Quantitative Research on Global Terrorist Attacks and Terrorist Attack Classification
Abstract
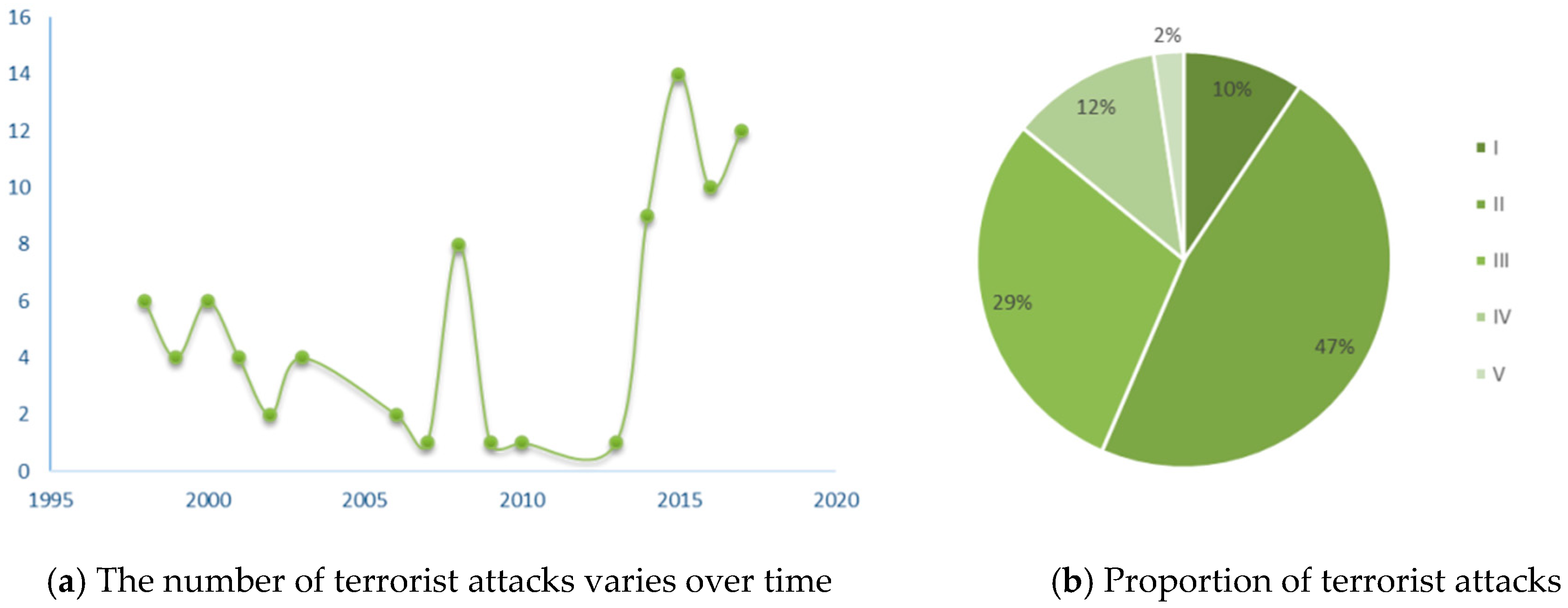
:1. Introduction
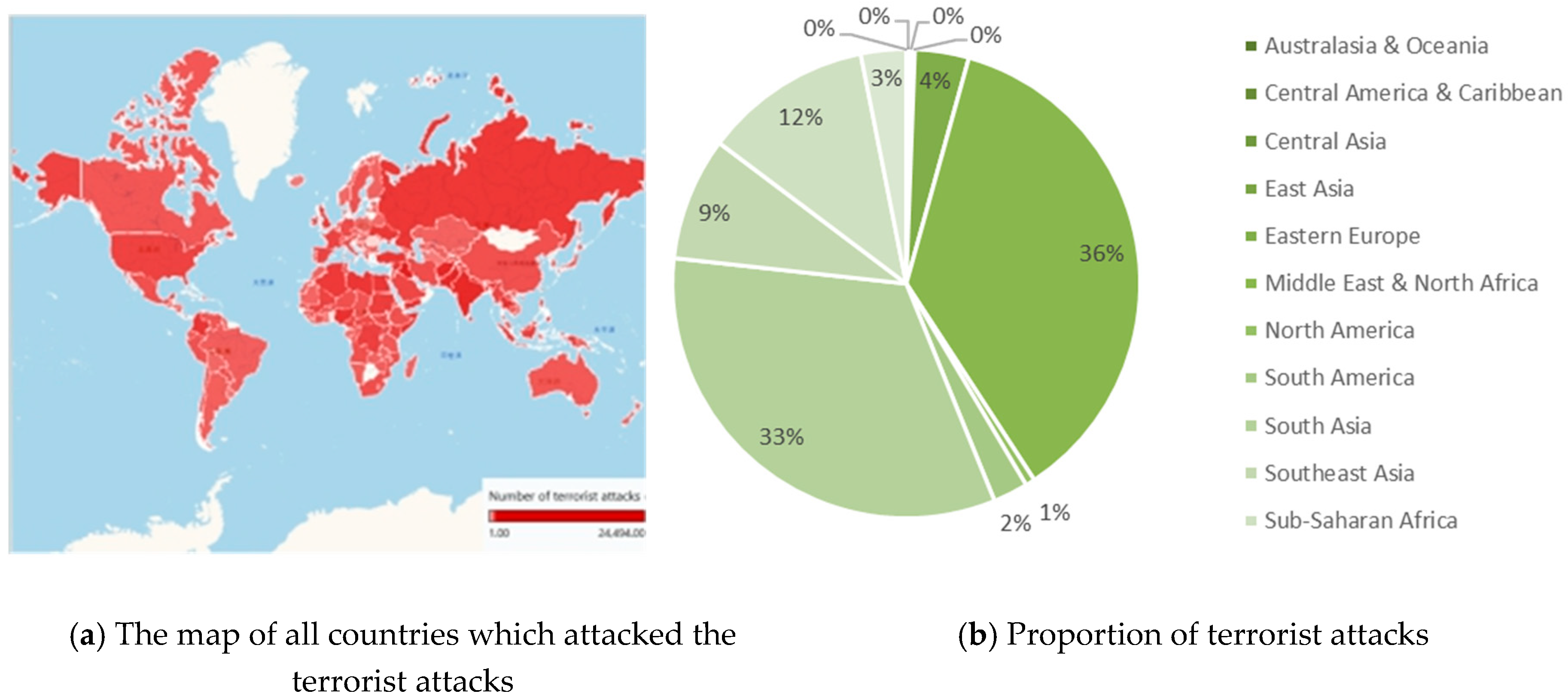
2. Terrorist Attack Analysis
3. Model Establishment
3.1. Factor Analysis Model
3.2. Mathematical Model
3.3. Factor Load
- (1)
- Data standardization;
- (2)
- Calculating the original sample covariance matrix;
- (3)
- Solving the non-zero eigenvalues of the covariance matrix, and sorting, the corresponding unit orthogonalization eigenvectors (i = 1, 2, …, p)
- (4)
- Calculate the factor load matrix, assuming k < p, then .
