A Secure Data Collection Method Based on Deep Reinforcement Learning and Lightweight Authentication
Abstract
1. Introduction
- (1)
- A lightweight authentication protocol for the multi-UAV system: We propose a lightweight authentication protocol based on chained PUF that aims to reduce the communication cost while supporting the variation in the number of UAVs. This protocol addresses identity security for mobile devices in scalable IoT environments by employing a chained PUF structure for rapid authentication, thereby enabling secure data collection through multi-UAV collaboration in dynamic IoT scenarios.
- (2)
- A data collection method based on multi-agent reinforcement learning: We transformed the multi-UAV path planning problem into a distributed partially observable Markov decision process (DEC-POMDP) model and designed a QMIX-based multi-UAV data collection method that combines the authentication process with path planning to ensure the efficiency and security of the data collection task in IoT; and a segmented reward function was designed to support online authentication of new UAV entrants.
2. Literature Review
3. System Model and Problem Formulation
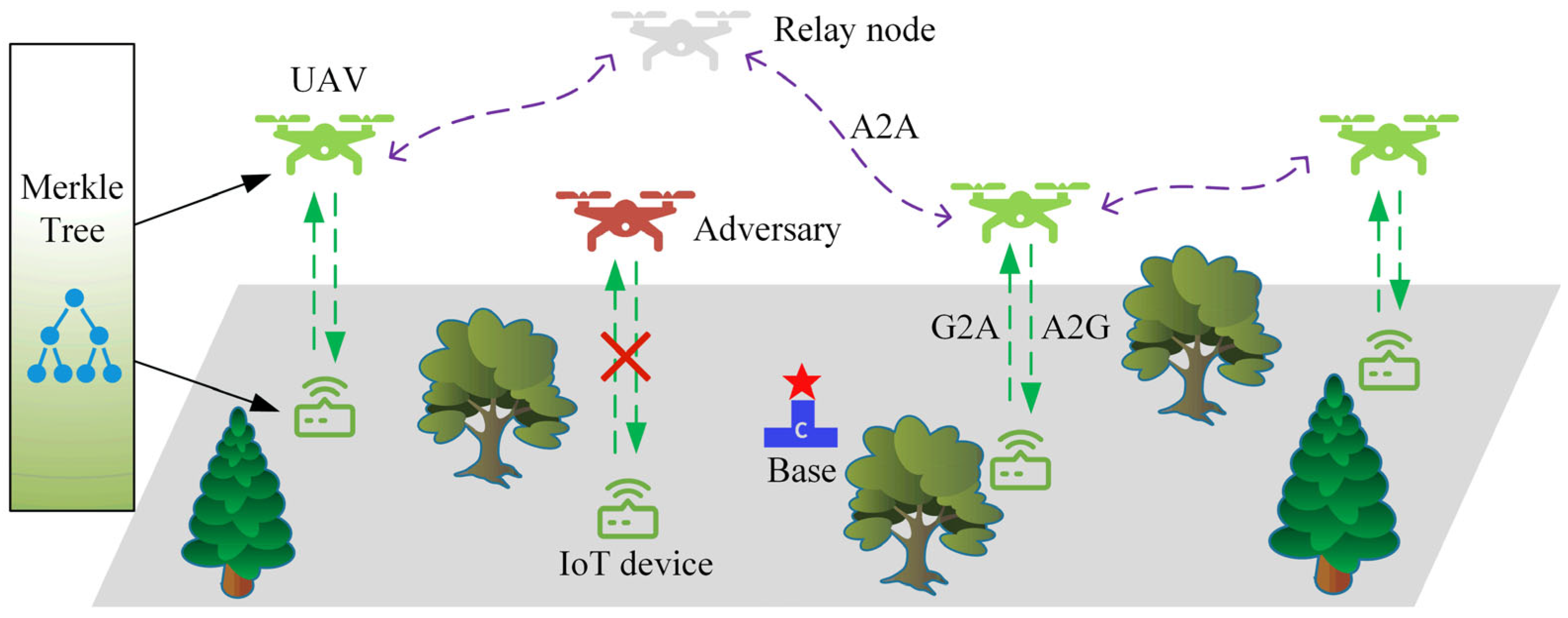
3.1. Mission Model
3.2. Communications Model
- (1)
