Abstract
People can access and obtain services from smart home devices conveniently through fog-enabled smart home environments. The security and privacy-preserving authentication protocol play an important role. However, many proposed protocols have one or more security flaws. In particular, almost all the existing protocols for the smart home cannot resist gateway compromised attacks. The adversary can not only know the user’s identity but also launch impersonation attacks. Designing a provable secure authentication protocol that avoids all known attacks on smart homes is challenging. Recently Guo et al. proposed an authentication scheme based on symmetric polynomials in the fog-enabled smart home environment. However, we found that their scheme suffers from gateway compromised attack, desynchronization attack, mobile device loss/stolen and attack, and has no untraceability and perfect forward secrecy. Therefore, we adopt a Physical Unclonable Function (PUF) to resist gateway compromised attack, adopt Elliptic Curve Diffie–Hellman (ECDH) key exchange protocol to achieve perfect forward secrecy, and propose a secure and privacy-preserving authentication protocol, which is provably secure under the random oracle model. According to the comparisons with some related protocols, the proposed protocol has better security and transmission efficiency with the same computation cost level.
1. Introduction
In recent years, with the iteration of communication technology and smart devices, the Internet of Things (IoT) has been gradually applied in many aspects, such as logistics, transportation, security, pollutants monitoring, smart home, etc. The smart home is one of the applications of IoT that connect the user and the devices in residence by using a common communication system and control technology [1,2], such as air conditioners, televisions, monitors, water heaters, etc. The new way of controlling devices provided by the smart home brings people safety, energy conservation, comfort, convenience, and healthcare [3].
Due to the smart devices having limited computation and storage, the smart home must have nodes that provide reliable computing services, storage services, and network services to build a communication system [4]. In general, the cloud is more suitable for resource nodes. However, real-time response is a requirement for some emergency applications in the smart home, so nodes also have to meet the requirements of high bandwidth and low latency. Cloud latency is often determined by physical distance, so real-time requirements cannot be met. To meet real-time requirements, distributing computation and storage to edge devices is an idea called fog computing [5].
Fog computing has the characteristics of low latency and high response, and it has been applied in healthcare and smart home [6,7,8,9]. Because the computing and storage resources of smart devices in the smart home are limited, they cannot afford much computation. A scheme is proposed in [9] which connects the sensor devices of the terminal based on the IoT controller as a gateway in the smart home. In the fog computing network, the fog layer composed of the smart gateways undertakes the message forwarding and the distributed computation and storage [10,11].
The fog-computing smart home enhances the user’s control over computation and storage nodes and provides more privacy. However, it is still vulnerable to malicious attacks because messages are transmitted on open channels. The data, after being maliciously attacked, will transmit false information, induce users to make wrong decisions, and directly affect residential security and privacy. There are great concerns about the security and privacy of remote access in emergencies and dangers. The security and privacy-preserving authentication protocol play an important role in the smart home.
Until now, many authentication protocols have been proposed. These authentication protocols have some shortcomings in terms of security, anonymity, and perfect forward secrecy [12]. Jeong et al. [13] proposed a user authentication (UA) protocol based on the one-time password (OTP) protocol. The scheme provides authentication of users and gateway, mainly used in remote access to the home network. In the smart home, secure communication between devices and gateways is essential. Xue et al. [14] proposed a temporal-credential-based scheme for Wireless Sensor Networks (WSN) using hash and XOR. Saqib et al. [15] indicated that Xue et al.’s scheme is not immune to smart card theft and server fraud attack. Shuai et al. [16] designed an anonymous authentication scheme based on Elliptic Curve Cryptography (ECC) for the smart home environment. The protocol avoided storing the validation table to reduce the harm caused by theft and resisted replay attacks and clock synchronization attacks. Unfortunately, Kaur et al. [17] pointed out that Shuai et al.’s scheme is vulnerable to offline password guessing attacks, insider attacks, replay attacks, gateway bypass attacks, and insecure session key agreement problems and proposed an improvement scheme for the smart home. However, the scheme is vulnerable to gateway compromised and replay attacks. Santoso et al. [18] proposed a scheme based on ECC for the smart home system. The scheme cannot provide anonymity and untraceability and cannot resist privileged-insider and smart card stolen attacks. Guo et al. [19] presented a new authentication mode based on a symmetric bivariate polynomial [20], which includes the edge negotiation phase and the authentication phase, and reduces communication consumption. The scheme has extremely low computational consumption, but we show it is vulnerable to gateway compromised attacks, desynchronization attacks, mobile device loss/stolen attacks, etc.
Some authentication schemes consider the gateway is trusted and store sensitive information. Wazid et al. [21] proposed a lightweight authentication protocol for the smart home environment based on XOR, symmetric cipher, and hash functions. The authentication table is stored in the gateway. Haseeb-ur-Rehman et al. [22] proposed a lightweight protocol for the smart home and declared that the gateway is trusted. Lee et al. [23] proposed a three-factor authentication protocol in an IoT environment; the gateway is also fully trusted and stores the long-term key. Gateway compromised attacks may lead to the disclosure of user identity, long-term secret values, and other information and lead to suffering impersonation attacks, privilege attacks, etc.
On the other hand, privacy-preserving is a necessary security requirement in the smart home. Yeh et al. [24] proposed an authentication scheme established on Elliptic Curve Cryptography (ECC) for WSN. The message in their scheme contains the real identity of the user, so it does not provide anonymity. In addition, the ECC multiplication is used many times, which makes the protocol have high computational complexity [15]. Yang et al. [25] proposed an ID-based authentication protocol for mobile devices, and the scheme has less computation time because it does not require users’ public keys. However, Islam et al. [26] stated that Yang et al.’s scheme has no anonymity.
Perfect forward secrecy (PFS) is an extremely harsh security condition; it is a security feature that can still maintain the confidentiality of previously transmitted messages even if long-term keys are leaked [12]. Although it will increase the computation costs, a better method is to use the Diffie–Hellman key exchange algorithm to design the protocol to guarantee PFS. However, many proposed protocols can not achieve PFS [16,17,19,21,25].
Physical capture attacks often have security implications, and PUF [27] is a way to provide physical device security. A PUF is a one-way function derived from the randomness of physical features caused by the manufacturing variation process. PUFs are unreproducible, unpredictable, and tamper-resistant and are widely used in security. Yi et al. [28] proposed an authentication protocol in WSN. The protocol introduced a PUF chip to provide the physical integrity of sensors. Yu et al. [29] proposed a physically secure privacy-preserving scheme in telecare medical information systems, and PUF is used to store long-term keys. The introduction of PUF to protect devices against physical capture attacks is effective.
Motivation and Contributions
According to the analysis of the existing protocols for smart homes, we found that most of them have one or more security flaws, which cannot achieve perfect forward secrecy, privacy protection, etc. In particular, almost all the existing protocols for a smart home cannot resist gateway compromised attacks. The adversary can not only know the user’s identity but also launch impersonation attacks. Designing a provable secure authentication protocol that avoids gateway compromised attacks for smart homes is challenging. The contributions of this paper are as follows:
- We pointed out that Guo et al.’s protocol in a fog-enabled smart home is vulnerable to smart gateway compromised attacks, desynchronization attacks, and mobile device lost/stolen attacks, and traceability has no perfect forward secrecy.
- We propose the first secure and privacy-preserving authentication protocol in fog-enabled smart homes to avoid a gateway compromised attack. We adopt PUF to resist gateway compromised attack, adopt ECDH key exchange protocol to achieve perfect forward secrecy, and redesign the process to provide privacy-preserving and makes it resistant to desynchronization attack and mobile device lost/stolen attack.
