1. Introduction
The museum has collections, displays, research, education, and dissemination of human history and cultural heritage. By collecting all kinds of material and intangible cultural heritage, museums are the biggest driving force for their development and progress, and also the embodiment of museum creativity and vitality. With the progress of society, people’s material living standards are improved at the same time; cultural consumption is widely valued by people.
Take the fire of Notre Dame Cathedral in Paris on 15 April 2019, as an example, which is a form of disaster. Although there were no casualties, what cannot be replaced is that the files and data that we had been working hard on for a long time were affected by the fire, and the spirit and symbolic meaning were also destroyed. The same situation happened in Taiwan’s Cloud Gate Dance Company, an outstanding modern dance performance group in Taiwan. Founded in 1973, it was the first contemporary dance company in Asia and a world-class modern dance company, enjoying a high reputation in the world [
1].
In the early hours of 11 February 2008, a fire broke out in the rehearsal venue of Bali Township, Taipei County, Taiwan (now Bali District, New Taipei City). The performance props and historical data were almost destroyed. As an institution for collecting, researching, and displaying natural and human cultural heritage, museums have attracted ever more attention. Museums, with the mission of social responsibility, collect the current social memorabilia, especially the effective management and utilization of “important cultural relics and archives information”, which is the foundation of museum’s construction and development, and, also, the basic task of museums.
However, due to various reasons, most people may not be able to visit their favorite museums one by one due to time and space constraints. For example, since the outbreak of the novel coronavirus (COVID-19) in early 2020, the American Alliance of Museums (AAM) recently stated that nearly one-third of the museums in the United States may be permanently closed, pointing out that museum operations are facing “extreme financial distress” [
2]. Digital museums based on the development of the Internet and multimedia technology can now satisfy people’s desires, enabling people to view museums around the world without leaving their homes.
Traditional cultural relics provide preservation conditions for digital storage, appreciation, and dissemination in the form of text, images, sound, and video. However, with the increasing degree of digitalization and informatization of museums, the security of digital cultural relics has become a key issue in the transmission, transaction, and reproduction of digital cultural relics. Although, the need for digitization in cultural heritage is well established, and also proven by the millions of already existing digital assets. However, if these digitalized cultural relics exhibitions lack a complete authorization verification mechanism, these digital materials will be arbitrarily spread or even falsified. As early as 2004, Triet and Due [
3] posited the idea of using digital watermarking technology to provide a wider range of online services for ordinary users of the palace music of Vietnam (recognized as a world heritage site by UNESCO in November 2003) and standardizing the limited access service for online registered users. In 2006, Chen et al. [
4] studied using personal mobile devices for digital rights management (DRM) of E-museums. Unfortunately, neither of them has a relatively detailed algorithm description. As for the issue of digital rights management, even in the past, Chen et al. [
5,
6,
7] proposed algorithm research on the digital content rights protection technology based on mobile devices for enterprises. However, in previous literature, there is little focus on the digital content of the museum that is valuable and important. Therefore, this paper aims to be a pioneer in research on museum digital rights and proposes a new authorization mechanism.
The blockchain mechanism was proposed by Nakamoto [
8] in 2008. Blockchain is essentially a new method of data management; an open, transparent, and decentralized database. Blockchain is comprised of point-to-point transmission, a consensus mechanism, a smart contract, an encryption algorithm, and a distributed data record list storage technology system. This system can realize the tamperproof data storage, traceable data viewing, and trusted point-to-point transmission to solve the problem of trust construction without third-party supervision. The core of this system is the realization of the trustworthy circulation of value and promotion of the transformation of the “Information Internet” to the “Value Internet”, which can be used as the basic protocol of the “Value Internet”.
Therefore, the concepts of decentralized rights management combining blockchain and digital watermarking technology [
9], blockchain, and cloud services [
10,
11,
12,
13] were proposed respectively, but these studies only focus on conceptual proposals. Some authors [
14,
15,
16,
17] reveal the recent international applications of blockchain, smart contracts, and cryptography for the protection of digital rights that have put forward more specific and detailed communication protocols.
Table 1 below presents a comparison of the existing digital rights management surveys.
Although museums have many advantages in the use of digitalization, they will also encounter some problems, especially for important cultural relics and archive information. The protection of intellectual property rights is one of them. As digital museums put exhibits on the Internet for browsing, anyone can download, modify, and disseminate them. As a cultural heritage carrier, museum archives have certain privacy requirements.
However, the advent of the digital era has exacerbated the excessive sharing of museum archives information, resulting in frequent leakage of such information. The source channels of museum archives information are complex, and incomplete information collection occurs from time to time. If there is no consensus mechanism, large and complex information may be fragmented, and as authentication is difficult, it could result in unclear property rights. Besides, there are other problems, such as the cumbersome authentication methods of existing museum archives information, which lead to the user’s poor experience and inhibit the effective use of museum social functions. Now, when exhibits are digitized, the existing mature digital watermarking technology and blockchain technology can solve this problem. Museums use this technology to label their digital exhibits with their copyright information and secure them through an authorization mechanism.
