Research on the Coupled Risk of Key Nodes in Maritime Transport Based on Improved Catastrophe Theory
Abstract
:1. Introduction
1.1. Key Nodes
1.2. Risk Coupling of Key Nodes
1.3. Application of Catastrophe Theory in Maritime Transport Security
2. Methods
2.1. Basic Theory
2.1.1. Characteristics of Security Threat Factors in the Nodes of Maritime Transport
- The degree of security of maritime transport nodes is affected by the mutual coupling of two types of control variables: external disaster factors and various measures to address disasters.
- The steady state of maritime transport nodes can suddenly change under different degrees of influence from the above two types of control variables. By measuring the catastrophe level associated with the security of maritime transport nodes, the degree of coupled risk of maritime transport nodes can be effectively evaluated.
- There are two stable states before and after the catastrophe state of maritime transport nodes.
2.1.2. Catastrophe Theory
2.1.3. Principal Component Analysis
- Because the ranges of values and the units of measurement of the original data sets are different, the indices should be normalized.
- Establish the correlation coefficient matrix based on standardized data matrix. reflects the degree of correlation between the standardized data, where is the correlation coefficient between the original variables and , and the calculation formula is,
- Calculate the eigenvalue and the cumulative variance contribution rate based on the correlation coefficient matrix , and then determine the number of principal components, wherein the eigenvalue and the variance contribution rate are calculated as (5) and (6).represents the variance contribution rate of the principal component . In addition, the formula for calculating the cumulative variance contribution rate is,According to the principle of selecting the number of principal components, corresponding to the eigenvalue of greater than 1 and the cumulative variance contribution rate of 80−95% is required, wherein the integer is the number of the main components.
- Establish a factor load matrix to explain the principal components, and the factor load matrix reveals the degree of correlation between principal components and indicators.where denotes the factor load of the th index on the th principal component and denotes the th component of the feature vector corresponding to the th eigenvalue.
- Based on the above results, the principal components are expressed and used for calculation and analysis
2.2. Improved Catastrophe Theory Model Based on PCA
2.2.1. Establish Model
2.2.2. Improved Measurement Model
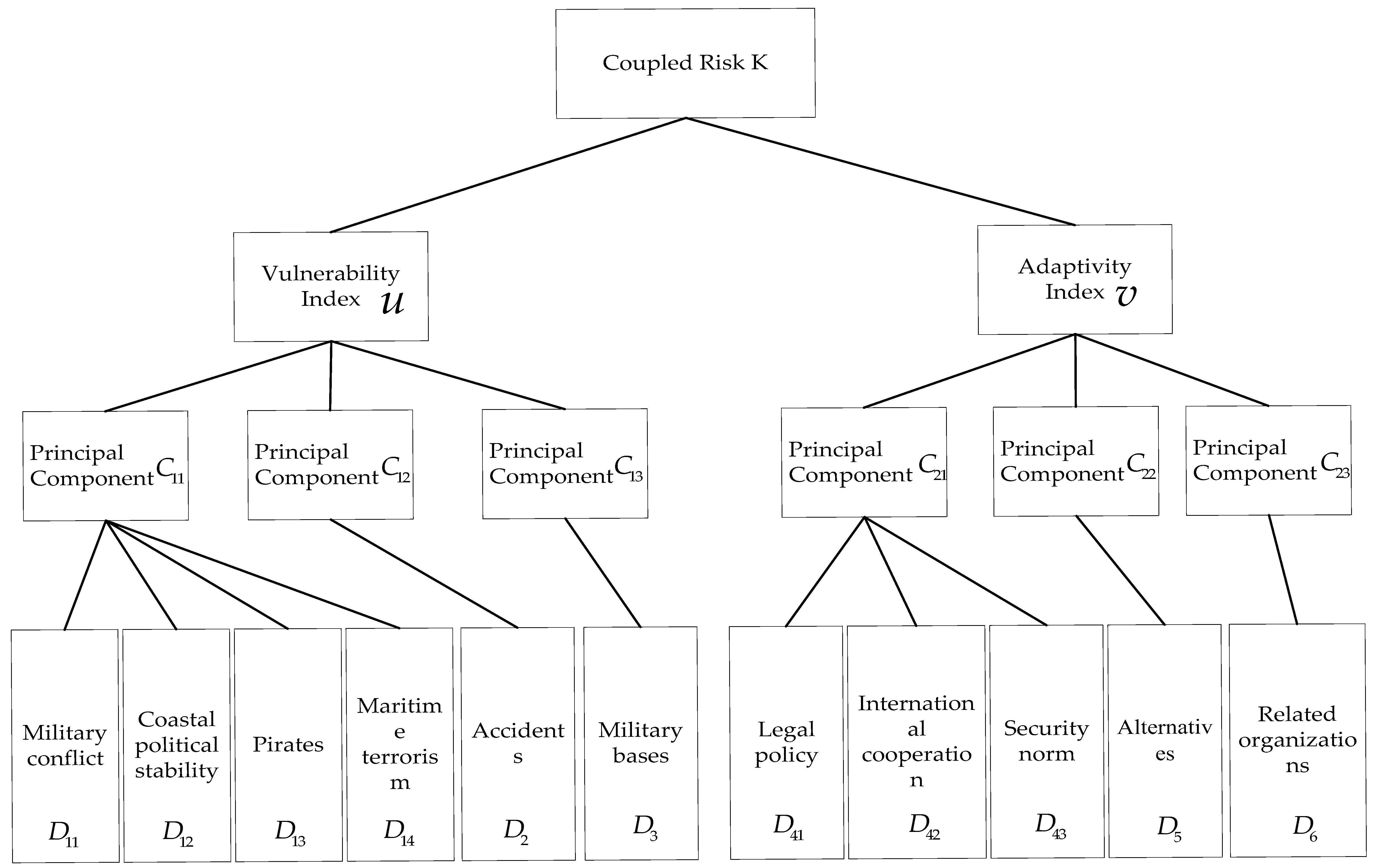
- According to the characteristics of the influential factors, these factors can be divided into two categories: external disaster factors, defined as a vulnerability index, and various measures to address disasters, defined as an adaptivity index.
