An Overview of Blockchain and IoT Integration for Secure and Reliable Health Records Monitoring
Abstract
1. Introduction
- To summarize the IoT and BC applications in EHR;
- To review the research and contributions applying IoT and BC in EHR;
- To deliberate on and review existing BC consensus algorithms for the BC-based IoT-EHR applications;
- To propose a BC-based IoT-EHR framework for secure and reliable health record storage supporting secure and reliable health record storage with interoperability features.
2. Background Study
2.1. Electronic Health Record (EHR) System
2.2. Internet of Things (IoT)
2.3. Security Challenges Related to IoT in EHR
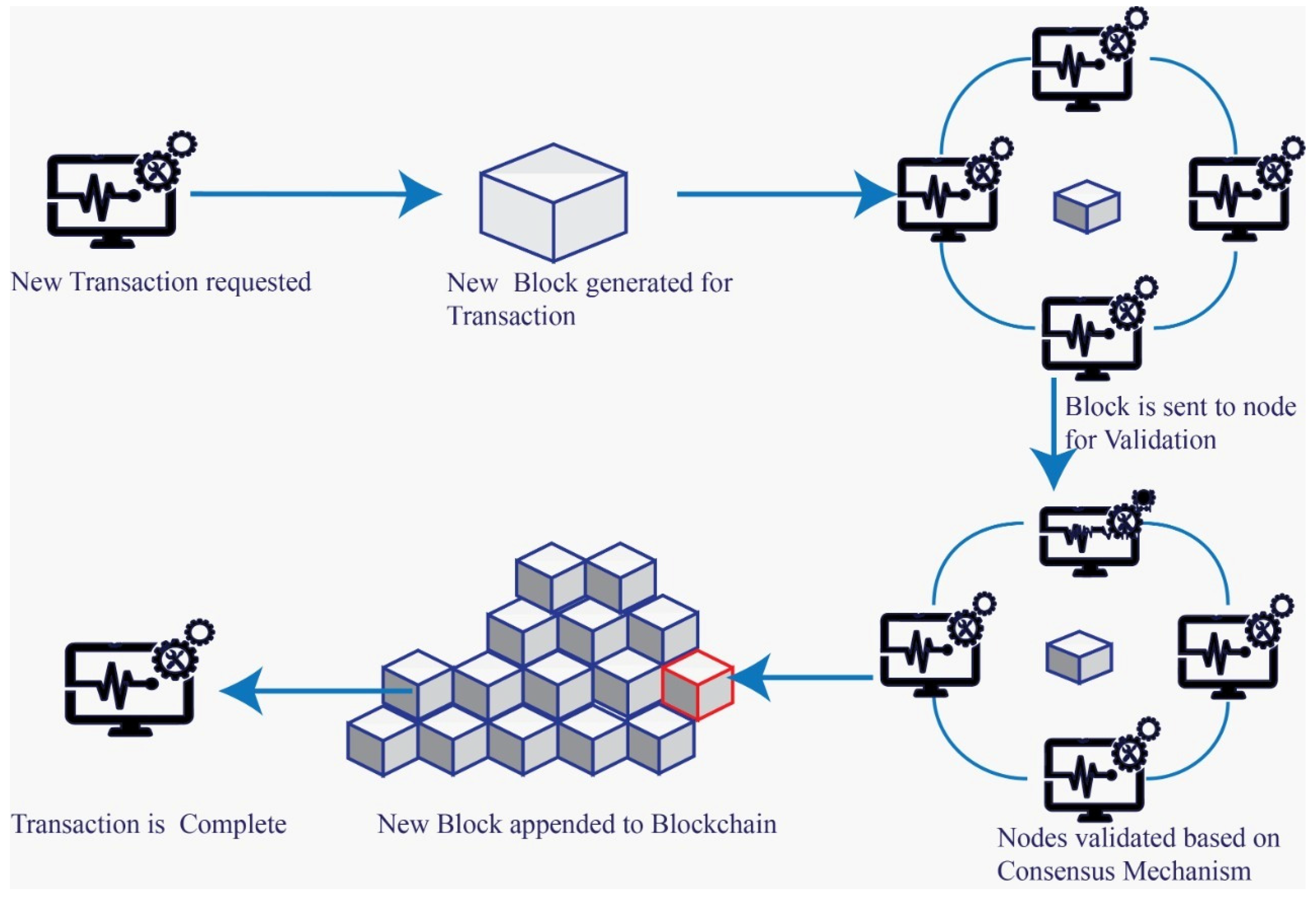
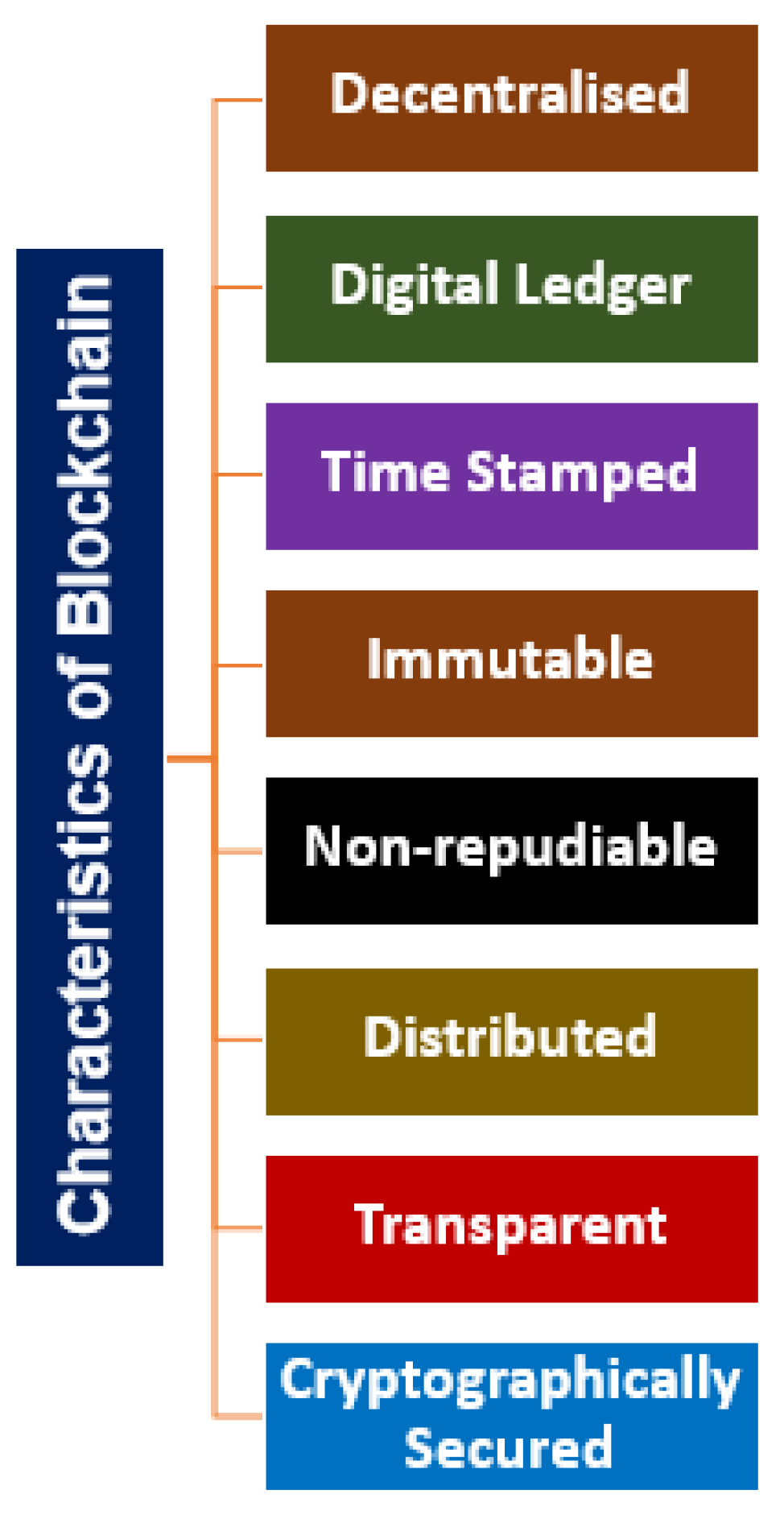
2.4. Blockchain (BC)
Types of BC
- Public BC: Anybody can join and exit the BC network. A participant does not need authorization to function as a miner or a typical BC node, and everyone has equal access. Incentives are used to guarantee participants’ involvement and activity in such a BC.
