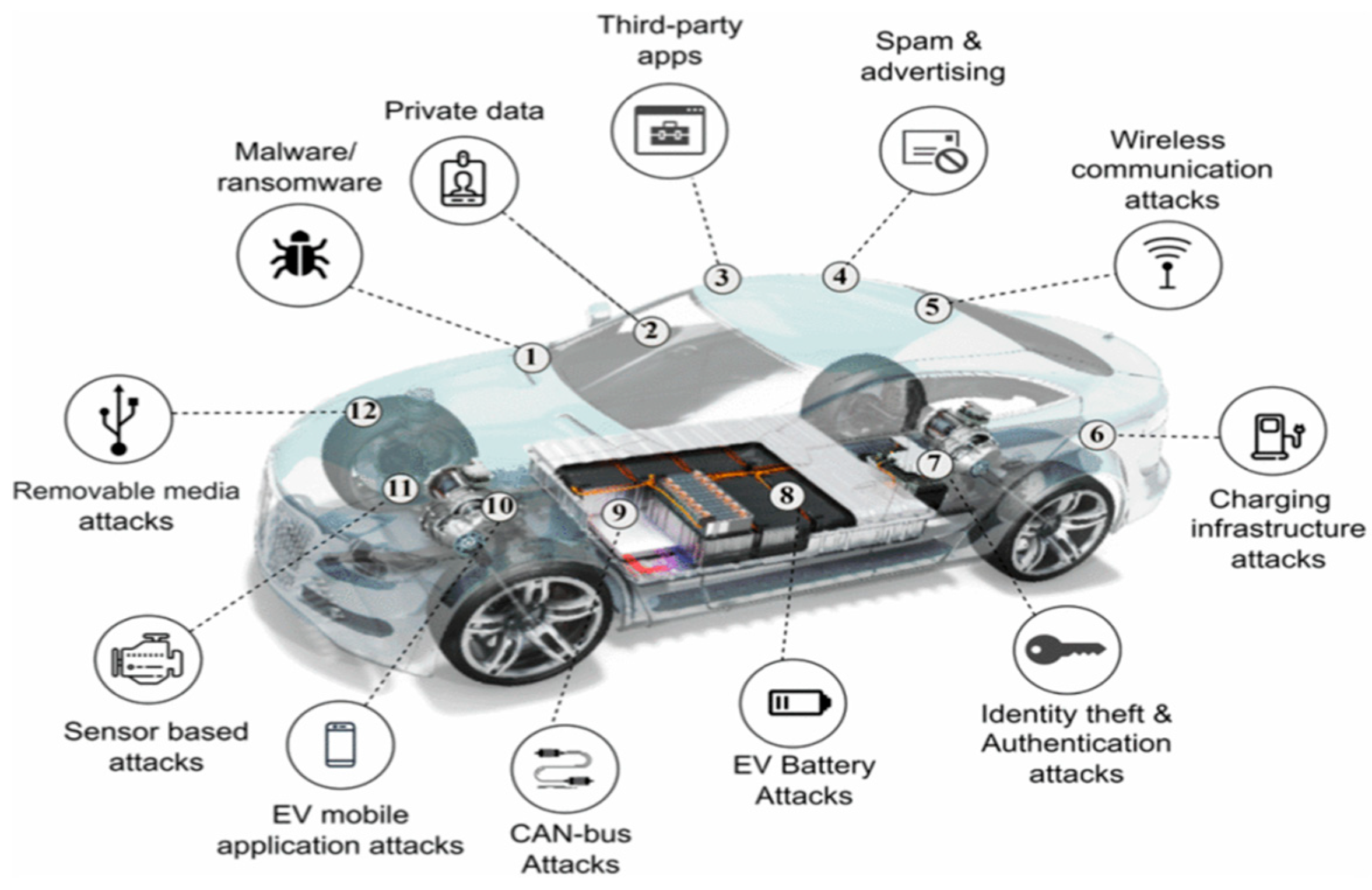
1. Introduction
The world needs to quickly switch to electric vehicles (EVs) in order to switch to sustainable energy. Electric vehicles (EVs) could make up as much as 30% of the car fleet by 2030, which would put a lot of stress on the current charging infrastructure [
1]. Multi-station EV charging networks face a number of challenges, such as cybersecurity threats, uneven load distribution, and the need for quick responses, especially when they are connected to smart grids. Electric vehicle charging stations often use traditional static control systems that are not very efficient and don’t adapt well to changing conditions. The Open Charge Point Protocol (OCPP) and other protocols have problems that make these systems very vulnerable to cyberattacks, such as spoofing, command injection, and unauthorized access [
2,
3,
4].
A lot of research has been done on how safe and effective electric vehicle charging infrastructure is. Centralized management systems and rule-based load distribution are examples of traditional solutions that do not always work well for scaling up and responding quickly to changing load demands and cyber threats [
5,
6]. At the same time, proposed solutions to cybersecurity issues related to OCPP have come up. However, many of these solutions only deal with security issues and do not include energy management features [
7,
8]. Artificial intelligence (AI) has surfaced as a potential solution to these constraints by facilitating intelligent, autonomous decision-making. AI methods like anomaly detection, reinforcement learning, and predictive analytics have been used in smart grid settings to make operations more efficient and make cybersecurity more resilient [
9,
10,
11]. This project seeks to enhance the safety and efficiency of electric vehicle charging networks featuring numerous stations by implementing an innovative AI-driven design that complies with OCPP standards. Previous solutions have dealt with problems with load distribution and security separately. Our system, on the other hand, combines AI-driven predictive modeling with a multi-tiered cybersecurity framework. The architecture adapts to different energy needs while also finding and fixing different cybersecurity threats, as shown in
Figure 1 and
Table 1.
