State-of-the-Art Review on IoT Threats and Attacks: Taxonomy, Challenges and Solutions
Abstract
1. Introduction
2. State-of-the-Art, Motivation, and Contributions of This Research
2.1. Trends in Literature and Motivation
2.2. Comparison with Existing Surveys
2.3. Scope of the Present Survey and Contributions
- This survey envisages providing a deeper insight into the IoT from the perspective of threats and attacks.
- An information-rich survey on various aspects of IoT, including threats and attacks from the literature, is presented.
- This survey presents a five-layer IoT architecture and seven-layer IoT architecture, along with the existing three-layer architecture.
- A comprehensive survey on the communication standards and protocols corresponding to three-layer, five-layer, and seven-layer IoT architectures is presented.
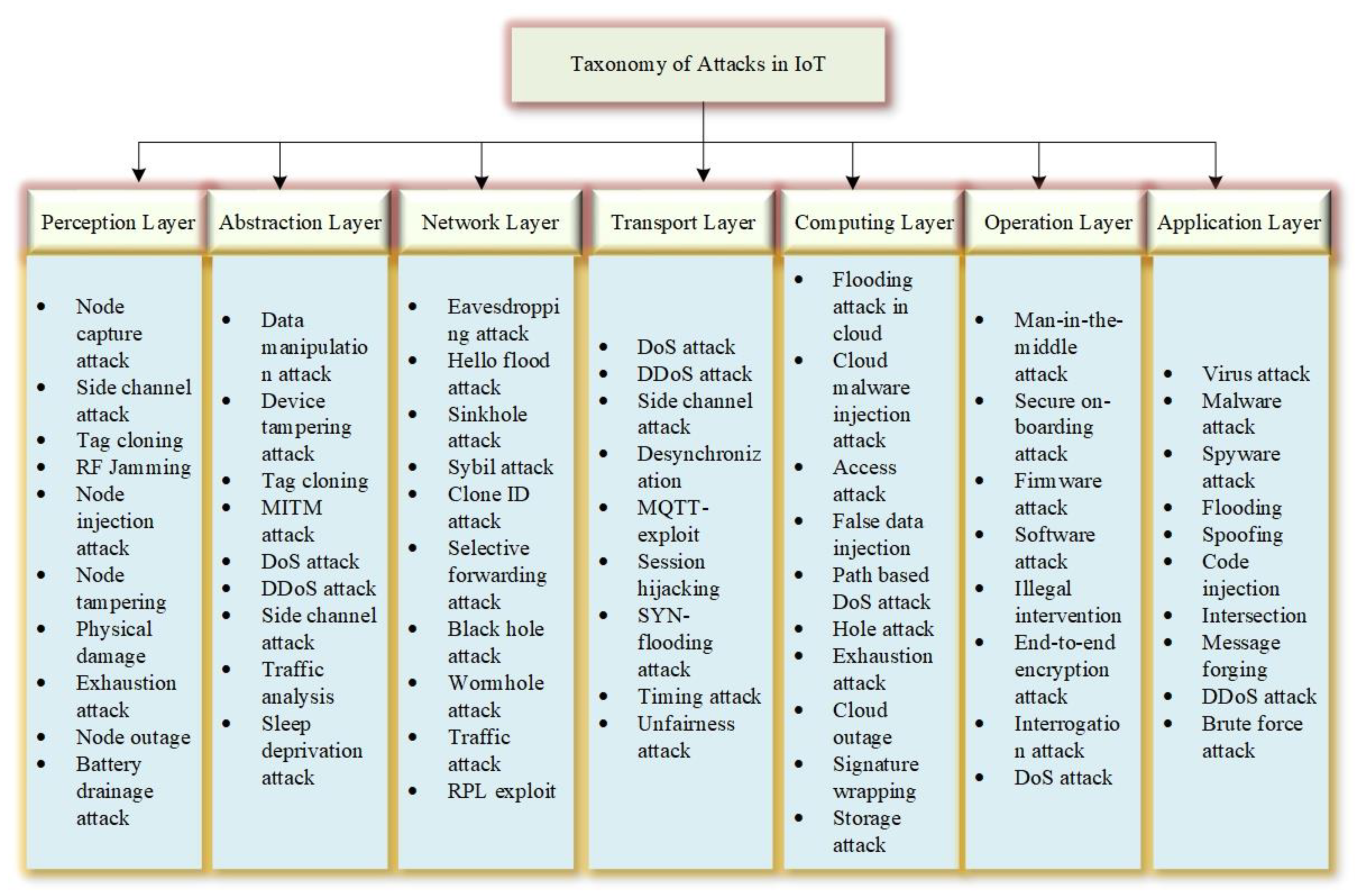
- The multidimensional taxonomy of threats and attacks in IoT is proposed with impact assessment on its architecture.
- With respect to communication standards and protocols, the threats and attacks corresponding to each of the proposed architectures, i.e., three-layer, five-layer, and seven-layer IoT architectures, are comprehensively reviewed.
- The potential use of ubiquitous technologies, such as BC, FC, EC, and ML, are presented in the context of security enhancement in IoT.
- The research gap, challenges, and some open problems are presented which can be further explored in the IoT paradigm.
3. Elementary Overview of an IoT System
3.1. IoT Devices, Controllers, and Peripherals
3.2. Gateways and Networks
- Facilitating contact with non-Internet linked or legacy devices.
- Data pre-processing, cleansing, filtering, and optimization.
- Data caching, buffering, and streaming.
- Aggregation of data.
- M2M (Machine-to-Machine) communications.
- Networking features and live data hosting.
- Data visualization and analytics.
- Security feature in data exchange.
- Physical Attack: Unauthorized access to gateway hardware or any unaccredited geographical movement.
- Software Attack: Trojan, Worms, virus, jamming, denial of services.
- Network Attack: Node capture, node subversion, node malfunctioning, message corruption, routing attacks, false node.
- Cryptanalysis Attack: Known-plaintext, Man-In-The-Middle-Attack (MITM), ciphertext only, chosen plaintext.
- Side Channel Attack: Micro probing, reverse engineering.
3.3. Cloud Servers and Control Device
4. IoT Reference Model and Protocol Stack
4.1. Three-Layer Reference Model
- Perception Layer: The perception layer is also often known as the physical layer. The layer deals with the various sensors affixed to the IoT devices. Sensor nodes, RFID Sensors, and other sensory technologies are provided by this layer [88]. The sensors in this layer gather data and transfer it to the network layer. Physical quantities such as temperature, humidity, light intensity, sound, etc., are measured by the sensors, which are pre-processed before they send the information to the network layer. The perception layer is primarily responsible for the data collection and its transmission to the network layer. Devices linked in short-range networks can collaborate with the help of the perception layer.
- Network Layer: The network layer is made up of network components that enable communication to take place. It facilitates the data exchanged between the IoT devices. The network layer serves as a connection between the perception layer and the application layer. It is in charge of IoT networking, which involves connecting and translating IoT devices over a network. The network layer’s job is to route and relay the data obtained by the perception layer over the network. The data are sent over the Internet to other computers or IoT hubs. Wi-Fi, Bluetooth, 3G/LTE, Zigbee, Lora, and other network technologies are examples of commonly used network technologies [89].
- Application Layer: The application layer is the topmost layer of the IoT architecture, and it is responsible for accomplishing the final purpose of community service. The application layer collects data from the network layer and uses them to accomplish the ultimate objective of delivering the IoT infrastructure’s intended service. The application layer is liable for offering types of assistance and decides a bunch of conventions for message passing at the application level. The application layer serves as a bridge between applications and end clients, allowing them to communicate. It defines the allocation of resources and computation in data production, processing, screening, and feature selection. The application layer is a client-driven layer that performs various tasks for the clients and offers customized assistance as per a client’s pertinent requirements [90]. This IoT layer brings together the industries to create high-level intelligent application solutions such as disaster monitoring, health monitoring, translation, fortune, medical, environmental monitoring, and global management for all intelligent applications.
4.2. Five-Layer Reference Model
- Service layer: This layer envisages facilitating the use of heterogeneous IoT devices, tools, testbeds, platforms, etc., for a wide range of IoT applications. The processing of the data from the network layers is also its responsibility. Generally, the data at this layer are voluminous, for which processing, computing, and analyzing are some key challenges to be handled by this layer.
- Operation layer: This is an important layer, especially from the business point of view in IoT. The supervision of services offered by IoT, creating business models, visualization of the data, decision-making, etc., are some of the key responsibilities of this layer. Ensuring QoS across all layers is one of the vital responsibilities associated with this layer. This layer is also responsible for real-time monitoring, control, and evaluation of various application-specific parameters in an IoT environment.
- Application layer: This layer is primarily responsible for providing service to the end-users related to particular applications. There exists a wide range of applications envisaged using IoT, viz., smart city, smart home, smart agriculture, industry 4.0, healthcare, environmental monitoring, etc. This is the layer through which end users usually interact and pay for the service provided to them.
4.3. Seven-Layer Reference Model
- Perception layer: This is the first level which consists of different IoT sensing and actuating devices such as sensors, actuators, RFID tags, controllers, etc. Being the first layer, the devices at this layer must adhere to the security protocols and standards to ensure they mitigate security threats to other layers originating from the perception layer.
- Abstraction layer: The IoT is based on a large and diverse set of items, each with specialized functionalities accessible through its dialect. Thus, this layer envisages harmonizing the potentials of other devices by providing a common language, protocol, and standard-based solutions.
- Network layer: This layer is responsible for providing various networking-related solutions to IoT devices. Routing, forwarding, security, etc., are some of the key responsibilities of this layer.
- Transport layer: This layer is responsible for transmitting the data from one service to other services within the application. The security at the transport layer is one of the key responsibilities in IoT in addition to the QoS.
- Computing layer: Voluminous data are generated and shared in IoT-based applications. The computing, processing, and analysis of such voluminous data is very cumbersome in general. Thus, this layer is associated to deal with such challenges in IoT. The integration of several burgeoning technologies such as cloud computing, big data, FC, EC, deep learning, machine learning, etc., is seen as promising at this layer for improving performance and security in IoT-based applications.
- Operation layer: This is an important layer, especially from the business point of view in IoT. The supervision of services offered by IoT, creating business models, visualization of the data, decision-making, etc., are some of the key responsibilities of this layer. Ensuring QoS in all layers is one of the vital responsibilities associated with this layer. This layer is also responsible for real-time monitoring, control, and evaluation of various application-specific parameters in an IoT environment.
- Application layer: This layer is primarily responsible for providing service to the end-users related to particular applications. There exists a wide range of applications envisaged using IoT, viz., smart city, smart home, smart agriculture, industry 4.0, healthcare, environmental monitoring, etc. This is the layer through which end users usually interact and pay for the service provided to them.
4.4. IoT Protocols and Standards
- CoAP: CoAP stands for Constrained Framework Protocol. COAP is a transfer protocol similar to HTTP, but it is designed to help devices with limited resources communicate [95]. This protocol is used to communicate between low-resource IoT devices and high-resource Internet-connected devices. CoAP is a binary protocol that communicates using UDP. The semantics of CoAP are designed to be very similar to those of HTTP [96]. It has less data overhead because it is a binary protocol, and because it uses UDP, it has more flexibility in communication models and can minimize latency. One of the advantages of using HTTP semantics on top of CoAP UDP rather than HTTP TCP is that a computer can easily communicate with the cloud and other devices on the local network using the same protocol language. One of the benefits of using HTTP semantics on top of CoAP UDP rather than HTTP TCP is that a machine can communicate with the cloud and other local network devices using the same protocol language [97].
- mDNS: Multicast DNS (mDNS) is having responsibility similar to the Domain Name Space (DNS) protocol in TCP/IP. This is responsible for mapping IP addresses and names among IoT devices. Since mDNS can be used without extra configuration or memory locally, it is quite flexible with speedy response [98].
- RPL: It is an abbreviation of routing protocols for low power and noisy network (RPL). It was established to assist the creation of a robust topology across lossy lines to provide minimal routing needs [99]. The point-to-multipoint, multipoint-to-point, and point-to-point traffic models are all supported by this routing protocol [100].
- 6LoWPAN: 6LoWPAN is an abbreviated form of IPv6 over Low power Wireless Personal Area. 6LoWPAN is a low-power wireless mesh network with individual IPv6 addresses for each node [101]. This enables the node to link to the Internet directly using open standards. Data are sent as packets in the form of a wireless sensor network. The protocol is used for transporting IPv6 packet data over IEEE 802.15.4 and other networks. It offers end-to-end IPv6 access, allowing it to provide direct connectivity to a wide range of networks, including the Internet. The 6LoWPAN protocol includes a layer that aids in the adaptation of resource-constrained devices to the IP environment [102]. This allows Internet access to sensor devices. Under the low power wide area network, LoRa (Long Range) and SigFox are some of the new emerging technologies.
- IEEE 802.15.4: The IEEE 802.15.4 protocol specifies a Medium Access Control (MAC) sublayer and a physical layer (PHY) for low-rate wireless personal area networks (LR-WPAN). Some of the notable characteristics are low data rate, low cost, low power consumption, and high throughput [103]. It also provides excellent security features and can support many smart IoT devices over the networks. However, the QoS feature is not guaranteed by this protocol.
- LTE-A: It stands for Long Term Evolution- Advanced (LTE-A) and it is based on cellular communication technology. Due to the utilization of sprawling existing infrastructure, it is a cost-effective and most affordable solution for IoT. Its performance is better than some other cellular-based technology in the IoT paradigm [104].
- IEEE 1905.1: The security protocols which are best for traditional Internet-based communication seem to be inappropriate for providing security in the IoT environment. Since resource constraints are among of the prominent challenges in IoT, security protocols must be built in a way that is not resource hungry. IEEE 1905.1 is designed to solve interoperability issues in IoT. Particularly, it envisages integrating heterogenous technologies with the digital home network. Interestingly, with IEEE 1905.1 as an interoperable protocol, IEEE 802.3, IEEE 802.11, IEEE 1901, and MoCA can coexist together in an IoT environment [105].
- UDP: UDP is a connectionless protocol; here, the sender sends data without waiting for the receiver to establish a link. They are connectionless datagrams that allow for the transmission of smaller packets and cycles with less overhead and a faster wake-up time [106].
- EXI: Efficient XML Interchange is abbreviated as EXI. This is an XML representation in a small package. To support XML applications on resource-constrained devices, EXI is described as a technique that uses less bandwidth and improves encoding/decoding efficiency. EXI compression aids in the reduction of document content by creating small tags internally based on the current XML schema, processing level, and context. It assures the tags are optimized for data representation. The document is in binary format, with all of the document’s data tags encoded using event codes. Event codes are binary tags that keep their value only in the EXI stream where they are allocated.
5. IoT Vulnerabilities, Security Threats, and Attacks
5.1. Vulnerability
5.2. Taxonomy of Threats and Attacks in IoT
- Unstructured threats: These are made up mainly of novice people who use the readily available hacking software.
- Structured threats: People aware of system vulnerabilities and can comprehend, build, and exploit code and scripts are known as structured risks.
- Advanced Persistent Threats (APT): A coordinated assault is an example of advanced persistent threats. APT is a sophisticated network attack that seeks to steal data from high-value information in industries such as manufacturing, banking, and national defense [112].
5.3. Security Concern Due to Threats and Attacks at Different Layers
5.3.1. Security Concern at Perception Layer
- Eavesdropping: Attackers can sniff the traffic generated by IoT data flow to gather users’ critical information by setting similar IoT devices.
- Malicious Data Injection: False sensor data injection is a form of attack in which the sensor data used in IoT applications are forged or modified for malicious purposes. False sensor data may be injected into devices by physical access or clandestine use of different networking mediums such as Bluetooth, Wi-Fi, GPS, etc. For instance, a spoof attack in a vehicle equipped with a GPS system. To change the location of the car, the attacker sends a forged GPS signal to the system. This conceals the vehicle’s true location, allowing the attacker to attack the targeted vehicle with any physical attack [113].
- Sybil Attack: The malicious nodes in this can have multiple identities of a genuine node by either impersonating it or with a fake identity through duplication. One such malicious node may have several identities simultaneously or at different instances.
- Disclosure of Critical Information: Sensors used in IoT gadgets can disclose sensitive information such as passwords, secret keys, credit card credentials, and so on. These details may be used to violate user privacy or to build a database for future attacks. One such example of this attack is eavesdropping. It is a kind of attack where a pernicious application records a discussion subtly by misusing sound sensors and extracts data from the discussion. An attacker can save the recorded discussion on a gadget or tune in to the discussion continuously. Soundcomber is one of the current instances of eavesdropping over the receiver of a cell phone. In this model, a pernicious application secretively records when a discussion is initiated from the gadget. Since the recording is carried out behind the scenes, a client is completely unaware of the chronicle [114].

- Side-Channel Attacks: The assailant gathers information and performs the reverse engineering process to collect the encryption credentials of an IoT device while the encryption process is under way. This information cannot be collected from plaintext or ciphertext during the encryption process, but from the encryption devices. Side-channel attacks the use of certain or all data to acquire the key the device uses. Some instances of such attacks include timing attacks, power or failure analysis, and electromagnetic attacks. The opponent uses data leaks and collects block cipher keys. In the event of the attacks, an intrusion prevention system such as Boolean masking can be directed.
- Malicious Data Injection: Attackers take advantage of flaws in communication protocols to insert data into the network [115]. The intruder will tamper with the information required to control the device if the protocol does not verify the integrity of the data. The injection attack may result in code execution or system control from afar.
- Node cloning: In most cases, IoT devices such as sensor nodes and CCTV cameras are developed without hardware defects, given the lack of standardization of the IoT device design. Therefore, for unauthorized purposes, these devices can be easily forged and replicated. This is also known as the cloning of nodes. It can take place in either of the two phases, i.e., production and during operations. An internal attacker can replace an original device with an unauthorized, pre-programmed object in the former case. A node can be captured and cloned during the operational phase. Capturing nodes could further remove security parameters and substitute firmware replacement attacks.
