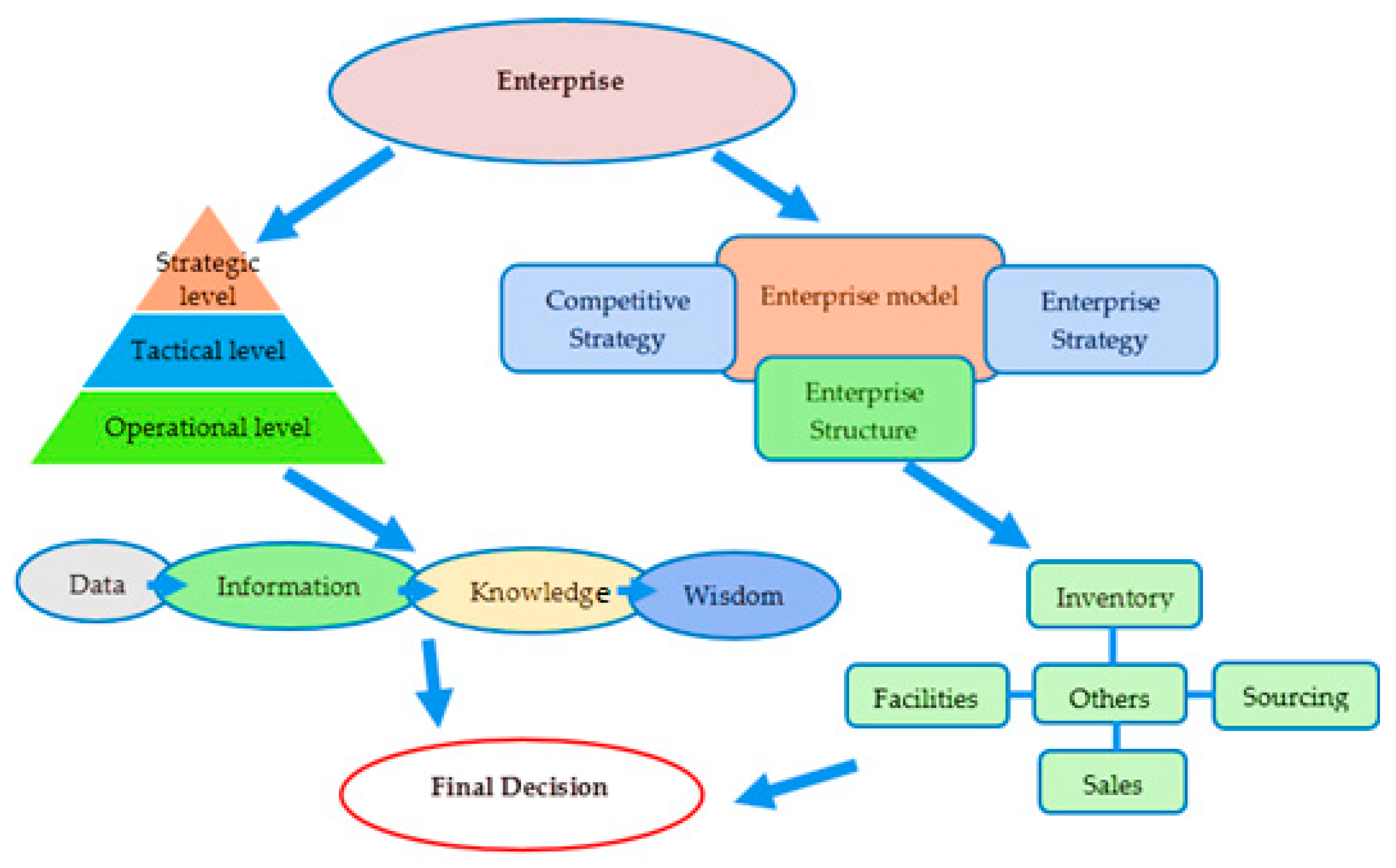
1. Introduction
The Internet of Things (IoT) is a field of engineering that aims to connect numerous small physical devices that can work together to accomplish a common objective. The widespread use of these small networked devices has increased the importance of IoT. These intelligent yet straightforward objects can detect each other wirelessly and communicate [
1] and have sensing capabilities [
2]. Smart devices are emerging on the market, supported by new paradigm-shifting technologies such as the Internet of Things and artificial intelligence (AI) [
3]. IoT is a network of interconnected devices and services (computer hardware, machines, and physical items) that can sense their surroundings or themselves, run computer operations, and connect to the Internet. Smart items include cyber–physical systems and Internet-based services. For instance, “smart” cars with cutting-edge embedded intelligence can connect to other cars, people, and the environment to provide creative data-driven services. These IoT-enriched products are “smartly connected” or “smart products”. Although “smart” is sometimes used to mean “intelligent”, “clever”, “nifty,” or “advanced”, the term “smart product” has considerably broader implications. Smart product creation requires new capabilities supported by cutting-edge tools, processes, and models, as these products are software-intensive, data-driven, and service-conscious.
Along with technological and financial advantages, the Internet of Things’ contribution to sustainability has grown in importance. IoT technologies are currently essential for achieving the sustainable development of enterprises, mainly because of their effects on responsible production, resource optimization, energy efficiency, and smart city infrastructure. Users access the Internet through various apps to conduct daily informational searches, browse specific websites, share documents, or communicate online, independent of time or space restrictions. Many states have recently explored opportunities for using IoT in various industries, including education, transportation, home appliances, healthcare, manufacturing, and smart cities. It is noteworthy that fourth industrial revolution involved the Internet of Things branching into the consumer and technology sectors. Strategic advantage realization is tied directly to the expected business transformation driven by digitization and the Internet of Things. IoT, a new informational engine, is projected to propel the communication technology market in the coming years [
3]. Using IoT-enhanced items can be significant for understanding how, why, and when customers buy and use certain products. As a result, there is potential for interactive customer communication. IoT provides platforms that allow computing devices to accept, store, and transfer data across the Internet.