- Consortium BC: It allows just a select set of nodes to act as the governing authority in the consensus mechanism.
- Private BC: A specific entity manages, approves, and administers a private BC. Users must obtain permission from the proper authorities in order to participate. Transactions are confirmed in confidence and may not be available to the general public. A private BC frequently generates blocks faster and produces more transactions than other types of BC.
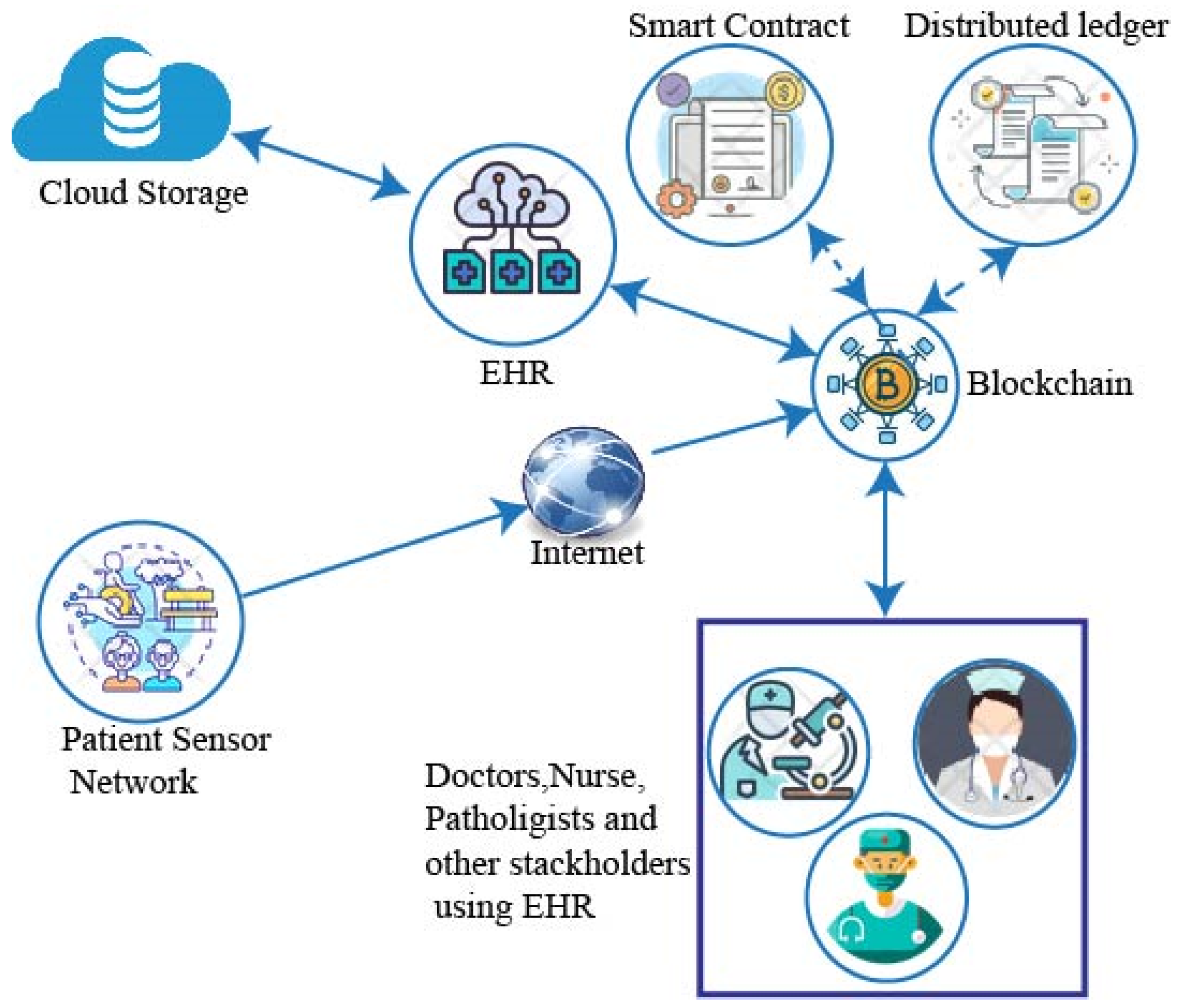
2.5. Blockchain and IoT in EHR
- It offers a secure platform whereby communication can safely take place between all devices connected to the network.
- It provides for ample security of the network, which safeguards the stored data against any information attacks.
2.5.1. Benefits of BC and IoT application in EHR
- Privacy/Anonymity: BCs employ public-key cryptography and use digital identities specific to various transactions. This feature obscures the actual identification of IoT applications that withhold sensitive information [44].
- Smart Contracts: Smart contracts are those that are executed once their conditions are fulfilled. Certain BCs like Ethereum provide this facility. For instance, one end of the system can make payments when certain associated conditions are fulfilled, like some product/service being delivered [45].
- Security:
- ▪
- Privacy: Only allows authenticated members to gain access to stored data. To preserve confidentiality and complete privacy, blockchain applications must be used wisely with other cryptographic mechanisms [50].
- ▪
- Integrity: An unidentified entity cannot modify the recorded data. It is a must that the data being transmitted are accurate.
- ▪
- Availability: The access to information is levied to legitimate users, and any improper access denial(s) to resources is prevented.
- ▪
- Accountability: Every requisite individual or entity will be duly audited, supervised, and held accountable for any adversity.
- DDoS warning and Mitigation: BC and smart contracts can merge together in collaborative architectures that can produce DDoS notifications on numerous domains. With transactions based on BC, it becomes improbable for information attackers to launch malware on devices connected through the IoT network and install their IoT botnets to make DDoS attacks. The stringent check on outgoing traffic makes it impossible for DDoS messages to spread from IoT devices [42].
2.5.2. Blockchain application in IoT-based EHR
3. Comparative Study of Blockchain Consensus Mechanism for IoT-Based EHR
- PoW (Proof of Work): It is based on the computational effort required based on mathematical puzzles used in asymmetric cryptography. Solving a problem is complex, but verifying that output is easy. As PoW is widely used in several platforms, due to high complexity and resource requirements, there is a mild prospect of involving PoW in healthcare systems involving IoT devices [61].