- Exhaustion attack: Jamming or DoS attacks that have been mentioned before could lead to attacks of exhaustion. In particular, energy consumption can affect the battery-operated devices if an assailant attacks the network continuously. Repeated retransmission attempts could cause collisions with IoT MAC protocols leading to high-energy depletion. Exhaustion is a dot attack and is connected with deactivation assaults, reducing the size of the network and removing nodes permanently from the network.
5.3.2. Security Concern at Abstraction Layer
- Illegal access: IoT equipment often operates without any physical protection in an untrusted environment, such as traffic light sensors, environmentally friendly sensors, agricultural sensors, smart city sensors, and much more. Problems such as illegal access and malicious change of data may arise during the processing of sensitive data.
- MITM: Man-in-the-Middle (MITM) is a system that listens in on traffic between a smart device and a gateway [116]. All traffic will be routed via the attacker’s computer using the ARP poisoning technique. This attack can be avoided if the attacker is unable to see the traffic in progress. As a result, encryption is required in the protocol [117].
- Spoofing: To initiate a spoofing attack, an attacker can mimic a node. Due to its manner of assault, a spoofing attack is one of the high-risk attacks. A transmission could be recorded using a compatible portable reader. Because the attacker is impersonating the node, the retransmission may appear to be coming from a legitimate node. This threat could exist in all three layers of the IoT. Spoofing attacks that impersonate nodes are classified as authentication attacks, and they also breach the privacy principle.
- Threat to communication protocols: The fact that most current wireless communication protocols adhere to the OSI layered protocol architecture and the physical layer encryption is not reinforced with additional security methods in the upper layers of the communication presents additional issues in IoT/CPS security design. Cellular technologies such as UMTS, GSM, and LTE, on the other hand, have their own set of security challenges. Because radio baseband stacks are implemented openly, mobile networks are vulnerable to hacking and cyber-attacks. Furthermore, aggressive attackers can use “IMSI Catching” to compromise GSM and UMTS networks.
- Tag cloning: An opponent can readily clone RFID tags by gaining direct access to a device or via reverse engineering to obtain the essential information. A tag cloning attack was described in the literature, in which an RFID scanner was unable to discriminate between legitimate and compromised tags.
- Denial-of-Service (DoS): It is a type of attack in which a device or application is maliciously denied normal operation. DoS attacks can be active attacks where an application or task is strongly denied or where passive attacks can stop another ongoing task on the device by attacking one application [118].
- DDoS: Any IoT device, network, or software program could be shut down by a distributed denial-of-service (DoS) attack, rendering the service inaccessible to its consumers. These attacks can take many different shapes. One method of attack is to generate a large amount of network traffic and send a massive request to the victim. The main goal of this attack is to make the target consumers’ devices, software, network services, and resources unavailable. Furthermore, the attacker may be able to obtain sensitive information from users. DDoS attacks are more harmful than DoS attacks, which use many attacking platforms to infiltrate one or more systems
- Traffic analysis: For attackers, a network’s traffic pattern may be as useful as the substance of data packets. Analyzing traffic patterns can provide valuable information about the networking topology. In WSNs, the sink nodes closer to the base station generate more transmissions than the other nodes because they relay more packets than the nodes further away. Similarly, clustering is a key scaling strategy in WSNs, and cluster heads are busier than the rest of the network’s nodes. For adversaries, detection of the base station, nearby nodes, or cluster heads may be very beneficial since a denial-of-service attack or packet eavesdropping against these nodes might be very useful
- Sleep deprivation: The denial of a sleep attack on a battery-powered device will result in energy depletion. Collision attacks or repetitive handshaking, i.e., repeatedly shaking hands, can be used to carry out this attack. Request to Send (RTS) and Clear to Send (CTS) manipulate flow control signals, stopping the node from entering the stage of sleep.
5.3.3. Security Concern at Network Layer
- Hello flood: Message flooding is amongst the biggest network layer threats. By sending multiple route establishment requests to a network or node. The nodes in the network interpret a hello message as coming from within and mark it as a communication route.
- Sinkhole: By using this approach, an attacker compromises a network’s central node and overrides it in a bid to render it unavailable. An attack that uses sinkholes is more likely to cause a major incident than a tempering attack, which involves a few affected nodes. As a result of sinkhole attacks, the whole infrastructure base could be controlled.
- Blackhole: If the malicious node experiences a Blackhole attack, it will drop all packets encountered and the entire network will be affected. Since it absorbs all routing data, it is considered a high-impact attack. By flooding malicious routing information, an intruder tries to hijack the most efficient route to a destination. Upon transmission through the malicious route, the source node continues to send packets, and the attacker drops all packets, preventing any traffic from being forwarded to the destination.
- Traffic Analysis: The attacker analyses the traffic and saves a copy for later use in this attack. As a result, the interface can be managed using the traffic that was previously communicating with the gateway. The traffic or data that have been checked are reused in a different context [119].
- Wormhole: This network attack would intercept traffic in one location and redirect it to another. As a result, it causes network congestion and efficiency problems.
- Selective forwarding: An attacker launches an SF attack by entering a network and dropping packets. Some packets are dropped casually, while others are selectively forwarded. Consequently, packet dropping can be difficult to figure out in IoT networks due to their lossy nature. As a consequence, the entire network may suffer bandwidth degradation and delay.
- RPL exploit: The IoT is made up of devices with limited resources, such as battery power, memory, and computational power. RPL is a new network layer routing protocol developed for these types of networks (routing protocol for low power and lossy networks). RPL is a lightweight routing protocol that does not contain all of the features of typical routing protocols. RPL was developed specifically for data sinks (multi-point to point communications) and has lately been adopted by the IoT. In such attacks, spiteful nodes can seek to redirect paths when data are transferred. Sinkhole attacks are a kind of routing attack in which an opponent advertises and hire a node to drive traffic [120]. Wormhole attacks can also pose a serious threat to IoT systems if associated with other attacks such as sinkhole attacks [121]. A wormhole is an out-of-band link that allows easy packet transfer between two nodes. An attacker will try to circumvent the basic security protocols in an IoT application by creating a wormhole between a compromised node and a computer on the Internet.
5.3.4. Security Concern at Transport Layer
- Desynchronization: De-synchronizing the transmissions between two nodes allows an attacker to break actual links between them. Trying to send fabricated messages to both sides of communication, such as false flag types of messages, is an example of this type of attack. By forcing them to lose their synchronization, they will lose their ability to communicate.
- Session hijacking: In session hijacking, an attacker steals the session ID and pretends to be the legitimate user to take over a user’s online session. The attacker can spoof the user’s session ID and do anything the authorized user can do on the network once the attacker obtains it.
5.3.5. Security Concern at Computing Layer
- Malicious Attack: As workers in the company download untrustworthy malicious software programs from the Internet, there is a good chance that the machine will be hacked. The malware would spread across the internal network, putting the whole company under its influence. The attacker would use the compromised machine to hack the IoT system connected to the network. As a result, it may result in economic loss and abasement of the company’s reputation.
- SQL injection: SQL injection is a web security flaw that permits an attacker to meddle with a web application’s database queries. It permits an attacker to access the information that they would not usually be able to reclaim. This may incorporate information belonging to different clients or whatever other information the application can access. An attacker may alter or erase these data, resulting in the application’s content being permanently altered. In certain circumstances, an attacker can improvise a SQL injection attack to alter the basic server or other back-end foundation or carry out a distributed denial-of-service (DDoS) attack [122].
- Illegal Access: It is one of the major challenges faced by companies providing cloud services. Most enterprise proprietors are unfamiliar with cloud-based technology, which opens them to a variety of data breaks that can affect their tasks. Since cloud computing is built to be simple to use and share, it is difficult for businesses to ensure that data are only available to legal parties. On the off chance that IoT gadgets do not properly configure, the entire network will be damaged. Additionally, companies using cloud-based computing lack complete control over their networks, which requires configuring and protecting their cloud deployments on security controls provided by their cloud service providers (CSP).
- Storage Attack: It can be very difficult to detect and deal with cryptojacking. The main problem here is that hackers will slow down the activity of the device as they use the cloud storage resources, but it will continue to operate. This means it may seem that nothing is malicious and that the machines are probably just struggling with their processing capacity. Many teams in IT experience the symptoms of cryptojacking as an upgrade fault or as a sluggish Internet link, so the real issue is much longer to be resolved.
- Access Attack: Advanced persistent threat is another term for an access attack. An unauthorized individual or adversary gains access to the IoT network in this form of attack. The intruder will remain undetected in the network for an extended period. Rather than causing network harm, the ultimate goal of such a type of attack is to steal valuable information. IoT applications receive and transmit valuable data regularly, making them particularly vulnerable to such attacks.
- Software modification: An IoT device can be compromised by modifying its software or firmware by using physical or remote access to take unauthorized actions. By patching or substituting code, or by making code extensions, the vulnerability can be exploited further.
5.3.6. Security Concern at Operation Layer
- Illegal Intervention: Cloud services are typically provided, monitored, and managed through APIs and software user interfaces. Although, cloud service providers are engaged diligently to improve APIs and interfaces, this boom has additionally extended safety dangers related to them. Cloud specialist organizations utilize a particular structure to give APIs to developers, making their frameworks more endangered against an attacker. In 2018, the social media platform Facebook suffered a security breach that affected around 50 million users due to a flaw [123]. API flaws, particularly when linked to user interfaces, may provide the attacker a direct path to steal employee or client credentials.
- Unauthorized Access: Access control is an approval system that permits authentic clients to acquire information. Multi-client access and simultaneous altering of design systems ought to be vigorous against multi-client access. When numerous clients can alter the designs of different segments of the IoT frameworks, simultaneous execution of setup changes and simultaneous altering of arrangement records effectively leads to temperamental framework status. In IoT applications, access control is important because if access is compromised, the entire IoT framework becomes susceptible to attacks.
5.3.7. Security Concern at Application Layer
- Malicious code: Malicious codes or targeted malware can easily exploit the vulnerabilities of IoT devices through the Internet, which allows hackers to compromise those devices. Further attacks can be launched on other endpoints/networking apps via the infected devices.
- Software Modification: Minor changes can lead to more complicated problems. Unexpected environment changes along with minor framework alterations and system changes may have unanticipated consequences. As the arrangement of framework develops, these results can spread to more concerning issues. If the programming mechanism is not secured, the attacker will be able to reprogram IoT devices remotely. This could result in the IoT network being hacked.
- Data tampering: During an attack of this type, the information on the end device is misrepresented by an attacker. Invaders retrieve data format and type, then insert tamper detection measures and recreate the original data. Due to this, there is considerable doubt about the precision of data collected over the network.
- Cross-site script: XSS (cross-site script) is a technique attackers use to insert malicious code into a website that is otherwise trusted. If an XSS attack is successful, the IoT system will be under the complete influence of the attacker.
- Identity Thefts: IoT systems deal with plenty of personal and sensitive information. Clients will hesitate to enlist their personal information on IoT applications if these applications are helpless against information burglary. Some of the protocols and methodologies used to protect IoT applications from information burglary include data isolation, data encryption, privacy management, user and network authentication, etc.
- Virus attack: The objective of these attacks is to breach the confidentiality of the system. The risk of these attacks is significantly higher for smartphones, sinks, or gateways in IoT networks. Hence, IoT applications must seriously consider mitigating viruses and malware.
- Spyware attack: Installed on IoT devices without consent, spyware is an installation program that collects information. Using this type of attack, attackers are looking to gather sensitive information about users by monitoring their behavior. Signature, behavior, and specification-based techniques are some common approaches to spyware detection.
- Code Injection: Attackers usually use the simplest or easiest way to break into a device or network. If the device is endangered to spiteful scripts and misdirection as a result of inadequate code tests, it will be the first point of entry for an attacker.
- Intersection: System integrity is a critical feature of the IoT framework. When a system’s integrity is compromised, there is a high risk of safety and security threats. High activity stress or irregular process conditions, network or device failures, multiple warnings, executing previously unexecuted error path code or system recovery code, or wrongly executed commands do not cause the system to crash. This necessitates extensive research.
- Brute force attack: A brute force attack involves systematically trying and guessing every possible passphrase or password combination to gain access to the system. Crypto-analysts are ultimately able to identify the correct one which allows them access to the system.
6. Security Goals and Roadmap in IoT
- Confidentiality: Confidentiality is an important security feature in the Internet of Things, but it is not always required, for example, in cases where data are exchanged with the public. In the vast majority of situations and cases, sensitive data must not be disclosed or read by unauthorized persons [180]. Sensitive information about patient data, company information, and possibly military information, as well as security accreditations, should all be kept private from unauthorized users. Confidentiality should be granted such that the information gathered or distributed is safe and only accessible to approved users. Data collected by a computer or a sensor should not be sent to other devices unless they are properly encrypted. To prevent malicious actors from accessing the collected data, only encrypted messages should be sent to neighboring devices. A data encryption system transforms each bit of data into ciphertext, followed by a two-step verification process in which two devices/components permit access only if the authentication test is passed by both the devices, and a biometric verification in which the user is uniquely identifiable and biometric authentication in which the person can be identified by his or her fingerprints.
- Integrity: Integrity should be offered to ensure data validity. Data integrity is critical since data recipients must be able to verify whether data obtained from other devices are authentic. In most cases, integrity is a necessary security property for IoT users to receive reliable services [181]. Different IoT systems have different levels of trustworthiness. As an example, because of data sensitivities, a patient observation framework would have high trustworthiness testing against arbitrary mistakes. It is integrated into the network to protect cybercrimes data in the communication process so that data manipulation cannot be carried out without the danger detected by the device. Two error detection methods are used to ensure data integrity in the inspection and cyclic redundancy search. For continuous data sync for backup purposes, a version control system is used.
- Authentication and authorization: Authenticity is related to credibility, and it means that each system in the network should be able to recognize and authenticate other devices. Since the IoT is made up of so many devices, it is critical to be able to recognize them; otherwise, malicious devices might use spoofing to target IoT networks. Due to the design of IoT settings, the possible communication between the device and device (M2M) is exacerbated by the problem of authentication in IoT connectivity. Different authentication criteria in different systems require different solutions. Some solutions, such as bank card or bank device authentication, require a high level of reliability. However, others will need to be foreign, such as e-Passport, while others will need to be local. Only approved entities (any authenticated entity) can conduct such network operations using the authorization property [182].
- Availability: The primary aim of every IoT protection system is to make data available to users promptly. The consumer should be able to obtain data from the resources right away, not only in usual circumstances but also in emergencies. Firewalls are installed in the network to protect against attacks on services such as denial-of-service attacks, which prevent data from reaching the end-user [183].
- Accountability: Accountability provides redundancy and responsibility for some activities, tasks, and the preparation of the execution of network security policies while designing security strategies to be used in a safe network [184]. Accountability cannot prevent attacks on its own, but it does help ensure that other security measures are functioning properly. Integrity and confidentiality, for example, can be rendered worthless if they are not subjected to transparency. Often, in a disapproved event, an entity’s behavior can also be traced through an accountability system, which can help determine the inside story of what occurred and who was ultimately responsible.
7. Scope of Security Enhancements in IoT with Burgeoning Technologies
7.1. BC for IoT
- To create blocks, a consensus algorithm is used; involved individuals (typically miners) verify the transactions’ coherence and validity.
- A monetary competition exists for block certification and the computation of a new branch, which is based on algorithms such as Proof of Work (PoW) or Proof of Stake (PoS).
- There is no third party to rely on; each individual produces his or her own keys.
- All ledger elements, such as blocks, and transactions are stored in the database.
- BC can be used to store the data from IoT devices: The IoT technologies incorporate a wide range of devices that are all interconnected. This arrangement is additionally associated with the cloud to empower IoT applications to be accessed from anywhere. BC is a promising method for storing and protecting such an enormous amount of data. BC is an apt solution for storing and transmitting data regardless of the layer in an IoT application.
- Terminating the centralized cloud server system: BC boosts the security of IoT frameworks by removing the centralized cloud server and establishing a peer-to-peer network framework. Data pirates are mostly interested in centralized cloud servers. BC enables the distribution of data across all the nodes of the network and encrypts them.
- Forestalling illegal access: Several IoT applications necessitate a lot of contact between different nodes on a regular basis. Since BC communication is based on public and private keys, data can only be accessed by the intended party or node. If an unintended person accesses the data, the content will be nonsensical because it is protected with keys. As a result, the BC data system attempts to address a variety of security problems that IoT applications face.
- A solution for resource-constrained devices: Because of the limited resources, IoT devices are unable to store large ledgers. There have been different works toward this path to work with the assistance of BC. One of the potential solutions for IoT devices to use BC is proxy-based architecture. By setting up the proxy servers, the data can be stored in an encrypted format and the encrypted resources can be downloaded via proxy servers.
- Forestalling spoofing attack: Spoofing is a type of attack where a foreign node enters the IoT ecosystem and tries to emulate the existing nodes to be seen as a member of the original framework. This foreign node can monitor or inject malicious data into the network. The BC technology appears to be a potential solution for preventing such attacks. Each genuine client or gadget is enlisted on BC, and gadgets can undoubtedly recognize and validate each other.
- Forestalling data loss: IoT devices acquire the danger of losing information. There is a possibility that the data are lost by the sender and the recipient due to natural environmental causes. The utilization of BC can forestall such losses as it is impossible to eliminate a block once it is included in the chain.
7.2. FC for IoT
- Incident response services: Some critical applications cannot be stopped completely to resolve malware issues. When the system is running, fog nodes can help with such resolutions. It is possible to program fog nodes to provide incident response services in real time. As soon as the fog nodes detect suspicious data or requests, they can generate a warning flag for the end-user or the IoT system. Using FC, malware can be detected and problems resolved in transit. Some of the real-time services include identity recognition, intrusion detection, access management, etc.
- Resource-constraint issues: IoT devices are typically resource-constrained, which makes them an ideal target for attackers. By damaging edge devices, attackers try to exploit weak points and worm their way in. Fog nodes can support edge devices so those devices will not be attacked. For protection, fog nodes can provide more sophisticated security functions, as well.
- Eavesdropping: Rather than routing the information throughout the network, usage of fog nodes enables communication with only the end-user and fog nodes. Because the network traffic is reduced, there is less opportunity for adversaries to eavesdrop.
