PVPBC: Privacy and Verifiability Preserving E-Voting Based on Permissioned Blockchain
Abstract
1. Introduction
- 1.
- Eligibility: each voter should only be allowed to vote once. Only eligible voters are allowed to vote;
- 2.
- Fairness: no early results can be declared during the election period which would influence others who have not voted yet;
- 3.
- Individual verifiability: the ability to check that the vote was correctly counted should be available to individual voters;
- 4.
- Universal verifiability: every independent person should be able to verify the operations performed at every stage of the election as well as to check that the published results actually sum to the total number of cast votes;
- 5.
- Vote privacy: how a voter voted should not be disclosed to anyone;
- 6.
- Receipt freeness: the system should not offer any information which voters can use to prove how they voted. This information is typically expressed in the form of a receipt;
- 7.
- Coercion resistance: the system should not allow the voter to present evidence to a coercer of how they voted.
1.1. Motivation
1.2. Contributions
- We propose an e-voting framework, which is called the PVPBC voting system, which preserves crucial e-voting features: (i) voter privacy and anonymity by making use of a permissioned ledger technology and smart contracts; and (ii) E2E verifiability by making use of the Selene voting scheme and a permissioned DL. Importantly, these crucial features are provided without affecting user experience, as the PVPBC framework does not affect the protocol fulfilled by the voter when they are voting.
- We propose a comprehensive architecture for a capability-based authorization protocol, which can be used to authenticate voters in e-voting platforms. The proposed approach supports dynamic voter authentication in e-voting systems based on an access-control model which supports revocable anonymity, as a result of using permissioned DLs. The protocol includes capability management and access-right validation.
1.3. Organisation
2. Related Work
3. Core of the PVPBC Voting System
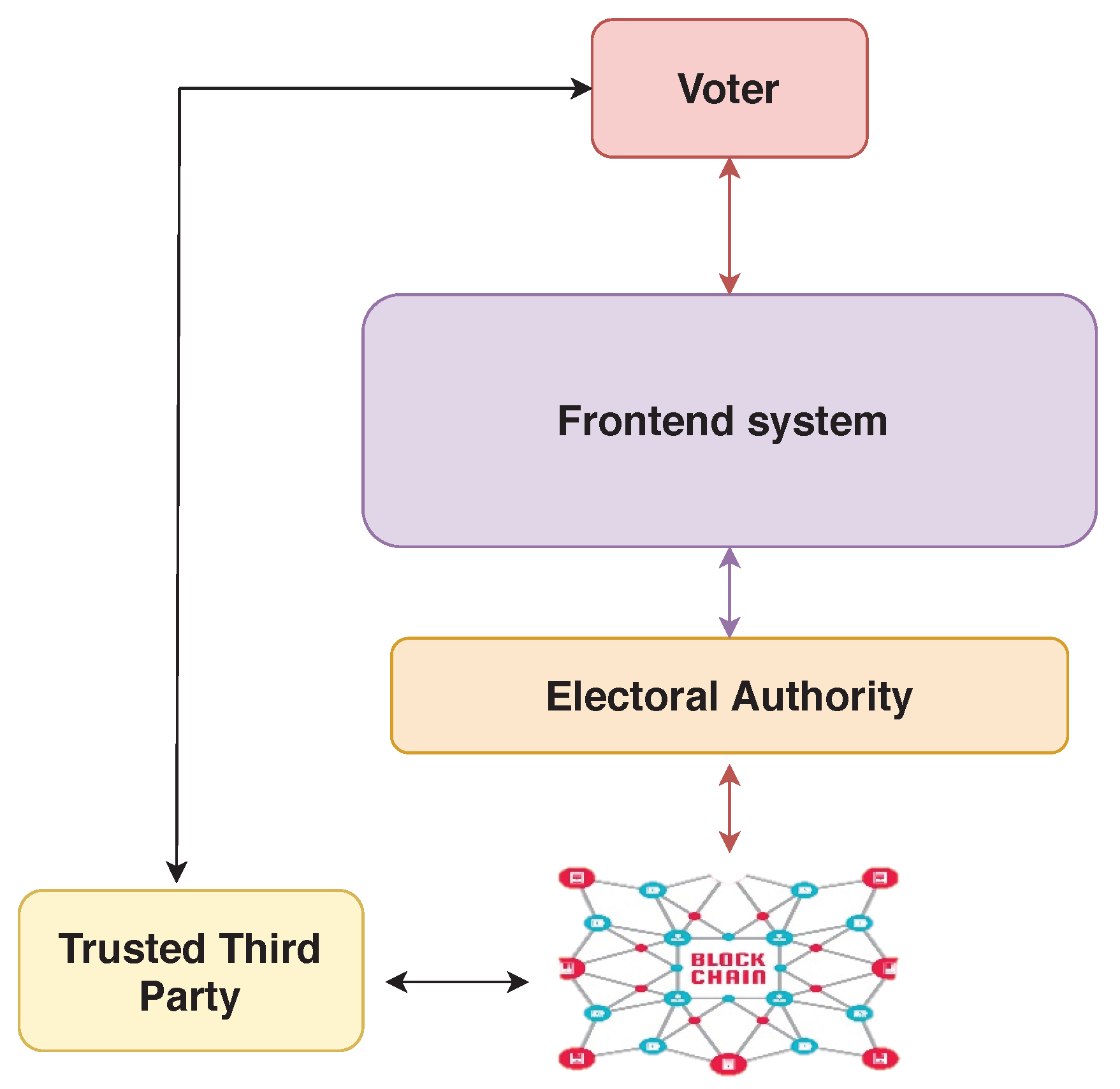
3.1. System Component Overview
- Trusted third party (TTP): an individual or organisation which ensures that the election is correctly held by making use of DL technologies and smart contract to verify eligible voters.
- Front-end system: a self-contained component which provides a verifiability functionality similar to the Selene protocol. A crucial difference from the Selene protocol is that the cryptographic functionality is provided by the front-end system, which includes key generation, signing, and decryption for voters. As a result, these functionalities do not have to be provided by the voters. This is managed independently of the EA. The front-end system also provides the authentication and voting services for voters. Specifically, the front-end system verifies voter-authentication requests and allows eligible voters to access the ballot and to cast their votes.
- Voter-key management: This component manages voter keys and their application. This is run, not by the EA, but by an independent trusted party.
- Tellers: generation and management of the election threshold key and the cryptographic manipulations required by the Selene protocol is performed by a set of tellers [30].
- Web bulletin board (WBB): To distribute trust, the front-end system utilizes a permissioned DL with a group of peers. This process requires a consensus of over two-thirds majority for agreement on the contents of the ledger.
- Voters: Voters interact with the registration website offered by the TTP. Other interactions with the voters are typically via email as well as a voting website which is offered by the front-end system. In our proposed system, voters are not required to handle their own keys. Instead, the voter-key management component manages this for the voters, and voters use the credentials provided to access the required cryptographic functions. The voter-key management component is run by trusted parties within the front-end system.
- Election authority: the EA is in charge of setting up the election, running it, and verifying voter eligibility in collaboration with the front-end system and the TTP.
- Authentication-permissioned DLT: The authentication DLT manages voter authentication by making use of capability tokens, which are embedded in a smart contract. The authentication DLT is maintained by the TTP.
3.2. Assumptions
- 1.
- There are authenticated channels from the front-end system to the authentication server of the EA.
- 2.
- There is a secure channel from the EA to the TTP.
- 3.
- Tellers are trusted parties who collaborate with the EA to run the election.
