1. Introduction
A wide range of solutions, beyond the classical one of building more lines, cables and transformers, have been proposed to modernize the power grid with new technologies, enabling a more smart automatic networked system. These solutions, typically using new technology, go by the name “smart grids” (SG) or “smart-grid technology”. Conventional electric grids have limited abilities to cope up with the present increasing energy demand [
1], whereas SGs can automate and manage the needs of the energy industry in a smarter way. The digital technology that allows two-way energy and information flow adds computing, controlling, monitoring and communication capabilities to the conventional power grid, making the grid smart [
2]. The concept of distributed generation in SG helps to replace traditional energy sources (fossil-fuel-based) by renewable energy sources (RESs), such as solar and wind energy. This created a new type of grid user called “prosumers” who can generate, consume and trade energy locally. Demand response (DR) programs in SG aim to provide services to reshape demand/load curve by scheduling the energy generation/consumption of grid users. These programs allow users to be part of the electric grid operation by minimizing and shifting their electricity usage during peak periods based on market rates and providing incentives [
3]. Electric vehicles (EVs) can also be used in DR programs, as they can act as energy carriers and mobile energy storage, which helps with de-carbonization and green city development [
4]. Grid-to-vehicle (G2V) and vehicle-to-grid (V2G) interaction allow electric vehicles to draw/deliver energy from/to the grid respectively. V2G is still in the conceptual stage; however, its potential for DR management is being explored.
Even though RES is considered one of the solutions to the energy problem, its integration causes challenges to the grid [
5]. The unpredictable nature of RES and energy users has added an additional level of uncertainty within the users and the grid. However, at a large scale, to ensure security and efficient energy utilization, it requires large number of communications [
6]. These communications should be maintained by a secure channel for ensuring complete grid security. Hence, the design of reliable and secure open communication system represents a key issue in SG deployments. Managing the increasing energy demand, number of electricity users, rise of EVs, energy trading and distributed generation using a centralized system is difficult. Such systems would require complex infrastructure and are effected by single point failure. Moreover, the privacy of users and security aspects will also become a major concern. With the current market structure that involves day-a-head predictions and intra-day predictions for determining energy price and trading, most of the time, energy predictions do not meet, which results in grid imbalance [
7]. Hence, the proper scheduling and prediction of energy usage is necessary [
8]. For all this, a sophisticated decentralized secure method and an intelligent system which can predict the amount of energy based on the usage pattern and energy demand are required.
Blockchain technology (BC) is a viable solution to overcome the issues of centralized system. BC is an immutable, distributed and P2P network that provides security, privacy and trust among peers using cryptographic techniques. It is the enabling technology behind the most popular cryptocurrency bitcoin [
9]. However, the potential of BC was explored in many areas beyond cryptocurrencies, and the invention of smart contracts created a significant impact on several sectors, namely healthcare, markets, supply chain, cyber–physical systems and IoT [
10,
11,
12]. In ref. [
13], the authors explain the application of blockchain in healthcare. Ref. [
14] explains the systematic review of blockchain applications in the supply chain. Ref. [
15] demonstrates the performance analysis of blockchain enabled wireless internet of things. Ref. [
16] proposes a novel blockchain enabled intelligent safe driving assessment framework and investigates the trustworthiness of distributed blockchain for connected and autonomous vehicles (CAVs) data. Ref. [
17] proposes a secure and smart framework using blockchain for ensuring trading between heterogeneous radio communications. Ref. [
10] performs a comprehensive survey on the application of blockchain technology in internet of things (IoT). In ref. [
12], a review of blockchain applications in cyber–physical systems is given. The use of BC in the energy sector is also a key research topic, and several works related to energy trading, electric vehicle security, load balancing, grid security, etc., are in progress [
18]. The key concepts of BC, such as encryption algorithms, consensus mechanisms, smart contracts, decentralization and distributed data storage, can be used as a solution to the problems faced in the energy sector today.
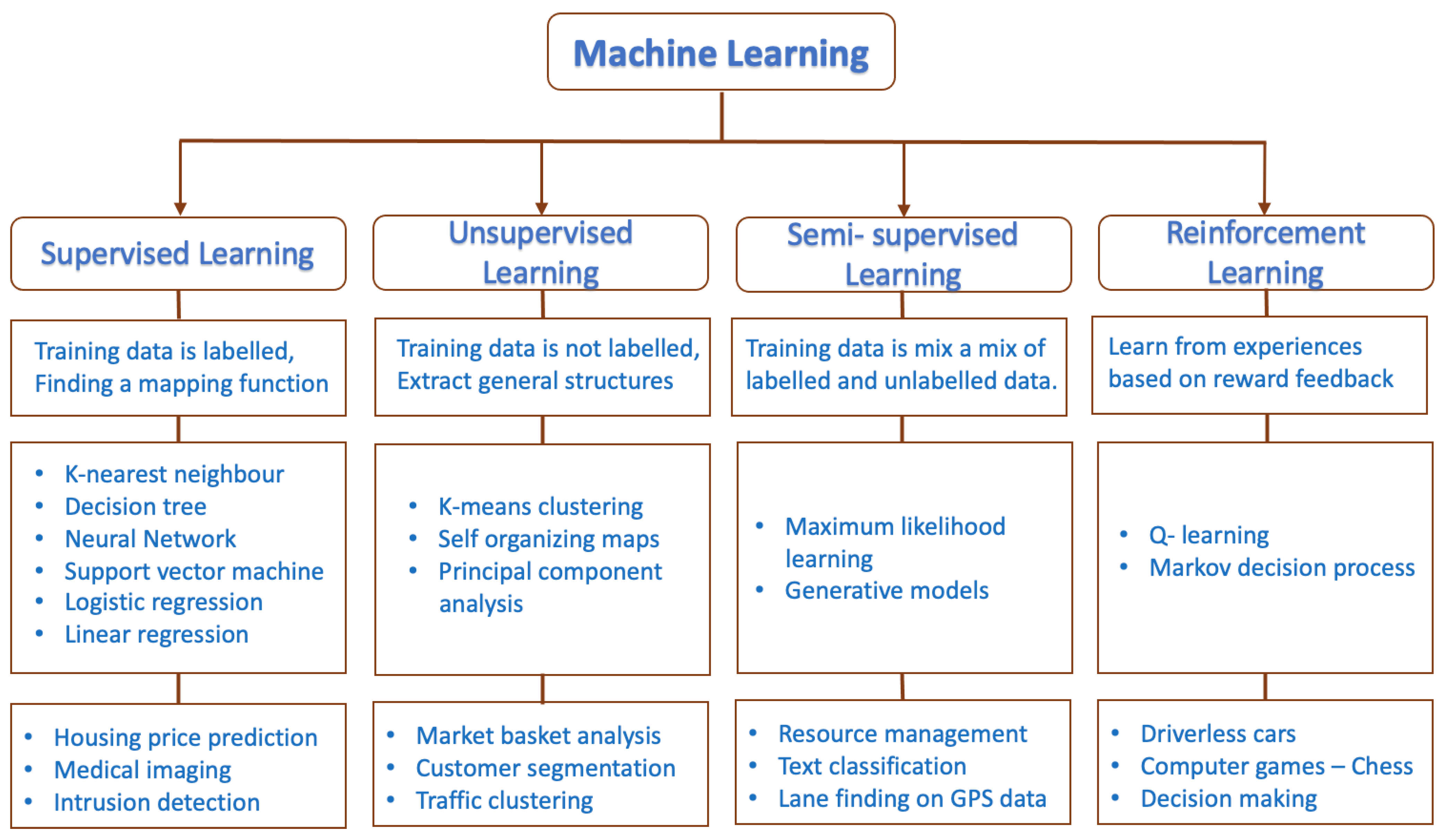
Machine learning (ML) techniques can be exploited to develop energy prediction algorithms and the proper scheduling of energy usage. A large amount of the energy consumption data of several users is generated from smart meters that also contain users’ private/confidential information as well as sensitive information of utility providers. This high volume of data increases the complexity of data analysis. Hence, a ML model is needed that can handle such a large amount of data for ensuring proper SG operation while preventing data security attacks. Extensive research is being carried out in this field [
19,
20,
21]. ML techniques applied in smart energy grids help in load prediction, faulty data detection, big data analysis, power quality measurement, DRM and weather forecasting [
22]. Further, the accurate, early prediction of energy helps to balance the generation/consumption by the proper scheduling of energy usage [
7,
8].
