WLAN Aware Cognitive Medium Access Control Protocol for IoT Applications
Abstract
1. Introduction
- Addition of a sensing phase in the superframe structure which allows IoT nodes to determine WLAN transmission and to subsequently identify extended inactive period between the cluster of WLAN frames.
- An adaptive wake-up scheduling scheme for IoT nodes which allows them to modify their superframe duration and beacon intervals in case the medium is busy with WLAN transmissions.
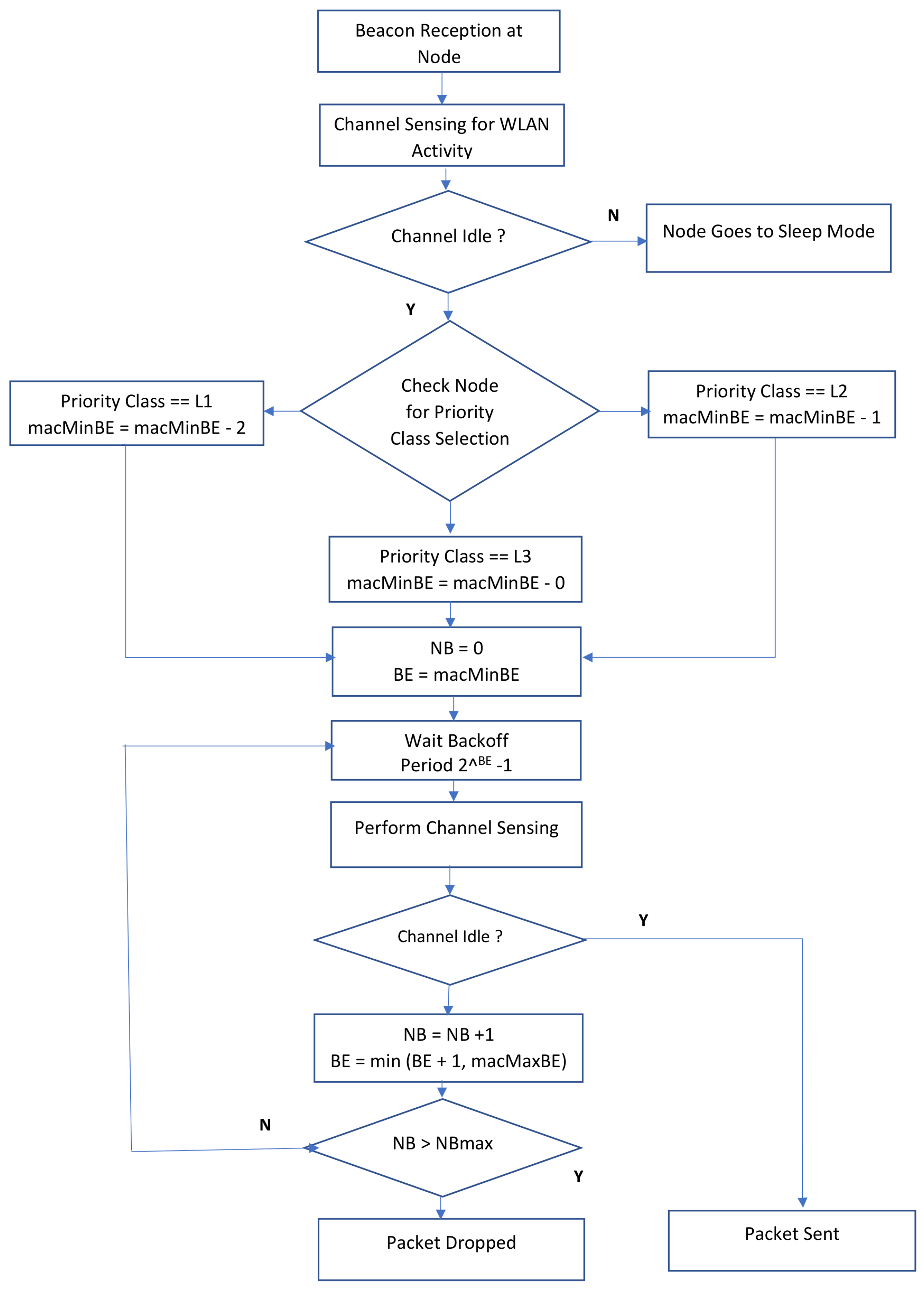
- An adaptive backoff scheme for IoT nodes which prioritizes the channel access for nodes with lower remaining battery life.
2. Related Work
3. Overview and Operation of IEEE 802.11 and IEEE 802.15.4
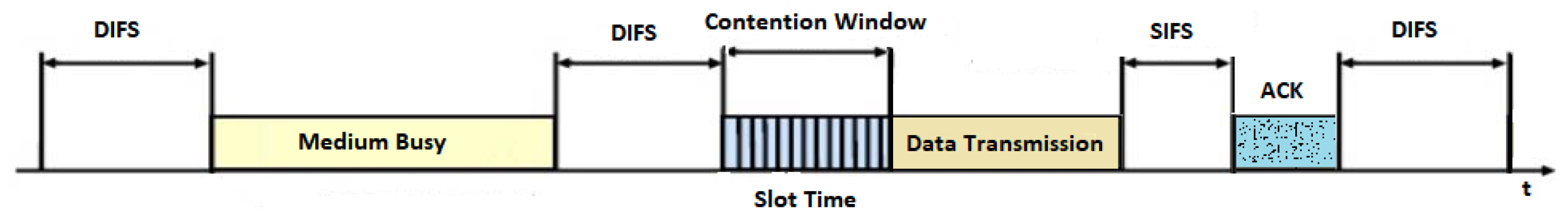
3.1. IEEE 802.11
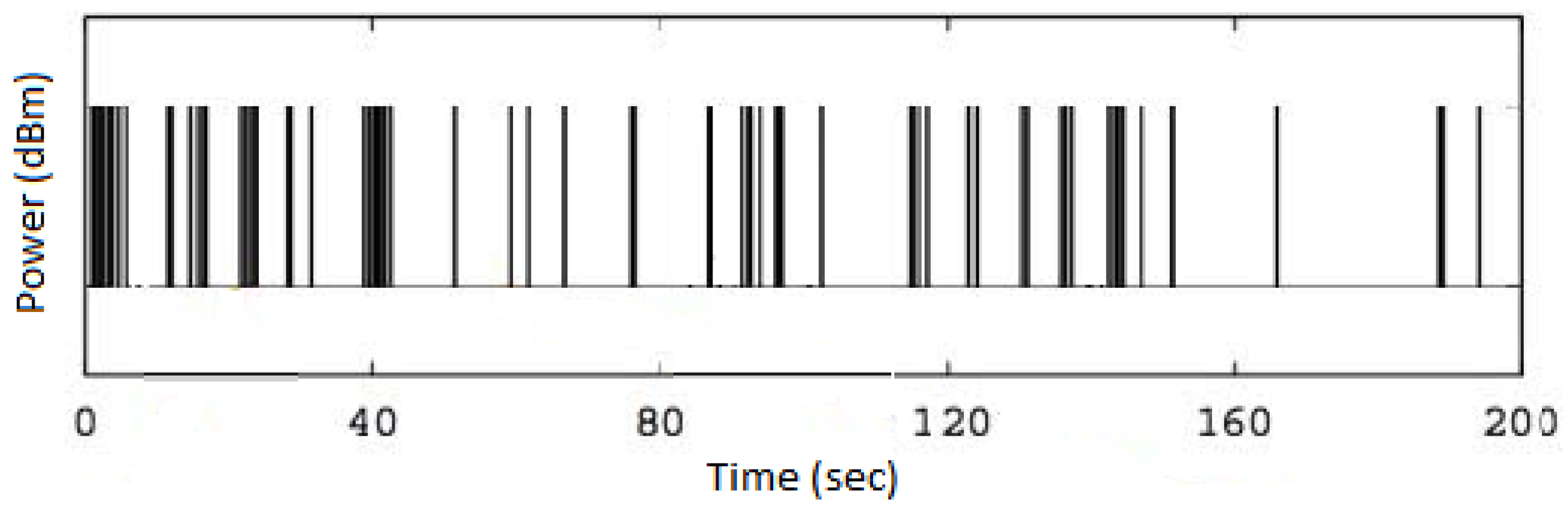
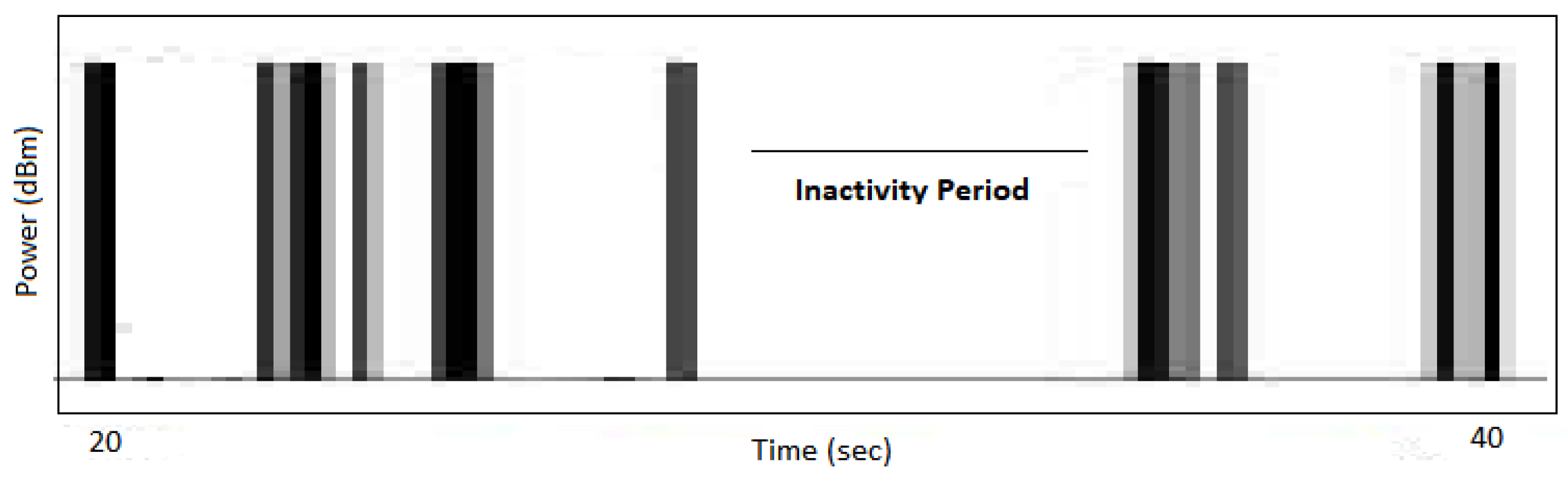
WLAN DCF Traffic Model
3.2. IEEE 802.15.4
3.2.1. Beacon Mode Versus Non-Beacon Mode Comparison
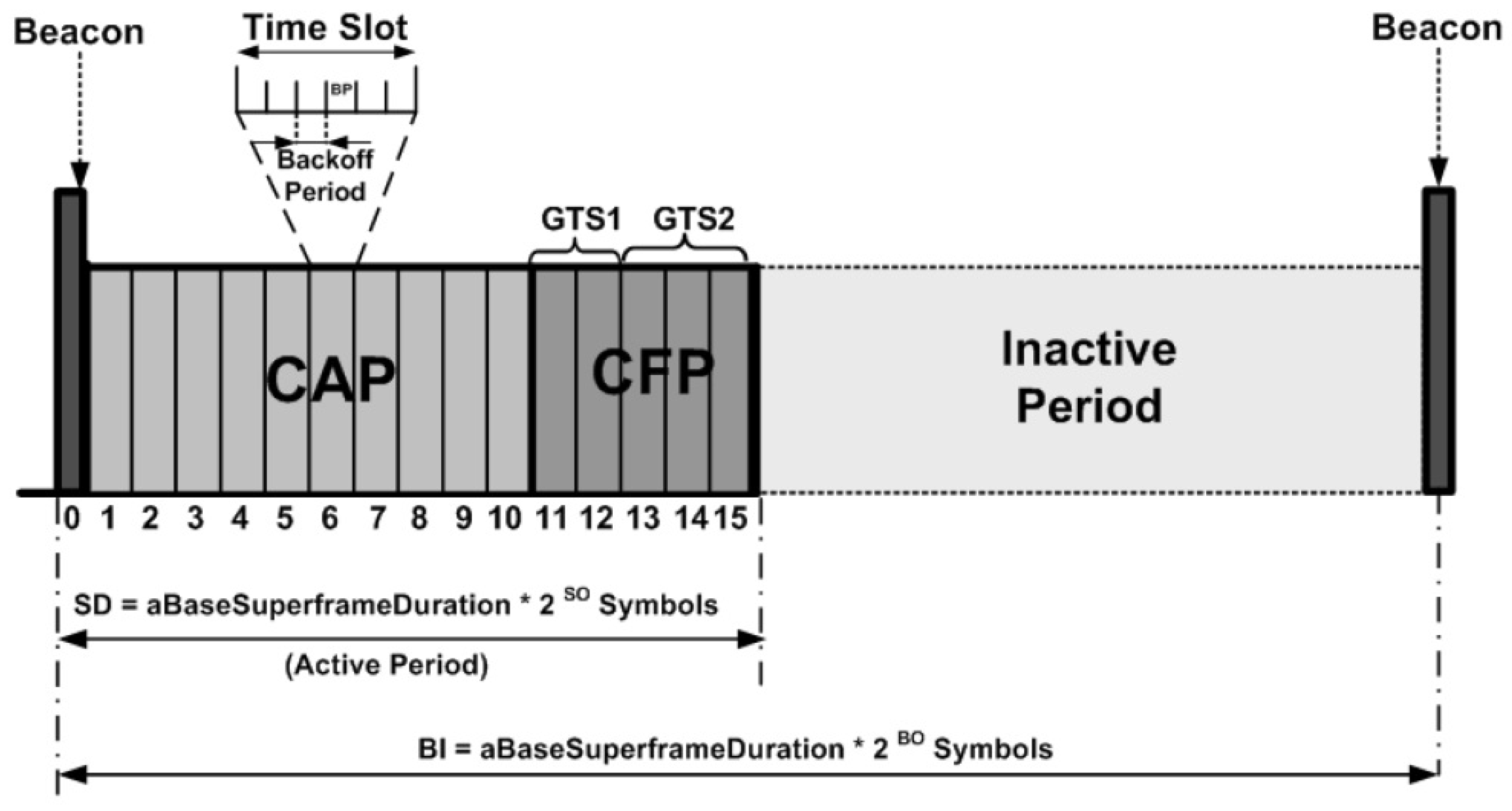
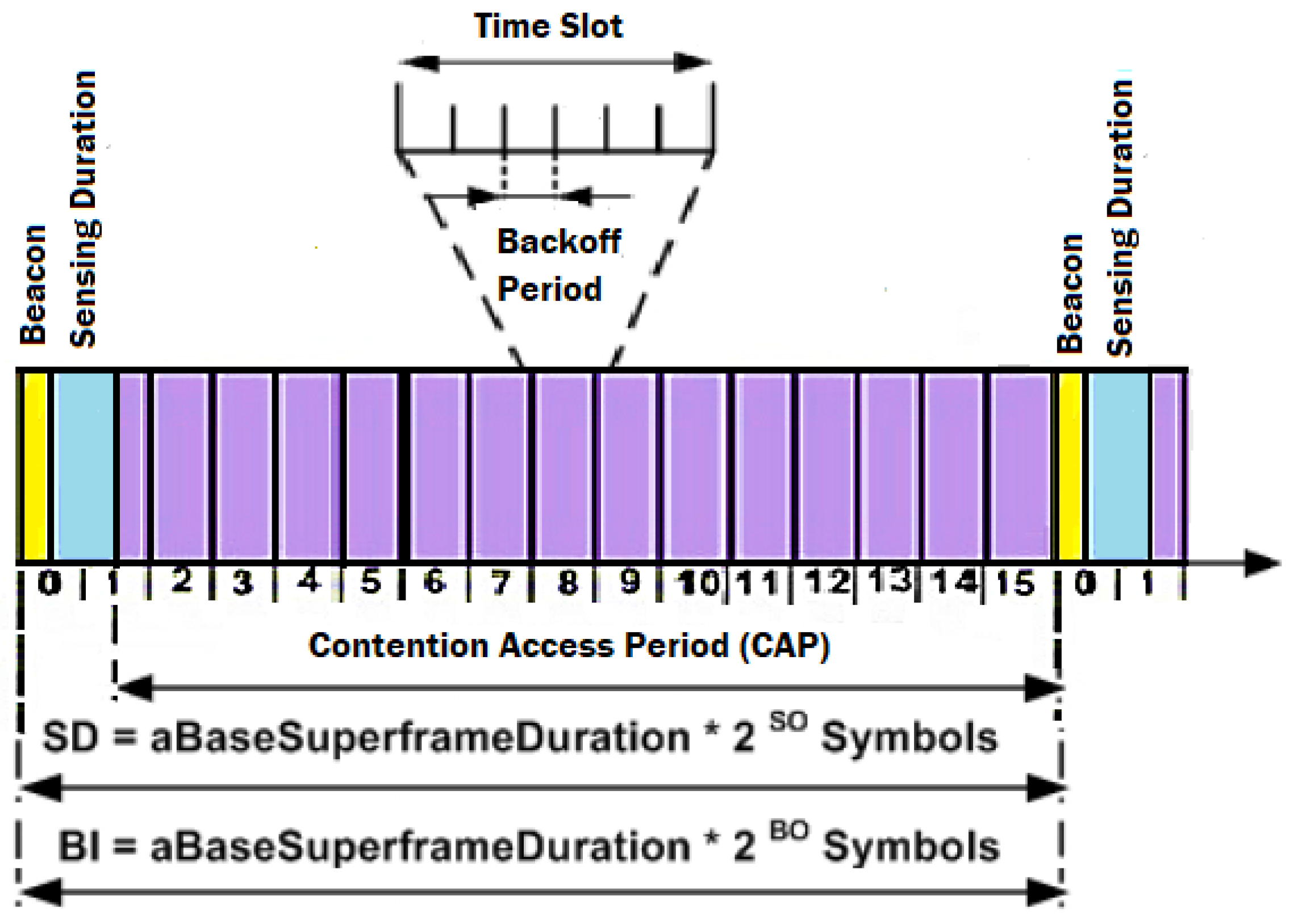
3.2.2. IEEE 802.15.4 Superframe Structure
3.2.3. IEEE 802.15.4 Contention-Based Channel Access in Beacon-Enabled Mode
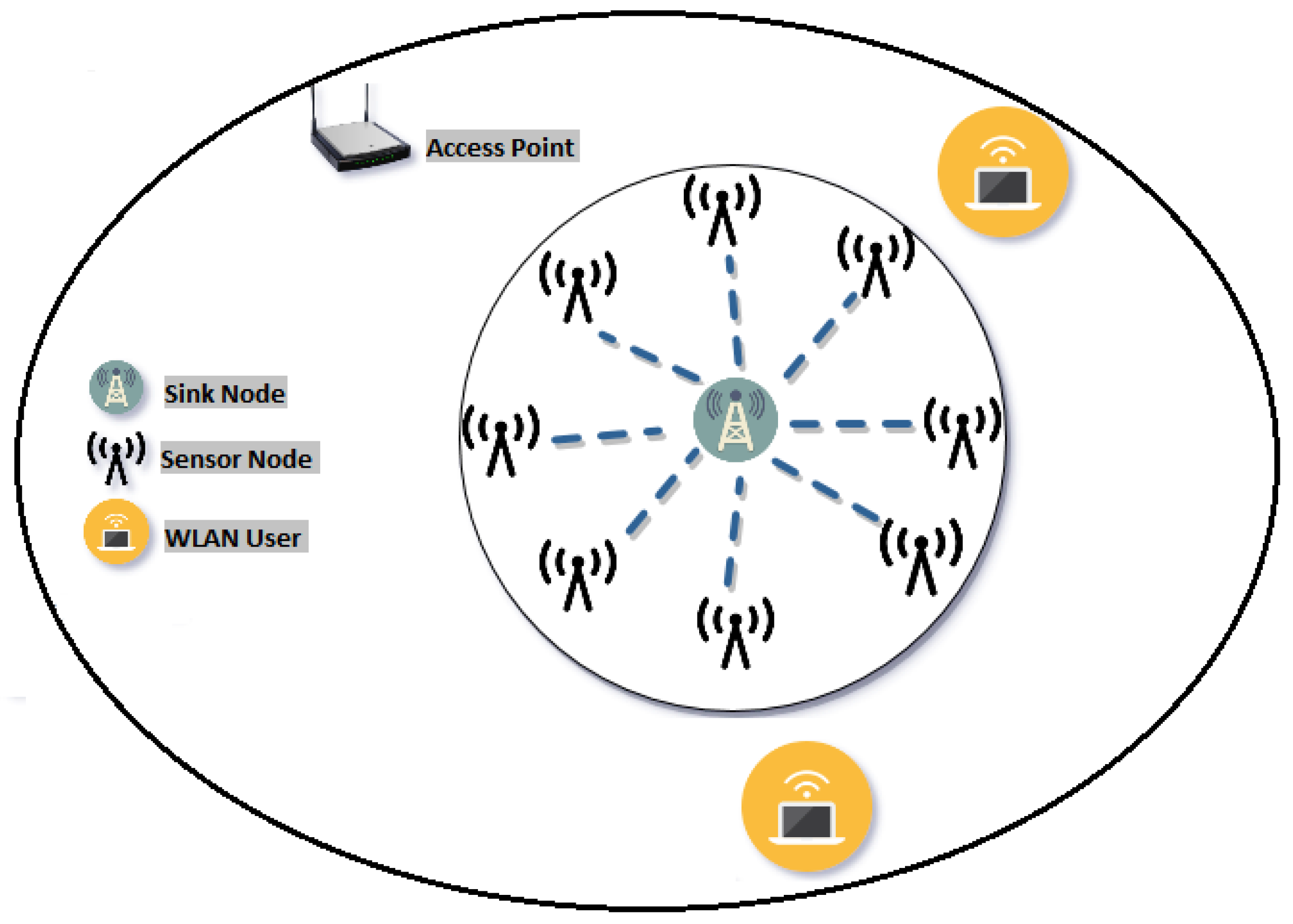
4. System Model
4.1. Interference Model
4.2. Sensing Model
4.3. Energy Consumption Model
