Integrating Physical Unclonable Functions with Machine Learning for the Authentication of Edge Devices in IoT Networks
Abstract
1. Introduction
- Grasping the concept of PUFs and their performance metrics, supported by illustrative examples.
- The development of a basic Arbiter PUF, focusing on the placement and routing of the switch blocks and logic elements. The design is deployed on an ALINX 400 board from Alinx Electronic Limited, Shanghai, China, featuring an Altera Cyclone IV FPGA to assess its PUF performance metrics.
- The utilization of Arbiter PUFs in security protocols and the design of a structure that integrates an Arbiter PUF to resist ML attacks.
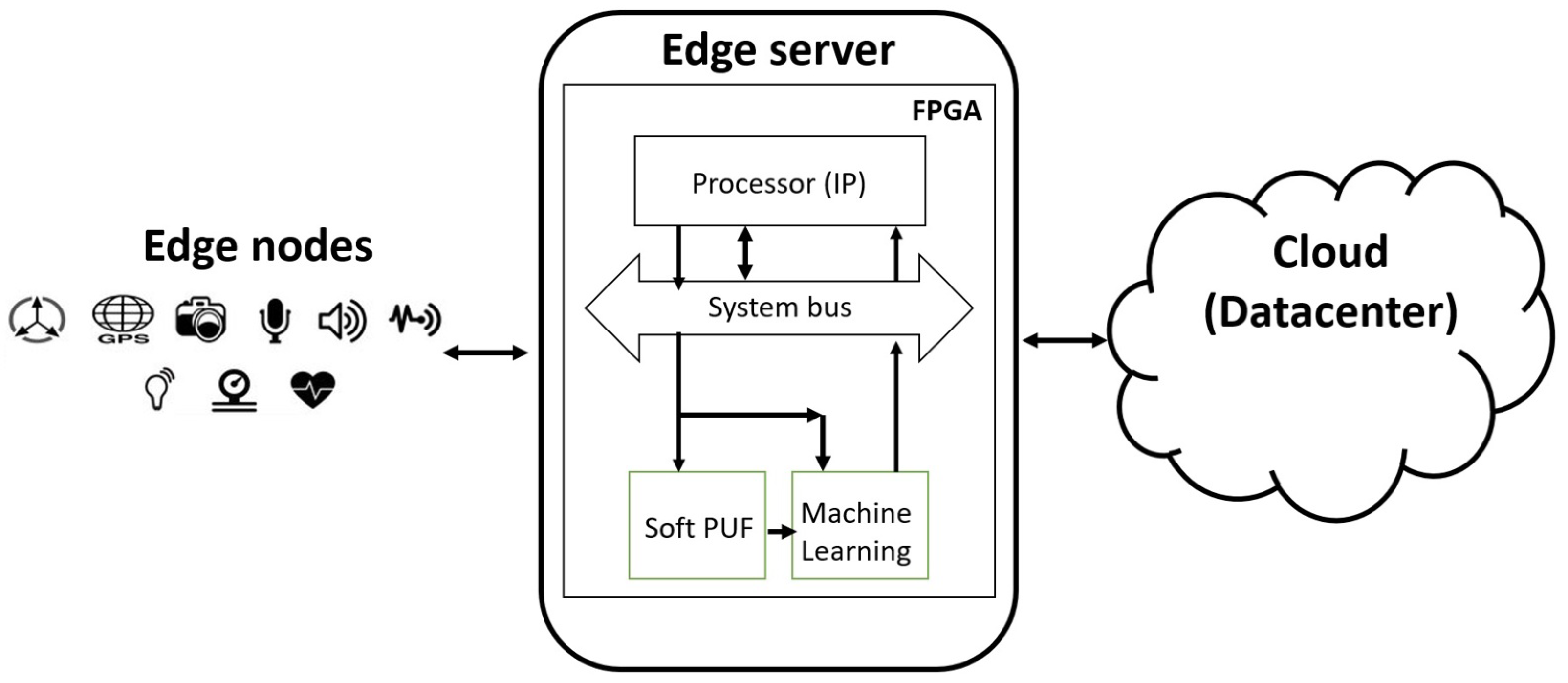
2. Edge Computing
2.1. Security and Privacy Challenges
2.1.1. Data Security and Privacy Threats Classification
2.1.2. Data Security Measures
- Data anonymization and pseudonymization: Anonymization drops the personally identifiable information (PII) from datasets, thus preventing their association with individuals during data analysis [43]. In contrast, pseudonymization is the processing of personal data so that it cannot be linked to a specific individual without additional information [44].
- Encryption: Data encryption converts data into an unreadable format, accessible only through specific secret information, commonly referred to as a key [45]. Lightweight encryption is ideal for resource-constrained edge devices, while blockchain-based encryption secures decentralized edge networks through immutability.
- Differential privacy (DP): The DP technique adds random noise to data, obscuring users’ sensitive information before it is shared on the network. Unlike traditional privacy protection methods, DP focuses on protecting individual data rather than the entire dataset [47].
- Federated Learning (FL): FL enables the training of deep learning models across multiple participants or computing nodes while keeping data security and privacy intact. It supports the collaborative training of ML and DL models by leveraging local data on edge devices and sending only the updated model parameters to a central cloud server [48].
- Access control and authentication: Edge devices frequently join and leave IoT networks dynamically, necessitating a connectivity framework that ensures security by authenticating the various devices within the network. Additionally, an access control mechanism should govern and monitor authorization to regulate access to network resources [49].
- Trusted execution environments (TEEs): TEEs provide a hardware-based secure sandbox to shield sensitive programs. A TEE establishes a secure and isolated region within edge devices through the application of both hardware and software techniques [50,51]. It typically includes key components such as secure bootstrapping, which ensures the system initializes in a trusted state; isolated execution, which safeguards data and computations; and secure input/output mechanisms, such as sealed storage for protecting data at rest. TEEs also support remote attestation, enabling a remote party to verify the integrity and trustworthiness of a communication peer within the TEE [52].
- Blockchains for decentralized security: Blockchain is a shared, decentralized, and distributed state machine in which a chain of blocks is linked through address pointers based on hash values [53]. A peer-to-peer model facilitates the storage and management of ledger data across multiple computers within the network. Integrating blockchain enables the distribution of computing and storage resources within the EC environment while also reducing the blockchain’s storage and computational load on performance-sensitive devices [54].
- Secure software and firmware updates: The use of software or firmware updates can help reduce potential threats posed by the malicious actions of cybercriminals [55]. IoT devices rely on Over-the-Air (OTA) updates throughout their lifecycle to address bugs and apply patches to their firmware. However, a device’s security can be compromised if the server-side firmware database is breached [56].
- Data minimization: This technique reduces the collection, processing, and storage of redundant data, thereby mitigating the risks of data breaches, unauthorized access, and misuse. This can be achieved through deduplication, which eliminates redundancy by retaining only a single copy of the data [57].
- Policy-based governance: Cultural beliefs, legal frameworks, and ethical practices collectively shape the concept of privacy. The General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) aim to protect privacy rights through effective data management [58].
- Edge-aware intrusion detection systems (IDSs): An IDS is a software- or hardware-based solution designed to detect malicious activities on data networks. IDSs can be categorized into two classes based on their detection approach: signature-based and anomaly-based techniques. A signature-based system compares monitored events against a database of known intrusion techniques, while an anomaly-based system learns the system’s normal behavior and flags any deviations [59].
- Secure multi-party computation (SMPC): It is a cryptographic method that enables collaborative computations among multiple participants [60]. The protocol ensures that no participant gains access to information beyond the final computational results, provided that at least some participants follow the protocol. It restricts access to inputs, intermediate computations, and metadata such as value frequency distributions [61]. Consequently, SMPC eliminates the need for a trusted third party, as all computations are carried out exclusively by the participants [62].
- Privacy-preserving AI models: AI-based applications enable real-time anomaly detection, allowing systems to identify and mitigate potential threats. Machine learning (ML) algorithms analyze network data patterns to predict vulnerabilities and implement countermeasures [63]. Edge AI deploys ML algorithms on end devices, enabling data processing at the network edge [64]. Integrating AI with edge computing (EC) also promotes context-aware processing and decision-making directly on edge devices [65].
- Audit and monitoring: The integrity of user data at the edge is crucial for network operations and often relies on a third-party auditing platform (TPA) [66]. Networks that implement stringent security policies should be audited using data that includes authentication and authorization attempts [40]. Security audit methodologies incorporate cyber risk management, cybersecurity assessments, compliance evaluations, penetration testing, intrusion simulations, and emulation simulations [67].
- Emerging trends: Quantum computing is an emerging technology that leverages quantum bits (qubits) instead of binary digits, enabling significantly faster computations than traditional computers. Quantum-Edge Cloud Computing (QECC) is an innovative approach that combines the computational power of quantum computing, the low-latency advantages of EC, and the scalability of cloud computing [68]. Another approach gaining traction is AI-powered EC, which deploys ML models for efficient, secure, and effective operations. Threat intelligence plays a crucial role in identifying, analyzing, and mitigating cybersecurity threats. Large datasets are analyzed on threat intelligence platforms powered by AI and ML to uncover patterns that can reveal cyber threats [69].
