An Architecture for Biometric Electronic Identification Document System Based on Blockchain † †
Abstract
:1. Introduction
- A Blockchain network architecture proposal for a national e-ID system with iris and fingerprint recognition features.
- A fingerprint and iris recognition set up for the proposed e-ID system.
- The design, implementation, and validation of a Blockchain network for the proposed e-ID system through a new consensus method called tournament consensus algorithm (TCA).
2. Related Work
- Decentralized autonomous organization (DAO) attack [14]: it is deployed on a smart contract platform, using it as malicious smart contract.
- Border gateway protocol (BGP) hijacking attack [15]: the purpose is to rerouting traffic to a mining pool controlled by the attacker and subsequently steal cryptocurrencies.
- Liveness attack [18]: it permits to delay the confirmation time of a determined transaction and in some BCT the transaction will be regarded valid. Then, the attacker could continue building a private blockchain to incorporate the blocks in the public blockchain.
- Balance attack [19]: this attack works to BCT using the proof of work (PoW) consensus algorithm and allows double-spending.
3. Authentication Methods
3.1. Document Authentication
3.1.1. A Changeable Laser Image (CLI)
3.1.2. Holograms
3.1.3. Watermarking Methods
3.1.4. One-Way Functions
3.1.5. Document Authentication Protocols
3.2. User Authentication
3.2.1. Fingerprint Recognition System
3.2.2. Face Recognition System
3.2.3. Iris Recognition System
3.2.4. The Password
3.2.5. A Personal Identification Number (PIN)
3.2.6. One-Time Password (OTP)
3.2.7. Zero-Knowledge Proofs (ZKP)
3.2.8. Smart Card
3.2.9. Barcode
3.2.10. Radio Frequency Identification (RFID)
3.2.11. Near Field Communication (NFC)
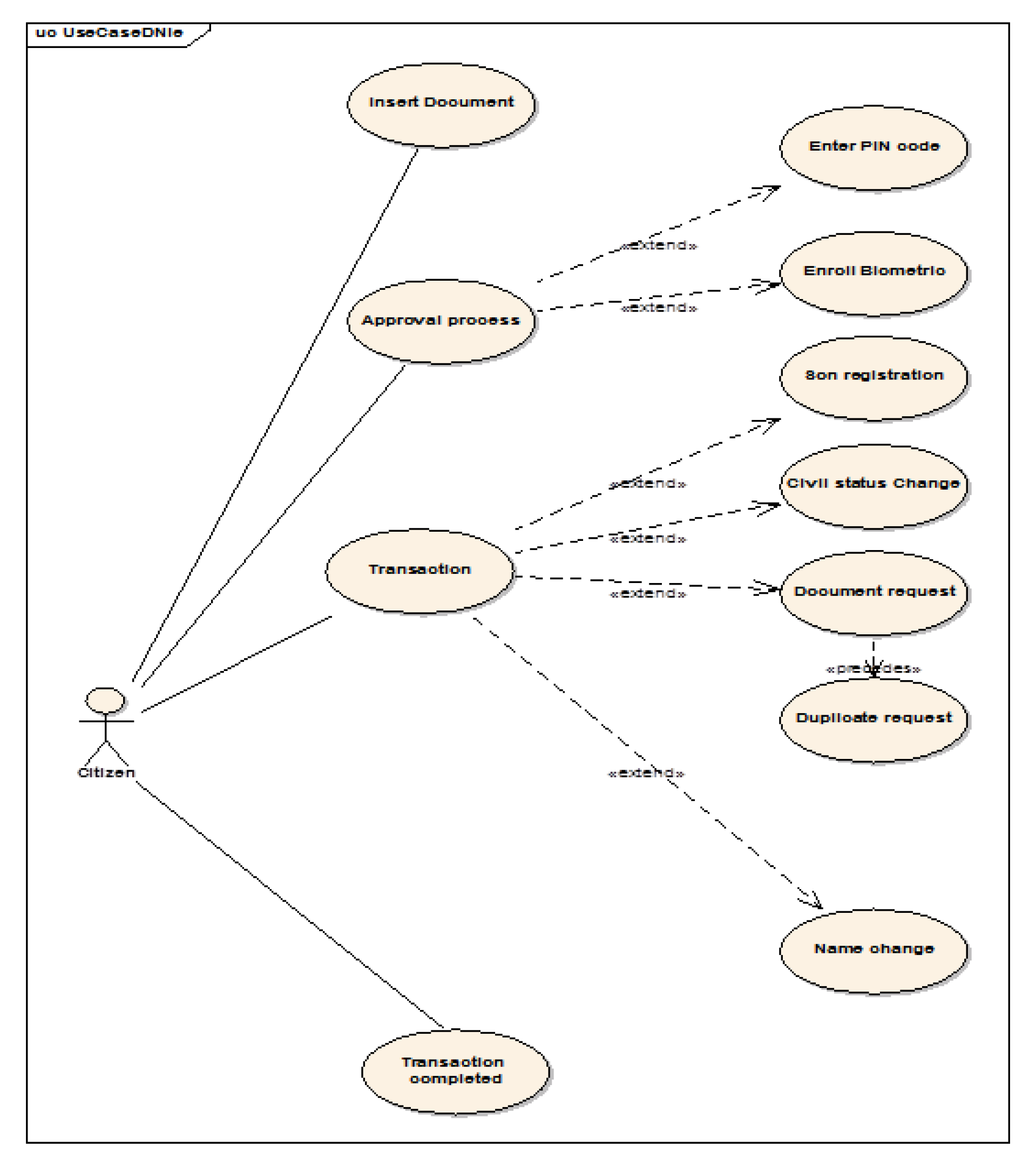
4. Proposed Architecture for Biometric E-ID System with Blockchain
4.1. Blockchain Architecture
4.2. Blockchain Node Architecture
4.3. Deployment Model
- (i)
- A citizen arrives at a governmental office (National Register office, local register office, notary’s office), and accesses to an authorized computer named Webserver identification, which is equipped with a card reader and a biometric reader.
- (ii)
- The citizen uses his/her card and biometric feature (iris) to authenticate himself.
- (iii)
- If the identification citizen is correct, automatically is shown the citizen’s information on a form and subsequently, the citizen could perform a transaction using a drop-down list.
- (iv)
- The identification webserver is connected to a database that will store the data of citizens along with their digital signatures, fingerprint templates, and iris. In this way, it is possible to verify the citizen authenticity.
- (v)
