A Case Study of Pyramid Scheme Finance Flow Network Based on Social Network Analysis
Abstract
1. Introduction
2. Materials and Methods
2.1. The “5.03” Finance Flow Network
2.2. Descriptive Statistical Analysis
2.3. Motifs Analysis
2.4. ERGMs Analysis
3. Results
3.1. Visualization and Statistical Analysis of the Finance Flow Network
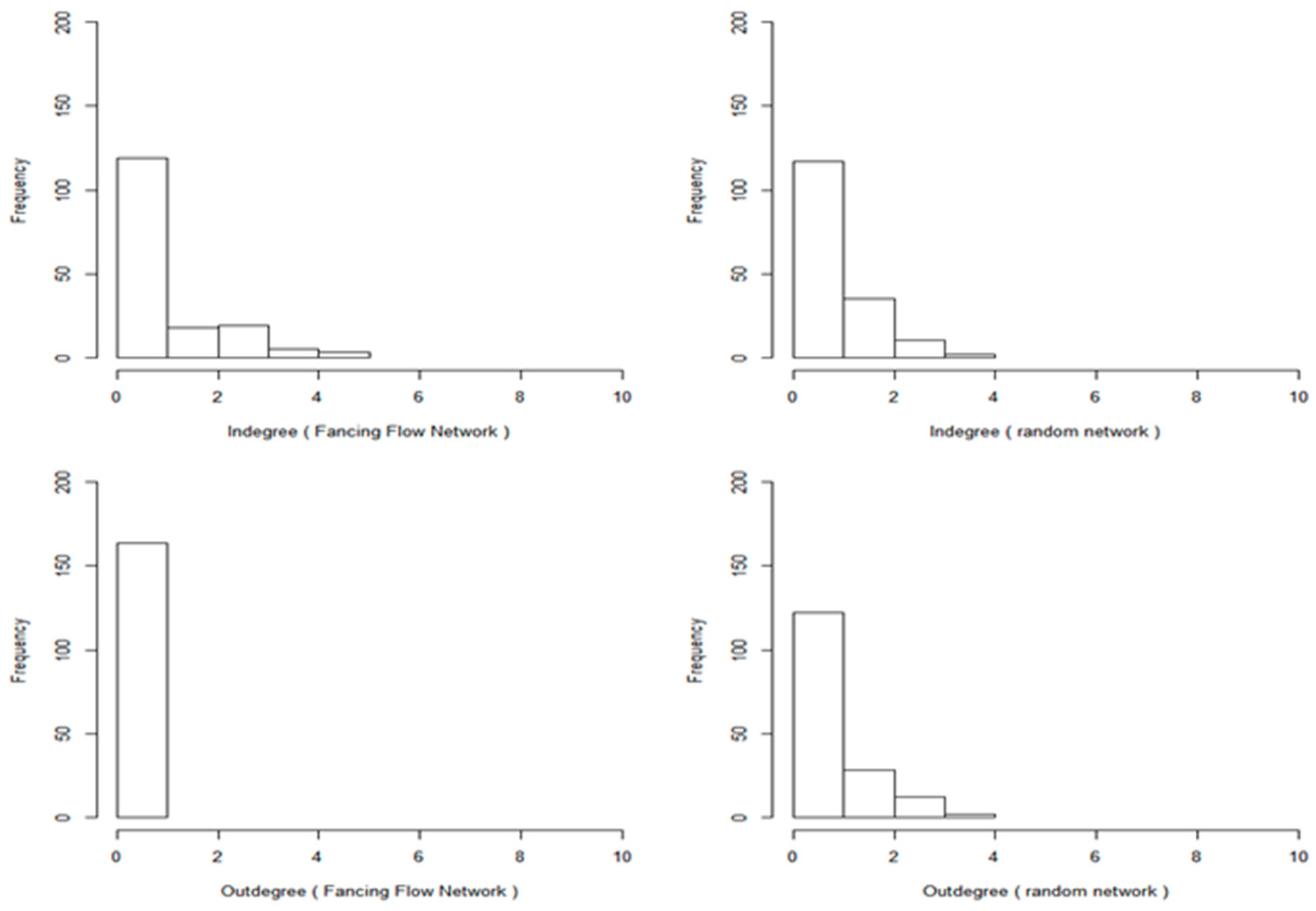
3.2. Motif Analysis Results
3.3. Exponential Random Graph Models Analysis Results
4. Conclusions and Discussion
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Antian Mobile Security Co., Ltd. 2017 China Mobile Pyramid Scheme Fraud Threat Situation Analysis Report; AVLTeam: Beijing, China, 2018. [Google Scholar]
- Moisander, J.; Groß, C.; Eräranta, K. Mechanisms of biopower and neoliberal governmentality in precarious work: Mobilizing the dependent self-employed as independent business owners. Hum. Relat. 2018, 71, 375–398. [Google Scholar] [CrossRef]
- Koehn, D. Ethical issues connected with multi-level marketing schemes. J. Bus. Ethics 2001, 29, 153–160. [Google Scholar] [CrossRef]
- Jarvis, C. The rise and fall of Albania’s pyramid schemes. Financ. Dev. 2000, 37, 46–49. [Google Scholar]
- Tencent Security Joint Lab. 2017 Pyramid Scheme Situational Awareness White Paper. Available online: https://slab.qq.com/news/authority/1745.html (accessed on 7 June 2019).