- UAV–UAV: The communication between UAVs takes place at high altitude with fewer obstacles, which is suitable for line-of-sight (LOS) links. At this time, the channel propagation characteristics can be modeled using the free-space path loss model [30]:
- (2)
- UAV–IoTD: In the device awareness phase, the UAV has not yet determined the location of the ground sensor, signal propagation may be blocked by obstacles, and the communication link is in non-line-of-sight (NLOS) conditions. The channel model can use a logarithmic distance path loss model [31]:
- (3)
- UAV–BS: The communication link between the UAV and the base is mainly a LOS link, and the free-space path loss model is usually applicable. However, when the UAV is far away from the base, the communication quality may degrade. In this case, multi-hop transmissions can be performed by introducing relay UAVs [30], thus extending the communication coverage and reducing the path loss. The total path loss can be expressed as follows:
3.3. Energy Consumption Model
3.4. Optimization Goals
4. Algorithm Design
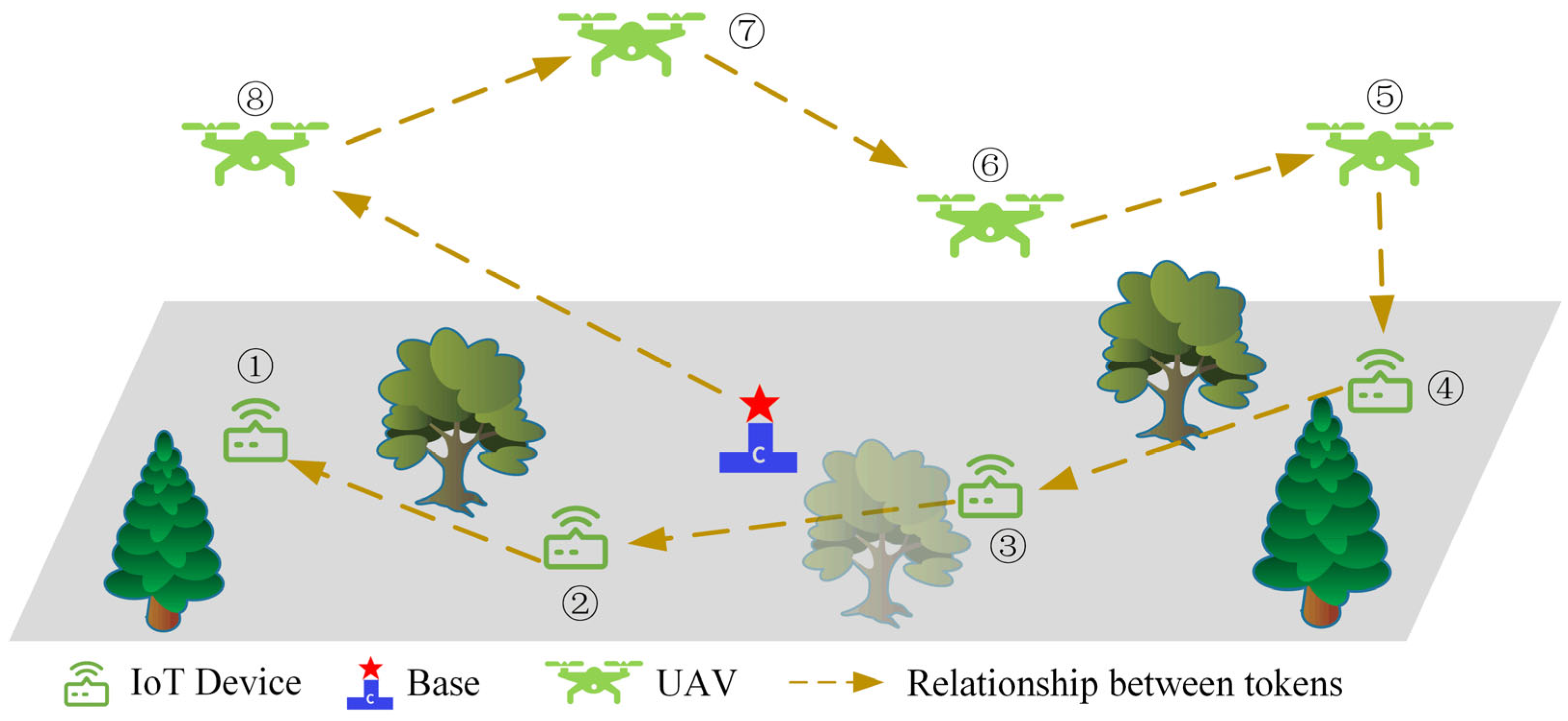
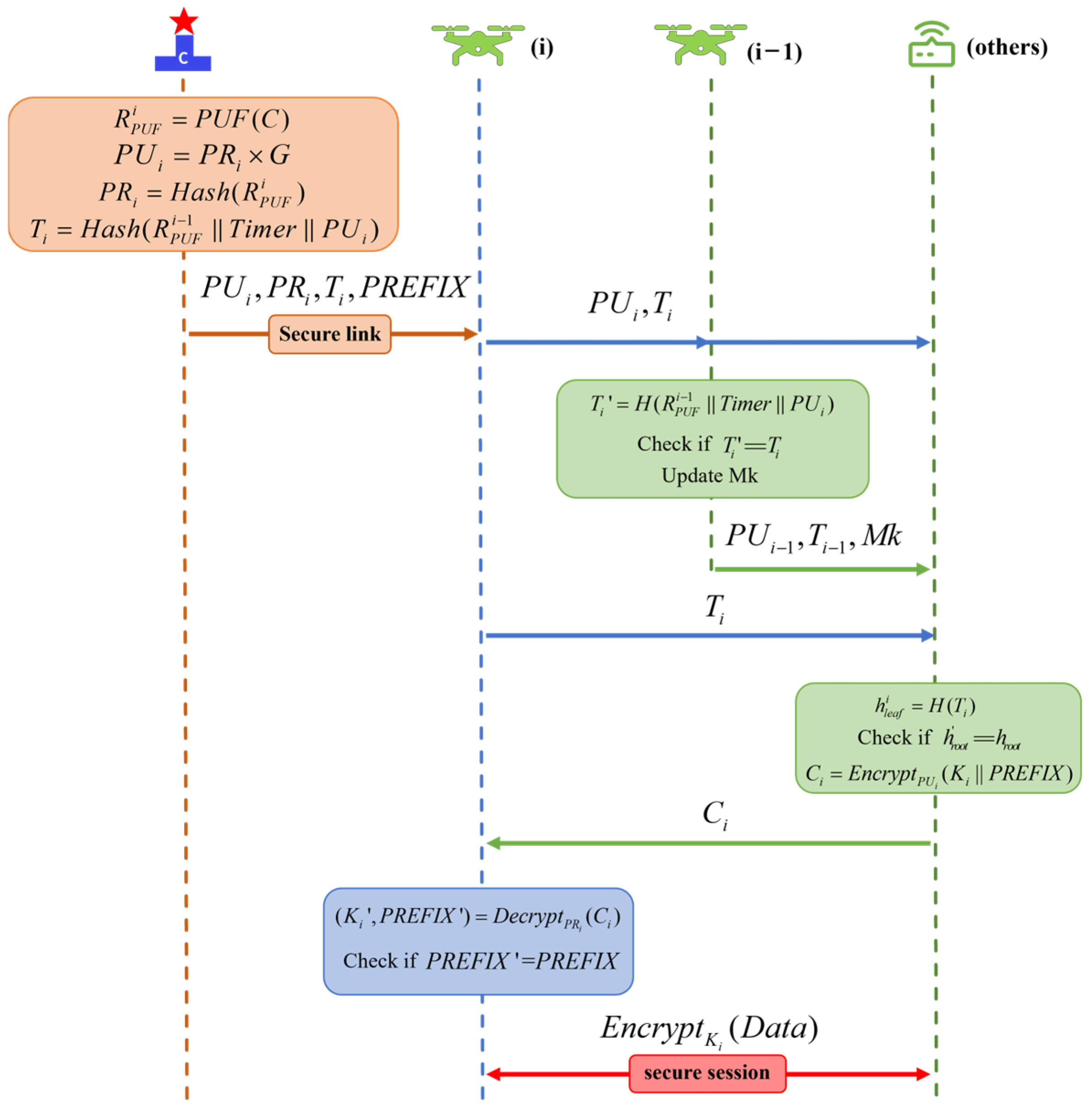
4.1. Scalable Authentication Protocol Based on Chained PUFs
- (1)
- Device generates its PUF response as:
- (2)
- The RA calculates the private key of device based on:
- (3)
- Token is the identity of device for the duration of the task and is calculated as:
- (1)
- If UAV is a newly added UAV, broadcast , to the mission area. otherwise skip to step 3.