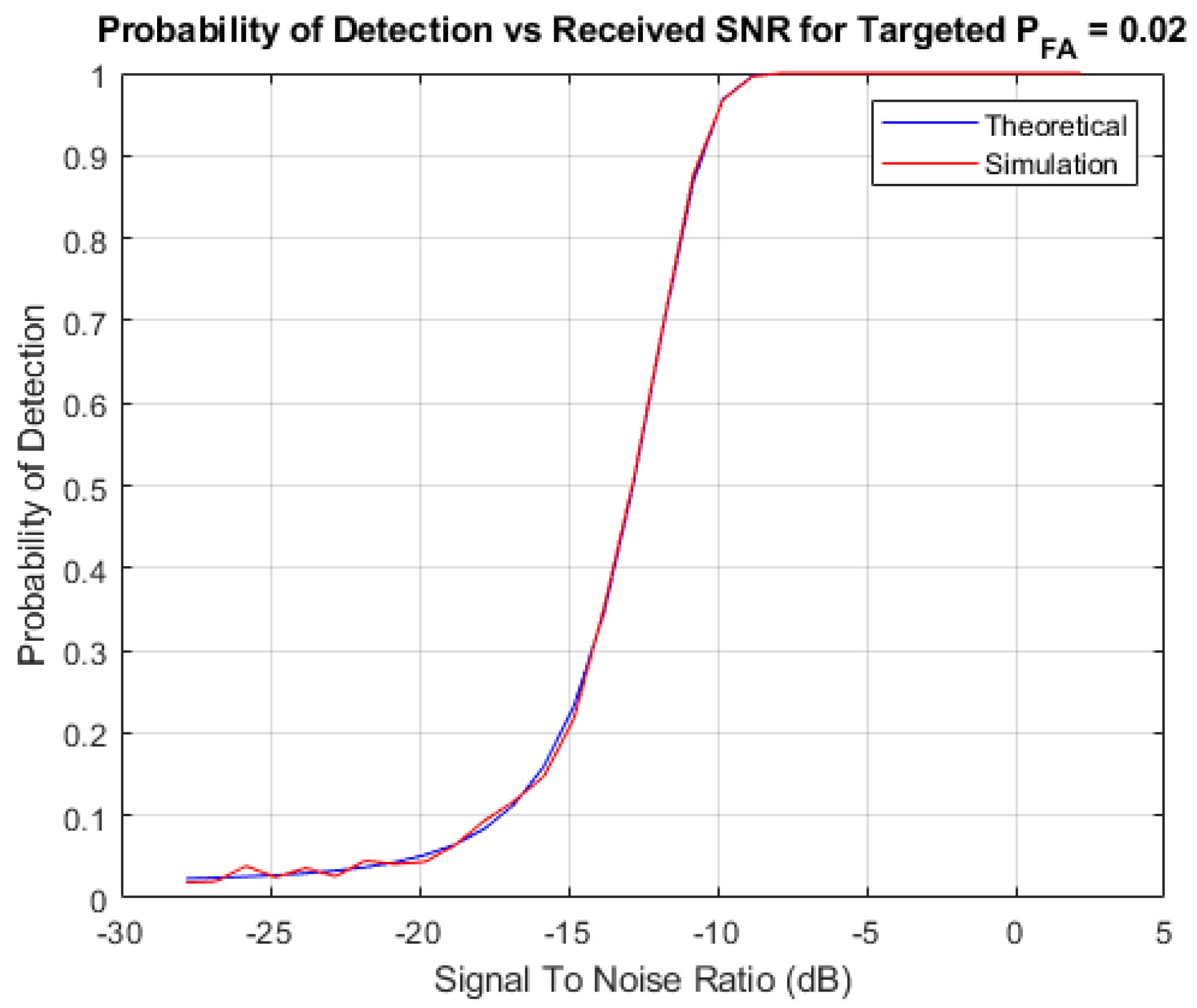
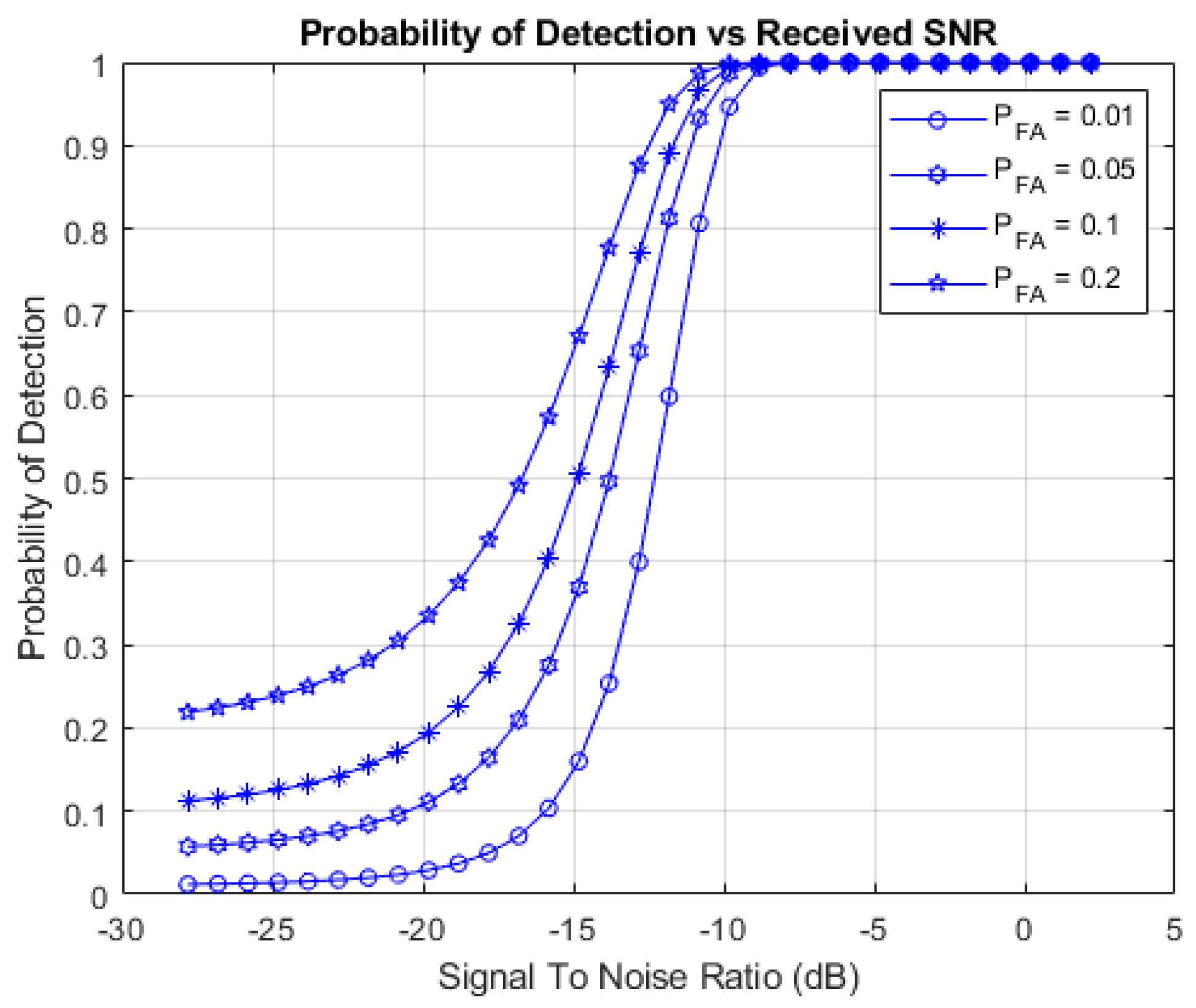
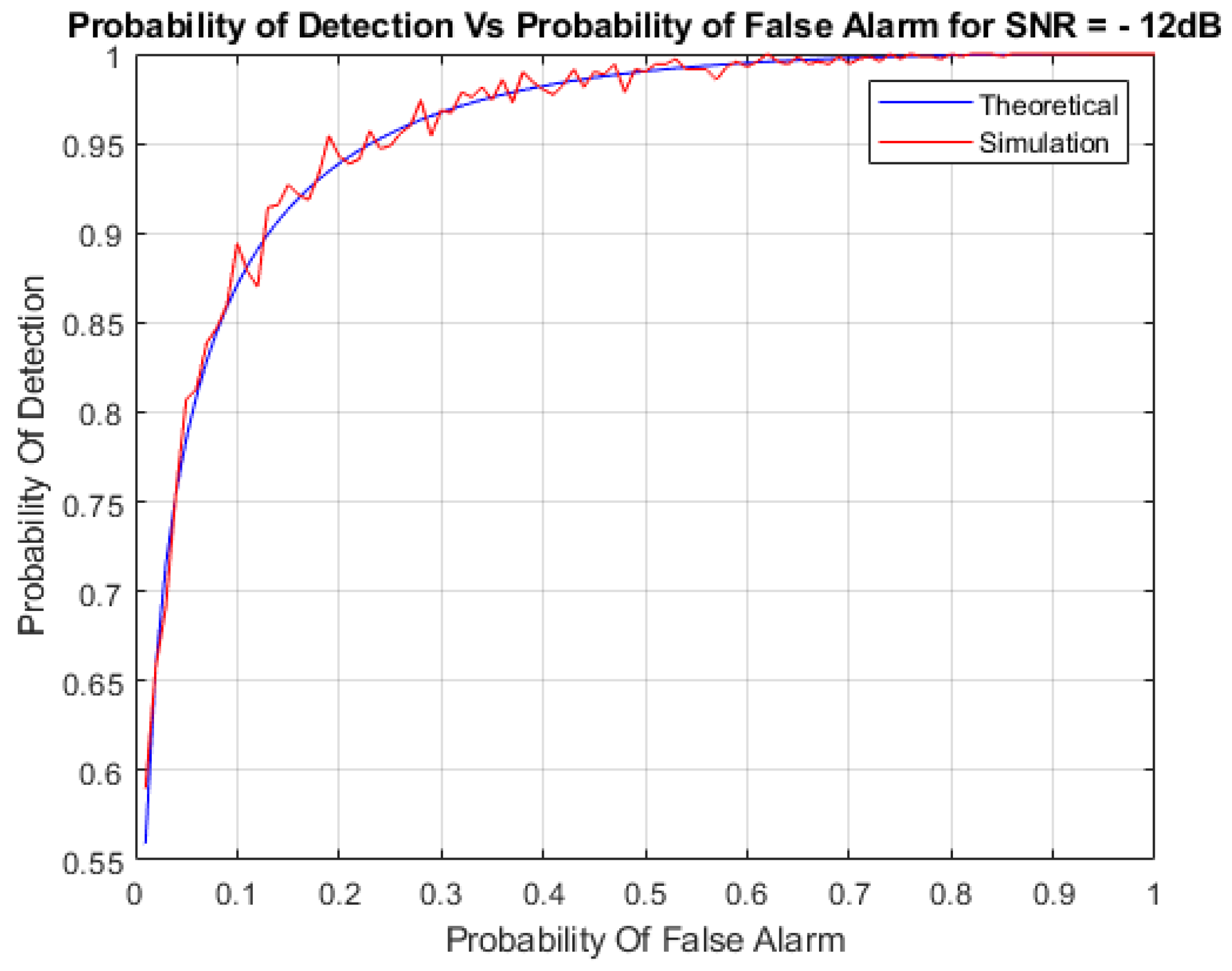
4.4. Performance Analysis of Energy Detection
5. Proposed WLAN Aware Cognitive MAC (WAC- MAC) Protocol
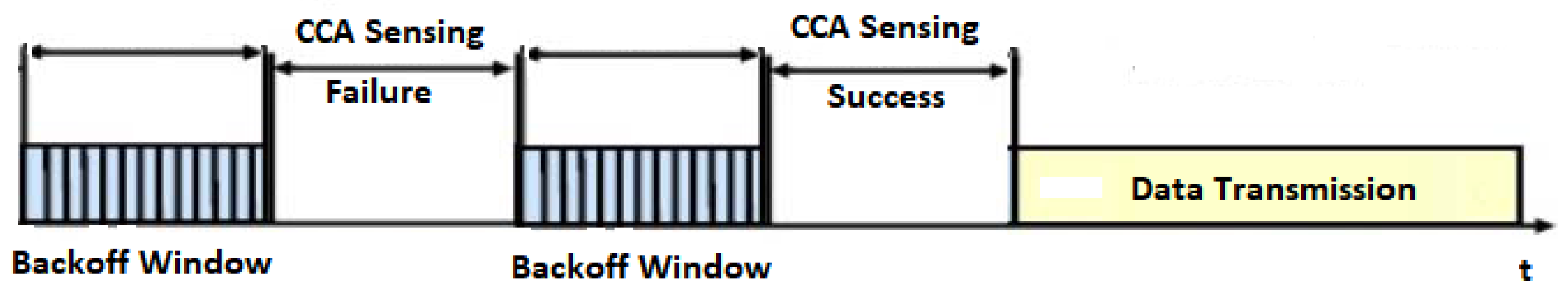
5.1. Sensing Time Slot in Superframe
5.2. Adaptive Wake-Up Scheduling for Sensor Nodes
| Algorithm 1: Adaptive Wake-Up Scheduling Algorithm |
 |
5.3. Adaptive Backoff
6. Simulation Results
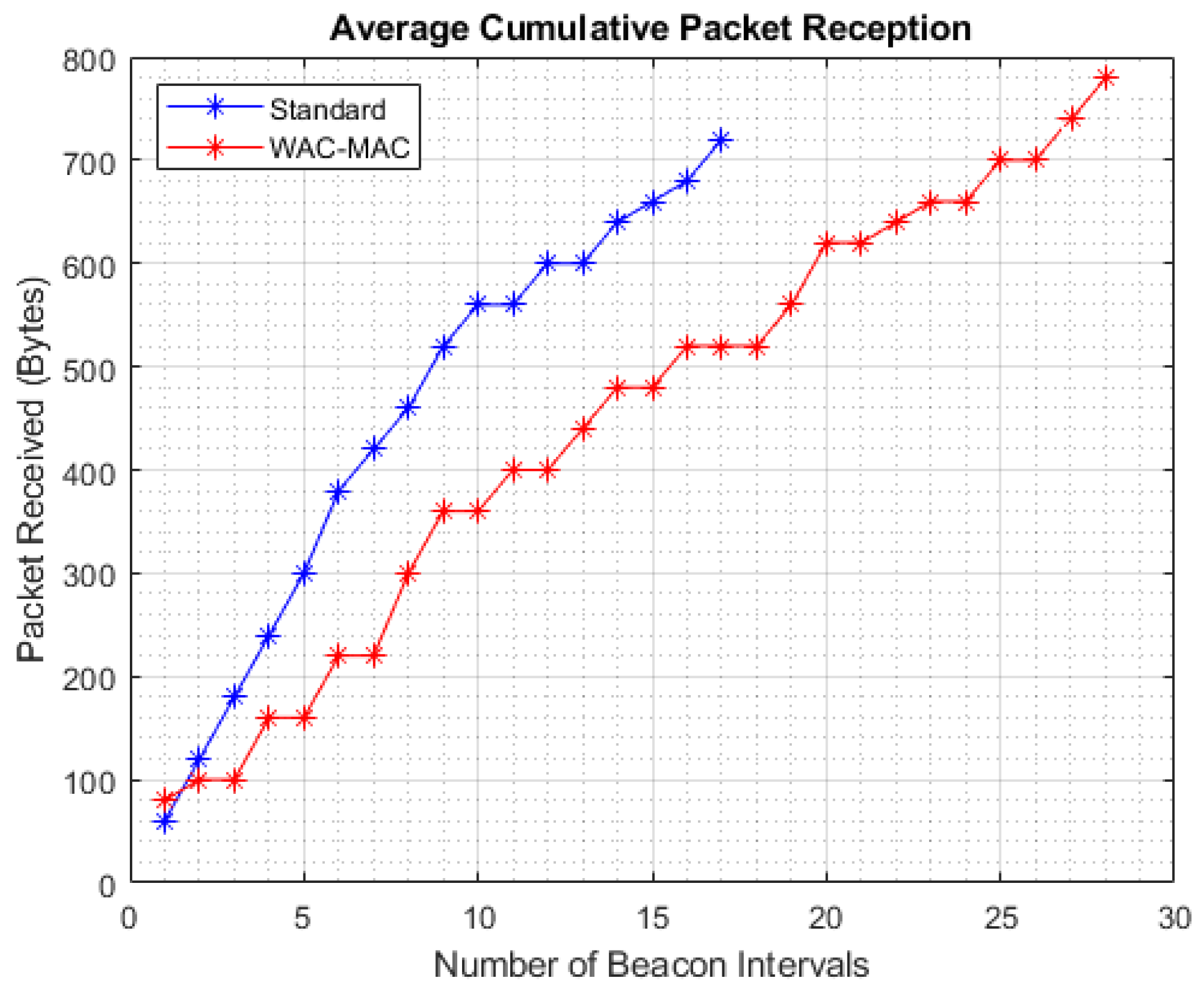
6.1. Number of Packets Received
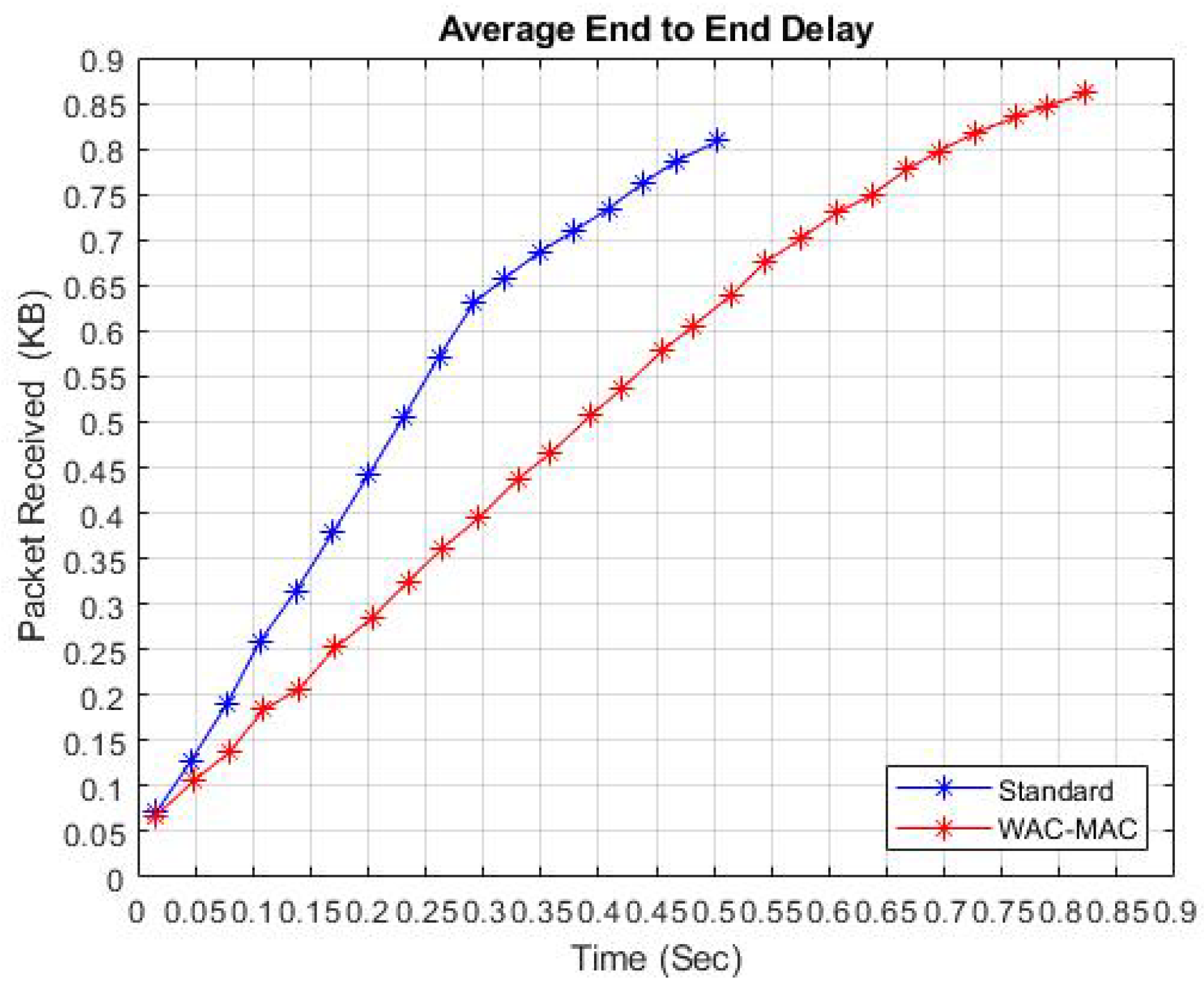
6.2. End-to-End Delay
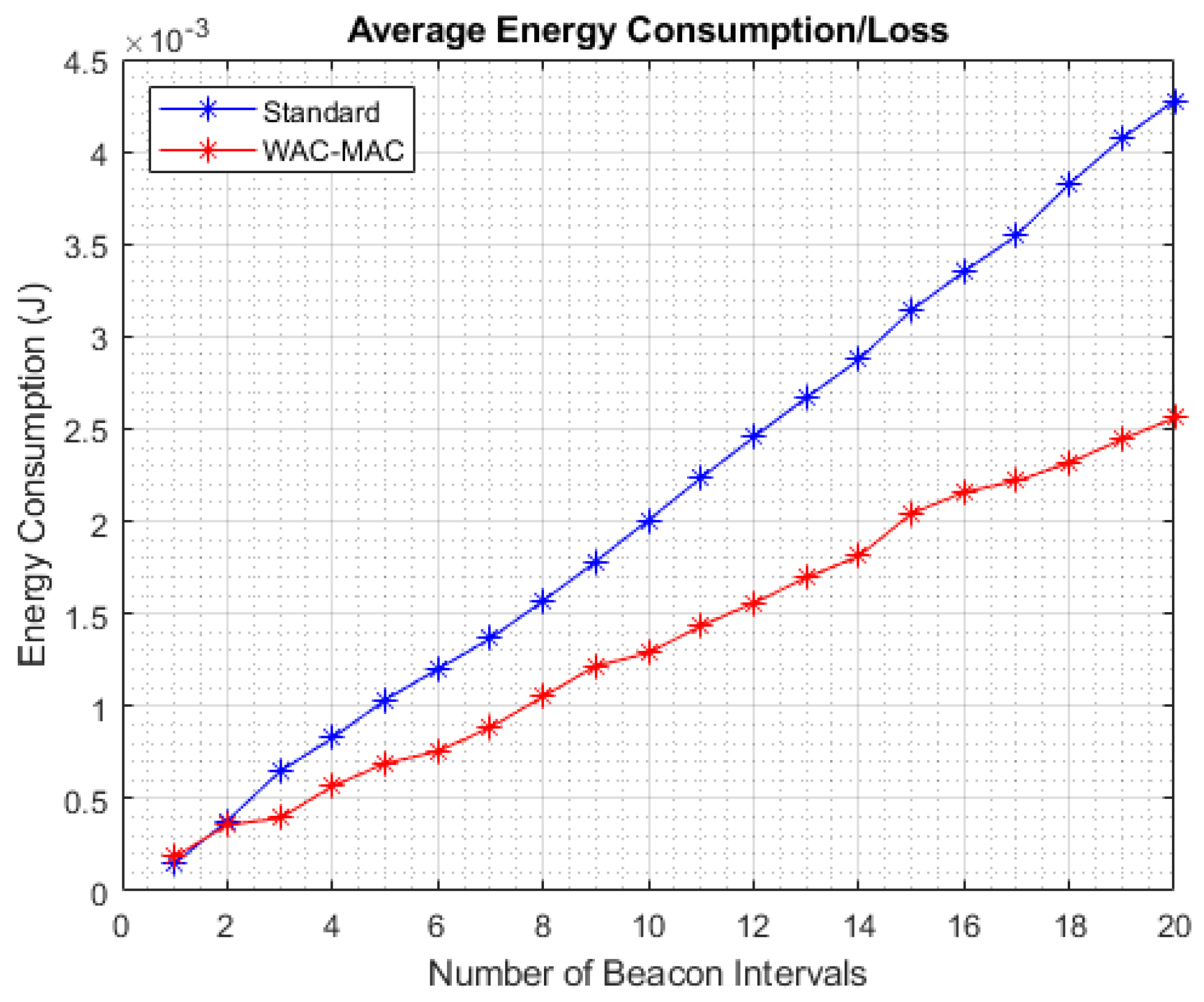
6.3. Network Energy Consumption
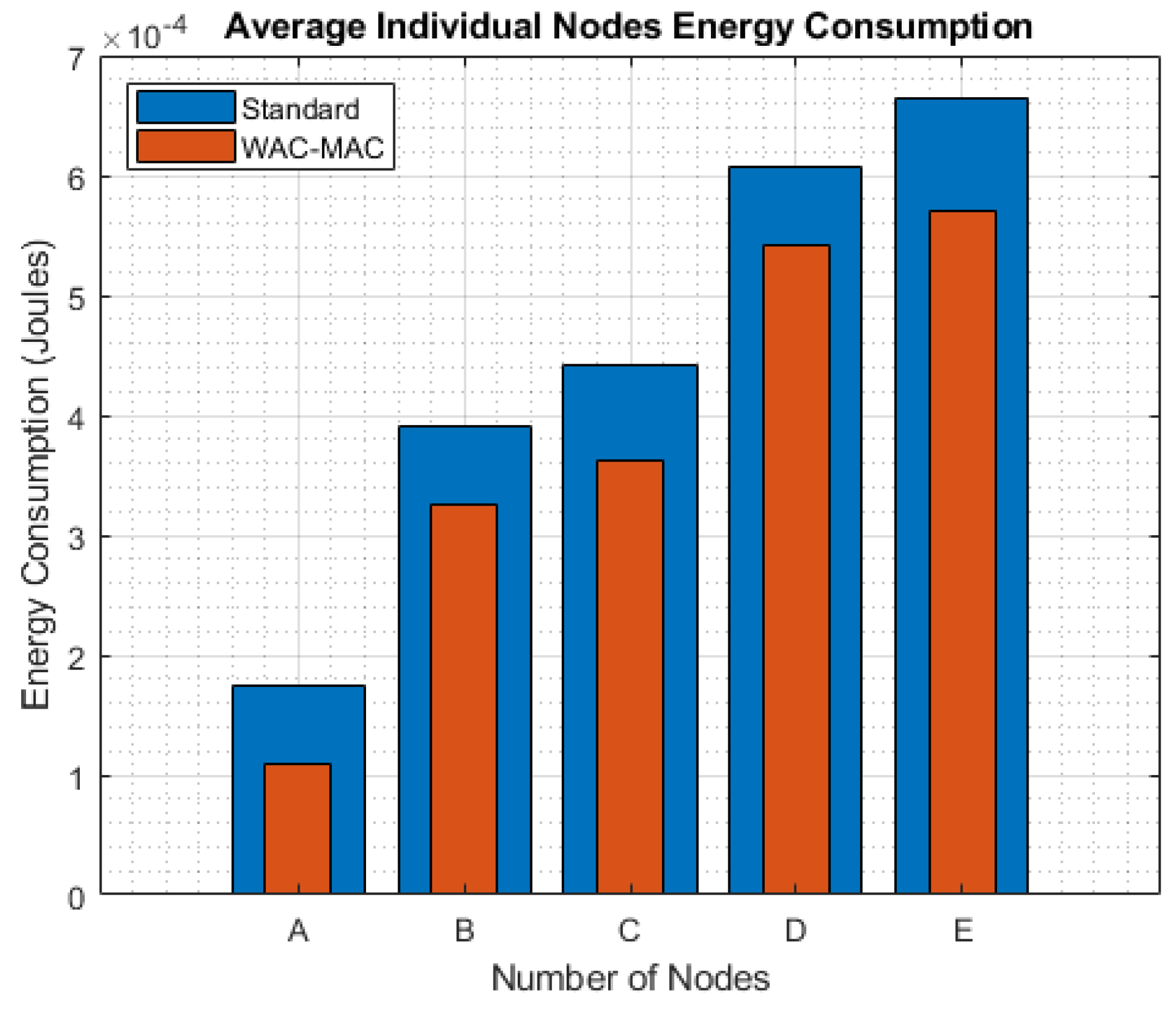
6.4. Energy Consumption of Individual Nodes
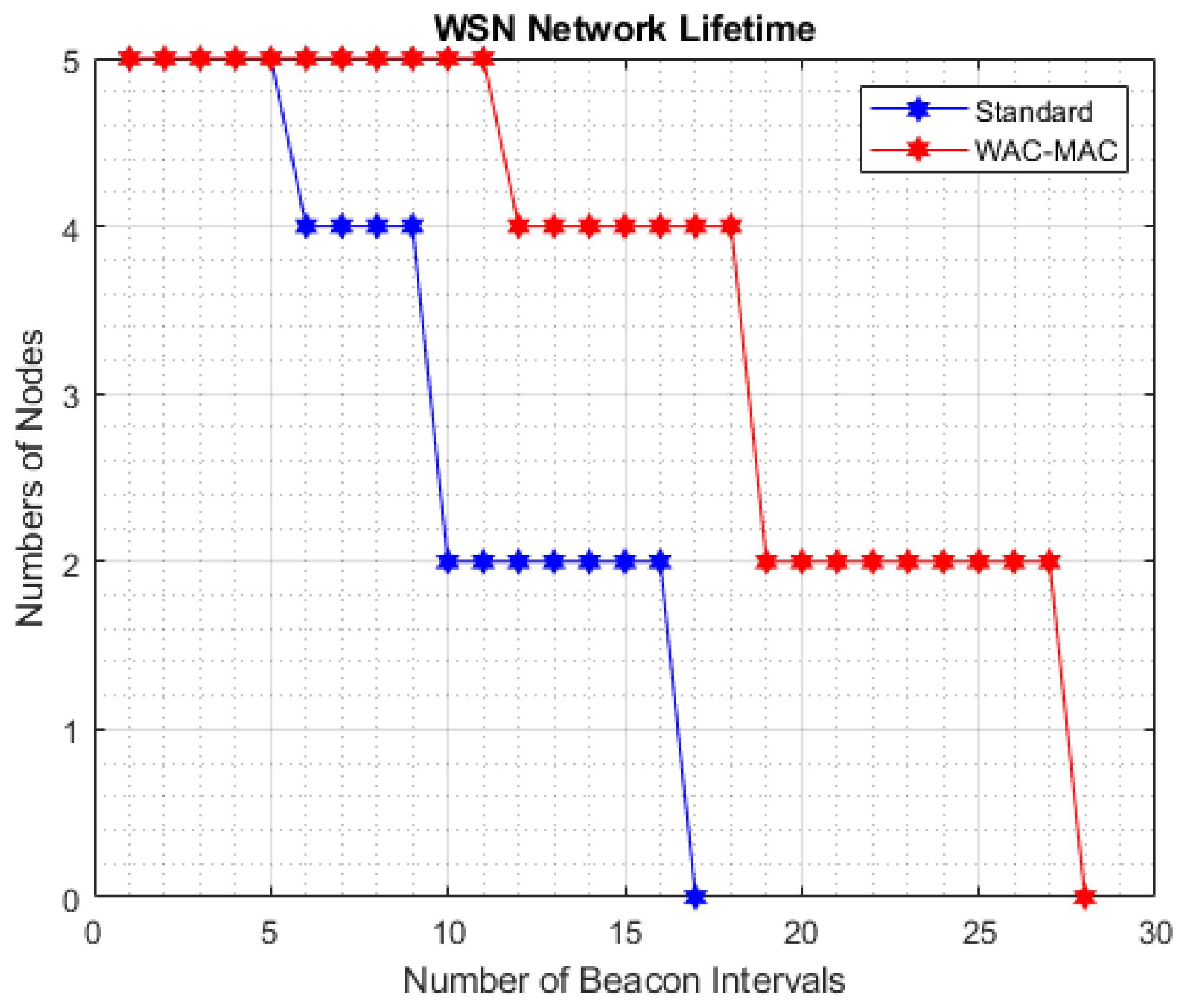
6.5. Network Lifetime
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Javed, M.A.; Zeadally, S.; Hamida, E.B. Data Analytics for Cooperative Intelligent Transport Systems. Veh. Commun. 2019, 15, 63–72. [Google Scholar] [CrossRef]
- Pollin, S.; Tan, I.; Hodge, B.; Chun, C.; Bahai, A. Harmful coexistence between 802.15.4 and 802.11: A measurement-based study. In Proceedings of the 3rd International Conference on Cognitive Radio Oriented Wireless Networks and Communications, Singapore, 15–17 May 2008; pp. 1–6. [Google Scholar]
