Enhanced Beacons Dynamic Transmission over TSCH
Abstract
1. Introduction
2. Time Slotted Channel Hopping Background and Related Work
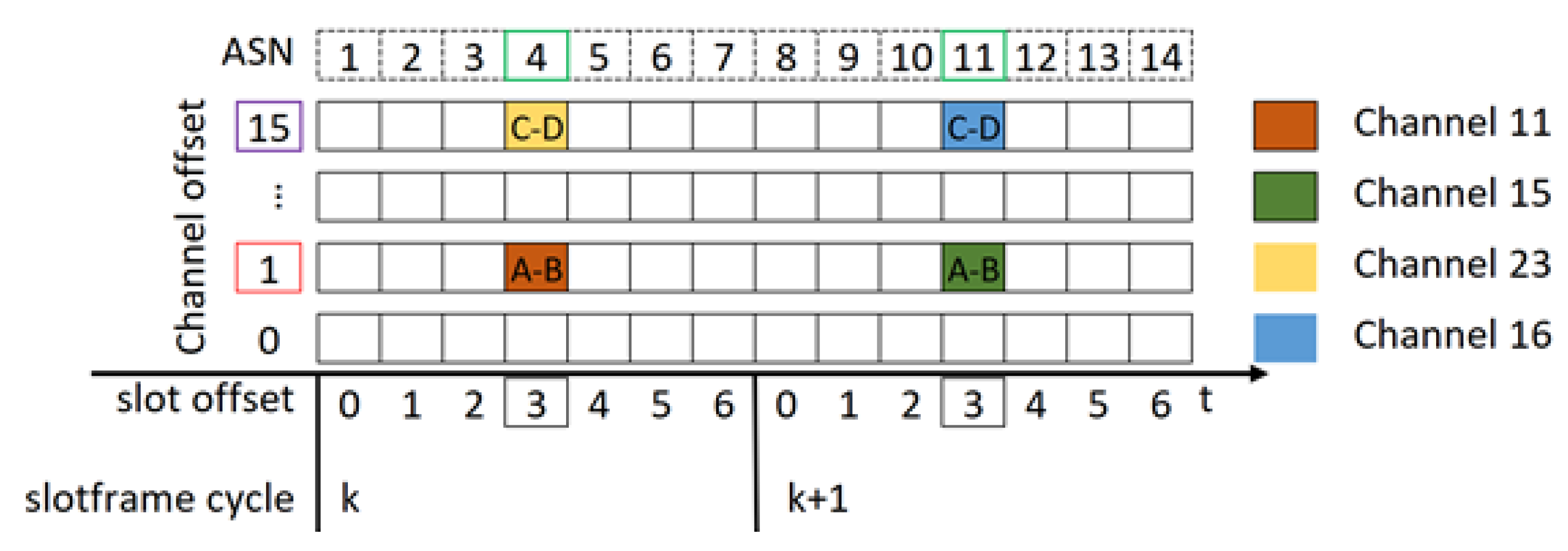
2.1. TSCH Background
2.2. Related Work
- The proposed mechanism achieves a shorter network formation time than the default association mechanism (i.e., default minimal 6TiSCH configuration) without a relevant increase in implementation complexity.
- The proposal is accompanied by a mathematical model validated through simulation, showing a good correspondence between theoretical and simulation results.
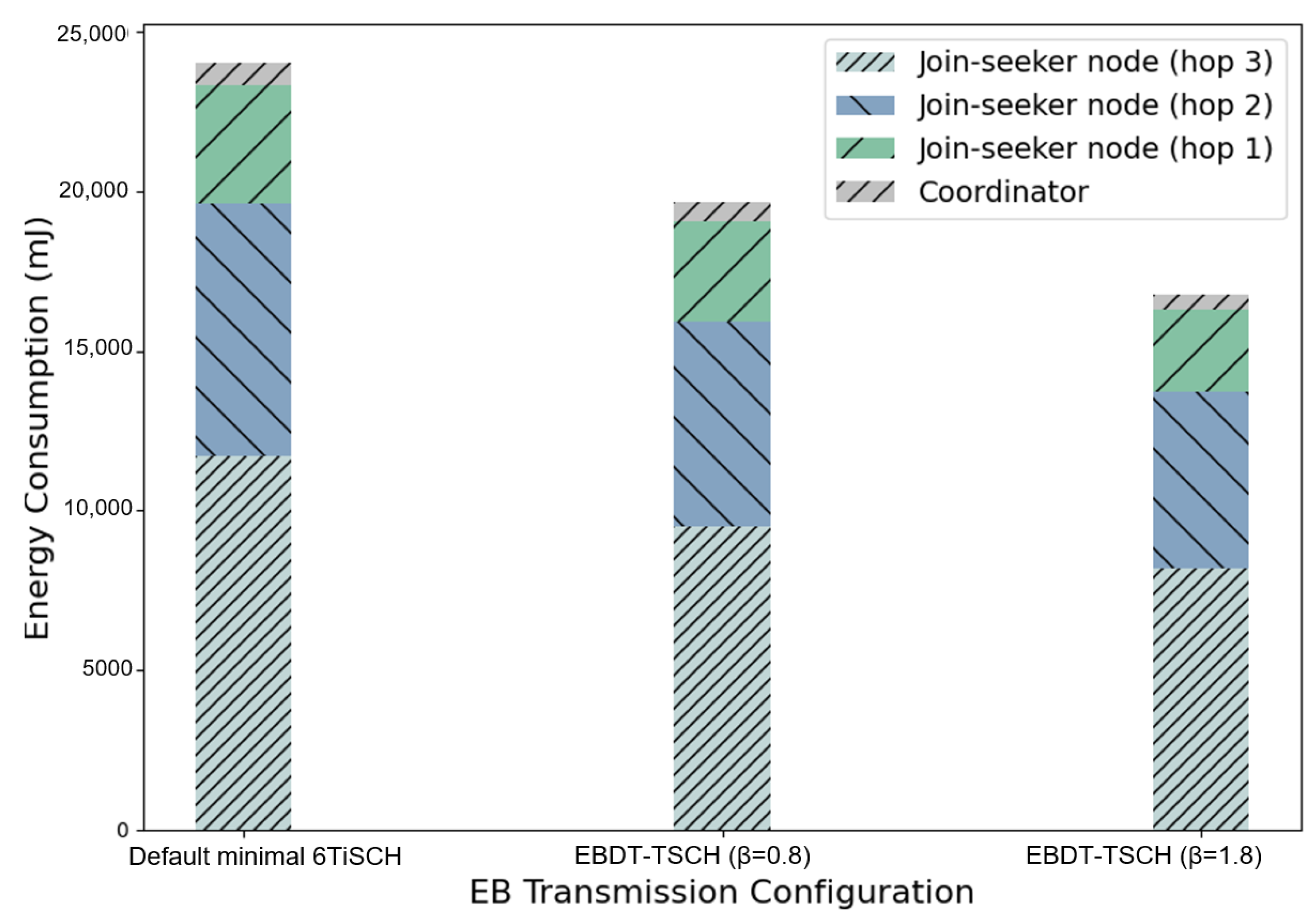
- Simulation results demonstrated that the proposed mechanism not only reduces the network formation time, resulting in data packets beginning to be transmitted earlier, but also reduces the energy consumption during the network formation process.