The twenty-first century has seen rapid advancements in industry, technology, and social convention. The plurality of industries has shifted toward automation, and human participation has decreased, resulting in an industrial revolution known as Industry 4.0. IoT and wireless sensor networks (WSNs) are crucial to Industry 4.0, often called the fourth industrial revolution (IR 4.0) [
4,
5]. Smart technologies are essential for long-term economic success. Without human interaction, they transform buildings into autonomous, self-regulating systems, including homes, workplaces, factories, and even entire cities [
6]. Enabling commercial operations both within factories and outside markets is the IoT’s ultimate purpose. Companies face obstacles when implementing novel ideas. Many scholarly publications have examined security challenges, including data on tracked actions from hardware, software, and intelligent gadgets. Industry 4.0 IoT connectivity allows devices to communicate and interact with each other automatically. The hazards of exposure to sensitive information, such as personal information in the human resources department, financial data, and documents in the R&D office, are increased by this function. IoT combines the Internet’s strength with the ability of businesses to operate infrastructure, machinery, and factories [
7]. IoT devices can be managed by end users using their smartphones or voice commands. The Internet of Things enables control over objects (such as computers, networks, laptops, etc.) to create products or services, ensuring the smart enterprise’s delivery [
8]. IoT is essential for connecting the digital and physical worlds; however, several obstacles need to be overcome in the future.
Enterprises face challenges in selecting and prioritizing the most influential factors for IoT implementation due to data uncertainty, subjective preferences, and a lack of structured evaluation frameworks. Previous studies focused on isolated applications of fuzzy or grey-based methods in areas such as supply chains, healthcare, or smart cities [
9,
10], but relatively few have developed integrated decision models specifically addressing sustainability in IoT enterprise settings. To fully realize these benefits, enterprises must systematically evaluate and prioritize IoT factors, ensuring that implementation efforts align with operational and strategic goals [
11]. Effectiveness and transparency in procedures are examples of invisible improvement, whereas adjustable productions and various completed commodities are examples of visible improvement [
12]. Because automatic equipment can communicate with devices without waiting for human input or commands, they can drastically minimize the waiting times of the production process and increase productivity [
13]. Self-starting appliances can improve operation cycles based on the data gathered in “big data” pools, reduce setup time between units, and increase machine utilization [
14]. This enables operators and management to make quick decisions to meet client demands. Additionally, implementing IoT in manufacturing would reduce gaps between operators, departments, and workshops.
Moreover, this strategy helps businesses conserve energy and address environmental challenges, as automated equipment typically uses less energy. Because their processes are transparent and efficient, manufacturing companies can create more customized products at a lower cost. This enhancement enables companies to expand their client base across multiple industries. These effects directly support key sustainability pillars, such as energy efficiency, climate action, and circular economy models. Thus, evaluating the effectiveness of IoT adoption is not only a matter of technological or business interest but also a pathway to achieving broader sustainability goals.
To evaluate IoT performance indicators in corporate contexts, this work contributes to the academic body of knowledge by presenting a novel hybrid approach that combines the Pythagorean Fuzzy Analytical Hierarchy Process (PFAHP) and the Interval Grey Analytical Hierarchy Process (IGAHP). The method enhances decision-making precision in situations involving imprecision and ambiguity, which are common in strategic planning associated with IoT. Our model provides a multi-criterion, generic framework that promotes operational efficiency and strategy alignment across various industries, in contrast to earlier research, which primarily focused on discrete industry use cases.
Hybrid fuzzy–grey MCDM methods have been applied in various fields, including logistics, energy planning, and smart city systems; however, their application in enterprise-level IoT implementation remains limited. Previous studies have primarily focused on specific use cases or employed single-method approaches that do not fully capture the multidimensional uncertainty inherent in IoT adoption processes. This study aims to bridge this gap by introducing a hybrid framework that combines the PFAHP and IGAHP methods, which is adapted to the challenges of assessing IoT success factors in business contexts. The PFAHP method takes into account ambiguity and hesitation in expert judgment, while the IGAHP compensates for incomplete or imprecise data. The results of the decision-making process are more dependable and applicable thanks to this mix of techniques. This study offers methodological advancements as well as practical significance for strategic planning in data-driven, sustainable companies by integrating important indicators, including information privacy, sensor networks, market demand, and data governance.
The article is structured as follows:
Section 2 presents the theoretical background and factors influencing IoT.
Section 3 defines indicators and provides a hierarchical structure, as well as the methodology for PFAHP and IGAHP.
Section 4 presents the results and discusses the ranking of indicators, and provides recommended key tasks for enhancing efficiency in sustainable IoT enterprises. This study is concluded in
Section 5, which also suggests some areas for further research.
