Abstract
Traffic density around the globe is increasing on a day-to-day basis, resulting in more accidents, congestion, and pollution. The dynamic vehicular environment induces challenges in designing an efficient and reliable protocol for communication. Timely delivery of safety and non-safety messages is necessary for traffic congestion control and for avoiding road mishaps. For efficient resource sharing and optimized channel utilization, the media access control (MAC) protocol plays a vital role. An efficient MAC protocol design can provide fair channel access and can delay constraint safety message dissemination, improving road safety. This paper reviews the applications, characteristics, and challenges faced in the design of MAC protocols. A classification of the MAC protocol is presented based on contention mechanisms and channel access. The classification based on contention is oriented as contention-based, contention-free, and hybrid, whereas the classification based on channel access is categorized as distributed, centralized, cluster-based, cooperative, token-based, and random access. These are further sub-classified as single-channel and multi-channel, based on the type of channel resources they utilize. This paper gives an analysis of the objectives, mechanisms, advantages/disadvantages, and simulators used in specified protocols. Finally, the paper concludes with a discussion on the future scope and open challenges for improving the MAC protocol design.
1. Introduction
In the last few decades, the number of vehicles has witnessed a surge in global transportation systems. Vehicular communication is a pivotal component for intelligent transportation system (ITS) and innovative city development. Rapid urbanization has led to expansion in the utilization of vehicles for transportation, attracting researchers in vehicular ad hoc networks (VANETs). VANETs uses a variety of communication technologies such as short-range wireless LAN (WLAN) and cellular technologies such as long-term evaluation (LTE) and voice over LTE (VoLTE) [1]. Since 1980, VANETs incorporating an ad hoc network framework have grown rapidly, with vehicles interacting via wireless networks. Emerging technologies such as 5G, 6G, cloud edge computing, and SDN have ameliorated VANET communication with the timely delivery of safety and non-safety messages in the recent era.
VANETs have a highly dynamic topology with fast-moving nodes, attracting researchers due to rapid urbanization. The field has drawn the attention of scholars towards research for a safer and more comfortable driving experience in the future. It consists of both inter-vehicular Vehicle-to-Vehicle (V2V) and intra-vehicular Vehicle-to-Infrastructure (V2I) communication [2], where infrastructure is the electronic control units within the vehicles. Two mechanisms of communication in an ITS are mobile ad hoc networks (MANETs) and VANETs [3]. There is no central administration or fixed infrastructure in MANETs; nodes self-configure themselves and interact. Unlike MANETs, VANETs follows predictable patterns along a road. Moreover, the processing and storage capacity of VANETs is better than that of MANETs. VANETs have unique features such as high mobility and the constraint of a dynamic road network topology, unpredictable network size, and infrastructure support that differentiates it from MANETs. A basic model diagram of VANETs includes vehicles and other infrastructures communicating via V2V, V2I, Road Side Units (RSUs), and Onboard Units (OBUs). These communications play a vital role in the transportation system to improve traffic efficiency and safety. A schematic representation of the communication is depicted in Figure 1.
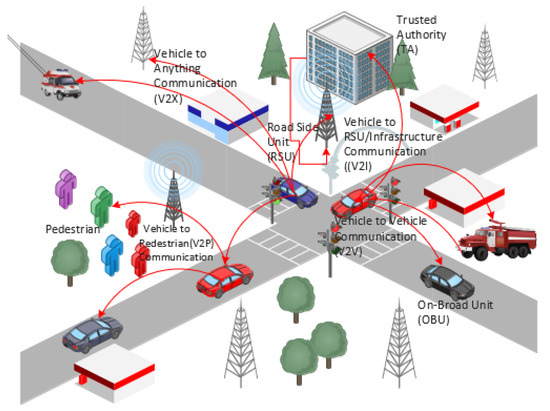
Figure 1.
VANET architecture [1].
VANET applications are divided into categories such as life-critical applications, safety, warning applications, e-toll collection, group communication, traffic management, and user applications, as in [4]. Most papers have broadly classified VANET applications into two categories: safety-based applications (handling real-time traffic and avoiding accidents) and non-safety-based applications (infotainment services, parking availability, GPS tracking of nearby places, etc.) [5,6]. The salient characteristics of VANETs include the dynamic topology, unpredictable network size, high scalability, recurrent information exchange, time-critical communication, wireless medium of communication, energy efficiency, and real-time applications [7,8].
Intelligent transportation systems (ITSs) in smart cities have improved road safety and minimized the risk of mishaps on the road. The use of DSRC [9] (IEEE 802.11p [10]), WAVE (IEEE 1609 protocol stack [11]), and 5G LTE have regulated communication in VANETs extensively. Different countries of the world have adopted dedicated frequency bands for vehicular communication by ITS [12]. Based on the division of a spectrum, the MAC protocols are divided into single-channel MAC and multi-channel MAC. The single-channel MAC focuses on resource allocation whereas the multi-channel MAC deals with collision avoidance and load balancing by providing multiple channel access mechanisms.
Some of the challenges tackled by MAC protocol design in VANETs are (1) the provision of low latency safety services and high throughput non-safety services, (2) the elimination of hidden/exposed terminal problems due to rapid mobility of nodes in VANETs and topology changes, (3)proper resource and bandwidth allocation in single-channel as well as multi-channel for load balancing and better network throughput.
Various MAC protocols have been reviewed in the past based on different criteria. The authors in [13] reviewed multi-channel MAC protocols in VANETs, with the design of an adaptive MAC protocol to handle topology changes by adjusting the control channel based on a Markov model. In [10], TDMA-based MAC protocols were studied, protocols were classified based on topology, and a comparative analysis along with the advantages of using contention-free access mechanism were provided. In [14], the authors assessed foreground multi-layer challenges for better performing VANETs, with a focus on different layers, and proposed solutions along with the limitations and future work.
1.1. Paper Contribution
Researchers have expressed considerable interest in vehicular networks, their applications (safety and non-safety), traffic conditions, network topology, protocols, and enhanced network performance. This survey provides the latest update on applications, standards, and MAC protocols for efficient vehicular communication. The state-of-the-art covers the essential aspects of vehicular communications, including architecture, applications, challenges, vehicular networks, standards in different countries, and classification of MAC protocol based on the channel access mechanism. To the best of our knowledge, this survey is the first of its kind to classify MAC protocols based on channel access mechanisms, including the latest protocols. Apart from the classification, the paper presents the details of ITS standard deployments in different regions, followed by a detailed explanation and implementation of the latest-generation technologies (C-V2X, 5G, and SDN). The article commences from a clear description of vehicular communication, architectural overview, objectives, and the state-of-the-art and concludes with the future scope and research directions.
1.2. Paper Organization
This paper represents a comprehensive study on MAC protocols in VANETs, the challenges, and issues related to the design of an efficient MAC protocol. The remainder of this paper is organized as follows: Section 2 provides a brief overview of DSRC and cellular technology for vehicular networks. Section 3 introduces some of the traditional MAC protocols along with their pros and cons. Section 4 represents studies on various recently proposed MAC protocols based on their objectives, mechanisms, advantages, and disadvantages. Section 5 discusses the future scope and challenges for designing a MAC protocol. Finally, we conclude this paper in Section 6.
2. Vehicular Networks
This section presents DSRC-based networks, their usage and challenges, WAVE architecture, and frequency range standards for vehicular communication of countries such as Europe, Korea, China and Japan. This section also illustrates cellular networks for vehicular communication, including LTE, C-V2X, and 5G.
2.1. DSRC-Based Networks
Standard organizations have allocated different frequency bands to different regions for efficient VANETs communication. This frequency spectrum allocation provides multi-channel capabilities with minimal collision and congestion during transmission. In the US, the Federal Communication Commission (FCC) allocated 75 MHz bandwidth for DSRC in the frequency band of 5.9 GHz [15]. Similarly, in Europe, the European Telecommunications Standards Institute (ETSI) provides vehicular communication for V2V and V2I with an allotted range of 50 MHz bandwidth in the frequency band of 5.855 to 5.905 GHz.
On the other hand, China has been provided by the Ministry of Industry and Information Technology (MIIT) with a dedicated 20 MHz and bandwidth range in 5.905–5.925 GHz. In Korea, the Ministry of Science and Information and Communications Technology (MSIT) allocates a frequency band of 10 MHz for V2I communication with a bandwidth of 5.895–5.905 MHz for CCH and SCH. For Japan, the Association of Radio Industries and Businesses (ARIB) is the organization that allocated 80 MHz as the frequency for DSRC, with bandwidths of 5.770–5.850 GHz and 755.5–764.5 MHz [16].
The WAVE architecture has seven channel divisions, each with 10 MHz, and 5 MHz is kept aside for future use as backup [17]. One of these channel divisions is reserved for safety applications through control channels (CCH), and the rest are for safety and non-safety applications through service channels (SCHs). The transceivers sense these fixed channels for multi-channel access at the same time interval without collision. Orthogonal frequency division multiplexing (OFDM) is used in the WAVE standard for interference avoidance during transmission [18], with data rates of 6–27 Mbps. The ITS-G5 standard uses 2 amplitude-shift keying (2ASK) or 2 phase-shift keying (2PSK), with data rates of 6–12 Mbps; quadrature phase-shift keying (QPSK) supports data rates of 1–4 Mbps. These are some of the modulation techniques used for vehicular communications. Vehicle-to-everything (V2X) communication with LTE and 5G has been adopted along with QPSK [19], which provides a high data rate for better transmission efficiency compared with OFDMA and 2ASK. Table 1 summarizes these standards.

Table 1.
Vehicular communication standards.
In IEEE 802.11 [20], the distributed coordination function (DCF) deals with medium access based on CSMA with collision avoidance (CSMA/CA). Here, the device first listens to the network channel before transmitting for collision avoidance. In IEEE 802.11, the main focus is on RTS/CTS/ACK mode of packet exchange to access the medium. A network allocation vector (NAV) is set according to the transmission duration indicated by RTS. However, CSMA/CA is not suitable for real-time scenarios due to its inherent channel access delay. The vehicular networks incorporates dedicated short-range communication (DSRC) for enriching the driver’s comfort and safety. Wireless access in vehicular environment (WAVE) [21] defines the IEEE 802.11p for MAC layer implementation in VANETs. The DSRC documents the physical (PHY) and medium access control (MAC) layers of the WAVE stack [22]. To achieve quality of service (QoS), the WAVE stack of IEEE 802.11p for a MAC protocol incorporates an enhanced distributed channel access (EDCA) mechanism [23]. The messages are divided into four types based on access priority, as access category AC[0]∼AC[3] with separate contention windows and frames set for each category.
2.2. Cellular-Based Networks
The Third Generation Partnership Project (3GPP) introduced cellular-V2X (C-V2X) in Release 14 [24]. The use cases of the ITS spectrum in various countries per government standardization is presented in [25,26]. A simulation model of the Third Generation Partnership Project (3GPP) Release 14 Cellular Vehicle-to-Everything (C-V2X) sidelink, upon which 5G New Radio mode 2 was based, is presented in [27]. To support V2X communications, C-V2X Mode 4 modifies the PHY and MAC layers of the LTE sidelink [28]. In high mobility situations, LTE’s PHY layer is designed to improve performance. The sensing-based semi-persistent scheduling (SB-SPS) mechanism is implemented at the MAC layer to autonomously select vehicle resources.
In [29], to support beacon broadcasting over V2V networks, a distributed network coding MAC protocol (NC-MAC) is proposed. By combining re-transmission, network coding, and preamble-based feedback mechanisms, reliability is improved. In various situations, including highway and urban, simulations demonstrate the performance gains obtained from the NC-MAC protocol compared with the 5G cellular vehicle-to-everything (C–V2X) MAC protocol. The DSRC protocol uses a random back-off scheme to propagate data between MAC and PHY, which causes the inter-layer data propagation delay. However, it remains within microseconds. Rate control is therefore directly proportional to end-to-end latency. The C-V2X MAC, however, can introduce a time offset (on average 50 ms) when translating a packet because of semi-persistent scheduling (SPS) operations [30].
As a part of the C-V2X communication, other technologies such as radar, cameras, and in-vehicle sensors support services such as semi-autonomous driving, autonomous driving, and assisted driving in these vehicles. In addition to better coverage and lower deployment costs, V2X services can be run on a dedicated network using the 5G public network, which offers high QoS features with its flexible network design, including ultra-fast data throughput and ultra low latency [31].
Release 14 of C-V2X released in March 2017 included the first version of the tool. The automotive vertical needs were addressed by a specification called LTE-V2X, which was created in conjunction with the development of the 4G LTE system. As a part of the LTE V2X revisions since Release 15, the 3GPP has begun looking at the 5G specification for 5G-V2X. NR V2X specifications defining the sidelink, which are integrated with the 5G-V2X specifications defined in Release 16, in June 2020. The sidelink 5G-V2X standard will be improved in Release 17, which is still undergoing testing and is scheduled for release in 2022 [32].
The framework of 5G is based on the fourth-generation LTE mobile standard. Unlike 4G signals, 5G signals are transferred over short distances through a plethora of small, low-power base stations that can be located on light holes or rooftops. This is the primary difference between 5G and 4G signals. Since the new 5G mobile generation uses the low-frequency spectrum to transmit signals, the mobile network structure was built via radio operators. With 5G, signal transmission is virtually unaffected by the weather, building obstructions, or distance. The previous generation of wireless communications worked in a low-frequency spectrum band, so millimeter-waves [33] have to deal with interference and distance challenges that were not present during the last era. Wireless communications over 5G will be highly reliable, with ultra-low latency and very high throughput. For future and existing applications, 5G is expected to support a large number of wireless connections. Proximity service (ProSe) [34], a critical feature in 5G, allows for awareness of nearby devices and remote services and is provided through D2D communications. It also provides data management services for cloud computing, software-defined networks (SDN). The 3GPP has built a backward and forward compatible 5G standard using current LTE technologies [35] and will soon reveal new air interfaces for 5G technology. In [36], the authors discuss the new radio access technologies for connected and autonomous vehicles, such as visible light communication (VLC), millimeter wave (mmWave), C-V2X, and 5G, along with the challenges and opportunities. The new directions in research related to seamless connectivity, edge, fog, SDN, and security are also focused. An in-depth survey and comparison of vehicular MAC routing protocols was conducted in [37]. It addressed routing protocols with a cross-layer approach with MAC for VANETs. The MAC-aware routing solutions were classified as contention-free and contention-based. It provided a fully standardized, cross-layer communication model that is fully compliant with the existing vehicular service and application layers and messaging sets established by automotive and standards communities.
3. MAC Classification in VANETs Based on Contention Mechanism
Traditional classification of the MAC protocol in the literature [38,39] includes contention-based, contention-free, and hybrid protocols. Similarly, in this section, we studied some traditional MAC protocols in VANETs and classified them as contention-based, contention-free, and hybrid. This section ended by stating some of the recent advancement in vehicular communication, giving future directions.
Contention-based protocols: Commonly referred to as “listen before talk”. The nodes perceive the channel first; if it is free, it transmits. The system contends for channel access; the node that wins transmits through the channel. It is primarily used in a sparse network scenario so that the bandwidth can be utilized efficiently. These types of protocols cannot be used in real-time applications due to the time-bound and reduced throughput caused by collision. IEEE 802.11p and CSMA-based protocols are examples of this type of protocol.
Contention-free protocols: The nodes need not compete to gain channel access, and the time period of transmission in the channel is pre-allocated. Collision is avoided during data transmission in the channel. The transmission frames are divided into slots, and the nodes are synchronized for channel access. Although this type of protocol provides quality of service (QoS), it suffers from improper bandwidth utilization due to explicit time slot allocation. The main challenge is the proper allocation of channel resources among nodes. TDMA, FDMA, and SDMA are examples of this type of protocol.
Hybrid protocols: It merges the advantages of the contention-free and contention-based protocols to achieve QoS and to enhance network performance. It is primarily applicable for safety applications as there are minor delays and improved throughput. CSMA with TDMA [40], Token-Ring passing, and clustering-based protocols are some examples of this type of protocol.