3. TSCH Implementation in Contiki-NG
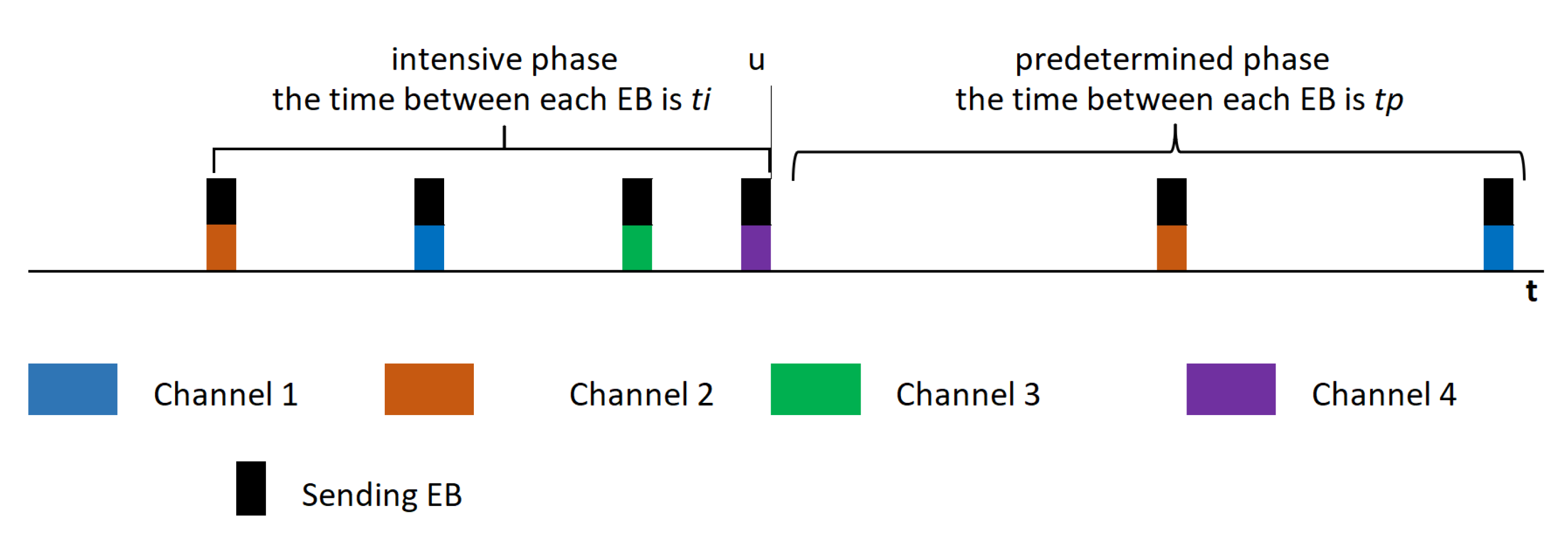
4. Proposed Enhanced Beacons Dynamic Transmission Mechanism
| Algorithm 1 EBDT-TSCH |
|
Input: , , , whiledo if then else end if send EB using end while |
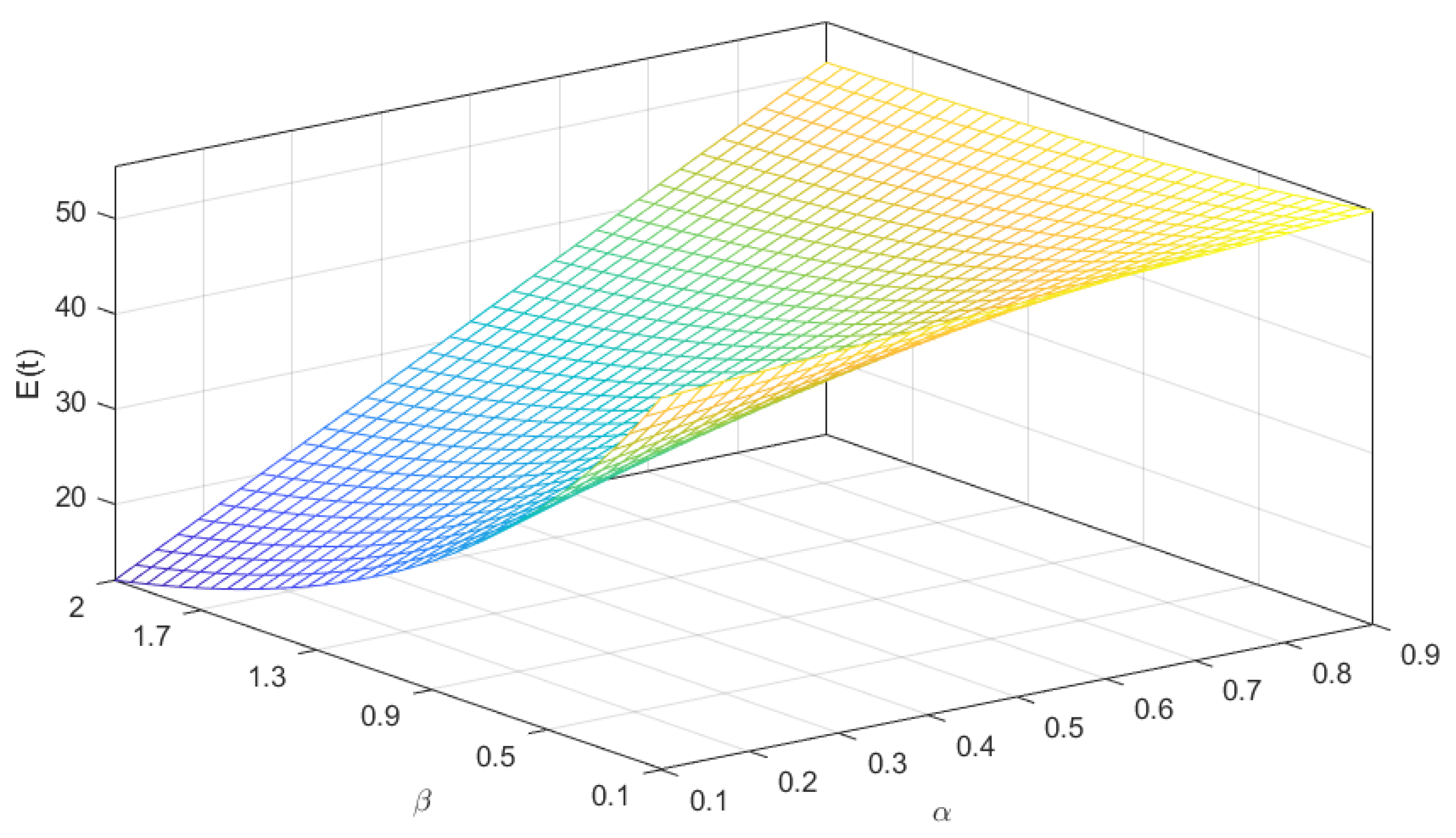
4.1. Theoretical Network Formation Expected Time
4.2. EBDT-TSCH Configuration Parameters
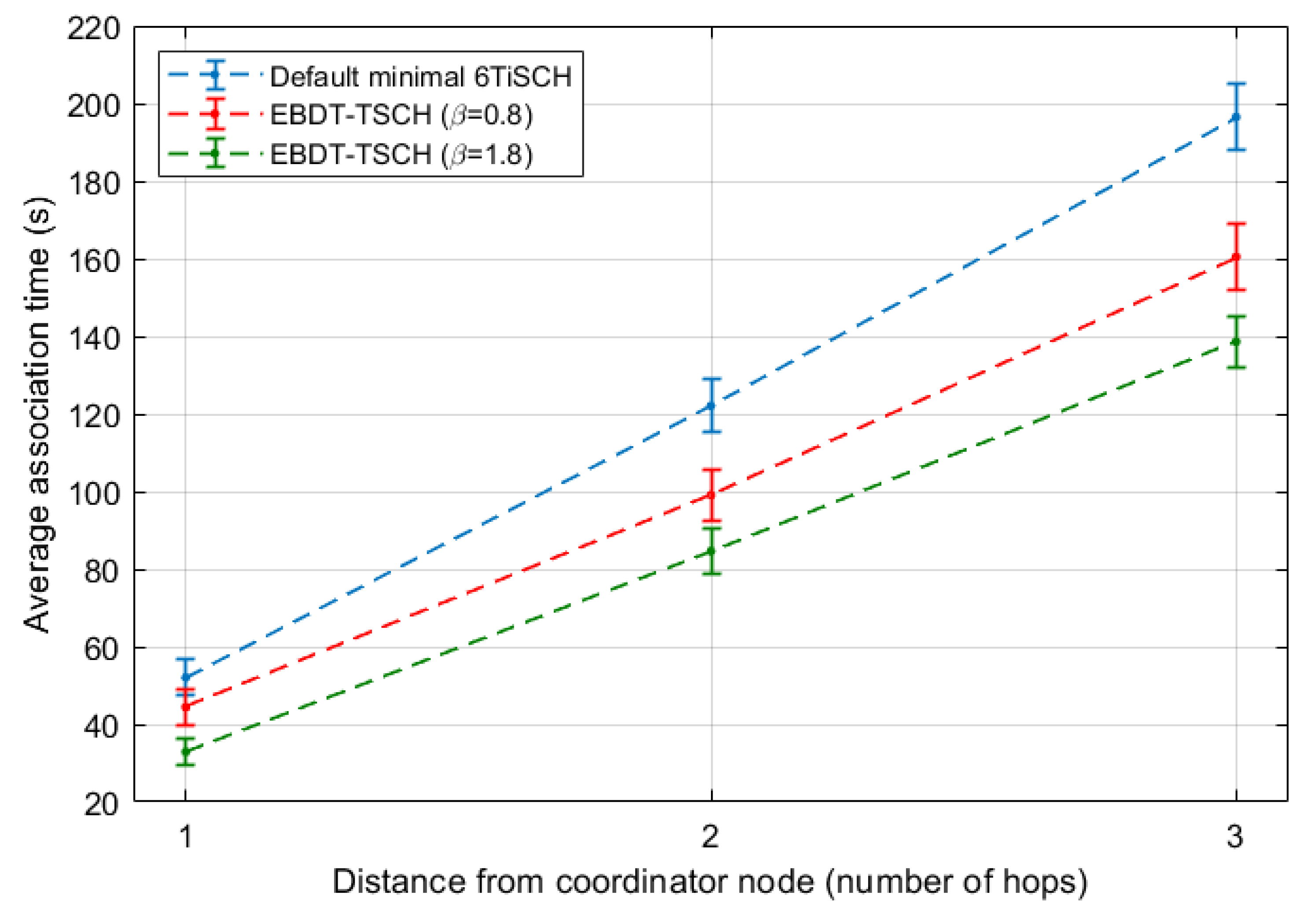
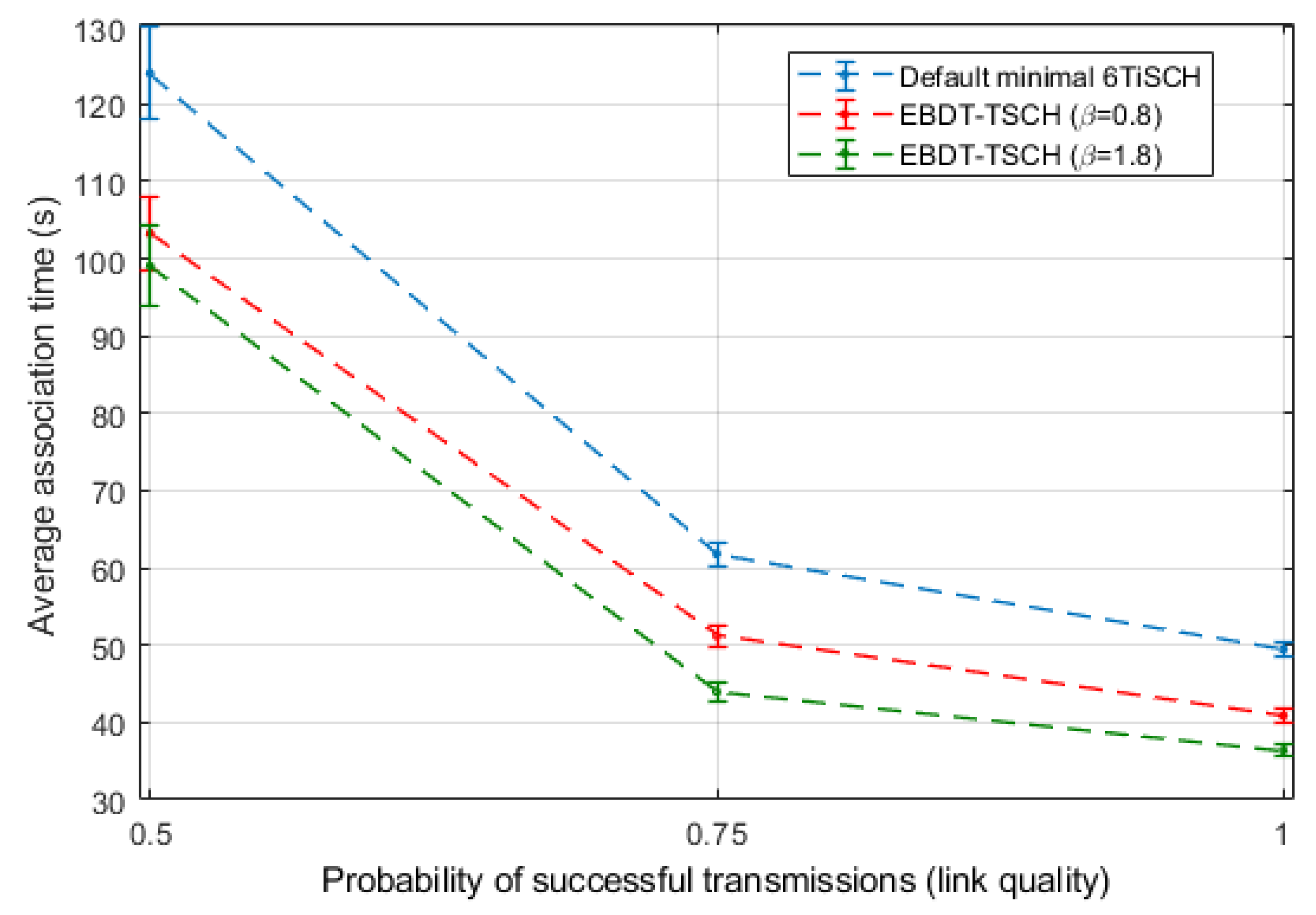
5. Experimental Results and Discussion
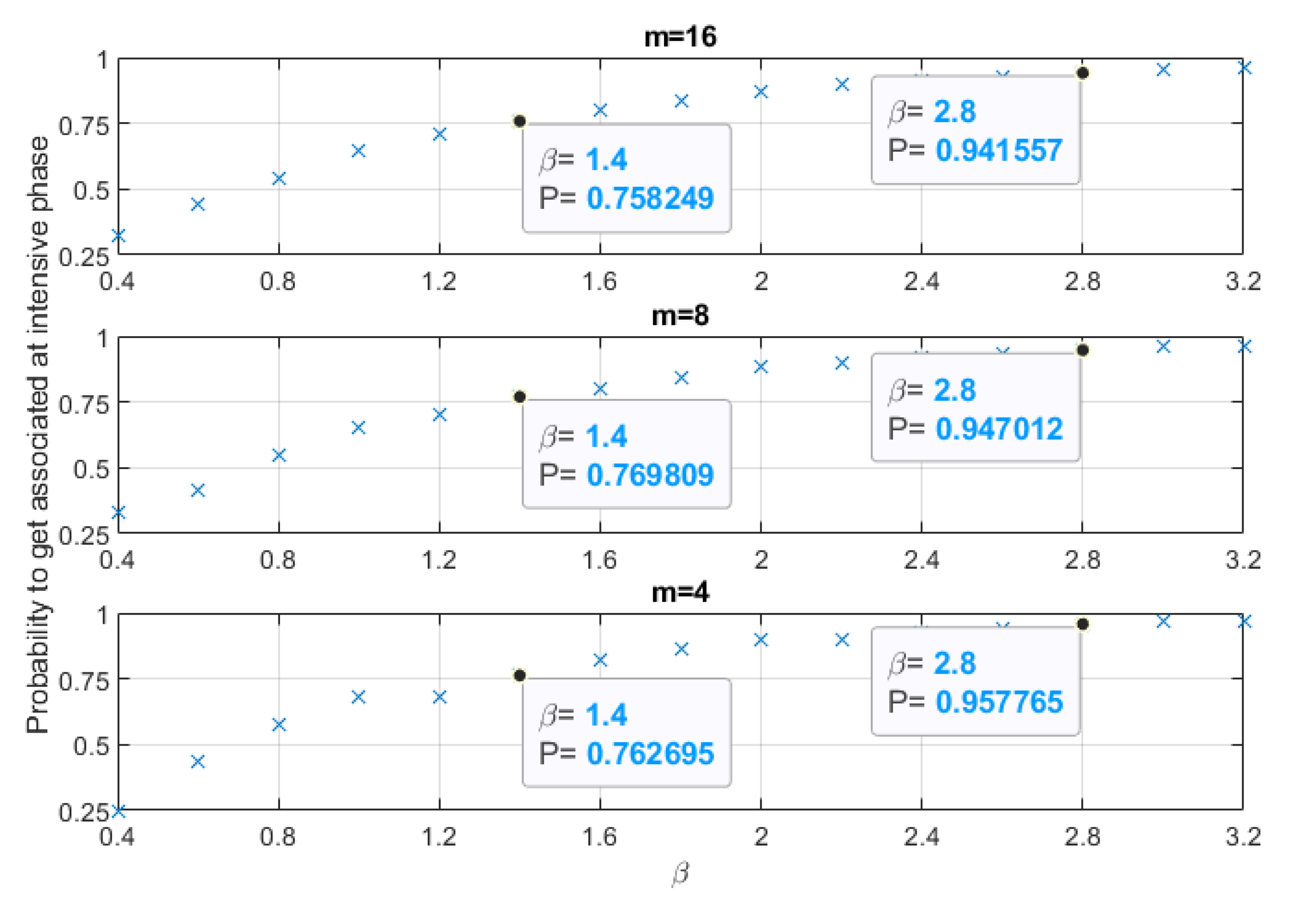
5.1. A Synchronizer–Join-Seeker Pair Scenario
5.2. A Linear Network Scenario
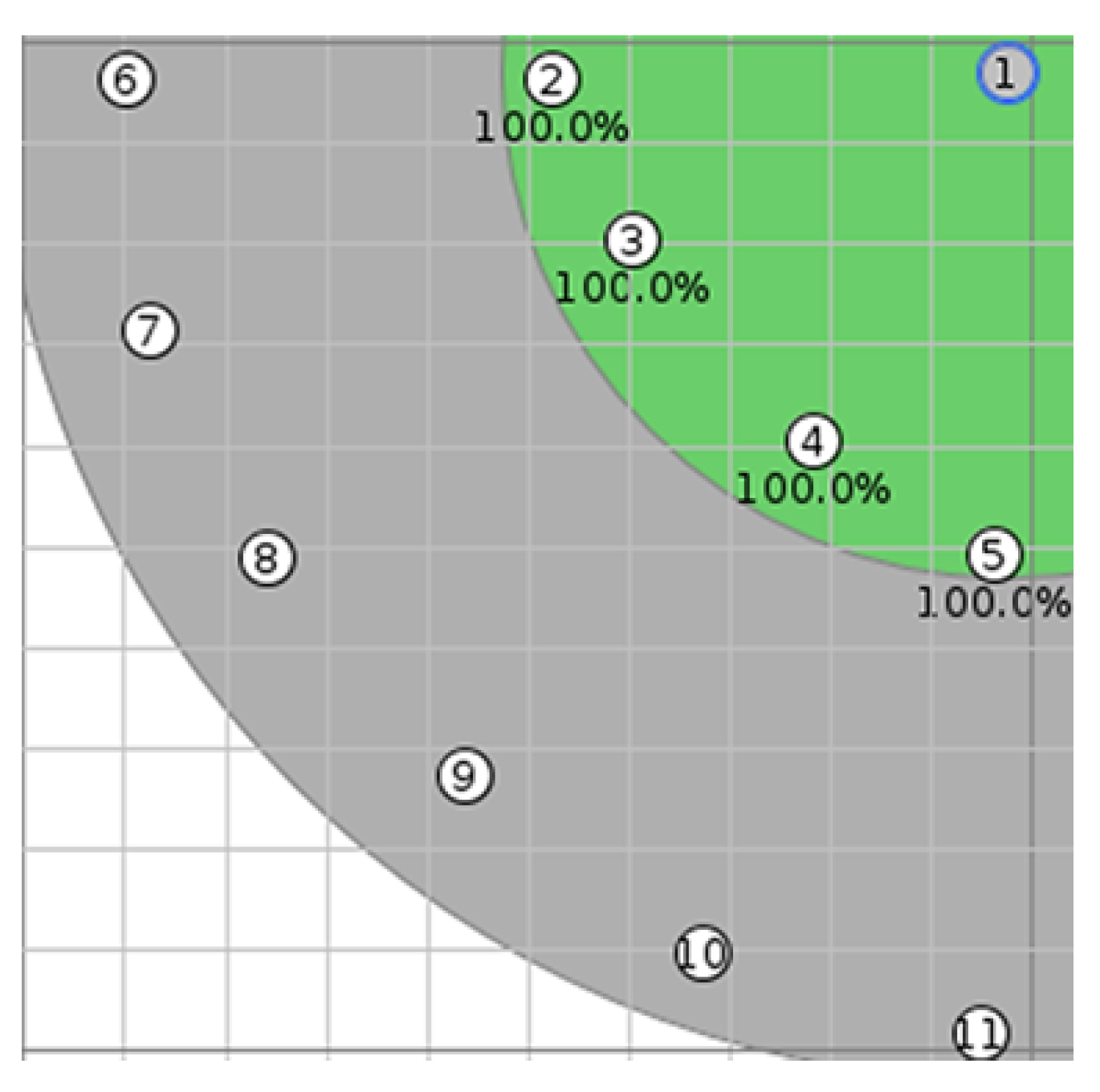
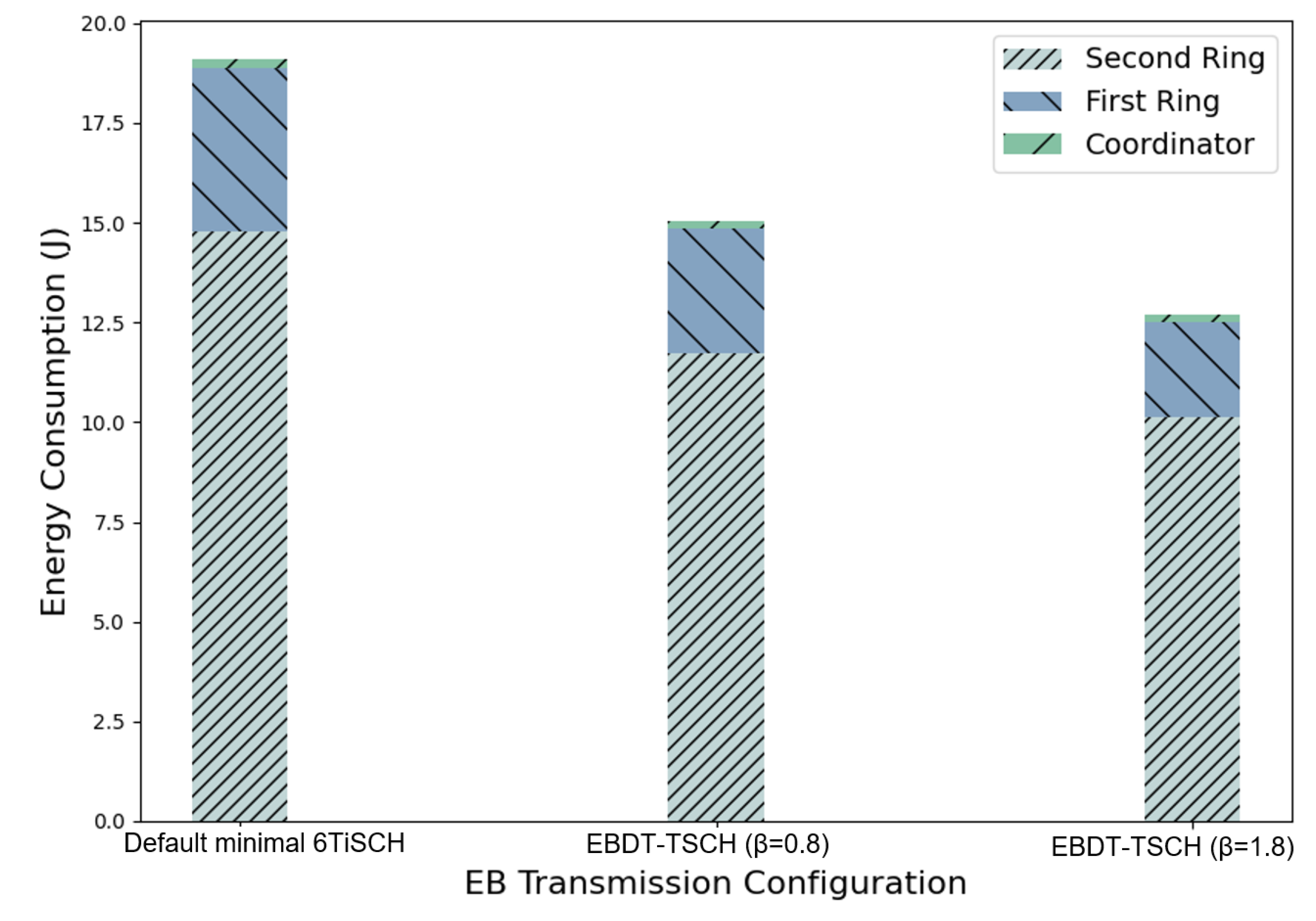
5.3. A Ring Network Scenario
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Proof of Equation (7)
References
- Shafique, K.; Khawaja, B.A.; Sabir, F.; Qazi, S.; Mustaqim, M. Internet of Things (IoT) for Next-Generation Smart Systems: A Review of Current Challenges, Future Trends and Prospects for Emerging 5G-IoT Scenarios. IEEE Access 2020, 8, 23022–23040. [Google Scholar] [CrossRef]