- PCA was performed on the two types of indices, and the hierarchical structure was established.(1) Because the ranges of values and the units of measurement of the original data sets are different, the indices should be normalized. This paper adopts standardized formulas such as (12) and (13) for this task.where is the value after the influential factor index is processed; denote key nodes; denote the influential factors; is the th influential factor index value of the th key node; and and denote the maximum and minimum values of the th influential factor of the th key node, respectively.(2) Calculate the correlation coefficient matrix of the normalized index data .(3) Calculate the eigenvalues of the correlation coefficient matrix , where denotes the total variance of the original index data explained by the principal component . The variance contribution of the original index data denoted by the principal component can be expressed as follows.Equation (14) denotes the ratio of the original information represented by the th principal component to all the original information. The calculated values are sorted from large to small. When the cumulative variance contribution of the th eigenvalue is greater than or equal to 85%, the principal components corresponding to the first eigenvalues are selected.(4) Calculate the factor load matrix to establish the relationships among indices and importance of each index. Finally, the hierarchical structure of the factor indices is established. Related calculation formula reference (8).
- When using the catastrophe progression method, the obtained values are often clustered. To make the calculated coupling value more intuitively represent the coupling degree of key nodes and facilitate subsequent operations, this paper improves the initial coupling degree value calculated by the traditional catastrophe progression method according to reference [32].First, according to the established coupled risk degree catastrophe model of key nodes, the comprehensive coupling degree value is calculated for control variable set , and the six values are used as the scales of the initial comprehensive values. The corresponding interval for different scales is .Second, the calculated coupling degree value (n denotes key node) is mapped to the corresponding interval according to the scale interval in which it falls, and the adjusted coupling degree value is .
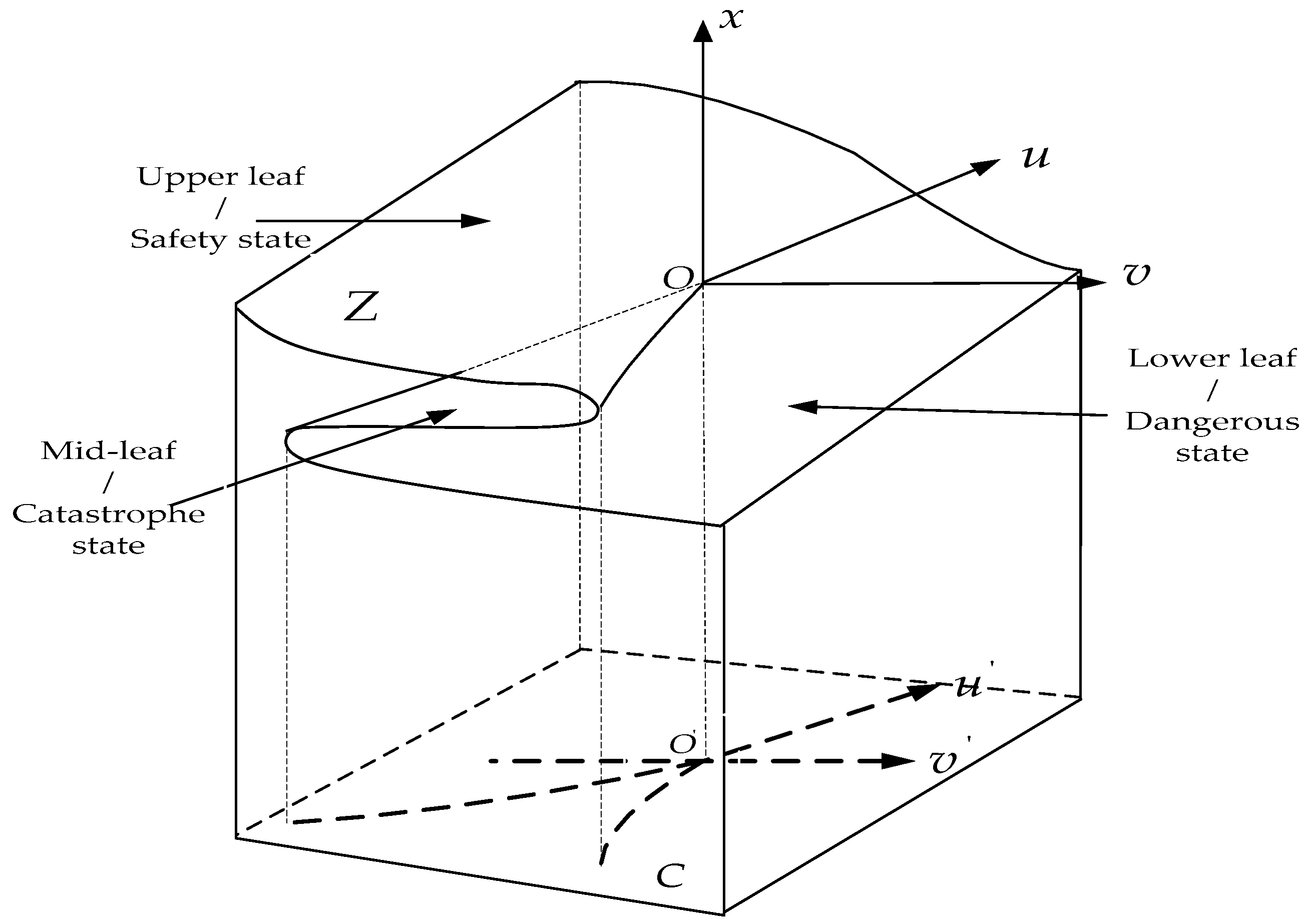
- Based on the above analysis, the final determination of the coupling degree of the key nodes considers both the vulnerability index and the adaptivity index. In addition, according to Table 1, the cusp catastrophe model can be used to describe the state of the security system of the key nodes. The cusp catastrophe state of the key node security system based on the equilibrium state and the control plane can be established as shown in Figure 1.
