Abstract
In recent years, the Internet of Things (IoT) has experienced considerable developments and has played an important role in various domains such as industry, agriculture, healthcare, transportation, and environment, especially for smart cities. Along with that, wireless sensor networks (WSNs) are considered to be important components of the IoT system (WSN-IoT) to create smart applications and automate processes. As the number of connected IoT devices increases, privacy and security issues become more complicated due to their external working environments and limited resources. Hence, solutions need to be updated to ensure that data and user privacy are protected from threats and attacks. To support the safety and reliability of such systems, in this paper, security issues in the WSN-IoT are addressed and classified as identifying security challenges and requirements for different kinds of attacks in either WSNs or IoT systems. In addition, security solutions corresponding to different types of attacks are provided, analyzed, and evaluated. We provide different comparisons and classifications based on specific goals and applications that hopefully can suggest suitable solutions for specific purposes in practical. We also suggest some research directions to support new security mechanisms.
1. Introduction
The Internet of Things (IoTs) is a system of connection and interaction between smart devices, machines and users via the Internet, thereby creating an automated and flexible interactive environment [1]. IoT devices usually incorporate technology like sensors and software, encompassing both mechanical and digital machines as well as everyday consumer items. The growth of smart city networks has made the Internet of Things (IoT) spread more worldwide. Deploying network edges that allow for smart services and computation for IoT devices is the goal of the development. Edge computing in IoT applications takes advantage of end-user proximity and distributed architecture to deliver higher quality of services and faster response times. In addition to the development, the security problems in such networks are critical and are primarily addressed to fend off attackable vulnerabilities [2]. A wireless sensor network (WSN) is defined as a collection of resources in which sensor nodes collect environmental data, process the outputs into a structured data set, and finally send the data over a wireless media to destination terminals. The sensing data acquired from various types of sensors, including flow, temperature, pressure, magnitude, level, etc., serve as the input sources. Compared to wired networks which have a robust architecture, wireless networks are often considered weak and vulnerable against adversaries due to their open nature [3].
In the context of the IoT, WSN and IoT are integrated (WSN-IoT) to build more powerful, flexible decision-making systems in which WSNs constitute the backbone of the IoT, providing sensing and data collection infrastructure, while the IoT provides the ability to connect and manage smart devices [4]. WSN-IoT networks increase the efficiency of data monitoring and analysis, ensuring information transmission between smart devices [5]. In recent years, studies and practical works with WSNs based on IoT platforms have been widely developed in many fields such as industry, agriculture, smart cities, healthcare, transportation, and environment [6,7,8].
However, such networks are vulnerable to attacks due to their unique characteristics such as large scale, self-organization, dynamic structure, and limited resources [9]. The dense deployment of WSNs in unsupervised environments makes sensor nodes vulnerable to attacks [10]. In WSN-IoT, security is an important aspect to ensure the safety and reliability of the system. WSN-IoT plays an important role in collecting, transmitting, and processing data from various types of sensors scattered in the environment, including sensitive information on medical records, environmental conditions, and location data [11,12]. The attacks entail harmful endeavors to take advantage of weaknesses in devices linked to the network, with the possibility of achieving unauthorized access, data theft, or operational disturbances. Therefore, security becomes a top priority to prevent unauthorized access and protect privacy. Implementing security measures not only prevents common types of cyber-attacks but also ensures that data is exchanged and stored securely [12]. In addition, security techniques also aim to support the optimization of energy usage in sensor devices, efficient resource management, and ensure the system availability. With the diversity of modern attack models, continuously updating and enhancing security measures becomes the key to building and ensuring safe, efficient, and reliable WSN-IoT applications [13,14].
Panahi et al. [15] studied the development, applications and challenges faced by IoT systems. The security issues in IoTs were analyzed through a multi-layered perspective, thereby proposing secure data transmission solutions for WSN-based IoT applications. Hameed et al. [16] proposed solutions to improve IoT security and abnormal detection methods. They were compared with state-of-the-art intrusion detection systems (IDSs). Hassija et al. performed a comprehensive analysis of security challenges and potential threats in IoT applications [17], thereby proposing solutions to improve IoT infrastructure to support secure interactions. Device security, transmission security, and data security are all included in the security classification criteria of Harbi et al. [18] to evaluate IoT security. In IoTs, some types of attacks can be mitigated by using authentication techniques and lightweight encryption algorithms. Jurcut et al. [19] emphasized vulnerabilities that can lead to security breaches and identified common threats and attack routes on IoT devices. The study also provides some security enhancements and preventive techniques to mitigate the risks, along with remediation measures for compromised devices.
To enhance the security effectiveness in WSN-IoT, some other authors have proposed the use of technologies such as machine learning, edge computing, cloud computing, and blockchain to improve IoT security. In the study of Khalid Haseeb et al. [20], an intrusion prevention framework for mobile IoT devices and integration with WSNs was proposed to provide data security with an improved network distribution ratio. Machine learning techniques are proven to be effective in WSN-IoT due to their intelligent and cost-effective computational procedures. In some recent studies [21,22,23,24], the authors have discussed machine learning algorithms to improve security performance, such as congestion-based intrusion detection in WSN-IoT.
The above-mentioned studies have highlighted the prominent WSN-IoT security attacks in recent years, based on criteria such as attack targets, technologies used, impact level, feasibility, and contribution to overall WSN-IoT security solutions. However, there are still gaps in these studies, especially in thoroughly analyzing attacks from a security perspective for WSNs while integrated with the IoT. Therefore, the corresponding security methods need to be comprehensively considered based on criteria such as cost optimization, resource efficiency, energy saving, and system availability assurance. In addition, other proposed solutions are also considered, including data aggregation methods, intrusion detection and trust modeling methods, and methods based on new technologies such as blockchain. Since there are many results related to security problems and solutions are considered separately in the fields, it is necessary to present some work that either leads to addressing the problems in some classifications or provides solutions corresponding to problems. The objective of this paper is to address these issues through the following research objectives and research questions (RQs), as shown in Figure 1.
Figure 1.
The study’s objectives.
In this paper, through a comprehensive review of the literature and a detailed analysis of the prominent WSN-IoT-related security attacks in recent years, the importance of WSN-IoT systems is highlighted based on their applications in various fields. Security issues in WSN-IoT systems are reviewed and related security attacks are classified in detail. The corresponding security solutions are proposed, compared, and evaluated to mitigate security attacks, threats, and vulnerabilities in WSN-IoT systems. In addition, we outline key security limitations and challenges, and present future research directions based on emerging application areas.
The rest of this paper is organized as follows. In Section 2, background and security problems are addressed to support the understanding of the correlation between security issues in the WSN-IoT context and the constraints. The impact analysis of related attacks on security requirements in the networks and a summary of the security mechanisms are also provided. In Section 3, security protection schemes for WSN and IoT interoperability are presented in different forms. Then, an extensive discussion on ensuring the security requirements of the methods is given by addressing the main security issues and challenges in Section 4. Finally, conclusions and future work are addressed in Section 5.
2. Backgrounds and Security Problems
2.1. WSN-IoT Context
WSNs are an emerging technology and are being deployed in many different fields of application. These sensor nodes are deployed in an area to self-organize into a wireless network to collect and to aggregate data about the environment [3,25]. A typical WSN consists of a large number of small-sized, low-cost, densely deployed sensing nodes that communicate wirelessly [8]. The networks have certain limitations due to the nature of such networks. They pose special challenges because of the resource limitations of each sensor node, especially in terms of memory and computing power [26]. Fundamental power constraints eventually lead to innovative design problems due to computational and storage limitations [27].
Realistic implementations show that sensor nodes are usually deployed in environments where they are highly vulnerable to physical damage [8] and where it is difficult to replace batteries or to maintain them. This affects the network topology due to damaged or compromised nodes. Furthermore, unreliable communications in unmonitored environments make the direct use of existing security methods on sensor platforms difficult due to the complexity of algorithms. These challenges are the foundation for further research on security in WSNs, especially while integrating the IoT [3]. Due to these unique challenges, traditional security techniques are insufficient to meet the security goals of confidentiality, integrity, reliability, and availability.
The IoT is considered a global network system where billions of connected devices can communicate with each other via the Internet without human interaction [28]. In particular, IoT networks can be deployed based on WSNs to provide numerous services and applications such as smart homes, battlefield monitoring systems, smart healthcare systems, and smart transportation for smart cities [29,30]. As shown in Figure 2, a WSN-based IoT application deployment scenario includes three layers: the network layer, cloud/fog layer, and application layer.
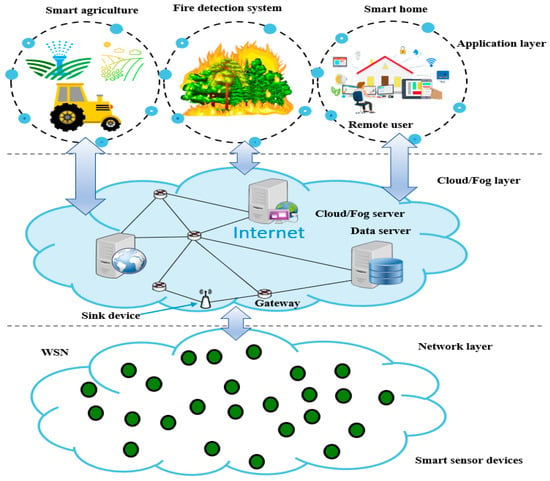
Figure 2.
WSN-based IoT application deployment scenarios for smart cities.
The highest layer of IoT is the application layer, including several applications such as smart agriculture, smart home, etc. Remote users can receive warning information through the Internet connected to computers and can make decisions based on the information collected. The cloud/fog computing layer is responsible for aggregating and processing enormous amounts of data accurately to reduce the computational burden on the upper layer as well as avoid network congestion. The procedures can be performed by smart IoT devices such as routers, base stations, or servers equipped with strong processing capabilities, large memory, and unlimited power [31]. The network layer is where sensor devices can be deployed in real environments to measure the parameters of diverse physical phenomena (temperature, humidity, air pressure, precipitation, etc.) connected to WSNs [32].