- Qureshi, N.M.; Siddiqui, I.F.; Unar, M.A.; Uqaili, M.A.; Nam, C.S.; Shin, D.R.; Kim, J.; Bashir, A.K.; Abbas, A. An Aggregate MapReduce Data Block Placement Strategy for Wireless IoT Edge Nodes in Smart Grid. Wirel. Pers. Commun. 2019, 106, 2225–2236. [Google Scholar] [CrossRef]
- Alvi, A.N.; Khan, S.; Javed, M.A.; Konstantin, K.; Almagrabi, A.O.; Bashir, A.K.; Nawaz, R. OGMAD: Optimal GTS-allocation mechanism for adaptive data requirements in IEEE 802.15.4 based Internet of Things. IEEE Access 2019, 7, 170629–170639. [Google Scholar] [CrossRef]
- Bauwens, J.; Jooris, B.; Ruckebusch, P.; Garlisi, D.; Szurley, J.; Moonen, M.; Giannoulis, S.; Moerman, I.; De Poorter, E. Coexistence between IEEE 802.15.4 and IEEE 802.11 through cross-technology signaling. In Proceedings of the 2017 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Atlanta, GA, USA, 1–4 May 2017; pp. 529–534. [Google Scholar]
- Guo, P.; Cao, J.; Zhang, K.; Liu, X. Enhancing ZigBee throughput under WiFi interference using real-time adaptive coding. In Proceedings of the IEEE INFOCOM 2014—IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 2858–2866. [Google Scholar]