- (1)
- If , the security system of key nodes in maritime transport is in a stable state.
- (2)
- If , the security system of key nodes in maritime transport is in a critical steady state.
- (3)
- If , the security system of key nodes in maritime transport is in an unstable state.
3. Empirical Analysis
3.1. Selection of Key Nodes in Chinese Maritime Transportation
3.2. Construction of a Coupled Risk Measurement System for Key Nodes
3.2.1. Security Factors
3.2.2. Risk Coupling Measurement System
3.3. Coupled Risk Measurement for Key Nodes in Maritime Transport
3.3.1. Data Sources and Normalization
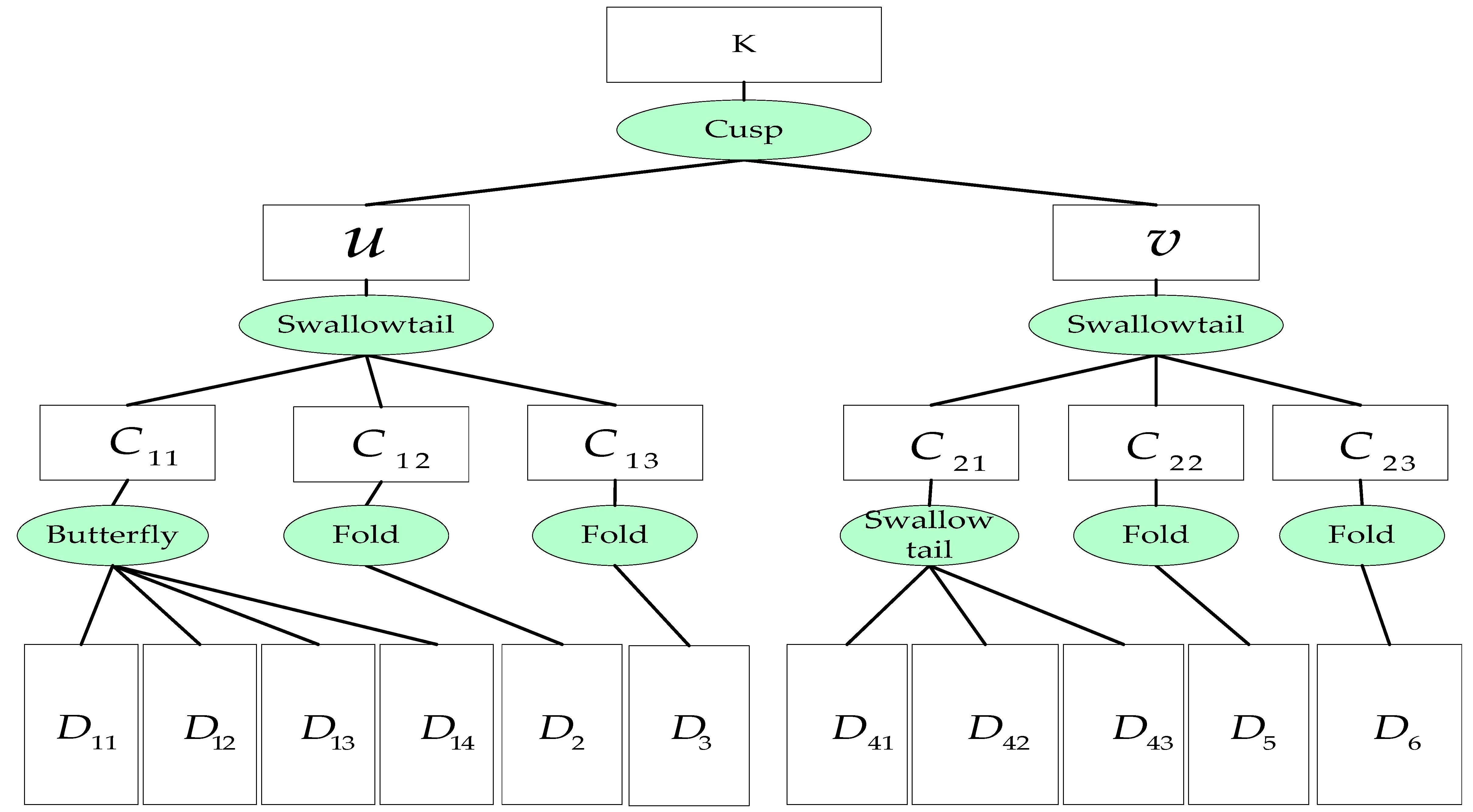
3.3.2. Establishment of the Hierarchy Structure of Key Nodes
3.3.3. Establishment of a Catastrophe Model Based on the Hierarchical Structure of Key Nodes
3.4. Results and Analysis
3.4.1. Calculation Results
3.4.2. Analysis of the Results
4. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Lu, J.; Wang, S. Security Evaluation of China’s Maritime Transport Key Nodes. J. Transp. Syst. Eng. Inf. Technol. 2015, 1, 30–36. [Google Scholar]
- Rusli, M.H.B.M. Protecting vital sea lines of communication: A study of the proposed designation of the Straits of Malacca and Singapore as a particularly sensitive sea area. Ocean Coast. Manag. 2012, 57, 79–94. [Google Scholar] [CrossRef]
- Lee, T.; Mcgahan, K. Norm subsidiarity and institutional cooperation: Explaining the straits of malacca anti-piracy regime. Pac. Rev. 2015, 28, 529–552. [Google Scholar] [CrossRef]
- Bonney, J. Panama canal’s growing risk. J. Commer. 2014, 15, 36. [Google Scholar]
- El-Eraki, M.A.; Abd El-Aal, E.A.K.; Mostafa, S.I. Multi-seismotectonic models, present-day seismicity and seismic hazard assessment for Suez Canal and its surrounding area, Egypt. Bull. Eng. Geol. Environ. 2015, 75, 503–517. [Google Scholar] [CrossRef]
- Katzman, K.; Nerurkar, N.; O’Rourke, R.; Mason, R. Iran’s threat to the strait of hormuz. Am. Foreign Policy Interests 2012, 32, 64–74. [Google Scholar]
- Essiz, B.; Dagkiran, B. Accidental risk analyses of the istanbul and canakkale straits. In IOP Conference Series Earth and Environmental Science; IOP Publishing: Bristol, UK, 2017; p. 95. [Google Scholar]
- Gao, T.; Lu, J. The impacts of strait and canal blockages on the transportation costs of the Chinese fleet in the shipping network. Marit. Policy Manag. 2019, 46, 669–686. [Google Scholar] [CrossRef]
- Di, W.; Nuo, W.; An, Q.Y.; Nuan, W. Vulnerability analysis of global container shipping liner network based on main channel disruption. Marit. Policy Manag. 2019, 46, 394–409. [Google Scholar]
- Zhi, H.; Tsz, L.Y. Impacts of Kra Canal and its toll structures on tanker traffic. Marit. Policy Manag. 2018, 45, 125–139. [Google Scholar]
- Guang, C.L. Preliminary Study on Coupling Theory of Engineering Geology. J. Eng. Geol. 2001, 4, 435–442. [Google Scholar]
- Qing, L.; Guan, X.W. Analysis of Coupling Mechanism of Ship Navigation Security Risk in Complex Waters. J. Wuhan Univ. Technol. 2014, 38, 59–63. [Google Scholar]
- Tian, H.G.; Jing, L.; Mao, J.S. Identification of Risk Factors in Sea Channel Considering Coupling Effect. J. Shanghai Marit. Univ. 2017, 38, 18–24. [Google Scholar]
- Hu, C.P.; Li, F.; Xi, Y.T. Simulation of the coupling mechanism of risk factors in marine transportation systems. J. Basic Sci. Eng. 2015, 2, 409–419. [Google Scholar]