Security in WSNs and the IoT is important and necessary for many specific cases and reasons, including protecting personal information, ensuring data integrity, and preventing negative consequences of attacks. In addition, security is also a factor that enhances the reliability and performance of the entire system. This work aims to focus on the security issues that arise when combining WSNs and the IoT. The current challenge is to address the security of WSN-IoT from a general perspective and not as a limited set of issues related to separate technologies. WSNs play a vital role in collecting information about the environment, while integrating with IoTs leads to different security requirements that might arise during the combination process as follows.
- WSN-IoT devices need strong authentication mechanisms to ensure that only authorized users and devices can access the network and data. At the same time, data transmitted between devices and systems must be encrypted to prevent unauthorized access and protect against interpretation.
- Routing and protocol protection: Ensure that the protocols and data routing used in the WSN-IoT network have security measures in place to prevent attacks and interference; the system must have effective key management to ensure that the keys used in encryption and authentication are managed securely.
- Integrated security: Integrate security mechanisms from the design phase of the WSN-IoT system to ensure that all components are protected.
- In addition, WSN-IoT needs to meet requirements for privacy, the security of the collected data and user data, and the ability to restore network and system functions after incidents [13]. In special applications of WSN-IoT (healthcare applications, applications operating in harsh environments, etc.), security requirements need to ensure additional strict elements. For example, security mechanisms must adapt quickly to dynamic topologies (when sensor nodes are not fixed in their active locations) [33]; in harsh environments where network nodes cannot replenish energy, the balance between security and network node resources also needs to be considered [3].
In summary, security issues in WSN-IoT are not only technical problems, but also concerns regarding the rights and the safety of users, data reliability, and system stability. In other words, security is not just a layer of protection, but a decisive factor in building and maintaining secure, reliable WSN-IoT systems. This is critical and crucial to be considered in a holistic manner.
2.2. Analysis of Attacks in WSNs
WSNs are facing many types of attacks due to the special nature of the networks, including widely distributed sensor nodes and insecure operating environments. This makes WSNs susceptible to various attack methods. Therefore, it is necessary to classify attacks in order to determine effective response methods. In this work, attacks in such networks are classified based on different criteria to clarify the nature of threats and provide a basis for corresponding security strategies. The criteria for classifying security attacks in WSNs include internal and external attacks, active and passive attacks, and network architecture-oriented attacks (as shown in Figure 3). All of the common attacks are addressed in detail as follows.
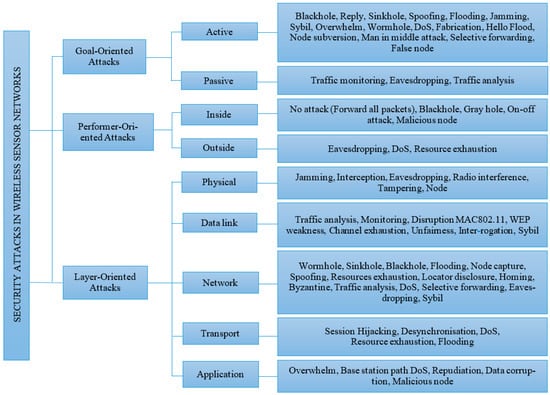
Figure 3.
Classification of security attacks in WSN-IoT networks.
2.2.1. Active and Passive Attacks
Passive attacks: Passive attacks are carried out by malicious nodes to perceive the nature of the activities and illegally collect data transmitted in the network without disrupting network operations (such as eavesdropping, interference, tampering, replay…). The collected packets are analyzed to determine the traffic and exchange process of the packets, thereby identifying the server, and determining the location.
Active attacks: Attacks that attempt to change, insert, delete, or destroy data transmitted in the network. Attacks can intercept data and attempt to modify and drop packets, which can be achieved internally or externally. On the other hand, some attacks may come from compromised nodes, which are part of the network. Based on the purpose of the attack, active attacks can be classified as node-compromising attacks; routing attacks; and DoS attacks [34,35].
2.2.2. Internal and External Attacks
Internal attacks: Insider attacks can avoid authentication and gain access to network information, and this type of attack cannot be easily predicted. Several types of attacks such as modification, misrouting, eavesdropping, packet dropping, etc., will prevent vital information from reaching the base station, significantly reducing network performance, such as speed package delivery due to multiple package drops [14]. There are several types of packet dropping attacks such as black hole attacks, gray holes, etc. [19]. This internal attack is a serious threat to many applications, such as military surveillance systems that monitor battlefields, and other critical infrastructure.
External attacks: This can cause passive eavesdropping during data transmission, as well as extending to injecting bogus data into the network for consumption of network resources and increased denial of service attacks [14,16].
2.2.3. Layer-Based Attacks in Network Architecture
Physical layer attacks: Usually involve activities targeting the physical components of the system, changing the structure or operation of sensor nodes, as well as degrading the quality of collected data, or harming network performance [36]. Different types of attacks on the physical layer include eavesdropping attacks [37]; jamming attacks [28]; attacking a compromised node [38]; and attacking via node copying [39].
Data link layer attacks: These are activities aimed at communication protocols and processes at the data link layer. Some common attack methods in the data link layer of WSNs are collision attacks; smart jamming attacks; and sleep denial attacks [40]. Figure 4 illustrates the power consumption of the node in different modes including data transmission/reception, idle mode, and sleep mode [41] in which the energy consumption of nodes in sleep mode is the lowest, so attacks are often aimed at blocking nodes from falling into sleep mode so that the nodes quickly exhaust energy [41].
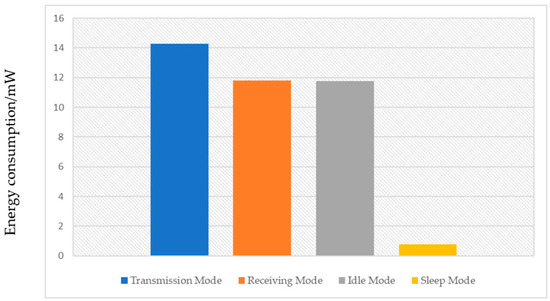
Figure 4.
Energy consumption of network nodes in different modes [42].
Network layer attacks: These attacks aim to focus on network protocols and infrastructure. Some of the common network layer attacks are the replay attack and the Sybil attack [43]. Other types of attacks include black hole attacks (Figure 5a) [44], gray hole attacks (Figure 5b) [45], wormhole attacks [46], sinkhole attacks [47], and hello flood attacks [48].
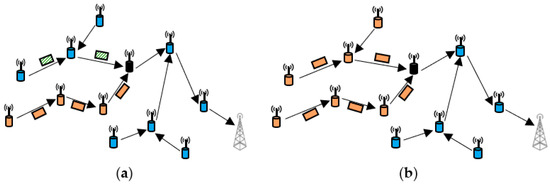
Figure 5.
Some types of attacks in the network layer: (a) black hole attack; (b) gray hole attack.
Transport layer attacks: Usually involve activities targeting communication protocols and processes at the transport layer. Some common attacks in the transport layer of WSNs: flooding attacks, attack synchronization, etc. [49,50].
Application layer attacks: These are activities aimed at specific applications or services that the sensor network is providing, including attacks on reliability, and malware attacks [50,51].
Cross-layer attacks: These are types of attacks that combine and affect layers of the network system. Some typical types of attacks include jamming attacks, DoS attacks, and man-in-the-middle attacks [49,52].
Although we have analyzed the attack classification from various perspectives to provide a systematic and comprehensive overview of attacks in WSNs, it should be noted that real-world attacks may satisfy different classification criteria (e.g., an insider attack may be classified as both active and passive, or an eavesdropping attack may fall into both physical and passive attack categories). This reflects the diversity and complexity of modern attacks directed at WSNs.
3. Security Protection Schemes
3.1. Encryption Schemes
In WSNs, choosing the right encryption algorithm is an important factor in improving the security of a system, and helping to protect important information from risks caused by potential attacks. However, due to the resource constraints of the sensing nodes in WSN-IoT networks, encryption methods are designed to ensure efficiency while meeting strict requirements. In WSNs, the two most common encryption methods are symmetric encryption (using the same key for encryption and decryption), and asymmetric encryption (using a pair of keys, one public, the other one private, for encryption and decryption). These encryption schemes are analyzed in detail as follows.
3.1.1. Asymmetric Encryption
Although asymmetric encryption algorithms are not popular in WSNs due to limitations in scalability, high energy consumption, and resource consumption due to complex computational requirements, some asymmetric encryption algorithms such as RSA (Rivest–Shamir–Adleman) or ECC (Elliptic Curve Cryptography) are still being researched and developed in WSNs for applications requiring high security levels.
The security of RSA depends on the difficulty of calculating large integers. In RSA, the larger and more complex the integers, the higher the security. The security level of RSA increases as the key size increases, but it also increases the complexity of the encryption and decryption processes (consequently, processing time and power consumption make application difficult when WSN-IoT systems are inherently resource-limited) [50,53]. In the context of WSN-IoT, several studies have implemented enhanced security models based on RSA. In [54], the author proposed an RSA-based solution for the Efficient Improved Digital Signature Technique (RSAEDSA). The simulation test results showed that the performance of the RSAEDSA outperformed the state of the art in terms of quality of service (QoS) parameters. The authors in [55] implemented a 2048-bit RSA technique based on improved RSA for WSN-IoT; the proposed scheme achieved encryption and decryption on MSP430 in just 0.14 s and 7.56 s, respectively. In addition, the method has a 112-bit security level, which helps to mitigate threats such as power analysis attacks.
Elliptic Curve Cryptography (ECC) is a public key cryptography technique based on elliptic curve theory, helping to create faster, smaller, and stronger cryptography. Thus, elliptic curve-based security systems emerged as an alternative to RSA cryptographic systems. ECC generates ciphers through the properties of elliptic curve equations instead of the traditional method of using large prime numbers. Just like in RSA, ECC uses a key pair consisting of a public key and a private key. In the study [56], the authors provided a comparative analysis between RSA and ECC. Experiments were conducted to compare the time required for encryption and decryption using RSA and ECC on three input data samples, 8-bit, 64-bit, and 256-bit, with random keys. The simulation results show that ECC outperforms RSA in terms of performance and security with fewer parameters and that ECC is especially suitable for resource-constrained devices. Table 1 summarizes the time taken for encryption, decryption, and the total time taken for ECC and RSA.

Table 1.