3. Materials and Methods
3.1. Problem Formulation
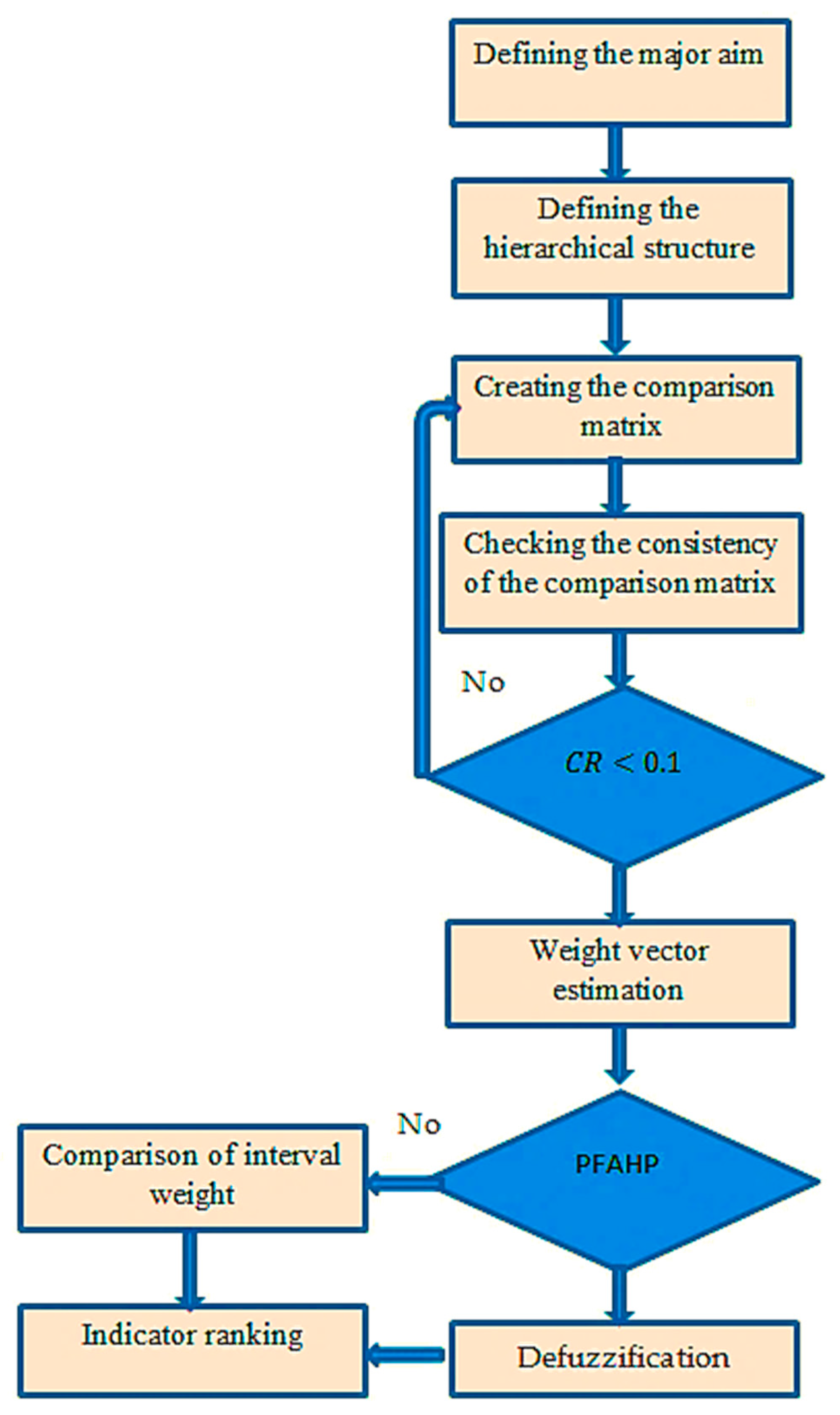
The methodological framework for this study was designed to systematically evaluate significant indicators that affect the adoption of IoT in sustainable initiatives, as shown in
Figure 3.
The following explains the methodological framework:
Problem Formulation and Research Objective: This study focused on evaluating critical components for the long-term deployment of IoT in enterprises, considering the unpredictability of the environment, to facilitate strategic planning and informed decision-making.
Literature Review and Criteria Identification: To extract and compile performance metrics used in enterprise IoT initiatives, a thorough assessment of previous IoT research was conducted. Initially, more than 40 possible indications were gathered, and Delphi rounds were used to refine them further.
Development of Hierarchical Structure: Indicators were organized hierarchically into main and sub-criteria based on their thematic relevance and interdependence. The structure was validated by senior academics and industry experts.
Expert Consultation and Data Collection: Experts from IoT-active enterprises in the manufacturing, logistics, energy, and IT sectors participated. Data were collected via structured pairwise comparison. Experts were grouped by experience and domain (technical vs. managerial). Inconsistent replies were eliminated using a consistency ratio cutoff (CR < 0.1).
Application of PFAHP and IGAHP: Expert feedback was examined using the two methods independently. PFAHP was used to model subjective preferences and linguistic hesitations, and IGAHP was used to record numerical estimate uncertainty. The final ranks were calculated after applying fuzzy and grey aggregation procedures. Spearman’s and Salabun similarity coefficients were used for cross-method validation.
Interpretation and Discussion of Results: The results were analyzed in terms of their strategic relevance to the implementation of IoT. The influence of indicators was discussed, and the complementary nature of the two methods was emphasized.
Conclusions and Recommendations: Important lessons learned were offered to help enterprise stakeholders. Future research prospects were explored, including the model’s scalability and transferability to various organizational contexts, as well as its structure.
Building on the theoretical framework, this section outlines the methodology used to assess and prioritize the factors influencing IoT adoption. Given the complexity and uncertainty associated with evaluating subjective criteria, we apply two advanced Multi-Criteria Decision-Making (MCDM) approaches—PFAHP and IGAHP. The following subsections describe the structure of the hierarchical model, the evaluation scales, and the implementation steps of both methods.
3.2. MCDM in Application with Literature Review
The MCDM problem calls for selecting the best alternatives from various options based on several predetermined criteria. Assume is a finite set of alternatives. A set of criteria is used to evaluate the options. For every alternative a performance score pick is determined by the criterion An MCDM method ranks the alternatives from best to worst based on the computed performance scores.