- Cao, J.H.; Xi, Y.T.; Hu, C.P. Coupling model of port ship navigation risk based on system dynamics. J. Secur. Environ. 2015, 3, 65–71. [Google Scholar]
- Fu, S.; Yan, X.; Zhang, D.; Zhang, M. Risk influencing factors analysis of Arctic maritime transportation systems: A Chinese perspective. Marit. Policy Manag. 2018, 45, 439–455. [Google Scholar] [CrossRef]
- Gudela, G. Organizational Measures for Achieving Loose Coupling in High-Risk Systems: The Importance of Systematic Rules Management. In Proceedings of the 2004 IEEE International Conference on Systems, Man and Cybernetics, The Hague, The Netherlands, 10–13 October 2004; pp. 2569–2573. [Google Scholar]
- Peter, B. Air Traffic Management Accident Risk. Part l: The Limits of Realistie Modeling. Secur. Seienee 2006, 44, 419–500. [Google Scholar]
- Poston, T.; Stewart, I. Catastrophe Theory and Its Applications; Courier Corporation: Washington, DC, USA, 1978. [Google Scholar]
- Nashwan, M.S.; Shahid, S.; Chung, E.; Ahmed, K.; Song, Y.H. Development of Climate-Based Indice for Hydrologic Hazard Susceptibility. Sustainability 2018, 10, 2182. [Google Scholar] [CrossRef]
- Ahammed, S.J.; Chung, E.; Shahid, S. Para measurement Assessment of Pre-Monsoon Agricultural Water Scarcity in Bangladesh. Sustainability 2018, 10, 819. [Google Scholar] [CrossRef]
- Zhu, L.Q.; Lu, J.; Li, J. Research on Security Warning of Marine Channel Based on High Dimensional Mutation Model. Oper. Res. Manag. 2016, 25, 261–266. [Google Scholar]
- Qi, J.; Zheng, Z.Y.; Li, J.M. Research on Causes of Maritime Traffic Accidents Based on Mutation Mechanism. China Navig. 2013, 36, 112–115. [Google Scholar]
- Papacharalampous, A.E.; Vlahogianni, E.I. Modeling Microscopic Freeway Traffic Using Cusp Catastrophe Theory. IEEE Intell. Transp. Syst. Mag. 2014, 6, 6–16. [Google Scholar] [CrossRef]
- Ahmed, K.; Shahid, S.; bin Harun, S.; Ismail, T.; Nawaz, N.; Shamsudin, S. Assessment of groundwater potential zones in an arid region based on catastrophe theory. Earth Sci. Inform. 2015, 8, 539–549. [Google Scholar] [CrossRef]
- Liu, W.Y.; Juan, P. Navigation Security Evaluation in Coastal Areas Based on Catastrophe Theory. China Secur. Sci. J. 2010, 20, 113–118. [Google Scholar]
- Thom, R. Structural Stability and Morphogenesis; Benjamin Press: New York, NY, USA, 1972. [Google Scholar]
- Zhong, R.L.; Tian, H.C. Analysis of the Formation Mechanism of Debris Flow in Open-pit Mine Dumping Site Based on Catastrophe Theory. Mod. Min. 2000, 1, 8–10. [Google Scholar]
- Fisher, G.H. Preparation of Ambiguous Stinalus Materials. Recept. Psychophys. 1967, 2, 421–422. [Google Scholar] [CrossRef]
- Sun, X. Research on Coupling of Highway Traffic Security Risk Based on Catastrophe Theory; Beijing Jiaotong University: Beijing, China, 2015. [Google Scholar]
- Zhu, X.Y. SPSS Multivariate Statistical Analysis Method and Application; Tsinghua University Press: Beijing, China, 2011. [Google Scholar]
- Tang, M.; Shao, D.G.; Yao, C.L. Application of improved catastrophe evaluation method in drought risk assessment. J. Hydraul. Eng. 2009, 40, 858–862. [Google Scholar]
- Liang, M.; Chen, R. The current situation and research of China’s maritime trade channel. Int. Econ. Coop. 2014, 11, 79–84. [Google Scholar]