Comparison of encryption, decryption, and total execution time of ECC and RSA [56].
In some applications of WSN-IoT, ECC-based encryption techniques are developed to meet the applications with strict security requirements. In [57], the authors proposed an improved ECC encryption technique (IECC) by adding a secret key to enhance the security of the system in which the generated secret key is added to the formula of encryption and subtracted from the formula of decryption. The complexity of the encryption and decryption process is enhanced, making it difficult to detect the original data. The advantages of IECC meet security requirements such as low encryption, decryption time, and communication cost. Simulation results show that IECC, with average encryption and decryption times of 1.032 μs and 1.004 μs, respectively, is lower than previous ECC and RSA algorithms.
3.1.2. Symmetric Encryption
The authors in [58] evaluated different encryption schemes on a variety of embedded architectures, including low-, mid-, and high-end embedded processors. The measurements were performed on Atmel AVR (8-bit), Mitsubishi M16C (16-bit), and StrongARM and Xscale (32-bit) platforms. In the study, five popular encryption schemes were selected, namely RC4, RC5, IDEA, SHA-1, and MD5. Among them, RC4 and RC5 are two symmetric encryption algorithms that use the same key to perform both encryption and decryption. RC4 uses a 256-byte permutation which is generated from the input key [59]. Similarly, RC5 uses fixed data blocks 32 to 128 bits in length. RC5 allows the use of keys 0 to 2048 bits in length [60].
IDEA works by encrypting and decrypting fixed-size blocks of data [59]. IDEA uses 64-bit blocks of data and 128-bit key size, and performs eight iterations for each block of data. The large key size makes IDEA very difficult to break because the time required to iterate through all possible key possibilities is too large. MD5 and SHA-1 are popular hashing algorithms, in which MD5 produces a hash value of 128 bits (16 bytes) [59] and SHA-1 produces a hash value of 160 bits [61].
In such research, the experiments show that the RC4 algorithm shows superior performance on 8-bit and 16-bit architectures compared to other schemes, especially in comparison to RC5. However, on 32-bit architectures, RC5 shows better compatibility with high-resource platforms than RC4. In addition, the computational cost of RC4, RC5, and IDEA is lower than that of hash algorithms (MD5 and SHA-1).
In addition, the Advanced Encryption Standard (AES) is widely recognized for its advantages such as balancing low power consumption, high security, and good performance [62]. AES is chosen in many applications, especially in standard wireless technologies such as IEEE 802.15.4, which are commonly used in smart homes and industrial automation. In [63], the authors provide a comprehensive review of the latest lightweight AES architecture designs to explore the application possibilities of AES in WSN-IoT. The authors in [64] propose a low-power AES encryption architecture LPADA (Low-Power AES Data Encryption Architecture). The system was simulated using the Synopsys library with five different supply voltages. The experimental results show that 62.0% of dynamic power reduction and 88.5% of leakage power lowering were achieved compared to the power consumed by traditional AES data encryption. In addition, the key update procedure for LPADA shows effectiveness against replay and eavesdropping attacks by mutual authentication between end nodes and application servers.
In WSN-IoT, encryption techniques help improve the effectiveness of protecting data from unauthorized access. In particular, in WSN-IoT applications containing sensitive information such as medical data, location information, environmental data, etc., flexibility in choosing encryption algorithms is an important factor, suitable for the diversity of many types of WSN-IoT devices with different resource limitations. In addition, encryption techniques can improve the overall security effectiveness by combining with other security mechanisms (such as authentication, routing or secure data aggregation). However, there are some limitations in deploying encryption techniques in WSN-IoT. Some techniques are not suitable for resource-limited devices (for example, RSA encryption technique depends on the difficulty of calculating large integers; although ECC is better, it is difficult to deploy with low-power sensor nodes). In addition, in large-scale sensor networks, asymmetric encryption methods face many limitations to scale.
3.2. Key Management Protocol Schemes
Key management includes establishing and maintaining keys (protection, distribution, use, destruction…) according to security policies (authenticity, confidentiality, integrity, scalability, and flexibility) and must ensure the resource constraints of the WSNs. The key management must also meet the handling requirements for malicious nodes (including resilience, revocation, and recovery). Key management protocols can be classified as shown in Figure 6.
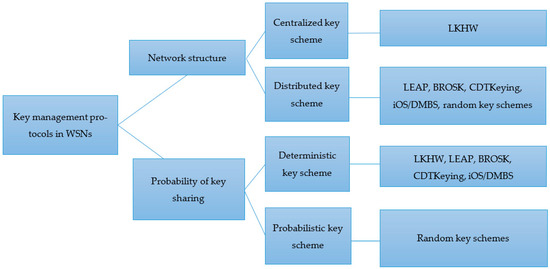
Figure 6.
Key management protocols in WSNs.
The underlying network structure plays a vital role in the operation of key management protocols. According to the network structure, protocols can be divided into two types: centralized keying mechanisms and distributed keying mechanisms. In a centralized key management mechanism, an entity called a key distribution center (KDC) controls key generation, regeneration, and distribution. The only proposed centralized key management mechanism is the LKHW mechanism, which is based on the logical key hierarchy (LKH) [65]. The LKHW combines the advantages of both LKH and directed diffusion, while implementing both forward and reverse secrecy in which the energy cost scales logarithmically with the group size. In distributed key management approaches, different controllers are used to manage key regeneration and distribution, leading to minimizing the risk of errors and allowing for better scalability. Most of the proposed key management methods are based on distributed keying mechanisms. These methods can also be classified into probabilistic key management schemes or deterministic key management schemes, which are discussed in detail as follows.
In the deterministic key management mechanism, the LEAP local authentication and encryption protocol was proposed by the authors of [66]. This proposed solution allows for key revocation and renewal, ensuring high resilience against node intrusion. The designed protocol supports the establishment of four separate key types: individual keys (to be shared with the base station), pairwise keys (shared with other sensor nodes), cluster keys (shared with multiple neighboring nodes), and global keys (shared by all nodes in the network). The security capabilities of LEAP were evaluated under various attack models, showing that LEAP is effective against wormhole attacks, node cloning attacks, and HELLO flood attacks. In addition, LEAP’s complexity is proportional to the number of nodes in the network and reasonable resource consumption. Simulation results to evaluate the performance of LEAP show its cost-effectiveness in computation, communication, and storage.
Lai [67] proposed the BROSK protocol (Broadcast Session Key Negotiation Protocol) which is resistant to some common attacks such as denial of service attacks, replay attacks, or spoofing attacks. The security mechanism of BROSK is based on the control of key exchange between network nodes in WSNs. The proposed BROSK method is scalable since the time required to complete the key negotiation does not depend on the number of sensor nodes. At the same time, the protocol saves energy costs by reducing the number of transmissions.
A key distribution mechanism for WSNs with distributed and randomly deployed network nodes was proposed by Camtepe and his colleagues [68]. The pairwise key pre-distribution (CDTKeying) solution proposed by the authors is based on the application of design theory to key distribution, thereby increasing the probability that two nodes will share a key and reducing the length of the key path. Another study to solve the problem of pairwise key establishment in distributed sensor networks was mentioned by the authors in [69]. The authors presented two pre-key distribution schemes including an ID-based one-way function scheme (IOS) and multi-deterministic Blom space scheme (DMBS). The advantages of the proposed method allow the storage capacity to be reduced by using one-way functions to generate secret keys; in addition, the pre-key distribution scheme has high resilience, resistant to spoofing or denial of service attacks.
To support further in WSNs, several pre-key distribution methods [70,71] were studied to enhance the security of the network against various malicious attacks. Based on the probabilistic key mechanism, Eschenauer [72] proposed a mechanism based on random key pre-distribution. In the mechanism, each sensor randomly selects a set of keys that recognize their identity from the key pool before deployment. After determining the public key, two neighboring nodes exchange and compare the identification list of keys in each node’s key chain. Simulation results show that to establish a shared key connection for a network of 10,000 nodes, it is only necessary to distribute a key ring of 250 keys to each sensor node (selected from a pool of 100,000 keys). This is suitable for network scalability. In addition, the security capability of the proposed method based on random graph theory allows for efficient key management, including selective revocation of node keys, management, or node addition/deleting.
Key management methods play an important role in establishing encryption, authentication, and access control of WSN systems. This is to ensure the security of all communication channels in the network. The advantage of key management schemes is their flexibility according to the network structure (LKHW techniques are suitable for small-scale networks, while larger networks with randomly deployed network nodes can deploy techniques such as LEAP, BROSK, and CDTKeying). The choice of key management scheme can be implemented based on the requirements of each specific application including factors such as network size, network node resources, security requirements and scalability. For example, deterministic key schemes are suitable for small-scale networks, randomly deployed, and do not require strict security, while probabilistic key schemes are suitable for larger-scale networks, with better performance, but require more resources.
In addition, some key management protocols show effective resistance to specific attacks. For example, the LEAP protocol can prevent wormhole attacks, HELLO flooding, and node replication; on the other hand, the BROSK protocol shows effectiveness against denial of service attacks, replay attacks, and spoofing attacks. Some key management solutions such as IOS/DMBS and CDTKeying are able to maintain security when the network is expanded. However, the high communication cost and key storage requirements of some protocols are not suitable for nodes with small resources (LEAP with four types of keys requires more memory and energy). In addition, some key management protocols are limited when the network has changes in the number of nodes (additional nodes, dead nodes) or mobile nodes.
3.3. Routing Security Protocol Schemes
Routing security includes two aspects: secure routing and secure data forwarding. In secure routing, nodes are required to cooperate to share accurate routing information, and to keep the network connected efficiently. Secure data forwarding of data packets must be protected from tampering, dropping, or alteration by any unauthorized party. Many routing protocols are specifically designed for WSNs that can be divided into three types according to the network structure: plane-based routing, hierarchy-based routing, and location-based routing [73].