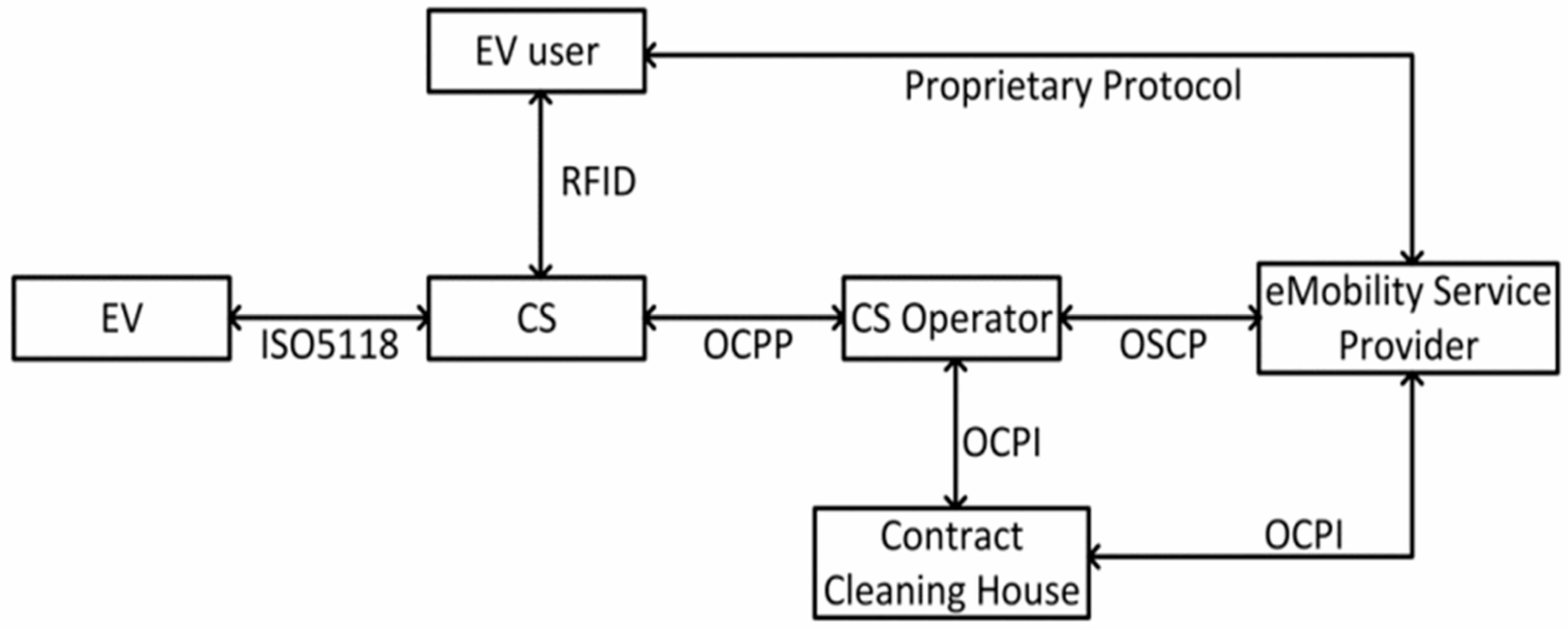
Figure 2 shows how the communication architecture and protocol flow work in the ecosystem of the electric vehicle (EV) charging infrastructure. The main parts are the electric vehicle (EV), charging station (CS), EV user, charging station operator (CS Operator), eMobility service provider, and contract clearing house.
Table 2 shows the different types of communication protocols and what they do in the EV charging ecosystem.
The main results of this research are as follows: (i) an AI-based algorithm for load balancing that works with electric vehicle charging networks spanning multiple stations; (ii) a robust cybersecurity framework compliant with OCPP standards; and (iii) an evaluation demonstrating improved operational efficiency and enhanced security resilience.
The paper is organized as follows:
Section 2 reviews relevant literature on the application of artificial intelligence in smart grids, cybersecurity, and EV charging load management.
Section 3 details the proposed AI-powered framework.
Section 4 reports the results of the performance evaluation.
Section 5 presents a discussion comparing our findings with existing studies and interpreting their implications. Finally,
Section 6 concludes the paper and proposes directions for future research.
2. Literature Review
The fast rise in the number of people using electric vehicles (EVs) has led to a lot of research into how to make EV charging infrastructure better and safer [
21]. Traditional charging methods often lead to poor load distribution and grid stress during peak hours, which means that better energy management solutions are needed. To help with grid overload, different load balancing methods have been suggested, like demand response (DR) programs and time-of-use pricing. However, these methods usually do not work well in real time or across multiple charging stations.
To get around these problems, people have been using artificial intelligence (AI) more and more. Reinforcement learning, neural networks, and predictive modeling are all types of machine learning that have been shown to be useful for predicting demand and dynamically allocating charging resources [
8]. For example, predictive models can guess when users will arrive and how long they will need to charge, which makes scheduling more flexible. But a lot of these methods focus on single charging stations instead of coordinated environments with multiple stations.
