A Survey of Context-Aware Messaging-Addressing for Sustainable Internet of Things (IoT)
Abstract
:1. Introduction and Background
- Tourism: This type of application provides the user with appropriate information relative to towns, museums, or sites they visit.
- Fieldwork: Where context is simultaneous regarding recording, separating, and presentation of information with respect to remarks made in fieldwork environment, for example, in the scope of archaeology/health.
- Expanded devices: Devices, especially handheld processing devices, are set up with at least one sensor to permit them to react to changes in the surrounding conditions.
- Management of resources: Resources are managed by making the computing devices and rooms/buildings aware of their context.
- Communication collaboration, and coordination: Context is utilized to arrange and help the correspondence, association, and coordination between users, such as selecting the most appropriate communication channel in a certain situation.
- storage and retrieval of information: The storage and retrieval of contextual information, such as names and addresses/documents.
Problem Formulation and Methodology
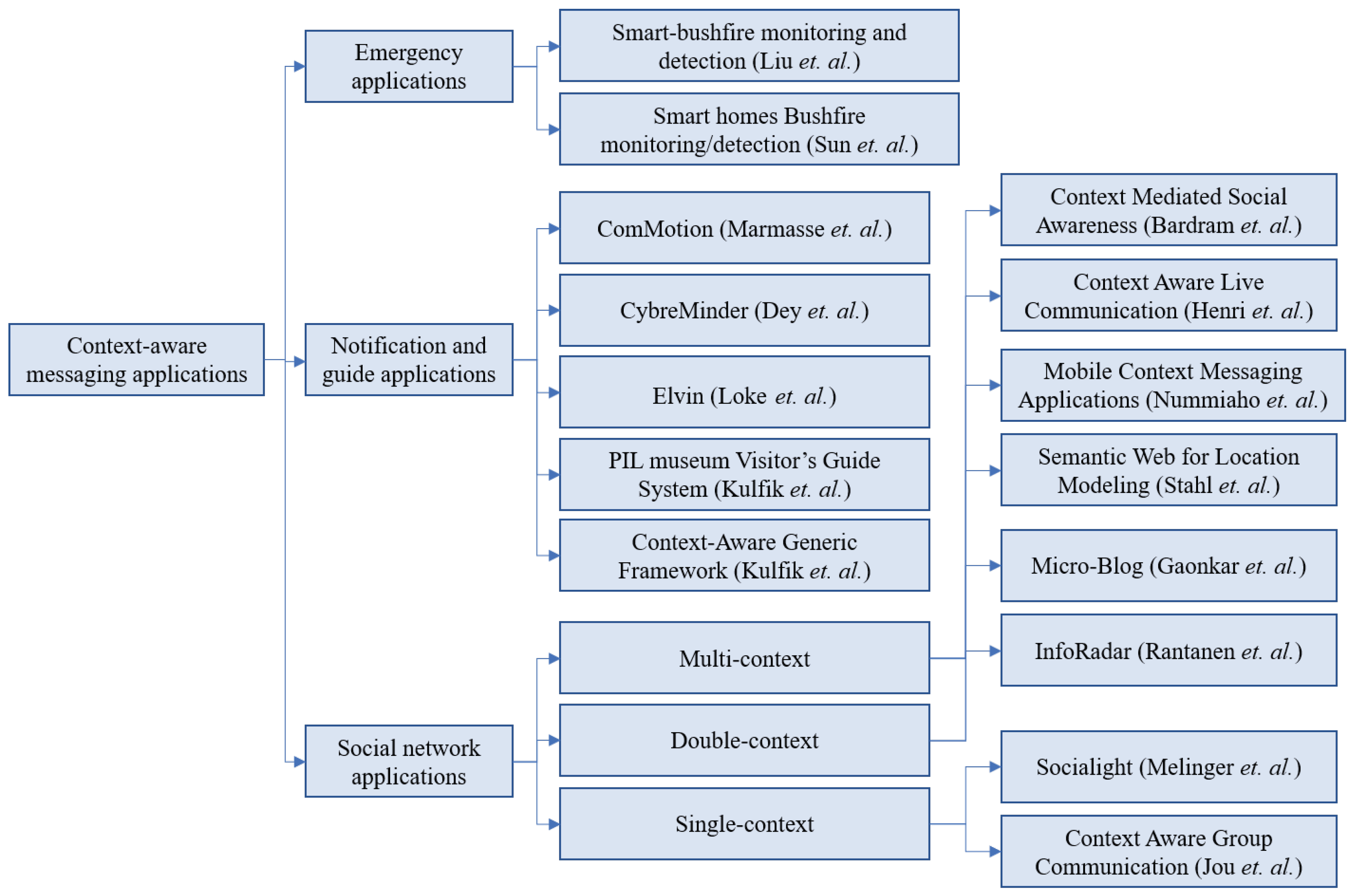
2. Applications that Use Context-Aware Messaging
2.1. Context-Aware Messaging in Emergency Applications
2.1.1. GSM Technology for a Smart Bushfire Monitoring System
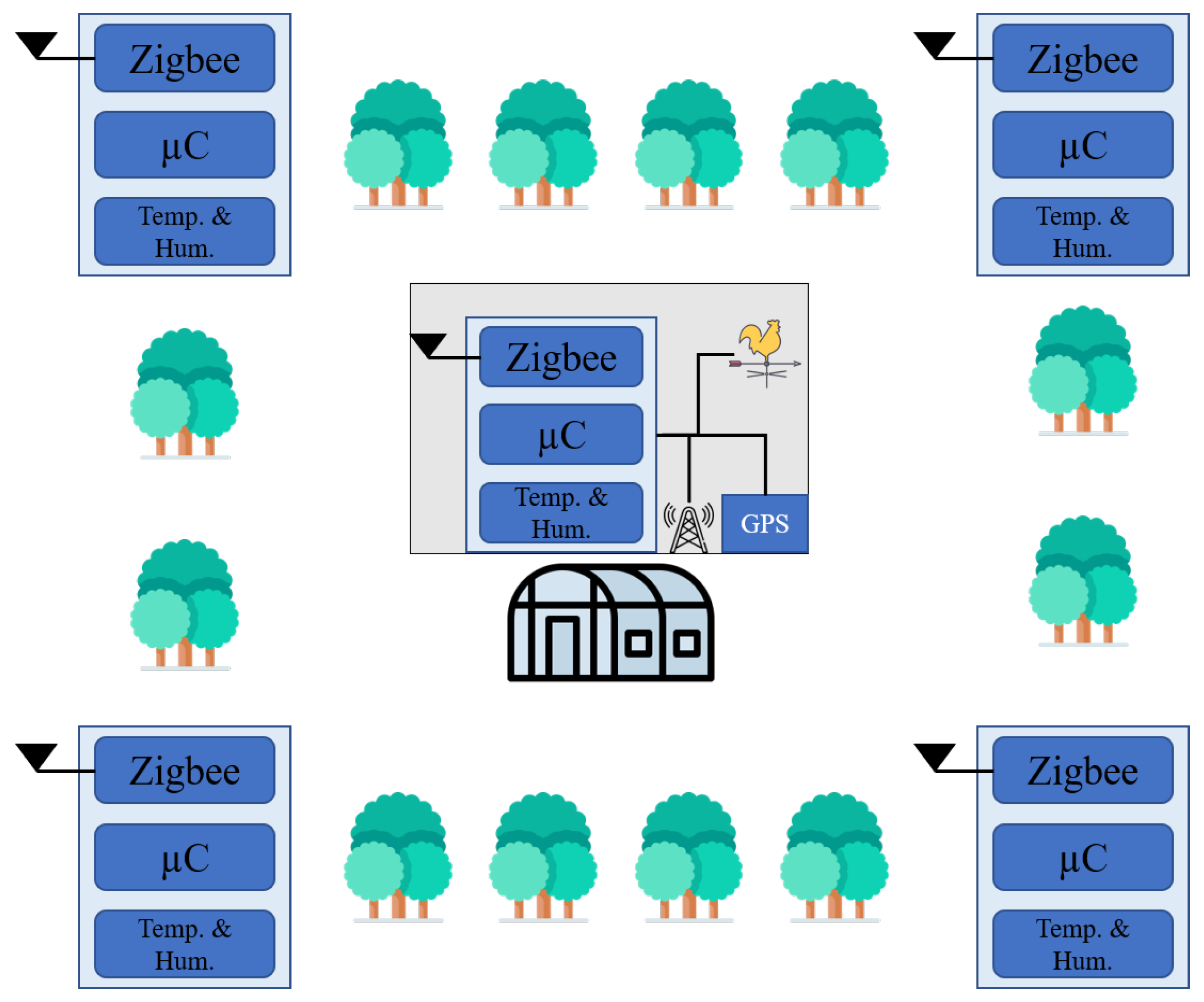
2.1.2. ZigBee-Based Smart-Homes Application System
2.2. Context Aware Applications for Reminder, Guidance, and Notification
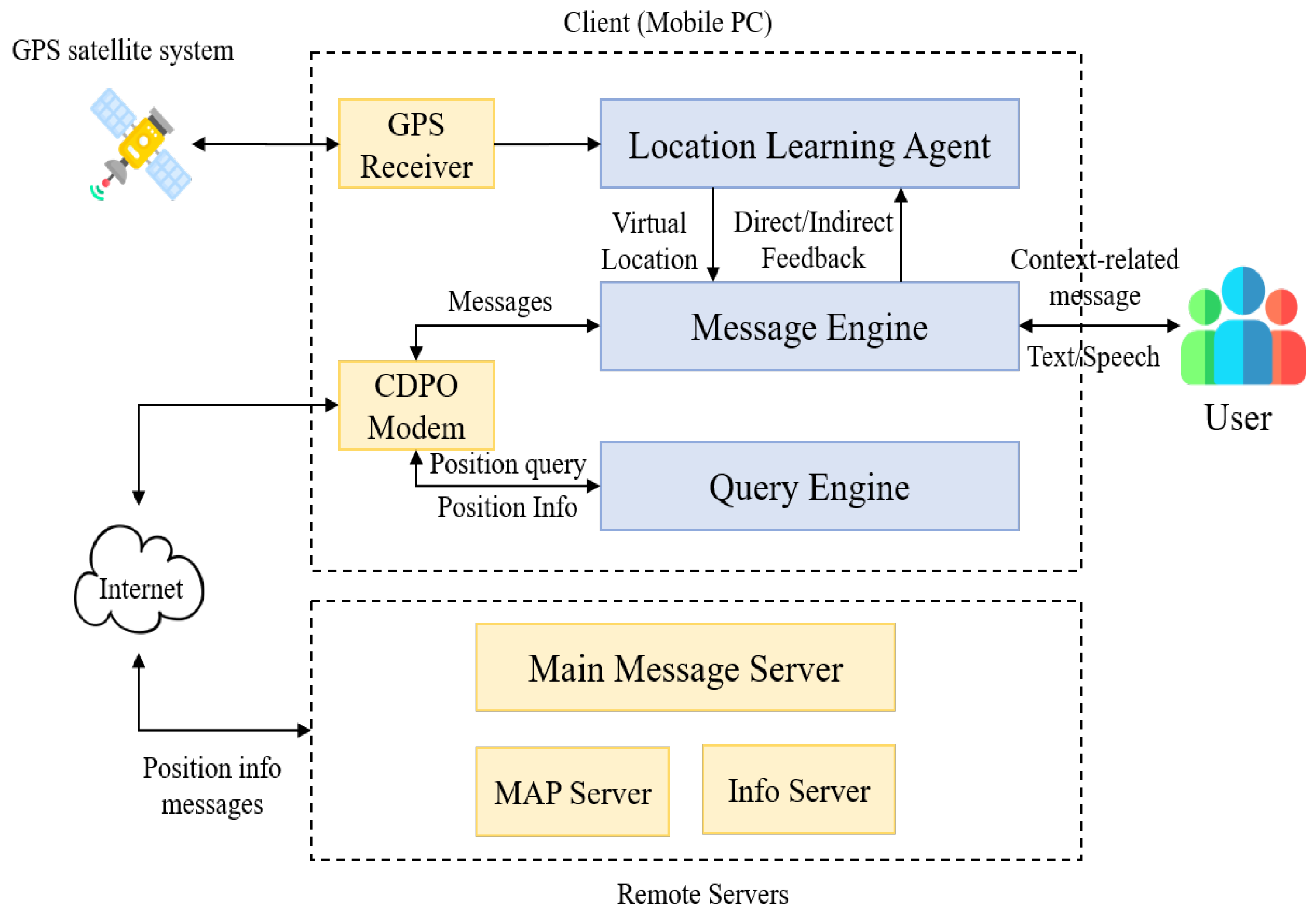
2.2.1. ComMotion
2.2.2. CybreMinder
2.2.3. Elvin for Inter-Agent Context-Aware Messaging
2.2.4. Visitor’s Guide System for PIL Museum
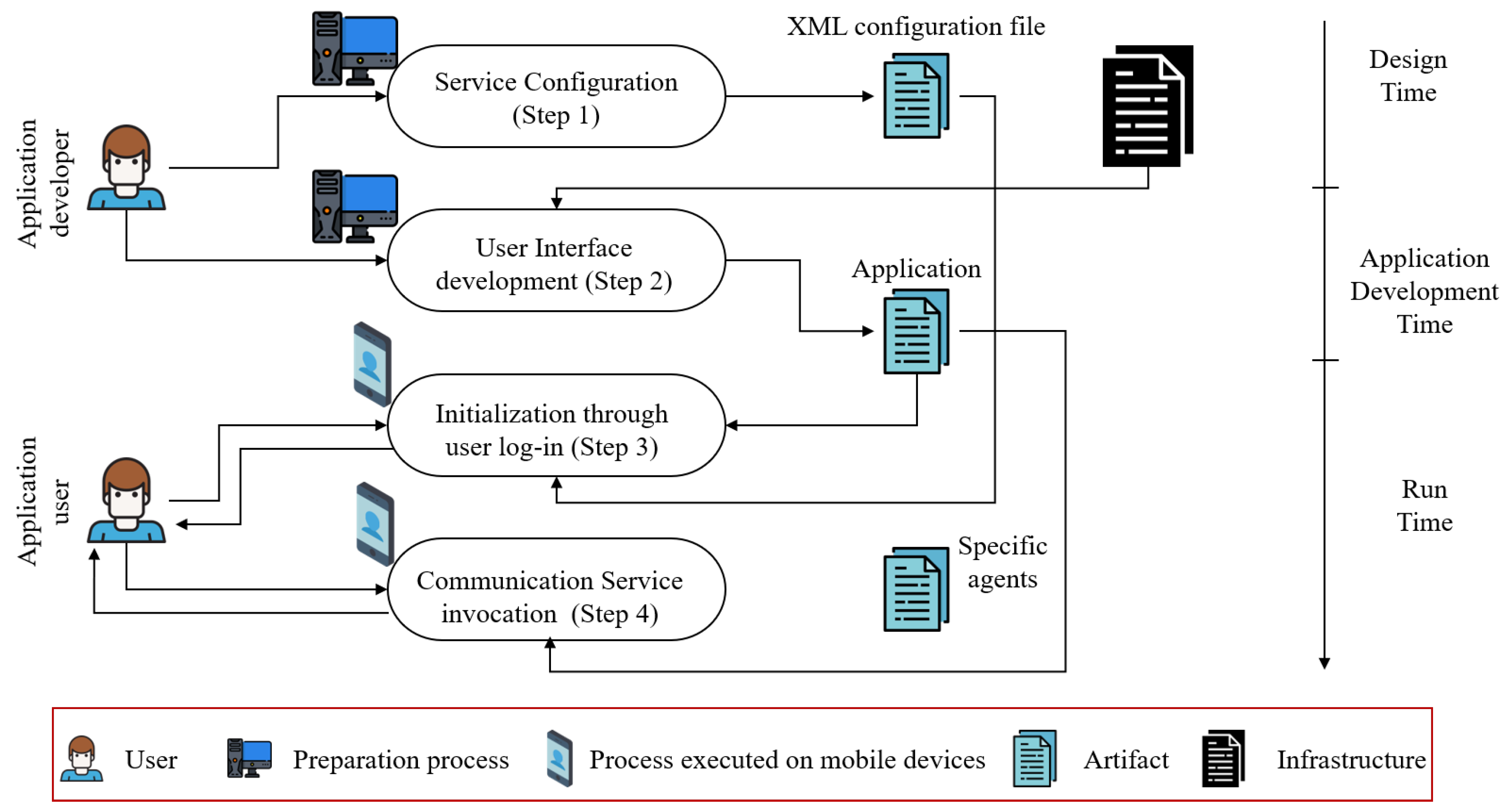
2.2.5. Conventional Framework for Context-Aware Communication Services for Visitor’s Guides
- Design time where the Communication Service Definition tool identifies the communication services.
- Application development time includes user interface development as well as the demands for sending or receiving services that are prepared at the design time.
- Runtime initialization level, the communication service generator produces communication services automatically.
- After the initialization of runtime, users can employ the communication services using the user interface.