SPINS (Security Protocols for Sensor Networks) is a set of security protocols optimized for WSNs [74]. It provides component protocols including SNEP (Secure Network Encryption Protocol) and μTESLA (micro-Timed Efficient Stream Loss-tolerant Authentication). SNEP is a symmetric encryption (RC5)-based protocol for data confidentiality and authentication, suitable for resource-constrained WSNs. It is effective against replay, eavesdropping, and spoofing attacks. The µTESLA protocol provides an authenticated broadcast protocol, which is an important mechanism for WSNs. µTESLA allows a node to authenticate broadcasting packets received from another node. Authenticity is guaranteed based on keys revealed at each time frame. This helps to prevent spoofing attacks since only the nodes holding valid keys can generate authentic messages. However, the limitation of µTESLA is that it requires authentication time before being accepted, which causes latency and requires large memory to store unauthenticated packets. To solve this problem, the multi-level key chain method was proposed by the authors in [75]. In this method, instead of sending µTESLA parameters via unicast, the authors used a multi-level key chain to distribute the necessary parameters to the network nodes in advance.
In [65], Pietro proposed a directed diffusion extension to the protocol that provides secure multicast functionality. The logical key hierarchy and extension mechanism for WSN (LKHW) ensures efficiency in routing and security. However, this method does not provide a data authentication. In addition, the LEAP protocol [66] uses a one-way key chain for one-hop broadcast authentication. When a node needs to send a message, the next authentication key in the key chain is attached to the message. The authenticated keys are revealed in reverse order of the order in which they are generated. A receiving neighbor node can verify the message based on the received authenticated key.
Secure routing protocols provide secure routing and ensure trust in data forwarding. Protocols such as SPINS (including SNEP and μTESLA) are effective against eavesdropping, spoofing, and replay attacks, while LEAP supports multi-level routing with one-hop broadcast authentication. Some protocols are suitable for resource-constrained network nodes (SPINS uses RC5 symmetric encryption with low computational and communication resource requirements). In addition, multiple routing architectures can be applied for scaling and layering, so that the protocol can be designed to suit the requirements of a specific application.
However, some protocols are not suitable for real-time WSN-IoT applications due to authentication latency (μTESLA requires waiting for key disclosure after a certain time before authentication can be performed). In addition, unauthenticated packets will be temporarily cached at sensor nodes, which greatly affects the operation of large-scale and high-traffic networks.
3.4. Secure Authentication Protocol Schemes
A secure authentication protocol in WSNs focuses on identifying and verifying the identity of sensor nodes in the network to ensure data integrity and confidentiality. The SPIN protocol is a set of security mechanisms that ensure message authentication, data integrity, and confidentiality. SPIN is particularly suitable for operational decentralized sensor networks. To improve the SPIN protocol, Luk [76] proposed a new authentication protocol RPT based on implementing the µTESLA protocol. It accepts urgent and infrequent authentications. However, RPT consumes more resources (computational capacity and energy storage) than the pTESLA protocol does. Luk [76] proposed a second authentication protocol called LEA which uses asymmetric encryption. To be authenticated, the sending node creates a digital signature and sends it along with the data to the receiving node. The signature using the public key is decrypted by the receiving node and compared with the received data to confirm its validity. However, LEA has a size of signature proportional to the size of the message sent. Hence, it requires more storage space. Furthermore, LEA requires a unique public key for each message, forcing the receiving node to store a large number of public keys, leading to high computational cost.
The TinySec protocol was proposed in the work of Karlof [77]. Two versions of the TinySec protocol are proposed without requiring high computational power: TinySec-Auth for authentication and TinySec-AE for encryption and authentication. The protocol is based on symmetric encryption and a 4-byte authentication code (MAC) mechanism which significantly reduces the security overhead. At the same time, by using a mechanism that allows a certain number of authentication attempts, the proposed protocol shows its effectiveness against MAC decryption attacks. The MiniSec protocol was developed by Luk [78] from the SPIN protocol to provide a new authentication mechanism that consumes fewer resources than the Tinsel protocol. This solution is based on a new symmetric encryption algorithm (based on the block cipher OCB—Offset Code Book) with two authentication mechanisms, single authentication (MiniSec-U) and broadcast authentication (MiniSec-B). The simulation results show that MiniSec is more efficient in authentication and security. It also has lower energy costs compared to the TinySec-AE protocol.
Furthermore, several secure authentication protocols were studied, such as the BASIS protocol with multi-user broadcast authentication mechanism based on ID proposed by Kyung-Ah Shim [79]. The MBS-UAKA protocol was designed by Amin [80] for efficient mutual authentication of WSNs with multiple base stations. Roy [81] proposed an efficient two-factor ASKI-WSN mechanism based on ECC to overcome resource constraints and provide an acceptable level of security. The SUBBASe protocol introduced by Riaz [82] aims to authenticate based on the user’s biometrics without using any password or additional hardware device.
In WSN-IoT applications such as medical and military, where data is highly sensitive, authentication protocols are needed to protect against tampering and unauthorized access. Authentication protocols such as TinySec, MiniSec, LEA, RPT, and SUBBASe all focus on ensuring that only authorized entities can join the network and transmit/receive data. Protocols such as MiniSec are suitable for devices with limited resources (MiniSec uses lightweight AES encryption and compact MAC, saving energy and memory). Some protocols are resistant to eavesdropping and tampering attacks (LEA uses ephemeral key agreement mechanism). However, some authentication protocols only focus on authentication from node to sink or vice versa, while modern WSN-IoT applications require bidirectional and multi-point authentication.
3.5. Secure Data Aggregation Schemes
Data aggregation protocols aim to eliminate redundant data transmission over the networks. They are essential for energy-constrained WSNs. Traditional data aggregation techniques include simple query types such as SUM, COUNT, AVERAGE, and MIN/MAX [83]. Secure data aggregation requires authentication, confidentiality, and integrity. This also requires the cooperation of sensor nodes. Figure 7 shows the classification of secure data aggregation tools in WSNs. According to the operation of the protocol, it can be classified into two types: plain text-based and cryptographic-based.
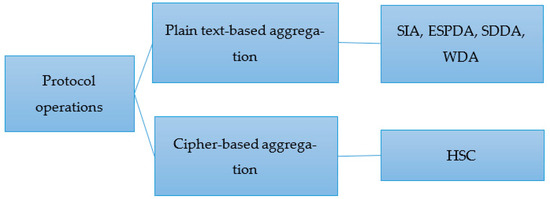
Figure 7.
Secure data aggregation in WSNs.
3.5.1. Secure Data Aggregation Based on Plain Text
Przydatek [84] proposed a SIA security information set for sensor networks. The fabric includes three types of nodes: server, base station nodes, and sensor nodes. The base station is a resource augmentation node used as an intermediary between the server and sensor nodes to perform the aggregation task. Cam [85] also proposed a data aggregation protocol based on the ESPDA energy-efficient safety pattern for WSNs. ESPADA applies to hierarchy-based sensor networks. In ESPDA, the cluster head node at first requests the sensor nodes to send the corresponding sample code for the sensing data. If multiple sensor nodes send the same sample code to the cluster head, only one of them is allowed to send data to the secure ESPDA cluster head since it is not required to decrypt the encoded data by the cluster head nodes for execution. Another method studied by Cam [86] introduced an SDDA data aggregation mechanism based on the sample code. In the SDDA data transmission mechanism, the raw data from sensor nodes are compared with reference data. The reference data are obtained by averaging the previously transmitted data.
Du [87] proposed a data aggregation mechanism based on WDA authentication node for WSN to ensure the authentication of data sent from data aggregation nodes to the base station that proves the validity of the results. As a result, the merged node must provide evidence from several attesting nodes. Each authenticator node calculates the resulting message authentication code (MAC) and then provides it to the data aggregation node, which must forward the information to the base station.
3.5.2. Secure Data Aggregation Based on Cryptography
Castelluccia [88] proposed the HSC solution which is a type of stream cipher capable of performing online homomorphic operations on encrypted data without decryption. This can help to protect the integrity and confidentiality of data being transmitted or processed. The new cipher uses modulo addition, and it is suitable for devices with limited CPUs such as those in WSNs. This cryptographic-based aggregation can be used to efficiently calculate statistical values such as the mean, variance, and standard deviation of the data.
Data aggregation techniques allow information to be aggregated at intermediate nodes before transmitting to the base station. This improves the performance of WSN-IoT networks with high node density by reducing transmission traffic and saving energy. For example, the ESPDA method allows similar data to be grouped and only representative data to be sent, which reduces communication costs and limits data analysis attacks (suitable for WSN-IoT applications in smart agriculture and environmental monitoring where many sensors measure the same type of data). In addition, the data is also protected against eavesdropping and forgery attacks. For example, SIA is an aggregated data authentication solution, suitable for high-precision WSN-IoT applications (medical, hazardous environment monitoring, etc.), while HSC allows aggregation on encrypted data, ensuring end-to-end security without decryption at intermediate nodes. HSC is suitable for systems that require high security (IoT in medical, civil, etc.), against insider attacks. However, data aggregation nodes often become targets of attacks, which leads to unreliable aggregated data. Similarly, legitimate nodes that are compromised and send fake data also distort aggregated data.
3.6. Integrating Blockchain Technology Schemes
Blockchain plays an important role in improving the security of wireless sensor networks (WSNs). Due to its distributed and immutable characteristics, blockchain helps to protect data during transmission, to minimize the risk of attacks, and to detect malicious nodes in such networks. In [89], traditional methods in WSNs rely on centralized decisions, which makes it difficult to trace and reproduce data and unfair to detect malicious nodes. Integrating blockchain into WSNs helps to store data securely and to increase the ability to detect and to eliminate bad nodes through smart contracts and distributed ledgers. The authors of [90] proposed a WSN architecture that uses blockchain to protect transmitted data. Each node in the network can store data in the form of blockchain blocks containing hash values, which helps prevent tampering and ensure data integrity. At the same time, the system also uses algorithms such as Merkel-tree to optimize the encryption and storage process. The authors of [91] proposed a blockchain-based trust management model to eliminate malicious nodes and to ensure network reliability and stability. By using blockchain to record the trust value of each node, this model helps to improve the attack detection performance and to maintain the accuracy of wireless sensor networks.
Blockchain stores data in an immutable way to reduce the risk of data tampering attacks, suitable for WSN-IoT applications that collect sensitive data (health information, location data, etc.) or applications that require transparency (IoT device status management, environmental warnings, etc.). Integrating blockchain will increase the reliability of data because many nodes can agree and verify data. In addition, this method supports strong authentication through digital signatures and hash functions. The distribution of control helps overcome the disadvantages of traditional WSNs (with the sink node being a single point for storing and processing data, and also being the target of attacks). However, this method requires high computing and storage costs and consensus mechanisms (PoW, PBFT…) and blockchain storage requires large computing resources, memory, and energy.