- LPoS (Leased Proof of Stake): Addresses centralization in PoS, makes low-balance nodes, leases contracts, and shares benefits with the owner. The PoS consensus algorithm will facilitate a high-quality e-health service [62].
- DPoS (Delegated Proof of Stake): With DPoS developed from PoS, network users can elect delegates to verify blocks. It can be used in highly possible electronic health situations [63].
- PoI (Proof of Importance): It is an enhancement of PoS. It studies the nodes’ balance and nodes’ credibility. It is an efficient network. We suggest using it for e-healthcare systems, as healthcare professionals’ credibility may be used for patient decision making [64].
- PBFT (Practical Byzantine Fault Tolerance): Each node works together to add the next block. Consensus requires 2/3 nodes. It provides low tolerance to malicious nodes. It is recommended for healthcare use [65].
- PoA (Proof of Activity): It is a hybrid version of PoW and PoS. First, PoW is completed. Then, after a PoS, a group of verifiers sign jointly to place the transaction in the miner’s header. Despite the long delay, it is not ideal for IoT; therefore, e-healthcare is not a reasonable option [66].
- DBFT (Delegated Byzantine Fault Tolerance): It is an enhancement of PBFT. Nodes are selected as representatives of another node. Therefore, using dBFT in IoT-based BC healthcare frameworks is not fully understood [67].
- PoC (Proof of Capacity): It is an upgraded PoW. It is used to record large data sets for mining other nodes’ next blocks. It is not adequate for IoT but is used for other health-specific programs [68].
- PoS (Proof of Stake): A prevalent consensus mechanism randomly selects the node to tackle and which block to mine next. Within PoS, the mining reward/coin production does not exist, but the miner is compensated with a transaction fee [69].
- PoB (Proof of Burn): It sends coins to an irreversible address. Many burned coins support miners in mining. It is a good choice for cryptocurrency architecture but poor for IoT due to the entirely conditional economic model and burning of the coin. Because of its uncontrolled burning method, it is not appropriate for e-healthcare applications [70].
- Proof of Trust (PoT): A consensus algorithm that offers equal opportunities to participate in crowdsourcing activities. Owing to the difference in reputational standards, only a few members are not in the consensus nodes. PoT consensus uses subjective logic algorithms, using time signs and digital signatures to maximize block node unpredictability. The improved algorithm will automatically complete a reputation evaluation of participating crowdsourcing members. The POT can achieve validity, fairness, and security [61,71].
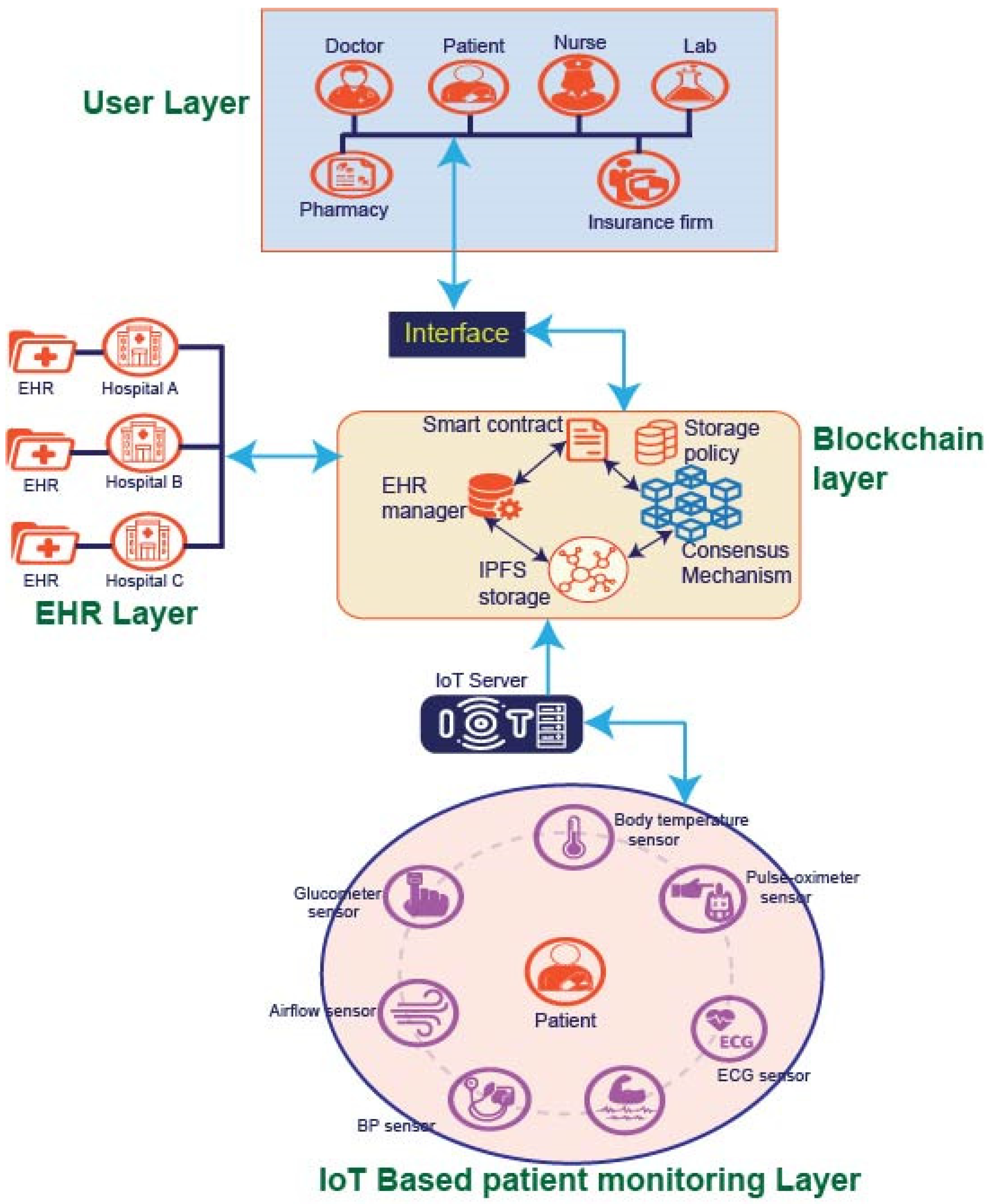
4. Blockchain-Based Framework for IoT-EHR
- Privacy and tracking of EHR of IoT-based patients without alteration or corruption;
- Security of EHR data is assured;
- To give and revoke permission by patients to parties wishing to use the EHR data;
- It provides a framework for engaging numerous healthcare organizations and pharmaceutical companies in clinical trials and research on drug design, medications, and delivery facilities across the publicly accessible ledger database;
- It reduces operating costs and increases interoperability, universal accessibility, and truthfulness.