- Li, X.; Xu, L.D. A Review of Internet of Things—Resource Allocation. IEEE Internet Things J. 2021, 8, 8657–8666. [Google Scholar] [CrossRef]
- Ud Din, I.; Guizani, M.; Hassan, S.; Kim, B.S.; Khurram Khan, M.; Atiquzzaman, M.; Ahmed, S.H. The Internet of Things: A Review of Enabled Technologies and Future Challenges. IEEE Access 2019, 7, 7606–7640. [Google Scholar] [CrossRef]
- Kandris, D.; Nakas, C.; Vomvas, D.; Koulouras, G. Applications of Wireless Sensor Networks: An Up-to-Date Survey. Appl. Syst. Innov. 2020, 3, 14. [Google Scholar] [CrossRef]
- 802.15.4c-2009; IEEE Standard for Information Technology, Part 15.4: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications for Low-Rate Wireless Personal Area Networks (LRWPANS). IEEE: Piscataway, NJ, USA, 2009. [CrossRef]
- De Guglielmo, D.; Brienza, S.; Anastasi, G. IEEE 802.15.4e: A survey. Comput. Commun. 2016, 88, 1–24. [Google Scholar] [CrossRef]
- Mantilla Gonzalez, I.A.; Meyer, F.; Turau, V. A Comprehensive Performance Comparison of IEEE 802.15.4 DSME and TSCH in a Realistic IoT Scenario for Industrial Applications. ACM Trans. Internet Things 2023, 4, 1–30. [Google Scholar] [CrossRef]