| Model Name | Control Variable | Potential Function | Normalization Formula |
|---|---|---|---|
| Fold | |||
| Cusp | |||
| Swallowtail | |||
| Butterfly |
| Strait/Canal | Affiliation Passage | Important Role | Transport Important Material |
|---|---|---|---|
| Taiwan Strait | China’s coastal areas - Southeast Asia, China’s coastal areas - Africa, China’s coastal areas - Europe, China’s coastal areas - the Middle East, China’s coastal areas - South America’s east coast, China’s coastal areas - Australia | The main channel between the East China Sea and its northern neighbouring seas and the South China Sea and the Indian Ocean | Crude oil, iron ore, coal, grain, container |
| Malacca Strait | China’s coastal areas - Africa, China’s coastal areas - Europe, China’s coastal areas - North America’s east coast - Middle East, China’s coastal areas - South America’s east coast | Important channel between the Indian Ocean and the Pacific Ocean; Important channel from West Asia to East Asia | Crude oil, iron ore, container |
| Mande Strait | China’s coastal areas - North Africa, China’s coastal areas - Europe | Located along the shortest route from the Atlantic Ocean to the Indian Ocean and is an important channel for maritime trade between Europe, Asia, and Africa | Crude oil, container |
| Suez Canal | China’s coastal areas - North Africa, China’s coastal areas - Europe | A famous international waterway connecting the Mediterranean Sea and the Red Sea; essential for maritime navigation in the North Atlantic, Indian Ocean, and Western Pacific | Container |
| Lombok Strait | Indian Ocean - China’s coastal areas, China’s coastal areas - Australia/New Zealand | Provides a connection to the Indonesian Archipelago; important channel for maritime shipping in the Pacific Ocean and the Indian Ocean | Crude oil, iron ore, grain |
| Sunta Strait | Indian Ocean - China’s coastal areas | An important sea route between the Pacific Ocean and the Indian Ocean; on the route from North Pacific countries to East Africa, West Africa; also a detour to the Cape of Good Hope and Europe | Crude oil |
| Makassar Strait | Indian Ocean - China’s coastal areas, China’s coastal areas - Australia/New Zealand | Along an important route to the South China Sea and from the Philippines to Australia | Iron ore, grain |
| Gibraltar Strait | China’s coastal areas - Europe, China’s coastal areas - North America’s east coast | The only channel from the Mediterranean to the Atlantic Ocean is also the throat of Western European and Northern European countries through the Mediterranean Sea, the Suez Canal, and the Indian Ocean | Crude oil, container |
| Hormuz Strait | China’s coastal areas - Middle East | Persian Gulf oil must pass through this sea channel on the way to Western Europe, the United States, Japan and the rest of the world | Crude oil, container |
| Panama Canal | China’s coastal areas - North America’s east coast | Important channel connecting to the Pacific Ocean and Atlantic Ocean | Crude oil, grain, container |
| Korean Strait | China’s coastal areas - Japan | Provides convenient access to the sea between the Japanese Archipelago and the Asian continent; the only channel connecting the Sea of Japan to the East China Sea and the Yellow Sea | Iron ore, grain, container |