- We prove the security of the proposed protocol formally under the random oracle model. According to the comparisons with some related protocols, the proposed protocol has better security and transmission efficiency with the same computation cost level.
2. System and Attack Models
In this section, we introduce the system and attack models in a fog-enabled smart home environment.
2.1. System Model
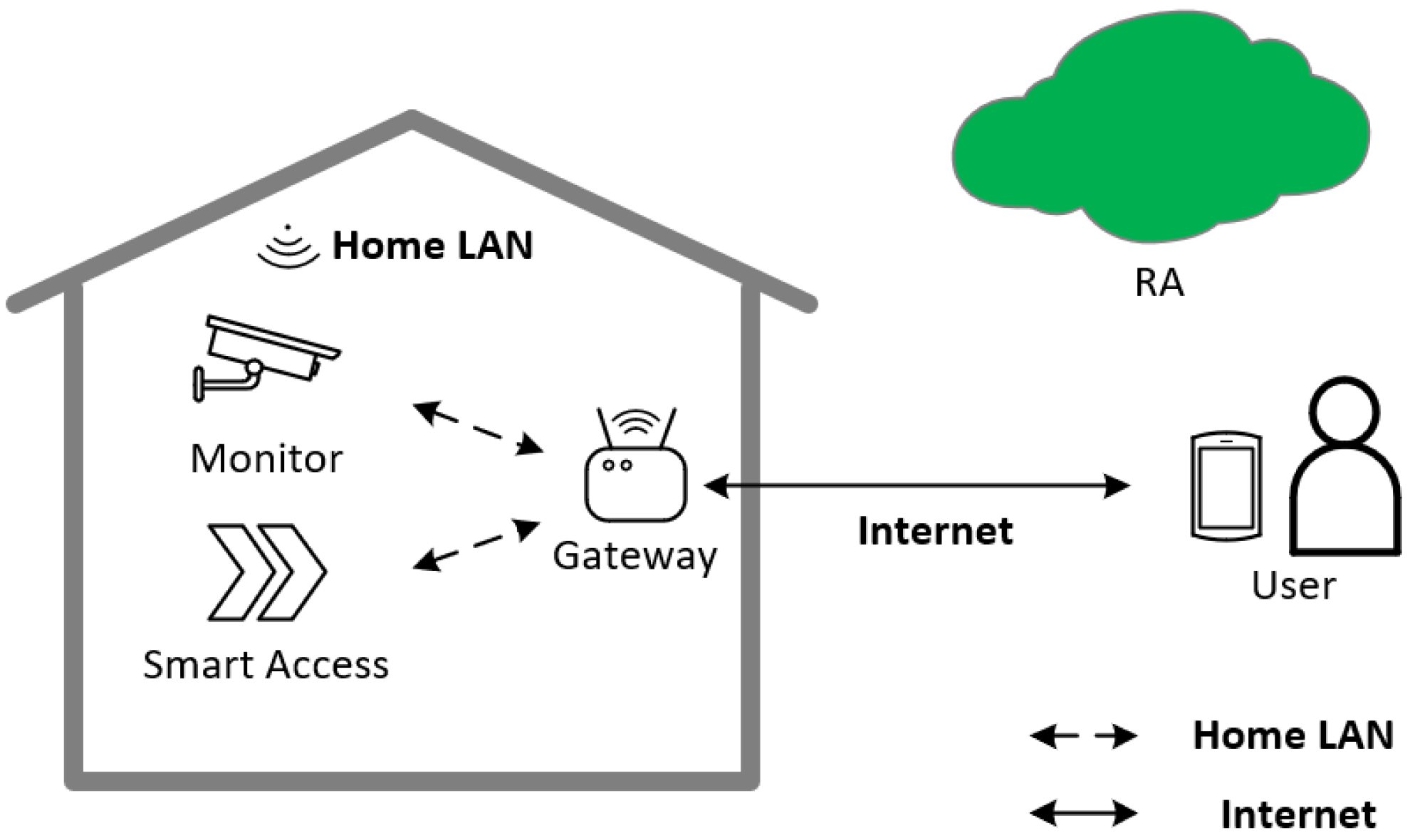
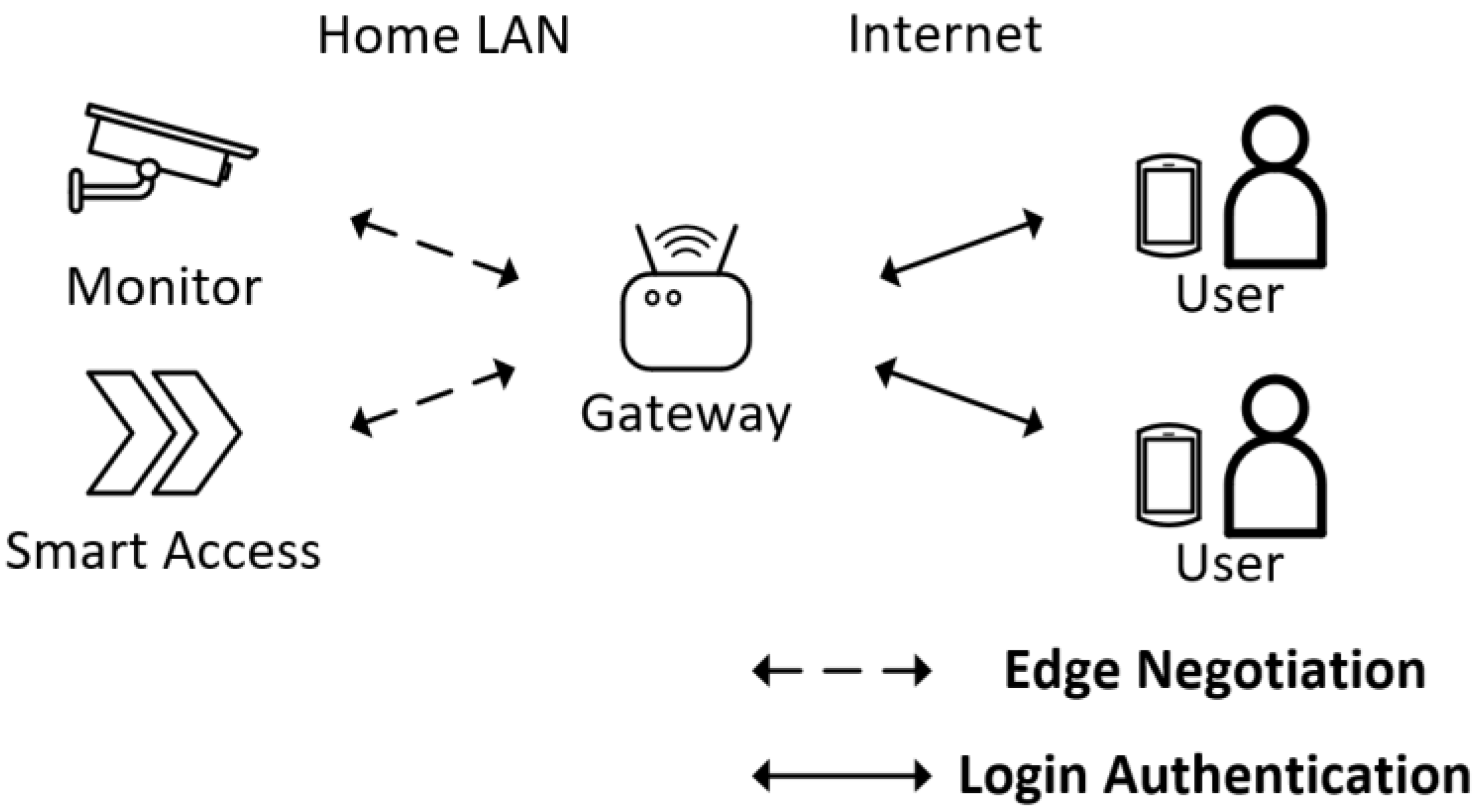
Figure 1 shows the system model of Guo et al.’s scheme. The communication system consists of smart devices, users & mobile devices, a smart gateway, and the cloud. The smart device is connected to the smart gateway via the home network, such as Wi-Fi and wired network. The smart gateway is connected to the cloud via the internet, and users can access the smart gateway remotely. The smart gateway provides computing and storage resources in the communication system to ensure real-time data transmission. The smart gateway in this architecture is responsible for collecting from smart devices and processing user requests. The entity negotiation model is shown in Figure 2.
