2.1. Fundamental Theory
One of the most accurate remote time synchronization methods is TWSTT [
15,
16,
17,
18]. In this mode, the transmission path symmetry enables the propagation delay on the link to be nearly fully offset, which can make the time synchronization reach a high accuracy.
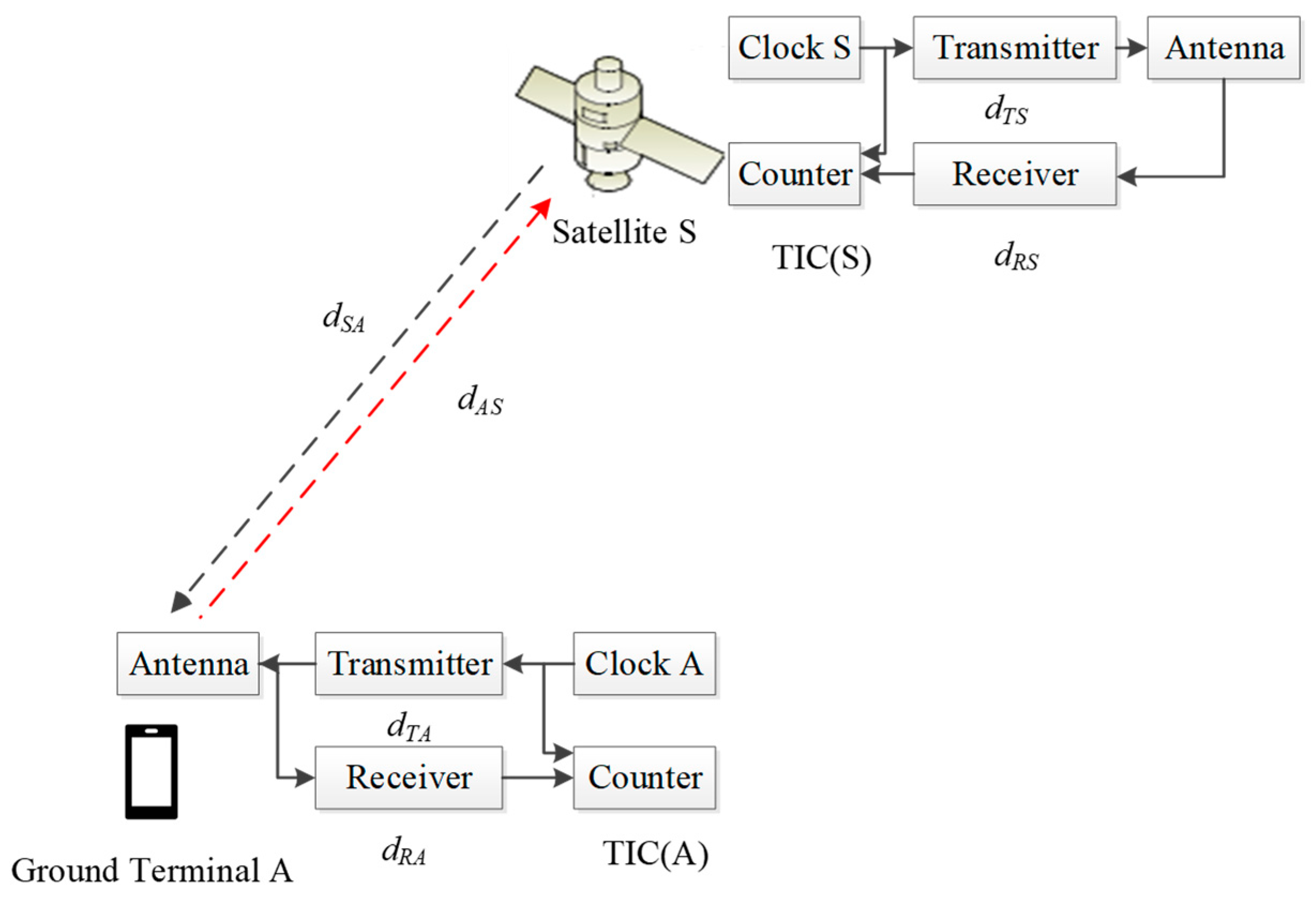
Figure 1 illustrates the principle of satellite–earth TWSTT.
As depicted in
Figure 1, the computational model of TWSTT can be written as follows:
where
and
represent the transmission pseudo-distance values, i.e., the readings of the time interval counter.
is measured by the satellite and its information is added to the downlink communication signal for transmission to the ground terminal, A and S represent the paper time at the respective stations,
represents the propagation delay, and
and
are the correction terms for the Sagnac effect. By taking the difference between Equations (1) and (2), we can derive the expression for the clock difference between the ground terminal A and the satellite S as follows:
In Equation (3), the first term to the right of the equal sign is the difference between the counter readings of the ground terminal and the satellite, which is the difference between the clock difference measured by the ground terminal and the satellite. The second term corresponds to the difference between the transmission and reception delays of the ground terminal, while the third term denotes the difference between the transmission and reception delays at the satellite end. The fourth term represents the correction for the relativistic effect caused by the rotation of the Earth, i.e., the Sagnac effect, and the fifth term accounts for the difference in the spatial propagation delays for the uplink signal and the downlink signal, including ionospheric delays, tropospheric delays, geometrical path delays, and so on.
The second to fourth terms can be measured or calculated in advance, and the fifth term can be well canceled due to the delay of the upper and lower paths in the very short TWSTT being equal. Thus, Equation (3) can be reduced to Equation (4).