- Data transit attacks: Data management and storage are much more efficient when using secure fog nodes instead of IoT devices. Fog nodes provide a greater level of protection for data than end-user devices for storing data.
- Man-in-the-middle attack: A fog serves as a layer of security between the cloud and the end-user. A fog layer stands in between all threats or attacks on IoT systems, and in this layer, unusual activity can be identified and mitigated before it reaches the system.
7.3. EC for IoT
- Data Compliance Issues: Data movement outside of borders is prohibited by many countries due to their restrictive regulatory acts, such as the GDPR (General Data Protection Regulation) of the European Union. Data sovereignty laws can be followed through EC, which keeps the data inside organizations [197]
- Data Breaches: Data are stored and processed entirely within local networks or devices in EC. In this case, no data are transferred from the source to the processor. Therefore, there is no risk of data theft or data breaches since the data are not in transit [198].
- Bandwidth Issues: Most of the data generated by IoT applications are raw and relatively of low value. As well as having a high bandwidth cost, the process of moving all the data to the cloud is also very hard in terms of security. The use of EC can enable data processing to be conducted at the edge nodes rather than sending the data to a cloud service [199].
- Safety issues: Physical safety can be compromised even if there is just a slight delay in responses. In the case of sensors that send all of their data and wait for the cloud to act, it may be too late to prevent injuries or deaths. Therefore, to achieve faster responses, devices can be deployed with EC to examine the abnormalities, process the data, and send them to the data center.
7.4. ML for IoT
- DoS Attack: DoS attacks on IoT or IoT devices are a major concern. A multilayer perceptron (MLP) protocol to secure networks against DoS attacks serves as an approach for preventing such attacks [200]. Pavani, K. et al. proposed to create an MLP to improve the safety of wireless networks through particle swarm optimization and a backpropagation algorithm [201]. ML technologies help increase the accuracy of deductions and secure IoT devices vulnerable to DoS attacks.
- Eavesdropping: Attackers can sweep messages while data are being transmitted. ML techniques such as Q learning-based offloading strategy [202] or Bayesian non-parametric techniques [203] can be used to protect against such attacks. ML techniques such as Q-learn and Dyna-Q can be used to protect devices from eavesdropping, as well. Experimental evaluation and strengthening education of those schemes are presented in [204].
- Digital Fingerprinting: Digital fingerprinting is a promising solution for safe IoT systems and for the end-user to have enough confidence in applications. Digital fingerprints are widely used for smartphones, payments, car and home doors, etc. Digital fingerprinting is a dominant bio-metric identification method thanks to its low cost, reliability, acceptability, and high level of safety [205]. Aside from the advantages of digital fingerprinting, the efficiency of using this technology in IoT is varied, including fingerprint classification, improved image, and functional matching.
8. Open Research Problems
- There is no generic validated architecture of IoT so far, i.e., most of the architectures are either domain-specific or application-specific. Thus, the security enhancement methodology may not fit the most generic architecture.
- The detailed protocols stack and its interoperability are still being explored. Due to immaturity, the exhaustive security aspects for protocols and the standards are far behind the actual realization.
- The amount of abstraction in security, the formal language to be utilized for policy encoding, and contextual IoT features to be considered for optimal usage of software-defined networking-based security mechanisms in a secure IoT framework is still an open problem.
- Given the inherent trade-off between flexibility, performance, and cost, the granularity of protection methods poses an open challenge in the provision of network slices specialized for IoT applications.
- The implementation methods and utilization of software and hardware are critical factors in BC to enhance security in IoT using BC. Being public in nature, the transactions of IoT data are still a problem of security concern that can be revealed to the public in general [238].
- Since FC is an extension to cloud computing, some of the serious concerns of cloud computing such as security and privacy are inherent to the FC, which are being extensively explored in the literature.
- EC poses serious security and privacy concerns since most of the computations are generally performed at the edge devices. However, most of the edge devices are resource-constrained in an IoT system, which may not be able to compute, analyze, and process the data securely.
- There are enormous ML algorithms. The selection of suitable algorithms is of vital importance, because choosing the incorrect algorithm will result in “garbage” output and a loss of effort, effectiveness, and accuracy. Similarly, selecting the incorrect data set will result in “garbage” input and inaccurate results. Thus, the correct data sets and appropriate algorithms are critically important, which can be explored for securing IoT environment using machine learning.
- The systematic review on vulnerabilities of BC, FC, EC, and ML and their mapping with impact on IoT are some of the research problems which can be further explored.
- The optimum resource sharing in FC is another research area that can be explored to avoid the burden on the cloud for processing the voluminous data during heavy traffic conditions.
- Further, the scope of other technologies such as artificial intelligence, big data, etc., must be also analyzed, which were shown to have great potential in IoT-based applications [239].
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Jha, A.V.; Appasani, B.; Ghazali, A.N. Performance Evaluation of Network Layer Routing Protocols on Wireless Sensor Networks. In Proceedings of the 2019 International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 17–19 July 2019; pp. 1862–1865. [Google Scholar] [CrossRef]
- Tiwary, A.; Mahato, M.; Chidar, A.; Chandrol, M.K.; Shrivastava, M.; Tripathi, M. Internet of Things (IoT): Research, architectures and applications. Int. J. Future Revolut. Comput. Sci. Commun. Eng. 2018, 4, 23–27. [Google Scholar]
- González-Zamar, M.D.; Abad-Segura, E.; Vázquez-Cano, E.; López-Meneses, E. IoT Technology Applications-Based Smart Cities: Research Analysis. Electronics 2020, 9, 1246. [Google Scholar] [CrossRef]
- Internet of Things in Healthcare: Applications, Benefits, and Challenges. Available online: https://www.peerbits.com/blog/internet-of-things-healthcare-applications-benefits-and-challenges.html (accessed on 12 April 2021).
- Cvar, N.; Trilar, J.; Kos, A.; Volk, M.; Stojmenova Duh, E. The Use of IoT Technology in Smart Cities and Smart Villages: Similarities, Differences, and Future Prospects. Sensors 2020, 20, 3897. [Google Scholar] [CrossRef] [PubMed]
- Ryan, P.J.; Watson, R.B. Research Challenges for the Internet of Things: What Role Can OR Play? Systems 2017, 5, 24. [Google Scholar] [CrossRef]
- Jha, A.V.; Appasani, B.; Ghazali, A.N.; Pattanayak, P.; Gurjar, D.S.; Kabalci, E.; Mohanta, D.K. Smart grid cyber-physical systems: Communication technologies, standards and challenges. Wirel. Netw. 2021, 27, 2595–2613. [Google Scholar] [CrossRef]
- Jha, A.V.; Mishra, S.K.; Appasani, B.; Ghazali, A.N. Communication Networks for Metropolitan E-Health Applications. IEEE Potentials 2021, 40, 34–42. [Google Scholar] [CrossRef]
- Lin, H.; Bergmann, N.W. IoT Privacy and Security Challenges for Smart Home Environments. Information 2016, 7, 44. [Google Scholar] [CrossRef]
- Rajendran, G.; Nivash, R.S.R.; Parthy, P.P.; Balamurugan, S. Modern security threats in the Internet of Things (IoT): Attacks and Countermeasures. In Proceedings of the International Carnahan Conference on Security Technology (ICCST), Chennai, India, 1–3 October 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Chen, L.; Thombre, S.; Järvinen, K.; Lohan, E.S.; Alén-Savikko, A.; Leppäkoski, H.; Bhuiyan, M.Z.H.; Bu-Pasha, S.; Ferrara, G.N.; Honkala, S.; et al. Robustness, security and privacy in location-based services for future IoT: A survey. IEEE Access 2017, 5, 8956–8977. [Google Scholar] [CrossRef]
- Shin, H.; Lee, H.K.; Cha, H.Y.; Heo, S.W.; Kim, H. IoT security issues and light weight block cipher. In Proceedings of the International Conference on Artificial Intelligence in Information and Communication (ICAIIC), Okinawa, Japan, 11–13 February 2019; pp. 381–384. [Google Scholar]
- Gamundani, A.M. An impact review on internet of things attacks. In Proceedings of the International Conference on Emerging Trends in Networks and Computer Communications (ETNCC), Windhoek, Namibia, 17–20 May 2015; pp. 114–118. [Google Scholar] [CrossRef]
- Kumar, N.; Madhuri, J.; Channe Gowda, M. Review on security and privacy concerns in Internet of Things. In Proceedings of the International Conference on IoT and Application (ICIOT), Nagapattinam, India, 19–20 May 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Abomhara, M.; Køien, G.M. Cyber security and the internet of things: Vulnerabilities, threats, intruders and attacks. J. Cyber Secur. Mobil. 2015, 4, 65–88. [Google Scholar] [CrossRef]
- Kozlov, D.; Veijalainen, J.; Ali, Y. Security and privacy threats in IoT architectures. BODYNETS 2012, 256–262. [Google Scholar] [CrossRef]
- Lee, E.; Seo, Y.D.; Oh, S.R.; Kim, Y.G. A Survey on Standards for Interoperability and Security in the Internet of Things. IEEE Commun. Surv. Tutor. 2021, 23, 1020–1047. [Google Scholar] [CrossRef]
- Abosata, N.; Al-Rubaye, S.; Inalhan, G.; Emmanouilidis, C. Internet of Things for System Integrity: A Comprehensive Survey on Security, Attacks and Countermeasures for Industrial Applications. Sensors 2021, 21, 3654. [Google Scholar] [CrossRef]
- Mann, P.; Tyagi, N.; Gautam, S.; Rana, A. Classification of Various Types of Attacks in IoT Environment. In Proceedings of the 12th International Conference on Computational Intelligence and Communication Networks (CICN), Bhimtal, India, 3 November 2020; pp. 346–350. [Google Scholar] [CrossRef]
- Ogonji, M.M.; Okeyo, G.; Wafula, J.M. A survey on privacy and security of Internet of Things. Comput. Sci. Rev. 2020, 38, 10031. [Google Scholar] [CrossRef]
- Zarpelão, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Hajiheidari, S.; Wakil, K.; Badri, M.; Navimipour, N.J. Intrusion Detection Systems in the Internet of Things: A Comprehensive Investigation. Comput. Netw. 2019, 160, 165–191. [Google Scholar] [CrossRef]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef]
- Sun, L.; Du, Q. A Review of Physical Layer Security Techniques for Internet of Things: Challenges and Solutions. Entropy 2018, 20, 730. [Google Scholar] [CrossRef]
- Elazhary, H. Internet of Things (IoT), mobile cloud, cloudlet, mobile IoT, IoT cloud, fog, mobile edge, and edge emerging computing paradigms: Disambiguation and research directions. J. Netw. Comput. Appl. 2019, 128, 105–140. [Google Scholar] [CrossRef]
- Taylor, P.J.; Dargahi, T.; Dehghantanha, A.; Parizi, R.M.; Choo, K.K.R. A systematic literature review of blockchain cyber security. Digit. Commun. Netw. 2020, 6, 147–156. [Google Scholar] [CrossRef]
- Memon, R.A.; Li, J.P.; Ahmed, J.; Nazeer, M.I.; Ismail, M.; Ali, K. Cloud-based vs. blockchain-based IoT: A comparative survey and way forward. Front. Inform. Technol. Electron. Eng. 2020, 21, 563–586. [Google Scholar] [CrossRef]
- Tran, N.K.; Babar, M.A.; Boan, J. Integrating blockchain and Internet of Things systems: A systematic review on objectives and designs. J. Netw. Comput. Appl. 2020, 173, 102844. [Google Scholar] [CrossRef]
- Fersi, G. Fog computing and Internet of Things in one building block: A survey and an overview of interacting technologies. Cluster Comput. 2021, 1–31. [Google Scholar] [CrossRef]
- Atlam, H.F.; Walters, R.J.; Wills, G.B. Fog Computing and the Internet of Things: A Review. Big Data Cogn. Comput. 2018, 2, 10. [Google Scholar] [CrossRef]
- Hamdan, S.; Ayyash, M.; Almajali, S. Edge-Computing Architectures for Internet of Things Applications: A Survey. Sensors 2020, 20, 6441. [Google Scholar] [CrossRef]
- Capra, M.; Peloso, R.; Masera, G.; Ruo Roch, M.; Martina, M. Edge Computing: A Survey on the Hardware Requirements in the Internet of Things World. Future Internet 2019, 11, 100. [Google Scholar] [CrossRef]
- Ashouri, M.; Lorig, F.; Davidsson, P.; Spalazzese, R. Edge Computing Simulators for IoT System Design: An Analysis of Qualities and Metrics. Future Internet 2019, 11, 235. [Google Scholar] [CrossRef]
- Amiri-Zarandi, M.; Dara, R.A.; Fraser, E. A survey of machine learning-based solutions to protect privacy in the Internet of Things. Comput. Secur. 2020, 96, 101921. [Google Scholar] [CrossRef]
- Adnan, A.; Muhammed, A.; Abd Ghani, A.A.; Abdullah, A.; Hakim, F. An Intrusion Detection System for the Internet of Things Based on Machine Learning: Review and Challenges. Symmetry 2021, 13, 1011. [Google Scholar] [CrossRef]
- Alwarafy, A.; Al-Thelaya, K.A.; Abdallah, M.; Schneider, J.; Hamdi, M. A Survey on Security and Privacy Issues in Edge-Computing-Assisted Internet of Things. IEEE Internet Things J. 2020, 8, 4004–4022. [Google Scholar] [CrossRef]
- Qiu, J.; Tian, Z.; Du, C.; Zuo, Q.; Su, S.; Fang, B. A survey on access control in the age of internet of things. IEEE Internet Things J. 2020, 7, 4682–4696. [Google Scholar] [CrossRef]
- Parmar, M.S.; Shah, P.P. Uplifting Blockchain Technology for Data Provenance in Supply Chain. Int. J. Adv. Sci. Technol. 2020, 29, 5922–5938. [Google Scholar] [CrossRef]
- Granjal, J.; Monteiro, E.; Silva, J.S. Security for the internet of things: A survey of existing protocols and open research issues. IEEE Commun. Surv. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Derdour, M.; Mukherjee, M.; Derhab, A.; Maglaras, L.; Janicke, H. Blockchain technologies for the internet of things: Research issues and challenges. IEEE Internet Things J. 2018, 6, 2188–2204. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A survey on security and privacy issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A survey on internet of things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Malik, M.; Dutta, M.; Granjal, J. A survey of key bootstrapping protocols based on public key cryptography in the Internet of Things. IEEE Access 2019, 7, 27443–27464. [Google Scholar] [CrossRef]
- Alshehri, F.; Muhammad, G. A comprehensive survey of the Internet of Things (IoT) and AI-based smart healthcare. IEEE Access 2021, 9, 3660–3678. [Google Scholar] [CrossRef]
- Stoyanova, M.; Nikoloudakis, Y.; Panagiotakis, S.; Pallis, E.; Markakis, E.K. A survey on the internet of things (IoT) forensics: Challenges, approaches, and open issues. IEEE Commun. Surv. Tutor. 2020, 22, 1191–1221. [Google Scholar] [CrossRef]
- Viriyasitavat, W.; Da Xu, L.; Bi, Z.; Hoonsopon, D. Blockchain technology for applications in internet of things—mapping from system design perspective. IEEE Internet Things J. 2019, 6, 8155–8168. [Google Scholar] [CrossRef]
- Butun, I.; Österberg, P.; Song, H. Security of the Internet of Things: Vulnerabilities, attacks, and countermeasures. IEEE Commun. Surv. Tutor. 2019, 22, 616–644. [Google Scholar] [CrossRef]
- Cha, S.C.; Hsu, T.Y.; Xiang, Y.; Yeh, K.H. Privacy enhancing technologies in the Internet of Things: Perspectives and challenges. IEEE Internet Things J. 2018, 6, 2159–2187. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A survey of machine and deep learning methods for internet of things (IoT) security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- Mosenia, A.; Jha, N.K. A comprehensive study of security of internet-of-things. IEEE Trans. Emerg. Top. Comput. 2016, 5, 586–602. [Google Scholar] [CrossRef]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT security: An exhaustive survey on IoT vulnerabilities and a first empirical look on Internet-scale IoT exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Integration of blockchain and cloud of things: Architecture, applications and challenges. IEEE Commun. Surv. Tutor. 2020, 22, 2521–2549. [Google Scholar] [CrossRef]
- Serror, M.; Hack, S.; Henze, M.; Schuba, M.; Wehrle, K. Challenges and opportunities in securing the industrial internet of things. IEEE Trans. Ind. Inform. 2020, 17, 2985–2996. [Google Scholar] [CrossRef]
- Ngu, A.H.; Gutierrez, M.; Metsis, V.; Nepal, S.; Sheng, Q.Z. IoT middleware: A survey on issues and enabling technologies. IEEE Internet Things J. 2016, 4, 1–20. [Google Scholar] [CrossRef]
- Makhdoom, I.; Abolhasan, M.; Lipman, J.; Liu, R.P.; Ni, W. Anatomy of threats to the internet of things. IEEE Commun. Surv. Tutor. 2018, 21, 1636–1675. [Google Scholar] [CrossRef]
- Qiu, T.; Chi, J.; Zhou, X.; Ning, Z.; Atiquzzaman, M.; Wu, D.O. Edge computing in industrial internet of things: Architecture, advances and challenges. IEEE Commun. Surv. Tutor. 2020, 22, 2462–2488. [Google Scholar] [CrossRef]
- Hamad, S.A.; Sheng, Q.Z.; Zhang, W.E.; Nepal, S. Realizing an internet of secure things: A survey on issues and enabling technologies. IEEE Commun. Surv. Tutor. 2020, 22, 1372–1391. [Google Scholar] [CrossRef]
- Ali, M.S.; Vecchio, M.; Pincheira, M.; Dolui, K.; Antonelli, F.; Rehmani, M.H. Applications of blockchains in the Internet of Things: A comprehensive survey. IEEE Commun. Surv. Tutor. 2018, 21, 1676–1717. [Google Scholar] [CrossRef]
- Meneghello, F.; Calore, M.; Zucchetto, D.; Polese, M.; Zanella, A. IoT: Internet of threats? A survey of practical security vulnerabilities in real IoT devices. IEEE Internet Things J. 2019, 6, 8182–8201. [Google Scholar] [CrossRef]
- Chaabouni, N.; Mosbah, M.; Zemmari, A.; Sauvignac, C.; Faruki, P. Network intrusion detection for IoT security based on learning techniques. IEEE Commun. Surv. Tutor. 2019, 21, 2671–2701. [Google Scholar] [CrossRef]
- Yu, W.; Liang, F.; He, X.; Hatcher, W.G.; Lu, C.; Lin, J.; Yang, X. A survey on the edge computing for the Internet of Things. IEEE Access 2017, 6, 6900–6919. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, K.; Lin, X.; Shen, X. Securing fog computing for internet of things applications: Challenges and solutions. IEEE Commun. Surv. Tutor. 2017, 20, 601–628. [Google Scholar] [CrossRef]
- Restuccia, F.; D’Oro, S.; Melodia, T. Securing the internet of things in the age of machine learning and software-defined networking. IEEE Internet Things J. 2018, 5, 4829–4842. [Google Scholar] [CrossRef]
- Omoniwa, B.; Hussain, R.; Javed, M.A.; Bouk, S.H.; Malik, S.A. Fog/edge computing-based IoT (FECIoT): Architecture, applications, and research issues. IEEE Internet Things J. 2018, 6, 4118–4149. [Google Scholar] [CrossRef]
- Khanam, S.; Ahmedy, I.B.; Idris, M.Y.I.; Jaward, M.H.; Sabri, A.Q.B.M. A survey of security challenges, attacks taxonomy and advanced countermeasures in the internet of things. IEEE Access 2020, 8, 219709–219743. [Google Scholar] [CrossRef]
- Alotaibi, B. Utilizing blockchain to overcome cyber security concerns in the internet of things: A review. IEEE Sens. J. 2019, 19, 10953–10971. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Hussain, F.; Hussain, R.; Hassan, S.A.; Hossain, E. Machine learning in IoT security: Current solutions and future challenges. IEEE Commun. Surv. Tutor. 2020, 22, 1686–1721. [Google Scholar] [CrossRef]
- Benkhelifa, E.; Welsh, T.; Hamouda, W. A Critical Review of Practices and Challenges in Intrusion Detection Systems for IoT: Toward Universal and Resilient Systems. IEEE Commun. Surv. Tutor. 2018, 20, 3496–3509. [Google Scholar] [CrossRef]
- Sengupta, J.; Ruj, S.; Bit, S.D. A Comprehensive Survey on Attacks, Security Issues and Blockchain Solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481. [Google Scholar] [CrossRef]
- Yugha, R.; Chithra, S. A survey on technologies and security protocols: Reference for future generation IoT. J. Netw. Comput. Appl. 2020, 169, 102763. [Google Scholar] [CrossRef]
- Bhoyar, P.; Sahare, P.; Dhok, S.B.; Deshmukh, R.B. Communication technologies and security challenges for internet of things: A comprehensive review. AEU-Int. J. Electron. Commun. 2019, 99, 81–99. [Google Scholar] [CrossRef]
- Bellavista, P.; Berrocal, J.; Corradi, A.; Das, S.K.; Foschini, L.; Zanni, A. A survey on fog computing for the Internet of Things. Pervasive Mob. Comput. 2019, 52, 71–99. [Google Scholar] [CrossRef]
- Peña-López, I. ITU Internet Report 2005: The Internet of Things. Available online: https://www.comminit.com/global/content/itu-internet-reports-2005-internet-things (accessed on 12 April 2021).