3.4. Factor Rotation
4. Model Solving
4.1. Establishment of Indicator System
4.2. KMO Inspection and Bartley Ball Test Results
4.3. Result Analysis
4.3.1. Comprehensive Factor Score
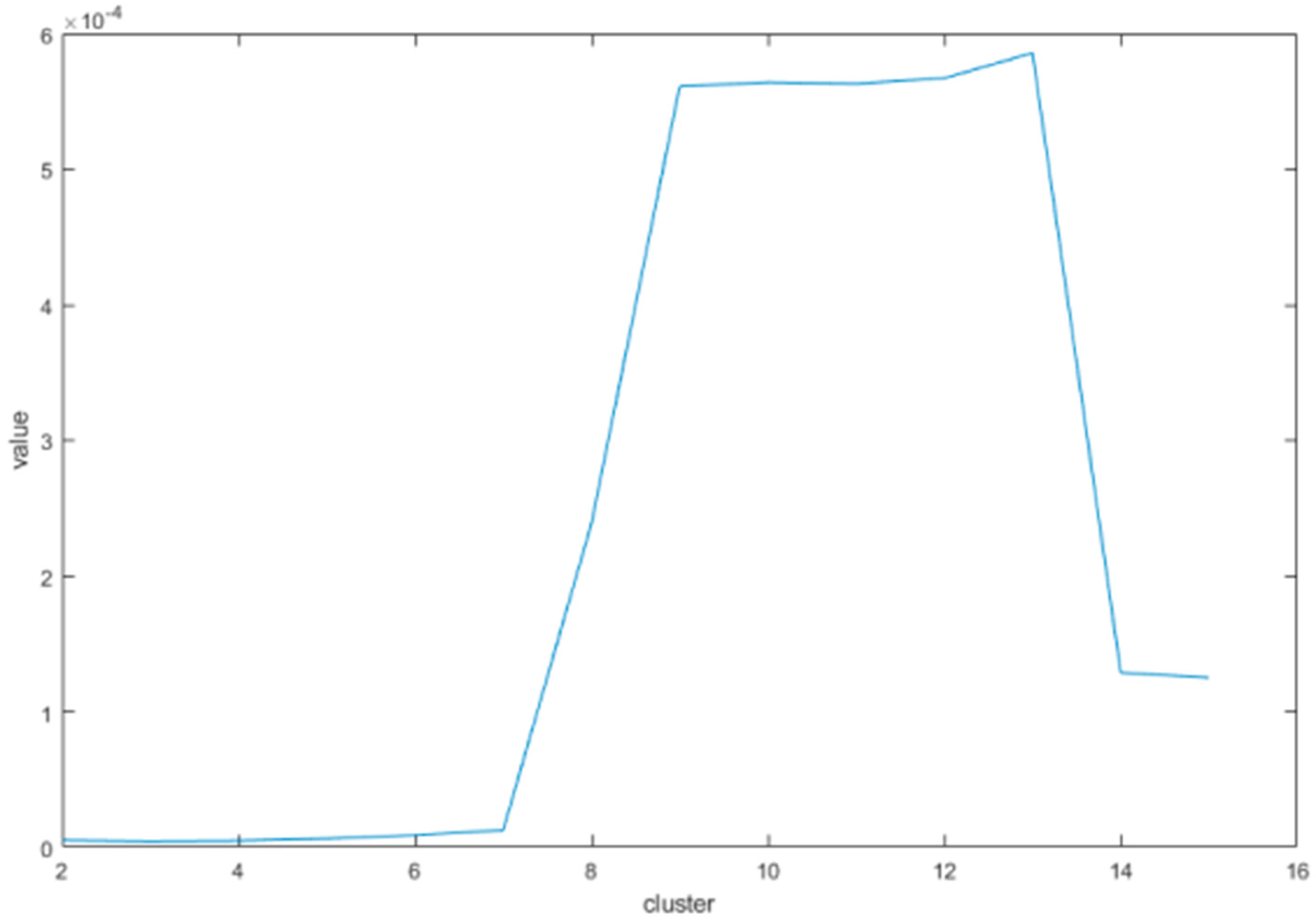
4.3.2. K-Means Clustering Method for Grading
- (1)
- Determine an initial cluster center for each cluster, so that there are K initial clustering centers.
- (2)
- The samples in the sample set are allocated to the nearest cluster according to the principle of minimum distance.
- (3)
- The sample mean of each cluster is used as the new cluster center.
- (4)
- Repeat steps (2) and (3) until the clustering center no longer changes.
- (5)
- End, and get K clusters.