Therefore, it is only necessary to accurately calibrate and deduct the arrival times of the signals measured by the ground terminals and satellites so that the clock difference measurement can be realized by two-way time comparison.
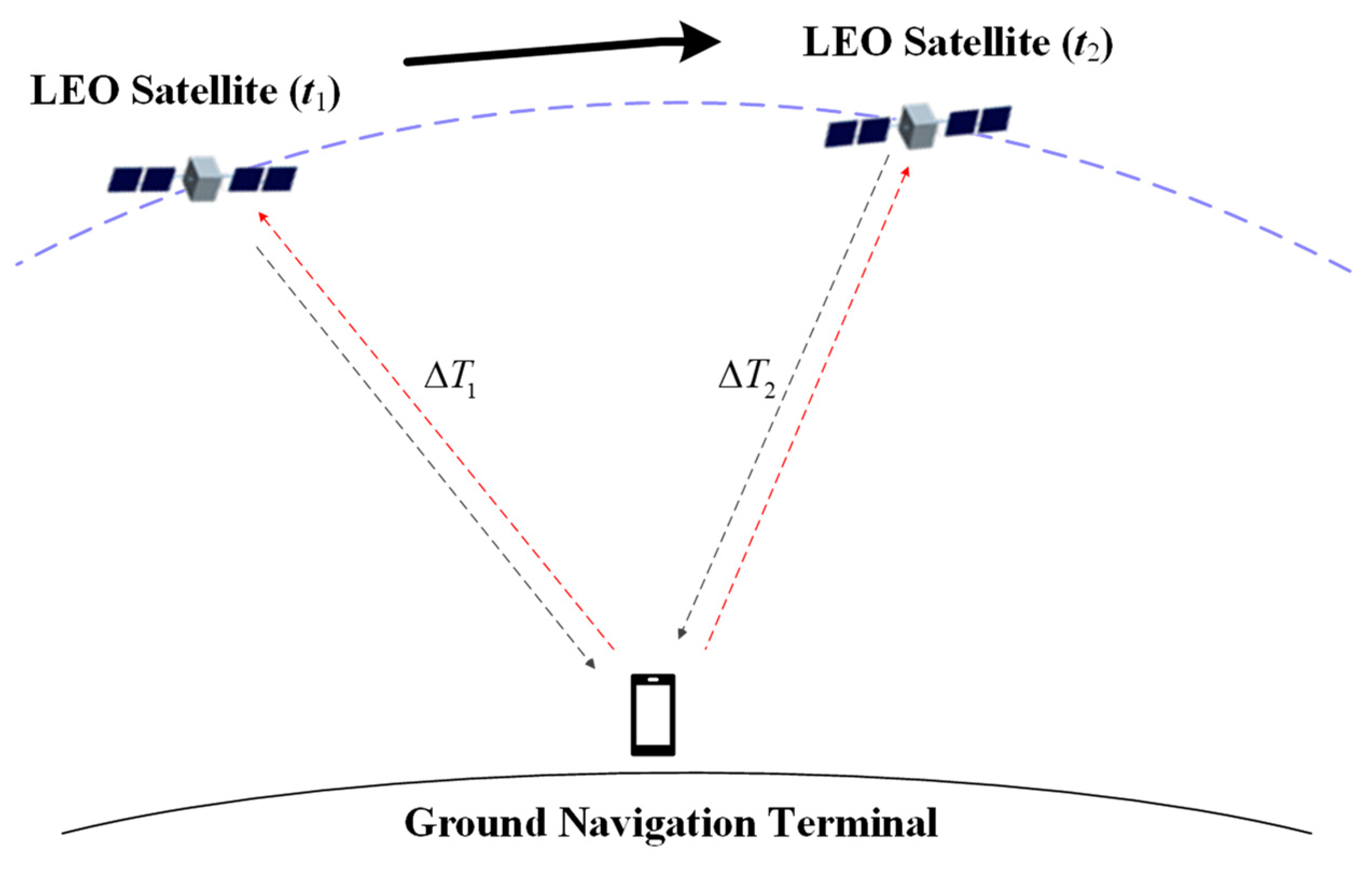
Due to the non-mutated nature of the clock difference, this paper proposes a novel NavCom signal authentication scheme based on twice TWSTT, which involves the user terminal conducting twice separate TWSTT with the same satellite. The scheme can achieve signal security authentication through a comparison of clock difference measurement values. The specific operation procedures are as follows: the user terminal initiates twice two-way authentications at two different moments, and , during the satellite’s visibility period. The clock difference measurements obtained from these two authentications are recorded as and , respectively.
Figure 2 illustrates a schematic of twice TWSTT. In
Figure 2, it can be observed that only the paths of the uplink and downlink signals change during the twice TWSTT processes. Fortunately, the paths of the uplink and downlink signals are equal for the same time transfer process, which can be canceled out. Hence, the twice clock difference measurements obtained should be identical without considering any errors according to Equation (4), i.e.,
.
Generally, there is a risk of being spoofed due to the satellite downlink signal being broadcast signals to the ground terminal, mainly including generated spoofing and repeater spoofing interference. For generated spoofing interference signals, information authentication or digital signature can be added to the message of navigation signals, so that the receivers in the satellite or earth can effectively block the unauthenticated signals and prevent the generated spoofing interference. However, it is impossible to block repeater spoofing interference signals in such a way, which is the main problem that the proposed authentication scheme focuses on solving.