2.3. Context-Aware Messaging in Social Network Applications
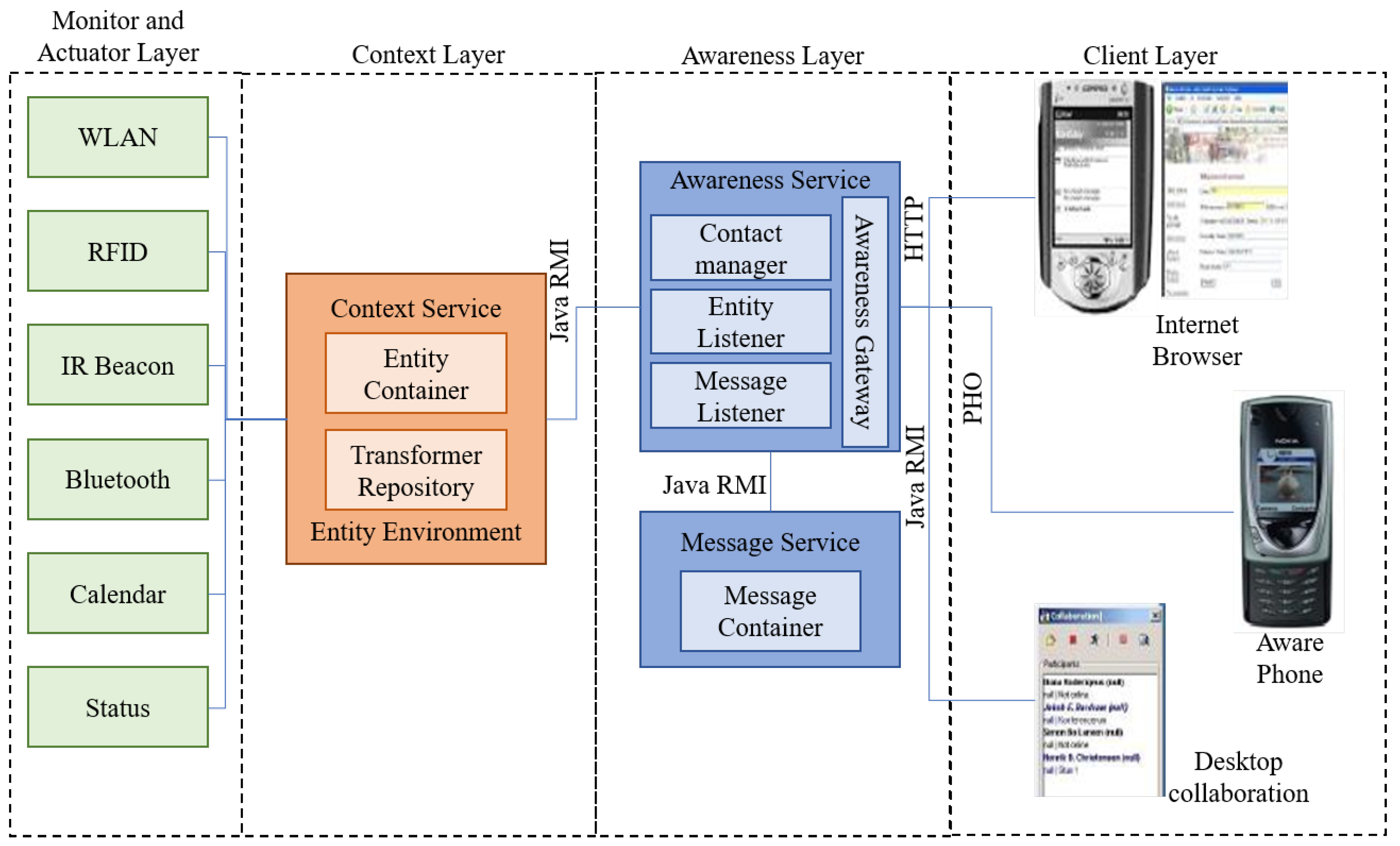
2.3.1. Context-Mediated Social Awareness Application
- The Client layer includes end-user applications using the framework as a back-end system. For example, internet browser, phone, or client layer.
- The Awareness layer contains the awareness service and message service or IM service, such as an SMS/MMS.
- The Context layer is responsible for the administration, transformation, and distribution of contextual information.
- The Monitor and Actuator layer is accountable for context gathering using numerous sensing and actuator technologies.
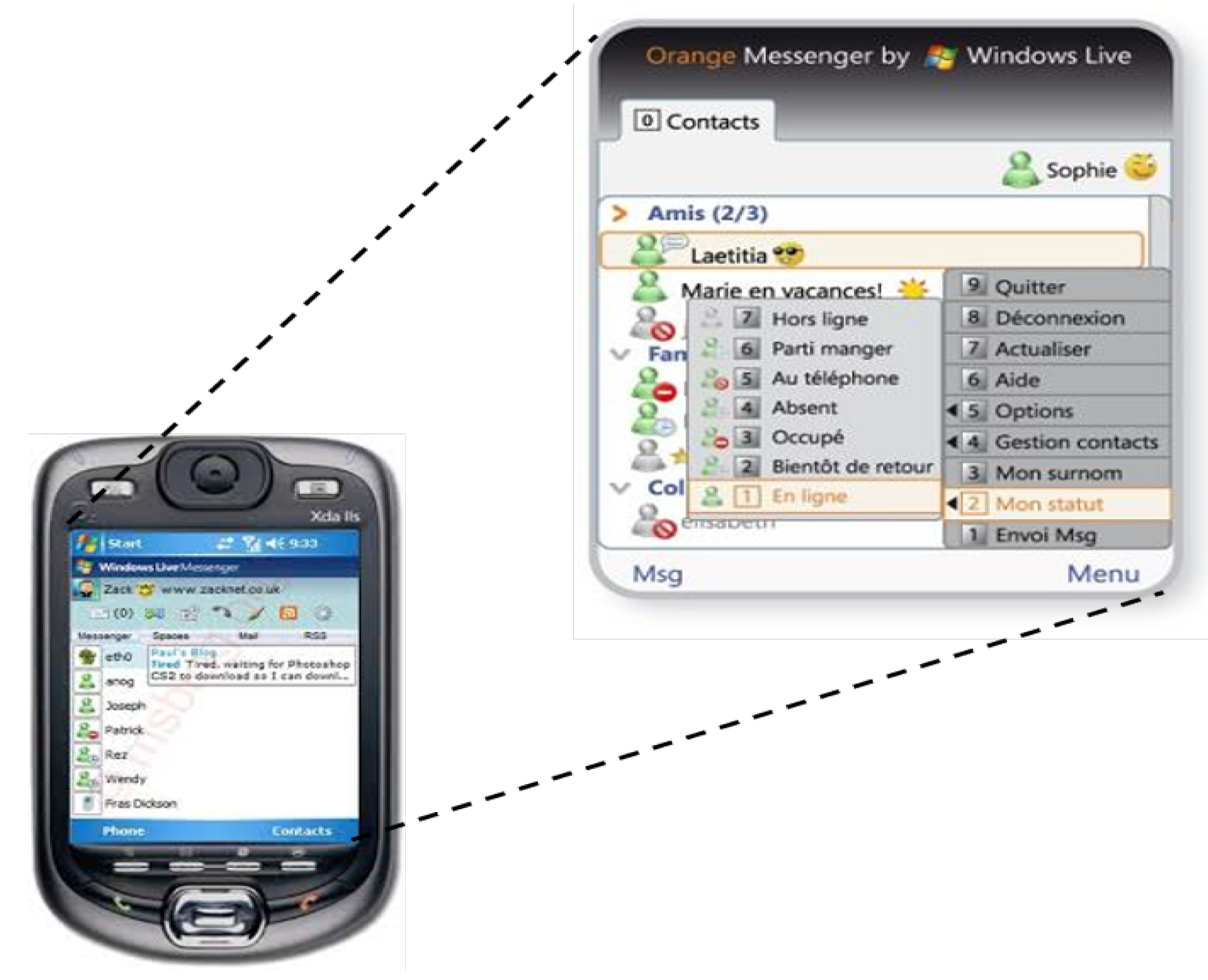
2.3.2. Context-Aware Communication with Live Contacts
2.3.3. A Framework for Mobile Context-Based Messaging Applications
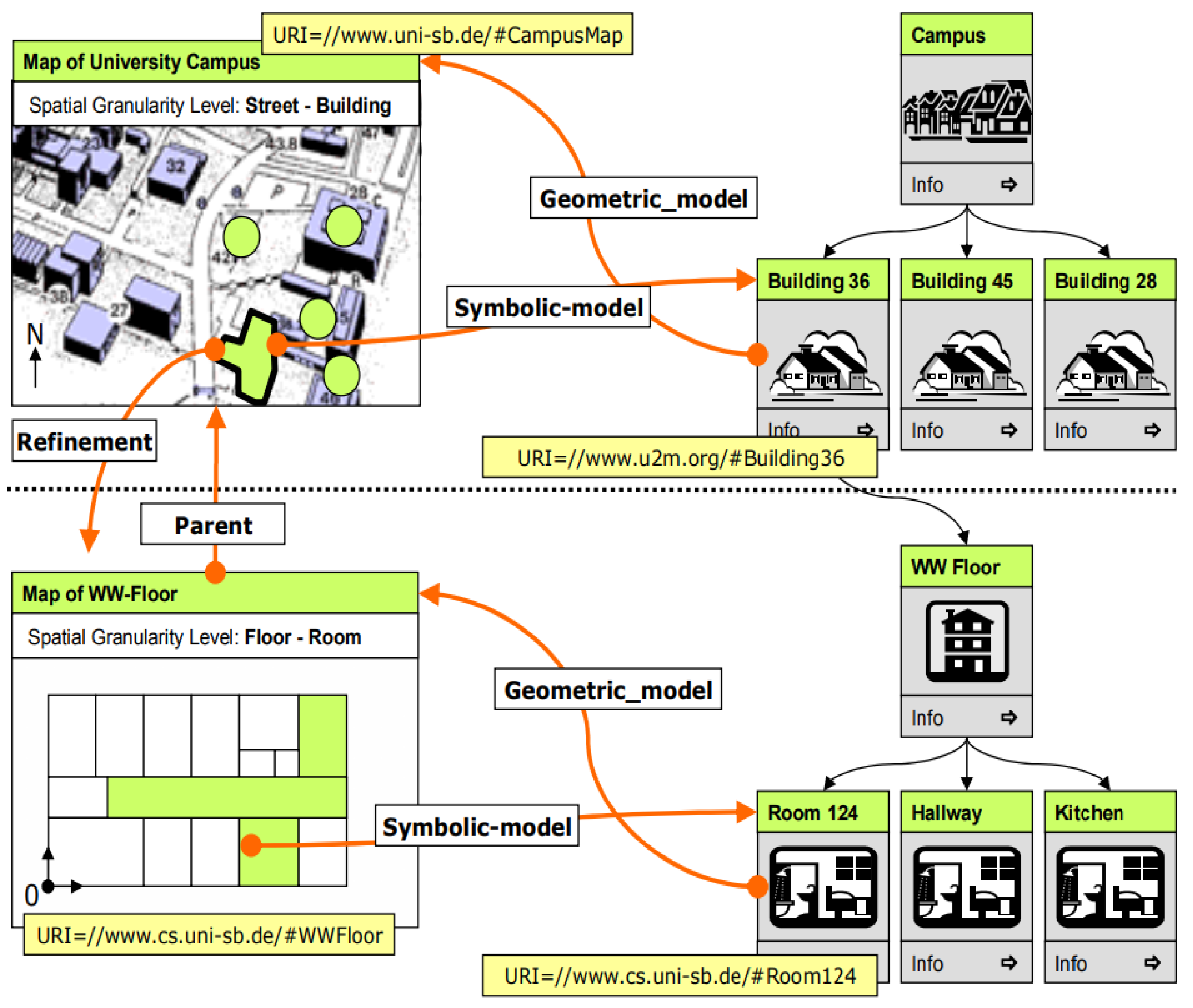
2.3.4. Using Semantic Web Technology for Ubiquitous Hybrid Location Modeling Application
2.3.5. Micro-Blog
2.3.6. InfoRadar
2.3.7. Socialight: A Mobile Social Networking System
- Friend Locator, which allows the user to discover the location of their friend within the surrounding area. (Many current social networking applications such as Facebook Places and Foursquare have such features.)