The traceability and tamperproof characteristics of blockchain technology can not only realize the effective “tracking” of the infringement of museum archive information due to excessive sharing but also prevent the privacy information of museum archives based on the encryption function. The distributed ledger technology, decentralization, autonomy, and other characteristics of blockchain technology can solve the complicated process and identification difficulties in the traditional museum archive information screening and authentication process, forming a kind of information based on an “address” instead of “personal identity” consensus mechanism. By setting up the “timestamp” module to build a smart authentication service program, a piece of information given by the authentication material can be recorded into the “timestamp” on the blockchain and confirm that the recorded piece of information can be open to public inquiry, thereby improving the efficiency of the “smart authentication” of museum archives. The trustlessness and smart contract features of blockchain technology can realize the synchronization and mutual verification of museum archive information, ensure that different information can automatically and programmatically flow safely, as well as easily and conveniently checking tamperproof file information. Blockchain technology can effectively solve several problems in current museum archive information management and construction.
At present, many institutions have explored the application of blockchain technology in museums. The Russian National Tretyakov Gallery uses blockchain technology to make the “world” a sponsor of the digital construction of the museum and a collector of gallery art, enabling individuals or companies to use the platform for the Tretyakov Art Gallery collection sponsorship for digitalization. Switzerland’s Zug launched the world’s first online trading and sponsorship platform for digital art masterpieces created by blockchain technology to make up for the shortcomings of the current traditional art market operation mode. China’s Baidu Super Chain and Baidu Baike have established a “Culture, Museum and Art Chain” based on blockchain technology and promoted the online collection of 246 museums in the Baike Museum project online, jointly promoting the confirmation and maintenance of online collection copyright and exploring online collection digital copyright trading methods [
18].
In short, the application of blockchain in museums is still in the experimental stage. The World Cultural Heritage Organization released a white paper on the cultural relics blockchain in 2019, stating that with the deepening of the application of blockchain technology and the continuous updating of management ideas in the Cultural, Museum, and Art industry, blockchain technology will play a revolutionary role in related fields, such as cultural relics collection, auction, evaluation, research, rescue, excavation, protection, and museum drafting and rating. This research is based on blockchain technology, focusing on the preservation, authorized display, and security of cultural relics, and constructing a museum’s design and application of digital rights management, thereby achieving the following goals:
- (1)
Publicly verifiable [
5,
6,
14,
15,
16]—The authorized on-chain information of cultural relics and important files can be disclosed, and the identity of the applicant can be verified through the verification of digital certificates.
- (2)
Transparency [
5,
14,
15,
16]—The authorization information for cultural relics and important files is transparent. Based on the open transparency of information on the chain, it can obtain trust between nodes at low cost, realize the sharing of digital content resources, and achieve the mission of museum social education.
- (3)
Unforgeability [
14,
15,
16]—The new decentralized model of blockchain combined with timestamp technology makes it impossible to arbitrarily change the data on the chain, thus effectively solving the trust problem.
- (4)
Traceability [
5,
14,
15,
16]—The source and authorization mechanism of cultural relics and important file information use timestamp and signature mechanisms to achieve traceability management.
- (5)
Non-repudiation [
6,
14]—The use of timestamp and signature mechanisms enables the implementation of the legal authorization mechanism.
- (6)
Standardization of stored data [
5,
6]—The effective classification of digital content and formatting on the chain help to effectively manage the copyright of digital rights so intellectual property rights can be protected.
- (7)
Timeliness [
5,
17]—There is a good management mechanism to realize the sharing of digital content resources. The license is timeliness and will not be monopolized.
The rest of this article is organized as follows.
Section 2 presents preliminary knowledge.
Section 3 deals with the proposed sustainable and traceable cultural relic display mechanism.
Section 4 presents an analysis of the proposed scheme. In
Section 5, the discussions and comparisons are given. Finally, we conclude this study.
3. Method
3.1. System Structure
In this study, we used the Elliptic Curve Digital Signature Algorithm (ECDSA), blockchain, and a smart contract to design a sustainable and traceable cultural relic display mechanism such that the museum social education function of the museum can be carried out at any time.