- Finally, the identification webserver will deploy a message on the screen indicating the correct user validation.
4.4. Transactions
4.5. System Implementation
5. Consensus Algorithms
5.1. Proof of Work (PoW) Algorithm
Security Problems in PoW
- It reduces the incentive of centralization by always rewarding (minimally) miners who produce obsolete or orphaned blocks because they are not part of a large group and get noticed about other blocks later (due to propagation delays of the network).
- It increases the safety of the chain by increasing the amount of work on the main chain. As a result, less work is wasted on alternative branches in favor of the main branch.
5.2. Proof of Stake (PoS) Algorithm
- Saving power: the PoS is a mechanism that consumes much less energy than PoW (which, in turn, requires a large number of cryptographic calculations to find the proof of work required for the validation of each block).
- The 51% attack is more difficult: in a PoS-type system, the 51% attack requires controlling more than half of the circulating token, which is usually much more expensive than controlling 51% of computing power in the PoW system.
Security Problem in PoS
5.3. Satoshi Consensus Algorithm
5.4. Proof of Luck (PoL) Algorithm
5.5. Consensus Algorithm for Private Blockchain
Tournament Consensus Algorithm (TCA)
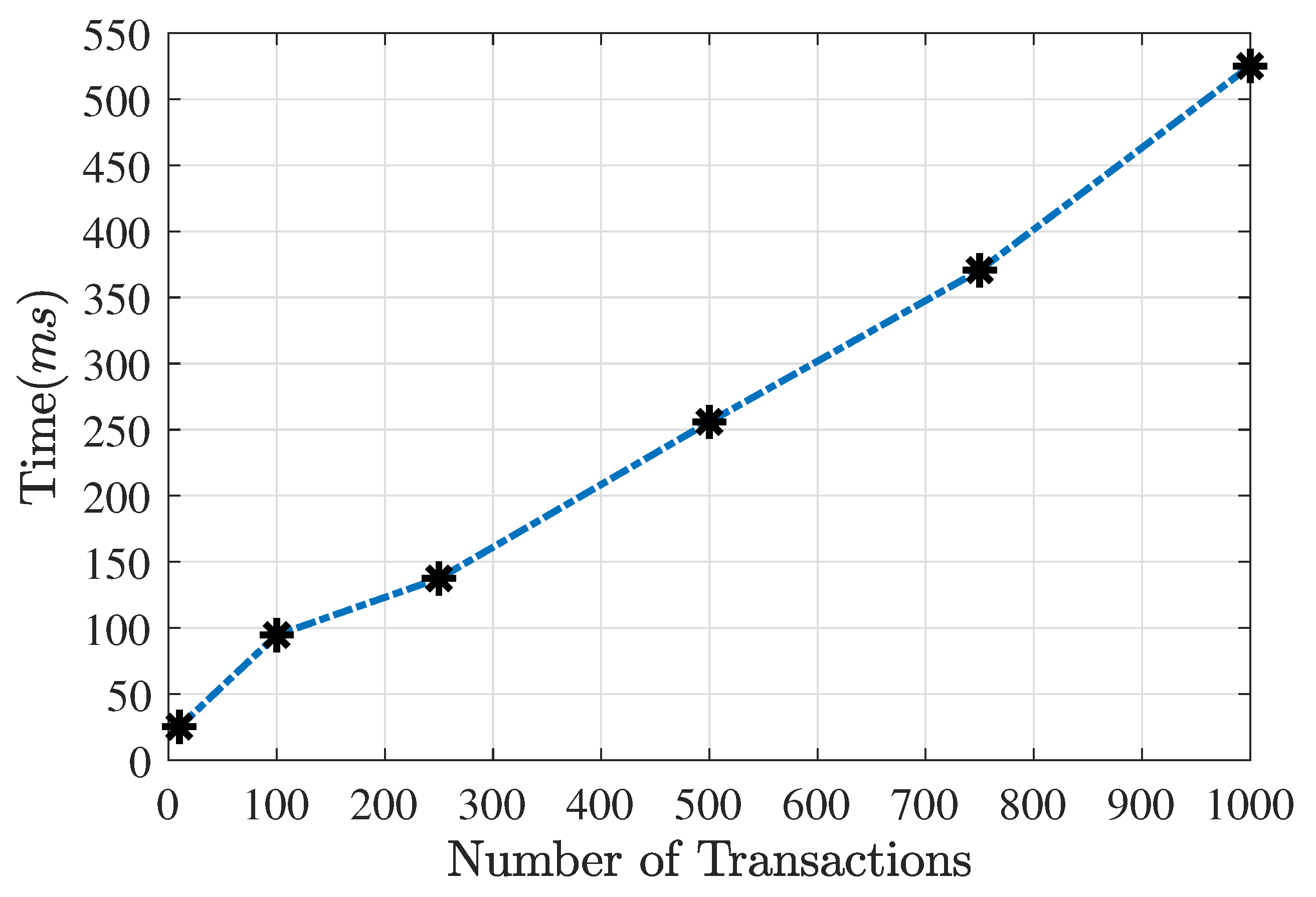