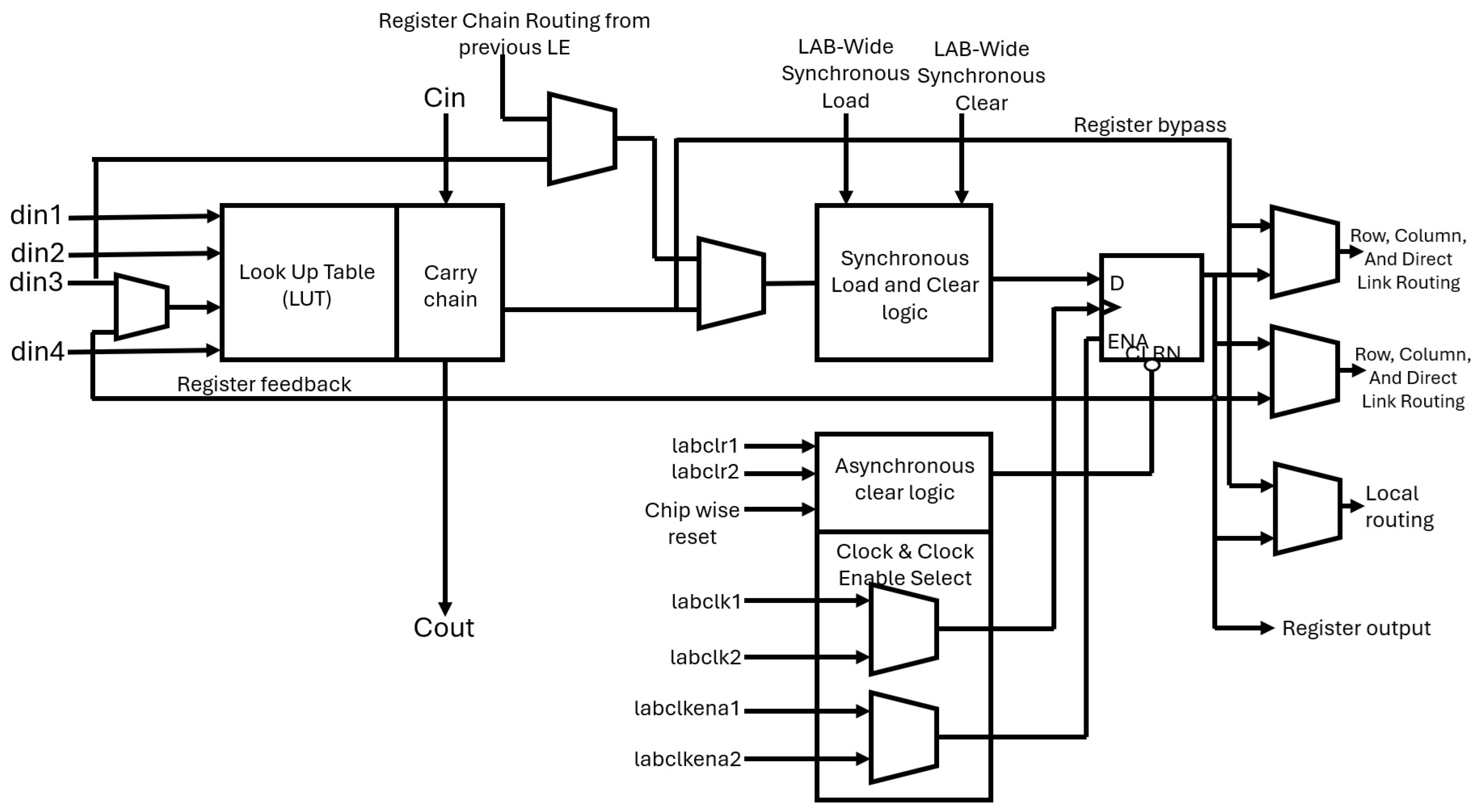
2.2. PUF-Based Authentication Mechanism
2.2.1. Arbiter PUFs
- : top path delay for ;
- : top path delay for ;
- : bottom path delay for ;
- : bottom path delay for .
2.2.2. PUF Performance Matrices
2.2.3. Temperature and Voltage Variations
2.3. Research Methodology
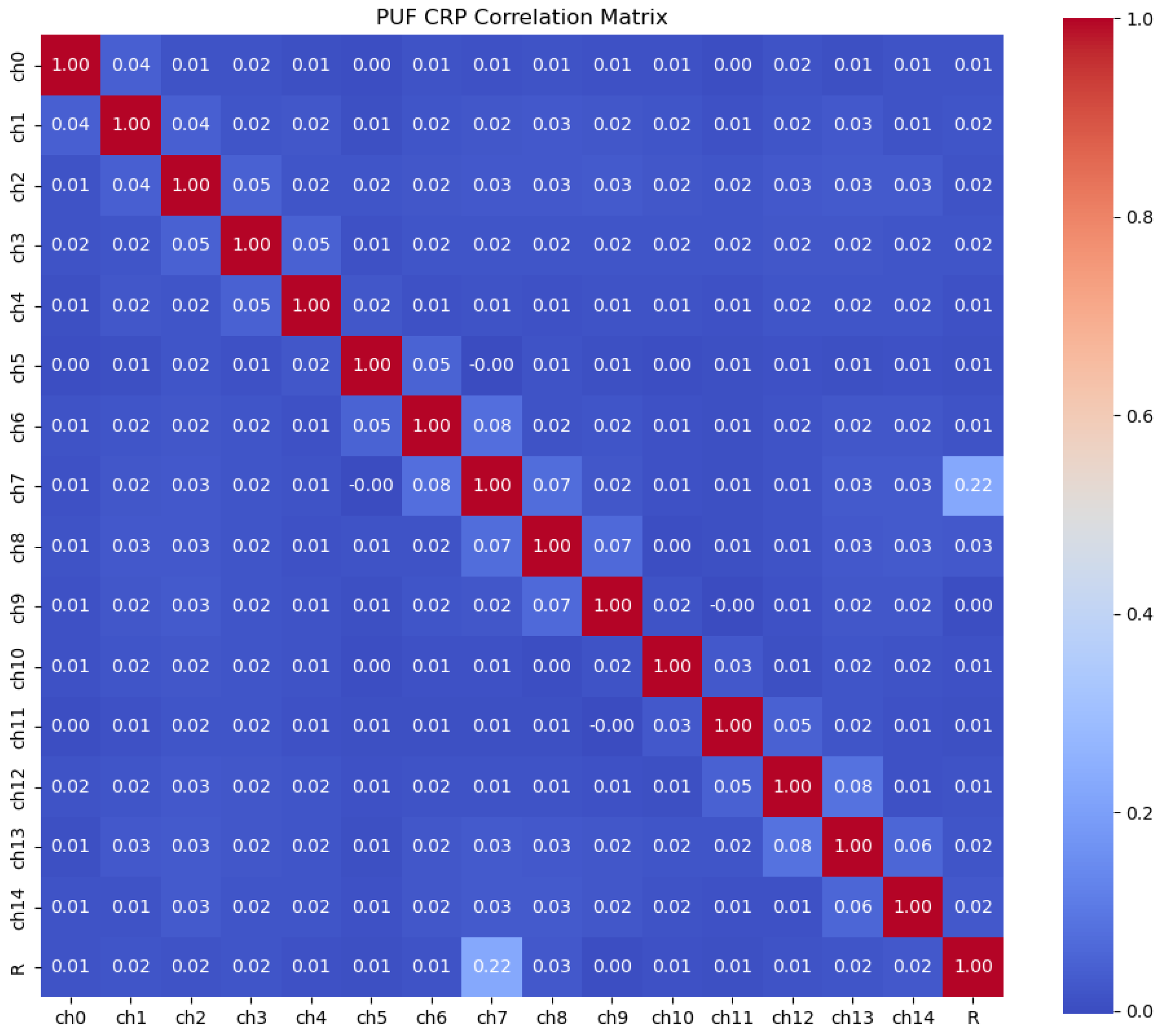
2.3.1. CRP Data Generation and Collection
2.3.2. Data Preprocessing
2.3.3. Dataset Splitting
2.3.4. Model Selection and Training
2.4. ML Algorithms
2.4.1. Support Vector Machine (SVM)
2.4.2. Logistic Regression (LR)
2.4.3. Random Forest (RF)
2.4.4. Multi-Layer Perceptron (MLP)
2.4.5. Gradient Boosting (GB)
3. Edge Artificial Intelligence
- AI-driven solutions address challenges such as task scheduling, resource management, delay reduction, energy efficiency, and privacy and security concerns encountered during the development of EC.
- Cloud-based AI training and inference can lead to considerable delays and raise concerns regarding data privacy and security. By hosting AI tasks closer to the edge nodes, EC enhances stability, reliability, and user experience, effectively addressing these challenges.
- The management of large volumes of data in Edge AI presents a major challenge, as edge devices frequently collect real-time data that may be incomplete or noisy, leading to inaccurate predictions and reduced performance.
- Compatibility challenges arise due to the diverse nature of hardware, software, and communication protocols. Edge devices have distinct specifications, architectures, and interfaces, making seamless integration with other devices and systems complex and non-trivial.
- The integration of Edge AI with other systems introduces data security threats. Edge devices often handle sensitive information, such as personal health records, financial data, and biometric details, making them prime targets for data breaches, cyberattacks, and privacy violations.
- Edge AI systems frequently encounter scalability challenges that affect performance, reliability, and flexibility. Techniques such as load balancing, parallel processing, and distributed computing help mitigate these issues while enhancing system efficiency.
3.1. AI for Security
- Threat detection:It detects unidentified threats in real time by analyzing network traffic, system logs, and other data sources.
- Access control: Reinforces access control mechanisms at edge devices by analyzing user behavior and identifying anomalies using AI.
- User authentication: User behavior and irregularities, like login attempts, can be monitored and detected using AI-based biometric data analysis, such as fingerprint recognition, facial recognition, and voice identification.
- Network security: AI effectively examines and responds to real-time cyberattacks by analyzing network traffic data from numerous sources, such as firewalls and intrusion detection systems.
- Vulnerability detection: AI identifies vulnerabilities in IoT devices and applications by examining code and configuration files. It can simulate attacks to uncover weaknesses and provide security updates or patch recommendations.
- Predictive maintenance: AI can predict potential device failures and security vulnerabilities by analyzing historical data and patterns.