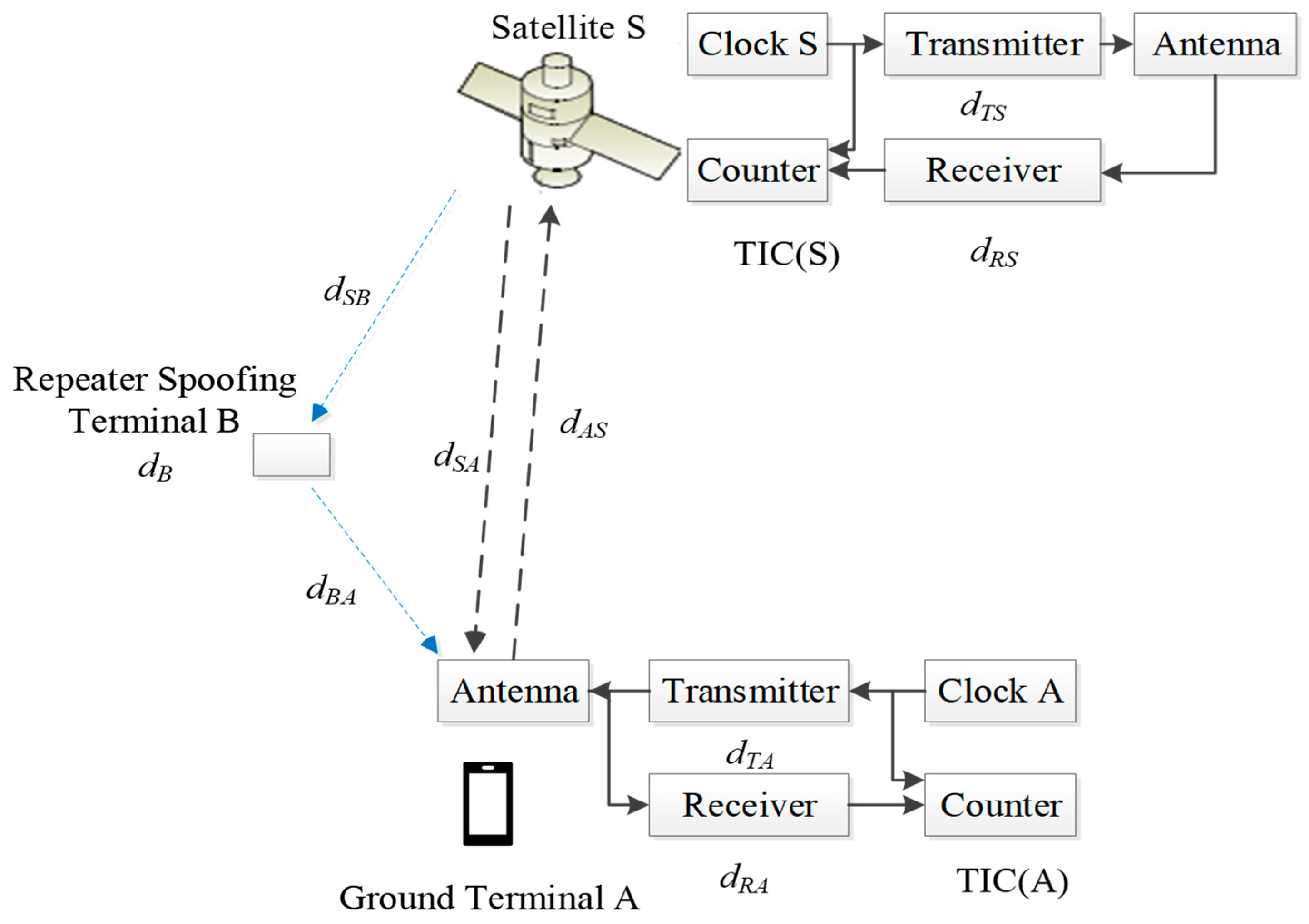
Figure 3 illustrates the scenario with repeater spoofing interference, where
denotes the delay of the spoofing interference signal,
represents the delay from satellite S to the repeater spoofing terminal B, and
denotes the delay from spoofing terminal B to ground terminal A. As the signal transmitted by ground terminal A to satellite S is pulsed, it is challenging to record and forward it. Therefore, it is the most common form of repeater spoofing interference as depicted in
Figure 3.
As a result, the clock difference can be determined by
It is obvious that the clock difference measurements are pulled out of alignment because of the last term in Equation (5). Therefore, ensuring that the clock difference measurements obtained from twice TWSTT are constant is crucial for them to be equal. However, satisfying this condition can be challenging in practice, and the reasons will be discussed below in two different scenarios.
Scenario 1: Ground terminal remains stationary.