- Aliber, R.Z.; Kindleberger, C.P. Manias, Panics, and Crashes: A History of Financial Crises; Springer: New York, NY, USA, 2017. [Google Scholar]
- Australian Competition and Consumer Commission. Available online: https://www.scamwatch.gov.au/types-of-scams/jobs-employment/pyramid-schemes (accessed on 7 June 2019).
- Bosley, S.; McKeage, K.K. Multilevel marketing diffusion and the risk of pyramid scheme activity: The case of fortune hi-tech marketing in Montana. J. Public Policy Market. 2015, 34, 84–102. [Google Scholar] [CrossRef]
- Walsh, J. You Can’t Cheat an Honest Man: How Ponzi Schemes and Pyramid Frauds Work and Why They’re More Common Than Ever; Silver Lake Publishing: Aberdeen, WA, USA, 1998. [Google Scholar]
- Schiffauer, L. Dangerous speculation: The appeal of pyramid schemes in rural Siberia. Focaal 2018, 2018, 58–71. [Google Scholar] [CrossRef]
- William, W.K.; Vander Nat, P.J. Multilevel marketing and pyramid schemes in the United States: An historical analysis. J. Hist. Res. Market. 2014, 6, 188–210. [Google Scholar]
- Otte, E.; Rousseau, R. Social network analysis: A powerful strategy, also for the information sciences. J. Inf. Sci. 2002, 28, 441–453. [Google Scholar] [CrossRef]
- Wasserman, S.; Faust, K. Social Network Analysis: Methods and Applications; Cambridge University Press: Cambridge, UK, 1994. [Google Scholar]
- Wellman, B. Network analysis: Some basic principles. Sociol. Theory 2007, 1, 155–200. [Google Scholar] [CrossRef]
- Amato, F.; Bosco, A.; Moscato, V.; Picariello, A.; Sperlí, G. A Novel Influence Diffusion Model based on User Generated Content in Online Social Networks. In Proceedings of the International Conference on Data Technologies and Applications, Madrid, Spain, 24–26 July 2017; pp. 314–320. [Google Scholar]
- Amato, F.; Castiglione, A.; Moscato, V.; Antonio, P.; Giancarlo, S. Multimedia summarization using social media content. Multimed. Tools Appl. 2018, 77, 17803–17827. [Google Scholar] [CrossRef]
- Newman, M.E.J. The Structure and Function of Complex Networks. SIAM Rev. 2003, 45, 167–256. [Google Scholar] [CrossRef]
- Shen-Orr, S.S.; Milo, R.; Mangan, S.; Alon, U. Network motifs in the transcriptional regulation network of Escherichia coli. Nat. Genet. 2002, 31, 64–68. [Google Scholar] [CrossRef]
- Lusher, D.; Robins, G. Exponential Random Graph Models for Social Networks: Example Exponential Random Graph Model Analysis; Cambridge University Press: Cambridge, UK, 2013. [Google Scholar]
- Wang, P.; Sharpe, K.; Robins, G.L.; Pattison, P.E. Exponential random graph (p∗) models for affiliation networks. Soc. Netw. 2009, 31, 12–25. [Google Scholar] [CrossRef]
- Carlos, L.; Machado, C.; Sarmiento, M. Identifying central bank liquidity super-spreaders in interbank finances networks. J. Financ. Stab. 2018, 35, 75–92. [Google Scholar]
- Massimiliano, A.; Pozzolo, A.F. The interbank network across the global financial crisis: Evidence from Italy. J. Bank. Financ. 2017, 80, 90–107. [Google Scholar]
- Rednet. Available online: http://hn.rednet.cn/c/2012/08/10/2710452.htm (accessed on 7 June 2019).