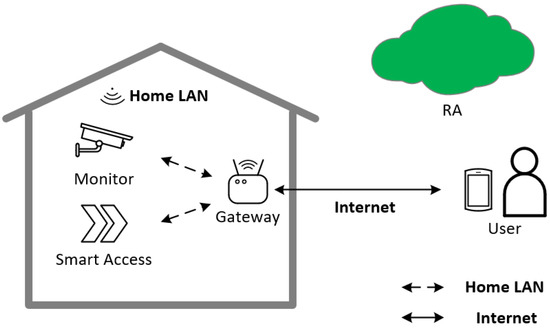
Figure 1.
The system model of a smart home.
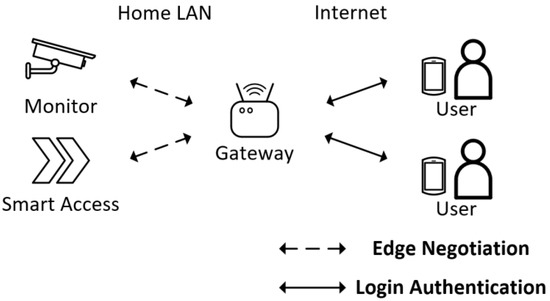
Figure 2.
The entity negotiation mode.
In the edge negotiation stage, the smart gateway and the smart device establish a persistent connection and re-establish the session after the session expires. After the session is established, the gateway can collect real-time data securely from the smart device and fast-forward commands to the smart device from the user.
In addition, the smart gateway will also establish a temporary session with the user. The user negotiates a one-time session key with the gateway after identity verification, accepts the smart device data sent by the gateway, and quickly sends instructions to the smart device via the user’s portable mobile device. The above two stages achieve the user’s security management of smart devices.
2.2. Attack Model
We provide an attack model consistent with the original protocol; according to the Dolev-Yao [30] threat model and CK-adversary [31] model in wireless networks, the attacker can compromise information such as session key and session state.
- The attacker can eavesdrop, delay, modify, and delete the messages transmitted on public communication channels;
- The attacker can compromise temporary information such as session key and session state;
- The smart gateway is not considered fully trusted. And it can be compromised by the attacker;
- The smart devices are considered untrusted because the device can be physically lost or stolen, and all data can be extracted;
- The user’s mobile device considers an untrusted entity; the mobile device can be captured or compromised by the attacker; the user’s mobile devices can be obtained by the attacker;
- Registration authority (RA) is completely credible and cannot be compromised;
- The private channels are secure and cannot be controlled or eavesdropped on by attackers.
3. Review of the Guo et al.’s Scheme
In this section, we describe Guo et al.’s scheme. The scheme includes a registration phase, edge negotiation phase, and login authentication phase. The secret sharing of Guo et al.’s scheme is based on symmetric bivariate polynomials. For symmetric bivariate polynomial , there is . Table 1 shows the notations used in this paper.

Table 1.
Notations.
3.1. Registration Phase
generates a long-term private key and chooses two symmetric bivariate polynomials and over the finite field .
The registration phase includes gateway registration, smart home device registration, and user registration.
- (1)
- Gateway registration
chooses a unique identity for the gateway and computes a pseudo-identity , a token and two polynomial functions . Finally, stores in its memory, where is the latest temporary identity of , and is the last temporary identity of .
- (2)
- Smart home device registration
chooses a unique identity , a temporary identity for a smart home device, and computes a pseudo-identity , the function . Finally, stores in the memory of .
- (3)
- User registration
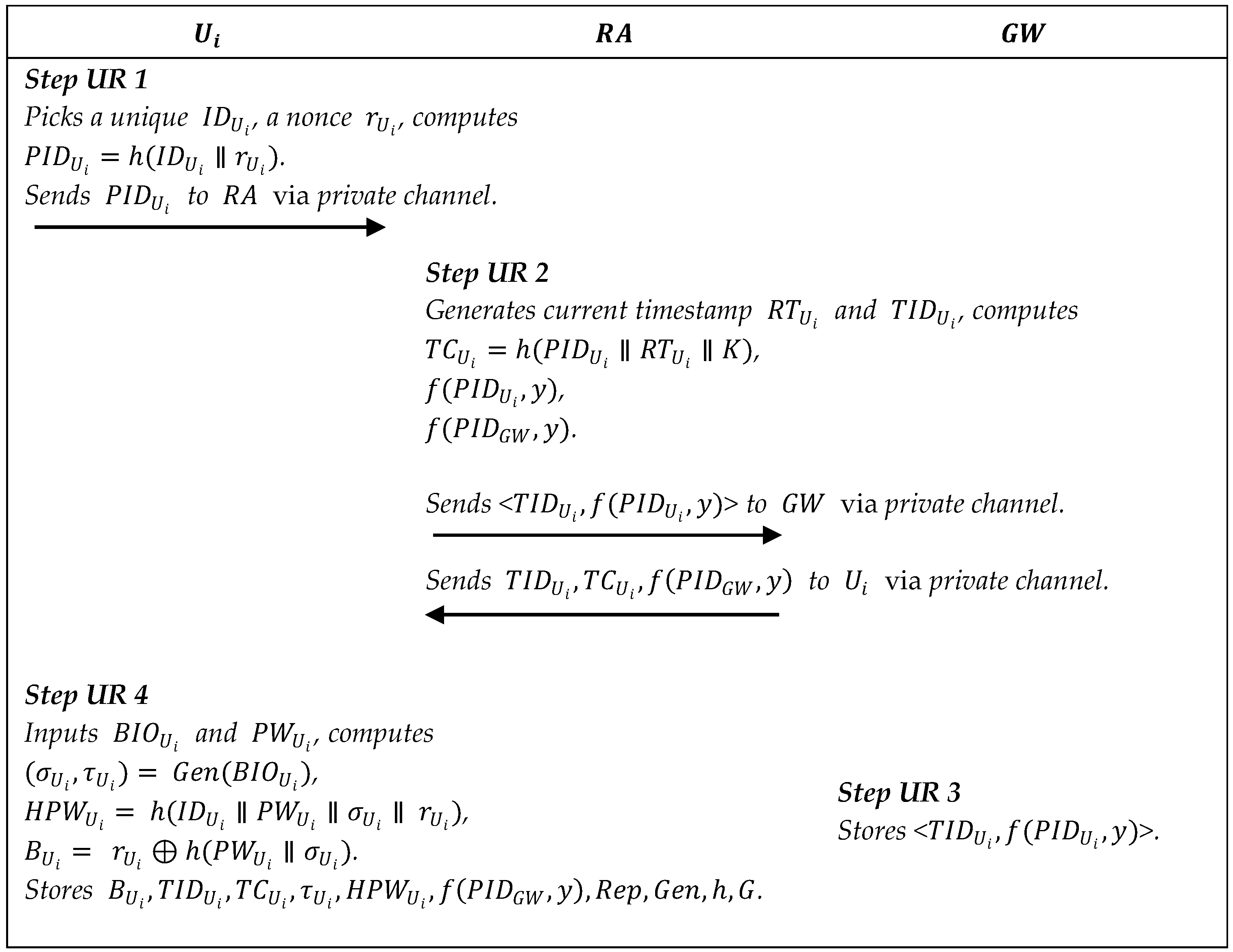
Step UR1: inputs a unique identity and biological information into mobile device . generates a nonce , and computes a pseudo-identity , [32], , . The message is sent to via a private channel.