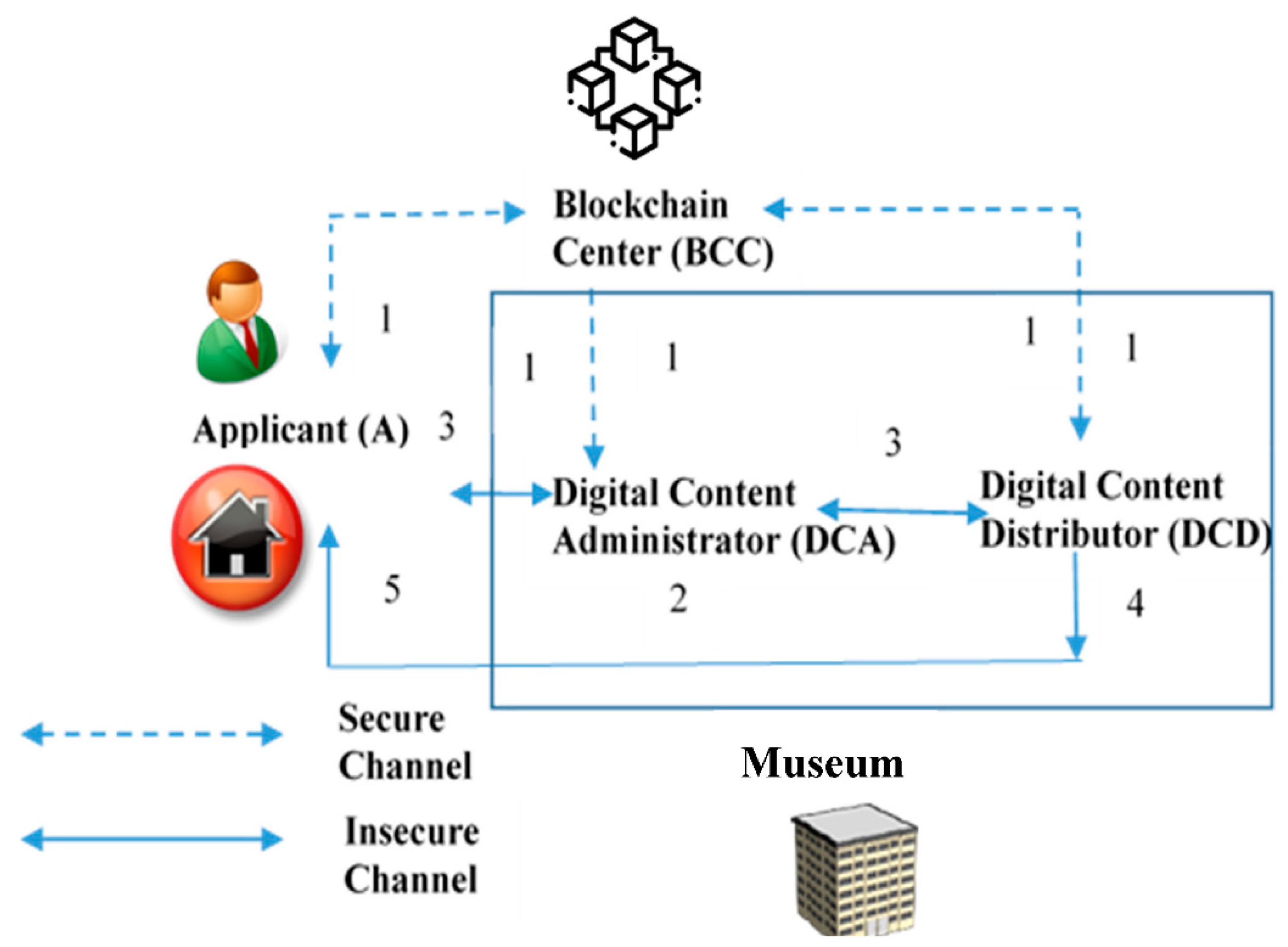
Figure 1 is the system architecture diagram. The roles in the environment include Applicant (A), Blockchain Center (BCC), Digital Content Administrator (DCA), and Digital Content Distributor (DCD).
- (1)
Applicant—It is intended that the citizens or institutions want to access the digital content resource of the museum.
- (2)
Blockchain Center (BCC)—This center records the information of the digital rights resource for the Applicant to query or verify the resource status. The BCC accepts the role’s registration and issues the identity certificate and public/private key pair to each party.
- (3)
Digital Content Administrator (DCA)—The DCA is responsible for the generation and management of the museum’s digital content resource. The digital content resource is classified and protected by the DCA. The DCA also reviews the Applicant’s request to determine whether to allow or deny access to the digital content resource.
- (4)
Digital Content Distributor (DCD)—The DCD is a proxy of the DCA. After the DCA authenticates the Applicant’s identification, the DCD is responsible for actual cloud authorization for the Applicant to access the museum’s digital content resource. The DCA and DCD are both cloud platforms set up in museums and co-manage the digital content resource.
We briefly illustrate the scenarios in the following steps.