- Coleman, T.F.; Moré, J.J. Estimation of sparse Jacobian matrices and graph coloring problems. SIAM J. Numer. Anal. 1983, 20, 187–209. [Google Scholar] [CrossRef]
- Pastor-Satorras, R.; Rubi, M.; Diaz-Guilera, A. Statistical Mechanics of Complex Networks; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2003; Volume 625. [Google Scholar]
- Jonathan, L.G. Graph Theory and Its Applications, 2nd ed.; CRC Press: London, UK, 2005. [Google Scholar]
- West, D.B. Introduction to Graph Theory; Prentice Hall: Upper Saddle River, NJ, USA, 1996. [Google Scholar]
- Milo, R.; Shen-Orr, S.; Itzkovitz, S.; Kashtan, N.; Chklovskii, D.; Alon, U. Network motifs: Simple building blocks of complex networks. Science 2002, 298, 824–827. [Google Scholar] [CrossRef]
- Alon, U. Network motifs: theory and experimental approaches. Nat. Rev. Genet. 2007, 8, 450–461. [Google Scholar] [CrossRef]
- Squartini, T.; Garlaschelli, D. Triadic Motifs and Dyadic Self-Organization in the World Trade Network; Springer: New York, NY, USA, 2012; pp. 24–35. [Google Scholar]
- Song, N.; Han, H.; Wu, Y. Research on the Model of Stock Market Network and the Purchasing Behavior of Investors. J. Wuhan Univ. Technol. 2013, 35, 257–261. [Google Scholar]
- Robins, G.; Pattison, P.; Kalish, Y.; Lusher, D. An introduction to exponential random graph (p*) models for social networks. Soc. Netw. 2007, 29, 173–191. [Google Scholar] [CrossRef]
- Snijders, T.A.B.; Pattison, P.E.; Robins, G.L.; Handcock, M.S. New specifications for exponential random graph models. Sociol. Methodol. 2006, 36, 99–153. [Google Scholar] [CrossRef]
- Robins, G.; Pattison, P.; Wang, P. Closure, connectivity and degree distributions: Exponential random graph (p*) models for directed social networks. Soc. Netw. 2009, 31, 105–117. [Google Scholar] [CrossRef]
- Harris, J.K. An Introduction to Exponential Random Graph Modeling; Sage: Thousand Oaks, CA, USA, 2013. [Google Scholar]
- Bastian, M.; Heymann, S.; Jacomy, M. Gephi: An open-source software for exploring and manipulating networks. In Proceedings of the Third International on Weblogs and Social Media ICWSM Conference (2009), San Jose, CA, USA, 17–20 May 2009. [Google Scholar]
- Csardi, G.; Nepusz, T. The igraph software package for complex network research. InterJ. Complex Syst. 2006, 1695, 1–9. [Google Scholar]
- Handcock, M.S.; Hunter, D.R.; Butts, C.T.; Goodreau, S.M.; Morris, M. Statnet: Software Tools for the representation, visualization, analysis and simulation of network data. J. Stat. Softw. 2008, 24, 1548–7660. [Google Scholar] [CrossRef]