- Raaju, V.A.; Meeran, J.M.; Sasidharan, M.; Premkumar, K. IOT Based Smart Garbage Monitoring System Using ZigBee. In Proceedings of the 2019 IEEE International Conference on System, Computation, Automation and Networking (ICSCAN), Pondicherry, India, 29–30 March 2019; pp. 1–7. [Google Scholar]
- Ali, A.I.; Partal, S.Z.; Kepke, S.; Partal, H.P. ZigBee and LoRa based Wireless Sensors for Smart Environment and IoT Applications. In Proceedings of the 2019 1st Global Power, Energy and Communication Conference (GPECOM), Nevsehir, Turkey, 12–15 June 2019; pp. 19–23. [Google Scholar]
- Pasolini, G.; Buratti, C.; Feltrin, L.; Zabini, F.; De Castro, C.; Verdone, R.; Andrisano, O. Smart City Pilot Projects Using LoRa and IEEE802.15.4 Technologies. Sensors 2018, 18, 1118. [Google Scholar] [CrossRef] [PubMed]
- Yuan, W.; Wang, X.; Linnartz, J.M.G. A Coexistence Model of IEEE 802.15.4 and IEEE 802.11b/g. In Proceedings of the 2007 14th IEEE Symposium on Communications and Vehicular Technology in the Benelux, Delft, The Netherlands, 15 November 2007; pp. 1–5. [Google Scholar]
- Heo, J.; Ju, H.; Park, S.; Kim, E. Simultaneous sensing and transmission in cognitive radio. IEEE Trans. Wirel. Commun. 2014, 13, 1948–1959. [Google Scholar] [CrossRef]