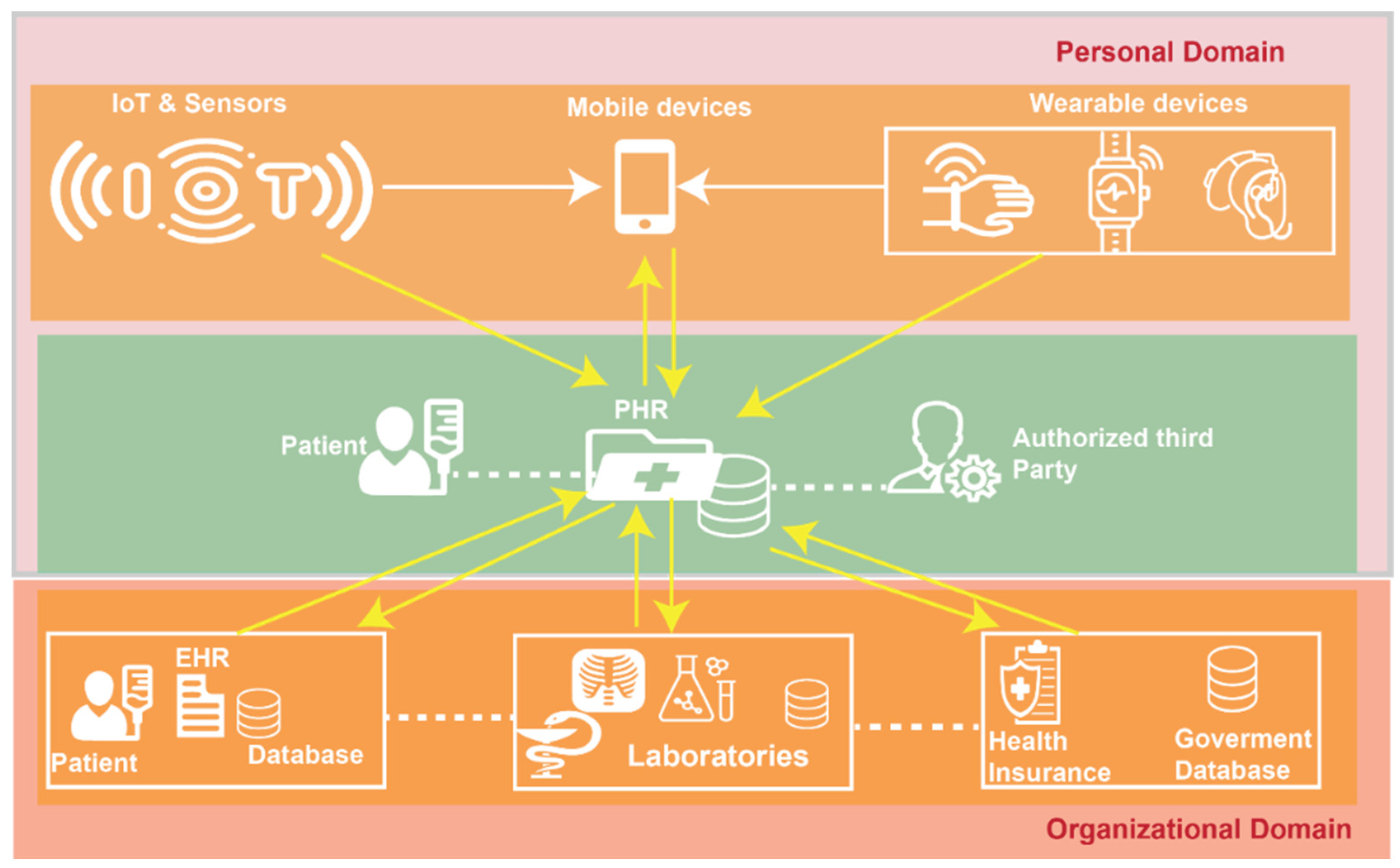
- EHR layer: At the EHR layer, which can also be termed as the healthcare provider layer, different healthcare organizations and entities collaborate to share their specific healthcare records, irrespective of the EHR storage type.
- BC layer: This layer connects with the EHR layer with the help of an interface that translates the records into a unified format, and details are stored in IPFS storage to support interoperability. The BC layer comprises a smart contract, storage policy, EHR manager, consensus mechanism, and IPFS storage. The EHR manager manages the records from different EHRs and processes them. The PoT consensus mechanism processes the new records before storing them in BC. Smart contracts provide auto-execution required for transaction processing.
- IoT-based patient monitoring layer: The patient sensor layer consists of different sensors to sense the various inputs for the patients, such as BP, EMG, ECG, glucose level, etc.
- User layer: The users connect with the system using the interface. They can enter any new record or view them based on their authorization in a standard template, irrespective of their actual storage format.
- Different hospitals or service providers can have their EHR with a heterogeneous structure having health records. They are processed at the BC layer for the sake of interoperability and security.
- The EHR layer is connected with the BC layer, and all the authentication and verification of records are conducted at the BC layer before storing them in EHRs. There is no direct connection between users of the system and EHRs.
- The IoT layer collects patient data. These sensor data are passed to the BC layer via the IoT server and are further processed using smart contract and storage policy before storing in the data storage.
- The BC layer consensus mechanism will mine and store the newly sensed data in the IPFS storage.
- The old records are mined using the EHR layer and processed. Furthermore, their hashes are stored in the BC layer to marinate records’ immutability.
| Algorithm 1: Oxygen Saturation Analysis |
| 1: oxygen_R Read Oxygen Saturation from sensor 2: Procedure oxygen_sat () 3: Store False 4: if (oxygen_R ≥ 94) then 5: Store True 6: end if 7: oxygen_sat Store 8: end procedure |
| Algorithm 2: Load record in EHR |
| 1: Load_EHR Store Record in EHR 2: Procedure EHR () 3: If Key_Entry == Owner_Key then 4: Create health Record object 5: Push the object in EHR 6: Return “New Record Stored” 7: Else 8: return Not authorized 9: end if 10: end procedure |
| Algorithm 3: Read EHR data |
| 1: View EHR record 2: procedure View EHR () 3: If Applicant ∈ Doctor then 4: Include All EHR Features 5: return EHR string 6: else if applicant ∈ Other then 7: Only Include EHR Attributes accessible by a Users 8: return EHR string 9: else 10: return Not authorized 11: end if 12: end procedure |
Security Analysis of the Proposed Framework
- Privacy: BC’s main strength lies in its immutability feature. The records are stored in a decentralized manner, and elliptical curve cryptography (ECC) is used to secure against privacy breach attacks and single-point failure. The decentralized nature also makes it secure against man-in-middle attacks.
- By utilizing digital signatures and the blockchain approach, the proposed solution significantly upholds the confidentiality of the data. The next step is to request permission to access the health archive’s record on the patient’s health. As a result, a session key is provided to the doctor so that they can access the EHR. This key allows access to the data and establishes the patient’s identity. A variety of degrees of authentication are employed to protect data confidentiality.
- Data Integrity: The hash of each record is stored, which can be used to verify the integrity of individual transactions. Each transaction is appended to the BC utilizing a consensus algorithm, but most existing consensus mechanisms are unsuitable for resource-constrained IoT devices. PoT can be a suitable consensus mechanism choice in such a case.
- In order to learn more about their clinical knowledge, doctors and patients want access to their EHRs. The client must first receive approval from the EHR system’s repository. The user information on the access list is double-checked to make sure of this. The customer is given access to the record at the stage at which they have been allowed access, if the value matches.
- Availability/DDoS Attack: Availability attacks affect resource or system usability. DDoS is a primary availability attack against any IoT network originating from unauthorized requests from unknown nodes. Such attacks can be avoided if nodes are fully identified and authorized. Two-factor authentication using IoT server and client IoT devices can be used to counter such attacks. BC-based identity frameworks can be other possible solutions.