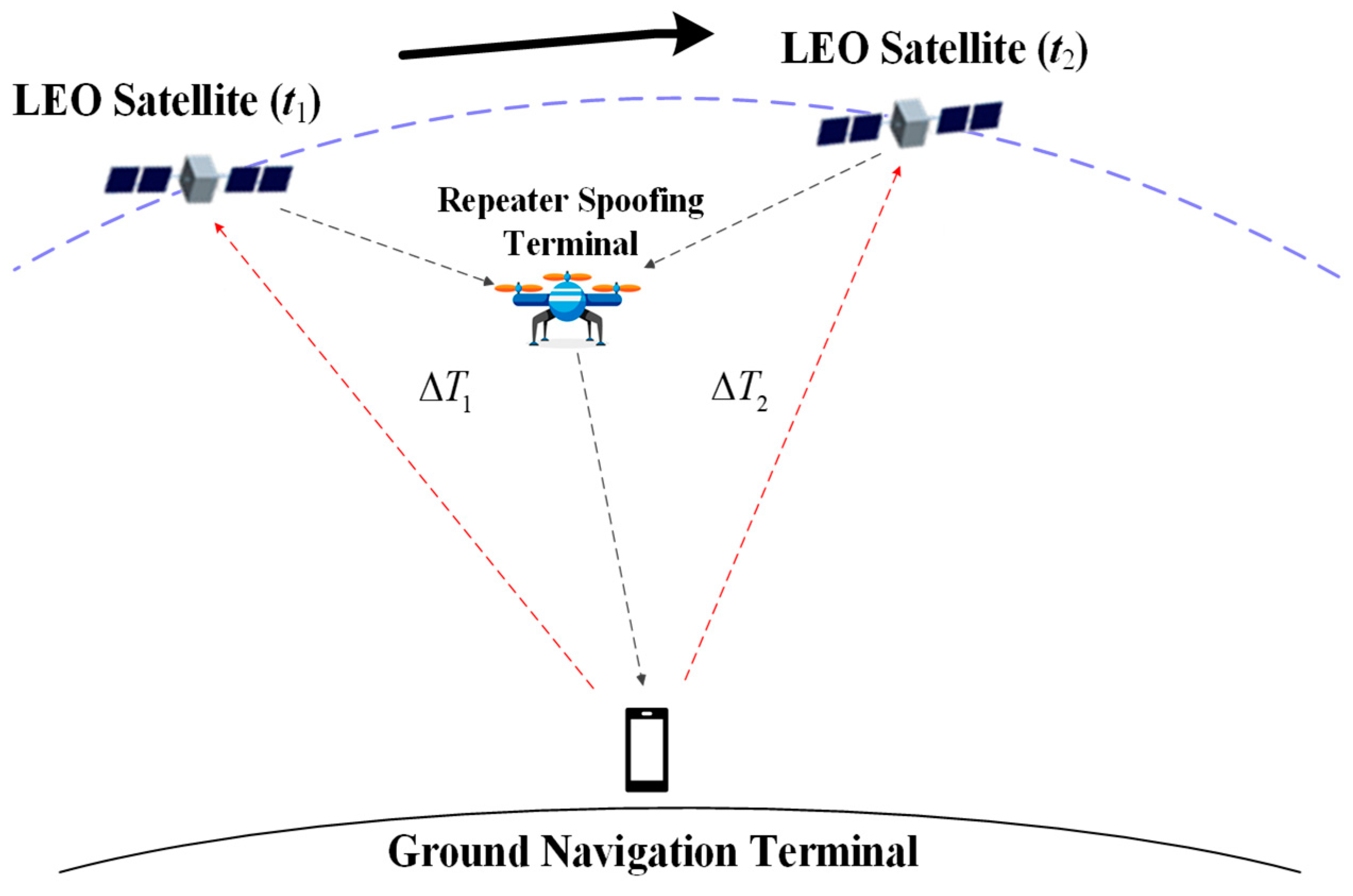
Figure 4 depicts the schematic diagram of twice TWSTT in the repeater spoofing interference scenario, where the satellite downlink signals are recorded and forwarded by the spoofing terminal. As shown in
Figure 4, the satellite’s position changes during the twice TWSTT processes. When the ground terminal remains motionless, the spoofing terminal can theoretically calculate the trajectory in advance based on the position of the ground terminal and the satellite ephemeris and follow the satellite movement to realize the same value of
in twice measurements. Fortunately, it is challenging to achieve such consistency in practice. Firstly, it is challenging for the spoofing terminal to accurately determine the precise geographic coordinates of the ground terminal. Secondly, there are numerous LEO satellites, and the ground terminal can simultaneously observe multiple satellites. As a result, the spoofing terminal cannot predict the specific moment when the ground terminal will initiate the authentication or the ID of the LEO satellites involved. Thirdly, it requires a high level of control accuracy for the flight platform carrying the spoofing terminal, even if the operation trajectory is calculated in advance. Any slight deviation can disrupt the spoofing scheme, making it infeasible to achieve the desired consistency in the measurements.
Scenario 2: Ground terminal is in motion.
It becomes even more difficult to achieve consistency in twice measurements if the ground terminal is also in motion. This is because the trajectory of the ground terminal cannot be precisely predicted in advance, which makes it impossible for the spoofing terminal to calculate the running trajectory ahead of time.
In summary, it is difficult to keep the two clock difference measurements consistent according to the analysis of scenario 1 and scenario 2. In such scenarios, the ground terminal can ascertain the presence of repeater spoofing interference, as the inconsistency in the measurements serves as an indication.
However, the previous analysis did not consider measurement errors, which can occur in real situations. The measurement of signal arrival time at the ground terminal can be subject to biases in twice TWSTT process. These biases may result in the same value of
and
when there are repeater spoofing interference signals, potentially leading to successful spoofing. Therefore, it is necessary to conduct further analysis and consider measurement errors when studying real scenarios [
19].
2.2. Signal and Detection Model
The earlier analysis indicates that the accuracy of the clock difference from the twice TWSTT is significant for security authentication capabilities. As such, it is essential to analyze the error associated with clock difference measurement accuracy.
Equation (3) reveals that the accuracy of clock difference measurement is influenced by four main factors: hardware device time delay difference, Sagnac effect error, space propagation time delay difference, and signal arrival time measurement error [
20].
(1) Hardware device time delay difference:
The hardware device time delay error mainly includes the hardware processing time delay error, the hardware storage time delay error, and the hardware variation error with temperature. From the literature [
20], these errors add up to about 80 ps.