- Improve the fairness of income distribution and enable the masses to share more development results.
- Respond to demographic changes and employment pressures, and build an economic development safety net.
- Promote reforms in various fields and provide strong institutional support for economic development.
5. Conclusions
Supplementary Materials
Author Contributions
Funding
Conflicts of Interest
Appendix A
Appendix A.1. Initial Common Factor and Factor Loading Matrix
| Factor | Eigenvalue | Difference | Proportion | Cumulative |
|---|---|---|---|---|
| 1 | 3.268 | 1.286 | 0.131 | 0.131 |
| 2 | 1.982 | 0.271 | 0.0793 | 0.210 |
| 3 | 1.710 | 0.170 | 0.0684 | 0.278 |
| 4 | 1.540 | 0.152 | 0.0616 | 0.340 |
| 5 | 1.388 | 0.0870 | 0.0555 | 0.396 |
| 6 | 1.301 | 0.0951 | 0.0520 | 0.448 |
| 7 | 1.206 | 0.131 | 0.0482 | 0.496 |
| 8 | 1.075 | 0.0315 | 0.0430 | 0.539 |
| 9 | 1.044 | 0.00736 | 0.0417 | 0.581 |
| 10 | 1.036 | 0.0333 | 0.0415 | 0.622 |
| 11 | 1.003 | 0.0368 | 0.0401 | 0.662 |
| 12 | 0.966 | 0.0196 | 0.0386 | 0.701 |
| 13 | 0.947 | 0.0334 | 0.0379 | 0.739 |
| 14 | 0.913 | 0.0123 | 0.0365 | 0.775 |
| 15 | 0.901 | 0.0564 | 0.0360 | 0.811 |
| 16 | 0.845 | 0.0551 | 0.0338 | 0.845 |
| 17 | 0.789 | 0.0659 | 0.0316 | 0.877 |
| 18 | 0.724 | 0.0588 | 0.0289 | 0.905 |
| 19 | 0.665 | 0.156 | 0.0266 | 0.932 |
| 20 | 0.509 | 0.0584 | 0.0203 | 0.952 |
| 21 | 0.450 | 0.0684 | 0.0180 | 0.970 |
| 22 | 0.382 | 0.100 | 0.0153 | 0.986 |
| 23 | 0.281 | 0.208 | 0.0113 | 0.997 |
| 24 | 0.0735 | 0.0713 | 0.00290 | 1.000 |
| 25 | 0.00219 | . | 0.000100 | 1 |
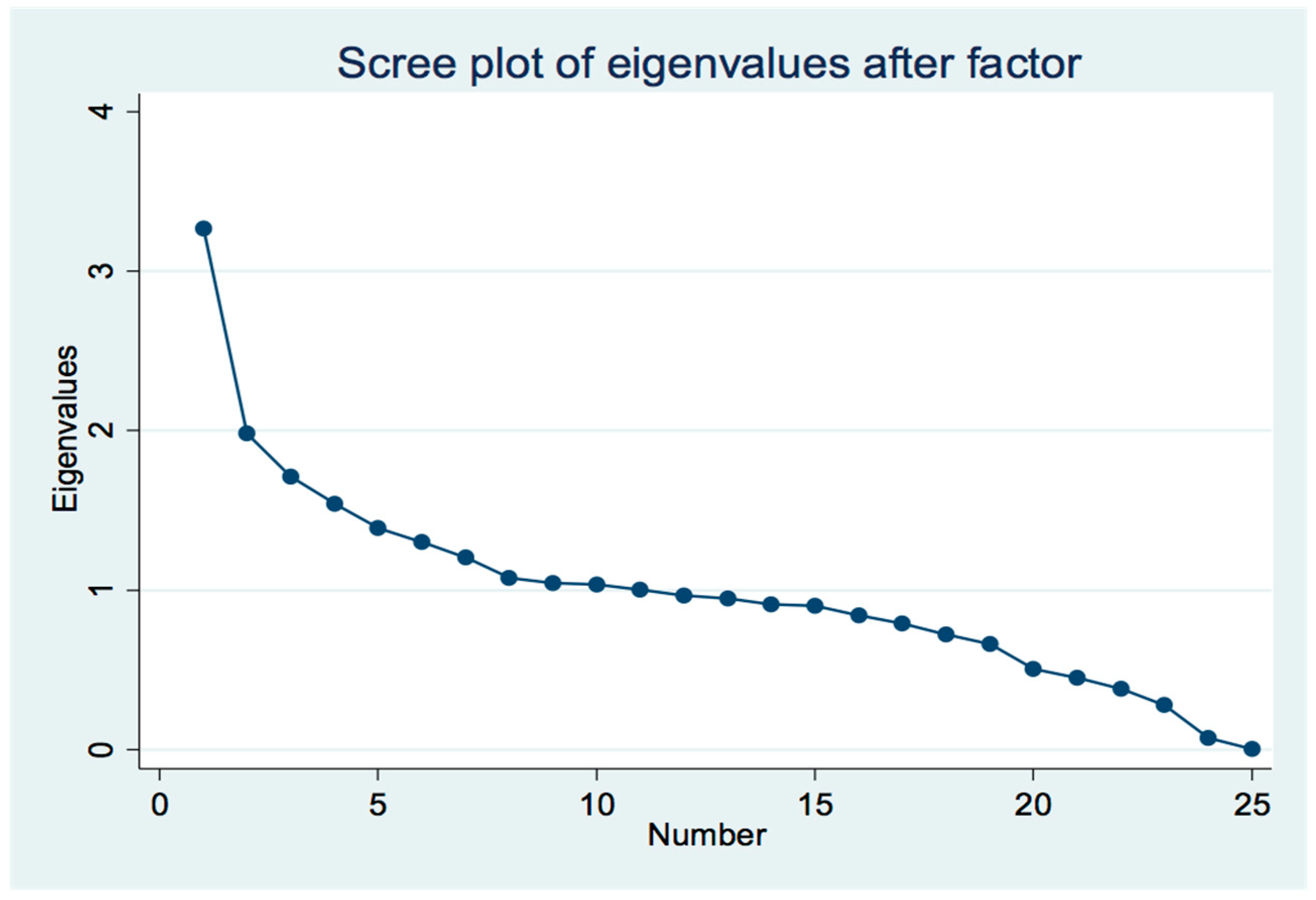
Appendix A.2. Factor Rotation and Factor Score Matrix
| Variable | Factor1 | Factor2 | Factor3 | Factor4 | Factor5 | Factor6 |
| c Workday | −0.0156 | 0.0151 | 0.0113 | −0.000220 | −0.00656 | −0.0323 |
| c extended | 0.285 | −0.412 | 0.378 | 0.301 | −0.00281 | 0.0377 |
| c crtnum | −0.0175 | −0.00347 | 0.0500 | 0.0498 | 0.00815 | −0.0268 |
| c multiple | 0.188 | 0.157 | −0.0783 | 0.0466 | 0.0858 | 0.193 |
| c region w~h | −0.0246 | 0.106 | −0.138 | 0.0969 | 0.360 | −0.201 |
| c city ornot | −0.0415 | 0.0239 | −0.0163 | −0.00858 | 0.137 | 0.0525 |
| c attackty~l | −0.342 | 0.699 | −0.202 | 0.0484 | −0.139 | 0.169 |
| c attackty~m | 0.245 | 0.194 | 0.450 | 0.496 | −0.365 | −0.140 |
| c success | 0.0741 | 0.157 | 0.194 | 0.255 | 0.0819 | 0.583 |
| c suicide | 0.144 | 0.308 | 0.105 | −0.237 | −0.203 | −0.189 |
| c weaptype~l | −0.358 | 0.708 | −0.194 | 0.0309 | −0.182 | 0.0665 |
| c weaptype~m | 0.233 | 0.356 | 0.335 | 0.362 | −0.401 | −0.179 |
| c targtype~l | −0.0176 | 0.0500 | 0.145 | 0.240 | 0.255 | 0.611 |
| c targtype~m | 0.168 | 0.153 | 0.163 | −0.0286 | −0.184 | −0.224 |
| c claimed | 0.226 | 0.0936 | −0.141 | −0.0151 | 0.103 | −0.0818 |
| c nkill | 0.195 | 0.294 | 0.626 | −0.468 | 0.216 | −0.00829 |
| c nwound | 0.0825 | 0.283 | 0.519 | −0.446 | 0.265 | −0.0108 |
| c property | 0.00723 | 0.136 | −0.0176 | 0.380 | 0.533 | −0.446 |
| c propexte~l | −0.0602 | 0.389 | 0.0289 | 0.424 | 0.539 | −0.0963 |
| c ishostkid | 0.144 | −0.293 | 0.299 | 0.270 | −0.0193 | 0.0185 |