ALOHA is one of the introductory MAC protocols [41] for radio packet networks. In ALOHA, there is throughput reduction for which S-ALOHA slotted ALOHA [42] was proposed, which splits the medium into various time slots and strives to transmit at the beginning of the time slot.
Multiple access with collision avoidance (MACA) [43] was proposed to overcome the hidden terminal problem using the handshaking method via RTS/CTS communication. The MACA for wireless (MACAW) [44] adds functionality to MACA to make it more robust when it comes to detecting collisions in WLAN data transmission. It requires nodes to send acknowledgements after every successful frame transmission. Similarly, BTMA [45] was proposed to overcome the hidden node problem by splitting the channel into data channels and a control channel. MC-MAC [46] uses two codes, one for control packet transmission and the other for data packet transmission.
ADHOC-MAC [47] uses a slotted frame and dynamic TDMA mechanism; R-ALOHA [48] was designed for dynamic TDMA in a distributed way. The reliable R-Aloha (RR-Aloha) [49] architecture was designed similar to ADHOC-MAC, which uses distributed MAC and UTRA-DD (UMTS terrestrial radio access time division duplex) for physical channel access with the single-hop broadcast. Directional antenna-based MAC [50] is yet another development in past years that uses the GPS of the terminals and restricts transmissions to a geographical area.
WAVE (802.11p) [51] mechanisms have no predetermined schedule, and channel access is random for vehicles, resulting in transmission collisions in a dense network scenario. 802.11p uses CSMA/CA; safety-critical applications cannot be guaranteed QoS due to its contention-based nature. Contention-based MAC protocols are designed to increase scalability under heavy loads by considering parameters such as the physical carrier sense threshold, contention window, and the transmission power control. WAVE employs the use of GPS to synchronize DSRC radios installed on all vehicles. Sync intervals (SIs) typically consist of CCH intervals (CCHIs) and SCH intervals (SCHIs), separated by guard intervals. Adaptive collision-free MAC (ACFM) [52] is a TDMA contention-based protocol with dynamic slot allocation. In ACFM protocols, unused slots are avoided during sparse traffic, and additional spaces are allocated in dense traffic.
The VeMAC [53] protocol supports multi-hop broadcasts and one-hop broadcasts on the control channel while reducing collisions caused by node mobility on the access channel. Vehicles moving the opposite way are assigned disjoint time slots and roadside units to reduce collisions during merging. Two transceivers are used per node, tuned to the control and service channels, and synced by the GPS signal. The VeSOMAC protocol [54] is a self-organizing, DSRC-based MAC protocol used in multimedia applications. The TDMA slot information is exchanged in-band during distributed MAC scheduling. In highway scenarios, this enables fast reconfiguration of TDMA slots without depending on roadside infrastructure. VeSOMAC operates both synchronously and asynchronously. Through cooperative TDMA MACs [55], non-safety applications can achieve greater throughput. This protocol overcomes problems associated with poor channel conditions, which lead to transmission failures. If a packet fails to be transmitted, the neighboring nodes call helper nodes to relay the packet in a time slot. It is important to note that the helper nodes use the available time slots, which may lead to access collisions between the vehicles and the helper nodes. An enhancement of ADHOC MAC, the adaptive real-time distributed MAC (A-ADHOC) [56] protocol, intends for real-time application in large-scale wireless vehicle networks that provide adaptive frame lengths. Both the channel resource utilization and response time of A-ADHOC were better than those of ADHOC MAC, and A-ADHOC avoided network failure regardless of traffic density.
Some of the hybrid protocols (TDMA + CSMA/CA) include HER-MAC (hybrid efficient and reliable MAC), TDMA/CSMA MAC (HTC MAC), SOFT-MAC (space orthogonal frequency–time MAC), and DMMAC (dedicated multi-channel MAC with adaptive broadcasting). The SDMA, OFDMA, TDMA, and CSMA techniques were incorporated into SOFT-MAC [57], with GPS to locate sub-carriers shared between vehicles belonging to that particular cell. The HER MAC [58] is a multi-channel MAC with adaptive broadcasting. Every vehicle in the CCH transmits safety/alert messages using a half-duplex transceiver without colliding with another vehicle. HTC MAC [59] alleviates the collision and enhances the throughput of HER MAC by broadcasting the announcement packet (ANC) and reservation period (RP). DMMAC [60] is also a dedicated multi-channel MAC with access time split into intervals (CCHI and SCHI), again split as contention-based reservation period (CRP) and adaptive broadcast frame (ABF).
This discussion presents some of the traditional MAC protocols classified based on contention mechanism as contention-based, contention-free, and hybrid presented in Figure 2. Furthermore, the next section provides a brief classification of contemporary MAC protocols in vehicular communication.
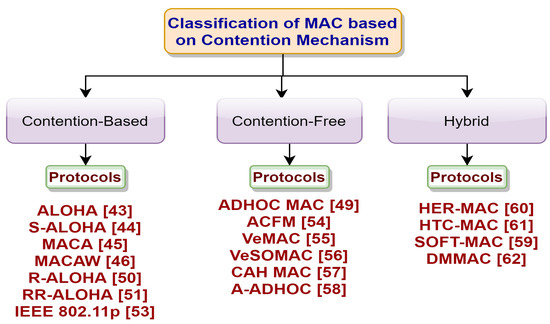
Figure 2.
Classification of MAC protocols based on the contention mechanism.
A summary of different MAC protocols is shown in Table 2.

Table 2.
Summary of traditional MAC protocols.
In recent years, MAC protocols with dynamic interval schemes [61] have been proposed for the optimization of channel control intervals. A MAC protocol for dynamic adaptation due to changing VANETs topology is a challenge as the static service channel and the control channel cannot adapt to the versatile VANETs environment. Protocols designed with a dynamic interval scheme provide maximized performance with less end-to-end delay and minimized collision.
Clustering is a prime concept in VANETs for efficient group communication. Some VANETs integrates machine learning and fuzzy logic algorithms to stabilize and make clusters more efficient. The clustering algorithms are classified into three broad categories: intelligence-based strategies (machine learning algorithms, fuzzy logic algorithms, and hybrid algorithms), mobility-based strategies (NEMO algorithm and mobility algorithm), and multi-hop-based strategies (2-hop algorithms and 2+-hop algorithms) [62]. Some other clustering-based algorithms are proposed in [63,64].
The SDN-based network is one of the technologies used recently in most fields for reliable and efficient communication; it splits the control plane from the data plane by providing centralized access to network resources. Reference [65] presents a concise layer structure of VANETs along with an SDN controller. The application of SDN-VANETs on various parameters in IoT and wireless communication is presented. The open challenges and research directions faced by the latest work, including VANET integration with SDN; the recent and emerging technologies; as well as the use cases are demonstrated in [66].
With the new standards described in Section 2, it is possible to transition from “legacy” IEEE 802.11p systems smoothly. By implementing the same frequency channel worldwide, IEEE 802.11bd takes advantage of existing deployments and infrastructure without interfering with current ITS applications. IEEE 802.11bd achieves interoperability through a compatible waveform structure. In addition, it employs a well-known channel access mechanism, “listen-before-talk” (carrier sensing) as asynchronous and non-persistent V2X network communication is substantially more flexible in size and transmission rate than conventional V2X networks [67]. The IEEE 802.11bd Next Generation V2X Study Group was formed in March 2018 to minimize the performance gap between DSRC and C-V2X, to support additional modes of operation, and to increase throughput [68].
4. Classification of MAC Protocols Based on Channel
This section presents the classification of MAC protocols in VANETs; oriented as distributed, centralized, cooperative, cluster-based, virtual token, and random selection based and further sub-divided as multi-channel and single-channel. The classified MAC protocols based on channel access mechanisms are depicted in Figure 3 and discussed.
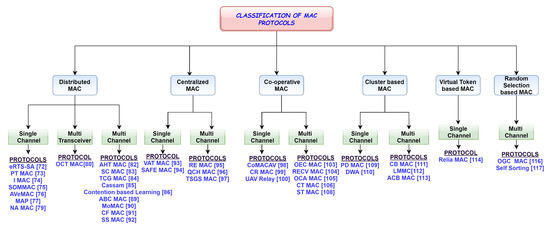
Figure 3.
Classification of MAC protocols.
4.1. Distributed Single-Channel MAC Protocols
There is no centralized assistant for channel access. In a single-channel MAC, the access channel is not divided, so there can be interference chances. These are basically designed to resolve challenges related to packet allocation and resource allocation based on TDMA, CDMA, and SDMA. The main focus is on TDMA- and SDMA-based time-slot allocations and contention-based parameters for improving network throughput from that of IEEE 802.11p. To adapt to VANETs’ dynamic change in topology, distributed MAC protocols are designed to minimize communication overhead.
4.1.1. eRTS-SA
The request transmission split-slotted ALOHA-based MAC protocol provides fair channel access with high throughput and interference avoidance using a GPS-embedded micro-cell unit.
Every vehicle reports their location information to micro base stations (mBS) by GPS, and MEC is used in the contention access phase to provide cloud capabilities. The road between mBS is divided into the segment and allocated with segment number to detect location information to reduce overheads. The vehicles are arranged for time slot allocation in increasing order of their segment number. To minimize channel interference, the same segment number is allocated to vehicles geographically apart. The methodology includes dividing the frame into three phases: contention access phase (CAP), broadcast feedback phase (BFP), and contention-free phase (CFP). In CAP, the vehicles send a request signal to RSUs. After the signal is received by RSU, successive interference cancellation (SIC) is implemented; then, the vehicle occupies the time slots to enable transmission without interference. To prevent interference, the BFP is divided into two divisions assigned to adjacent mBSs. The mBS are equipped with the MEC server to serve vehicles within their micro-cells, and vehicles move in a bi-directional highway with no “on-and-off-ramp” [69].
The physical interference model based on signal-to-interference-plus-noise ratio (SINR) is calculated to keep track of successful transmission. Vehicles and mBSs are time-synchronized; the time-slot allocation mechanism avoids the hidden terminal problem. This protocol is better in throughput (4.8 percent lower than the theoretical maximum throughput) and transmission efficiency. The protocol does not prioritize safety-based applications or non-safety-based applications, energy efficiency is not analyzed, and the scalability issue is not addressed.
4.1.2. PTMAC
This protocol is used for collision prediction and collision reduction effectively in two-way traffic as well as in four-way intersections. The protocol revolves around three steps: potential collision detection, potential collision prediction, and potential collision elimination. Potential collision is detected based on slot information; the prediction of collisions in the future is based on traffic and vehicle information conditions. The potential collision can be eliminated by rescheduling the slots (mostly tackling encounter collision). Every node broadcasts its information, including location, slot reserved, speed, and direction. The frame information (FI) contains information about its one-hop neighbor nodes and itself. The new joining node has to listen to the channel before contending for slot allocation. Potential collision detection in same and opposite directions is depicted in Figure 4.
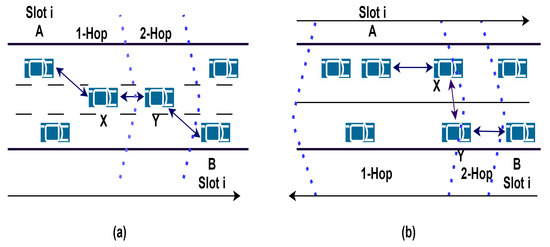
Figure 4.
Potential collision detection: (a) same direction; (b) opposite direction [70].
In potential collision detection, every node checks whether the same slot is occupied by any of its one-hop or two-hop neighbors. The intermediate nodes contain slot reservation information and detects potential collision between the two one-hop neighbors. After detecting potential collisions, the nodes that collide are allocated different slots and broadcast messages to their one-hop neighbor.
There is no slot partitioning; thus, unbalanced traffic density has no impact on the performance. PTMAC effectively handles access collision as well as contention collision. However, network overhead and power consumption need to be studied more.
4.1.3. I-MAC
Improved MAC (I-MAC) avoids collision in high-density VANET scenarios via proper channel access. It reduces the loss of messages due to efficient channel utilization. It employs a dynamic TDMA-based mechanism with CSMA. An initial broadcast table (IBT) containing the vehicle’s MAC address is created before sending data. Due to the possibility of more than one vehicle sending to IBT simultaneously, causing a collision, the nodes sense the channel before sending to IBT. A collision may even occur if nodes start transmitting as soon as it senses an idle channel; therefore, I-MAC uses dynamic inter-frame spacing (DIFS), which means nodes wait for a random time before transmitting through an idle channel to provide fair channel access.
The protocol avoids merging collision and access collision, thus improving the channel’s performance and the reliability of data transmission. There is much communication overheads, and the hidden node problem analysis needs further investigation.
4.1.4. SOMMAC
A self-organizing multi-channel protocol was proposed for rapid handover in the network without disconnecting and maintaining the performance level of the network. It aimed to alleviate access to collisions, to improve the packet delivery rate, and to minimize delay.
It uses DSRC for multi-channel transmission in two-way traffic. The vehicles listen to channels to verify whether there is a message from the scheduling channel (SCCH). If no message is found, the vehicle waits and sends a joining request from the contention-based sub channel (CBCH) by CSMA. The RSU that controls the network frequently sends RSU heart-beat packets (RSUHB) from SCCH to let other vehicles know that the vehicles receiving data packets are near the RSU, thus avoiding collision. Upon accepting a channel request packet (CRP) from CBCH, the RSU assigns a service channel based on the direction of the vehicle. It assigns time slots to vehicles based on vehicle direction. RSU consists of a vehicle channel information table, which holds the vehicle’s information. A configuration packet is prepared consisting of channel information and sent to the destination.
As soon as a vehicle receives a configuration packet (CP) belonging to itself, it fixes the channel assigned for transmission and releases all other channel and time slots. The vehicle is then added to the network and sends vehicle heart-beat (VHB) packets from the heart-beat channel (HBCH) based on its direction. Upon receiving VHB, the RSU checks the vehicle information table; if the vehicle is present, then it checks the time period in which the vehicle should be present in the network. After the vehicle drops this time, it is removed from the network so that other vehicles can assign themselves to the released time slot. The dynamic channel assignment method is used to improve efficiency and fairness in accessing the channel based on TDMA, with a better packet delivery ratio and minimized latency.The main challenge includes power consumption and handling multi-directional scenarios with minimized communication overhead.
4.1.5. AVeMAC
Adaptive vehicular MAC is proposed to adaptively vary the channel condition and to handle unbalanced traffic in the opposite direction in a two-way intersection road scenario. It also eliminates merging collision and access collision and improves channel utilization. AVeMAC is an enhanced VeMAC [53], which is a TDMA-based protocol supporting one control channel and several service channels.
The frames in the control channel are partitioned into disjoint sets of time slots analogous to moving vehicles in the left or right directions [71]. The partitioning of the channel is not fixed as in VeMAC; rather, it varies adaptively to the traffic condition. Here, vehicles cannot use the time slots occupied by vehicles one-hop or two-hop away but can use the slots occupied by at least three-hop neighbors. Before adapting to timeslot partitioning, vehicles need to listen to the channel for N successive time slots to obtain information about a set of one-hop and two-hop neighbors. Then, the set of timeslots available for allocation can be determined so that the vehicle can randomly select a time slot to be allocated for further transmission. It then checks whether the reservation of that slot is successful by listening to the channel for the next N-1 slots. Suppose that the reservation is found to be unsuccessful. In that case, it is estimated that some other vehicle in a two-hop neighbor attempts to reserve that slot, so the vehicle tries to reserve a new slot, thus avoiding access collision. The vehicle continues to access the same time slot until a merging collision occurs detected based on frame information (FI) messages.
The protocol improves channel utilization. However, it does not consider the hidden terminal problem. QoS matrices such as reliability, packet delivery ratio, and network throughput are also not analyzed.