- Supervised learning: ML algorithms process labeled training data to learn a function capable of mapping new data samples. Supervised learning is further categorized into classification and regression tasks. Classification involves mapping inputs to discrete values, whereas regression maps inputs to continuous values. Examples of classification-based supervised ML methods include Support Vector Machines (SVMs) and random forests, while linear regression and logistic regression are commonly used for regression tasks.
- Unsupervised learning: This detects patterns within input data without the need for labeled training data. It is widely applied in enhancing network security functions such as authentication, access control, anti-jamming strategies, and malware detection. Unsupervised learning is typically divided into two main categories: clustering and dimensionality reduction. Clustering organizes similar data instances based on shared features, while dimensionality reduction aims to reduce the number of features in a dataset while retaining as much relevant information as possible. Common unsupervised ML techniques include k-means and k-nearest neighbors (KNN) for clustering and principal component analysis (PCA) and singular value decomposition (SVD) for dimensionality reduction.
- Reinforcement learning (RL): This is a feedback-driven machine learning approach that enables learning through trial and error. In IoT networks, RL helps nodes autonomously make decisions for various networking tasks such as routing, scheduling, and resource allocation. The RL agent learns environmental dynamics solely from collected data without any prior knowledge to determine the best actions for achieving networking objectives. Common RL techniques include Monte Carlo and Temporal Difference (TD) learning for prediction, as well as SARSA and Q-learning for control.
Federated Learning (FL)
3.2. Edge AI Platforms
4. Proposed Method
Implementation of APUF
5. Experimental Results and Analysis
5.1. Experimental Setup
| Algorithm 1. Arbiter PUF |
Input: N: number of challenge bits per PUF instance : vector of size N bits : system clock signal Output: response bit /* Initialization */  |
5.2. Machine Learning-Based Modeling Attacks
6. Conclusions
- A robust approach against temperature and voltage variations, in addition to aging-induced errors in APUF responses.
- APUFs are vulnerable to newer attack forms, such as ML-based modeling. Research should focus on incorporating nonlinear or complex designs to complicate ML modeling attempts.
- APUFs design approaches should be scalable and optimal in terms of area, power, and latency. Integration with 5G/6G networks, blockchains, and ML supports scalable, intelligent, and resilient security architectures.
- The integration of APUFs with different PUF types can create hybrid systems that leverage complementary strengths to enhance the uniqueness and unpredictability of responses.
- Advances in APUF technology will require standard evaluation and benchmarking metrics. Future research should be focused on creating testing frameworks that define comprehensive performance indicators for assessing uniqueness, reliability, and security.
- Future works should focus beyond traditional silicon-based designs, as emerging materials and technologies could redefine APUFs.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| ALMs | Adaptive Logic Modules |
| ANN | Artificial Neural Network |
| APUF | Arbiter PUF |
| ASIC | Application-Specific Integrated Circuit |
| CCPA | California Consumer Privacy Act |
| CNN | Convolutional Neural Network |
| CRPs | Challenge-Response Pairs |
| DDoS | Distributed Denial of Service |
| DNN | Deep Neural Network |
| DP | Differential Privacy |
| DTSA | Dynamic Trust Security Approach |
| EC | Edge Computing |
| EER | Equal Error Rate |
| EE | Energy Efficiency |
| FAR | False Acceptance Rate |
| FFPUF | Feedback-Forward PUF |
| FL | Federated Learning |
| FPGA | Field-Programmable Gate Array |
| FRR | False Rejection Rate |
| GB | Gradient Boosting |
| GDPR | General Data Protection Regulation |
| HD | Hamming Distance |
| IC | Integrated Circuit |
| IDS | Intrusion Detection Systems |
| LAB | Logic Array Block |
| LE | Logic Elements |
| LFSR | Linear Feedback Shift Register |
| LPUF | Lightweight PUF |
| LR | Logistic Regression |
| LUTs | Lookup Tables |
| MEC | Mobile Edge Computing |
| ML | Machine Learning |
| MLP | Multi-Layer Perceptron |
| MTBF | Mean Time Between Failures |
| OTA | Over-The-Air |
| PII | Personally Identifiable Information |
| PUFs | Physical Unclonable Functions |
| QECC | Quantum-Edge Cloud Computing |
| RF | Random Forest |
| RL | Reinforcement Learning |
| ROs | Ring Oscillators |
| SDA | Secure Data Aggregation |
| SMPC | Secure Multi-Party Computation |
| SoC | System-on-Chip |
| SVM | Support Vector Machines |
| TEEs | Trusted Execution Environments |
| TPA | Third-Party Auditing |
| VCS | Version Control System |
References
- Schiller, E.; Aidoo, A.; Fuhrer, J.; Stahl, J.; Ziörjen, M.; Stiller, B. Landscape of IoT security. Comput. Sci. Rev. 2022, 44, 100467. [Google Scholar] [CrossRef]
- Albreem, M.A.; Sheikh, A.M.; Alsharif, M.H.; Jusoh, M.; Yasin, M.N.M. Green Internet of Things (GIoT): Applications, practices, awareness, and challenges. IEEE Access 2021, 9, 38833–38858. [Google Scholar] [CrossRef]
- Albreem, M.A.; Sheikh, A.M.; Bashir, M.J.; El-Saleh, A.A. Towards green Internet of Things (IoT) for a sustainable future in Gulf Cooperation Council countries: Current practices, challenges and future prospective. Wirel. Netw. 2023, 29, 539–567. [Google Scholar] [CrossRef]
- Svorobej, S.; Bendechache, M.; Griesinger, F.; Domaschka, J. Orchestration from the Cloud to the Edge. In The Cloud-to-Thing Continuum: Opportunities and Challenges in Cloud, Fog and Edge Computing; Springer: Berlin/Heidelberg, Germany, 2020; pp. 61–77. [Google Scholar]
- Liu, F.; Tang, G.; Li, Y.; Cai, Z.; Zhang, X.; Zhou, T. A survey on edge computing systems and tools. Proc. IEEE 2019, 107, 1537–1562. [Google Scholar] [CrossRef]
- Yahuza, M.; Idris, M.Y.I.B.; Wahab, A.W.B.A.; Ho, A.T.; Khan, S.; Musa, S.N.B.; Taha, A.Z.B. Systematic review on security and privacy requirements in edge computing: State of the art and future research opportunities. IEEE Access 2020, 8, 76541–76567. [Google Scholar] [CrossRef]
- Rupanetti, D.; Kaabouch, N. Combining Edge Computing-Assisted Internet of Things Security with Artificial Intelligence: Applications, Challenges, and Opportunities. Appl. Sci. 2024, 14, 7104. [Google Scholar] [CrossRef]
- Douch, S.; Abid, M.R.; Zine-Dine, K.; Bouzidi, D.; Benhaddou, D. Edge computing technology enablers: A systematic lecture study. IEEE Access 2022, 10, 69264–69302. [Google Scholar] [CrossRef]
- Kolevski, D.; Michael, K. Edge Computing and IoT Data Breaches: Security, Privacy, Trust, and Regulation. IEEE Technol. Soc. Mag. 2024, 43, 22–32. [Google Scholar] [CrossRef]
- Zhang, J.; Chen, B.; Zhao, Y.; Cheng, X.; Hu, F. Data security and privacy-preserving in edge computing paradigm: Survey and open issues. IEEE Access 2018, 6, 18209–18237. [Google Scholar] [CrossRef]
- El Kafhali, S.; El Mir, I.; Hanini, M. Security threats, defense mechanisms, challenges, and future directions in cloud computing. Arch. Comput. Methods Eng. 2022, 29, 223–246. [Google Scholar] [CrossRef]
- Gill, S.S.; Golec, M.; Hu, J.; Xu, M.; Du, J.; Wu, H.; Walia, G.K.; Murugesan, S.S.; Ali, B.; Kumar, M.; et al. Edge AI: A taxonomy, systematic review and future directions. Clust. Comput. 2025, 28, 1–53. [Google Scholar] [CrossRef]
- He, D.; Chan, S.; Guizani, M. Security in the Internet of Things Supported by Mobile Edge Computing. IEEE Commun. Mag. 2018, 56, 56–61. [Google Scholar] [CrossRef]
- Porambage, P.; Kumar, T.; Liyanage, M.; Partala, J.; Lovén, L.; Ylianttila, M.; Seppänen, T. Sec-EdgeAI: AI for edge security Vs security for edge AI. In Proceedings of the 1st 6G Wireless Summit, Levi, Finland, 24–26 March 2019. [Google Scholar]
- El-Saleh, A.A.; Sheikh, A.M.; Albreem, M.A.; Honnurvali, M.S. The internet of medical things (IoMT): Opportunities and challenges. Wirel. Netw. 2025, 31, 327–344. [Google Scholar] [CrossRef]
- Wang, C.; Yuan, Z.; Zhou, P.; Xu, Z.; Li, R.; Wu, D.O. The Security and Privacy of Mobile-Edge Computing: An Artificial Intelligence Perspective. IEEE Internet Things J. 2023, 10, 22008–22032. [Google Scholar] [CrossRef]
- Liu, H.; Zhang, S.; Zhang, P.; Zhou, X.; Shao, X.; Pu, G.; Zhang, Y. Blockchain and federated learning for collaborative intrusion detection in vehicular edge computing. IEEE Trans. Veh. Technol. 2021, 70, 6073–6084. [Google Scholar] [CrossRef]