- (2)
- UAV calculates UAV’s token based on its own and the received public key:
- (3)
- When there is a “to be collected” IoT device in the data collection range, UAV sends its token and public key to it.
- (4)
- The IoT device calculates the hash value of the corresponding Merkle leaf node based on the received :
- (5)
- The IoT device calculates the root hash value accordingly and compares it with the root hash value of the locally stored Merkle tree. If they are the same, the authentication passes, otherwise the authentication fails.
- (6)
- After passing the authentication, the IoT device generates a random session key and encrypts it using by splicing it with the prefix , which is subsequently sent to the UAV to ensure the confidentiality of the key during transmission. The encryption process is as follows:
- (7)
- The UAV receives and decrypts the data using its private key, and the decryption process is as follows:
4.2. QMIX-Based Algorithm for Secure Multi-UAV Data Collection
4.2.1. Dec-POMDP Model
- (1)
- 2D Distance between UAVs
- (2)
- Data collection
- (3)
- Obstacle avoidance
- (4)
- Authentication reward for newly joining UAV
4.2.2. LS-QMIX Data Collection Algorithm
| Algorithm 1: LS-QMIX Algorithm Flow |
|
5. Simulation and Analysis
5.1. Security Analysis and Comparison
5.2. Cost Analysis of Computing Time
5.3. Communications Cost Analysis
5.4. Convergence Curves for LS-QMIX
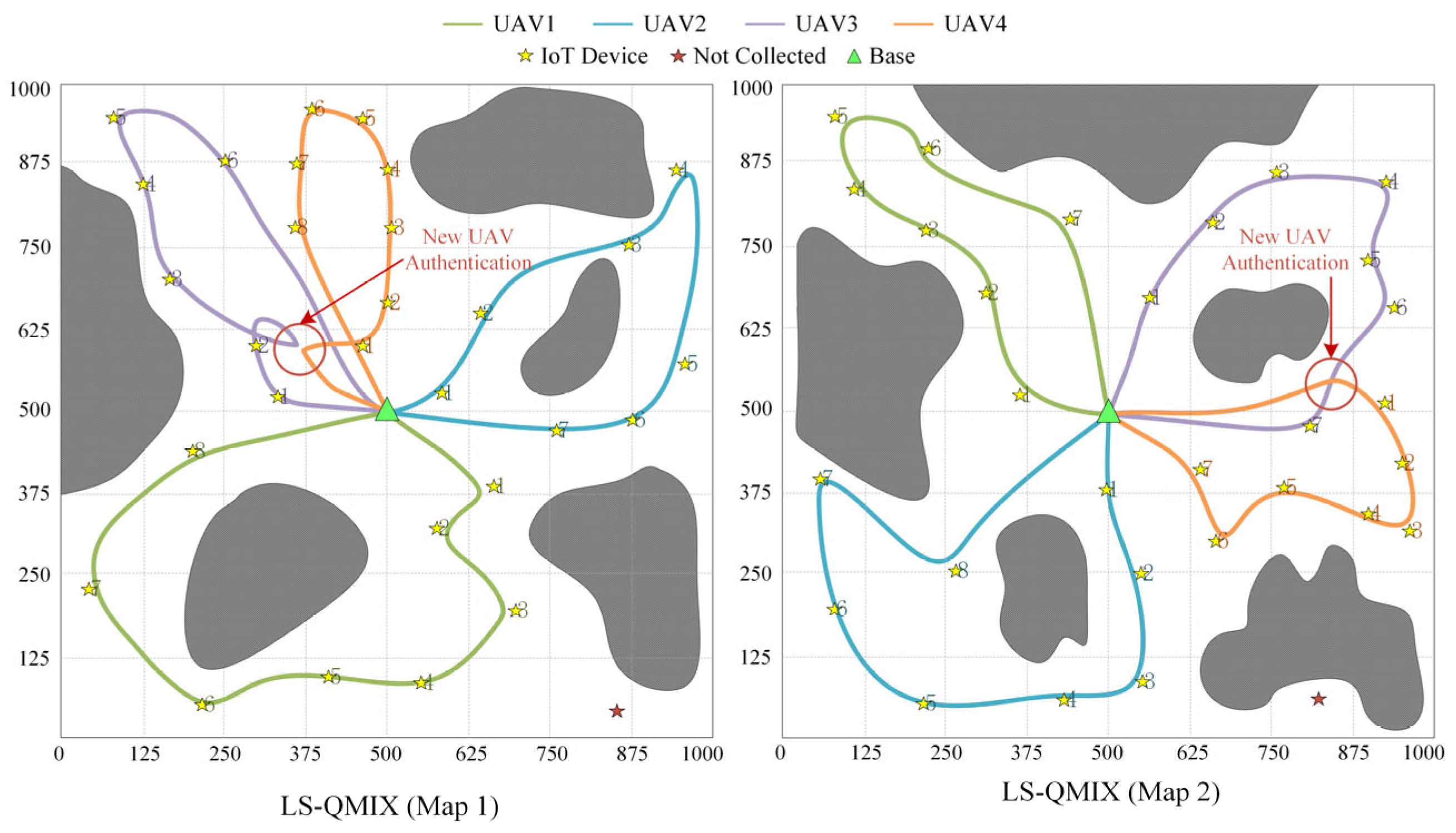
5.5. UAVs Flight Path
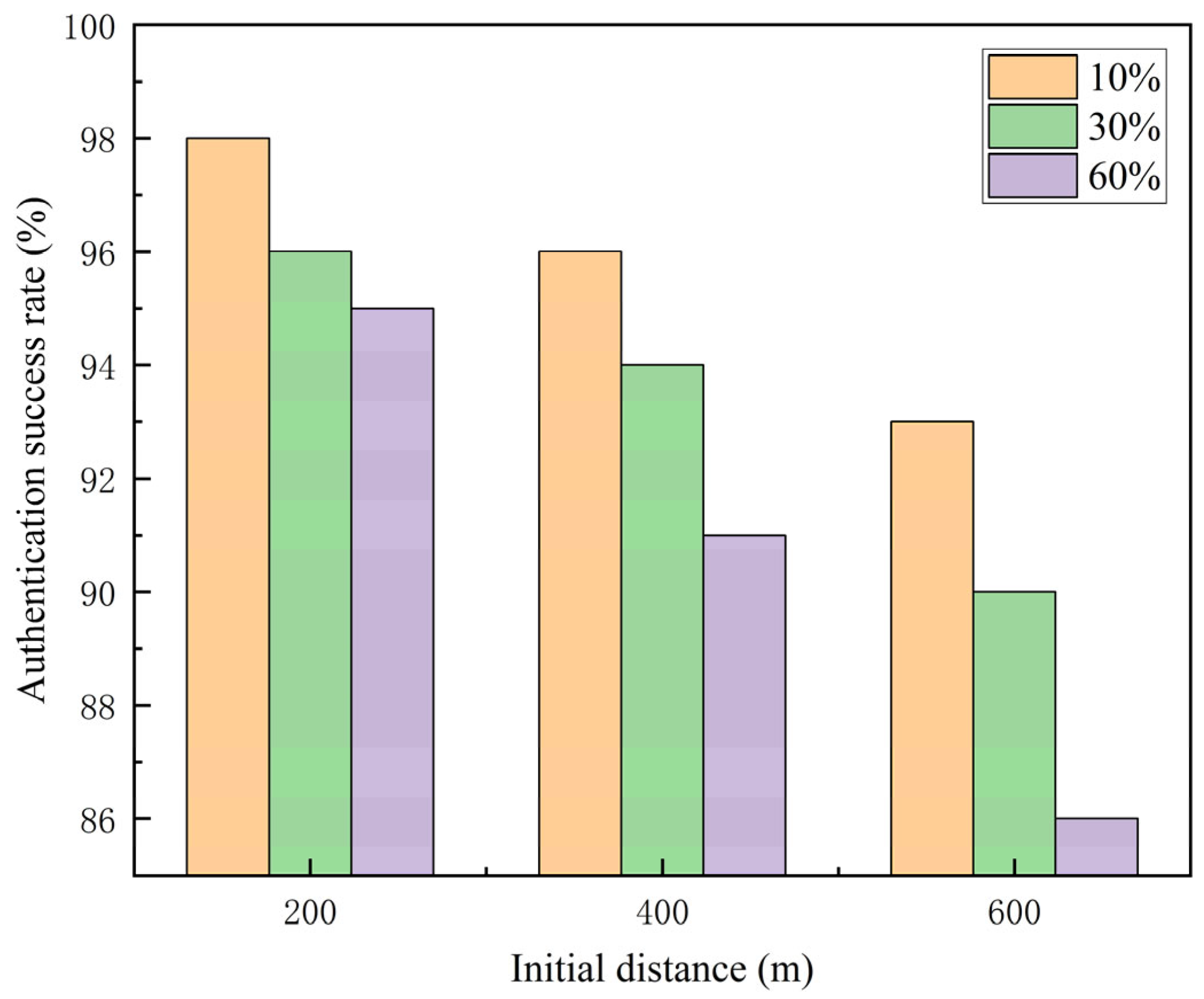
5.6. Authentication Success Rate
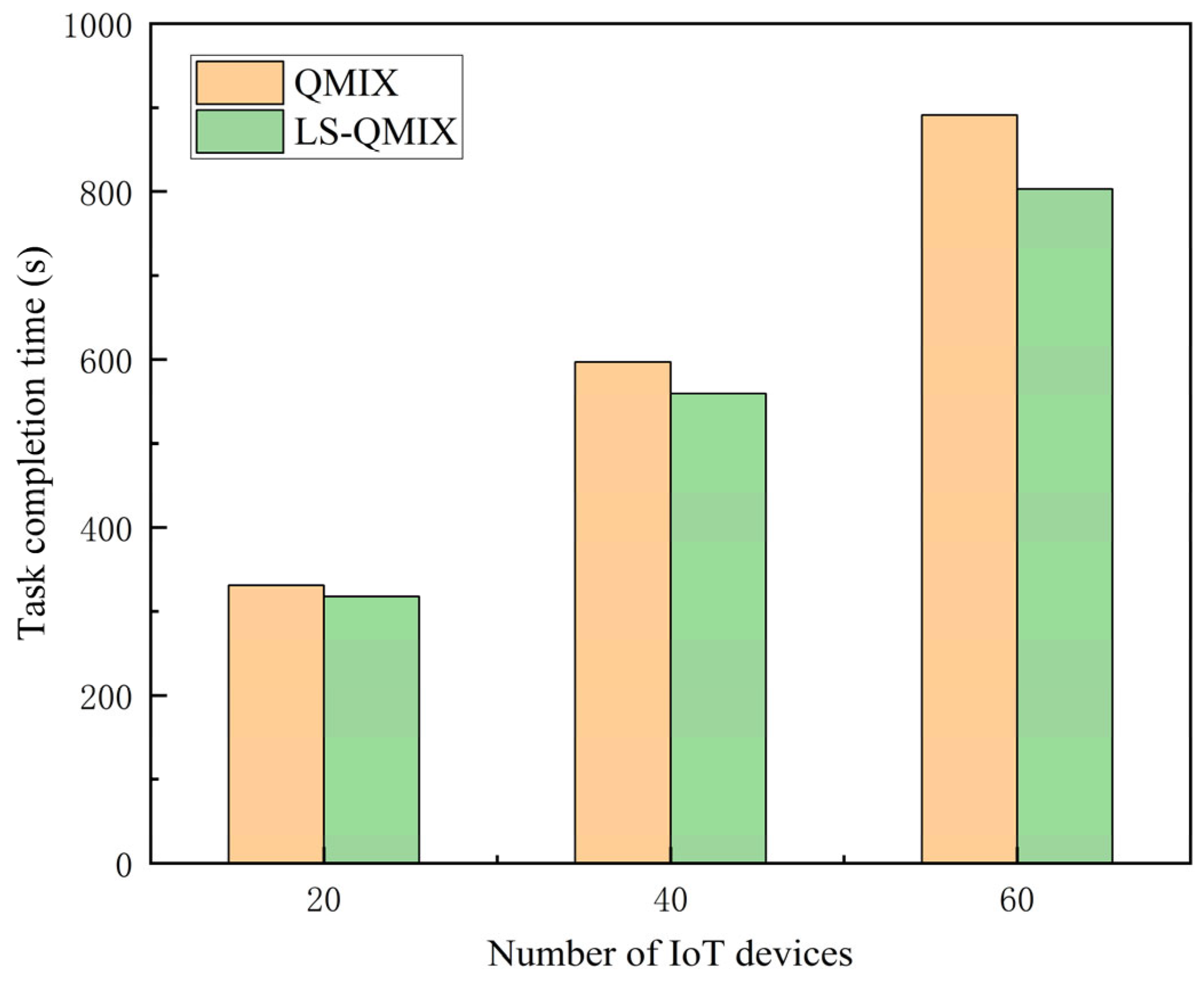
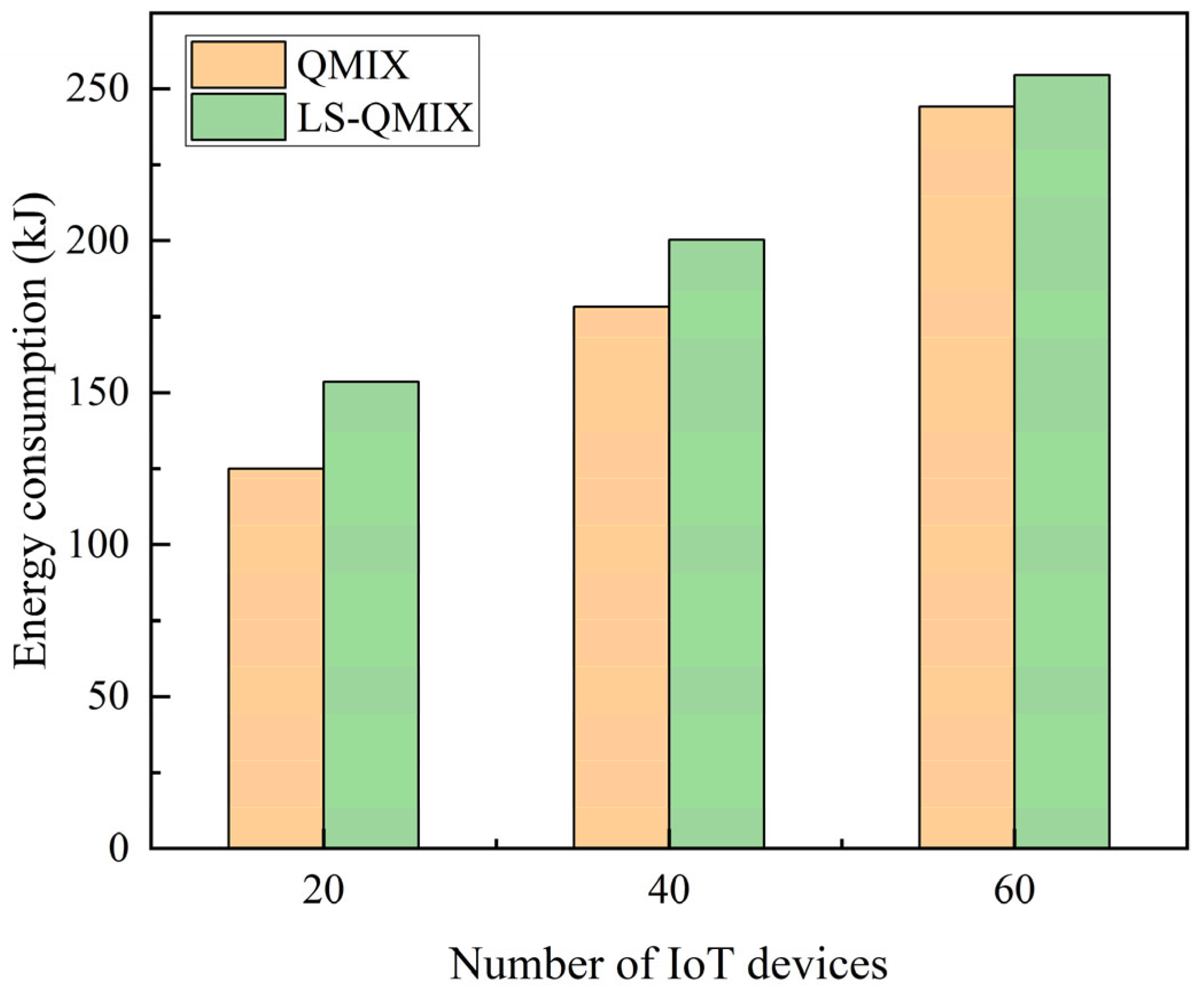
5.7. Analysis of Task Completion Time and Energy Consumption
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Du, J. Application Analysis of IoT Technology in Smart Cities. In Proceedings of the 2021 2nd International Conference on E-Commerce and Internet Technology (ECIT), Hangzhou, China, 5–7 March 2021; pp. 264–269. [Google Scholar]
- Ketu, S.; Mishra, P.K. Internet of Healthcare Things: A Contemporary Survey. J. Netw. Comput. Appl. 2021, 192, 103179. [Google Scholar] [CrossRef]
- Ang, L.-M.; Seng, K.P.; Wachowicz, M. Embedded Intelligence and the Data-Driven Future of Application-Specific Internet of Things for Smart Environments. Int. J. Distrib. Sens. Netw. 2022, 18, 15501329221102371. [Google Scholar] [CrossRef]