To achieve a decentralized, secure, efficient network optimization and management, combined BC and ML solutions will give significant benefits [
23]. Centralized ML techniques are inefficient and require many complicated parameters [
24]. Similarly, BC can only achieve, at most, two of the three properties—decentralization, scalability and security—at the same time. Motivated from these facts, the joint consideration of BC technology and ML techniques has many potential advantages in several fields, especially in the energy sector. BC principles, such as data security, distributed consensus, and immutability along with ML prediction algorithms will help to develop a secure, decentralized and balanced grid [
25,
26]. The major concern for applications considering BC and ML is (1) the ideal choice of the BC type, miners and consensus mechanism, and (2) the choice of a suitable prediction algorithm which provides a scalable, reliable, accurate and secure energy trading or charging system. Considering these aspects, we identify the need for a literature review in the area that can give insights into addressing the challenges arising from their combined use in smart grids.
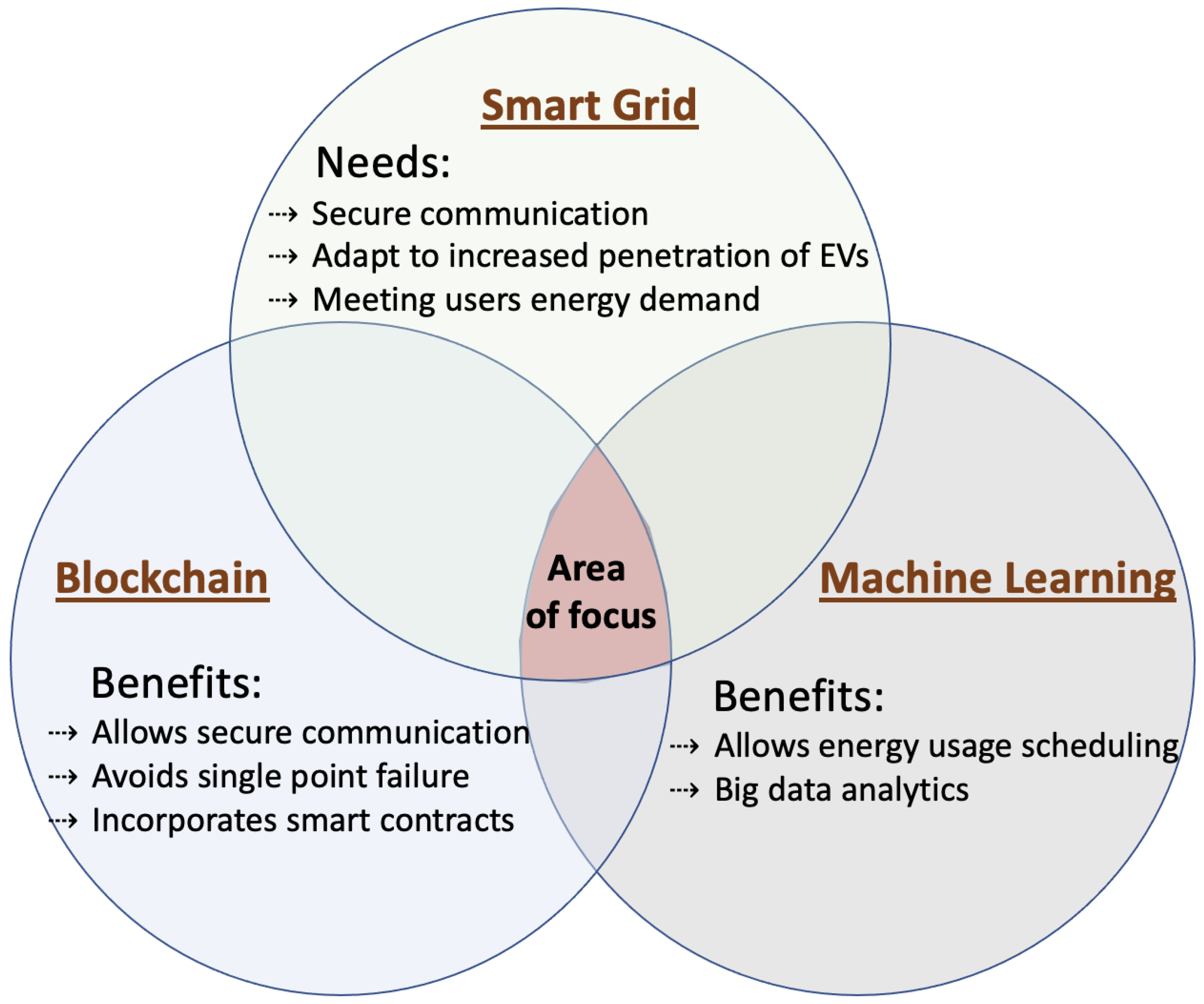
The scope of this article (see
Figure 1) is to understand the use of BC and ML techniques in SG applications. A number of surveys that address the integration of BC with SG are presented in [
6,
18,
27,
28,
29,
30], while others have looked into the integration of ML with SG [
8,
31]. From these, we identify the potential of integrating the combination of BC and ML for SGs. However, to the best of our knowledge, there is no extensive review that integrates BC and ML in the context of SG.
In our review paper, we used the following methodology. We selected papers that were identified based on relevance, publication venue, and citations. We used the keywords “smart grid”, “blockchain”, “machine learning”, “smart grid and blockchain applications”, “smart grid and machine learning applications”, and “smart grid, blockchain and machine learning”. With the initial search, we identified the main smart grid application areas as energy trading, demand response management and electric vehicles. In this context, we reviewed more than 100 related research publications and aim to discuss the overview of SGs, BC, and ML, analyze and classify different approaches that model SG using BC and ML, and understand the existing research problems in this field. Our review specifically focuses on (1) SG security issues, (2) P2P energy trading, (3) EVs, (4) demand management using BC and ML, and (5) the interoperability of BC networks. There are studies that closely resemble our study ([
25,
32,
33]), which evaluates the state of the art. However, our aim is to identify the application of BC and ML in SGs and the benefits/challenges of applying both techniques together for smart grids. Our review helps the researchers to identify the BC, ML applications for SGs, existing research gaps and the need for further research to address those gaps.
The main contributions of this article include the following:
An introduction and tutorial for the concepts of smart grid, blockchain technology, machine learning and associated challenges.
Identifying the benefits and challenges of blockchain and machine learning techniques within smart grid application.
Investigating the combined integration of blockchain and machine learning in the context of smart grid.
Identifying the gaps in the research covering the integration of smart grids, blockchain and machine learning with a review of the existing works.
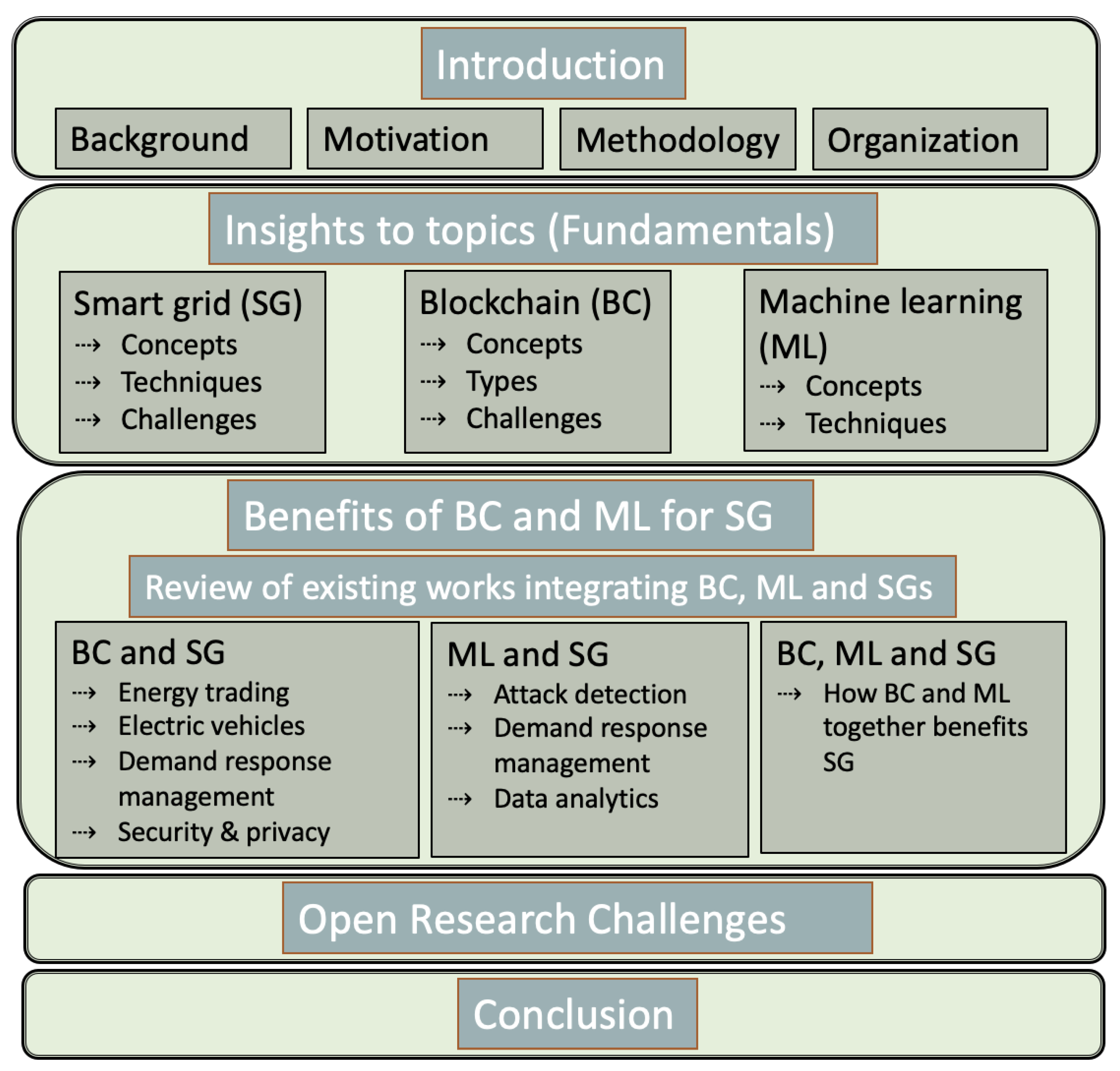
The outline of the survey is depicted in
Figure 2.