3.7. Intrusion Detection Methods and Trust Models
3.7.1. Intrusion Detection
The security mechanisms discussed above are deployed to prevent malicious nodes from entering the network. However, a valid node in such networks can still be compromised and all encrypted network information can be decrypted. Therefore, a second precaution is needed to increase the level of security. By detecting intrusions to prevent harmful intrusions into the WSN, various intrusion detection solutions are studied and discovered. In Yu’s study [92], an automatic training system was proposed for intrusion detection systems. To detect intrusions, sensor nodes continuously monitor the traffic of neighboring nodes. Parameters for evaluation include collision rate, latency, RTS packet rate, number of neighboring nodes, number of hops, energy consumption, etc. Dimitriou [93] proposed a local algorithm to detect sink node attacks by using the underlying communication mechanism to detect inconsistencies in connectivity between nodes in the network. Hai [94] proposed a method to detect routing attacks in clustered network structures in which a local monitoring agent is installed on all cluster nodes, and a global monitoring agent is deployed in the cluster head node. Hence, all packets sent and received by a sensor node are analyzed by the local agent. The authentication result is given by the cluster head node and is compared with the established threshold value.
3.7.2. Trust Models
In order to strengthen the security level, some studies proposed security mechanisms based on the trust index. These new mechanisms protect networks from malicious attacks that encryption solutions cannot perform. The trust model in a WSN plays a vital role in ensuring the security and reliability of the system [95]. The trust model can help to detect suspicious activities or attacks in sensor networks. Sensor nodes can have their reliability evaluated based on their behavior and the collected data [96,97]. The trust model can be used to optimize resource capacity utilization in the network. Exceptionally reliable sensor nodes can be given priority in the process of sending and receiving data [98,99]. A trust model was proposed in the study of Sivagurunathan [100], in which each node calculates the trust index of its adjacent neighbors based on the statistical information, data values, and recommendations of other neighboring nodes. In the study of Tanachaiwiwat [101], a trust model was proposed to isolate malicious nodes. The cryptographic method is used to calculate the trust index of each node. A node’s position is considered unsafe if the trust index is less than a fixed threshold.
Intrusion detection and remediation models in WSN-IoT are capable of learning normal network behavior and detecting anomalies, including unknown attacks. For example, Sybil, selective forwarding, and wormhole attacks can be detected based on behavioral patterns. At the same time, the monitoring and decision-making process is also automatically executed. However, the deployment of machine learning or deep learning-based models requires heavy resources, so it is not suitable for direct deployment on network nodes. In addition, data quality and data variety play an important role in the training process (machine learning or deep learning-based detection models will be effective when the training data set is complete, labeled, and balanced between normal and abnormal data).
In trust models, metrics such as the number of valid packets, interaction level, abnormal response, etc., are used to detect malicious behavior and increase the accuracy of detecting attacks. However, each WSN-IoT application has different functions and operations, so there will be no common trust index for all systems.
4. Results and Discussion
4.1. In Key Management Protocols
The key management protocol in WSNs plays a vital role in ensuring the security of the system to build and to maintain security, especially in environments with special security risks and limited resources. The choice of key management protocol for WSNs depends on many factors, especially on the computing and communication capabilities of sensor nodes according to the purpose of each specific application.
In this subsection, several key management protocols for sensor networks are considered. The analysis and comparative results show that all the proposed key management protocols have some certain advantages, and all the studies prioritize the ability to balance memory, processing, and communication factors (Table 2). Currently, some proposed key management protocols assume that the base station is trusted (LEAP). However, there might be some situations (e.g., on the battlefield) where a base station security needs to be considered. Therefore, it is necessary to research the design of key management protocols that consider the security of base stations. Additionally, revoking existing nodes and adding new nodes are other challenges when designing key management for WSNs.

Table 2.
Classification and comparison of key management protocols in WSNs.
4.2. In Routing Security Protocols
The routing security protocol must ensure integrity, authentication, and availability. Safety and security depend on the appropriate key management mechanisms in WSNs.
The results of analyzing several routing security protocols (Table 3) show that each protocol has certain advantages and disadvantages, and the choice between them often depends on the specific requirements of specific applications, working environments, and the deployment. The performance of a secure protocol in WSNs depends not only on security but also on energy consumption, latency, and flexibility. Security and performance challenges are often solved through a combination of different methods and protocols. Developing routing security protocols is challenging since sensor nodes are error-prone, and the network topology may change frequently due to either node failures or their mobility. Some proposed secure routing protocols do not consider the mobility factor since WSNs have only static nodes.

Table 3.
Classification and comparison of routing security protocols.
4.3. In Secure Authentication Protocols
Secure authentication protocol is vital in WSNs for ensuring security. The comparative evaluation results in Table 4 show that the SPINS protocol is often chosen for security and performance applications.

Table 4.
Evaluation of advantages and disadvantages of authentication protocols in WSNs.
The TinySec protocol shows the ability to integrate lightweight symmetric encryption, and it is often designed with the goal of optimizing energy consumption, making it suitable for networks with limited resources. The MiniSec protocol provides flexible options for WSN security without complicating the system.
All protocols have certain advantages and disadvantages. Choosing one of them heavily depends on specific requirements of a system and the deployment environments. At the same time, the quality of service (QoS) in WSN needs to be evaluated with the addition of secure routing services.
4.4. In Secure Data Aggregation
Data aggregation is an essential technique to reduce the transmission load and save energy for resource-limited sensor nodes in WSNs. Data aggregation is essential for WSNs and security is required to protect against compromised sensor nodes. Several typical secure data aggregation methods have been studied and implemented. Among them, ESPDA is suitable for sensor networks with high density, homogeneous data, and basic security requirements. SDDA is especially effective in event detection systems (when data only changes significantly in abnormal cases such as forest fires, gas leaks, etc.). However, SDDA requires precision in setup, avoiding errors if the data fluctuates randomly. The resulting authentication method is equal to the aggregation node having to include authentication proofs (e.g., MAC authentication codes) generated by multiple trusted nodes before sending the data to the receiving station, which enhances the reliability and integrity of the data and protects against tampering at the aggregation node, although at the cost of higher communication costs. For applications requiring high levels of privacy and security, HSC allows direct computations on encrypted data (without decryption during transmission and aggregation). In addition, some approaches such as aggregation frameworks with interactive proofs are suitable for large-scale WSNs or high-security environments. In practice, new data aggregation protocols need to be developed to address the issues of scalability and higher reliability to protect against attacks on aggregators and sensor nodes. WSN-IoT systems should flexibly combine multiple methods according to the requirements of specific applications, thereby achieving comprehensive and secure data aggregation. Table 5 shows the number of secure data aggregation protocols mentioned and analyzed.

Table 5.
Secure data aggregation in wireless sensor network security.
4.5. In Integrating Blockchain Technology
The research results show that blockchain is a potential solution to enhance the security of WSNs. In [102], blockchain not only helps protect data from attacks but also optimizes data transmission efficiency and network resource management. In [103], blockchain deployment in WSNs can be widely applied in fields such as environmental monitoring, healthcare, national security, and smart cities. Studies show that blockchain-based security systems help to improve the accuracy of attack detection and maintain service quality in such networks (Table 6). In [104], blockchain can be combined with technologies such as federated machine learning to enhance the detection and classification of security threats in WSNs.

Table 6.
Blockchain application in wireless sensor network security.
One restriction of blockchain application in WSN-IoTs is that the system requires complex computation that leads to excessive energy usage. To solve this problem, the authors [105] proposed the use of efficient consensus algorithms such as Proof of Stake (PoS) or Practical Byzantine Fault Tolerance (PBFT) which significantly reduce energy consumption compared to traditional methods such as Proof of Work (PoW). Simulation results show that blockchain systems applying PBFT can maintain high data transmission efficiency without significantly reducing the lifetime of the networks.
4.6. Opening Research Directions
WSN-IoT is a promising option for many applications in various fields such as smart cities, environmental monitoring, healthcare, etc. At the same time, security is often a major concern with increasingly complex and multi-dimensional requirements. Although much effort has been devoted to cryptography, key management, secure routing, secure data aggregation, and intrusion detection, there are still some critical challenges and gaps that need to be considered.
The integration of WSN-IoT with new platforms (such as NB-IoT, LTE Cat M1, or 6G) [106,107] brings superior scalability and connectivity. However, this poses security challenges due to the asynchrony and incompatibility between protocols. In addition, different integrated service packages will also make it difficult to ensure security standards. Therefore, future security models need to be designed based on self-adaptation, support cross-layer protocols, and adapt to heterogeneous connection environments.
Although some issues related to energy sources have been temporarily solved (such as energy harvesting from the environment, using deep sleep mode) to save energy consumption. However, there are still other issues related to the external working environment of devices in WSNs and IoTs, leading to direct intervention from unauthorized users. Therefore, developing advanced manufacturing technologies such as ultra-power-saving sensors or chip-level hardware security will increase the operating time of nodes, while minimizing the risk of physical attacks in harsh and difficult-to-control environments.
Applying machine learning and deep learning techniques to security tasks in WSN-IoT is a promising research direction. Therefore, it is necessary to focus on lightweight learning models (TinyML), federated learning to optimize operations with limited resources, while still ensuring the prevention of malicious attacks and the detection of abnormal behaviors.
With the development of distributed IoT architecture, the synchronization of secure data and secure information sharing also needs to be considered. Future solutions need to focus on optimizing key sharing, dynamic access control, and data protection according to the requirements of each specific application, and from there, maintain a high level of security while ensuring the performance of the system.
In summary, the proposed future research directions are not only aimed at solving specific technical problems, but also at building a flexible, adaptive, and sustainable security platform for WSN-IoT, especially in the context of diverse applications, diverse connections that are increasingly open and complex.