The idea of fuzzy sets, first presented by Zadeh [
51], has been a formal and practical tool for dealing with ambiguity, partially known knowledge, and inaccurate data in ambiguous and inconclusive real-life situations. Fuzzy sets, also known as type-1 fuzzy sets, are classical crisp set generalizations that allow elements of the universal set to have a given probability of belonging to a specific set. To do this, membership functions—often denoted by μ—that map each member of the universal set to the interval [0, 1] are used. Zadeh [
52] created type-2 fuzzy sets as ordinary fuzzy set generalizations with a membership function grade formed of a type-1 fuzzy set because it can be challenging to quantify uncertainty and determine the proper weight of the membership function. They are convenient when setting a membership function for a fuzzy set is difficult [
53]. Intuitionistic fuzzy sets (IFSs), which have both the membership and non-membership functions, were presented by Atanasov [
54]. Intuitionistic fuzzy sets of the second type [
55], more recently known as Pythagorean fuzzy sets (PFSs), were introduced by Yager [
56]. The sum of the squares of their membership function and non-membership function lies in the interval [0, 1]. They improved the preexisting circumstances and allowed the decision-makers to characterize the hazy portion of the material more thoroughly and in depth. Geometrically speaking, focusing on the first quadrant expands the surface of decision-making options from a triangle constrained by the points (0, 0), (1, 0), and (0, 1) to the circle section. Based on this method, decision makers express their opinions regarding the support (membership) and opposition (non-membership) grades for alternative eligibility in practice. The sum of these grades of membership and non-membership may be greater than 1, and their square sum is equal to or less than 1 [
57]. PFSs are incorporated into a risk assessment methodology in [
58] and a superiority and inferiority ranking methodology in [
57]. For MCDM issues, the Pythagorean fuzzy Technique for Order of Preference by Similarity to Ideal Solution was developed in [
59,
60], Pythagorean fuzzy scoring was developed in [
61], and Pythagorean Fuzzy AHP was used to solve issues associated with landfill site selection and scientific education innovation platforms [
62]. Using the Interval Valued Pythagorean Fuzzy AHP, a scoring model for the smartness of public buildings was developed [
63]. PFSs were applied in the development of solar technology [
64], multi-criteria evaluation of cloud service providers [
65], assessment of the performance of course content indicators [
66], and selection of locations for waste disposal [
67]. MCDM has found applications in various spheres, from AHP methods [
68,
69], the Fuzzy Analytical Hierarchy Process (FAHP), and Type-2 methods [
70], to more recent applications [
70,
71].
3.3. Hierarchy Structure of IoT Effectiveness
Creating a platform for enhancing efficiency in sustainable IoT by modeling indicators is a complex task. Every company is unique, and achieving IoT efficiency in different environmental conditions is a challenge. Other domains and constitutive variables associated with successful IoT are identified by reviewing the literature.
3.3.1. Expert Involvement
When selecting indicators, an agreement was reached on the source of indicators based on the given literature. One group of experts opted for interval scoring, while another opted for a linguistic scale. Fifty-five experts from 27 companies in Serbia participated in the selection and evaluation of the indicators. Companies operate across a range of industry sectors—such as manufacturing, logistics, energy, and smart services—with a strong emphasis on ensuring that the collected data accurately represent real-world operational practices and conditions. Instead of relying on assumptions or theoretical opinions, the experts provided input based on their own experience working on IoT projects and the decision-making process within their organizations. In this way, the priorities among the indicators are established based on their practical usability, rather than theoretical assumptions.
The proposed literature served as the basis for selecting the sub-criteria. The professional profiles of the experts are shown in
Figure 4a, and their work experience is shown in
Figure 4b.
Professional consultation with specialists actively utilizing IoT technologies was a component of the qualitative study. Experts were grouped based on age, education, and job experience to minimize potential bias in the assessment process and to benefit from a variety of viewpoints. These experts came from both the ICT sector and business management fields, offering balanced insights from both technical and business perspectives. The expert engagement followed these phases:
Initial outreach and participant selection from IoT-adopting enterprises, ensuring representation across roles (technical and managerial) and domains (
Figure 4a).
Categorization by work experience to balance junior and senior perspectives (
Figure 4b).
Distribution of structured pairwise comparison questionnaires tailored to each method (PFAHP/IGAHP), along with short training materials to ensure methodological understanding.
Independent and anonymous scoring to minimize peer influence or groupthink.
Cross-validation by applying both methods and comparing results using Spearman’s and Salabun coefficients to assess the reduction of subjectivity.
Bias Mitigation Measures were taken to lessen subjective bias and improve the validity of expert contributions throughout data gathering and analysis:
A wide range of expertise. Experts were selected to ensure a mix of practical and strategic perspectives.
Structured guidance: All participants received methodological instructions and examples to ensure consistency in pairwise comparisons across both PFAHP and IGAHP formats.
Consistency filtering.
Methodological cross-checking.
3.3.2. Hierarchy Development
By examining the references according to the primary sets of indicators, we generated a hierarchical structure, as shown in
Figure 5.
This research was conducted according to a specified research design consisting of preliminary research or an introduction to further quantitative research. Along with the formulation of the problem, the definition of the subject, the importance and objectives of this research, the enterprise being investigated, and the structure of this research were elaborated in detail. Interviews covered the set topics and subtopics; these were followed by linguistic evaluations. The examination was conducted in accordance with the methodological (technical) rules of the interview. Information informing the experts’ evaluations was obtained, taking into consideration the respondents’ personalities and dignity. Given the differences in the importance of the indicators, the experts provided two assessments: linguistic and interval. The experts’ choices between these two approaches are provided in the methodology.
We utilized the experts’ responses and judgments to construct pairwise comparison matrices necessary for both PFAHP and IGAHP methods. These empirical data were utilized to make the decision model more applicable and realistic for the practical validation of the proposed framework. Criteria for expert selection included established experience with IoT implementation or strategic planning in enterprise environments.