- Sikder, A.K.; Petracca, G.; Aksu, H.; Jaeger, T.; Uluagac, A.S. A survey on sensor-based threats to internet-of-things (IoT) devices and applications. arXiv 2018, arXiv:1802.02041v1. [Google Scholar]
- Hongsong, C.; Zhongchuan, F.; Dongyan, Z. Security and trust research in m2m system. In Proceedings of the 2011 IEEE International Conference on Vehicular Electronics and Safety, Beijing, China, 10–12 July 2011; pp. 286–290. [Google Scholar] [CrossRef]
- Kumar, S.A.; Vealey, T.; Srivastava, H. Security in internet of things: Challenges, solutions and future directions. In Proceedings of the 49th Hawaii International Conference on System Sciences (HICSS), Koloa, HI, USA, 5–8 January 2016; pp. 5772–5781. [Google Scholar] [CrossRef]
- Lee, S.K.; Bae, M.; Kim, H. Future of IoT networks: A survey. Appl. Sci. 2017, 7, 1072. [Google Scholar] [CrossRef]
- Chen, H.; Jia, X.; Li, H. A Brief Introduction to IoT Gateway. In Proceedings of the IET International Conference on Communication Technology and Application (ICCTA), Beijing, China, 14–16 October 2011; pp. 1–4. [Google Scholar] [CrossRef]
- Tan, H.; Tsudik, G.; Jha, S. MTRA: Multi-Tier randomized remote attestation in IoT networks. Comput. Secur. 2019, 81, 78–93. [Google Scholar] [CrossRef]
- Internet of Things Challenges in Storage and Data. Available online: https://www.computerweekly.com/news/252450705/Internet-of-things-challenges-in-storage-and-data (accessed on 25 April 2021).
- 12 Benefits of Cloud Computing. Available online: https://www.salesforce.com/in/products/platform/best-practices/benefits-of-cloud-computing/ (accessed on 25 April 2021).
- Li, X.; Wang, Q.; Lan, X.; Chen, X.; Zhang, N.; Chen, D. Enhancing Cloud-Based IoT Security Through Trustworthy Cloud Service: An Integration of Security and Reputation Approach. IEEE Access 2019, 7, 9368–9383. [Google Scholar] [CrossRef]
- Kepçeoğlu, B.; Murzaeva, A.; Demirci, S. Performing energy consuming attacks on IoT devices. In Proceedings of the 27th Telecommunications Forum (TELFOR), Belgrade, Serbia, 26–27 November 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Bilal, M. A Review of Internet of Things Architecture, Technologies and Analysis Smartphone-based Attacks Against 3D printers. arXiv 2017, arXiv:1708.04560. Available online: https://arxiv.org/abs/1708.04560 (accessed on 25 April 2021).
- Dodig, I.; Cafuta, D.; Kramberger, T.; Cesar, I. A Novel Software Architecture Solution with a Focus on Long-Term IoT Device Security Support. Appl. Sci. 2021, 11, 4955. [Google Scholar] [CrossRef]
- Capella, J.V.; Campelo, J.C.; Bonastre, A.; Ors, R. A Reference Model for Monitoring IoT WSN-Based Applications. Sensors 2016, 16, 1816. [Google Scholar] [CrossRef]
- Sadiku, M.N.; Tembely, M.; Musa, S.M. Home area networks: A primer. Int. J. 2017, 7, 208. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Swamy, S.N.; Kota, S.R. An Empirical Study on System Level Aspects of Internet of Things (IoT). IEEE Access 2020, 8, 188082–188134. [Google Scholar] [CrossRef]
- Lombardi, M.; Pascale, F.; Santaniello, D. Internet of Things: A General Overview between Architectures, Protocols and Applications. Information 2021, 12, 87. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Shelby, Z.; Hartke, K.; Bormann, C.; Frank, B. Constrained Application Protocol (CoAP), Draft-Ietf-Corecoap-18, Work in Progress. sl: IETF. 2013. Available online: http://tools.ietf.org/html/draft-ietf-corecoap-18 (accessed on 1 July 2021).
- IoT Standards and Protocols Guide—Protocols of the Internet of Things. Available online: https://www.avsystem.com/blog/iot-protocols-and-standards/ (accessed on 25 April 2021).
- Bormann, C.; Castellani, A.P.; Shelby, Z. Coap: An application protocol for billions of tiny internet nodes. IEEE Internet Comput. 2012, 16, 62–67. [Google Scholar] [CrossRef]
- Cheshire, S.; Krochmal, M. Multicast DNS. RFC 2013, 6762. Available online: https://www.rfc-editor.org/info/rfc6762 (accessed on 1 July 2021). [CrossRef]
- Vasseur, J.; Agarwal, N.; Hui, J.; Shelby, Z.; Bertrand, P.; Chauvenet, C. RPL: The IP routing protocol designed for low power and lossy networks. IPSO Alliance 2011, 1–20. Available online: http://www.cse.chalmers.se/edu/year/2019/course/DAT300/PAPERS/rpl.pdf (accessed on 1 July 2021).
- Winter, T.; Thubert, P.; Brandt, A.; Hui, J.W.; Kelsey, R.; Levis, P.; Alexander, R.K. RPL: IPv6 routing protocol for low-power and lossy networks. RFC 2012, 6550, 1–157. Available online: https://datatracker.ietf.org/doc/html/rfc6550 (accessed on 1 July 2021).
- Yang, Z.; Yue, Y.; Yang, Y.; Peng, Y.; Wang, Z.; Liu, W. Study and Application on the Architecture and Key Technologies for IOT. In Proceedings of the International Conference on Multimedia Technology, Hangzhou, China, 26–28 July 2011; pp. 747–751. [Google Scholar] [CrossRef]
- Palattella, M.R.; Accettura, N.; Vilajosana, X.; Watteyne, T.; Grieco, L.A.; Boggia, G.; Dohler, M. Standardized protocol stack for the internet of (important) things. IEEE Commun. Surv. Tutor. 2012, 15, 1389–1406. [Google Scholar] [CrossRef]
- IEEE 802 Working Group. IEEE Standard for Local and Metropolitan Area Networks—Part 15.4: Low-Rate Wireless Personal Area Networks (LR-WPANs); IEEE Std 802.15.4-2011 (Revision of IEEE Std 802.15.4-2006); IEEE: Manhattan, NY, USA, 2011; pp. 1–314. [Google Scholar] [CrossRef]
- Hasan, M.; Hossain, E.; Niyato, D. Random access for machine-to-machine communication in LTE-advanced networks: Issues and approaches. IEEE Commun. Mag. 2013, 51, 86–93. [Google Scholar] [CrossRef]
- IEEE 802 Working Group. IEEE Standard for a Convergent Digital Home Network for Heterogeneous Technologies; IEEE Std 1905.1-2013; IEEE: Manhattan, NY, USA, 2013; pp. 1–93. [Google Scholar] [CrossRef]
- User Datagram Protocol(UDP). Available online: https://www.geeksforgeeks.org/user-datagram-protocol-udp/ (accessed on 25 April 2021).
- Pipkin, D.L. Halting the Hacker: A Practical Guide to Computer Security, 2nd ed.; Prentice Hall Professional: Hoboken, NJ, USA, 2003. [Google Scholar]
- Bertino, E.; Martino, L.D.; Paci, F.; Squicciarini, A.C. Web services threats, vulnerabilities, and countermeasures. In Security for Web Services and Service-Oriented Architectures; Springer: Heidelberg, Germany, 2019; pp. 25–44. [Google Scholar] [CrossRef]
- Kizza, J.M. Guide to Computer Network Security, 1st ed.; Springer: Heidelberg, Germany, 2009; pp. 387–411. [Google Scholar] [CrossRef]
- Dahbur, K.; Mohammad, B.; Tarakji, A.B. A survey of risks, threats and vulnerabilities in cloud computing. In Proceedings of the 2011 International Conference on Intelligent Semantic Web-Services and Applications, New York, NY, USA, 18–20 April 2011; pp. 1–6. [Google Scholar] [CrossRef]
- Rainer, R.K.; Cegielski, C.G. Ethics, privacy, and information security. In Introduction to Information Systems: Supporting and Transforming Business; John Wiley & Sons: Hoboken, NJ, USA, 2010; Volume 3, pp. 70–121. [Google Scholar]
- Tankard, C. Advanced persistent threats and how to monitor and deter them. Netw. Secur. 2011, 2011, 16–19. [Google Scholar] [CrossRef]
- Coffed, J. The Threat of Gps Jamming: The Risk to An Information Utility; EXELIS: Herndon, VA, USA, 2014; pp. 6–10. [Google Scholar]
- Tippenhauer, N.O.; Pöpper, C.; Rasmussen, K.B.; Capkun, S. On the requirements for successful GPS spoofing attacks. In Proceedings of the 18th ACM Conference on COMPUTER and Communications Security, Chicago, IL, USA, 17–21 October 2011; pp. 75–86. [Google Scholar] [CrossRef]
- Uluagac, A.S.; Subramanian, V.; Beyah, R. Sensory channel threats to cyber physical systems: A wake-up call. In Proceedings of the IEEE Conference on Communications and Network Security, San Francisco, CA, USA, 29–31 October 2014; pp. 301–309. [Google Scholar] [CrossRef]
- Ge, M.; Hong, J.B.; Guttmann, W.; Kim, D.S. A framework for automating security analysis of the internet of things. J. Netw. Comput. Appl. 2017, 83, 12–27. [Google Scholar] [CrossRef]
- Anthi, E.; Ahmad, S.; Rana, O.; Theodorakopoulos, G.; Burnap, P. Eclipse. IoT: A secure and adaptive hub for the Internet of Things. Comput. Secur. 2018, 78, 477–490. [Google Scholar] [CrossRef]
- Sanchez Alcon, J.A.; López, L.; Martínez, J.F.; Rubio Cifuentes, G. Trust and privacy solutions based on holistic service requirements. Sensors 2016, 16, 16. Available online: https://www.mdpi.com/1424-8220/16/1/16 (accessed on 25 April 2021). [CrossRef] [PubMed]
- Mauro, C.; Pallavi, K.; Rabbani, M.M.; Ranise, S. Attestation-enabled secure and scalable routing protocol for IoT networks. Ad Hoc Netw. 2020, 98, 102054. [Google Scholar] [CrossRef]
- Prabadevi, B.; Jeyanthi, N. Distributed Denial of service attacks and its effects on Cloud environment-a survey. In Proceedings of the International Symposium on Networks, Computers and Communications, Hammamet, Tunisia, 17–19 June 2014; pp. 1–4. [Google Scholar] [CrossRef]
- Varga, P.; Plosz, S.; Soos, G.; Hegedus, C. Security threats and issues in automation IoT. In Proceedings of the IEEE 13th International Workshop on Factory Communication Systems (WFCS), Trondheim, Norway, 31 May–2 June 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Qian, L.; Zhu, Z.; Hu, J.; Liu, S. Research of SQL injection attack and prevention technology. In Proceedings of the International Conference on Estimation, Detection and Information Fusion (ICEDIF), Harbin, China, 10–11 January 2015; pp. 303–306. [Google Scholar] [CrossRef]
- Everything You Need to Know About Facebook’s Data Breach Affecting 50M Users. Available online: http://https//techcrunch.com/2018/09/28/everything-you-need-to-know-about-facebooks-data-breach-affecting-50m-users/ (accessed on 26 April 2021).
- Zou, Y.; Wang, G. Intercept Behavior Analysis of Industrial Wireless Sensor Networks in the Presence of Eavesdropping Attack. IEEE Trans. Ind. Inform. 2016, 12, 780–787. [Google Scholar] [CrossRef]
- Chan, H.; Perrig, A.; Song, D.X. Random key predistribution schemes for sensor networks. In Proceedings of the IEEE Symposium Security Privacy, Berkeley, CA, USA, 11–14 May 2003; pp. 197–213. [Google Scholar] [CrossRef]
- Abomhara, M.; Køien, G.M. Security and privacy in the Internet of Things: Current status and open issues. In Proceedings of the IEEE International Conference Privacy Security Mobile System (PRISMS), Aalborg, Denmark, 11–14 May 2014; pp. 1–8. [Google Scholar] [CrossRef]
- Ashraf, Q.M.; Habaebi, M.H. Autonomic schemes for threat mitigation in Internet of Things. J. Netw. Comput. Appl. 2015, 49, 112–127. [Google Scholar] [CrossRef]
- Znaidi, W.; Minier, M.; Babau, J.P. An Ontology for Attacks in Wireless Sensor Networks; RR-6704; INRIA: Rocquencourt, France, 2008. [Google Scholar]
- Ye, F.; Luo, H.; Lu, S.; Zhang, L. Statistical en-route filtering of injected false data in sensor networks. IEEE J. Sel. Areas Commun. 2005, 23, 839–850. [Google Scholar]
- Newsome, J.; Shi, E.; Song, D.; Perrig, A. The sybil attack in sensor networks: Analysis & defenses. In Proceedings of the ACM Third International Symposium on Information Processing in Sensor Networks, Berkeley, CA, USA, 27 April 2004; pp. 259–268. [Google Scholar]
- Sarigiannidis, P.G.; Karapistoli, E.D.; Economides, A.A. Detecting sybil attacks in wireless sensor networks using UWB ranging-based information. Expert Syst. Appl. 2015, 42, 7560–7572. [Google Scholar] [CrossRef]
- Savola, R.M.; Abie, H.; Sihvonen, M. Towards metrics-driven adaptive security management in e-health IoT applications. In Proceedings of the 7th International Conference Body Area Network, Brussels, Belgium, 24–26 February 2012; pp. 276–281. [Google Scholar]
- Choi, H.; Zhu, S.; Porta, T.F.L. SET: Detecting node clones in sensor networks. In Proceedings of the IEEE 3rd Int. Confernce Security Privacy Commun. Netw. Workshops (SecureComm), Nice, France, 17–21 September 2007; pp. 341–350. [Google Scholar] [CrossRef]
- Xing, K.; Liu, F.; Cheng, X.; Du, D.H.C. Real-time detection of clone attacks in wireless sensor networks. In Proceedings of the 28th International Conference on Distributed Computing Systems (ICDCS), Beijing, China, 17–20 June 2008; pp. 3–10. [Google Scholar] [CrossRef]
- Standaert, F.X. Introduction to side-channel attacks. Secure Integrated Circuits and Systems; Springer: Boston, MA, USA, 2010; pp. 27–42. ISBN 978-0-387-71829-3. [Google Scholar]
- Wood, A.D.; Stankovic, J.A.; Son, S.H. JAM: A jammed-area mapping service for sensor networks. In Proceedings of the 24th IEEE Real-Time Systems Symposium, Cancun, Mexico, 5 December 2003; pp. 286–297. [Google Scholar] [CrossRef]
- Hussein, A.A.; Leow, C.Y.; Rahman, T.A. Robust multiple frequency multiple power localization schemes in the presence of multiple jamming attacks. PLoS ONE 2017, 12, e0177326. [Google Scholar] [CrossRef][Green Version]
- Shabana, K.; Fida, N.; Khan, F.; Jan, S.R.; Rehman, M.U. Security issues and attacks in wireless sensor networks. Int. J. Adv. Res. Comput. Sci. Electron. Eng. 2016, 5, 81. [Google Scholar]
- Ho, J.-W.; Wright, M.; Das, S.K. Fast detection of replica node attacks in mobile sensor networks using sequential analysis. In Proceedings of the IEEE INFOCOM, Rio de Janeiro, Brazil, 19–25 April 2009; pp. 1773–1781. [Google Scholar] [CrossRef]
- Wurm, J.; Hoang, K.; Arias, O.; Sadeghi, A.-R.; Jin, Y. Security analysis on consumer and industrial IoT devices. In Proceedings of the 21st IEEE Asia South Pacific Design Automation Conference (ASP-DAC), Macao, China, 25–28 January 2016; pp. 519–524. [Google Scholar] [CrossRef]
- Puthal, D.; Nepal, S.; Ranjan, R.; Chen, J. Threats to networking cloud and edge datacenters in the Internet of Things. IEEE Cloud Comput. 2016, 3, 64–71. [Google Scholar] [CrossRef]
- Koh, J.Y.; Nevat, I.; Leong, D.; Wong, W.C. Geo-spatial location spoofing detection for Internet of Thing. IEEE Internet Things J. 2016, 3, 971–978. [Google Scholar] [CrossRef]
- Lough, D.L. A Taxonomy of Computer Attacks with Applications to Wireless Networks; Virginia Polytechnic Institute and State University: Blacksburg, VA, USA, 2001. [Google Scholar]
- Bu, K.; Xu, M.; Liu, X.; Luo, J.; Zhang, S.; Weng, M. Deterministic detection of cloning attacks for anonymous RFID systems. IEEE Trans. Ind. Informat. 2015, 11, 1255–1266. [Google Scholar] [CrossRef]
- Wood, A.D.; Stankovic, J.A. Denial of service in sensor networks. Computer 2002, 35, 54–62. [Google Scholar] [CrossRef]
- Mirai “Internet of Things” Malware From Krebs DDoS Attack Goes Open Source. Available online: https://nakedsecurity.sophos.com/2016/10/05/mirai-internet-of-things-malware (accessed on 30 June 2021).