- Vera-Pérez, J.; Silvestre-Blanes, J.; Sempere-Payá, V. TSCH and RPL Joining Time Model for Industrial Wireless Sensor Networks. Sensors 2021, 21, 3904. [Google Scholar] [CrossRef] [PubMed]
- Algora, C.M.G.; Lopez, E.P.; Reguera, V.A.; Nowe, A.; Steenhaut, K. Poster: Comparative study of EM-MAC and TSCH/Orchestra for IoT. In Proceedings of the 2016 Symposium on Communications and Vehicular Technologies (SCVT), Mons, Belgium, 22 November 2016; pp. 1–6. [Google Scholar]
- Raza, S.; van Der Lee, T.; Exarchakos, G.; Güneş, M. A reliability analysis of TSCH protocol in a mobile scenario. In Proceedings of the 2019 16th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2019; pp. 1–6. [Google Scholar]
- 802.15.4e-2012; IEEE Standard for Local and Metropolitan Area Networks–Part 15.4: Low-Rate Wireless Personal Area Networks (LR-WPANs) Amendment 1: MAC Sublayer. IEEE: Piscataway, NJ, USA, 2012. [CrossRef]
- Elsts, A.; Kim, S.; Kim, H.S.; Kim, C. An empirical survey of autonomous scheduling methods for TSCH. IEEE Access 2020, 8, 67147–67165. [Google Scholar] [CrossRef]