5. Conclusions and Future Work
This paper addresses a comprehensive study on the primary security concerns of WSN-IoT in a vast field of applications including smart cities. Different kinds of security attacks in WSN-IoT systems are addressed, classified, analyzed and evaluated, including security solutions to protect the systems. It is shown that attacks often focus on data transmission links. Hence, different routing protocols, intrusion detect methods and trust models are considered including solutions to support such networks. We provide a certain number of evaluations, comparative tables with some discussions to provide/suggest different options for suitable choices of security methods depending on the specific purposes of applications. Challenges and future research directions are also discussed. In future work, as the growing research into security fields still plays a vital role in overcoming challenges in building WSN-IoT systems and integrating with other networks, we continue to improve security solutions (such as security protocols, secure routing, key management, and secure data aggregation…) targeting specific WSN-IoT applications. Among the vast of applications and integrated networks, secret sharing schemes would be considered to build stable networks, starting from WSN-IoT applications and expanding to other practical networks.
Author Contributions
Conceptualization, M.L.T., D.T.N. and M.T.N.; methodology, M.D.N. and L.Q.D.; software, M.D.N., T.C.V. and D.T.N.; validation, M.L.T., D.T.N. and M.T.N.; formal analysis, L.Q.D., M.D.N. and T.V.N.; investigation, M.T.N. and D.T.N.; resources, M.D.N. and T.C.V.; data curation, L.Q.D.; writing—original draft preparation, D.T.N., M.T.N. and T.V.N.; writing—review and editing, M.T.N. and M.L.T.; visualization, T.C.V. and L.Q.D.; supervision, M.T.N.; project administration, M.L.T., M.T.N. and T.V.N.; funding acquisition, M.L.T. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Acknowledgments
The authors would like to thank Thai Nguyen University of Technology (TNUT), Viet Nam for the support.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Sharma, H.; Haque, A.; Blaabjerg, F. Machine learning in wireless sensor networks for smart cities: A survey. Electronics 2021, 10, 1012. [Google Scholar] [CrossRef]
- Deebak, B.D.; Al-Turjman, F. A hybrid secure routing and monitoring mechanism in IoT-based wireless sensor networks. Ad Hoc Netw. 2020, 97, 102022. [Google Scholar]
- Nguyen, M.T.; Rahnavard, N. Cluster-based energy-efficient data collection in wireless sensor networks utilizing compressive sensing. In Proceedings of the MILCOM 2013–2013 IEEE Military Communications Conference, San Diego, CA, USA, 18–20 November 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 1708–1713. [Google Scholar]
- Yamini, B.; Pradeep, G.; Kalaiyarasi, D.; Jayaprakash, M.; Janani, G.; Uthayakumar, G.S. Theoretical study and analysis of advanced wireless sensor network techniques in Internet of Things (IoT). Meas. Sens. 2024, 33, 101098. [Google Scholar] [CrossRef]
- Yadav, G.; Srivastava, G.; Shrivastava, A.; Monika; Sharma, S. Wsn, iot & rfid integrated solutions for smart cities & industries: Introduction, applications, framework and challenges. In Proceedings of the 2024 2nd International Conference on Disruptive Technologies (ICDT), Greater Noida, India, 15–16 March 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1128–1135. [Google Scholar]
- Kandris, D.; Anastasiadis, E. Advanced wireless sensor networks: Applications, challenges and research trends. Electronics 2024, 13, 2268. [Google Scholar] [CrossRef]
- Vishwakarma, A.K.; Chaurasia, S.; Kumar, K.; Singh, Y.N.; Chaurasia, R. Internet of things technology, research, and challenges: A survey. Multimed. Tools Appl. 2024, 84, 8455–8490. [Google Scholar] [CrossRef]
- Nguyen, M.T.; Nguyen, V.-C.; Nguyen, H.N. Visualization-based monitoring in early warning systems with wireless sensor networks. Indones. J. Electr. Eng. Comput. Sci. 2023, 31, 281–289. [Google Scholar] [CrossRef]
- Ram, G.M.; Ilavarasan, E. Security Challenges in Wireless Sensor Network: Current Status and Future Trends. Wirel. Pers. Commun. 2024, 139, 1173–1202. [Google Scholar] [CrossRef]
- Faris, M.; Mahmud, M.N.; Salleh, M.F.M.; Alnoor, A. Wireless sensor network security: A recent review based on state-of-the-art works. Int. J. Eng. Bus. Manag. 2023, 15, 18479790231157220. [Google Scholar] [CrossRef]
- Samha, A.K.; Alshammri, G.H.; Pani, N.K.; Misra, Y.; Kolluru, V.R. Privacy-Preserving Wireless Sensor Networks for E-Healthcare Applications. Int. J. Coop. Inf. Syst. 2024, 34, 2450006. [Google Scholar] [CrossRef]
- Singh, K.; Yadav, M.; Singh, Y.; Barak, D. Finding security gaps and vulnerabilities in IoT devices. In Revolutionizing Automated Waste Treatment Systems: IoT and Bioelectronics; IGI Global: Hershey, PA, USA, 2024; pp. 379–395. [Google Scholar]
- Hasan, M.Z.; Mohd Hanapi, Z. Efficient and secured mechanisms for data link in IoT WSNs: A literature review. Electronics 2023, 12, 458. [Google Scholar] [CrossRef]
- Adu-Manu, K.S.; Engmann, F.; Sarfo-Kantanka, G.; Baiden, G.E.; Dulemordzi, B.A.; Zhang, Z. WSN protocols and security challenges for environmental monitoring applications: A survey. J. Sens. 2022, 2022, 1628537. [Google Scholar] [CrossRef]
- Panahi, U.; Bayılmış, C. Enabling secure data transmission for wireless sensor networks based IoT applications. Ain Shams Eng. J. 2023, 14, 101866. [Google Scholar] [CrossRef]
- Hameed, A.; Alomary, A. Security issues in IoT: A survey. In Proceedings of the 2019 International conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Sakhier, Bahrain, 22–23 September 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [Google Scholar]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Harbi, Y.; Aliouat, Z.; Harous, S.; Bentaleb, A.; Refoufi, A. A review of security in internet of things. Wirel. Pers. Commun. 2019, 108, 325–344. [Google Scholar] [CrossRef]
- Jurcut, A.; Niculcea, T.; Ranaweera, P.; Le-Khac, N.-A. Security considerations for Internet of Things: A survey. SN Comput. Sci. 2020, 1, 193. [Google Scholar] [CrossRef]
- Haseeb, K.; Islam, N.; Almogren, A.; Din, I.U. Intrusion prevention framework for secure routing in WSN-based mobile Internet of Things. IEEE Access 2019, 7, 185496–185505. [Google Scholar] [CrossRef]
- Islam, M.N.U.; Fahmin, A.; Hossain, S.; Atiquzzaman, M. Denial-of-service attacks on wireless sensor network and defense techniques. Wirel. Pers. Commun. 2021, 116, 1993–2021. [Google Scholar] [CrossRef]
- Vinayakumar, R.; Alazab, M.; Soman, K.P.; Poornachandran, P.; Al-Nemrat, A.; Venkatraman, S. Deep learning approach for intelligent intrusion detection system. IEEE Access 2019, 7, 41525–41550. [Google Scholar] [CrossRef]
- Liu, H.; Lang, B. Machine learning and deep learning methods for intrusion detection systems: A survey. Appl. Sci. 2019, 9, 4396. [Google Scholar] [CrossRef]
- Talukder, A.; Sharmin, S.; Uddin, A.; Islam, M.; Aryal, S. MLSTL-WSN: Machine learning-based intrusion detection using SMOTETomek in WSNs. Int. J. Inf. Secur. 2024, 23, 2139–2158. [Google Scholar] [CrossRef]
- Nguyen, M.T.; Teague, K.A.; Rahnavard, N. CCS: Energy-efficient data collection in clustered wireless sensor networks utilizing block-wise compressive sensing. Comput. Netw. 2016, 106, 171–185. [Google Scholar] [CrossRef]
- Coboi, A.; Nguyen, M.T.; Primeiro, I.Z.; Van Nam, P.; Van Huy, B.; Ta, T.M.; Nguyen, T.T. Towards Multiple Sources for Energy Harvesting in Wireless Sensor Networks in Practical Applications. Comput. Netw. Commun. 2024, 2, 123–145. [Google Scholar] [CrossRef]
- Coboi, A.; Nguyen, M.T.; Pham, V.N.; Vu, T.C.; Nguyen, M.D.; Nguyen, D.T. Zigbee Based Mobile Sensing for Wireless Sensor Networks. Comput. Netw. Commun. 2023, 1, 325–342. [Google Scholar] [CrossRef]
- Abidoye, A.P.; Obagbuwa, I.C. Models for integrating wireless sensor networks into the Internet of Things. IET Wirel. Sens. Syst. 2017, 7, 65–72. [Google Scholar] [CrossRef]
