Abstract
In this paper, we propose a mobile edge computing (MEC)-enabled unmanned aerial vehicle (UAV)-assisted vehicular ad hoc network (VANET) architecture, based on which a number of vehicles are served by UAVs equipped with computation resource. Each vehicle has to offload its computing tasks to the proper MEC server on the UAV due to the limited computation ability. To counter the problems above, we first model and analyze the transmission model and the security assurance model from the vehicle to the MEC server on UAV, and the task computation model of the local vehicle and the edge UAV. Then, the vehicle offloading problem is formulated as a multi-objective optimization problem by jointly considering the task offloading, the resource allocation, and the security assurance. For tackling this hard problem, we decouple the multi-objective optimization problem as two subproblems and propose an efficient iterative algorithm to jointly make the MEC selection decision based on the criteria of load balancing and optimize the offloading ratio and the computation resource according to the Lagrangian dual decomposition. Finally, the simulation results demonstrate that our proposed scheme achieves significant performance superiority compared with other schemes in terms of the successful task processing ratio and the task processing delay.
1. Introduction
With the increasing number of vehicles and the rising popularity of on-board applications, vehicular ad hoc networks (VANETs) have attracted extensive attention in recent years [1]. As an important application of intelligent transport systems (ITSs), VANETs have been widely used in the traffic prediction, road safety, and driver behavior detection fields [2]. In VANETs, the cellular network (CN) and the IEEE 802.11p wireless access are the two most common communication strategies. Vehicles can obtain the traffic-related content directly from the service providers by using a CN, or indirectly from road side units (RSUs) by using IEEE 802.11p protocol. Due to the bulk data transmissions, the CN faces the challenge of network congestion [3]. An efficient method to solve the congestion issue is enabling the vehicles to acquire the traffic-related content from the RSU, instead of obtaining it from the CN.
However, the obstructions of vehicles affect the vehicle–RSU links, which degrade the service quality [4]. UAVs equipped with communication devices can be used as air base stations (BSs) [5]. As UAVs can be flexibly deployed and freely move in 3D space, the air-to-ground wireless channel (higher probability with LOS links) is usually better than the ground-to-ground counterpart [6]. Therefore, the UAV-assisted VANETs have great potential in improving the quality-of-service (QoS) vehicle-related applications [7].
In addition, the computation ability of most vehicles is limited, and multiple latency sensitive tasks cannot be fully processed within the allowed latency, such as the traffic information, the security applications, etc. [8]. To solve the limitations of vehicle computation ability, mobile edge computing (MEC) can be used. MEC can extend the computation ability to VANETs edge and satisfy the needs of data access demands. The work in [9] proposed a multi-resource allocation scheme to accommodate deadline sensitive tasks in VANETs. Liu et al. in [10] adopted the queuing theory to study multi-user vehicle-mounted MEC systems by jointly considering the system delay and the energy consumption. Moreover, the researchers of [11] devised a MEC infrastructure adopting UAVs, and they evaluated the performance of the MEC server mounted on the UAV in terms of user coverage. Furthermore, the authors of [12] proposed the concept of vehicular fog computing (VFC) by utilizing vehicles and RSUs as the infrastructures for computation. Similarly, Wang et al. [13] proposed a vehicular edge computing (VEC) caching scheme to minimize the average latency to mobile vehicles.
The above works in [9,10,11,12,13] have enhanced VANETs’ computation ability to achieve significant performance. Nevertheless, there are still some deficiencies to be tackled. On the one hand, the authors of [9,10] consider that all mobile users have to offload their tasks to only one MEC server. Thus, all tasks cannot be fully cannot be processed within the allowed latency threshold. On the other hand, the works of [11,12,13] cannot balance the load among MEC servers, which are unable to cope with the huge computation demands generated by urban ITS. In addition, the researchers of [9,10,11,12,13] ignore the impact of the physical layer security performance on the VANETs, which results in great limitations to apply these schemes in practical vehicle networking applications.
Motivated by the above discussions, we study jointly the task offloading, the resource allocation, and the security assurance problem for the UAV-assisted VANETs. As shown in Figure 1, we investigate the MEC architecture in UAV-assisted VANETs. Specifically, UAVs can collect the traffic density information and the state of vehicles connectivity on the ground and exchange them with vehicles through the vehicle-to-everything (V2X) communications. The MEC architecture can reduce the computational delay, reduce energy requirement, and improve the computation ability by distributing the latency-sensitive tasks to MEC servers around the vehicles, which can be widely used in the automatic drive, the multimedia entertainment service, the intelligent traffic management, and the geographic information service. The main contributions are summarized as follows.
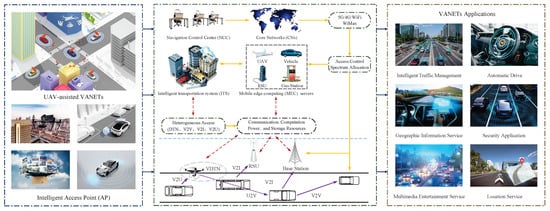
Figure 1.
A mobile edge computing (MEC) architecture in unmanned aerial vehicle (UAV)-assisted vehicular ad hoc networks (VANETs).
- We propose an MEC-enabled UAV-assisted VANET to provide vehicles with the low latency and reliable computing services through UAVs. Specifically, we adopt comprehensive task processing delay as the optimization objective by jointly considering the transmission model and the security assurance model from the vehicle to the MEC server on UAV, and the task computation model of the local vehicle and the edge UAV.
- We design a network optimization scheme by jointly considering the task offloading, the resource allocation, and the security assurance for VANETs. Moreover, to fully exploit the advantages of the MEC-enabled UAV-assisted VANET architecture, we use UAVs for boosting VANETs communications to improve VANETs’ computation ability. Furthermore, we propose an efficient iterative algorithm based the relax-and-rounding method and the Lagrangian method, which can effectively solve the joint optimization problem.
- We conduct simulations to evaluate the performance of our proposed scheme. The simulation results indicate that our designed MEC-enabled UAV-assisted VANET architecture is superior to the traditional ground-based VANETs. In addition, our proposed scheme can achieve significant performance superiority compared with other schemes in the successful task processing ratio and the task processing delay.
This paper is organized as follows. Section 2 overviews the related works. In Section 3, we introduce the considered system model and problem formulation. Section 4 describes the proposed scheme. Simulation results are presented in Section 5, after which a discussion is presented in Section 6. Finally, we conclude our paper in Section 7.
2. Related Works
2.1. UAV-Assisted VANETs
VANETs have paved the path to numerous road safety applications, which can share critical information about the automatic drive with security services [14]. However, the existing obstructions and the high mobility of vehicles can disturb the communication links between vehicles and RSUs, resulting in many disconnections [15]. Recently in modern cities, the number of UAVs has increased significantly. UAVs can be considered as suitable candidates to improve the connectedness of VANETs, which have been used to relay and process mobile messages for ground terminals [16,17,18,19]. Based on this concept, the UAVs can form an aerial subnetwork in the sky and assist ground vehicles to communicate.
Due to their flexible mobility, the works in [20,21] proposed that the UAVs can act as the relay nodes when the ground VANETs encounter a disconnection. In [22], Zhang et al. designed a software-defined space air–ground-integrated network architecture for supporting diverse vehicular services in a seamless, efficient, and cost-effective manner. In [23], Oubbati et al. proposed UAVs that can cooperate with existing ground vehicles, which can make the data delivery more reliable and guarantee robust paths. The above works in [20,21,22,23] consider the UAV-assisted VANET is a fully connected network, which is unreasonable. This is because one of the characteristics of UAVs and vehicles is that they are highly mobile and therefore the UAV-assisted VANET has intermittent connectivity. Therefore, the authors of [24,25] proposed that UAV-assisted VANETs can be regarded as the vehicular delay tolerant networks (VDTNs). UAVs can assist the ground vehicle in data transmission by the storage-carry-forward (SCF) method [26]. Additionally, the authors of [27,28,29,30] proposed UAVs can be deployed to help ground vehicles find communication paths for their message. In addition, the researchers of [31,32,33] proposed that UAV-based remote sensing can apply deep learning techniques to UAV-assisted VANETs. Furthermore, Mukherjee et al., in [34,35], study UAV-assisted MEC and aim to maximize UAV energy efficiency by jointly optimizing the UAV trajectory, the user transmit power, and computation load allocation. In [36], the authors proposed an Energy-aware Collaborative Routing (ECoR) scheme for optimally handling task offloading between source and destination UAVs in a grid-locked UAV swarm. The work in [37] addressed the challenges of a decentralized and heterogeneous UAV swarm deployment and proposed a Nash bargaining-based weighted intra-Edge processing offload scheme to mitigate the problem of heavy processing in some of the swarm members. The difference is that the UAV deployment problem is not considered in this paper. We consider a unidirectional road, where UAVs are randomly located along the road and investigate the MEC technique for UAV-assisted VANETs that aims at minimizing the task processing delay.