- Authentication and Access Control: Proper authentication and role segregation of entities are essential for access control. The smart contract-based approach in the proposed framework provides a solution for proper access control.
5. Future Work
- Resources constraint: IoT systems have restricted memory and processing capacity, while BC requires tremendous energy. BC’s computational specifications for mining blocks are far beyond resource-constrained IoT devices.
- Bandwidth constraint: Verification of transactions is facilitated by the decentralization of the BC, where network nodes work together. The bandwidth of IoT devices in the end-device layer is constrained. BC-based applications may require more bandwidth; thus, any edge device should be able to handle them.
- Connectivity constraint: All nodes remain attached to the BC and communicate through predetermined protocols within BC technology. This feature also connects BC to IoT devices and is perhaps more vulnerable to security threats.
- Memory constraint: Many public BC technologies start charging transaction fees and use them to compensate those peers engaged in block mining. However, in the case of healthcare software, our requirements and limitations are very exceptional. Health data are analyzed regularly. Collecting and storing health data for various patients could expose a severe memory issue.
- GDPR compliance: GDPR mandates the appropriate and transparent acquisition, processing, and storage of personal data to reclaim data control. GDPR makes data protection compliance more manageable and less expensive for businesses. GDPR and HIPAA are primarily used to reduce the likelihood of privacy abuses in healthcare data [73].
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Rahmani, M.K.I.; Shuaib, M.; Alam, S.; Siddiqui, S.T.; Ahmad, S.; Bhatia, S.; Mashat, A. Blockchain-Based Trust Management Framework for Cloud Computing-Based Internet of Medical Things (IoMT): A Systematic Review. Comput. Intell. Neurosci. 2022, 2022, 9766844. [Google Scholar] [CrossRef] [PubMed]
- Alam, S.; Shuaib, M.; Khan, W.Z.; Garg, S.; Kaddoum, G.; Hossain, M.S.; Zikria, Y. Bin Blockchain-Based Initiatives: Current State and Challenges. Comput. Netw. 2021, 198, 108395. [Google Scholar] [CrossRef]
- Khubrani, M.M.; Alam, S. A Detailed Review of Blockchain-Based Applications for Protection against Pandemic like COVID-19. Telecommun. Comput. Electron. Control 2021, 19, 1185–1196. [Google Scholar] [CrossRef]
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On Blockchain and Its Integration with IoT. Challenges and Opportunities. Futur. Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Selvaraj, S.; Sundaravaradhan, S. Challenges and Opportunities in IoT Healthcare Systems: A Systematic Review. SN Appl. Sci. 2020, 2, 139. [Google Scholar] [CrossRef]
- Nazir, S.; Ali, Y.; Ullah, N.; García-Magariño, I. Internet of Things for Healthcare Using Effects of Mobile Computing: A Systematic Literature Review. Wirel. Commun. Mob. Comput. 2019, 2019, 1–20. [Google Scholar] [CrossRef]
- Pradhan, B.; Bhattacharyya, S.; Pal, K. IoT-Based Applications in Healthcare Devices. J. Healthc. Eng. 2021, 2021, 6632599. [Google Scholar] [CrossRef]
- Ratta, P.; Kaur, A.; Sharma, S.; Shabaz, M.; Dhiman, G. Application of Blockchain and Internet of Things in Healthcare and Medical Sector: Applications, Challenges, and Future Perspectives. J. Food Qual. 2021, 2021, 7608296. [Google Scholar] [CrossRef]
- Naresh, V.S.; Pericherla, S.S.; Murty, P.S.R.; Sivaranjani, R. Internet of Things in Healthcare: Architecture, Applications, Challenges, and Solutions. Comput. Syst. Sci. Eng. 2020, 35, 411–421. [Google Scholar] [CrossRef]
- Awotunde, J.B.; Jimoh, R.G.; Folorunso, S.O.; Adeniyi, E.A.; Abiodun, K.M.; Banjo, O.O. Privacy and Security Concerns in IoT-Based Healthcare Systems. In The Fusion of Internet of Things, Artificial Intelligence, and Cloud Computing in Health Care; Springer: Berlin/Heidelberg, Germany, 2021; pp. 105–134. [Google Scholar]
- Mustafa, M.; Alshare, M.; Bhargava, D.; Neware, R.; Singh, B.; Ngulube, P. Perceived Security Risk Based on Moderating Factors for Blockchain Technology Applications in Cloud Storage to Achieve Secure Healthcare Systems. Comput. Math. Methods Med. 2022, 2022, 6112815. [Google Scholar] [CrossRef]
- Reegu, F.A.; Abas, H.; Hakami, Z.; Tiwari, S.; Akmam, R.; Muda, I.; Almashqbeh, H.A.; Jain, R. Systematic Assessment of the Interoperability Requirements and Challenges of Secure Blockchain-Based Electronic Health Records. Secur. Commun. Netw. 2022, 2022, 1953723. [Google Scholar] [CrossRef]
- Zulkifl, Z.; Khan, F.; Tahir, S.; Afzal, M.; Iqbal, W.; Rehman, A.; Saeed, S.; Almuhaideb, A.M. FBASHI: Fuzzy and Blockchain-Based Adaptive Security for Healthcare IoTs. IEEE Access 2022, 10, 15644–15656. [Google Scholar] [CrossRef]
- Bigini, G.; Freschi, V.; Lattanzi, E. A Review on Blockchain for the Internet of Medical Things: Definitions, Challenges, Applications, and Vision. Futur. Internet 2020, 12, 208. [Google Scholar] [CrossRef]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of Things Security: A Top-down Survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef]
- Butpheng, C.; Yeh, K.-H.; Xiong, H. Security and Privacy in IoT-Cloud-Based e-Health Systems—A Comprehensive Review. Symmetry 2020, 12, 1191. [Google Scholar] [CrossRef]
- Yaqoob, I.; Salah, K.; Jayaraman, R.; Al-Hammadi, Y. Blockchain for Healthcare Data Management: Opportunities, Challenges, and Future Recommendations. Neural Comput. Appl. 2021, 34, 11475–11490. [Google Scholar] [CrossRef]