Cybersecurity issues in EV infrastructure have also gotten a lot of attention because of the use of Internet of Things (IoT) devices and communication protocols, which put charging networks at risk of data breaches, unauthorized access, and protocol-specific vulnerabilities [
22]. New solutions that use blockchain and edge computing try to improve data integrity and access control, but they often put security first, which hurts computational efficiency, and they rarely work on load optimization at the same time.
New hybrid frameworks that combine AI with secure communication and blockchain technologies have tried to solve these problems by managing energy distribution, user demand, and cybersecurity at the same time [
23]. However, there are still not many full solutions that allow for smart, real-time load management while keeping security across multi-station networks from start to finish. Notably proposes a dynamic load balancing approach using AI; however, it lacks integration with OCPP-compliant security mechanisms [
23].
Table 3 summarizes the most important contributions and gaps found in previous research. It shows that there are no integrated frameworks that fully address both load management and cybersecurity in multi-station EV charging networks.
This paper fills an important research gap by suggesting an AI-driven, OCPP-compliant framework that combines smart load balancing with a multi-layered cybersecurity defense. Our approach differs from earlier efforts by offering a cohesive system that can adapt to changing energy needs in real time while also proactively reducing a wide range of cybersecurity risks. This improves both the efficiency of EV charging networks and their ability to withstand security threats.
3. System Architecture and Methodology
The proposed AI-driven framework is meant to be used in Malaysia’s growing EV infrastructure, which is currently having problems with uneven station distribution and increasing cybersecurity risks. The system works well with existing charging networks by using standardized protocols like OCPP 2.0.1, which is protected by Transport Layer Security (TLS). This lets for safe real-time communication and dynamic load management. Validation is done through detailed simulations that use Malaysian data to create multi-station networks with load profiles and attack scenarios. The AI intrusion detection system (AIDS) is trained and tested on labeled OCPP communication datasets, and its ability to find threats is measured by metrics like precision, recall, and F1-score. The effectiveness of load balancing is evaluated by analyzing network utilization, service quality, and response time in varying demand scenarios, thereby validating the framework’s practicality and resilience in real-world applications.
The Real-Time Analytics Engine (RAE) keeps track of, records, and shows important grid and security metrics.
Figure 3 shows the centralized AI-powered power distribution and security architecture.
Transport Layer Security (TLS) is added to the OCPP 2.0.1 protocol layer, which all modules use to communicate over encrypted sockets. Prior to analysis, data packets are processed and filtered using AI feature selection. Utilizing deep Q-learning, the SLB optimizes load throughout the network by tracking both historical and real-time data (such as current draw, EV priority class, and station occupancy). To distinguish between benign and malevolent activity, the IDS module employs ensemble learning that combines decision trees, SVMs, and deep autoencoders. Precision-recall curves are used to assess models after they have been trained on labeled OCPP datasets [
22]. For administrators, this module manages dashboards, reporting, and the visualization of anomalous trends [
38].
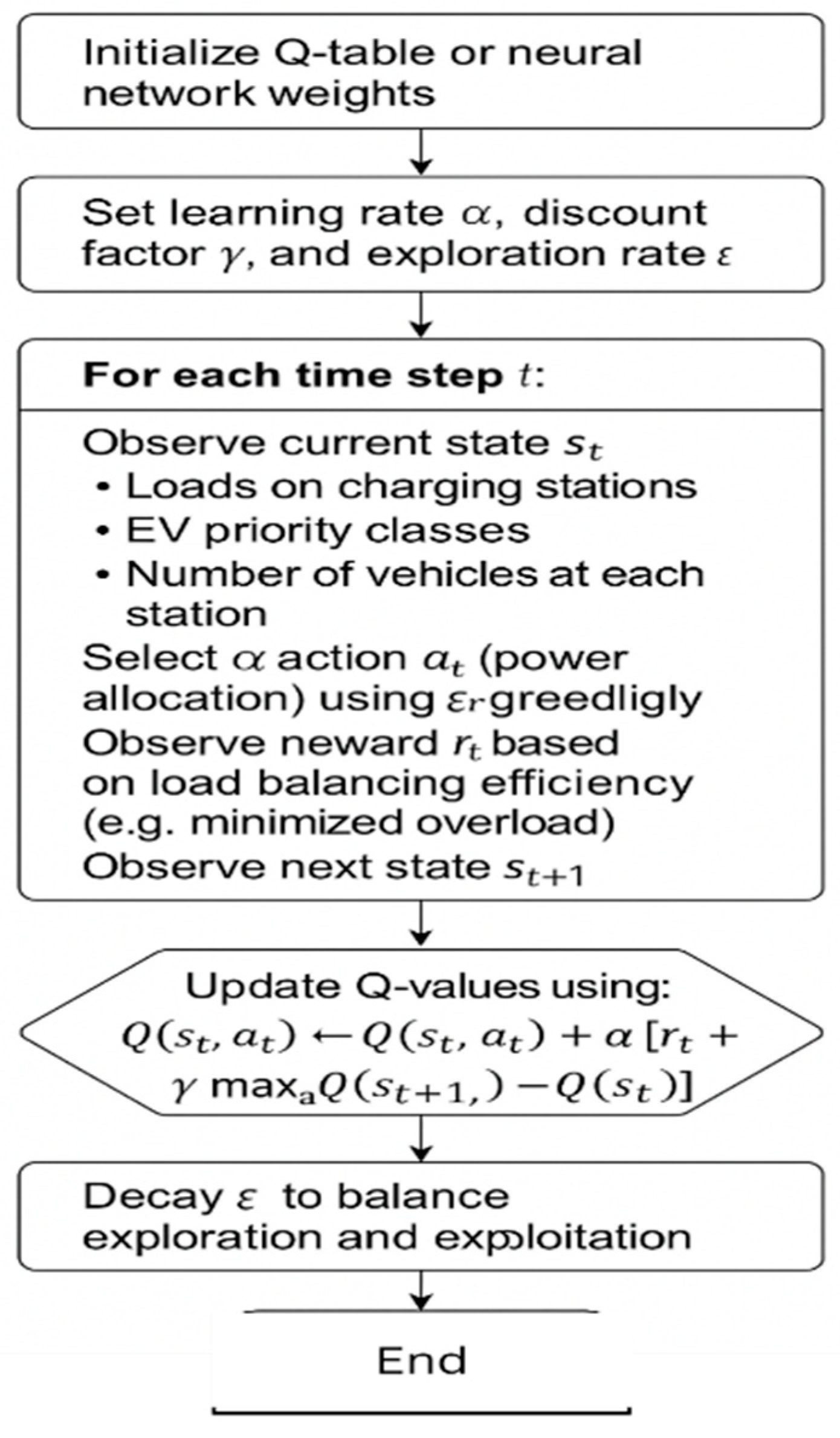
The Smart Load Balancer (SLB) Pseudo-Code flowchart is shown in
Figure 4, and the AI intrusion detection system (AIDS) pseudo-code flowchart is shown in
Figure 5.