- Tran, N.T.L.; Mohan, S.; Xu, Z.; Huang, C.H. Current innovations and future challenges of network motif detection. Brief. Bioinform. 2014, 16, 497–525. [Google Scholar] [CrossRef]
- Wernicke, S.; Rasche, F. FANMOD: A tool for fast network motif detection. Bioinformatics 2006, 22, 1152–1153. [Google Scholar] [CrossRef]
- Wang, P.; Robins, G.; Pattison, P. PNet: A Program for the Simulation and Estimation of Exponential Random Graph Models; University of Melbourne: Parkville, Australia, 2006. [Google Scholar]
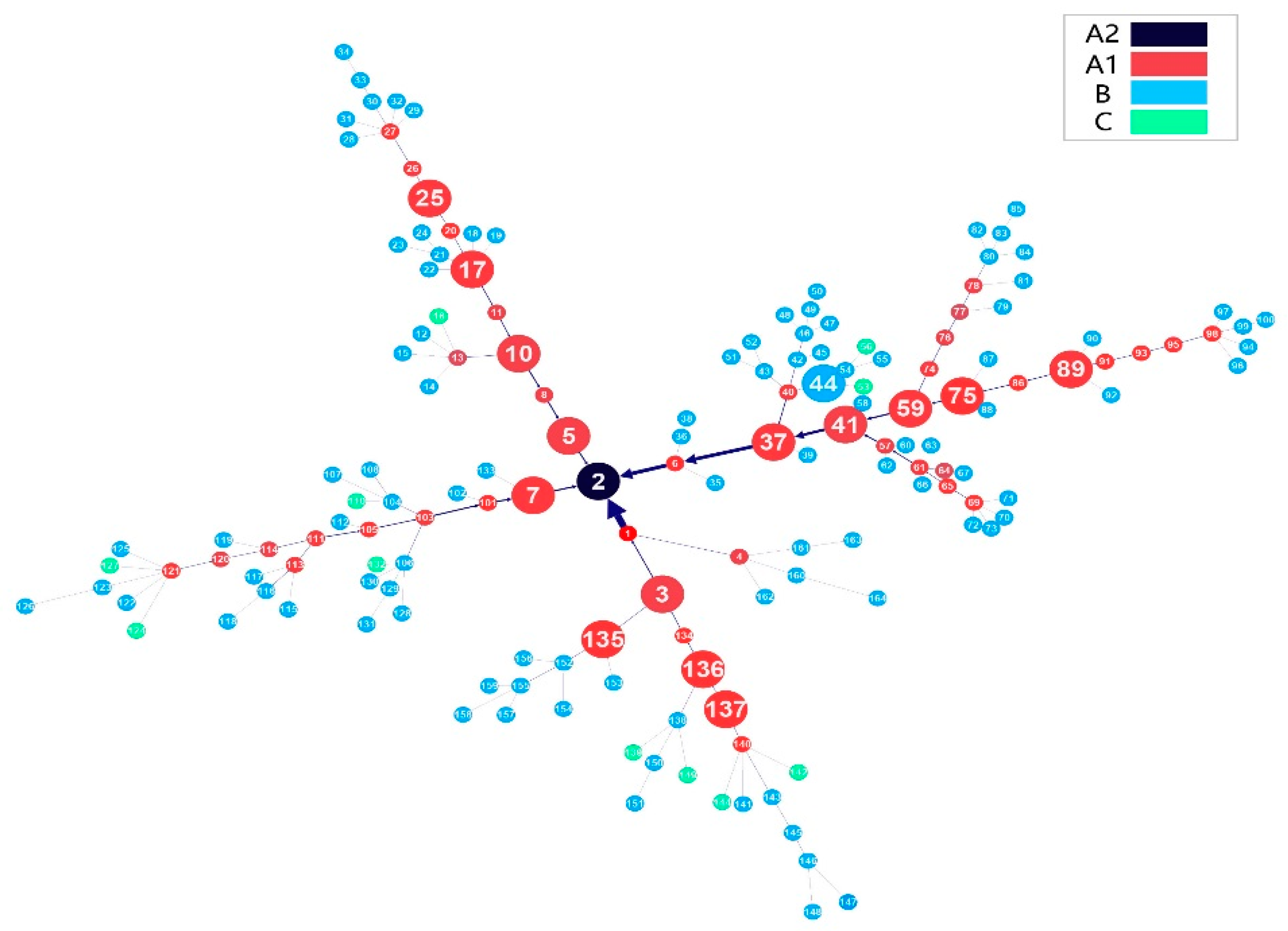
| Node Number | Level | Node Number | Level | Node Number | Level |
|---|---|---|---|---|---|
| 2 | A2 | 25 | A1 | 89 | A1 |
| 3 | A1 | 37 | A1 | 135 | A1 |
| 5 | A1 | 41 | A1 | 136 | A1 |
| 7 | A1 | 44 | A1 | 137 | A1 |
| 10 | A1 | 59 | A1 | ||
| 17 | A1 | 75 | A1 |
| Measure | Definition |
|---|---|
| Density | The density is the ratio of the actual number of connections between network members to the number of connections that may exist in the network [24]. It can represent the tightness of connections between nodes. |
| Average Distance | The average distance is the ratio of the sum of the distances between all nodes in the network to the number of node pairs that are linked in the network [25]. It is used to describe the extent of the network hierarchy. |
| Connectivity | The connectivity refers to the degree of reachability between any node in the network [26]. It is used to measure the flexibility of the network. |
| Transitivity | The transitivity refers to the ratio of the number of observed triangles in the network to the number of triangles in theory [27]. It is used to describe the degree of intimacy of regional members. |
| Degree Centralization | The degree centralization of a network is the variation in the degrees of vertices divided by the maximum degree, which is possible in the network of the same size [26]. It is used to describe the closeness of the graph around a certain core node. |
| Index | Number of Nodes | Isolated Node | Number of Relationships | Density | Average Distance | Transitivity | Connectivity | Degree Centralization |
|---|---|---|---|---|---|---|---|---|
| Value | 177 | 14 | 163 | 0.006 | 4.468 | 0.039 | 0.964 | 0.006 |
| ID | Adj. | Frequency | Mean Freq. | Standard Dev. | Z-Score | p-Value |
|---|---|---|---|---|---|---|
| 12 |  | 53.767% | 53.55% | 0.0036855 | 0.58812 | 0 |
| 2116 | 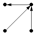 | 13.628% | 12.222% | 0.0043736 | 3.2151 | 0 |
| 2184 |  | 9.5764% | 8.6781% | 0.0028508 | 3.151 | 0.001 |