Step UR2: On receiving the message from , generates a nonce and a timestamp , then calculates a token , , , . Then picks a temporary identity , calculates a function , and sends a message to via a secure channel.
Step UR3: Once the message is received, computes , , , , , , , . Finally, stores in the memory of .
In this phase, the user can update password and biometrics information.
3.2. Edge Negotiation Phase
This phase establishes a session key between the gateway and the smart home device. The steps are as follows.
Step EN1: The smart device sends message to the smart gateway via the public channel, where is current timestamp and is a random number.
Step EN2: On receiving the message, generates the current timestamp , checks the freshness of the timestamp , chooses a random number , and finds by . Then computes , , , , , . Finally, updates and sends to .
Step EN3: On receiving the message from , checks the freshness of the timestamp and calculates , , , . Then checks . If yes, updates in its memory.
3.3. Login Authentication Phase
When wants to access a smart home device, the user does the following steps.
Step LA1: inputs , and into the mobile device .
Step LA2: computes , , , , , , . If , do the next step; otherwise, re-do the step LA1.
Step LA3: generates a random number and current timestamp and calculates , , , , , . Finally, sends message to publicly.
Step LA4: When receives the message from , . checks the freshness of the timestamp . Then computes , , . If , terminate. Otherwise, generates a random number and current timestamp , and computes , , , . Subsequently, chooses a new random number and computes . Finally, sends to .
Step LA5: checks the freshness of the timestamp after receiving the message, and calculates , , , . checks . If yes, the authentication is successful, updates .
4. Cryptanalysis of the Guo et al.’s Scheme
In this section, we show the weaknesses of Guo et al.’s scheme.
4.1. Smart Gateway Compromised Attack
In Guo et al.’s scheme, the smart gateway stores sensitive information and is not fully trusted. Suppose that an attacker compromises the smart gateway and steals information , each shared secret between and can be calculated from and .
- (1)
- The attacker impersonates the smart device.
The attacker extracts from the stolen information and sends to in Step EN1, where is a random number and is a current timestamp. In Step EN3, the attacker gets from , picks from the stolen information and can calculate , , , .
- (2)
- The attacker eavesdrops on the smart device.
The attacker eavesdrops in Step EN1 and in Step EN2, and picks from the stolen information, then calculates , , and in Step EN3. The attacker gets and successfully. The attacker can also eavesdrop on the next session by .
4.2. Desynchronization Attack
The attacker intercepts and modifies in Step EN1. In Step EN2, the smart gateway will receive the tampered and calculate , , , , by the tampered . In Step EN3, the smart device calculates , , by the real , so and won’t update in Step EN3.