- Liu, Y.; Li, Y.; Man, H. MAC layer anomaly detection in ad hoc networks. In Proceeding of the 6th Annual IEEE SMC Information Assurance Workshop (IAW), West Point, NY, USA, 15–17 June 2005; pp. 402–409. [Google Scholar] [CrossRef]
- Riaz, R.; Kim, K.-H.; Ahmed, H.F. Security analysis survey and framework design for IP connected LoWPANs. In Proceedings of the IEEE International Symposium Autonomous Decentralized Systems (ISADS), Athens, Greece, 23–25 March 2009; pp. 1–6. [Google Scholar]
- Hamid, M.A.; Rashid, M.; Hong, C.S. Routing security in sensor network: Hello flood attack and defense. In Proceedings of the IEEE ICNEWS, Phoenix Park, Korea, 20–22 February 2006; pp. 2–4. [Google Scholar]
- Murphy, J. Enhanced Security Controls for IBM Watson IoT Platform, Armonk. Available online: https://developer.ibm.com/iotplatform/2016/09/23/enhanced-securitycontrols-for-ibm-watson-iot-platform/ (accessed on 30 June 2021).
- Teng, L.; Zhang, Y. SERA: A secure routing algorithm against sinkhole attacks for mobile wireless sensor networks. In Proceedings of the IEEE 2nd International Conference on Computer Modeling Simulation (ICCMS), Sanya, China, 22–24 January 2010; pp. 79–82. [Google Scholar]
- Sathish, R.; Scholar, P.G. Dynamic detection of clone attack in wireless sensor networks. In Proceedings of the International Conference on Communication Systems Network Technologies, Gwalior, India, 6–8 April 2013; pp. 501–505. [Google Scholar]
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: Attacks and countermeasures. Ad Hoc Netw. 2003, 1, 293–315. [Google Scholar] [CrossRef]
- Karakehayov, Z. Using reward to detect team black-hole attacks in wireless sensor networks. In Proceedings of the Workshop on Real World Wireless Sensor Network, Stockholm, Sweden, 20–21 June 2005; pp. 20–21. [Google Scholar]
- Wang, W.; Bhargava, B.K. Visualization of wormholes in sensor networks. In Proceedings of the 3rd ACM Workshop Wireless Security, Philadelphia, PA, USA, 1 October 2001; pp. 51–60. [Google Scholar] [CrossRef]
- Kaissi, R.Z.E.; Kayssi, A.; Chehab, A.; Dawy, Z. DAWWSEN: A Defense Mechanism Against Wormhole Attacks in Wireless Sensor Networks. Ph.D. Thesis, American University of Beirut, Beirut, Lebanon, 2005. [Google Scholar]
- Perrey, H.; Landsmann, M.; Ugus, O.; Wählisch, M.; Schmidt, T.C. TRAIL: Topology Authentication in RPL. In Proceedings of the ACM International Conference on Embedded Wireless System and Network (EWSN), Graz, Austria, 15–17 February 2016; pp. 59–64. [Google Scholar]
- Dvir, A.; Holczer, T.; Buttyán, L. Vera-version number and rank authentication in RPL. In Proceedings of the IEEE 8th International Conference on Mobile Ad Hoc Sensor Systems (MASS), Valencia, Spain, 17–22 October 2011; pp. 709–714. [Google Scholar] [CrossRef]
- Accettura, N.; Piro, G. Optimal and secure protocols in the IETF 6TiSCH communication stack. In Proceedings of the IEEE 23rd International Symposium on Industrial Electronics (ISIE), Istambul, Turkey, 1–4 June 2014; pp. 1469–1474. [Google Scholar] [CrossRef]
- Singh, M.; Rajan, M.; Shivraj, V.; Balamuralidhar, P. Secure MQTT for Internet of Things (IoT). In Proceedings of the IEEE 5th International Conference on Communication Systems and Network Technologies (CSNT), Gwalior, India, 4–6 April 2015; pp. 746–751. [Google Scholar] [CrossRef]
- Song, S.; Choi, H.-K.; Kim, J.-Y. A secure and lightweight approach for routing optimization in mobile IPv6. EURASIP J. Wirel. Commun. Netw. 2009, 2009, 1–10. [Google Scholar] [CrossRef][Green Version]
- Neisse, R.; Steri, G.; Baldini, G. Enforcement of security policy rules for the Internet of Things. In Proceedings of the IEEE 10th International Confernce on Wireless and Mobile Computing Networking and Communications (WiMob), Larnaca, Cyprus, 8–10 October 2014; pp. 165–172. [Google Scholar] [CrossRef]
- Xbox 360 Timing Attack. Available online: http://beta.ivc.no/wiki/index.php/Xbox_360_Timing_Attack (accessed on 30 June 2021).
- Zhang, Q.; Wang, X. SQL injections through back-end of RFID system. In Proceedings of the International Symposium on Computer Network and Multimedia Technology, Wuhan, China, 18–20 January 2009; pp. 1–4. [Google Scholar]
- Farris, I.; Taleb, T.; Khettab, Y.; Song, J. A survey on emerging SDN and NFV security mechanisms for IoT systems. IEEE Commun. Surv. Tutor. 2019, 21, 812–837. [Google Scholar] [CrossRef]
- Singh, J.; Pasquier, T.; Bacon, J.; Ko, H.; Eyers, D. Twenty security considerations for cloud-supported Internet of Things. IEEE Internet Things J. 2016, 3, 269–284. [Google Scholar] [CrossRef]
- Bose, T.; Bandyopadhyay, S.; Ukil, A.; Bhattacharyya, A.; Pal, A. Why not keep your personal data secure yet private in IoT: Our lightweight approach. In Proceedings of the IEEE 10th International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), Singapore, 7–9 April 2015; pp. 1–6. [Google Scholar]
- Kumar, J.; Rajendran, B.; Bindhumadhava, B.S.; Babu, N.S.C. XML wrapping attack mitigation using positional token. In Proceedings of the International Confernce Public Key Infrastructure and its Applications (PKIA), Bangalore, India, 14–15 November 2017; pp. 36–42. [Google Scholar]
- Deng, J.; Han, R.; Mishra, S. Defending against path-based dos attacks in wireless sensor networks. In Proceedings of the 3rd ACM Workshop Security Ad Hoc Sensor Network, Alexandria, VA, USA, 14–15 November 2005; pp. 89–96. [Google Scholar]
- Gupta, H.; Oorschot, P.C.V. Onboarding and Software Update Architecture for IoT Devices. In Proceedings of the 17th International Conference on Privacy, Security and Trust (PST), Fredericton, NB, Canada, 26–28 August 2019; pp. 1–11. [Google Scholar] [CrossRef]
- Skorobogatov, S. Fault attacks on secure chips: From glitch to flash. In Design and Security of Cryptographic Algorithms and Devices (ECRYPT II); University of Cambridge: Cambridge, UK, 2011; pp. 1–64. [Google Scholar]
- Stanciu, A.; Balan, T.-C.; Gerigan, C.; Zamfir, S. Securing the IoT gateway based on the hardware implementation of a multi pattern search algorithm. In Proceedings of the International Conference on Optimization of Electrical and Electronic Equipment (OPTIM) & 2017 Intl Aegean Conference on Electrical Machines and Power Electronics (ACEMP), Brasov, Romania, 25–27 May 2017; pp. 1001–1006. [Google Scholar]
- MohammadI, S.; Jadidoleslamy, H. A comparison of link layer attacks on wireless sensor networks. Int. J. Appl. Graph Theory Wirel. Ad Hoc Netw. Sens. Netw. 2011, 3, 35–56. [Google Scholar]
- Swamy, S.N.; Jadhav, D.; Kulkarni, N. Security threats in the application layer in IoT applications. In Proceedings of the International Confernce IoT Social, Mobile, Analytics Cloud (I-SMAC), Palladam, India, 10–11 February 2017; pp. 477–480. [Google Scholar]
- Sharmeen, S.; Huda, S.; Abawajy, J.H.; Ismail, W.N.; Hassan, M.M. Malware Threats and Detection for Industrial Mobile-IoT Networks. IEEE Access 2018, 6, 15941–15957. [Google Scholar] [CrossRef]
- Ham, H.-S.; Kim, H.-H.; Kim, M.-S.; Choi, M.-J. Linear SVM-based Android malware detection for reliable IoT services. J. Appl. Math. 2014, 2014, 594501. [Google Scholar] [CrossRef]
- Kaur, P.; Sharma, S. Spyware detection in Android using hybridization of description analysis permission mapping and interface analysis. Procedia Comput. Sci. 2015, 46, 794–803. [Google Scholar] [CrossRef]
- Wolinsky, D.I.; Syta, E.; Ford, B. Hang with your buddies to resist intersection attacks. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security (CCS), Berlin, Germany, 4–8 November 2013; pp. 1153–1166. [Google Scholar]
- Grover, J.; Laxmi, V.; Gaur, M.S. Attack models and infrastructure supported detection mechanisms for position forging attacks in vehicular ad hoc networks. CSI Trans. ICT 2013, 1, 261–279. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of Things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Cherian, M.; Chatterjee, M. Survey of security threats in iot and emerging countermeasures. In Proceedings of the International Symposium on Security in Computing and Communication, Bangalore, India, 19–22 September 2018; pp. 591–604. [Google Scholar]
- Sepulveda, J.; Willgerodt, F.; Pehl, M. SEPUFSoC: Using PUFs for memory integrity and authentication in multi-processors system-on-chip. In Proceedings of the GLSVLSI ‘18: Proceedings of the 2018 on Great Lakes Symposium on VLSI, Chicago, IL, USA, 23–25 May 2018; pp. 39–44. [Google Scholar] [CrossRef]
- Bîrleanu, F.G.; Bizon, N. Reconfigurable computing in hardware security–a brief review and application. J. Electr. Eng. Electron. Control Comput. Sci. 2016, 2, 1–12. [Google Scholar]
- Katsikogiannis, G.; Kallergis, D.; Garofalaki, Z.; Mitropoulos, S.; Douligeris, C. A policy-aware Service Oriented Architecture for secure machine-to-machine communications. Ad Hoc Netw. 2018, 80, 70–80. [Google Scholar] [CrossRef]
- Laplante, P.A. Blockchain and the Internet of Things in the industrial sector. IEEE Comput. Soc. 2018, 20, 15–18. [Google Scholar]
- Orman, H. Blockchain: The emperors new PKI? IEEE Internet Comput. 2018, 22, 23–28. [Google Scholar] [CrossRef]
- Henry, R.; Herzberg, A.; Kate, A. Blockchain access privacy: Challenges and directions. IEEE Secur. Priv. 2018, 16, 38–45. [Google Scholar] [CrossRef]
- Fog Computing: Focusing on Mobile Users at the Edge. Available online: https://arxiv.org/abs/1502.01815 (accessed on 1 July 2021).
- Dastjerdi, A.V.; Buyya, R. Fog Computing: Helping the Internet of Things Realize Its Potential. Computer 2016, 49, 112–116. [Google Scholar] [CrossRef]
- Sehgal, V.K.; Patrick, A.; Soni, A.; Rajput, L. Smart human security framework using Internet of Things, cloud and fog computing. Intelligent Distributed Computing. Springer 2015, 321, 251–263. [Google Scholar] [CrossRef]
- Feasibility of Fog Computing. Available online: https://arxiv.org/abs/1701.05451 (accessed on 31 June 2021).
- IoT Agenda. IoT and Big Data Analytics. Available online: https://internetofthingsagenda.techtarget.com/ (accessed on 30 June 2021).
- Alwaris, A.; Alhothaily, A.; Hu, C.; Cheng, X. Fog Computing for the Internet of Things: Security and Privacy Issues. IEEE Comput. 2017, 21, 34–42. [Google Scholar] [CrossRef]
- Mollah, M.B.; Azad, M.A.K.; Vasilakos, A. Secure data sharing and searching at the edge of cloud-assisted Internet of Things. IEEE Cloud Comput. 2017, 4, 34–42. [Google Scholar] [CrossRef]
- Alrowaily, M.; Lu, Z. Secure edge computing in IoT systems: Review and case studies. In Proceedings of the IEEE/ACM Symposium on Edge Computing (SEC), Seattle, WA, USA, 25–27 October 2018; pp. 440–444. [Google Scholar] [CrossRef]
- Li, Y.; Wang, S. An energy-aware edge server placement algorithm in mobile edge computing. In Proceedings of the IEEE International Confernce Edge Comput. (EDGE), San Francisco, CA, USA, 2–7 July 2018; pp. 66–73. [Google Scholar] [CrossRef]
- 6 Significant Issues That Edge Computing in IoT Solves. Available online: https://internetofthingsagenda.techtarget.com/feature/6-significant-issues-that-edge-computing-in-IoT-solves (accessed on 30 June 2021).
- Premsankar, G.; Di Francesco, M.; Taleb, T. Edge computing for the Internet of Things: A case study. IEEE Internet Things J. 2018, 5, 1275–1284. [Google Scholar] [CrossRef]
- Abbas, N.; Zhang, Y.; Taherkordi, A.; Skeie, T. Mobile edge computing: A survey. IEEE Internet Things J. 2018, 5, 450–465. [Google Scholar] [CrossRef]
- Pavani, K.; Damodaram, A. Intrusion detection using MLP for MANETs. In Proceedings of the Third International Conference on Computational Intelligence and Information Technology (CIIT 2013), Mumbai, India, 18–19 October 2013; pp. 440–444. [Google Scholar] [CrossRef]
- Kulkarni, R.V.; Venayagamoorthy, G.K. Neural network based secure media access control protocol for wireless sensor networks. In Proceedings of the 2009 International Joint Conference on Neural Networks, Atlanta, GA, USA, 14–19 June 2009; pp. 1680–1687. [Google Scholar] [CrossRef]
- Xiao, L.; Xie, C.; Chen, T.; Dai, H.; Poor, H.V. A mobile offloading game against smart attacks. IEEE Access 2016, 4, 2281–2291. [Google Scholar] [CrossRef]
- Xiao, L.; Yan, Q.; Lou, W.; Chen, G.; Hou, Y.T. Proximity-based security techniques for mobile users in wireless networks. IEEE Trans. Inf. Forensics Secur. 2013, 8, 2089–2100. [Google Scholar] [CrossRef]
- Xiao, L.; Li, Y.; Han, G.; Liu, G.; Zhuang, W. PHY-layer spoofing detection with reinforcement learning in wireless networks. IEEE Trans. Veh. Technol. 2016, 65, 10037–10047. [Google Scholar] [CrossRef]
- Spirina, K. Biometric Authentication: The Future of IoT Security Solutions. Available online: https://www.IoTevolutionworld.com/IoT/articles/438690-biometricauthenticationfuture-IoT-security-solutions.html (accessed on 9 February 2019).
- Blanco-Novoa, Ó.; Fernández-Caramés, T.; Fraga-Lamas, P.; Castedo, L. An electricity price-aware open-source smart socket for the Internet of energy. Sensors 2017, 17, 643. [Google Scholar] [CrossRef]
- Zhang, Y.; Wen, J. An IoT electric business model based on the protocol of bitcoin. In Proceedings of the 18th International Conference on Intelligence in Next Generation Networks, Paris, France, 17–19 February 2015; pp. 184–191. [Google Scholar] [CrossRef]
- Lundqvist, T.; Blanche, A.; Andersson, H.R.H. Thing-to-thing electricity micro payments using blockchain technology. In Proceedings of the Global Internet of Things Summit (GIoTS), Geneva, Switzerland, 6–9 June 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Salahuddin, M.A.; Al-Fuqaha, A.; Guizani, M.; Shuaib, K.; Sallabi, F. Softwarization of Internet of Things infrastructure for secure and smart healthcare. arXiv 2018, arXiv:1805.11011. Available online: https://arxiv.org/abs/1805.11011 (accessed on 1 July 2021).