- Xia, Q.; Ye, W.; Tao, Z.; Wu, J.; Li, Q. A survey of federated learning for edge computing: Research problems and solutions. High-Confid. Comput. 2021, 1, 100008. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Ding, M.; Pham, Q.V.; Pathirana, P.N.; Le, L.B.; Seneviratne, A.; Li, J.; Niyato, D.; Poor, H.V. Federated learning meets blockchain in edge computing: Opportunities and challenges. IEEE Internet Things J. 2021, 8, 12806–12825. [Google Scholar] [CrossRef]
- Tulkinbekov, K.; Kim, D.H. Blockchain-enabled approach for big data processing in edge computing. IEEE Internet Things J. 2022, 9, 18473–18486. [Google Scholar] [CrossRef]
- Bhatta, N.P.; Amsaad, F.; Singh, H.; Sherif, A.; Hopkinson, K. Enhancing Hardware Security: An Analysis of SRAM-PUFs. In Proceedings of the NAECON 2023-IEEE National Aerospace and Electronics Conference, Dayton, OH, USA, 28–31 August 2023; pp. 174–180. [Google Scholar]
- Ang, K.L.M.; Seng, J.K.P. Embedded Intelligence: Platform Technologies, Device Analytics, and Smart City Applications. IEEE Internet Things J. 2021, 8, 13165–13182. [Google Scholar] [CrossRef]
- Manan, A. Implementation of image processing algorithm on fpga. Akgec J. Technol. 2006, 2, 25–28. [Google Scholar]
- Manan, A. Efficient 16 nm SRAM Design for FPGA’s. In Proceedings of the 2018 5th International Conference on Signal Processing and Integrated Networks (SPIN), Noida, India, 22–23 February 2018; pp. 457–461. [Google Scholar]
- Cao, Y.; Xu, J.; Wu, J.; Wu, S.; Huang, Z.; Zhang, K. Advances in Physical Unclonable Functions Based on New Technologies: A Comprehensive Review. Mathematics 2023, 12, 77. [Google Scholar] [CrossRef]
- Shao, H.; Fu, B.; Yang, J.; Luo, W.; Su, C.; Fu, Z.; Tang, K.; Huang, R. IMCE: An In-Memory Computing and Encrypting Hardware Architecture for Robust Edge Security. In Proceedings of the 2024 Design, Automation & Test in Europe Conference & Exhibition (DATE), Valencia, Spain, 25–27 March 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge computing: Vision and challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Hassan, N.; Yau, K.L.A.; Wu, C. Edge computing in 5G: A review. IEEE Access 2019, 7, 127276–127289. [Google Scholar] [CrossRef]
- Yu, W.; Liang, F.; He, X.; Hatcher, W.G.; Lu, C.; Lin, J.; Yang, X. A survey on the edge computing for the Internet of Things. IEEE Access 2017, 6, 6900–6919. [Google Scholar] [CrossRef]
- Shi, W.; Pallis, G.; Xu, Z. Edge computing [scanning the issue]. Proc. IEEE 2019, 107, 1474–1481. [Google Scholar] [CrossRef]
- Alwarafy, A.; Al-Thelaya, K.A.; Abdallah, M.; Schneider, J.; Hamdi, M. A survey on security and privacy issues in edge-computing-assisted internet of things. IEEE Internet Things J. 2021, 8, 4004–4022. [Google Scholar] [CrossRef]
- Sheikh, A.M.; Islam, M.R.; Habaebi, M.H.; Zabidi, S.A.; Bin Najeeb, A.R.; Kabbani, A. A Survey on Edge Computing (EC) Security Challenges: Classification, Threats, and Mitigation Strategies. Future Internet 2025, 17, 175. [Google Scholar] [CrossRef]
- Zhao, Y.; Wang, W.; Li, Y.; Meixner, C.C.; Tornatore, M.; Zhang, J. Edge computing and networking: A survey on infrastructures and applications. IEEE Access 2019, 7, 101213–101230. [Google Scholar] [CrossRef]
- Kommera, A.R. The Role of Distributed Systems in Cloud Computing: Scalability, Efficiency, and Resilience. NeuroQuantology 2013, 11, 507–516. [Google Scholar]
- Sharma, R.; Chan, C.A.; Leckie, C. Probabilistic Distributed Intrusion Detection For Zero-Trust Multi-Access Edge Computing. In Proceedings of the NOMS 2023-2023 IEEE/IFIP Network Operations and Management Symposium, Miami, FL, USA, 8–12 May 2023; pp. 1–9. [Google Scholar] [CrossRef]
- Hong, J.; Hong, Y.G.; de Foy, X.; Kovatsch, M.; Schooler, E.; Kutscher, D. Internet of Things (IoT) Edge Challenges and Functions RFC 9556 Internet Engineering Task Force: 2024. Available online: https://www.rfc-editor.org/info/rfc9556 (accessed on 16 April 2025).
- Sheikh, A.M.; Islam, M.R.; Habaebi, M.H.; Kabbani, A.; Zabidi, S.A.; bin Najeeb, A.R. Securing the IoT Edge Devices Using Advanced Digital Technologies. Asian J. Electr. Electron. Eng. 2024, 4, 52–60. [Google Scholar] [CrossRef]
- Singh, S.; Sulthana, R.; Shewale, T.; Chamola, V.; Benslimane, A.; Sikdar, B. Machine-learning-assisted security and privacy provisioning for edge computing: A survey. IEEE Internet Things J. 2021, 9, 236–260. [Google Scholar] [CrossRef]
- Johnsson, A.; Nordling, A. Edge Computing Security for IoT: A Systematic Literature Review. In Economics of Grids, Clouds, Systems, and Services; Springer: Berlin/Heidelberg, Germany, 2023. [Google Scholar]
- Fazeldehkordi, E.; Grønli, T.M. A survey of security architectures for edge computing-based IoT. IoT 2022, 3, 332–365. [Google Scholar] [CrossRef]
- Ma, Y.; Liu, L.; Liu, Z.; Li, F.; Xie, Q.; Chen, K.; Lv, C.; He, Y.; Li, F. A Survey of DDoS Attack and Defense Technologies in Multi-Access Edge Computing. IEEE Internet Things J. 2024, 12, 1428–1452. [Google Scholar] [CrossRef]
- Smith, R.; Palin, D.; Ioulianou, P.P.; Vassilakis, V.G.; Shahandashti, S.F. Battery draining attacks against edge computing nodes in IoT networks. Cyber-Phys. Syst. 2020, 6, 96–116. [Google Scholar] [CrossRef]
- Krishnamoorthy, G.; Konidena, B.K.; Pakalapati, N. Machine Learning in Edge Computing: Opportunities and Challenges. Int. J. Innov. Sci. Res. Technol. 2024, 9. [Google Scholar] [CrossRef]
- Monteiro, M.M. Patterns for Anonymization and Pseudonymization of Datasets 2024. Available online: https://repositorio-aberto.up.pt/bitstream/10216/161014/2/682127.pdf (accessed on 16 April 2025).
- Li, N. Data Encryption. In Encyclopedia of Database Systems; Liu, L., Özsu, M.T., Eds.; Springer: Boston, MA, USA, 2009; p. 574. [Google Scholar] [CrossRef]
- Yousefpoor, M.S.; Yousefpoor, E.; Barati, H.; Barati, A.; Movaghar, A.; Hosseinzadeh, M. Secure data aggregation methods and countermeasures against various attacks in wireless sensor networks: A comprehensive review. J. Netw. Comput. Appl. 2021, 190, 103118. [Google Scholar] [CrossRef]
- Yao, A.; Li, G.; Li, X.; Jiang, F.; Xu, J.; Liu, X. Differential privacy in edge computing-based smart city Applications: Security issues, solutions and future directions. Array 2023, 19, 100293. [Google Scholar] [CrossRef]
- Man, D.; Zeng, F.; Yang, W.; Yu, M.; Lv, J.; Wang, Y. Intelligent Intrusion Detection Based on Federated Learning for Edge-Assisted Internet of Things. Secur. Commun. Netw. 2021, 2021, 9361348. [Google Scholar] [CrossRef]
- Kukreti, A. Access control and authentication for secure systems and networks. NeuroQuantology 2022, 20, 5321. [Google Scholar]
- Xiaohong, D.; Linru, J.; Yuan, J.; Lin, C.; Taoyong, L.; Bin, L. Intelligent computing scheme of blockchain based on trusted execution environment. In Proceedings of the 2022 IEEE International Conference on Artificial Intelligence and Computer Applications (ICAICA), Dalian, China, 24–26 June 2022; pp. 399–407. [Google Scholar]
- Ning, Z.; Liao, J.; Zhang, F.; Shi, W. Preliminary Study of Trusted Execution Environments on Heterogeneous Edge Platforms. In Proceedings of the 2018 IEEE/ACM Symposium on Edge Computing (SEC), Seattle, WA, USA, 25–27 October 2018; pp. 421–426. [Google Scholar] [CrossRef]
- Chakrabarti, S.; Knauth, T.; Kuvaiskii, D.; Steiner, M.; Vij, M. Trusted execution environment with intel sgx. In Responsible Genomic Data Sharing; Elsevier: Amsterdam, The Netherlands, 2020; pp. 161–190. [Google Scholar]
- Jayasinghe, U.; Lee, G.M.; MacDermott, Á.; Rhee, W.S. TrustChain: A privacy preserving blockchain with edge computing. Wirel. Commun. Mob. Comput. 2019, 2019, 2014697. [Google Scholar] [CrossRef]
- Xu, R.; Hang, L.; Jin, W.; Kim, D. Distributed secure edge computing architecture based on blockchain for real-time data integrity in IoT environments. Actuators 2021, 10, 197. [Google Scholar] [CrossRef]
- Wu, Y.; Wang, J.; Wang, Y.; Zhai, S.; Li, Z.; He, Y.; Sun, K.; Li, Q.; Zhang, N. Your firmware has arrived: A study of firmware update vulnerabilities. In Proceedings of the 33rd USENIX Security Symposium (USENIX Security 24), Philadelphia, PA, USA, 14–16 August 2024; pp. 5627–5644. [Google Scholar]
- Gupta, P. A decentralized approach towards secure firmware updates and testing over commercial IoT Devices. arXiv 2020, arXiv:2011.12052. [Google Scholar]
- Said, G.; Ghani, A.; Ullah, A.; Alzahrani, A.; Azeem, M.; Ahmad, R.; Kim, D.H. Fog-assisted de-duplicated data exchange in distributed edge computing networks. Sci. Rep. 2024, 14, 20595. [Google Scholar] [CrossRef]
- Ok, E.; Grace, J.; John, M. Security and Privacy Challenges 2023. Available online: https://www.researchgate.net/publication/386251008_Security_and_Privacy_Challenges (accessed on 23 April 2025).