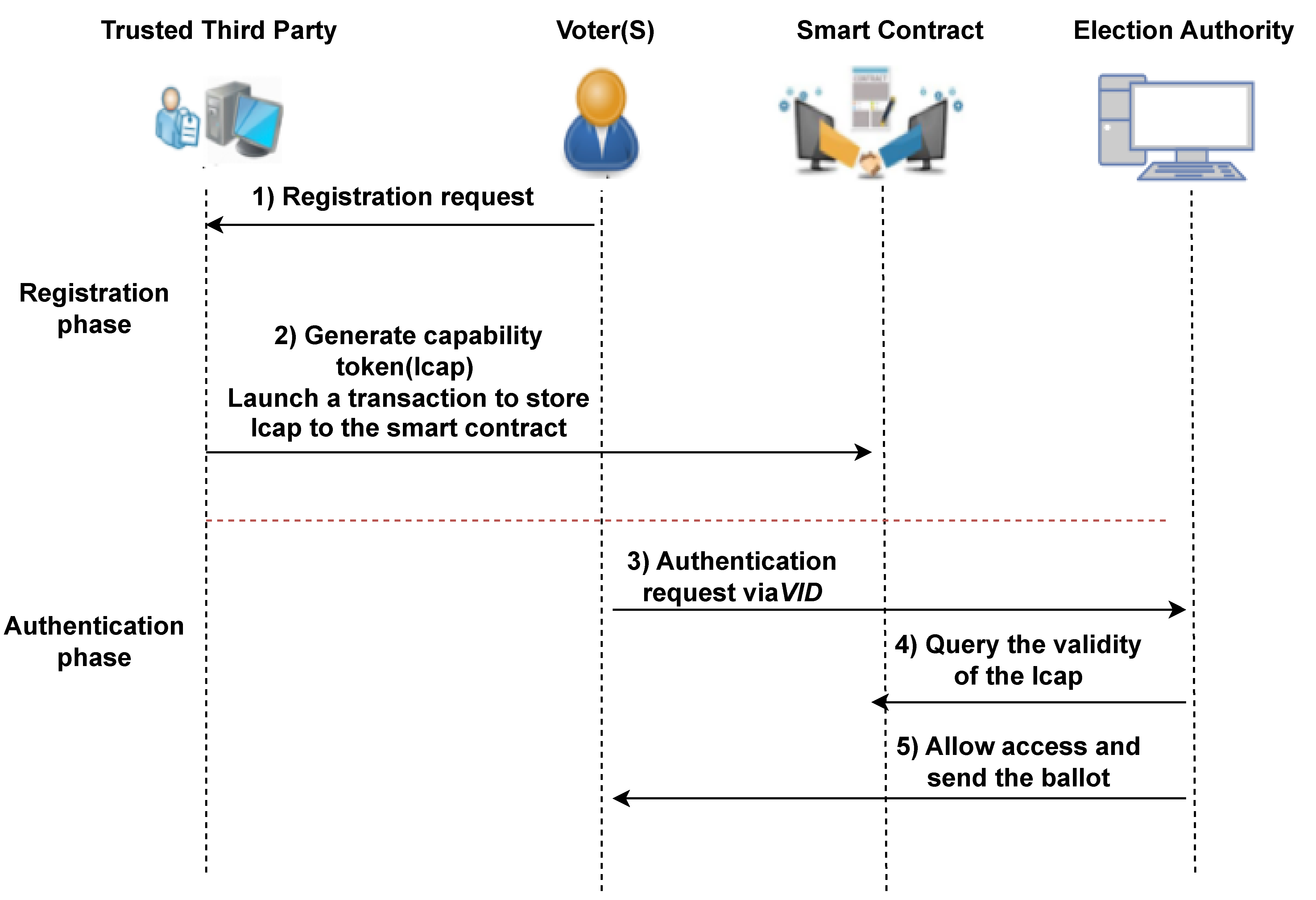
3.3. Authentication with Revocable Anonymity
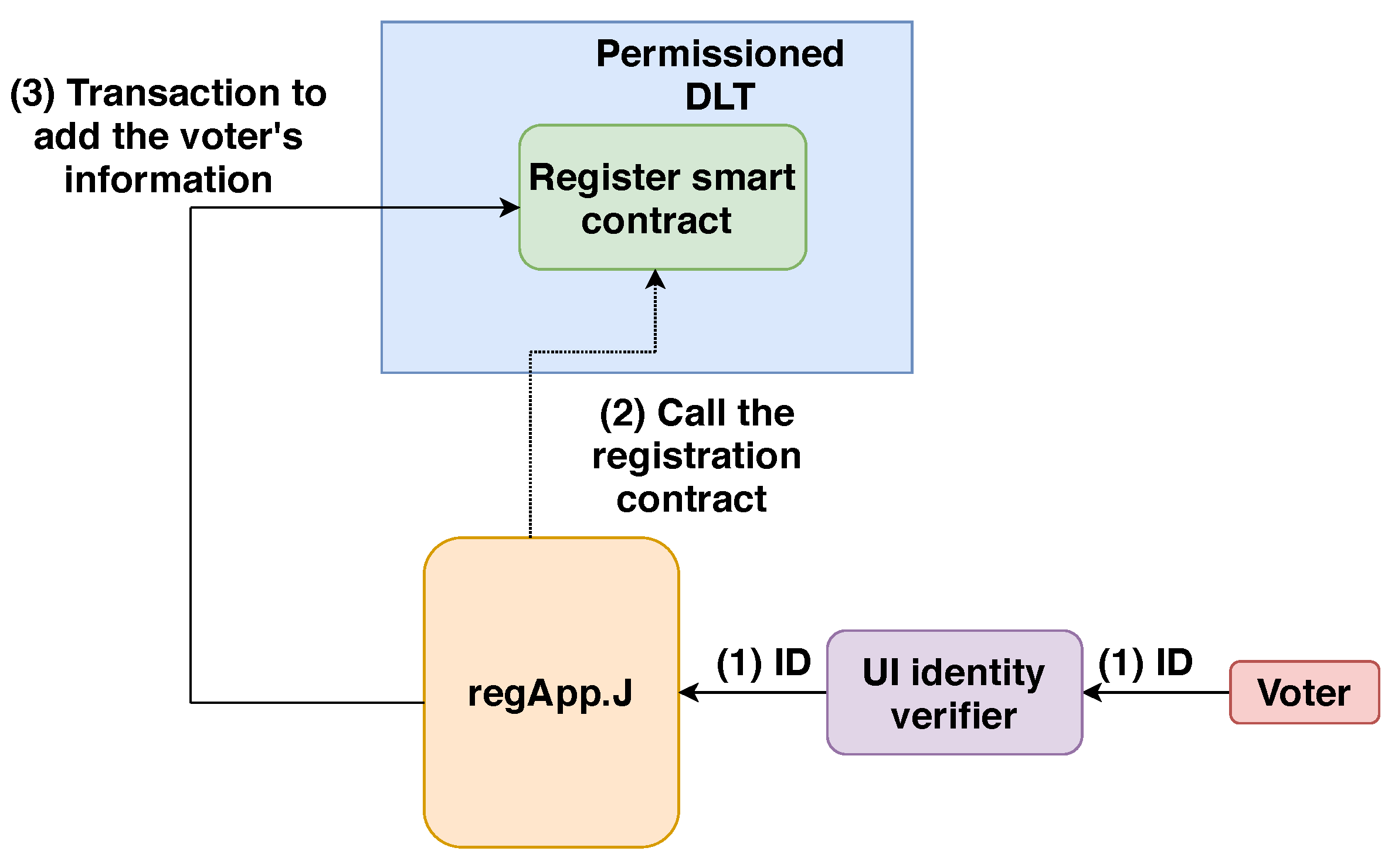
- Initialisation phase: Prior to the election, the maintains a list of ID numbers, which belong to eligible voters. It is populated on the DLT by the TTP administrator . Once the ID number related to the voter is verified, a profile for the registered voter is created on the DLT by calling the Register Smart Contract (more details are provided in Section 6.1). Each voter profile on the DLT includes the registration information tuples (Voter ID number (VID), Flag—“Not voted”). The VID is a unique virtual ID, which is assigned for each registered voter on the DLT.