2.2. MEC-Enabled UAV-Assisted VANETs
The MEC technique have been widely applied to improve the successful task processing ratio in VANETs [38,39,40]. The MEC technique brings the computing ability and the storage resource to the edge of the network, which can enable the computing ability and the storage resource in close proximity to users. Therefore, the task offloading problem has been investigated in many researches in the context of VANETs [41,42,43,44]. In those works, the main objective is to minimize task processing delay by selecting the optimal MEC server, while the load balancing is not taken into account. Aiming at this problem, the authors of [45,46] focused on task offloading and execution utilizing the computing resources on vehicles to load balancing. Moreover, the works in [47,48,49,50] proposed to reduce task processing delay by offloading computation-heavy and latency-sensitive tasks to nearby RSUs or UAVs for remote execution. Furthermore, in [51,52,53], the offloading problem was studied with an objective to minimize the weighted sum of mobile energy consumption for a multiuser UAV-assisted VANET. The work in [54] designed a new system model where UAVs can offload and/or share intensive computation tasks with other nearby network nodes. Then, the authors of [55] used the computation response time, the energy consumed for the computation, the cost of cellular communication, and the computation cost as the main system metrics to make any computation offloading/sharing decisions that optimized the system performance. The difference is herein we propose a MEC-enabled UAV-assisted VANETs architecture, based on which a number of vehicles are served by UAVs equipped with computational resources. Each vehicle has to offload its computing tasks to the proper MEC server on UAV due to the limited computation ability. In addition, we assume that each vehicle can only select one MEC server for computational offloading.
2.3. Synthesis
Different from the above works, in this paper, we investigate the MEC technique for UAV-assisted VANETs. This is because most of the works neglect the task processing delay, in which the adjustment on workload allocation for a task can affect the performance of other tasks, which can reduce the overall performance of the network. Moreover, as a common feature of the existing works, the task offloading, the resource allocation, and the security assurance are independently utilized with different purposes. Motivated by this, in this paper, we propose a mobile edge computing framework for task offloading, resource allocation, and security assurance in UAV-assisted VANETs. To be more specific, each vehicle can select one appropriate MEC server on UAV and offload parts of the computation task, which can achieve load balancing and service reliability improvement by the task scheduling among edge MEC servers on UAVs.
3. System Model and Problem Formulation
In this section, we introduce the concerned system model and definitions, and then we formulate the multi-objective optimization problem by jointly considering the task offloading, the resource allocation, and the security assurance.
3.1. Network Model
As shown in Figure 2, we consider a unidirectional road, where M UAVs are located along the road. Each UAV is equipped with a MEC server with limited computing resources. We denote the ID set of UAVs as . For ease of description, we divide the road into M segments and denote the ID set of roads as .
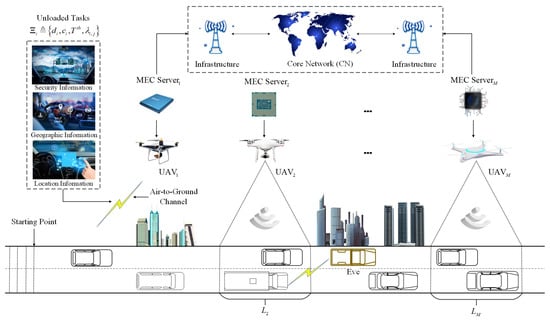
Figure 2.
Joint task offloading, resource allocation, and security assurance for MEC-enabled UAV-assisted VANETs.
There are N vehicles arriving at the starting point of the road (we denote the ID set of vehicles as ), and they obey the Poisson distribution. Each vehicle has a task to be processed (for example, the geographic information, the security information, and the location service information can be exchanged between vehicles and UAVs), expressed as , , , where represents the size of the computing task, represents the computing resources required for the execution of task , represents the task maximized allowed latency, and represents the ratio of the offloaded task to the total task. In other words, vehicle i can offload a task, , to the MEC server on UAV j and compute the rest of the task, , locally. In this scheme, we assume that each vehicle can only select one MEC server for computational offloading. We define as the selection decision of vehicle i, i.e., . Specifically, if vehicle i chooses UAV j for task offloading, , and otherwise. In addition, there is an eavesdropper in our concerned system model, denoted as Eve, that can eavesdrop the transmitted information .
Therefore, based on the above analysis, the task processing delay consists of three parts:
Part 1: The time that vehicle i moves from the starting point to the coverage of UAV j, i.e., , .
Part 2: The transmission time for vehicle i to offload the task to UAV j via a wireless channel.
Part 3: The time that for UAV j processes the task .
According to the above analysis, our proposed algorithm operation in the real scenario mainly includes the following steps. First, N vehicles arrive at the starting point of the road, and each vehicle has tasks waiting to be processed. Then, according to our proposed algorithm, each vehicle selects the MEC server and calculates the ratio of the offloaded task. Afterward, each vehicle uses the IEEE 802.11p protocol to transmit the unloading task. After receiving the unloading task, the MEC server on the UAV allocates computing resources to process the unloading task according to our proposed algorithm. Meanwhile, the vehicle processes the rest of the computing task locally. Finally, the MEC server on the UAV returns the processing results to the vehicle.
3.2. Transmission Model
The communication between vehicle and UAV is based on the IEEE 802.11p protocol, which adopts the carrier sense multiple access protocol with collision avoidance (CSMA/CA) for data transmission [56]. In the IEEE 802.11p protocol, the transmission of computing task within a single time slot has two states: (i) successful transmission and (ii) collision and back off. More specifically, the task can be successfully transmitted when the wireless channel is idle. If two vehicles try to transmit their computing tasks simultaneously, a collision occurs. According to the Markov chain [57], we define to represent the probability of vehicle i transmitting the task in a certain time slot (vehicle offloads its task to UAV in a random time slot). Let represent that there are at least two offloading tasks transmitted in the same time slot. Let and denote the probability of channel idle and the successful transmission probability between vehicle i and UAV j, respectively. We can get
According to (1)–(3), we have
where represents the maximum number of times to avoid, represents the maximum number of retransmissions, represents the minimum contention window, and represents the maximum contention window.
3.3. Task Computation Model
To reduce collisions, we take the request to send/clear to send (RTS/CTS) method into account [58]. As shown in Figure 3, before sending the task, the vehicle i needs to send an RTS control frame to request channel occupancy. Then, if the wireless channel is idle, UAV j can receive the RTS frame and reply with a CTS frame after the time interval SIFS. Afterward, vehicle i receives the CTS frame and starts sending the task after the time interval SIFS. Finally, UAV j responds with an ACK frame to vehicle i after receiving the task.
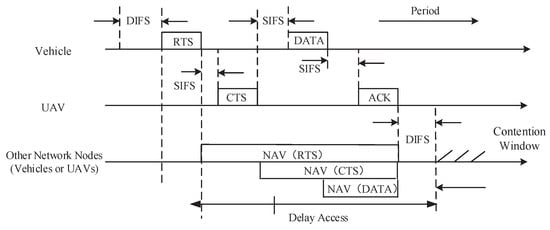
Figure 3.
Request to send/clear to send (RTS/CTS) method.
