Redactable Blockchain: Comprehensive Review, Mechanisms, Challenges, Open Issues and Future Research Directions
Abstract
1. Introduction
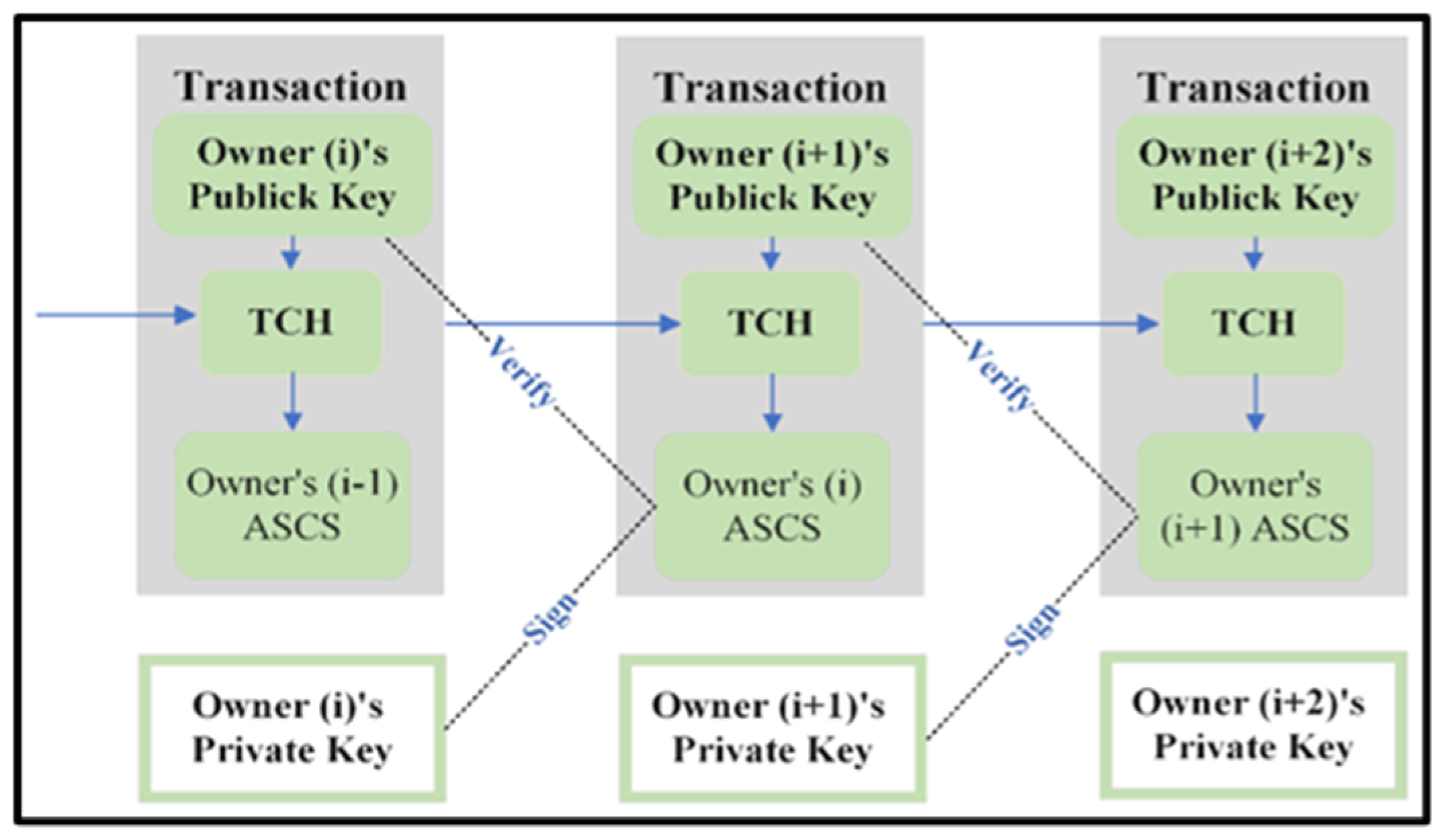
2. Blockchain Technology
3. Blockchain Construction Features
4. Blockchain Types
5. Security Properties
- Chain Quality:
- Common Prefix:
- Chain Growth:
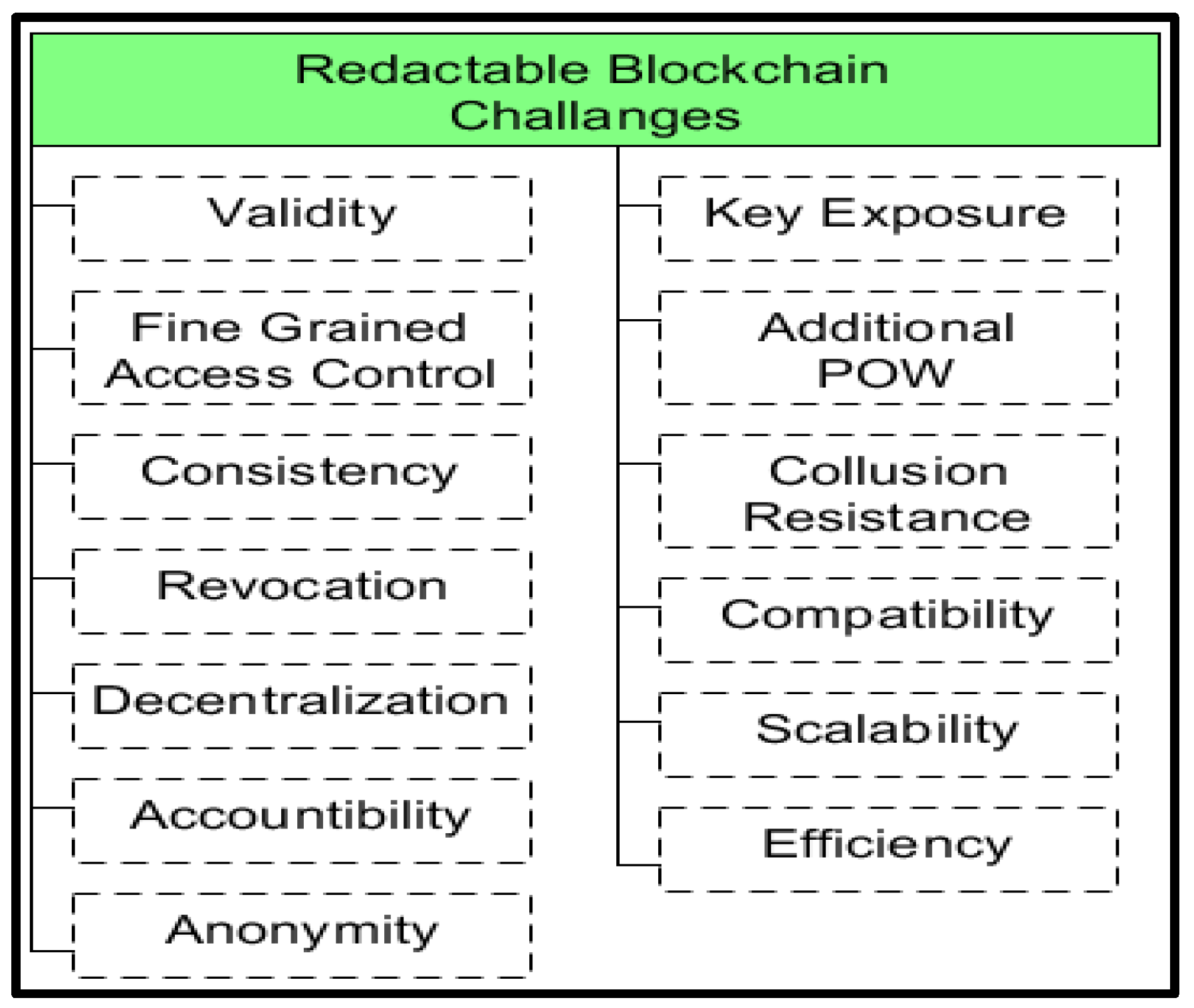
6. Redactable Blockchain Implementation Challenges
6.1. Validity
6.2. Consistency
6.3. Fine Grained
6.4. Decentralization
6.5. Accountability
6.6. Revocation
6.7. Anonymity
6.8. Collusion Resistance
6.9. Scalability
6.10. Efficiency
6.11. Computation Overhead
6.12. Additional PoW
6.13. Key Exposure
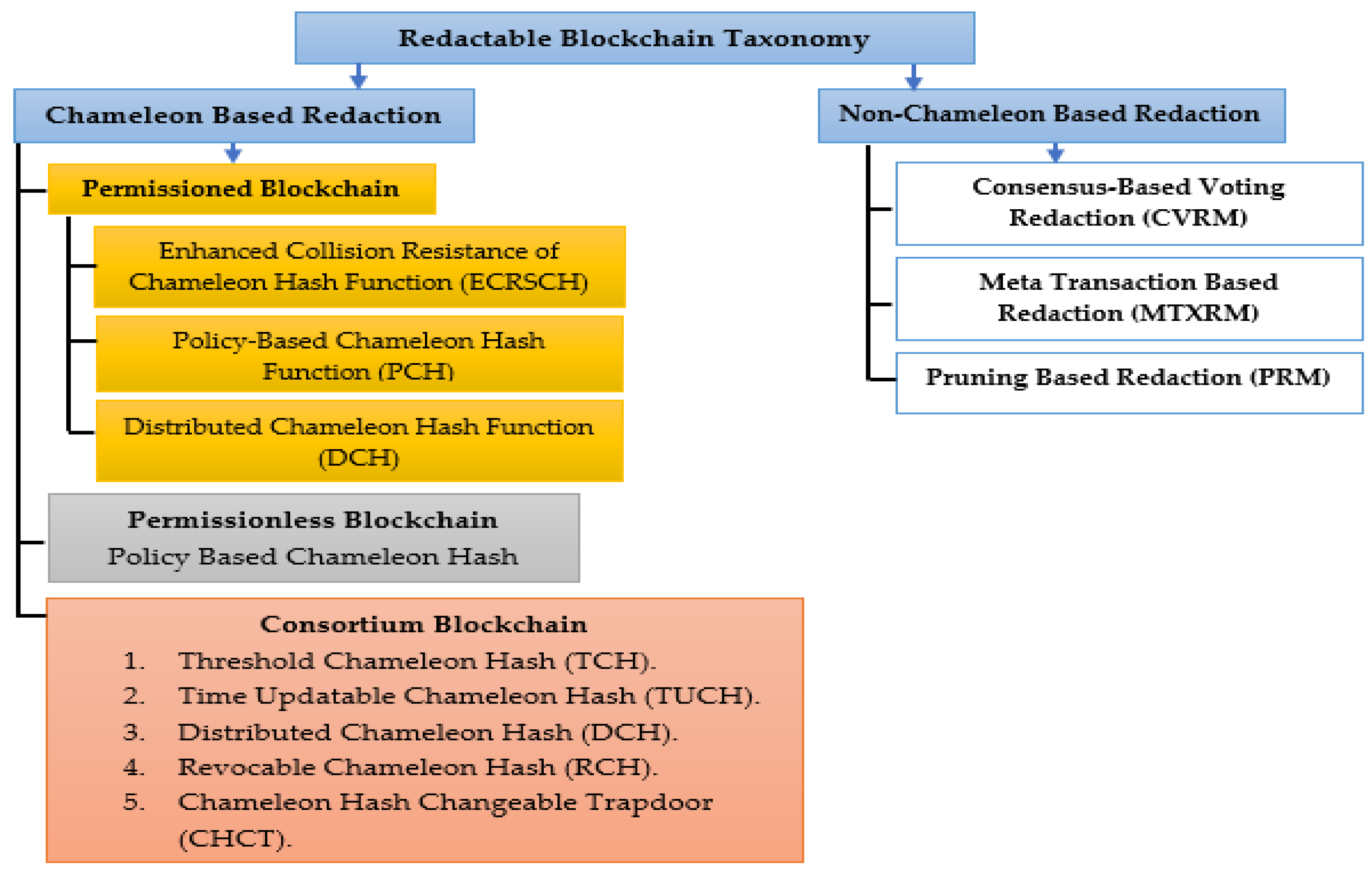
7. Redaction Mechanisms in Blockchain
7.1. Redactable Blockchain-Based Chameleon
7.1.1. Redactable Permissioned Blockchain
- Enhanced Collision-Resistance of Chameleon Hash Function (ECRSCH)
- Policy-based Chameleon Hash Function (PCH)
- Distributed Chameleon Hash
7.1.2. Redactable Permissionless Blockchain
7.1.3. Redactable Consortium Blockchain
7.2. Non-Chameleon Hash-Based Redactable Blockchain
7.2.1. Consensus-Based Voting Redaction Approach (CVRA)
7.2.2. Meta-Transaction-Based Redaction Approach
7.2.3. Pruning-Based Redaction Approach (PRA)
8. Comparisons and Discussion
9. Open Challenges and Future Research Direction
- ▪
- Permissionless settings. Permissioned and consortium blockchain concepts have adopted most of the proposed solutions where permissionless settings remain a challenge due to their openness and unrestricted characteristics and, hence, it is still unclear how to solve chameleon-based redaction in public blockchain. However, there are several suggestions for a non-chameleon method which proved to be inefficient due to time overhead. Non-chameleon is out of the scope of this research.
- ▪
- Redaction exceptional circumstances. Redaction in total is a delicate case due to violating major blockchain immutability features. The balance requires special supplements, and careful procedures in order to succeed in redaction without any contradiction.
- ▪
- Revocation scalability consequences. Centralization revoking mechanisms lack efficiency and effectiveness. Consequently, it overwhelmingly poses cost, time, communication overhead and even other equipment that might be required.
- ▪
- Trapdoor key exposure. The trapdoor key is the main weakness of the chameleon hashing function; meanwhile, the entire collision being indistinguishable relies on its secrecy.
- ▪
- Revocation centralization authorities. Studies in the current domain have employed central authorities to perform redaction; however, centralization is considered a drawback and decentralization is highly recommended.
- ▪
- Punishment methodologies. Punishment has been replaced by accountability where violators remain safe without any further actions taken against them.
