The extracted articles which have been identified to provide significant research contributions on the examined topic are presented in
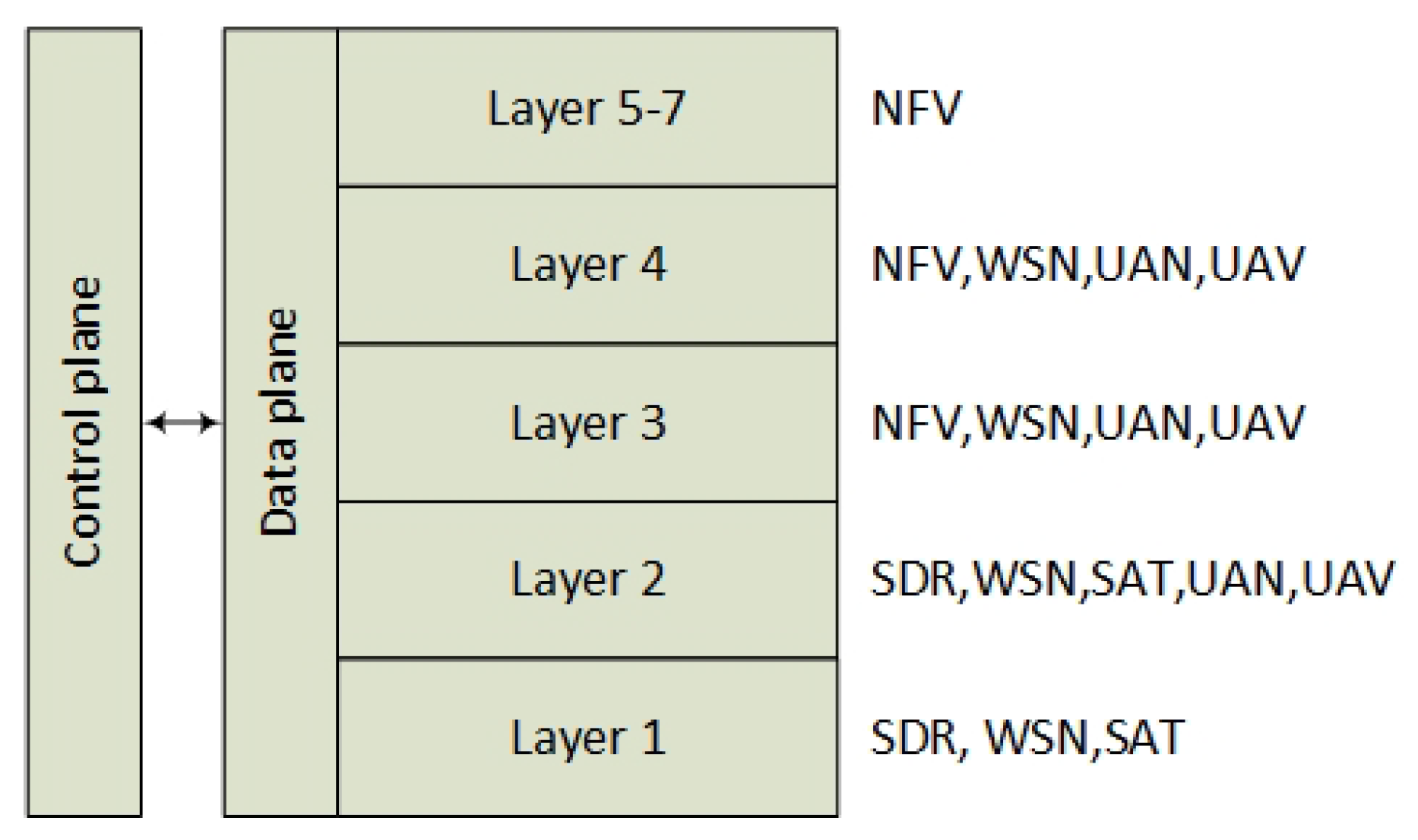
Table 1. Furthermore, in this section, we discuss these articles, categorizing them in accordance with their research contributions. The articles have been classified in accordance with their application domain (as mentioned by the articles’ authors: aerial, coalition, distributed, heterogeneous, military, mission critical, mobile ad hoc, naval, and tactical networks), their research contribution (as extracted: architectures, basic evaluation, tools, services, control systems), their scope (as extracted: basic evaluation, design and management, monitoring and control, policy based management, resource sharing, security, and simulations), the layer that the contribution is focused on (as extracted: all, application, control, physical), and finally with respect to the extent of their focus on security (as extracted: no, yes, only mentioned).