- Khezr, S.; Moniruzzaman, M.; Yassine, A.; Benlamri, R. Blockchain Technology in Healthcare: A Comprehensive Review and Directions for Future Research. Appl. Sci. 2019, 9, 1736. [Google Scholar] [CrossRef]
- Zhao, S.; Li, S.; Yao, Y. Blockchain Enabled Industrial Internet of Things Technology. IEEE Trans. Comput. Soc. Syst. 2019, 6, 1442–1453. [Google Scholar] [CrossRef]
- Saha, A.; Amin, R.; Kunal, S.; Vollala, S.; Dwivedi, S.K. Review on “Blockchain Technology Based Medical Healthcare System with Privacy Issues”. Secur. Priv. 2019, 2, e83. [Google Scholar] [CrossRef]
- Kassab, M.H.; DeFranco, J.; Malas, T.; Laplante, P.; Destefanis, G.; Graciano Neto, V.V. Exploring Research in Blockchain for Healthcare and a Roadmap for the Future. IEEE Trans. Emerg. Top. Comput. 2019, 9, 1835–1852. [Google Scholar] [CrossRef]
- Hussien, H.M.; Yasin, S.M.; Udzir, S.N.I.; Zaidan, A.A.; Zaidan, B.B. A Systematic Review for Enabling of Develop a Blockchain Technology in Healthcare Application: Taxonomy, Substantially Analysis, Motivations, Challenges, Recommendations and Future Direction. J. Med. Syst. 2019, 43, 320. [Google Scholar] [CrossRef] [PubMed]
- Agbo, C.; Mahmoud, Q.; Eklund, J. Blockchain Technology in Healthcare: A Systematic Review. Healthcare 2019, 7, 56. [Google Scholar] [CrossRef]
- De Aguiar, E.J.; Faiçal, B.S.; Krishnamachari, B.; Ueyama, J. A Survey of Blockchain-Based Strategies for Healthcare. ACM Comput. Surv. 2020, 53, 1–27. [Google Scholar] [CrossRef]
- Wang, X.; Zha, X.; Ni, W.; Liu, R.P.; Guo, Y.J.; Niu, X.; Zheng, K. Survey on Blockchain for Internet of Things. Comput. Commun. 2019, 136, 10–29. [Google Scholar] [CrossRef]
- Taylor, P.J.; Dargahi, T.; Dehghantanha, A.; Parizi, R.M.; Choo, K.K.R. A Systematic Literature Review of Blockchain Cyber Security. Digit. Commun. Netw. 2020, 6, 147–156. [Google Scholar] [CrossRef]
- Houtan, B.; Hafid, A.S.; Makrakis, D. A Survey on Blockchain-Based Self-Sovereign Patient Identity in Healthcare. IEEE Access 2020, 8, 90478–90494. [Google Scholar] [CrossRef]
- Jaiswal, K.; Anand, V. A Survey on IoT-Based Healthcare System: Potential Applications, Issues, and Challenges. In Advances in Biomedical Engineering and Technology; Springer: Berlin/Heidelberg, Germany, 2021; pp. 459–471. [Google Scholar]
- Soltanisehat, L.; Alizadeh, R.; Hao, H.; Choo, K.-K.R. Technical, Temporal, and Spatial Research Challenges and Opportunities in Blockchain-Based Healthcare: A Systematic Literature Review. IEEE Trans. Eng. Manag. 2020, 70, 353–368. [Google Scholar] [CrossRef]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. A Survey on the Adoption of Blockchain in IoT: Challenges and Solutions. Blockchain Res. Appl. 2021, 2, 100006. [Google Scholar] [CrossRef]
- Chukwu, E.; Garg, L. A Systematic Review of Blockchain in Healthcare: Frameworks, Prototypes, and Implementations. Ieee Access 2020, 8, 21196–21214. [Google Scholar] [CrossRef]
- Hasselgren, A.; Kralevska, K.; Gligoroski, D.; Pedersen, S.A.; Faxvaag, A. Blockchain in Healthcare and Health Sciences—A Scoping Review. Int. J. Med. Inform. 2020, 134, 104040. [Google Scholar] [CrossRef]
- Shi, S.; He, D.; Li, L.; Kumar, N.; Khan, M.K.; Choo, K.-K.R. Applications of Blockchain in Ensuring the Security and Privacy of Electronic Health Record Systems: A Survey. Comput. Secur. 2020, 97, 101966. [Google Scholar] [CrossRef] [PubMed]
- Srivastava, G.; Parizi, R.M.; Dehghantanha, A. The Future of Blockchain Technology in Healthcare Internet of Things Security. Blockchain Cybersecur. Trust Priv. 2020, 79, 161–184. [Google Scholar]
- Marques, G.; Pitarma, R.; Garcia, N.M.; Pombo, N. Internet of Things Architectures, Technologies, Applications, Challenges, and Future Directions for Enhanced Living Environments and Healthcare Systems: A Review. Electronics 2019, 8, 1081. [Google Scholar] [CrossRef]
- Somasundaram, R.; Thirugnanam, M. Review of Security Challenges in Healthcare Internet of Things. Wirel. Netw. 2021, 27, 5503–5509. [Google Scholar] [CrossRef]
- HaddadPajouh, H.; Dehghantanha, A.; Parizi, R.M.; Aledhari, M.; Karimipour, H. A Survey on Internet of Things Security: Requirements, Challenges, and Solutions. Internet Things 2021, 14, 100129. [Google Scholar] [CrossRef]
- Aceto, G.; Persico, V.; Pescapé, A. Industry 4.0 and Health: Internet of Things, Big Data, and Cloud Computing for Healthcare 4.0. J. Ind. Inf. Integr. 2020, 18, 100129. [Google Scholar] [CrossRef]
- Raikwar, M.; Gligoroski, D.; Kralevska, K. SoK of Used Cryptography in Blockchain. IEEE Access 2019, 7, 148550–148575. [Google Scholar] [CrossRef]
- Reegu, F.; Daud, S.M.; Alam, S. Interoperability Challenges in Healthcare Blockchain System-A Systematic Review. Ann. Rom. Soc. Cell Biol. 2021, 25, 15487–15499. [Google Scholar]
- Alam, S. A Blockchain-Based Framework for Secure Educational Credentials. Turk. J. Comput. Math. Educ. 2021, 12, 5157–5167. [Google Scholar]
- Zaman, U.; Imran; Mehmood, F.; Iqbal, N.; Kim, J.; Ibrahim, M. Towards Secure and Intelligent Internet of Health Things: A Survey of Enabling Technologies and Applications. Electronics 2022, 11, 1893. [Google Scholar] [CrossRef]
- Dimitrov, D. V Blockchain Applications for Healthcare Data Management. Healthc. Inform. Res. 2019, 25, 51–56. [Google Scholar] [CrossRef] [PubMed]
- Ray, P.P.; Dash, D.; Salah, K.; Kumar, N. Blockchain for IoT-Based Healthcare: Background, Consensus, Platforms, and Use Cases. IEEE Syst. J. 2020, 15, 85–94. [Google Scholar] [CrossRef]