- Akan, O.B.; Dinc, E.; Kuscu, M.; Cetinkaya, O.; Bilgin, B.A. Internet of Everything (IoE)—From Molecules to the Universe. IEEE Commun. Mag. 2023, 61, 122–128. [Google Scholar] [CrossRef]
- Krejčí, J.; Babiuch, M.; Suder, J.; Krys, V.; Bobovský, Z. Internet of Robotic Things: Current Technologies, Challenges, Applications, and Future Research Topics. Sensors 2025, 25, 765. [Google Scholar] [CrossRef] [PubMed]
- Messaoudi, K.; Oubbati, O.S.; Rachedi, A.; Lakas, A.; Bendouma, T.; Chaib, N. A Survey of UAV-Based Data Collection: Challenges, Solutions and Future Perspectives. J. Netw. Comput. Appl. 2023, 216, 103670. [Google Scholar] [CrossRef]
- Cao, Y.; Cheng, X.; Mu, J. Concentrated Coverage Path Planning Algorithm of UAV Formation for Aerial Photography. IEEE Sens. J. 2022, 22, 11098–11111. [Google Scholar] [CrossRef]
- Wang, W.; Liu, Y.; Srikant, R.; Ying, L. 3M-RL: Multi-Resolution, Multi-Agent, Mean-Field Reinforcement Learning for Autonomous UAV Routing. IEEE Trans. Intell. Transport. Syst. 2022, 23, 8985–8996. [Google Scholar] [CrossRef]
- Liu, Z.; Cao, Y.; Chen, J.; Li, J. A Hierarchical Reinforcement Learning Algorithm Based on Attention Mechanism for UAV Autonomous Navigation. IEEE Trans. Intell. Transport. Syst. 2023, 24, 13309–13320. [Google Scholar] [CrossRef]
- Wu, J.; Sun, Y.; Li, D.; Shi, J.; Li, X.; Gao, L.; Yu, L.; Han, G.; Wu, J. An Adaptive Conversion Speed Q-Learning Algorithm for Search and Rescue UAV Path Planning in Unknown Environments. IEEE Trans. Veh. Technol. 2023, 72, 15391–15404. [Google Scholar] [CrossRef]
- Zhang, J.; Guo, Y.; Zheng, L.; Yang, Q.; Shi, G.; Wu, Y. Real-Time UAV Path Planning Based on LSTM Network. J. Syst. Eng. Electron. 2024, 35, 374–385. [Google Scholar] [CrossRef]
- Lv, H.; Chen, Y.; Li, S.; Zhu, B.; Li, M. Improve Exploration in Deep Reinforcement Learning for UAV Path Planning Using State and Action Entropy. Meas. Sci. Technol. 2024, 35, 056206. [Google Scholar] [CrossRef]
- Fu, X.; Huang, X.; Pan, Q.; Pace, P.; Aloi, G.; Fortino, G. Cooperative Data Collection for UAV-Assisted Maritime IoT Based on Deep Reinforcement Learning. IEEE Trans. Veh. Technol. 2024, 73, 10333–10349. [Google Scholar] [CrossRef]