4.1.6. MAP
Medium access for PLNC is a contention-free MAC protocol used to provide quick and reliable data transmission in VANETs. It addresses two fundamental problems: collision due to hidden terminals in CSMA/CA-based networks and handling excess control messages in dense TDMA-based network scenarios. It is a decentralized location-based scheme, where the network is divided into sub-zones of equal length. Vehicles incorporate CSMA/CA schemes to access the channel; the successful node transmits and is called the intra-zone relay node [72]. The transmission occurs in two phases: the access phase, when nodes transmit packets to relay nodes, and the broadcast phase, where the relay forwards the network-coded packet. MAP handles the hidden terminal problem by priority-based indexing [73]. To prevent dissemination delays, a session order prioritization scheme is implemented. It provides reliable and faster transmission.
There is a possibility of merging collision as this protocol only handles access collision; delay, Packet Delivery Ratio, and network throughput are not analyzed. The network model presented is based only on a 1D network.
4.1.7. NA MAC
A novel neighbor association-based MAC is designed for reliable broadcast. The protocol is based on TDMA with the CSMA approach for disseminating basic safety messages (BSM), providing a short time for each slot. Duplicate slots allocated are avoided by the implementation of communication via a three-way handshake. The frame structure of NA MAC for collision avoidance is depicted in Figure 5. TDMA-based broadcast is provided by V2V and V2I communication. The protocol alleviated collision and hidden-terminal problems, providing reliable communication with less overhead and a good packet reception ratio. It also minimizes the latency of safety message transmission.
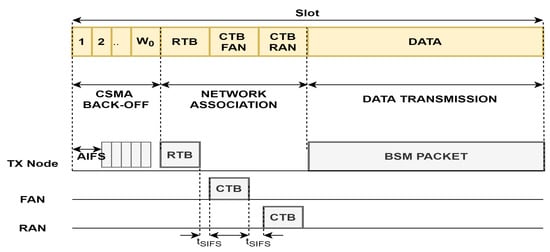
Figure 5.
Frame structure of NA MAC for collision avoidance [74].
This protocol’s shortcoming is that it does not emphasize non-safety message transmission; single-channel access leads to improper resource utilization when considering both safety and non-safety messages. A broadcast storm problem causes performance degradation.
4.2. Distributed Multi-Transceiver MAC Protocols
It is capable of longer distance communications with less cost as the transmitter and receiver run on parallel interfaces and use the same components. It basically incorporates a cooperative mechanism of transmission.
OCT MAC
The optical CDMA with TDMA is a visible light communication (VLC)-based protocol designed for V2V communication [75]. The vehicle transmits information via optimal orthogonal codes (OOCs) to improve throughput; the nodes send and receive signals with optical CDMA [76]. Two photo-detectors are deployed at the front and rear of the vehicle at their centres and four next to each of the headlights and taillights. GPS is used with 1PPS to know the location of the vehicle and to obtain proper time synchronization. The signal-to-noise ratio (SNR) is estimated to find whether two vehicles are present in each other’s communication range. A collision during transmission is finite due to the fixed time slot allocation.
The OCT MAC enhances the network throughput and minimizes the average access delay. The main demerit of this protocol is that the mobility and dynamic characteristics of VANETs are not analyzed.
4.3. Distributed Multi-Channel MAC Protocols
In multi-channel-based distributed MAC protocols, the access channel is divided into one CCH and several SCHs. The protocol mostly focuses on TDMA for the synchronous transmission and CSMA/CA for the asynchronous transmission. As the channel is divided, there is prioritization for safety and non-safety messages; thus, latency in terms of safety messages can be minimized.
4.3.1. AHT MAC
An adaptive high-throughput MAC protocol was designed for resource reservation and sharing, adapting to rapid node density changes. AHT MAC follows the CCH and SCH mechanisms siimilar to IEEE 802.11p. Each node is equipped with GPS for proper time synchronization to avoid collision during transmission. Two ranges are included in this protocol for efficient transmission, i.e., transmission range (TR) and interference range (IR). The nodes transmit in their TR only, and IR is present to detect interference when nodes transmit in their TR and avoid it. Distributed TDMA is used for the periodic broadcast of information such as node ID, location, and velocity of nodes. As in IEEE 1604.9, the SCH is divided into SCH intervals (SCHIs) consisting of payload intervals and guard intervals; furthermore, the PI is divided into service resource blocks (SRBs) as depicted in Figure 6. SRB management eliminates the hidden terminal and exposed terminal problem.
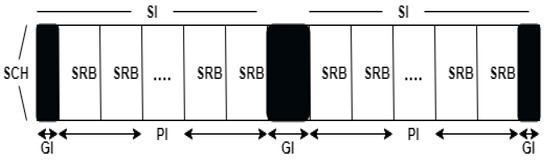
Figure 6.
SCH intervals [77].
SRBs are fully utilized, and the nodes show high performance by transmitting and receiving even when the density is increased. The handshake process in DTR/DTA is secured by a request conflict resolution mechanism [77]. The protocol has less contention time and, thus, improves throughput and minimizes delay. The demerit of this protocol is the broadcast overhead due to DTR/DTS in dense and large networks with packet loss.
4.3.2. SCMAC
The slotted contention-based MAC protocol addresses two types of collision. First, one occurs due to nodes not being present in close proximity, and the other is due to hidden terminals. The first is overcome by the back-off scheme of IEEE 802.11p, and the latter is overcome by TDMA. Here, the time slot is divided into two periods, i.e., TP (transmission period) and RP (reception period). During the TP, a node broadcast packet is needed to transmit, whereas the channel is reserved in the RP. If there is a reservation failure, the node does not transmit the packet in the TP but dedicates another time slot for further transmission. In SCMAC, black burst-based slot reservation is used to jam signals, thus allowing only one node to broadcast the message at a particular TP. The hidden terminal problem is overcome by utilizing spatio-temporal co-ordination (STC). The road is divided into four segments with fixed lengths, and different slots are assigned to the segments.
SCMAC outperforms other back-off schemes in terms of packet delivery ratio. The use of STC is suitable for highway scenarios but not for rapid topological changes in VANET, as it is difficult to divide the road into segments as in STC. Thus, there is some transmission delay and performance degradation even if interference is avoided.
4.3.3. TCG MAC
The TDMA-based MAC with the collision alleviation protocol combines TDMA plus CSMA-based MAC for collision mitigation. The methodology of game theory is implemented when more nodes acquire the same slot as in the CSMA period for efficient slot allocation. This reduces access collision. Vehicles are equipped with GPS to know the position and direction. Synchronization among vehicles is performed by the 1PPS signal administered by a GPS receiver.
The nodes are divided into the direct neighbor set (DNS) belonging to a one-hop neighbor of the transmitting node and the indirect neighbor set (INS), those not a direct neighbor but within the communication range and other nodes that are not in the transmission range. Upon broadcasting the packet, the vehicle ID and slot reservation information of each node belonging to DNS are attached to the header; this enables the nodes to know the slot allocation information of its two-hop neighbors. The nodes update their neighbor set based on information from the DNS. Only collision nodes send reservation messages in CP when they hold a TP slot, and each node must acquire exactly a single-time slot in TP to broadcast messages. The transmission ranges of R and 2R are broadcast by nodes in TP and CP, respectively, as depicted in Figure 7. For all relative neighbor set (RNS) nodes to receive the slot reservation message transmitted by CP, it must have a longer transmission range. The strategy of game theory alleviates collision; this protocol shows high throughput with proper allocation of slots in different channel conditions. There is high power consumption due to the use of transmitters and receivers. There is high network overhead due to the game theory approach.
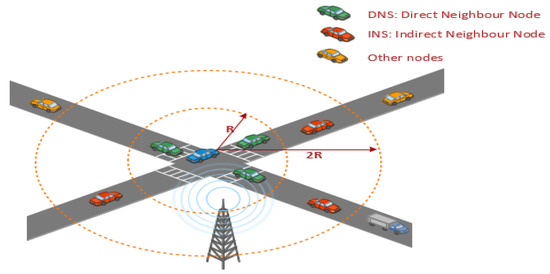
Figure 7.
Mechanism of TCG MAC [78].
4.3.4. CaSSaM
The author in [79] proposed a context-oriented information-based system. It is a dissemination-based protocol that works in a decentralized environment. This protocol considers the channel busy ratio (CBR), collision, number of neighbors, speed, and inter-vehicular distance. The CaSSaM system decides which parameter is adjusted for performance enhancement. The slotted 1-persistence protocol is used for the dissemination mechanism. When a node receives a packet for the first time, a time slot is allocated to the node and the node is then re-broadcasted with a probability of 1; for re-broadcast, priority is given to the farther node.
It is mostly used for guaranteed safety applications with reduced delay and enhanced throughput. The power consumption of nodes is not analyzed; the protocol has a decentralized approach, and performance can be improved by implementing a centralized approach or by a combination of both.
4.3.5. Contention-Based Learning MAC Protocol
The primary objective is to increase the network scalability, to reduce the bandwidth usage, and to minimize packet collision in a dense topology. The machine learning-based reinforcement learning (RL) [80] technique is used. A self-based Q-learning technique, suitably used based on RL, improves performance by controlling contention in the network. The distributed coordination function of the IEEE 802.11p standard is used with the CSMA/CA mechanism for both unicast and broadcast. The back-off mechanism is used to check whether more than one node accesses a channel at the same time. Q-learning [81] and a Markov-decision process are used to avoid packet collision using an optimized CW based on binary feedback.
The protocol minimizes latency, improves the packet delivery ratio and throughput of the network. There is performance degradation due to a high-mobility, dynamic environment. The fairness in transmission and latency still need be improved.
4.3.6. ABC MAC
The adaptive beacon control protocol is proposed to avoid collision at the rear ends due to congestion. The authors proposed an adaptive beacon rate scheme based on rear end collision, considering the kinematics status of adjacent vehicles and considering a danger co-efficient . Based on the bandwidth requirement and channel capacity, a distributed beacon rate adaptive (DBRA) problem is formulated. A vehicle bearing high estimates is assigned high beacon rate to avoid collision. During congestion, the vehicle adopts a greedy algorithm to solve the DBRA problem and TDMA-based broadcasting is conducted for neighboring vehicles. The protocol works in three basic steps: (i) detection of congestion, (ii) adaptation to distributed beacon rates, and (iii) broadcasting the adapting result to other vehicles.
The protocol guaranteed high performance in dynamic traffic scenario alleviates collision and provides an efficient transmission ratio. QoS in terms of throughput can still be improved. However, it does not emphasis non-safety messages. The off-road collision, real-time traffic management is not analyzed.
4.3.7. MoMAC
The mobility-aware MAC protocol was proposed to achieve collision-free transmission and to enhance the message delivery and reception rates of safety applications. It handles the hidden terminal problem. TDMA-based slot partitioning is used; vehicles use GPS to synchronize and use the same slot until collision is detected. Different time slots are selected by vehicles within the same OHS. To resolve the hidden terminal problem, vehicles in the same THS should choose different communication time-slots. During a THS, the hidden terminal problem can occur when two vehicles, located in the two OHSs, cannot hear each other and decide to send messages simultaneously. For instance, in Figure 8, vehicle A wishes to transmit a message to vehicle B, and vehicle C wishes to transmit a message to vehicle D at the same time. Vehicle C does not realize that vehicle A has already started transmitting because it is not within its communication range, which results in a collision with vehicle B. Since there is no RTS/CTS mechanism, each vehicle should collect and broadcast information about all other vehicles occupying time slots from one-hop neighbors to the other THS, so there is no hidden terminal problem. The protocol is implemented in a multi-lane road segment where the segment is divided into time slots. The collision detection scheme and distributed slot access are employed to eliminate hidden terminal problem [82].
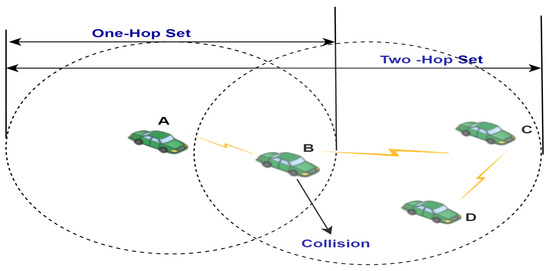
Figure 8.
Illustration of hidden terminals [82].
The protocol aims to minimize delays in access to and delivery of packets. The communication is decentralized, not RSU centric. Therefore, current traffic detection is not easy and cannot handle dynamic traffic scenarios.
4.3.8. CF MAC
The main objective of the collision-free MAC protocol is to make collision-free transmissions, improving the performance and reliability of channel access. Here, an initial broadcast table (IBT) aligns MAC addresses of vehicles in ascending order for setting priorities for transmission. The IBT is updated and broadcast periodically to share the status of the channel. A receiver checks the IBT for the initiator from the first slot; if it wants to send it, it sends a WTS to the initiator. Upon reception, the WTS initiator adds 1 to the IBT. The priority in sending is highest in the vehicle that is at the first slot of BT, so the other vehicles synchronize themselves according to the information of a vehicle’s priority received from BT [83].
This protocol eliminates mergers and access collisions for better performance and reliable transmission. There is a delay in transmission caused during contention avoidance, as vehicles have to wait for a random amount of time before sending. Performance degrades in dense scenarios due to transmission delays.
4.3.9. SS MAC
Slot-sharing MAC was proposed to provide a scalable, reliable, efficient protocol with less delays for safety message broadcasting. Multiple vehicles broadcast alternately on the same time slot using inconsistent coordinations. A circular recording queue is implemented to record the time slot status of the periodic broadcast of safety messages. A distributed time slot sharing (DTSS) mechanism is designed to check on the periodical broadcasting of messages and to share the time slots for reliable transmission. To improve the channel utilization based on heuristic packaging strategy, a random index fit-first (RIFF) scheme is proposed [84]. This assists the vehicles in selecting a suitable time slot for sharing. It employs a traditional TDMA-based mechanism with a slot sharing scheme.
The major demerit is that the protocol cannot handle dynamic resource environments, and safety and non-safety applications. There is overhead for maintaining the table and broadcasting.
4.4. Centralized Single-Channel MAC Protocols
It is either RSU based or cluster head (CH) based. RSUs allocate time slots to the nodes for channel access. It is a better mechanism for providing collision-free access as scheduling of time slots is not as complicated. The periodical broadcasting mechanism employed by RSUs minimizes collision by communicating the time slot reservation messages to nearby vehicles.
The coordination is wholly dependent on either the RSU or the CH. The data are transmitted by a time-synchronization mechanism to avoid collision, but there is network overload due to the centralized control.
4.4.1. VAT MAC
According to VAT-MAC (novel adaptive TDMA-based MAC) protocols, RSU is used to provide efficient access management for more efficient network performance [85].
In the VAT-MAC time management period (TMP), the RSU broadcasts a time management frame (TMF), noting the length of the free transmission period (FTP) and contention period (CP) depicted in Figure 9. The FTP protocol is used for packet transmissions of allocated time-slots, and unidentified vehicles can compete for idle slots in the CP. The RSU can identify the assigned slot in the upcoming FTP if the vehicle successfully accesses the CP without colliding. The RSU further calculates the average vehicle density based on the collision probability in order to anticipate the number of newly entering vehicles. By doing so, it is able to predict the collision probability. By adjusting the frame length accordingly, VAT-MAC is capable of improving network scalability and of ensuring the efficient use of time slots. The mathematical analysis and simulation experiments indicate that VAT-MAC can significantly enhance system scalability and throughput. The performance can be enhance with incorporation of CSMA/CA along with TDMA mechanism.
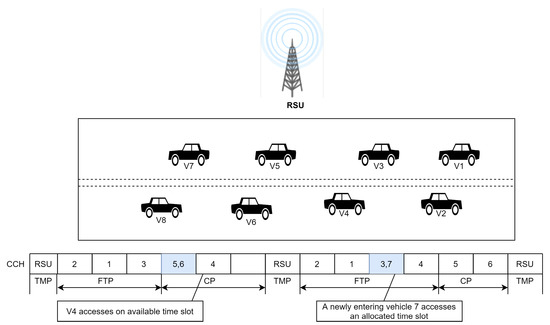
Figure 9.