3.4. Pythagorean Fuzzy Analytical Hierarchy Process (PFAHP)
As a fuzzy set generalization, the Pythagorean fuzzy set proposed by Yager [
56] considers membership and non-membership. The proposed Pythagorean fuzzy analytic hierarchy method is presented through the following phases: linguistic evaluation and weights in fuzzy numbers. In the first phase, the experts must rate their opinion on the dimensions against the identified indicators according to the problem. Experts were asked to rate the pairwise comparison of fuzzy AHP on a five-point scale. The use of five-point linguistic scales is widespread in the application of such methods. It is associated with a person’s ability to easily distinguish five degrees on a scale. The linguistic variables are presented in
Table 3. Then, decision-makers (DMs) are asked to provide a rating using Pythagorean fuzzy number linguistic scales defined by the two parameters of PFN (membership and non-membership functions).
Let
be a fixed set, then a Pythagorean fuzzy set (PFS)
is an object with the following form (Equation (1)):
where
denotes the degree of membership and
denotes the degree of non-membership of the element
to the set
and satisfies (Equation (2)):
The pair
is called a Pythagorean fuzzy number (PFN), with the degree of indeterminacy defined by Equation (3).
The geometric interpretation of the space of a Pythagorean membership grade is provided in
Figure 6.
Definition 1.
For any two PFS, , and the basic operations are defined by Equations (4)–(7).
Definition 2.
A score function, defined to compare the magnitude of two PFNs, is presented in Equation (8).
Definition 3.
The accuracy function, defined to compare the magnitude of two PFNs, is presented in Equation (9).
The PFAHP method can be expressed as follows [
63]:
- (1)
The MCDM problem is generated in a hierarchical structure with a defined goal.
- (2)
The comparison matrix shows a pairwise comparison of the criteria based on the DMs’ preferences. The definition in
Table 2 is used to build the relevant comparison matrices.
- (3)
Apply Saaty’s classic consistency analysis to determine the comparison matrix’s consistency. Each pairwise comparison matrix is examined for consistency using the matrix consistency indexes and , where is the matrix’s largest eigenvalue, and RI is the random index. The is suitable; if not, experts should reevaluate their conclusions to make them more consistent.
- (4)
Fuzzy weights of each criterion and global fuzzy weights are calculated. By multiplying the values for each criterion using Equation (5), the geometric mean for each row is determined. Then, the root values are calculated by applying Equation (7).
- (5)
The defuzzification process is conducted using Formula (10).
The PFAHP method has the following advantages:
Compared to the ordinary fuzzy AHP, the Pythagorean AHP allows for greater freedom in expressing the degree of certainty and uncertainty.
It enables the expression of more complex expert opinions, especially when the opinions are uncertain or conflicting. The modeling of expert ratings is more precise.
When experts cannot agree, Pythagorean fuzzy numbers enable the expression of differences in certainty.
Multidimensional thought processing enables the use of multiple experts with varying degrees of expertise.
3.5. Interval Grey Analytical Hierarchy Process (IGAHP) Method
One way to overcome the shortcomings of the AHP method is to combine the application of intervals and AHP methods by using interval comparison matrices in pairs in the AHP technique and the application of the IAHP method.
IGAHP is an extension of the classical Analytic Hierarchy Process (AHP) that utilizes grey theory and interval values to enhance the handling of uncertainty and imprecision in decision-making, particularly when subjective expert judgment is involved. This method is mostly used in multi-criteria decision-making (MCDM) when the data are incomplete or imprecise, and expert ratings are given as intervals, which introduces ambiguity in preferences between criteria.
An interval grey number is an interval, defined by Equation (11).
The main characteristic of is that its exact value is unknown. The only known information is the range where the value lies.
Definition 4.
For two interval grey numbers and and scalar , the basic operations are defined as follows:
Addition:
Subtraction:
Multiplication:
Inverse: 1/
Division:
Scalar multiplication:
Interval grey numbers are presented in [
72,
73]. Even in the case of the opinion of only one expert, that expert often cannot decide on a specific numerical value that would express their position on the dominance of one criterion over another. The problem becomes more significant when multiple experts from various professions are involved, and the issue is multidimensional. To overcome these problems, instead of using classic comparison matrices, interval comparison matrices can be used
,
, where
represents the lower limit and
represents the upper limit. Some interval mathematics algorithms can be found in [
74,
75].
The IGAHP method can be expressed as follows:
- (1)
The general goal definition and identification, and the hierarchical structure formation through the criteria and sub-criteria identification contribute to the general goal (Equation (12)).
- (2)
The comparison judgment matrix
Cint creation [
76]:
In the matrix
for all
.
- (3)
The consistency of matrix
examination. Based on the matrix
, non-interval matrices
,
and
,
are constructed and presented by Equations (13)–(15).
The consistency of the matrix is examined by checking the consistency of introduced non-interval matrices and If matrices and are consistent and meet the condition then the interval matrix is also consistent.
- (4)
Determination of interval matrix weighting vectors. The convex combination method is used to calculate interval matrix
weights [
77]. Let
is a vector containing the weights of a matrix
, then
, for all
and all
.
- (5)
Determination of the probability matrix of preferences
. Let
and
be two intervals. Then,
and
Using Equation (16), we obtained the probability
that interval
is bigger than interval
by
.
Interval weights are ranked using the row–column elimination method according to the obtained probability matrix [
78]. Fuzzy and interval approaches can be used in more ways when using MCDM [
79,
80].
With the IGAHP method, respondents are expected to give an interval value of the liking rating, which is much easier than deciding on a specific value. With the PFAHP method, respondents are allowed to determine how much they like or dislike each statement (which is a novelty). The use of five-point linguistic scales is the most widespread in the application of such methods, and it is associated with the possibility of a person being able to distinguish five degrees on a scale with great ease. Using a combination of these two methods and comparing their rankings was introduced to overcome potential biases in expert judgments and scalability challenges of the proposed model.
