Joint Task Offloading, Resource Allocation, and Security Assurance for Mobile Edge Computing-Enabled UAV-Assisted VANETs
Abstract
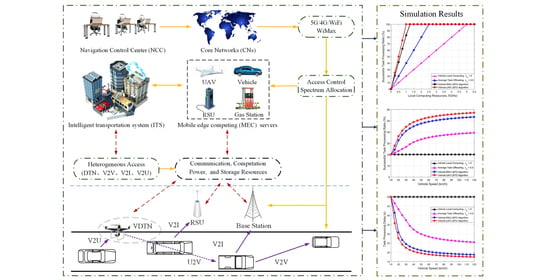
:1. Introduction
- We propose an MEC-enabled UAV-assisted VANET to provide vehicles with the low latency and reliable computing services through UAVs. Specifically, we adopt comprehensive task processing delay as the optimization objective by jointly considering the transmission model and the security assurance model from the vehicle to the MEC server on UAV, and the task computation model of the local vehicle and the edge UAV.
- We design a network optimization scheme by jointly considering the task offloading, the resource allocation, and the security assurance for VANETs. Moreover, to fully exploit the advantages of the MEC-enabled UAV-assisted VANET architecture, we use UAVs for boosting VANETs communications to improve VANETs’ computation ability. Furthermore, we propose an efficient iterative algorithm based the relax-and-rounding method and the Lagrangian method, which can effectively solve the joint optimization problem.
- We conduct simulations to evaluate the performance of our proposed scheme. The simulation results indicate that our designed MEC-enabled UAV-assisted VANET architecture is superior to the traditional ground-based VANETs. In addition, our proposed scheme can achieve significant performance superiority compared with other schemes in the successful task processing ratio and the task processing delay.
2. Related Works
2.1. UAV-Assisted VANETs
2.2. MEC-Enabled UAV-Assisted VANETs
2.3. Synthesis
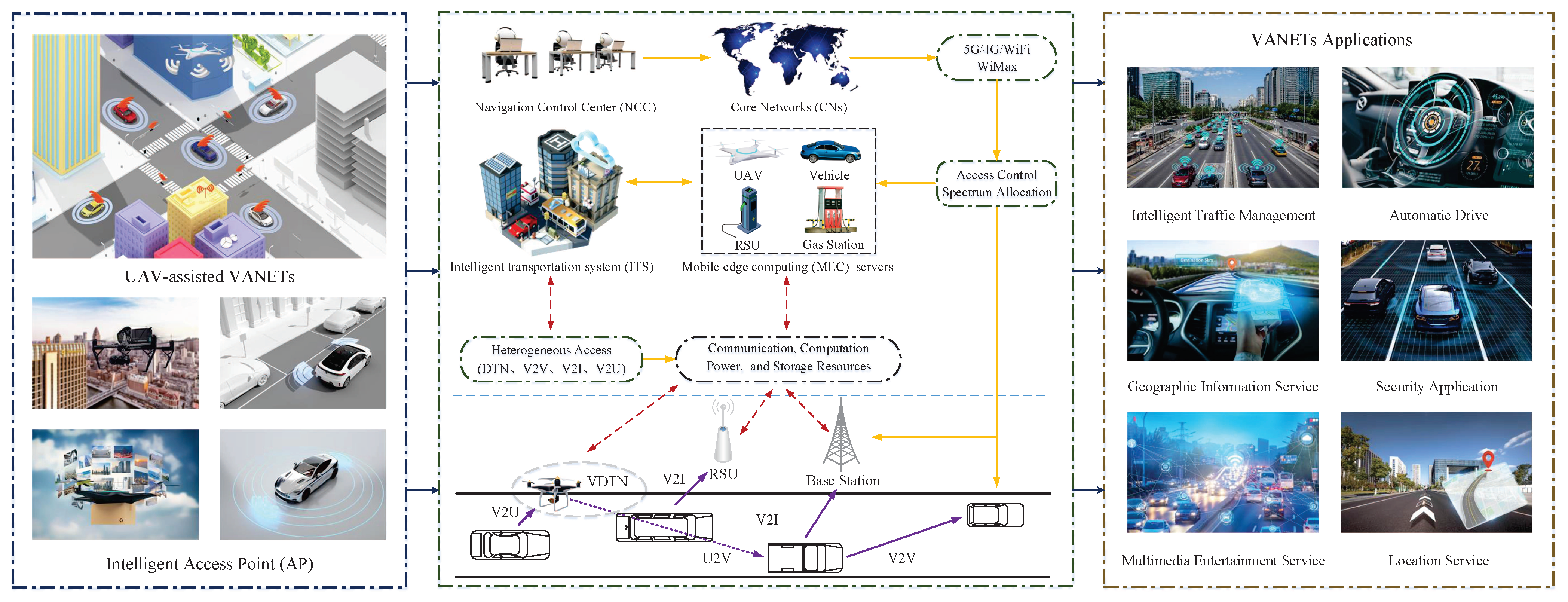
3. System Model and Problem Formulation
3.1. Network Model
3.2. Transmission Model
3.3. Task Computation Model
3.4. Security Assurance Model
3.5. Problem Formulation
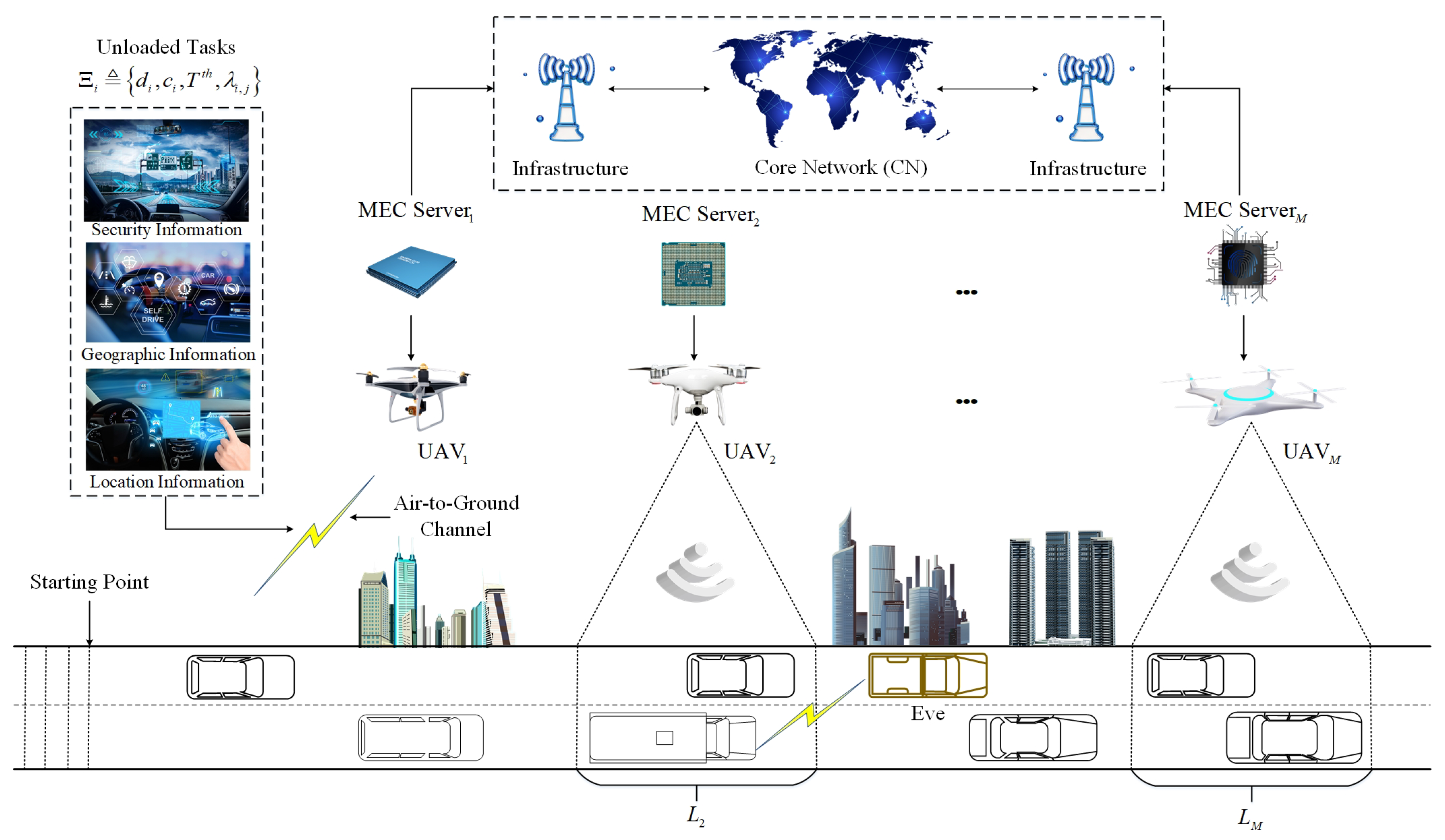
4. Joint Task Offloading, Resource Allocation, and Security Assurance Algorithm
4.1. Problem Transformation
4.2. MEC Server Selection
4.3. Joint Task Offloading and Resource Allocation
4.3.1. Optimization of Resource Allocation
4.3.2. Optimization of Task Offloading
4.4. Overall Algorithm
| Algorithm 1 The Proposed LBTO Algorithm. |
| 1: Initialization |
| 2: Set iterations . |
| 3: Set , , and . |
| 4: repeat |
| 5: k = k+1. |