- Bocek, T.; Rodrigues, B.B.; Strasser, T.; Stiller, B. Blockchains everywhere-a use-case of blockchains in the pharma supply-chain. In Proceedings of the IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 772–777. [Google Scholar] [CrossRef]
- Shae, Z.; Tsai, J.J.P. On the Design of a Blockchain Platform for Clinical Trial and Precision Medicine. In Proceedings of the IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 1972–1980. [Google Scholar] [CrossRef]
- Lei, A.; Cruickshank, H.; Cao, Y.; Asuquo, P.; Ogah, C.P.A.; Sun, Z. Blockchain-Based Dynamic Key Management for Heterogeneous Intelligent Transportation Systems. IEEE Internet Things J. 2017, 4, 1832–1843. [Google Scholar] [CrossRef]
- Huh, S.; Cho, S.; Kim, S. Managing IoT devices using blockchain platform. In Proceedings of the 19th International Conference on Advanced Communication Technology (ICACT), PyeongChang, Koreea, 19–22 February 2017; pp. 464–467. [Google Scholar] [CrossRef]
- Samaniego, M.; Deters, R. Internet of Smart Things-IoST: Using Blockchain and CLIPS to Make Things Autonomous. In Proceedings of the IEEE International Conference on Cognitive Computing (ICCC), Honulul, HI, USA, 25–30 June 2017; pp. 9–16. [Google Scholar] [CrossRef]
- Faruque, M.A.A.; Vatanparvar, K. Energy Management-as-a-Service Over Fog Computing Platform. IEEE Internet Things J. 2016, 3, 161–169. [Google Scholar] [CrossRef]
- SGao, S.; Peng, Z.; Xiao, B.; Xiao, Q.; Song, Y. SCoP: Smartphone energy saving by merging push services in Fog computing. In Proceedings of the IEEE/ACM 25th International Symposium on Quality of Service (IWQoS), Vilanova i la Geltrú, Spain, 14–16 June 2017; pp. 1–10. [Google Scholar] [CrossRef]
- Dubey, H.; Monteiro, A.; Constant, N.; Abtahi, M.; Borthakur, D.; Mahler, L. Fog computing in medical Internet-of-Things: Architecture implementation and applications. In Handbook of Large-Scale Distributed Computing in Smart Healthcare, 1st ed.; Khan, S.U., Zomaya, A.Y., Abbas, A., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2017; pp. 281–321. ISBN 978-3-319-58280-1. [Google Scholar]
- Rahmani, A.M.; Gia, T.N.; Negash, B.; Anzanpour, A.; Azimi, I.; Jiang, M. Exploiting smart e-health gateways at the edge of healthcare Internet-of-Things: A fog computing approach. Future Gener. Comput. Syst. 2018, 78, 641–658. [Google Scholar] [CrossRef]
- Gia, T.N.; Jiang, M.; Rahmani, A.M.; Westerlund, T.; Liljeberg, P.; Tenhunen, H. Fog computing in healthcare Internet of Things: A case study on ecg feature extraction. In Proceedings of the 2015 IEEE International Conference on Computer and Information Technology, Liverpool, UK, 26–28 October 2015; pp. 356–363. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, A.; Lin, X.; Shen, X.S. Security, Privacy, and Fairness in Fog-Based Vehicular Crowdsensing. IEEE Commun. Mag. 2017, 55, 146–152. [Google Scholar] [CrossRef]
- Markakis, E.K.; Karras, K.; Zotos, N.; Sideris, A.; Moysiadis, T.; Corsaro, A.; Pallis, E. EXEGESIS: Extreme Edge Resource Harvesting for a Virtualized Fog Environment. IEEE Commun. Mag. 2017, 55, 173–179. [Google Scholar] [CrossRef]
- Huang, Y.; Lu, Y.; Wang, F.; Fan, X.; Liu, J.; Leung, V.C. An Edge Computing Framework for Real-Time Monitoring in Smart Grid. In Proceedings of the 2018 IEEE International Conference on Industrial Internet (ICII), Seattle, WA, USA, 21–23 October 2018; pp. 99–108. [Google Scholar] [CrossRef]
- Oyekanlu, E.; Nelatury, C.; Fatade, A.O.; Alaba, O.; Abass, O. Edge computing for industrial IoT and the smart grid: Channel capacity for M2M communication over the power line. In Proceedings of the IEEE 3rd International Conference on Electro-Technology for National Development (NIGERCON), Owerri, Nigeria, 7–10 November 2017; pp. 1–11. [Google Scholar] [CrossRef]
- Muhammed, T.; Mehmood, R.; Albeshri, A.; Katib, I. UbeHealth: A Personalized Ubiquitous Cloud and Edge-Enabled Networked Healthcare System for Smart Cities. IEEE Access 2018, 6, 32258–32285. [Google Scholar] [CrossRef]
- Barik, R.K.; Dubey, H.; Mankodiya, K. SOA-FOG: Secure service-oriented edge computing architecture for smart health big data analytics. In Proceedings of the IEEE Global Conference on Signal and Information Processing (GlobalSIP), Montreal, UK, 14–16 November 2017; pp. 477–481. [Google Scholar] [CrossRef]
- Singh, D.; Tripathi, G.; Alberti, A.M.; Jara, A. Semantic edge computing and IoT architecture for military health services in battlefield. In Proceedings of the 14th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2017; pp. 185–190. [Google Scholar] [CrossRef]
- Aman, M.N.; Sikdar, B.; Chua, K.C.; Ali, A. Low Power Data Integrity in IoT Systems. IEEE Internet Things J. 2018, 5, 3102–3113. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. Lightweight and Privacy-Preserving Two-Factor Authentication Scheme for IoT Devices. IEEE Internet Things J. 2019, 6, 580–589. [Google Scholar] [CrossRef]
- Ahmed, S.; Lee, Y.; Hyun, S.; Koo, I. Feature Selection–Based Detection of Covert Cyber Deception Assaults in Smart Grid Communications Networks Using Machine Learning. IEEE Access 2018, 6, 27518–27529. [Google Scholar] [CrossRef]
- Ozay, M.; Esnaola, I.; Vural, F.T.Y.; Kulkarni, S.R.; Poor, H.V. Machine Learning Methods for Attack Detection in the Smart Grid. IEEE Trans. Neural Netw. Learn. Syst. 2016, 27, 1773–1786. [Google Scholar] [CrossRef] [PubMed]
- Zhang, D.; Han, X.; Deng, C. Review on the research and practice of deep learning and reinforcement learning in smart grids. CSEE J. Power Energy Syst. 2018, 4, 362–370. [Google Scholar] [CrossRef]
- Hossain, E.; Khan, I.; Un-Noor, F.; Sikander, S.S.; Sunny, M.S.H. Application of Big Data and Machine Learning in Smart Grid and Associated Security Concerns: A Review. IEEE Access 2019, 7, 13960–13988. [Google Scholar] [CrossRef]
- Mercer, C. How Machine Learning Will Change Society. Available online: https://www.techworld.com/picture-gallery/tech-innovation/5-ways-machine-learning-will-change-society-3666674 (accessed on 1 July 2021).
- Chen, M.; Hao, Y.; Hwang, K.; Wang, L.; Wang, L. Disease prediction by machine learning over big data from healthcare communities. IEEE Access 2017, 5, 8869–8879. [Google Scholar] [CrossRef]
- Vito, S.D.; Francia, G.D.; Esposito, E.; Ferlito, S.; Formisano, F.; Massera, E. Adaptive machine learning strategies for network calibration of IoT smart air quality monitoring devices. Pattern Recognit. Lett. 2020, 136, 264–271. [Google Scholar] [CrossRef]
- Punithavathi, P.; Geetha, S.; Karuppiah, M.; Islam, S.K.F.; Hassan, M.M.; Choo, K.K.R. A lightweight machine learning-based authentication framework for smart IoT devices. Inf. Sci. 2019, 484, 255–268. [Google Scholar] [CrossRef]
- Bigini, G.; Freschi, V.; Lattanzi, E. A Review on Blockchain for the Internet of Medical Things: Definitions, Challenges, Applications, and Vision. Future Internet 2020, 12, 208. [Google Scholar] [CrossRef]
