1. Introduction and Motivations
Digital copyright protection is one of the most pressing needs of the current Internet due to the economic losses it causes to companies that produce multimedia content. The enormous investments made in developing tools for protecting content distributed on the Internet are nullified mainly by the growing and rapid evolution of network and multimedia technologies through which it is possible to easily duplicate and distribute on the network originally protected content without reducing its perceived quality. Added to this problem is the more current one relating to the need to identify the creators of multimedia content present on the Internet so as to be able to distinguish such original content from that illegally created through the use of artificial intelligence.
Many of the solutions proposed to solve the problem of digital copyright are based on the use of “digital rights management” (DRM) systems [
1,
2,
3], which try to limit the use of digital content only to those who have regularly purchased it. However, these systems cannot prevent legitimate purchasers of content from downloading and spreading it online, thus making the protection system ineffective.
On the other hand, content providers use watermarking protocols to discourage legitimate buyers of content from spreading it online [
4]. These protocols implement digital copyright protection by exploiting the principle of deterrence. They are based on inserting a digital watermark in each document sold. The inserted watermark is imperceptible and represents a fingerprint uniquely linked to the seller of the content, the buyer, and the purchase transaction. The watermark thus ensures that the content represents a personalized and unique copy for the buyer. The protocol then defines the purchase transaction scheme capable of guaranteeing that only that buyer obtains his personalized copy of the purchased content. In this way, if such protected content is found in the possession of a user without the relative purchase title, it is possible to trace its legitimate buyer who has made an illegal sharing. The deterrent action, therefore, consists in the fact that the greater the sharing of protected content on the network, the greater the possibility that an illegally distributed copy will be found and allow its owner, the only one who can have done the initial sharing, to be punished.
Watermarking protocols developed in recent years mostly follow the “buyer-seller” scheme [
4,
5]. They try to guarantee the security of purchase transactions between buyers and sellers and the protection of digital copyright without having to resort to a “trusted third party” (TTP) and without having to request complex cryptographic actions from buyers. In this sense, an innovative solution is now represented by protocols based on blockchains and smart contracts [
6]. Blockchains can be used in place of TTPs as distributed ledgers capable of publishing data on digital content purchase transactions, guaranteeing their immutability and verifiability [
7,
8]. Smart contracts, for their part, can be used to execute the code that defines the scheme of interactions envisaged by watermarking protocols. Also in this case, the code included in smart contracts, once published by the blockchain, becomes de facto immutable and is executed automatically when predefined conditions occur [
9,
10].
Although promising and able to satisfy the main requirements of use and security [
4], watermarking protocols based on blockchains and smart contracts suffer from the main limitations exhibited by these technologies [
11,
12,
13,
14,
15,
16,
17]. These limitations mainly concern the following:
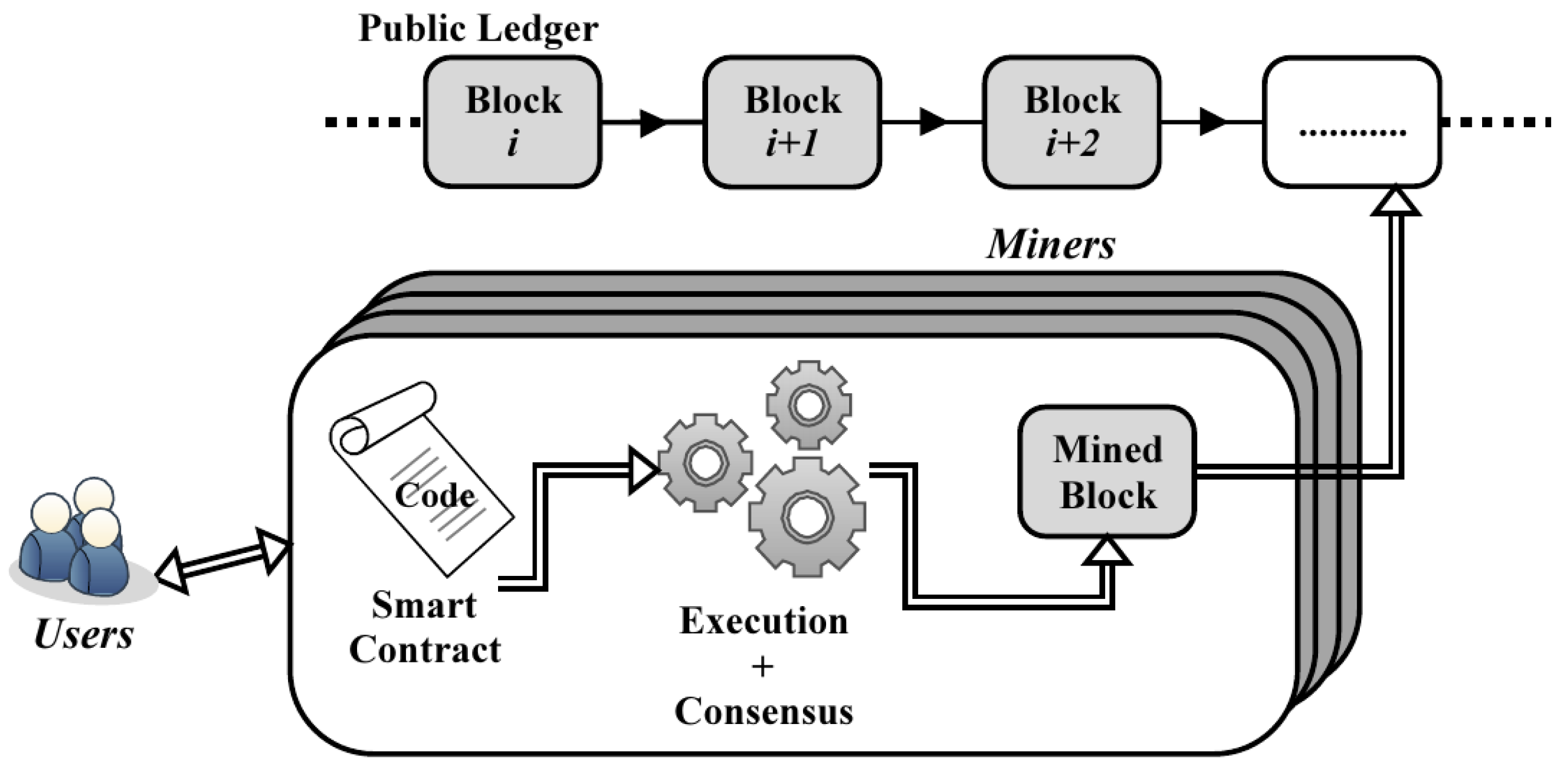
The poor performance in terms of the number of transactions that a blockchain can validate in the unit of time;
The lack of confidentiality in the execution of smart contracts, which makes the input/output parameters, the state, and the code of smart contracts accessible to blockchain nodes;
The impossibility of smart contracts to execute complex code due to the economic execution models implemented by blockchains.
Such limitations end up, in fact, making the use of blockchains and smart contracts in the implementation of watermarking protocols difficult and disadvantageous.