| 6: Based on and , we can solve the optimization problem P3 by the constraint relaxation scheme and the relax-and-rounding method. |
| 7: until Obtain the feasible solution . |
| 8: repeat |
| 9: According to the Lagrangian dual decomposition, we can solve the optimization problem P7 and P8. |
| 10: Calculate the optimal solution and . |
| 11: until Convergence. |
4.5. Potential Applications
5. Simulation Results
5.1. Simulation Parameters
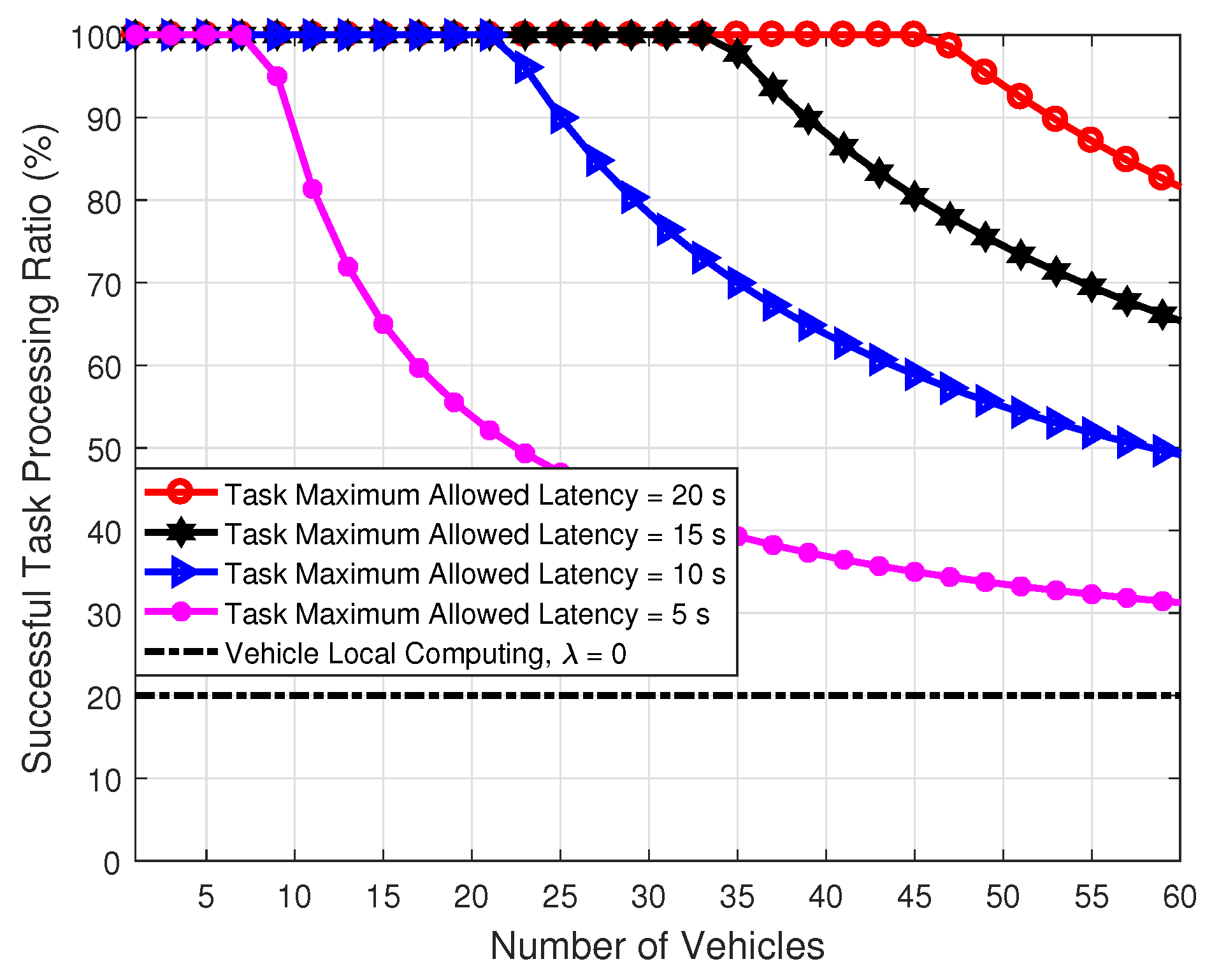
5.2. Simulation Results
6. Discussion
6.1. Research Questions
6.2. Research Limitations and Future Research Prospects
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
Appendix B
Appendix C
References
- Cui, J.; Wei, L.; Zhong, H.; Zhang, J.; Xu, Y.; Liu, L. Edge Computing in VANETs-An Efficient and Privacy-Preserving Cooperative Downloading Scheme. IEEE J. Sel. Areas Commun. 2020, 38, 1191–1204. [Google Scholar] [CrossRef]
- Nazib, R.A.; Moh, S. Routing Protocols for Unmanned Aerial Vehicle-Aided Vehicular Ad Hoc Networks: A Survey. IEEE Access 2020, 8, 77535–77560. [Google Scholar] [CrossRef]
- Cui, J.; Wei, L.; Zhang, J.; Xu, Y.; Zhong, H. An Efficient Message-Authentication Scheme Based on Edge Computing for Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2019, 20, 1621–1632. [Google Scholar] [CrossRef]
- Oubbati, O.S.; Lakas, A.; Zhou, F.; Güneş, M.; Lagraa, N.; Yagoubi, M. Intelligent UAV-assisted routing protocol for urban VANETs. Comput. Commun. 2017, 107, 93–111. [Google Scholar] [CrossRef]
- He, Y.; Zhai, D.; Jiang, Y.; Zhang, R. Relay Selection for UAV-Assisted Urban Vehicular Ad Hoc Networks. IEEE Wirel. Commun. Lett. 2020, 9, 1379–1383. [Google Scholar] [CrossRef]
- Chadwick, A.J.; Goodbody, T.R.H.; Coops, N.C.; Hervieux, A.; Bater, C.W.; Martens, L.A.; White, B.; Röeser, D. Automatic Delineation and Height Measurement of Regenerating Conifer Crowns under Leaf-Off Conditions Using UAV Imagery. Remote Sens. 2020, 12, 4104. [Google Scholar] [CrossRef]
- Egli, S.; Höpke, M. CNN-Based Tree Species Classification Using High Resolution RGB Image Data from Automated UAV Observations. Remote Sens. 2020, 12, 3892. [Google Scholar] [CrossRef]
- Huang, C.M.; Lai, C.F. The Delay-Constrained and Network-Situation-Aware V2V2I VANET Data Offloading Based on the Multi-Access Edge Computing (MEC) Architecture. IEEE Open J. Veh. Technol. IEEE Wirel. Commun. Lett. 2020, 1, 331–347. [Google Scholar] [CrossRef]