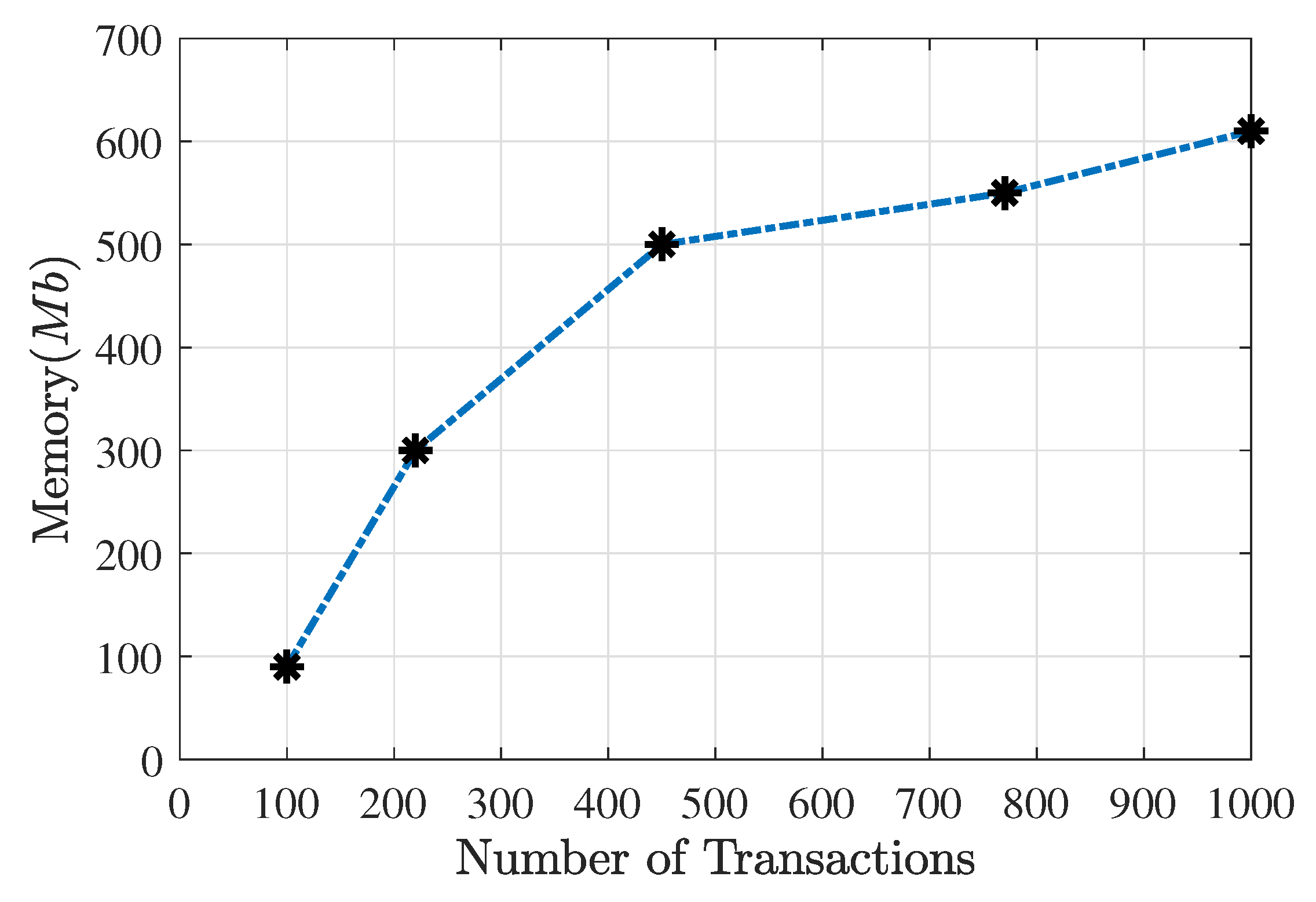
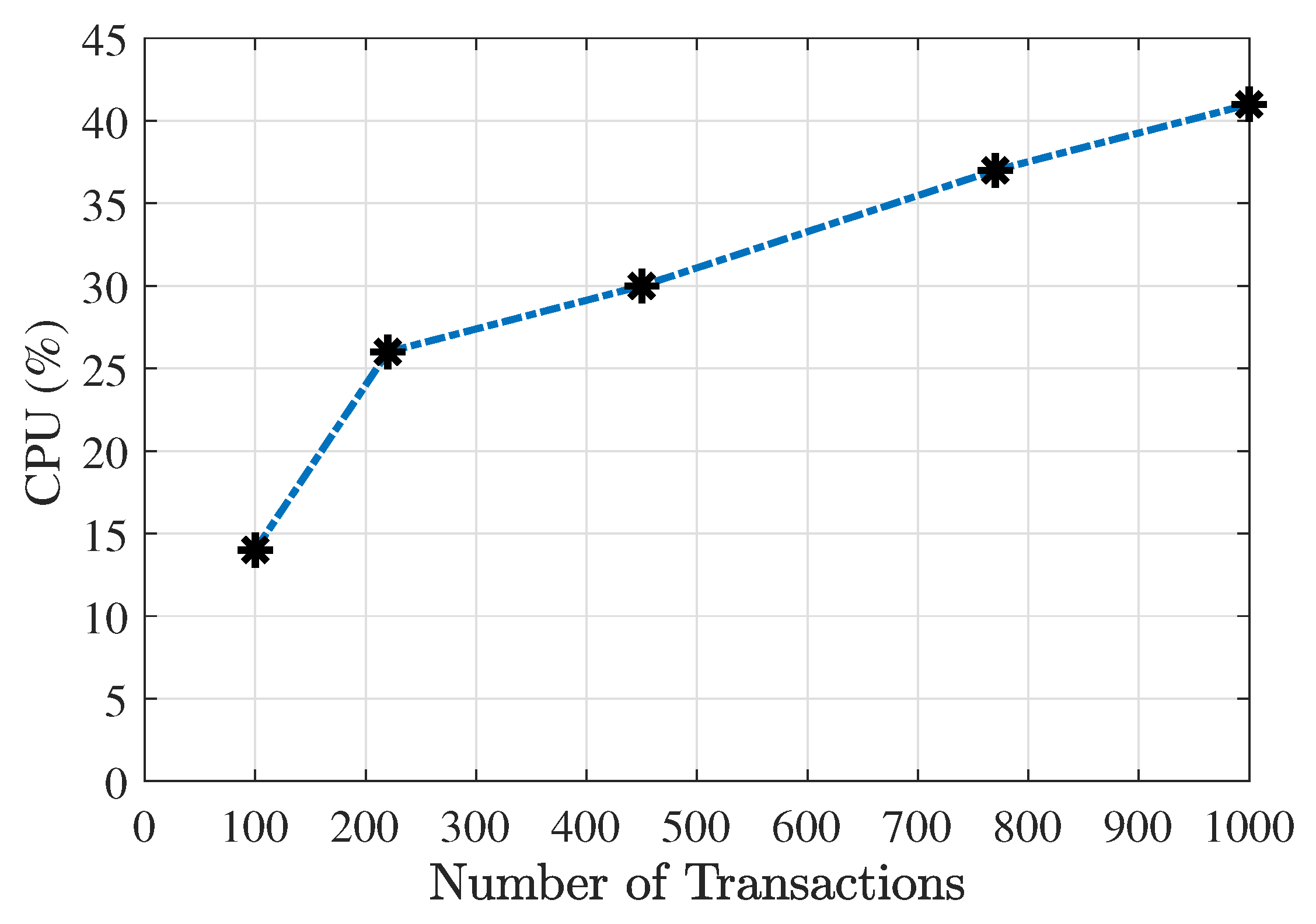
6. System Performance Results
- Processor: Intel Core i5 750, 2.66 GHz of 4 Cores.
- RAM Memory: 4 GB.
- HDD: 512 GB.
- Network Card: Intel 82574L Gigabit Ethernet NIC.
- OS: Linux Ubuntu 18.04.
- If the number of users is not so high, adjusting the number of transactions setting a limit of CPU usage. For example with 30%, and according to Figure 8, could be managed four hundred fifty (450) transactions.
- In special dates, where thousands of transactions could be made, (for example popular elections) it could be possible to maintain the number of transactions (1000 transactions), but dedicating some special machines with better characteristics for creating and broadcasting transactions when a block is mined.
7. Conclusions and Future Work
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| MDPI | Multidisciplinary Digital Publishing Institute |
| ICT | Information and communication technologies |
| e-ID | Electronic identity document |
| BCT | Blockchain technology |
| CLI | Changeable laser image |
| PKC | Public key cryptography |
| PIN | Personal identification number |
| OTP | One-time password |
| ZKP | Zero-knowledge proofs |
| RFID | Radio frequency identification |
| NFC | Near field communication |
| PoW | Proof of work |
| PoS | Proof of stake |
| PoL | Proof of luck |