Time frame structure of VAT MAC [85].
4.4.2. SAFE MAC
The speed-aware fairness-enabled MAC [86] is a RSU-based centralized approach utilizing the CSMA/CA mechanism with dynamic adjustment of CW, a back-off, and a re-transmission limit. Based on the mobility metrics, including speed, location, and direction, the system computes the time spent by vehicles in the service area. Moreover, the vehicles are divided into three groups according to their duration of stay. Each batch has its own MAC parameters. These parameter values are then dynamically changed to ensure that the vehicles with higher speed receives a certain minimum number of messages, which can guarantee fair channel access for V2I. The main limitation of this protocol is it does not consider fairness issues in channel access for V2V and V2D communications.
4.5. Centralized Multi-Channel MAC Protocols
Control is centralized by a central coordinator, but the channel is partitioned to deal with safety and non-safety messages by prioritizing it to minimize latency for safety messages.
4.5.1. ReMAC
The main objective of the reliable MAC protocol is to connect vehicles with a multi-channel hybrid medium of access. It reduces collision and hidden terminal problem and deals with high mobility by randomly minimizing transmission delay. Here, the modeled system consists of RSUs placed at regular intervals in a two-way highway with vehicles moving at high speed. For determining the next RSU, the vehicle’s direction is considered, and the channel is assigned before it enters the range of next RSU. FDMA-based access is used, dividing the CCHs and SCHs into a sub-frequency channel of same bandwidth. This mechanism avoids collision and provides reliable and efficient communication. Each sub-frequency channel are divided into time slots by TDMA. Figure 10 demonstrates the network model or structure of ReMAC.
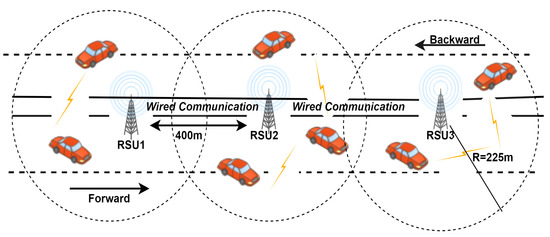
Figure 10.
Network model of ReMAC [87].
The separation of a guard band is chosen to be wide to minimize the channel interference. A joining network channel (JNCH) for new vehicles is used when they initially enter the network; then, the request is sent to RSU from JNCH by CSMA. The vehicle at the beginning adjusts to communicate with control channel and data channel and then sends a channel request packet to RSU by CSMA from JNCH. The RSU upon receiving VSIP [87] allocates a data channel to the vehicle and time slots from convenient channel, taking into account the moving direction of vehicles. The updates are provided in the VCAT table. When RSU receives a package present in the private network within its range, it searches for the vehicle’s information in the VCAT table. The table is updated on a regular basis and channel is allocated per the requirement. The calculation of network drop time (DT) is carried out to check whether the vehicle is dropped out of the network or still present, and the vehicles not sending heartbeats within 0.5 s are disconnected. The channel and slot allocation algorithm is based on FDMA by selecting a backward frequency band and a forward frequency band.
The protocol provides better performance in channel access rate, collision avoidance, high throughput, and minimized delay in dense city scenarios. It also improved the scalability of the network and adapted to frequent diverse topological changes. There is communication overhead (at RSUs and OBUs) along with high energy consumption that need to be optimized.
4.5.2. QCH MAC
The QoS-aware centralized hybrid protocol avoids collision and provides QoS in terms of transmission delays, throughput of the network, and packet delivery. The protocol combines an extended version of EDCA and TDMA. The transmission of safety-based messages is prioritized based on slot scheduling mechanism by RSUs. The access time is divided into two periods: the transmission and reservation periods. The transmission period uses time slots for scheduling, and the reservation period is used only by new vehicles to reserve the slot as soon as it enters the traffic scenario.
Safety and non-safety messages are treated differently; safety messages are considered higher priority, denoted as CL1, than non-safety messages, denoted as CL2 [88]. The vehicles that enter the transmission initially sense the channel and wait for the medium to become free for transmitting. If the channel is busy, the back-off mechanism is used to prevent collision. Second, after reservation of the slot, the vehicles enter the transmission period and are ready to transmit. The mechanism is depicted in Figure 11.
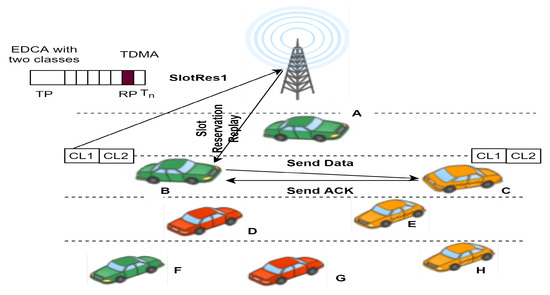
Figure 11.
Access mechanism of QCH MAC [88].
The major demerit is that the protocol does not deal with hidden terminal problem and throughput can still be improved using optimized scheduling.
4.5.3. TSGS MAC
A Transmission Scheduling Greedy Search (TSGS) algorithm provides a contention-based scheduling mechanism with less time complexity. The algorithm is based on setting a time for each transmission with CSMA/CA. By minimizing the overlap of transmission, the number of collisions is reduced, thereby minimizing the probability of activation of the back-off timer.
The implementation of TSGS provides an optimal time slot for connection, thereby providing better packet delivery ratio. The major demerit is the protocol designed is RSU centric, so there is communication overhead on RSU. The protocol does not address hidden terminal problem and scalability when the number of vehicles increases in the network.
4.6. Cooperative Single-Channel MAC Protocols
It basically deals with packet relay from the source to destination in an cooperative way. It improves the reliability of transmission and the throughput of channels.
4.6.1. CoMACAV
Cooperative MAC was proposed for autonomous vehicles to provide high network throughput. There are three modes of data transmission on which the protocol works. These are direct transmission (DT), cooperative relaying (CR), and multi-hop relaying (MHR). The main objective of this protocol is to increase throughput by selecting the optimal value of relay (R) produced by the SNR concept. The DT (RTS/CTS) and CR modes of transmission are implemented when nodes are present in the same network. In contrast, the MHR mode is implemented when nodes are in different networks. New control packets such as RRTS, RH, RRR, RCR, and RACK are introduced and depicted in Figure 12.
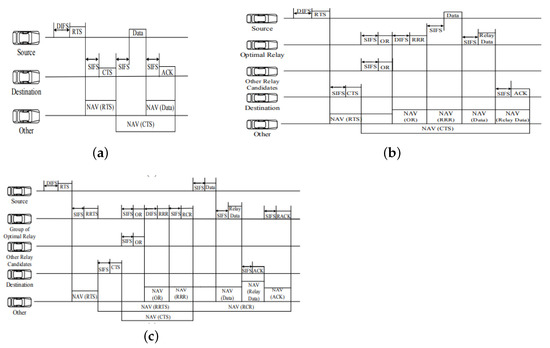
Figure 12.
Mechanism of packet exchange: (a) DT mode, (b) CR mode, and (c) MHR mode [89].
All neighboring nodes through RTS/CTS know the SNR of both source and destination nodes. Thus, neighboring nodes that are free then broadcast optimal relays. The node with the highest SNR becomes the optimal relay node and sends RRR to both the source and destination. This increases the reliability of transmission. The analysis is performed through the Markov model. The demerit of this protocol is a delay in transmission due to collision.
4.6.2. CRMAC
A cooperative-based protocol is proposed, where the three types of data transmission modes employed are direct transmission, cooperative relaying, and multi-hop relaying to achieve good throughput. Cooperative communication is performed via optimal relay selection. The RTS/CTS mechanism is used in a direct transmission (DT) mode. In the cooperative relay (CR) mode, all nodes know the sender and receiver SNR information (nodes with higher SNRs are chosen). The sender sends data to the optimal relay and then optimal relay sends it to the destination. If the sender does not receive any ACK after being sent by a short inter-frame space (SIFS) sender, the relay re-transmits the data to the destination. Nodes transmit with an interval of dynamic short-frame space (DIFS). Upon receiving a RACK, a sender knows that the transmission was successful. The mechanism of exchange for the packet is depicted in Figure 13.
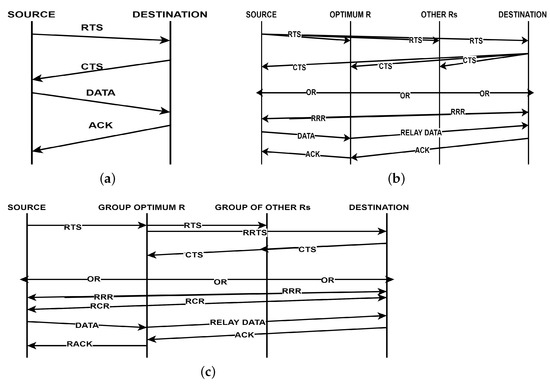
Figure 13.
Mechanism of packet exchange: (a) DT mode, (b) CR mode, and (c) MHR mode [90].
It is basically a relay selection algorithm proposed to select the optimal relay based on the highest SNR among nodes. A performance analysis was performed based on the probability calculation, average transmission time, and Markov-Model used for analysis of the result. The protocol provides enhanced throughput and efficient communication. The demerit of this protocol is the lack of performance analysis on collision avoidance, power consumption, delay factors for real-time applications, and efficient use of channels.
4.6.3. UAV Relay
The unmanned aerial vehicle-based MAC protocol was proposed for performance enhancement using a relay strategy. It improves the efficiency of communication hampered by interference or jammers at RSUs. UAVs use specific relay strategies to send messages from OBUs to RSUs. The Nash equilibria strategy was implemented, and UAV relay was optimized based on transmission cost and a UAV channel model. A hotbooting policy hill climbing (PHC) mechanism (a reinforcement learning technique) was used in the UAV relay strategy to resist jamming signals. The implementation of the network model was based on the calculation of bit error rate (BER) and SINR. Anti-jamming transmission stochastic game strategy (an extended work of [91]) was used depending on the quality of the channels and BER; this strategy minimizes the power consumption by making decision to choose the relay and whether to transmit. Dynamic anti-jamming game with the hotbooting PHC-based relay strategy was used to formulate the interaction between UAVs and jammers [92], determined the jamming power, and selected the relay based on the state of the system.
The drawback of this protocol is communication and computation overhead. Highly mobile nodes and dense scenarios are not analyzed for this mechanism.
4.7. Cooperative Multi-Channel MAC Protocols
In this type MAC protocol, the capabilities of multiple channels and cooperative communications are integrated for performance enhancement at the MAC layer.
4.7.1. OEC MAC
A novel OFDMA-based efficient cooperative (OEC) MAC protocol was proposed by providing efficient sub-carrier channel assignments and access mechanisms. The concept of OFDMA was introduced to handle the delay and collision problem in high-density traffic, which could not be overcome by simple CSMA/CA. ACK, CRM, and CAM are used for safety messages (sm) and CWSA for non-safety messages (nsm). ACK is assigned for sm: if no acknowledgment is received, then there is no packet transmission; then, for successful delivery, the packets need to send with cooperative communication (broadcast CRM). This mechanism provides a reliable transmission broadcast service. A node with higher SINR, transmission rate, and channel condition sends back CAM, and the optimal relay is selected from nodes sending CAM. Once ORM selects the optimal relay, other nodes are held back from sending CAM. For the delivery of non-safety messages, WAVE communicates with periodic broadcast of WAVE service advertisement (WSA). If the relay node has better channel conditions and SINR, CWSA, which consists of the relay information, WSA information, and channel information, is broadcast. The optimal relay is chosen after receiving CWSA by broadcasting ORM. Lastly, the destination on receiving ORM from the source activates the SCH. For channel access, the data transmission occurs on slots allocated for a duration of DIFS. For the DIFS time, if the channel is idle, then the back-off scheme is applied based on the contention window size. A third-party handshake mechanism is employed for source, destination, and relay for both sm and nsm.
This protocol provides successful probability of transmission and collision. Hence, a high throughput, high packet delivery ratio, and minimized latency are achieved. The major shortcoming is that unsaturated network conditions are not considered. Channel fading conditions and other effects of signals such as capture effect are also not considered in performance analysis.
4.7.2. RECV-MAC
Reliable and efficient cooperative (RECV) MAC is a novel protocol proposed to provide efficient communication with high throughput. The protocol provides better packet dropping rates (PDRs) and lowers delay for safety messages. CSMA/CA is used with random access as in IEEE 802.11p. Modified control messages are used to provide cooperative communication. Negative acknowledgement (NACK) and keen to help (KTH) messages are introduced for exchange of safety messages. Cooperative wave service advertisement (CWSA) and willing to involve (WTI) are introduced for non-safety messages. Packets transmit NACK; if the node hears broadcasts but does not receive a notification in short inter-frame space (SIFS), there is failed transmission. These packets are sent through cooperative transmission to improve the transmission reliability. After NACK, the nodes with improved transmission rate, SINR, and proper channel condition transmit KTH. Upon receiving KTH, an optimal helper node (having optimal SINR) can be chosen among neighboring nodes. Basic service set (BSS) is used for non-safety message transmission, with a period broadcasting WSA in the CCH interval. The receiver sends WTI, and when a neighbor node has better SINR and channel conditions, it sends CWSA to the sender. The node with optimal SINR is chosen as the optimal WAVE helper node; after hearing the selector helper message (SHM), other nodes suspend cooperation with WTI. The optimal helper joins BSS, and thus, the sender transmits through the optimal helper to the receiver.
RECV MAC provides an optimal helper selection mechanism for reliable data transmission. However, the performance of the protocol in unsaturated conditions and in high vehicle density is not analyzed. The power consumption factor is not taken into consideration.
4.7.3. OCA-MAC
The optimal cooperative ad hoc (OCA) MAC protocol was proposed to provide cooperative communication to improve transmission probability. The optimal cooperative node was chosen based on TDMA for successful transmission. A probabilistic model was designed to know the number of optimal cooperative nodes in each channel. The methods of cooperative forwarding and optimal node determination were used for reliable communication. The cooperative transmission mechanism was employed when the transmission rates go below the threshold. The node broadcast control frame periodically contains information about it such as node ID, neighbor node ID, and slot reserved. Choosing an optimal cooperative node is based on the distance calculated between the potential cooperative node and the mid-point between the sender and receiver, thereby increasing the network throughput. The node with a minimum value of distance calculated is chosen as the optimal cooperative node. To analyze the number of cooperative nodes, a probabilistic mathematical model was designed. In this model, the time slots are divided into free time slots, successful time slots, and failed time slots.
The protocol provides QoS in terms of successful transmission rate, transmission delay, and transmission in highway scenarios. Since the protocol does not consider the dynamic topology scenario, there might be performance degradation in dynamic scenarios.
4.7.4. CT MAC
The proposed cooperative TDMA (CT) MAC uses a relay strategy to improve communication efficiency hampered by interference or jammers at RSUs. It uses a slot sharing scheme; the status information of each node is present in the MAC header. The slots are shared and prioritized by analyzing the slot state. Every time slot is partitioned into two CWs; DSRC specifies the payload for safety application and a slot information (SI) header. The carrier signal sensed by vehicles at each time slot is used to detect the state of the slot. This slot is again divided into three states: first, check the packet is correctly received; second, when the packet is received; and third, when no packet is received and SINR is low (channel is idle). The slot is prioritized by a value accumulated and received during a frame, containing the data generated by the neighbors. The category of the channel sensed that is idle, busy, or noisy is defined. An overview of CTMAC is shown in Figure 14.
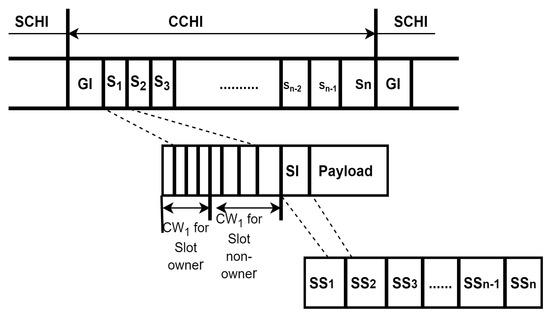
Figure 14.