- Vogli, E.; Ribezzo, G.; Grieco, L.A.; Boggia, G. Fast join and synchronization schema in the IEEE 80215.4e MAC. In Proceedings of the 2015 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), New Orleans, LA, USA, 9–12 March 2015; pp. 85–90. [Google Scholar] [CrossRef]
- Vogli, E.; Ribezzo, G.; Grieco, L.A.; Boggia, G. Fast network joining algorithms in industrial IEEE 802.15.4 deployments. Ad. Hoc. Netw. 2018, 69, 65–75. [Google Scholar] [CrossRef]
- Duy, T.P.; Kim, Y. An efficient joining scheme in IEEE 80215.4e. In Proceedings of the 2015 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 28–30 October 2015; pp. 226–229. [Google Scholar] [CrossRef]
- Duy, T.P.; Dinh, T.; Kim, Y. A rapid joining scheme based on fuzzy logic for highly dynamic IEEE 802.15.4e time-slotted channel hopping networks. Int. J. Distrib. Sens. Netw. 2016, 12, 1550147716659424. [Google Scholar] [CrossRef]
- Kim, J.Y.; Chung, S.H.; Ha, Y.V. A fast joining scheme based on channel quality for IEEE80215.4e TSCH in severe interference environment. In Proceedings of the 2017 Ninth International Conference on Ubiquitous and Future Networks (ICUFN), Milan, Italy, 4–7 July 2017; pp. 427–432. [Google Scholar] [CrossRef]