- ▪
- IOT-based redaction in blockchain performance. Scalability is an ineffective factor due to a lack of blockchain redaction in the IoT domain wherein performance criteria are still low due to edge device limitations not being considered. According to authentic requirements, blockchain-based IOT/IIOT designs cannot provide networking resources. Current designs mainly suffer from a dispute among network resources, security, and redaction.
- ▪
- The balance between accountability and anonymity. Privacy is a legal right to preserve identity concealment. Proposals mainly prioritize accountability over personal privacy. However, GDPR legislation strictly states that hidden identities must be maintained which is acutely confronted by the recent redaction mechanisms concepts.
- ▪
- Rewriting flexibility limiting. Absolute power offered to the rewriting modifiers sabotaged data integrity and confined rewriting abilities to themselves.
- ▪
- Redactor granting privileges agreement. The cooperation between owners and modifiers demands prearranged agreements.
- ▪
- Collusion resistance: Colluding must be prevented due to illegal privilege accumulation among different colluded, revoked users who are willing to either access authentic data or try to falsely redact data.
- ▪
- Consistency preservation: Redacted chain stability remains a major obstacle in designing any redaction mechanism. Removal operation performed after storing transaction/block state prior redaction in the current proposal’s methods is as yet vulnerable due to verifications and transaction chain failure.
10. Conclusions
Author Contributions
Funding
Informed Consent Statement
Acknowledgments
Conflicts of Interest
Appendix A
| Abbreviation | Description |
|---|---|
| CH | Chameleon Hash Function |
| PKE | Public Key Encryption |
| ABE | Attribute Base Encryption |
| TCH | Threshold Chameleon Hash |
| DS | Digital Signature |
| ZR | Zero Knowledge Proof |
| TTCH | Threshold Trapdoor Chameleon Hash |
| MA_ABE | Multi Authority Attribute Base Encryption |
| TEE | Trusted Execution Environment |
| DGS | Digital Group Signature |
| TUCH | Time Update Chameleon Hash |
| CHCT | Chameleon Hash Changeable Trapdoor |
| MTRA | Meta Transaction Base Redactable Approach |
| CVRA | Consensus Voting Base Redaction Approach |
| PRA | Pruning Base redaction Approach |
| P | Permissioned Blockchain (Privat Blockchain) |
| PL | Permissionless Blockchain (Public Blockchain) |
| CP | Consortium Blockchain |
| BL | Block Level |
| TL | Transaction Level |
| TFL | Transaction Field Level |
| DLP | Discrete Logarithm Problem |
| CDHP | Computational Diffie Hillman Problem |
| SXDH | Standard Symmetric External Diffie Hillman |
| SIS | Small Integer Solution |
| DLIN | Decision Linear Assumption |
| DPDH | Decisional Bilinear Diffie Hillman |
References
- Ma, Z.; Jiang, M.; Gao, H.; Wang, Z. Blockchain for Digital Rights Management. Future Gener. Comput. Syst. 2018, 89, 746–764. [Google Scholar] [CrossRef]
- Aitzhan, N.Z.; Svetinovic, D. Security and Privacy in Decentralized Energy Trading Through Multi-Signatures, Blockchain and Anonymous Messaging Streams. IEEE Trans. Dependable Secur. Comput. 2018, 15, 840–852. [Google Scholar] [CrossRef]
- Khan, K.M.; Arshad, J.; Khan, M.M. Investigating Performance Constraints for Blockchain Based Secure E-Voting System. Future Gener. Comput. Syst. 2020, 105, 13–26. [Google Scholar] [CrossRef]
- Khan, N.; Aljoaey, H.; Tabassum, M.; Farzamnia, A.; Sharma, T.; Tung, Y.H. Proposed Model for Secured Data Storage in Decentralized Cloud by Blockchain Ethereum. Electronics 2022, 11, 3686. [Google Scholar] [CrossRef]
- Wang, B.; Li, Z. Healthchain: A Privacy Protection System for Medical Data Based on Blockchain. Future Internet 2021, 13, 247. [Google Scholar] [CrossRef]
- Yiu, N.C.K. Toward Blockchain-Enabled Supply Chain Anti-Counterfeiting and Traceability. Future Internet 2021, 13, 86. [Google Scholar] [CrossRef]
- Abidi, M.H.; Alkhalefah, H.; Umer, U.; Mohammed, M.K. Blockchain-Based Secure Information Sharing for Supply Chain Management: Optimization Assisted Data Sanitization Process. Int. J. Intell. Syst. 2021, 36, 260–290. [Google Scholar] [CrossRef]
- Kapassa, E.; Themistocleous, M.; Christodoulou, K.; Iosif, E. Blockchain Application in Internet of Vehicles: Challenges, Contributions and Current Limitations. Future Internet 2021, 13, 313. [Google Scholar] [CrossRef]
- Petroc Taylor. Worldwide Spending on Blockchain Solutions from 2017 to 2024. Available online: https://www.statista.com/statistics/800426/w.orldwide-blockchain-solutions-spending (accessed on 23 May 2022).
- Hyla, T.; Pejaś, J. EHealth Integrity Model Based on Permissioned Blockchain. Future Internet 2019, 11, 76. [Google Scholar] [CrossRef]
- Sanka, A.I.; Irfan, M.; Huang, I.; Cheung, R.C.C. A Survey of Breakthrough in Blockchain Technology: Adoptions, Applications, Challenges and Future Research. Comput. Commun. 2021, 169, 179–201. [Google Scholar] [CrossRef]
- Narayanan, A.; Bonneau, J.; Felten, E.; Miller, A.; Goldfeder, S.; Clark, J. Bitcoin and Cryptocurrency Technologies: A Comprehensive Introduction; Princeton University Press: Princeton, NJ, USA, 2016; ISBN 978-0-691-17169-2. [Google Scholar]
- Voulgaris, S.; Fotiou, N.; Siris, V.A.; Polyzos, G.C.; Jaatinen, M.; Oikonomidis, Y. Blockchain Technology for Intelligent Environments. Future Internet 2019, 11, 213. [Google Scholar] [CrossRef]
- Przytarski, D.; Stach, C.; Gritti, C.; Mitschang, B. Query Processing in Blockchain Systems: Current State and Future Challenges. Future Internet 2022, 14, 1. [Google Scholar] [CrossRef]
- Al-Abdullah, M.; Alsmadi, I.; AlAbdullah, R.; Farkas, B. Designing Privacy-Friendly Data Repositories: A Framework for a Blockchain That Follows the GDPR. Digit. Policy Regul. Gov. 2020, 22, 389–411. [Google Scholar] [CrossRef]
- Zhang, D.; Le, J.; Mu, N.; Liao, X. An Anonymous Off-Blockchain Micropayments Scheme for Cryptocurrencies in the Real World. IEEE Trans. Syst. Man Cybern. Syst. 2020, 50, 32–42. [Google Scholar] [CrossRef]
- Zheng, X.; Zhu, Y.; Si, X. A Survey on Challenges and Progresses in Blockchain Technologies: A Performance and Security Perspective. Appl. Sci. 2019, 9, 4731. [Google Scholar] [CrossRef]
- El Ioini, N.; Pahl, C. A Review of Distributed Ledger Technologies. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Valletta, Malta, 22–26 October 2018; Volume 11230. [Google Scholar]
- Casino, F.; Politou, E.; Alepis, E.; Patsakis, C. Immutability and Decentralized Storage: An Analysis of Emerging Threats. IEEE Access 2020, 8, 4737–4744. [Google Scholar] [CrossRef]
- Matzutt, R.; Hiller, J.; Henze, M.; Ziegeldorf, J.H.; Müllmann, D.; Hohlfeld, O.; Wehrle, K. A Quantitative Analysis of the Impact of Arbitrary Blockchain Content on Bitcoin. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Nieuwpoort, The Netherlands, 26 February–2 March 2018; Volume 10957. [Google Scholar]
- Jordan Pearson The Bitcoin Blockchain Could Be Used to Spread Malware, INTERPOL Says: (27 March 2015). Available online: https://www.vice.com/en/article/ezv8jn/the-bitcoin-blockchain-could-be-used-to-spread-malware-interpol-says (accessed on 23 May 2022).