4.3. Traceability
In the login authentication phase, , where and are constant, and doesn’t change. Therefore, the attacker can trace by eavesdropping on the constant value .
4.4. Mobile Device Lost/Stolen Attack
Assuming that ’s mobile device is lost or stolen, all the information stored in the mobile device will be obtained by the attacker. The attacker eavesdrops in Step EN2 and in Step LA3, and computes . The attacker can perform the following attacks.
- (1)
- The attacker impersonates the user.
The attacker picks , . and , generates a random number , a fake token , a current timestamp , and calculates , , , and . Finally, the attacker sends in Step LA3. In Step LA5, the attacker calculates , , .
- (2)
- The attacker eavesdrops on the user.
The attacker picks , and and intercepts in Step LA3, calculates , . Then the attacker eavesdrops in Step LA4 and calculates , , , in Step LA5. The next session key can be calculated in the same way.
4.5. No Perfect Forward Secrecy
In Guo et al.’s scheme, and are long-term for the session key agreement.
In the login and authentication phase, if leaks, the attacker can eavesdrop in Step LA3 and in Step LA4, then calculate , , , . In the same way, the attacker can calculate the previous session key.
In the edge negotiation phase, If leaks, the attacker can compute , , , where can be obtained in Step EN1 and can be obtained in Step EN2. The previous session key can also be calculated in the same way.
5. The Proposed Scheme
In this section, we propose a security-enhanced scheme. The scheme consists of a system initialization phase, entity registration phase, edge negotiation phase, and login authentication phase.
In the proposed scheme, the PUF can improve security. PUF is a one-way function derived from complex physical and environmental characteristics. When a challenge stimulates the device, the device calculates a response from the complex physical functions, and the response is unpredictable and repeatable. The attackers cannot predict the response to the challenge and build the same PUF based on the same design and blueprint [27].
5.1. System Initialization Phase
generates private key and two symmetric bivariate polynomials and with degree over the field , and selects the elliptic curve over finite field , is the base point.
5.2. Entity Registration Phase
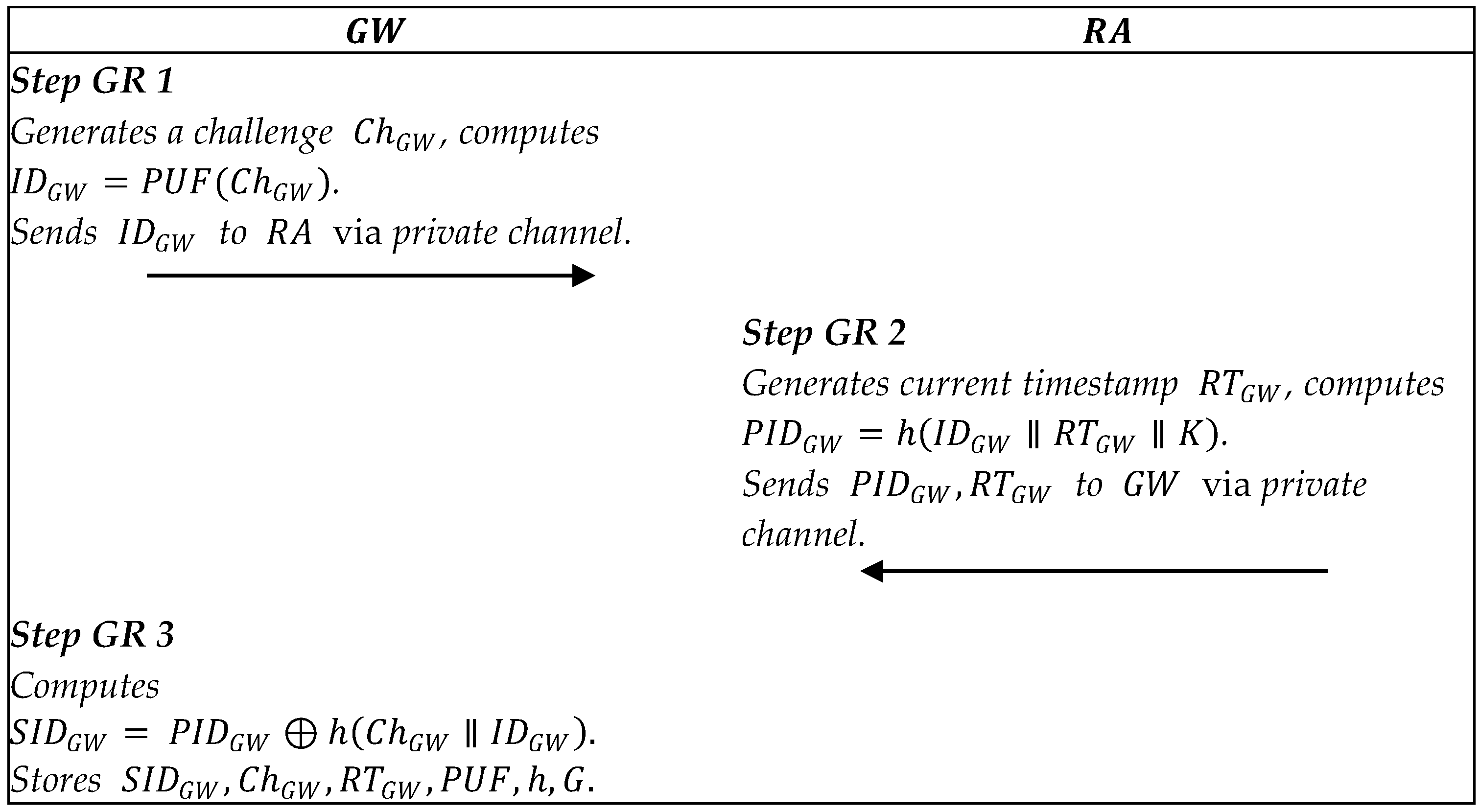
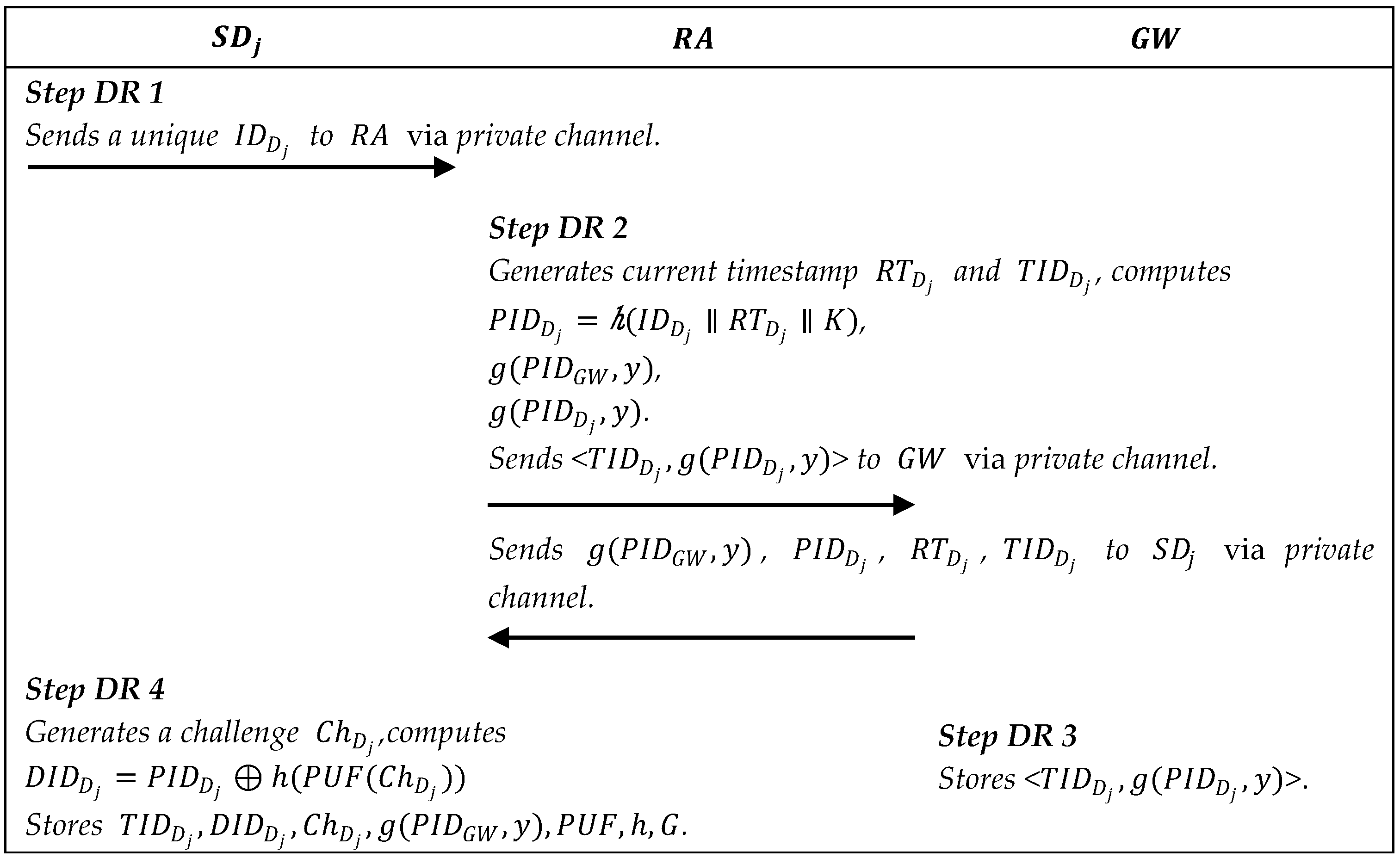
In this phase, we use the PUF to protect the private data of the smart gateway and the smart devices. Figure 3, Figure 4 and Figure 5 describe the registration processes.
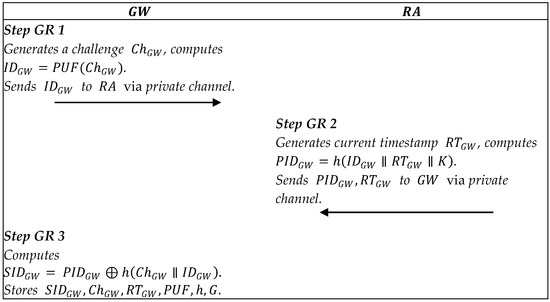
Figure 3.
Summary of smart gateway registration.
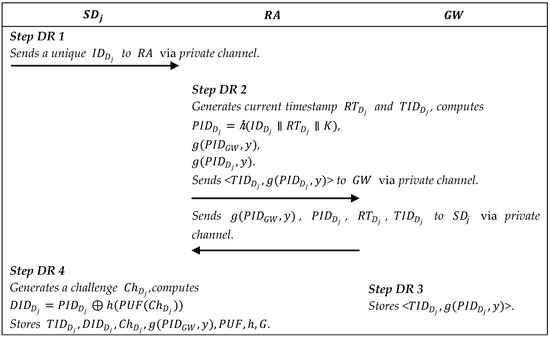
Figure 4.
Summary of smart device registration.
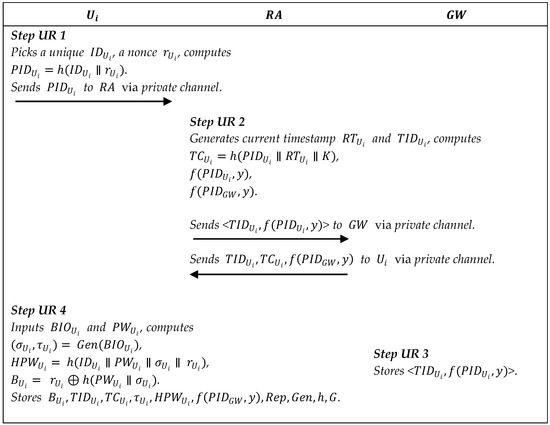
Figure 5.
Summary of user registration.
5.2.1. Smart Gateway Registration
Step GR1: The smart gateway picks a and generates a challenge , then computes . The smart gateway sends the message to the via the private channel.