- Geirhofer, S.; Tong, L.; Sadler, B. Dynamic spectrum access in the time domain: Modeling and exploiting white space. IEEE Commun. Mag. 2007, 45, 66–72. [Google Scholar] [CrossRef]
- Bahl, P.; Chandra, R.; Moscibroda, T.; Narlanka, G.S.H.; Wu, Y.; Yuan, Y. Media Access Control (MAC) Protocol for Cognitive Wireless Networks. U.S. Patent 8879573, 4 November 2014. [Google Scholar]
- Ali, A.; Abbas, L.; Shafiq, M.; Bashir, A.K.; Afzal, M.K.; Liaqat, H.B.; Siddiqi, M.H.; Kwak, K.S. Hybrid Fuzzy Logic Scheme for Efficient Channel Utilization in Cognitive Radio Networks. IEEE Access 2019, 7, 24463–24476. [Google Scholar] [CrossRef]
- Ali, A.; Feng, L.; Bashir, A.K.; El-Sappagh, S.H.; Ahmed, S.H.; Iqbal, M.; Raja, G. Quality of Service Provisioning for Heterogeneous Services in Cognitive Radio-enabled Internet of Things. IEEE Trans. Netw. Sci. Eng. 2018. [Google Scholar] [CrossRef]
- Javed, M.A.; Nafi, N.S.; Basheer, S.; Bivi, M.A.; Bashir, A.K. Fog-Assisted Cooperative Protocol for Traffic Message Transmission in Vehicular Networks. IEEE Access 2019, 7, 166148–166156. [Google Scholar] [CrossRef]
- Bachir, A.; Dohler, M.; Watteyne, T.; Leung, K. MAC essentials for Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2010, 12, 222–248. [Google Scholar] [CrossRef]