- Wei, Z.; Zhu, M.; Zhang, N.; Wang, L.; Zou, Y.; Meng, Z.; Wu, H.; Feng, Z. UAV-Assisted Data Collection for Internet of Things: A Survey. IEEE Internet Things J. 2022, 9, 15460–15483. [Google Scholar] [CrossRef]
- Shobiri, B.; Pourali, S.; Migault, D.; Boureanu, I.; Preda, S.; Mannan, M.; Youssef, A. LURK-T: Limited Use of Remote Keys with Added Trust in TLS 1.3. IEEE Trans. Netw. Sci. Eng. 2024, 11, 6313–6327. [Google Scholar] [CrossRef]
- Bian, Y.; Zheng, F.; Wang, Y.; Lei, L.; Ma, Y.; Zhou, T.; Dong, J.; Fan, G.; Jing, J. AsyncGBP+: Bridging SSL/TLS and Heterogeneous Computing Power With GPU-Based Providers. IEEE Trans. Comput. 2024, 74, 356–370. [Google Scholar] [CrossRef]
- Shan, T.; Wang, Y.; Zhao, C.; Li, Y.; Zhang, G.; Zhu, Q. Multi-UAV WRSN Charging Path Planning Based on Improved Heed and IA-DRL. Comput. Commun. 2023, 203, 77–88. [Google Scholar] [CrossRef]
- Ejaz, M.; Gui, J.; Asim, M.; El-Affendi, M.A.; Fung, C.; Abd El-Latif, A.A. RL-Planner: Reinforcement Learning-Enabled Efficient Path Planning in Multi-UAV MEC Systems. IEEE Trans. Netw. Serv. Manag. 2024, 21, 3317–3329. [Google Scholar] [CrossRef]
- Silvirianti; Narottama, B.; Shin, S.Y. UAV Coverage Path Planning With Quantum-Based Recurrent Deep Deterministic Policy Gradient. IEEE Trans. Veh. Technol. 2023, 73, 7424–7429. [Google Scholar] [CrossRef]
- Liang, J.; Li, Y.; Yin, G.; Xu, L.; Lu, Y.; Feng, J.; Shen, T.; Cai, G. A MAS-Based Hierarchical Architecture for the Cooperation Control of Connected and Automated Vehicles. IEEE Trans. Veh. Technol. 2023, 72, 1559–1573. [Google Scholar] [CrossRef]
- Liang, J.; Yang, K.; Tan, C.; Wang, J.; Yin, G. Enhancing High-Speed Cruising Performance of Autonomous Vehicles through Integrated Deep Reinforcement Learning Framework. IEEE Trans. Intell. Transp. Syst. 2025, 26, 835–848. [Google Scholar] [CrossRef]
- Wang, L.; Wang, K.; Pan, C.; Xu, W.; Aslam, N.; Hanzo, L. Multi-Agent Deep Reinforcement Learning-Based Trajectory Planning for Multi-UAV Assisted Mobile Edge Computing. IEEE Trans. Cogn. Commun. Netw. 2021, 7, 73–84. [Google Scholar] [CrossRef]
- Wu, R.; Gu, F.; Liu, H.; Shi, H. UAV Path Planning Based on Multicritic-Delayed Deep Deterministic Policy Gradient. Wirel. Commun. Mob. Comput. 2022, 2022, 9017079. [Google Scholar] [CrossRef]