Step 1: Registration phase—Applicant, Digital Content Administrator, and Digital Content Distributor need to register with the Blockchain Center; the Blockchain Center issues the identity certificate and public/private key pair to each party.
Step 2: Digital content production phase—The DCA classifies the museum’s resources and then encrypts them into a protected digital resource and then stores it in the DCD. The DCA also uploads the detailed categories into the Blockchain Center.
Step 3: Digital content authorization phase—After the Applicant proposes to access a digital resource request, the DCA reviews the Applicant’s qualifications, issues the license key of the Applicant, and transmits the related information to the DCD.
Step 4: Digital content issuing phase—After the DCD receives the DCA’s authorization, the DCD uses the proxy re-encryption mechanism to issue the license key, a time-limited key, and player (or reader) to the Applicant.
Step 5: Digital content browsing phase—After the Applicant receives the license key, the Applicant uses it to decrypt the protected digital content. The digital content can be read (or played) normally.
3.2. Notation
Table 2 shows the notation of the proposed scheme.
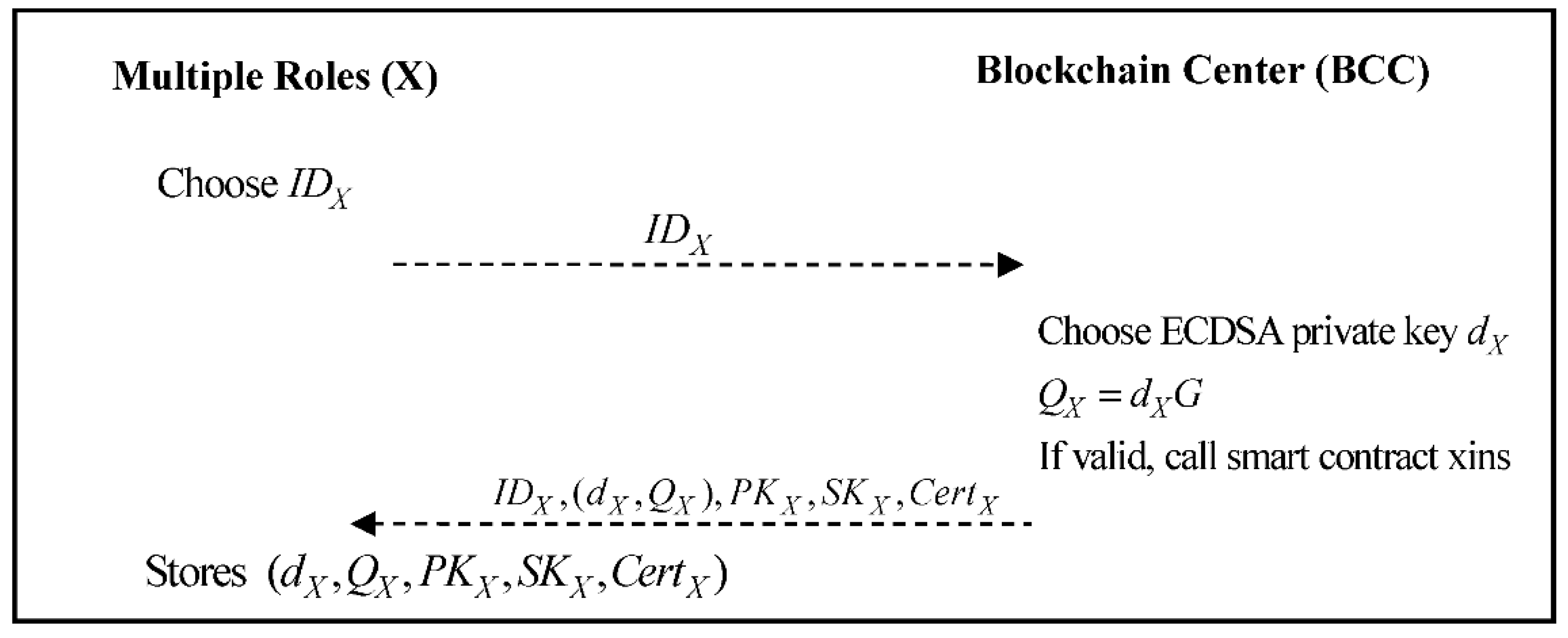
3.3. Registration Phase
The Applicant, DCA, and DCD should register with the Blockchain Center and obtain a relative public/private key pair. The Applicant also gets an identity digital certificate from the Blockchain Center via a secure channel. The system role X can represent the Applicant, DCA, and DCD.
Figure 2 shows the flowchart of the registration phase.
Step 1: System role X generates a name , and sends it to the Blockchain Center.