- Tap and Tickle, which allows the user to communicate with another friend on the network by controlling the length of vibration on their phone.
- Sticky Shadow, which is a location-based messaging feature built around a geographical place for specific users. The content of the messages can include text, audio, video, or any combination thereof.
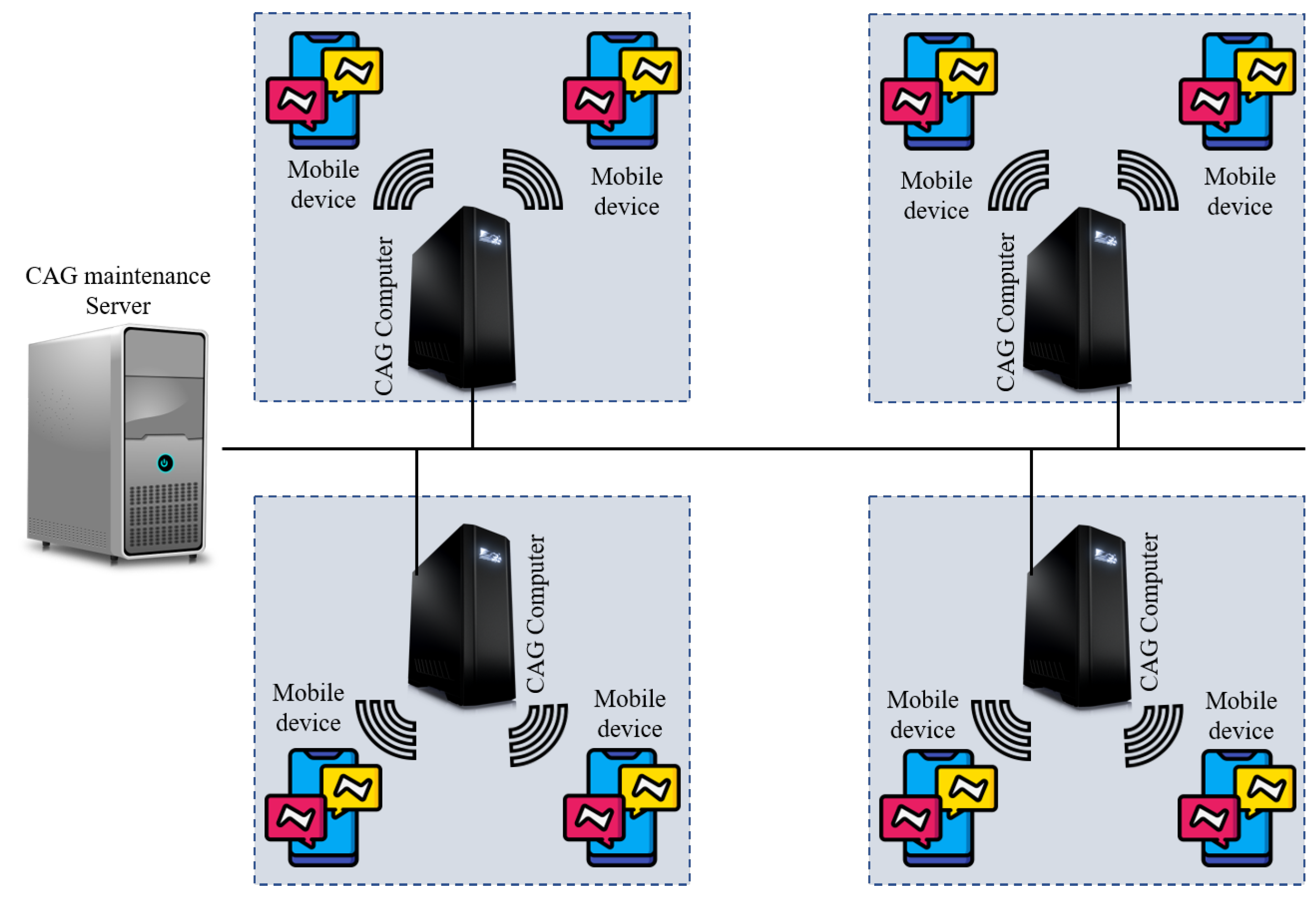
2.3.8. Context-Aware Group (CAG) Communication System
3. Recent Related Work
3.1. Machine Learning-Based Context-Aware Messaging
3.2. Context-Aware Sentiment Analysis
3.3. Context-Aware Security Applications
4. Discussion
5. Observations and Conclusions
- There is a tremendous similarity in the systems we reviewed in terms of architecture and the way context is used, even when the application type is different, thereby suggesting the feasibility of a general context-aware messaging framework applicable to a wide range of applications, where the range of context information used can be adapted (e.g., some use only location, and others, location, time, user profile, etc.).
- There is a need to combine indoor and outdoor positioning in the direction of several systems mentioned above, but to be able to do so an integrated manner (e.g., to be able to send messages to everyone within the Chadstone shopping mall or near it, say, the parking area or on a route leading into the mall. There is a need to exploit richer spatial information, not just point-based locations, but geofencing and being able to use spatial features of the environment for addressing (e.g., send a message to all the people near that pond), which has not been addressed in the reviewed systems. The potential of activity-awareness, situation-awareness, and context-awareness for messaging has only been explored to a limited extent in the work reviewed. Richer context can be explored for future context-aware communication and messaging, e.g., information about the situations or activities of people; for example, we might want to send a message to “everyone running or walking (and not those standing still) in a particular area, next to burning building” or even more precisely, to “everyone who started running or walking (and not those standing still) away from the burning building, in a particular area, 5 min ago and who are still doing so”.
- Hybrid peer-to-peer and centralized client-server architectures have tremendous value, and current context-aware messaging has not fully exploited their potential; e.g., peer-to-peer devices can share contexts to route messages, and as mobile devices move, they can act as probes providing light into more areas and places. Moreover, peer-to-peer messaging, using Bluetooth, for example, can complement other wide-area communication mechanisms (e.g., SMS) in a hybrid style communication, which may be useful in emergency settings when network coverage is reduced.
- In the applications reviewed, some utilized text and others richer media as smartphones and mobile devices become more powerful, and there is an opportunity to use rich media, even videos, and combinations of sound and graphics in messages that provide better information for emergency and/or social networking reasons.
- Redundancy of communication is not fully exploited in the above systems we reviewed—especially dealing with dynamically changing contexts, errors in sensed context, or node and system failures.
- Machine learning techniques have proven their importance in context-aware messaging applications. Numerous researchers have proposed techniques based on supervised, semi-supervised, and deep learning strategies for the context-aware classifications, which can be utilized to suggest context-aware messaging for IoT applications. However, most of the works focus on manifest contents and neglect individual elements and logical variables that may influence a user’s decisions for messages.
- For context-aware sentiment analysis, multiple domain-specific repositories have been designed so that a few words can have various meanings. However, a significant challenge is that these repositories require linguistic assets that are lacking for certain languages such as Chinese.
- Privacy and security have not been dealt with extensively in the reviewed systems; for example, controlling the extent that someone’s location is revealed (whether by frequency of reporting or obfuscating the location, or adapting the presentation of locations at different granularities/accuracies depending on levels of friendship).