| c nhostkid | 0.0647 | 0.0245 | 0.321 | −0.231 | 0.171 | 0.0354 |
| c INT LOG | 0.932 | 0.120 | −0.232 | −0.0439 | 0.00739 | 0.110 |
| c INT IDEO | 0.936 | 0.120 | −0.231 | −0.0482 | 0.00742 | 0.102 |
| c INT MISC | 0.161 | 0.0281 | −0.0904 | 0.0264 | 0.0880 | −0.307 |
| c INT ANY | 0.915 | 0.117 | −0.246 | −0.0372 | 0.0366 | 0.00508 |
| Variable | Factor8 | Factor9 | Factor10 | Factor11 | Uniqueness | Variable |
| c Workday | 0.0227 | −0.109 | 0.0430 | −0.0441 | 0.954 | 0.0713 |
| c extended | 0.139 | −0.114 | −0.0196 | 0.218 | −0.0247 | 0.433 |
| c crtnum | 0.390 | −0.0305 | −0.0868 | −0.590 | −0.193 | 0.448 |
| c multiple | −0.201 | 0.415 | 0.226 | −0.0842 | −0.0397 | 0.615 |
| c region w~h | 0.450 | 0.429 | −0.0130 | 0.0478 | 0.0918 | 0.392 |
| c city ornot | 0.00671 | 0.416 | 0.407 | 0.306 | −0.0622 | 0.540 |
| c attackty~l | 0.173 | −0.139 | −0.149 | 0.195 | −0.0277 | 0.193 |
| c attackty~m | −0.0548 | 0.224 | −0.0842 | −0.0316 | 0.0322 | 0.239 |
| c success | 0.145 | −0.288 | 0.242 | −0.0319 | −0.0342 | 0.355 |
| c suicide | −0.0589 | −0.157 | 0.313 | 0.0619 | −0.0318 | 0.610 |
| c weaptype~l | 0.148 | −0.0849 | −0.186 | 0.178 | −0.00984 | 0.198 |
| c weaptype~m | −0.121 | 0.298 | −0.0945 | −0.0967 | 0.0397 | 0.259 |
| c targtype~l | 0.126 | 0.156 | 0.0242 | −0.0278 | 0.0851 | 0.431 |
| c targtype~m | 0.186 | −0.288 | 0.534 | −0.000300 | −0.104 | 0.424 |
| c claimed | −0.198 | 0.0382 | 0.0478 | 0.471 | −0.0319 | 0.638 |
| c nkill | −0.0127 | 0.0375 | −0.0940 | −0.0183 | 0.00807 | 0.207 |
| c nwound | −0.00278 | 0.0210 | 0.101 | −0.0778 | 0.0578 | 0.355 |
| c property | −0.236 | −0.210 | −0.0993 | −0.0290 | −0.0413 | 0.242 |
| c propexte~l | −0.205 | −0.181 | 0.112 | −0.116 | −0.0294 | 0.263 |
| c ishostkid | 0.205 | −0.221 | −0.0587 | 0.378 | −0.0170 | 0.493 |
| c nhostkid | 0.0813 | 0.0181 | −0.477 | 0.230 | −0.0905 | 0.512 |
| c INT LOG | −0.0541 | −0.0574 | −0.0877 | −0.0352 | 0.00689 | 0.0333 |
| c INT IDEO | −0.0420 | −0.0562 | −0.0814 | −0.0314 | 0.00676 | 0.0316 |
| c INT MISC | 0.662 | 0.0492 | 0.0940 | 0.0960 | 0.0315 | 0.403 |
| c INT ANY | 0.136 | −0.0275 | −0.0652 | −0.0169 | 0.0127 | 0.0609 |
| Factor | Eigenvalue | Difference | Proportion | Cumulative |
|---|---|---|---|---|
| Factor1 | 3.02524 | 1.18055 | 0.121 | 0.121 |
| Factor2 | 1.84469 | 0.17846 | 0.0738 | 0.1948 |
| Factor3 | 1.66624 | 0.12263 | 0.0666 | 0.2614 |
| Factor4 | 1.54361 | 0.13754 | 0.0617 | 0.3232 |
| Factor5 | 1.40607 | 0.07832 | 0.0562 | 0.3794 |
| Factor6 | 1.32775 | 0.03406 | 0.0531 | 0.4325 |
| Factor7 | 1.29368 | 0.08486 | 0.0517 | 0.4843 |
| Factor8 | 1.20882 | 0.05961 | 0.0484 | 0.5326 |
| Factor9 | 1.14922 | 0.06732 | 0.046 | 0.5786 |
| Factor10 | 1.08189 | 0.07579 | 0.0433 | 0.6219 |
| Factor11 | 1.0061 | 0.0402 | 0.6621 |
| Variable | Factor1 | Factor2 | Factor3 | Factor4 | Factor5 | Factor6 | Factor7 |
| c_Workday | −0.0058 | −0.0054 | 0.0144 | 0.0104 | −0.0042 | 0.0121 | −0.0059 |
| c_extended | 0.0804 | −0.3864 | −0.0235 | 0.1875 | −0.0189 | 0.1827 | 0.5814 |
| c_crtnum | −0.009 | −0.0501 | 0.0135 | 0.0384 | −0.0053 | 0.0846 | −0.0979 |