- Asghar Khan, M.; Ullah, I.; Kumar, N.; Afghah, F.; Barb, G.; Noor, F.; Alqahtany, S. A Certificate-Based Ring Signcryption Scheme for Securing UAV-Enabled Private Edge Computing Systems. IEEE Access 2024, 12, 83466–83479. [Google Scholar] [CrossRef]
- Nyangaresi, V.O.; Jasim, H.M.; Mutlaq, K.A.-A.; Abduljabbar, Z.A.; Ma, J.; Abduljaleel, I.Q.; Honi, D.G. A Symmetric Key and Elliptic Curve Cryptography-Based Protocol for Message Encryption in Unmanned Aerial Vehicles. Electronics 2023, 12, 3688. [Google Scholar] [CrossRef]
- Dong, C.; Jiang, F.; Li, X.; Yao, A.; Li, G.; Liu, X. A Blockchain-Aided Self-Sovereign Identity Framework for Edge-Based UAV Delivery System. In Proceedings of the 2021 IEEE/ACM 21st International Symposium on Cluster, Cloud and Internet Computing (CCGrid), Melbourne, Australia, 10–13 May 2021; pp. 622–624. [Google Scholar]
- Li, G.; He, B.; Wang, Z.; Cheng, X.; Chen, J. Blockchain-Enhanced Spatiotemporal Data Aggregation for UAV-Assisted Wireless Sensor Networks. IEEE Trans. Ind. Inf. 2022, 18, 4520–4530. [Google Scholar] [CrossRef]
- Zhang, L.; Xu, J.; Obaidat, M.S.; Li, X.; Vijayakumar, P. A PUF-based Lightweight Authentication and Key Agreement Protocol for Smart UAV Networks. IET Commun. 2022, 16, 1142–1159. [Google Scholar] [CrossRef]
- Tian, C.; Ma, J.; Li, T.; Zhang, J.; Ma, C.; Xi, N. Provably and Physically Secure UAV-Assisted Authentication Protocol for IoT Devices in Unattended Settings. IEEE Trans. Inf. Forensic Secur. 2024, 19, 4448–4463. [Google Scholar] [CrossRef]
- Wang, H.-M.; Zhang, Y.; Zhang, X.; Li, Z. Secrecy and Covert Communications against UAV Surveillance via Multi-Hop Networks. IEEE Trans. Commun. 2020, 68, 389–401. [Google Scholar] [CrossRef]
- Kuzulugil, K.; Hasirci, Z.; Cavdar, I.H. Optimum Reference Distance Based Path Loss Exponent Determination for Vehicle-to-Vehicle Communication. Turk. J. Electr. Eng. Comput. Sci. 2020, 28, 2956–2967. [Google Scholar] [CrossRef]
- Li, Z.; Tong, P.; Liu, J.; Wang, X.; Xie, L.; Dai, H. Learning-Based Data Gathering for Information Freshness in UAV-Assisted IoT Networks. IEEE Internet Things J. 2023, 10, 2557–2573. [Google Scholar] [CrossRef]
- Lei, Y.; Zeng, L.; Li, Y.-X.; Wang, M.-X.; Qin, H. A Lightweight Authentication Protocol for UAV Networks Based on Security and Computational Resource Optimization. IEEE Access 2021, 9, 53769–53785. [Google Scholar] [CrossRef]