Overview of CT MAC [90].
The stability of the network is maintained by prioritizing those vehicles occupying the slot through a carrier sensing algorithm. The proposed work eliminates merger and access collision using the back-off method in the slots. Priority-based slot allocation avoids communication interference. However, the reliability and throughput metrics are not analyzed in dense and sparse scenarios.
4.7.5. ST MAC
The spatio-temporal (ST) coordination-based MAC protocol for VANETs is designed to provide contention-free channel access for safety message exchange. It provides reliable and efficient data transmission for safe driving. Here, transmission occurs by line-of-collision graph based on a set-cover algorithm [93] so that vehicles transmit in the same slot but do not collide due to directional antennas and transmission power control. An optimization-based contention period scheme is proposed for vehicle registration on RSUs to minimize channel utilization. A hybrid MAC is designed by coordination of spatio-temporal characteristics based on PCF for registration of vehicles. This allocates slots and disseminates emergency messages from RSUs to vehicles based on DCF for safety and emergency messages via V2V communication by WPCF [94].
The proposed work provides better end-to-end delays and packet delivery ratio and less frame access delays. However, it does not handle non-safety-based applications, and the communication efficiency in highway scenarios for safe driving is not discussed. Since it is RSU centric, there is an overhead on RSU.
4.8. Cluster-Based Single-Channel MAC Protocols
A cluster head (CH) is chosen from a group of vehicles that is responsible for channel access, allocation of time slots, and resource management. Clusters provide stable communication and extend the lifetime of communication links.
4.8.1. PDMAC
Priority-based enhanced TDMA MAC was designed to prevent accidents via in-time delivery of time-critical safety messages and non-safety messages using the priority assignment technique. The protocol provides better clock synchronization, reduced message loss, latency, and improved throughput in the network. This protocol was based on an intra-cluster V2V model on two-directional highways and inter-cluster clock synchronization to reduce overhead and to improve channel utilization. It describes a three-tier priority assignment method for better delivery of warning messages estimating the type of message, severity level, and direction components. A single bit field called Validate_timer in the message header is used to check whether the timer is synchronized. The node’s timer is considered synchronized when Validate_timer = 1 and, hence, validated. Conversely, the clock needs synchronization when Validate_timer = 0 and Validate_timer remains invalid for all other nodes on the network. Validate_timer is set the default value of 0 to make synchronization of clock mandatory for each and every node upon entering the highway [95]. The clustering mechanism of PD MAC in a bidirectional scenario is depicted in Figure 15.
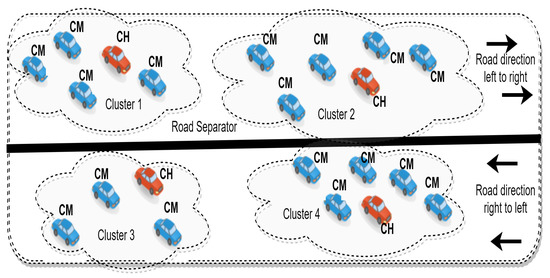
Figure 15.
Clustering in PDMAC in the bidirectional traffic scenario [95].
The protocol’s performance in urban or city scenarios (dense and highly mobile networks) shows less efficiency.
4.8.2. Enhanced IEEE 802.15.4
The proposal of a V2R protocol based on the dynamic window algorithm (DWA) improves delay and throughput using a back-off scheme and the IEEE 802.15.4 standard employed for low power. Short-range communication is used in the PHY and MAC layer by CSMA/CA for contention access. A change in the binary exponent back-off (BEB) is implemented for improved performance. The frame structure known as super-frame is divided into two active parts containing a contention-free period (CFP) and a contention-based period (CBP), the inactive part, which is optional. The main objective of DWA is to minimize the delay via an extended back-off period in an exponential back-off scheme. The nodes have queues and are arranged in the form of a cluster. The nodes with empty queues have low priority and nodes with full queues have high priority, i.e., the less frames in the node queue, the smaller the exponential window size. The size of the cluster is also taken into consideration: the more nodes in the cluster, the higher the probability of collision.
According to the simulation results, the DWA algorithm provides better results even when the cluster size is increased as it structures a balance between the nodes in the cluster and frames in the queues. Future enhancements include switching off at a threshold of different values between BEB and DWA and making the model energy-efficient by minimizing the power requirement with a collision avoidance scheme.
4.9. Cluster-Based Multi-Channel MAC Protocols
Basically, the cluster-based multi-channel MAC protocols are proposed to minimize channel contention, to increase network capacity by reusing resources, to provide fair access to channels within the cluster, and to efficiently control the network topology.
4.9.1. CB MAC
Cluster-based MAC eliminates the hidden terminal problem for non-safety applications and efficient hand-over (shifting of data sessions from one base station to another). Each cluster head assigns bandwidths to the members of the cluster for efficient communication. As IEEE 802.11 is not cluster-based, the control packets are modified in CB-MAC with new control packets containing RTCF (request to cluster formation), ReTCl (registration to cluster), RCLM (request to cluster merging) [96]. For cluster member, a vehicle RTCF message is broadcast in the network; after any cluster head has received the message, it transmits ReTCI, which includes a cluster member ID(CM-ID), a cluster ID (Cl-ID), and a cluster head address (CHA). Then, the cluster head updates the cluster member list and broadcasts it to all cluster members. If the new vehicle that wants to enter a cluster does not receive any ReTCI, it forms a new cluster and has to be the cluster head itself. If a CH does not receive any CTS when it has sends an RTS during the SIFS time interval, it assumes that the cluster member is out of the range of transmission and deletes it from the cluster member list. Then, again, the updated information is broadcast to all other members. A CH with a more significant number of cluster members becomes the CH.
This protocol is contention-free and provides high throughput, better PDR, and better resource utilization. When the number of vehicles increases rapidly, there might be chances of collision, leading to less throughput and a reduction in system performance.
4.9.2. LMMC
A multi-channel MAC based on learning automata is designed for optimized utilization of channel access for VANET applications. The multi-channel scheme with the use of a radio transceiver and a smart model of learning automaton is used to learn about the cluster members’ traffic parameters. Nodes are equipped with GPS, unlike other MACs that use CCH for safety applications and SCH for both safety and non-safety applications. The learning automaton model is implemented for the polling of cluster members to find out its parameter using the cluster head, with dynamic TDMA allocation of resources within the cluster [97].
The protocol provides better PDR for safety applications in real-time scenarios. It provides proper bandwidth and channel access utilization and, thus, increases throughput in the network. Still, there are not many analyses on QoS for non-safety applications. The protocol does not deal with best-effort, video, background, and other non-safety-based services.
4.9.3. ACB MAC
It is a novel MAC protocol based on a clustering MAC with a blockchain framework providing reliable and secure communication. It uses the decentralized blockchain concept for vehicle authentication and registration before they communicate. The control packet of IEEE 802.11 was modified for handling hidden nodes, packet drop, and packet overloading on channel access. Cluster-based concepts provide a faster and efficient method of communication. The messages are divided into safety and non-safety messages and groups the vehicles as general vehicles and emergency vehicles. Priorities are set for general and emergency vehicles so that there is less delay on transmission of safety messages.
The protocol minimizes computational as well as storage overheads by efficient blockchain implementation. The protocol can be enhanced for different attacks and threats with reputation management, including more security features. A clustering based on the SDN architecture can be implemented in future enhancement for better network performance.
4.10. Virtual Token Based
This approach allocates different time slots to vehicles, thereby minimizing collision and providing efficient channel access. The protocol also provides minimized propagation delay with high throughput.
Reliable MAC
The reliable MAC protocol scheme was proposed to avoid collision in high-density VANET scenarios via proper channel access. An adaptive byte-level HARQ was used for error control and to provide reliable communication. Via this methodology, the bit error rate and burst bit rate of the channel were calculated [98]. The frame error control redundancy size was checked, which was added to the MAC frame structure; along with the FEC bit, a checksum calculator was also added to the MAC frame. Frame segmentation and fragmentation were performed, and each frame consisted of MAC service data units. The virtual token approach performs the packet delivery mechanism (allocates each node with the specified channel access time) and forward node selection approach (selects efficient forwarders for message broadcasting) for on-time delivery of safety messages. The node that wants to transmit data initiates the virtual token formation containing the nodes present in its transmission range. The node initiator keeps track of nodes leaving and entering the token ring. An efficient forwarder node is selected that restricts other nodes to broadcast messages, thus avoiding collision.
The use of AB-HARQ shows better error recovery probability even upon increasing the channel error. The reliable MAC provides better throughput and packet delivery ratio. Hidden terminals, energy consumption, and communication overheads are not addressed or analyzed, turning out to be the major demerits.
4.11. Random Selection Based
The time slot is accessed randomly; the channel is split up into frames and further divided into slots. This mechanism provides better channel utilization and minimizes collision. Some slots may be left idle and may be overloaded, leading to resource wastage and collision.
4.11.1. OGC MAC
A novel OFDM MAC based on contention is proposed for reliable, efficient, fast, collision-free resource block allocation. The protocol reduces the use of contention windows (CWs) and improves resource allocation efficiency by proposing a new CCH architecture. Multi-carrier burst contention (MCBC) [99] inspired its creation, which reduces the size of CWs and reduces resource wastage by sequential channel allocation with the traditional TDMA approach. The bandwidth of CCH is divided into sub-channels by OFDM. A group contention strategy is proposed to overcome resource wastage along with a greedy approach. The RBs are chosen using the RB selection policy [100], where RBs are randomly selected from the groups formed from the subdivision of frame, to minimize collision when broadcasting a beacon to one-hop neighbor. A MAC announcement is initiated before a beacon is transmitted and embedded in the beacon. The RBs with a collision flag are considered collisions that occurred in the previous frame and are released. The nodes know the status of their two-hop neighbor and broadcast accordingly.
The protocol improves throughput by eliminating the hidden terminal problem and by avoiding merger and access collision. By proper resource utilization, resource wastage is minimized. The major disadvantage of this protocol is CW overload, causing delays in packet delivery. The network scalability in dense scenarios is not considered.
4.11.2. Self-Sorting-Based MAC
This protocol is based on self-sorting the channel allocation based on TDMA. It provides collision-free transmission with reduced packet loss and delays in message delivery in even dense scenarios. The un-ordered random access is altered by ordered self-sorting-based access. Vehicles access channels in a queue via a TDMA-based mechanism. Nodes in the same queue compete to access the channel to minimize access collision via random channel access. The self-sorting process occurs in three steps: self-sorting, channel reservation, and data transmission [101]. Figure 16 depicts the mechanism of the protocol for sorting the message in queue, reservation of the channel, and the transmission of data.
Figure 16.
Mechanism of self-sorting [101].
As soon as the capacity of a queue reaches its threshold, the members or nodes of the queue start to transmit in the channel in the order in which they joined the queue. An M/G/1/∞ queuing model was used in the analysis for the computation of average service time, delay, and packet delivery ratio. Markov chain modeling was used to estimate the probability of queuing successfully.
The protocol overcomes the overhead of maintaining a schedule table, unlike other slotted protocols, as the nodes are self-sorted. It effectively handles delays and PDR. However, adapting the dynamic scenarios, handling hidden terminals, and various other requirements of delay and PDR are still challenges. No analysis is given based on merging collision.
An extensive study of the MAC layer protocols for VANETs was conducted in the survey under various categories. These protocols aim to build an efficient mechanism for data dissemination. There are, however, numerous issues to be addressed in the future. The future directions include but are not limited to prioritizing safety messages for guaranteed reliability; ensuring fairness, in which a robust MAC protocol should also meet different QoS requirements, prioritizing services; handling network loads with dynamic channel access and proper channel utilization not limited to a single CCH; and minimizing interference by adopting a multi-channel access mechanism, where a centralized MAC protocol should be implemented under the premise of unreliable link and high vehicle mobility since RSUs and CHs can support direct multi-hop transmissions by adjusting to high dynamic networks. To conclude, the research direction includes designing an optimized MAC scheme providing QoS, adapting appropriate channel mechanisms based on the scenario (dense/sparse), and adapting clustering mechanisms for efficiency.
A chronological diagram of the above discussed MAC protocols is depicted in Figure 17, and a summary of the overall comparison is shown in Table 3.
Figure 17.
Chronological diagram of MAC protocols survey.

Table 3.
Comparison of MAC protocols.
5. Future Scope, Open Challenges, and Research Direction
Being one of the promising technologies for ITS, VANETs provide safety, efficient driving, infotainment services, pollution-free driving, and a pleasant environment for drivers. To provide these services in smart vehicles based on IoT, Internet of Vehicles (IoVs) are designed. Handling real-time events efficiently and reliably for safety applications is a foremost challenge. Many challenges have already been overcome by using new technologies such as edge cloud-computing (ECC) for resource virtualization, IoV for smart communication, SDN for network virtualization, and clustering for efficient communication. However, problems still persist and give a thorough layout for future scopes and research directions alike such as designing a low latency protocol for real-time safety applications. Providing a coherent connection among vehicles is essential to maintaining efficient and reliable communication of vehicles but is a challenge due to the dynamic environment of VANETs. Nonetheless, providing high bandwidth is necessary for streaming and other non-safety 3D-based, high-dimensional applications such as navigation systems, reading of maps, games, video streaming, etc. However, bandwidth is mostly impeded due to the dynamic VANET topology. Hence, designing an efficient MAC for VANETs is necessary for both safety-critical and non-safety critical applications.
Congestion control in the network is an essential factor for providing collision-free communication and high network throughput since a long CSMA/CA has been used for congestion control and, in recent research, many modifications have also proposed efficient algorithms for congestion control. Improved channel utilization with continuous and alternate channel access and broadcast safety messages effectively is yet another challenge and future scope. Hidden and exposed node problems should be dealt with efficiently to improve throughput, scalability, and network performance. Time-synchronization among vehicles is also an important issue that needs to be maintained to provide collision-free transmission in multi-channel scenarios that provide proper time slots to the nodes. Additionally, it offers optimized performance and load-balancing in terms of channel access. The minimization of communication overhead opens discussion on the implementation of centralized and distributed protocols. Centralized protocols suffer from overhead, latency, scalability, and flexibility, whereas the decentralized approach is not easily maintained and has a high cost.
6. Conclusions
The objective of this survey was to obtain insight into various MAC protocols designed for VANETs. This paper presents a brief introduction to VANETs along with its challenges and applications. The protocols are classified into distributed, centralized, cluster-based, random-access, and virtual token-based and sub-classified into single-channel and multi-channel MAC protocols. The identified primary challenges in the design of MAC protocol are latency, dynamic topology, mobility of nodes, reliability, and bandwidth utilization. This paper also briefly elaborates on various DSRC-based and cellular-based networks, giving a gist of the ITS-G5 standard, LTE, 5G, and C-V2X communication. Furthermore, Table 3 presents a structured, detailed review of recent MAC protocols along with their mechanisms, objectives, comparisons, and classifications.
An efficient MAC design is of utmost importance to providing delay-intolerant and reliable messaging. Data packets are prioritized based on safety and non-safety applications and disseminated based on priority. With multi-channel protocols, multiple channels can handle interference caused by channel access, resulting in better channel utilization. A multi-channel clustering mechanism with dynamic interval-based channel access is an open challenge for MAC protocols to provide QoS and to improve network performance. Technologies such as SDN, which separates the data plane from the control plane, have also emerged to eliminate traffic congestion. Edge-computing vehicles, VANETs based on the Internet of Things, and cloud-based VANETs are all emerging technologies for reliable and efficient transportation. Multi-transceivers, multi-channel operations, and multiple inputs and outputs (MIMO) are some methods for enhancing the network throughput. Future work includes experimental analyses of the MAC protocols in VANET in terms of QoS metrics such as throughput, packet reception ratio, energy consumption, and performance improvements using an efficient MAC design.