| c_multiple | 0.1764 | −0.0973 | 0.0114 | 0.159 | 0.0023 | 0.2323 | −0.438 |
| c_region_w~h | −0.0101 | 0.0449 | 0.0098 | −0.0073 | 0.1191 | −0.0009 | −0.0943 |
| c_city_ornot | −0.1094 | −0.0941 | 0.0123 | 0.0074 | −0.0708 | 0.1695 | −0.1911 |
| c_attackty~l | −0.1088 | 0.8839 | −0.0192 | 0.0061 | 0.0294 | 0.1001 | −0.0434 |
| c_attackty~m | 0.0632 | −0.0248 | 0.0164 | 0.8541 | 0.04 | 0.0527 | 0.1426 |
| c_success | 0.0744 | 0.1243 | 0.026 | −0.0177 | 0.0431 | 0.7338 | 0.1496 |
| c_suicide | 0.1161 | 0.1453 | 0.2272 | 0.0734 | −0.0449 | −0.1478 | −0.0889 |
| c_weaptype~l | −0.1339 | 0.8784 | −0.0091 | 0.0677 | 0.0248 | −0.0106 | −0.0749 |
| c_weaptype~m | 0.1106 | 0.0973 | 0.0606 | 0.8406 | 0.0165 | −0.0522 | −0.0655 |
| c_targtype~l | −0.0164 | 0.0131 | 0.0477 | 0.0187 | −0.0068 | 0.6986 | −0.0117 |
| c_targtype~m | 0.071 | −0.0045 | 0.0798 | 0.0716 | 0.0067 | 0.0119 | 0.0799 |
| c_claimed | 0.2396 | 0.0725 | −0.0061 | −0.0461 | 0.1145 | −0.1171 | 0.0891 |
| c_nkill | 0.076 | −0.0148 | 0.8826 | 0.0829 | −0.0085 | 0.0085 | 0.0217 |
| c_nwound | −0.017 | −0.0351 | 0.7785 | −0.0177 | 0.0381 | 0.0671 | −0.1018 |
| c_property | 0.0043 | −0.0462 | −0.021 | 0.0177 | 0.8461 | −0.1674 | 0.081 |
| c_propexte~l | −0.0267 | 0.1261 | 0.0381 | 0.0454 | 0.8029 | 0.2374 | −0.1125 |
| c_ishostkid | 0.0035 | −0.1527 | −0.0438 | 0.0923 | −0.0098 | 0.1315 | 0.6646 |
| c_nhostkid | 0.0367 | 0.0836 | 0.4566 | −0.0252 | −0.0486 | −0.0948 | 0.3338 |
| c_INT_LOG | 0.9768 | −0.0733 | 0.0225 | 0.0508 | −0.0009 | 0.0245 | −0.0128 |
| c_INT_IDEO | 0.9783 | −0.0742 | 0.0255 | 0.0491 | −0.0046 | 0.0209 | −0.0092 |
| c_INT_MISC | 0.1444 | 0.0615 | −0.027 | −0.0503 | −0.038 | −0.1001 | 0.2166 |
| c_INT_ANY | 0.9527 | −0.057 | 0.0147 | 0.0347 | −0.009 | −0.0176 | 0.0393 |
| Variable | Factor8 | Factor9 | Factor10 | Factor11 | Uniqueness | ||
| c_Workday | 0.0247 | −0.0061 | 0.0232 | 0.9628 | 0.0713 | ||
| c_extended | 0.0258 | 0.0166 | 0.0429 | −0.0309 | 0.433 | ||
| c_crtnum | 0.1873 | 0.0449 | −0.688 | −0.1446 | 0.4477 | ||
| c_multiple | 0.0721 | −0.055 | 0.2338 | −0.1006 | 0.6152 | ||
| c_region_w~h | 0.747 | −0.1513 | 0.015 | 0.0343 | 0.3924 | ||
| c_city_ornot | 0.316 | 0.1086 | 0.49 | −0.1308 | 0.5399 | ||
| c_attackty~l | 0.0175 | 0.0169 | 0.0142 | −0.0113 | 0.1929 | ||
| c_attackty~m | −0.0089 | 0.0348 | −0.0169 | 0.0062 | 0.2393 | ||
| c_success | −0.145 | 0.1813 | −0.0787 | −0.0025 | 0.3553 | ||
| c_suicide | −0.1051 | 0.493 | 0.1128 | 0.0091 | 0.6097 | ||
| c_weaptype~l | 0.0341 | 0.0031 | 0.0091 | 0.0028 | 0.1983 | ||
| c_weaptype~m | −0.0203 | 0.0307 | −0.0101 | 0.0097 | 0.2592 | ||
| c_targtype~l | 0.0885 | −0.2604 | 0.019 | 0.0382 | 0.4313 | ||
| c_targtype~m | 0.0407 | 0.7415 | −0.031 | −0.0288 | 0.4236 | ||
| c_claimed | 0.0152 | 0.0055 | 0.5078 | −0.0694 | 0.6375 | ||
| c_nkill | −0.0221 | 0.0107 | −0.0086 | −0.0051 | 0.2067 | ||
| c_nwound | 0.0213 | 0.1314 | 0.001 | 0.058 | 0.3546 | ||
| c_property | 0.0489 | −0.0456 | 0.004 | −0.0081 | 0.242 | ||
| c_propexte~l | 0.0124 | 0.052 | 0.0114 | 0.0029 | 0.2633 | ||