- Khan, W.Z.; Rehman, M.H.; Zangoti, H.M.; Afzal, M.K.; Armi, N.; Khaled, S. Industrial internet of things: Recent advances, enabling technologies and open challenges. Comput. Electr. Eng. 2020, 81, 106522. [Google Scholar] [CrossRef]
- Nguyen, M.T. An energy-efficient framework for multimedia data routing in internet of things (iots). EAI Endorsed Trans. Ind. Netw. Intell. Syst. 2019, 19, e1. [Google Scholar] [CrossRef][Green Version]
- Din, I.U.; Guizani, M.; Hassan, S.; Kim, B.-S.; Khan, M.K.; Atiquzzaman, M.; Ahmed, S.H. The Internet of Things: A review of enabled technologies and future challenges. IEEE Access 2018, 7, 7606–7640. [Google Scholar] [CrossRef]
- Jawhar, I.; Mohamed, N.; Al-Jaroodi, J. Networking architectures and protocols for smart city systems. J. Internet Serv. Appl. 2018, 9, 26. [Google Scholar] [CrossRef]
- Ng, H.S.; Sim, M.L.; Tan, C.M. Security issues of wireless sensor networks in healthcare applications. BT Technol. J. 2006, 24, 138–144. [Google Scholar] [CrossRef]
- Keerthika, M.; Shanmugapriya, D. Wireless sensor networks: Active and passive attacks-vulnerabilities and countermeasures. Glob. Transit. Proc. 2021, 2, 362–367. [Google Scholar] [CrossRef]
- Silpa, C.; Niranjana, G.; Ramani, K. Securing data from active attacks in IoT: An extensive study. In Proceedings of the International Conference on Deep Learning, Computing and Intelligence (ICDCI 2021), Chennai, India, 7–8 January 2021; Springer Nature: Singapore, 2022; pp. 51–64. [Google Scholar]
- Illi, E.; Qaraqe, M.; Althunibat, S.; Alhasanat, A.; Alsafasfeh, M.; De Ree, M.; Mantas, G.; Rodriguez, J.; Aman, W.; Al-Kuwari, S. Physical layer security for authentication, confidentiality, and malicious node detection: A paradigm shift in securing IoT networks. IEEE Commun. Surv. Tutor. 2023, 26, 347–388. [Google Scholar] [CrossRef]
- Zhu, J.; Zou, Y.; Zheng, B. Physical-layer security and reliability challenges for industrial wireless sensor networks. IEEE Access 2017, 5, 5313–5320. [Google Scholar] [CrossRef]
- Smache, M.; El Mrabet, N.; Gilquijano, J.-J.; Tria, A.; Riou, E.; Gregory, C. Modeling a node capture attack in a secure wireless sensor networks. In Proceedings of the 2016 IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, USA, 12–14 December 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 188–193. [Google Scholar]
- Conti, M.; Di Pietro, R.; Mancini, L.; Mei, A. Distributed detection of clone attacks in wireless sensor networks. IEEE Trans. Dependable Secur. Comput. 2010, 8, 685–698. [Google Scholar] [CrossRef]
- Mahalakshmi, G.; Subathra, P. A survey on prevention approaches for denial of sleep attacks in wireless networks. J. Emerg. Technol. Web Intell. 2014, 6, 106–110. [Google Scholar] [CrossRef][Green Version]
- Lin, H.-T.; Liang, Y.-Y. A PUF-based secure wake-up scheme for Internet of Things. Comput. Secur. 2021, 110, 102415. [Google Scholar] [CrossRef]
- Lin, D.; Wang, Q.; Min, W.; Xu, J.; Zhang, Z. A survey on energy-efficient strategies in static wireless sensor networks. ACM Trans. Sens. Netw. (TOSN) 2022, 17, 1–48. [Google Scholar] [CrossRef]
- Najafabadi, S.G.; Naji, H.R.; Mahani, A. Sybil attack Detection: Improving security of WSNs for smart power grid application. In Proceedings of the 2013 Smart Grid Conference (SGC), Tehran, Iran, 17–18 December 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 273–278. [Google Scholar]
- Bansal, V.; Saluja, K.K. Anomaly based detection of Black Hole Attack on leach protocol in WSN. In Proceedings of the 2016 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 23–25 March 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1924–1928. [Google Scholar]
- Alajmi, N.M.; Elleithy, K. A new approach for detecting and monitoring of selective forwarding attack in wireless sensor networks. In Proceedings of the 2016 IEEE Long Island Systems, Applications and Technology Conference (LISAT), Farmingdale, NY, USA, 29 April 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–6. [Google Scholar]
- Amish, P.; Vaghela, V. Detection and prevention of wormhole attack in wireless sensor network using AOMDV protocol. Procedia Comput. Sci. 2016, 79, 700–707. [Google Scholar] [CrossRef]
- Jin, Q.; Tang, H.; Kuang, X.; Liu, Q. Detection and defence of Sinkhole attack in Wireless Sensor Network. In Proceedings of the 2012 IEEE 14th International Conference on Communication Technology, Chengdu, China, 9–11 November 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 809–813. [Google Scholar]
- Sharma, S.; Jena, S.K. A survey on secure hierarchical routing protocols in wireless sensor networks. In Proceedings of the 2011 International Conference on Communication, Computing & Security, Rourkela, India, 12–14 February 2011; pp. 146–151. [Google Scholar]
- Sharma, N.; Kaushik, I.; Agarwal, V.K.; Bhushan, B.; Khamparia, A. Attacks and security measures in wireless sensor network. In Intelligent Data Analytics for Terror Threat Prediction: Architectures, Methodologies, Techniques and Applications; Wiley: Hoboken, NJ, USA, 2021; pp. 237–268. [Google Scholar]
- Yousefpoor, M.S.; Yousefpoor, E.; Barati, H.; Barati, A.; Movaghar, A.; Hosseinzadeh, M. Secure data aggregation methods and countermeasures against various attacks in wireless sensor networks: A comprehensive review. J. Netw. Comput. Appl. 2021, 190, 103118. [Google Scholar] [CrossRef]
- Ahemd, M.M.; Shah, M.A.; Wahid, A. IoT security: A layered approach for attacks & defenses. In Proceedings of the 2017 International Conference on Communication Technologies (ComTech), Rawalpindi, Pakistan, 19–21 April 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 104–110. [Google Scholar]
- Ebrahimi, Y.; Younis, M. Energy-aware cross-layer technique for countering traffic analysis attacks on wireless sensor network. IEEE Access 2022, 10, 131036–131052. [Google Scholar] [CrossRef]
- Arulselvan, J.; Bharani, K.E.; Manoj Kumar, S.; Balachandran, A. Secured RSA Algorithm Based Healthcare Monitoring System for IoT Devices. In Proceedings of the 2023 3rd International Conference on Pervasive Computing and Social Networking (ICPCSN), Salem, India, 19–20 June 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1098–1106. [Google Scholar]
- Yadav, S.K.; Jha, S.K.; Singh, S.; Sharma, U.K.; Dixit, P.; Prakash, S.; Gangwar, A. An Efficient Model for IoT Security Using Adopted RSA. In Proceedings of the Third International Conference on Information Management and Machine Intelligence (ICIMMI), Jaipur, India, 23–24 December 2021; Springer Nature: Singapore, 2022; pp. 59–64. [Google Scholar]
- Gulen, U.; Baktir, S. Side-channel resistant 2048-bit RSA implementation for wireless sensor networks and internet of things. IEEE Access 2023, 11, 39531–39543. [Google Scholar] [CrossRef]
- Mahto, D.; Yadav, D.K. RSA and ECC: A comparative analysis. Int. J. Appl. Eng. Res. 2017, 12, 9053–9061. [Google Scholar]
- Quasim, M.T.; Alghamdi, N.S.; Khan, M.Y. A secure framework for authentication and encryption using improved ECC for IoT-based medical sensor data. IEEE Access 2020, 8, 52018–52027. [Google Scholar]
- Ganesan, P.; Venugopalan, R.; Peddabachagari, P.; Dean, A.; Mueller, F.; Sichitiu, M. Analyzing and modeling encryption overhead for sensor network nodes. In Proceedings of the 2nd ACM International Conference on Wireless Sensor Networks and Applications, San Diego, CA, USA, 19 September 2003; pp. 151–159. [Google Scholar]
- Menezes, A.; Van Oorschot, C.; Vanstone, S. Handbook of Applied Cryptography; CRC Press: Boca Raton, FL, USA, 2018. [Google Scholar]
- Zhu, D.; Tong, X.; Wang, Z.; Zhang, M. A novel lightweight block encryption algorithm based on combined chaotic system. J. Inf. Secur. Appl. 2022, 69, 103289. [Google Scholar] [CrossRef]
- Eastlake, D., 3rd; Jones, P. Rfc3174: Us Secure Hash Algorithm 1 (Sha1). 2001. Available online: https://datatracker.ietf.org/doc/html/rfc3174 (accessed on 13 July 2025).