Step 2: The Blockchain Center generates an ECDSA private key
based on the role
X, calculates
. If the identity of the registered role is verified, the smart contract xins will be triggered, the content of which is the Algorithm 1 as follows:
| Algorithm 1. Smart contract xins of the proposed scheme. |
function insert x smart contract xins (
string x_id, string x_detail) {
count ++;
x[count].id = id;
x[count].detail = detail;
}
string x_keypairs; |
Then, the Blockchain Center will transmit to role X.
Step 3: The role X will store .
3.4. Digital Content Production Phase
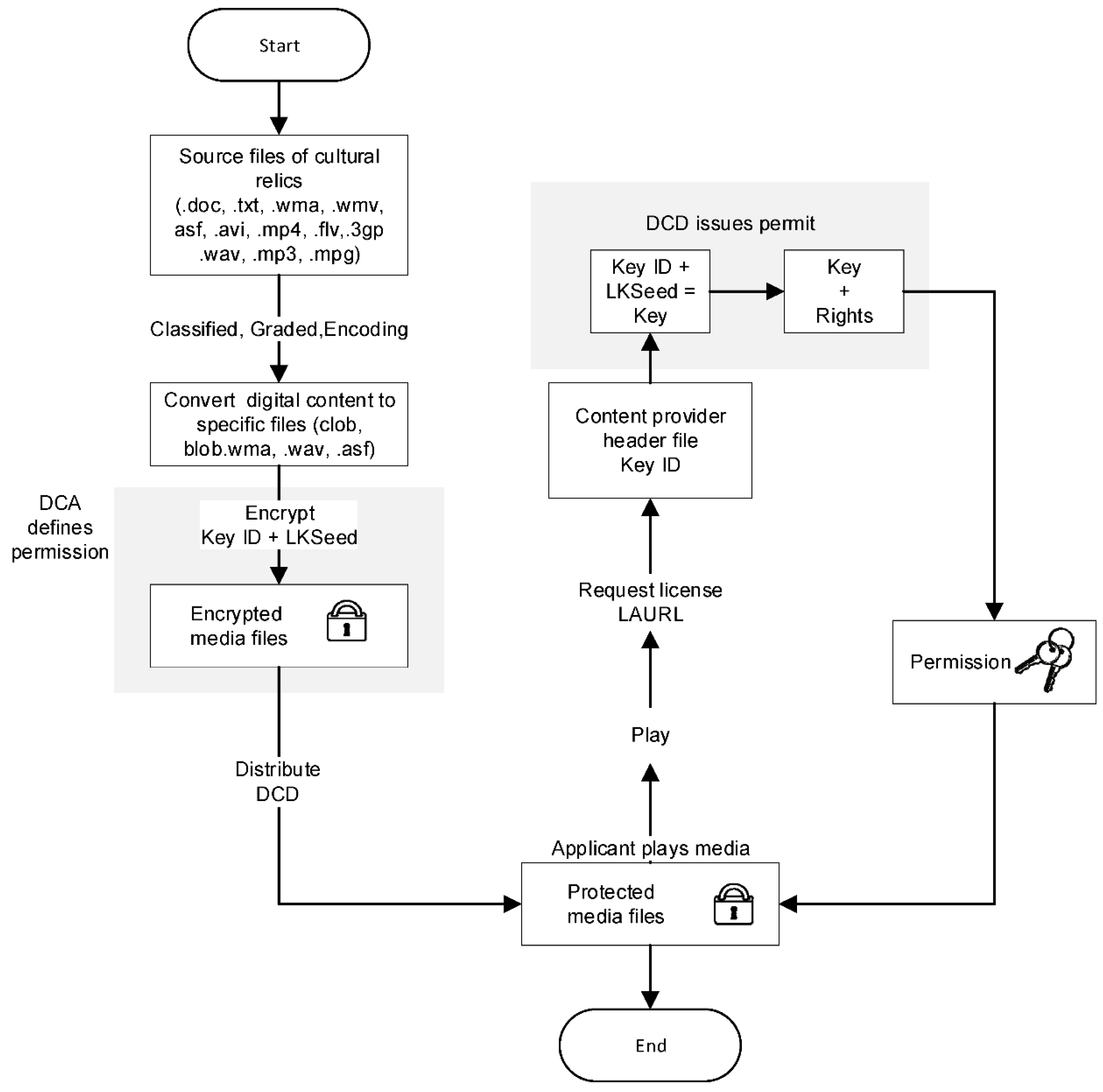
The museum collects many precious cultural relics. The digital content production process of valuable cultural relics has a specific process. In general, experts and scholars classify (such as biological classification, antiquities classification, etc.), grade (grade of antiquities is divided into general, important, and national treasures, etc.), and clarify the importance (such as rare or era significance or endangered species, etc.), and then different competent authorities proceed with various kinds of appointments. Finally, it is handed over to professional and technical personnel to produce digital content through photography and 3D surroundings. In this phase, we will focus on illustrating the protection technology of digital content.