- Smart-contract deployment: A smart contract, which oversees the capability access token for each eligible voter, must be deployed on the DLT by the TTP. The smart contract can securely manage any algorithmically specified protocol, thanks to cryptographic protocols, when it is deployed over the DLT network. The smart contract supplies a deployAction () ABI (smart-contract interaction interface) for this function. The permission to execute this ABI rests with . When operating this ABI, the must send a transaction which includes the voter information defined in the previous phase, namely, the initialization phase. After synchronizing the permissioned DLT data, any node in the permissioned network, for example, the or the , has the ability to communicate with the smart contract using the contract address provided.
- Authorization validation: The authorization-validation process takes place at the election service provider, in response to receiving an authentication request from the voter during the pre-election phase. More precisely, as shown in Figure 2, the election service provider verifies the present condition of the smart contract in the permissioned DLT to obtain the capability token associated with the voter’s VID. The smart contract furnishes an accessRequest() ABI for verification of the token. The election service provider can accomplish this ABI by submitting the pertinent information, the voter’s VID and the action to be performed using the transaction. The transaction is mined, included into a block and broadcast to the nodes, and , in the TTP DLT network. As part of this process, each node that receives the transaction carries out the ABI to check if the voter possesses the necessary access rights. This assures system users that nodes cannot deceive others with false processing results. The result is a robust and trustworthy access-control system. The election service provider will grant access to the ballot to the voter if the access-right policies and conditional constraints are satisfied and also depending on the capability-token validation and access-authorization-process result. If these conditions are not satisfied, the voting request is denied.