- Tziakouris, G. Cryptocurrencies—A Forensic Challenge or Opportunity for Law Enforcement? An INTERPOL Perspective. IEEE Secur. Priv. 2018, 16, 92–94. [Google Scholar] [CrossRef]
- Schellinger, B.; Völter, F.; Urbach, N.; Sedlmeir, J. Yes, I Do: Marrying Blockchain Applications with GDPR. In Proceedings of the 55th Hawaii International Conference on System Sciences, Maui, HI, USA, 4–7 January 2022. [Google Scholar]
- Bai, P.; Kumar, S.; Kumar, K.; Kaiwartya, O.; Mahmud, M.; Lloret, J. GDPR Compliant Data Storage and Sharing in Smart Healthcare System: A Blockchain-Based Solution. Electronics 2022, 11, 3311. [Google Scholar] [CrossRef]
- Campanile, L.; Iacono, M.; Marulli, F.; Mastroianni, M. Designing a GDPR Compliant Blockchain-Based IoV Distributed Information Tracking System. Inf. Process. Manag. 2021, 58, 102511. [Google Scholar] [CrossRef]
- Bigini, G.; Freschi, V.; Lattanzi, E. A Review on Blockchain for the Internet of Medical Things: Definitions, Challenges, Applications, and Vision. Future Internet 2020, 12, 208. [Google Scholar] [CrossRef]
- Gatteschi, V.; Lamberti, F.; Demartini, C.; Pranteda, C.; Santamaría, V. Blockchain and Smart Contracts for Insurance: Is the Technology Mature Enough? Future Internet 2018, 10, 20. [Google Scholar] [CrossRef]
- Zheng, J.; Dike, C.; Pancari, S.; Wang, Y.; Giakos, G.C.; Elmannai, W.; Wei, B. An In-Depth Review on Blockchain Simulators for IoT Environments. Future Internet 2022, 14, 182. [Google Scholar] [CrossRef]
- Politou, E.; Alepis, E.; Patsakis, C. Forgetting Personal Data and Revoking Consent under the GDPR: Challenges and Proposed Solutions. J. Cybersecur. 2018, 4, tyy001. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System, October 2008. Cited 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 23 May 2022).
- Swan, M. Blockchain: Blueprint for a New Economy; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2015. [Google Scholar]
- Koblitz, N.; Menezes, A.J. Cryptocash, Cryptocurrencies, and Cryptocontracts. Des. Codes Cryptogr. 2016, 78, 87–102. [Google Scholar] [CrossRef]
- Workie, H. Distributed Ledger Technology: Implications of Blockchain for the Securities Industry. J. Secur. Oper. Custody 2017, 9, 347–355. [Google Scholar]
- Chaudhary, K.; Fehnker, A.; Van De Pol, J.; Stoelinga, M. Modeling and Verification of the Bitcoin Protocol. In Proceedings of the Electronic Proceedings in Theoretical Computer Science, EPTCS, Suva, Fiji, 23 November 2015; Volume 196. [Google Scholar]
- Tschorsch, F.; Scheuermann, B. Bitcoin and beyond: A Technical Survey on Decentralized Digital Currencies. IEEE Commun. Surv. Tutor. 2016, 18, 2084–2123. [Google Scholar] [CrossRef]
- Christodoulou, K.; Iosif, E.; Inglezakis, A.; Themistocleous, M. Consensus Crash Testing: Exploring Ripple’s Decentralization Degree in Adversarial Environments. Future Internet 2020, 12, 53. [Google Scholar] [CrossRef]
- Chen, Y.; Guo, J.; Li, C.; Ren, W. FaDe: A Blockchain-Based Fair Data Exchange Scheme for Big Data Sharing. Future Internet 2019, 11, 225. [Google Scholar] [CrossRef]
- Conte de Leon, D.; Stalick, A.Q.; Jillepalli, A.A.; Haney, M.A.; Sheldon, F.T. Blockchain: Properties and Misconceptions. Asia Pac. J. Innov. Entrep. 2017, 11, 286–300. [Google Scholar] [CrossRef]
- Khanal, Y.P.; Alsadoon, A.; Shahzad, K.; Al-Khalil, A.B.; Prasad, P.W.C.; Rehman, S.U.; Islam, R. Utilizing Blockchain for IoT Privacy through Enhanced ECIES with Secure Hash Function. Future Internet 2022, 14, 77. [Google Scholar] [CrossRef]
- Buccafurri, F.; De Angelis, V.; Lazzaro, S. A Blockchain-Based Framework to Enhance Anonymous Services with Accountability Guarantees. Future Internet 2022, 14, 243. [Google Scholar] [CrossRef]
- Chen, Y.-C.; Chou, Y.-P.; Chou, Y.-C. An Image Authentication Scheme Using Merkle Tree Mechanisms. Future Internet 2019, 11, 149. [Google Scholar] [CrossRef]
- Feng, H.; Wang, J.; Li, Y. An Efficient Blockchain Transaction Retrieval System. Future Internet 2022, 14, 267. [Google Scholar] [CrossRef]
- Eyal, I.; Gencer, A.E.; Sirer, E.G.; Van Renesse, R. Bitcoin-NG: A Scalable Blockchain Protocol. In Proceedings of the 13th USENIX Symposium on Networked Systems Design and Implementation, NSDI 2016, Santa Clara, CA, USA, 16–18 March 2016. [Google Scholar]
- Qu, Q.; Xu, R.; Chen, Y.; Blasch, E.; Aved, A. Enable Fair Proof-of-Work (PoW) Consensus for Blockchains in IoT by Miner Twins (MinT). Future Internet 2021, 13, 291. [Google Scholar] [CrossRef]
- Bentov, I.; Gabizon, A.; Mizrahi, A. Cryptocurrencies without Proof of Work. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Christ Church, Barbados, 26 February 2016; Volume 9604. [Google Scholar]
- Gazi, P.; Kiayias, A.; Zindros, D. Proof-of-Stake Sidechains. In Proceedings of the IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 19–23 May 2019; Volume 2019. [Google Scholar]
- Bentov, I.; Lee, C.; Mizrahi, A.; Rosenfeld, M. Proof of Activity: Extending Bitcoin’s Proof of Work via Proof of Stake. Cryptol. Eprint Arch. 2014, 452, 34–37. [Google Scholar]
- Duan, S.; Reiter, M.K.; Zhang, H. BEAT: Asynchronous BFT Made Practical. In Proceedings of the ACM Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018. [Google Scholar]
- Xiao, Y.; Zhang, N.; Lou, W.; Hou, Y.T. A Survey of Distributed Consensus Protocols for Blockchain Networks. IEEE Commun. Surv. Tutor. 2020, 22, 1432–1465. [Google Scholar] [CrossRef]
