 8764.14 | 0.1245 | 3857.84 | 6733.56 | 0.0031 | 232.95 | 7153.58 |
| {F, 30, low} | 4.5 × 10−4 | 158.90 | 7555.69 | 1.0000 | 33,801.74 | 8636.41 | 0.0994 | 6797.18 | 6515.08 | 3.8 × 10−4 | 176.34 | 6733.99 |
| OVAR | 25% | 41.67% | 0% | 0% | 0% | 0% | 0% | 0% | 91.66% | 75% | 58.33% | 8.33% |
| Instance Type | Local Execution | Random Offloading | DALEOS | DDFTO | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| aRPV | aSL | aEC | aRPV | aSL | aEC | aRPV | aSL | aEC | aRPV | aSL | aEC | |
| {A, 15, low} | 0.0138 | 1318.22 | 4436.11 | 1.0000 | 49,211.48 | 4803.42 | 0.0557 | 4164.82 | 3415.79 | 5.1 × 10−4 | 344.87 | 469.89 |
| {B, 15, low} | 0.0211 | 954.01 | 3969.16 | 1.0000 | 36,736.82 | 4343.96 | 0.0475 | 2728.17 | 3165.18 | 0.0000 | 254.59 | 3981.18 |
| {C, 15, low} | 0.0040 | 190.32 | 3804.91 | 1.0000 | 22,411.34 | 4074.59 | 0.0044 | 251.90 | 3113.46 | 0.0000 | 121.91 | 3489.86 |
| {D, 15, low} | 0.1199 | 2850.99 | 3713.90 | 1.0000 | 30,349.57 | 4168.34 | 0.0615 | 3387.67 | 3228.45 | 0.0000 | 123.16 | 3771.09 |
| {E, 15, low} | 0.0085 | 310.55 | 3785.44 | 1.0000 | 32,505.32 | 4288.40 | 0.0020 | 139.21 | 3275.27 | 0.0000 | 99.92 | 3262.42 |
| {F, 15, low} | 0.0030 | 132.61 | 3598.91 | 1.0000 | 19,458.29 | 4307.39 | 0.0186 | 689.76 | 3287.60 | 0.0000 | 93.20 | 3367.35 |
| OVAR | 0% | 41.67% | 0% | 0% | 0% | 0% | 0% | 0% | 83.33% | 100% | 100% | 16.67% |
| Instance Type | Local Execution | Random Offloading | DALEOS | DDFTO | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| aRPV | aSL | aEC | aRPV | aSL | aEC | aRPV | aSL | aEC | aRPV | aSL | aEC | |
| {C, 2, low} | 0.8632 | 118.71 | 537.51 | 0.3027 | 567.60 | 609.03 | 0.2512 | 66.26 | 486.84 | 0.0000 | 38.04 | 549.19 |
| {C, 4, low} | 0.4479 | 106.64 | 1001.55 | 0.6366 | 4477.50 | 1041.43 | 0.2032 | 83.02 | 854.51 | 0.0000 | 44.26 | 860.44 |
| {C, 6, low} | 0.2080 | 148.62 | 1404.25 | 0.8714 | 9274.55 | 1679.38 | 0.0948 | 127.34 | 1185.29 | 0.0000 | 53.44 | 1421.18 |
| {C, 8, low} | 0.1095 | 127.26 | 1953.01 | 0.9378 | 10,267.03 | 2185.59 | 0.0652 | 162.51 | 1570.33 | 4.1 × 10−5 | 85.29 | 1878.07 |
| {C, 10, low} | 0.0059 | 148.71 | 2777.45 | 1.0000 | 13,353.12 | 3054.30 | 0.0420 | 972.52 | 2339.67 | 0.0000 | 94.85 | 2692.88 |
| {C, 12, low} | 0.0037 | 158.46 | 3221.83 | 1.0000 | 13,061.91 | 3522.47 | 0.0101 | 268.96 | 2631.71 | 7.6 × 10−4 | 110.89 | 3188.37 |
| {C, 14, low} | 0.0046 | 164.22 | 3864.22 | 1.0000 | 21,333.83 | 4270.94 | 0.0108 | 326.01 | 3157.89 | 0.0000 | 125.00 | 3434.52 |
| {C, 16, low} | 0.0021 | 178.32 | 4296.15 | 1.0000 | 29,990.68 | 4524.43 | 0.0048 | 329.91 | 3282.43 | 1.3 × 10−4 | 150.01 | 3967.27 |
| {C, 18, low} | 0.0025 | 196.32 | 4875.38 | 1.0000 | 31,174.33 | 5301.99 | 0.0912 | 5380.43 | 3809.38 | 3.2 × 10−4 | 152.35 | 4610.90 |
| {C, 20, low} | 0.0012 | 204.49 | 5506.41 | 1.0000 | 30,025.85 | 5831.97 | 0.0207 | 1031.62 | 4359.45 | 0.0019 | 208.68 | 5161.47 |
| {C, 22, low} | 0.0012 | 241.70 | 5882.84 | 1.0000 | 36,929.39 | 6457.77 | 0.0304 | 1904.91 | 4672.92 | 8.3 × 10−4 | 220.60 | 5828.34 |
| {C, 24, low} | 8.2 × 10−4 | 240.26 | 6915.95 | 1.0000 | 37,058.53 | 7195.91 | 0.0982 | 4744.11 | 5508.89 | 0.0022 | 261.36 | 6813.02 |
| {C, 26, low} | 2.6 × 10−4 | 254.90 | 7399.23 | 1.0000 | 33,985.64 | 7937.18 | 0.0589 | 2845.19 | 5413.30 | 0.0197 | 1192.96 | 6471.63 |
| {C, 28, low} | 8.7 × 10−4 | 262.29 | 7620.08 | 1.0000 | 40,233.24 | 8204.79 | 0.0576 | 2930.33 | 6217.39 | 0.0040 | 415.83 | 6882.54 |
| {C, 30, low} | 4.4 × 10−4 | 251.48 | 8348.84 | 1.0000 | 42,611.64 | 8630.32 | 0.0420 | 2169.42 | 6162.36 | 4.9 × 10−4 | 279.29 | 7747.13 |
| OVAR | 33.33% | 33.33% | 0% | 0% | 0% | 0% | 0% | 0% | 100% | 66.67% | 66.67% | 0% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, R.; Yang, Y.; Li, H. A Distributed Deadlock-Free Task Offloading Algorithm for Integrated Communication–Sensing–Computing Satellites with Data-Dependent Constraints. Remote Sens. 2024, 16, 3459. https://doi.org/10.3390/rs16183459
Zhang R, Yang Y, Li H. A Distributed Deadlock-Free Task Offloading Algorithm for Integrated Communication–Sensing–Computing Satellites with Data-Dependent Constraints. Remote Sensing. 2024; 16(18):3459. https://doi.org/10.3390/rs16183459
Chicago/Turabian StyleZhang, Ruipeng, Yikang Yang, and Hengnian Li. 2024. "A Distributed Deadlock-Free Task Offloading Algorithm for Integrated Communication–Sensing–Computing Satellites with Data-Dependent Constraints" Remote Sensing 16, no. 18: 3459. https://doi.org/10.3390/rs16183459
APA StyleZhang, R., Yang, Y., & Li, H. (2024). A Distributed Deadlock-Free Task Offloading Algorithm for Integrated Communication–Sensing–Computing Satellites with Data-Dependent Constraints. Remote Sensing, 16(18), 3459. https://doi.org/10.3390/rs16183459