Section 2 deals with the necessary insights, terminologies and challenges of the topics involved i.e, SGs (
Section 2.1), BC (
Section 2.2) and ML (
Section 2.3).
Section 3 presents a review of works related to BC and SG,
Section 4 presents a review of works related to ML and SG, and
Section 5 presents a review of works that integrate BC, ML and SG. Further,
Section 6 discusses the identified open challenges. Finally, in
Section 7, the survey is concluded with a reflection of the observed gaps and findings.
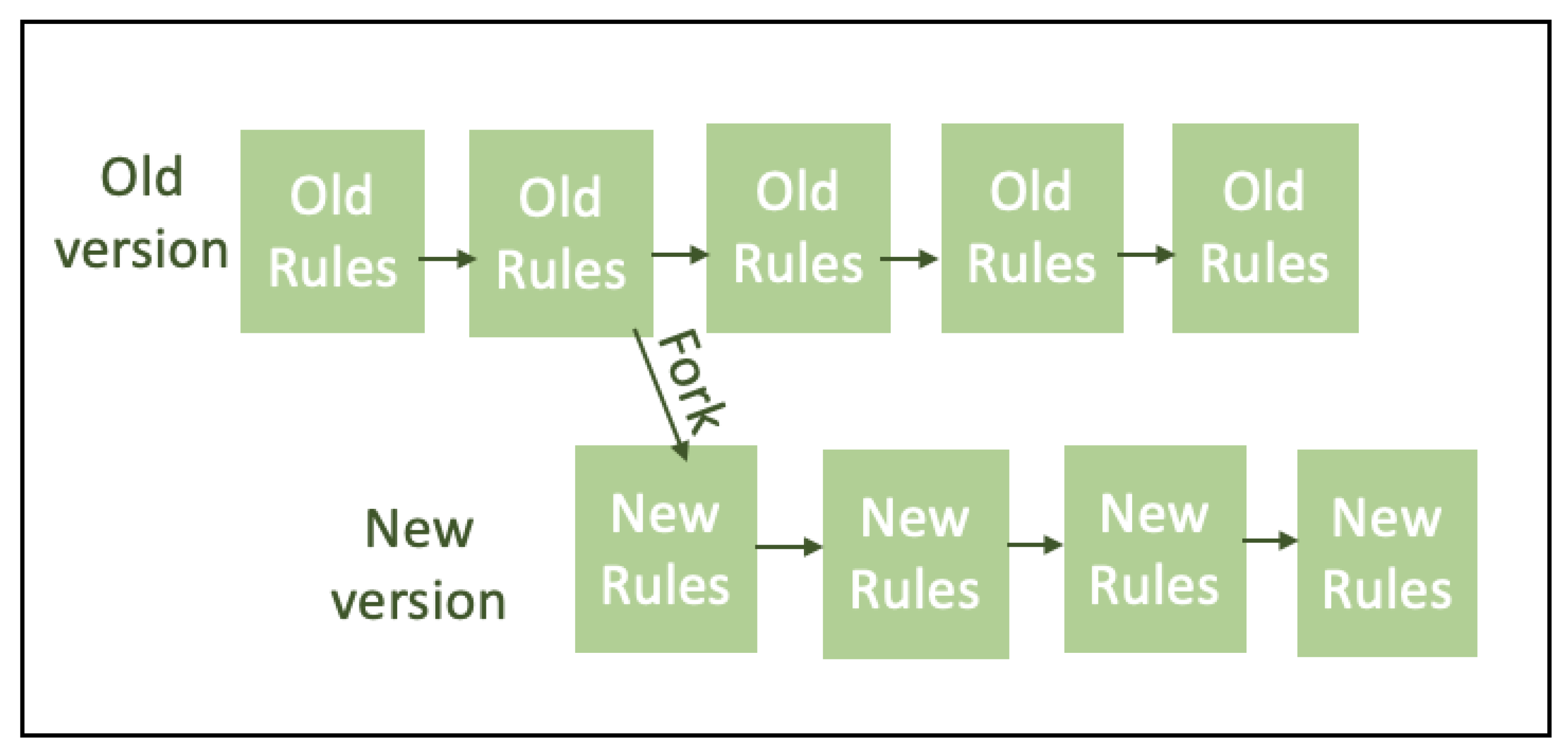
3. Review of Blockchain in Smart Grids
The use of BC technology in the energy sector is a key research topic nowadays. As the energy industry is undergoing tremendous transformations with the adoption of ICT, it has become a prominent research area. Intelligent grid implementation with minimal power loss, high power quality, reliability and security are the main goals to be attained. Many research works introduce BC technology in the energy sector for achieving these goals [
6,
18,
27,
28,
32]. However, more research is required. In this section, the main idea of SG and BC integration, its benefits and potential opportunities related to several existing works is discussed.