- Antonopoulo, A.M. Mastering Bitcoin Unlocking Digital Cryptocurrencies; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2014; Volume 9. [Google Scholar]
- Habib, G.; Sharma, S.; Ibrahim, S.; Ahmad, I.; Qureshi, S.; Ishfaq, M. Blockchain Technology: Benefits, Challenges, Applications, and Integration of Blockchain Technology with Cloud Computing. Future Internet 2022, 14, 341. [Google Scholar] [CrossRef]
- Makridakis, S.; Christodoulou, K. Blockchain: Current Challenges and Future Prospects/Applications. Future Internet 2019, 11, 258. [Google Scholar] [CrossRef]
- Gong, Y.; van Engelenburg, S.; Janssen, M. A Reference Architecture for Blockchain-Based Crowdsourcing Platforms. J. Theor. Appl. Electron. Commer. Res. 2021, 16, 937–958. [Google Scholar] [CrossRef]
- Yu, H.; Yang, Z.; Sinnott, R.O. Decentralized Big Data Auditing for Smart City Environments Leveraging Blockchain Technology. IEEE Access 2019, 7, 6288–6296. [Google Scholar] [CrossRef]
- Cai, W.; Wang, Z.; Ernst, J.B.; Hong, Z.; Feng, C.; Leung, V.C.M. Decentralized Applications: The Blockchain-Empowered Software System. IEEE Access 2018, 6, 53019–53033. [Google Scholar] [CrossRef]
- Xie, J.; Tang, H.; Huang, T.; Yu, F.R.; Xie, R.; Liu, J.; Liu, Y. A Survey of Blockchain Technology Applied to Smart Cities: Research Issues and Challenges. IEEE Commun. Surv. Tutor. 2019, 21, 2794–2830. [Google Scholar] [CrossRef]
- Bodziony, N.; Jemioło, P.; Kluza, K.; Ogiela, M.R. Blockchain-Based Address Alias System. J. Theor. Appl. Electron. Commer. Res. 2021, 16, 1280–1296. [Google Scholar] [CrossRef]
- Garay, J.; Kiayias, A.; Leonardos, N. The Bitcoin Backbone Protocol: Analysis and Applications. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Sofia, Bulgaria, 26–30 April 2015; Volume 9057. [Google Scholar]
- Kiayias, A.; Russell, A.; David, B.; Oliynykov, R. Ouroboros: A Provably Secure Proof-of-Stake Blockchain Protocol. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Santa Barbara, CA, USA, 20–24 August 2017; Volume 10401. [Google Scholar]
- Krawczyk, H.; Rabin, T. Chameleon Hashing and Signatures. IACR Cryptol. Eprint Arch. 1998, 1998. Available online: https://eprint.iacr.org/1998/010 (accessed on 23 May 2022).
- Ateniese, G.; Magri, B.; Venturi, D.; Andrade, E.R. Redactable Blockchain—Or—Rewriting History in Bitcoin and Friends. In Proceedings of the 2nd IEEE European Symposium on Security and Privacy, EuroS and P 2017, Paris, France, 26–28 April 2017. [Google Scholar]
- Khalili, M.; Dakhilalian, M.; Susilo, W. Efficient Chameleon Hash Functions in the Enhanced Collision Resistant Model. Inf. Sci. 2020, 510, 155–164. [Google Scholar] [CrossRef]
- Derler, D.; Samelin, K.; Slamanig, D. Bringing Order to Chaos: The Case of Collision-Resistant Chameleon-Hashes. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Edinburgh, UK, 4–7 May 2020; Volume 12110. [Google Scholar]
- Derler, D.; Samelin, K.; Slamanig, D.; Striecks, C. Fine-Grained and Controlled Rewriting in Blockchains: Chameleon-Hashing Gone Attribute-Based. IACR Crypto ePrint Archive. 2019. 406p. Available online: https://eprint.iacr.org/2019/406 (accessed on 23 May 2022).
- Tian, Y.; Li, N.; Li, Y.; Szalachowski, P.; Zhou, J. Policy-Based Chameleon Hash for Blockchain Rewriting with Black-Box Accountability. In Proceedings of the ACM International Conference Proceeding Series, Austin, TX, USA, 7–11 December 2020. [Google Scholar]
- Xu, S.; Ning, J.; Ma, J.; Huang, X.; Deng, R.H. K-Time Modifiable and Epoch-Based Redactable Blockchain. IEEE Trans. Inf. Forensics Secur. 2021, 16, 4507–4520. [Google Scholar] [CrossRef]
- Chen, X.; Gao, Y. CDEdit: A Highly Applicable Redactable Blockchain with Controllable Editing Privilege and Diversified Editing Types. arXiv 2022, arXiv:2205.07054. [Google Scholar]
- Panwar, G.; Vishwanathan, R.; Misra, S. ReTRACe: Revocable and Traceable Blockchain Rewrites Using Attribute-Based Cryptosystems. In Proceedings of the ACM Symposium on Access Control Models and Technologies, SACMAT, Virtual, 16–18 June 2021. [Google Scholar]
- Jia, Y.; Sun, S.F.; Zhang, Y.; Liu, Z.; Gu, D. Redactable Blockchain Supporting Supervision and Self-Management. In Proceedings of the ASIA CCS 2021—Proceedings of the 2021 ACM Asia Conference on Computer and Communications Security, Hong Kong, China, 7–11 June 2021. [Google Scholar]
- Xu, S.; Ning, J.; Ma, J.; Xu, G.; Yuan, J.; Deng, R.H. Revocable Policy-Based Chameleon Hash. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Darmstadt, Germany, 4–8 October 2021; Volume 12972. [Google Scholar]
- Zhang, Z.; Li, T.; Wang, Z.; Liu, J. Redactable Transactions in Consortium Blockchain: Controlled by Multi-Authority CP-ABE. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Virtual Event, 1–3 December 2021; Volume 13083. [Google Scholar]
- Ma, J.; Xu, S.; Ning, J.; Huang, X.; Deng, R.H. Redactable Blockchain in Decentralized Setting. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1227–1242. [Google Scholar] [CrossRef]
- Guo, L.; Wang, Q.; Yau, W.C. Online/Offline Rewritable Blockchain with Auditable Outsourced Computation. IEEE Trans. Cloud Comput. 2021, 14, 1–16. [Google Scholar] [CrossRef]
- Hou, H.; Hao, S.; Yuan, J.; Xu, S.; Zhao, Y. Fine-Grained and Controllably Redactable Blockchain with Harmful Data Forced Removal. Secur. Commun. Netw. 2021, 2021, 3680359. [Google Scholar] [CrossRef]