- Khoufi, I.; Minet, P.; Livolant, E.; Rmili, B. Building an IEEE 80215.4e TSCH network. In Proceedings of the 2016 IEEE 35th International Performance Computing and Communications Conference (IPCCC), Las Vegas, NV, USA, 9–11 December 2016; pp. 1–2. [Google Scholar] [CrossRef]
- Khoufi, I.; Minet, P.; Rmili, B. Beacon advertising in an IEEE 802.15.4e TSCH network for space launch vehicles. Acta Astronaut. 2019, 158, 76–88. [Google Scholar] [CrossRef]
- Vallati, C.; Brienza, S.; Anastasi, G.; Das, S.K. Improving Network Formation in 6TiSCH Networks. IEEE Trans. Mob. Comput. 2019, 18, 98–110. [Google Scholar] [CrossRef]
- Karalis, A. ATP: A Fast Joining Technique for IEEE80215. 4-TSCH Networks. In Proceedings of the 2018 IEEE 19th International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Chania, Greece, 12–15 June 2018; pp. 588–599. [Google Scholar] [CrossRef]
- Karalis, A.; Zorbas, D.; Douligeris, C. Collision-Free Advertisement Scheduling for IEEE 802.15.4-TSCH Networks. Sensors 2019, 19, 1789. [Google Scholar] [CrossRef] [PubMed]
