IEC 61850-Based Communication Networks of Distribution System against Cyber and Physical Failures
Abstract
:1. Introduction
- Introduce a co-simulation platform to link between the system model on RSCAD/RTDS and SEL 421 protective relays.
- Publish/subscribe SV/GOOSE messages between the system model and the external relays to provide a protection scheme for the distributed system
- Divide the system into several agent zones and send the voltage of each bus to the agents as SV message. Based on the under-voltage technique, the agents send a GOOSE message to the breakers.
- Two solutions are suggested to mitigate the effects of failure in the communications signals and enhance the resiliency of the system.
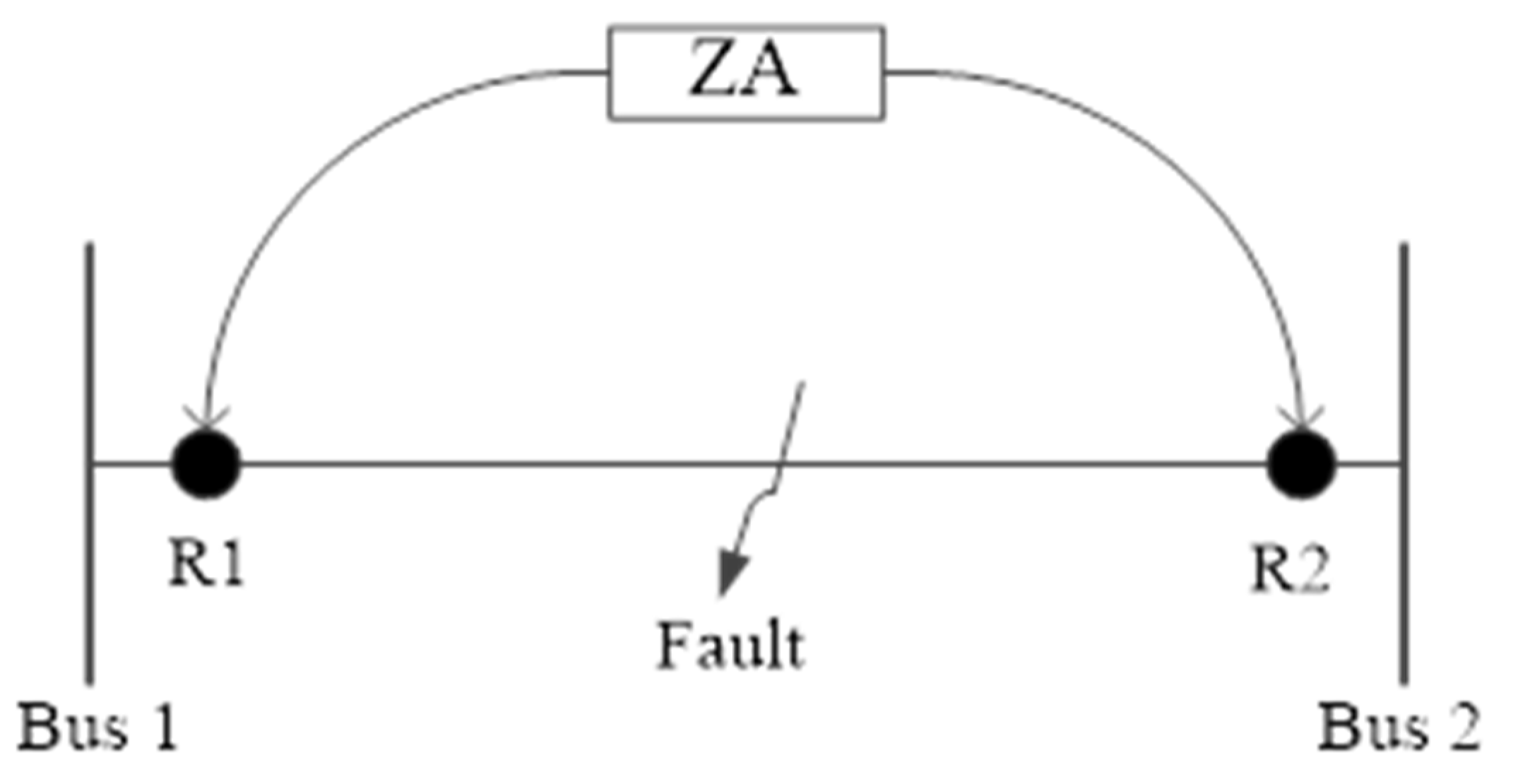
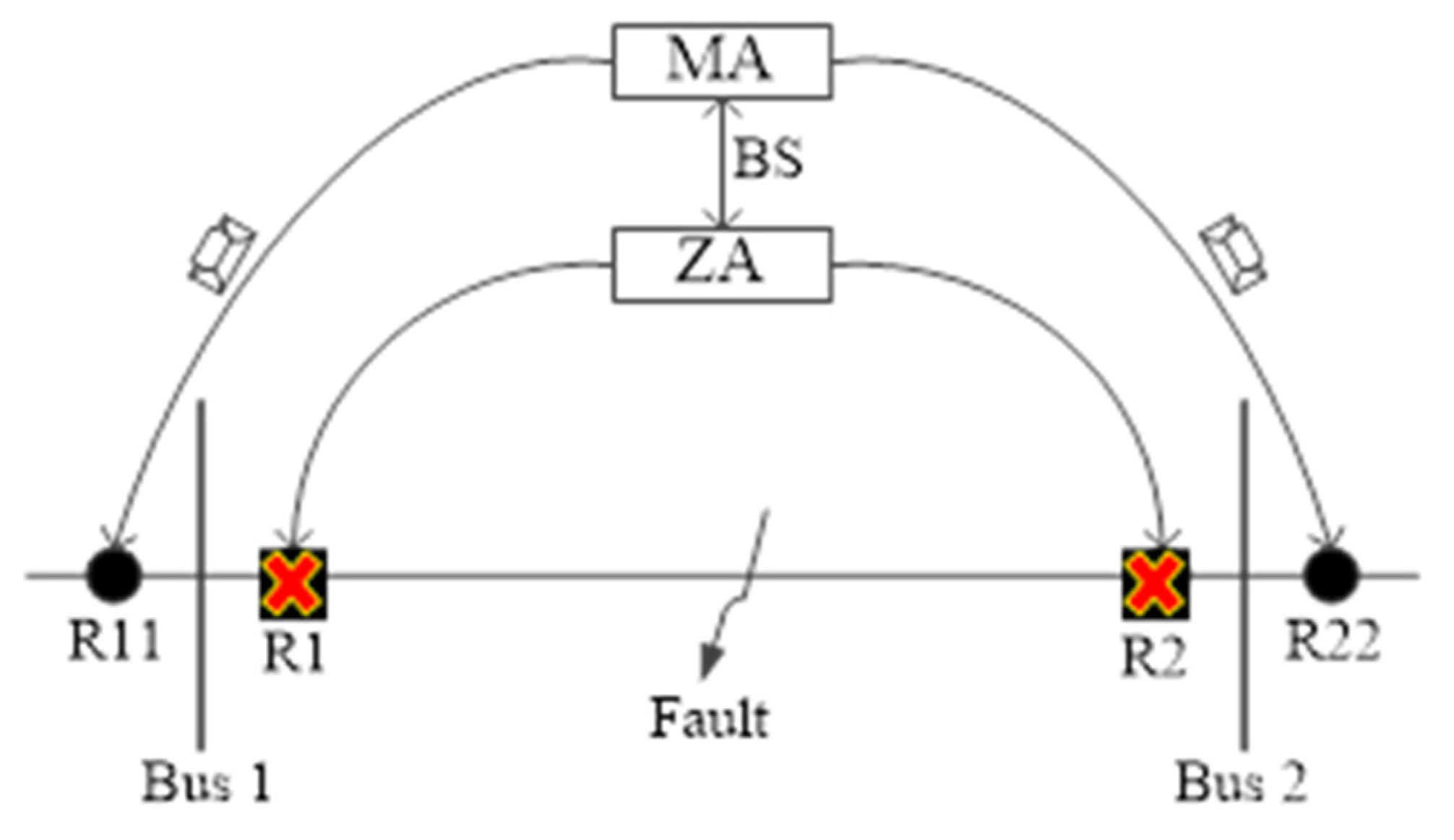
2. Protection Issues in the Network System
2.1. Selectivity and Sensitivity Features
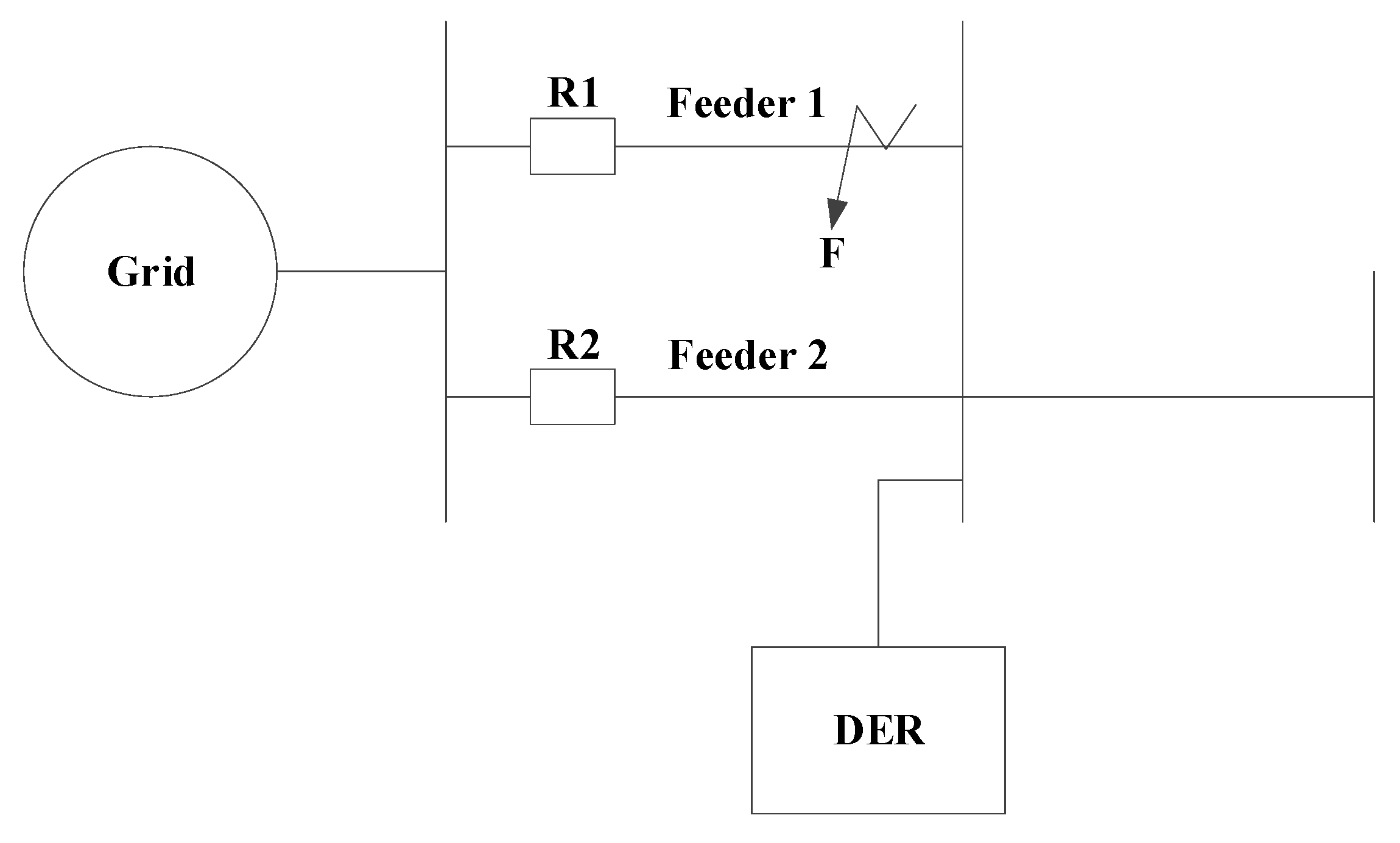
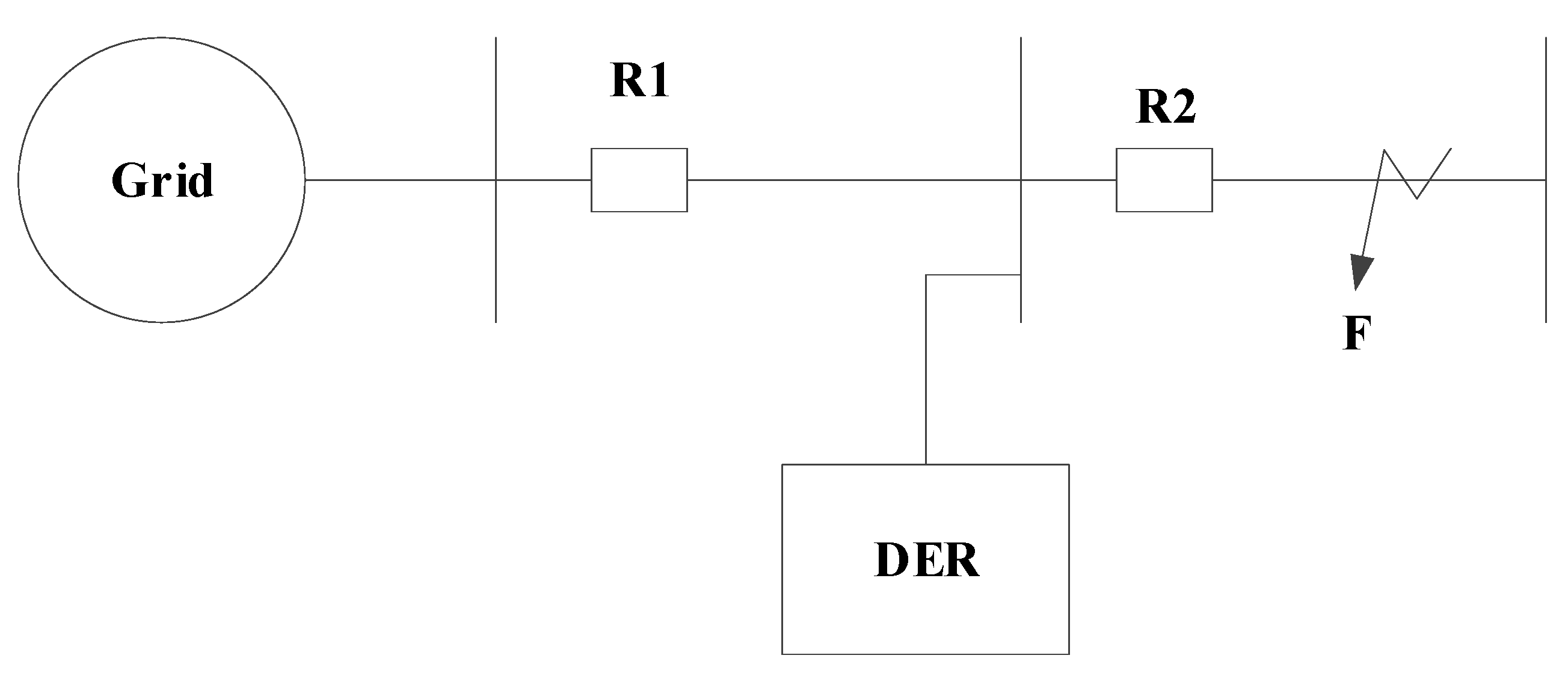
2.2. Direction of Power Flow in the Relays
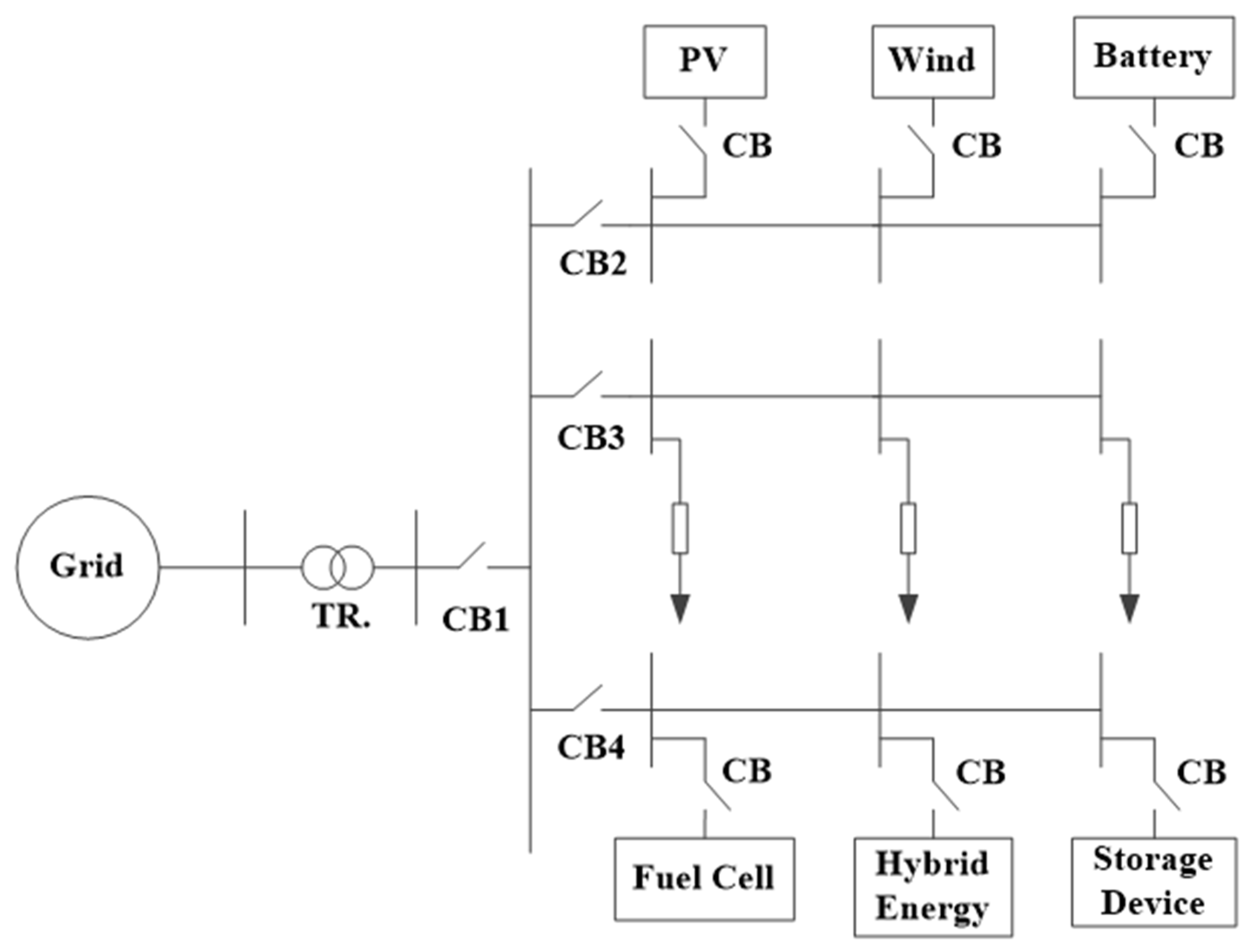
2.3. Architecture of the System