- Liu, L.; Tan, L.; Liu, J.; Xiao, J.; Yin, H.; Tan, S. Redactable Blockchain Technology Based on Distributed Key Management and Trusted Execution Environment. In Proceedings of the Communications in Computer and Information Science, Guangzhou, China, 5–6 August 2021; Volume 1490. [Google Scholar]
- Wu, C.; Ke, L.; Du, Y. Quantum Resistant Key-Exposure Free Chameleon Hash and Applications in Redactable Blockchain. Inf. Sci. 2021, 548, 438–449. [Google Scholar] [CrossRef]
- Matzutt, R.; Ahlrichs, V.; Pennekamp, J.; Karwacik, R.; Wehrle, K. A Moderation Framework for the Swift and Transparent Removal of Illicit Blockchain Content. In Proceedings of the IEEE International Conference on Blockchain and Cryptocurrency, ICBC 2022, Shanghai, China, 2–5 May 2022; Institute of Electrical and Electronics Engineers Inc.: New York, NY, USA, 2022. [Google Scholar]
- Tian, Y.; Liu, B.; Li, Y.; Szalachowski, P.; Zhou, J. Accountable Fine-Grained Blockchain Rewriting in the Permissionless Setting. arXiv 2021, arXiv:2104.13543. [Google Scholar]
- Huang, K.; Zhang, X.; Mu, Y.; Wang, X.; Yang, G.; Du, X.; Rezaeibagha, F.; Xia, Q.; Guizani, M. Building Redactable Consortium Blockchain for Industrial Internet-of-Things. IEEE Trans. Ind. Inform. 2019, 15, 3670–3679. [Google Scholar] [CrossRef]
- Huang, K.; Zhang, X.; Mu, Y.; Rezaeibagha, F.; Du, X.; Guizani, N. Achieving Intelligent Trust-Layer for Internet-of-Things via Self-Redactable Blockchain. IEEE Trans. Ind. Inform. 2020, 16, 2677–2686. [Google Scholar] [CrossRef]
- Zhang, J.; Lu, Y.; Liu, Y.; Yang, X.; Qi, Y.; Dong, X.; Wang, H. Serving at the Edge: A Redactable Blockchain with Fixed Storage. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Guangzhou, China, 23–25 September 2020; Volume 12432. [Google Scholar]
- Lv, W.; Wei, S.; Li, S.; Yu, M. Verifiable Blockchain Redacting Method for a Trusted Consortium with Distributed Chameleon Hash Authority. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Dallas, TX, USA, 11–13 December 2020; Volume 12575. [Google Scholar]
- Huang, K.; Zhang, X.; Mu, Y.; Rezaeibagha, F.; Du, X. Scalable and Redactable Blockchain with Update and Anonymity. Inf. Sci. 2021, 546, 25–41. [Google Scholar] [CrossRef]
- Gao, W.; Chen, L.; Rong, C.; Liang, K.; Zheng, X.; Yu, J. Security Analysis and Improvement of a Redactable Consortium Blockchain for Industrial Internet-of-Things. Comput. J. 2022, 65, 2430–2438. [Google Scholar] [CrossRef]
- Zhang, C.; Ni, Z.; Xu, Y.; Luo, E.; Chen, L.; Zhang, Y. A Trustworthy Industrial Data Management Scheme Based on Redactable Blockchain. J. Parallel Distrib. Comput. 2021, 152, 167–176. [Google Scholar] [CrossRef]
- Wei, J.; Zhu, Q.; Li, Q.; Nie, L.; Shen, Z.; Choo, K.K.R.; Yu, K. A Redactable Blockchain Framework for Secure Federated Learning in Industrial Internet of Things. IEEE Internet Things J. 2022, 9, 17901–17911. [Google Scholar] [CrossRef]
- Camenisch, J.; Derler, D.; Krenn, S.; Pöhls, H.C.; Samelin, K.; Slamanig, D. Chameleon-Hashes with Ephemeral Trapdoors and Applications to Invisible Sanitizable Signatures. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Amsterdam, The Netherlands, 28–31 March 2017; Volume 10175. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data. In Proceedings of the ACM Conference on Computer and Communications Security, Taipei, Taiwan, 21–24 March 2006. [Google Scholar]
- Rivest, R.L.; Shamir, A.; Adleman, L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Boldyreva, A.; Goyal, V.; Kumart, V. Identity-Based Encryption with Efficient Revocation. In Proceedings of the ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 27–31 October 2008. [Google Scholar]
- Agrawal, S.; Chase, M. FAME: Fast Attribute-Based Message Encryption. In Proceedings of the ACM Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017. [Google Scholar]
- Liu, J.K.; Wei, V.K.; Wong, D.S. Linkable Spontaneous Anonymous Group Signature for Ad Hoc Groups (Extended Abstract). Lect. Notes Comput. Sci. (Incl. Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinform.) 2004, 3108, 325–335. [Google Scholar] [CrossRef]
- Sabt, M.; Achemlal, M.; Bouabdallah, A. Trusted Execution Environment: What It Is, and What It Is Not. In Proceedings of the 14th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, TrustCom 2015, Helsinki, Finland, 20–22 August 2015; Volume 1. [Google Scholar]
- Ateniese, G.; Chou, D.H.; Medeiros, B.D.; Tsudik, G. Sanitizable Signatures. In Proceedings of the n European Symposium on Research in Computer Security, Milan, Italy, 12–14 September 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 159–177. [Google Scholar]
- Deuber, D.; Magri, B.; Thyagarajan, S.A.K. Redactable Blockchain in the Permissionless Setting. In Proceedings of the Proceedings—IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 19–23 May 2019. [Google Scholar]
- Thyagarajan, S.A.K.; Bhat, A.; Magri, B.; Tschudi, D.; Kate, A. Reparo: Publicly Verifiable Layer to Repair Blockchains. In Proceedings of the Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics), Virtual Event, 1–5 March 2021; Volume 12675. [Google Scholar]
- Puddu, I.; Zurich, E.; Dmitrienko, A.; Capkun, S. Μchain: How to Forget without Hard Forks. arXiv 2017. Available online: https://eprint.iacr.org/2017/106.pdf (accessed on 23 May 2022).