Capability Token Structure
- F: a cryptographic hash function which operates in one direction only;
- : the virtual ID of an eligible voter which solicits access, with the purpose of taking part in the election;
- : the token expiration time;
- : the set of access rights pertaining to a predetermined set of actions;
- T: a timestamp;
- : the tracking number for registered voters. This tracking number is a sparse selection of integers.
4. Role of Permissioned DLTs
4.1. Election Permissioned DLT in the Front-End System
4.2. Authentication Permissioned DLT
5. Voting Experience
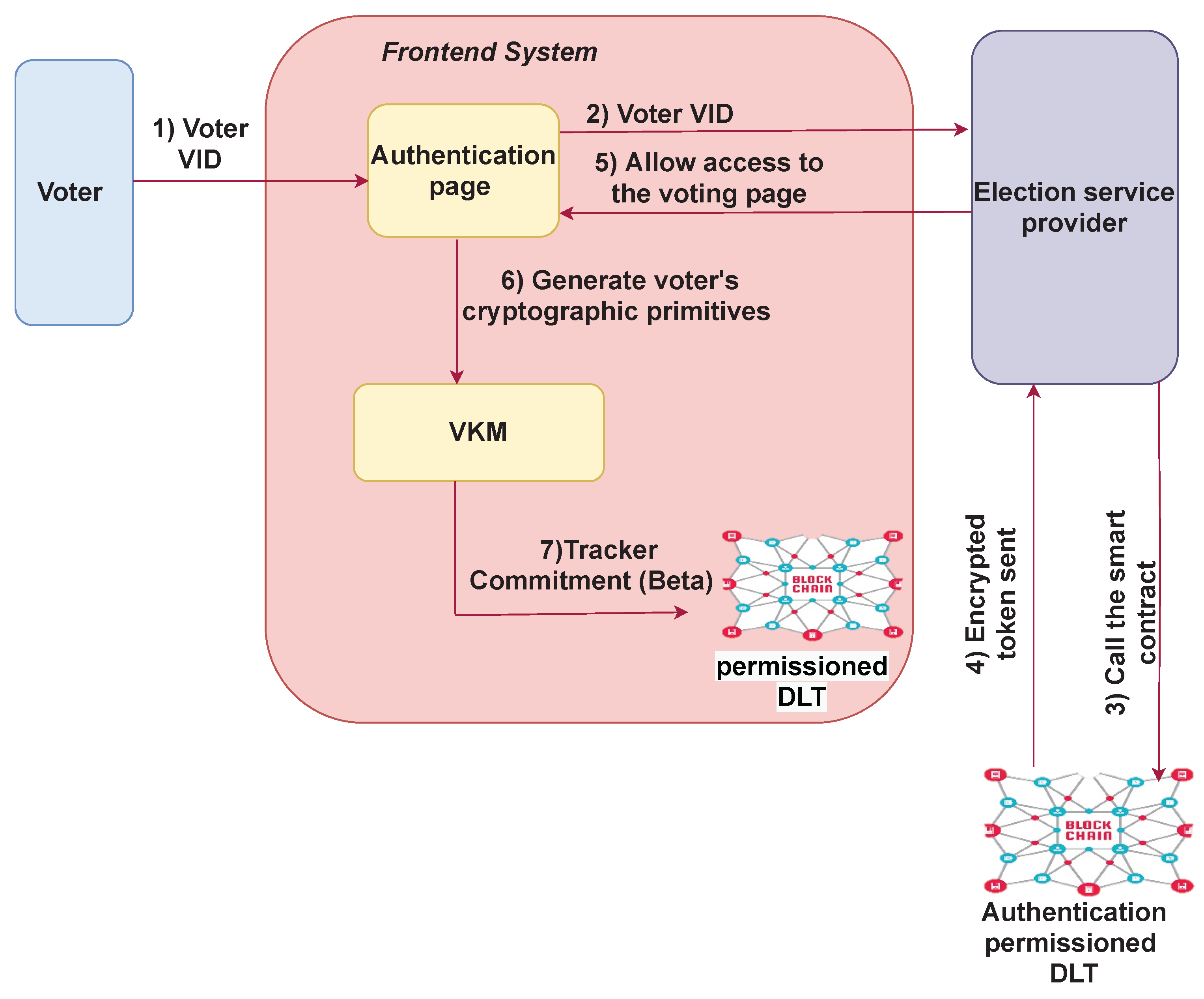
5.1. Pre-Election Phase
5.2. Voting Phase
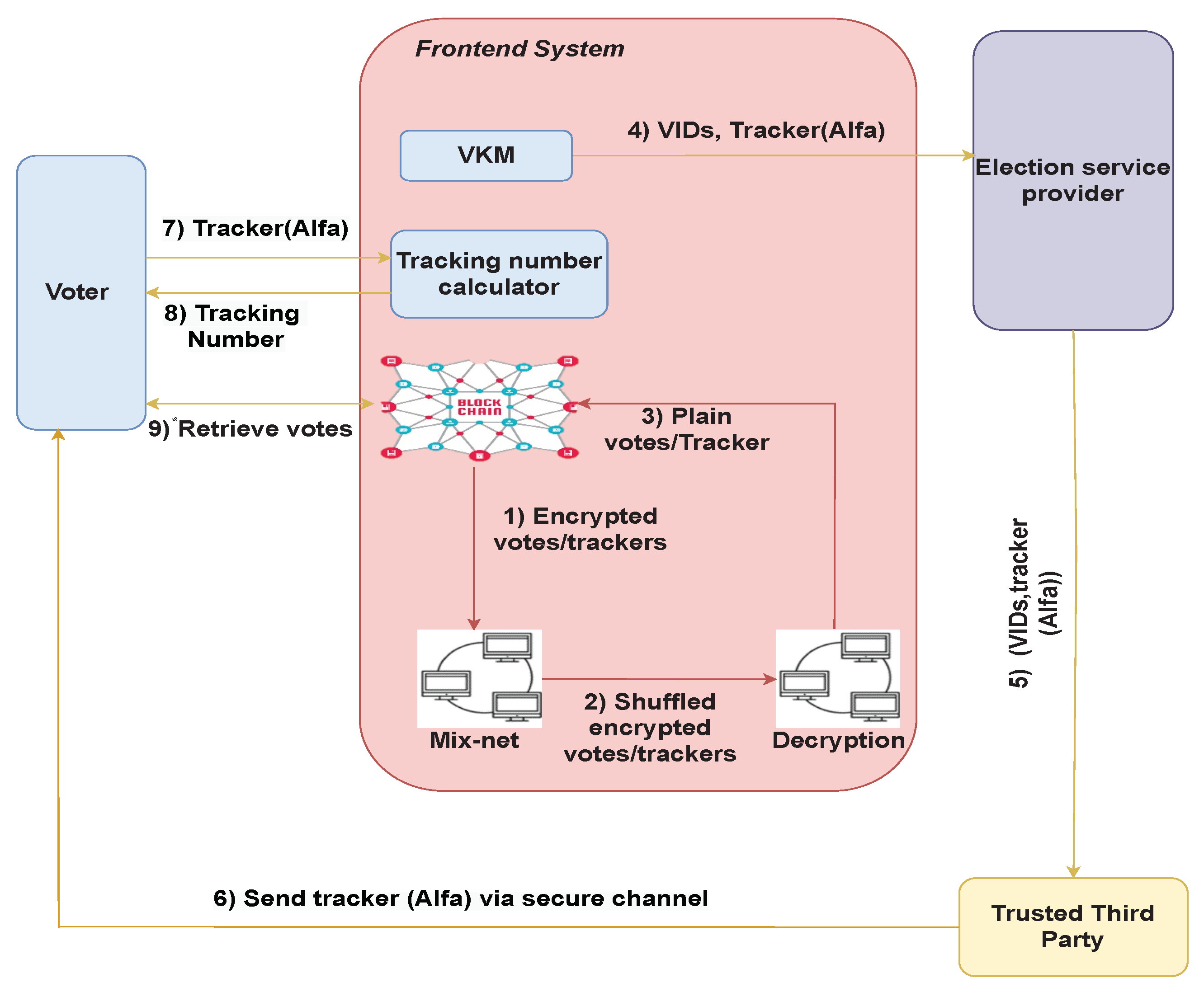
5.3. Post-Election Phase and Tracking-Number Retrieval
6. PVPBC Protocol: Cryptographic Considerations
6.1. Pre-Election Technical Setup
- 1.
- The tracking number, , for the registered voter is extracted from the retrieved token.
- 2.
- The term, , is calculated for the imported tracking number, , in order to make sure that the tracking number falls in the appropriate subgroup.
- 3.
- Tracking numbers, , are encrypted using the encryption key, .
- 4.
- The Sako–Kilian protocol [30] is used to re-encrypt and shuffle the set of encrypted tracking numbers, . The resulting shuffled list is then assigned to the voters, so that each voter is associated with a unique secret encrypted tracker, , where is the permutation induced by the shuffle.
- 1.
- A random number, , is generated for each voter, i, by summing random values, , which were generated by each teller, j, for voter i, where, .
- 2.
- The product, , is generated using the component which is generated by each teller, j, , and then by taking the product of these components. Similarly, can be computed in a distributed fashion. The value, , will not be published, but it will be communicated privately to voters at the end of the election. In the PVPBC voting system, it is not computed until the end of the election.
- 3.
- The product of and is computed to obtain .
- 4.
- Threshold decryption is applied to reveal the commitment . The commitment is published.
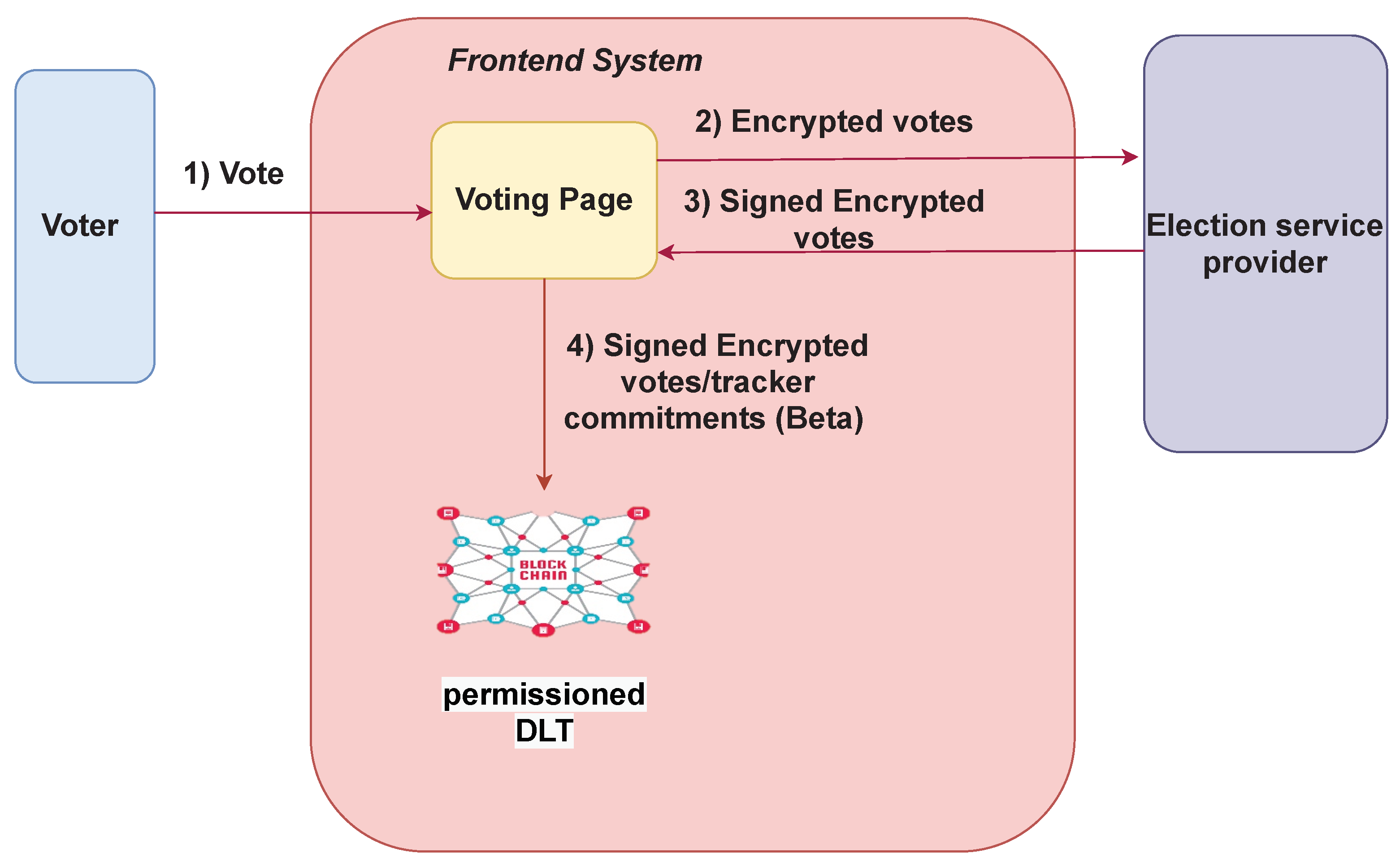
6.2. Election Phase
- 1.