Author Contributions
Acknowledgments
Conflicts of Interest
Abbreviations
| IET | information engineering technology |
| IoT | Internet of Things |
| UC | ubiquitous computing |
| CET | communication engineering technologies |
| SMS | short messaging service |
| GPS | Global positioning system |
| ID | identification |
| mC | microcontroller |
References
- Weiser, M. The future of ubiquitous computing on campus. Commun. ACM 1998, 41, 41–42. [Google Scholar] [CrossRef]
- Nummiaho, A. User survey on context-aware communication scenarios. In Proceedings of the 4th International Conference on Mobile Technology, Applications, and Systems and the 1st International Symposium on Computer Human Interaction in Mobile Technology, New York, NY, USA, 10–12 September 2007; pp. 478–481. [Google Scholar]
- Lehikoinen, J.T.; Kaikkonen, A. PePe field study: Constructing meanings for locations in the context of mobile presence. In Proceedings of the 8th Conference on Human-Computer Interaction with Mobile Devices and Services, Helsinki, Finland, 12–15 September 2006; pp. 53–60. [Google Scholar]
- Wu, J.; Guo, S.; Li, J.; Zeng, D. Big data meet green challenges: Big data toward green applications. IEEE Syst. J. 2016, 10, 888–900. [Google Scholar] [CrossRef]
- Wu, J.; Bisio, I.; Gniady, C.; Hossain, E.; Valla, M.; Li, H. Context-aware networking and communications: Part 1 [guest editorial]. IEEE Commun. Mag. 2014, 52, 14–15. [Google Scholar] [CrossRef] [Green Version]
- Atat, R.; Liu, L.; Wu, J.; Li, G.; Ye, C.; Yang, Y. Big data meet cyber-physical systems: A panoramic survey. IEEE Access 2018, 6, 73603–73636. [Google Scholar] [CrossRef]
- Want, R.; Hopper, A.; Falcao, V.; Gibbons, J. The active badge location system. Trans. Inf. Syst. (TOIS) 1992, 10, 91–102. [Google Scholar] [CrossRef]
- Schilit, B.N.; Theimer, M.M. Disseminating active map information to mobile hosts. Network 1994, 8, 22–32. [Google Scholar] [CrossRef]
- Damasceno, K.; Cacho, N.; Garcia, A.; Romanovsky, A.; Lucena, C. Exception handling in context-aware agent systems: A case study. Springer LNCS 2007, 4408, 57–76. [Google Scholar]
- Geiger, L.; Durr, F.; Rothermel, K. On context cast: A context-aware communication mechanism. In Proceedings of the 2009 IEEE International Conference on Communications, Dresden, Germany, 14–18 June 2009; pp. 1–5. [Google Scholar]
- Buthpitiya, S.; Madamanchi, D.; Kommaraju, S.; Griss, M. Mobile context-aware personal messaging assistant. In Proceedings of the International Conference on Mobile Computing, Applications, and Services MobiCASE 2009: Mobile Computing, Applications, and Services, San Diego, CA, USA, 26–29 October 2009; pp. 254–272. [Google Scholar]
- Abbaspour, R.A.; SamadZadegam, F. Building a Context-aware Mobile Tourist Guide System based on Service Oriented Architecture. Int. Arch. Photogramm. Remote Sens. Spat. Inf. Sci. 2008, 37, 871–874. [Google Scholar]
- Hofer, T.; Schwinger, W.; Pichler, M.; Leonhartsberger, G.; Altmann, J.; Retschitzegger, W. Context-awareness on mobile devices-the hydrogen approach. In Proceedings of the 36th Annual Hawaii International Conference on System Sciences, Big Island, HI, USA, 6–9 June 2003; pp. 1–10. [Google Scholar]
- Coppola, P.; Mea1, V.D.; Gaspero, L.D.; Mizzaro1, S.; Scagnetto, I.; Selva1, A.; Vassena, L.; Rizio, P.Z. MoBe: A framework for context-aware mobile applications. In Proceedings of the Workshop on Context-Awareness for Proactive Systems (CAPS 2005), Helsinki, Finland, 16 June 2005; pp. 1–10. [Google Scholar]
- Schilit, B.; Adams, N.; Want, R. Context-aware computing applications. In Proceedings of the First Workshop on Mobile Computing Systems and Applications, Santa Cruz, CA, USA, 8–9 December 1994; pp. 85–90. [Google Scholar]
- Chen, G.; Kotz, D. A Survey of Context-Aware Mobile Computing Research; Technical Report TR2000-381; Department of Computer Science, Dartmouth College: Hanover, NH, USA, November 2000. [Google Scholar]
- Abowd, G.D.; Dey, A.K.; Brown, P.J.; Davies, N.; Smith, M.; Steggles, P. Towards a better understanding of context and context-awareness. Handheld Ubiquitous Comput. 2001, 1707, 304–307. [Google Scholar]
- Dey, A.K. Understanding and using context. Pers. Ubiquitous Comput. 2001, 5, 4–7. [Google Scholar] [CrossRef]
- Brown, P.J.; Bovey, J.D.; Chen, X. Context-aware applications: From the laboratory to the marketplace. IEEE Pers. Commun. 1997, 4, 58–64. [Google Scholar] [CrossRef]
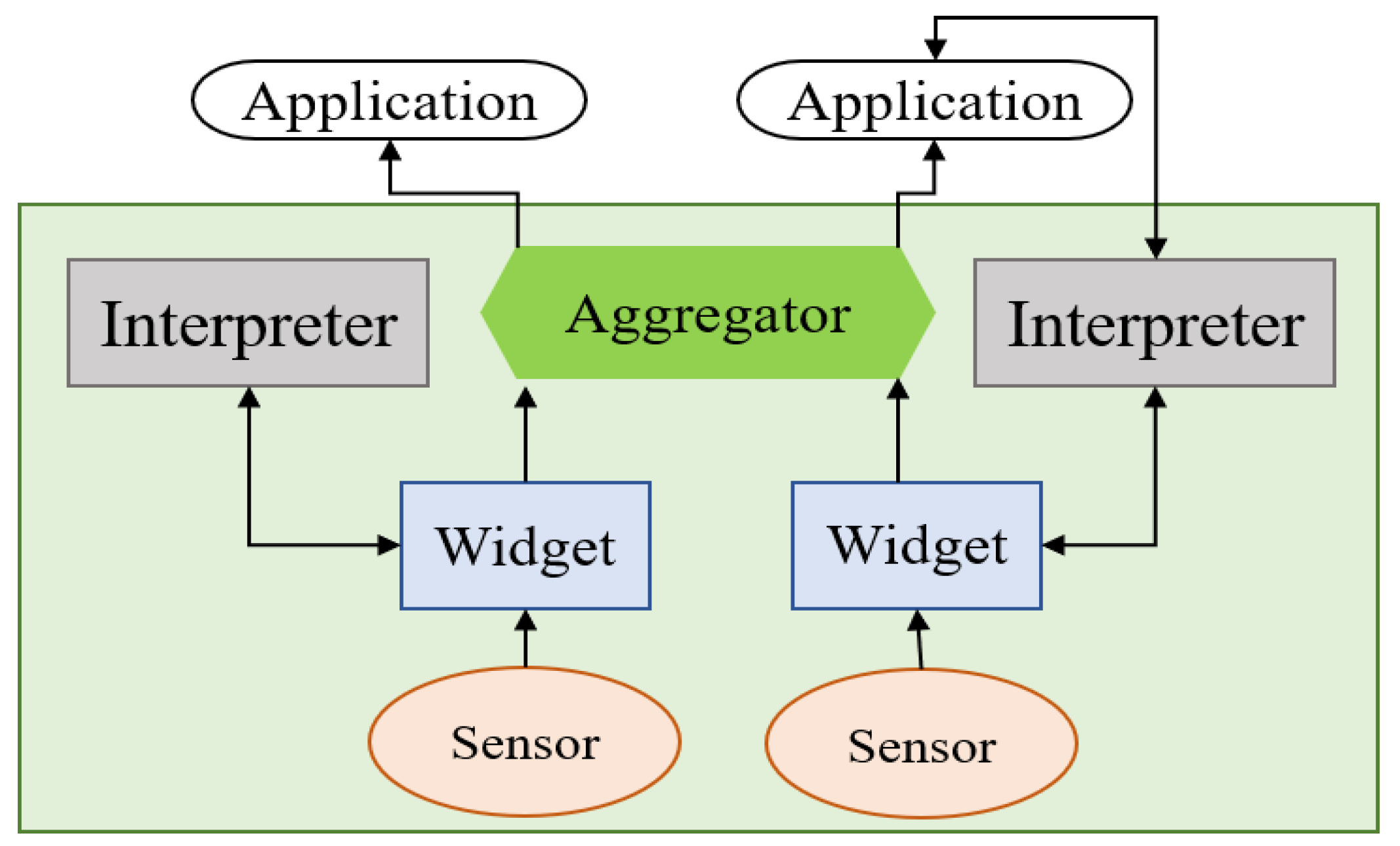
- Gellersen, H.W.; Schmidt, A.; Beigl, M. Multi-sensor context-awareness in mobile devices and smart artifacts. Mob. Netw. Appl. 2002, 7, 341–351. [Google Scholar] [CrossRef]
- Satyanarayanan, M. Pervasive computing: Vision and Challenges. IEEE Pers. Commun. 2001, 8, 10–17. [Google Scholar] [CrossRef]
- Schilit, B.N.; Hilbert, D.M.; Trevor, J. Context-aware communication. Wirel. Commun. 2002, 9, 46–54. [Google Scholar] [CrossRef]
- Haseloff, S. Context-Awareness in Information Logistics. Ph.D. Thesis, Technical University of Berlin, Berlin, Germany, 2005. [Google Scholar]