- Kalita, A.; Khatua, M. Channel Condition Based Dynamic Beacon Interval for Faster Formation of 6TiSCH Network. IEEE Trans. Mob. Comput. 2021, 20, 2326–2337. [Google Scholar] [CrossRef]
- Mohamadi, M.; Djamaa, B.; Senouci, M.R.; Mellouk, A. FAN: Fast and Active Network Formation in IEEE 802.15.4 TSCH Networks. J. Netw. Comput. Appl. 2021, 183–184, 103026. [Google Scholar] [CrossRef]
- 802.15.4w-2020; IEEE Standard for Low-Rate Wireless Networks. IEEE Standard: Piscataway, NJ, USA, 2020. [CrossRef]
- Vilajosana, X.; Watteyne, T.; Chang, T.; Vučinić, M.; Duquennoy, S.; Thubert, P. Ietf 6tisch: A tutorial. IEEE Commun. Surv. Tutorials 2019, 22, 595–615. [Google Scholar] [CrossRef]
- Hussain, S.J.; Roopa, M. Performance Assessment of the Minimal 6TiSCH Configuration. In Proceedings of the 2022 International Conference on Computing, Communication, Security and Intelligent Systems (IC3SIS), Communication, Kochi, India, 23–25 June 2022; pp. 1–4. [Google Scholar] [CrossRef]
- Vilajosana, X.; Pister, K.; Watteyne, T. Minimal IPv6 over the TSCH Mode of IEEE 802.15.4e (6TiSCH) Configuration. 2017. Available online: https://www.rfc-editor.org/info/rfc8180 (accessed on 1 April 2024).