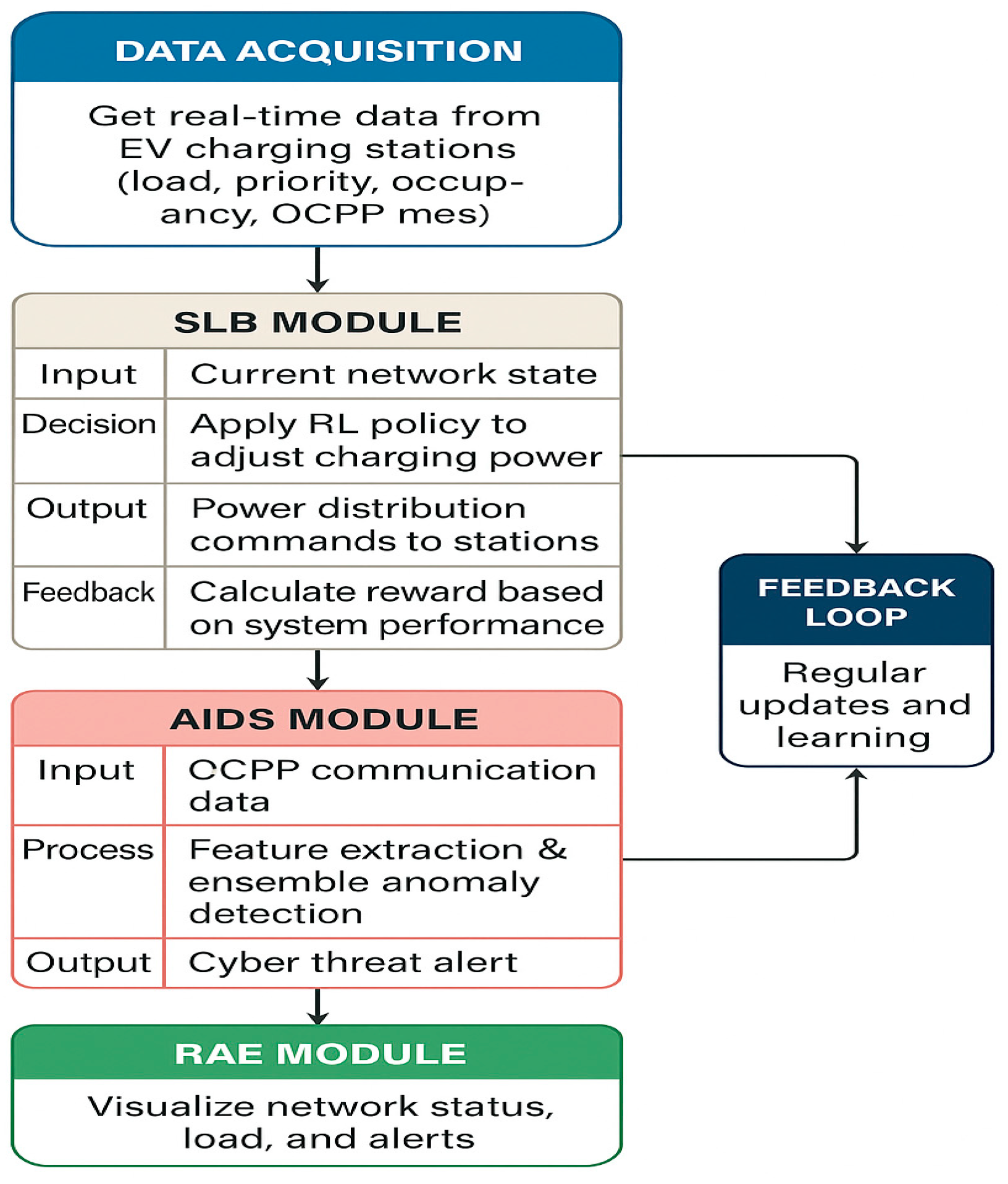
Figure 5 depicts the overall architecture of the AI-powered EV charging management system. It begins with real-time data acquisition from EV charging stations, capturing load, priority, occupancy, and OCPP communication messages. The Smart Load Balancer (SLB) module dynamically allocates charging power based on reinforcement learning policies and system feedback to optimize load distribution. Concurrently, the AI intrusion detection system (AIDS) monitors OCPP data to detect cybersecurity threats through ensemble anomaly detection techniques. The Real-Time Analytics Engine (RAE) visualizes network status, load levels, and security alerts for operators. A continuous feedback loop ensures adaptive learning and real-time system updates, maintaining operational efficiency and security resilience.