- Liu, W.; Li, X.; Huang, D. A survey on context awareness. In Proceedings of the 2011 International Conference on Computer Science and Service System (CSSS), Nanjing, China, 27–29 July 2011; pp. 144–147. [Google Scholar]
- Berry, J.K. Spatial Reasoning for Effective GIS; Wiley Books: Hoboken, NJ, USA, 1996. [Google Scholar]
- Cohn, A.G.; Hazarika, S.M. Qualitative spatial representation and reasoning: An overview. Fundam. Inf. Qual. Spat. Reason. 2001, 46, 1–29. [Google Scholar]
- Nakashima, H.; Aghajan, H.; Augusto, J.C. Handbook of Ambient Intelligence and Smart Environments; Springer Books: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
- Kortuem, G.; Kray, C.; Gellersen, H. Sensing and visualizing spatial relations of mobile devices. In Proceedings of the 18th Annual ACM Symposium on User Interface Software and Technology, Seattle, WA, USA, 23–26 October 2005; pp. 93–102. [Google Scholar]
- Bigley, G.A.; Roberts, K.H. The incident command system: High-reliability organizing for complex and volatile task environments. Acad. Manag. J. 2017, 44, 1281–1299. [Google Scholar]
- Huang, W.; Kong, W.; Tong, Z.; Zhu, X. Research on context-based knowledge representation in emergency domain. In Proceedings of the 3rd International Conference on Biomedical Engineering and Informatics, Yantai, China, 16–18 October 2010; pp. 2953–2957. [Google Scholar]
- Liu, L.; Sun, R.; Sun, Y.; Al-Sarawi, S. A smart bushfire monitoring and detection system using GSM technology. Int. J. Comput.-Aided Eng. Technol. 2010, 2, 218–233. [Google Scholar] [CrossRef]
- Sun, Y.; Yuan, Q.; Al-Sarawi, S. A bushfire monitoring and detection system for smart homes using ZigBee technology. Int. J. Comput.-Aided Eng. Technol. 2010, 2, 234–249. [Google Scholar] [CrossRef]
- Marmasse, N.; Schmandt, C. Location-aware information delivery with commotion. In Proceedings of the 2nd International Symposium on Handheld and Ubiquitous Computing; ACM Digital Library: New York, NY, USA, 2000; pp. 157–171. [Google Scholar]
- Dey, A.; Abowd, G. CybreMinder: A context-aware system for supporting reminders. In Handheld and Ubiquitous Computing; Springer: Berlin, Germany, 2000; pp. 201–207. [Google Scholar]
- Loke, S.W.; Zaslavsky, A. Communicative acts of Elvin-enhanced mobile agents. In Proceedings of the IEEE/WIC International Conference on Intelligent Agent Technology, Halifax, NS, Canada, 13–17 October 2003; pp. 1–4. [Google Scholar]
- Kuflik, T.; Sheidin, J.; Jbara, S.; Goren-Bar, D.; Soffer, P.; Stock, O.; Zancanaro, M. Supporting small groups in the museum by context-aware communication services. In Proceedings of the 12th International Conference on Intelligent User Interfaces, Honolulu, HI, USA, 28–31 January 2007; pp. 305–308. [Google Scholar]
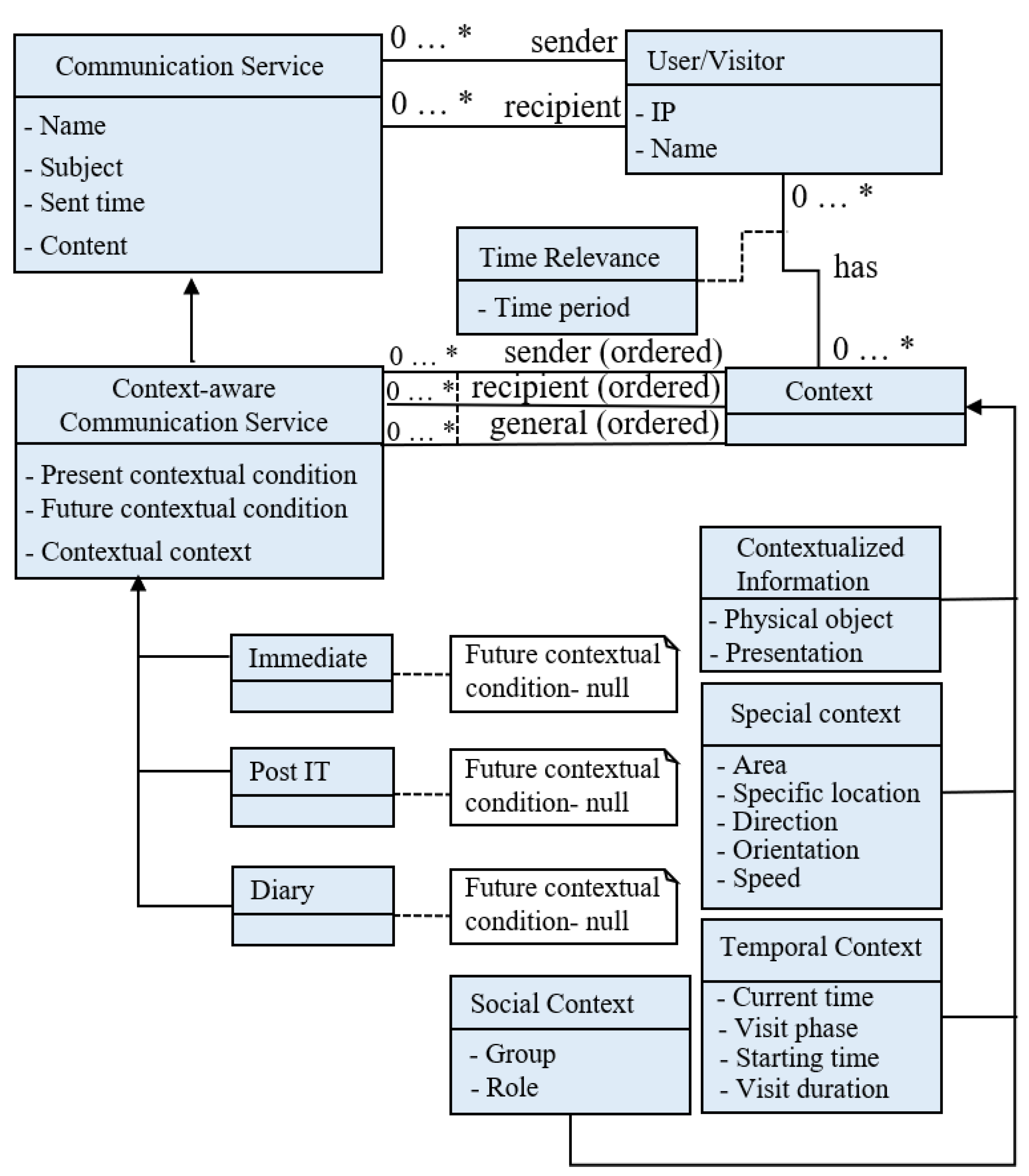
- Kuflik, T.; Soffer, P.; Reinhartz-Berger, I.; Jbara, S.; Stock, O. Generic Framework for Context-Aware Communication Services in Visitors Guides. J. Softw. Eng. Appl. 2011, 4, 268–281. [Google Scholar] [CrossRef] [Green Version]
- Bardram, J.E.; Hansen, T.R. The AWARE architecture: Supporting context-mediated social awareness in mobile cooperation. In Proceedings of the 2004 ACM Conference on Computer Supported Cooperative Work, Chicago, IL, USA, 6–10 November 2004; pp. 192–201. [Google Scholar]
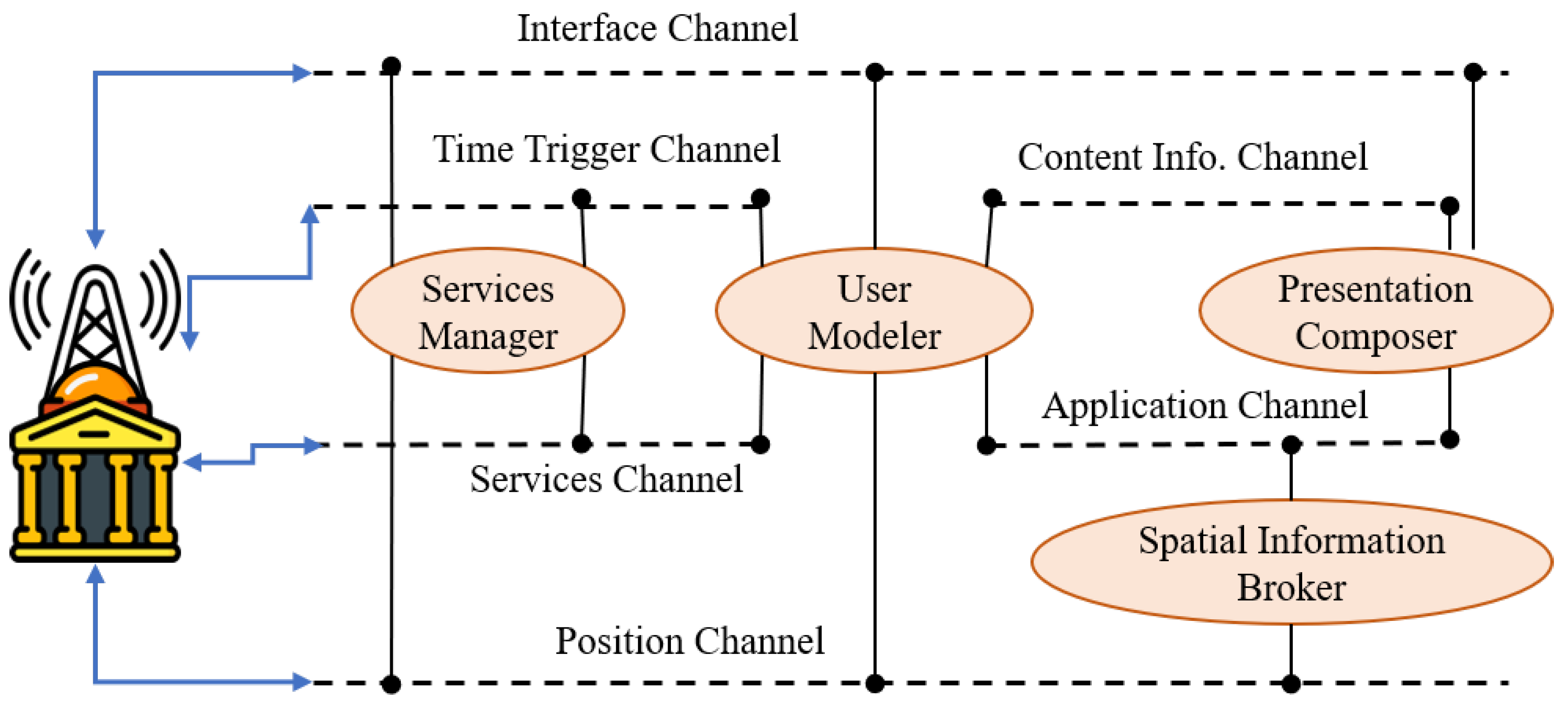
- Henri, G.; Otte, R.A.A.; Kruse, H.C.J.; Snijders, M. Context-aware communication with Live Contacts. In Proceedings of the Conference Supplement of CSCW, Chicago, IL, USA, 6–10 November 2004. [Google Scholar]
- Nummiaho, A.; Laakko, T. A framework for mobile context-based messaging applications. In Proceedings of the 4th International Conference on Mobile Technology, Applications, and Systems, Singapore, 10–12 September 2007; pp. 619–622. [Google Scholar]
- Stahl, C.; Heckmann, D. Using semantic web technology for ubiquitous hybrid location modeling. Geogr. Inf. Sci. 2009, 10, 157–165. [Google Scholar]
- Gaonkar, S.; Li, J.; Choudhury, R.R.; Cox, L.; Schmidt, A. Micro-Blog: Sharing and querying content through mobile phones and social participation. In Proceedings of the 6th International Conference on Mobile Systems, Applications, and Services, Breckenridge, CO, USA, 17–20 June 2008; pp. 174–186. [Google Scholar]
- Rantanen, M.; Oulasvirta, A.; Blom, J.; Tiitta, S.; Mantyla, M. InfoRadar: Group and public messaging in the mobile context. In Proceedings of the Third Nordic Conference on Human-Computer Interaction, Tampere, Finland, 23–27 October 2004; pp. 131–140. [Google Scholar]
- Melinger, D.; Bonna, K.; Sharon, M.; SantRam, M. Socialight: A mobile social networking system. In Proceedings of the Sixth International Conference on Ubiquitous Computing, Nottingham, UK, 7–10 September 2004; pp. 1–2. [Google Scholar]
- Jou, C.; Wang, W.J. The Design and Implementation of a Context-Aware Group Communication System. In Proceedings of the International Conference on Pervasive Systems & Computing (PSC 2006), Las Vegas, NV, USA, 26–29 June 2006; pp. 1–7. [Google Scholar]