- The ballot is encrypted and signed, obtaining
- 2.
- A non-interactive zero-knowledge proof of the knowledge of the plaintext is created, , and it is attached to the encrypted ballot. In addition, this proof also includes the voter’s verification key, aiming to ensure the proof is valid only for this verification key.
- 3.
- The front end, , submits vi’s ballot to the authentication server, EA, using an authenticated channel alongside the voter’s VID. If the ballot is correctly formed, then the EA signs the ballot and sends the ballot back to the front-end system.
- 4.
- The signed encrypted ballot and the NIZKP are posted on the ledger alongside the previously published encrypted tracking number, tracking number commitment, and voter’s identity (). This process is defined mathematically inThis is the only information published on the ledger. It is important to note that the standard voting information collected by the election system is not published.
6.3. Post-Election Phase
7. Security Analysis
7.1. Security Attributes
7.1.1. Eligibility
7.1.2. Privacy
7.1.3. Integrity
7.1.4. Fairness
7.1.5. Verifiability
7.1.6. Usability
7.2. Malicious-Attack Analysis
7.2.1. Malware
7.2.2. Cross-Site-Scripting (XSS) Attacks
7.2.3. Collusion between DLT Participants
7.2.4. Broken Authentication
8. Performance Analysis
8.1. Prototype System: Voter Registration and Authentication Scheme
- Voter registration: The voter-registration process is described in Algorithm 1. The registerVoter() function in the register-smart-contracts component is used to register a voter on the blockchain. During voter registration, the TTP calls the smart-contract registrar to verify that the provided voter’s ID () is part of the whitelist. If the check is successfully passed, the voter is allowed to register themselves for the election (). The TTP handles the registration transaction, which adds the voter’s information to the authentication blockchain. Subsequently, an access token is placed on the blockchain. The voter’s access token () is entered by the TTP responsible for pushing the contract to the blockchain. It is then stored in the contract state (smartContract).
Algorithm 1: Voter registration. Input: Output: ,invalid()
- Time and gas cost: In order to determine the number of units of gas required by PVPBC to perform voter registration, we measured the gas required to deploy the smart contract as part of voter registration for 10 contracts. We repeated each experiment 30 times for each contract, and report the average time in seconds and cost for each contract. The results are tabulated in Table 2 for each contract. The average, of the average time required for each contract, is 34 s and the average gas cost for all contracts is 181000.
- Authorisation: During the voter-authorisation phase, the voter submits an access request to the front-end system. This process is described in Algorithm 2. When an access request is initiated using the voter’s VID (), the EA initially checks whether or not the token data associated with the user’s address exists in the local database (). If the search for token data fails, the EA interacts with the authorisation contract (querySmartContract(VIDv)), which fetches the token data from the TTP DLT network by calling an exposed-contract method and saving the token data to the local database. After retrieving the access token, the accessRequest() checks the current capability status of the token, such as the initialized, isValid, issuedate, and expireddate functions. If the status of any token is not valid, the authorisation process stops and a deny-access request is sent back to the subject. The EA goes through all the access rules specified in the retrieved token to decide whether to grant the access to the ballot, or not (e.g., Flag ’voted’). The process checks whether or not the request made by the voter (REST-ful method) to access the ballot matches the access rules in the retrieved access token.
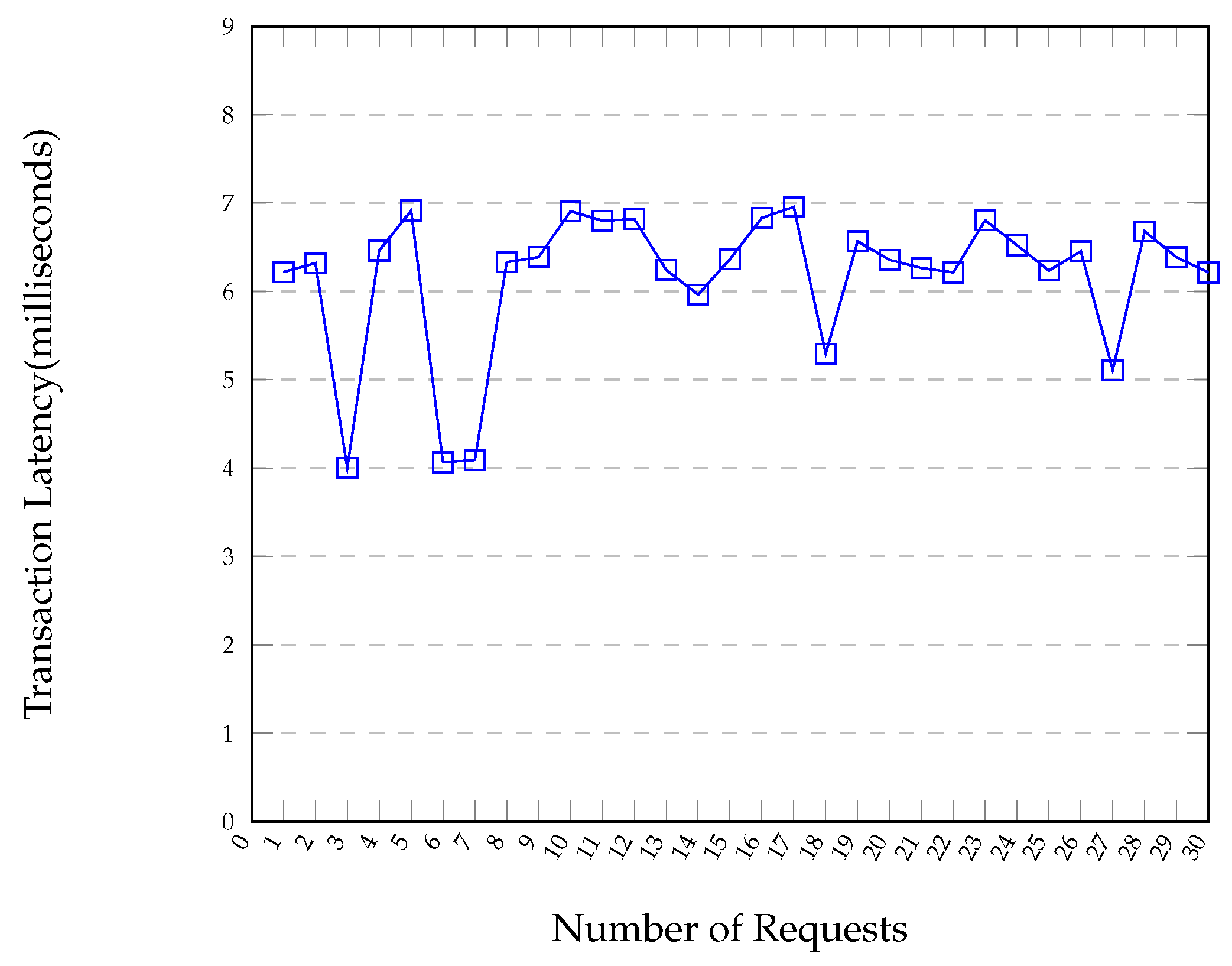
Algorithm 2: Authorise Access (Function accessRequest()). Input: Output: - Time and gas cost: We measured the gas required to deploy the authorisation contract and the associated time. The experiments were repeated 30 times for each contract, and the results obtained are given in Table 3. The average time reported is 33 s, which is similar to the average time report for voter registration; however, the average gas cost reported is significantly larger, e.g., 549719.