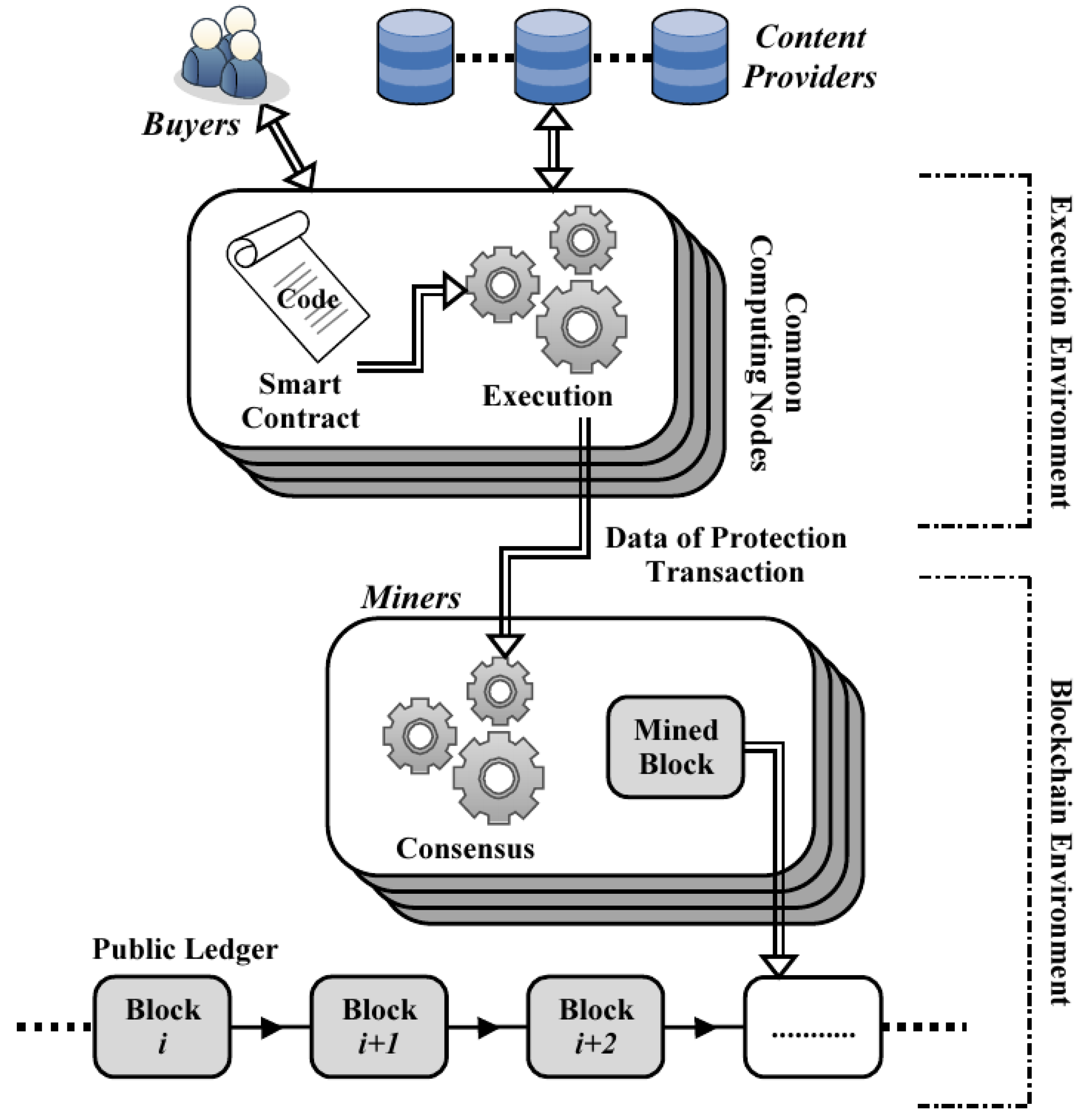
This paper presents an evolution of the watermarking protocol described in [
18]. The new version was necessary to better adapt the protocol to an implementation that follows the “layer-2” blockchain-based execution scheme, in which the execution of smart contracts is separated from the achievement of consensus for the generated transactions [
8,
13,
19,
20]. In particular, the execution of smart contracts occurs “off-chain”, within “trusted execution environments” (TEEs), while the achievement of consensus is guaranteed by the blockchain, to which the results of the execution of smart contracts are sent in terms of transactions to be validated [
19]. In this way, the off-chain execution of smart contracts within TEEs allows both to achieve the objective of confidentiality and to drastically reduce the execution costs, in terms of “gas”, to those related solely to the achievement of consensus, while increasing the number of transactions that can be validated in the unit of time [
8,
13,
16,
17,
21].
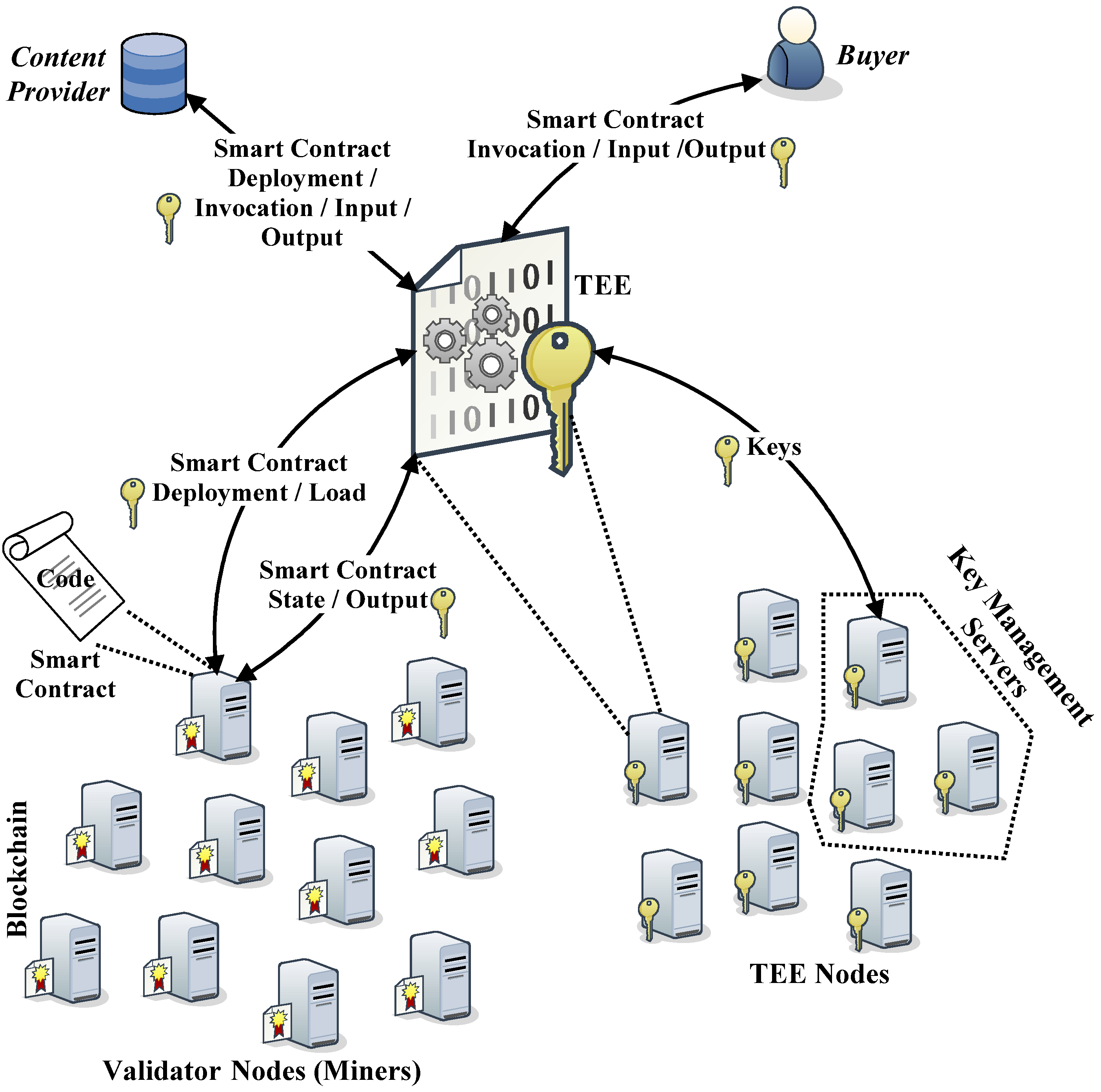
4. The Execution Model
The proposed watermarking protocol is based on the confidential execution of smart contracts according to a layer-2 scheme, in which the blockchain is used solely to validate the transactions produced by the smart contracts [
14,
19] (see
Figure 4). In this scheme, it is necessary to differentiate the processing nodes that are responsible for the execution of the smart contracts, and which must therefore be equipped with TEE, from the blockchain nodes, which instead act as simple “validators” of the generated transactions and which can be common processing nodes capable of executing the consensus algorithm implemented by the blockchain.