- Dorri, A.; Kanhere, S.S.; Jurdak, R. MOF-BC: A Memory Optimized and Flexible Blockchain for Large Scale Networks. Future Gener. Comput. Syst. 2019, 92, 357–373. [Google Scholar] [CrossRef]
- Florian, M.; Henningsen, S.; Beaucamp, S.; Scheuermann, B. Erasing Data from Blockchain Nodes. In Proceedings of the 4th IEEE European Symposium on Security and Privacy Workshops, EUROS and PW 2019, Stockholm, Sweden, 17–19 June 2019. [Google Scholar]
- Matzutt, R.; Kalde, B.; Pennekamp, J.; Drichel, A.; Henze, M.; Wehrle, K. How to Securely Prune Bitcoin’s Blockchain. In Proceedings of the IFIP Networking 2020 Conference and Workshops, Networking 2020, Paris, France, 22–26 June 2020. [Google Scholar]
- Yiu, N.C.K. An Overview of Forks and Coordination in Blockchain Development. arXiv 2021, arXiv:2102.10006. [Google Scholar]
- Webb, N. A Fork in the Blockchain: Income Tax and the Bitcoin/Bitcoin Cash Hard Fork. North Carol. J. Law Technol. 2018, 19, 283. [Google Scholar]
- Marsalek, A.; Zefferer, T. A Correctable Public Blockchain. In Proceedings of the 2019 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/13th IEEE International Conference on Big Data Science and Engineering, TrustCom/BigDataSE 2019, Rotorua, New Zealand, 5–8 August 2019. [Google Scholar]
- Ostrovsky, R.; Yung, M. How to Withstand Mobile Virus Attacks (Extended Abstract). In Proceedings of the Tenth Annual ACM Symposium on Principles of Distributed Computing—PODC ’91, Montreal, QC, Canada, 19–21 August 1991. [Google Scholar]
- Pyoung, C.K.; Baek, S.J. Blockchain of Finite-Lifetime Blocks with Applications to Edge-Based IoT. IEEE Internet Things J. 2020, 7, 2102–2116. [Google Scholar] [CrossRef]
- Xu, X.; Zhu, D.; Yang, X.; Wang, S.; Qi, L.; Dou, W. Concurrent Practical Byzantine Fault Tolerance for Integration of Blockchain and Supply Chain. ACM Trans. Internet Technol. 2021, 21, 1–17. [Google Scholar] [CrossRef]
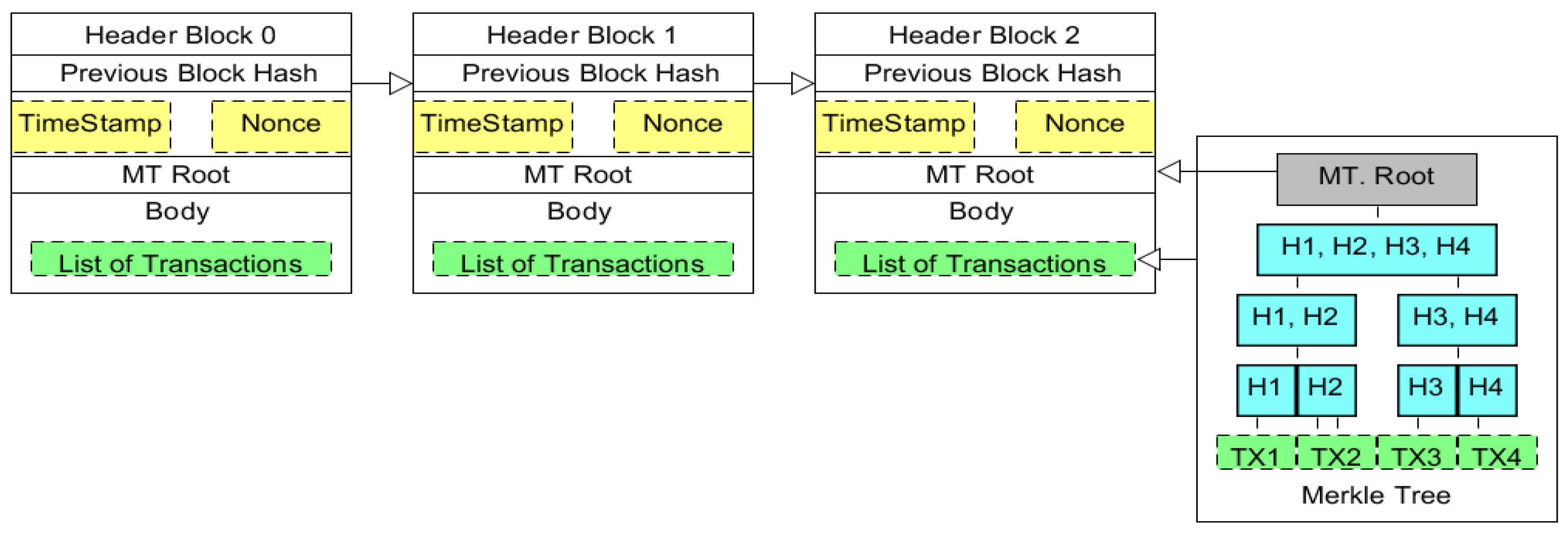
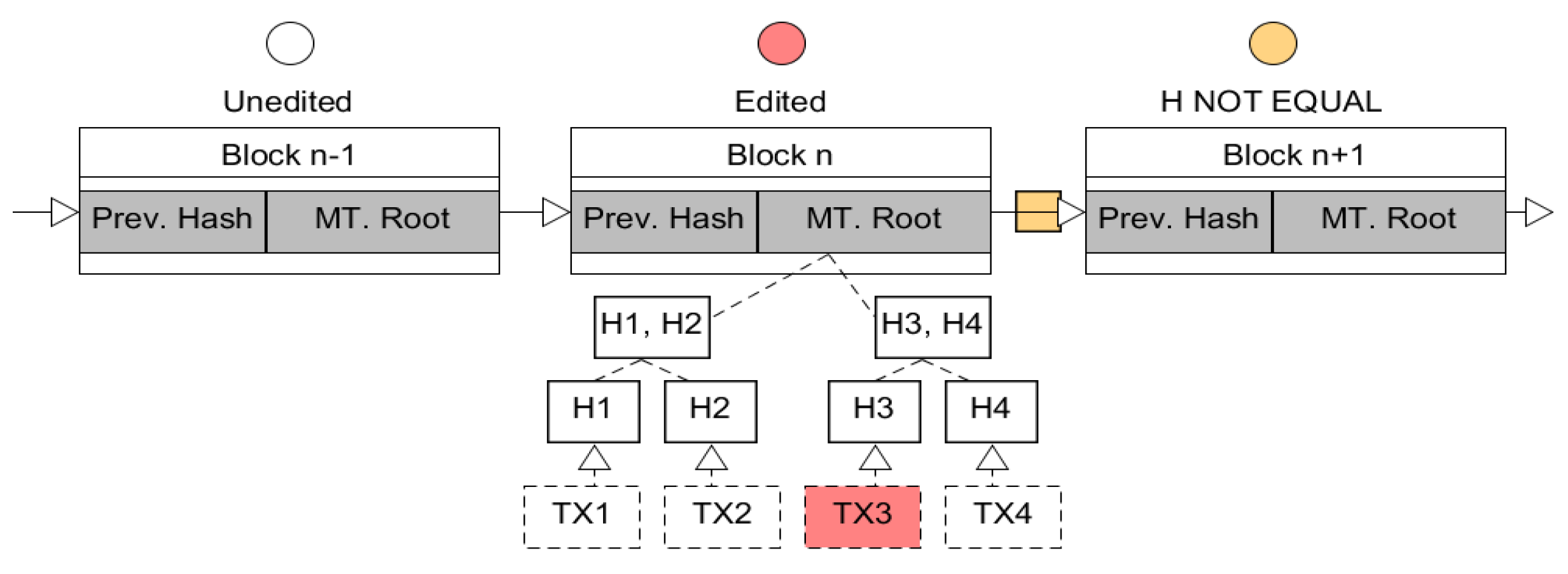


| Type | Public (Permissionless) | Private (Permissioned) | Consortium |
|---|---|---|---|
| Network | Decentralized | Decentralized Partially | Hybrid Among Public and Private |
| Access | Any participant | Predefined Participant | Multiple Predefined Participants |
| Concept |
|
|
|
| Consensus | PoW/PoS | Multi party | Multi party |
| Approval Time | 10 Minutes | 100 ms | 100 ms |
| Scalability | Slow | Fast, Light | Fast, Light |
| Security, Privacy | Lack of privacy and anonymity. | High Privacy | High Privacy |
| Cost | Costive. | Costive. | Costive. |
| Energy | High Consumption | Low Consumption | Low Consumption |
| Efficiency | Non-Efficient | Efficient | Efficient |
| Immutability | Non-tempered | Can Be Tampered | Can Be Tampered |
| Centralization | No | Yes | Partially |
| Use Cases | Cryptocurrency | Supply Chain | Banking, Insurance |
| Application | Bitcoin | Ethereum | Edexa |
| Schema | Methods | Security Assumption | Setting (Blockchain Type) | Redaction Type |
|---|---|---|---|---|
| [61], (2017) | CH and PKE | DLP | Private | BL |
| [62], (2020) | CH and ZR | SXDH | Private | BL |
| [63], (2020) | CH and ZR | SXDH | Private | BL |
| [64], (2019) | CH and ABE | DLP | Private | TL |
| [65], (2020) | CH and ABE and DS | DLP | Private | TL |
| [66], (2021) | CH and DS | DDH | Private | TL |
| [67], (2022) | CH and ABE and DS | DLP | Private | TL\BL |
| [68], (2021) | CH and MA-ABE and DGS | DLIN | Private | TL |
| [69], (2021) | CH | DLP | Private\Public | TFL |
| [70], (2021) | CH and ABE and DS | DLIN | Private | TL |
| [71], (2021) | CH and MA_ABE | DLP | Private | TL |
| [72], (2022) | CH and ABE and DS | DLP | Private | TL |
| [73], (2021) | CH and ABE | DBDH | Private | TL |
| [74], (2021) | CH and ABE and DS | DLP | Private | TL |
| [75], (2021) | CH and TEE | DLP | Private | BL |
| [76], (2021) | CH and Lattice | SIS | Private | BL |
| [77], (2022) | CH | DLP | Private\Public | TL |
| [78], (2021) | CH and MA_ABE and DS | DLP | Public | TL |
| [79], (2019) | TCH and DS | CDHP | Consortium | TL |
| [80], (2019) | RCH | CDHP | Consortium | TL |
| [81], (2020) | TTCH | CDHP | Consortium | TL |
| [82], (2020) | CH | DLP | Consortium | TL |
| [83], (2021) | TCH and DS | CDHP | Consortium | TL |
| [84], (2021) | TCH and DS | CDHP | Consortium | TL |
| [85], (2021) | CH | DLP | Consortium | TL |
| [86], (2022) | CH | CDHP | Consortium | TL |