2.4. Nuisance Tripping
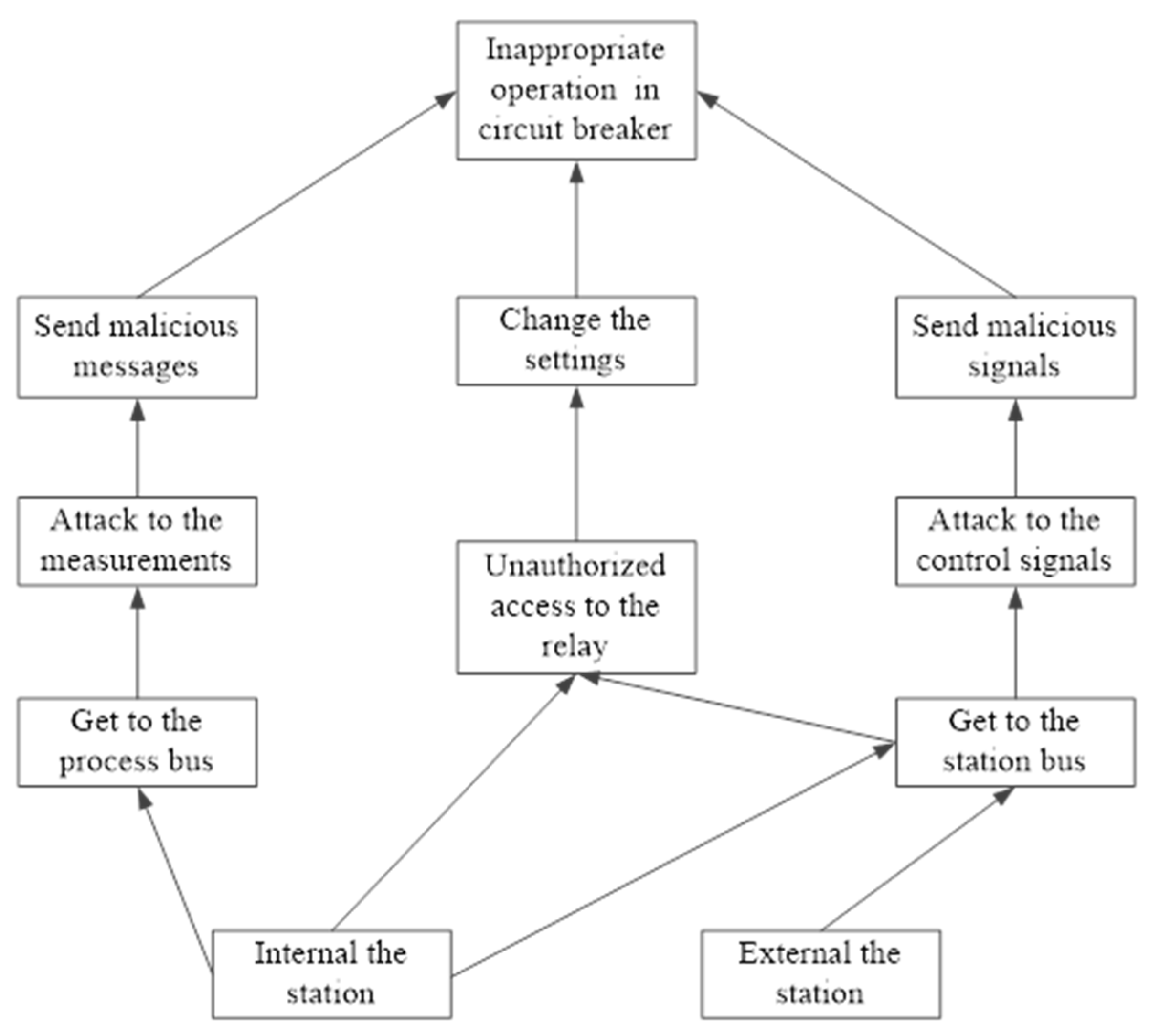
2.5. Protection Blinding Phenomena
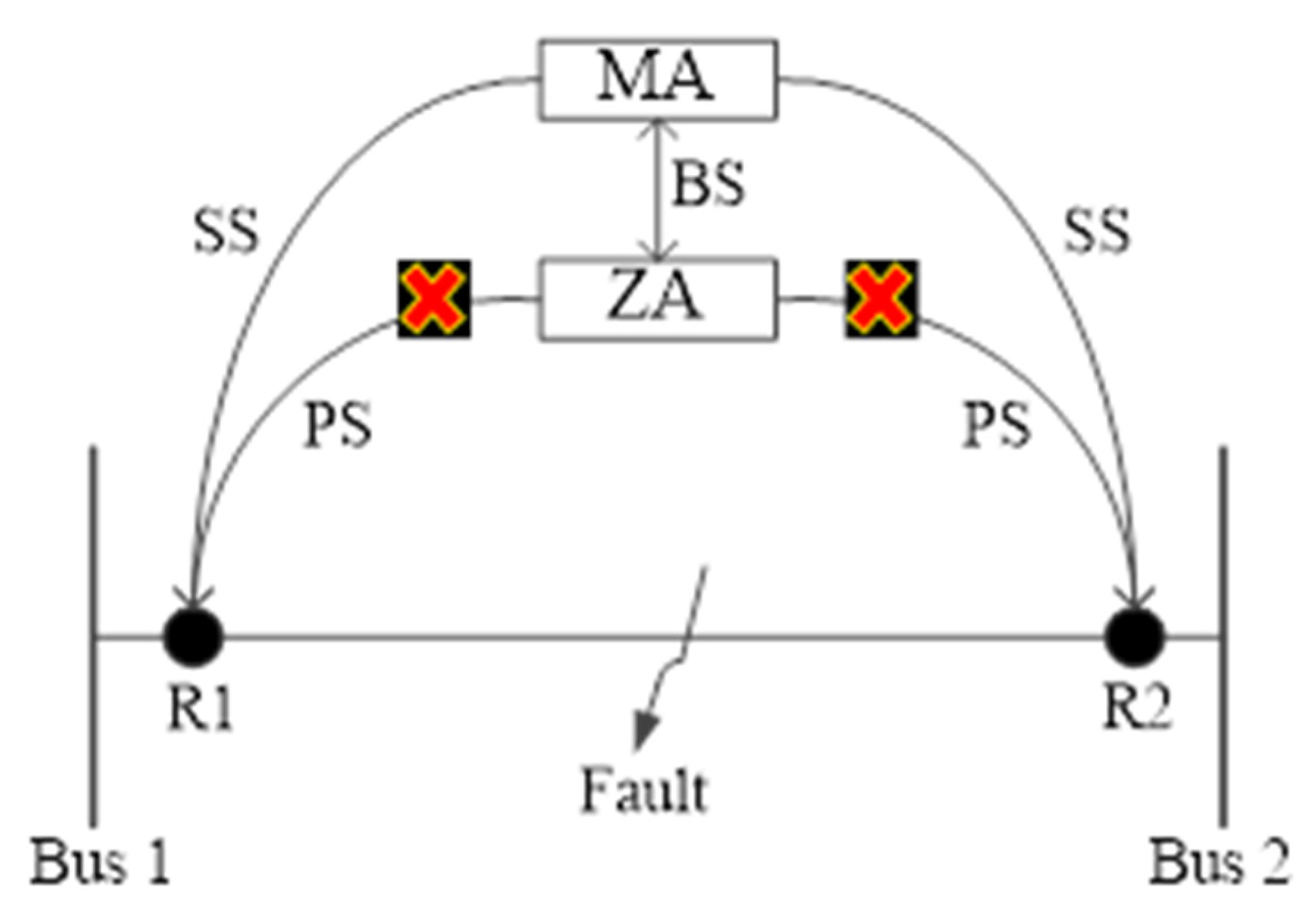
3. Platform of the Protection Technique
3.1. IEC 61850 Communication Protocol
3.2. Proposed Protection System
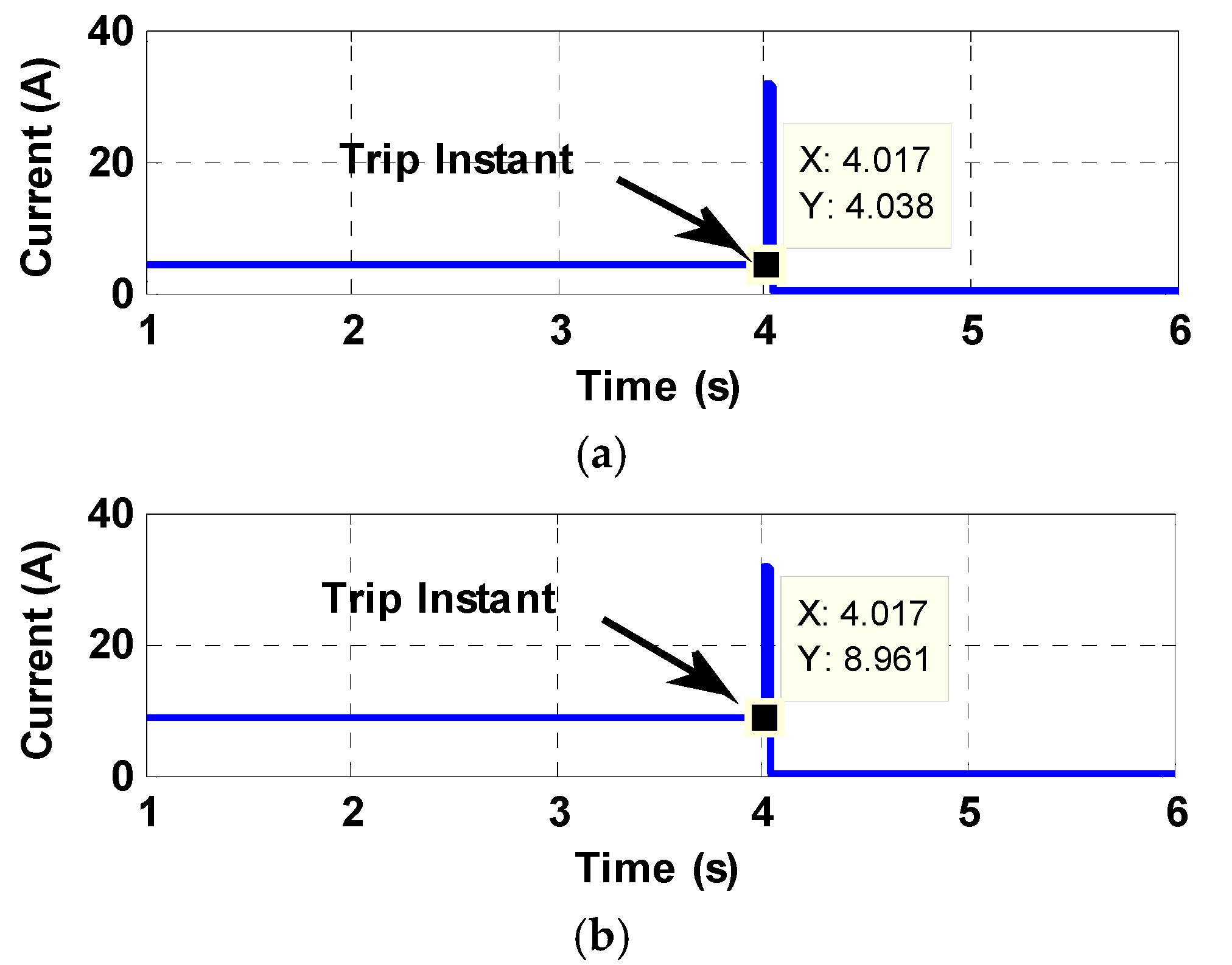
4. Simulation Case Studies
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ameli, A.; Hooshyar, A.; El-Saadany, E.F. Development of a cyber resilient line current differential relay. IEEE Trans. Ind. Inform. 2018, 15, 305–318. [Google Scholar] [CrossRef]
- Fawzy, N.; Habib, H.F.; Mokhtari, S. Performance Evaluation of Electric Vehicle Model under Skid Control Technique. World Electr. Veh. J. 2021, 12, 83. [Google Scholar] [CrossRef]
- Yan, Y.; Qian, Y.; Sharif, H.; Tipper, D. A survey on cyber security for smart grid communications. IEEE Commun. Surv. Tuts. 2012, 14, 998–1010. [Google Scholar] [CrossRef] [Green Version]
- Hahn, A.; Ashok, A.; Sridhar, S.; Govindarasu, M. Cyber-physical security testbeds: Architecture, application, and evaluation for smart grid. IEEE Trans. Smart Grid 2013, 4, 847–855. [Google Scholar] [CrossRef]