- Sudharshan, R.; Yogesh, P.; Prathiba, A. Enhancing AES Security and Performance: A Novel 8-bit Architecture with Unique Key Expansion for IoT Applications. In Proceedings of the 2024 IEEE Silchar Subsection Conference (SILCON 2024), Agartala, India, 15–17 November 2024; IEEE: Piscataway, NJ, USA, 2024; pp. 1–6. [Google Scholar]
- Ahmed, S.; Ahmad, N.; Shah, N.A.; Abro, G.E.M.; Wijayanto, A.; Hirsi, A.; Altaf, A.R. Lightweight AES Design for IoT Applications: Optimizations in FPGA and ASIC with DFA Countermeasure Strategies. IEEE Access 2025, 13, 22489–22509. [Google Scholar] [CrossRef]
- Tsai, K.-L.; Leu, F.-Y.; You, I.; Chang, S.-W.; Hu, S.-J.; Park, H. Low-power AES data encryption architecture for a LoRaWAN. IEEE Access 2019, 7, 146348–146357. [Google Scholar] [CrossRef]
- Di Pietro, R.; Mancini, L.; Law, Y.W.; Etalle, S.; Havinga, P. LKHW: A directed diffusion-based secure multicast scheme for wireless sensor networks. In Proceedings of the 2003 International Conference on Parallel Processing Workshops, Kaohsiung, Taiwan, 6–9 October 2003; IEEE: Piscataway, NJ, USA, 2003; pp. 397–406. [Google Scholar]
- Zhu, S.; Setia, S.; Jajodia, S. LEAP + Efficient security mechanisms for large-scale distributed sensor networks. ACM Trans. Sens. Netw. (TOSN) 2006, 2, 500–528. [Google Scholar] [CrossRef]
- Lai, B.; Kim, S.; Verbauwhede, I. Scalable session key construction protocol for wireless sensor networks. In Proceedings of the IEEE Workshop on Large Scale RealTime and Embedded Systems (LARTES), Austin, TX, USA, 3–5 December 2002; Volume 7. [Google Scholar]
- Camtepe, S.A.; Yener, B. Combinatorial design of key distribution mechanisms for wireless sensor networks. IEEE/ACM Trans. Netw. 2007, 15, 346–358. [Google Scholar] [CrossRef]
- Lee, J.; Douglas, R.S. Deterministic key predistribution schemes for distributed sensor networks. In International Workshop on Selected Areas in Cryptography; Springer: Berlin/Heidelberg, Germany, 2004; pp. 294–307. [Google Scholar]
- Chan, H.; Perrig, A.; Song, D. Random key predistribution schemes for sensor networks. In Proceedings of the 2003 Symposium on Security and Privacy, Berkeley, CA, USA, 11–14 May 2003; IEEE: Piscataway, NJ, USA, 2003; pp. 197–213. [Google Scholar]
- Huang, H.-F. A pairwise key pre-distribution scheme for wireless sensor network. In Proceedings of the Intelligence and Security Informatics: IEEE ISI 2008 International Workshops: PAISI, PACCF, and SOCO 2008, Taipei, Taiwan, 17 June 2008; Springer: Berlin/Heidelberg, Germany, 2008. Proceedings 6. pp. 77–82. [Google Scholar]
- Eschenauer, L.; Gligor, V.D. A key-management scheme for distributed sensor networks. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 41–47. [Google Scholar]
- Bhushan, B.; Gadadhar, S. Recent advances in attacks, technical challenges, vulnerabilities and their countermeasures in wireless sensor networks. Wirel. Pers. Commun. 2018, 98, 2037–2077. [Google Scholar] [CrossRef]
- Fasee, U.; Mehmood, T.; Habib, M.; Ibrahim, M.; Zulfikar, S. SPINS: Security protocols for sensor networks. In Proceedings of the International Conference on Communication Engineering and Networks (IPCSIT’11), Hong Kong, China, 25–27 November 2011. [Google Scholar]
- Liu, D.; Peng, N. Efficient Distribution of Key Chain Commitments for Broadcast Authentication in Distributed Sensor Networks. In Proceedings of the NDSS Symposium 2003, San Diego, CA, USA, 6 February 2003. [Google Scholar]
- Luk, M.; Perrig, A.; Whillock, B. Seven cardinal properties of sensor network broadcast authentication. In Proceedings of the Fourth ACM Workshop on Security of ad Hoc and Sensor Networks, Alexandria, VA, USA, 30 October 2006; pp. 147–156. [Google Scholar]
- Karlof, C.; Sastry, N.; Wagner, D. TinySec: A link layer security architecture for wireless sensor networks. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, MD, USA, 3–5 November 2004; pp. 162–175. [Google Scholar]
- Luk, M.; Mezzour, G.; Perrig, A.; Gligor, V. MiniSec: A secure sensor network communication architecture. In Proceedings of the 6th International Conference on Information Processing in Sensor Networks, Cambridge, MA, USA, 25–27 April 2007; pp. 479–488. [Google Scholar]
- Shim, K.-A. BASIS: A practical multi-user broadcast authentication scheme in wireless sensor networks. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1545–1554. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.; Obaidat, M.S. A robust mutual authentication protocol for WSN with multiple base-stations. Ad Hoc Netw. 2018, 75, 1–18. [Google Scholar] [CrossRef]
- Roy, P.K.; Parai, K.; Hasnat, A. User authentication with session key interchange for wireless sensor network. In Methodologies and Application Issues of Contemporary Computing Framework; Springer: Singapore, 2018; pp. 153–165. [Google Scholar]
- Riaz, R.; Gillani, N.-U.; Rizvi, S.; Shokat, S.; Kwon, S.J. SUBBASE: An authentication scheme for wireless sensor networks based on user biometrics. Wirel. Commun. Mob. Comput. 2019, 2019, 6370742. [Google Scholar] [CrossRef]
- Shrivastava, N.; Buragohain, C.; Agrawal, D.; Suri, S. Medians and beyond: New aggregation techniques for sensor networks. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, MD, USA, 3–5 November 2004; pp. 239–249. [Google Scholar]
- Przydatek, B.; Song, D.; Perrig, A. SIA: Secure information aggregation in sensor networks. In Proceedings of the 1st International Conference on Embedded Networked Sensor Systems, Los Angeles, CA, USA, 5–7 November 2003; pp. 255–265. [Google Scholar]
- Cam, H.; Ozdemir, S.; Muthuavinashiappan, D.; Nair, P. Energy efficient security protocol for wireless sensor networks. In Proceedings of the 2003 IEEE 58th Vehicular Technology Conference, VTC 2003-Fall (IEEE Cat. No. 03CH37484), Orlando, FL, USA, 6–9 October 2003; IEEE: Piscataway, NJ, USA, 2003; Volume 5, pp. 2981–2984. [Google Scholar]
- Begum, B.A.; Nandury, S.V. Data aggregation protocols for WSN and IoT applications–A comprehensive survey. J. King Saud Univ.-Comput. Inf. Sci. 2023, 35, 651–681. [Google Scholar] [CrossRef]
- Du, W.; Deng, J.; Han, Y.; Varshney, P. A witness-based approach for data fusion assurance in wireless sensor networks. In Proceedings of the GLOBECOM’03, IEEE Global Telecommunications Conference (IEEE Cat. No. 03CH37489), San Francisco, CA, USA, 1–5 December 2003; IEEE: Piscataway, NJ, USA, 2003; Volume 3, pp. 1435–1439. [Google Scholar]
- Castelluccia, C.; Mykletun, E.; Tsudik, G. Efficient aggregation of encrypted data in wireless sensor networks. In Proceedings of the Second Annual International Conference on Mobile and Ubiquitous Systems: Networking and Services, San Diego, CA, USA, 17–21 July 2005; IEEE: Piscataway, NJ, USA, 2005; pp. 109–117. [Google Scholar]
- Ramasamy, L.K.; Khan, F.; Imoize, A.L.; Ogbebor, J.O.; Kadry, S.; Rho, S. Blockchain-based wireless sensor networks for malicious node detection: A survey. IEEE Access 2021, 9, 128765–128785. [Google Scholar] [CrossRef]
- Hsiao, S.-J.; Sung, W.-T. Employing blockchain technology to strengthen security of wireless sensor networks. IEEE Access 2021, 9, 72326–72341. [Google Scholar] [CrossRef]
- Kim, T.-H.; Goyat, R.; Rai, M.K.; Kumar, G.; Buchanan, W.J.; Saha, R.; Thomas, R. A novel trust evaluation process for secure localization using a decentralized blockchain in wireless sensor networks. IEEE Access 2019, 7, 184133–184144. [Google Scholar] [CrossRef]
- Yu, Z.; Tsai, J.J.P. A framework of machine learning based intrusion detection for wireless sensor networks. In Proceedings of the 2008 IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC 2008), Taichung, Taiwan, 11–13 June 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 272–279. [Google Scholar]
- Dimitriou, T.; Giannetsos, A. Wormholes no more? localized wormhole detection and prevention in wireless networks. In Proceedings of the Distributed Computing in Sensor Systems: 6th IEEE International Conference, DCOSS 2010, Santa Barbara, CA, USA, 21–23 June 2010; Springer: Berlin/Heidelberg, Germany, 2010. Proceedings 6. pp. 334–347. [Google Scholar]
- Hai, T.H.; Huh, E.N.; Jo, M. A lightweight intrusion detection framework for wireless sensor networks. Wirel. Commun. Mob. Comput. 2010, 10, 559–572. [Google Scholar] [CrossRef]
- Souissi, I.; Ben Azzouna, N.; Ben Said, L. A multi-level study of information trust models in WSN-assisted IoT. Comput. Netw. 2019, 151, 12–30. [Google Scholar] [CrossRef]
- Alhandi, S.A.; Kamaludin, H.; Alduais, N.A.M. Trust evaluation model in IoT environment: A comprehensive survey. IEEE Access 2023, 11, 11165–11182. [Google Scholar] [CrossRef]
- Javaid, N. A secure and efficient trust model for wireless sensor IoTs using blockchain. IEEE Access 2022, 10, 4568–4579. [Google Scholar] [CrossRef]
- Khan, T.; Singh, K. Resource management based secure trust model for WSN. J. Discret. Math. Sci. Cryptogr. 2019, 22, 1453–1462. [Google Scholar] [CrossRef]
- She, W.; Liu, Q.; Tian, Z.; Chen, J.-S.; Wang, B.; Liu, W. Blockchain trust model for malicious node detection in wireless sensor networks. IEEE Access 2019, 7, 38947–38956. [Google Scholar] [CrossRef]
- Sivagurunathan, S.; Prathapchandran, K. Trust Based Security Schemes in Mobile Ad Hoc Networks-A Review. In Proceedings of the 2014 International Conference on Intelligent Computing Applications, Coimbatore, India, 6–7 March 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 291–295. [Google Scholar]
- Tanachaiwiwat, S.; Dave, P.; Bhindwale, R.; Helmy, A. Location-centric isolation of misbehavior and trust routing in energy-constrained sensor networks. In Proceedings of the IEEE International Conference on Performance, Computing, and Communications, 2004, Phoenix, AZ, USA, 15–17 April 2004; IEEE: Piscataway, NJ, USA, 2004; pp. 463–469. [Google Scholar]
- Hsiao, S.-J.; Sung, W.-T. Utilizing blockchain technology to improve WSN security for sensor data transmission. Comput. Mater. Contin. 2021, 68, 1899–1918. [Google Scholar] [CrossRef]
- Gebremariam, G.G.; Panda, J.; Indu, S.; Prieto, J. Blockchain-Based Secure Localization against Malicious Nodes in IoT-Based Wireless Sensor Networks Using Federated Learning. Wirel. Commun. Mob. Comput. 2023, 2023, 8068038. [Google Scholar] [CrossRef]
- Bukhari, S.M.S.; Zafar, M.H.; Houran, M.A.; Moosavi, S.K.R.; Mansoor, M.; Muaaz, M.; Sanfilippo, F. Secure and privacy-preserving intrusion detection in wireless sensor networks: Federated learning with SCNN-Bi-LSTM for enhanced reliability. Ad Hoc Netw. 2024, 155, 103407. [Google Scholar] [CrossRef]
- Chanana, R.; Singh, A.K.; Killa, R.; Agarwal, S.; Mehra, P.S. Blockchain based secure model for sensor data in wireless sensor network. In Proceedings of the 2020 6th International Conference on Signal Processing and Communication (ICSC), Noida, India, 5–7 March 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 288–293. [Google Scholar]
- Wang, S.-Y.; Chang, J.-E.; Fan, H.; Sun, Y.-H. Comparing the performance of NB-IoT, LTE Cat-M1, Sigfox, and LoRa for IoT end devices moving at high speeds in the air. J. Signal Process. Syst. 2022, 94, 81–99. [Google Scholar] [CrossRef]
- Maraveas, C.; Loukatos, D.; Arvanitis, K.G. Intelligent sensors: Wireless sensor networks and Internet of Things. In Nature-Derived Sensors; Elsevier: Amsterdam, The Netherlands, 2025; pp. 295–339. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).