Step GR2: After receiving the message , generates the current timestamp , and computes . returns a response via a private channel.
Step GR3: After receiving the response, the smart gateway calculates and stores in the memory.
5.2.2. Smart Device Registration
Step DR1: The smart device sends a unique identity to via the private channel.
Step DR2: After receiving the message, generates a random number , current registration timestamp , then calculates and two functions from the symmetric bivariate polynomial , and . Then sends the message <> to and the message to via the private channel.
Step DR3: stores the message <> in its memory.
Step DR4: The smart device chooses a and generates a challenge , and computes . Finally, stores in its memory.
5.2.3. User Registration
Step UR1: selects a unique identity , a random number , computes , and sends to via the private channel.
Step UR2: generates a random , a current registration timestamp , two functions and by the symmetric bivariate polynomial , and computes . Then sends <> to and to via the private channel.
Step UR3: stores <> in its memory.
Step UR4: inputs , , and computes , where is ’s biological information. Later computes , , where is the password. Finally, stores in the memory of a mobile device.
5.3. Edge Negotiation Phase
In the edge negotiation phase, the session key is negotiated between the smart gateway and the smart devices. Figure 6 describes the executive process.
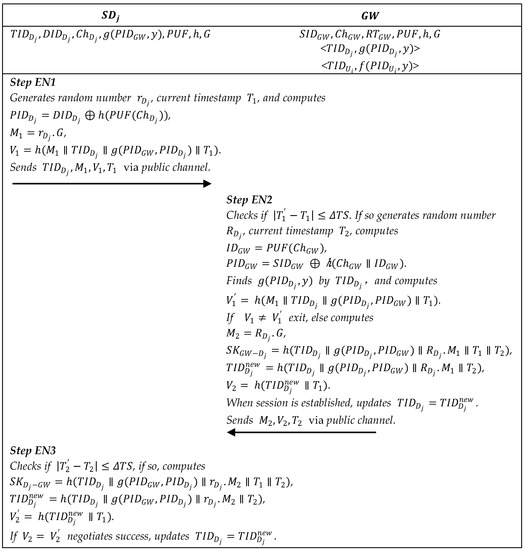
Figure 6.
Summary of edge negotiation phase.
Step EN1: The smart device generates a random number , current timestamp , and computes , the secret value , , , and sends to via the public channel, where is the base point.
Step EN2: On receiving the request, checks the freshness of the timestamp . After that, finds the function by , and calculates , , the secret value , . If , the request is integrity. Then generates a random number and timestamp , and calculates , , , . Then returns via the public channel. It is worth noting that the does not immediately update at the time, and updates after a secure session is established. Even if the session establishment fails, it will not cause the smart device to get out of sync.
Step EN3: On receiving the response, the smart device checks the freshness of timestamp . Then calculates , . If , the negotiation is successful, and calculates , updates and sends a secure message to notify the to update .
5.4. Login and Authentication Phase
When the user needs to access the smart home, Figure 7 describes the executive process.

Figure 7.
Summary of login and authentication phase.
Step LA1: The user inputs identity information and biometric information into the mobile device, the mobile device computes , , . If , login failed. Otherwise, the mobile device generates a random number and current timestamp , computes , , . Then the mobile device sends to the via the public channel.
Step LA2: After receiving the message, checks the freshness of the timestamp . Then extracts the information , , gets by and calculates the secret value . Similarly, the calculates . If , terminate. Otherwise, generates random number and current timestamp , calculates , , , , and updates the with after the session is established. Finally, sends the message to via the public channel.
Step LA3: On receiving the response, the user ’s mobile device checks the freshness of the timestamp . And the mobile device computes , , . If , the authentication succeeded, and the mobile device updates with and securely informs the smart gateway to update .
6. Formal Security Proof
6.1. Random Oracle Model
Definition 1 (Participants & partnering).
The participants are composed of User (), Smart Device (), and Gateway (). In the i-th instance, the participants are denoted as
, , and
, respectively. The state
represents that an oracle receives a correct message.
If two oracles are in and the session keys have been agreed upon, the oracles get their session identities and participant identities. The oracles can be considered partners if the following conditions are satisfied:
Their session keys are the same;
Their session identities are the same;
The participant’s identity is equal to each other’s identity.
Definition 2 (Queries).
The queries simulate the capabilities of attackers.
: All the messages transmitted openly can be intercepted by the adversary .
: forges and sends the message to , , or , if is correct, , , or responses .
: can get the current session key between , , and .
: This query is allowed to be executed at most once, which generates a random bit , if , the real session key is returned.
: Which simulates the side-channel attack on the user’s device and returns the stored information .
: Which simulates the attack of capturing a smart device and returns the stored information .
: Which simulates the attack of capturing the smart gateway and returns the stored information , <>, and <>.
Definition 3 (Freshness).
An instance can be regarded as fresh if it satisfies:
,, andare in.
The queryhas not been executed.
The querieshave been executed at most once.
Definition 4 (Semantic security).
is allowed to execute at most once and multiple other queries to determine the correctness of the return value of . That is guesses the random bit generated by . The possibility is , represents the protocol is secure, where is sufficiently small.
6.2. Formal Security Proof under the Random Oracle Model
Theorem 1.
The advantage of obtaining the session key in polynomial time by is .
Where,, andrepresents the times of executing Hash, Send, and Execute, respectively.,, andare the length of hash, transcripts, and biological key, respectively. The advantage of breaking PUF, ECDLP, and the symmetric bivariate polynomial byare,, and, respectively.
Proof.
The games are defined to simulate the attacks launched by . means guesses the random bit in the . The games are defined as:
: This game simulates the real attack first launched by . According to the definition, we get:
: This game simulates the eavesdropping attack. gets all the messages transmitted publicly. Then, guesses the random bit . However, because of the ECDLP, the attacker cannot judge the association between the captured messages and the session keys. Therefore, we get:
: This game simulates the collision attack on the transcripts and hash results according to the definition of the birthday paradox, the probability of hash collision is less than , and the collision probability of other transcripts is less than . Therefore, we have:
: This game simulates executes , , and to obtain the stored information in the user’s device, in the smart device, and , <>, and <> in the smart gateway. Where , , is the biometric key, , , , , and are used for verification and session key agreement. If wants to obtain the valuable parameters, must guess or break PUF. Suppose the probability of breaking PUF by is . Therefore, we have:
: can obtain , , , and publicly, the session key agreements are based on ECDLP and the symmetric bivariate polynomial. This game simulates that calculates the session keys according to the transcripts. We have:
The session keys are generated independently and randomly. Hence, the advantage of guessing is equal to guessing the session key. We have:
Combining the above formulas, we have:
That is:
□
7. Informal Security Analysis
7.1. Anonymity and Untraceability
In our proposed scheme, all messages are calculated from random numbers, and the temporary identities are changed in each session. Therefore, the proposed scheme is anonymous and untraceable.
7.2. Perfect Forward Secrecy
In our proposed scheme, the session key negotiation is based on long-term shared secrets and ECDLP. Even if the long-term key , and the current session key is leaked, the attacker cannot get the random number and cannot calculate the previous or later session key. Therefore, the protocol has perfect forward secrecy.
7.3. Impersonation Attack
If an attacker wants to impersonate , stealing the secret is a precondition. The attacker can’t get the because of the security features of PUF, and the secret will not be revealed even if the gateway is compromised, so the attacker can’t impersonate .
If an attacker wants to impersonate . Calculating , where is public. But calculating is difficult because of the biological key , so it is impossible to impersonate .