- Sepasgozar, S.; Karimi, R.; Farahzadi, L.; Moezzi, F.; Shirowzhan, S.M.; Ebrahimzadeh, S.; Hui, F.; Aye, L. A Systematic Content Review of Artificial Intelligence and the Internet of Things Applications in Smart Home. Appl. Sci. 2020, 10, 3074. [Google Scholar] [CrossRef]
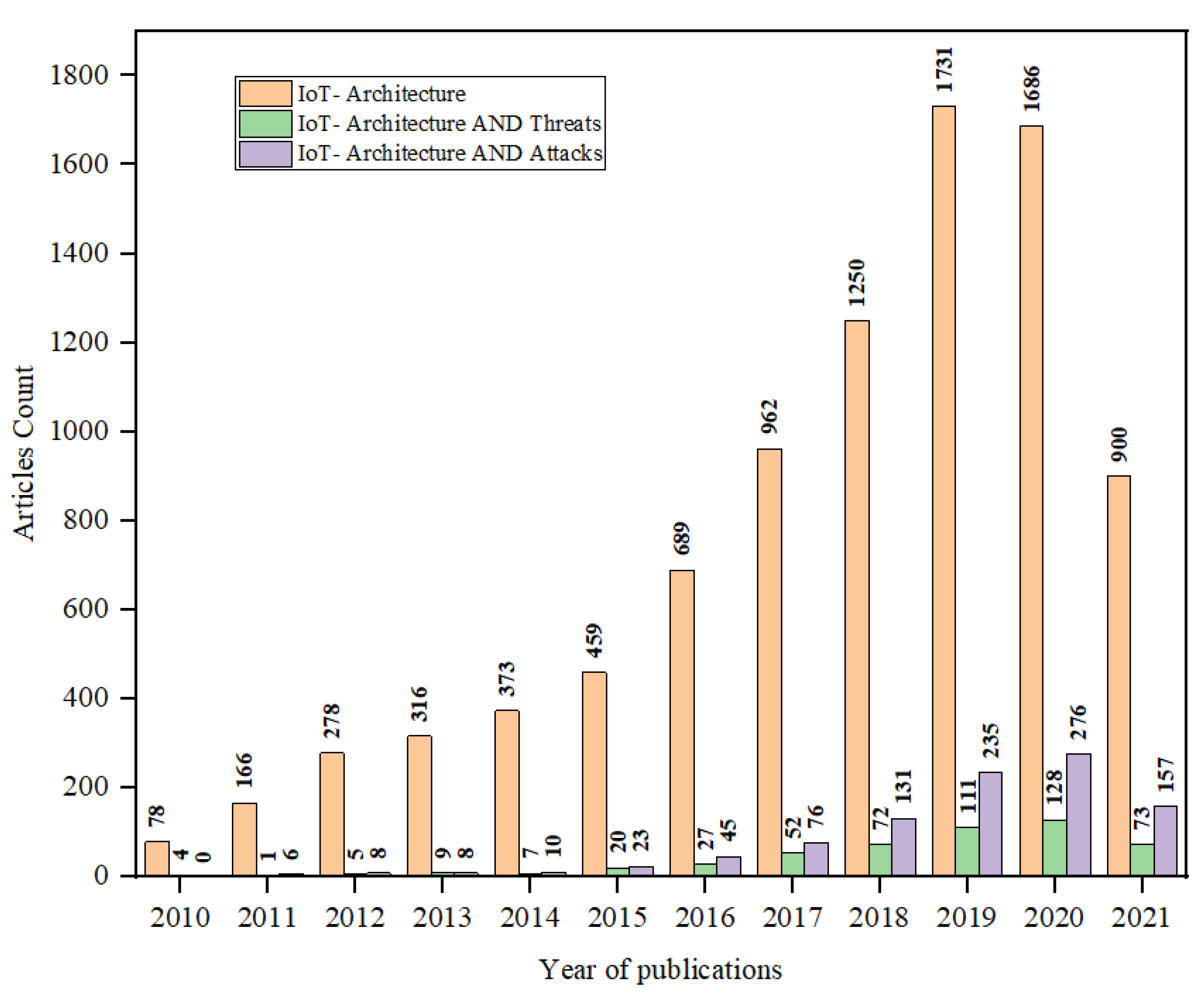

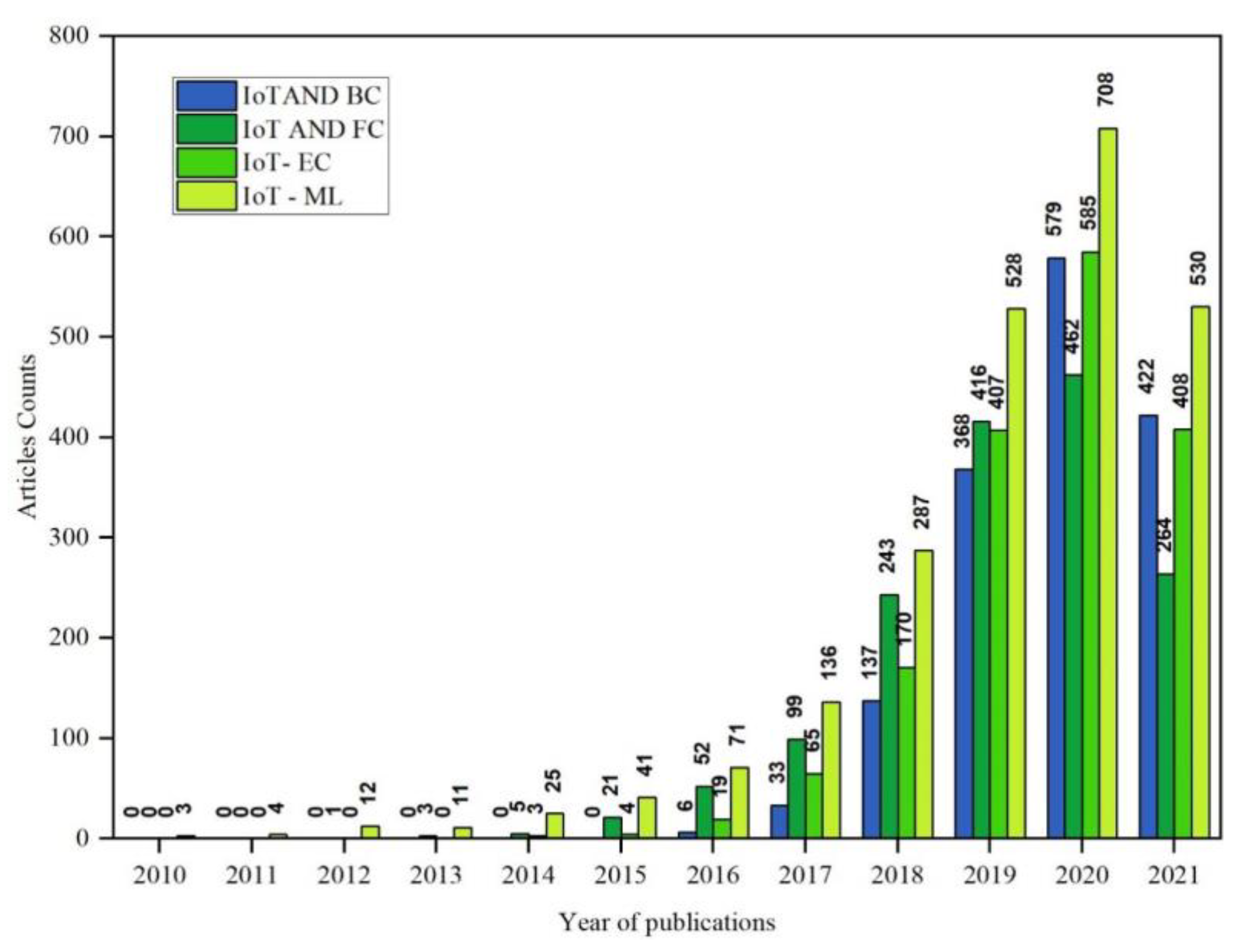
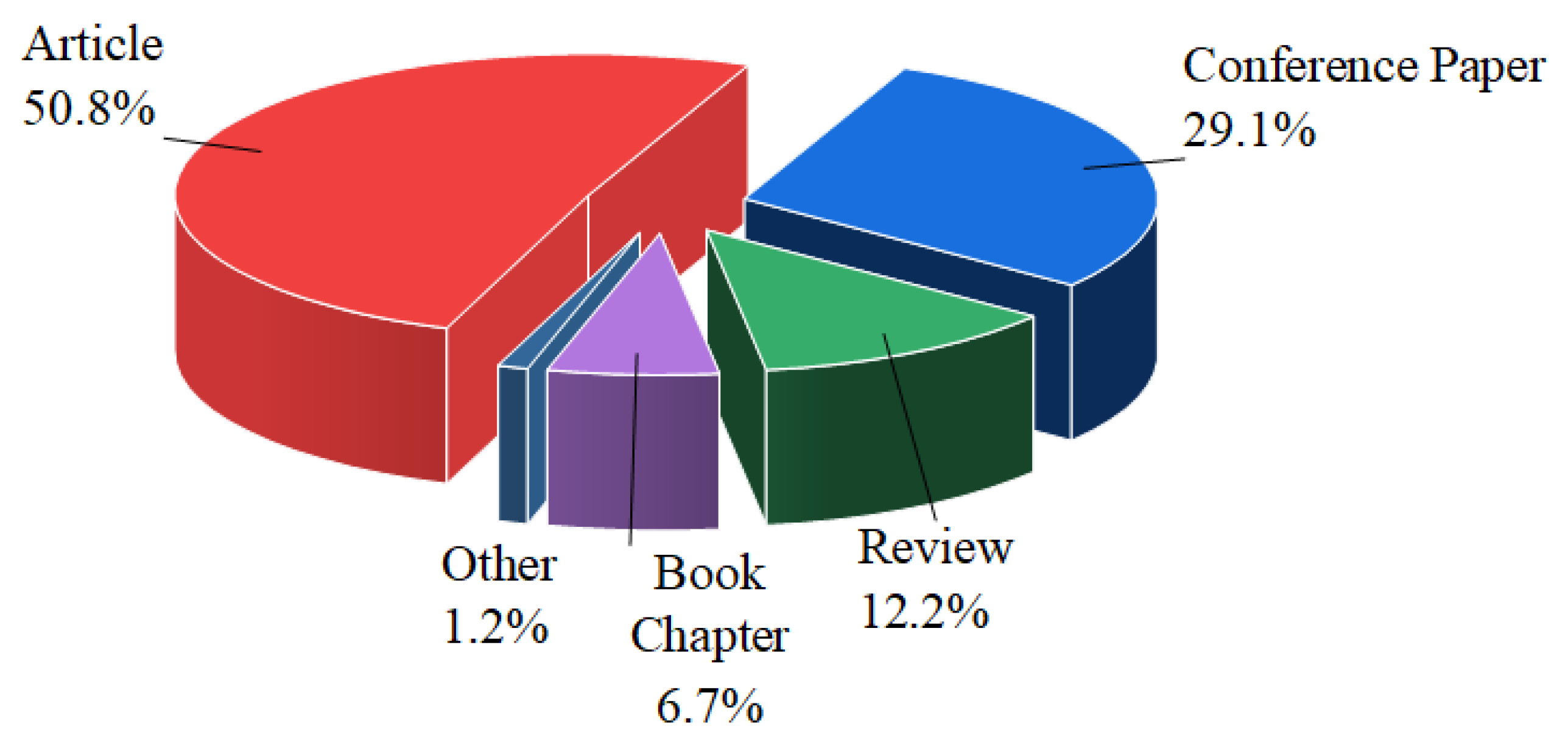
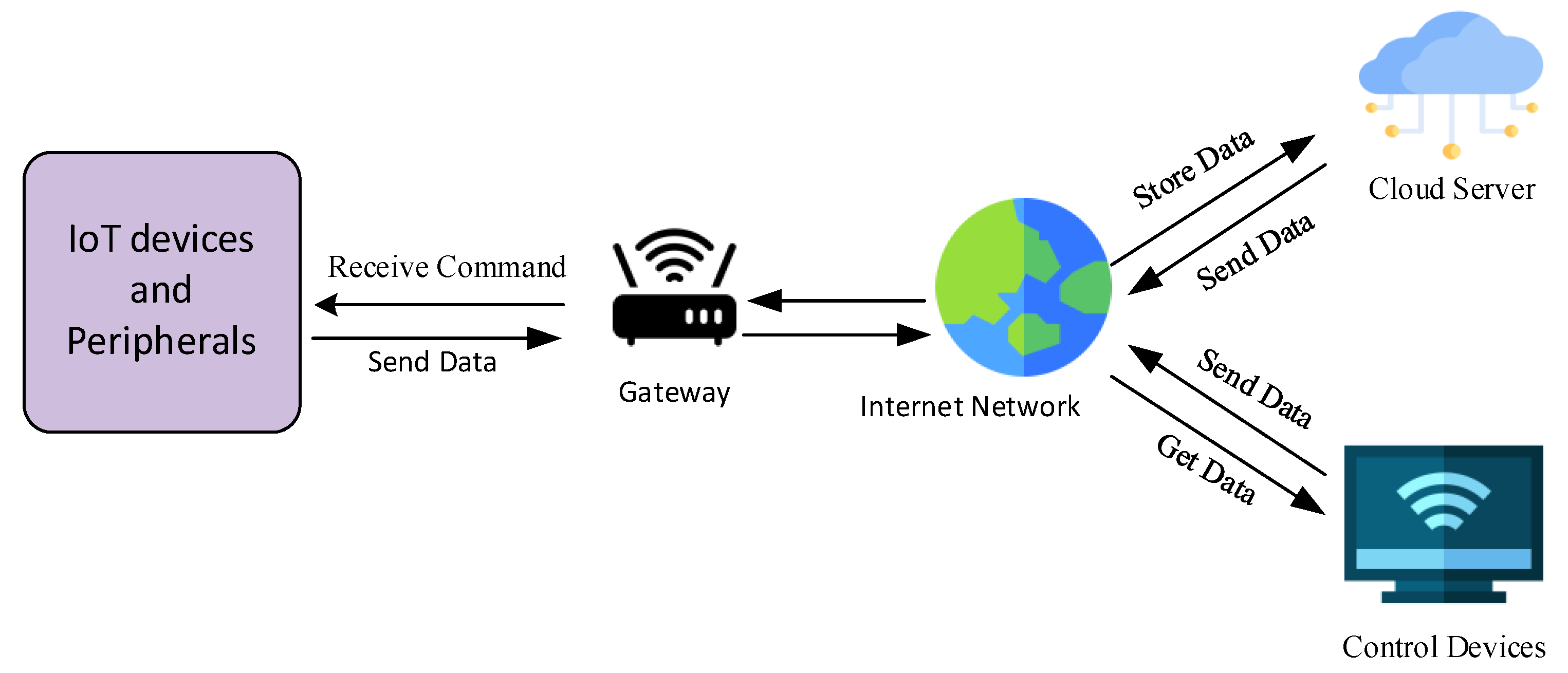
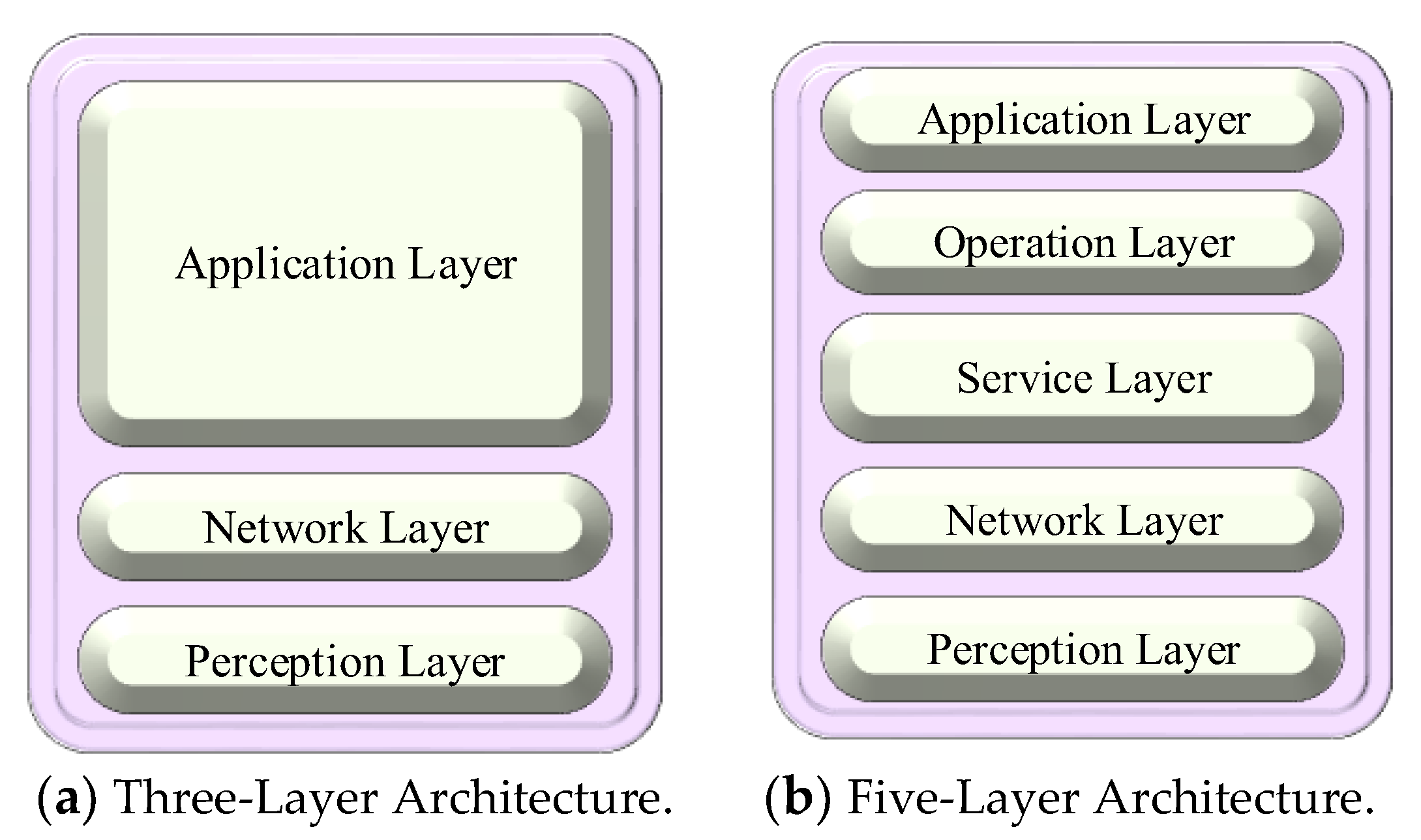
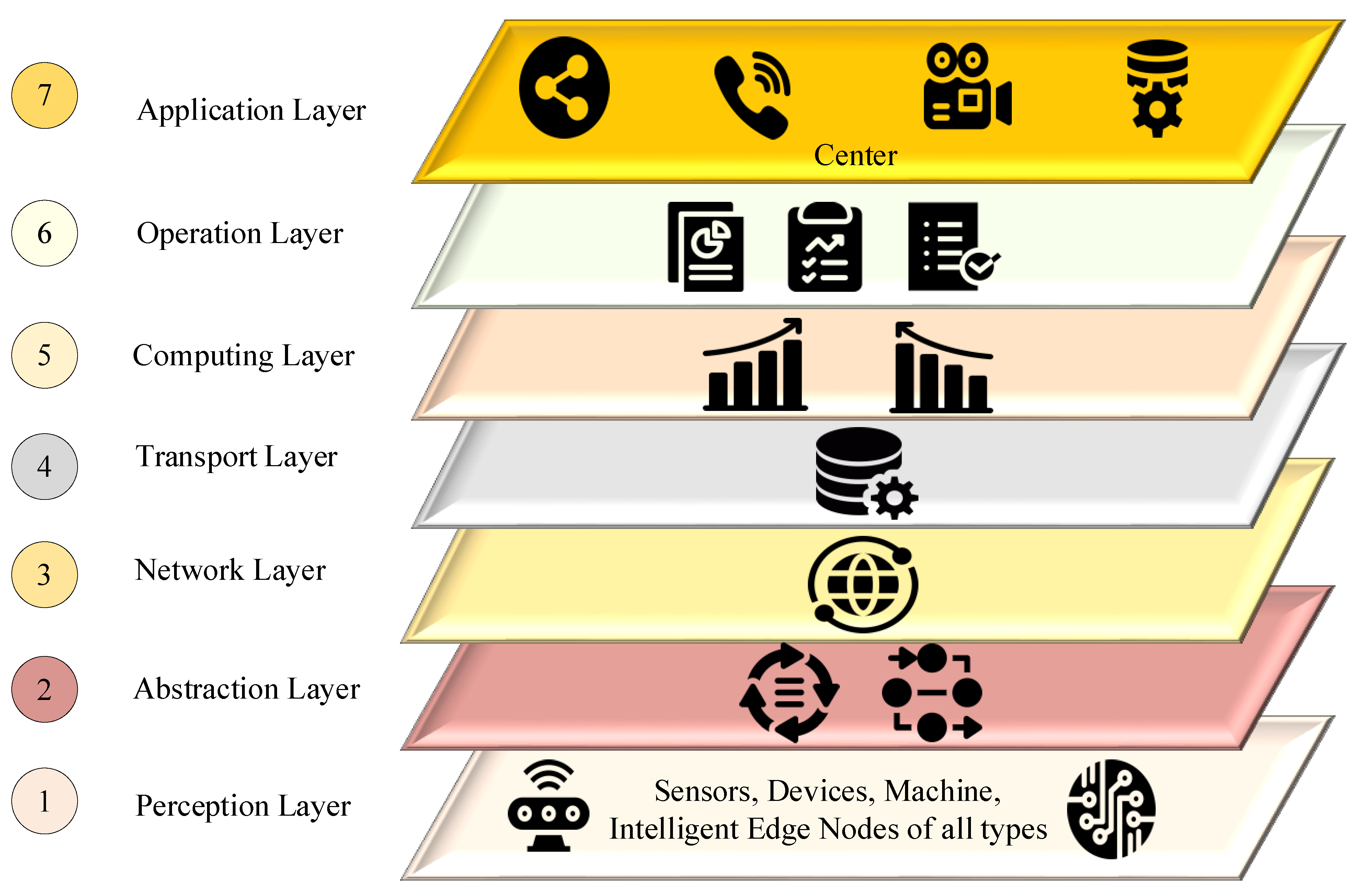
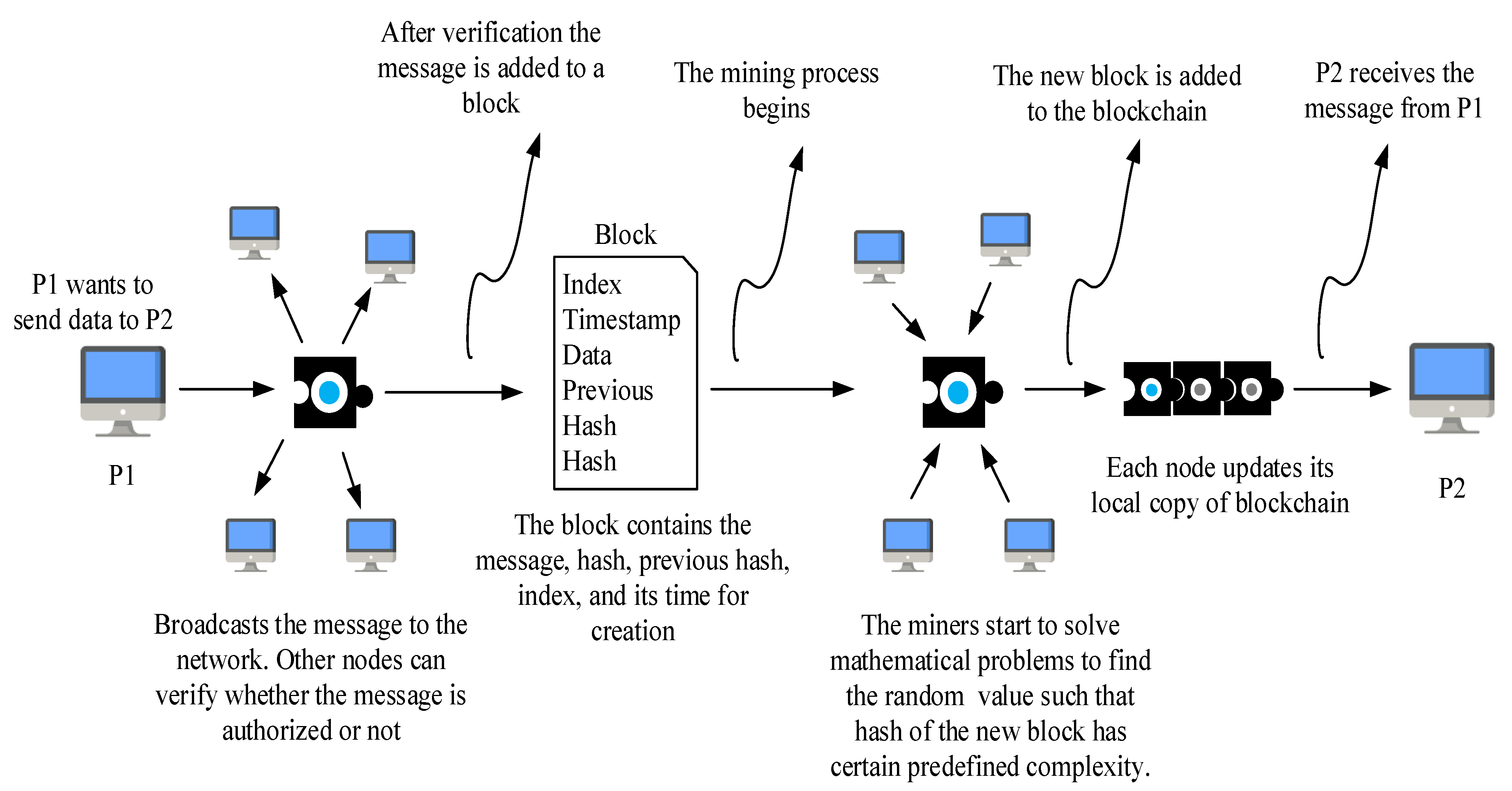

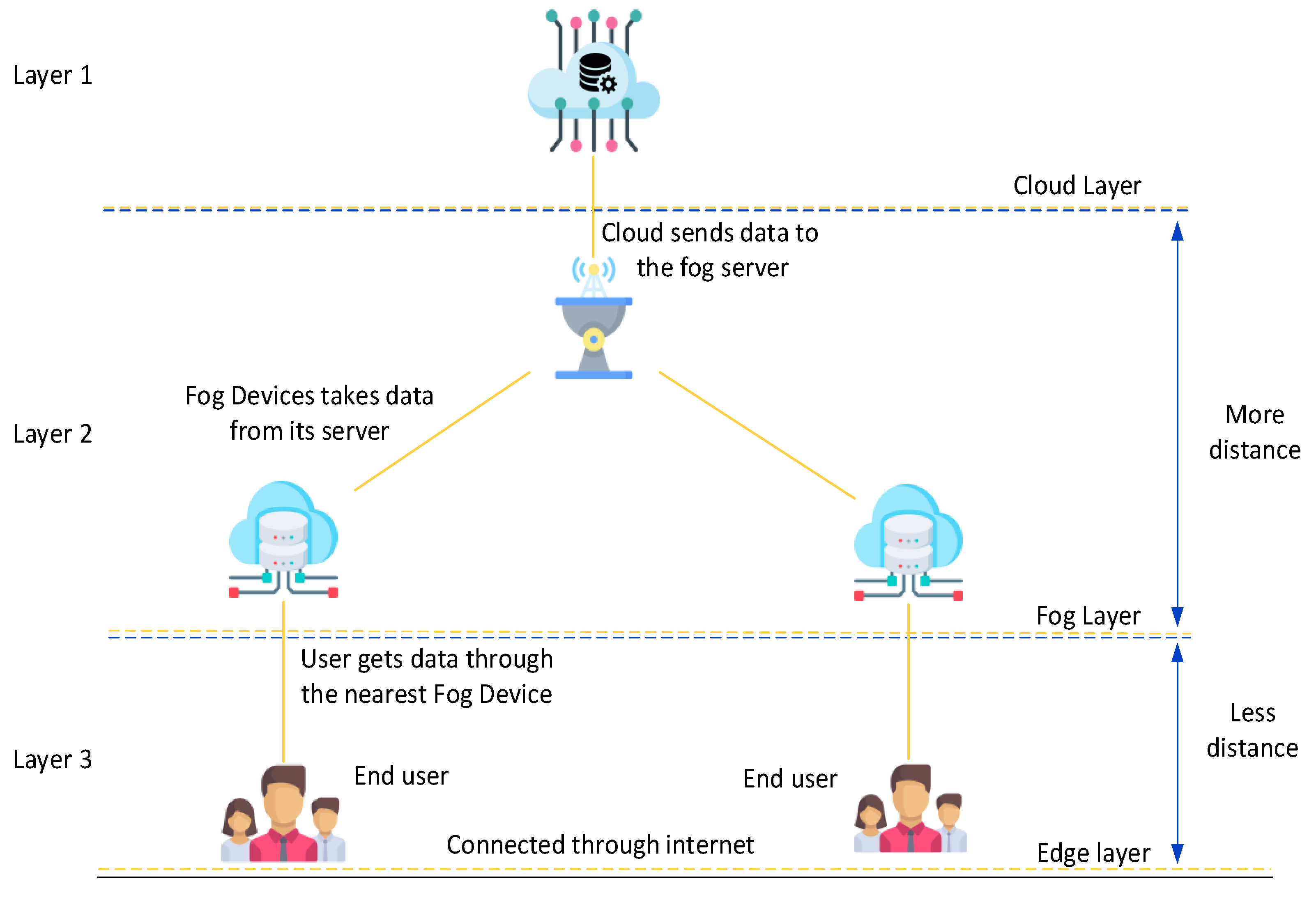


| Reference | Scope of Threats and Attacks Analysis | Technology Adopted for the Solution to Threats and Attacks | Research Gap and Open Challenges | Year | ||||
|---|---|---|---|---|---|---|---|---|
| Architecture | Protocols and Standards | BC | FC | EC | ML | |||
| [38] | ✕ | ✕ | ✕ | ✕ | ✓ | ✕ | ✓ | 2021 |
| [39] | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ | 2020 |
| [40] | ✕ | ✕ | ✓ | ✕ | ✕ | ✕ | ✓ | 2019 |
| [41] | ✕ | ✓ | ✕ | ✕ | ✕ | ✕ | ✓ | 2015 |
| [42] | ✕ | ✕ | ✓ | ✕ | ✕ | ✕ | ✓ | 2019 |
| [43] | ✓ | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ | 2017 |
| [44] | ✓ | ✕ | ✕ | ✓ | ✓ | ✕ | ✕ | 2017 |
| [45] | ✕ | ✓ | ✕ | ✕ | ✕ | ✕ | ✕ | 2019 |
| [46] | ✕ | ✕ | ✕ | ✕ | ✓ | ✕ | ✓ | 2021 |
| [47] | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ | ✓ | 2020 |
| [48] | ✓ | ✕ | ✓ | ✕ | ✕ | ✕ | ✕ | 2019 |
| [49] | ✓ | ✕ | ✓ | ✕ | ✕ | ✕ | ✓ | 2020 |
| [50] | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ | ✓ | 2019 |
| [51] | ✓ | ✕ | ✕ | ✕ | ✕ | ✓ | ✓ | 2020 |
| [52] | ✓ | ✕ | ✕ | ✕ | ✓ | ✕ | ✓ | 2017 |
| [53] | ✓ | ✓ | ✕ | ✕ | ✕ | ✕ | ✓ | 2019 |
| [54] | ✕ | ✓ | ✓ | ✕ | ✕ | ✕ | ✓ | 2020 |
| [55] | ✓ | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ | 2021 |
| [56] | ✕ | ✓ | ✕ | ✕ | ✕ | ✕ | ✓ | 2017 |
| [57] | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ | ✓ | 2019 |
| [58] | ✕ | ✕ | ✕ | ✓ | ✓ | ✕ | ✓ | 2020 |
| [59] | ✓ | ✕ | ✕ | ✓ | ✕ | ✕ | ✓ | 2020 |
| [60] | ✕ | ✕ | ✓ | ✕ | ✕ | ✕ | ✓ | 2019 |
| [61] | ✕ | ✓ | ✕ | ✕ | ✕ | ✕ | ✓ | 2019 |
| [62] | ✓ | ✕ | ✕ | ✕ | ✕ | ✓ | ✓ | 2019 |
| [63] | ✕ | ✕ | ✕ | ✕ | ✓ | ✕ | ✓ | 2018 |
| [64] | ✕ | ✕ | ✕ | ✓ | ✕ | ✕ | ✓ | 2018 |
| [65] | ✕ | ✕ | ✓ | ✕ | ✕ | ✓ | ✓ | 2018 |
| [66] | ✓ | ✓ | ✕ | ✓ | ✓ | ✕ | ✕ | 2019 |
| [67] | ✓ | ✕ | ✕ | ✕ | ✕ | ✓ | ✕ | 2020 |
| [68] | ✕ | ✓ | ✓ | ✕ | ✕ | ✕ | ✓ | 2019 |
| [69] | ✓ | ✕ | ✓ | ✓ | ✓ | ✓ | ✓ | 2019 |
| [70] | ✓ | ✕ | ✕ | ✕ | ✕ | ✓ | ✓ | 2020 |
| [71] | ✓ | ✓ | ✕ | ✕ | ✕ | ✕ | ✕ | 2018 |
| [72] | ✕ | ✕ | ✓ | ✕ | ✕ | ✕ | ✓ | 2020 |
| [73] | ✓ | ✓ | ✕ | ✕ | ✕ | ✕ | ✓ | 2020 |
| [16] | ✓ | ✓ | ✕ | ✕ | ✕ | ✕ | ✓ | 2017 |
| [74] | ✕ | ✕ | ✕ | ✕ | ✕ | ✕ | ✓ | 2019 |
| [75] | ✕ | ✓ | ✕ | ✓ | ✕ | ✕ | ✓ | 2019 |
| This survey | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | NA |
| Sensor Type | Sensor | Vulnerabilities |
|---|---|---|
| Motion Sensors | Accelerometer | Task Inference |
| Gyroscope | False Data Injection | |
| Linear Acceleration Sensor | Malware Transmission | |
| Environmental Sensors | Light Sensor | Eavesdropping |
| Proximity Sensor | Task Inference | |
| Air Pressure Sensor | Smudge Attack | |
| Audio Sensor | False Data Injection | |
| Temperature Sensor | Transferring Malware | |
| Soil Moisture sensor | DoS | |
| Noise Sensor | Information Leakage | |
| Position Sensors | GPS | Location Inference |
| Magnetic Sensor | Eavesdropping False Data Injection |
| Broad Category | Dominant Protocols | Functionality | |
|---|---|---|---|
| Application protocol | CoAP, DDS, AMQP, MQTT, MQTT-SN, XMPP, HTTP REST | Services to end-users for various applications | |
| Service discovery protocol | mDNS, DNS-SD | Domain name resolution, client pairing for service discovery | |
| Connectivity and networking protocol | Routing protocol | RPL | Routing in low power lossy networks |
| Network layer protocol | 6LoWPAN, IPv4, IPv6 | To provide networking for effective communication in IoT over the existing IPv4 and IPv6 infrastructure | |
| Data link layer protocol | IEEE 802.15.4 | To provide channel access, coordination, scheduling, and resource management tasks. | |
| Connectivity protocol | LTE-A, EPC global, IEEE 802.15.4, Z-Wave | To interconnect IoT devices at the perception layer for effective communication | |
| Other dominant protocols | IEEE 1888.3, IPSec, IEEE 1905.1 | To provide interoperability, security in an IoT environment | |
| Threats/Attacks | Scope on Different Layers in IoT Architecture | Scope on Different Protocols and Standards of IoT | Impact | References Focusing Detection, Prevention, or Mitigation Strategies |
|---|---|---|---|---|
| Eavesdropping | PL, AbsL, NL, TL | AP, SDP, RP, NLP, DLLP, CP, ODP | Affect user’s privacy and confidentiality | [124,125] |
| Battery drainage | PL | CP | Drain the batters of IoT devices at a much faster rate | [126] |
| Hardware failure | PL | NLP, CP | Affect the service due to failure causing unreliability | [127,128] |
| Malicious data injection | PL, | AP, SDP, ODP | Can harm applications services | [129] |
| Sybil threat | PL, NL | SDP, CP | Enhances packet drop probability | [130,131] |
| Disclosure of critical information | PL, AL | AP, SDP, | Affect user’s privacy | [132] |
| Node cloning | PL | SDP, DLLP, NP, CP | Can copy the functions, data, etc., of a particular node or even capture a node | [133,134] |
| Side-channel attack | PL, AbsL | SDP, RP | Indirect attack on node leaking sensitive information | [135] |
| RF jamming | PL, TL | CP | Cause interreference, and DoS | [136,137] |
| Physical damage | PL | CP, DLLP | Affect service of a node | [127] |
| Exhaustion attack | PL, CL | SDP, NLP, DLLP, CP | Affect network lifetime | [138] |
| Node outage | PL | SDP, CP | Causing unreliability | [126] |
| Node replication | AbsL | ODP, SDP, NLP | Injecting huge traffic flow | [139] |
| Illegal access | AbsL, NL, CL, OL | AP, SDP | Can steal user’s confidential data | [126] |
| Device compromise | AbsL, NL | AP, SDP, RP, NLP, DLLP, CP, ODP | Affect credibility of device | [140] |
| MITM | AbsL, NL, OL | AP, SDP, RP, NLP, DLLP, CP, ODP | Affect network resources and authenticity | [141] |
| Spoofing | AbsL, NL, AL | AP, SDP, RP, NLP, DLLP, CP | Affect trust and confidentiality | [142] |
| Threats to communication protocols | AbsL | CP, NLP, DLLP | Affect connectivity | [143] |
| Tag cloning | AbsL | SDP, RP | Affect authenticity | [144] |
| DoS | AbsL, TL, OL | AP, SDP, RP, NLP | Affect service availability resulting in huge losses | [145] |
| DDoS | AbsL, TL, AL | AP, SDP, RP, NLP | Affect reliability, and availability | [146] |
| Traffic analysis | AbsL, NL | NLP | Affect user’s privacy and confidentiality | [124] |
| Sleep deprivation attack | AbsL | SDP, DLLP | Affect the network lifetime | [147] |
| Fragmentation threat | NL | NLP, RP | Affect data integrity | [148] |
| Hello flood | NL | NLP, RP | Creates unnecessary traffic in the system | [149] |