- Yin, B.; Cheng, Y.; Cai, L.X.; Cao, X. Online SLA-aware multi-resource allocation for deadline sensitive jobs in edge-clouds. In Proceedings of the 2017 IEEE Global Communications Conference (GLOBECOM), Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- Liu, L.; Chang, Z.; Guo, X.; Mao, S.; Ristaniemi, T. Multiobjective optimization for computation offloading in fog computing. IEEE Internet Things J. 2018, 5, 283–294. [Google Scholar] [CrossRef]
- Narang, M.; Xiang, S.; Liu, W.; Gutierrez, J.; Chiaraviglio, L. UAV-assisted edge infrastructure for challenged networks. In Proceedings of the 2017 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Atlanta, GA, USA, 1–4 May 2017; pp. 60–65. [Google Scholar]
- Hou, X.; Li, Y.; Chen, M.; Wu, D.; Jin, D.; Chen, S. Vehicular fog computing: A viewpoint of vehicle as the infrastructures. IEEE Trans. Veh. Technol. 2016, 65, 3860–3873. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, Z.; Yu, R.; Zhang, Y. Low-latency caching with auction game in vehicular edge computing. In Proceedings of the 2017 IEEE/CIC International Conference on Communications in China (ICCC), Qingdao, China, 22–24 October 2017; pp. 1–6. [Google Scholar]
- Azmat, M.; Kummer, S. Potential applications of unmanned ground and aerial vehicles to mitigate challenges of transport and logistics-related critical success factors in the humanitarian supply chain. Asian J. Sustain. Soc. Responsib. 2020, 5, 1–22. [Google Scholar] [CrossRef] [Green Version]
- Liu, P.; Liu, J. Selfish or Utilitarian Automated Vehicles? Deontological Evaluation and Public Acceptance. Int. J. Hum. Comput. Interact. 2021. [Google Scholar] [CrossRef]
- Zaabi, A.O.A.; Yeun, C.Y.; Damiani, E. Autonomous Vehicle Security: Conceptual Model. In Proceedings of the 2019 IEEE Transportation Electrification Conference and Expo, Asia-Pacific (ITEC Asia-Pacific), Seogwipo, Korea, 8–10 May 2019; pp. 1–5. [Google Scholar]
- Oubbati, O.S.; Lakas, A.; Zhou, F.; Güneş, M.; Yagoubi, M.B. A survey on position-based routing protocols for flying ad hoc networks (FANETs). Veh. Commun. 2017, 10, 29–56. [Google Scholar] [CrossRef]
- Zhai, D.; Li, H.; Tang, X.; Zhang, R.; Ding, Z.; Yu, F.R. Height Optimization and Resource Allocation for NOMA Enhanced UAV-Aided Relay Networks. IEEE Trans. Commun. 2021, 69, 962–975. [Google Scholar] [CrossRef]