| TEE | Trusted execution environments |
| TCA | Tournament consensus algorithm |
References
- Supriyanto, A.; Mustofa, K. E-gov readiness assessment to determine E-government maturity phase. In Proceedings of the 2016 2nd International Conference on Science in Information Technology, ICSITech 2016: Information Science for Green Society and Environment, Balikpapan, Indonesia, 26–27 October 2016; pp. 270–275. [Google Scholar]
- Registraduria Nacional del Estado Civil. Available online: https://www.registraduria.gov.co/ (accessed on 18 September 2019).
- Ansari, A.Q. E-Document retrieval using rough-set theory. In Proceedings of the ICIIP 2011 International Conference on Image Information Processing, Shimla, India, 3–5 November 2011. [Google Scholar]
- Waldmann, U.; Vow, S.; Sven, T.; Poller, A. Electronic Identity Cards for User Authentication—Promise and Practice. IEEE Secur. Priv. 2012, 10, 46–54. [Google Scholar]
- Policia Nacional de Colombia. Available online: https://www.policia.gov.co/ (accessed on 18 September 2019).
- Haque, M.A.; Khan, N.Z.; Khatoon, G. Authentication through keystrokes: What you type and how you type. In Proceedings of the 2015 IEEE International Conference on Research in Computational Intelligence and Communication Networks, ICRCICN, Kolkata, India, 20–22 November 2015; pp. 257–261. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 10 January 2020).