- Spadaccino, P.; Cuomo, F. Intrusion Detection Systems for IoT: Opportunities and challenges offered by Edge Computing and Machine Learning. arXiv 2020, arXiv:2012.01174. [Google Scholar]
- Zhao, C.; Zhao, S.; Zhao, M.; Chen, Z.; Gao, C.Z.; Li, H.; Tan, Y.A. Secure multi-party computation: Theory, practice and applications. Inf. Sci. 2019, 476, 357–372. [Google Scholar] [CrossRef]
- Volgushev, N.; Schwarzkopf, M.; Getchell, B.; Varia, M.; Lapets, A.; Bestavros, A. Conclave: Secure multi-party computation on big data. In Proceedings of the Fourteenth EuroSys Conference 2019, Dresden, Germany, 25–28 March 2019; pp. 1–18. [Google Scholar]
- Luo, Y.; Chen, Y.; Li, T.; Wang, Y.; Yang, Y. Using information entropy to analyze secure multi-party computation protocol. In Proceedings of the 2021 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Virtual, 25–28 October 2021; pp. 312–318. [Google Scholar] [CrossRef]
- Chirra, D.R. Secure Edge Computing for IoT Systems: AI-Powered Strategies for Data Integrity and Privacy. Rev. Intel. Artif. Med. 2022, 13, 485–507. [Google Scholar]
- Rivadeneira, J.E.; Borges, G.A.; Rodrigues, A.; Boavida, F.; Silva, J.S. A unified privacy preserving model with AI at the edge for Human-in-the-Loop Cyber-Physical Systems. Internet Things 2024, 25, 101034. [Google Scholar] [CrossRef]
- Le, K.H.; Le-Minh, K.H.; Thai, H.T. Brainyedge: An ai-enabled framework for iot edge computing. ICT Express 2023, 9, 211–221. [Google Scholar] [CrossRef]
- Cao, K.; Liu, Y.; Meng, G.; Sun, Q. An Overview on Edge Computing Research. IEEE Access 2020, 8, 85714–85728. [Google Scholar] [CrossRef]
- Amodu, O. Security Auditors’ Perspective in Tackling Cyber-Threats. Computer 2024, 11, 2458–9403. Available online: https://www.researchgate.net/publication/381280763 (accessed on 1 May 2025).
- Hossain, M.I.; Sumon, S.A.; Hasan, H.M.; Akter, F.; Badhon, M.B.; Islam, M.N.U. Quantum-Edge Cloud Computing: A Future Paradigm for IoT Applications. arXiv 2024, arXiv:2405.04824. [Google Scholar]
- Nacheva, R.; Azeroual, O. Security of AI-Powered Systems: Threat Intelligence on the Edge. In Proceedings of the 2024 8th International Symposium on Multidisciplinary Studies and Innovative Technologies (ISMSIT), Ankara, Turkey, 7–9 November 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Li, Q.; Chen, F.; Kang, J.; Wang, P.; Su, J.; Huang, F.; Li, M.; Zhang, J. Intrinsic random optical features of the electronic packages as physical unclonable functions for internet of things security. Adv. Photonics Res. 2022, 3, 2100207. [Google Scholar] [CrossRef]
- Guan, Z.; Liu, H.; Qin, Y. Physical unclonable functions for IoT device authentication. J. Commun. Inf. Netw. 2019, 4, 44–54. [Google Scholar] [CrossRef]
- Liu, W.; Zhang, L.; Zhang, Z.; Gu, C.; Wang, C.; O’neill, M.; Lombardi, F. XOR-based low-cost reconfigurable PUFs for IoT security. ACM Trans. Embed. Comput. Syst. TECS 2019, 18, 1–21. [Google Scholar] [CrossRef]
- Aparicio-Téllez, R.; Garcia-Bosque, M.; Díez-Señorans, G.; Celma, S. Oscillator Selection Strategies to Optimize a Physically Unclonable Function for IoT Systems Security. Sensors 2023, 23, 4410. [Google Scholar] [CrossRef]
- Zerrouki, F.; Ouchani, S.; Bouarfa, H. A survey on silicon PUFs. J. Syst. Archit. 2022, 127, 102514. [Google Scholar] [CrossRef]
- Barbareschi, M.; Casola, V.; Emmanuele, A.; Lombardi, D. On the adoption of PUF for key agreement scheme in Internet of Things. In Proceedings of the 21st ACM International Conference on Computing Frontiers: Workshops and Special Sessions, Naples, Italy, 7–9 May 2024; pp. 17–24. [Google Scholar]
- Hoffman, C.; Gebotys, C.; Aranha, D.F.; Cortes, M.; Araujo, G. Circumventing uniqueness of XOR arbiter PUFs. In Proceedings of the 2019 22nd Euromicro Conference on Digital System Design (DSD), Kallithea, Greece, 28–30 August 2019; pp. 222–229. [Google Scholar]
- Ali, R.; Ma, H.; Hou, Z.; Zhang, D.; Deng, E.; Wang, Y. A Reconfigurable Arbiter MPUF with High Resistance Against Machine Learning Attack. IEEE Trans. Magn. 2021, 57, 1–7. [Google Scholar] [CrossRef]
- Alahmadi, S.; Idriss, H.; Rojas, P.; Bayoumi, M. Security Scalability of Arbiter PUF Designs. In Proceedings of the 2023 IEEE International Symposium on Circuits and Systems (ISCAS), Monterey, CA, USA, 21–25 May 2023; pp. 1–5. [Google Scholar] [CrossRef]
- Wang, H.; Hao, W.; Tang, Y.; Zhu, B.; Dong, W.; Liu, W. Deep neural network modeling attacks on arbiter-PUF-based designs. Cybersecurity 2025, 8, 1–16. [Google Scholar] [CrossRef]
- ISO/IEC 20897-1:2020, Germany. Information Security, Cybersecurity and Privacy Protection—Physically Unclonable Functions Part 1: Security Requirement. Available online: https://www.iso.org/standard/76353.html (accessed on 30 April 2025).
- ISO/IEC 20897-2:2022, Germany. Information Security, Cybersecurity and Privacy Protection—Physically Unclonable Functions Part 2: Test and Evaluation Methods. Available online: https://www.iso.org/standard/76354.html (accessed on 30 April 2025).
- Sembiring, R.L.; Pahlevi, R.R.; Sukarno, P. Randomness, Uniqueness, and Steadiness Evaluation of Physical Unclonable Functions. In Proceedings of the 2021 9th International Conference on Information and Communication Technology (ICoICT), Yogyakarta, Indonesia, 3–5 August 2021; pp. 429–433. [Google Scholar] [CrossRef]
- Al-Meer, A.; Al-Kuwari, S. Physical unclonable functions (PUF) for IoT devices. ACM Comput. Surv. 2023, 55, 1–31. [Google Scholar] [CrossRef]
- Asif, R.; Ghanem, K.; Irvine, J. Proof-of-puf enabled blockchain: Concurrent data and device security for internet-of-energy. Sensors 2020, 21, 28. [Google Scholar] [CrossRef]
- Najafi, F.; Kaveh, M.; Martín, D.; Reza Mosavi, M. Deep PUF: A highly reliable DRAM PUF-based authentication for IoT networks using deep convolutional neural networks. Sensors 2021, 21, 2009. [Google Scholar] [CrossRef] [PubMed]
- Idriss, H.; Idriss, T.; Bayoumi, M. A Highly Reliable Delay-Based Arbiter PUF Architecture. 2021. Available online: https://www.researchgate.net/publication/355982050_A_Highly_Reliable_Delay-Based_Arbiter_PUF_Architecture (accessed on 10 June 2025).