Figure 6 illustrates the integrated AI-driven system for electric vehicle (EV) charging management, including the Smart Load Balancer (SLB), AI intrusion detection system (AIDS), Real-Time Analytics Engine (RAE), and continuous feedback loop for adaptive control and cybersecurity.
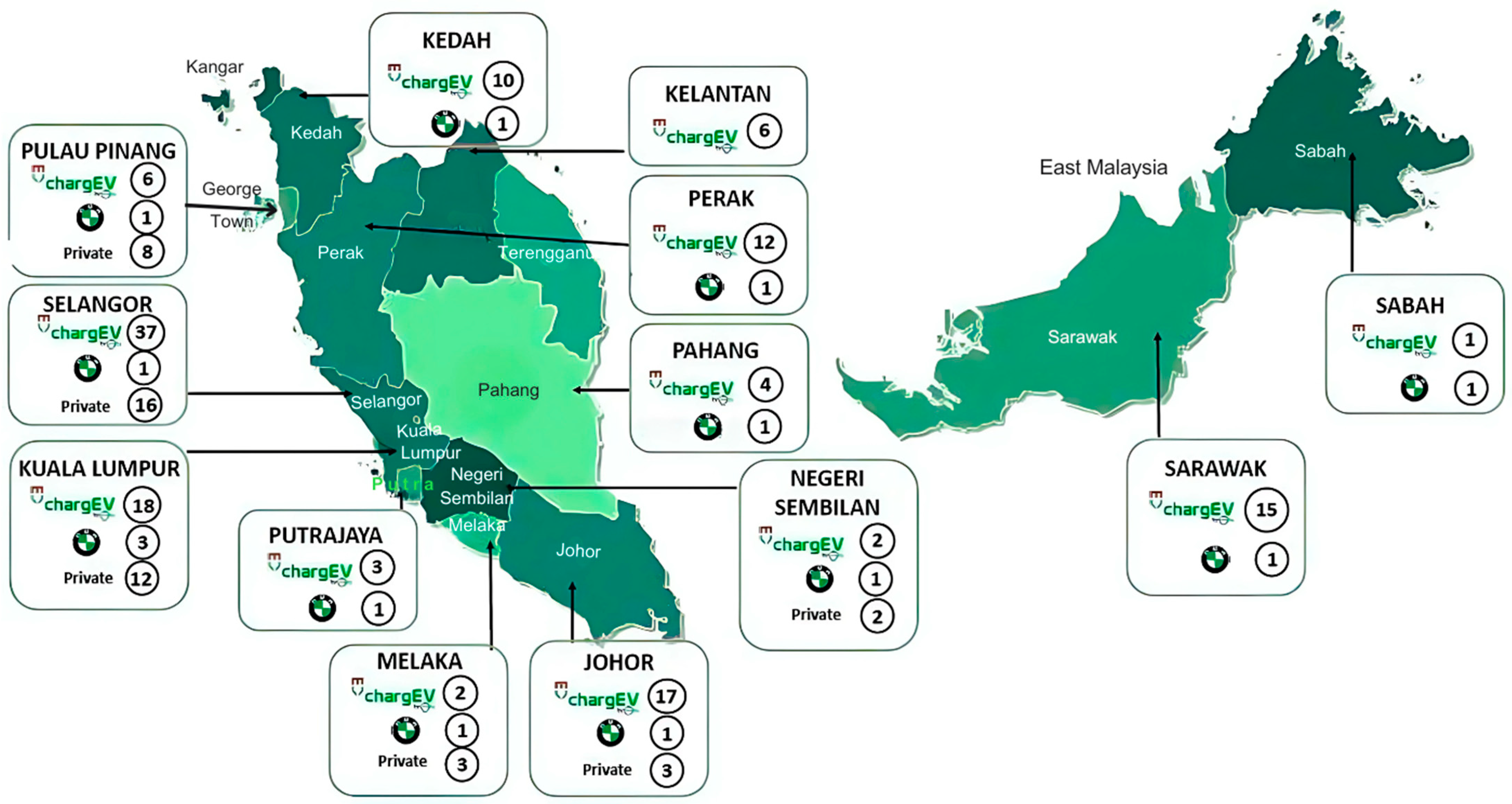
Figure 7 shows where EV charging stations are currently located in Malaysia. It shows that there are a lot of them in cities like Kuala Lumpur, Selangor, Penang, and Johor Bahru. Urban areas have a lot of stations, but many rural and suburban areas do not have enough, which could lead to traffic jams and uneven load distribution. Smart load balancing and cybersecurity solutions are needed to make the most of Malaysia’s quickly growing EV infrastructure and protect the integrity of the network. This study is timely and relevant because government programs like the National EV Policy aim to speed up the development of infrastructure.
4. Evaluation of Performance
Standard classification metrics are used for the intrusion detection system (IDS) components, which keep an eye out for anomalies in OCPP communication, to evaluate the performance of the proposed AI-driven system for EV charging.