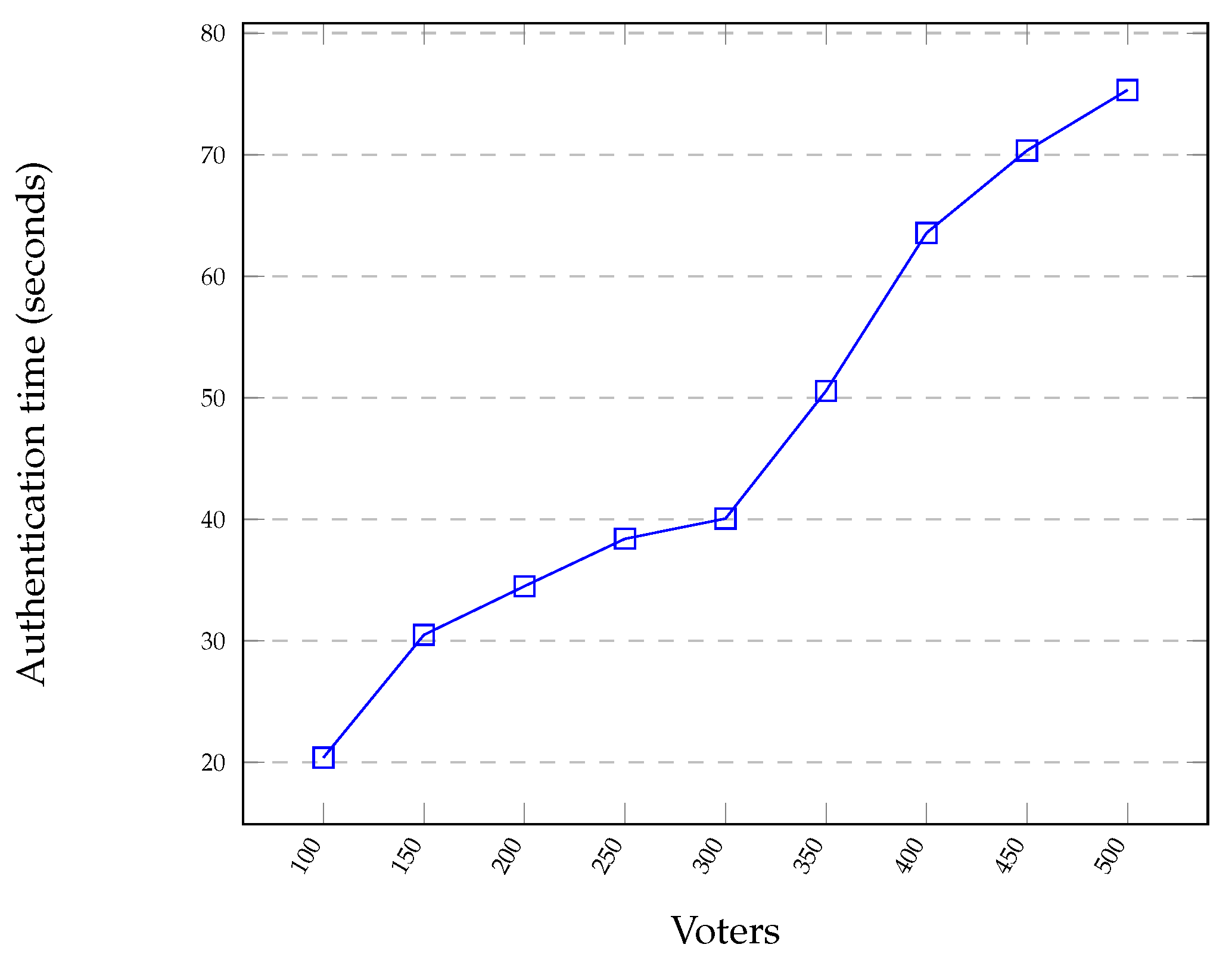
- Authorisation time: The duration between when an access request is submitted to the front-end system and when the request is granted or acted upon is called the authorisation time. To measure the authorisation time, we used the ConsenSys Quorum blockchain to emulate the authentication DLT. For the blockchain private network, we implemented three nodes, which were distributed over three Linux machines, to mimic the TTP nodes. We developed a PoC front-end system which allows the voter to submit the VID to the EA.
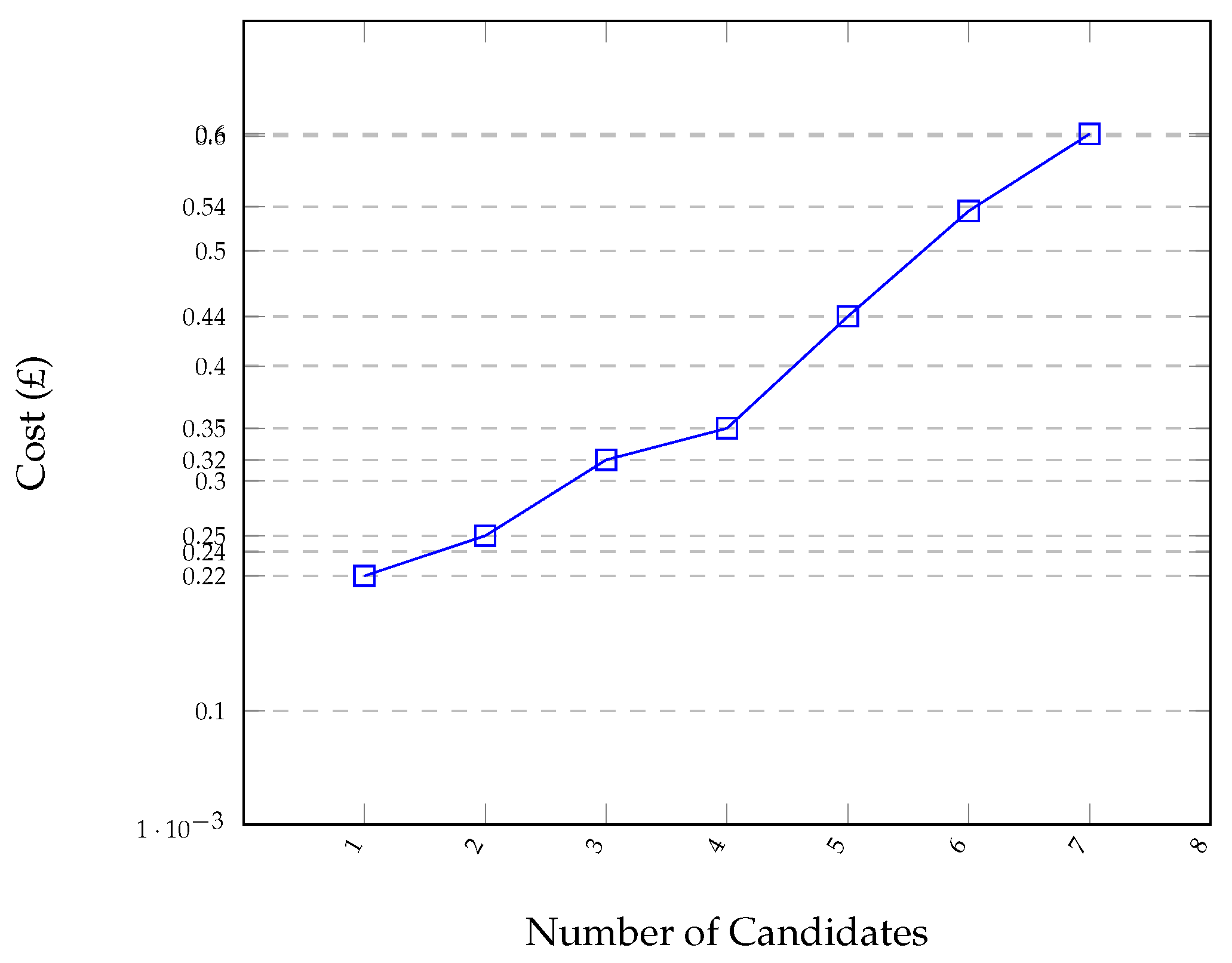
8.2. Voting-Phase Performance Evaluation
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Tarasov, P.; Tewari, H. The future of e-voting. IADIS Int. J. Comput. Sci. Inf. Syst. 2017, 12, 148–165. [Google Scholar]
- Jafar, U.; Aziz, M.J.A.; Shukur, Z. Blockchain for electronic voting system—Review and open research challenges. Sensors 2021, 21, 5874. [Google Scholar] [CrossRef] [PubMed]
- Sallal, M.; Schneider, S.; Casey, M.; Dragan, C.; Dupressoir, F.; Riley, L.; Treharne, H.; Wadsworth, J.; Wright, P. VMV: Augmenting an internet voting system with Selene verifiability. arXiv 2019, arXiv:1912.00288. [Google Scholar]
- Kho, Y.X.; Heng, S.H.; Chin, J.J. A Review of Cryptographic Electronic Voting. Symmetry 2022, 14, 858. [Google Scholar] [CrossRef]
- Mursi, M.F.; Assassa, G.M.; Abdelhafez, A.; Samra, K.M.A. On the development of electronic voting: A survey. Int. J. Comput. Appl. 2013, 61, 1–11. [Google Scholar]
- Arapinis, M.; Kashefi, E.; Lamprou, N.; Pappa, A. A comprehensive analysis of quantum e-voting protocols. arXiv 2018, arXiv:1810.05083. [Google Scholar]
- Ryan, P.Y.; Rønne, P.B.; Iovino, V. Selene: Voting with transparent verifiability and coercion-mitigation. In Financial Cryptography and Data Security: FC 2016 International Workshops, BITCOIN, VOTING, and WAHC, Christ Church, Barbados, 26 February 2016, Revised Selected Papers 20; Springer: Berlin/Heidelberg, Germany, 2016; pp. 176–192. [Google Scholar]
- Cruz, J.P.; Kaji, Y. E-voting system based on the bitcoin protocol and blind signatures. IPSJ Trans. Math. Model. Its Appl. 2016, 10, 14–22. [Google Scholar]
- Kardaş, S.; Kiraz, M.S.; Bingöl, M.A.; Birinci, F. Norwegian internet voting protocol revisited: Ballot box and receipt generator are allowed to collude. Secur. Commun. Netw. 2016, 9, 5051–5063. [Google Scholar] [CrossRef]
- Basin, D.; Radomirović, S.; Schmid, L. Dispute resolution in voting. In Proceedings of the 2020 IEEE 33rd Computer Security Foundations Symposium (CSF), IEEE, Boston, MA, USA, 22–26 June 2020. [Google Scholar]
- Adida, B. Helios: Web-based open-audit voting. In Proceedings of the 17th conference on Security symposium (SS’08); USENIX Association: Berkeley, CA, USA, 2008; pp. 335–348. [Google Scholar]
- Chaum, D.; Ryan, P.Y.A.; Schneider, S. A practical voterverifiable election scheme. In Proceedings of the Computer Security—ESORICS 2005, 10th European Symposium on Research in Computer Security, Milan, Italy, 12–14 September 2005; pp. 118–139. [Google Scholar]
- Ben-Nun, J.; Fahri, N.; Llewellyn, M.; Riva, B.; Rosen, A.; Ta-Shma, A.; Wikström, D. A new implementation of a dual (paper and cryptographic) voting system. In Proceedings of the 5th International Conference on Electronic Voting, (EVOTE), Bregenz, Austria, 11–14 July 2012. [Google Scholar]
- Carback, R.; Chaum, D.; Clark, J.; Conway, J.; Essex, A.; Herrnson, P.S.; Mayberry, T.; Popoveniuc, S.; Rivest, R.L.; Shen, E.; et al. Scantegrity II Municipal Election at Takoma Park: The First E2E Binding Governmental Election with Ballot Privacy. In Proceedings of the 19th USENIX Security Symposium, Washington, DC, USA, 11–13 August 2010. [Google Scholar]
- Cortier, V.; Fuchsbauer, G.; Galindo, D. BeleniosRF: A Strongly Receipt-Free Electronic Voting Scheme. IACR Cryptol. EPrint Arch. 2015, 2015, 629. [Google Scholar]
- Clarkson, M.R.; Chong, S.; Myers, A.C. Civitas: Toward a secure voting system. In Proceedings of the IEEE Symposium on Security and Privacy (S&P 2008), Oakland, CA, USA, 18–21 May 2008; pp. 354–368. [Google Scholar]
- Benaloh, J. Simple verifiable elections. In Proceedings of the 2006 USENIX/ACCURATE Electronic Voting Technology Workshop, Vancouver, BC, Canada, 1 August 2006. [Google Scholar]