The execution model, therefore, provides for two types of entities: TEE nodes and validator nodes.
The former execute the contracts in the TEE and generate the appropriate attestations of correct execution and generation of results. The only requirement is that they can implement the TEE. Some of them are also expected to act as servers to manage the encryption keys used by the TEE nodes. In particular, these nodes implement specific distributed protocols for key management.
The latter are the blockchain nodes responsible for managing the public ledger and executing the implemented consensus algorithm. They are part of a public blockchain and validate the transactions generated by the execution of smart contracts.
The proposed protocol is then implemented by executing a smart contract. The contract is initially registered in the blockchain after some preliminary actions between the smart contract developer and one of the TEE nodes. These actions are necessary to guarantee the confidentiality of the execution of the contract. They are performed in the TEE and allow the following:
Generation of the public-private key pair with which to encrypt the input/output parameters of the contract;
Generation of the symmetric key with which to encrypt the state information produced by the execution of the contract;
Generation of the attestation of the correct execution of the previous actions.
At the end of this phase, the smart contract is published on the blockchain, with the information necessary for the invocation, such as the public key associated with the contract.
To invoke the contract, users first retrieve from the blockchain the information needed to encrypt the parameters to be passed to the contract, such as the previously generated public key. They then invoke the contract by passing the invocation parameters encrypted with the public key. These parameters include, among others, the symmetric keys with which the contract can encrypt any output parameters to be returned to users.
The contract is then executed confidentially on one or more TEE nodes. At the end of the execution, the TEE nodes involved generate the results, status information, and attestations of correct execution. The formers are encrypted with the symmetric keys previously sent by the users, while the latter are encrypted with the symmetric key generated in the initial phase by the TEE node. Everything is passed to the blockchain, which publishes the information received once the validator nodes have reached consensus.
5. Basics Assumptions
The proposed watermarking protocol is based on the following assumptions.
First, the entities participating in the protocol and all communications among them are secured using a public key infrastructure (PKI) and Transport Layer Security (TLS).
Digital contents and watermarks are represented according to block diagrams of the type
and
, respectively. The elements of
W are binary values that usually represent fingerprinting anti-collusion codes [
22,
23,
24].
Encryption and watermarking processes are represented by block-wise functions. As a consequence, the encryption
E of a content
under the key
k can be calculated as
Likewise, the insertion of the watermark
W into the content can be calculated as
in which
is the watermarked content, and the symbol ⊕ represents the insert function [
22].
Furthermore,
denotes an encryption function “homomorphic” with respect to the watermark insertion [
25]. Therefore, the watermark can be directly inserted into the encrypted domain according to the following formula [
26]:
In particular, the function
has to be “probabilistic” and “semantically secure”. This means that the knowledge of a ciphertext does not provide any useful information on the plaintext to an adversary having only a reasonably restricted computational power represented by polynomial resources. Furthermore,
can be limited to homomorphic encryption schemes that support addition or multiplication since such operations are functionally complete sets over finite sets and are sufficient to implement the most common and safe watermarking algorithms [
25]. Therefore, if
x is an element of
X and
w is an element of
W, the multiplicatively homomorphic encryption schemes ensure that [
27]
whereas the additively homomorphic encryption schemes ensure that [
28,
29]
Finally, nodes that execute smart contracts must provide a CPU-based implementation of the TEE, such as the one provided by INTEL Software Guard eXtensions (SGX) [
30,
31,
32]. This implementation must guarantee the confidentiality and integrity of the computation performed and must also be able to provide proof, in the form of attestations, of its correctness. To this end, following the example of the INTEL SGX system, a TEE node must generate an attestation each time it executes a smart contract. Then, the TEE node obtains proof of the validity of the attestation by contacting a specific service, such as the INTEL Attestation Service (IAS). The IAS receives the attestation and verifies it. If the attestation received is considered valid, the IAS returns a certification
consisting of the attestation itself digitally signed by the IAS.
6. The Protocol
The proposed watermarking protocol is of the “buyer-seller” type and is based on a “buyer-friendly” approach [
4]. It is implemented by a smart contract executed by TEE nodes. The execution result is then validated by the blockchain nodes (miners) according to the layer-2 scheme described in
Section 4. In particular, the execution of the smart contract consists of two phases.
In the first phase, the smart contract is activated by the content provider and the buyer and generates the tokens needed to start inserting the watermark into the content to be protected. This phase ends with publishing a series of information preparatory to activating the next phase. All information is exchanged and published in encrypted form to guarantee complete confidentiality.
In the second phase, the smart contract generates the final information constituting the content purchase license published in the blockchain ledger. This phase can be activated only if the information sent as input to the smart contract by the buyer and the content provider is consistent with that published previously, downstream of the first phase.
The proposed protocol does not employ any TTP and, thanks to the layer-2 execution scheme, executes the smart contract entirely “off-chain”, within the enclave provided by the TEE. It can be described at a high level as follows: (1) the protocol is implemented by a smart contract that is published by a blockchain (); (2) the protocol can be used by any seller or content provider () who wishes to protect its content distributed on the web; (3) by activating the smart contract, and the buyer () enable the execution of the watermarking protocol, after which the purchased content is released in encrypted form and protected by the watermark; (4) , at the end of the execution of the smart contract, decrypts the received content, obtaining its version with the customized protection; (5) the smart contract takes care of generating all the tokens and information needed to protect the content without resorting to TTP; (6) s are able, once they have found a suspicious copy of their content sold on the Internet, to trace it back to the original purchaser and establish whether there has been illicit distribution.