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Bocek, T.; Rodrigues, B.B.; Strasser, T.; Stiller, B. Blockchains everywhere—A use-case of blockchains in the pharma supply-chain. In Proceedings of the IM 2017—2017 IFIP/IEEE International Symposium on Integrated Network and Service Management, Lisbon, Portugal, 8–12 May 2017; pp. 772–777. [Google Scholar]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Future Gener. Comput. Syst. 2017. [Google Scholar] [CrossRef] [Green Version]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends. In Proceedings of the 2017 IEEE 6th International Congress on Big Data, (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar] [CrossRef]
- Solat, S.; Potop-butucaru, M. ZeroBlock: Preventing Selfish Mining in Bitcoin. Ph.D. Thesis, Sorbonne Universites, Paris, France, 2016. [Google Scholar]
- Eyal, I.; Sirer, E.G. Majority is not Enough: Bitcoin Mining is Vulnerable. In Proceedings of the 18th International Conference on Financial Cryptography and Data Security, Barbados, Federation of the West Indies, 3–7 March 2014; Volume 8437, pp. 436–454. [Google Scholar] [CrossRef]
- Zhao, X.; Chen, Z.; Chen, X.; Wang, Y.; Tang, C. The DAO attack paradoxes in propositional logic. In Proceedings of the 4th International Conference on Systems and Informatics, ICSAI 2017, Hangzhou, China, 11–13 November 2017; pp. 1743–1746. [Google Scholar] [CrossRef]
- Apostolaki, M.; Zohar, A.; Vanbever, L. Hijacking Bitcoin: Routing Attacks on Cryptocurrencies. In Proceedings of the IEEE Symposium on Security and Privacy, San Jose, CA, USA, 22–26 May 2017; pp. 375–392. [Google Scholar] [CrossRef] [Green Version]
- Singh, A.; Ngan, T.W.; Druschel, P.; Wallach, D.S. Eclipse attacks on overlay networks: Threats and defenses. In Proceedings of the IEEE INFOCOM, Barcelona, Spain, 23–29 April 2006; pp. 1–12. [Google Scholar] [CrossRef] [Green Version]
- Heilman, E.; Kendler, A.; Zohar, A.; Goldberg, S. Eclipse Attacks on Bitcoin’s Peer-to-Peer Network. In Proceedings of the USENIX Security Symposium, Washington, DC, USA, 12–14 August 2015; pp. 129–144. [Google Scholar]
- Aggelos Kiayias, G.P. On Trees, Chains and Fast Transactions in the Blockchain. In Proceedings of the International Conference on Cryptology and Information Security in Latin America, Havana, Cuba, 20–22 September 2017. [Google Scholar] [CrossRef] [Green Version]
- Natoli, C.; Gramoli, V. The Balance Attack or Why Forkable Blockchains are Ill-Suited for Consortium. In Proceedings of the 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, DSN 2017, Denver, CO, USA, 26–29 June 2017; pp. 579–590. [Google Scholar] [CrossRef]
- Saia, R. Internet of Entities (IoE): A Blockchain-based Distributed Paradigm to Security. arXiv 2018, arXiv:1808.08809. [Google Scholar]
- Delgado-Mohatar, O.; Fierrez, J.; Tolosana, R.; Vera-Rodriguez, R. Blockchain and biometrics: A first look into opportunities and challenges. Adv. Intell. Syst. Comput. 2019, 1010, 169–177. [Google Scholar] [CrossRef] [Green Version]
- Prause, G. E-Residency: A business platform for Industry 4.0? Entrep. Sustain. Issues 2016, 3, 216–227. [Google Scholar] [CrossRef] [Green Version]
- Garcia, P. Biometrics on the blockchain. Biom. Technol. Today 2018, 2018, 5–7. [Google Scholar] [CrossRef]
- Ministerio del Interior España. Guía De Refernecia Del DNIE Con NFC. Available online: https://www.dnielectronico.es/PDFs/Guia_de_Referencia_DNIe_con_NFC.pdf (accessed on 10 January 2020).