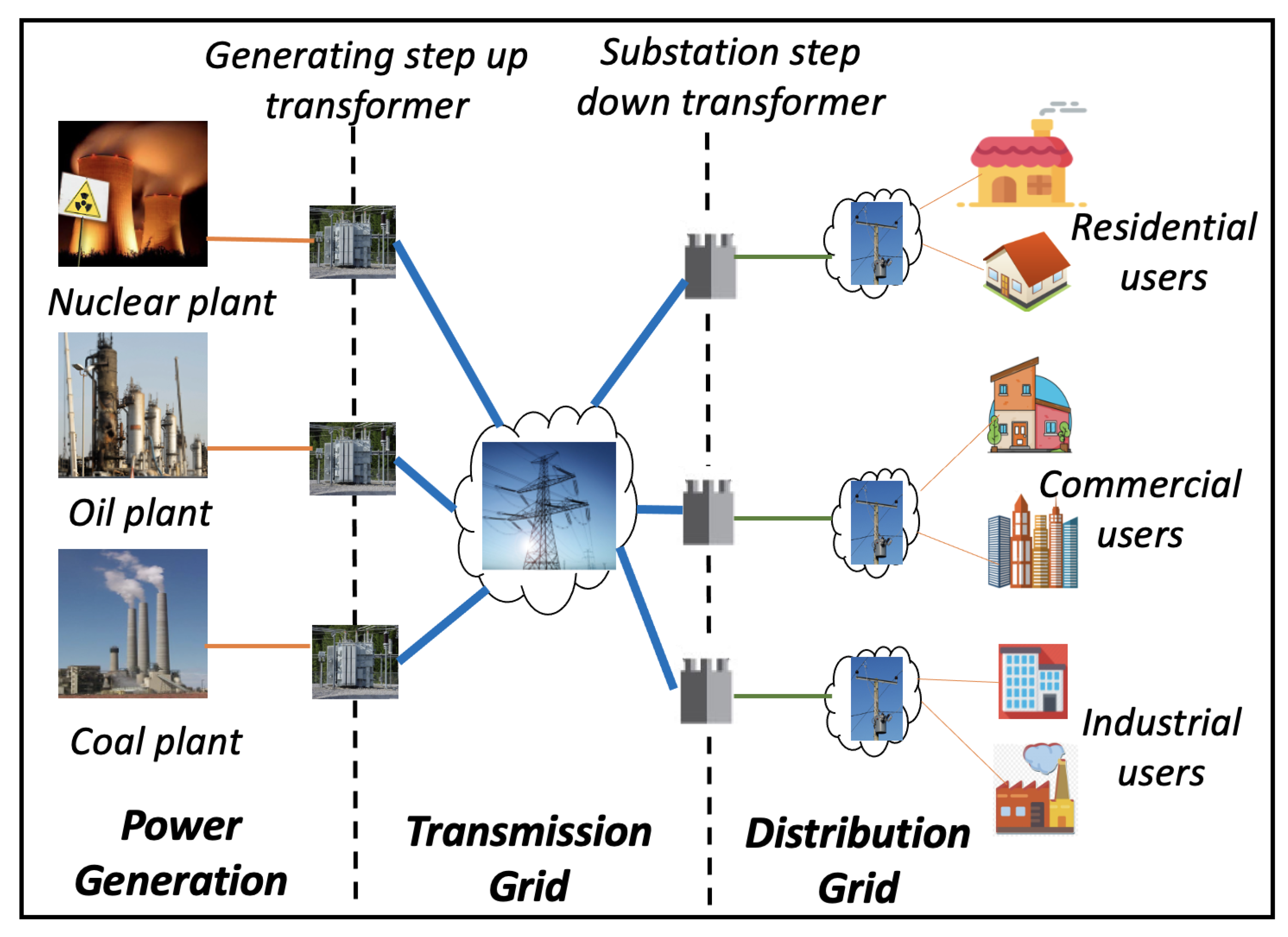
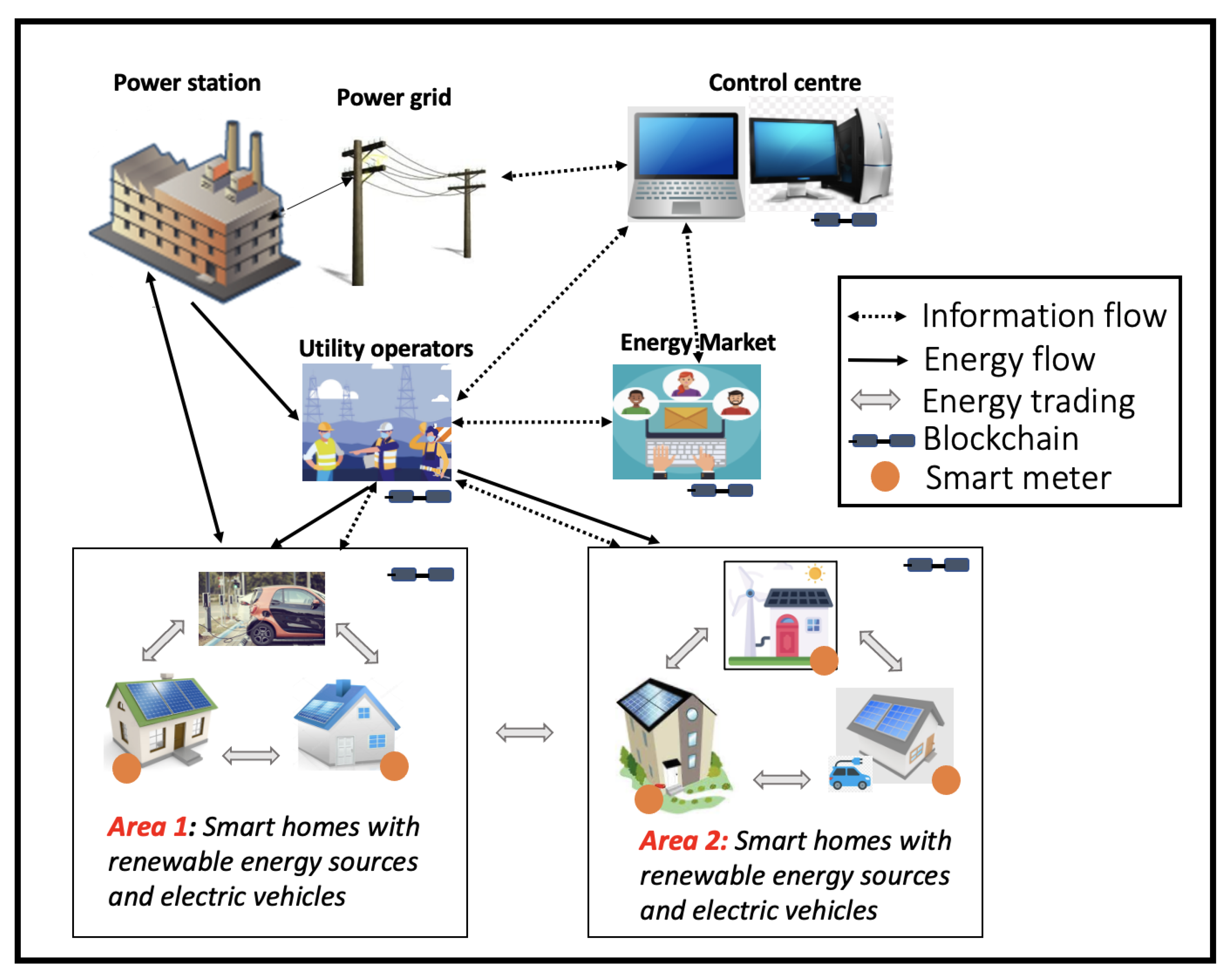
The distributed architecture of SG is depicted in
Figure 4. However, maintaining all these distributed functionalities by a single centralized server is complex and highly vulnerable [
6]. The ultimate aim of all the transformations in the grid is to reform the existing energy industry by bringing producers and consumers closer to each other using distributed generation and resources. In centralized systems, all the users, energy operators and market system interactions are dependent on central entities. These intermediaries can monitor, control and support all activities within the elements in the grid [
18]. Additionally, the long-distance transmission network is opted to deliver energy to end users through distribution stations. The increase in the number of elements associated with the grid raises some concerns [
27], which include scalability, reliability, availability, communication overhead and so on. All of these issues point toward the need for a decentralized structure for energy grids to create a more dynamic and flexible grid structure [
50].
Security, energy management, EV charging and energy trading are also some of the areas to be transformed and implemented effectively. As users are becoming prosumers through distributed generation, they can trade electrical energy to other grid users. Traditional methods fail to provide a secure and flexible energy trading platform [
44] where users can trust each other. Due to privacy and security concerns, most of the users show less interest in participating in energy trading. Hence, a decentralized platform which can create a trust environment for secure energy trading is required. Indeed, the penetration of EVs also has effects, as energy trading between EVs can also be done [
62]. EV users have concerns about charging their vehicle from anywhere because of security reasons. At the same time, the proper scheduling of EV charging is also necessary for balancing the entire grid, which is a problem to be addressed.
All these issues, mainly, the need for decentralization, security and in building the trust platform for trading without third party intervention, point toward the use of emerging BC technology [
63]. Applying BC technology in the energy sector has many potential benefits and can avoid most of the bottlenecks in the development of smart grid. Many studies and industry experts believe that BC adoption will eventually help for a smooth shift toward smart grid [
6,
18,
29,
63,
64].