The proposed protocol comprises the
protection protocol and the
identification and arbitration protocol.
Table 1 defines the symbols used to describe the protocol.
6.1. The Protection Protocol
The protection protocol consists of a preliminary phase through which the smart contract that implements the protocol is deployed on . The deployment can be performed by and makes the smart contract code immutable and public so that anyone can evaluate its correctness and the level of security offered. This phase makes the contract available for subsequent invocations through which the watermarking protocol is executed to protect the contents distributed by .
6.1.1. Deployment
The deployment phase, whose scheme is shown in
Table 2, starts with
contacting one of the computation nodes equipped with TEE (
). This node is part of the computation structure and is responsible for executing off-chain the smart contract that implements the watermarking protocol. The structure must be composed of computation nodes, all equipped with TEE. Some of these nodes exclusively perform the functions of servers to manage the keys necessary for the confidential execution of the smart contract (see
Figure 4). The nodes, similarly to those of a public blockchain, participate voluntarily and are remunerated during the execution phase of the smart contract. It is important to note that it is possible to carry out multiple deployments of the smart contract on the blockchain. This makes it possible to have multiple concurrent executions of the same copy of the smart contract, thus increasing the number of purchase transactions in the unit of time depending on the available TEE nodes.
initially sends the contract code to a in message , which loads it into its secure enclave. then creates the contract identifier and sends it to one of the TEE nodes that manage the encryption keys, indicated by , in the message . This node generates three keys: a first public-private key pair (, ) to be used to exchange encrypted data with the contract when it is executed in the TEE; and a secret key used by the contract to encode the state information generated by the execution.
Upon receiving the keys in message , generates the initial state associated with the contract and encrypts it, creating the token . Then, generates an attestation, denoted by , that proves both the correct initialization of the contract and the association of the public key to the contract.
At this point, obtains a proof of correctness of by contacting a specific official attestation service, such as the Intel Attestation Service (IAS) for SGX-based TEE systems, which performs the verification and returns a digitally signed certification of correct execution attestation in TEE, denoted by .
The deployment phase ends with sending message and obtaining the publication on of the contract, together with the , its initial encrypted state , the certification of the correct execution of the deployment , and the public key associated with the contract.
6.1.2. Protection
This phase, whose scheme is shown in
Table 3, starts when
requests the purchase of content
X from
in message
, also sending its unique identifier
. In particular,
can be a personal digital certificate, an anonymous digital certificate, a credit card reference, or any other document that can refer to
unambiguously [
18].
generates a unique descriptor of X, denoted by , and a timestamp needed to identify the ongoing transaction. Then, generates a secret key to be used only in this transaction, which must be used by the smart contract to encrypt the output data to be returned to . also reads from the identifier and the corresponding public key relating to the previously deployed contract that implements the watermarking protocol. Finally, chooses one or more TEE nodes to which to delegate the execution of the contract. Assuming, for simplicity, that the contract is executed by a single TEE node, indicated by , sends it the message , which contains two tokens: the and the set of , , , , and the payment specification , all encrypted with the contract’s public key . In particular, the specification allows to be remunerated for the execution activity performed. then sends the reference of , , , , and to in message .
Similarly to , generates its secret key to be used only in this transaction and needed to receive the encrypted output data of the smart contract. Then, encrypts , , , and with the key , and sends the encrypted token and to in message .
Once messages and are received, starts the execution in TEE of the contract identified by . fetches the contract from , together with the associated information , , and , and loads them into its TEE. sends message to . Then, receives in response message , which contains the keys and , which can be used to decrypt the current state and the information received as input related to the contract.
, once decrypted, checks the consistency of the information contained in messages and . If the check is passed, continues the execution of the contract in its secure enclave. generates three tokens: (1) a public-private key pair (, ) to be used exclusively in the current transaction; (2) a “nonce” N consisting of a binary string; and (3) the token obtained by encrypting N with and a “privacy homomorphic” cryptosystem with respect to the watermarking algorithm used.
At this point,
generates the block
and encrypts it with the key
, generating
. Then,
calculates the digest of
, denoted by
, and obtains the certification of the correct execution of this first computational phase, denoted by
.
concludes this phase by publishing on the information generated and represented by , , , and . Then, sends two messages, and , to and , respectively. In the first one it includes the tokens , , , encrypted with the symmetric key of ; in the second one it includes the tokens and encrypted with the symmetric key of . In this way, and obtain the output information generated by executing this first phase of the contract in confidential form.
receives in
the information needed to create the customized protection of
X to be associated with
and the current transaction. For this purpose,
generates the watermark
, which consists of the union of an anti-collusion code and an error-correcting code needed to correct any errors that may occur while extracting the watermark from
X. Then,
encrypts
X and
with the key
and with the same homomorphic encryption system used to obtain
. Once the tokens
and
have been generated,
can proceed to insert the watermark directly into the encrypted domain as indicated in the previous
Section 5. In particular, the watermark
W to be inserted is given by the union of the two binary strings
and
N and can be represented with
, according to a block diagram. Therefore,
The insertion of
W into
X is done according to the following expression:
sends the encrypted and protected content to in message . Then, starts the second phase of contract execution by sending message to , which includes , , , and the encrypted token . After sending the message, saves the tokens , , , , , and in its database, associating as the lookup key.
Also , after receiving the message , sends to the message , which contains , , , and the encrypted token .
Once messages
and
are received,
starts the execution of the contract in its TEE. It accesses
with the
and
related to the ongoing transaction and collects the tokens
and
. Then,
extracts the information contained in
and compares it with that received in messages
and
. If the information matches,
will allow the completion of the payment phase and publish the final license for the purchase of content
X by
on
. This license is represented by the tokens
and
, and the digest
. Finally,
obtains a proof of correctness of
by contacting IAS and sends the private key
to
so as to enable the decryption of
and the consequent generation of the personalized content
according to the following expression:
6.1.3. The Identification and Arbitration Protocol
This protocol can be executed by
whenever it detects a copy of its content
X suspected of having been illegally distributed on the Internet (see
Table 4). In this way,
can identify, with statistical certainty, the legitimate purchaser of
X who has illegally distributed the purchased copy.
extracts the watermark
from the suspicious copy, indicated by
. It uses
as a search key and, if it finds a match [
33], it obtains the corresponding tokens
,
,
,
,
, and
. At this point,
calculates the digest
and accesses
to obtain the digest corresponding to the transaction
, equal to
. If the two digests coincide, then it turns out that
and that
, identified through his reference
, can be considered guilty of having illicitly distributed his regularly purchased copy.
7. Security Analysis
Analyzing the security of the proposed protocol is very difficult due to the many components used. However, leaving aside the most common ones, such as the TLS protocol for communications, the symmetric or public-key encryption algorithms considered “semantically secure”, or the common PKI based on digital certificates, it is evident that the level of security that the protocol can achieve depends directly on three basic components that enable its implementation: the watermark insertion technique, the CPU-based implementation of the TEE, and the key management system used by the smart contracts. In the following, their impact on the protocol’s security is preliminarily discussed.