- Hong, J.; Liu, C.C.; Govindarasu, M. Integrated anomaly detection for cyber security of the substations. IEEE Trans. Smart Grid 2014, 5, 1643–1653. [Google Scholar] [CrossRef]
- Bulbul, R.; Gong, Y.; Ten, C.W.; Ginter, A.; Mei, S. Impact quantification of hypothesized attack scenarios on bus differential relays. In Proceedings of the 2014 Power Systems Computation Conference, Wroclaw, Poland, 18–22 August 2014; pp. 1–7. [Google Scholar]
- Jahromi, A.A.; Kemmeugne, A.; Kundur, D.; Haddadi, A. Cyber physical attacks targeting communication-assisted protection schemes. IEEE Trans. Power Syst. 2020, 35, 440–450. [Google Scholar] [CrossRef]
- Habib, H.F.; Fawzy, N.; Brahma, S. Performance Testing and Assessment of Protection Scheme Using Real-Time Hardware-in-the-Loop and IEC 61850 Standard. IEEE Trans. Ind. Appl. 2021, 57, 4569–4578. [Google Scholar] [CrossRef]
- Liu, X.; Shahidehpour, M.; Li, Z.; Liu, X.; Cao, Y.; Li, Z. Power system risk assessment in cyber attacks considering the role of protection systems. IEEE Trans. Smart Grid 2017, 8, 572–580. [Google Scholar] [CrossRef]