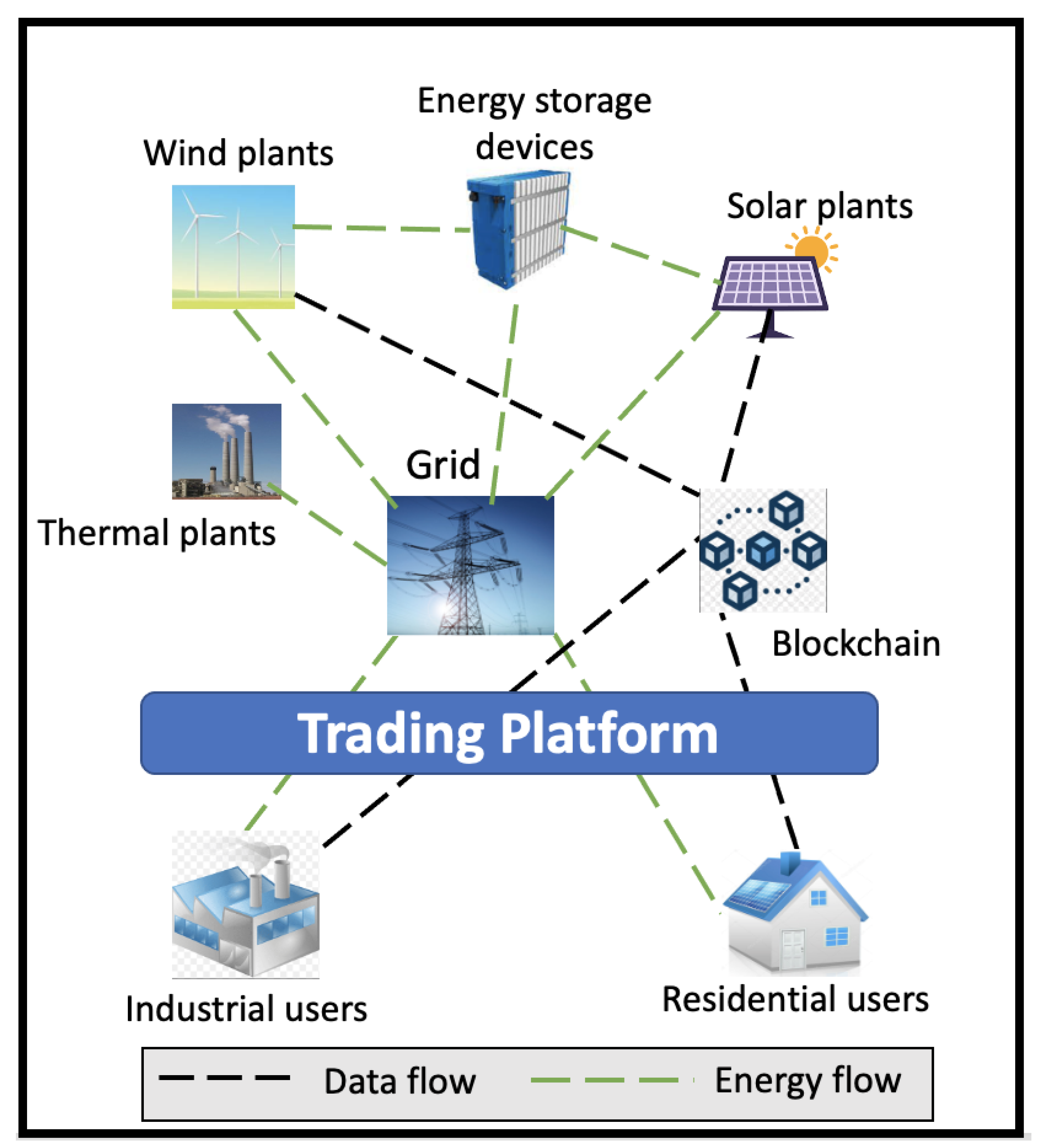
Figure 9 represents a model for blockchain-enabled future smart grid.
The main motivation of applying BC technology is to achieve an increased level of security [
65]. Since BC uses cryptographic techniques and a ledger is shared among all peer nodes, data alteration is not possible unless the majority of the nodes become malicious. As all the network nodes can verify the transactions and records, it adds transparency to the system. Due to secure hashing algorithms, any malicious activity or faults in the communication network are easily identifiable and recovered easily, which makes the system resilient to attacks. Above all, the most important benefit comes from the secure scripting using smart contracts, which can automate the transactions by automatically executing them when certain conditions are met. Thus, with all these critical features and cryptographic techniques, BC adoption promises to be a suitable alternative to traditional centralized systems with increased security, resilience, privacy and trust [
66].
The United States (US) is the first country in the world that has applied combined energy and blockchain to practical applications [
67]. Applied engineering projects combining energy and blockchain in the US are Brooklyn microgrid, Filament, Shared EV charging pile and Omega grid. There have been many other implementations made in several other countries, but research and advancements are still ongoing.
Table 4 lists some of the existing projects related to SG and BC.
Blockchain can be extensively used in most of the smart grid areas [
30]. Research results shows that many papers are coming up with blockchain-based proposals for energy trading, advanced metering infrastructure (AMI), the managing and charging of electric vehicles, demand response management, issue of green certificate, microgrids and information security. The authors in [
28] reviewed around 140 BC projects and start ups in the energy sector and classified each work based on BC use cases in energy sector according to the field of activity, blockchain platform used and consensus mechanism used. BC use cases in energy sector were classified into eight main groups according to the activity field: (1) metering/billing and security; (2) cryptocurrencies, tokens and investment; (3) decentralized energy trading; (4) green certificates and carbon trading; (5) grid management; (6) IoT, smart devices, automation and asset management; (7) electric e-mobility; and (8) general purpose initiatives and consortia. Their systematic study results based on activity field, platform used and consensus mechanism used shows that (1) in BC use-case classification according to the activity field, 33% was for decentralized energy trading, (2) in BC use-case classification according to the platform used, 50% was built on Ethereum, and (3) in BC use case classification according to the consensus algorithm used, 55% was based on the PoW algorithm.
In the following subsections, the use cases of blockchain in smart grids, mainly energy trading, electric vehicles, demand response management, security and privacy, are discussed using several references.
3.1. Energy Trading
Blockchain plays a very significant role in energy-trading applications. BC technology is most widely used in decentralized energy-trading application compared to all others [
28]. In
Figure 10, we show a model of energy trading using BC technology. The main reasons for BC adoption in energy trading are transformation from centralized to distributed resources, the need for a secure P2P trading platform among prosumers avoiding third parties, building trust and privacy in the trading platform and managing the needs of all grid users. Some of the existing BC-based energy trading works are summarized in
Table 5.
In [
77], a PriWatt system, a token-based energy trading system which uses a multi-signature technique, BC technology and anonymous messaging streams that provide security and privacy in decentralized energy trading, is introduced. They use the PoW consensus algorithm and elliptic curve digital signature algorithm (ECDSA) to validate transaction authenticity as in bitcoin. The main advantages of the PriWatt system are that it avoids single point failure, privacy and anonymity are preserved, and the use of authentication techniques. However lack of routing and message redundancy may lead to scalability issues. Ref. [
44] proposes a secure private blockchain (SPB) based solution for energy trading by building a routing method on top of BC using atomic-meta transactions and private authentication methods to verify smart meters. A lightweight consensus algorithm called distributed time-based consensus (DTC) is proposed to overcome the BC processing overhead, where each miner has to wait for a random time prior to mining a block rather than solving a complex cryptographic puzzle. A proof-of-concept (PoC) implementation of SPB [
44] on the Ethereum private blockchain to explain their applicability in energy trading is performed in ref. [
78]. They evaluate the performance of SPB by comparing with a baseline over 100 runs of the experiments using different metrics, mainly end-to-end delay, cost, throughput and size of BC. Results indicate that SPB gives better performance than the baseline compared with end-to end delay, monetary cost and transactions per minute. Ref. [
79] explains a secure energy trading platform using consortium BC and a credit-based payment scheme with optimal pricing strategy based on game theory for attaining faster transactions. The security analysis shows that the proposed energy blockchain achieves secure energy trading, and the numerical results illustrate that the energy blockchain and the credit-based payment scheme are effective and efficient for energy trading. In
Figure 11 we depict the credit-based payment scheme [
79] via a sequence diagram.