| c_ishostkid | 0.0424 | 0.0459 | 0.1022 | −0.0129 | 0.4926 | ||
| c_nhostkid | 0.0271 | −0.3614 | 0.0135 | −0.1271 | 0.5121 | ||
| c_INT_LOG | −0.0518 | 0.0001 | 0.025 | −0.005 | 0.0334 | ||
| c_INT_IDEO | −0.0395 | 0.0094 | 0.0252 | −0.0049 | 0.0316 | ||
| c_INT_MISC | 0.659 | 0.2348 | −0.1407 | 0.04 | 0.403 | ||
| c_INT_ANY | 0.1455 | 0.0554 | −0.0245 | 0.0029 | 0.0609 |
| Variable | Factor1 | Factor2 | Factor3 | Factor4 | Factor5 | Factor6 | Factor7 |
| c Workday | 0.00467 | −0.0137 | 0.0110 | 0.00952 | −0.00858 | 0.0158 | −0.00795 |
| c extended | −0.0188 | −0.142 | −0.0257 | 0.0859 | −0.00172 | 0.117 | 0.401 |
| c crtnum | 0.00835 | −0.0546 | 0.0104 | 0.0293 | 0.000540 | 0.0678 | −0.123 |
| c multiple | 0.0345 | −0.116 | −0.00407 | 0.125 | −0.0258 | 0.185 | −0.387 |
| c region w~h | −0.0139 | 0.00102 | 0.0216 | 0.0263 | 0.0386 | −0.00254 | −0.0749 |
| c city ornot | −0.0842 | −0.0998 | 0.00387 | 0.0256 | −0.0842 | 0.148 | −0.166 |
| c attackty~l | 0.0276 | 0.505 | −0.0234 | −0.0141 | −0.0261 | 0.0622 | 0.0961 |
| c attackty~m | −0.0365 | −0.0145 | −0.0301 | 0.562 | −0.00440 | −0.00430 | 0.0528 |
| c success | 0.0302 | 0.0805 | −0.0109 | −0.0836 | 0.0174 | 0.557 | 0.113 |
| c suicide | 0.0143 | 0.0614 | 0.108 | 0.00809 | −0.0281 | −0.0970 | −0.0513 |
| c weaptype~l | 0.0152 | 0.496 | −0.0160 | 0.0382 | −0.0297 | −0.0242 | 0.0689 |
| c weaptype~m | −0.00928 | 0.0329 | −0.00273 | 0.565 | −0.0261 | −0.0787 | −0.0954 |
| c targtype~l | 8.00 × 10−5 | 0.00101 | 0.0291 | 0.000980 | −0.0392 | 0.521 | −0.0337 |
| c targtype~m | −0.0225 | −0.0221 | 0.00860 | −0.0151 | 0.0133 | 0.0342 | 0.0515 |
| c claimed | 0.0724 | 0.0757 | −0.0112 | −0.0520 | 0.0740 | −0.0955 | 0.113 |
| c nkill | −0.00400 | −0.0137 | 0.532 | 0.0125 | −0.00642 | −0.0139 | 0.00553 |
| c nwound | −0.0367 | −0.0576 | 0.470 | −0.0486 | 0.0273 | 0.0475 | −0.0946 |
| c property | 0.000700 | −0.0503 | −0.00698 | −0.0160 | 0.618 | −0.160 | 0.0793 |
| c propexte~l | −0.00652 | 0.00900 | 0.0148 | −0.0131 | 0.564 | 0.156 | −0.0722 |
| c ishostkid | −0.0254 | 0.00548 | −0.0362 | 0.0158 | −0.00114 | 0.0775 | 0.516 |
| c nhostkid | 0.0249 | 0.119 | 0.295 | −0.0317 | −0.0360 | −0.109 | 0.294 |
| c INT LOG | 0.337 | 0.0293 | −0.0159 | −0.0290 | 0.00402 | 0.0125 | −0.0268 |
| c INT IDEO | 0.337 | 0.0291 | −0.0143 | −0.0306 | 0.00109 | 0.0102 | −0.0239 |
| c INT MISC | 0.0337 | 0.0645 | −0.0215 | −0.0514 | −0.0506 | −0.0669 | 0.180 |
| c INT ANY | 0.325 | 0.0410 | −0.0192 | −0.0384 | −0.00862 | −0.0168 | 0.0168 |
| Variable | Factor8 | Factor9 | Factor10 | Factor11 | |||
| c Workday | 0.0245 | −0.0141 | 0.0284 | 0.958 | |||
| c extended | 0.0267 | 0.0198 | 0.0596 | −0.0257 | |||
| c crtnum | 0.142 | 0.0346 | −0.640 | −0.147 | |||
| c multiple | 0.0738 | −0.0478 | 0.196 | −0.0927 | |||
| c region w~h | 0.619 | −0.139 | 0.0260 | 0.0365 | |||
| c city ornot | 0.289 | 0.121 | 0.465 | −0.126 | |||
| c attackty~l | 0.00430 | −0.0124 | 0.0205 | −0.0196 | |||
| c attackty~m | 0.0104 | −0.0289 | −0.00984 | 0.00776 | |||
| c success | −0.127 | 0.185 | −0.0707 | −0.000380 | |||
| c suicide | −0.0866 | 0.409 | 0.102 | 0.00488 | |||