Therefore, we define the successful transmission task period between vehicle i and UAV j as , such that
where represents the task overhead of packet header, and represents the propagation delay. , , , , and represent the SIFS frame interval, the ACK frame interval, the DIFS frame interval, the RTS frame interval, and the CTS frame interval, respectively. In addition, represents the transmission delay, which can be written as
where represents the bandwidth of UAV j, represents the transmission power of vehicle i, represents the noise power at the receiver input, and represents the channel gain between vehicle i and UAV j.
Let denote the wireless channel collision period, which can be expressed as
Therefore, the normalized throughput can be calculated as
where represents the duration of a timeslot.
According to (5)–(8), the transmission time of task from vehicle i offloading to UAV j is given by
For the local computing task of vehicle i, the local computation time can be calculated as
where represents the local computing frequency of vehicle i (GHz/s).
The computing resources of UAV j are limited, so the limited computing resources need to be divided into N vehicles as evenly as possible to ensure that the task can be completed on time. Let denote the total computing frequency of UAV j and represent the computing frequency assigned to vehicle i by UAV j, i.e., . We have . The computing time of MEC server on UAV j can be expressed as
As the task can be executed in parallel on vehicle i and UAV j, the task processing delay can be expressed as
where represents the processing delay of MEC server on UAV j, .
3.4. Security Assurance Model
We adopt the wiretap coding scheme to protect the vehicle MEC. According to the Shannon formula, the channel capacity between the vehicle i and the UAV j is
For our proposed UAV-assisted VANETs, we assume that there is an eavesdropper, which can eavesdrop the transmitted information . To prevent eavesdroppers from eavesdropping transmitted information , we have
where represents the target secure transmission rate, represents the wiretap rate, and represents the maximized permitted wiretap rate.
3.5. Problem Formulation
In this paper, we focus on the UAV-assisted VANETs problem by jointly considering the task offloading, the resource allocation, and the security assurance that aims at minimizing the task processing delay. We formulate the optimization problem as follows:
In (15), C1.1 ensures that the local computation time and the processing delay of the MEC server on UAV j cannot exceed the task maximum allowed latency . C1.2 and C1.3 indicate that each vehicle selects only one MEC service for task offloading. C1.4 and C1.5 guarantee that the total amount of computing resources allocated by the MEC server to all tasks cannot exceed the total computation capacity of this MEC server. C1.6 and C1.7 represent that the total offloaded task of vehicle i cannot exceed 1. C1.8 guarantees the security of the transmission.
4. Joint Task Offloading, Resource Allocation, and Security Assurance Algorithm
In this section, we decouple the multi-objective optimization problem as two subproblems, i.e., the MEC server selection problem and the task offloading problem. Then, as shown in Figure 4, we use the relax-and-rounding method and the Lagrangian dual decomposition method to solve it. Finally, we propose an efficient iterative algorithm by jointly considering the task offloading, the resource allocation, and the security assurance.
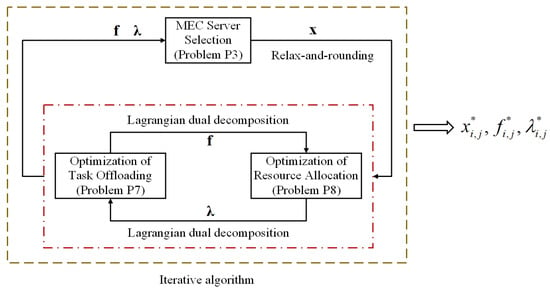
Figure 4.
General architecture of the proposed solution.
4.1. Problem Transformation
C1.3 is an integer constraint, thus the optimization problem P1 is mixed integer nonlinear programming, non-convex, and non-deterministic polynomials (NP) problem [59]. In order to solve P1, we set and transform P1 into an equivalent form as shown in Lemma 1.
Lemma 1.
The optimization problem P1 can be equivalently recast as the following problem P2.
Proof of Lemma 1.
See the Appendix A. □
Due to the highly complex coupling among optimization variables and mixed combinatorial feature, the solution of P2 is still challenging. Then, we further decouple the primal problem P2 into two subproblems, i.e., load balancing problem and task offloading problem. Specifically, we first determine and to get . Then, we obtain under given and . Finally, we repeat this process until convergence.
4.2. MEC Server Selection
Given and , the MEC server selection problem can be expressed as
In (17), as the constraint C3.5 is , the optimization problem P3 is a zero-one integer programming problem. In addition, the objective function is nonlinear with respect to . Accordingly, the optimization problem P3 is a mixed integer nonlinear programming problem, which is also a NP-hard problem [60].
To solve the above optimization problem P3, we relax the constraint C3.5, i.e., . We can get the following relaxed nonlinear programming problem.
Lemma 2.
The optimization problem P4 is a convex optimization problem.
Proof of Lemma 2.
See the Appendix B. □
By the corollary to Lemma 2, we can solve the optimization problem P4 by general convex optimization algorithms and we can obtain an optimal fractional solution, which can be expressed as , where n represents the number of solutions and . However, because of the relaxation of the constraint, the space of the solution is larger. Thus, this solution is an upper bound of the primal optimization problem P3. In addition, is continuous and cannot satisfy the integer constraint of problem P3, i.e., . In the light of the analyses above, we adopt the relax-and-rounding method from in [61] to obtain the feasible solution , where .
4.3. Joint Task Offloading and Resource Allocation
As can be seen in (6), (9), and (11), for the optimization problem P2, in the case of given , the joint resource allocation and task offloading problem can be written as
As is nondifferentiable with respect to and , can be transformed into
where , , and can be expressed as
where is the upper bound of .
Substituting (20) into the optimization problem P5, the optimization problem P5 can be equivalently recast as
Lemma 3.
The optimization problem P6 is a non-convex problem.
Proof of Lemma 3.
See the Appendix C. □
Unfortunately, the resource allocation variables and the offload ratio variables are highly coupled with each other in both the objective function and constraints. To solve the problem in (24), we decouple the two variables. Specifically, we obtain under given and then obtain under given , and repeat this process until convergence.
4.3.1. Optimization of Resource Allocation
Given and , the resource allocation problem can be written as
As and C7.1–C7.4 are linear constraints, the optimization problem P7 is a convex optimization problem. We use the Lagrangian method to solve this optimization problem P7. Let denote the Lagrangian function of the optimization problem P7, which can be given by
where , , , , and are Lagrangian multipliers, respectively. We have
Thus, the dual problem of optimization problem P7 can be expressed as
As the above problem is convex, we adopt the gradient descent method to solve (28). As the Lagrange function is differentiable, the gradients of Lagrangian multipliers can be expressed as
The Lagrangian multipliers can be calculated iteratively as follows:
where t represents the gradient number; represents ; and , , , , and are gradient iteration steps.
The first-order derivatives of the Lagrangian function with respect to can be written as
Let , we have the optimal solution , which can be calculated as
4.3.2. Optimization of Task Offloading
Given and , the offload ratio problem can be written as
As and C8.1–C8.3 are linear constraints, the optimization problem P8 is a convex optimization problem. We use the Lagrangian method to solve this optimization problem P8. Let denote the Lagrangian function of the optimization problem for P8, which can be given by
where , , , and are Lagrangian multipliers, respectively. Due to the Lagrange function is differentiable, the gradients of Lagrangian multipliers can be expressed as
Similarly, we iterate computation the Lagrangian multipliers , , , and , which can be calculated as
where l represents the gradient number; represents ; and , , , and are gradient iteration steps.