7.1. Basic Components and Their Impact on Security
The first component that directly influences the level of security the protocol can reach is represented by the watermark insertion technique. In fact,
’s ability to identify a dishonest buyer depends on the ability of the watermark inserted in the content to resist both attacks by malicious users and manipulations conducted legitimately by the buyer himself. In this regard, it is possible to hypothesize the use of sufficiently secure and robust watermark insertion techniques, for which the removal, even partial, of the watermark determines an evident degradation of the perceived quality of the protected content, so much so as to render it substantially devoid of economic value. Insertion techniques with such characteristics are those, for example, based on ”spread spectrum” (SS) algorithms or based on “quantization index modulation” (QIM), which have shown overall positive results [
22,
34,
35].
Another critical component for the security of the proposed protocol is represented by the CPU-based implementation of the TEE, which, as reported in
Section 5, must guarantee confidentiality, integrity, and proof of correctness in the form of attestations of the computation performed. In this regard, it is important to note that current implementations of the TEE, such as that provided by INTEL SGX [
31], are characterized by several security problems [
19,
30,
32].
For example, the first problem is represented by the possibility of a malicious to interrupt the execution in TEE of the smart contract that implements the proposed protocol. In this case, the purchase transaction in progress is canceled and must be repeated. This is because the protocol considers transactions to have no internal state. They are complete only with publishing the final purchase license on the blockchain. Such a condition may seem penalizing from the point of view of the protocol’s efficiency because it does not allow recovery actions. On the other hand, it constitutes a valid security countermeasure because it prevents the malicious acquisition of information relating to the interrupted transition.
Other problems may arise from the manipulation of I/O operations through which data is transferred to and from the TEE’s enclave. In fact, the exchanged information could be acquired or modified illegally by the processes running on . However, even in this case, the protocol is not vulnerable because all data entering or leaving the enclave are always encrypted, and their freshness is ensured by the transaction identifiers managed by the protocol.
In addition, several security problems caused by side-channel attacks are documented in the literature. These are specific problems caused by malicious users who try to manipulate the data managed by the TEE. However, it is impossible to identify generalized solutions for these problems, but ad hoc solutions are needed, mostly based on using cryptographic primitives.
In reality, it is necessary to observe that the proposed protocol can correctly complete a content purchase transaction in the presence of at least one honest
. In this hypothesis, the validator nodes can certify the correct execution of the transaction by executing a specific algorithm usually present in the “layer-2” execution models (see
Section 4 and
Figure 4). Such an algorithm is executed before reaching consensus in the blockchain and allows comparing the results of the
s’ executions in order to identify any malicious behavior [
12,
14,
36]. In fact, the presence of at least one honest
allows validator nodes to highlight discrepancies in the different executions and thus to identify the correct execution. However, to minimize the risk of incorrect executions by
s, two useful measures can be adopted.
The first is based on implementing an economic model that incentivises honest s and imposes penalties on malicious ones. In this way, the participation of malicious s would be discouraged or make them less numerous than honest ones. Such a condition would make it easy to produce correct transactions and identify incorrect ones, thus eliminating malicious s from the pool of those available to execute the protocol.
The second provides a “permissioned” approach for s, which can join the protocol execution pool only after their honesty has been assessed. In this case, the risks of possible attacks on the TEE’s enclave would be drastically reduced, even if this approach is more restrictive than the “permissionless” one used for blockchain nodes.
As it appears from the considerations reported so far, the proposed protocol still manages to be immune to attacks on the TEE’s enclave, although the proposed measures can improve its execution and mitigate the consequences of the attacks. Moreover, despite the large attack surfaces, TEEs are still considered the basis for confidential executions in secure enclaves [
19,
30,
32], and several important companies, such as INTEL and AMD, are investing in this area. Therefore, the next proposed implementations will likely be characterized by increasingly limited attack surfaces, so as to make such implementations substantially secure [
17,
31,
32].
The last critical component is represented by the system of servers responsible for managing the keys used by the smart contract that implements the proposed protocol. By virtue of the importance of the function performed, these servers should be correctly managed
s with a good reputation. However, the protocol is not based on specific assumptions, and only assumes that the servers implement the protocol described in [
14], or at least an equivalent one, so as to satisfy the security, confidentiality, and availability requirements that enable the watermarking protocol to be executed in a secure manner.
7.2. Assumptions
Limiting the analysis to the watermarking protocol only and based on what is reported above, it is possible to assume the following description:
sells X to ;
implements the ledger that publishes the smart contract responsible for executing the watermarking protocol;
is a computation node equipped with TEE in whose enclave it executes the smart contract that implements the off-chain protocol in confidential form;
The results of the execution of the protocol are published in encrypted form on ;
can autonomously ascertain whether has illegally distributed the copy received with his/her personalized protection.
Furthermore, the entities participating in the protocol are assumed to have the following behavior:
and do not distribute pirated copies of the contents in their possession when they are not corrupted;
is considered an “honest-but-curious” entity [
37] whose nodes (miners), while being able to access some of the information managed by the protocol, are still forced to follow the rules set by the protocol in accordance with the concept of a public blockchain;
, when executing the smart contract in its TEE, guarantees correctness, integrity, and confidentiality, and it is supposed to be incorruptible;
correctly executes the key management protocol in its TEE without compromising the keys;
and
can be corrupted only “statically”, i.e., deciding which of the two entities is corrupt is made before running the protocol and can no longer be changed [
37].
Consistent with what has been reported and in the absence of corrupt entities, the protocol allows to receive from the chosen content X protected by the insertion of a personalized watermark. Once extracted from a copy of X, the watermark allows the link of the content to the legitimate purchaser, the content provider, and the purchase transaction, thus carrying out a deterrent action against the illegal sharing of content on the network.
If or are corrupted, the protocol can always take appropriate countermeasures. In particular, if is corrupted, the protocol aborts the ongoing transaction, preventing the release of the content X requested by . On the contrary, if is corrupted, then the content X is released to incorrectly protected by inserting a watermark that is not correctly linked to . The result is as if X had been released without being protected, and this damages itself.
Starting from what has been exposed so far, a brief series of considerations on the security of the protocol are reported below. A specific protocol analysis was conducted using the AVISPA tool (Automated Validation of Internet Security Protocols and Applications) [
38]. This analysis, which is not reported here for brevity, highlighted how the tool failed to document successful attacks.
7.3. Analysis
The security analysis of the protocol can be conducted by mainly focusing on the specific functions performed by the smart contract and the blockchain, leaving aside the contract deployment phase, the outcome of which can be verified directly by by accessing the information published on .
As reported in
Section 6, the smart contract is executed by
in two phases.
In the first phase of contract execution, schematized in
Figure 5,
receives from
and
in
and
the preliminary encrypted information relating to the transaction by which
wishes to purchase
X from
.
performs the first check and, if the received tokens are consistent, continues the execution of the contract, generating all the information and tokens necessary to protect
X correctly. Then,
publishes on
two tokens, among others,
and
: the first contains the encrypted information to be used for the protection of
X and also represents the current state reached by the execution of the smart contract; the second represents a summary of this state. Both tokens can be generated and are accessible only to
. Finally,
sends two messages,
and
, to
and
, respectively. In them, it includes, in the form of tokens encrypted with the secret keys of
and
, part of the information published on
and necessary to start phase 2 of the execution of the smart contract.