- Andrulevičius, M. Methods and applications of optical holography. Mater. Sci. 2011, 17, 371–377. [Google Scholar] [CrossRef] [Green Version]
- Chan, H.T.; Hwang, W.J.; Cheng, C.J. Digital hologram authentication using a hadamard-based reversible fragile watermarking algorithm. IEEE/OSA J. Disp. Technol. 2015, 11, 193–203. [Google Scholar] [CrossRef]
- Hanchez, D. A Comparative Study of Software Protection Tools Suited for E-Commerce with Contributions to Software Watermarking and Smart Cards. Ph.D. Thesis, Univesité Chatolique de Louvain, Ottignies-Louvain-la-Neuve, Belgium, 2003. [Google Scholar]
- Duncan, R. An Overview of Different Authentication Methods. Available online: https://www.sans.org/reading-room/whitepapers/authentication/overview-authentication-methods-protocols-118 (accessed on 10 January 2020).
- Nagel, R.H. System and Method for Production and Authentication of Original Documents. U.S. Patent 7080041, 18 July 2006. [Google Scholar]
- Hoang, B.; Caudill, A. Biometrics; Technical Report; IEEE: Piscataway, NJ, USA, 2012. [Google Scholar]
- Liu, S.; Silverman, M. Practical guide to biometric security technology. IT Prof. 2001, 3, 27–32. [Google Scholar] [CrossRef]
- National Science and Technology Council. Biometrics in Goverment POST-9/11—Advancing Science, Enhancing Operations. Available online: https://fas.org/irp/eprint/biometrics.pdf (accessed on 10 January 2020).
- Jain, A.; Feng, J.; Nandakumar, K. Fingerprint matching. Computer 2010, 43, 36–44. [Google Scholar] [CrossRef]
- Moi, S.H.; Rahim, N.B.A.; Saad, P.; Sim, P.L.; Zakaria, Z.; Ibrahim, S. Iris biometric cryptography for identity document. In Proceedings of the SoCPaR 2009—Soft Computing and Pattern Recognition, Malacca, Malaysia, 4–7 December 2009; pp. 736–741. [Google Scholar]
- Wayman, J.; Jain, A.; Maltoni, D.; Maio, D. Biometric Systems—Technology, Design and Performance Evaluation; Springer: London, UK, 2005; pp. 1–369. [Google Scholar]
- Thing, V.L.L.; Ying, H.M. Rainbow Table Optimization for Password Recovery. Int. J. Adv. Softw. 2011, 4, 479–488. [Google Scholar]
- Vaidya, S.A.; Bhosale, V. Invisible touch screen based PIN authentication to prevent shoulder surfing. In Proceedings of the 2016 International Conference on Inventive Computation Technologies (ICICT), Coimbatore, India, 26–27 August 2016; pp. 1–4. [Google Scholar]
- Martín-Fernández, F.; Caballero-Gil, P.; Caballero-Gil, C. Authentication Based on Non-Interactive Zero-Knowledge Proofs for the Internet of Things. Sensors 2016, 16, 75. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Fisher, R.; Lyu, M.; Cheng, B.; Hancke, G. Public key cryptography: Feasible for security in modern personal area sensor networks? In Proceedings of the IEEE International Conference on Industrial Technology Taipei, Taiwan, 14–17 March 2016; pp. 2020–2025. [Google Scholar]
- Murrell, S.; Einspruch, N.G. Electronic identification, personal privacy and security in the services sector. In Proceedings of the 5th International Conference Service Systems and Service Management—Exploring Service Dynamics with Science and Innovative Technology, ICSSSM’08, Melbourne, VIC, Australia, 30 June–2 July 2008. [Google Scholar]
- Liu, Y.; Li, J.; Guizani, M. PKC based broadcast authentication using signature amortization for WSNs. IEEE Trans. Wirel. Commun. 2012, 11, 2106–2115. [Google Scholar]
- Yaakob, W.F.H.; Manab, H.H.; Adzmi, S.N.M. Smart card chip design implementation on ARM processor-based FPGA. In Proceedings of the 2014 IEEE 3rd Global Conference on Consumer Electronics, GCCE, Tokyo, Japan, 7–10 October 2014; pp. 294–297. [Google Scholar]
- Sigar, K.O.; Jared, O.K. A Critical Look of USSD Technology Adoption and Benefits. Int. J. Adv. Res. Comput. Sci. 2014, 5, 27–29. [Google Scholar]
- Siyang, Z. Deformed Two-Dimension Code Quick Recognition Algorithm Design and Implementation in Uncertain Environment. In Proceedings of the 2015 7th International Conference on Measuring Technology and Mechatronics Automation, ICMTMA 2015, Nanchang, China, 13–14 June 2015; pp. 322–325. [Google Scholar]