Let , we have the optimal solution , which can be calculated as
4.4. Overall Algorithm
In this paper, we propose an efficient iterative algorithm by jointly considering the task offloading, the resource allocation, and the security assurance for UAV-assisted VANETs, named the LBTO algorithm. The proposed LBTO algorithm is summarized in Algorithm 1. In detail, we first decompose the optimization problem P1 into two subproblems, i.e., the MEC server selection problem and the task offloading problem. Then, given and , we use the constraint relaxation scheme and the relax-and-rounding method to solve the optimization problem P3. Afterward, based on the selected MEC server on UAV, we adopt the method of Lagrangian dual decomposition to solve the optimization problem. Finally, we repeat this process until convergence.
| Algorithm 1 The Proposed LBTO Algorithm. |
| 1: Initialization |
| 2: Set iterations . |
| 3: Set , , and . |
| 4: repeat |
| 5: k = k+1. |
| 6: Based on and , we can solve the optimization problem P3 by the constraint relaxation scheme and the relax-and-rounding method. |
| 7: until Obtain the feasible solution . |
| 8: repeat |
| 9: According to the Lagrangian dual decomposition, we can solve the optimization problem P7 and P8. |
| 10: Calculate the optimal solution and . |
| 11: until Convergence. |
4.5. Potential Applications
In the present decade, the potential applications of MEC-enabled UAV-assisted VANETs are under discussion in commercial settings. Several researchers emphasized that the potential of MEC-enabled autonomous vehicles to significantly reduce the traffic and logistics-related challenges in complex urban ITS environments. For example, the benefits of using MEC-enabled UAV-assisted VANETs in urban ITS environments or commercial settings include, but are not limited to, increased safety, reduced congestion, reduced fuel consumption and emissions, and transporting disabled or older people [14]. Specifically, UAVs can keep the services and applications of urban ITS environments stable and active. The MEC architecture can effectively complete the task distribution and migration scheduling, thus alleviating task aggregation and improving UAV-assisted VANETs QoS.
5. Simulation Results
In this section, we evaluate the performance of the proposed LBTO algorithm via simulations.
5.1. Simulation Parameters
In our simulations, we consider a unidirectional road, where UAVs are randomly located along the road. Each vehicle has a divisible computing task that can be processed on both the MEC server on the UAV and the vehicle. The vehicle and the UAV adopt the IEEE 802.11p wireless communication techniques [62]. We compare it with three algorithms: the vehicle local computing (), the average task offloading (), and the vehicle-RSU LBTO algorithm. In the vehicle-RSU LBTO algorithm, the MEC server is installed on the RSU. In order to adapt to the statistical significance of the results, we adopt the Monte Carlo method to calculate the average of results. The detailed simulation parameters are summarized in Table 1 [50]. In the following, the simulations are performed by Matlab.

Table 1.
Simulation parameters.
In our simulations, we consider the following two different metrics to demonstrate the performance.
(1) Task Processing Delay: The task processing delay includes two parts, namely, the vehicle local processing delay and the MEC server processing delay, which can be expressed as Formula (12).
(2) Successful Task Processing Ratio: The ratio of number of tasks that have been successfully processed to the number of total tasks. The successful task processing ratio can be defined as
where m represents the tasks have been successfully processed in the task maximum allowed latency and n represents number of total tasks.
5.2. Simulation Results
Figure 5 illustrates the comparison of the task processing delay with respect to the local computation resources under different algorithms. In the early stages, we find that the task processing delay of the vehicle local computing algorithm is much higher than other algorithms. This is because the computation ability of most vehicles is limited, and thus multiple tasks cannot be fully processed within the allowed latency. Moreover, with the increase of the local computation resources, the task processing delay of all algorithms decreases accordingly. When the vehicle local computing resources are larger than some values (referred to as break points), the task processing delay will decline sharply, which represents that adding a small amount of local computing resources in the initial phase can effectively reduce the task processing delay. Furthermore, we note that the UAV-assisted strategy expedites the uploading progress in the simulated scenario, which verifies the validity to apply UAVs as MEC servers, allowed them to be regarded as suitable candidates to improve VANETs connectivity.
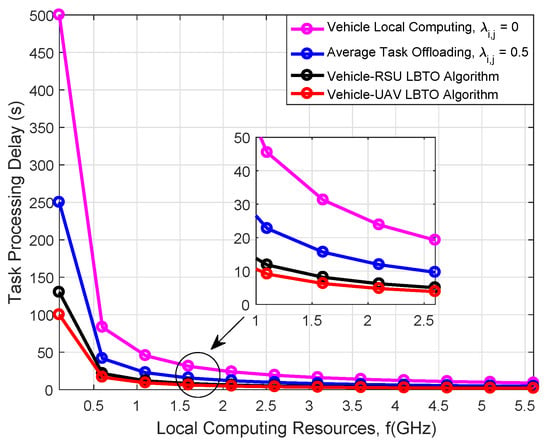
Figure 5.
Comparison of the task processing delay with respect to the local computation resources under different algorithms.
Figure 6 shows the comparison of the successful task processing ratio of the local computation resources under different algorithms. The simulation results indicate that compared with other algorithms, our proposed LBTO algorithm can offload tasks with minimal local computing resources. This is because the LBTO algorithm can take full advantage of the computation resources of all MEC servers in the entire VANETs. As we optimize the task offload ratio when the local computation resources can satisfy the basic processing requirements of tasks, the successful task processing ratio is counted as 100%. Therefore, increasing the local computation resources can also improve the successful task processing ratio. In addition, as the channel between the vehicle and the UAV has a better quality of service than the channel between the vehicle and the RSU, we can find that using UAVs for MEC can offload tasks more quickly. Therefore, the UAV-assisted VANETs architecture can provide vehicles with lower latency and more reliable computing services.
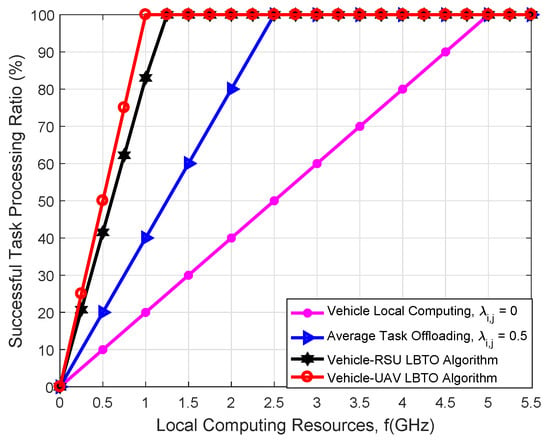
Figure 6.
Comparison of the successful task processing ratio with respect to the local computation resources under different algorithms.
Figure 7 shows the comparison of the task processing delay with respect to the vehicle speed under different algorithms. We can observe that our proposed LBTO algorithm greatly outperforms the other algorithms with different vehicle speeds, which verifies the effectiveness of our proposed algorithm. On the other hand, we can find that the task processing delay of the vehicle’s local computing algorithm cannot change with the change of the vehicle speed. This is because in vehicle’s local computing algorithm, tasks are not offloaded to the MEC server on UAV for processing. By contrast, with the increment of the vehicle speed, the task processing delay of the LBTO algorithm declines greatly. In addition, it can be observed that with the increase of vehicle speed, the decrease trend of task processing delay gradually slows down. Our proposed LBTO algorithm can reach the critical point (when the vehicle speed is larger than some values, the task processing delay will decline relaxedly) faster, which shows that the proposed LBTO algorithm has good applicability in both low-speed and high-speed scenarios. Therefore, these results tell us that the task processing delay can be reduced by increasing the vehicle speed appropriately.
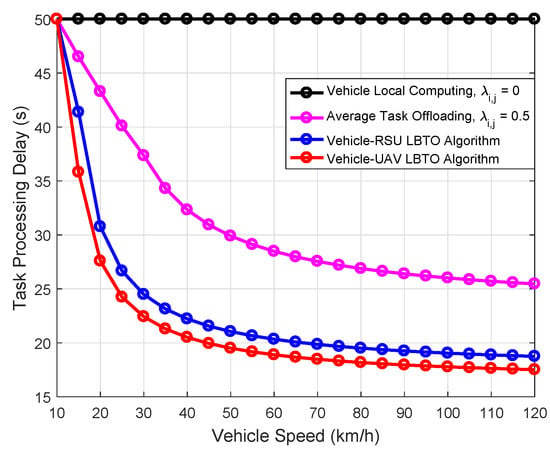
Figure 7.
Comparison of the task processing delay with respect to the vehicle speed under different algorithms.