In [
80], EnergyChain, a BC-based model for secure data storage, access and energy trading in SG environment, is introduced. It includes two types of nodes, miner nodes and normal nodes. EnergyChain uses the PoW consensus algorithm, where the miner node solves the mathematical problem of nonce calculation and the winner reaps the rewards. They explain the security evaluation results with respect to the communication cost and computation time. Paper [
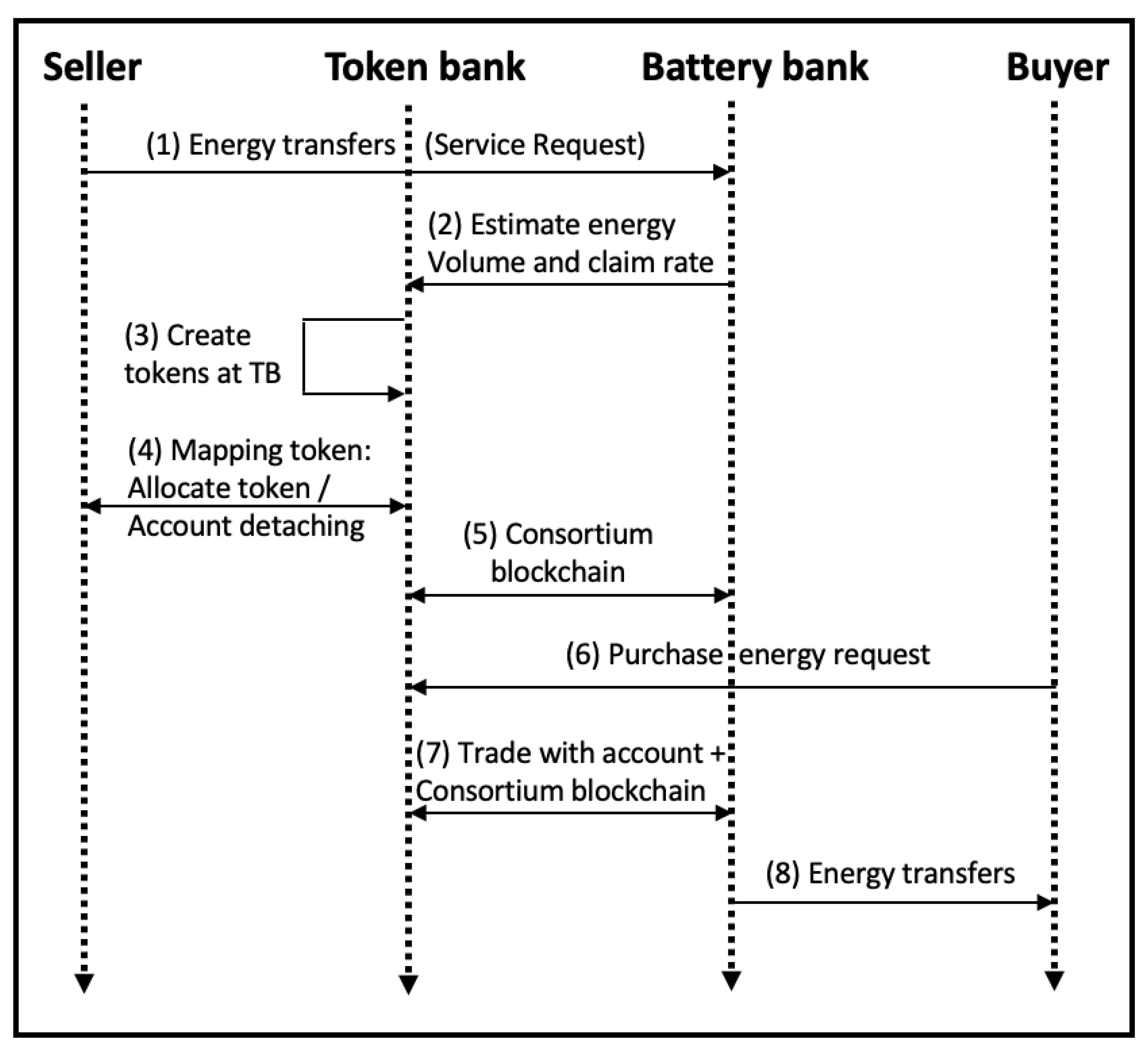
81] proposes a privacy preserving BC-enabled energy trading (PBT) model using consortium BC in the SG ecosystem. We depict the main steps proposed in the PBT model in
Figure 12. Their main operating principle is to create noises to prevent adversarial activities in the network. It uses account mapping techniques to avoid data mining and linkage attacks. A comparison with other differential mechanisms shows that PBT can effectively handle assumed attacks. Ref. [
82] explains a BC-based P2P energy trading framework using the Cipher text policy attribute-based encryption (CP-ABE) scheme for establishing P2P energy trading. It also introduces a redactable blockchain with chameleon hash, which allows users (data owners) to modify their personal information uploaded in blockchain. A simulation was conducted by constructing a private Ethereum chain and tested using PoW and PoA consensus algorithms. However, based on the results, they concluded that a more suitable consensus algorithm to ensure low latency has to be selected.
More works on BC-based energy trading are present.
Table 5 shows that the commonly used consensus algorithm is PoW, despite its computational power requirement. The PriWatt system in [
77] addresses the issues of transaction security as well as user privacy in trading environment; however, no detailed discussion about the miners in PoW and rewards given to them is given. To overcome the inefficiency of PoW, a distributed time-based consensus is proposed in [
44], and a PoC implementation and the results of the same logic are explained in [
78]. The credit-based payment scheme introduced in [
79] improves the delay in transaction confirmation occurring in bitcoin PoW, which allows nodes to obtain energy coin loans from credit banks to achieve faster payments. Still, they fail to provide a formal proof for the double-spending attacks and implementation details. Similarly, ref. [
80] explains an EnergyChain with a miner node selection algorithm and transaction handling scheme, but proper implementation details are not well-discussed; instead, they claim their superiority by comparison results. The noise-based differential privacy scheme proposed in [
81] protects user privacy by hiding data patterns to avoid data mining and linkage attacks. They use the consortium BC and PBFT algorithm and implementation is performed using hyperledger. Due to the decreased scalability and communication overhead of PBFT, it may not be suitable for large-scale applications. The redactable BC-based scheme in [
82] allows users to modify their sensitive information if needed, while the normal BC is immutable. However, this modification is secured by signature algorithms, and it may result in some malpractices as well. In some of these works [
77,
82,
83], smart contracts were used in trading applications. The review shows that the main problems to overcome are the scalability and latency issues. Privacy is also a concern for users participating in trading. Who can be miners in the network which is decided by consensus algorithms and the type of BC to use should be the main consideration in energy-trading applications.
3.2. Electric Vehicles
EVs play a significant role in the smart grid infrastructure and they also solve some of the environmental problems by facilitating green travel. However, EV users are facing challenge in charging, as the number of EVs are increasing while the number of available charging stations are decreased. Additionally, short communication ranges, the need for frequent communications and mobility of EVs add new security and privacy concerns [
84]. On the other hand, the high penetration of EVs and less-coordinated charging schedules might lead to overloading in the grid. Hence, there in an open challenge to integrate all these EVs in the grid, schedule the charging operations effectively and develop a transparent and secure charging system. Many researchers adopt decentralized BC technology to solve these issues and enhance the use of EVs and its charging management [
62,
85,
86,
87,
88,
89,
90,
91]. These works are summarized in
Table 6.
Ref. [
62] exploits consortium BC to develop a secure P2P energy trading system for EVs (PETCON). Electricity pricing and the amount of electricity traded are calculated using an iterative double auction mechanism for maximizing social welfare in electricity trading. Consortium BC ensures that only authorized nodes (LAGs) perform consensus process. The double auction mechanism allows users to negotiate the energy, bidding and transactions between EVs. Security analysis and numerical results show the defense ability of PETCON against many security attacks. Ref. [
85] explains a decentralized security model called lightning network and smart contracts (LNSC) to improve the security of transactions between EVs and charging stations. The model involves four phases, namely registration, scheduling, authentication, charging. The experimental results show that the model is capable of achieving increased security in energy trading between EVs and charging stations, and it can also incorporate scheduling mechanisms. However, the explained security goals are not much relevant when a BC-based system is considered. The authors in [
86] proposed an adaptive EV charging scheme in a decentralized BC-enabled smart grid system (AdBev) which minimizes power fluctuation level in grids and entire charging cost for EV users. To improve EV charging/discharging, an iceberg order execution algorithm is used. The Ethereum platform is used to deploy the AdBEV scheme and compare it with the benchmark GA algorithm. The simulation results show that the proposed system has less power fluctuation level (PFL) compared to the benchmark system. The computational cost is compared using gas values associated with running a contract in EVM, which is observed to be lesser for the AdBEV scheme compared to the benchmark algorithm as the number of nodes increases. However, the paper does not explain how user identity is verified. Ref. [
87] introduces an autonomous, transparent and privacy-preserved method that helps EVs to find the cheapest and nearest charging stations depending on the energy price and distance to the charging station. It can be seen that privacy is preserved, as none of the other participants can know the location of EV, none of the participants except the EV and selected charging stations know the purchased energy price, and involved EVs cannot be tracked. However, no detailed discussion about scalability (possibility of incorporating large number of EVs) and how BC handles payments is given. Ref. [
88] focuses on building a smart contract based permissioned BC to develop a secure charging framework for EVs integrating RES and smart grid in a smart community. A reputation-based delegated Byzantine fault tolerance (DBFT) consensus algorithm is introduced to achieve efficient and fast consensus in the permissioned system that allows only authorized EVs to participate in the verification process. However, no discussion about who performs transaction validation and who provides incentives for validators is given. Ref. [
89] proposes a secure charging system for electric vehicles based on BC and Hyperledger. They critically review the existing lightning network and smart contract (LNSC) method [
85] and demonstrate their security weakness and inefficiencies. The authors aim to propose an EV charging scheme which solves these security weaknesses and flaws. The performance of the proposed scheme was compared with different related works based on computation cost and communication cost. However, the explained security goals are not much relevant for a BC-based system. In [
90], a local V2V trading model based on consortium BC and fog computing is proposed, and the paper addresses the balancing problem due to charging/discharging interests of PHEVs. The paper improves the PBFT consensus algorithm by combining it with the DPoS algorithm to design an efficient consensus mechanism called DPOSP. The aim of such a consensus mechanism is to reduce the latency involved in verification and achieve faster transactions. Authors compare the proposed consensus algorithm with other mechanisms based on energy saving, fault tolerance, error node processing and block cycle. In future, they plan to design smart contract for processing transactions automatically. Ref. [
91] mainly focuses on preserving EV privacy by proposing a blockchain based differential privacy approach. Differential privacy on top of consensus energy management is used to secure the broadcast information. However, there is no clear discussion about how the authentication of EVs is performed and how verification is carried out. As future work, their idea is to explore neighboring energy trading where dynamic pricing is an issue for charging EVs and more security aspects to prevent privacy breach.