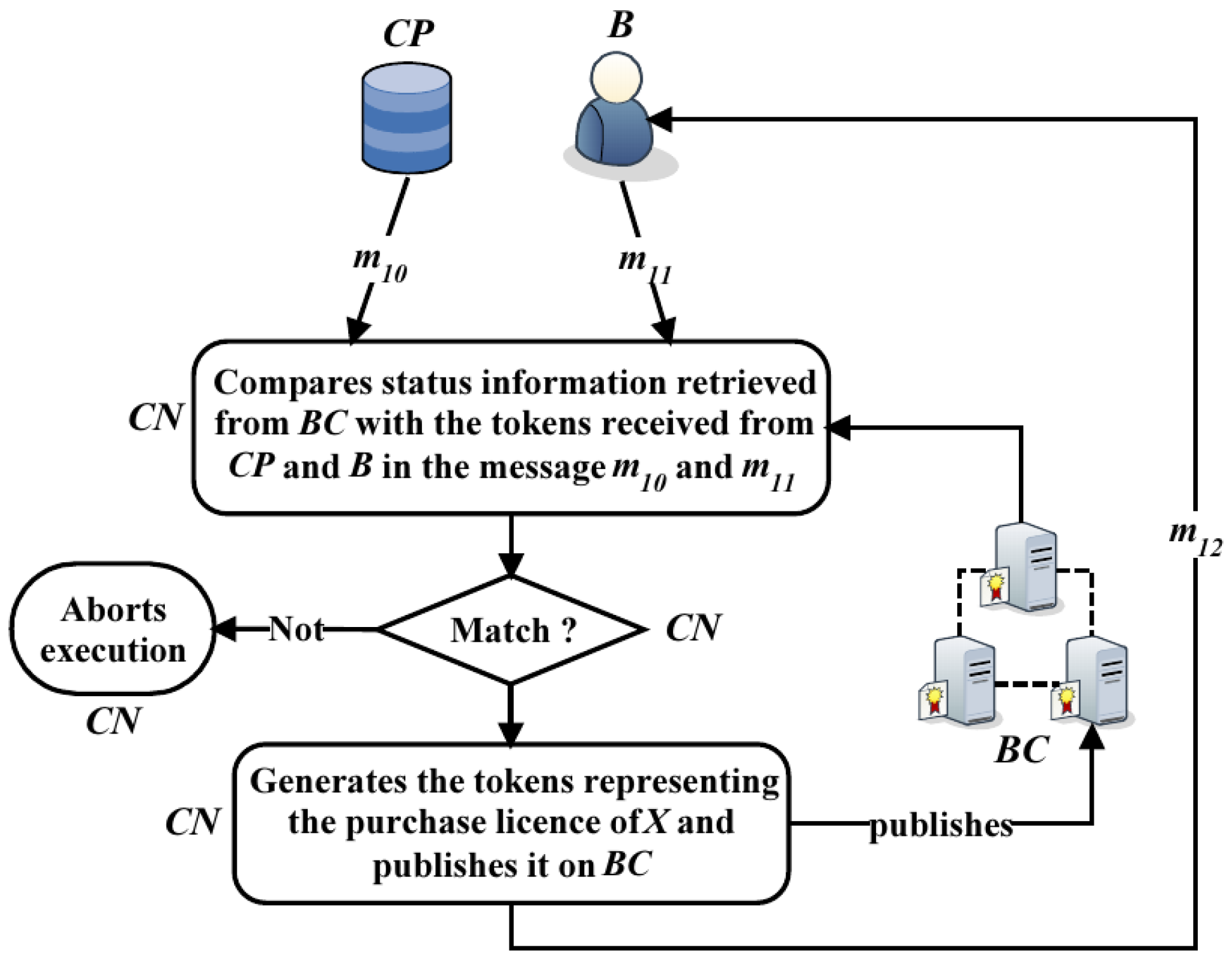
Phase 2 of contract execution, shown in
Figure 6, is started by
after
has released the watermarked content
X to
, still in encrypted form.
retrieves the encrypted information from
related to the ongoing transaction. It checks and, if the encrypted information sent by
and
is consistent with that published on
,
generates the license to purchase
X sold by
to
and publishes it on
. Then,
sends the private key
to
, with which
can decrypt
and obtain his protected and personalized accessible copy of
.
From what has been reported so far, it emerges that the security of the proposed watermarking protocol depends on the following factors:
As reported in the preliminary assumptions, the execution of in TEE ensures the correctness, integrity, and confidentiality of the computation performed.
All tokens and information in messages exchanged between , , , and are always encrypted and accessible only to the entities responsible for managing them.
The watermarking phase of X implemented by uses the security tokens generated during the first phase of smart contract execution. This phase can trigger the second phase of smart contract execution, which leads to the generation of the license to purchase X only if the information generated in the first phase by , , and is confirmed by in the second phase.
The security tokens generated and used in the first phase of execution of the smart contract are fixed by the publication on the blockchain. By accessing , is responsible for ensuring that these tokens are also used in the second execution phase of the smart contract.
Suppose that
is corrupt. Following the “buyer-friendly” approach,
participates in the protocol without generating tokens or security information except for
, which qualifies its identity. In fact,
is assumed to be valid since the problems resulting from false identities are not considered in this analysis. Therefore, the tokens that
exchanges in messages are generated by other entities and can only be confirmed by
, under penalty of interrupting the purchase transaction as a result of the checks performed at the end of the first or second phase of execution of the smart contract. Consequently, in this hypothesis, no content is released by
in accordance with the provisions of
Section 7.
Suppose that is corrupt. In this case, , which is responsible for inserting the watermark into X, can maliciously generate or attempt to alter the tokens it is responsible for, such as and , or the tokens to be used to protect X. However, the checks performed by the two phases of execution of the smart contract, as reported above, force to behave as follows:
cannot reuse tokens already used in previous transactions;
cannot modify or change the part of the watermark generated during the first phase of the smart contract execution, nor reuse watermarks used to protect other content.
This is because all tokens validly used in previous purchase transactions are published on . In detail, and are published in clear text, and any previous duplication can be directly verified by the smart contract. As regards tokens for which only the digest is published, it is necessary to observe that they are generated by the smart contract during the first execution phase, are published in the form of an encrypted state on the blockchain, and must be confirmed by and during the second execution phase of the smart contract. Therefore, any watermark generated or reused independently by to protect X that is different from the one generated by the smart contract during the first execution phase can never be inserted in the purchase license downstream of the second execution phase of the smart contract. Such a condition can only lead to the generation of protected content that cannot be validly linked to any buyer since no valid purchase license can be associated with it. This result would end up damaging itself, which would release incorrectly protected content.
In essence, the immutability of the smart contract code, its secure execution in TEE, and the exchange and publication of tokens and security information always in encrypted form on blockchain guarantee the security of the proposed protocol both with respect to corrupt entities and to “honest-but-curious” ones.
8. Implementation and Performance
The implementation of the described protocol consists of two main parts: the first concerns the watermark insertion algorithm, while the second concerns the execution model of the smart contract that is responsible for running the protocol.
As for the first part, two different watermark insertion algorithms are available: one based on the SS insertion technique [
22] and the other based on QIM [
34]. Both are used in conjunction with the Paillier homomorphic cryptosystem [
29], as described in [
39,
40,
41], and exploit the optimizations, described in [
26,
42], capable of improving the watermark insertion directly in the encrypted domain.