Figure 8 demonstrates the comparison of the task offloading efficiency with respect to the vehicle speed under different algorithms. It is observed that our proposed LBTO algorithm outperforms other algorithms in terms of the task offloading efficiency. In addition, the task offloading efficiency of all algorithms (except the vehicle local computing algorithm) increases with an increasing vehicle speed. The higher speed implies that a certain task can pass by more MEC servers in a given timeslot. The simulation results in Figure 8 are similar to those in Figure 7; we can find that with the increase of vehicle speed, the growth trend of successful task processing ratio gradually slows down. Our proposed LBTO algorithm can reach the critical point (when the vehicle speed is larger than some values, the successful task processing ratio will increase relaxedly) faster. Therefore, as the vehicle speed increases, the LBTO algorithm can make better MEC server choices.
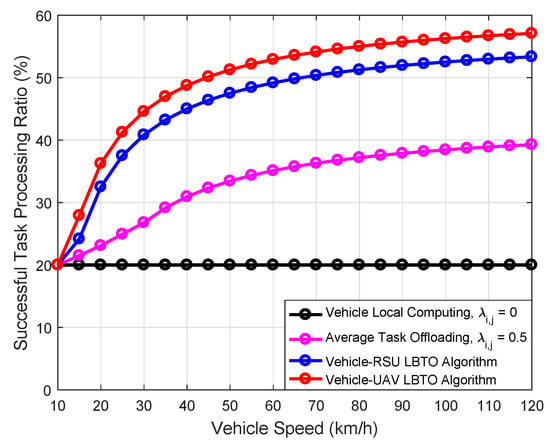
Figure 8.
Comparison of the successful task processing ratio with respect to the vehicle speed under different algorithms.
Figure 9 plots the comparison of the successful task processing ratio with respect to the UAV flight altitude under different algorithms. As can be seen from the results, with the increase of the UAV flight altitude, the successful task processing ratio increased first and then decreased. This is because the channel power gain from the vehicle to UAV increases with the UAV flight altitude in low-altitude scenarios, which can improve the transmission rate. In high-altitude scenarios, the channel power gain from the vehicle to the UAV decreases with the UAV flight altitude. The reason is that excessive UAV flight altitude can increase the path loss, which can lead to a decrease in the successful task processing ratio. Therefore, increasing the UAV flight altitude appropriately can improve the transmission quality, which can increase the successful task processing ratio.
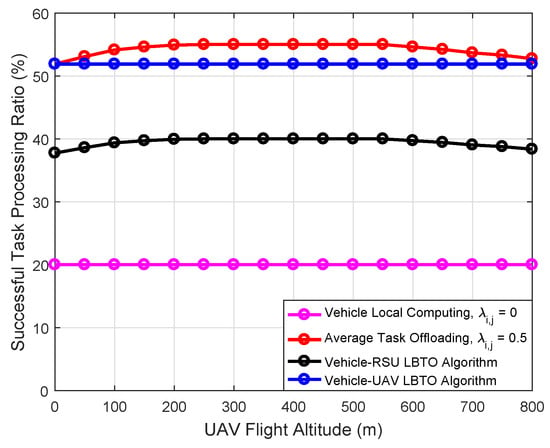
Figure 9.
Comparison of the successful task processing ratio with respect to the UAV flight altitude under different algorithms.
Figure 10 depicts the comparison of the successful task processing ratio with respect to the number of vehicles under the number of MEC servers on UAVs. From this figure, we can observe that increasing the number of UAVs can improve the performance of UAV-assisted VANET in terms of the successful task processing ratio. However, the successful task processing ratio growth slows as the number of UAVs increases. This is because the task has a maximum allowed latency, and therefore the MEC servers on UAVs far from the starting point cannot serve the vehicle well. Therefore, we can increase the computing resources of the remote MEC servers on UAVs to provide better computing services for the vehicle. In addition, it can be seen that especially in the scenario with a small number of vehicles, the MEC-enabled UAV-assisted VANETs architecture can better provide task processing services for vehicles. Compared to the MEC-enabled RSU-assisted VANETs, our proposed network architecture has lower cost and better coverage capability, which can be regarded as the potential candidates for providing different type of solutions in the futuristic ITS.
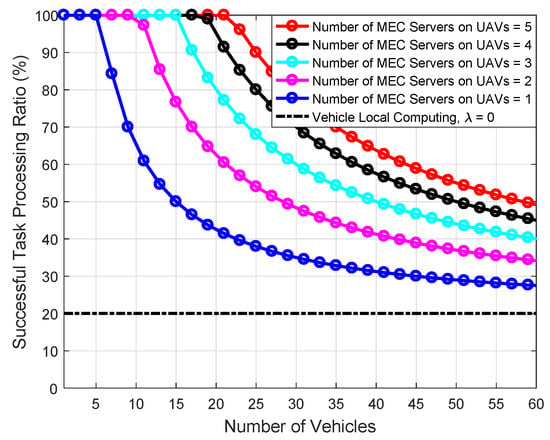
Figure 10.
Comparison of the successful task processing ratio with respect to the number of vehicles under the number of MEC servers on UAVs.
Figure 11 illustrates the comparison of the successful task processing ratio with respect to the local computation resources under different task sizes. We can observe that the successful task processing ratio increases sub-linearly with the local computation resources. This is because, with the increment of local computation resources, more resources can be exploited to process tasks. Besides, we can find that when the task size is small, the task can be processed successfully even without local computing resources. Furthermore, the simulation results indicate that the successful task processing ratio decreases with the increase in the number of tasks under the given local computing resources.
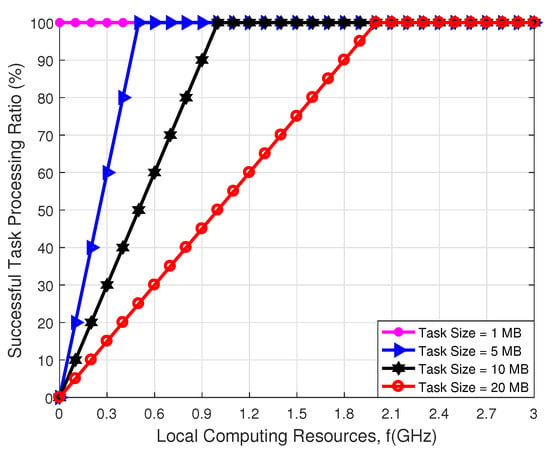
Figure 11.
Comparison of the successful task processing ratio with respect to the local computation resources under different task sizes.
Figure 12 depicts the comparison of the successful task processing ratio with respect to the vehicle speed under different task intervals. This figure shows that the successful task processing ratio increases with the task interval. This is because our proposed LBTO algorithm is based on IEEE 802.11p protocol, which adopts the carrier sense multiple access protocol with collision avoidance for data transmission. Therefore, a higher task frequency will lead to more collisions, which will decrease the successful task processing ratio. It is also noticed that the increase in the successful task processing ratio is not significant when the task interval is increased from 30 s to 40 s. Thereforee, from this figure, we can know that the proper utilization of the task interval can effectively improve the MEC-enabled UAV-assisted VANETs performance comprehensively.
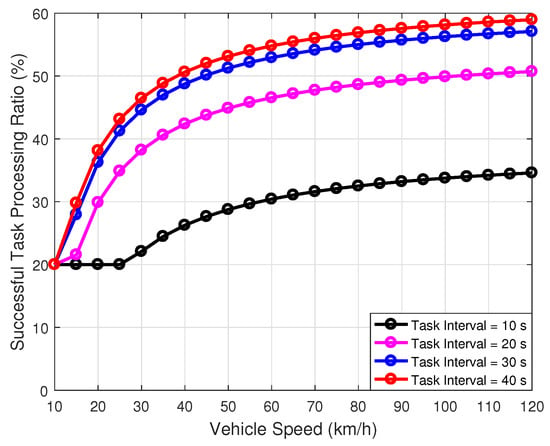
Figure 12.
Comparison of the successful task processing ratio with respect to the vehicle speed under different task intervals.