Advantages of the IGAHP method:
Imprecision robustness—instead of forcing exact values, it embraces uncertainty.
Better reflects expert opinion—experts can provide approximate values.
Suitable for complex decisions—especially when there are multiple experts and differences in opinion.
Flexibility—can be combined with other methods.
Figure 7 shows a graphic representation of these algorithms.
Following the previously defined methodological setting, this research continued with consistent application of the PFAHP and IGAHP methods within the framework of the developed hierarchical model. The criteria were evaluated and weighted. In the following section, the results of applying the model will be presented, including the obtained priority values and their significance for strategic decision-making in the context of IoT implementation.
4. Results and Discussion
This study uses two approaches for the investigation. The AHP (fuzzy and interval grey method) is suitable for MCDM problems when it is difficult to precisely quantify the impact of criteria on decision problems. With the introduction and execution of PFAHP and IGAHP methods, the subjective aspects that dominate the decision-making process are reduced, making the prioritization process more transparent.
In this section, we apply the algorithms described in
Section 3.3 and
Section 3.4. All comparison matrices have been created based on the opinions of experts in the IoT and entrepreneurship fields, and are consistent. The experts determined how the criteria and sub-criteria were compared. Business experts agreed on the interval approach, whereas experts from the ICT and scientific domains employed the PFAHP method in the evaluation of IoT.
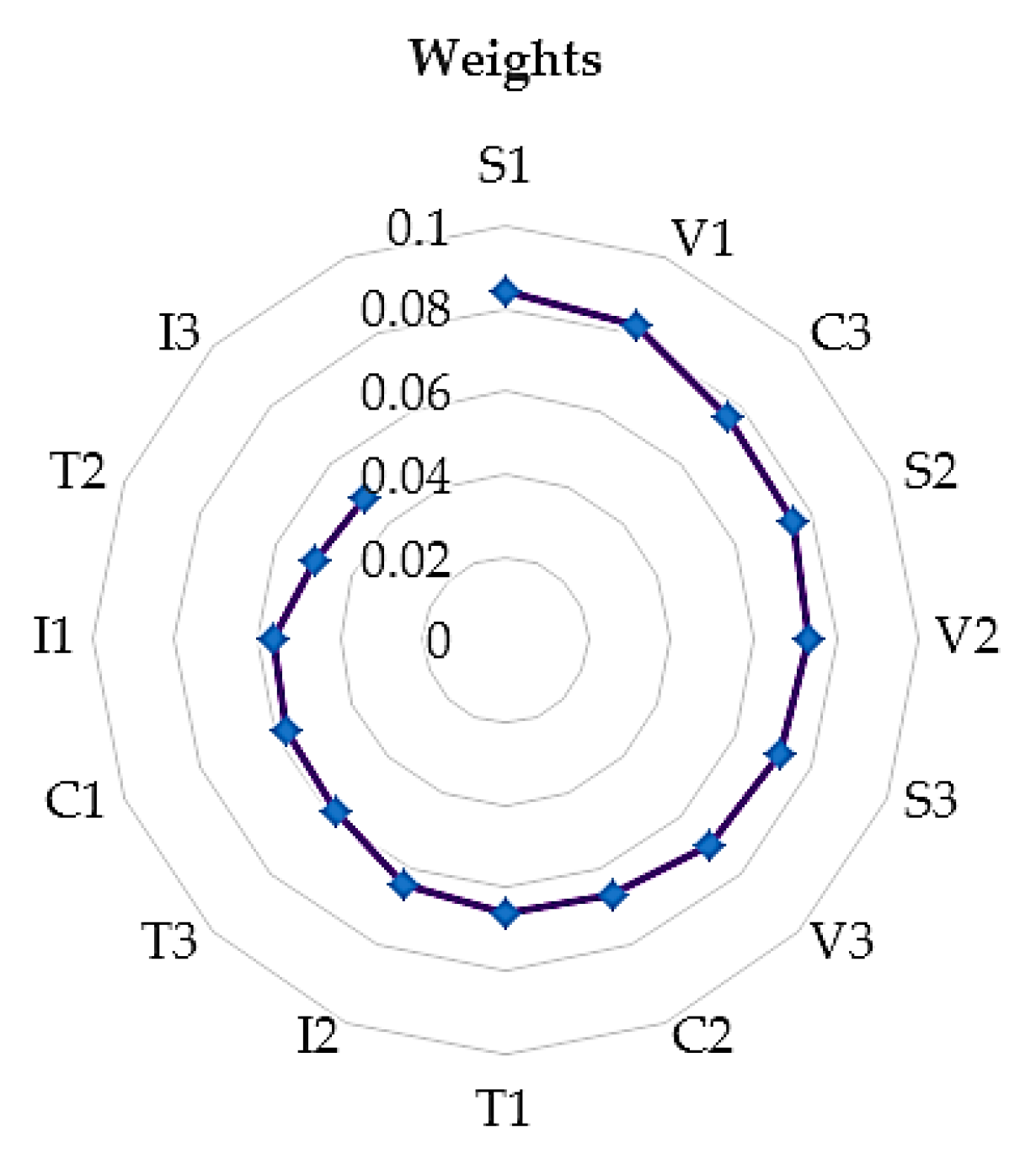
Figure 8 graphically displays the weights of the sub-criteria.
Let
denote the lower limit and
denote the upper limit of interval weights.
Figure 9a shows the interval weights of the indicators, and
Figure 9b shows the final ranking of the indicators using the IGAHP method.
Interval assessment assigns equal weights to all values from the expert-selected intervals, but the Pythagorean fuzzy techniques assign more weight to central values.