- Ryan, P.Y.A.; Teague, V. Pretty good democracy. In Proceedings of the Security Protocols XVII, 17th International Workshop, Cambridge, UK, 1–3 April 2009; Revised Selected Papers. pp. 111–130. [Google Scholar]
- Lee, K.; James, J.I.; Ejeta, T.G.; Kim, H.J. Electronic voting service using block-chain. J. Digit. Forensics Secur. Law 2016, 11, 8. [Google Scholar] [CrossRef]
- Meter, C. Design of Distributed Voting Systems. arXiv 2017, arXiv:1702.02566. [Google Scholar]
- Bistarelli, S.; Mantilacci, M.; Santancini, P.; Santini, F. An end-to-end voting-system based on bitcoin. In Symposium on Applied Computing; ACM: Rochester, NY, USA, 2017. [Google Scholar]
- Faour, N. Transparent Voting Platform Based on Permissioned Blockchain. arXiv 2018, arXiv:1802.10134. [Google Scholar]
- Benabdallah, A.; Audras, A.; Coudert, L.; Madhoun, N.E.; Badra, M. Analysis of Blockchain Solutions for E-Voting: A Systematic Literature Review. IEEE Access 2022, 10, 70746–70759. [Google Scholar] [CrossRef]
- Leng, J.; Zhou, M.; Zhao, J.L.; Huang, Y.; Bian, Y. Blockchain Security: A Survey of Techniques and Research Directions. IEEE Trans. Serv. Comput. 2022, 15, 2490–2510. [Google Scholar] [CrossRef]
- Sallal, M.; de Fréin, R.; Malik, A.; Aziz, B. An empirical comparison of the security and performance characteristics of topology formation algorithms for Bitcoin networks. Array 2022, 15, 100221. [Google Scholar] [CrossRef]
- Sallal, M.F. Evaluation of Security and Performance of Clustering in the Bitcoin Network, with the Aim of Improving the Consistency of the Blockchain. Doctoral Dissertation, University of Portsmouth, Portsmouth, UK, 2018. [Google Scholar]
- de Fréin, R.; Izima, O.; Malik, A. Detecting Network State in the Presence of Varying Levels of Congestion. In Proceedings of the 2021 IEEE 31st International Workshop on Machine Learning for Signal Processing (MLSP), Gold Coast, Australia, 25–28 October 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Izima, O.; de Fréin, R.; Malik, A. A Survey of Machine Learning Techniques for Video Quality Prediction from Quality of Delivery Metrics. Electronics 2021, 10, 2851. [Google Scholar] [CrossRef]
- Malik, A.; de Fréin, R.; Al-Zeyadi, M.; Andreu-Perez, J. Intelligent SDN Traffic Classification Using Deep Learning: Deep-SDN. In Proceedings of the 2020 2nd International Conference on Computer Communication and the Internet (ICCCI), Nagoya, Japan, 26–29 June 2020; pp. 184–189. [Google Scholar] [CrossRef]
- Sako, K.; Kilian, J. Receipt-free mix-type voting scheme. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Saint-Malo, France, 21–25 May 1995; Springer: Berlin/Heidelberg, Germany, 1995; pp. 393–403. [Google Scholar]
- Sallal, M.; Owenson, G.; Salman, D.; Adda, M. Security and performance evaluation of master node protocol based reputation blockchain in the bitcoin network. Blockchain Res. Appl. 2022, 3, 100048. [Google Scholar] [CrossRef]
- Sallal, M.; Owenson, G.; Adda, M. Bitcoin network measurements for simulation validation and parametrisation. In Proceedings of the 11th International Network Conference, Frankfurt, Germany, 19–21 July 2016. [Google Scholar]
- Pedersen, T.P. A threshold cryptosystem without a trusted party. In Workshop on the Theory and Application of of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1991; pp. 522–526. [Google Scholar]
- Wikström, D. User Manual for the Verificatum Mix-Net Version 1.4. 0; Verificatum AB: Stockholm, Sweden, 2013. [Google Scholar]
- Estehghari, S.; Desmedt, Y. Exploiting the Client Vulnerabilities in Internet E-voting Systems: Hacking Helios 2.0 as an Example. EVT/WOTE 2010, 10, 1–9. [Google Scholar]
- Iqbal, R.; Butt, T.A.; Afzaal, M.; Salah, K. Trust management in social internet of vehicles: Factors, challenges, blockchain, and fog solutions. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719825820. [Google Scholar] [CrossRef]
- Abuidris, Y.; Kumar, R.; Yang, T.; Onginjo, J. Secure large-scale E-voting system based on blockchain contract using a hybrid consensus model combined with sharding. Etri J. 2021, 43, 357–370. [Google Scholar] [CrossRef]
- Riadi, I.; Raharja, P.A. Vulnerability analysis of E-voting application using open web application security project (OWASP) framework. Int. J. Adv. Comput. Sci. Appl. 2019, 10. [Google Scholar] [CrossRef]