- Shuaib, M.; Daud, S.M.; Alam, S.; Khan, W.Z. Blockchain-Based Framework for Secure and Reliable Land Registry System. TELKOMNIKA (Telecommun. Comput. Electron. Control) 2020, 18, 2560–2571. [Google Scholar] [CrossRef]
- Shuaib, M.; Alam, S.; Ahmed, R.; Qamar, S.; Nasir, M.S.; Alam, M.S. Current Status, Requirements, and Challenges of Blockchain Application in Land Registry. Int. J. Inf. Retr. Res. 2022, 12, 20. [Google Scholar] [CrossRef]
- Shuaib, M.; Hassan, N.H.; Usman, S.; Alam, S.; Bhatia, S.; Agarwal, P.; Idrees, S.M. Land Registry Framework Based on Self-Sovereign Identity (SSI) for Environmental Sustainability. Sustainability 2022, 14, 5400. [Google Scholar] [CrossRef]
- Odeh, A.; Keshta, I.; Al-Haija, Q.A. Analysis of Blockchain in the Healthcare Sector: Application and Issues. Symmetry 2022, 14, 1760. [Google Scholar] [CrossRef]
- Aslam, T.; Maqbool, A.; Akhtar, M.; Mirza, A.; Khan, M.A.; Khan, W.Z.; Alam, S. Blockchain Based Enhanced ERP Transaction Integrity Architecture and PoET Consensus. Comput. Mater. Contin. 2022, 70, 1089–1109. [Google Scholar] [CrossRef]
- Feng, Q.; He, D.; Zeadally, S.; Khan, M.K.; Kumar, N. A Survey on Privacy Protection in Blockchain System. J. Netw. Comput. Appl. 2019, 126, 45–58. [Google Scholar] [CrossRef]
- Uddin, M.A.; Stranieri, A.; Gondal, I.; Balasubramanian, V. Blockchain Leveraged Decentralized IoT EHealth Framework. Internet Things 2020, 9, 100159. [Google Scholar] [CrossRef]
- Bhalaji, N.; Abilashkumar, P.C.; Aboorva, S. A Blockchain Based Approach for Privacy Preservation in Healthcare Iot. In Proceedings of the ICICCT 2019–System Reliability, Quality Control, Safety, Maintenance and Management: Applications to Electrical, Electronics and Computer Science and Engineering; Springer: Berlin/Heidelberg, Germany, 2020; pp. 465–473. [Google Scholar]
- Khatoon, A. A Blockchain-Based Smart Contract System for Healthcare Management. Electronics 2020, 9, 94. [Google Scholar] [CrossRef]
- Gupta, S.; Malhotra, V.; Singh, S.N. Securing IoT-Driven Remote Healthcare Data through Blockchain. In Proceedings of the Advances in Data and Information Sciences: Proceedings of ICDIS 2019; Springer: Berlin/Heidelberg, Germany, 2020; pp. 47–56. [Google Scholar]
- Ellouze, F.; Fersi, G.; Jmaiel, M. Blockchain for Internet of Medical Things: A Technical Review. In Proceedings of the The Impact of Digital Technologies on Public Health in Developed and Developing Countries: 18th International Conference, ICOST 2020, Hammamet, Tunisia, 24–26 June 2020; pp. 259–267. [Google Scholar]
- Attia, O.; Khoufi, I.; Laouiti, A.; Adjih, C. An IoT-Blockchain Architecture Based on Hyperledger Framework for Health Care Monitoring Application. In Proceedings of the NTMS 2019-10th IFIP International Conference on New Technologies, Mobility and Security, Canary Islands, Spain, 24–26 June 2019; IEEE Computer Society: Washington, DC, USA, 2019; pp. 1–5. [Google Scholar]
- Shen, B.; Guo, J.; Yang, Y. MedChain: Efficient Healthcare Data Sharing via Blockchain. Appl. Sci. 2019, 9, 1207. [Google Scholar] [CrossRef]
- Dwivedi, A.D.; Srivastava, G.; Dhar, S.; Singh, R. A Decentralized Privacy-Preserving Healthcare Blockchain for IoT. Sensors 2019, 19, 326. [Google Scholar] [CrossRef] [PubMed]
- Nguyen, D.C.; Nguyen, K.D.; Pathirana, P.N. A Mobile Cloud Based Iomt Framework for Automated Health Assessment and Management. In Proceedings of the 2019 41st Annual International Conference of the IEEE Engineering in Medicine and Biology Society (EMBC), Berlin, Germany, 23–27 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 6517–6520. [Google Scholar]
- Salimitari, M.; Chatterjee, M.; Fallah, Y.P. A Survey on Consensus Methods in Blockchain for Resource-Constrained IoT Networks. Internet Things 2020, 11, 100212. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://assets.pubpub.org/d8wct41f/31611263538139.pdf (accessed on 5 January 2023).
- Indhuja, E.; Venkatesulu, M. A Survey of Blockchain Technology Applications and Consensus Algorithm. In Sustainable Communication Networks and Application. Lecture Notes on Data Engineering and Communications Technologies; Karuppusamy, P., Perikos, I., Shi, F., Nguyen, T.N., Eds.; Springer: Singapore, 2021; Volume 55, pp. 173–187. [Google Scholar] [CrossRef]
- Bachani, V.; Bhattacharjya, A. Preferential Delegated Proof of Stake (PDPoS)—Modified DPoS with Two Layers towards Scalability and Higher TPS. Symmetry 2022, 15, 4. [Google Scholar] [CrossRef]
- Aggarwal, S.; Kumar, N. Cryptographic Consensus Mechanisms. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2021; Volume 121, pp. 211–226. ISBN 0065-2458. [Google Scholar]
- Kotla, R.; Alvisi, L.; Dahlin, M.; Clement, A.; Wong, E. Zyzzyva: Speculative Byzantine Fault Tolerance. ACM Trans. Comput. Syst. 2009, 27, 45–58. [Google Scholar] [CrossRef]
- Barinov, I.; Baranov, V.; Khahulin, P. POA Network Whitepaper. 2018. Available online: https://github.com/poanetwork/wiki/wiki/POANetwork-Whitepaper (accessed on 5 January 2023).
- Bodkhe, U.; Mehta, D.; Tanwar, S.; Bhattacharya, P.; Singh, P.K.; Hong, W.C. A Survey on Decentralized Consensus Mechanisms for Cyber Physical Systems. IEEE Access 2020, 8, 54371–54401. [Google Scholar] [CrossRef]
- Dziembowski, S.; Faust, S.; Kolmogorov, V.; Pietrzak, K. Proofs of Space. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin/Heidelberg, Germany, 2015; Volume 9216, pp. 585–605. ISBN 9783662479995. [Google Scholar]
- Larimer, D. Transactions as Proof-of-Stake. 2013, pp. 1–8. Available online: https://cryptochainuni.com/wp-content/uploads/Invictus-Innovations-Transactions-As-Proof-Of-Stake.pdf (accessed on 5 January 2023).