- Habib, H.F.; Fawzy, N.; Esfahani, M.M.; Mohammed, O.A. Enhancement of Protection Scheme for Distribution System Using the Communication Network. In Proceedings of the 2019 IEEE Industry Applications Society Annual Meeting, Baltimore, MD, USA, 29 September–3 October 2019. [Google Scholar]
- Yang, Y.; Jiang, H.T.; McLaughlin, K.; Gao, L.; Yuan, Y.B.; Huang, W.; Sezer, S. Cybersecurity test-bed for IEC 61850 based smart substations. In Proceedings of the IEEE Power Energy Society General Meeting, Denver, CO, USA, 26–30 July 2015; pp. 1–5. [Google Scholar]
- Kabir-Querrec, M.; Mocanu, S.; Thiriet, J.; Savary, E. A Test bed dedicated to the Study of Vulnerabilities in IEC 61850 Power Utility Automation Networks. In Proceedings of the 2016 IEEE 21st International Conference on Emerging Technologies and Factory Automation (ETFA), Berlin, Germany, 6–9 September 2016; pp. 1–4. [Google Scholar]
- Esmaeilian, A.; Popovic, T.; Kezunovic, M. Transmission line relay mis-operation detection based on time-synchronized field data. Electr. Power Syst. 2015, 125, 174–183. [Google Scholar] [CrossRef]