| English Channel | China’s coastal areas - Western European countries, North America’s east coast - Caribbean routes | The channel connects the Atlantic Ocean and the North Sea | Container |
| Florida Strait | Western Europe - North America’s south coast | An important channel connecting the Gulf of Mexico and the Atlantic Ocean | Grain, container |
| Dagu Strait | China’s coastal areas - North America’s east coast, China’s coastal areas - North America’s west coast | Sea channel between the ports of the East China Sea, the Yellow Sea coast and the east coast ports of Japan | Grain, container |
| Zonggu Strait | China’s coastal areas - North America’s west coast | An important entrance to the seas of Japan | Container |
| Mindoro Strait | China’s coastal areas - Australia/New Zealand | An important channel along the route from China to the Indian Ocean | Iron ore, grain |
| Windward Strait | Northwest Europe/North America’s east coast - Caribbean routes | An important channel from the Atlantic Ocean to the Caribbean | Grain, container |
| Mona Strait | Northwest Europe/North America’s east coast - Caribbean routes | An important channel connecting the Caribbean Sea and the Atlantic Ocean | Grain, container |
| First-Level Index | Second-Level Index | ||
|---|---|---|---|
| Index | Index Interpretation | Nature of the Index * | |
| Vulnerability | Military conflict | Number of countries at risk of military conflict along the strait or canal/Number of countries in which the strait or canal is located | Negative |
| Military base | Number of countries with military bases along the strait or canal/Number of countries in which the strait or canal is located | ||
| Pirates | Average number of pirate attacks per year in the strait or canal | ||
| Maritime terrorism | Number of countries in which maritime terrorism has occurred along the strait or canal/Number of countries in which the strait or canal is located | ||
| Accident (caused by extreme weather, etc.) | Average number of accidents per year in the strait or canal | ||
| Coastal political stability | Number of countries in which the strait or canal is classified as dangerous/Number of countries in which the strait or canal is located | ||
| Adaptivity | Alternative | Number of alternative channels for the strait or canal | Positive |
| Related organization | Number of responsible agencies in the relevant country or new agencies established to coordinate the management of the strait or canal | ||
| Security norm | Number of special agencies established by the country/countries in which the channel or canal is located to ensure the smooth flow of traffic through the strait or canal | ||
| Legal policy | Number of relevant laws and policies for the strait or canal | ||
| International cooperation | Number of international cooperation measures for the strait or canal | ||
| Index | Military Conflict | Military Base | Pirates | Maritime Terrorism | Accident | Coastal Political Stability | |
|---|---|---|---|---|---|---|---|
| Key Node | |||||||
| Taiwan Strait | 1.00 | 0.75 | 1.00 | 1.00 | 0.40 | 1.00 | |
| Malacca Strait | 0.33 | 0.75 | 0.00 | 0.33 | 0.00 | 0.67 | |
| Mande Strait | 0.00 | 1.00 | 0.45 | 1.00 | 0.88 | 0.00 | |
| Suez Canal | 1.00 | 0.75 | 0.86 | 0.00 | 0.49 | 1.00 | |