Table 16 contains the final rankings of indicators using the PFAHP and IGAHP methods.
Comparing ranked indicators involves analyzing the different ranks, scores, or values of indicators to determine their relative positions, importance, or relationships. Depending on the nature of the data, several methods are used to compare ranks. Spearman’s rank correlation is a non-parametric technique used to determine the degree and direction of association between two ranked datasets. This method is employed when dealing with ordinal (ranked) data or data that are not regularly distributed. We used Spearman’s rank correlation coefficient to compare the lists of ranked sub-criteria generated using the PFAHP and IGAHP methods [
81], as per Equation (17).
There are
elements ranked in total, and the ranks of element
in the compared rankings are
and
. Salabun similarity ranking is a specific approach for rank comparison that was developed to analyze the similarity between different ranking methods or ranked datasets. This method is used to assess the similarity between two rankings, specifically how well they align in terms of the relative order of the objects or factors being ranked. Salabun
SW coefficient was utilized to analyze the ranking similarity [
82] following Equation (18):
Based on the formulas, the indices of agreement obtained for the PFAHP and IGAHP methods are =, . The listed coefficients indicate good agreement between the ranks of these two methods. The consistent application of the PFAHP and IGAHP methods, as the most influential indicators for efficiency in sustainable IoT enterprises, highlights the importance of information privacy and market demand. For IoT to be sustainable in enterprises, information privacy is a primary guideline due to the vast amount of personal data collected. From the outset, entrepreneurs must prioritize data protection by implementing strong encryption and authentication and conducting regular security audits. Navigating the complex legal landscape surrounding data privacy is also essential. Ensuring sustainable growth and fostering consumer trust require robust security protocols and adherence to privacy laws. Because it influences production and helps direct competition in the market, market demand has an impact on both consumers and businesses. Vendors can capitalize on future growth prospects and align their sales efforts with industry and regional trends by leveraging market information and projections. Adopters can make well-informed decisions about their IoT investments and plans by monitoring market trends, drivers, and growth projections. Significant indicators of gains from PFAHP are sensor networks, authorization, convenience, and data management. The differences in the interval approach are that the sequence is somewhat different; these are, in order of importance, data management, sensor networks, performance, and authorization. In contrast to IGAHP, which promotes data management, the PFAHP technique favors authorization. The differences in the final ranks between the IGAHP and the PFAHP methods are due to different evaluation approaches. The least influential indicators are functional orientation, monitoring, and cloud computing.
Improving efficiency in a sustainable IoT enterprise enables IoT technologies to achieve lower resource consumption, faster and more accurate operations, waste reduction, and cost optimization, all while preserving environmental and social standards. To measure efficiency not only by speed and profit, but also by how smartly and responsibly an enterprise uses IoT to improve sustainability and competitiveness, we developed an integrated model that incorporates the identified influential factors based on the final rankings obtained, as shown in
Figure 10.
In addition to the two primary indicators, sensor network, authorization, convenience, data management, and performance are key factors in achieving IoT system efficiency in enterprises. Each of these factors directly affects the overall functionality of the IoT solution, enabling better data collection, analysis, and management, as well as improving security and user experience.
Considering the influential factors, creating a platform for a successful IoT business requires the following key tasks:
Companies should take certain steps to improve information privacy in IoT systems. To ensure that data transmitted from IoT devices cannot be intercepted or modified, end-to-end encryption should be used. Cloud services or on-premises servers that comply with data protection regulations should be used. Additionally, measures should be implemented to collect only necessary information, thereby reducing the likelihood of sensitive data leaks.
Increased market competitiveness may influence how businesses deploy IoT technologies. Data analytics enables IoT devices to collect extensive information about consumers, markets, and operations. Businesses can better understand user wants and react to demand changes more rapidly by evaluating these data; additionally, increased flexibility through the use of IoT devices enables companies to adjust production, distribution, and logistics processes swiftly based on real-time market data.
The sensor network is the heart of an IoT system. To improve the efficiency of an IoT system, sensor optimization requires the use of high-quality, low-power sensors that provide accurate and relevant data. For scalability, a company needs planar networks that can be easily expanded to include new IoT devices and sensors as the business grows.
Authorization and access control are essential for protecting and securing data. To provide safe access to devices and data, multi-factor authentication must be used. Employee roles and responsibilities should be specified to provide regulated access to sensitive data. Regularly updating security protocols involves maintaining up-to-date protection and audit protocols to ensure constant system security.
IoT solutions should be easy to implement and use. It is necessary to develop a simple interface for end-users and administrators, allowing them to easily manage and interpret the data. Tools for easy monitoring of device operation, as well as quick problem-solving (such as automatic warnings of malfunctions or device crashes), should be provided.
High performance in IoT systems is largely dependent on efficient data handling. Analysis and reporting should be made easier with the use of data in centralized databases. Real-time data analysis technologies must be implemented to facilitate prompt decision-making in business operations. This requires investing in technologies for cleaning and validating data to avoid errors that can affect analysis and decision-making.
For businesses to optimize network resources and enhance IoT device performance, they must select protocols and architectures that strike a balance between speed and reliable data transfer. To manage the load effectively, infrastructure overload should be avoided, the best possible resource allocation should be enabled, and scalable systems and cloud resources should be implemented. Additionally, to enable autonomous system performance modifications, integration with machine learning and artificial intelligence is required.
Data management includes its proper life cycle. Data should be backed up regularly, and old data should be archived to ensure business continuity. Data must comply with all legislative and regulatory requirements related to their storage and processing.
Standardization of IoT systems enables easier interoperability and reduces complexity. Standardized protocols should be used to facilitate the interoperability of devices from different manufacturers. It is necessary to commit to industry standards and certifications.