| c weaptype~l | 0.0205 | −0.0331 | 0.0159 | −0.00626 | |||
| c weaptype~m | 0.000780 | −0.0449 | −0.0131 | 0.0104 | |||
| c targtype~l | 0.0832 | −0.206 | 0.0188 | 0.0455 | |||
| c targtype~m | 0.0284 | 0.652 | −0.0176 | −0.0344 | |||
| c claimed | 0.00820 | −0.00425 | 0.464 | −0.0655 | |||
| c nkill | −0.00881 | −0.0413 | −0.0160 | −0.00225 | |||
| c nwound | 0.0256 | 0.0885 | −0.00550 | 0.0590 | |||
| c property | −0.00718 | −0.0345 | −0.0148 | −0.0109 | |||
| c propexte~l | −0.0307 | 0.0617 | −0.0106 | 0.000780 | |||
| c ishostkid | 0.0362 | 0.0449 | 0.123 | −0.0113 | |||
| c nhostkid | 0.0249 | −0.357 | 0.0167 | −0.124 | |||
| c INT LOG | −0.0688 | −0.0520 | −0.0185 | 0.00582 | |||
| c INT IDEO | −0.0585 | −0.0441 | −0.0178 | 0.00588 | |||
| c INT MISC | 0.538 | 0.192 | −0.107 | 0.0381 | |||
| c INT ANY | 0.0939 | −0.00474 | −0.0554 | 0.0125 |
Appendix A.3. Factor Score
References
- Freilich, J.D.; LaFree, G. Criminology theory and terrorism: Introduction to the special issue. Terror. Political Violence 2015, 27, 1–18. [Google Scholar] [CrossRef]
- Freilich, J.D.; Newman, G. (Eds.) Reducing Terrorism through Situational Crime Prevention; Criminal Justice Press: Monsey, NY, USA, 2009. [Google Scholar]
- LaFree, G.; Dugan, L.; Miller, E. Putting Terrorism in Context: Lessons from the Global Terrorism Database; Routledge: London, UK, 2015. [Google Scholar]
- Hirschfield, A. Surveillance and Situational Crime Prevention: Lessons for Counter-Terrorism. 2005. Available online: http://eprints.hud.ac.uk/id/eprint/7392/ (accessed on 3 March 2019).
- Taamneh, M.; Taamneh, S.; Alkheder, S. Clustering-based classification of road traffic accidents using hierarchical clustering and artificial neural networks. Int. J. Inj. Control Saf. Promot. 2016, 24, 1. [Google Scholar] [CrossRef] [PubMed]
- Clarke, R.V.; Newman, G.R. Outsmarting the Terrorists; Praeger: New York, NY, USA, 2006. [Google Scholar]
- Clarke, R.V.; Newman, G.R. Situational crime prevention and the control of terrorism. In Understanding and Responding to the Terrorism Phenomenon: A Multidimensional Perspective; Nikbay, O., Hancerli, S., Eds.; IOS Press: Amsterdam, The Netherlands, 2007; pp. 285–297. [Google Scholar]
- Cohen, L.E.; Felson, M. Social change and crime rate trends: A routine activities approach. Am. Sociol. Rev. 1979, 44, 588–608. [Google Scholar] [CrossRef]
- Dahl, E.J. The plots that failed: Intelligence lessons learned from unsuccessful terrorist attacks against the United States. Stud. Confl. Terror. 2011, 34, 621–648. [Google Scholar] [CrossRef]
- Felson, M.; Cohen, L.E. Human ecology and crime: A routine activity approach. Hum. Ecol. 1980, 8, 389–406. [Google Scholar] [CrossRef]
- Freilich, J.D.; Chermak, S.M.; Simone, J. Surveying American state police agencies about terrorism threats, terrorism sources, and terrorism definitions. Terror. Political Violence 2009, 21, 450–475. [Google Scholar] [CrossRef]
- Galam, S. The September 11 attack: A percolation of individual passive support. Eur. Phys. J. B Condens. Matter Complex Syst. 2002, 26, 269–272. [Google Scholar] [CrossRef]