Figure 13 presents the comparison of the successful task processing ratio with respect to the number of vehicles under different task maximum allowed latencies. This figure shows that when the number of vehicles is larger than some values (referred to as turning points), the successful task processing ratio will decline sharply, which means the task cannot be processed in time. It can be seen that the turning point of task maximum allowed latency = 5 s is the smallest and that of the task maximum allowed latency = 20 s is the largest. This indicates that increasing the task maximum allowed latency can provide better task processing capability for the vehicles. In addition, from examining Figure 12 and Figure 13, we realize that there is a trade-off between the task interval and the task maximum allowed latency in terms of the successful task processing ratio. The successful task processing ratio optimization by jointly considering the task interval and the task maximum allowed latency is an important problem for future research.
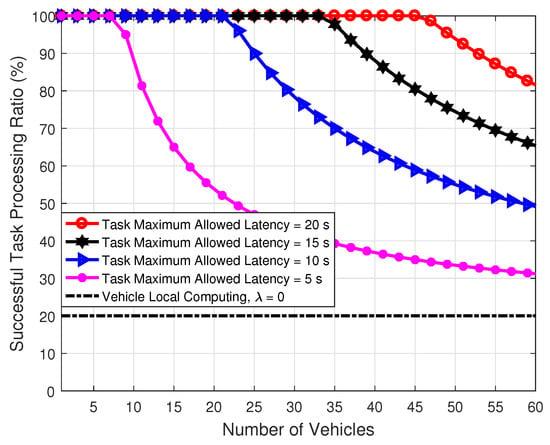
Figure 13.
Comparison of the successful task processing ratio with respect to the number of vehicles under different task maximum allowed latencies.
6. Discussion
6.1. Research Questions
To address the objective of this work, we have studied the following research questions (Table 2).

Table 2.
Research questions.
Specifically, in this paper, we investigate the MEC-enabled UAV-assisted VANET architecture to provide vehicles with low latency and reliable computing services through UAVs. On this basis, the network optimization problem is formulated as a joint problem of the task offloading, the resource allocation, and the security assurance, and the objective is to minimize the task processing delay. For tackling this joint optimization problem, we decouple the optimization problem as two subproblems and propose an efficient iterative algorithm according the relax-and-rounding method and the Lagrangian dual decomposition.
The simulation results show that the proposed LBTO algorithm achieves better performance than the other algorithms in terms of the successful task processing ratio and the task processing delay. In our designed LBTO algorithm, each vehicle can select one appropriate MEC server on UAV and offload parts of the computation task, which can achieve load balancing and service reliability improvement by the task scheduling among edge MEC servers on UAVs. Furthermore, these results fully show that our proposed LBTO algorithm is better than the benchmarking algorithms, and the schemes with optimized network parameters are superior to those without optimization.
6.2. Research Limitations and Future Research Prospects
In addition to those problems listed in the previous sections, there are many research issues beckoning for further investigation. In this paper, we ignore the UAV energy factor in the objective function and assume that the UAV is fixed. The UAV can be a tethered UAV, which can adopt a ground power source transmitted via tethered cables to achieve a long period of hovering. Compared with the balloon-based platform or the fixed camera on a pole scheme, UAVs can be flexibly deployed in three-dimensional (3-D) space according to the user’s special requirements and has better anti-damage capability.
As a future work, we plan to study the UAV energy consumption and combine it with our proposed algorithm for practical application. In addition, cooperative secure transmission is also a factor that cannot be neglected in the MEC-enabled UAV-assisted VANET architecture, which can be an interesting aspect for further investigation.
7. Conclusions
In this paper, we have formulated a multi-objective optimization problem for MEC-enabled UAV-assisted VANETs by jointly considering the task offloading, the resource allocation, and the security assurance with the aim to minimize the task processing delay. To deal with this hard problem, we have decoupled the multi-objective optimization problem as two subproblems. Exploiting the relax-and-rounding method and the Lagrangian method, we have proposed an iterative algorithm, which effectively solves the joint optimization problem. The simulation results have demonstrated that our proposed LBTO algorithm can achieve a significant performance gain in comparison with other algorithms in terms of the successful task processing ratio and the task processing delay. Our work can be widely applied to offer low-latency and high-reliable edge computing services to vehicle users in a complex network environment, such as the urban ITS and the smart city.
Author Contributions
Y.H.: Conceptualization, Methodology, Software, Validation, Formal Analysis, Investigation, Data Curation, Writing—Original Draft Preparation, and Visualization. D.Z.: Conceptualization, Methodology, Software, Validation, Formal Analysis, Investigation, Resources, Data Curation, Writing—Review and Editing, Visualization, Supervision, Project Administration, and Funding Acquisition. F.H.: Conceptualization, Software, Validation, Formal Analysis, Investigation, Writing—Review and Editing. D.W.: Conceptualization, Methodology, Software, Formal Analysis, Investigation, Resources, Writing—Review and Editing, Supervision, Project Administration, and Funding Acquisition. X.T.: Conceptualization, Software, Formal Analysis, Writing—Review and Editing, Supervision, and Funding Acquisition. R.Z.: Conceptualization, Formal Analysis, Resources, Writing—Review and Editing, Supervision, Project Administration, and Funding Acquisition. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Natural Science Foundation of China under Grant 61901381, 61901379, and 61102078, in part by the Foundation of the State Key Laboratory of Integrated Services Networks of Xidian University under Grant ISN21-06, in part by the National Key Research and Development Program of China under Grants 2020YFB1807004 and 2020YFB1807003, in part by the open research fund of National Mobile Communications Research Laboratory, Southeast University under Grant 2020D04, in part by the Innovation Foundation for Doctor Dissertation of Northwestern Polytechnical University under Grant CX202037, and in part by the Program of China Scholarships Council under Grant 202006290166. Part of the journal has been accepted by the 2021 IEEE International Conference on Computer Communications Workshops (INFOCOM Workshops).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
Due to , (12) can be transformed into the following formulas:
Therefore, C1.1 can be equivalently changed to C2.1–C2.3. According to C1.2 and C1.3, the objective function can be equivalent to . Moreover, as there is only one , and , , C1.6 is naturally satisfied. As such, we have proved Lemma 1.
Appendix B
The second-order derivative of with respect to can be written as
As the second-order derivative of with respect to is equal to 0, we know that the objective function is convex [63]. Constraints C4.1–C4.6 are linear convex constraints. Therefore, it can be concluded that optimization problem P4 is a convex optimization problem.
Appendix C
The first-order and second-order derivatives of the objective function with respect to are
and
The first-order and second-order derivatives of the objective function with respect to are
and
According to (55)–(58), we have
and
Therefore, we can obtain
As the above inequation (60) is indefinite, we can prove that optimization problem P6 is nonconvex. To this end, we have proved Lemma 3.