The rapid rise of EV remains as a threat to the grid, because the current grid structure is not capable of managing all the energy needs, which causes a grid imbalance. The proper scheduling of EV charging, accurate predictions based on charging data, etc., are critical. Above all, security is also a major concern. Even though there are many related works to solve these issues, optimally managing EV charging by maintaining the overall grid balance is still a problem being faced.
3.3. Demand Response Management
Several research works explore different techniques to develop an innovative DRM system with the adoption of BC technology. The main idea of most of the works was to develop a secure trading platform for distributed prosumers and EVs. Smart contracts which can execute upon reaching desired conditions gained great acceptance in the DR application [
92,
93,
94,
95,
96,
97,
98,
99]. Some of the works which aims to develop better DR prototypes are listed in
Table 7.
Ref. [
92] reviews the use of BC in DRM programs. They use BC for storing transactions in a tamper-proof manner and smart contracts to define expected energy levels and rules for balancing grid. The model is validated and tested using a prototype developed in the Ethereum BC platform based on U.K. buildings’ power consumption and production datasets. Their results shows that it is possible to adapt electricity demand in real time based on initiated DR events. However, a description on how anonymity in energy profiles is preserved is not present. Ref. [
93] compares the traditional energy trading system (TETS) which relies on centralized system with a secure energy trading system (SETS) which uses blockchain technology. In SETS, all local prosumers are connected in a local/microgrid for becoming a node, and payments are made using Etcoins, which are purchased from the BC controller. Performance is evaluated using computational cost and computational time paradigms. However, the paper does not explain the consensus mechanisms used, how prosumer/consumer verification is done, and more security issues of the system. Ref. [
94] explains an algorithm for energy trading and demand response management in SGs using BC technology with an algorithm for miner node selection. Security aspects for the system are also evaluated. However, their results depict higher throughput and lower consumption time for one of the selected datasets. The authors claim that it is because the concerned dataset is structured as compared to the other. Thus, in their future, the main aim is to test the proposed scheme using bigger datasets. Inspired from the works in [
94,
101], the authors in [
95] propose a secure energy trading model using BC, a contract-based incentive mechanism for load balancing, and route optimization algorithm to reduce the EV traveling time. They use a PoW based on reputation (PoWR) consensus for energy trading to meet the time complexity of the BC-based system. Ref. [
96] presents a decentralized cooperative DR framework to manage daily energy exchanges in a smart community which adopts RES. It provides flexibility to users to decide on their day-ahead power profile and ensures the efficient tracking of the next day requirements. The simulation results show that under a special tariff structure, the peak demand can be reduced. Scalability analysis shows that it is applicable up to a group of 100 smart buildings. However, details about prediction accuracy and security aspects are not explained. Ref. [
97] presents an energy scheduling mechanism among multiple microgrids (MGs) and EVs integrated with MGs. An incentive-based contribution index is introduced which gives priority to prosumers with high production points. However, they fail to explain how the verification of bids is performed. Ref. [
99] addresses the problems in microgrid design using BC technology for providing a real time demand response while considering the economic, environmental and social goals. However, their prototype using smart contracts is similar to the self enforcing smart contracts idea for demand response explained in [
92]. A fully decentralized and cost effective optimal power flow (OPF) based DRM solution for smart grids is proposed in [
100]. The implementation of the OPF model in a private blockchain using smart contracts is explained in detail. Their execution cost results indicate that the proposed scheme provides a much cheaper execution for a complex problem. Ref. [
98] proposes a BC-based transactive energy (TE) P2P trading platform and distributed auction mechanisms will make all the peers capable of becoming an auctioneer. The main concentration of the system is on social welfare, where all implementations (TE auction model and DR) aim to improve the overall living standard.
Most of the works try to apply demand response by implementing secure P2P trading between prosumers, EVs and using self-executing smart contracts. However, developing a completely decentralized grid structure with DRM programs is still a topic of research. Developing accurate day-to-day prediction for energy generation based on energy consumption data and managing the overall balance securely with proper scheduling techniques is challenging.
3.4. Security and Privacy
Smart meters placed at each home in a smart grid provide real-time information about electricity consumption and pricing. This information may contain aspects about users which are private and thus require mechanisms to preserve privacy. If a malicious attacker gains access to this data, they can track the energy usage behavior of users based on their consumption profile. The major concern for every user or entity in the SG environment is privacy, and the associated security of such information exchange [
65]. Most of the works discussed in previous sections (
Section 3.1,
Section 3.2 and
Section 3.3) aim to provide security and privacy in smart grid operations using BC technology. Similarly, security of power information system is also an important area of research. SG incorporates several communications for proper functioning and power delivery, and this information has to be stored securely. If the system is hacked, it may impact the grid and create unpredictable effects in the grid, leading grid operators toward making wrong energy decisions, eventually resulting in interruptions or even large-scale blackouts. Providing security for all parts of the SG is critical. The use of BC alone does not directly guarantee security and privacy; however, adding advanced cryptographic mechanisms such as multi-signatures, elliptic curve cryptography, etc., are also needed.
3.5. Research Challenges and Solutions in Integration of Blockchain and Smart Grids
So far, a complete review of SGs, BC, their overview and individual challenges was given. Additionally, the advantages and applications by combining BC technology with SG were discussed in detail. However, as an emerging concept, BC-based solutions for future SG are facing challenges in their complete incorporation. Some of the challenges are related to SGs (
Section 2.1.2) and some are BC-specific (
Section 2.2.5). In this section, the challenges faced while moving toward a decentralized SG using BC and possible solutions will be discussed.
Inefficiencies of consensus mechanisms: Consensus mechanisms are an integral part of a BC system, as they help to decide who can verify and add blocks. These mechanism determine most of the performance characteristics of the involved BC system, such as scalability, fault tolerance, throughput and overall security. PoW is the widely accepted consensus mechanism which is adopted in bitcoin, but high computational power makes it unsuitable for energy applications. From the review of related works, it is understood that PoW and its modifications are widely used by researchers in energy sectors. In [
44], a distributed time-based consensus is proposed, which modifies the PoW computational puzzle solving to a random waiting time for reducing the processing overhead. In [
95], a reputation-based PoW is introduced that assigns a positive reputation to honest nodes and negative reputation to malicious nodes. The PBFT mechanism is also used in some works ([
81,
89]); however, less scalability and communication overhead make it unsuitable for large-scale applications. A modified PBFT version, DBFT, which is a reputation-based delegated Byzantine fault tolerance, was introduced in [
88] for attaining faster consensus in permissioned BCs. PBFT and DPoS was combined in [
90] to develop the DPOSP consensus mechanism that aims to reduce transaction latency. PoA, which allows only authorized entities to participate in network consensus is used by energy web foundation [
51] that achieves confirmation time in 3–4 s. As the consensus mechanism is important while developing a BC-based application, many researchers are working on modifying existing algorithms or implementing new ideas of consensus for achieving high scalability and high transaction speed with minimal energy consumption. Developing such mechanisms will be challenging, and this has great research interest.
Smart contracts designing: As discussed, smart contracts are pieces of code that execute by themselves when certain conditions are met. However, these may be vulnerable to malicious attacks since they are built on programming codes. The designing of a smart contract for a critical application should be done with the utmost care. Small bugs or programming errors open it to several malicious activities [
102]. For example, in 2016, around 3.6M ether was stolen from a decentralized autonomous organization (DAO) by taking advantage of the inefficiencies in the smart contract. Here, an attacker uses an empty malicious contract that contains a fallback function, and with successive recursive calls, they can empty the complete balance in the DAOs account. This occurs mainly due to the programming methods used by DAO, and making modifications in call functions may help to avoid such errors. Hence, it is clear that the designing of smart contracts plays an important role if it is used for the decentralized applications.
Chances of centralization: In an energy application, the number of users is very high. If a public BC structure is used, many users will be involved in the consensus process at the same time. As the number of node increases, the efficiency of the system decreases, which in turn increases the response time. However, by using a permissioned BC structure, the number of nodes and participants can be limited to authorized users. From the review of related works, it is understood that in most of the BC-enabled SG cases, a private or consortium BC is used rather than public BC. However, this results in a semi-centralized structure, as there are certain authorized nodes that decide about the network, thus moving toward a complete decentralized highly scalable system.