- Feng, L.; Zhang, H.; Chen, Y.; Lou, L. Scalable dynamic multi-agent practical byzantine fault-tolerant consensus in permissioned blockchain. Appl. Sci. 2018, 8, 1919. [Google Scholar] [CrossRef]
- Sohoel, H.; Jaatun, M.G.; Boyd, C. OWASP Top 10-Do Startups Care? In Proceedings of the 2018 International Conference on Cyber Security and Protection of Digital Services (Cyber Security), IEEE, Scotland, UK, 11–12 June 2018; pp. 1–8. [Google Scholar]
- Baliga, A.; Subhod, I.; Kamat, P.; Chatterjee, S. Performance evaluation of the quorum blockchain platform. arXiv 2018, arXiv:1809.03421. [Google Scholar]
- de Fréin, R. State Acquisition in Computer Networks. In Proceedings of the 2018 IFIP Networking Conference (IFIP Networking) and Workshops, Zurich, Switzerland, 14–16 May 2018; pp. 1–9. [Google Scholar] [CrossRef]


| Voting Scheme | El | Pr | Vr | Us | Limitations | Strengths |
|---|---|---|---|---|---|---|
| Prét à Voter [12] | ✓ | ✓ | ✓ | × | Secrecy of the election is at risk when the election authority is compromised. Uses cut-and-choose protocols which require complex interaction with the voter. | Offers verifiable elections. |
| Wombat [13] | × | ✓ | ✓ | × | Paper-and-cryptographic-based voting system. Usability issues identified during the trials which arise due to the ballot design. | Overcomes the privacy issues associated with on-demand print ballots. |
| Scantegrity II [14] | × | ✓ | ✓ | × | Does not support verifiability in remote voting. Uses cut-and-choose protocols which require complex interaction with the voter. | Individual verifiability is achieved by a cut-and-choose mechanism. |
| Helios [11] | × | ✓ | × | × | Does not support verifiability in remote voting. Requires a separated public authentication-mechanism service. It is vulnerable to ballot stuffing. | Offers verifiable online elections. |
| Pretty Good Democracy [18] | ✓ | × | ✓ | × | Privacy is at risk as the election system has knowledge of the voting codes associated with the verifiability process. | Individual verifiability is achieved by making use of a code-vote approach. |
| Belenios [15] | ✓ | ✓ | ✓ | × | Not suitable for use in high-stake elections as it is not coercion-resistant. | Offers verifiable online elections. |
| VMV [3] | ✓ | × | ✓ | ✓ | The voter-privacy property is at risk as the EA has full control of the voter’s identity. | Offers verifiable and usable online elections. |
| DLT systems [19,20,21,22] | ✓ | × | × | × | Fails to tackle concerns related to electronic voting. These concerns include, but are not limited to, ballot secrecy, E2E verifiability, resistance to coercion, confirmation of accurate casting and recording of votes, voter eligibility, and the guarantee that all cast ballots before the end of the election will be counted. | Offers faster Internet voting based on blockchain. |
| Contract | Time (s) | Cost (Gas) |
|---|---|---|
| 1 | 32 | 182000 |
| 2 | 35 | 173000 |
| 3 | 33 | 185000 |
| 4 | 34 | 180000 |
| 5 | 35 | 182000 |
| 6 | 35 | 179000 |
| 7 | 34 | 184000 |
| 8 | 33 | 186000 |
| 9 | 35 | 175000 |
| 10 | 34 | 184000 |
| Average | 34 | 181000 |
| Contract | Time (s) | Cost (Gas) |
|---|---|---|
| 1 | 49 | 582033 |
| 2 | 25 | 539234 |
| 3 | 30 | 524892 |
| 4 | 35 | 489234 |
| 5 | 28 | 547834 |
| 6 | 20 | 542934 |
| 7 | 27 | 593485 |
| 8 | 42 | 534584 |
| 9 | 39 | 558394 |
| 10 | 35 | 584574 |
| Average | 33 | 549719 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sallal, M.; de Fréin, R.; Malik, A. PVPBC: Privacy and Verifiability Preserving E-Voting Based on Permissioned Blockchain. Future Internet 2023, 15, 121. https://doi.org/10.3390/fi15040121
Sallal M, de Fréin R, Malik A. PVPBC: Privacy and Verifiability Preserving E-Voting Based on Permissioned Blockchain. Future Internet. 2023; 15(4):121. https://doi.org/10.3390/fi15040121
Chicago/Turabian StyleSallal, Muntadher, Ruairí de Fréin, and Ali Malik. 2023. "PVPBC: Privacy and Verifiability Preserving E-Voting Based on Permissioned Blockchain" Future Internet 15, no. 4: 121. https://doi.org/10.3390/fi15040121
APA StyleSallal, M., de Fréin, R., & Malik, A. (2023). PVPBC: Privacy and Verifiability Preserving E-Voting Based on Permissioned Blockchain. Future Internet, 15(4), 121. https://doi.org/10.3390/fi15040121