| Lombok Strait | 0.00 | 0.75 | 0.48 | 0.00 | 0.93 | 0.00 | |
| Sunta Strait | 0.00 | 1.00 | 0.48 | 0.00 | 0.84 | 0.00 | |
| Makassar Strait | 0.00 | 0.50 | 0.74 | 0.00 | 0.88 | 0.00 | |
| Gibraltar Strait | 1.00 | 0.50 | 0.96 | 1.00 | 0.75 | 1.00 | |
| Hormuz Strait | 0.50 | 0.25 | 0.86 | 1.00 | 0.62 | 0.50 | |
| Panama Canal | 1.00 | 1.00 | 1.00 | 1.00 | 0.80 | 1.00 | |
| Korean Strait | 1.00 | 0.75 | 1.00 | 1.00 | 0.22 | 1.00 | |
| English Channel | 1.00 | 0.00 | 1.00 | 1.00 | 0.31 | 1.00 | |
| Florida Strait | 1.00 | 0.50 | 1.00 | 1.00 | 0.84 | 1.00 | |
| Dagu Strait | 1.00 | 1.00 | 1.00 | 1.00 | 0.97 | 1.00 | |
| Zonggu Strait | 1.00 | 0.75 | 1.00 | 1.00 | 0.93 | 1.00 | |
| Mindoro Strait | 0.00 | 1.00 | 0.98 | 1.00 | 0.88 | 0.00 | |
| Windward Strait | 1.00 | 0.75 | 1.00 | 1.00 | 1.00 | 0.50 | |
| Mona Strait | 1.00 | 0.75 | 0.98 | 1.00 | 1.00 | 1.00 | |
| Index | Alternative | Related Organization | Security Norm | Legal Policy | International Cooperation | |
|---|---|---|---|---|---|---|
| Key Node | ||||||
| Taiwan Strait | 0.33 | 0.33 | 1.00 | 0.60 | 0.25 | |
| Malacca Strait | 1.00 | 1.00 | 1.00 | 0.80 | 1.00 | |
| Mande Strait | 0.33 | 1.00 | 0.00 | 0.20 | 0.00 | |
| Suez Canal | 0.33 | 0.33 | 1.00 | 1.00 | 0.00 | |
| Lombok Strait | 1.00 | 0.50 | 0.00 | 0.40 | 0.00 | |
| Sunta Strait | 1.00 | 0.50 | 0.00 | 0.20 | 0.00 | |
| Makassar Strait | 0.67 | 0.50 | 0.00 | 0.20 | 0.00 | |
| Gibraltar Strait | 0.33 | 0.33 | 1.00 | 0.40 | 0.00 | |
| Hormuz Strait | 0.00 | 0.17 | 0.00 | 0.40 | 0.25 | |
| Panama Canal | 0.33 | 0.33 | 1.00 | 0.00 | 0.00 | |
| Korean Strait | 0.33 | 0.67 | 0.00 | 0.20 | 0.00 | |
| English Channel | 0.33 | 0.50 | 0.00 | 0.20 | 0.00 | |
| Florida Strait | 0.67 | 0.67 | 0.00 | 0.20 | 0.00 | |
| Dagu Strait | 0.67 | 0.33 | 0.00 | 0.20 | 0.00 | |
| Zonggu Strait | 0.67 | 0.33 | 0.00 | 0.20 | 0.00 | |
| Mindoro Strait | 0.67 | 0.17 | 0.00 | 0.00 | 0.00 | |
| Windward Strait | 0.67 | 0.00 | 0.00 | 0.00 | 0.00 | |
| Mona Strait | 0.67 | 0.00 | 0.00 | 0.00 | 0.00 | |
| Vulnerability Index | Principal Component 1 | Principal Component 2 | Principal Component 3 |
|---|---|---|---|
| Cumulative variance contribution (%) | 48.018 | 70.042 | 87.431 |
| Adaptivity Index | Principal Component 1 | Principal Component 2 | Principal Component 3 |
|---|---|---|---|
| Cumulative variance contribution (%) | 40.294 | 63.347 | 85.610 |
| Vulnerability Factors | Principal Component | ||
|---|---|---|---|
| 1 | 2 | 3 | |
| Military conflict | 0.945 | −0.044 | 0.189 |
| Coastal political stability | 0.898 | −0.221 | 0.290 |
| Pirates | 0.793 | 0.425 | −0.243 |
| Maritime terrorism | 0.723 | 0.312 | −0.022 |
| Accidents | −0.137 | 0.903 | −0.255 |
| Military bases | −0.358 | 0.556 | 0.743 |
| Adaptivity Factors | Principal Component | ||
|---|---|---|---|
| 1 | 2 | 3 | |
| Legal policy | 0.857 | −0.199 | 0.045 |
| International cooperation | 0.818 | 0.257 | 0.144 |
| Security norm | 0.744 | −0.474 | 0.234 |
| Alternatives | 0.044 | 0.847 | 0.481 |
| Related organizations | 0.545 | 0.504 | −0.643 |
| Security Level | |||||
|---|---|---|---|---|---|
| Scale | [0, 0.9035) | [0.9035, 0.9436) | [0.9436, 0.9680) | [0.9680, 0.9859) | [0.9859, 1] |
| Key Node | Rank | Security Level | Coupling Degree Value | Adjusted Coupling Degree Value |
|---|---|---|---|---|