4.1. Architectures
A multitude of articles in this category investigate topics related to network monitoring and control. Nobre et al. [
15] proposed a battlefield networking architecture, enabling the deployment of SDN based applications and policies. The article examines in detail the benefits and disadvantages of (i) centralized, (ii) hierarchical, and (iii) federated approaches, comparing the two later and discussing in detail the supported policy based management solutions. Furthermore, the authors briefly discuss security implications and proceed by examining two use cases related to (i) bidirectional video streaming, and (ii) task coordination. Overall, the article is comprehensive and consistent with current research trends, although further evaluation is suggested. Furthermore, Zacarias et al. [
16] proposed a joint exploration of the SDN and Delay Tolerant Network (DNT) concepts, in order to address the specific constraints and problems arising at the last-mile Tactical Edge Networking (TEN). The proposed approach takes under consideration the resource constrained devices used by troops in the field, while it benefits from the programmability of SDN, and the ability of DTN to handle link outages. Two use cases are examined in order to highlight the applicability of the proposed architecture. The first sets out a scenario that highlights some of the SDN features within network partitions supporting a non-elastic application. The second use case deals with the management of communication between heterogeneous nodes in the TEN, which spread across different partitions.
Mihailescu et al. [
17] suggested a prototype framework for (i) network control, (ii) traffic prioritization management, and (iii) radio/protocol integration, with the use of SDN for emergency response and military networks. Initially, the article contributes with a two-tier hierarchical SDN controller setup, which exposes a modular interface for the management of wireless networks. Furthermore, the authors proposed a framework that allows the integration and interoperability across distinct wireless network technologies. Both frameworks are presented in detail, related to the desired functionalities of (i) traffic prioritization, (ii) remote network management, and (iii) multiple radio integration. Accordingly, the authors present the results of their initial evaluation process, presenting a small scale prototype implementation. The article investigates an interesting research path, but further evaluation and development is required, since the presented validation approach is small in scale for comprehensively highlighting the overall benefits.
Moreover, Phemius et al. [
18] described an architectural framework for traffic management in tactical networks, combining elements of Mobile Edge Cloud (MED) and SDN, to allow optimal network reactivity to the wireless link variations. The proposed framework can be decomposed into four layers, namely: the (i) “waveform layer” which consists of the multiple deployed programmable radios, the (ii) “SDN layer” which contains a virtual switch and the SDN controller, the (iii) “application management layer” which is mapped to the MED where the applications run, and the (iv) “mobile edge controller” which is a module that bridges the other three layers. Channel state information are periodically measured and aggregated at the controller, which routes the traffic in accordance with these information and dedicated policies deployed within the “mobile edge controller”, in order to detect network saturation or bottlenecks and react accordingly. The authors have implemented the proposed architecture in a test-bed that emulates a platoon level tactical network, abstracting the backbone infrastructure, towards the validation of their results. The utilized test-bed is described in detail within the article, while two distinct scenarios are used for validation purposes that primarily relate to network management. Further validation is proposed, given the limited size of the examined topology, but also limitations related to node mobility and communication patterns, which have not been captured extensively under the realistic characteristics of tactical deployments. Nonetheless, the experimentation method is sound and provides viable insights towards future work, which as the authors suggest will include extended configurations.
White et al. [
19] proposed an SND and Network Function Virtualization (NFV) based architecture, within the highly mobile environment of Unamaned Aerial Vehicles (UAV) infrastructures. The proposed architecture aims at (i) improving situational awareness for pilots and payload operators during UAV missions, (ii) increasing continuity of services in deployments with weak backbone infrastructure, (iii) reduction of latency in applications related to situational awareness, and (iv) reduction of the requirements imposed on the backbone infrastructure in cases of outages or traffic spikes. Each UAV is defined as a host, with mobile ground vehicles operating as switches, which route traffic towards the pilots in command and mission payload operators, in accordance with predefined OpenFlow rules. The chained containers hosting the VNFs (Virtual Network Functions) are located in the ground vehicles, while the SDN controller is located at the central command center. The authors implement their architecture with Linux based chained containers for instantiation of the VNFs and the Python SDN controller. Validating their architecture, the authors utilize scenarios that focus on pilot saturation with alerts. The results support an improvement of situational awareness, due to the programmability of reports related to emerging challenges, and an overall improvement in terms of resilience. Furthermore, high mobility patterns are supported through the integrated distributed selection of resilient links with sufficient capacity and availability.