- Cao, H.; Hu, Y.; Yang, L. Towards intelligent virtual resource allocation in UAVs-assisted 5G networks. Comput. Netw. 2021, 185, 107660. [Google Scholar] [CrossRef]
- He, Y.; Tang, X.; Zhang, R.; Du, X.; Zhou, D.; Guizani, M. A Course-Aware Opportunistic Routing Protocol for FANETs. IEEE Access 2019, 7, 144303–144312. [Google Scholar] [CrossRef]
- Zhou, Y.; Cheng, N.; Lu, N.; Shen, X.S. Multi-UAV-aided networks: Aerial-ground cooperative vehicular networking architecture. IEEE Veh. Technol. Mag. 2015, 10, 36–44. [Google Scholar] [CrossRef]
- Zhang, N.; Zhang, S.; Yang, P.; Alhussein, O.; Zhuang, W.; Shen, X.S. Software Defined Space-Air-Ground Integrated Vehicular Networks: Challenges and Solution. IEEE Commun. Mag. 2017, 55, 101–109. [Google Scholar] [CrossRef] [Green Version]
- Oubbati, O.S.; Chaib, N.; Lakas, A.; Lorenz, P.; Rachedi, A. UAV-Assisted Supporting Services Connectivity in Urban VANETs. IEEE Trans. Veh. Technol. 2019, 68, 3944–3951. [Google Scholar] [CrossRef] [Green Version]
- He, Y.; Zhai, D.; Wang, D.; Tang, X.; Zhang, R. A Relay Selection Protocol for UAV-Assisted VANETs. Appl. Sci. 2020, 10, 8762. [Google Scholar] [CrossRef]
- Seliem, H.; Shahidi, R.; Ahmed, M.H.; Shehata, M.S. Drone-Based Highway-VANET and DAS Service. IEEE Access 2018, 6, 20125–20137. [Google Scholar] [CrossRef]
- Fawaz, W.; Atallah, R.; Assi, C.; Khabbaz, M. Unmanned Aerial Vehicles as Store-Carry-Forward Nodes for Vehicular Networks. IEEE Access 2017, 5, 23710–23718. [Google Scholar] [CrossRef]
- Bai, T.; Wang, J.; Ren, Y.; Hanzo, L. Energy-Efficient Computation Offloading for Secure UAV-Edge-Computing Systems. IEEE Trans. Veh. Technol. 2019, 68, 6074–6087. [Google Scholar] [CrossRef] [Green Version]
- Oubbati, O.S.; Lakas, A.; Lagraa, N.; Yagoubi, M.B. UVAR: An intersection UAV-assisted VANET routing protocol. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference (WCNC), Doha, Qatar, 3–6 April 2016; pp. 1–6. [Google Scholar]
- Athukoralage, D.; Guvenc, I.; Saad, W.; Bennis, M. Regret based learning for UAV assisted LTE-U/WiFi public safety networks. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–7. [Google Scholar]
- Mozaffari, M.; Saad, W.; Bennis, M.; Debbah, M. Unmanned aerial vehicle with underlaid device-to-device communications: Performance and tradeoffs. IEEE Trans. Wirel. Commun. 2016, 15, 3949–3963. [Google Scholar] [CrossRef]