- Ghosh, M.; Richardson, M.; Ford, B.; Jansen, R. A TorPath to TorCoin: Proof-of-Bandwidth Altcoins for Compensating Relays; Naval Research Lab: Washington, DC, USA, 2014. [Google Scholar]
- Zou, J.; Ye, B.; Qu, L.; Wang, Y.; Orgun, M.A.; Li, L. A Proof-of-Trust Consensus Protocol for Enhancing Accountability in Crowdsourcing Services. IEEE Trans. Serv. Comput. 2019, 12, 429–445. [Google Scholar] [CrossRef]
- Milutinovic, M.; He, W.; Wu, H.; Kanwal, M. Proof of Luck. In Proceedings of the 1st Workshop on System Software for Trusted Execution, Trento, Italy, 12 December 2016; ACM: New York, NY, USA, 2016; pp. 1–6. [Google Scholar]
- Rahman, M.S.; Islam, M.A.; Uddin, M.A.; Stea, G. A Survey of Blockchain-Based IoT EHealthcare: Applications, Research Issues, and Challenges. Internet Things 2022, 19, 100551. [Google Scholar] [CrossRef]
| Ref | Contribution | Year | BC | HC | IoT |
|---|---|---|---|---|---|
| [5] | Reviews the various IoT-based healthcare systems and IoT application areas across multiple healthcare aspects, especially EHR. | 2020 | N | Y | Y |
| [6] | The research highlights the various applications of IoT in healthcare and shows the security and privacy concerns. Further reviews the different cryptographic mechanisms to provide security to the IoT systems. | 2019 | N | Y | Y |
| [7] | A review of various HIoT applications, advantages, and recent trends in the domain. It also highlighted various challenges that include privacy and security concerns and suggested the possible solutions. | 2021 | N | Y | Y |
| [8] | Reviews the various security standards for healthcare data like Health Insurance Portability and Accountability Act (HIPAA) and its implications. | 2021 | N | Y | Y |
| [9] | Reviews various architectures that include cloud- and fog-based IoT healthcare systems. This study highlights significant challenges like latency, fault tolerance, energy efficiency, security, and interoperability and the role of fog- and cloud-based IoT healthcare architectures. | 2020 | N | Y | Y |
| [18] | Reviews the BC applications and BC technologies for healthcare. | 2019 | Y | Y | N |
| [20] | Review of applying BC technology in medical healthcare for protecting patient healthcare data, | 2019 | Y | Y | N |
| [21] | A comprehensive study of defining and assessing BC’s use in healthcare and an analysis of its problems and advantages. | 2019 | Y | Y | N |
| [22] | A systematic survey of applying BC in healthcare applications that further analyzes and evaluates the adoption. | 2019 | Y | Y | N |
| [23] | Reviews many use cases for applying BC in healthcare. | 2019 | Y | Y | N |
| [24] | The authors explored BC healthcare applications. However, neither the issues nor the solutions were highlighted. | 2019 | Y | P | Y |
| [25] | The article concentrated on BC applications for the IoT. | 2019 | Y | N | Y |
| [26] | They discussed BC in cybersecurity but not specifically its applications in healthcare. | 2019 | Y | N | Y |
| [27] | Discussed the usage of BC-based patient identification in healthcare. | 2020 | Y | Y | N |
| [28] | The authors examined IoT-based healthcare systems, including possible uses, difficulties, and limitations. However, numerous recent studies have presented viable methods for using BC in healthcare, which is lacking from this research. | 2020 | Y | P | Y |
| [29] | A thorough examination of BC-based healthcare-related work conducted between 2016 and January 2020 was included in the research. As a result, a new review article highlighting current challenges and solutions is required. | 2020 | Y | Y | Y |
| [17] | The study focuses mainly on the potential and features of BC in healthcare data management. It did not stress how BC works or how it addresses the shortcomings of the current healthcare IT mechanisms. | 2021 | Y | Y | N |
| [30] | The study focuses on BC’s applicability and problems in IoT. However, the writers did not address all of the major healthcare challenges. | 2021 | Y | P | Y |
| [13] | This study proposes a BC-based framework for Authentication, Authorization, and Audit in healthcare applications. It also reviews the issues with the traditional systems not implementing BC and the advantages of BC adoption in healthcare. It does not discuss the EHR aspects. | 2022 | Y | Y | Y |
| Our paper | This paper discusses the use of BC and the IoT in EHR systems and proposes a new framework | 2022 | Y | Y | Y |
| Feature | Description |
|---|---|
| Decentralization | BC allows for decentralization, which makes storing crucial data like documents, contracts, etc., easier, which means the possessor can access it from everywhere through the net. Moreover, full account control is in their hands, and they can share their data/assets with any entity they need to. |
| Transparency | The details of assets and transactions are made public and can be viewed by all parties, allowing for maximum transparency. |
| Immutability | No entity member can change the data once fed into the BC ledger. In case of an error, a new transaction must be made for rectification. However, both transactions, the erroneous and the rectified, will be shown in the ledger. |
| Ref. | Framework | BC Type | Consensus Mechanism | Type of Storage | Smart Contract | Domain |
|---|---|---|---|---|---|---|
| [51] | Not Defined | Consortium | Verified by group head, and then blocks are added | Off-chain (On cloud) | Data management and analysis | IoMT data management |
| [52] | Not Defined | Private | Not Defined | On-chain (hospitals) | Not Defined | Data Security |
| [53] | Ethereum | Private | Not Defined | Off-chain (exterior server) | Smart health records illustration | IoMT data management |
| [54] | Ethereum | public | Not Defined | Off-chain (IPFS) | Manage patients and doctor’s communication | IoMT data management |
| [55] | Ethereum | Private | Proof of medical stake | Off-chain (IPFS) | Manage access control | Access control in IoMT |
| [56] | Hyperledger Fabric | Private | Not Defined | On-chain | Verification and validation of transactions | Remote health monitoring |
| [57] | Not Defined | Consortium | BFT-SMaRt | On-chain | Not Defined | IoMT data management |
| [58] | Not Defined | Private | Verified by Cluster head, and then blocks are added | Off-chain (cloud) | IoMT data analysis and patient health monitoring | Patient monitoring remotely |
| [59] | Ethereum | Private | Not Defined | Off-chain (on cloud) | Access control | Monitor a neurological disorder of patients |
| Algorithms | CHARACTERISTICS | ||||||
|---|---|---|---|---|---|---|---|
| IoT Compliant | Basic Concept | Popularity | E-Health Support | Adaptability | Accessibility | Energy | |
| PoW [61] | ○ | CPU | ● | ◐ | ● | Open | ● |
| LPoS [62] | ◐ | PoS | ◐ | ● | ◐ | Open | ◐ |
| DPoS [63] | ◐ | PoS | ◐ | ● | ◐ | Open | ◐ |
| PoI [64] | ○ | PoS | ◐ | ● | ◐ | Open | ◐ |
| PBFT [65] | ○ | 67% Node | ○ | ● | ○ | Prop | ○ |
| PoA [66] | ○ | PoW-PoS | ○ | ○ | ◐ | Prop | ○ |
| DBFT [67] | ○ | PBFT | ○ | ○ | ○ | Prop | ○ |
| PoC [68] | ○ | PoW | ○ | ○ | ○ | Open | ○ |
| PoS [69] | ◐ | Stake | ● | ● | ● | Open | ◐ |
| PoB [70] | ○ | -- | ○ | ○ | ○ | Prop | ○ |
| PoT [71] | ● | PoW | ◐ | ● | ◐ | Prop | ○ |
| PoL [72] | ◐ | PoW | ◐ | ● | ◐ | Prop | ○ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alam, S.; Bhatia, S.; Shuaib, M.; Khubrani, M.M.; Alfayez, F.; Malibari, A.A.; Ahmad, S. An Overview of Blockchain and IoT Integration for Secure and Reliable Health Records Monitoring. Sustainability 2023, 15, 5660. https://doi.org/10.3390/su15075660
Alam S, Bhatia S, Shuaib M, Khubrani MM, Alfayez F, Malibari AA, Ahmad S. An Overview of Blockchain and IoT Integration for Secure and Reliable Health Records Monitoring. Sustainability. 2023; 15(7):5660. https://doi.org/10.3390/su15075660
Chicago/Turabian StyleAlam, Shadab, Surbhi Bhatia, Mohammed Shuaib, Mousa Mohammed Khubrani, Fayez Alfayez, Areej A. Malibari, and Sadaf Ahmad. 2023. "An Overview of Blockchain and IoT Integration for Secure and Reliable Health Records Monitoring" Sustainability 15, no. 7: 5660. https://doi.org/10.3390/su15075660
APA StyleAlam, S., Bhatia, S., Shuaib, M., Khubrani, M. M., Alfayez, F., Malibari, A. A., & Ahmad, S. (2023). An Overview of Blockchain and IoT Integration for Secure and Reliable Health Records Monitoring. Sustainability, 15(7), 5660. https://doi.org/10.3390/su15075660