Several studies emphasize the importance of integrating IoT technology into industrial systems to enhance productivity, reduce resource consumption, and improve operational efficiency. For example, it was demonstrated in [
83] that an Internet of Things system with a multi-layered design and real-time analytics has a direct impact on operational efficiency and sustainability. Similarly, an IoT system for monitoring and analyzing energy consumption and environmental parameters was developed in [
84]. The results confirm the possibility of optimization through intelligent management, demonstrating real savings in energy costs and improvement of environmental parameters.
The authors of [
85] conducted research using Japanese manufacturing enterprises as an example to evaluate the impact of IoT investments. The study claimed that investments in IoT led to quantifiable improvements in operational and financial efficiency, as well as faster amortization. In support of this viewpoint, the authors of [
86] demonstrated that IoT monitoring enables the analysis of energy trends and recommended production management to optimize operational parameters.
Numerous metrics, including energy efficiency, equipment availability, production precision, return on investment, and the quality of a company’s decisions, can be used to measure the effects of IoT adoption. Therefore, by applying methods such as PFAHP and IGAHP, it is possible to systematically evaluate and rank relevant indicators that support decision-making towards the digital and sustainable transformation of enterprises.
Most studies focus on specific applications of IoT systems in enterprises and industrial environments. Compared to these approaches, the application of PFAHP and IGAHP methodologies provides a structured, multi-criteria framework for identifying and prioritizing IoT performance indicators in enterprises. While the studies above analyze the effects of IoT through practical case studies, PFAHP and IGAHP facilitate a systematic and analytical assessment of various criteria under uncertainty, thereby contributing to more reliable decision-making in the strategic management of IoT infrastructure.
The reliability and credibility of indicator rankings were enhanced by the hybrid use of PFAHP and IGAHP, which yielded complementary insights. The framework enabled a deeper understanding of the factors that most significantly impact IoT success in business environments by integrating two methods for modeling uncertainty.
Although this study does not present individual company case studies in narrative form, the framework was validated through real-world consultations with subject matter experts who provided input based on their companies’ specific IoT strategies and challenges. This type of integrated empirical evaluation enhances the credibility and applicability of the suggested model in various business contexts. The practical value of the hybrid PFAHP–IGAHP approach is enhanced by consistent prioritization patterns across sectors, which further validates that the identified indicators are context-sensitive and generalizable.
The significant degree of agreement between the two methodologies validates the robustness of the proposed hybrid framework and further confirms the set priorities. The approach’s strength lies in its ability to offer multiple perspectives on uncertainty, in addition to its numerical consistency. When assessing subjective factors such as convenience, perceived value, or information privacy, a PFAHP approach is necessary to capture linguistic ambiguity and complex expert preferences adequately. By better managing incomplete data and structural ambiguity, the IGAHP technique offers greater clarity in data-driven indications, such as market demand or data governance.
The proposed framework enables a more comprehensive, context-aware assessment process that supports strategic decision-making in IoT business environments by integrating these two approaches. In addition to highlighting the most important elements, this two-layer viewpoint clarifies the circumstances under which particular signs become crucial. In this way, the model bridges the gap between technical feasibility and business relevance, providing a scalable and adaptable decision support tool that enhances business outcomes. Unlike previous studies that have frequently concentrated on assessing the Internet of Things (IoT) within specific domains, this study presents a comprehensive framework suitable for the strategic and operational needs of enterprises pursuing sustainable digital transformation. Therefore, the methodological contribution lies not only in the combination of techniques but in their targeted and synergistic application to an under-researched context of high-impact decision-making.
The current study is positioned as a development of a decision support framework, based on expert consensus in real business contexts. Case studies can further enhance empirical validation. This provides a strong foundation for future work, where the framework can be tested and refined through the implementation of specific cases.
5. Conclusions
The development and implementation of the Internet of Things (IoT) concept are key elements of digital transformation in the modern business environment. By connecting devices, systems, and users, IoT creates new opportunities for improving efficiency and improving the quality of services, as well as for making decisions based on real-time data analysis. However, despite the great potential, numerous challenges still limit the full exploitation of IoT technologies, particularly in the domains of security, user trust, and understanding of system complexity by end users and decision makers. To enhance efficiency in sustainable IoT enterprises, this study developed and presented a multi-criteria decision support model that integrates the PFAHP and IGAHP methods. Combining these approaches enables comprehensive modeling of critical indicators while simultaneously accounting for uncertainty (through fuzzy logic) and incomplete data definition (through grey logic), resulting in a more flexible and reliable assessment model. The investigation’s findings indicate that, when it comes to ranking the elements that affect the successful deployment of IoT devices, metrics such as security, value, and connectivity occupy a prominent place. However, even though they are important, qualities such as intelligence and telepresence have a lesser effect. At the same time, the application of both methodological perspectives (PFAHP and IGAHP) enabled the identification of additional, highly relevant indicators, such as information privacy, market demand, sensor networks, data management, and authorization. Comparing the obtained rankings revealed a good degree of agreement between the different analytical frameworks, further confirming the reliability of the results and the practical applicability of the proposed model. In addition to the theoretical contribution to the field of multi-criteria decision-making under uncertainty, this study offers concrete guidelines for optimizing business processes and infrastructure in the IoT environment. The results have multiple implications, ranging from supporting managers in making informed and objective decisions to better resource allocation and prioritization of investments, and the creation of regulatory and technological policies that affirm security, data protection, and trust in digital technologies. In future research, the model can be extended by applying it to various industrial domains and improved through integration with dynamic systems for real-time risk and performance assessment, further enhancing its practical value in the context of digitally oriented, sustainable business. This integration would provide methods for assessing risk and performance in real time. The findings of this study are not purely theoretical; they are derived from applied knowledge within actual IoT-adopting enterprises, providing a foundation for reliable strategic planning in uncertain and dynamic IoT environments.