- Shi, L.; Ma, X.; Xi, L.; Duan, Q.; Zhao, J. Rough set and ensemble learning-based semi-supervised algorithm for text classification. Expert Syst. Appl. 2011, 38, 6300–6306. [Google Scholar] [CrossRef]
- Joachims, T. A statistical learning model of text classification for support vector machines. In Proceedings of the ACM SIGIR, New Orleans, LA, USA, 9–12 September 2001; pp. 128–136. [Google Scholar]
- Peng, F.; Schuurmans, D. Combining naive Bayes and n-gram language models for text classification. In Proceedings of the ECIR, Pisa, Italy, 14–16 April 2003; pp. 335–350. [Google Scholar]
- Li, W.; Miao, D.; Wang, W. Two-level hierarchical combination method for text classification. Expert Syst. Appl. 2011, 38, 2030–2039. [Google Scholar] [CrossRef]
- Onan, A.; Korukoglu, S.; Bulut, H. Ensemble of keyword extraction methods and classifiers in text classification. Expert Syst. Appl. 2016, 57, 232–247. [Google Scholar] [CrossRef]
- Liu, C.; Hsaio, W.; Lee, C.; Chang, T.; Kuo, T. Semi-supervised text classification with universum learning. IEEE Trans. Cybern. 2016, 46, 462–473. [Google Scholar] [CrossRef]
- Joulin, A.; Grave, E.; Bojanowski, P.; Mikolov, T. Bag of tricks for efficient text classification. arXiv 2016, arXiv:1607.01759. [Google Scholar]
- Kim, Y. Convolutional neural networks for sentence classification. In Proceedings of the 2014 Conference on Empirical Methods in Natural Language Processing (EMNLP), Doha, Qatar, 25–29 October 2014; pp. 1746–1751. [Google Scholar]
- Rout, J.K.; Choo, K.R.; Dash, A.K.; Bakshi, S.; Jena, S.K.; Williams, K.L. A model for sentiment and emotion analysis of unstructured social media text. Electron. Commer. Res. 2018, 18, 181–199. [Google Scholar] [CrossRef]
- Song, Y.; Jeong, S.; Kim, H. Semi-automatic construction of a named entity dictionary for entity-based sentiment analysis in social media. Multimed. Tools Appl. 2017, 76, 11319–11329. [Google Scholar] [CrossRef]
- Uysal, E.; Yumusak, S.; Oztoprak, K.; Dogdu, E. Sentiment analysis for social media: A case study for Turkish general elections. In Proceedings of the ACM Southeast Regional Conference, Kennesaw, GA, USA, 13–15 April 2017; pp. 215–218. [Google Scholar]
- Suerdem, A.K.; Kaya, E. Using sentiment analysis to detect customer attitudes in social media comments. Res. Comput. Sci. 2015, 90, 207–215. [Google Scholar] [CrossRef]
- Esuli, A.; Sebastiani, F. SENTIWORDNET: A publicly available lexical resource for opinion mining. In Proceedings of the LREC, Genoa, Italy, 22–28 May 2006; pp. 417–422. [Google Scholar]
- Raez, A.M.; Camara, E.M.; Martın-Valdivia, M.T.; Lopez, L.A.U. Ranked wordnet graph for sentiment polarity classification in twitter. Comput. Speech Lang. 2014, 28, 93–107. [Google Scholar] [CrossRef]
- Cambria, E.; Poria, S.; Hazarika, D.; Kwok, K. Senticnet 5: Discovering conceptual primitives for sentiment analysis by means of context embeddings. In Proceedings of the Thirty-Second AAAI Conference on Artificial Intelligence, New Orleans, LA, USA, 2–7 February 2018; pp. 1795–1802. [Google Scholar]
- Molina-Gonzalez, M.D.; Martınez-Camara, E.; Martın-Valdivia, M.T.; Perea-Ortega, J.M. Semantic orientation for polarity classification in Spanish reviews. Expert Syst. Appl. 2013, 40, 7250–7257. [Google Scholar] [CrossRef]
- Cruz, F.L.; Troyano, J.A.; Pontes, B.; Ortega, F.J. Ml-senticon: Un lexicon multiling ue de polaridades semanticas a nivel delemas. Proces. Del Leng. Nat. 2014, 53, 113–120. [Google Scholar]
- Deng, S.; Sinha, A.P.; Zhao, H. Adapting sentiment lexicons to domain-specific social media texts. Decis. Support Syst. 2017, 94, 65–76. [Google Scholar] [CrossRef]
- Kouicem, D.E.; Abdelmadjid, B.; Hicham, L. Distributed Fine-Grained Secure Control of Smart Actuators in Internet of Things. In Proceedings of the 2017 IEEE International Symposium on Parallel and Distributed Processing with Applications and 2017 IEEE International Conference on Ubiquitous Computing and Communications (ISPA/IUCC), Guangzhou, China, 12–15 December 2017; pp. 653–660. [Google Scholar]
- Gusmeroli, S.; Piccione, S.; Rotondi, D. A capability-based security approach to manage access control in the internet of things. Math. Comput. Model. 2013, 58, 1189–1205. [Google Scholar] [CrossRef]
- Mahalle, P.N.; Anggorojati, B.; Prasad, N.R.; Prasad, R. Identity Establishment and Capability-based Access Control (iecac) scheme for Internet of Things. In Proceedings of the 15th International Symposium on Wireless Personal Multimedia Communications, Taipei, Taiwan, 24–27 September 2012; pp. 187–191. [Google Scholar]
- Hernandez-Ramos, J.L.; Pawlowski, M.P.; Jara, A.J.; Skarmeta, A.F.; Ladid, L. Towards a Lightweight Authentication and Authorization Framework for Smart Objects. IEEE J. Sel. Areas Commun. 2015, 33, 690–702. [Google Scholar] [CrossRef] [Green Version]