- Keohane, N.O.; Zeckhauser, R.J. The Ecology of Terror Defense. In The Risks of Terrorism; Springer: New York, NY, USA, 2003. [Google Scholar]
- RAND Corporation. Deterrence & Influence in Counterterrorism; The Defense Advanced Research Projects Agency: Arlington, VA, USA, 2002. [Google Scholar]
- Carly, K.M.; Lee, J.-S.; Krackhardt, D. Destabilizing Networks. Connections 2001, 24, 31–34. [Google Scholar]
- Newman, M.E.J.; Girvan, M. Finding and evaluating community structure in networks. Phys. Rev. E Stat. Nonlinear Soft Matter Phys. 2004, 69, 026113. [Google Scholar] [CrossRef] [PubMed]
- Zhu, P.; Han, J.; Guo, Y.; Lombardi, F. Reliability and Criticality Analysis of Communication Networks by Stochastic Computation. IEEE Netw. 2016, 30, 70–76. [Google Scholar] [CrossRef]
- Zhu, P.; Song, X.; Liu, L.; Wang, Z.; Han, J. Stochastic Analysis of Multiplex Boolean Networks for Understanding Epidemic Propagation. IEEE Access 2018, 6, 35292–35304. [Google Scholar] [CrossRef]
- Gorsuch, R.L. Factor analysis. In Handbook of Psychology; Wiley: Hoboken, NJ, USA, 1983. [Google Scholar]
- Kaiser, H.F. The Application of Electronic Computers to Factor Analysis. Educ. Psychol. Meas. 1960, 20, 141–151. [Google Scholar] [CrossRef]
- Mapa, N.; Jayasinghe, P. The Impact of Terrorist Attacks on Stock Returns and Volatility: Evidence from Colombo Stock Exchange. Soc. Sci. Electron. Publ. 2014, 13. [Google Scholar] [CrossRef]



| KMO (Kaiser Meyer Olkin) | 0.617 | |
|---|---|---|
| Bartley spherical test | Approx. Chi-Square | 1.15 × 106 |
| df. | 300 | |
| Sig | 0.000 |
| Attack Time | F | |
|---|---|---|
| 1 | 20010911 | 10.17531 |
| 2 | 20010911 | 10.15382 |
| 3 | 20140803 | 6.044597 |
| 4 | 20140612 | 5.470455 |
| 5 | 19980807 | 3.775518 |
| 6 | 20040901 | 2.761074 |
| 7 | 20160804 | 2.653305 |
| 8 | 20171014 | 2.194661 |
| 9 | 20140815 | 1.999051 |
| 10 | 20140610 | 1.992567 |
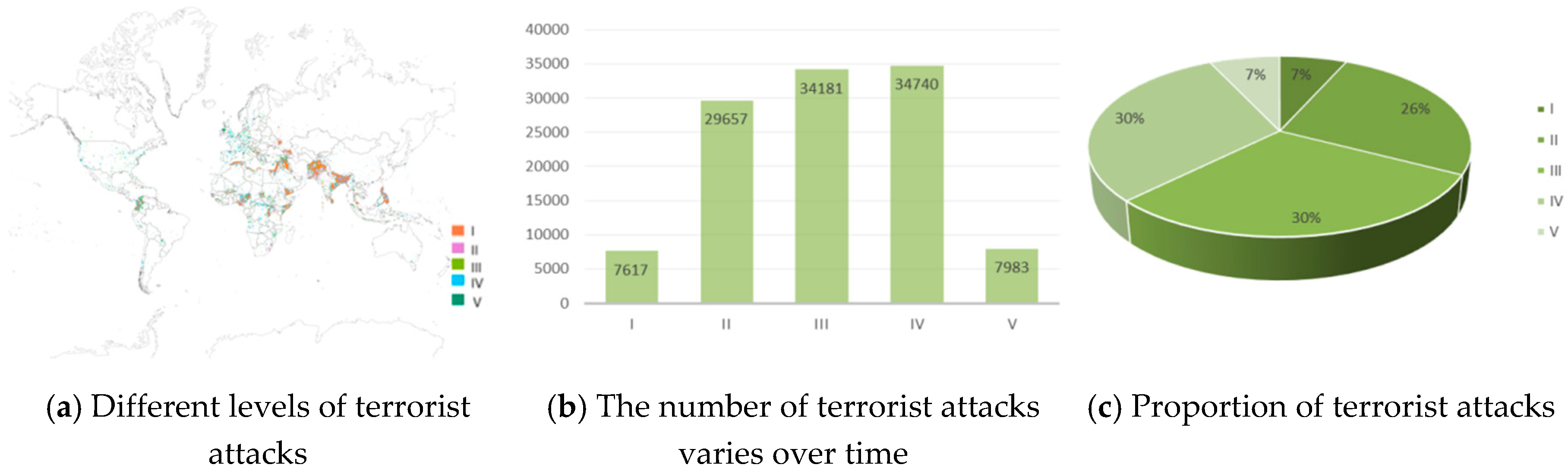
| Grade | Min | Max | Number |
|---|---|---|---|
| I | 0.303 | 10.175 | 7617 |
| II | 0.089 | 0.303 | 29,657 |
| III | −0.079 | 0.089 | 34,181 |
| IV | −0.267 | −0.079 | 34,740 |
| V | −1.535 | −0.267 | 7983 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hu, X.; Lai, F.; Chen, G.; Zou, R.; Feng, Q. Quantitative Research on Global Terrorist Attacks and Terrorist Attack Classification. Sustainability 2019, 11, 1487. https://doi.org/10.3390/su11051487
Hu X, Lai F, Chen G, Zou R, Feng Q. Quantitative Research on Global Terrorist Attacks and Terrorist Attack Classification. Sustainability. 2019; 11(5):1487. https://doi.org/10.3390/su11051487
Chicago/Turabian StyleHu, Xueli, Fujun Lai, Gufan Chen, Rongcheng Zou, and Qingxiang Feng. 2019. "Quantitative Research on Global Terrorist Attacks and Terrorist Attack Classification" Sustainability 11, no. 5: 1487. https://doi.org/10.3390/su11051487
APA StyleHu, X., Lai, F., Chen, G., Zou, R., & Feng, Q. (2019). Quantitative Research on Global Terrorist Attacks and Terrorist Attack Classification. Sustainability, 11(5), 1487. https://doi.org/10.3390/su11051487