Kumar et al. [
20] describe a framework that leverages the benefits of the SDN paradigm, in order to guarantee end-to-end timing constraints in safety critical Real Time Systems (RTS). The advantage of using SDN in such systems is that it provides a centralized mechanism for developing and managing the system. Furthermore, such a global view is useful in providing the end-to-end delay limitation guarantees that are required. As the authors suggest, another advantage is that the hardware/software resources needed to implement the proposed framework are limited. A prototype is implemented as an application that uses the northbound Application Programming Interface (API) for the controller, which accepts a specification of flows that contain a classification, bandwidth requirements, and the delay constraints of each individual flow. The proposed solution is evaluated using the following two methods: (i) a performance exploration of the path layout algorithm design, and (ii) an empirical evaluation using Mininet, which demonstrate the effectiveness of the end-to-end delay guaranteeing mechanisms. As noted, most hardware switches limit the maximum number of queues that can be allocated to flows, while the presented realization mechanism reserves only one queue per port for each flow, leading to the depletion of available queues. Moreover, Spencer and Willink [
21] provide a basic evaluation of SDN within coalition networks, and address research challenges related to the dynamic ecosystem of military networks. In particular, the authors focus on dynamic wireless networks and network controller topologies, by presenting the identified challenges and vulnerabilities. The challenges are reflected by the constraints of military networks such as (i) limited bandwidth, (ii) unreliable wireless connectivity, (iii) dependencies of the network controllers, (iv) east–west control plane channels, and (v) data integrity in open networks. Overall, the main contribution of this article, is to present a summary of related challenges identified within the proceedings of a TTCP-C3I (The Technical Cooperation Program—Command, Control, Communications and Information Systems) group.
Finally, investigating design and management systems, Elgendi et al. [
22] propose a three-tiered SDN architecture of heterogeneous and highly dense low-power femtocells at the tactical edge, aiming to satisfy the increasing capacity demands while simplifying the management overhead and increasing scalability. The proposed architecture consists of (i) the physical layer, based on dense low-power femtocells, (ii) the control layer which acts as a local controller, and (iii) a management layer which acts as a global controller. Routing and Quality of Service (QoS) decisions are made at the control layer in coordination with the management layer, the latter also being responsible for handovers. Furthermore, the authors focus on mobility and session management, describing in detail the developed sequential processes and required subsystems. The authors use the Mininet simulator in order to validate their results and evaluate the suggested architecture. The results suggest that within the utilized scenario, the proposed three-tier architecture reduces the delay, while increasing the throughput. Furthermore, the performance of the suggested architecture is evaluated in different mobility scenarios, suggesting that in low speeds a smooth flow rate among femtocells is achievable, while in speeds over 30 km/h the use of hotspots or macrocells is required in order to enhance connectivity. The utilized simulation scenarios are aligned with the high level architectural requirements of tactical networks, although limitations in terms of the deployed number of nodes and mobility models are visible.
4.2. Control Systems
As in the previous subsection, the majority of articles with research contribution related to control systems have a scope that is targeted towards monitoring and control. Nazari et al. [
45] proposed an SDN framework for a fleet of ships that relies on multiple satellite communication systems for on-board communications. The SDN framework addresses practical issues in current naval networks, such as sharing and load balancing of multiple communication links, as well as overcoming constraints related to bandwidth limitations. To overcome link intermittence and outage, the authors propose the use of Multi Path Transmission Control Protocol (MPTCP), which improves end-to-end data delivery by creating several sub-flows under a TCP session. The cooperation between MPTCP and the SDN controller leads to an agile, bandwidth efficient, and robust naval network. The authors conducted SDN-SAT performance evaluation tests, using the Mininet emulator on a commodity laptop, where the SDN-SAT controller protocol and the MPTCP Linux kernel run on the same machine. Open vSwitch is used in order to emulate the switches, while the initial results are promising in terms of functionality support and performance, although the performance of SDN and MPTCP is not addressed when the underlying network consists of a large number of ship nodes. Additionally, Du et al. [
56] designed and implemented SDN-SAT traffic optimization algorithms and associated SDN protocols on the SDN network emulator Mininet, with focus on naval surface fleets utilizing satelite communication systems. The SDN emulation testbed uses Mininet 2.1.0, Floodlight 1.2 (for the controller), OpenFlow 1.3 Software (for the switch) and MPTCP Linux Kernel Implementation v0.90. The Flow Deviation Method (FDM) is used as a network-wide optimal load-balancing solution that maximizes total throughput and minimizes traffic flow delay and jitter, while this optimization is carried out via a central controller in a Software Defined Networking (SDN) framework. It must be noted that the FDM algorithm convergence time and control overhead (in terms of SATCOM bandwidth) exchanged between SDN switches and their controller are not addressed in this work.