Figure 3 shows the production flowchart of protected digital content. To enhance performance, we use the digital envelope for implementation. That is, the DCA uses the symmetry key to encrypt the digital content and then employs the ElGamal-based system of the public-key system to protect the symmetry key.
Step 1: The DCA classifies the original multimedia files and encodes them into clob and blob formats for storage. The DCA also makes the identity of these digital contents IDDC.
Step 2: The DCA encrypts these encoded multimedia data with KeyID and Seed, and transfers the keym and encrypted digital content to the DCD for storage.
Step 3: When the Applicant wants to access these multimedia materials, it must first obtain legal authorization from the DCA, and the DCA will provide the Applicant with an authorization key.
Step 4: The Applicant can use the authorization key to unlock the information provided by the DCD and obtain the identity of the digital content IDDC. The DCD can then use IDDC to get encryption key keym, which can be used to obtain the plaintext of the digital content. The IDDC must be obtained after authorization verification, and then connect to the DCD from the multimedia player/reader to obtain the keym and play the digital content. This step is performed automatically by the smart contract, and the Applicant cannot skip the verification process privately. The details will be introduced in the rest of the phase.
3.5. Digital Content Authorization Phase
After reviewing the Applicant’s identity, the DCA, according to the valid authorized time key issues, authorizes access to the digital content. We present the flowchart of the digital content authorization phase in
Figure 4.
Step 1: The Applicant generates a random value , calculates , , , , , and sends to the DCA.
Step 2: The DCA first calculates , uses to confirm whether the timestamp is valid, and then verifies the correctness of the ECDSA signature, and calculates , , , , .
If the verification is passed, the DCA will get the relevant content request information and trigger the smart contracts adcains and adcachk. The content is as follows: timestamp is valid, and then verify the correctness of the ECDSA signature, calculating , , , , .
If the verification is passed, the DCA will get the relevant content request information and trigger the smart contracts adcains and adcachk. The content is the Algorithm 2 as follows:
| Algorithm 2. Smart contract adcains and adcachk of the proposed scheme. |
function insert smart contract adcains(
string adca_id, string adca_detail,
string adca_cert, string adca_tsp) {
count ++;
adca[count].id = id;
adca[count].detail = detail;
adca[count].cert = cert;
adca[count].tsp = tsp;
}
sign string a_key (adca_id, adca_detail,
adca_cert, adca_tsp);
verify string a_key (adca_id, adca_detail,
adca_cert, adca_tsp);
function check smart contract adcachk(
string adca_id, string adca_detail,
string adca_cert, string adca_tsp) {
return adca_id.exist;
return adca_detail.exist;
return adca_cert.exist;
return adca_tsp.exist;
} |
The DCA calculates ; will also be uploaded to the Blockchain Center. Then the DCA generates a random value and calculates , , , , and sends to the Applicant.
Step 3: The Applicant first calculates , uses to confirm whether the timestamp is valid, then verifies the correctness of the ECDSA signature, and calculates , , , .
If the verification is passed, the content request information is confirmed by the DCA, and the smart contracts dcaains and dcaachk will be sent. The content is the Algorithm 3 as follows:
| Algorithm 3. Smart contract dcaains and dcaachk of the proposed scheme. |
function insert smart contract dcaains(
string dcaa_id, string dcaa_detail,
string dcaa_akey, string dcaa_tsp) {
count ++;
dcaa[count].id = id;
dcaa[count].detail = detail;
dcaa[count].akey = akey;
dcaa[count].tsp = tsp;
}
sign string dca_key (dcaa_id, dcaa_detail,
dcaa_akey, dcaa_tsp);
verify string dca_key (dcaa_id, dcaa_detail,
dcaa_akey, dcaa_tsp);
function check smart contract dcaachk(
string dcaa_id, string dcaa_detail,
string dcaa_akey, string dcaa_tsp) {
return dcaa_id.exist;
return dcaa_detail.exist;
return dcaa_akey.exist;
return dcaa_tsp.exist;
} |
The Applicant calculates , and will also be uploaded to the Blockchain Center.
3.6. Digital Content Issuing Phase
The DCD is to be a proxy and uses the proxy re-encryption mechanism to issue the license key—time-limited key and player (or reader) to the Applicant.
Figure 5 illustrates the flowchart of the digital content issuing phase.
Step 1: The DCA generates a random value , calculates , , , , , and sends to the DCD.
Step 2: The DCD first calculates , uses to confirm whether the timestamp is valid, then verifies the correctness of the ECDSA signature, and calculates , , , , .