(2) Sagnac effect error:
The Sagnac effect error is a result of the signal transmission process and arises from the continuous rotation of the Earth, which is caused by the changing relative distance between the ground terminal and the satellite. This error can be calculated using calibration formulas and is typically on the order of 1 ps [
21].
(3) Space propagation time delay difference:
The space propagation delay difference includes ionospheric delay, tropospheric delay, and geometric path delay. Among them, the ionospheric time delay difference is 10 ps, the tropospheric time delay can be negligible after correction by the tropospheric delay model, and as for the geometric path delay, TWSTT can be accomplished within 10 ms due to the low orbital altitude of LEO satellites so that the uplink and downlink can be regarded as completely symmetrical between the satellite and the ground terminal. Therefore, the space propagation time delay difference is about 10 ps [
22].
(4) Signal arrival time measurement error:
Without loss of generality, a detailed analysis using conventional BPSK navigation signals as an example is presented in this section. The measurement of signal arrival time can be performed either through carrier phase measurement or code phase measurement for receivers. The receiver typically utilizes code phase measurement, due to the long convergence time required for carrier phase measurement, and the TWSTT usually uses a short burst signal. In this case, assuming the receiver uses a code-ring discriminator with a noncoherent pre-subtracted post-power method, we can calculate the mean square error of the code phase measurement in terms of pseudo-code code slices using Equation (6) [
23]:
where
is the loop noise bandwidth,
is the coherence accumulation time,
is the early-late correlator spacing, and
is the CNR. If the chip duration is
, then the mean square deviation of time measurement error
can be determined by
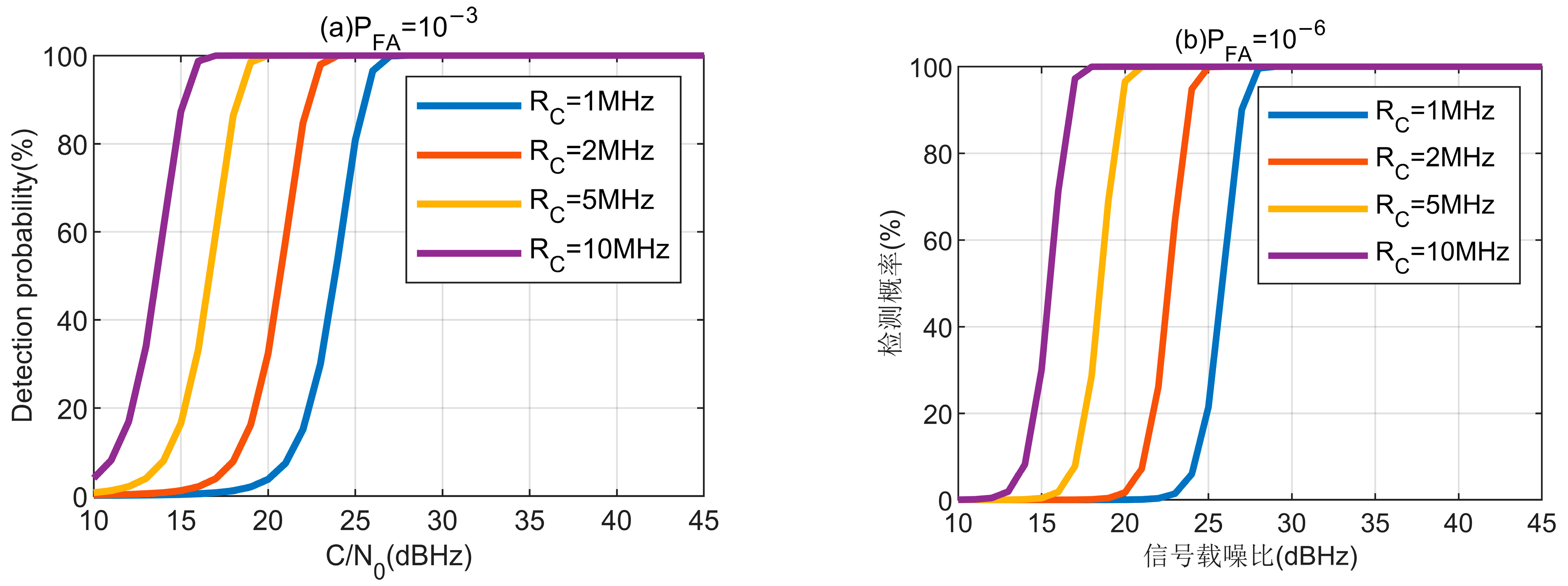
Let the chip rate of the BPSK navigation signal be 1.023 MHz, then
Tc = 1/1023 ms,
Hz,
ms,
chip, and
dBHz; this can be seen the variation trend of concern in
Figure 5.
Figure 5 is only the signal arrival measurement time error of the ground terminal, the signal arrival measurement time error of the satellite can be calculated similarly, and it should be in the same order of magnitude.
From the above analysis, it can be seen that the hardware device time delay difference, the Sagnac effect error, and the space propagation time delay difference together do not exceed 100 ps at most, which is much smaller than the signal arrival time measurement error and can be ignored. Therefore, when there is no repeater spoofing interference signal, it can be obtained that the measurement errors of
and
obey the probability density distributions shown in Equation (8).
where
and
are the pseudo-code width and mean square deviation of the downlink signal’s code phase measurement error, and
and
are the pseudo-code width and mean square deviation of the uplink signal’s code phase measurement error, respectively. Then, the clock difference measurement
will obey the probability density distribution shown in Equation (9), where
is the true value of the clock difference.