- Veeranampalayam Sivakumar, A.N.; Li, J.; Scott, S.; Psota, E.; Jhala, A.J.; Luck, J.D.; Shi, Y. Comparison of Object Detection and Patch-Based Classification Deep Learning Models on Mid-to Late-Season Weed Detection in UAV Imagery. Remote Sens. 2020, 12, 2136. [Google Scholar] [CrossRef]
- Baur, J.; Steinberg, G.; Nikulin, A.; Chiu, K.; de Smet, T.S. Applying Deep Learning to Automate UAV-Based Detection of Scatterable Landmines. Remote Sens. 2020, 12, 859. [Google Scholar] [CrossRef] [Green Version]
- Machefer, M.; Lemarchand, F.; Bonnefond, V.; Hitchins, A.; Sidiropoulos, P. Mask R-CNN Refitting Strategy for Plant Counting and Sizing in UAV Imagery. Remote Sens. 2020, 12, 3015. [Google Scholar] [CrossRef]
- Mukherjee, A.; Misra, S.; Chandra, V.S.P.; Obaidat, M.S. Resource-Optimized Multiarmed Bandit-Based Offload Path Selection in Edge UAV Swarms. IEEE Internet Things 2019, 6, 4889–4896. [Google Scholar] [CrossRef]
- Yang, M.-D.; Tseng, H.-H.; Hsu, Y.-C.; Tsai, H.P. Semantic Segmentation Using Deep Learning with Vegetation Indices for Rice Lodging Identification in Multi-date UAV Visible Images. Remote Sens. 2020, 12, 633. [Google Scholar] [CrossRef] [Green Version]
- Mukherjee, A.; Misra, S.; Chandra, V.S.P.; Raghuwanshi, N.S. ECoR: Energy-Aware Collaborative Routing for Task Offload in Sustainable UAV Swarms. IEEE Trans. Sustain. Comput. 2020, 5, 514–525. [Google Scholar] [CrossRef]
- Mukherjee, A.; Misra, S.; Sukrutha, A.; Raghuwanshi, N.S. Distributed aerial processing for IoT-based edge UAV swarms in smart farming. Comput. Netw. 2020, 167, 107038. [Google Scholar] [CrossRef]
- Wu, Y.; Zheng, J. Modeling and Analysis of the Downlink Local Delay in MEC-Based VANETs. IEEE Trans. Veh. Technol. 2020, 69, 6619–6630. [Google Scholar] [CrossRef]
- Li, G.; Li, X.; Sun, Q.; Boukhatem, L.; Wu, J. An Effective MEC Sustained Charging Data Transmission Algorithm in VANET-Based Smart Grids. IEEE Access 2020, 8, 101946–101962. [Google Scholar] [CrossRef]
- Wu, Y.; Zheng, J. Analysis of the Uplink Local Delay in an MEC-Based VANET. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–7. [Google Scholar]
- Li, M.; Gao, J.; Zhao, L.; Shen, X. Deep Reinforcement Learning for Collaborative Edge Computing in Vehicular Networks. IEEE Trans. Cogn. Commun. Netw. 2016, 15, 3949–3963. [Google Scholar] [CrossRef]