- Duquennoy, S.; Elsts, A.; Al Nahas, B.; Oikonomo, G. Tsch and 6tisch for contiki: Challenges, design and evaluation. In Proceedings of the 2017 13th International Conference on Distributed Computing in Sensor Systems (DCOSS), Ottawa, ON, Canada, 5–7 June 2017; pp. 11–18. [Google Scholar]
- Algora, C.M.G.; Reguera, V.A.; Fernández, E.M.G.; Steenhaut, K. Parallel rendezvous-based association for IEEE 802.15. 4 TSCH networks. IEEE Sensors J. 2018, 18, 9005–9020. [Google Scholar] [CrossRef]
- Algora, C.M.G.; Guerra, E.O.; Montejo-Sánchez, S.; Fernández, E.M.G.; Steenhaut, K. A Theoretical Association Time Model for IEEE 802.15. 4 TSCH Networks. IEEE Commun. Lett. 2020, 25, 656–659. [Google Scholar] [CrossRef]
- Pettorali, M.; Righetti, F.; Vallati, C.; Das, S.K.; Anastasi, G. Mobility Management in TSCH-based Industrial Wireless Networks. IEEE Trans. Mob. Comput. 2024, 1–18. [Google Scholar] [CrossRef]
- Tavallaie, O.; Taheri, J.; Zomaya, A.Y. Design and Optimization of Traffic-Aware TSCH Scheduling for Mobile 6TiSCH Networks. In Proceedings of the International Conference on Internet-of-Things Design and Implementation, New York, NY, USA, 18–21 May 2021; IoTDI ’21. pp. 234–246. [Google Scholar] [CrossRef]
- Pettorali, M.; Righetti, F.; Vallati, C.; Das, S.K.; Anastasi, G. Mobility Management in Industrial IoT Environments. In Proceedings of the 2022 IEEE 23rd International Symposium on a World of Wireless, Mobile and Multimedia Networks (WoWMoM), Belfast, UK, 14–17 June 2022; pp. 271–280. [Google Scholar] [CrossRef]
- Haubro, M.; Orfanidis, C.; Oikonomou, G.; Fafoutis, X. TSCH-over-LoRA: Long range and reliable IPv6 multi-hop networks for the internet of things. Internet Technol. Lett. 2020, 3, e165. [Google Scholar] [CrossRef]
- Iglesias-Rivera, A.; Van Glabbeek, R.; Guerra, E.O.; Braeken, A.; Steenhaut, K.; Cruz-Enriquez, H. Time-Slotted Spreading Factor Hopping for Mitigating Blind Spots in LoRa-Based Networks. Sensors 2022, 22, 2253. [Google Scholar] [CrossRef] [PubMed]




| Parameter | Symbol | Value/Calculation |
|---|---|---|
| Slotframe length | L | 11 slots |
| Number of network channels | m | 4, 8, 16 |
| Maximum time between beacons | 4 s | |
| Minimum time between beacons | ||
| Maximum time between beacons in the intensive phase | , | |
| Minimum time between beacons in the intensive phase | ||
| Number of EBs sent in the intensive phase | u | , |
| Join-seeker scan period | - |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ortiz Guerra, E.; Martínez Morfa, M.; García Algora, C.M.; Cruz-Enriquez, H.; Steenhaut, K.; Montejo-Sánchez, S. Enhanced Beacons Dynamic Transmission over TSCH. Future Internet 2024, 16, 187. https://doi.org/10.3390/fi16060187
Ortiz Guerra E, Martínez Morfa M, García Algora CM, Cruz-Enriquez H, Steenhaut K, Montejo-Sánchez S. Enhanced Beacons Dynamic Transmission over TSCH. Future Internet. 2024; 16(6):187. https://doi.org/10.3390/fi16060187
Chicago/Turabian StyleOrtiz Guerra, Erik, Mario Martínez Morfa, Carlos Manuel García Algora, Hector Cruz-Enriquez, Kris Steenhaut, and Samuel Montejo-Sánchez. 2024. "Enhanced Beacons Dynamic Transmission over TSCH" Future Internet 16, no. 6: 187. https://doi.org/10.3390/fi16060187
APA StyleOrtiz Guerra, E., Martínez Morfa, M., García Algora, C. M., Cruz-Enriquez, H., Steenhaut, K., & Montejo-Sánchez, S. (2024). Enhanced Beacons Dynamic Transmission over TSCH. Future Internet, 16(6), 187. https://doi.org/10.3390/fi16060187