If an attacker wants to impersonate negotiate with or communicate with , the attacker needs to know the to calculate the secret or . However, the of the smart gateway also needs to be calculated by the PUF, so the attacker can’t impersonate .
7.4. Replay Attack
If an attacker captures previous data transmitted on the public channel and resends it, the data recipient will verify the freshness of timestamp. The integrity of the message is combined with the timestamps. The modified timestamp cannot pass the verification.
7.5. Mobile Device Loss/Stolen Attack
If an attacker gets the user’s mobile device, all the information is extracted in the ’s mobile device. Because the secret value is calculated from the ’s bioinformatic features , the attacker cannot calculate and secret value . Therefore, the scheme can resist the mobile device loss/stolen attack.
7.6. Smart Device Captured Attack
Suppose an attacker captures the smart device and extracts the information stored in it. Due to the security features of PUF, the attacker cannot calculate , and . So, the attacker cannot impersonate , and it is impossible to affect other smart devices.
7.7. Smart Gateway Compromised Attack
Suppose an attacker compromises the smart gateway; he can get the information stored in the memory. Because of the features of PUF, the attacker cannot calculate , , . Therefore, the scheme can resist the smart gateway compromised attack.
7.8. Man-in-the-Middle Attack
Since an attacker can neither impersonate , nor and , which is described in the Impersonation Attack. Therefore, the scheme can resist the man-in-the-middle attack.
7.9. Desynchronization Attack
The reason our protocol can resist the desynchronization attack is that is updated after passing the authentication and establishing the session key.
7.10. The Ephemeral Secret Leakage (ESL) Attack
Suppose an attacker gets an ephemeral secret during a negotiation, such as , , , . However, the session key calculation requires the long-term key or . Therefore, the scheme is resistant to the ephemeral secret leakage (ESL) attack.
8. Comparisons
In this section, we compared the security features and performance between our protocol and some related schemes [16,17,19,21]. The performance evaluation consists of communication and computation costs.
In terms of computational consumption, TI MSP430 microcontrollers are widely used in measurement and control equipment, so we take them to carry the TMP36 sensor to simulate the calculation consumption of the smart device. The mobile device chip uses ARM Cortex-A9 MPCore@890 Mhz CPU, and the smart gateway uses Intel Core i5-2500@3.3 GHz. To ensure the consistency of statistical methods, we adopt the conversion method of [19], , where is the time of the hash function, is the time of symmetric key encryption or decryption, is the time of symmetric polynomial, is the time of ECC point multiplication, is the time of message authentication code (MAC), is the time of hashed MAC and the time of is modular exponentiation; the notations are shown in Table 2. According to the smart device simulation result, , , . According to the mobile device simulation, , , . According to the smart gateway simulation, , , . The result is shown in Table 3.

Table 2.
Notations.

Table 3.
Algorithm execution time (ms).
In terms of communication consumption, the length of the output, such as random number, identity, timestamp, hash, MAC, symmetric encryption block, and ECC point are 128 bits, 128 bits, 32 bits, 256 bits, 256 bits, 128 bits, and 1024 bits, respectively.
Table 4 is the comparison of the security features, and the comparison of the computation and communication consumptions are shown in Table 5 and Table 6.

Table 4.
Security features.

Table 5.
Computation costs (ms).

Table 6.
Communication costs (bits).
In the scheme [16], the user inputs the identity and the password to achieve verification. When facing the offline password guessing attack, the password will no longer be secure. In addition, the gateway stores the long-term keys, the keys of users and devices will be leaked when the gateway is compromised, which threatens the security of communication data and session keys. The protocol cannot resist the gateway compromised attack and has no perfect forward secrecy. In addition, there is no timestamp verification in the authentication process; messages can be replayed.
In terms of communication consumption, the scheme [16] performs a total of 4 transmissions, the message sent by the user is 2560 bits (1024 + 1024 + 256 + 256), the gateway sent to the device is 768 bits (512 + 256), the returned message from the device is 512 bits (256 + 256), and the gateway sends to the user is 640 bits (384 + 256), so a total consumption is 4480 bits (2560 + 768 + 512 + 640).
In scheme [17], protocol is improved based on [16]. However, it can not resist the offline password-guessing attack and the replay attack. Similarly, because the gateway stores keys and sensitive data, the protocol does not provide perfect forward secrecy and cannot resist the gateway compromised attack. On the communication consumption, this protocol makes 4 transmissions. The user sends to the gateway 2592 bits (1024 + 1024 + 256 + 256 + 32), the gateway sends to the device 800 bits (512 + 256 + 32), the device returns 544 bits (256 + 256 + 32) message, then the gateway returns 672 bits (384 + 256 + 32) message to the user, the total consumption is 4608 bits (2592 + 800 + 544 + 672).
The scheme [21] stores the keys in the gateway, and the authors claimed that the gateway is fully trusted and cannot be compromised. So, the gateway compromised attack does not apply to this scheme. The biometric information and password are used for user verification, which can resist offline password guessing attacks and mobile device stolen attacks. A temporary identifier is used in the scheme to provide anonymity, which brings the issue of updating the temporary identifier. If the attacker intercepts the last message, the temporary identifier will be out of sync. In addition, the session key is built based on the shared secret key, so the scheme has no perfect forward secrecy. The data transmission communication consumptions in the protocol are 672 bits (128 + 256 + 256 + 32), 1056 bits (768 + 256 + 32), 800 bits (256 + 256 + 256 + 32), 1472 bits (896 + 256 + 256 + 32 + 32) respectively, so the total communication consumption is 4000 bits (672 + 1056 + 800 + 1472). The scheme [21] is based on symmetric encryption, and the shared key is preset in the gateway, so the calculation is fast.
We have pointed out that Guo et al.’s scheme [19] is not immune to the mobile device stolen attack, the gateway compromised attack, and the desynchronization attack. There is traceability and no perfect forward secrecy. In terms of communication consumption, access to the smart home requires 2 message transfers, consuming 1056 bits (256 + 128 + 256 + 256 + 128 + 32), 1056 bits (256 + 256 + 256 + 256 + 32), respectively, so total consumption is 2112 bits (1056 + 1056).
Our proposed scheme can support all security features. In terms of communication, our authentication requires 2 message transfers, sending 1440 bits (128 + 1024 + 256 + 32) and 1312 bits (1024 + 256 + 32), respectively, so total consumption is 2752 bits (1440 + 1312).
Table 2 and Table 5 show that our protocol has better security and transmission efficiency. To achieve perfect forward secrecy (PFS), it needs at least four times elliptic curve point multiplication. Since only our scheme achieves PFS, the computation cost of our scheme is a little more than others but at the same computation cost level.
9. Conclusions
In this paper, we first pointed out that many existing authentication protocols for a smart home have one or more security flaws. It further showed that almost all these protocols may suffer from gateway compromised attacks. Then we described that Guo et al.’s protocol in a fog-enabled smart home is vulnerable to smart gateway compromised attacks, desynchronization attacks, and mobile device lost/stolen attacks and has no perfect forward secrecy and untraceability. To overcome the shortcomings of Guo et al.’s protocol, we adopt PUF to resist gateway compromised attacks, adopt ECDH to achieve perfect forward secrecy, and propose a secure and privacy-preserving authentication protocol that avoids gateway compromised attacks in fog-enabled smart homes, and formally prove the security of the proposed protocol under random oracle model. Finally, we compare our protocol with some related protocols. The proposed protocol has better security and transmission efficiency with the same computation cost level.
Author Contributions
Conceptualization, Q.X. and J.H.; methodology, Q.X.; validation, Q.X., J.H., and Z.D.; formal analysis, Z.D.; investigation, J.H.; writing—original draft preparation, J.H.; writing—review and editing, Q.X.; supervision, Q.X.; project administration, Q.X.; funding acquisition, Q.X. All authors have read and agreed to the published version of the manuscript.