Also focusing on naval networks, Lee et al. [
43] proposed an SDN based Naval Ship System (NSS) and an algorithm called “Real-time Transmission via Flow-rate-control” (RTF) for environment specific optimization. With the proposed algorithm, SDN is employed as a new network architecture for the NSS, in order to control the QoS of real-time data over a tactical scenario. An optimization problem in terms of delay and prioritization is formulated, in order to achieve real-time transmission over SDN based NSSs. Consequently, a dual-decomposition method is applied in order to solve the non-convex optimization, while the authors measure the performance of the proposed solution by employing a tailored Floodlight SDN controller. The proposed SDN-based NSS is virtually established using Mininet, in order to verify the efficiency of the algorithm. The network topology used for the executed experiments is composed of 500 nodes and eight gateways, while Floodlight V1.1 and OpenVswitch are utilized for the implementation. Finally, the traffic of each node is generated individually, by utilizing the Hierarchical Multi-level On/Off Source (HMLOS) traffic model.
In respect to coalition operations, McLaughlin et al. [
42] proposed an SDN based framework for the mobility management of operational nodes within coalition military environments. The examined problem is analyzed in depth by the authors, providing significant insights in terms of operational, functional, and security constraints and requirements. The proposed framework seeks to implement Protected Core Networking (PCN) utilizing SDN, where PCN separates the transport and information domains, towards multinational networks that provide flexible and secure transport services. The authors describe in detail three logical topologies for the SDN controller, namely: (i) centralized, (ii) partially-meshed, and (iii) extension to static hosts.
Within the same application domain, Pham et al. [
31] summarized a set of research challenges related to Content Based Networking (CBN) in military coalition networks. As presented by the authors, in a joint military operation, the key focus is to bring together different partners into a single mission, maintaining the ability to securely share data across the distinct teams. Furthermore, it is required that the network operators are capable of performing analytics and maintain service related situational awareness in a resource constrained network. SDN is promoted by the authors as an enabler for CBN in respect of easing the complexity, and allowing the dynamic discovery of distributed information. However, centralized network control, such as OpenFlow, does not fit with disruptive networks. The paper suggests placing future research focus on: (i) hybrid SDN in order to allow network independence from the controllers, (ii) east–west control plane communication between network controllers, (iii) security implications related to dynamic distributed services, (iv) content aware networking by mapping the service request to the network control, and (v) distributed analysis in order to derive human situational understanding.
Also focusing on coalition networks, Mishra et al. [
40] examined how the principles of SDN can be utilized in order to improve cyber situational awareness in coalition environments within military networks. The authors discuss the adaptation of the Observe, Orient, Decide, Act (OODA) loop within SDN in order to improve security awareness. The OODA loop describes a decision-making process and is reflected in an SDN controller application. The authors also suggest that an east–west communication protocol is required for controllers to share what they have learned. The article explains comprehensively the concepts related to the OODA loop but does not provide an extensive discussion over the corresponding requirements and constraint for its adaptation on SDN. Consequently, Mishra et al. [
28] examined the application of SDN across military coalition operations, proposing a mechanism for enabling dynamic Communities of Interest (CoI) within these environments, and evaluating such interoperability architectures in accordance with key performance metrics. Furthermore, this article provides a comprehensive overview of tactical communities of interest and the underlying constraints towards their deployment and management. The authors proceed by merging the two, and discussing the topic of Software Defined Coalitions (SDC), as the mechanism that is capable of facilitating the operation of dynamic tactical CoIs. Accordingly, they identify three interoperability levels, namely: (i) network, (ii) network and storage, and (iii) network, storage, and compute. They clarify that (ii) combines mechanisms from SDN and Software Defined Storage, while (iii) builds upon the concept of Software Defined Environments. Consequently, the article proposed three types of architectures, namely: (i) simplification, (ii) brokered, and (iii) federated, comparing the three in terms of complexity, trust, and standardization. The presentation and discussion of the proposed mechanisms is sound and comprehensive, although further scenario based validation/verification can be desirable.