If the verification is passed, the DCD will get the relevant content issuing information and trigger the smart contracts dcadcdins and dcadcdchk. The content is the Algorithm 4 as follows:
| Algorithm 4. Smart contract dcadcdins and dcadcdchk of the proposed scheme. |
function insert smart contract dcadcdins(
string dcadcd_id, string dcadcd_detail,
string dcadcd_iddc, string dcadcd_ekey,
string dcadcd_akey, string dcadcd_tsp) {
count ++;
dcadcd[count].id = id;
dcadcd[count].detail = detail;
dcadcd[count].iddc = iddc;
dcadcd[count].ekey = ekey;
dcadcd[count].akey = akey;
dcadcd[count].tsp = tsp;
}
sign string dca_key (dcadcd_id, dcadcd_detail,
dcadcd_iddc, dcadcd_ekey, dcadcd_akey,
dcadcd_tsp);
verify string dca_key (dcadcd_id, dcadcd_detail, dcadcd_iddc, dcadcd_ekey, dcadcd_akey,
dcadcd_tsp);
function check smart contract dcadcdchk(
string dcadcd_id, string dcadcd_detail,
string dcadcd_iddc, string dcadcd_ekey,
string dcadcd_akey, string dcadcd_tsp) {
return dcadcd_id.exist;
return dcadcd_detail.exist;
return dcadcd_iddc.exist;
return dcadcd_ekey.exist;
return dcadcd_akey.exist;
return dcadcd_tsp.exist;
} |
The DCD calculates ; will also be uploaded to the Blockchain Center. The DCD then generates a random value and calculates , , , , and sends to the DCA.
Step 3: The DCA first calculates
, uses
to confirm whether the timestamp is valid, then verifies the correctness of the ECDSA signature, and calculates
,
,
,
,
. If the verification is passed, the content issuing information is confirmed by the DCD, and the smart contracts dcddcains and dcddcachk will be sent. The content is the Algorithm 5 as follows:
| Algorithm 5. Smart contract dcddcains and dcddcachk of the proposed scheme. |
function insert smart contract dcddcains(
string dcddca_id, string dcddca_detail,
string dcddca_tsp) {
count ++;
dcddca[count].id = id;
dcddca[count].detail = detail;
dcddca[count].tsp = tsp;
}
sign string dcd_key (dcddca_id, dcddca_detail,
dcddca_tsp);
verify string dcd_key (dcddca_id, dcddca_detail,
dcddca_tsp);
function check smart contract dcddcachk(
string dcddca_id, string dcddca_detail,
string dcddca_tsp) {
return dcddca_id.exist;
return dcddca_detail.exist;
return dcddca_tsp.exist;
} |
The DCA calculates ; will also be uploaded to the Blockchain Center.
3.7. Digital Content Browsing Phase
After authorization, the Applicant’s application (reader or player) can use the authorized key to decrypt the symmetry key. The Applicant can browse the digital content normally.
Figure 6 illustrates the flowchart of the digital content browsing phase.
Step 1: The Applicant downloads the application and generates a random value , calculates , , , , and sends to the DCD.
Step 2: The DCD first calculates , uses to confirm whether the timestamp is valid, and then verifies the correctness of the ECDSA signature, calculates , , , , .
If it passes the verification, the DCD will get the relevant content and trigger the smart contracts adcdins and adcdchk. The content is the Algorithm 6 as follows:
| Algorithm 6. Smart contract adcdins and adcdchk of the proposed scheme. |
function insert smart contract adcdins(
string adcd_id, string adcd_detail,
string adcd_tsp) {
count ++;
adcd[count].id = id;
adcd[count].detail = detail;
adcd[count].tsp = tsp;
}
sign string a_key (adcd_id, adcd_detail,
adcd_tsp);
function insert smart contract adcdins(
string adcd_id, string adcd_detail,
string adcd_tsp) {
count ++;
adcd[count].id = id;
adcd[count].detail = detail;
adcd[count].tsp = tsp;
}
sign string a_key (adcd_id, adcd_detail,
adcd_tsp); |
The DCD calculates ; will also be uploaded to the Blockchain Center. The DCD then generates a random value and calculates , , , ,
, and sends to the Applicant.