| Schema | Methods | Security Assumption | Setting (Blockchain Type) | Redaction Type |
|---|---|---|---|---|
| [95], (2019) | CVRA | N/A | Public | TL |
| [96], (2020) | CVRA | N/A | Private/Public | TL |
| [97], (2017) | MTRA | N/A | Private/Public | TL |
| [98], (2020) | MTRA | N/A | Private | TL |
| [99], (2019) | PRA | N/A | Public | BL |
| [100], (2020) | PRA | N/A | Public | BL |
| Schema (Year) | Security Properties | Challenges | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Chain Growth | Chain Quality | Common Prefix | Validity | Block Consistency | Transaction Consistency | Scalability | Additional POW | Compatibility | Fined Grained | Secret Sharing | Accountably | Anonymity | Decentralization | Revocation | Anti-Collusion | Efficiency (High (H)/Medium (M), Poor (P)) | |
| [61], (2017) | √ | √ | √ | H | |||||||||||||
| [62], (2020) | √ | √ | √ | √ | H | ||||||||||||
| [63], (2020) | √ | √ | √ | √ | H | ||||||||||||
| [64], (2019) | √ | √ | √ | √ | √ | √ | √ | √ | H | ||||||||
| [65], (2020) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | H | |||||
| [66], (2021) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | M | |||||
| [67], (2022) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | H | |||
| [68], (2021) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | M | |||
| [69], (2021) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | M | ||||
| [70], (2021) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | H | ||||
| [71], (2021) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | H | |||||
| [72], (2022) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | H | ||||
| [73], (2021) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | H | ||||||
| [74], (2021) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | H | |||||
| [75], (2021) | √ | √ | √ | √ | H | ||||||||||||
| [76], (2021) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | H | ||||||
| [77], (2022) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | M | |||||
| [78], (2021) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | H | ||||
| [79], (2019) | √ | √ | √ | √ | √ | √ | √ | √ | √ | M | |||||||
| [80], (2019) | √ | √ | √ | √ | √ | √ | √ | M | |||||||||
| [81], (2020) | √ | √ | √ | √ | √ | √ | M | ||||||||||
| [82], (2020) | √ | √ | √ | √ | √ | √ | √ | √ | √ | L | |||||||
| [83], (2021) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | M | ||||||
| [84], (2021) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | M | ||||||
| [85], (2021) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | M | ||||||
| [86], (2022) | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | M | ||||||
| Schema (Year) | Security Properties | Challenges | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Chain Growth | Chain Quality | Common Prefix | Validity | Block Consistency | Transaction Consistency | Scalability | Additional POW | Compatibility | Fined Grained | Secret Sharing | Accountably | Anonymity | Decentralization | Revocation | Anti-Collusion | Efficiency (High (H)/Medium (M), Poor (P) | |
| [95], (2019) | √ | √ | √ | √ | √ | √ | √ | √ | P | ||||||||
| [96], (2020) | √ | √ | √ | √ | √ | √ | √ | √ | √ | P | |||||||
| [97], (2017) | √ | √ | √ | √ | √ | √ | M | ||||||||||
| [98], (2020) | √ | √ | √ | M | |||||||||||||
| [99], (2019) | √ | √ | P | ||||||||||||||
| [100], (2020) | √ | √ | √ | √ | √ | √ | √ | P | |||||||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abd Ali, S.M.; Yusoff, M.N.; Hasan, H.F. Redactable Blockchain: Comprehensive Review, Mechanisms, Challenges, Open Issues and Future Research Directions. Future Internet 2023, 15, 35. https://doi.org/10.3390/fi15010035
Abd Ali SM, Yusoff MN, Hasan HF. Redactable Blockchain: Comprehensive Review, Mechanisms, Challenges, Open Issues and Future Research Directions. Future Internet. 2023; 15(1):35. https://doi.org/10.3390/fi15010035
Chicago/Turabian StyleAbd Ali, Shams Mhmood, Mohd Najwadi Yusoff, and Hasan Falah Hasan. 2023. "Redactable Blockchain: Comprehensive Review, Mechanisms, Challenges, Open Issues and Future Research Directions" Future Internet 15, no. 1: 35. https://doi.org/10.3390/fi15010035
APA StyleAbd Ali, S. M., Yusoff, M. N., & Hasan, H. F. (2023). Redactable Blockchain: Comprehensive Review, Mechanisms, Challenges, Open Issues and Future Research Directions. Future Internet, 15(1), 35. https://doi.org/10.3390/fi15010035