- He, Y.; Zhai, D.; Zhang, R.; Du, X.; Zhou, D.; Guizani, M. An Anti-Interference Scheme for UAV Information Link in Air-Ground Integrated Vehicular Networks. Sensors 2019, 19, 4742. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Qi, Q.; Wang, J.; Ma, Z.; Sun, H.; Cao, Y.; Zhang, L.; Liao, J. Knowledge-Driven Service Offloading Decision for Vehicular Edge Computing: A Deep Reinforcement Learning Approach. IEEE Trans. Veh. Technol. 2019, 68, 4192–4203. [Google Scholar] [CrossRef]
- Wang, X.; Ning, Z.; Wang, L. Offloading in Internet of Vehicles: A fog-enabled real-time traffic management system. IEEE Trans. Ind. Informat. 2018, 14, 4568–4578. [Google Scholar] [CrossRef]
- Sun, Y.; Guo, X.; Song, J.; Zhou, S.; Jiang, Z.; Liu, X.; Niu, Z. Adaptive Learning-Based Task Offloading for Vehicular Edge Computing Systems. IEEE Trans. Veh. Technol. 2019, 68, 3061–3074. [Google Scholar] [CrossRef] [Green Version]
- Ning, Z.; Kwok, R.Y.K.; Zhang, K.; Wang, X.; Obaidat, M.S.; Guo, L.; Hu, X.; Hu, B.; Guo, Y.; Sadoun, B. Joint computing and caching in 5G-envisioned Internet of Vehicles: A deep reinforcement learning-based traffic control system. IEEE Trans. Intell. Transp. Syst. 2020. [Google Scholar] [CrossRef]
- Yu, Y.; Zhang, J.; Letaief, K.B. Joint subcarrier and CPU time allocation for mobile edge computing. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar]
- Wang, F.; Xu, J.; Wang, X.; Cui, S. Joint offloading and computing optimization in wireless powered mobile-edge computing systems. IEEE Trans. Wirel. Commun. 2018, 17, 1784–1797. [Google Scholar] [CrossRef]
- Mao, Y.; Zhang, J.; Letaief, K.B. Dynamic computation offloading for mobile-edge computing with energy harvesting devices. IEEE J. Sel. Areas Commun. 2016, 34, 3590–3605. [Google Scholar] [CrossRef] [Green Version]
- Dai, Y.; Xu, D.; Maharjan, S.; Zhang, Y. Joint Load Balancing and Offloading in Vehicular Edge Computing and Networks. IEEE Internet Things 2019, 6, 4377–4387. [Google Scholar] [CrossRef]
- You, C.; Huang, K.; Chae, H.; Kim, B.H. Energy-efficient resource allocation for mobile-edge computation offloading. IEEE Trans. Wirel. Commun. 2017, 16, 1397–1411. [Google Scholar] [CrossRef]
- Dong, L.; Ni, Q.; Wu, W.; Huang, C.; Znati, T.; Du, D.Z. A Proactive Reliable Mechanism-Based Vehicular Fog Computing Network. IEEE Internet Things J. 2020, 7, 11895–11907. [Google Scholar] [CrossRef]