- Habib, H.F.; Fawzy, N.; Mohammed, O.A. A Fault Clearing for Microgrid Protection System Utilized the Communication Network with Centralized Approach. In Proceedings of the 2019 SoutheastCon, Huntsville, AL, USA, 11–14 April 2019. [Google Scholar]
- Mokhtari, S.; Abbaspour, A.; Yen, K.K.; Sargolzaei, A. Neural Network-Based Active Fault-Tolerant Control Design for Unmanned Helicopter with Additive Faults. Remote Sens. 2021, 13, 2396. [Google Scholar] [CrossRef]
- Habib, H.F.; Fawzy, N.; Esfahani, M.M.; Mohammed, O.A.; Brahma, S.; Habib, N.F.K. An Enhancement of Protection Strategy for Distribution Network Using the Communication Protocols. IEEE Trans. Ind. Appl. 2020, 56, 1240–1249. [Google Scholar] [CrossRef]
- Fawzy, N.; Habib, H.F.; Mohammed, O.; Brahma, S. Protection of Microgrids with Distributed Generation based on Multiagent System. In Proceedings of the 2020 IEEE International Conference on Environment and Electrical Engineering and 2020 IEEE Industrial and Commercial Power Systems Europe (EEEIC/I&CPS Europe), Madrid, Spain, 9–12 June 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Shah, R.; Goli, P.; Shireen, W. Adaptive Protection Scheme for a Microgrid with High Levels of Renewable Energy Generation. In Proceedings of the 2018 Clemson University Power Systems Conference (PSC), Charleston, SC, USA, 4–7 September 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Habib, H.; Fawzy, N.; Brahma, S. Hardware in the Loop Testing of a Protection Scheme for Microgrid using RTDS with IEC 61850 Protocol. In Proceedings of the 2020 IEEE Industry Applications Society Annual Meeting, Detroit, MI, USA, 10–16 October 2020; pp. 1–8. [Google Scholar] [CrossRef]



| Fault | Relay | Side | Direction |
|---|---|---|---|
| L12 | R1 R2 | 1 1 | L U |
| L24 | R2 R4 | 3 1 | U L |
| L25 | R2 R5 | 2 3 | U L |
| L15 | R1 R5 | 1 1 | U L |
| L34 | R3 R4 | 1 3 | U L |
| L45 | R4 R5 | 1 3 | U U |
| L47 | R4 R7 | 3 1 | U L |
| L78 | R7 R8 | 3 1 | U L |
| L79 | R7 R9 | 1 1 | U L |
| L56 | R5 R6 | 1 1 | U L |
| L9–10 | R9 R10 | 1 3 | U U |
| L9–14 | R9 R14 | 3 3 | U L |