| Taiwan Strait | 1 | 0.9617 | 0.5480 | |
| Malacca Strait | 14 | 0.8771 | 0.1941 | |
| Mande Strait | 9 | 0.9225 | 0.2945 | |
| Suez Canal | 5 | 0.9472 | 0.4301 | |
| Lombok Strait | 10 | 0.9107 | 0.2356 | |
| Sunta Strait | 11 | 0.9076 | 0.2205 | |
| Makassar Strait | 12 | 0.8986 | 0.1989 | |
| Gibraltar Strait | 2 | 0.9558 | 0.5004 | |
| Hormuz Strait | 15 | 0.8661 | 0.1917 | |
| Panama Canal | 3 | 0.9533 | 0.4795 | |
| Korean Strait | 8 | 0.9268 | 0.3164 | |
| English Channel | 16 | 0.8362 | 0.1851 | |
| Florida Strait | 7 | 0.9463 | 0.4226 | |
| Dagu Strait | 4 | 0.9500 | 0.4526 | |
| Zonggu Strait | 6 | 0.9464 | 0.4232 | |
| Mindoro Strait | 13 | 0.8896 | 0.1969 | |
| Windward Strait | 18 | 0.8338 | 0.1846 | |
| Mona Strait | 17 | 0.8360 | 0.1850 |
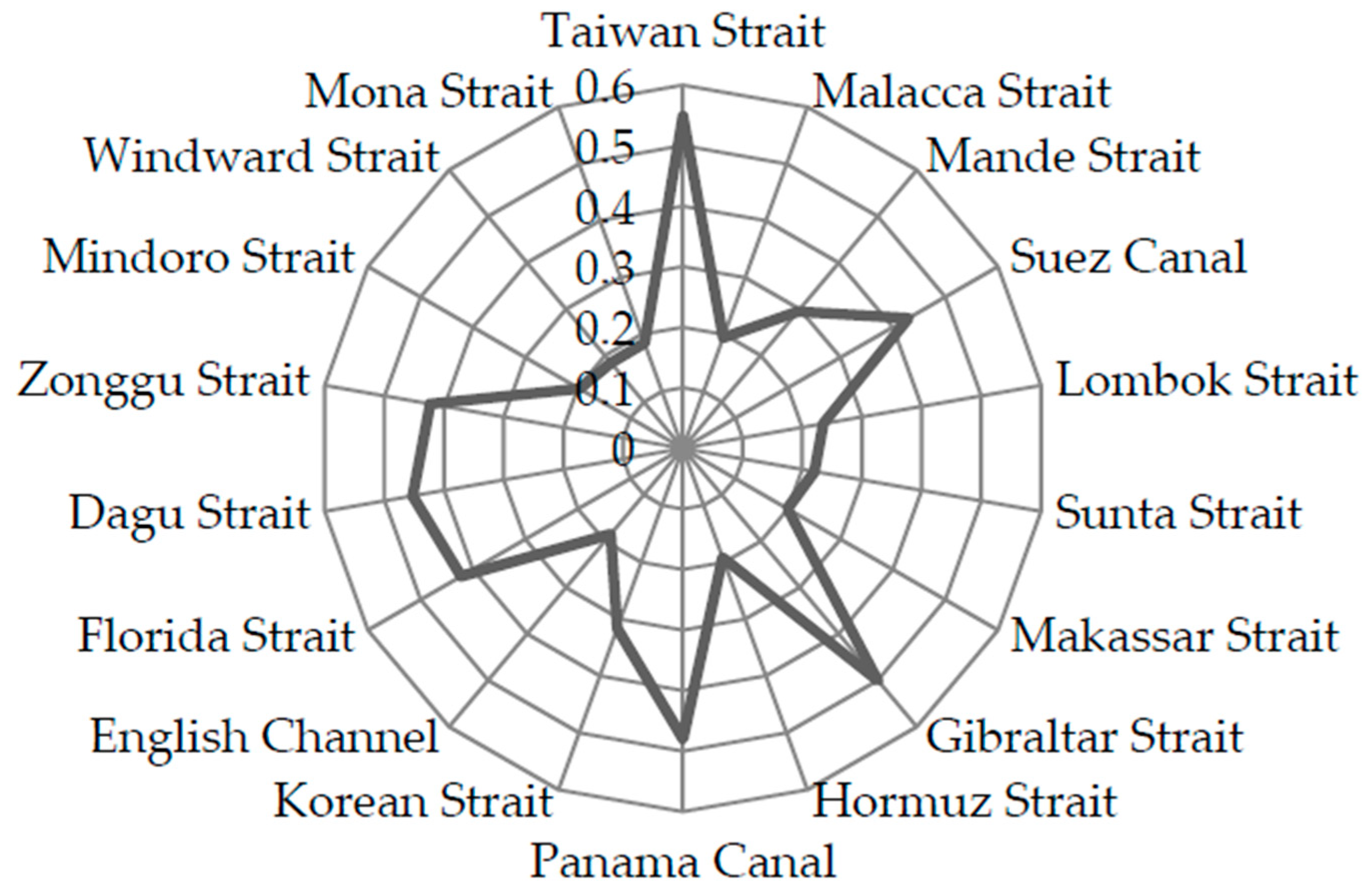
| Key Node | Vulnerability Index Coupling Value (u) | Adaptivity Index Coupling Value (v) |
|---|---|---|
| Taiwan Strait | 0.9408 | 0.8665 |
| Malacca Strait | 0.5718 | 0.9941 |
| Mande Strait | 0.8847 | 0.7396 |
| Suez Canal | 0.9041 | 0.8403 |
| Lombok Strait | 0.8030 | 0.7921 |
| Sunta Strait | 0.8094 | 0.7677 |
| Makassar Strait | 0.7927 | 0.7459 |
| Gibraltar Strait | 0.9565 | 0.8140 |
| Hormuz Strait | 0.8982 | 0.4827 |
| Panama Canal | 0.9876 | 0.7606 |
| Korean Strait | 0.9141 | 0.7231 |
| English Channel | 0.6075 | 0.7119 |
| Florida Strait | 0.9628 | 0.7571 |
| Dagu Strait | 0.9985 | 0.7308 |
| Zonggu Strait | 0.9842 | 0.7308 |
| Mindoro Strait | 0.8953 | 0.5780 |
| Windward Strait | 0.9795 | 0.3116 |
| Mona Strait | 0.9880 | 0.3116 |
| Key Node | Status | ||
|---|---|---|---|
| Taiwan Strait | 0.8665 | 0.4967 | Stable |
| Malacca Strait | 0.9941 | 0.2353 | Stable |
| Mande Strait | 0.7396 | 0.4530 | Stable |
| Suez Canal | 0.8403 | 0.4679 | Stable |
| Lombok Strait | 0.7921 | 0.3917 | Stable |
| Sunta Strait | 0.7677 | 0.3963 | Stable |
| Makassar Strait | 0.7459 | 0.3842 | Stable |
| Gibraltar Strait | 0.8140 | 0.5092 | Stable |
| Hormuz Strait | 0.4827 | 0.4634 | Stable |
| Panama Canal | 0.7606 | 0.5342 | Stable |
| Korean Strait | 0.7231 | 0.4757 | Stable |
| English Channel | 0.7119 | 0.2578 | Stable |
| Florida Strait | 0.7571 | 0.5143 | Stable |
| Dagu Strait | 0.7308 | 0.5431 | Stable |
| Zonggu Strait | 0.7308 | 0.5315 | Stable |
| Mindoro Strait | 0.5780 | 0.4611 | Stable |
| Windward Strait | 0.3116 | 0.5277 | Unstable |
| Mona Strait | 0.3116 | 0.5346 | Unstable |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, B.; Li, J.; Lu, J. Research on the Coupled Risk of Key Nodes in Maritime Transport Based on Improved Catastrophe Theory. Sustainability 2019, 11, 4640. https://doi.org/10.3390/su11174640
Li B, Li J, Lu J. Research on the Coupled Risk of Key Nodes in Maritime Transport Based on Improved Catastrophe Theory. Sustainability. 2019; 11(17):4640. https://doi.org/10.3390/su11174640
Chicago/Turabian StyleLi, Baode, Jing Li, and Jing Lu. 2019. "Research on the Coupled Risk of Key Nodes in Maritime Transport Based on Improved Catastrophe Theory" Sustainability 11, no. 17: 4640. https://doi.org/10.3390/su11174640
APA StyleLi, B., Li, J., & Lu, J. (2019). Research on the Coupled Risk of Key Nodes in Maritime Transport Based on Improved Catastrophe Theory. Sustainability, 11(17), 4640. https://doi.org/10.3390/su11174640