With focus on aerial networks, Iqbal et al. [
58] proposed an SDN and SDR architecture that can predict network outage in aerial networks. Under the assumption that aerial flights have fixed orbits, the authors suggest that the radio can inform the centralized controller about its future position, allowing for the flow routes and radio links to be switched in advance and prior to network outege. Hence, the availability is expected to be increased by the use of predictive SDN. The presented architecture is based on the assumption that the radio link outage can be predicted. Accordingly a corresponding architecture is proposed and tested in a virtual environment with OpenDaylight, Quagga, and OVS. The availability is tested by comparing network convergence for Open Shortest Path First (OSPF), reactive SDN (LLDP) and proactive SDN, where the proactive SDN showed maximum availability. Nevertheless, it must be noted that the proposed solution is not compared with overlay networks such as Multiprotocol Label Switching (MPLS) with segment routing.
Within the application domain of military networks, the majority of articles is focused towards policy based management. Skappel [
47] presented a master thesis with the objective of testing how an SDN controller can be used as a tool for controlling traffic in a dynamic environment. This thesis shows that SDN can allow network monitoring, and utilize this input in combination with predefined policies in order to prioritize, police, ensure QoS, and dynamically adjust the flows for different controllers. Wrona et al. presented two consecutive articles withing the same application domain and scope [
30,
39]. Within these articles, the authors discuss content-based security policies at different levels in the OSI stack, and present a proof of concept implementation in an SDN environment. They base their security concept on content based protection and release policies developed by NATO. The principle is that an information object is not labeled by a sensitivity tag, but it is labeled by a content tag that describes the object. Access control is based on the authentication of both the user and the terminal, while if both policies are accepted then the system release the object to the user. In the SDN context, a network packet header information can also have a content label that defines a security label. Their first article shows a proof of concept implementation of the proposed solution by retrieving information from different network layers, while the second article shows how an SDN controller that calculates the whole path in the network can also make the path itself a security label. The proof of concept implementation showed that the packet forwarding path can be protected in this manner. Hence, different paths can have different security protection levels, and the forwarding path can be decided based on content and access levels.
Nguyen et al. [
24] presented a short review of military policy based management methods and suggest a model for verifying, prioritizing and deploying a group of policies based on SDN. The core of the article is a graph model that detects conflicting network polices within the sum of applied network policies. The output of the model is a set of resources that a node can access. In order to detect conflicting policies, the authors suggested a step by step procedure to conform the policy and deploy it in SDN. The authors used a standard SDN controller with virtual switches to deploy policies across SDN. The core of this article relates to network policies and deconflictation, while the validation focuses primarily on policy deployment as OpenFlow rules. Moreover, Armando et al. [
29] proposed a method for facilitating the specification of access control policies in accordance with the NATO—Content Based Protection and Release model (CBPR). The CBPR model is built upon the Attribute Based Access Control (ABAC) model, and supports the specification of access control policies in complex organizations and coalitions, with extended variety of deployed resources. Accordingly, the authors propose the replacement of monitor based policy enforcement with cryptographic enforcement, in order to reduce the administrative burden, and enhance performance specifically within cloud and SDNs. The suggested solution relies on Cipher text-Policy Attribute-Based Encryption (CP-ABE), for which as the authors describe “The key idea is that a user should be able to decrypt a ciphertext only if he/she holds a key associated to certain attributes, under the assumption that user keys are issued by some trusted party”. Furthermore, the authors propose the adoption of this method to SDNs, for the enforcement of protection policies (during message forwarding decisions) in accordance with specific node and link attributes. The aforementioned statement is promoted as a suggestion by the authors, while deployment and validation is required.