Author Contributions
This work was completed with contributions from all the authors. conceptualization, L.H. and A.K.; methodology, L.H. and A.K.; software, L.H., B.P.N. and A.K.; validation, formal analysis, data curation and writing—original draft preparation, L.H., A.K., and G.G.M.N.A.; writing—review and editing, L.H., A.K., G.G.M.N.A. and P.H.J.C.; visualization, L.H., and B.P.N.; funding acquisition, P.H.J.C. All authors did edit, review and improve the manuscript. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Not applicable, the study does not report any data.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| Acronym | Description | Acronym | Description |
| 3GPP | Third Generation Partnership Project | AB HARQ | Adaptive Byte-Level Hybrid Automatic Repeat reQuest |
| ABC MAC | Adaptive Beacon Control MAC | AC | Access Category |
| ACB MAC | Authentication Cluster-Based MAC | ACFM | Adaptive Collision-Free MAC |
| ACK | Acknowledgment | AHT MAC | Adaptive High-Throughput MAC |
| ASAS | Adaptive TDMA Slot Assignment Strategy | AVeMAC | Adaptive Vehicular MAC |
| BB MAC | Black Burst MAC | BEB | Binary Exponent Back-Off |
| BER | Bit Error Rate | BFP | Broadcast Feedback Phase |
| BSS | Basic Service Set | BT | Broadcast Table |
| BTMA | Busy Tone Multiple Access | CAC MAC | Cellular Automata to Form CAR MAC |
| CAH MAC | Cooperative Ad Hoc MAC | CAM | Cooperation Acceptance Message |
| CAP | Contention Access Phase | CaSSaM | Context Aware System for Safety Messages |
| CB MAC | Cluster-Based MAC | CBCH | Contention-Based Sub-Channel |
| CBP | Contention-Based Period | CBR | Channel Busy Rate |
| CCH | Control Channel | CDMA | Code Division Multiple Access |
| CF MAC | Collision-Free MAC | CFP | Contention-Free Phase |
| CFP | Contention-Free Period | CFR MAC | Collision-Free Reservation MAC |
| CH | Cluster Head | CI | Control Interval |
| CoMACAV | Cooperative MAC for Autonomous Vehicle | CR | Cooperative Relaying |
| CRM | Cooperation Request Message | CRMAC | Cooperative Relay-Based MAC |
| CRP | Channel Request Packet | CSMA/CA | Carrier Sense Multiple Access/Collision Avoidance |
| CT MAC | Cooperative TDMA MAC | CTS | Clear To Send |
| C-V2X | Cellular-Vehicle-to-Everything | CW | Contention Window |
| CWSA | Cooperative Wave Service Advertisement | CWSA | Cooperative Wave Service Advertisement |
| D2D | Device-to-Device | DBCC | Distributed Beacon Congestion Control |
| DBRA | Distributed Beacon Rate Adaptive | DCF | Distributed Coordination Function |
| DIFS | Dynamic Inter-Frame Spacing | DMMAC | Dedicated Multi-Channel MAC |
| DNS | Direct Neighbor Set | DSRC | Dedicated Short-Range Communication |
| DT | Direct Transmission | DT MAC | Distributed TDMA MAC |
| DTA | Data Transmission Acceptance | DTB MAC | Dynamic Token-Based MAC |
| DTR | Data Transmission Request | DTSS | Distributed Time Slot Sharing |
| DWA | Dynamic-Window Algorithm | EDCA | Enhanced Distributed Channel Access |
| eRTS-SA | Request Transmission Split- Slotted ALOHA | ETCM | Enhanced TDMA Cluster-Based MAC |
| ETSI | European Telecommunications Standards Institute | FCC | Federal Communication Commission |
| FDMA | Frequency Division Multiple Access | FI | Frame Information |
| GPS | Global Positioning System | HBCH | Heart-Beat Channel |
| HC MAC | Hybrid CSMA MAC | HER MAC | Hybrid Efficient and Reliable MAC |
| I MAC | Improvised MAC | IBT | Initial Broadcast Table |
| INS | Indirect Neighbor Set | IR | Interference Range |
| ITS | Intelligent Transportation System | JNCH | Joining Network Channel |
| KTH | Keen To Help | LIMERIC | Linear Message Rate Control Algorithm |
| LMA | Location and Mobile Aware MAC | LMMC | Learning Automata Multi-Channel MAC |
| LTE | Long-Term Evolution | MAC | Media Access Control |
| MACA | Multiple Access with Collision Avoidance | MACAW | Multiple Access with Collision Avoidance Wireless |
| MANET | Mobile Ad Hoc Network | MAP | Medium Access for PLNC (Physical Layer Network Coding) |
| mBS | Micro Base Station | MCBC | Multi-Carrier Burst Contention |
| MC-MAC | Multi-Code Media Access Control | MEC | Multi-Access Edge Computing |
| MHR | Multi-Hop Relaying | MoMAC | Mobility-Aware MAC |
| NA MAC | Neighbor Association-Based MAC | NACK | Non-Acknowledgement |
| NAV | Network Allocation Vector | NEMO | Network Mobility |
| NC-MAC | Network Coding MAC | OBU | On-Board Unit |
| OCA MAC | Optimal Cooperative Ad Hoc MAC | OCC | Optimal Orthogonal Codes |
| OCT MAC | Optical CDMA with TDMA MAC | OEC MAC | OFDMA-Based Efficient Cooperative MAC |
| OFDMA | Orthogonal Frequency Division Multiplexing Access | OGC MAC | OFDM-Based Group Contention MAC |
| OppCast | Opportunistic Broadcast | OR | Offer to Relay |
| ORM | Optimal Relay Message | PCF | Point-Coordination Function |
| PDMAC | Priority-Based Enhanced TDMA MAC | ProSe | Proximity Service |
| PHC | Policy Hill Climbing | PLNC | Physical Layer Network Coding |
| PPS | Pulse Per Second | PTMAC | Prediction-Based TDMA MAC |
| QCH MAC | QoS-Aware Centralized Hybrid | QoS | Quality of Service |
| RACK | Relay Acknowledgement | RCLM | Request to Cluster Merging |
| RCR | Relay Clear to Relay | RECV MAC | Reliable and Efficient Cooperative MAC |
| Relia MAC | Reliable MAC | ReMAC | Reliable MAC |
| ReTCL | Registration To CLuster | RIFF | Random Index Fit First |
| RP | Reservation Period | RRR | Relay Ready to Relay |
| RRTS | Relay Request To Send | RSU | Road-Side Unit |
| RSUHB | RSU Heart-Beat | RTCF | Request To Cluster Formation |
| RTS | Request To Send | SAFE MAC | Speed Aware Fairness-Enabled MAC |
| SB-SPS | Sensing Based Semi-Persistent Scheduling | SCCH | Scheduling Channel |
| SCH | Service Channel | SCHI | Service Channel Interval |
| SCMAC | Slotted Contention-Based MAC | SDMA | Spatial Division Multiple Access |
| SDN | Software Defined Network | SHM | Selector Helper Message |
| SIC | Successive Interference Cancellation | SIFS | Short Inter-Frame Space |
| SINR | Signal to Interference Noise Ratio | SNR | Signal-to-Noise Ratio |
| SOFT MAC | Space-Orthogonal Frequency Time MAC | SOMMAC | Self-Organizing Multi-Channel MAC |
| SR MAC | Simple Relay-Enabled MAC | SRBs | Service Resource Blocks |
| SS MAC | Slot Sharing MAC | ST MAC | spatio-temporal Coordination-Based MAC |
| STC | spatio-temporal Coordination | TC MAC | TDMA Cluster-Based MAC |
| TCG MAC | TDMA with CSMA MAC | TDMA | Time Division Multiple Access |
| TP | Transmission Period | TR | Transmission Range |
| TSGS MAC | Transmission Scheduling Greedy Search | UAV MAC | Unmanned Aerial Vehicle MAC |
| V2I | Vehicle-to-Infrastructure Communication | V2V | Vehicle-to-Vehicle Communication |
| VANET | Vehicular Ad Hoc Network | VAT MAC | Novel Adaptive TDMA MAC |
| VCAT | Vehicle Channel Allocation Table | VHB | Vehicle Heart-Beat |
| VoLTE | Voice-Over Long-Term Evolution | VSIP | Vehicular Specific Packet type |
| WAVE | Wireless Access in Vehicular Environment | WPCF | WAVE PCF |
| WSA | WAVE Service Advertisement | WTI | Willing To Involve |
| WTS | Want To Send |
References
- Maalej, Y.; Abderrahim, A.; Guizani, M.; Hamdaoui, B.; Balti, E. Advanced Activity-Aware Multi-channel Operations 1609.4 in VANETs for Vehicular Clouds. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; Volume 4, pp. 142–149. [Google Scholar]
- Kakarla, J.; Sathya, S.S. A Survey and Qualitative Analysis of Multi-channel MAC Protocols for VANET. Int. J. Comput. Appl. 2012, 38, 0975-8887. [Google Scholar] [CrossRef]
- AlMheiri, M.S.; AlQamzi, S.H. MANETs and VANETs Clustering Algorithms: A Survey. In Proceedings of the 8th IEEE GCC Conference and Exhibition, Muscat, Oman, 1–4 February 2015; pp. 1–4. [Google Scholar]
- Gillani, S.; Shah, A.P.; Qayyum, A.; Hasbullah, B.H. MAC Layer Challenges and Proposed Protocols for Vehicular Adhoc Networks. Adv. Intell. Syst. Comput. 2015, 306, 3–13. [Google Scholar] [CrossRef]
- Sheikh, S.M.; Liang, J. A Comprehensive Survey on VANET Security Services in Traffic Management System. Wirel. Commun. Mob. Comput. 2019, 2019, 2423915. [Google Scholar] [CrossRef] [Green Version]
- Sheikh, S.M.; Liang, J.; Wang, W. A Survey of Security Services, Attacks, and Applications for Vehicular Ad Hoc Networks (VANETs). Sensors 2019, 19, 3589. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Kelarestaghi, B.K.; Mahsa Foruhandeh, M.; Heaslip, K.; Gerdes, R. Survey on Vehicular Ad Hoc Networks and Its Access Technologies Security Vulnerabilities and Countermeasures. arXiv 2019, arXiv:1903.01541. [Google Scholar]
- Dhamgaye, A.; Chavhan, N. Survey on security challenges in VANET. Int. J. Comput. Sci. Netw. 2013, 2, 2277–5420. [Google Scholar]
- Fuentes, D.J.; Manzano, G.L.; González-Tablas, I.A.; Blasco, J. Security models in vehicular ad-hoc networks: A survey. IETE Tech. Rev. 2014, 31, 47–64. [Google Scholar] [CrossRef]
- Hadded, M.; Muhlethaler, P.; Laouiti, A.; Zagrouba, R.; Saidane, A.L. TDMA-based MAC protocols for vehicular ad hoc networks: A survey, qualitative analysis, and open research issues. IEEE Commun. Surv. Tutor 2015, 17, 2461–2492. [Google Scholar] [CrossRef] [Green Version]
- Mohammed, A.M.; Al-Daraiseh, A.A. Toward secure vehicular adhoc networks: A survey. IETE Tech. Rev. 2012, 29, 80–89. [Google Scholar]
- Choi, J.; Marojevic, V.; Carl, B.; Dietrich, B.C.; Reed, H.J.; Ahn, S. Survey of Spectrum Regulation for Intelligent Transportation Systems. IEEE Access 2020, 8, 140145–140160. [Google Scholar] [CrossRef]
- Nguyen, V.; Kim, T.T.O.; Pham, C.; Oo, Z.T.; Tran, H.T.; Hong, S.C.; Huh, N.E. A survey on adaptive multi-channel MAC protocols in VANETs using Markov models. IEEE Access 2018, 6, 16493–16514. [Google Scholar] [CrossRef]
- Khan, A.U.; Lee, S.S. Multi-Layer Problems and Solutions in VANETs: A Review. Electronics 2019, 8, 204. [Google Scholar] [CrossRef] [Green Version]
- Teixeira, F.A.; Silva, V.F.; Leoni, J.L.; Macedo, D.F.; Nogueira, J.M. Vehicular networks using the IEEE 802.11p standard: An experimental analysis. Veh. Commun. 2014, 1, 91–96. [Google Scholar] [CrossRef]
- Kiela, K.; Barzdenas, V.; Jurgo, M.; Macaitis, V.; Rafanavicius, J.; Vasjanov, A.; Kladovscikov, L.; Navickas, R. Review of V2X–IoT Standards and Frameworks for ITS Applications. Appl. Sci. 2020, 10, 4314. [Google Scholar] [CrossRef]
- Kim, J.W.; Kim, J.W.; Jeon, D.K. A Cooperative Communication Protocol for QoS Provisioning in IEEE 802.11p/Wave Vehicular Networks. Sensors 2018, 18, 3622. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Yao, Y.; Rao, L.; Liu, X. Performance and Reliability Analysis of IEEE 802.11p Safety Communication in a Highway Environment. IEEE Trans. Veh. Technol. 2013, 62, 4198–4212. [Google Scholar] [CrossRef]
- Nardini, G.; Virdis, A.; Campolo, C.; Molinaro, A.; Stea, G. Cellular-V2X Communications for Platooning: Design and Evaluation. Sensors 2018, 18, 1527. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Bai, F.; Krishnan, H. Reliability Analysis of DSRC Wireless Communication for Vehicle Safety Applications. In Proceedings of the IEEE Conference on Intelligent Transportation Systems—ITSC, Toronto, ON, Canada, 17–20 September 2006; pp. 355–362. [Google Scholar] [CrossRef]
- Gast, S.M. 802.11 Wireless Networks: The Definitive Guide; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2002; ISBN 9780596100520. Available online: http://196.223.158.148/bitstream/handle/123456789/2499/E302.pdf?sequence=1&isAllowed=y (accessed on 8 November 2021).
- Reddy, G.R.; Ramanathan, R. An Empirical study on MAC layer in IEEE 802.11p/ WAVE based Vehicular Ad hoc Networks. In Proceedings of the 8th International Conference On Advances in Computing & Communications (ICACC), Kochi, India, 13–15 September 2018; Volume 143, pp. 720–727. [Google Scholar] [CrossRef]
- Liu, W.; He, X.; Huang, Z.; Ji, Y. Transmission Capacity Characterization in VANETs with Enhanced Distributed Channel Access. Electronics 2019, 8, 340. [Google Scholar] [CrossRef] [Green Version]
- 3GPP Release 14. Available online: https://www.3gpp.org/release-14 (accessed on 1 September 2021).