- Chen, X.; Jiao, L.; Li, W.; Fu, X. Efficient multi-user computation offloading for mobile-edge cloud computing. IEEE/ACM Trans. Netw. 2016, 24, 2795–2808. [Google Scholar] [CrossRef] [Green Version]
- Li, M.; Cheng, N.; Gao, J.; Wang, Y.; Zhao, L.; Shen, X. Energy-Efficient UAV-Assisted Mobile Edge Computing: Resource Allocation and Trajectory Optimization. IEEE Trans. Veh. Technol. 2020, 69, 3424–3438. [Google Scholar] [CrossRef]
- Alioua, A.; Djeghri, H.; Cherif, M.E.T.; Senouci, S.M.; Sedjelmaci, H. UAVs for traffic monitoring: A sequential game-based computation offloading/sharing approach. Comput. Netw. 2020, 177, 107273. [Google Scholar] [CrossRef]
- Klapez, M.; Grazia, C.A.; Casoni, M. Application-Level Performance of IEEE 802.11p in Safety-Related V2X Field Trials. IEEE Internet Things J. 2020, 7, 3850–3860. [Google Scholar] [CrossRef]
- Han, C.; Dianati, M.; Tafazolli, R.; Kernchen, R. Throughput Analysis of the IEEE 802.11p Enhanced Distributed Channel Access Function in Vehicular Environment. In Proceedings of the 2010 IEEE 72nd Vehicular Technology Conference-Fall, Ottawa, ON, Canada, 6–9 September 2010; pp. 1–5. [Google Scholar]
- Mjeku, M.; Gomes, N.J. Analysis of the Request to Send/Clear to Send Exchange in WLAN Over Fiber Networks. J. Lightw. Technol. 2008, 26, 2531–2539. [Google Scholar] [CrossRef]
- Zhai, D.; Zhang, R. Joint Admission Control and Resource Allocation for Multi-Carrier Uplink NOMA Networks. IEEE Wirel. Commun. Lett. 2018, 7, 922–925. [Google Scholar] [CrossRef]
- Srinivas, S.T.P.; Shanti Swarup, K. A New Mixed Integer Linear Programming Formulation for Protection Relay Coordination Using Disjunctive Inequalities. IEEE Power Energy Technol. Syst. J. 2019, 6, 104–112. [Google Scholar] [CrossRef]
- Zhai, D.; Zhang, R.; Cai, L.; Yu, F.R. Delay Minimization for Massive Internet of Things with Non-Orthogonal Multiple Access. IEEE J. Sel. Top. Signal Process. 2019, 13, 553–566. [Google Scholar] [CrossRef]
- Secinti, G.; Canberk, B.; Duong, T.Q.; Shu, L. Software Defined Architecture for VANET: A Testbed Implementation with Wireless Access Management. IEEE Commun. Mag. 2017, 55, 135–141. [Google Scholar] [CrossRef]
- Antoniou, A.; Lu, W.S. Practical Optimization: Algorithm and Engineering Applications; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar]