Step 3: The Applicant’s application first calculates
, uses
to confirm whether the timestamp is valid, then verifies the correctness of the ECDSA signature, and calculates
,
,
,
,
. If it passes the verification, the content browsing request information is confirmed by the DCD, and the smart contracts dcdains and dcdachk will be executed. The content is the Algorithm 7 as follows:
| Algorithm 7. Smart contract dcdains and dcdachk of the proposed scheme. |
function insert smart contract dcdains(
string dcda_id, string dcda_detail,
string dcda_akey, string dcda_iddc,
string dcda_tsp) {
count ++;
dcda[count].id = id;
dcda[count].detail = detail;
dcda[count].akey = akey;
dcda[count].iddc = iddc;
dcda[count].tsp = tsp;
}
sign string dcd_key (dcda_id, dcda_detail,
dcda_akey, dcda_iddc, dcda_tsp);
verify string dcd_key (dcda_id, dcda_detail,
dcda_akey, dcda_iddc, dcda_tsp);
function check smart contract dcdachk(
string dcda_id, string dcda_detail,
string dcda_akey, string dcda_iddc,
string dcda_tsp) {
return dcda_id.exist;
return dcda_detail.exist;
return dcda_akey.exist;
return dcda_iddc.exist;
return dcda_tsp.exist;
} |
The Applicant calculates ; will also be uploaded to the Blockchain Center. Finally, the Applicant’s application calculates to obtain the identity of the digital content IDDC successfully. Therefore, the DCD can use IDDC to obtain the corresponding decryption key keym, which can be used to obtain the plaintext of digital content through the reader or player. This step is performed automatically by the smart contract, and the Applicant cannot skip the verification process privately.
4. Analysis
4.1. Public Authentication
Using digital certificate verification can publicly verify the identity of the applicant, and the authorization information can be made public. The open transparency of the museum’s information on the chain solves the actual problematic points of information asymmetry and cumbersome process and low efficiency, breaking the original barriers, and truly realizing high efficiency and specialization in the field of museum’s digital rights. Let us take the message transmitted by the Applicant (A) and Digital Content Administrator (DCA) as an example. When the DCA sends a message signed by ECDSA to the Applicant, the Applicant will first verify the correctness of the time stamp and signature, then generate blockchain data , and use as an index to upload the blockchain data to the Blockchain Center (BCC). That is to say, after verifying the correctness of the time stamp and signature for each role that receives the message, it also verifies the correctness of the blockchain data generated by the previous role. Therefore, our proposed solution achieves the characteristics of public verification through blockchain technology and ECDSA digital signature.
4.2. Transparency
The identity of the authorized object of digital content is verified by the Digital Content Administrator of the museum. The authorization period is controlled by the Digital Content Administrator. The Applicant cannot occupy or transfer privately. Any nodes that participate in the system do not need to trust each other. The operation of the system and operating rules are open and transparent, and all information is open. A node cannot deceive other nodes. In this way, the trust relationship between nodes is realized, making it possible to obtain trust between nodes at a low cost. For example, when the Applicant (A) requests digital content authorization from the Digital Content Administrator (DCA), the DCA will send an authorization key to A. This key contains A’s certificate and the hash value of the authorization period; A will not be able to privately occupy or transfer digital content privately.
4.3. Tamperproof
Use the timestamp and signature mechanism to irreversibly generate a string composed of random numbers and letters for the data placed in each block. This original text cannot be inferred from the string, thus effectively solving the trust problem. The messages are illustrated as follows after performing the hash function operation:
The messages cannot be reversed back to the original content, so this agreement achieves the characteristic that the message cannot be tampered with.
4.4. Traceable
After the digital content of the museum is on the chain, the data block containing the copyright information is permanently stored on the blockchain and cannot be tampered with. All transaction traces can be traced throughout the entire process, which can be used as a digital deposit certificate of the museum to deal with infringement. For example, when we want to verify and trace whether the blockchain data between the Applicant (A) and Digital Content Administrator (DCA) is legal, we can compare and verify and .
When we want to verify and trace whether the blockchain data between the Digital Content Administrator (DCA) and Digital Content Distributor (DCD) is legal, we can compare and verify and . When we want to verify and trace whether the blockchain data between the Applicant (A) and Digital Content Distributor (DCD) is legal, we can compare and verify and .
4.5. Nonrepudiation
The content of the message sent by each role is signed by the role of its ECDSA private key. After the receiver receives the message, it will verify the message with the sender’s public key. If the message is successfully verified, the sender cannot deny the content of the message is transmitted.
Table 3 is an undeniable description of each role in this program.
4.6. Data Format Standardization
Effectively categorizing the digital content of the museum and formatting it on the chain is helpful to effectively manage digital property rights and control the unique authorization power of digital content, and intellectual property rights can be protected.
This study re-encodes various original multimedia files into blob and clob formats, which will provide fast and consistent authorized content transmission services.
4.7. Timeless
In our proposed scheme, the Digital Content Administrator (DCA) of the museum is responsible for the production and management of the digital content property rights and the identity verification of the Applicant (A); the Digital Content Administrator (DCA) is also responsible for the issuance of a time-sensitive playback license, and the applicant’s playback key identification code cannot permanently occupy the playback of digital content. The Applicant must obtain the decryption key through the authorization key; the authorization key contains the hash value of the Applicant’s certificate and the authorization period. If the authorization period expires, the Applicant will not be able to obtain the decryption key; that is, it cannot perform digital content playback. Thus, we will not worry about the leakage of digital property rights.