- Bansal, G.; Sikdar, B. Location Aware Clustering: Scalable Authentication Protocol for UAV Swarms. IEEE Netw. Lett. 2021, 3, 177–180. [Google Scholar] [CrossRef]
- Pu, C.; Li, Y. Lightweight Authentication Protocol for Unmanned Aerial Vehicles Using Physical Unclonable Function and Chaotic System. In Proceedings of the 2020 IEEE International Symposium on Local and Metropolitan Area Networks (LANMAN), Orlando, FL, USA, 13–15 July 2020; pp. 1–6. [Google Scholar]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J.P.C. Design and Analysis of Secure Lightweight Remote User Authentication and Key Agreement Scheme in Internet of Drones Deployment. IEEE Internet Things J. 2019, 6, 3572–3584. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Kumar, N.; Rodrigues, J.J.P.C. TCALAS: Temporal Credential-Based Anonymous Lightweight Authentication Scheme for Internet of Drones Environment. IEEE Trans. Veh. Technol. 2019, 68, 6903–6916. [Google Scholar] [CrossRef]
- Ali, Z.; Chaudhry, S.A.; Ramzan, M.S.; Al-Turjman, F. Securing Smart City Surveillance: A Lightweight Authentication Mechanism for Unmanned Vehicles. IEEE Access 2020, 8, 43711–43724. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Khan, M.; Lee, J. Anonymous Two-Factor Authentication for Consumer Roaming Service in Global Mobility Networks. IEEE Trans. Consum. Electron. 2013, 59, 811–817. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Rodrigues, J.J.P.C.; Park, Y. Physically Secure Lightweight Anonymous User Authentication Protocol for Internet of Things Using Physically Unclonable Functions. IEEE Access 2019, 7, 85627–85644. [Google Scholar] [CrossRef]
- Biham, E.; Chen, R.; Joux, A.; Carribault, P.; Lemuet, C.; Jalby, W. Collisions of SHA-0 and Reduced SHA-1. In Advances in Cryptology—EUROCRYPT 2005; Cramer, R., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2005; Volume 3494, pp. 36–57. ISBN 978-3-540-25910-7. [Google Scholar]



| Parameter | Value |
|---|---|
| Initial energy | 300 kJ |
| Flight altitude | 95 m, 100 m, 105 m, 110 m |
| Flight speed | 5 m/s |
| Wind speed | 1 m/s |
| Blade-tip speed | 100 m/s |
| Hover induced velocity | 4.5 m/s |
| Air density | 1.225 kg/m3 |
| Communication range | 150 m |