When there is no repeater spoofing interference signal, the two clock difference measurements
and
obey the probability density distribution shown in Equation (10).
For further analysis, we define the certified detection volume of this method as the difference between two clock difference measurements, as shown in Equation (11).
Therefore, when there is no repeater spoofing interference signal, the authentication detection volume will obey the probability density distribution shown in Equation (12).
When the repeater spoofing interference signal is present, there will be an offset in the clock difference due to the spoofing signal, which can be denoted as
, and
. At this point, the two clock difference measurements
and
will obey the probability density distribution shown in Equation (13).
where
and
represent the clock difference offsets of the twice TWSTT, respectively. Therefore, when the repeater spoofing interference signal is present, the authentication detection volume will obey the probability density distribution shown in Equation (14).
where
. Owing to
not being a fixed value, its probability distribution must be analyzed. Due to once TWSTT time being relatively short and the ground terminal being fixed in most scenarios, it is assumed that the positions of the spoofing terminal and the ground terminal remain unchanged during the twice TWSTT processes, then
can be rewritten as Equation (15).
where
and
represent the paths from satellite S to ground terminal A and from satellite S to spoofing terminal B in the first TWSTT, respectively. Similarly,
and
represent the paths from satellite S to ground terminal A and from satellite S to spoofing terminal B in the second TWSTT, respectively.
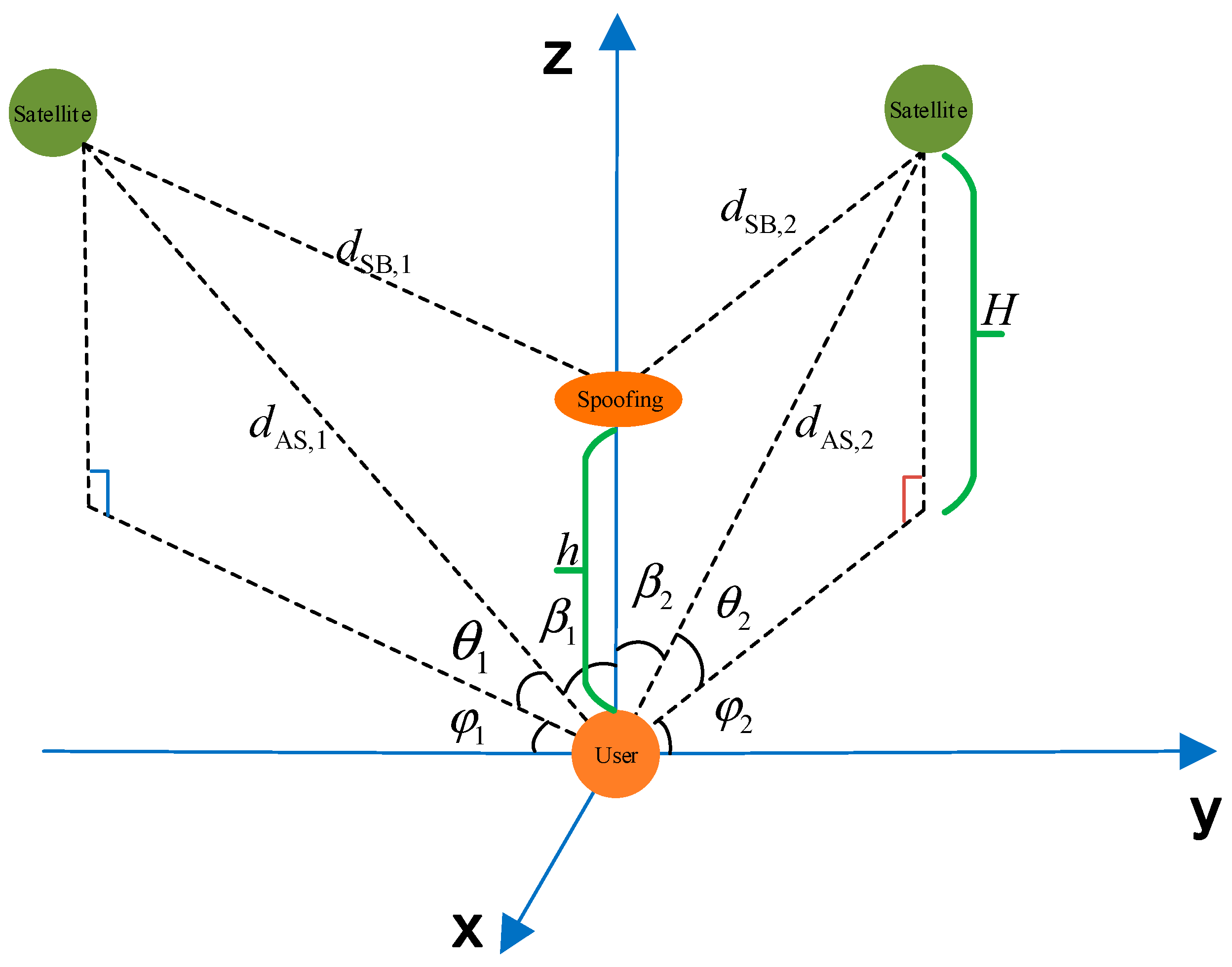
If the spoofing terminal is directly positioned above the ground terminal, the spatial propagation loss of the spoofing signal would be minimized, making it more effective in suppressing the genuine signal. Consequently, this method is considered the most cost-effective way for the spoofing terminal to carry out its deception. To facilitate a more accurate modeling of this scenario, we can establish a spatial geometry model as depicted in
Figure 6.