Mulec et al. [
32] proposed a distributed flow controller for mobile ad hoc networks, seeking to provide dynamic reconfiguration and to improve security. The functions of the controller are (i) provisioning of AAA (authentication, authorization and accounting) services, (ii) flow management across the network nodes, (iii) centralized network traffic control, and (iv) enforcement of security policy. Unicast, multicast and broadcast communication is supported, while suitable mechanisms are provided for the management of topology changes. A core component of the proposed system is the selection mechanism, which establish the number of required controllers and their prioritization. This mechanism is mathematically analyzed, and tested within a test-bed consisting of seven wireless nodes providing positive initial results. The article provides a small scale validation, while further testing is recommended, primarily related to the size of the network and the tested mobility patterns. Furthermore, Poularakis et al. [
55] proposed a set of novel architecture designs for SDN-enabled mobile ad hoc networks in the tactical edge, discussed the challenges raised by the ad hoc and coalition network environment, and presented corresponding solutions. The proposed approaches build on experimental evaluations, utilizing theoretical results from SDN deployments in large backbone networks. The study provides useful insights on the examined environment, yet security related aspects could benefit from further evaluation.
Qing et al. [
26] described an optimization algorithm that can be used for prioritizing service requests in military operations. According to the article, when a network does not have enough resources to serve all requests, these can be prioritized based on a predefined policy. To enable service prioritization, a set of resources that are required by the service must be prioritized. In the context of SDN, this primarily concerns prioritization of traffic on network devices. The authors suggest precombining these resources into groups, and proposed an algorithm to optimize this precombination. The authors suggested two models of optimization, where the provided results show that precombination of resource dispatching improves the network performance.
Furthermore, Bouet et al. [
33] proposed a DIstributed SDN Control (DISCO) plane which allows handling the distributed and heterogeneous nature of modern mission-critical networks. The proposed approach relies on a per domain organization, where each DISCO controller is in charge of an SDN domain, using a lightweight and manageable publish–subscribe mechanism for sharing aggregated local and network-wide information with neighbor SDN controllers. Furthermore, the authors demonstrate how DISCO dynamically adapts to heterogeneous network topologies, while providing classic functionalities such as end-point migration and being resilient enough to survive disruptions and attacks. The authors implement DISCO on top of Floodlight, an OpenFlow controller, and the Advanced Message Queuing Protocol (AMQP). The network is emulated using Mininet to create topologies and instantiate Open vSwitch switches and virtual hosts. Mininet is hosted on a dedicated VM (Virtual Machine) and the controllers are hosted on separate VMs. To measure performance, the authors show an evaluation of its functionalities on an emulated SDN according to two use cases: (i) inter-domain connectivity disruption and (ii) migration of a virtual machine. The results show how DISCO dynamically adapts to heterogeneous network topologies, while being resilient enough to survive disruptions and attacks, and further being able to provide classic functionalities such as end-point migration.
Additionally, Chen et al. [
51] proposed a transmission framework for Software Defined-Airborn Tactical Networks with the aim of providing a fundamental infrastructure for improving the communications capability between the control and data planes. Furthermore, the authors proposed a dedicated communication protocol, aiming at transmitting the non-elastic C/D information in both a reliable and timely manner. The authors conducted a simulation for the purpose of illustrating the performance of their scheme. They built a simplified avionics network in EXata 5.1 for every aircraft, and regarded an avionics network as a node of the SD-ATN. The simplified avionics network, which is considered as the common node, includes two devices that implement the functions of the platform controller and SD-ATN transmission system, respectively. The avionics network that represents the active control node includes one more device that implements the functions of the SD-ATN controller, while the devices within an aircraft are connected through wired links. Finally, Fagervoll [
50] explored how SDN can be incorporated, both physically and logically, within heterogeneous tactical networks. Being a Master’s thesis, this work provides a comprehensive introduction into the related concepts and underlying requirements, while the main contribution is focused towards the collection of network information for the establishment of topology mapping. The author evaluated three conceptual models and proposed an approach for topology mapping through local legacy routers.
4.4. Tools
With a research contribution related to tools, one article provided a basic evaluation related to tactical networks. In this, Spencer et al. [
46] assessed the integration of the SDN paradigm across tactical networks, discussing the expected benefits and potential threats. The article provides a comprehensive analysis of the characteristics of tactical networks, in conjunction with an overview of the architectural and operational attributes of SDN, aligning the two by extracting the expected benefits to the tactical user. These relate primarily to enhancements of information dissemination, service delivery, and link utilization. Furthermore, the authors provide an iterative assessment methodology regarding the performance gains by such an integration, the design options in respect to tactical SDN controllers, and challenges that need to be addressed. It must be noted that no extensive validation is provided within the article referring to the proposed methodology. Therefore, it is not clear if the results of the study are exhaustive, mutually exclusive, or if there are any identified interdependencies.