- Streit, F.J.; Krüger, P.; Becher, A.; Wildermann, S.; Teich, J. Design and Evaluation of a Tunable PUF Architecture for FPGAs. ACM Trans. Reconfigurable Technol. Syst. 2021, 15, 1–27. [Google Scholar] [CrossRef]
- Ma, C.; Mu, J.; Ye, J.; Chen, S.; Cao, Y.; Li, H.; Li, X. Online Reliability Evaluation Design: Select Reliable CRPs for Arbiter PUF and Its Variants. In Proceedings of the 2023 IEEE European Test Symposium (ETS), Venezia, Italy, 22–26 May 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Gisha, C.G.; Jose, B.A.; Mathew, J. A novel mixed-signal PUF based on Current Mirror Inverter. In Proceedings of the 2022 IEEE International Symposium on Smart Electronic Systems (iSES), Warangal, India, 18–22 December 2022; pp. 89–94. [Google Scholar] [CrossRef]
- Valkenborg, D.; Rousseau, A.J.; Geubbelmans, M.; Burzykowski, T. Support vector machines. Am. J. Orthod. Dentofac. Orthop. 2023, 164, 754–757. [Google Scholar] [CrossRef]
- Sweilam, N.H.; Tharwat, A.; Moniem, N.A. Support vector machine for diagnosis cancer disease: A comparative study. Egypt. Inform. J. 2010, 11, 81–92. [Google Scholar] [CrossRef]
- Jha, J.; Ragha, L. Intrusion detection system using support vector machine. Int. J. Appl. Inf. Syst. IJAIS 2013, 3, 25–30. [Google Scholar]
- Khan, M.M.; Alkhathami, M. Anomaly detection in IoT-based healthcare: Machine learning for enhanced security. Sci. Rep. 2024, 14, 5872. [Google Scholar] [CrossRef]
- Al-Rbabah, L.; Al-Qerem, A.; Al Khaldy, M.A.; Turki, H.M. Enhancing IoT Security and Efficiency Using Machine Learning. In Proceedings of the 2025 1st International Conference on Computational Intelligence Approaches and Applications (ICCIAA), Petra, Jordan, 28–30 April 2025; pp. 1–7. [Google Scholar]
- Chalichalamala, S.; Govindan, N.; Kasarapu, R. Logistic regression ensemble classifier for intrusion detection system in internet of things. Sensors 2023, 23, 9583. [Google Scholar] [CrossRef] [PubMed]
- Rührmair, U.; Sehnke, F.; Sölter, J.; Dror, G.; Devadas, S.; Schmidhuber, J. Modeling attacks on physical unclonable functions. In Proceedings of the 17th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 4–8 October 2010; pp. 237–249. [Google Scholar]
- Zhang, J.; Shen, C.; Su, H.; Arafin, M.T.; Qu, G. Voltage Over-Scaling-Based Lightweight Authentication for IoT Security. IEEE Trans. Comput. 2022, 71, 323–336. [Google Scholar] [CrossRef]
- Hasan, M.; Islam, M.M.; Zarif, M.I.I.; Hashem, M. Attack and anomaly detection in IoT sensors in IoT sites using machine learning approaches. Internet Things 2019, 7, 100059. [Google Scholar] [CrossRef]
- Gugueoth, V.; Safavat, S.; Shetty, S. Security of Internet of Things (IoT) using federated learning and deep learning—Recent advancements, issues and prospects. ICT Express 2023, 9, 941–960. [Google Scholar] [CrossRef]
- Christo, M.S.; Menandas, J.J.; George, M.; Nuna, S.V. DDoS Detection using Multilayer Perceptron. In Proceedings of the 2023 4th International Conference on Electronics and Sustainable Communication Systems (ICESC), Coimbatore, India, 6–8 July 2023; pp. 688–693. [Google Scholar] [CrossRef]
- Ali, A.; Assam, M.; Khan, F.U.; Ghadi, Y.Y.; Nurdaulet, Z.; Zhibek, A.; Shah, S.Y.; Alahmadi, T.J. An optimized multilayer perceptron-based network intrusion detection using Gray Wolf Optimization. Comput. Electr. Eng. 2024, 120, 109838. [Google Scholar] [CrossRef]
- Upadhyay, D.; Manero, J.; Zaman, M.; Sampalli, S. Gradient boosting feature selection with machine learning classifiers for intrusion detection on power grids. IEEE Trans. Netw. Serv. Manag. 2020, 18, 1104–1116. [Google Scholar] [CrossRef]
- Saied, M.; Guirguis, S.; Madbouly, M. A comparative study of using boosting-based machine learning algorithms for IoT network intrusion detection. Int. J. Comput. Intell. Syst. 2023, 16, 177. [Google Scholar] [CrossRef]
- Bourechak, A.; Zedadra, O.; Kouahla, M.N.; Guerrieri, A.; Seridi, H.; Fortino, G. At the confluence of artificial intelligence and edge computing in iot-based applications: A review and new perspectives. Sensors 2023, 23, 1639. [Google Scholar] [CrossRef]
- Hua, H.; Li, Y.; Wang, T.; Dong, N.; Li, W.; Cao, J. Edge computing with artificial intelligence: A machine learning perspective. ACM Comput. Surv. 2023, 55, 1–35. [Google Scholar] [CrossRef]
- Sheikh, A.M.; Islam, M.R.; Habaebi, M.H.; Zabidi, S.A.; Najeeb, A.R.B.; Basahel, A. Machine Learning (ML) assisted Edge security framework on FPGAs. In Proceedings of the 2023 9th International Conference on Computer and Communication Engineering (ICCCE), Kuala Lumpur, Malaysia, 15–16 August 2023; pp. 155–160. [Google Scholar]
- Bhattacharya, T.; Peddi, A.V.; Ponaganti, S.; Veeramalla, S.T. A survey on various security protocols of edge computing. J. Supercomput. 2025, 81, 310. [Google Scholar] [CrossRef]
- Hao, C.; Dotzel, J.; Xiong, J.; Benini, L.; Zhang, Z.; Chen, D. Enabling Design Methodologies and Future Trends for Edge AI: Specialization and Codesign. IEEE Des. Test 2021, 38, 7–26. [Google Scholar] [CrossRef]
- Gohil, H. Enhancing IoT Security with Artificial Intelligence. 2024. Available online: https://www.einfochips.com/blog/enhancing-iot-security-with-artificial-intelligence/ (accessed on 8 February 2025).
- Firouzi, F.; Jiang, S.; Chakrabarty, K.; Farahani, B.; Daneshmand, M.; Song, J.; Mankodiya, K. Fusion of IoT, AI, edge–fog–cloud, and blockchain: Challenges, solutions, and a case study in healthcare and medicine. IEEE Internet Things J. 2022, 10, 3686–3705. [Google Scholar] [CrossRef]
- Khoramnejad, F.; Hossain, E. Generative AI for the optimization of next-generation wireless networks: Basics, state-of-the-art, and open challenges. IEEE Commun. Surv. Tutor. 2025. early access. [Google Scholar] [CrossRef]
- Aouedi, O.; Vu, T.H.; Sacco, A.; Nguyen, D.C.; Piamrat, K.; Marchetto, G.; Pham, Q.V. A survey on intelligent Internet of Things: Applications, security, privacy, and future directions. IEEE Commun. Surv. Tutor. 2024, 27, 1238–1292. [Google Scholar] [CrossRef]
- Abbas, G.; Mehmood, A.; Carsten, M.; Epiphaniou, G.; Lloret, J. Safety, security and privacy in machine learning based internet of things. J. Sens. Actuator Netw. 2022, 11, 38. [Google Scholar] [CrossRef]
- Alwahedi, F.; Aldhaheri, A.; Ferrag, M.A.; Battah, A.; Tihanyi, N. Machine learning techniques for IoT security: Current research and future vision with generative AI and large language models. Internet Things -Cyber-Phys. Syst. 2024, 4, 167–185. [Google Scholar] [CrossRef]
- Frikha, M.S.; Gammar, S.M.; Lahmadi, A.; Andrey, L. Reinforcement and deep reinforcement learning for wireless Internet of Things: A survey. Comput. Commun. 2021, 178, 98–113. [Google Scholar] [CrossRef]
- Hussain, B.; Du, Q.; Imran, A.; Imran, M.A. Artificial Intelligence-Powered Mobile Edge Computing-Based Anomaly Detection in Cellular Networks. IEEE Trans. Ind. Inform. 2020, 16, 4986–4996. [Google Scholar] [CrossRef]
- Jedidi, A. Dynamic trust security approach for edge computing-based mobile IoT devices using artificial intelligence. Eng. Res. Express 2024, 6, 025211. [Google Scholar] [CrossRef]
- Kohli, V.; Chougule, A.; Chamola, V.; Yu, F.R. MbRE IDS: An AI and edge computing empowered framework for securing intelligent transportation systems. In Proceedings of the IEEE INFOCOM 2022-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Virtual, 2–5 May 2022; pp. 1–6. [Google Scholar]
- Yao, A.; Jiang, F.; Li, X.; Dong, C.; Xu, J.; Xu, Y.; Li, G.; Liu, X. A Novel Security Framework for Edge Computing based UAV Delivery System. In Proceedings of the 2021 IEEE 20th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Shenyang, China, 20–22 October 2021; pp. 1031–1038. [Google Scholar] [CrossRef]
- Xue, H.; Chen, D.; Zhang, N.; Dai, H.N.; Yu, K. Integration of blockchain and edge computing in internet of things: A survey. Future Gener. Comput. Syst. 2023, 144, 307–326. [Google Scholar] [CrossRef]
- Abreha, H.G.; Hayajneh, M.; Serhani, M.A. Federated learning in edge computing: A systematic survey. Sensors 2022, 22, 450. [Google Scholar] [CrossRef]
- Wen, J.; Zhang, Z.; Lan, Y.; Cui, Z.; Cai, J.; Zhang, W. A survey on federated learning: Challenges and applications. Int. J. Mach. Learn. Cybern. 2023, 14, 513–535. [Google Scholar] [CrossRef]
- Duan, Q.; Huang, J.; Hu, S.; Deng, R.; Lu, Z.; Yu, S. Combining federated learning and edge computing toward ubiquitous intelligence in 6G network: Challenges, recent advances, and future directions. IEEE Commun. Surv. Tutor. 2023, 25, 2892–2950. [Google Scholar] [CrossRef]
- Li, H.; Ge, L.; Tian, L. Survey: Federated learning data security and privacy-preserving in edge-Internet of Things. Artif. Intell. Rev. 2024, 57, 130. [Google Scholar] [CrossRef]
- Paripati, L.K.; Hajari, V.R. Edge Computing and its Role in Enhancing Artificial Intelligence and Machine Learning Applications in the Cloud. J. Electr. Syst. 2024, 2958–2969. [Google Scholar] [CrossRef]
- Li, D.; Liu, D.; Qi, Y.; Liu, F.; Guan, Z.; Liu, J. PUF-Based Lightweight Authentication Framework for Large-Scale IoT Devices in Distributed Cloud. IEEE Netw. 2023, 37, 56–62. [Google Scholar] [CrossRef]
- Iyer, M.A.; Junaid Khan, S.Q.; Zhuang, N. Advanced Physical Synthesis in the Quartus® Prime Pro Edition Software WP-01327-1.0; Technical Report; Altera, Intel: San Jose, CA, USA, 2025; Available online: https://cdrdv2-public.intel.com/786711/advanced-physical-synthesis-white-paper.pdf (accessed on 9 June 2025).