Deployment and operational costs: Implementation of BC based system requires high infrastructural costs since it requires re-architecting the current grid network, upgrading smart meters, developing the ICT infrastructure and other related advanced metering interfaces [
30].
Legal and regulatory support: As of now, there are a large number of technical solutions developed for the BC-based SG system. However, wide acceptance from the legal and regulatory bodies is missing and are lacking supporting standards. These regulatory bodies do support user participation in energy markets and community energy structures, but energy trading between prosumers and consumers using distributed ledgers is not widely supported [
30]. The integration of smart meters, EVs, and other IoT devices is possible; however, interoperability between them is lacking [
18]. Before moving toward a complete decentralized grid structure without a trusted central authority, new standardization rules are essential to avoid disputes.
5. Integration of Blockchain and Machine Learning for Smart Grids
Combining BC and ML for various applications is increasing. The learning capabilities of machine learning can be applied with blockchain to make the chain smarter [
105]. Additionally, the computational power for ML models can minimize the time taken for the nonce calculation. On the other hand, using the decentralized data architecture of blockchain, better ML models can be built. The main benefits of combining BC and ML are (a) security, (b) improving energy consumption, (c) improving the smart contracts, (d) data trading and more. BC is a continuously growing data ledger, whereas ML requires large volumes of data. Both techniques complement each other and have high potential when combined for different applications.
With the decentralized and immutable structure, BC builds a trust environment without third parties for any transactions occurring. ML-based solutions mainly help in demand management using prediction techniques and help in handling large amount of data from smart meters [
33]. Additionally, optimization techniques can be used for scheduling the energy usage of users. Applying BC into ML systems helps such systems to use information collected by BCs to clear problems quickly, and applying ML techniques to BC adds powerful intelligence to BC systems for data processing and other intensive applications [
24]. The storing of large-scale data in a secure and tamper-proof manner by BC-based systems ensures the confidentiality and auditability of the collaborative data training process and trained model using cryptographic techniques. Additionally, it enables decentralization that ensure access control with central authorities. Smart contracts and Dapps allow to model interactions between entities in the decentralized ML application. In the same way, adding ML helps the BC system to achieve energy efficiency, scalability, security and intelligent smart contracts. As ML can predict and speedily calculate data, it provides a feasible way for miners in selecting important transactions. Using predictive analysis can ensure energy and resource requirements to be met and improve overall efficiency. Hence, considering the future SG scenario, both BC and ML can together solve the issues regarding energy trading, EV charging and scheduling, load prediction, DRM, security and privacy concerns.
Table 9 summarizes the existing works that combine BC, ML and SGs.
In [
25], the authors evaluate the integration of BC, artificial intelligence (AI) and SGs for developing a decentralized EV-charging infrastructure. In their view, the main challenges faced by an EV are vulnerable charging stations and non-optimal charging schedules. In the context of EV charging, AI adds solutions to implement optimal charging schemes based on the drivers’ charging behavior, and BC can solve security and privacy issues in the charging infrastructure. Their main idea is to combine both and attain the best of both technologies to develop a decentralized EV-charging infrastructure. They also discuss several future research directions of this integration.
Ref. [
106] explains an advanced decentralized electricity trading framework (DETF) for connected EVs (CEVs) and parking lots using consortium BC, game theory and ML. They implement a smart contract based auction model and HLcoin (Happy Light coin) using hyperledger for trading electricity. A smart contract is made between all stakeholders and deployed in BC. CEV sellers will submit the amount of energy to be sold out, and other CEV bidders will submit their bids. The smart contract runs an auction model to determine the winner and amount. The selected bidder is awarded electricity and the seller receives the corresponding HLcoin. Their algorithm HLProfitX was compared with PETCON [
62], and the results show that their method outperforms it. In the future, they aim to extend the work by adding RES and a microgrid architecture.
Ref. [
107] proposes DeepCoin, a deep learning (DL) and BC-based framework for protecting SGs from cyber attacks. The proposed framework is composed of a BC-based system and a DL-based system. It consists of four entities: energy buyer, energy vendor, BC and intrusion-detection system (IDS). The BC-based system provides a secure environment for the energy system and the DL-based scheme detects network attacks and fraud transactions. The DeepCoin framework uses the PBFT consensus algorithm in the BC system and recurrent neural networks (RNN) in the DL system. The performance was evaluated using three different datasets, and the efficiency of the framework was discussed. For the future study, their aim is to add edge computing to the DeepCoin framework and study the performance in SG.
Ref. [
108] explains a P2P trading mechanism based on BC and ML for sustainable power supply in SGs. It contains two modules: a BC-based energy trading module with real-time energy consumption monitoring, energy trading, reward model, and a smart contract enabled predictive analysis module for building a prediction model using energy consumption data. Predictive analysis is implemented using deep learning approaches based on recurrent neural networks and Hyperledger fabric is used for building the P2P trading platform with the PBFT consensus algorithm. Their results show that the proposed method is better in terms of latency and throughput. However, discovering hidden patterns from data using predictive model is difficult. In the future, they plan to consider more features for the optimization algorithm.
In [
110], an efficient energy trading approach using machine learning and blockchain is explained. The K-nearest neighbor (KNN) ML algorithm is used to calculate the distance between the EV and charging station. Energy brokers/aggregators find the nearest charging station for EV when an energy request is received and calculate the amount of time required for EV charging. All the communications between EVs and charging station are secured using the blockchain-based proposed authentication process. Smart contract maintains the secure energy trading, and the transaction cost is calculated from the used gas price. In the future, their aim is to compare the proposed method with other charging schemes and implement real time models.
These works show that combining BC and ML techniques provides benefits in the development of SGs. The main concern is whether these solutions help in building a fully fledged SG infrastructure that satisfies the need for secure P2P trading, managing balance in the grid by proper scheduled energy usage and EV charging. From the previous sections, the applications offered by BC and ML individually become clear, although with certain limitations. These combined can offer benefits to each other and to the overall system. For example, BC technology can benefit ML techniques for data and model sharing, security and privacy, decentralized intelligence and trustful decision making [
24]. Similarly, ML techniques can also benefit BC technology, i.e., it can optimize energy and resource efficiency, optimize scalability, improve security and privacy and develop intelligent smart contracts [
26]. As research on integrating BC and ML is in progress, there are some open issues and challenges to be addressed.
7. Conclusions
Smart grid (SG) is a vast interconnected system with many new emerging technologies. Several features of SG include communications, demand response, microgrid, the integration of RES, security and EVs. However, achieving the full benefits of SG still remains a challenge. Major challenges faced are the integration of RES, data management, cyber security, energy balancing and stability. There is no reasonable solution found; however, several research approaches are under investigation. Additionally, the solution to many technical, security and socio-economical issues have to be found for the better realization of the smart grid. The advancements in blockchain (BC) and machine learning (ML) add benefits to the electricity grid for building an improved grid architecture. Hence, in this review, the potential of BC technology in SG, ML applications in SG and applications of BC and ML integration in SG is investigated. Some of the relevant research in the field of BC, ML and SGs is critically reviewed, and challenges as well as open issues are identified. As discovered, BC provides several solutions to SG in the field of energy trading, EVs and DRM by providing security and privacy. However, the scalability issues of BC, energy consumption and stability of the grid were not well addressed in most of them. For example, an EV charging system should be secure and capable of building a trustful environment for EV users with proper scheduling techniques by managing the variations in the power grid. Such a system requires both BC technology and ML techniques. To the best of our knowledge, this is the first review article that combines BC and ML techniques in the context of energy applications.
BC solutions create a trust environment by building decentralized secure networks. ML techniques provide increased insight in the operation of SG which helps in better prediction and scheduling. This is done by finding patterns from large amount of data, which is challenging. Additionally, the involved computational power and scalability of networks have to be addressed. Hence, after this review, we conclude that for integrating BC solutions and ML techniques to develop secure and stable SG architecture, there remain certain challenges to overcome. The requirements for building a secure and stable SG architecture is not yet clearly understood and careful study has to be conducted in both BC and ML fields. Specifically, areas that need further research are as follows: (1) developing a consensus mechanism that can reduce energy consumption and latency while maintaining security; (2) developing electricity prediction models from large amount of real-time or non-real-time consumption data patterns, thereby balancing the grid using self-executing smart contracts; (3) developing a universal charging and scheduling system specifically for EVs; (4) microgrids design—including prosumers in residential homes, buildings, and EVs; and (5) the interoperability of blockchain platforms.