The SS insertion algorithm is based on the following formula:
in which
x is a host signal feature obtained by calculating the cosine discrete transform,
is the corresponding watermarked feature,
is the bit to embed,
s is the component of a spreading sequence, and
is a scaling factor that controls the watermark’s strength. Therefore, inserting the watermark into the encrypted domain employs the following formula [
26,
39,
40]:
The insertion algorithm using QIM is based on the following formula [
26]:
where
x,
, and
b have the same meaning reported above, while
and
denote a function of the original signal features and a signal-dependent quantization step, respectively [
4,
34]. Consequently, the insertion of the watermark into the encrypted domain uses the following formula [
26,
40,
41]:
As for the second part, the smart contract execution model has been implemented using the Oasis Network [
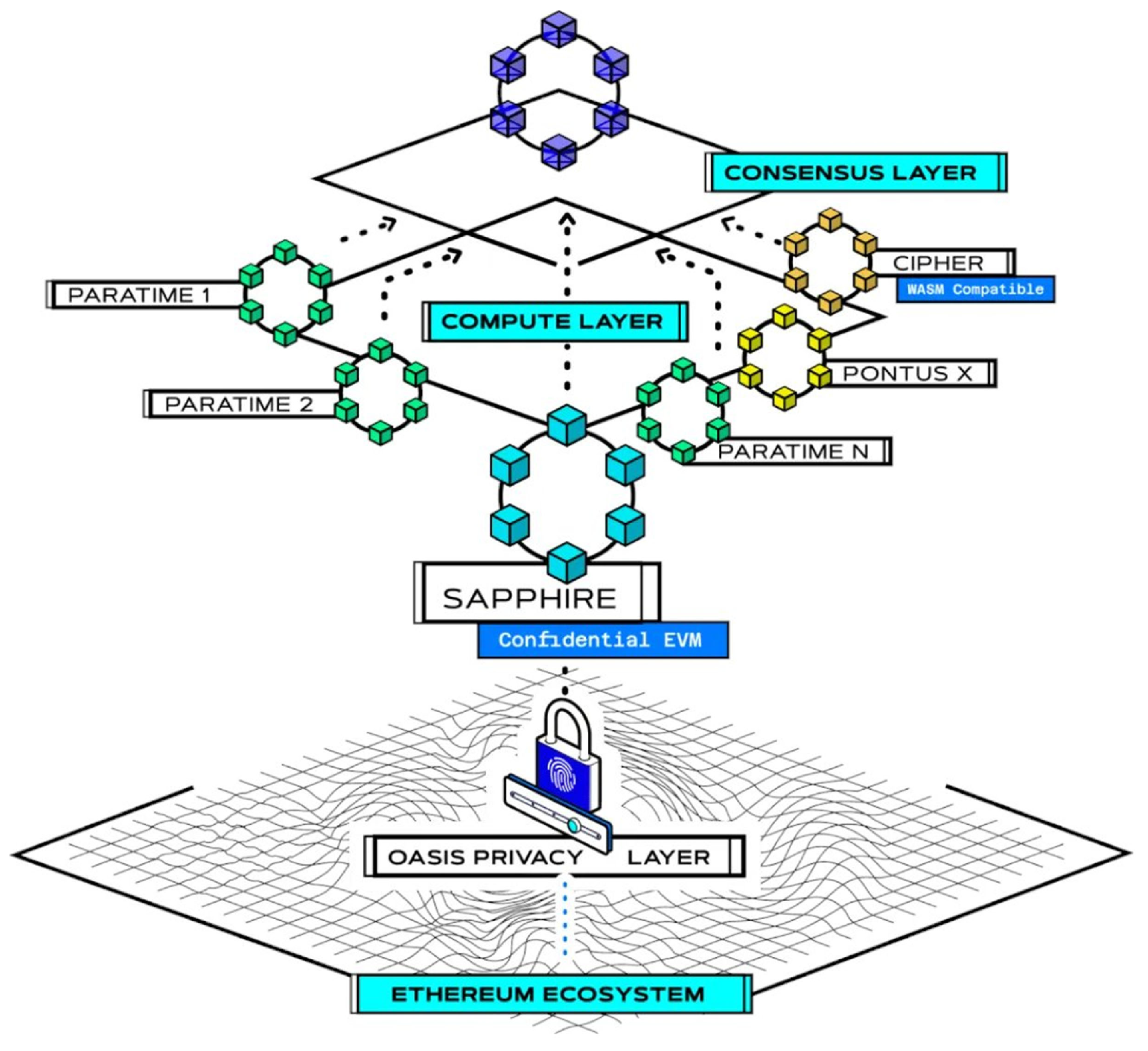
43], a blockchain based on the “layer-2” architecture adopted by the proposed protocol. Oasis is, in fact, composed of a layer dedicated to reaching consensus and an off-chain execution layer of smart contracts (see
Figure 7).
In particular, the consensus layer is implemented by validator nodes that maintain the integrity of the blockchain by running the Tendermint BFT (Byzantine Fault Tolerance) protocol and employing a proof-of-stake as the block proposer protocol.
The execution layer of smart contracts is implemented by execution nodes hosting the so-called “paratimes” (parallel runtimes), which represent the environments dedicated to executing smart contracts. In this regard, the proposed protocol uses a specific paratime made available by Oasis, called Sapphire, which supports the confidential execution of EVM-compatible smart contracts in TEE, just like the one implementing the proposed protocol, which was written in Solidity (see
Figure 8).
Sapphire leverages INTEL SGX as a TEE, which ensures that all input, output, intermediate, and final states of smart contracts are always encrypted and managed securely, even with respect to the nodes hosting the TEEs. As a confidential paratime, Sapphire provides a key manager that can guarantee the generation, storage, distribution, and revocation of the keys needed for execution in TEE. In addition, Sapphire ensures the integrity of the computation performed in TEE through the “discrepancy-detection” algorithm. This algorithm provides that the results of the execution in TEE of the same smart contract by multiple execution nodes are sent to a “committee” of nodes in the form of “cryptographic commitment”. The nodes of the committee then execute the discrepancy-detection algorithm and, if they reach an agreement, they declare the smart contract execution as complete and send the result to the consensus layer for finalization on the blockchain. Otherwise, the committee nodes run the more expensive “discrepancy-resolution” algorithm to identify the correct result of the smart contract execution. In this way, Sapphire guarantees high scalability to the off-chain execution of smart contracts, which is penalized only in case of a lack of agreement between the committee nodes.
As for the performance of the proposed protocol, it is important to note that the time
T needed to complete a purchase transaction of
X is given by the sum of the following contributions:
where
is the time taken by a TEE-equipped node to execute the smart contract implementing the protocol,
is the time taken by
to secure the content
X,
is the time taken by the committee of TEE nodes to evaluate the integrity of the computation performed to execute the smart contract, and
is the time taken to finalize the purchase transaction on the blockchain.
In particular, thanks to the layer-2 execution paradigm, and are related to an off-chain execution. They mainly depend (1) on the power and number of TEE nodes involved in executing the smart contract and (2) on the discrepancy-detection protocol. Therefore, the higher the degree of replication of the smart contract execution and the number of nodes involved in the integrity committee, the higher the recorded times will be.