Furthermore, three articles within this sub-category have a scope related to security, either directly related to military or distributed networks. Wrona et al. [
44] described an OpenFlow-based test-bed for the validation of SDN security mechanisms—including both the mechanisms for protecting the SDN and the cross-layer enforcement of higher level policies, such as data-centric security policies. Such cross-layer security mechanisms are important in the context of software-defined infrastructure and implementation of new security paradigms, such as data-centric security. Furthermore, the authors demonstrate the functional correctness of the test-bed, as well as its suitability to provide validation and additional insight into the behavior of analytically designed security mechanisms. The authors present a low-cost implementation of a flexible SDN test-bed, specifically focused on security experimentation in respect to security services provided by SDN to both the network and application layer. The test-bed consists of seven switches (annotated S1 to S7), a controller, a server and a typical switch for VPN connection. It can be split into two networks: a control network (connections between the switches and the controller) and a data network (connections between the switches, including the server). There is also a VPN network allowing remote configuration of all test-bed nodes via SSH protocol. All switches use the Ubuntu 16.04 operating system and OpenVSwitch 2.1.1-based (OVS) implementation of OpenFlow protocol in bridge configuration. The test-bed can be also used for the validation of earlier results, obtained analytically or from emulation (e.g., Mininet) and simulation (e.g., ns-3) tools.
Lee et al. [
48] proposed a redesigned untraceable Blind Packet Forwarding (BPF) method, based on the Public-key Encryption with Keyword Search for Restricted Testability (PEKS-RT) algorithm, in which the specific host IP address cannot be guessed. The main feature of this approach is that when the source host encrypts the destination host address, it includes the source host’s private key, the destination host’s public key, and the destination host address as parameters for encryption. Another feature is that the destination host generates the trapdoor value using the destination host address, the source host’s public key and the destination host’s private key. A centralized SDN controller is used for reducing the overhead of routing data processing of the existing method, increasing this way the operational efficiency. The authors describe a prototype implementation for the blind packet forwarding using PEKS-RT. Their approach is realized in the SDN environment using the Mininet emulator, where Open vSwitch is used as a switch and Floodlight as a controller. The function of the Floodlight controller is expanded to implement the untraceable blind packet forwarding, and it can manage the trapdoor table and control the path using PEKS-RT. Stanford PBC library is used to generate key pairs, trapdoor values and encrypted addresses.
Furthermore, Soule et al. [
34] described active defensive deception in the context of distributed systems, and built a prototype that creates an alternate reality in which to trap, learn about, and manipulate adversarial actors without affecting normal and legitimate operations. This prototype, called KAGE, employs SDN and virtualization in order to create a malleable substrate in which deception can occur. The authors demonstrate a preliminary feasibility test of an active deception approach. The test implemented and successfully executed multiple variations of a demonstration scenario that integrates and exercises many of the major KAGE components, in order to orchestrate a brief deception campaign. The demonstration makes use two KAGE plugins: a port scan detector acting as a sensor, and an SQL injection detector adapted to work as both a KAGE sensor and actuator. The distributed nature of KAGEs’ building blocks adds complexity, in terms of dynamic distributed composition, and with respect to the timing expectations/challenges regarding interactions with networks, hosts, and services. Furthermore, deviation from expectations can provide indicators to attackers that they are being deceived.