- Chen, S.; Hu, J.; Shi, Y.; Zhao, L.; Li, W. A Vision of C-V2X: Technologies, Field Testing, and Challenges With Chinese Development. IEEE IoT J. 2020, 7, 3872–3881. [Google Scholar] [CrossRef] [Green Version]
- Katranaras, E.; Dillinger, M.; Abbas, T.; Theillaud, R.; Calvo, J.L.; Zang, Y. Standardization and Regulation. In Cellular V2X for Connected Automated Driving; John Wiley Sons, Ltd.: Hoboken, NJ, USA, 2021; Chapter 3; pp. 63–90. [Google Scholar] [CrossRef]
- McCarthy, B.; Burbano-Abril, A.; Rangel-Licea, V.; O’Driscoll, A. OpenCV2X: Modelling of the V2X Cellular Sidelink and Performance Evaluation for Aperiodic Traffic. arXiv 2021, arXiv:2103.13212. [Google Scholar]
- Noor-A-Rahim, M.; Liu, Z.; Lee, H.; Ali, G.G.M.N.; Pesch, D.; Xiao, P. A Survey on Resource Allocation in Vehicular Networks. IEEE Trans. Intell. Transp. Syst. 2020, 2020, 3019322. [Google Scholar] [CrossRef]
- Mosavat-Jahromi, H.; Li, Y.; Cai, L.; Lu, L. NC-MAC: Network Coding-based Distributed MAC Protocol for Reliable Beacon Broadcasting in V2X. In Proceedings of the GLOBECOM 2020—IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Saifuddin, M.; Zaman, M.; Toghi, B.; Fallah, Y.P.; Rao, J. Performance Analysis of Cellular-V2X with Adaptive and Selective Power Control. arXiv 2020, arXiv:2008.03453. [Google Scholar]
- Abdel Hakeem, S.A.; Hady, A.A.; Kim, H. 5G-V2X: Standardization, architecture, use cases, network-slicing, and edge-computing. Wirel. Netw. 2020, 26, 6015–6041. [Google Scholar] [CrossRef]
- Bazzi, A.; Berthet, A.O.; Campolo, C.; Masini, B.M.; Molinaro, A.; Zanella, A. On the Design of Sidelink for Cellular V2X: A Literature Review and Outlook for Future. IEEE Access 2021, 9, 97953–97980. [Google Scholar] [CrossRef]
- Boban, M.; Kousaridas, A.; Manolakis, K.; Eichinger, J.; Xu, W. Use Cases, Requirements, and Design Considerations for 5G V2X. arXiv 2017, arXiv:1712.01754. [Google Scholar]
- Garcia, M.H.C.; Molina-Galan, A.; Boban, M.; Gozalvez, J.; Coll-Perales, B.; ¸Sahin, T.; Kousaridas, A. A Tutorial on 5G NR V2X Communications. IEEE Commun. Surv. Tutor. 2021, 23, 1972–2026. [Google Scholar] [CrossRef]
- Tassi, A.; Egan, M.; Piechocki, R.J.; Nix, A. Modeling and Design of Millimeter-Wave Networks for Highway Vehicular Communication. IEEE Trans. Veh. Technol. 2017, 66, 10676–10691. [Google Scholar] [CrossRef] [Green Version]
- Singh, P.K.; Nandi, S.K.; Nandi, S. A tutorial survey on vehicular communication state of the art, and future research directions. Veh. Commun. 2019, 18, 100164. [Google Scholar] [CrossRef]
- Rebei, A.; Hadded, M.; Touati, H.; Boukhalfa, F.; Muhlethaler, P. MAC-aware Routing Protocols for Vehicular Ad Hoc Networks: A Survey. In Proceedings of the International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 17–19 September 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Shukla, N.; Katiyar, P.; Devgan, N.; Kumar, N.; Dinker, G.A. Comparison of the MAC Protocols in Vehicular Ad-Hoc Network. Int. J. Adv. Res. Electr. Electron. Instrum. Eng. 2014, 3, 6709. [Google Scholar]
- Jayaraj, V.; Hemanth, C.; Sangeetha, R.G. A survey on hybrid MAC protocols for vehicular ad-hoc networks. Veh. Commun. 2016, 6, 29–36. [Google Scholar] [CrossRef]
- Huang, J.; Li, Q.; Zhong, S.; Liu, L.; Zhong, P.; Wang, J.; Ye, J. Synthesizing Existing CSMA and TDMA Based MAC Protocols for VANETs. Sensors 2017, 17, 338. [Google Scholar] [CrossRef] [PubMed]
- Menouar, H.; Filali, F.; Lenardi, M.E. A Survey and Qualitative Analysis of MAC Protocols for Vehicular Ad Hoc Networks. IEEE Wirel. Commun. 2006, 13, 30–35. [Google Scholar] [CrossRef]
- Jurdak, R.; Lopes, V.C.; Baldi, P. A Survey, Classification and Comparative Analysis of Medium Access Control Protocols for Ad Hoc Networks. IEEE Commun. Surv. 2004, 6, 2–16. [Google Scholar] [CrossRef]
- Karn, P. MACA-A New Channel Access Method for Packet Radio. In Proceedings of the ARRL/CRRL Amateur Radio 9th Computer Networking Conference, London, ON, Canada, 22 September 1990; pp. 134–140. [Google Scholar]
- Bargrodia, R.; Demers, A.; Shenker, S.; Zhang, L. MACAW: A Media Access Protocol for Wireless LAN’s. In Proceedings of the Conference on Communications Architectures, Protocols and Applications, London, UK, 31 August–2 September 1994; pp. 212–225. [Google Scholar]
- Tobagi, A.F.; Kleinrock, L. Packet Switching in Radio Channels: Part II—The Hidden Terminal Problem in Carrier Sense Multiple-Access and the Busy-Tone Solution. IEEE Trans. Commun. 1975, 23, 1417–1433. [Google Scholar] [CrossRef]
- Jin, T.K.; Cho, H.D. Multi-Code MAC for Multi-Hop Wireless Ad hoc Networks. IEEE Vehic. Tech. Conf. 2002, 2, 1100–1104. [Google Scholar]
- Borgonovo, F.; Capone, A.; Cesana, M.; Fratta, L. ADHOC MAC: A New MAC Architecture for Ad Hoc Networks Providing Efficient and Reliable Point-to-Point and Broadcast Services. Wirel. Netw. 2004, 10, 359–366. [Google Scholar] [CrossRef] [Green Version]
- Crowther, W.; Rettberg, R.; Walden, D.; Ornstein, S.; Heart, F. A System for Broadcast Communications: Reservation ALOHA. In Proceedings of the 6th Hawaii International Conference on Systems Sciences, Honolulu, HI, USA, 9–11 January 1973; pp. 596–603. [Google Scholar]
- Borgonovo, F.; Capone, A.; Cesana, M.; Fratta, L. RR-ALOHA, a Reliable R-ALOHA broadcast channel for ad-hoc inter-vehicle communication networks. In Proceedings of the Med-Hoc-Net, Sardegna, Italy, 4–6 September 2002; Available online: https://www.researchgate.net/publication/228598697 (accessed on 8 November 2021).
- Nasipuri, A.; Ye, S.; You, J.; Hiromoto, E.R. A MAC Protocol for Mobile Ad Hoc Networks Using Directional Antennas. In Proceedings of the Wireless Communications and Networking Conference, Chicago, IL, USA, 23–28 September 2000; Volume 1, pp. 1214–1219. [Google Scholar]
- 802.11p-2010. In IEEE Standard for Information Technology Telecommunications and Information Exchange between Systems—Local and Metropolitan Area Networks—Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) and Physical Layer (PHY) Specifications Amendment 6; Wireless Access in Vehicular Environments Std. IEEE: Piscataway, NJ, USA, 2010.
- Guo, W.; Huang, L.; Chen, L.; Xu, H.; Xie, J. An adaptive collision-free MAC protocol based on TDMA for inter-vehicular communication. In Proceedings of the International Conference on Wireless Communications and Signal Processing (WCSP), Huangshan, China, 25–27 October 2012; pp. 1–6. [Google Scholar]
- Omar, A.H.; Zhuang, W. VeMAC: A TDMA-Based MAC Protocol for Reliable Broadcast in VANETs. IEEE Trans. Mob. Comput. 2013, 12, 1724–1736. [Google Scholar] [CrossRef] [Green Version]
- Yu, F.; Biswas, S. Self-configuring TDMA protocols for enhancing vehicle safety with DSRC based vehicle-to-vehicle communications. IEEE J. Sel. Areas Commun. 2007, 25, 1526–1537. [Google Scholar] [CrossRef]
- Bharati, S.; Zhuang, W. CAH-MAC: Cooperative ADHOC MAC for vehicular networks. IEEE J. Sel. Areas Commun. 2013, 31, 470–479. [Google Scholar] [CrossRef] [Green Version]
- Liu, J.; Ren, F.; Miao, L.; Lin, C. A-ADHOC: An adaptive real-time distributed MAC protocol for Vehicular Ad Hoc Networks. Mob. Netw. Appl. 2011, 16, 576–585. [Google Scholar] [CrossRef]
- Abdalla, M.G.; Abu-Rgheff, A.M.; Senouci, M.S. Space-Orthogonal Frequency Time Medium Access Control(SOFT MAC) in VANET. In Proceedings of the IEEE Global Information Infrastructure Symposium, Hammemet, Tunisia, 23–26 June 2009; pp. 1–8. [Google Scholar]
- Dang, D.N.M.; Dang, H.N.; Nguyen, V.; Htike, Z.; Hong, C.S. HER-MAC: A hybrid efficient and reliable MAC for vehicular ad hoc networks. In Proceedings of the IEEE 28th International Conference on Advanced Information Networking and Applications, Victoria, BC, Canada, 13–16 May 2014; pp. 186–193. [Google Scholar]
- Nguyen, V.; Oo, T.Z.; Chuan, P.; Hong, C.S. An efficient time slot acquisition on the hybrid TDMA/CSMA multichannel MAC in VANETs. IEEE Commun. Lett. 2016, 20, 970–973. [Google Scholar] [CrossRef]
- Lu, N.; Ji, Y.; Liu, F.; Wang, X. A dedicated multi-channel MAC protocol design for VANET with adaptive broadcasting. In Proceedings of the IEEE Wireless Communication and Networking Conference, Sydney, NSW, Australia, 18–21 April 2010; pp. 1–6. [Google Scholar]
- Nguyen, V.; Pham, C.; Thant Zin Oo, Z.H.; Tran, H.N.; Huh, N.E.; Hong, S.C. MAC protocols with dynamic interval schemes for VANETs. Veh. Commun. 2018, 15, 4–62. [Google Scholar] [CrossRef]
- Mukhtaruzzaman, M.; Atiquzzaman, M. Clustering in VANET: Algorithms and Challenges. J. Comput. Electr. Eng. 2020, 88, 106851. Available online: https://arxiv.org/ftp/arxiv/papers/2009/2009.01964.pdf (accessed on 8 November 2021). [CrossRef]
- Chen, W.; Jia, J.; Du, X.; Zhang, Y.; Liu, K. A Clustering-Based Adaptive Multiple Access Protocol for Vehicular Ad Hoc Networks. In Proceedings of the International Conference on Communication Systems, Chengdu, China, 19–21 December 2018; pp. 463–467. [Google Scholar]
- Senouci, O.; Harous, S.; Aliouat, Z. Survey on vehicular ad hoc networks clustering algorithms: Overview, taxonomy, challenges, and open research issues. Int. J. Commun. Syst. 2020, 33, e4402. [Google Scholar] [CrossRef]
- Al-heety, S.O.; Zakaria, Z.; Ismail, M.; Shakir, M.M.; Alani, S.; Alsariera, H. A Comprehensive Survey: Benefits, Services, Recent Works, Challenges, Security, and Use Cases for SDN-VANET. IEEE Access 2020, 8, 91028–91047. [Google Scholar] [CrossRef]
- Jaballah, B.W.; Conti, M.; Lal, C. Software-Defined VANETs: Benefits, Challenges, and Future Directions, Networking and Internet Architecture. arXiv 2019, arXiv:1904.04577. [Google Scholar]
- Arena, F.; Pau, G.; Severino, A. A review on IEEE 802.11 p for intelligent transportation systems. J. Sens. Actuator Netw. 2020, 9, 22. [Google Scholar] [CrossRef]
- Naik, G.; Choudhury, B.; Park, J.M. IEEE 802.11 bd & 5G NR V2X: Evolution of radio access technologies for V2X communications. IEEE Access 2019, 7, 70169–70184. [Google Scholar]
- Peng, S.; Zhou, L.; He, X.; Du, J. GPS-aided inter-microcell interference avoidance for request-transmission splitting slotted ALOHA-based scheme in smart cities with connected vehicles. Future Gener. Comput. Syst. 2020, 108, 501–511. [Google Scholar] [CrossRef]
- Jiang, X.; Du, D.H.C. PTMAC: A Prediction-based TDMA MAC Protocol for Reducing Packet Collisions in VANET. IEEE Trans. Veh. Technol. 2016, 65, 9209–9223. [Google Scholar] [CrossRef]
- Chen, P.; Zheng, J.; Wu, Y. A-VeMAC: An Adaptive Vehicular MAC Protocol for Vehicular Ad Hoc Networks. In Proceedings of the ICC—Ad-Hoc and Sensor Networks Symposium, Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Ndih, N.D.E.; Cherkaoui, S. Modulation Network Coding. IET Commun. 2013, 7, 1715–1728. [Google Scholar] [CrossRef] [Green Version]
- Ndih, N.D.E.; Cherkaoui, S. MAP: Contention-Free MAC protocol for VANETs with PLNC. In Proceedings of the ICC-2017 Mobile and Wireless Networking, Paris, France, 21–25 May 2017; pp. 1–7. [Google Scholar]
- Urmonov, O.; Kim, H. Highly Reliable MAC Protocol Based on Associative Acknowledgement for Vehicular Network. Electronics 2021, 10, 382. [Google Scholar] [CrossRef]
- Mao, Q.; Yue, P.; Xu, M.; Ji, Y.; Cui, Z. OCTMAC: A VLC Based MAC Protocol Combining Optical CDMA with TDMA for VANETs. In Proceedings of the International Conference on Computer, Information and Telecommunication Systems (CITS), Dalian, China, 21–23 July 2017; pp. 234–238. [Google Scholar]
- Guerra-Medina, F.M.; Rojas-Guillama, B.; Gonzalez, M.A.J.; Poves, E. Experimental optical code-division multiple access system for visible light communications. In Proceedings of the 2011 Wireless Telecommunications Symposium (WTS), New York, NY, USA, 13–15 April 2011; pp. 1–6. [Google Scholar]
- Cao, Y.; Zhang, H.; Fang, Y.; Yuan, D. An Adaptive High-Throughput Multi-Channel MAC Protocol for VANETs. IEEE Internet Things J. 2020, 7, 8249–8262. [Google Scholar] [CrossRef]
- Li, S.; Liu, Y.; Wang, J.; Ge, Y.; Deng, L.; Deng, W. TCGMAC: A TDMA-based MAC protocol with collision alleviation based on slot declaration and game theory in VANETS. Trans. Emerg. Telecommun. Technol. 2019, 30, e3730. [Google Scholar] [CrossRef]
- Yanez, A.; Cespedes, S.; Rubio-Loyola, J. CaSSaM: Context-aware System for Safety Messages Dissemination in VANETs. In Proceedings of the IEEE COLCOM, Medellin, Colombia, 16–18 May 2018; pp. 1–6, ISBN 978-1-5386-6820-7/18. [Google Scholar]
- Sutton, S.R.; Barto, G.A. Introduction to Reinforcement Learning, 1st ed.; MIT Press: Cambridge, MA, USA, 1998. [Google Scholar]
- Watkins, H.C.J.C.; Dayan, P. Q-learning. Mach. Learn. 1992, 8, 279–292. [Google Scholar] [CrossRef]
- Lyu, F.; Zhu, H.; Zhou, H.; Qian, L.; Xu, W.; Li, M.; Shen, S.X. MoMAC: Mobility-Aware and Collision Avoidance MAC for Safety Applications in VANETs. IEEE Trans. Veh. Technol. 2018, 67, 10590–10602. [Google Scholar] [CrossRef]
- Samara, G. An Efficient Collision Free Protocol for VANET. Int. J. Comput. Appl. 2018, 180, 30–34. [Google Scholar] [CrossRef]
- Lyu, F.; Zhu, H.; Zhou, H.; Xu, W.; Zhang, N.; Li, M.; Shen, S.X. SS-MAC: A Novel Time Slot-Sharing MAC for Safety Messages Broadcasting in VANETs. IEEE Trans. Veh. Technol. 2018, 67, 3586–3597. [Google Scholar] [CrossRef]