- Hanninen, M.; Suhonen, J.; Hamalainen, T.; Hannikainen, M. Link quality-based channel selection for resource constrained WSNs. Springer Adv. Grid Pervasive Comput. 2011, 6646, 254–263. [Google Scholar]
- Hwang, K.i.; Yeo, S.-S.; Park, J.H. Adaptive multi-channel utilization scheme for coexistence of IEEE 802.15.4 LR-WPAN with other interfering systems. In Proceedings of the 11th IEEE International Conference on High Performance Computing and Communications, HPCC’09, Seoul, Korea, 25–27 June 2009; pp. 297–304. [Google Scholar]
- Kamruzzaman, S.M. An Energy Efficient Multichannel MAC Protocol for Cognitive Radio Ad Hoc Networks. Int. J. Commun. Netw. Inf. Secur. (IJCNIS) 2010, 2, 112–119. [Google Scholar]
- Amna, J.; Tham, C.; Wong, W. CR-WSN MAC: An energy efficient and spectrum aware MAC protocol for cognitive radio sensor network. In Proceedings of the 2014 9th International Conference Cognitive Radio Oriented Wireless Networks and Communications (CROWNCOM), Oulu, Finland, 2–4 June 2014. [Google Scholar]
- Daewon, J.; Kim, Y.; Lim, H. Energy-Efficient MAC Protocol for IEEE 802.11-Based Cognitive Radio Networks. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–5. [Google Scholar]
- Liang CJ, M.; Priyantha, N.B.; Liu, J.; Terzis, A. Surviving wi-fi interference in low power zigbee networks. In Proceedings of the 8th ACM Conference on Embedded Networked Sensor Systems, Zurich, Switzerland, 3–5 November 2010. [Google Scholar]
- Chowdhury, K.; Akyildiz, I. Interferer Classification, Channel Selection and Transmission Adaptation for Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Communications, Dresden, Germany, 14–18 June 2009; pp. 1–5. [Google Scholar]
- Glaropoulos, I.; Laganà, M.; Fodor, V.; Petrioli, C. Energy efficient cognitive-MAC for sensor networks under WLAN co-existence. IEEE Trans. Wirel. Commun. 2015, 14, 4075–4089. [Google Scholar] [CrossRef]
- Rathod, P.; Dabeer, O.; Karandikar, A.; Sahoo, A. Characterizing the exit process of a non-saturated IEEE 802.11 wireless network. In Proceedings of the tenth ACM international symposium on Mobile ad hoc networking and computing, New Orleans, LA, USA, 18–21 May 2009. [Google Scholar]
- Misic, J.; Misic, V. Characterization of idle periods in IEEE 802.11e networks. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Cancun, Quintana Roo, Mexico, 28–31 March 2011; pp. 1004–1009. [Google Scholar]
- Understanding the IEEE 802.11 Standard for Wireless Networks. Available online: https://www.juniper.net/documentation/en_US/junos-space-apps/network-director3.2/topics/concept/wireless-80211.html (accessed on 10 December 2019).