| 218401 |  | 2.3941% | 2.1695% | 0.0007127 | 3.151 | 0.001 |
| 211601 |  | 4.7882% | 4.3219% | 0.0015432 | 3.0217 | 0.001 |
| 541200 |  | 1.434% | 1.133% | 0.00084792 | 3.5503 | 0.001 |
| 532744 |  | 3.9197% | 3.0479% | 0.0025339 | 3.4405 | 0 |
| 532744 |  | 1.0516% | 0.82421% | 0.00068279 | 3.3306 | 0 |
| 532744 | 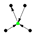 | 1.2428% | 0.97106% | 0.00095356 | 2.8501 | 0 |
| 67632 |  | 0.57361% | 0.14426% | 0.0017707 | 2.4248 | 0.02 |
| 532520 |  | 0.66922% | 0.24601% | 0.0017472 | 2.4222 | 0.014 |
| 67088 |  | 0.66922% | 0.24834% | 0.0017529 | 2.401 | 0.014 |
| 49680 |  | 0.86042% | 0.35767% | 0.0021958 | 2.2895 | 0.021 |
| 67632 | 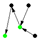 | 1.7208% | 0.97039% | 0.0035135 | 2.1359 | 0.001 |
| 532744 |  | 6.501% | 4.7668% | 0.0039283 | 4.4144 | 0 |
| 67632 |  | 11.95% | 8.8995% | 0.0076069 | 4.0105 | 0 |
| 541200 |  | 1.912% | 1.4323% | 0.0012142 | 3.9514 | 0.001 |
| 66704 |  | 13.193% | 10.192% | 0.0096039 | 3.1248 | 0.001 |
| Effects | Estimates | Std. Err. | t-Ratio | Sign. |
|---|---|---|---|---|
| Purely structural effects | ||||
| arc | −5.961773 | 0.19058 | −0.00001 | * |
| 2-in-star | 2.039363 | 0.26784 | −0.04876 | * |
| 2-path | 0.27058 | 0.06397 | −0.05768 | * |
| isolates | −2.712007 | 0.34793 | 0.00452 | * |
| AinS(2.00) | 1.967811 | 0.60594 | 0.02872 | * |
| Ain1out-star(2.00) | 2.925775 | 0.87962 | −0.01153 | * |
| Actor-relation effects | ||||
| indicted_sender | −0.482213 | 0.37923 | 0.10449 | |
| indicted_receiver | 0.805792 | 0.23738 | 0.05713 | * |
| indicted_interaction | 1.292391 | 0.55386 | 0.01906 | * |
| community_matching | 11.645678 | 0.16729 | −0.00087 | * |
| level_matching | −2.396961 | 0.12295 | 0.00001 | * |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Feng, P.; Sun, D.; Gong, Z. A Case Study of Pyramid Scheme Finance Flow Network Based on Social Network Analysis. Sustainability 2019, 11, 4370. https://doi.org/10.3390/su11164370
Feng P, Sun D, Gong Z. A Case Study of Pyramid Scheme Finance Flow Network Based on Social Network Analysis. Sustainability. 2019; 11(16):4370. https://doi.org/10.3390/su11164370
Chicago/Turabian StyleFeng, Pihu, Duoyong Sun, and Zaiwu Gong. 2019. "A Case Study of Pyramid Scheme Finance Flow Network Based on Social Network Analysis" Sustainability 11, no. 16: 4370. https://doi.org/10.3390/su11164370
APA StyleFeng, P., Sun, D., & Gong, Z. (2019). A Case Study of Pyramid Scheme Finance Flow Network Based on Social Network Analysis. Sustainability, 11(16), 4370. https://doi.org/10.3390/su11164370