References
- Cui, J.; Wei, L.; Zhong, H.; Zhang, J.; Xu, Y.; Liu, L. Edge Computing in VANETs-An Efficient and Privacy-Preserving Cooperative Downloading Scheme. IEEE J. Sel. Areas Commun. 2020, 38, 1191–1204. [Google Scholar] [CrossRef]
- Nazib, R.A.; Moh, S. Routing Protocols for Unmanned Aerial Vehicle-Aided Vehicular Ad Hoc Networks: A Survey. IEEE Access 2020, 8, 77535–77560. [Google Scholar] [CrossRef]
- Cui, J.; Wei, L.; Zhang, J.; Xu, Y.; Zhong, H. An Efficient Message-Authentication Scheme Based on Edge Computing for Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2019, 20, 1621–1632. [Google Scholar] [CrossRef]
- Oubbati, O.S.; Lakas, A.; Zhou, F.; Güneş, M.; Lagraa, N.; Yagoubi, M. Intelligent UAV-assisted routing protocol for urban VANETs. Comput. Commun. 2017, 107, 93–111. [Google Scholar] [CrossRef]
- He, Y.; Zhai, D.; Jiang, Y.; Zhang, R. Relay Selection for UAV-Assisted Urban Vehicular Ad Hoc Networks. IEEE Wirel. Commun. Lett. 2020, 9, 1379–1383. [Google Scholar] [CrossRef]
- Chadwick, A.J.; Goodbody, T.R.H.; Coops, N.C.; Hervieux, A.; Bater, C.W.; Martens, L.A.; White, B.; Röeser, D. Automatic Delineation and Height Measurement of Regenerating Conifer Crowns under Leaf-Off Conditions Using UAV Imagery. Remote Sens. 2020, 12, 4104. [Google Scholar] [CrossRef]
- Egli, S.; Höpke, M. CNN-Based Tree Species Classification Using High Resolution RGB Image Data from Automated UAV Observations. Remote Sens. 2020, 12, 3892. [Google Scholar] [CrossRef]
- Huang, C.M.; Lai, C.F. The Delay-Constrained and Network-Situation-Aware V2V2I VANET Data Offloading Based on the Multi-Access Edge Computing (MEC) Architecture. IEEE Open J. Veh. Technol. IEEE Wirel. Commun. Lett. 2020, 1, 331–347. [Google Scholar] [CrossRef]
- Yin, B.; Cheng, Y.; Cai, L.X.; Cao, X. Online SLA-aware multi-resource allocation for deadline sensitive jobs in edge-clouds. In Proceedings of the 2017 IEEE Global Communications Conference (GLOBECOM), Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- Liu, L.; Chang, Z.; Guo, X.; Mao, S.; Ristaniemi, T. Multiobjective optimization for computation offloading in fog computing. IEEE Internet Things J. 2018, 5, 283–294. [Google Scholar] [CrossRef]
- Narang, M.; Xiang, S.; Liu, W.; Gutierrez, J.; Chiaraviglio, L. UAV-assisted edge infrastructure for challenged networks. In Proceedings of the 2017 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Atlanta, GA, USA, 1–4 May 2017; pp. 60–65. [Google Scholar]
- Hou, X.; Li, Y.; Chen, M.; Wu, D.; Jin, D.; Chen, S. Vehicular fog computing: A viewpoint of vehicle as the infrastructures. IEEE Trans. Veh. Technol. 2016, 65, 3860–3873. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, Z.; Yu, R.; Zhang, Y. Low-latency caching with auction game in vehicular edge computing. In Proceedings of the 2017 IEEE/CIC International Conference on Communications in China (ICCC), Qingdao, China, 22–24 October 2017; pp. 1–6. [Google Scholar]
- Azmat, M.; Kummer, S. Potential applications of unmanned ground and aerial vehicles to mitigate challenges of transport and logistics-related critical success factors in the humanitarian supply chain. Asian J. Sustain. Soc. Responsib. 2020, 5, 1–22. [Google Scholar] [CrossRef]
- Liu, P.; Liu, J. Selfish or Utilitarian Automated Vehicles? Deontological Evaluation and Public Acceptance. Int. J. Hum. Comput. Interact. 2021. [Google Scholar] [CrossRef]
- Zaabi, A.O.A.; Yeun, C.Y.; Damiani, E. Autonomous Vehicle Security: Conceptual Model. In Proceedings of the 2019 IEEE Transportation Electrification Conference and Expo, Asia-Pacific (ITEC Asia-Pacific), Seogwipo, Korea, 8–10 May 2019; pp. 1–5. [Google Scholar]
- Oubbati, O.S.; Lakas, A.; Zhou, F.; Güneş, M.; Yagoubi, M.B. A survey on position-based routing protocols for flying ad hoc networks (FANETs). Veh. Commun. 2017, 10, 29–56. [Google Scholar] [CrossRef]
- Zhai, D.; Li, H.; Tang, X.; Zhang, R.; Ding, Z.; Yu, F.R. Height Optimization and Resource Allocation for NOMA Enhanced UAV-Aided Relay Networks. IEEE Trans. Commun. 2021, 69, 962–975. [Google Scholar] [CrossRef]
- Cao, H.; Hu, Y.; Yang, L. Towards intelligent virtual resource allocation in UAVs-assisted 5G networks. Comput. Netw. 2021, 185, 107660. [Google Scholar] [CrossRef]
- He, Y.; Tang, X.; Zhang, R.; Du, X.; Zhou, D.; Guizani, M. A Course-Aware Opportunistic Routing Protocol for FANETs. IEEE Access 2019, 7, 144303–144312. [Google Scholar] [CrossRef]
- Zhou, Y.; Cheng, N.; Lu, N.; Shen, X.S. Multi-UAV-aided networks: Aerial-ground cooperative vehicular networking architecture. IEEE Veh. Technol. Mag. 2015, 10, 36–44. [Google Scholar] [CrossRef]
- Zhang, N.; Zhang, S.; Yang, P.; Alhussein, O.; Zhuang, W.; Shen, X.S. Software Defined Space-Air-Ground Integrated Vehicular Networks: Challenges and Solution. IEEE Commun. Mag. 2017, 55, 101–109. [Google Scholar] [CrossRef]
- Oubbati, O.S.; Chaib, N.; Lakas, A.; Lorenz, P.; Rachedi, A. UAV-Assisted Supporting Services Connectivity in Urban VANETs. IEEE Trans. Veh. Technol. 2019, 68, 3944–3951. [Google Scholar] [CrossRef]
- He, Y.; Zhai, D.; Wang, D.; Tang, X.; Zhang, R. A Relay Selection Protocol for UAV-Assisted VANETs. Appl. Sci. 2020, 10, 8762. [Google Scholar] [CrossRef]
- Seliem, H.; Shahidi, R.; Ahmed, M.H.; Shehata, M.S. Drone-Based Highway-VANET and DAS Service. IEEE Access 2018, 6, 20125–20137. [Google Scholar] [CrossRef]
- Fawaz, W.; Atallah, R.; Assi, C.; Khabbaz, M. Unmanned Aerial Vehicles as Store-Carry-Forward Nodes for Vehicular Networks. IEEE Access 2017, 5, 23710–23718. [Google Scholar] [CrossRef]
- Bai, T.; Wang, J.; Ren, Y.; Hanzo, L. Energy-Efficient Computation Offloading for Secure UAV-Edge-Computing Systems. IEEE Trans. Veh. Technol. 2019, 68, 6074–6087. [Google Scholar] [CrossRef]
- Oubbati, O.S.; Lakas, A.; Lagraa, N.; Yagoubi, M.B. UVAR: An intersection UAV-assisted VANET routing protocol. In Proceedings of the 2016 IEEE Wireless Communications and Networking Conference (WCNC), Doha, Qatar, 3–6 April 2016; pp. 1–6. [Google Scholar]
- Athukoralage, D.; Guvenc, I.; Saad, W.; Bennis, M. Regret based learning for UAV assisted LTE-U/WiFi public safety networks. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–7. [Google Scholar]
- Mozaffari, M.; Saad, W.; Bennis, M.; Debbah, M. Unmanned aerial vehicle with underlaid device-to-device communications: Performance and tradeoffs. IEEE Trans. Wirel. Commun. 2016, 15, 3949–3963. [Google Scholar] [CrossRef]
- Veeranampalayam Sivakumar, A.N.; Li, J.; Scott, S.; Psota, E.; Jhala, A.J.; Luck, J.D.; Shi, Y. Comparison of Object Detection and Patch-Based Classification Deep Learning Models on Mid-to Late-Season Weed Detection in UAV Imagery. Remote Sens. 2020, 12, 2136. [Google Scholar] [CrossRef]