In the geometric relationship shown in
Figure 6, we denote
as the vertical distance between the LEO satellite and the user terminal, and
as the vertical distance between the spoofing terminal and the user terminal. Based on this geometry, we can derive the following relationship, where c represents the speed of light.
Substituting Equation (16) into Equation (15) transforms the expression as follows:
It can be seen from Equation (17) that
is a function using
,
,
, and
. Where
is determined by the spoofing terminal, for example, the UAV flight altitude is usually 1~15 km, and
,
, and
are determined by the satellite position and the user terminal position; when the user terminal is fixed, the values of
and
can be changed by changing the moment of initiating the authentication. Therefore, it is necessary to analyze the optimal elevation angle and initiation timing for authentication at the user terminal. By performing calculations,
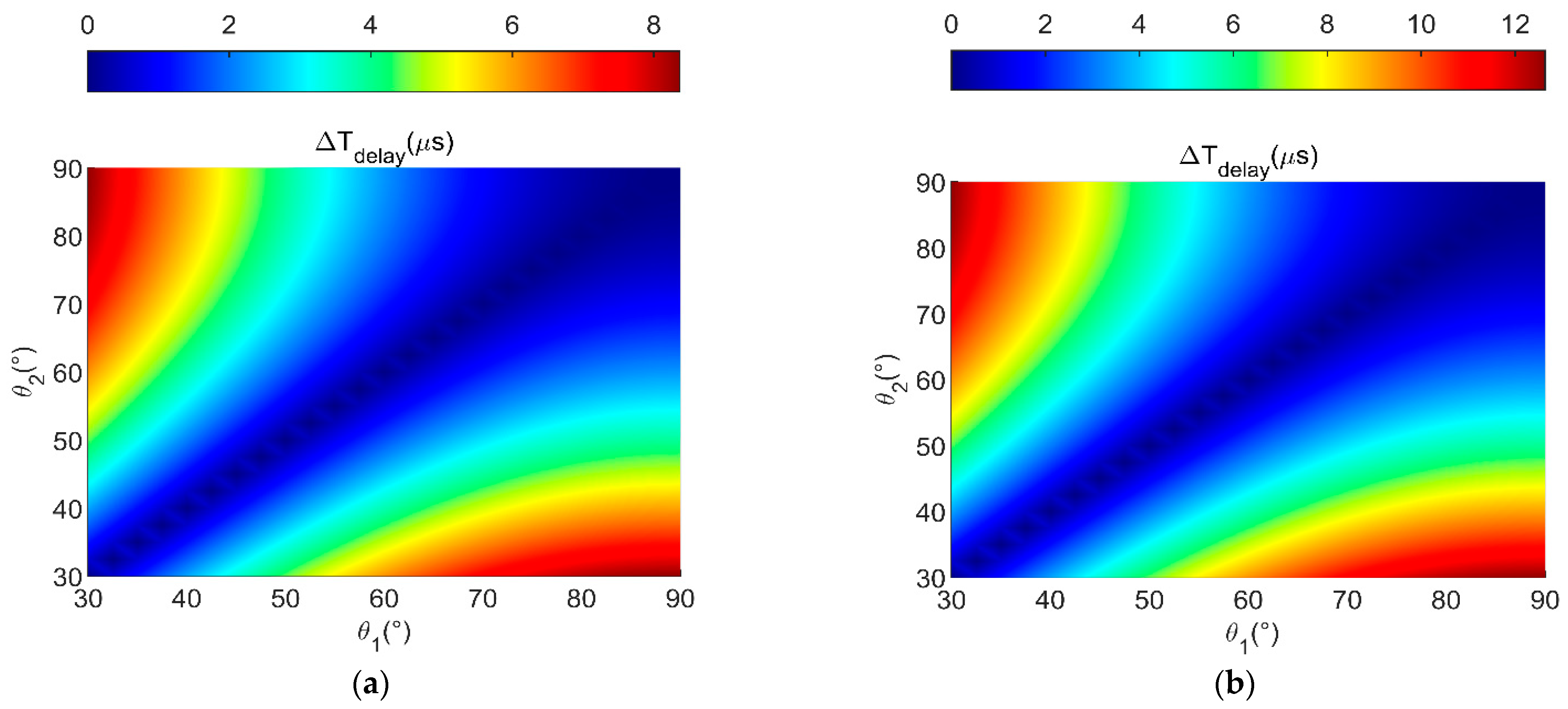
Figure 7 shows the relationship between
and
with
when different combinations of
and
are used. The visible elevation angle of the satellite is generally required to be larger than 15°. To ensure adequate visibility between the satellite and the user terminal, the range of
and
inthe figure is set from 30° to 90°.
From
Figure 7, we can draw the following two conclusions:
- (1)
When the vertical distance between the LEO satellite and the user terminal and the vertical distance between the spoofing terminal and the user terminal are fixed, and the elevation angles ( and ) of the user terminal to the satellite are equal, it results in being 0. This indicates that the user terminal can successfully be spoofed by a spoofing terminal.
- (2)
The larger the difference between and , the greater the value of . In this context, a higher value of indicates a lower likelihood of being spoofed by the spoofing terminal.
Therefore, in order to ensure that this authentication scheme can perform optimally, the moment when the user terminal initiates the authentication request needs to meet the requirement of maximizing the difference between the values of and . Without loss of generality, we set , or , . As users can obtain satellite ephemeris through communication signals in advance, they can predict the launch angle and launch time in advance.