- Hussein, D.; Bertin, E.; Frey, V. A community-driven access control approach in distributed iot environments. IEEE Commun. Mag. 2017, 55, 146–153. [Google Scholar] [CrossRef]
- Hong, J.; Xue, K.; Li, W.; Xue, Y. LABAC: A Location-aware Attribute-based Access Control Scheme for Cloud Storage. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar]
- Hong, J.; Xue, K.; Li, W.; Xue, Y. TAFC: Time and attribute factors combined access control on time-sensitive data in public cloud. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–6. [Google Scholar]
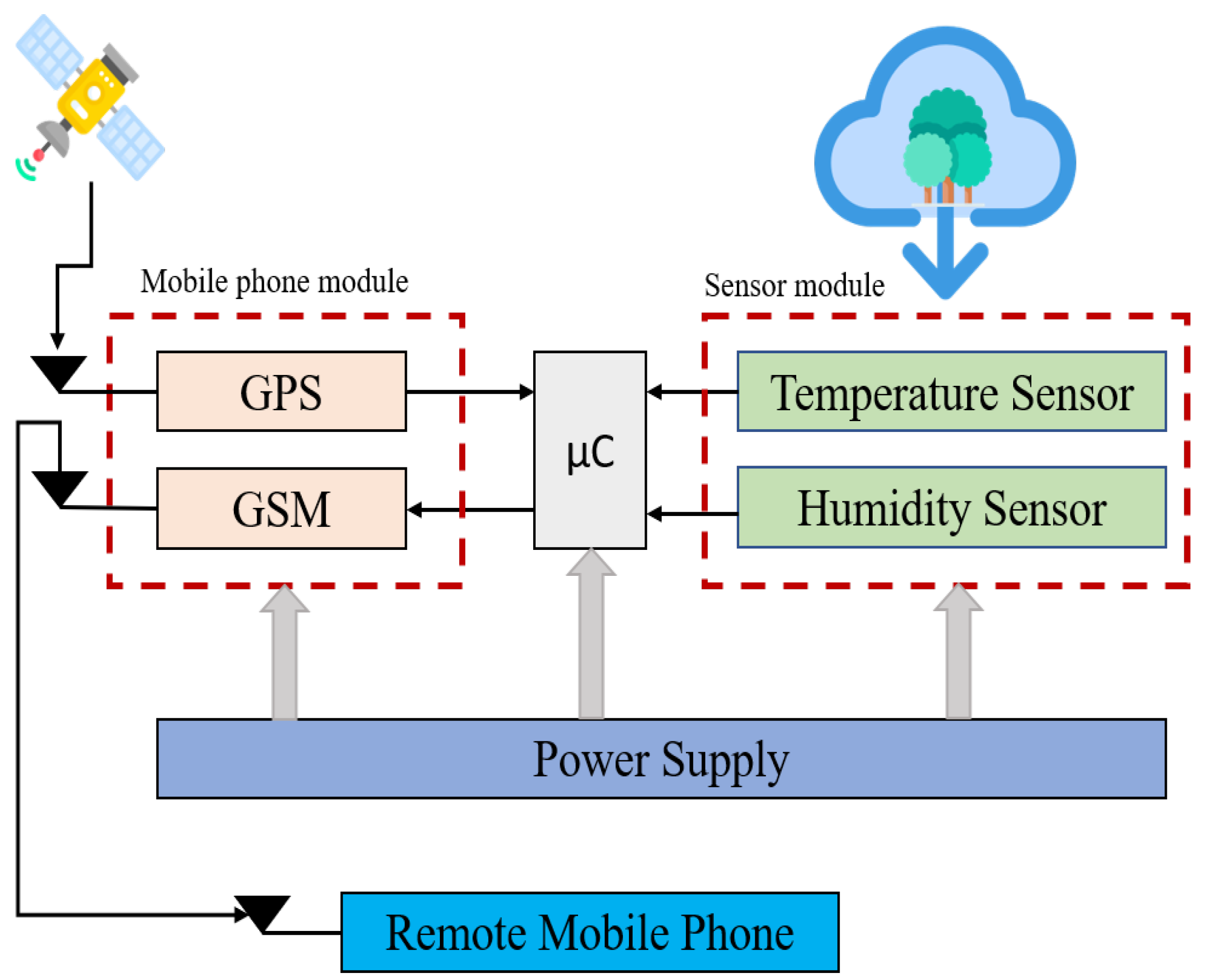
| Message | Definition |
|---|---|
| ID | Using an identification number (ID), this proposed system allows millions of devices to be identified. |
| TEM | It represents the temperature in centigrade. |
| HUM | It the environment’s humidity. |
| GPGLL | It includes latitude and longitude information in GPS Signal (compatible to NMEA-0183 GPS). |
| Application | Type | Technology | Architecture | Usage | Context |
|---|---|---|---|---|---|
| Smart bushfire Monitoring and detection system [31] | emergency application | GSM modem, GPS receiver, Sensors, microcontroller and power supply | hybrid | SMS format | Sensors for location, temperature and humidity |
| Bushfire monitoring and detection system for smart homes [32] | emergency application | ZigBee modules, GSM modem, GPS receiver, Sensors, microcontroller and power supply | hybrid | SMS format | Sensors for location, temperature, humidity, wind speed and direction. |
| ComMotion [33] | notification and guidance | GPS, Web-Server, Sensors, CDPD and Data Mapping | centralized | Graphical and textual interface for messaging | location, time and activity. |
| CybreMinder [34] | notification and guidance | Context-Toolkit, CRB, GPS, Sensors | centralized | text, audio, video and multimedia | contextual data, location, time and nearby people. |
| Elvin [35] | notification and guidance | Mobile agent, Server, ACL communicative | centralized | Integers, floating point and strings | location using GPS, time and event (message content) |
| The PIL museum Visitor’s Guide System [36] | notification and guidance | IR and Wi-Fi | centralized | messaging, guide book | location using IR and Wi-Fi, time and contextual states. |
| Generic Framework for Context-Aware Communication Services [37] | notification and guidance | IR and Wi-Fi | centralized (multi agents) | SMS-like and Post-It services, Memories and Visit Reminder | location, time and contextual information. |
| Context Mediated Social Awareness [38] | social network and collaboration | PDA for the client and GPRS to communicate with server | hybrid | messaging: Text, audio, video, multimedia | time, location, personal status, and activity. |
| Context Aware Communication with Live Contacts [39] | social network: Communication and collaboration | C# Clients, Microsoft.NET Servers and uses GPRS to connect with GSM | hybrid | messaging technique (text, voice, video, multimedia) | location, time, instant messaging, calendar, and color coded availability. |
| Framework for Mobile Context Messaging Applications [40] | social network: Communication and collaboration | J2ME, XML, JSR-179 Location API and GPS locator device. | centralized | text message: SMS format and Multimedia elements | location, time and application services. |
| Semantic Web Technology for Ubiquitous Location Modeling [41] | social network: Communication and collaboration | Mobile, IR- GPS, sensors, Semantic OWL, Yamamoto and URIs | hybrid | text information, presentation of audio and visual media | location, user characteristics, any situational context (event, objects) and map. |
| Micro-Blog [42] | social network: Communication and collaboration | J2ME and Nokia N95 for Client side and MySQL for Server is built using MySQL, wireless networking | hybrid | sharing, browsing, and querying; global information in SMS format and Photos | location and time of the device. |
| InfoRadar [43] | social network and communication | PDA, GPS and radar metaphor | centralized | SMS and multimedia elements | location and time. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almagrabi, A.O.; Al-Otaibi, Y.D. A Survey of Context-Aware Messaging-Addressing for Sustainable Internet of Things (IoT). Sustainability 2020, 12, 4105. https://doi.org/10.3390/su12104105
Almagrabi AO, Al-Otaibi YD. A Survey of Context-Aware Messaging-Addressing for Sustainable Internet of Things (IoT). Sustainability. 2020; 12(10):4105. https://doi.org/10.3390/su12104105
Chicago/Turabian StyleAlmagrabi, Alaa Omran, and Yasser D. Al-Otaibi. 2020. "A Survey of Context-Aware Messaging-Addressing for Sustainable Internet of Things (IoT)" Sustainability 12, no. 10: 4105. https://doi.org/10.3390/su12104105
APA StyleAlmagrabi, A. O., & Al-Otaibi, Y. D. (2020). A Survey of Context-Aware Messaging-Addressing for Sustainable Internet of Things (IoT). Sustainability, 12(10), 4105. https://doi.org/10.3390/su12104105