Mishra et al. [
38] discuss the Global Environment for Network Innovation (GENI) deployment and research at the US Army Research Laboratory. GENI is a comprehensive test-bed technology to promote rapid network research and application development. It provides sliceable experimental spaces for conducting isolated computational experiment, and supports OpenFlow and other SDN features for conducting comprehensive network research. The Army Research Laboratory (ARL) deploys its own clearinghouse that can act as GENI authority for its own nodes, as well as for all other GENI nodes that come up on the Department of Defense (DOD) network. This customization helps ARL to stand up its node, without delegating its authority to an external entity. Moreover, Jalaian et al. [
41] developed a mathematical model in order to realize a unified programmable control plane for heterogeneous wireless networks. The developed framework characterizes the interaction between the physical, link, and network layers for the unified programmable control plane in a heterogeneous wireless network. By applying the framework on a throughput maximization problem, the authors show an application of the model on solving practical issues in a tactical network and gaining some theoretical insights on the optimal behavior of the unified programmable control plane for a heterogeneous wireless network. The authors present numerical results to study the performance of the unified control plane for wireless heterogeneous network. Simulation settings consider a randomly generated multi-hop wireless network with 30 nodes that are distributed in a 100 × 100 area. All units for distance, data rate, bandwidth, and power with appropriate dimensions are normalized, while at the network layer minimum-hop routing is employed. Additionally, Battiati et al. [
53] presented a Cyber Security Simulation Service (CSSS) platform, which provides a simulation environment for modeling the impact of cyber-attacks and related countermeasures in tactical networks using SDN. The CSSS integrates a scenario simulator, a network/cyber simulator, a graphical user interface, and a real SDN Controller. Furthermore, the authors showed the functionality of the CSSS in a specific use case, i.e., a black hole attack is performed and the BRAVO (A Black-hole Resilient Ad Hoc on demand distance Vector Routing for tactical communications) approach is utilized as a countermeasure.
Finally, Li et al. [
49] presented a hierarchical self-organizing SDN architecture for mobile tactical networks, where the network is dynamically self organized and partitioned into multiple temporary domains, while each domain is assigned with a node that operates as the local SDN controller. A corresponding protocol is proposed by the authors, including (i) a neighborhood discovery mechanism, (ii) a distributed network partition algorithm, and (iii) an abstraction of dynamics. The proposed mechanisms provide strong incentives towards future research and development, although extended verification and proof of concept experiments are recommended.
4.5. Basic Evaluation
Five articles provided a basic evaluation in respect to tactical, military, and naval networks with main focus on the control layer. Athmiya et al. [
37] demonstrated and evaluated the implementation of an OpenFlow SDN controller within tactical scenarios, seeking to identify how such implementations can enhance agility, scalability, and network management flexibility for the tactical edge. The article provides a comprehensive presentation of OpenFlow, in terms of overall operation, matching criteria and internal messaging between the controller and the switches. Accordingly, the article briefly describes the Mininet prototyping environment, which is further utilized for the development of an experimental setup, towards verifying the capacity of OpenFlow to satisfy the requirements of the tactical environment. The examined test cases refer to (i) diversion networking, (ii) central policy management for access control lists, and (iii) the distribution of SDN controllers. The article is comprehensive, and promotes further evaluation for providing proof that OpenFlow can be aligned with the requirements of the tactical environment.
Dilmaghani and Kwon [
35] proposed an SDN based approach for load balancing within naval military scenarios. The authors construct an experimental setup using Mininet, and utilize Floodlight as the protocol for the communication among switches and the controller. The experimental setup consist of five WAN (Wide Area Network) switches, which correspond to three ships and two on-shore data centers. Furthermore, the scenario assumes three types of traffic with distinct priorities. The article offers a detailed presentation of the evaluation scenario details, while the results highlight the benefits of corresponding SDN implementations, in terms of network programmability and management automation, but also in terms of load balancing and reliability.
Additionally, Anderson [
52] described an investigation into five open-source controllers using a specific set of criteria based on the characteristics of these networks. A qualitative investigation compared the controllers based on their state handling and failure recovery mechanisms, and resulted in the selection of two controllers for further investigation. Further quantitative tests were performed on these two controllers, in order to determine which was more suitable for deployment in an airborne environment. Fonger et al. [
57] proposed an architecture that serves as a guide for current and future experimentation on trust management and protection in tactical SDN when used with mobile nodes in a coalition operation. However, this work does not discuss thoroughly the security of the information transported through the network, focusing on the protection and separation of different data flows. This separation needs to be robust and reliable, but it does not provide security services on the content of the flows. Finally, Spencer et al. [
36] identified the key types of messages used in OpenFlow, and how their overhead is influenced by network characteristics in military networks. Furthermore, the authors presented a series of mitigation measures for reducing or eliminating the overheads, some of which are possible to implement within the current SDN standards, while others require further extensions. The authors perform an experimental validation to quantify and confirm their analysis, where the scenario is implemented using Mininet with OpenVSwitch as the switching element, and netem for performing network simulation.