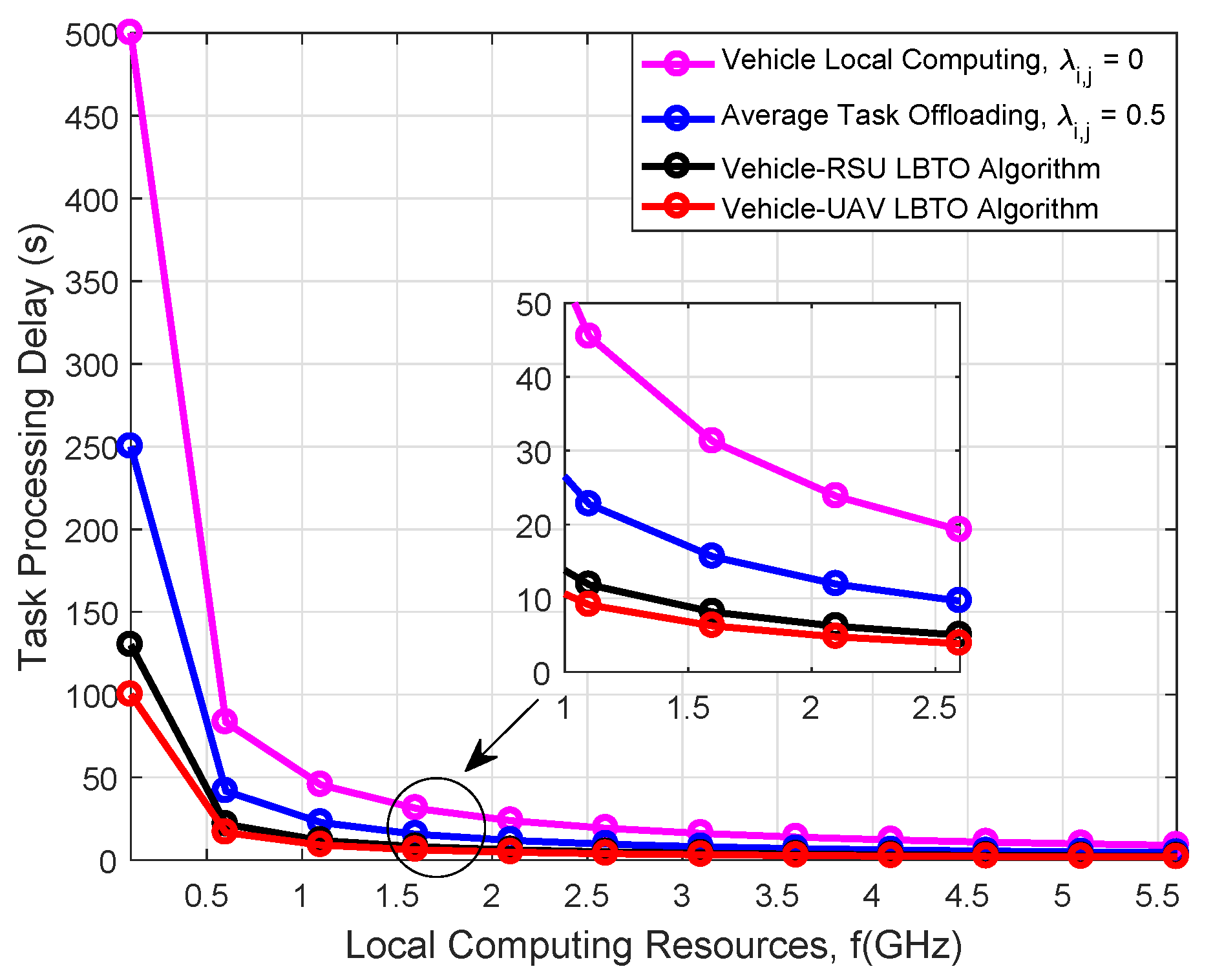
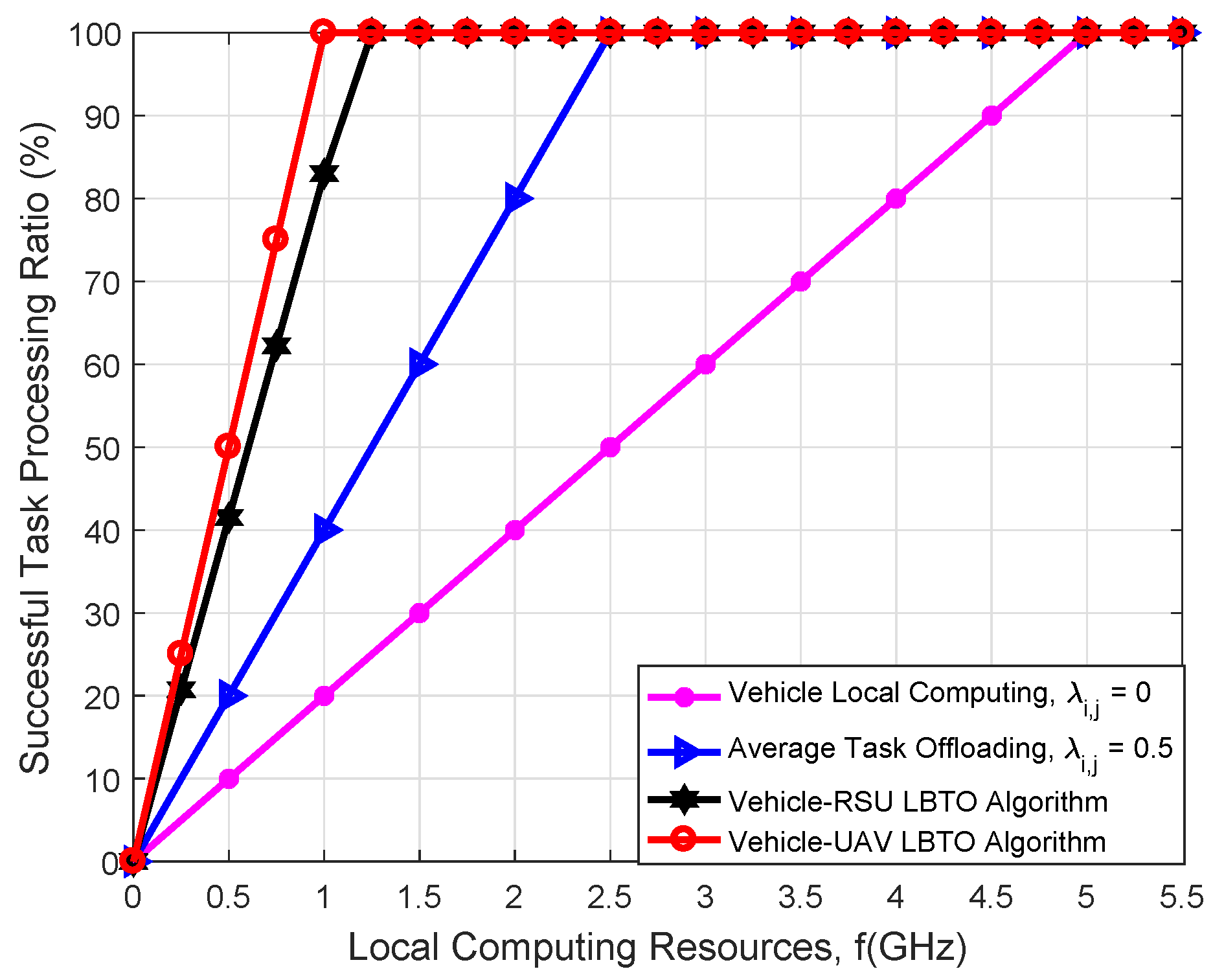
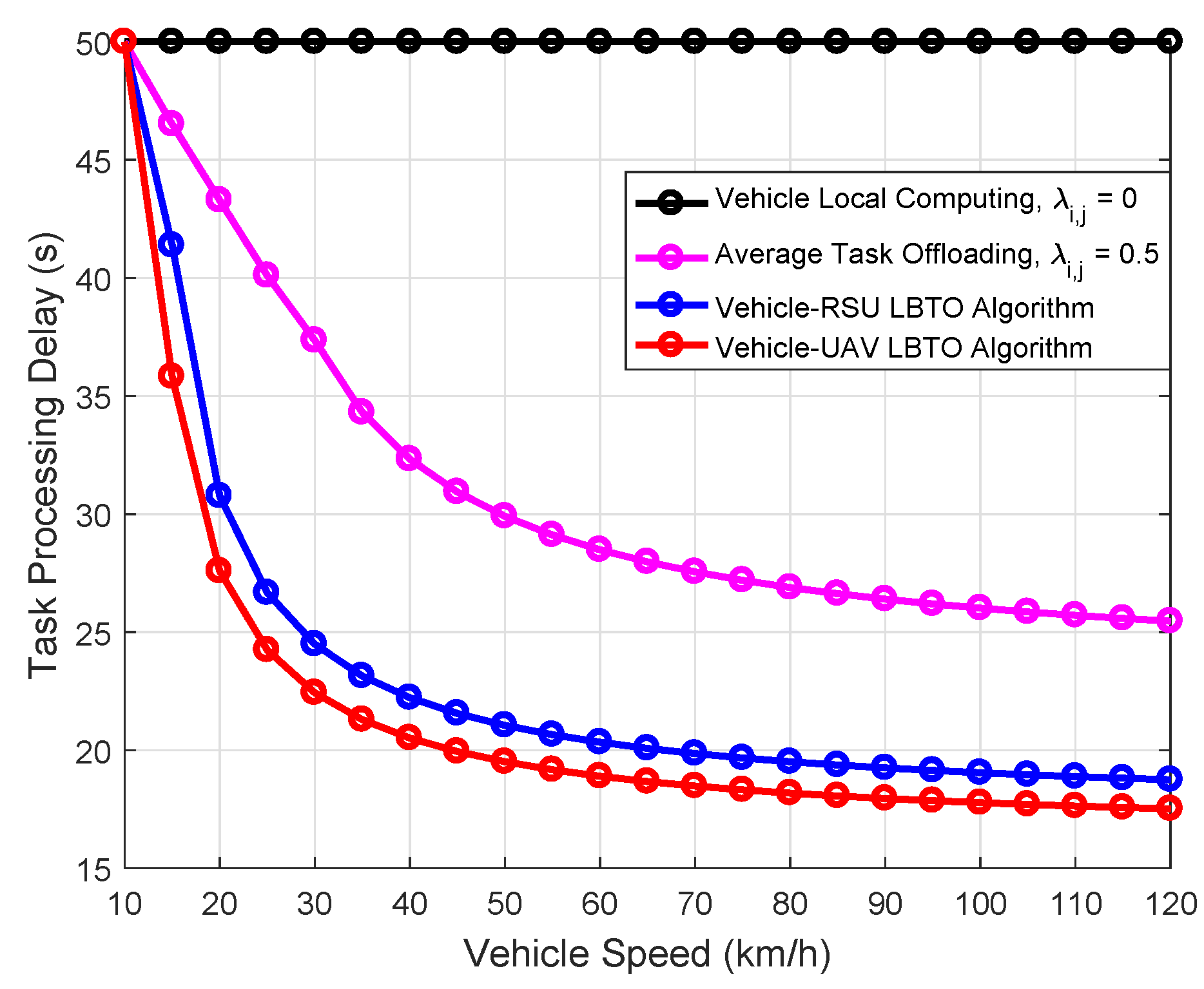
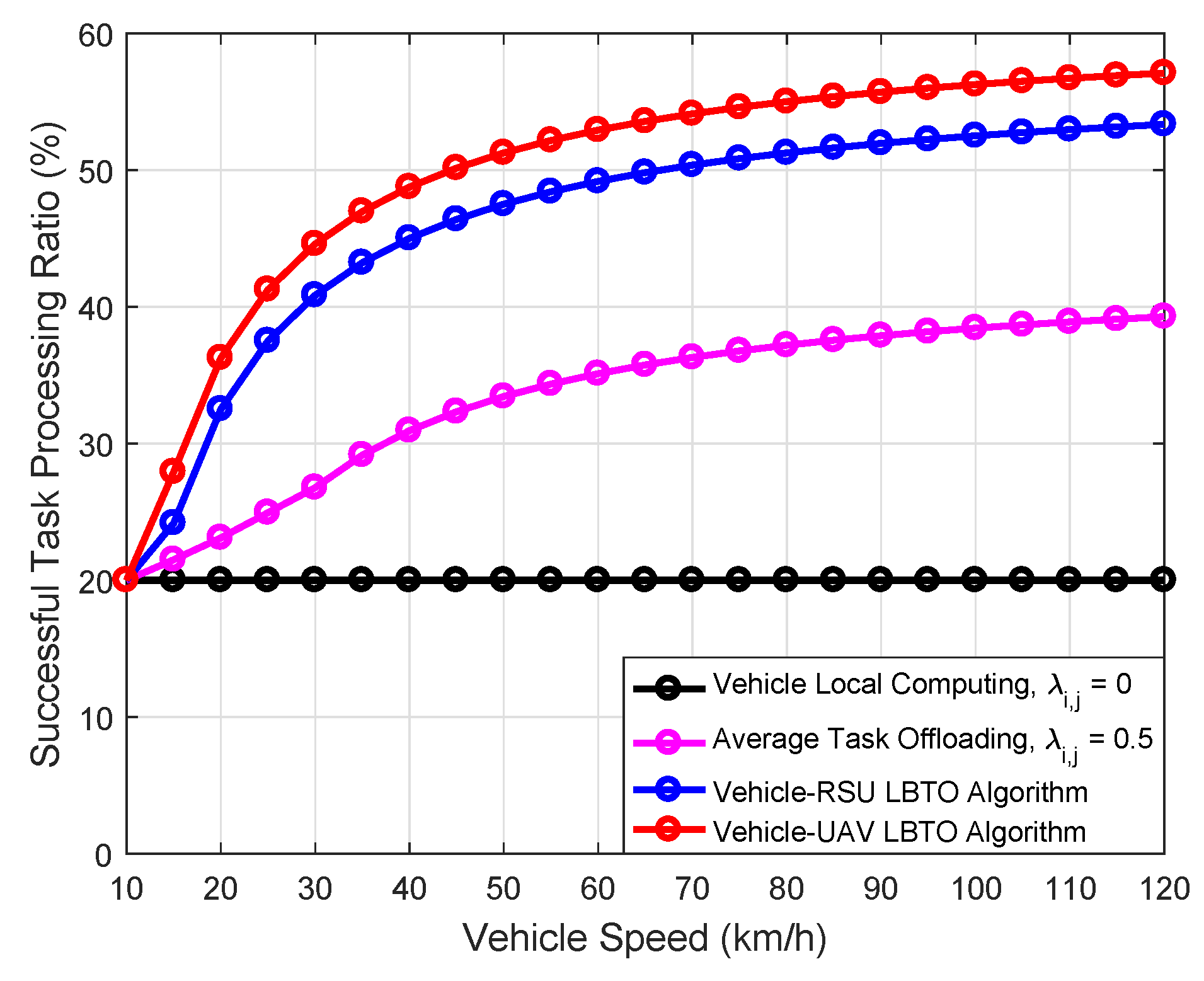
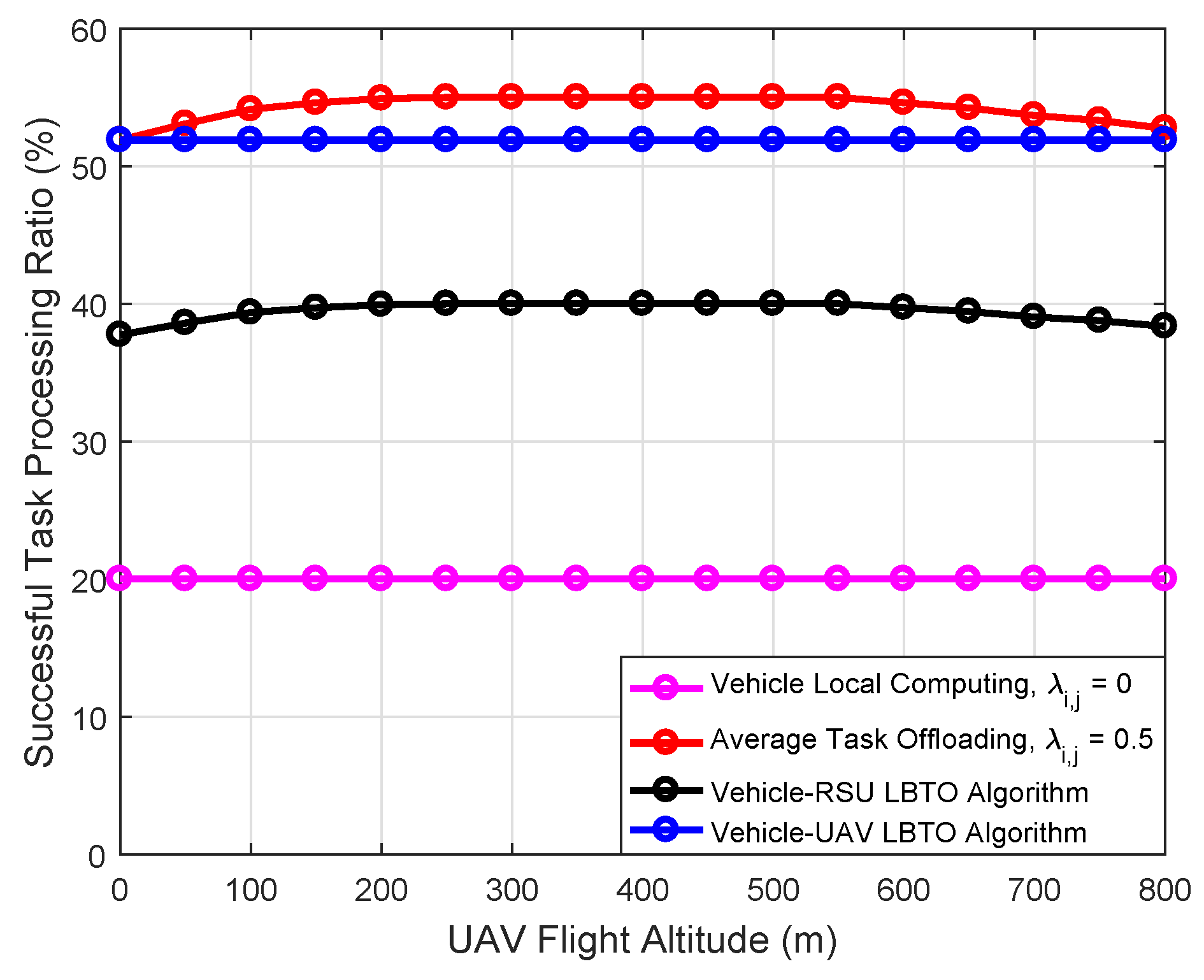
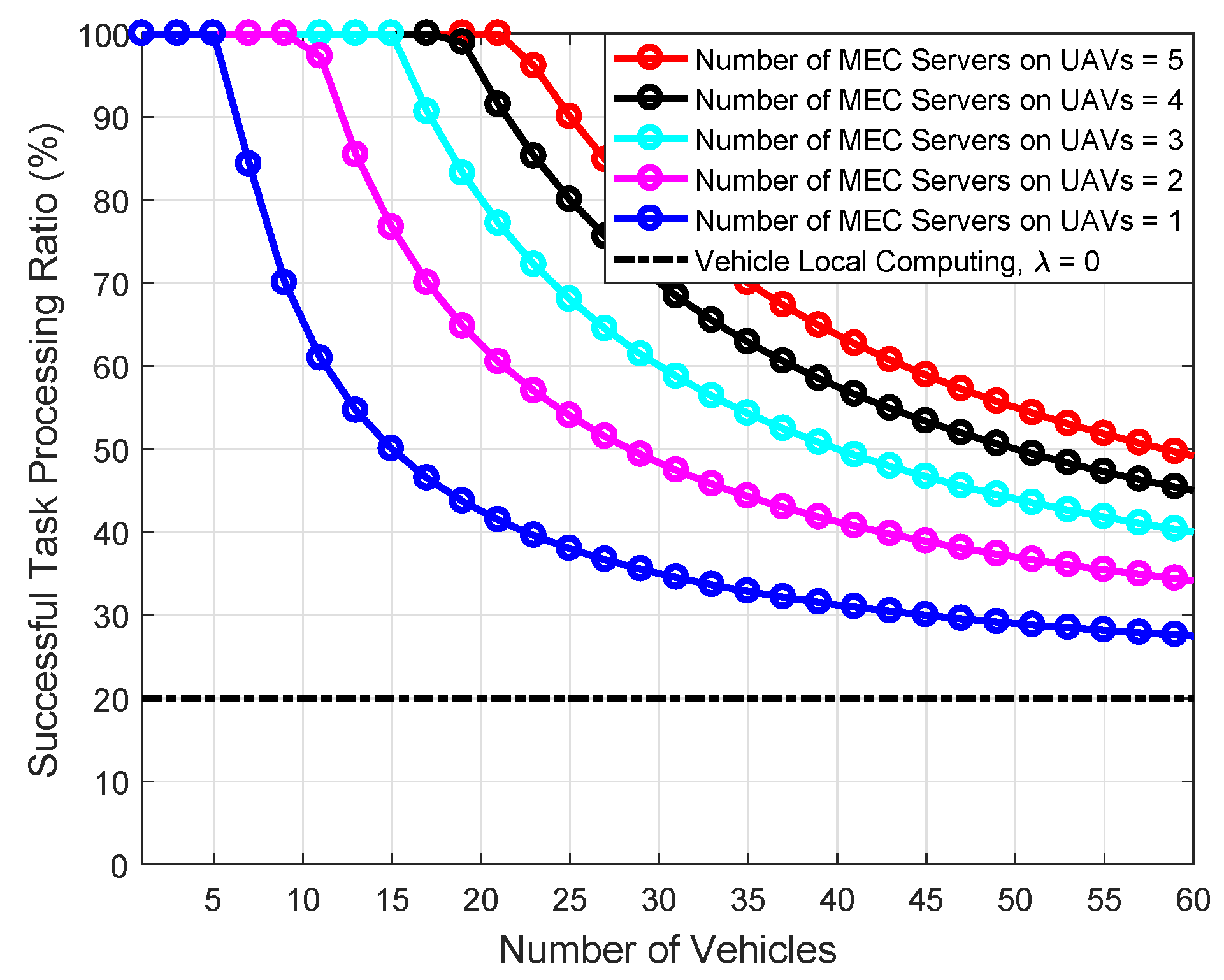
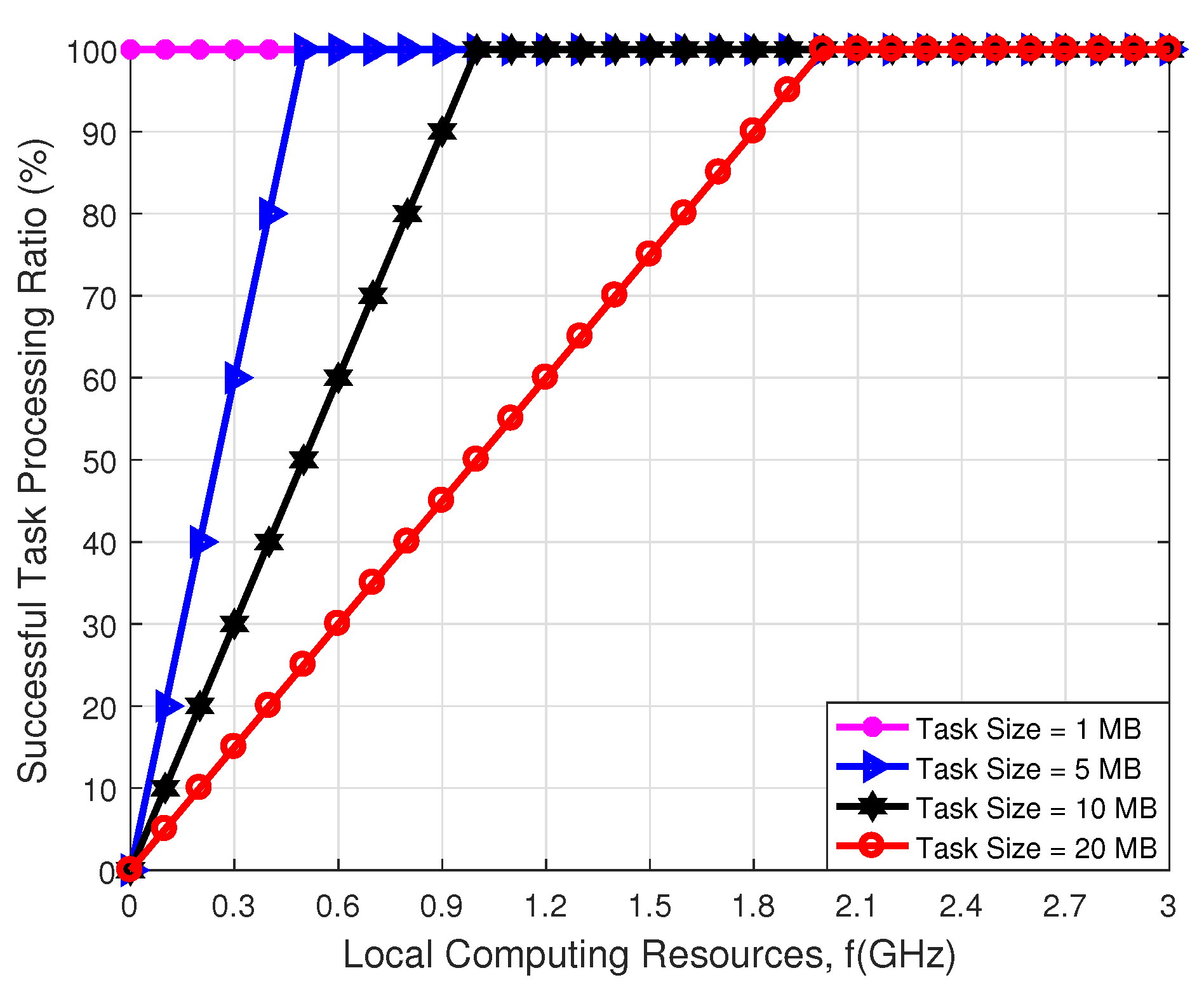
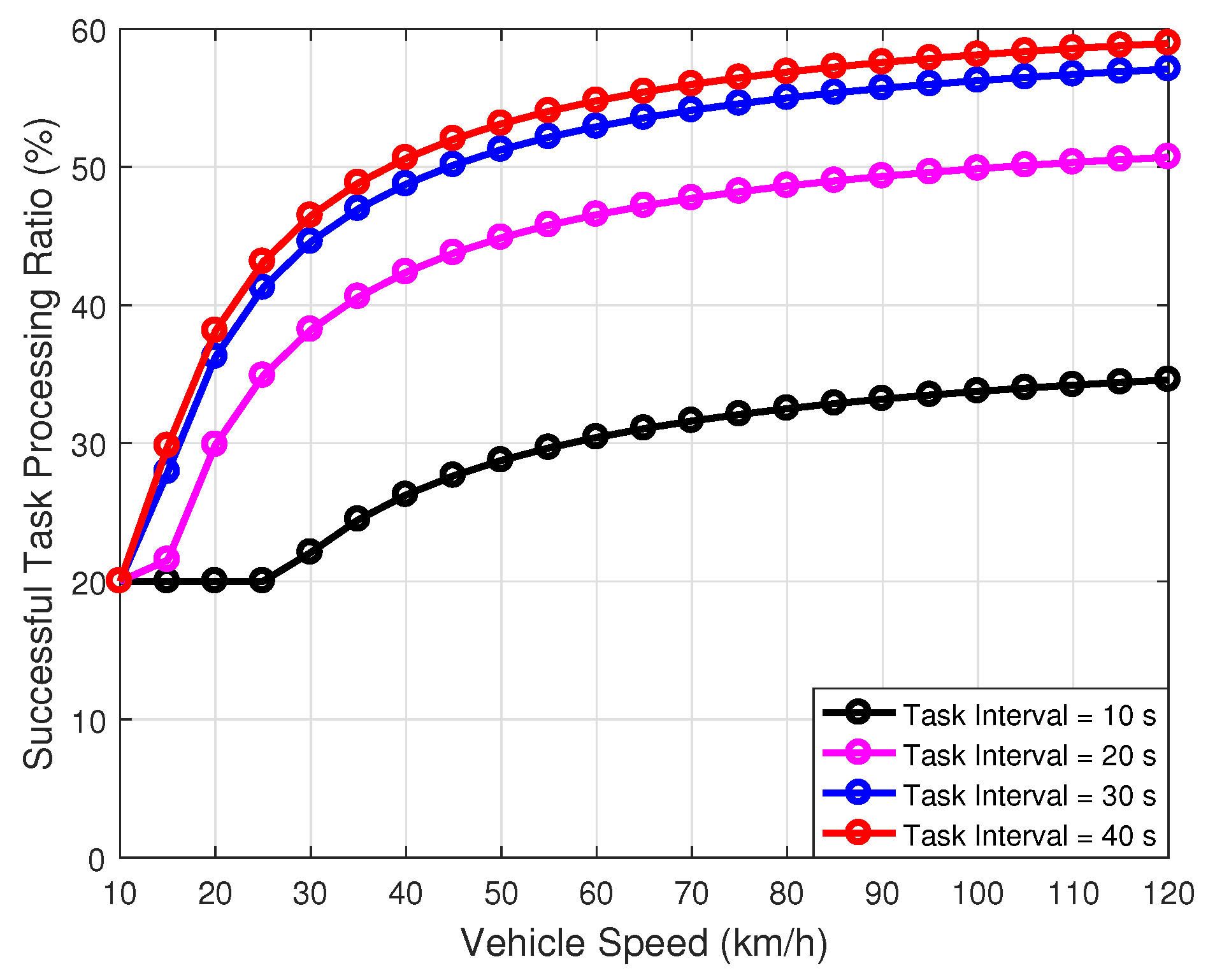
| Parameter | Value |
|---|---|
| Vehicle transmission power | 1 Watt |
| UAV transmission power | 5 Watt |
| Number of UAVs | 5 |
| Number of vehicles | [0, 60] |
| UAV computing resources | 20 GHz |
| Vehicle computing resources | 1 GHz |
| Task size | 10 MB |
| Task interval | 30 s |
| Task maximum allowed latency | 10 s |
| Simulation times | 1000 |
| No. | Research Questions. |
|---|---|
| 1 | As the obstructions of vehicles can affect the service quality of vehicle-RSU links, how can we improve the connectivity of VANETs? |
| 2 | As the obstructions of vehicles can affect the service quality of vehicle-RSU links, how can we improve the connectivity of VANETs? |
| 3 | How do we minimize the task processing delay for MEC-enabled UAV-assisted VANETs by jointly considering the task offloading, the resource allocation, and the security assurance? |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, Y.; Zhai, D.; Huang, F.; Wang, D.; Tang, X.; Zhang, R. Joint Task Offloading, Resource Allocation, and Security Assurance for Mobile Edge Computing-Enabled UAV-Assisted VANETs. Remote Sens. 2021, 13, 1547. https://doi.org/10.3390/rs13081547
He Y, Zhai D, Huang F, Wang D, Tang X, Zhang R. Joint Task Offloading, Resource Allocation, and Security Assurance for Mobile Edge Computing-Enabled UAV-Assisted VANETs. Remote Sensing. 2021; 13(8):1547. https://doi.org/10.3390/rs13081547
Chicago/Turabian StyleHe, Yixin, Daosen Zhai, Fanghui Huang, Dawei Wang, Xiao Tang, and Ruonan Zhang. 2021. "Joint Task Offloading, Resource Allocation, and Security Assurance for Mobile Edge Computing-Enabled UAV-Assisted VANETs" Remote Sensing 13, no. 8: 1547. https://doi.org/10.3390/rs13081547
APA StyleHe, Y., Zhai, D., Huang, F., Wang, D., Tang, X., & Zhang, R. (2021). Joint Task Offloading, Resource Allocation, and Security Assurance for Mobile Edge Computing-Enabled UAV-Assisted VANETs. Remote Sensing, 13(8), 1547. https://doi.org/10.3390/rs13081547