- Leithner, M.; Kieseberg, P.; Schrittwieser, S.; Munroe, L.; Mulazzani, M.; Sinha, M.; Weippl, E. QR code security. In Proceedings of the MoMM’2010—The Eighth International Conference on Advances in Mobile Computing and Multimedia, Paris, France, 8–10 November 2010; p. 430. [Google Scholar]
- Roberts, C.M. Radio frequency identification (RFID). Comput. Secur. 2006, 25, 18–26. [Google Scholar] [CrossRef] [Green Version]
- Sarma, S.E.; Weis, S.A.; Engels, D.W. RFID Systems and Security and Privacy Implications. In Proceedings of the Cryptographic Hardware and Embedded Systems, Redwood Shores, CA, USA, 13–15 August 2002; pp. 454–469. [Google Scholar]
- Jara, A.J.; Alcolea, A.F.; Zamora, M.A.; Skarmeta, A.F. Analysis of different techniques to define metadata structure in NFC/RFID cards to reduce access latency, optimize capacity, and guarantee integrity. IFAC Proc. Vol. 2010, 10, 192–197. [Google Scholar] [CrossRef]
- Shobha, N.S.S.; Aruna, K.S.P.; Bhagyashree, M.D.P.; Sarita, K.S.J. NFC and NFC payments: A review. In Proceedings of the 2016 International Conference on ICT in Business, Industry, and Government, ICTBIG, Indore, India, 18–19 November 2016; pp. 1–7. [Google Scholar]
- Juan, M.D.; Andrés, R.P.; Rafael, P.M.; Gustavo, R.E.; Manuel, P.C. A Model for National Electronic Identity Document and Authentication Mechanism Based on Blockchain. Int. J. Model. Optim. 2018, 8, 160–165. [Google Scholar] [CrossRef] [Green Version]
- Giang Truong, N.; Kyungbaek, K. A survey about consensus algorithms used in Blockchain. J. Inf. Process. Syst. 2018, 14, 101–128. [Google Scholar]
- Ittay Eyal, E.G.S. How to Disincentivize Large Bitcoin Mining Pools. Available online: http://hackingdistributed.com/2014/06/18/how-to-disincentivize-large-bitcoin-mining-pools/ (accessed on 18 September 2019).
- Miller, A.; Kosba, A.; Katz, J.; Shi, E. Nonoutsourceable scratch-off puzzles to discourage bitcoin mining coalitions. In Proceedings of the ACM Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 680–691. [Google Scholar]
- King, S.; Nadal, S. PPCoin: Peer-to-Peer Crypto-Currency with Proof-of-Stake. Available online: https://bitcoin.peryaudo.org/vendor/peercoin-paper.pdf (accessed on 10 January 2020).
- Vasin, P. BlackCoin’s Proof-of-Stake Protocol v2 Pavel. Available online: https://blackcoin.org/blackcoin-pos-protocol-v2-whitepaper.pdf (accessed on 10 January 2020).
- Bentov, I.; Gabizon, A.; Mizrahi, A. Cryptocurrencies without proof of work. In Proceedings of the International Conference on Financial Cryptography and Data Security, Barbados, Federation of the West Indies, 22–26 February 2016. [Google Scholar]
- Milutinovic, M.; He, W.; Wu, H.; Kanwal, M. Proof of Luck: An efficient blockchain consensus protocol. In Proceedings of the SysTEX 2016—1st Workshop on System Software for Trusted Execution, Colocated with ACM/IFIP/USENIX Middleware 2016, Trento, Italy, 12–16 December 2016; pp. 2–7. [Google Scholar]




| ID Number | 101 |
| Serial number | 1 |
| Class | Notary |
| Type | Civil status |
| Information | Married |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Páez, R.; Pérez, M.; Ramírez, G.; Montes, J.; Bouvarel, L. An Architecture for Biometric Electronic Identification Document System Based on Blockchain †. Future Internet 2020, 12, 10. https://doi.org/10.3390/fi12010010
Páez R, Pérez M, Ramírez G, Montes J, Bouvarel L. An Architecture for Biometric Electronic Identification Document System Based on Blockchain †. Future Internet. 2020; 12(1):10. https://doi.org/10.3390/fi12010010
Chicago/Turabian StylePáez, Rafael, Manuel Pérez, Gustavo Ramírez, Juan Montes, and Lucas Bouvarel. 2020. "An Architecture for Biometric Electronic Identification Document System Based on Blockchain †" Future Internet 12, no. 1: 10. https://doi.org/10.3390/fi12010010