, instead, depends on the computing power used by : the greater this power, the less time will be required to protect X.
coincides with the so-called “time to finality” that characterizes
, that is, the time needed to confirm a transaction completely [
8]. It measures the time that elapses between sending the transaction to
and its confirmation, by publication in one of the
blocks, with a guarantee of irreversibility. This time is a very variable value and difficult to obtain because it depends on many factors, such as, for example, the consensus algorithm used, the block propagation method, the number of validator nodes used, the speed of their network interconnection, and the finality method. In essence, it is possible to reduce
by using a reduced number of validator nodes, but this expedient ends up also reducing the level of security implemented by
, as foreseen by the so-called “trilemma” of blockchains, according to which the classic objectives of a blockchain, such as decentralization, scalability, and security, are substantially conflicting [
8].
In the preliminary tests conducted, three TEE nodes (Intel(R) Core(TM) i7-10870H with a frequency up to 4.8 GHz and 16 GB of RAM) and three validator nodes (Intel(R) Core(TM) i5-12450HX with a frequency up to 4.4 GHz and 16 GB of RAM) were used. All nodes are connected by a Gb Ethernet. As for , an Intel(R) Core(TM) i5-12450HX compute node with a frequency up to 4.4 GHz and 16 GB of RAM was used.
With these limited hardware resources, varies approximately between 12 and 14 s, mainly due to the operations needed to generate encryption keys, encrypt tokens, and calculate hashes.
was found to vary between 29–41 s and 107–145 s, depending on the size of the protected image, 512
512 or 1024
1024 pixels, and the watermarking algorithm used, such as SS or QIM [
18].
was calculated using all three nodes in the committee to evaluate the integrity of the computation performed by the smart contract. It was found to vary approximately between 1 and 1.5 s when no discrepancy was detected. On the contrary, the discrepancy-resolution algorithm takes approximately between 5 and 6 s in case of no agreement.
Finally, was calculated using all three available execution nodes as validators. The result obtained was approximately between 6 and 7 s.
It is important to note that , , and values are independent of the blockchain used since they are obtained, as previously mentioned, by exploiting a layer-2 execution paradigm. Such a condition guarantees scalability to the proposed solution since, by increasing the number of TEE nodes used as well as their power, these times can be drastically reduced without undermining the security of the protocol. As for the value of , it can be reduced by adopting a more efficient consensus algorithm. However, the one used by Oasis still guarantees good performance in relation to other solutions documented in the literature, with a maximum theoretical value of TPS (transactions per second) equal to 1000.
Finally, the adoption of the layer-2 execution paradigm allows the execution of the smart contract that implements the watermarking protocol to be moved off-chain, thus overcoming the gas limits imposed by layer-1 blockchains without having to give up the advantages of immutability, automation, and decentralization of smart contracts on blockchains.
9. Related Work
The evolution of watermarking protocols has led to “buyer-seller” solutions that leverage public key infrastructures, asymmetric fingerprinting, and “privacy homomorphic” encryption for watermark insertion. Such solutions effectively address classic issues documented in the literature, such as the “unbinding problem” and the “customer’s right problem” [
4]. In these solutions, the seller inserts a watermark encrypted with the buyer’s public key directly into the content, which is also encrypted using the same public key. Consequently, the buyer can access the content with personalized protection by decrypting it with his/her private key. However, many existing protocols rely on TTPs as “watermark certification authorities” or agents essential for ensuring the correctness and security of the protection transactions executed. Such a situation has prompted researchers to seek new solutions that eliminate TTPs from the developed protocols, all while avoiding complex actions for buyers during the content purchase transactions from sellers. According to such an approach, watermarking protocols that utilize blockchain technology and smart contracts to bypass TTPs represent one of the most advanced and promising solutions in the literature.
Y-DWMS [
44] adopts the aforementioned approach and leverages blockchain technology and smart contracts to deliver traditional services such as watermark verification for disclosed copies, authentication of informers’ reports, and traceability of infringements. In addition to these classic services, Y-DWMS introduces specific functionalities to reward informers, penalize infringers, and mitigate losses incurred by copyright holders. Despite these innovative services, Y-DWMS is affected by specific problems, particularly concerning privacy, and its security level has not been validated.
SBBC (Secret Block-Based Blockchain) [
45] exploits blockchain technology and smart contracts to create a digital content trading system. It comprises both off-chain and on-chain components. The off-chain components implement an initial authentication phase, enabling users to engage in digital content transactions. Digital fingerprints are embedded in the traded content to monitor any illegal leaks. Additionally, the content is encrypted, ensuring that only authorized users can access it, thereby safeguarding the income of legitimate content creators. The on-chain components provide licensing services. Specifically, authorized users run smart contracts to initiate the licensing process, generating secret blocks representing their transactions and recording them on the blockchain. Following verification and agreement from all blockchain nodes, public blocks are added to the blockchain to finalize purchase licenses. SBBC also addresses performance issues that typically affect blockchain-based systems by proposing an efficient consensus algorithm. However, it lacks a thorough security analysis and has yet to demonstrate resilience against the traditional challenges faced by watermarking protocols [
4,
46].
FingerChain [
47] is a multi-owner media-sharing system focused on digital copyright protection, built on a consortium blockchain network. It employs smart contracts and asymmetric fingerprinting to allow authorized owners to share their media for a fee. This system benefits from the absence of a TTP to implement the protection protocol and a high efficiency level on the owner’s side due to the “client-side embedding” technique for watermark insertion [
48]. However, the watermarking scheme used requires clients to eliminate noise sequences from the purchased content and generate secret fingerprints. These security measures can be complex for ordinary web users [
4].
While the systems discussed above present innovative approaches to watermarking protocols, they exhibit certain limitations that the protocol outlined in this article aims to address.
For instance, Y-DWMS is characterized by many innovative aspects, but there is no information about the performance offered or the level of security achieved.
FingerChain employs a watermarking insertion technique that is significantly more efficient than those assessed for the proposed protocol; specifically, the “client-side embedding” watermark insertion technique requires at least an order of magnitude less time than the SS or QIM techniques when processing the same content. However, FingerChain necessitates that buyers execute complex security primitives, which represent a fundamental limitation of its protection scheme.
Conversely, SBBC is the first system to divide the execution of the watermarking protocol into both off-chain and on-chain components. Nonetheless, the on-chain component relies on the execution of smart contracts, which exposes SBBC to the issues outlined in
Section 2. From a performance perspective, SBBC surpasses the proposed protocol in efficiency due to two primary factors: (1) its “permissioned” execution model does not mandate the implementation of the discrepancy-detection algorithm prior to achieving consensus among blockchain nodes, and (2) it utilizes more efficient consensus algorithms than that employed by the Oasis Network, resulting in a reduction in execution time of around 10% on average, which increases up to 20% when the number of nodes in the blockchain reaches the maximum tested value of 50. Therefore, SBBC provides a more overall efficient solution than the proposed protocol, although it still suffers notable limitations related to both the execution on-chain of smart contracts and the lack of adequate security analysis. On the contrary, the solution proposed in this paper marks a pioneering instance of a watermarking protocol built on a layer-2 confidential execution model based on TEE.