| Network intrusion | NL | NLP, RP, CP | Affect the network resources | [79] |
| Insertion of rogue devices | NL | NLP, RP, ODP, CP | Affect network security and data integrity | [150] |
| Sinkhole | NL | NLP, RP | Result in network failure | [151] |
| Clone ID attack | NL | NLP, RP | Results in other network attacks | [152] |
| Selective forwarding attack | NL | NLP, RP, DLLP | Affect data integrity | [153] |
| Blackhole attack | NL | NLP, RP | Affect entire network | [154] |
| Wormhole attack | NL | SDP, RP, NLP, DLLP, CP, ODP | Affect entire network | [155,156] |
| RPL exploit | NL | RP | Affect routing of packets | [157,158] |
| False data injection | TL, CL | DLLP, CP | Affect the legitimate information | [129] |
| Unfair access | TL | AP, SDP, RP, NLP, DLLP, CP, ODP | Affect the performance | [145] |
| Congestion | TL | AP, ODP | Can cause more packet drop and latency | [126] |
| Desynchronization | TL | SDP, RP, NLP, DLLP | Affect data integrity | [159] |
| MQTT-exploit | TL | AP | Affect transmission of packets | [160] |
| Session hijacking | TL | SDP, RP, NLP, DLLP, CP | Exploitation and tampering with the legitimate session | [161] |
| SYN-flooding | TL | SDP, RP, NLP | Affect node resources such as energy and memory | [162] |
| Timing attack | TL | SDP, RP, CP | Leads to SCA | [163] |
| SQL injection | CL, AL | AP, SDR, ODP | Affect SQL database | [164] |
| Data integrity | CL | AP | Affect credibility of data | [141] |
| Virtualization | CL | AP, SDP, ODP | Affect data protection | [165] |
| Software modification | CL | AP, SDP, ODP | Affect entire application resources | [166] |
| Identity theft | CL | AP, SDP | Affect user’s privacy, and data confidentiality | [167] |
| Access attack | CL | AP, SDP, RP, NLP, DLLP, CP, ODP | Can steal valuable data from the network | [126] |
| Cloud outage | CL | AP, SDP, RP, NLP, DLLP, CP, ODP | Affect cloud-related services | [166] |
| Signature wrapping | CL | AP, SDP | Affect signature algorithm resulting in eavesdropping attack | [168] |
| Storage attack | CL | AP, SDP, NLP | Affect the data storage | [166] |
| Path-based DoS attack | CL | RP, NLP | Affect application layer similar to DoS | [169] |
| Badmouthing | OL | AP, ODP | Affect the credibility | [126] |
| Unauthorized access | OL | AP, SDP, CP | Can result in stealing of critical information | [167] |
| User privacy compromise | OL | AP | Affect the privacy of users | [167] |
| Secure on-boarding attack | OL | AP, SDP, NLP, DLLP, CP | Can cause eavesdropping during on-boarding of new devices | [170] |
| Firmware attack | OL | AP, SDP, RP, NLP, DLLP, CP | Affect low-level control software of IoT | [171] |
| Software attack | OL | AP, CP | Affect software of IoT | [171] |
| End-to-end encryption attack | OL | AP | Affect privacy and integrity of the end-users | [172] |
| Interrogation attack | OL | AP, SDP, RP, NLP, DLLP, CP, ODP | Affect the channel resources | [173] |
| Malicious code | AL | AP | Can cause illegitimate access to the IoT resources | [174] |
| Virus attack | AL | AP | Affect high-end IoT devices | [175,176] |
| Malware attack | AL | AP, SDP | Affect high-end IoT devices causing user’s security concern | [175,176] |
| Spyware attack | AL | AP, SDP | Indirect harm to users | [177] |
| Intersection | AL | AP, SDP | Affect privacy | [178] |
| Message forging | AL | AP | Can steal critical information | [179] |
| Brute force attack | AL | AP, SDP, ODP | Affect the user’s privacy and can steal critical login information | [174] |
| Burgeoning Technology | Scope of Security Enhancement in IoT |
|---|---|
| BC | Due to its key operational characteristics such as decentralized behavior, encryption-based communication, distributed functionality, inbuilt cryptography, authenticated access, etc., it offers security solutions against several threats and attacks across multiple layers of the IoT such as malicious data injection, disclosure of critical information, device compromise, node cloning, tag cloning, exhaustion attack, illegal access, information theft, spoofing, data manipulation, false data injection, unfair access, session hijacking, unfairness attack, fake information, unauthorized access, stealing users critical information, illegal interventions, software modification, message forging, brute force attack, etc. |
| FC | With abundant capabilities in processing, storing, managing the voluminous data, it offers security solutions against various threats and attacks such as eavesdropping, hardware failure, disclosure of critical information, device compromise, node capture attack, node tampering, battery drainages attack, node replication, illegal access, MITM, information theft, data manipulation, DoS, DDoS, false data injection, session hijacking, malicious attack, data integrity, virtualization, illegal access, cloud malware injection, illegal intervention, etc. |
| EC | The real-time services such as identity recognition, intrusion detection, access management, etc., enable EC to enhance security against several threats and attacks such as eavesdropping, battery drainage, hardware failure, node capture, DoS, DDoS, jamming, malicious attack, SQL injection, data integrity, virtualization, illegal access, flooding attack in the cloud, access attack, signature wrapping, etc. |
| ML | With enormous success in the paradigm of speech recognition, fraud detection, computer vision, spam detection, computer networks, etc., it is envisaged to solve several threats and attacks persisting to IoT. Some of these include device compromise, Sybil threat, node cloning, node capture, RF jamming, battery drainage attack, node replication, MITM, information theft, threats to communication protocols, DoS, DDoS, SCA, hello flood, congestion, MQTT-exploit, hole attack, firmware attack, illegal intervention, SQL injection, cross-site script, intersection, etc. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Krishna, R.R.; Priyadarshini, A.; Jha, A.V.; Appasani, B.; Srinivasulu, A.; Bizon, N. State-of-the-Art Review on IoT Threats and Attacks: Taxonomy, Challenges and Solutions. Sustainability 2021, 13, 9463. https://doi.org/10.3390/su13169463
Krishna RR, Priyadarshini A, Jha AV, Appasani B, Srinivasulu A, Bizon N. State-of-the-Art Review on IoT Threats and Attacks: Taxonomy, Challenges and Solutions. Sustainability. 2021; 13(16):9463. https://doi.org/10.3390/su13169463
Chicago/Turabian StyleKrishna, Ritika Raj, Aanchal Priyadarshini, Amitkumar V. Jha, Bhargav Appasani, Avireni Srinivasulu, and Nicu Bizon. 2021. "State-of-the-Art Review on IoT Threats and Attacks: Taxonomy, Challenges and Solutions" Sustainability 13, no. 16: 9463. https://doi.org/10.3390/su13169463
APA StyleKrishna, R. R., Priyadarshini, A., Jha, A. V., Appasani, B., Srinivasulu, A., & Bizon, N. (2021). State-of-the-Art Review on IoT Threats and Attacks: Taxonomy, Challenges and Solutions. Sustainability, 13(16), 9463. https://doi.org/10.3390/su13169463