- Balijabudda, V.S.; Chakrabarti, I.; Chakraborty, R.S. Design, Implementation and Characterization of a Novel Robust-by-Construction Arbiter PUF Circuit on Xilinx FPGAs. In Proceedings of the 2024 IEEE 33rd Asian Test Symposium (ATS), Hiroshima, Japan, 17–20 December 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Gassend, B.; Clarke, D.; van Dijk, M.; Devadas, S. Silicon physical random functions. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 148–160. [Google Scholar]
- Machida, T.; Yamamoto, D.; Iwamoto, M.; Sakiyama, K. A new arbiter PUF for enhancing unpredictability on FPGA. Sci. World J. 2015, 2015, 864812. [Google Scholar] [CrossRef] [PubMed]
- Hori, Y.; Yoshida, T.; Katashita, T.; Satoh, A. Quantitative and statistical performance evaluation of arbiter physical unclonable functions on FPGAs. In Proceedings of the 2010 International conference on reconfigurable computing and FPGAs, Cancun, Mexico, 13–15 December 2010; pp. 298–303. [Google Scholar]
- Mahalat, M.H.; Mandal, S.; Mondal, A.; Sen, B.; Chakraborty, R.S. Implementation, characterization and application of path changing switch based arbiter PUF on FPGA as a lightweight security primitive for iot. ACM TRansactions Des. Autom. Electron. Syst. TODAES 2021, 27, 1–26. [Google Scholar] [CrossRef]
- Anandakumar, N.N.; Hashmi, M.S.; Chaudhary, M.A. Implementation of Efficient XOR Arbiter PUF on FPGA with Enhanced Uniqueness and Security. IEEE Access 2022, 10, 129832–129842. [Google Scholar] [CrossRef]
- Lim, D.; Lee, J.W.; Gassend, B.; Suh, G.E.; Van Dijk, M.; Devadas, S. Extracting secret keys from integrated circuits. IEEE Trans. Very Large Scale Integr. VLSI Syst. 2005, 13, 1200–1205. [Google Scholar]
- Tran, M.K.; Panchal, S.; Chauhan, V.; Brahmbhatt, N.; Mevawalla, A.; Fraser, R.; Fowler, M. Python-based scikit-learn machine learning models for thermal and electrical performance prediction of high-capacity lithium-ion battery. Int. J. Energy Res. 2022, 46, 786–794. [Google Scholar] [CrossRef]
- Arnold, C.; Biedebach, L.; Küpfer, A.; Neunhoeffer, M. The role of hyperparameters in machine learning models and how to tune them. Political Sci. Res. Methods 2024, 12, 841–848. [Google Scholar] [CrossRef]
- Gu, C.; Liu, W.; Cui, Y.; Hanley, N.; O’Neill, M.; Lombardi, F. A flip-flop based arbiter physical unclonable function (APUF) design with high entropy and uniqueness for FPGA implementation. IEEE Trans. Emerg. Top. Comput. 2019, 9, 1853–1866. [Google Scholar] [CrossRef]
- Rührmair, U.; Sölter, J.; Sehnke, F.; Xu, X.; Mahmoud, A.; Stoyanova, V.; Dror, G.; Schmidhuber, J.; Burleson, W.; Devadas, S. PUF modeling attacks on simulated and silicon data. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1876–1891. [Google Scholar] [CrossRef]
- Ma, Q.; Gu, C.; Hanley, N.; Wang, C.; Liu, W.; O’Neill, M. A machine learning attack resistant multi-PUF design on FPGA. In Proceedings of the 2018 23rd Asia and South Pacific Design Automation Conference (ASP-DAC), Jeju, Republic of Korea, 22–25 January 2018; pp. 97–104. [Google Scholar]
- Saleh, H.; Abulibdeh, E.; Naser, S.; Mohammad, B.; Alqutayri, M.; Muhaidat, S. Security Analysis of Digital-Based Physically Unclonable Functions: Dataset Generation, Machine Learning Modeling, and Correlation Analysis. Machine Learning Modeling, and Correlation Analysis. Available online: https://ssrn.com/abstract=4855555 (accessed on 9 June 2025).
- Ali-Pour, A.; Afghah, F.; Hely, D.; Beroulle, V.; Di Natale, G. Secure puf-based authentication and key exchange protocol using machine learning. In Proceedings of the 2022 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Nicosia, Cyprus, 4–6 July 2022; pp. 386–389. [Google Scholar]
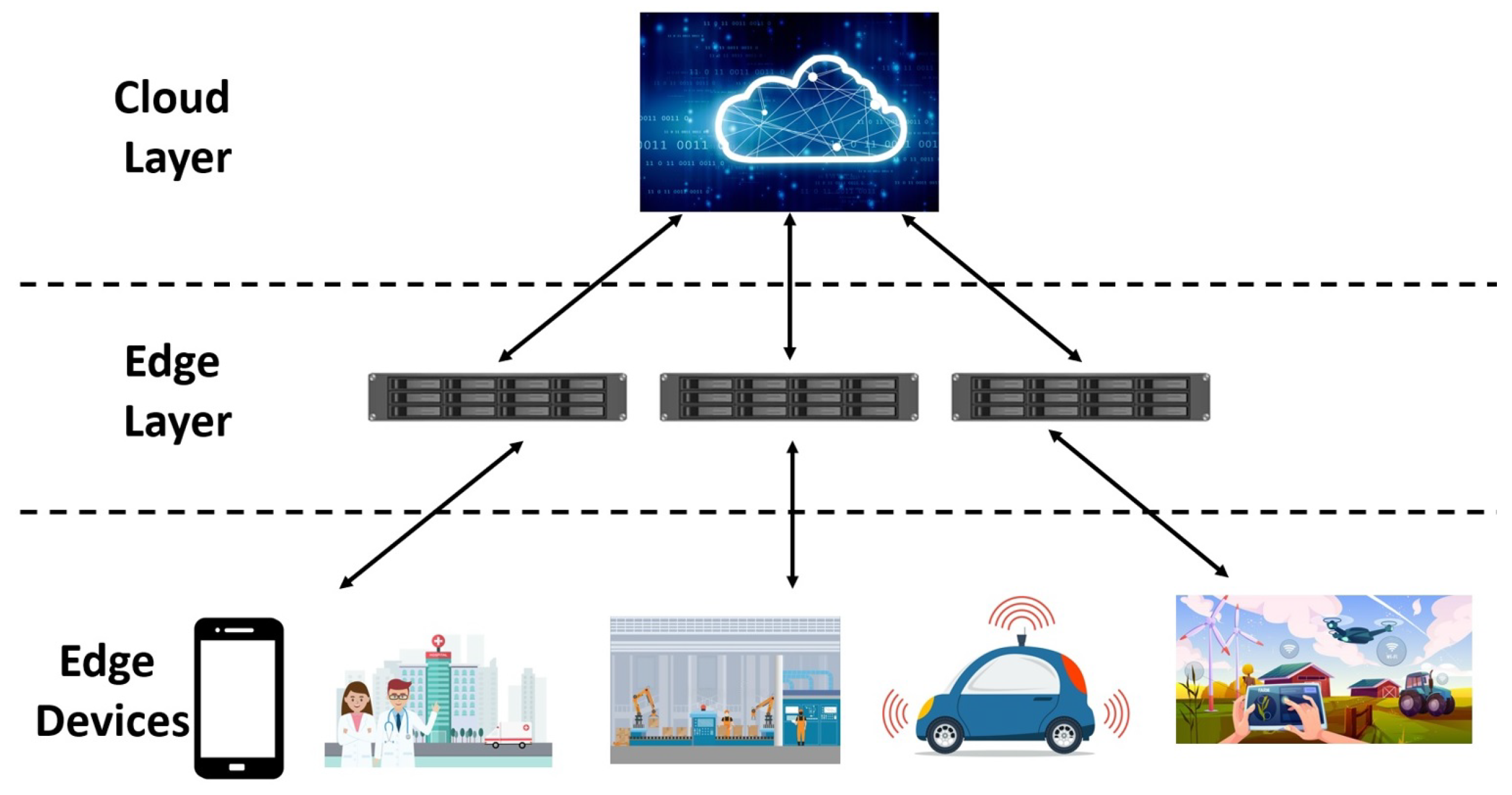







| Type of Threat | Description |
|---|---|
| Hardware or software malware | Software malware exploits vulnerabilities in the operating systems, applications, or network protocols of EC systems. In contrast, hardware malware intrudes at the physical or firmware level, leveraging vulnerabilities in the hardware or its microcode. Malware such as Trojans, worms, and viruses can cause privacy leakage, power depletion, and degraded system performance [38]. |
| Physical tampering and attacks | Physical attacks attempt to gain unauthorized access to and manipulate IoT devices or EC infrastructure. Adversaries might alter hardware characteristics, extract sensitive information, or insert malicious components [39]. |
| Routing information attacks | The routing of data packets in a network can be maliciously manipulated by redirecting or dropping packets [31]. Such attacks include routing loops, false error messages, blackhole attacks (diverting data to incorrect destinations), and grayhole attacks (selectively dropping packets), as well as wormhole attacks, hello flood attacks, and Sybil attacks, which introduce nodes with fake identities [40]. |
| DDoS attacks | Edge servers can be overwhelmed by massive data volumes that exceed network capacity during DDoS attacks, thereby disrupting their responses to legitimate users and posing ransom threats to service providers [41]. |