- Baur, J.; Steinberg, G.; Nikulin, A.; Chiu, K.; de Smet, T.S. Applying Deep Learning to Automate UAV-Based Detection of Scatterable Landmines. Remote Sens. 2020, 12, 859. [Google Scholar] [CrossRef]
- Machefer, M.; Lemarchand, F.; Bonnefond, V.; Hitchins, A.; Sidiropoulos, P. Mask R-CNN Refitting Strategy for Plant Counting and Sizing in UAV Imagery. Remote Sens. 2020, 12, 3015. [Google Scholar] [CrossRef]
- Mukherjee, A.; Misra, S.; Chandra, V.S.P.; Obaidat, M.S. Resource-Optimized Multiarmed Bandit-Based Offload Path Selection in Edge UAV Swarms. IEEE Internet Things 2019, 6, 4889–4896. [Google Scholar] [CrossRef]
- Yang, M.-D.; Tseng, H.-H.; Hsu, Y.-C.; Tsai, H.P. Semantic Segmentation Using Deep Learning with Vegetation Indices for Rice Lodging Identification in Multi-date UAV Visible Images. Remote Sens. 2020, 12, 633. [Google Scholar] [CrossRef]
- Mukherjee, A.; Misra, S.; Chandra, V.S.P.; Raghuwanshi, N.S. ECoR: Energy-Aware Collaborative Routing for Task Offload in Sustainable UAV Swarms. IEEE Trans. Sustain. Comput. 2020, 5, 514–525. [Google Scholar] [CrossRef]
- Mukherjee, A.; Misra, S.; Sukrutha, A.; Raghuwanshi, N.S. Distributed aerial processing for IoT-based edge UAV swarms in smart farming. Comput. Netw. 2020, 167, 107038. [Google Scholar] [CrossRef]
- Wu, Y.; Zheng, J. Modeling and Analysis of the Downlink Local Delay in MEC-Based VANETs. IEEE Trans. Veh. Technol. 2020, 69, 6619–6630. [Google Scholar] [CrossRef]
- Li, G.; Li, X.; Sun, Q.; Boukhatem, L.; Wu, J. An Effective MEC Sustained Charging Data Transmission Algorithm in VANET-Based Smart Grids. IEEE Access 2020, 8, 101946–101962. [Google Scholar] [CrossRef]
- Wu, Y.; Zheng, J. Analysis of the Uplink Local Delay in an MEC-Based VANET. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–7. [Google Scholar]
- Li, M.; Gao, J.; Zhao, L.; Shen, X. Deep Reinforcement Learning for Collaborative Edge Computing in Vehicular Networks. IEEE Trans. Cogn. Commun. Netw. 2016, 15, 3949–3963. [Google Scholar] [CrossRef]
- He, Y.; Zhai, D.; Zhang, R.; Du, X.; Zhou, D.; Guizani, M. An Anti-Interference Scheme for UAV Information Link in Air-Ground Integrated Vehicular Networks. Sensors 2019, 19, 4742. [Google Scholar] [CrossRef] [PubMed]
- Qi, Q.; Wang, J.; Ma, Z.; Sun, H.; Cao, Y.; Zhang, L.; Liao, J. Knowledge-Driven Service Offloading Decision for Vehicular Edge Computing: A Deep Reinforcement Learning Approach. IEEE Trans. Veh. Technol. 2019, 68, 4192–4203. [Google Scholar] [CrossRef]
- Wang, X.; Ning, Z.; Wang, L. Offloading in Internet of Vehicles: A fog-enabled real-time traffic management system. IEEE Trans. Ind. Informat. 2018, 14, 4568–4578. [Google Scholar] [CrossRef]
- Sun, Y.; Guo, X.; Song, J.; Zhou, S.; Jiang, Z.; Liu, X.; Niu, Z. Adaptive Learning-Based Task Offloading for Vehicular Edge Computing Systems. IEEE Trans. Veh. Technol. 2019, 68, 3061–3074. [Google Scholar] [CrossRef]
- Ning, Z.; Kwok, R.Y.K.; Zhang, K.; Wang, X.; Obaidat, M.S.; Guo, L.; Hu, X.; Hu, B.; Guo, Y.; Sadoun, B. Joint computing and caching in 5G-envisioned Internet of Vehicles: A deep reinforcement learning-based traffic control system. IEEE Trans. Intell. Transp. Syst. 2020. [Google Scholar] [CrossRef]
- Yu, Y.; Zhang, J.; Letaief, K.B. Joint subcarrier and CPU time allocation for mobile edge computing. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar]
- Wang, F.; Xu, J.; Wang, X.; Cui, S. Joint offloading and computing optimization in wireless powered mobile-edge computing systems. IEEE Trans. Wirel. Commun. 2018, 17, 1784–1797. [Google Scholar] [CrossRef]
- Mao, Y.; Zhang, J.; Letaief, K.B. Dynamic computation offloading for mobile-edge computing with energy harvesting devices. IEEE J. Sel. Areas Commun. 2016, 34, 3590–3605. [Google Scholar] [CrossRef]
- Dai, Y.; Xu, D.; Maharjan, S.; Zhang, Y. Joint Load Balancing and Offloading in Vehicular Edge Computing and Networks. IEEE Internet Things 2019, 6, 4377–4387. [Google Scholar] [CrossRef]
- You, C.; Huang, K.; Chae, H.; Kim, B.H. Energy-efficient resource allocation for mobile-edge computation offloading. IEEE Trans. Wirel. Commun. 2017, 16, 1397–1411. [Google Scholar] [CrossRef]
- Dong, L.; Ni, Q.; Wu, W.; Huang, C.; Znati, T.; Du, D.Z. A Proactive Reliable Mechanism-Based Vehicular Fog Computing Network. IEEE Internet Things J. 2020, 7, 11895–11907. [Google Scholar] [CrossRef]
- Chen, X.; Jiao, L.; Li, W.; Fu, X. Efficient multi-user computation offloading for mobile-edge cloud computing. IEEE/ACM Trans. Netw. 2016, 24, 2795–2808. [Google Scholar] [CrossRef]
- Li, M.; Cheng, N.; Gao, J.; Wang, Y.; Zhao, L.; Shen, X. Energy-Efficient UAV-Assisted Mobile Edge Computing: Resource Allocation and Trajectory Optimization. IEEE Trans. Veh. Technol. 2020, 69, 3424–3438. [Google Scholar] [CrossRef]
- Alioua, A.; Djeghri, H.; Cherif, M.E.T.; Senouci, S.M.; Sedjelmaci, H. UAVs for traffic monitoring: A sequential game-based computation offloading/sharing approach. Comput. Netw. 2020, 177, 107273. [Google Scholar] [CrossRef]
- Klapez, M.; Grazia, C.A.; Casoni, M. Application-Level Performance of IEEE 802.11p in Safety-Related V2X Field Trials. IEEE Internet Things J. 2020, 7, 3850–3860. [Google Scholar] [CrossRef]
- Han, C.; Dianati, M.; Tafazolli, R.; Kernchen, R. Throughput Analysis of the IEEE 802.11p Enhanced Distributed Channel Access Function in Vehicular Environment. In Proceedings of the 2010 IEEE 72nd Vehicular Technology Conference-Fall, Ottawa, ON, Canada, 6–9 September 2010; pp. 1–5. [Google Scholar]
- Mjeku, M.; Gomes, N.J. Analysis of the Request to Send/Clear to Send Exchange in WLAN Over Fiber Networks. J. Lightw. Technol. 2008, 26, 2531–2539. [Google Scholar] [CrossRef]
- Zhai, D.; Zhang, R. Joint Admission Control and Resource Allocation for Multi-Carrier Uplink NOMA Networks. IEEE Wirel. Commun. Lett. 2018, 7, 922–925. [Google Scholar] [CrossRef]
- Srinivas, S.T.P.; Shanti Swarup, K. A New Mixed Integer Linear Programming Formulation for Protection Relay Coordination Using Disjunctive Inequalities. IEEE Power Energy Technol. Syst. J. 2019, 6, 104–112. [Google Scholar] [CrossRef]
- Zhai, D.; Zhang, R.; Cai, L.; Yu, F.R. Delay Minimization for Massive Internet of Things with Non-Orthogonal Multiple Access. IEEE J. Sel. Top. Signal Process. 2019, 13, 553–566. [Google Scholar] [CrossRef]
- Secinti, G.; Canberk, B.; Duong, T.Q.; Shu, L. Software Defined Architecture for VANET: A Testbed Implementation with Wireless Access Management. IEEE Commun. Mag. 2017, 55, 135–141. [Google Scholar] [CrossRef]
- Antoniou, A.; Lu, W.S. Practical Optimization: Algorithm and Engineering Applications; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).