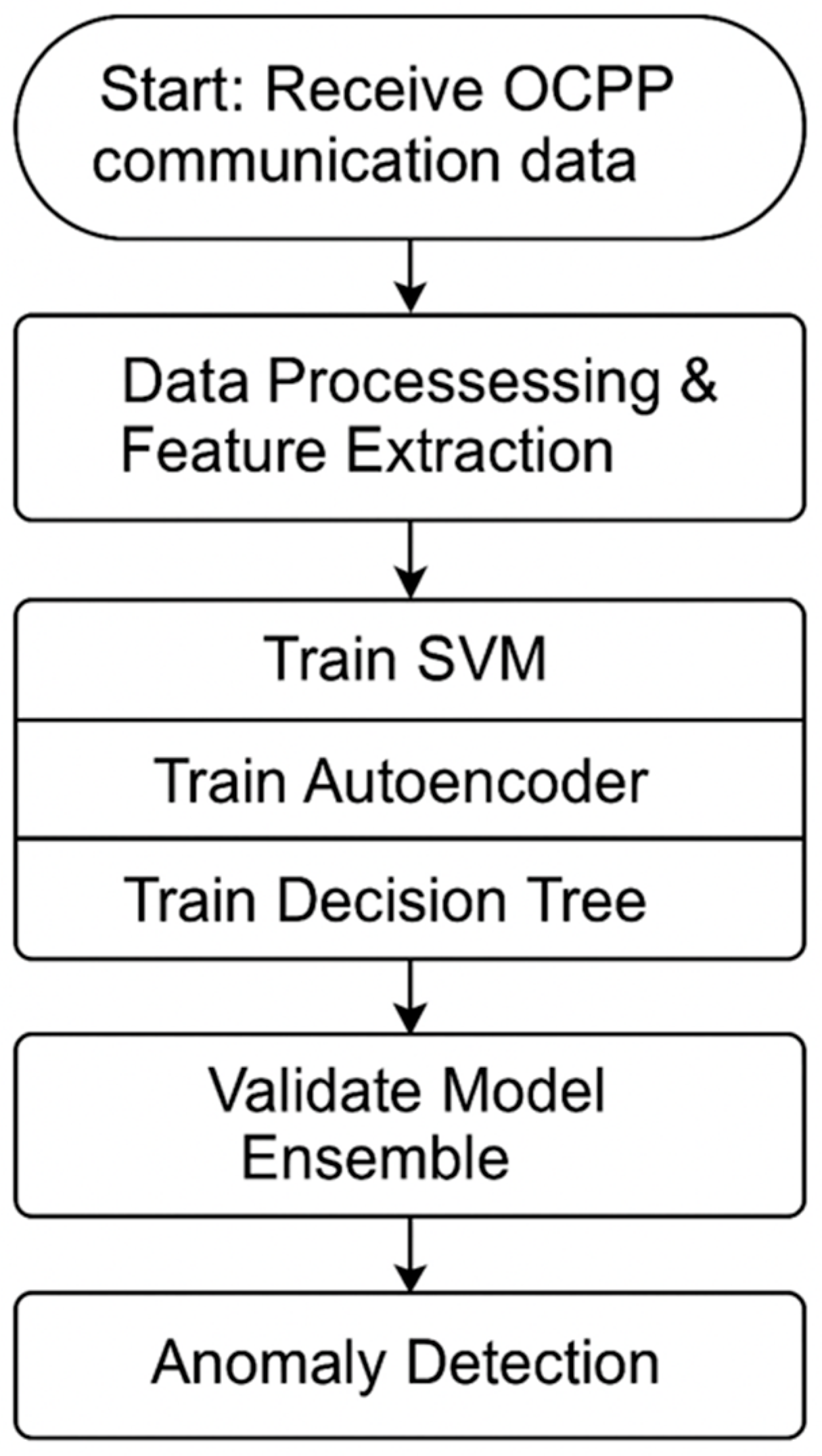
Figure 8 shows the workflow for AI-Based intrusion detection in OCPP-enabled EV charging systems. The data is preprocessed and used to train three models: SVM, autoencoder, and decision tree. Each model is validated using labeled data, with evaluation metrics and confusion matrices generated to assess performance. Based on comparative analysis, the autoencoder is selected for anomaly detection, the SVM for broader classification tasks, and the decision tree for its explainability. This structured pipeline supports both accurate detection and interpretability in cybersecurity applications.
- (a)
Model Evaluation Metrics: Each of these metrics’ precision, accuracy, recall, and F1-score has a distinct function in evaluating the efficacy of the model. Precision gauges how well the model reduces false positives by calculating the percentage of accurately predicted positive cases among all instances projected as positive. By dividing the number of accurate forecasts by the total number of predictions, accuracy calculates the model’s overall correctness. Recall, also referred to as sensitivity, assesses how well the model can detect every true positive instance, reducing false negatives. When both false positives and false negatives are important to the application, the F1-score, which is the harmonic mean of accuracy and recall, offers a fair assessment.
These equations evaluate the performance of AI models such as SVM, decision trees, and autoencoders used for attack detection and load balancing. These are standard metrics used in AI security systems [
39].
- (b)
Anomaly Score for Autoencoder: When explaining how the autoencoder detects attacks based on reconstruction error in your modeling or evaluation section.
where
is the original input, and
is the reconstructed input from the autoencoder. Higher scores indicate anomalies.
Based on unsupervised learning methods in anomaly detection [
40].