- Cao, S.; Lee, S.C.V. A Novel Adaptive TDMA-Based MAC Protocol for VANETs. IEEE Commun. Lett. 2018, 22, 614–617. [Google Scholar] [CrossRef]
- Siddik, M.A.; Moni, S.S.; Alam, M.S.; Johnson, W.A. SAFE-MAC: Speed Aware Fairness Enabled MAC Protocol for Vehicular Ad-hoc Networks. Sensors 2019, 19, 2405. [Google Scholar] [CrossRef] [Green Version]
- AĞGÜN, F.; Çibuk, M.; UR-Rehman, S. ReMAC: A novel hybrid and reservation-based MAC protocol for VANETs. Turk. J. Electr. Eng. Comput. Sci. 2020, 28, 1886–1904. [Google Scholar] [CrossRef]
- Boulila, N.; Hadded, M.; Laouiti, A.; Saidane, A.L. QCH-MAC: A Qosaware Centralized Hybrid MAC protocol for Vehicular Ad Hoc NETworks. In Proceedings of the 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 55–62. [Google Scholar] [CrossRef]
- Karabulut, A.M.; Shahen Shah, M.F.A.; Ilhan, H. CR-MAC: Cooperative Relaying MAC Protocol for VANETs. In Proceedings of the Scientific Meeting on Electrical-Electronics and Biomedical Engineering and Computer Science (EBBT), Istanbul, Turkey, 24–26 April 2019; pp. 1–4, ISBN 978-1-7281-1013-4/19. [Google Scholar]
- Karabulut, A.M.; Shahen Shah, M.F.A.; İlhan, H. CoMACAV: Cooperative MAC Protocol for Autonomous Vehicles. In Proceedings of the IEEE International Symposium on Innovations in Intelligent SysTems and Applications (INISTA), Sofia, Bulgaria, 3–5 July 2019; pp. 1–8. [Google Scholar]
- Lu, X.; Xu, D.; Xiao, L.; Wang, L.; Zhuang, W. Anti-jamming communication game for UAV-aided VANETs. In Proceedings of the IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- Benslimane, A.; Nguyen-Minh, H. Jamming attack model and detection method for beacons under multi-channel operation in vehicular networks. IEEE Trans. Veh. Technol. 2016, 66, 6475–6488. [Google Scholar] [CrossRef]
- Cormen, H.T.; Leiserson, E.C.; Rivest, R.L.; Stein, C. Introduction to Algorithms, 3rd ed.; MIT Press: Cambridge, MA, USA, 2009. [Google Scholar]
- Jeong, J.; Shen, Y.; Sangsoo Jeong, S.; Lee, S.; Jeong, H.; Oh, J.; Park, T.; Ilyas, U.M.; Son, H.S.; Du, H.C.D. STMAC: Spatio-Temporal Coordination-Based MAC Protocol for Driving Safety in Urban Vehicular Networks. IEEE Trans. Intell. Transp. 2017, 19, 1520–1536. [Google Scholar] [CrossRef]
- Abbas, G.; Abbas, H.Z.; Haider, S.; Baker, T.; Boudjit, S.; Muhammad, F. PDMAC: A Priority-Based Enhanced TDMA Protocol for Warning Message Dissemination in VANETs. Sensors 2020, 20, 45. [Google Scholar] [CrossRef] [Green Version]
- Shahen Shah, M.F.A.; Ilhan, H.; Tureli, U. CB-MAC: A novel cluster-based MAC protocol for VANETs. IET Intell. Transp. Syst. 2019, 13, 587–595. [Google Scholar] [CrossRef]
- Daknou, E.; Tabbane, N.; Thaalbi, M. A MAC Multi-channel Scheme based on Learning Automata for Clustered VANETs. In Proceedings of the 32nd International Conference on Advanced Information Networking and Applications, Cracow, Poland, 16–18 May 2018; pp. 71–78. [Google Scholar]
- Aredla, J.; Zhang, S.; Liu, E. Relia-MAC: Timely and Reliable Communication for Safety Critical Applications of VANET. In Proceedings of the 25th International Conference on Automation and Computing, Lancaster University, Lancaster, UK, 5–7 September 2019; pp. 1–6. [Google Scholar]
- Roman, B.; Wassell, I.; Chatzigeorgiou, I. Scalable Cross-Layer Wireless Access Control Using Multi-Carrier Burst Contention. IEEE J. Sel. Areas Commun. 2011, 29, 113–128. [Google Scholar] [CrossRef]
- Cao, Y.; Zhang, H.; Wu, D.; Yuan, D. OGCMAC: A Novel OFDM based Group Contention MAC for VANET Control Channel. IEEE Trans. Wirel. Commun. 2017, 16, 5796–5809. [Google Scholar] [CrossRef]
- Shen, Z.; Zhang, X.; Zhang, M.; Li, W.; Yang, D. Self-Sorting Based MAC Protocol for High-Density Vehicular Ad Hoc Networks. IEEE Access 2017, 5, 7350–7361. [Google Scholar] [CrossRef]
- Peng, S.; Zhou, L.; He, X.; Du, J.; Guan, L.Y. A request-transmission splitting scheme for V2X networks: Design and throughput analysis. IEEE Access 2019, 7, 158317–158325. [Google Scholar] [CrossRef]
- Zhuo, X.; Hua, S.; Miao, L.; Dai, Y. Direction matters: A decentralized direction-based tdma scheduling strategy for vanet. In Proceedings of the 13th International Conference on Communication Technology (ICCT), Jinan, China, 25–28 September 2011; pp. 566–571. [Google Scholar]
- Samara, G. An improved CF-MAC protocol for VANET. Int. J. Electr. Comput. Eng. 2019, 9, 2668–2674. [Google Scholar] [CrossRef]
- Balador, A.; Calafate, T.C.; Cano, C.J.; Manzoni, P. DTB-MAC: Dynamic Token-Based MAC Protocol for Reliable and Efficient Beacon Broadcasting in VANETs. In Proceedings of the 12th Annual IEEE Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2015; pp. 109–114. [Google Scholar]
- Aggun, F.; Cibuk, M.; Rehman, U.S. A new Self-Organizing Multi-channel MAC schema for RSU-centric VANETs. Phys. A Stat. Mech. Appl. 2020, 551, 124098. [Google Scholar] [CrossRef]
- Ndih, N.D.E.; Cherkaoui, S. Mac for Physical-Layer Network Coding in VANETs. Int. J. Bus. Data Commun. 2012, 8, 84–106. [Google Scholar] [CrossRef]
- El-Gawad, M.A.A.; ElSharief, M.; Kim, H. A cooperative V2X MAC protocol for vehicular networks. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 65. [Google Scholar] [CrossRef] [Green Version]
- Zheng, Z.; Sangaiah, K.; Wang, T. Adaptive Communication Protocols in Flying Ad Hoc Network. IEEE Commun. Mag. 2018, 56, 136–142. [Google Scholar] [CrossRef]
- Li, S.; Liu, Y.; Wang, J.; Sun, Z. SCMAC: A Slotted-Contention-Based Media Access Control Protocol for Cooperative Safety in VANETs. IEEE Internet Things J. 2020, 7, 3812–3821. [Google Scholar] [CrossRef]
- Zhang, X.; Jiang, X.; Zhang, M. A black-burst based time slot acquisition scheme for the hybrid TDMA/CSMA multichannel MAC in VANETs. IEEE Wirel. Commun. Lett. 2019, 8, 137–140. [Google Scholar] [CrossRef]
- Lyu, F.; Cheng, N.; Zhou, H.; Xu, W.; Shi, W.; Chen, J.; Li, M. DBCC: Leveraging link perception for distributed beacon congestion control in VANETs. IEEE Internet Things J. 2018, 5, 4237–4249. [Google Scholar] [CrossRef]
- Verma, P.; Singh, N.; Sharma, M. Modelling a vehicle-ID-based IEEE 802.11 OCB MAC scheme for periodic broadcast in vehicular networks. IET Commun. 2018, 12, 2401–2407. [Google Scholar] [CrossRef]
- Pressas, A.; Sheng, Z.; Ali, F.; Tian, D.; Nekovee, M. Contention-based Learning MAC Protocol for Broadcast Vehicle-to-Vehicle Communication. In Proceedings of the IEEE Vehicular Networking Conference (VNC), Taipei, Taiwan, 5–7 December 2018; pp. 263–270. [Google Scholar] [CrossRef] [Green Version]
- Qiu, F.J.H.; Ho, W.I.; Tse, K.C.; Xie, Y. Technical Report: A Methodology for Studying 802.11p VANET Broadcasting Performance with Practical Vehicle Distribution. IEEE Trans. Veh. Technol. 2015, 64, 1939–9359. [Google Scholar] [CrossRef]
- Lyu, F.; Zhu, H.; Cheng, N.; Zhu, Y.; Zhou, H.; Xu, W.; Xue, G.; Li, M. ABC: Adaptive Beacon Control for Rear-End Collision Avoidance in VANETs. In Proceedings of the 15th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Hong Kong, China, 11–13 June 2018; pp. 1–9, ISBN 978-1-5386-4281-8/18. [Google Scholar]
- Kenney, B.J.; Bansal, G.; Rohrs, E.C. LIMERIC: A Linear Message Rate Control Algorithm for Vehicular DSRC Systems. IEEE Trans. Veh. Technol. 2013, 62, 4182–4197. [Google Scholar] [CrossRef]
- Yang, W.; Liu, W.; Li, P.; Sun, L. TDMA-Based Control Channel Access for IEEE 802.11p in VANETs. Int. J. Distrib. Sens. Netw. 2014, 2014, 579791. [Google Scholar] [CrossRef]
- Hadded, M.; Laouiti, A.; Zagrouba, R.; Muhlethaler, P.; Saidane, A.L. A Fully Distributed TDMA based MAC Protocol for Vehicular Ad Hoc Networks; Research Report; Inria Paris Rocquen Court. HAL-Inria: Lyon, France, 2015; Available online: https://hal.archives-ouvertes.fr/hal-01211456/document (accessed on 8 November 2021).
- Karamad, E.; Ashtiani, F. Performance analysis of IEEE 802.11 DCF and 802.11e EDCA based on queueing networks. IET Commun. 2009, 3, 871–881. [Google Scholar] [CrossRef]
- Chung, M.J.; Kim, M.; Park, S.Y.; Choi, M.; Lee, S.; Oh, S.H. Time coordinated V2I communications and handover for WAVE networks. IEEE J. Sel. Areas Commun. 2011, 29, 545–558. [Google Scholar] [CrossRef]
- Cheng, S.T.; Horng, G.J.; Chou, C.L. Using Cellular Automata to Form Car Society in Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2011, 12, 1374–1384. [Google Scholar] [CrossRef]
- Zafar, A.B.; Boulila, N.; Saidane, L. Communication delay guarantee for IEEE 802.11p/wave Vehicle networks with RSU control. In Proceedings of the 13th International Conference on Networking, Sensing, and Control (ICNSC), Mexico City, Mexico, 28–30 April 2016; pp. 1–7. [Google Scholar] [CrossRef]
- Zhang, Y.; Ye, M.; Guan, L. Overlap-Minimization Scheduling Strategy for Data Transmission in VANET. In Proceedings of the 2021 International Symposium on Networks, Computers and Communications (ISNCC), Dubai, United Arab Emirates, 31 October–2 November 2021. [Google Scholar]
- Kim, S.; Stark, E.W. Simple relay enabled MAC (SRMAC) protocol for cooperative communication. In Proceedings of the IEEE Military Communications Conference, San Diego, CA, USA, 18–20 November 2013; pp. 175–180. [Google Scholar]
- Wang, S.; Liu, J.; Zhou, S.; Zhou, L.; Yin, M.; Hao, H. Cooperative relay MAC protocol for ad hoc networks. In Proceedings of the 17th International Conference on Communication Technology (ICCT), Chengdu, China, 27–30 October 2017; pp. 612–616. [Google Scholar]
- Xiao, L.; Lu, X.; Xu, D.; Tang, Y.; Wang, L.; Zhuang, W. UAV Relay in VANETs Against Smart Jamming with Reinforcement Learning. IEEE Trans. Veh. Technol. 2018, 67, 4087–4097. [Google Scholar] [CrossRef]
- Valantina, M.G.; Jayashri, S. Q-Learning based point to point data transfer in Vanets. In Proceedings of the 3rd International Conference on Recent Trends in Computing (ICRTC), Ghaziabad, India, 12–13 March 2015; Volume 57, pp. 1394–1400. [Google Scholar]
- Karabulut, A.M.; Shahen Shah, M.F.A.; Ilhan, H. OEC-MAC: A Novel OFDMA Based Efficient Cooperative MAC Protocol for VANETS. IEEE Access 2020, 8, 94665–94677. [Google Scholar] [CrossRef]
- Shahen Shah, M.F.A.; Ilhan, H.; Tureli, U. RECV-MAC: A novel reliable and efficient cooperative MAC protocol for VANETs. IET Commun. 2019, 13, 2541–2549. [Google Scholar] [CrossRef]
- Liu, Y.; Zhou, H.; Huang, J. OCA-MAC: A Cooperative TDMA-Based MAC Protocol for Vehicular Ad Hoc Networks. Sensors 2019, 19, 2691. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Yoon, H.Y.; Ko, B.Y. CTMAC: A Cooperative TDMA MAC in Vehicular Ad Hoc Networks. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 18–20 October 2017; pp. 772–774. [Google Scholar] [CrossRef]
- Feng, T.K. LMA: Location- and Mobility-Aware Medium-Access Control Protocols for Vehicular Ad Hoc Networks Using Directional Antennas. IEEE Trans. Veh. Technol. 2007, 56, 3324–3336. [Google Scholar] [CrossRef]
- Huang, W.; Mao, Y.; Min, X.; Hu, J.; Shen, L. Analysis of SFR’s Impaction on Delay Time Based DMMAC for VANETs. In Proceedings of the 7th International Conference on Wireless Communications & Signal Processing (WCSP), Nanjing, China, 15–17 October 2015; pp. 1–5. [Google Scholar] [CrossRef]
- Lin, Z.; Tang, Y. Distributed multi-channel MAC protocol for VANET: An adaptive frame structure scheme. IEEE Access 2019, 7, 12868–12878. [Google Scholar] [CrossRef]
- Salem, F.; Elhillali, Y.; Nisar, S. Efficient modelling of IEEE 802.11p MAC output process for V2X interworking enhancement. IET Netw. 2018, 7, 210–219. [Google Scholar] [CrossRef]
- Khanafer, M.; Kandil, M.; Al-Baghdadi, R.; Al-Ajmi, A.; Mouftah, T.H. Enhancements to IEEE 802.15.4 MAC Protocol to Support Vehicle-to-Roadside Communications in VANETs. In Proceedings of the IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; p. 15. [Google Scholar] [CrossRef]
- Khanafer, M.; Guennoun, M.; Mouftah, H. A Survey of Beacon Enabled IEEE 802.15.4 MAC Protocols in Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2014, 16, 856–876. [Google Scholar] [CrossRef]
- Almalag, S.M.; Olariu, S.; Weigle, C.M. TDMA Cluster-based MAC for VANETs (TC-MAC). In Proceedings of the International Symposium on a World of Wireless, Mobile and Multimedia Networks (WoWMoM), San Francisco, CA, USA, 25–28 June 2012; pp. 1–6. [Google Scholar] [CrossRef]
- Hadded, M.; Zagrouba, R.; Laouiti, A.; Muhlethaler, P.; Saïdane, A.L. An Adaptive TDMA Slot Assignment Strategy in Vehicular Ad Hoc Networks. J. Mach. Mach. Commun. 2014, 1, 175–194. [Google Scholar] [CrossRef]
- Shahin, N.; Kim, T.Y. An Enhanced TDMA Cluster-based MAC (ETCM) for Multichannel Vehicular Networks. In Proceedings of the International Conference on Selected Topics in Mobile and Wireless Networking (MoWNeT), Cairo, Egypt, 11–13 April 2016; pp. 1–8. [Google Scholar] [CrossRef]
- Akhter, S.M.F.A.; Ahmed, M.; Shahen Shah, M.F.A.; Anwar, A.; Zengin, A. A Secured Privacy-Preserving Multi-Level Blockchain Framework for Cluster Based VANET. Sustainability 2021, 13, 400. [Google Scholar] [CrossRef]
- Li, M.; Lou, W.; Zeng, K. OppCast: Opportunistic Broadcast of Warning Messages in VANETs with Unreliable Links. In Proceedings of the 6th International Conference on Mobile Adhoc and Sensor Systems, Macau, China, 12–15 October 2009; pp. 534–543. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).