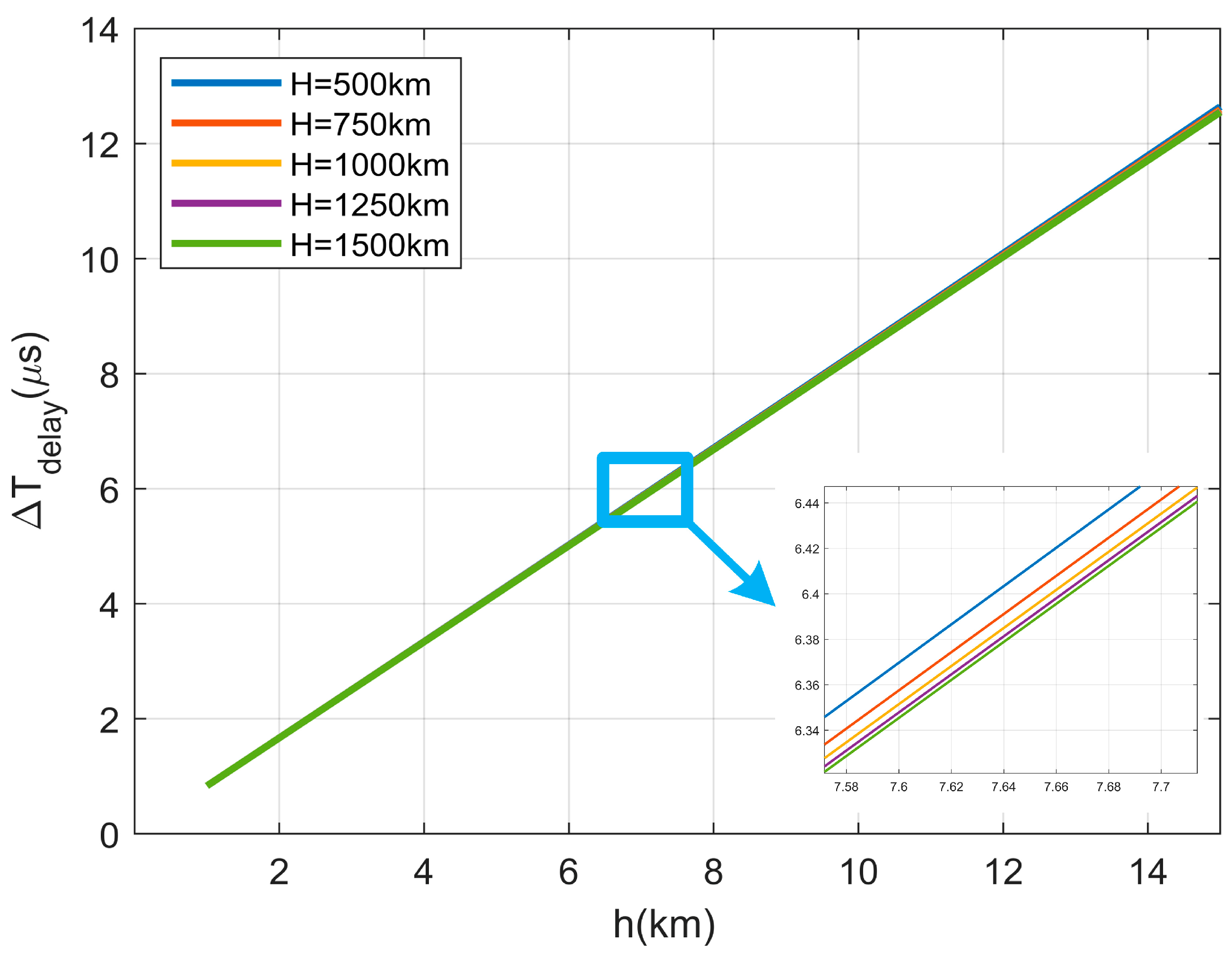
Figure 8 illustrates the variation trend of
versus
and
when
and
. From
Figure 8, we can draw the following conclusions:
- (1)
When , , and are fixed during user terminal authentication, it can be observed that the smaller the , the smaller becomes, resulting in a higher likelihood of successful spoofing.
- (2)
When , , and are fixed, the larger and the smaller become, the easier it is to spoof successfully.
- (3)
has a relatively small effect on the . In contrast, has a larger effect on the .
To analyze the impact of
and
on
more effectively, we substitute the optimal elevation angles into Equation (17);
can be rewritten as follows:
Owing to the user terminal already possessing the satellite ephemeris in advance, the value of
is known to the user terminal. Therefore, we can consider
as a function solely dependent on
. Through numerical calculations and fitting analysis, we establish the following relationship:
The fitted correlation coefficient of Equation (19) is 0.9923, indicating a strong correlation between the variables
and
. Additionally, the mean squared error of the fitting is 1.294 ps, suggesting that the Equation (19) provides an accurate characterization of the original function. To investigate the performance limits of the proposed NavCom signal authentication scheme, the worst-case spoofing scenario is considered. In this scenario, we assume that
takes its minimum value, and then the Equation (14) can be transformed into the following:
where
=
−
+
. As a result, the hypothesis testing for the certified detection volume of this method is shown below:
When the false alarm probability of the constant false alarm detection is denoted as
PFA, the detection threshold
can be determined by Equation (22).
where
is the right-tailed function of the standard normal distribution. At this point, the detector for signal authentication can be defined as Equation (23).
Specifically, after the calculation of the clock difference measurements from twice TWSTT, the magnitude of the difference is compared against the detection threshold to determine whether the difference exceeds this threshold.