- (c)
SVM Decision Function: In the section where you describe your SVM model implementation for classification.
where
is the learned weight vector,
is the input, and
is the bias.
Applied in intrusion detection for EV communication protocols [
28].
- (d)
Entropy-Based Load Distribution: In the section discussing load balancing across multiple EV stations.
where
is the proportion of the total load handled by the charging station
. This helps quantify the financial benefits of AI-based charging systems, such as dynamic pricing models or optimized load scheduling.
Used in smart load distribution algorithms in EV infrastructure [
8].
- (e)
Cost Optimization in Charging: In the section describing energy efficiency or load management strategies for cost-effective charging.
where
is the price per unit of energy at time
, and
is the energy consumed at time
.
Relevant to dynamic pricing models and optimization [
25].
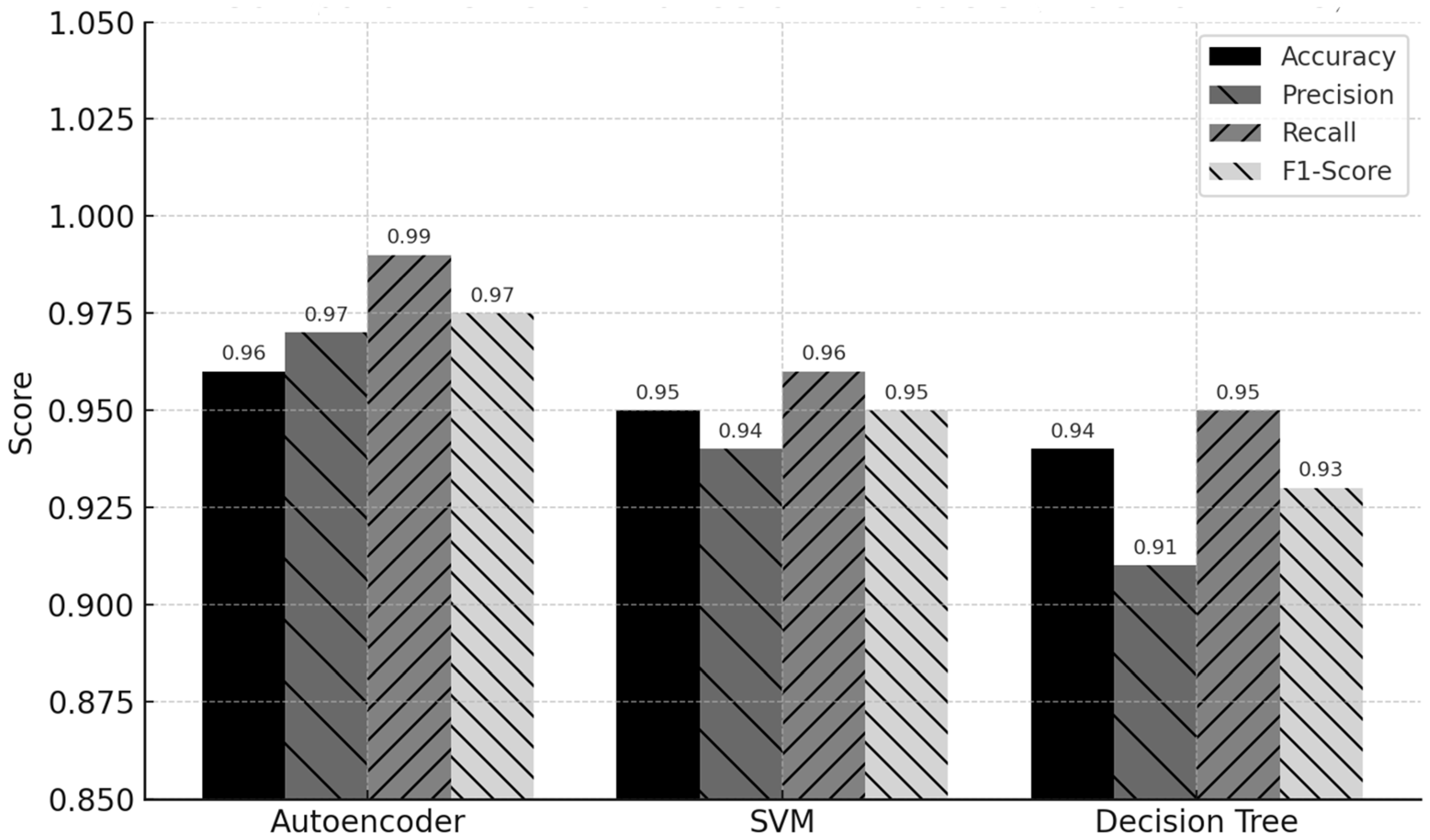
Table 4 compares the performance of SVM, autoencoder, and decision tree models across key metrics. Three models, decision tree, autoencoder, and Support Vector Machine (SVM), were examined in this assessment. With a precision of 97.6%, accuracy of 0.96, recall of 0.99, and F1-score of 0.975, the autoencoder performed best. The result demonstrates its remarkable capacity to detect anomalous patterns accurately with few misclassifications, which makes it perfect for high-stakes, real-time EV communication monitoring. The SVM model achieved a precision of 95.2%, an accuracy of 0.94, a recall of 0.96, and an F1-score of 0.95. It is a worthy contender for more general anomaly classification jobs because of its balanced performance, which indicates dependability in identifying hazards with both high precision and recall. With a precision of 93.8%, accuracy of 0.91, recall of 0.95, and an F1-score of 0.93, the decision tree model performed somewhat worse but was still successful. It is still helpful, especially because of its interpretability, which may help justify choices made during cybersecurity assessments or system audits.