Funding
This research was supported by the National Natural Science Foundation of China (Grant No. U21A20466).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Lutolf, R. Smart home concept and the integration of energy meters into a home based system. In Proceedings of the Seventh International Conference on Metering Apparatus and Tariffs for Electricity Supply, Glasgow, UK, 17–19 November 1992; pp. 277–278. [Google Scholar]
- Berlo, A.V.; Allen, B. Design Guidelines on Smart Homes: A COST 219bis Guidebook; COST, European Co-Operation in the Field of Scientific and Technical Research: Cham, Switzerland, 1999. [Google Scholar]
- Zemrane, H.; Baddi, Y.; Hasbi, A. Internet of things smart home ecosystem. In Emerging Technologies for Connected Internet of Vehicles and Intelligent Transportation System Networks; Springer: Cham, Switzerland, 2020; pp. 101–125. [Google Scholar]
- Zanella, A.; Bui, N.; Castellani, A.; Vangelista, L.; Zorzi, M. Internet of things for smart cities. IEEE Internet Things J. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 17 August 2012; pp. 13–16. [Google Scholar]
- Rahimi, M.; Songhorabadi, M.; Kashani, M.H. Fog-based smart homes: A systematic review. J. Netw. Comput. Appl. 2020, 153, 102531. [Google Scholar] [CrossRef]
- Alatoun, K.; Matrouk, K.; Mohammed, M.A.; Nedoma, J.; Martinek, R.; Zmij, P. A Novel Low-Latency and Energy-Efficient Task Scheduling Framework for Internet of Medical Things in an Edge Fog Cloud System. Sensors 2022, 22, 5327. [Google Scholar] [CrossRef] [PubMed]
- Rocha Filho, G.P.; Brandão, A.H.; Nobre, R.A.; Meneguette, R.I.; Freitas, H.; Gonçalves, V.P. HOsT: Towards a Low-Cost Fog Solution via Smart Objects to Deal with the Heterogeneity of Data in a Residential Environment. Sensors 2022, 22, 6257. [Google Scholar] [CrossRef]
- Chen, Y.-Y.; Chen, M.-H.; Chang, C.-M.; Chang, F.-S.; Lin, Y.-H. A Smart Home Energy Management System Using Two-Stage Non-Intrusive Appliance Load Monitoring over Fog-Cloud Analytics Based on Tridium’s Niagara Framework for Residential Demand-Side Management. Sensors 2021, 21, 2883. [Google Scholar] [CrossRef]
- Debauche, O.; Nkamla Penka, J.B.; Mahmoudi, S.; Lessage, X.; Hani, M.; Manneback, P.; Lufuluabu, U.K.; Bert, N.; Messaoudi, D.; Guttadauria, A. RAMi: A New Real-Time Internet of Medical Things Architecture for Elderly Patient Monitoring. Information 2022, 13, 423. [Google Scholar] [CrossRef]
- Verma, P.; Sood, S.K. Fog assisted-IoT enabled patient health monitoring in smart homes. IEEE Internet Things J. 2018, 5, 1789–1796. [Google Scholar] [CrossRef]
- Hu, B.; Tang, W.; Xie, Q. A Two-factor Security Authentication Scheme for Wireless Sensor Networks in IoT Environments. Neurocomputing 2022, 500, 741–749. [Google Scholar] [CrossRef]
- Jeong, J.; Chung, M.Y.; Choo, H. Integrated OTP-based user authentication scheme using smart cards in home networks. In Proceedings of the 41st Annual Hawaii International Conference on System Sciences (HICSS 2008), Waikoloa, HI, USA, 7–10 January 2008; p. 294. [Google Scholar]
- Xue, K.; Ma, C.; Hong, P.; Ding, R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 316–323. [Google Scholar] [CrossRef]
- Saqib, M.; Jasra, B.; Moon, A.H. A lightweight three factor authentication framework for IoT based critical applications. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 6925–6937. [Google Scholar] [CrossRef]
- Shuai, M.; Yu, N.; Wang, H.; Xiong, L. Anonymous authentication scheme for smart home environment with provable security. Comput. Secur. 2019, 86, 132–146. [Google Scholar] [CrossRef]
- Kaur, D.; Kumar, D. Cryptanalysis and improvement of a two-factor user authentication scheme for smart home. J. Inf. Secur. Appl. 2021, 58, 102787. [Google Scholar] [CrossRef]
- Santoso, F.K.; Vun, N.C. Securing IoT for smart home system. In Proceedings of the 2015 International Symposium on Consumer Electronics (ISCE), Madrid, Spain, 24–26 June 2015; pp. 1–2. [Google Scholar]
- Guo, Y.; Zhang, Z.; Guo, Y. SecFHome: Secure remote authentication in fog-enabled smart home environment. Comput. Netw. 2022, 207, 108818. [Google Scholar] [CrossRef]
- Blundo, C.; Santis, A.D.; Herzberg, A.; Kutten, S.; Vaccaro, U.; Yung, M. Perfectly-Secure Key Distribution for Dynamic Conferences. Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1992; pp. 471–486. [Google Scholar]
- Wazid, M.; Das, A.K.; Odelu, V.; Kumar, N.; Susilo, W. Secure remote user authenticated key establishment protocol for smart home environment. IEEE Trans. Dependable Secur. Comput. 2017, 17, 391–406. [Google Scholar] [CrossRef]
- Haseeb-ur-rehman, R.M.A.; Liaqat, M.; Aman, A.H.M.; Almazroi, A.A.; Hasan, M.K.; Ali, Z.; Ali, R.L. LR-AKAP: A Lightweight and Robust Security Protocol for Smart Home Environments. Sensors 2022, 22, 6902. [Google Scholar] [CrossRef]
- Lee, J.; Oh, J.; Kwon, D.; Kim, M.; Yu, S.; Jho, N.-S.; Park, Y. PUFTAP-IoT: PUF-Based Three-Factor Authentication Protocol in IoT Environment Focused on Sensing Devices. Sensors 2022, 22, 7075. [Google Scholar] [CrossRef]
- Yeh, H.L.; Chen, T.H.; Liu, P.C.; Kim, T.H.; Wei, H.W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar] [CrossRef]
- Yang, J.H.; Chang, C.C. An ID-based remote mutual authentication with key agreement scheme for mobile devices on elliptic curve cryptosystem. Comput. Secur. 2009, 28, 138–143. [Google Scholar] [CrossRef]
- Islam, S.H.; Biswas, G.P. A more efficient and secure ID-based remote mutual authentication with key agreement scheme for mobile devices on elliptic curve cryptosystem. J. Syst. Softw. 2011, 84, 1892–1898. [Google Scholar] [CrossRef]
- Zerrouki, F.; Ouchani, S.; Bouarfa, H. A survey on silicon PUFs. J. Syst. Archit. 2022, 127, 102514. [Google Scholar] [CrossRef]
- Yi, F.; Zhang, L.; Xu, L.; Yang, S.; Lu, Y.; Zhao, D. WSNEAP: An Efficient Authentication Protocol for IIoT-Oriented Wireless Sensor Networks. Sensors 2022, 22, 7413. [Google Scholar] [CrossRef] [PubMed]
- Yu, S.; Park, K. PUF-PSS: A Physically Secure Privacy-Preserving Scheme Using PUF for IoMT-Enabled TMIS. Electronics 2022, 11, 3081. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Analysis of key-exchange protocols and their use for building secure channels. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2001; pp. 453–474. [Google Scholar]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2004; pp. 523–540. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).