| L10–11 | R10 R11 | 1 3 | L L |
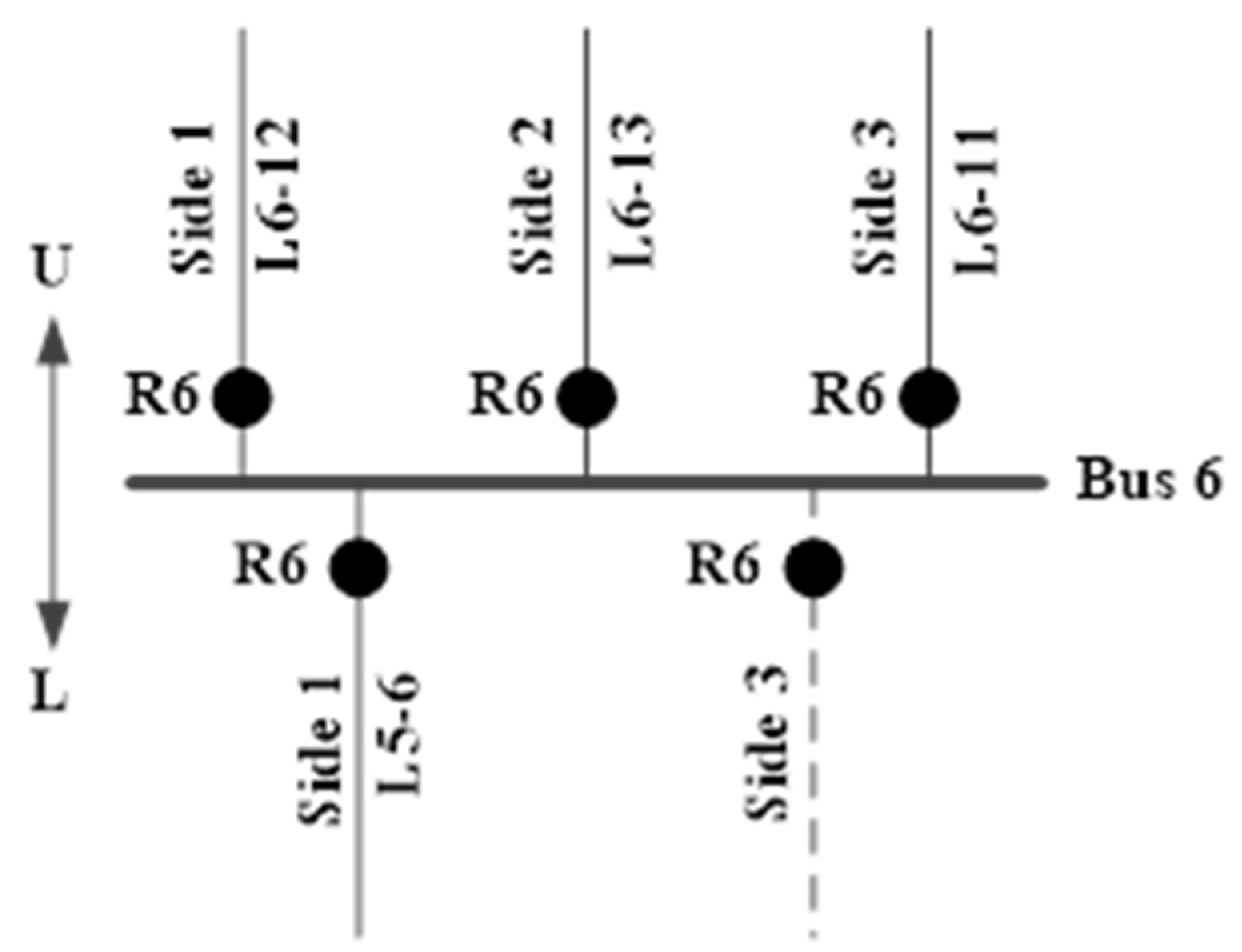
| L6–11 | R6 R11 | 3 1 | U L |
| L6–12 | R6 R12 | 1 1 | U L |
| L12–13 | R12 R13 | 3 1 | L L |
| L6–13 | R6 R13 | 2 2 | U L |
| L13–14 | R13 R14 | 3 1 | L L |
| Fault | Primary | Secondary | ||||
| R | S | D | R | S | D | |
| L12 | R1 R2 | 1 1 | L U | R1 R2 | 1 1 | L L |
| L24 | R2 R4 | 3 1 | U L | R2 R4 | 1 1 | L U |
| L25 | R2 R5 | 2 3 | U L | R2 R5 | 1 3 | L U |
| L15 | R1 R5 | 1 1 | U L | R1 R5 | 1 3 | L L |
| L34 | R3 R4 | 1 3 | U L | R3 R4 | 1 3 | L U |
| L45 | R4 R5 | 1 3 | U U | R4 R5 | 1 3 | L L |
| L47 | R4 R7 | 3 1 | U L | R4 R7 | 3 3 | L U |
| L78 | R7 R8 | 3 1 | U L | R7 R8 | 1 1 | L L |
| L79 | R7 R9 | 1 1 | U L | R7 R9 | 1 1 | L U |
| L56 | R5 R6 | 1 1 | U L | R5 R6 | 1 1 | L U |
| L9–10 | R9 R10 | 1 3 | U U | R9 R10 | 1 1 | L L |
| L9–14 | R9 R14 | 3 3 | U L | R9 R14 | 1 1 | L L |
| L10–11 | R10 R11 | 1 3 | L L | R10 R11 | 3 1 | L L |
| L6–11 | R6 R11 | 3 1 | U L | R6 R11 | 2 3 | U L |
| L6–12 | R6 R12 | 1 1 | U L | R6 R12 | 1 3 | L L |
| L12–13 | R12 R13 | 3 1 | L L | R12 R13 | 1 2 | L L |
| L6–13 | R6 R13 | 2 2 | U L | R6 R13 | 1 1 | U L |
| L13–14 | R13 R14 | 3 1 | L L | R13 R14 | 2 3 | L L |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fawzy, N.; Habib, H.F.; Mohammed, O. IEC 61850-Based Communication Networks of Distribution System against Cyber and Physical Failures. World Electr. Veh. J. 2021, 12, 155. https://doi.org/10.3390/wevj12030155
Fawzy N, Habib HF, Mohammed O. IEC 61850-Based Communication Networks of Distribution System against Cyber and Physical Failures. World Electric Vehicle Journal. 2021; 12(3):155. https://doi.org/10.3390/wevj12030155
Chicago/Turabian StyleFawzy, Nevin, Hany F. Habib, and Osama Mohammed. 2021. "IEC 61850-Based Communication Networks of Distribution System against Cyber and Physical Failures" World Electric Vehicle Journal 12, no. 3: 155. https://doi.org/10.3390/wevj12030155
APA StyleFawzy, N., Habib, H. F., & Mohammed, O. (2021). IEC 61850-Based Communication Networks of Distribution System against Cyber and Physical Failures. World Electric Vehicle Journal, 12(3), 155. https://doi.org/10.3390/wevj12030155