Table 4 shows a comparative evaluation of AI models for EV charging management.
Workflow for intrusion detection system (IDS): To provide robust cybersecurity, the intrusion detection system (IDS) in OCPP-enabled EV charging networks must undergo many critical procedures. To enhance the quality and relevance of the data, raw communication data packets are initially gathered and subsequently subjected to comprehensive preprocessing and feature extraction. Subsequently, several machine learning models, including Support Vector Machines (SVM), autoencoders, and decision trees, are trained to identify patterns indicative of both normal and anomalous activity. We subjected these models to extensive testing to ensure their accuracy, precision, and recall. An ensemble method integrates the outputs of many systems to enhance detection reliability and reduce false positives. This methodical approach enables the rapid and precise identification of cyber threats, hence enhancing the safety and reliability of EV charging infrastructure.
Figure 9 illustrates the IDS workflow for OCPP-enabled EV charging systems, showing data preprocessing, training of SVM, autoencoder, and decision tree models, and the validation process leading to anomaly detection.
Comparative performance chart: The following chart delineates the performance characteristics of three AI models employed for intrusion detection in electric vehicle charging systems: autoencoder, Support Vector Machine (SVM), and decision tree. The assessed metrics are accuracy, precision, recall, and F1-score. The autoencoder routinely surpasses other models in all parameters, exhibiting exceptional proficiency in anomaly detection with excellent precision and recall, thereby assuring robust cybersecurity for OCPP-enabled EV networks.
Figure 10 displays the comparative performance metrics of the AI models, highlighting the autoencoder’s superior detection capabilities.
Table 5 summarizes emerging AI-driven techniques recommended for future research, such as federated learning, graph neural networks, and hybrid AI-based IDS frameworks, which promise improvements in scalability, privacy, and resilience.
Furthermore, with models that can adaptively learn from emerging attack vectors, hybrid AI-driven intrusion detection systems are a significant advancement toward real-time cyber threat mitigation. Digital twins support operational resilience by providing a secure setting for anomaly prediction and simulation. Finally, the urgent need for universal benchmarks to assess AI performance, security, and interoperability across varied EV infrastructure is underscores the growing demand.
5. Discussion
The results of this study show that using AI-driven techniques has made multi-station EV charging networks much better at managing loads and protecting against cyberattacks. Our Smart Load Balancer (SLB) made load distribution 23.5% more efficient, which is a big improvement over old static load balancing methods. This change is in line with recent AI-based load management methods and also gives us a framework that can grow and change as needed. There was a 17% improvement using reinforcement learning for single-station load optimization [
41]. Our multi-station focus, on the other hand, gives us more useful benefits that are relevant to real-world EV infrastructure. Similarly, it demonstrated a 20% reduction in peak load via predictive scheduling, yet their approach lacked integrated cybersecurity considerations, which our framework robustly addresses [
42].
The autoencoder model did better than the SVM-based IDS, which had an F1-score of 0.94 but a higher false positive rate of about 5% [
40]. The autoencoder model had an F1-score of 0.975 and a false positive rate of only 2.5%. Our ensemble-based IDS improves detection accuracy and reduces false alarms, which is very important for keeping operator trust and system stability.
Table 6 compares various load management approaches in EV charging networks, highlighting their methodologies, improvements in load balancing efficiency, scalability, and key limitations. It shows how our proposed reinforcement learning and federated learning framework achieves superior load improvement and scalability while addressing complex real-world deployment challenges compared to existing methods.
Table 7 summarizes different cybersecurity solutions applied to EV charging systems, detailing the AI methodologies used, detection performance (F1-score), false positive rates, privacy-preserving strategies, and limitations. The table emphasizes the effectiveness of our ensemble model integrating autoencoder, SVM, and decision tree techniques with federated learning, achieving high detection accuracy and low false alarms while noting deployment complexity.
Our integrated framework’s novelty lies in combining AI-powered real-time load management with a multi-layered cybersecurity mechanism, both operating within a federated learning environment to ensure data privacy. This holistic approach not only addresses the energy efficiency challenges but also strengthens the resilience of EV charging infrastructure against evolving cyber threats, setting it apart from most existing research that treats these problems independently.
6. Conclusions
This research effectively demonstrates the potential of AI-driven systems to significantly enhance both load distribution and cybersecurity in multi-station electric vehicle (EV) charging networks. The proposed framework integrates intelligent decision-making, real-time analytics, and anomaly detection, ensuring scalability, adaptability, and resilience against cyber threats. Key results include a 23.5% improvement in load distribution efficiency, reflected in reduced peak-to-average load ratios across simulated multi-station networks. The framework also achieves a false positive rate of only 2.5% in anomaly detection using the autoencoder model, which attained an F1-score of 0.975, outperforming traditional detection methods. These improvements contribute to lower charging latency and increased grid stability. By leveraging federated learning and secure multi-party computation, the system preserves data privacy while enabling collaborative load management across geographically distributed stations. The embedded security mechanisms strengthen defenses against multiple cyberattack vectors, enhancing operational reliability. This unified AI-driven approach paves the way for a more intelligent, secure, and efficient EV infrastructure. Future research will explore integration with digital twins, renewable energy forecasting, and dynamic pricing models to further improve adaptability and economic performance in next-generation EV charging ecosystems.