| Privacy leakage | Privacy threats are amplified when legitimate entities, including edge data centers, infrastructure providers, service providers, and end nodes, have access to user data. In an open IoT ecosystem operating across various trust domains, it becomes difficult to authenticate the trustworthiness of service providers [10]. |
| Eavesdropping or sniffing | Adversaries covertly listen to users’ conversations and data transactions, gaining access to user data, passwords, and communication networks [31]. By eavesdropping, they effectively mask themselves within the system environment, making detection difficult [13]. |
| Jamming attacks | Attackers deliberately flood the communication network with falsified data to deplete its communication, computing, and storage resources [31]. In a jamming attack, the network is disrupted and rendered inoperable by the continuous transmission of random data bits or the emission of radio frequency (RF) signals [42]. |
| Integrity attacks against machine learning | Attackers can compromise the training of machine learning models by manipulating or injecting deceptive data into the training datasets. They may also exploit existing vulnerabilities without directly interfering with the training process [31]. |
| Resources | # |
|---|---|
| Logic elements (LEs) | 10,320 |
| Embedded memory (Kbits) | 414 |
| Embedded 18 × 18 multipliers | 23 |
| General-purpose PLLs | 2 |
| Global clock networks | 10 |
| User I/O banks | 8 |
| Maximum user I/O | 179 |
| Hardware Platforms | Uniformity | Intra-HD | Uniqueness | Ref. |
|---|---|---|---|---|
| Artix7 FPGA | 51.22% | - | 50.81% | [128] |
| Xilinx XC2S200 FPGA | 49% | 5% | 45–50% | [129] |
| Virtex-5 FPGA | 54.78% | - | 4.7% | [130] |
| Virtex-5 FPGA | 42.34% | - | 36.75% | [131] |
| Artix-7 FPGA | 57.64% | - | 51.34% | [132] |
| Artix-7 FPGA | 51.84% | - | 46.21% | [133] |
| HSPICE 65 nm ptm | 55.69% | 11.36% | 42.12% | [134] |
| Cyclone IV | 49.28% | 10.81% | 38.6% | Proposed APUF |
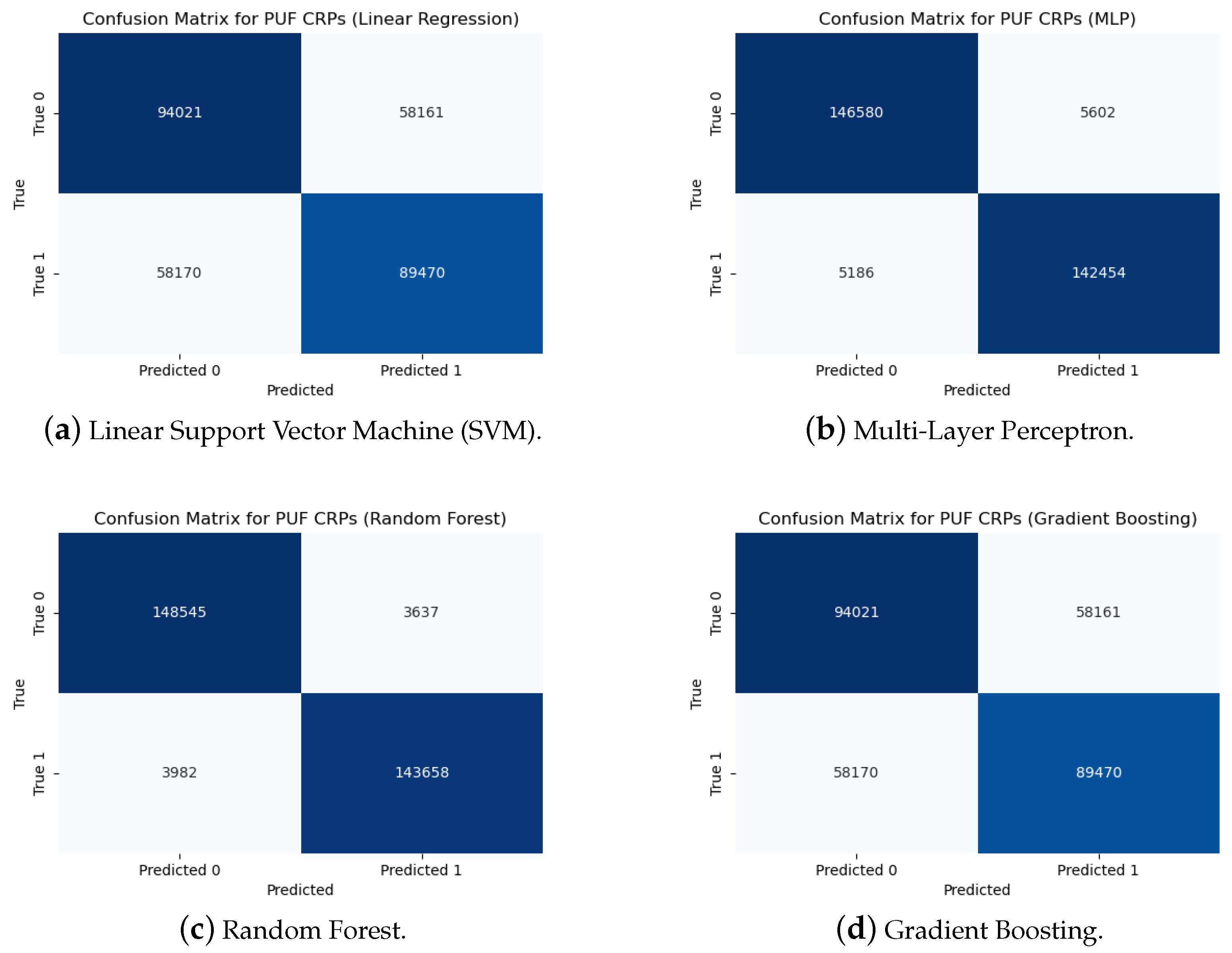
| Regression | TP | TN | FP | FN | Accuracy | Precision | Recall | FDR | F1-Score |
|---|---|---|---|---|---|---|---|---|---|
| LR | 94,021 | 89,470 | 58,170 | 58,161 | 0.612 | 0.617783 | 0.6178195 | 0.393999 | 0.617801 |
| RF | 148,545 | 143,658 | 3982 | 3637 | 0.974588 | 0.973893 | 0.976101 | 0.026971 | 0.974996 |
| MLP | 146,580 | 142,454 | 5186 | 5602 | 0.964019 | 0.965829 | 0.9631888 | 0.035126 | 0.964507 |
| GB | 94,021 | 89,470 | 58,170 | 58,161 | 0.612 | 0.617783 | 0.6178195 | 0.393999 | 0.617801 |
| ML Model | Hyperparameters | Range | Selected Value |
|---|---|---|---|
| SVM | C, , Kernel | [0.1, 0.2, 0.3, 0.4], [0.001, 0.01, 0.1, 1], RBF | 10, 0.1, RBF |
| LR | Regularization C, Max Iterations | [0.001, 0.01, 0.1, 1], [50, 100, 200, 1000] | 0.1, 100 |
| MLP | Hidden Layers, Learning Rate, Epoch | [[64, 32], [128, 64], [100]], [0.001, 0.01, 0.1], 100 (Early Stopping) | [100], 0.01, Early Stopping |
| RF | n_estimators, max_depth, criterion | [50, 100, 200], [5, 15, 25], entropy | 100, 15, entropy |
| GB | n_estimators, learning_rate, max_depth, loss | [50, 100, 200], [0.01, 0.05, 0.1], [3, 5, 7], log_loss | 100, 0.1, 3, log_loss |
| Learning Model | Challenge Bits | Prediction Rate | Training CRP | Ref. |
|---|---|---|---|---|
| LR | 64 | 66.5% | 40,000 | [133] |
| SVM | 64 | 74.7% | 40,000 | [133] |
| LR | 64 | 97% | 40,000 | [137] |
| LR | 64 | 99% | 6500 | [138] |
| SVM | 64 | 86.31% | 1000 | [130] |
| LR | 64 | 80% | 40,000 | [139] |
| LR/SVM | 64 | 51.22%/52.61% | 2,097,152 | [128] |
| Learning Model | Number of CRP’s | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| 50 | 2155 | 4261 | 6366 | 8472 | 105,77 | 12,683 | 14,788 | 16,894 | 19,000 | |
| SVM | 54.6% | 60.7% | 61.6% | 61.2% | 61.3% | 61.2% | 61.1% | 61.1% | 61.1% | 61.1% |
| LR | 55.8% | 63.5% | 63.5% | 63.5% | 63.5% | 63.5% | 63.5% | 63.5% | 63.5% | 63.5% |
| MLP | 57% | 93.7% | 94.3% | 94.9% | 94.9% | 95.3% | 95.4% | 95.2% | 96.3% | 95.4% |
| Random forest | 49.7% | 85% | 91.6% | 94% | 93.9% | 94.8% | 95.9% | 95.2% | 95.5% | 95.9% |
| Gradient Boosting | 56.3% | 63% | 63.4% | 63.8% | 63.1% | 63.2% | 63.3% | 62.5% | 62.7% | 63% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sheikh, A.M.; Islam, M.R.; Habaebi, M.H.; Zabidi, S.A.; Bin Najeeb, A.R.; Kabbani, A. Integrating Physical Unclonable Functions with Machine Learning for the Authentication of Edge Devices in IoT Networks. Future Internet 2025, 17, 275. https://doi.org/10.3390/fi17070275
Sheikh AM, Islam MR, Habaebi MH, Zabidi SA, Bin Najeeb AR, Kabbani A. Integrating Physical Unclonable Functions with Machine Learning for the Authentication of Edge Devices in IoT Networks. Future Internet. 2025; 17(7):275. https://doi.org/10.3390/fi17070275
Chicago/Turabian StyleSheikh, Abdul Manan, Md. Rafiqul Islam, Mohamed Hadi Habaebi, Suriza Ahmad Zabidi, Athaur Rahman Bin Najeeb, and Adnan Kabbani. 2025. "Integrating Physical Unclonable Functions with Machine Learning for the Authentication of Edge Devices in IoT Networks" Future Internet 17, no. 7: 275. https://doi.org/10.3390/fi17070275
APA StyleSheikh, A. M., Islam, M. R., Habaebi, M. H., Zabidi, S. A., Bin Najeeb, A. R., & Kabbani, A. (2025). Integrating Physical Unclonable Functions with Machine Learning for the Authentication of Edge Devices in IoT Networks. Future Internet, 17(7), 275. https://doi.org/10.3390/fi17070275