| Maximum episodes | 18,000 |
| Replay buffer size | 100,000 |
| Batch size | 256 |
| Learning rate | 0.0005 |
| Discount factor | 0.99 |
| Target network update frequency | 100 steps |
| Scheme | C5.1 | C5.2 | C5.3 | C5.4 | C5.5 | C5.6 | C7 | C8 | C10 | C11 | C12 |
|---|---|---|---|---|---|---|---|---|---|---|---|
| [33] | √ | √ | √ | ✗ | ✗ | √ | ✗ | √ | ✗ | √ | √ |
| [34] | √ | √ | √ | √ | √ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| [35] | √ | √ | √ | √ | √ | √ | √ | √ | √ | ✗ | √ |
| [36] | √ | √ | √ | ✗ | ✗ | √ | √ | ✗ | √ | √ | √ |
| [37] | √ | √ | √ | ✗ | ✗ | √ | √ | ✗ | √ | √ | √ |
| [38] | √ | √ | √ | ✗ | ✗ | √ | √ | ✗ | √ | √ | √ |
| Ours | √ | √ | √ | √ | √ | √ | √ | √ | √ | ✗ | √ |
| Scheme | UAV | Ground Station | IoTD/User | Total Cost |
|---|---|---|---|---|
| [33] | 2Th | 4Th + Ta | 2Th ≈ 1.0 ms | 8Th + Ta ≈ 6.045 ms |
| [34] | 2Te | 2Te | - | 4Te ≈ 34.8 ms |
| [35] | 4Te | 4Te | - | 8Te ≈ 69.6 ms |
| [36] | 7Th | 8Th | 16Th + Tf | 31Th + Tf ≈ 78.575 ms |
| [37] | 7Th | 9Th | 14Th + Te | 30Th + Te ≈ 23.7 ms |
| [38] | 7Th | 7Th | 10Th + Ta | 24Th + Ta ≈ 14.045 ms |
| Ours | Th + Te | - | Th + Te | 2Th + 2Te ≈ 18.4 ms |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Published by MDPI on behalf of the World Electric Vehicle Association. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Y.; Zhang, J.; Han, G.; Chen, D. A Secure Data Collection Method Based on Deep Reinforcement Learning and Lightweight Authentication. World Electr. Veh. J. 2025, 16, 281. https://doi.org/10.3390/wevj16050281
Wang Y, Zhang J, Han G, Chen D. A Secure Data Collection Method Based on Deep Reinforcement Learning and Lightweight Authentication. World Electric Vehicle Journal. 2025; 16(5):281. https://doi.org/10.3390/wevj16050281
Chicago/Turabian StyleWang, Yunlong, Jie Zhang, Guangjie Han, and Dugui Chen. 2025. "A Secure Data Collection Method Based on Deep Reinforcement Learning and Lightweight Authentication" World Electric Vehicle Journal 16, no. 5: 281. https://doi.org/10.3390/wevj16050281
APA StyleWang, Y., Zhang, J., Han, G., & Chen, D. (2025). A Secure Data Collection Method Based on Deep Reinforcement Learning and Lightweight Authentication. World Electric Vehicle Journal, 16(5), 281. https://doi.org/10.3390/wevj16050281