- Huang, J.; Xing, G.; Zhou, G.; Zhou, R. Beyond co-existence: Exploiting WiFi white space for Zigbee performance assurance. In Proceedings of the 18th IEEE International Conference on Network Protocols, Kyoto, Japan, 5–8 October 2010; pp. 305–314. [Google Scholar]
- Crow, B.P.; Widjaja, I.; Kim, J.G.; Sakai, P.T. IEEE 802.11 wireless local area networks. IEEE Commun. Mag. 1997, 35, 116–126. [Google Scholar] [CrossRef]
- Geirhofer, S.; Tong, L.; Sadler, B.M. Cognitive medium access: Constraining interference based on experimental models. IEEE J. Sel. Areas Commun. 2008, 26, 95–105. [Google Scholar] [CrossRef]
- Rajab, S.A.; Balid, W.; Refai, H.H. Toward enhanced wireless coexistence in ISM band via temporal characterization and modelling of 802.11 b/g/n networks. Wirel. Commun. Mob. Comput. 2016, 16, 3212–3229. [Google Scholar] [CrossRef]
- Shih, K.P.; Wang, S.S.; Chen, H.C.; Yang, P.H. CollECT: Collaborative event detection and tracking in wireless heterogeneous sensor networks. Comput. Commun. 2008, 31, 3124–3136. [Google Scholar] [CrossRef]
- IEEE Standard for Telecommunications and Information Exchange Between Systems—LAN/MAN Specific Requirements—Part 11: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications: High Speed Physical Layer in the 5 GHz Band; Technical Report; IEEE: Piscataway, NJ, USA, December 1999.
- IEEE Standard for Low-Rate Wireless Networks; Technical Report; IEEE: Piscataway, NJ, USA, 22 April 2016.
- Koubaa, A.; Alves, M.; Tovar, E. A comprehensive simulation study of slotted CSMA/CA for IEEE 802.15.4 wireless sensor networks. In Proceedings of the 2006 IEEE International Workshop on Factory Communication Systems, Torino, Italy, 27–30 June 2006; pp. 183–192. [Google Scholar]
- IEEE Draft Standard for Local and Metropolitan Area Networks—Part 15.4: Low-Rate Wireless Personal Area Networks (LR-WPANs) Amendment for an Ultra Low Power Physical Layer; IEEE: Piscataway, NJ, USA, 9 September 2015; pp. 1–51.
- Buratti, C. Performance Analysis of IEEE 802.15.4 Beacon-Enabled Mode. IEEE Trans. Veh. Technol. 2010, 59, 2031–2045. [Google Scholar] [CrossRef]
- Tse, D.; Viswanath, P. Fundamentals of Wireless Communication; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar]
- 2.4 GHz IEEE 802.15.4/ZigBee-ready RF Transceiver. Available online: https://www.ti.com/lit/ds/symlink/cc2420.pdf (accessed on 10 January 2020).
- Wu, T.; Yang, H. On the Performance of Overlaid Wireless Sensor Transmission with RF Energy Harvesting. IEEE J. Sel. Areas Commun. 2015, 33, 1693–1705. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Lo, B.F.; Balakrishnan, R. Cooperative Spectrum Sensing in Cognitive Radio networks: A Survey. Phys.Commun. 2011, 4, 40–62. [Google Scholar] [CrossRef]
- Ku, M.-L.; Lin, J.C. Cognitive Radio and Interference Management: Technology and Strategy; IGI Global: Hershey, PA, USA, 2012. [Google Scholar]
- MicaZ Sensor Datasheet. Available online: Memsic.com/userfiles/files/Datasheets/WSN/micazdatasheet.pdf (accessed on 10 January 2020).
| Energy Level | Priority Class | MacMinBE Value |
|---|---|---|
| 0%–30% | L1 | 1 |
| 30%–60% | L2 | 2 |
| >60% | L3 | 3 |
| Parameters Setup for Performance Evaluation | |
|---|---|
| Parameter | Value |
| Path Loss Exponent | 4.0 |
| Noise Power | −103 dBm |
| Path Loss Attenuation | 9.98 × 10−5 |
| Sensing Time | 0.512 × 10−3 |
| Sampling Frequency | 5 MHz |
| Battery | 3 V |
| Sleeping Current | 0.001 mA |
| Idle Current | 0.02 mA |
| Receive Current | 19.7 mA |
| Transmit Current | 17.4 mA |
| Sensing Current | 15.3 mA |
| System Parameters Used for Simulation | ||
|---|---|---|
| Parameter | IEEE 802.15.4 | IEEE 802.11b/g |
| Bandwidth | 5 MHz | 22 MHz |
| Transmission Power | 0 dBm | 12 dBm |
| Receiver Sensitivity | −85 dBm | −82 dBm |
| Transmission Rate | 250 kbps | 54 Mbps |
| Backoff unit time | 320 μs | 20 μs |
| CCA | 128 μs | N/A |
| DIFS | N/A | 50 μs |
| CWmin | N/A | 15 |
| Payload Size | 15 byte | 512 bytes |
| BO = SO | 0 | N/A |
| macMinBE | 3 | N/A |
| macMaxBE | 5 | N/A |
| Max Retransmission | 5 | N/A |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ausaf, A.; Khan, M.Z.; Javed, M.A.; Bashir, A.K. WLAN Aware Cognitive Medium Access Control Protocol for IoT Applications. Future Internet 2020, 12, 11. https://doi.org/10.3390/fi12010011
Ausaf A, Khan MZ, Javed MA, Bashir AK. WLAN Aware Cognitive Medium Access Control Protocol for IoT Applications. Future Internet. 2020; 12(1):11. https://doi.org/10.3390/fi12010011
Chicago/Turabian StyleAusaf, Asfund, Mohammad Zubair Khan, Muhammad Awais Javed, and Ali Kashif Bashir. 2020. "WLAN Aware Cognitive Medium Access Control Protocol for IoT Applications" Future Internet 12, no. 1: 11. https://doi.org/10.3390/fi12010011
APA StyleAusaf, A., Khan, M. Z., Javed, M. A., & Bashir, A. K. (2020). WLAN Aware Cognitive Medium Access Control Protocol for IoT Applications. Future Internet, 12(1), 11. https://doi.org/10.3390/fi12010011








