1. Introduction
In the
stable marriage problem, every vertex of an undirected bipartite graph,
G, represents either a woman or a man. Their sympathy for each person of the opposite gender is expressed by their
preference lists: the more beloved person has the higher rank. A marriage scheme is a matching,
M on
G. We say that such a scheme is
stable, if there is no pair of participants willing to leave their partners in order to marry each other. More formally: an edge,
,
blocks M, if
u and
v both are unpaired or prefer each other to their partners in
M. A matching
M is
stable, if there is no blocking edge in
G. Gale and Shapley [
1] were the first to state that a stable matching always exists. Their well-known deferred-acceptance algorithm finds a stable marriage in strongly polynomial time.
One of the most advanced extensions of the stable marriage problem is the
stable allocation problem. It was introduced by Baïou and Balinski [
2] in 2002. Here, we talk about jobs and machines instead of men and women. Edges have capacity and participants have quota on their matched edges. This quota stands for the time a job needs to get done and the time a machine is able to work in total. Edges are used for assigning jobs to machines, such that none of the machines spends more time on a job than the edge capacity allows them.
The goal is to find a feasible set of contracts, such that no machine-job pair exists where both could improve their states by breaking the scheme. Edge
e is
blocking, if it is unsaturated, and neither end vertices of
e could fill up its quota with at least as good edges as
e. An allocation,
x, is
stable, if none of the edges of
G are blocking. Baïou and Balinski [
2] give two algorithms to solve the problem: while their augmenting path algorithm runs in strongly polynomial time, the refined Gale-Shapley algorithm is more efficient in simple cases, e.g., on instances where all jobs get one of their best choices, it only needs sublinear time. Dean
et al. [
3,
4] succeeded in speeding up the first method, relying on sophisticated data structures, such as dynamic trees. They also extended the second one to the case of irrational data.
Stable allocations have been further generalized to
stable flows by Ostrovsky [
5] and Fleiner [
6]. Fleiner also gave a constructive proof for the existence of a stable flow in every network by solving a stable allocation problem in a modified network. In an instance of stable flow, special vertices are designated as terminals, and each non-terminal vertex has a preference list of its incoming and outgoing edges that specifies from which edges it prefers to receive flow and which edges it prefers to send flow along. Stable flows are well suited for modeling real-world market situations, as they capture the different trading preferences of vendors and customers.
We extend this model to the setting of
flows over time. Flows over time were introduced by Ford and Fulkerson [
7,
8]. In addition to the stable flow instance, we have transit times on the edges and a time horizon specifying the end of the process. We prove the existence of stable flows over time and, moreover, show that, for the case of an infinite (or sufficiently large) time horizon, there is a stable flow over time, which converges to a static stable flow. By introducing time to the stable flow setting, one can achieve a considerably more realistic and more interesting description of real market situations. With flows over time and transit times on the edges, we can model transportation problems or illustrate distances amongst the vendors.
Structure of the Paper: In
Section 2, we introduce the stable flow problem and present an elegant version of the Gale-Shapley algorithm that operates directly on the given network. We also give a simple proof of its correctness. In
Section 3, we present the stable flow over time problem and show the existence of stable flows, even in the case of networks with an infinite time horizon. We conclude the section by analyzing how different variations of storage at vertices can influence the stability of flows in a network.
2. Stable Flows
Although most bipartite matching problems can be easily interpreted as network flow problems, stability was defined for flows only in 2008 by Ostrovsky [
5]. He proved the existence and some basic properties of stable flows in acyclic networks. Two years later, Fleiner [
6] came up with a generalized setting and further results. In this paper, we use this general setting and build upon Fleiner’s remarkable achievements.
2.1. Basic Notions
We consider a network, , where D is a directed graph, whose vertices are partitioned into a set of terminals, , and non-terminal vertices, . Moreover, there is a capacity function, , on the edges. The digraph, D, might contain multiple edges, as well as loops. This concession forces us to slightly modify the structure of the preference lists: each vertex, , sets up a strictly ordered list of the neighboring edges instead of the neighboring vertices. For convenience, we consider the orderings on incoming and outgoing edges as two separate lists. The set of these lists are denoted by O. Vertex v prefers to , if has a lower number on v’s preference list than . In this case, we say that dominates at v and denote it by . The same notation is used for outgoing edges.
Definition 2.1 (flow).
A flow,
f, in network, , is a function, , such that the following properties hold: for all edges, ;
for all vertices, .
We would like to emphasize that we do not distinguish sources and sinks in S; their role is the same: they are the vertices in D that do not have to obey the Kirchhoff law.
Definition 2.2 (stable flow).
A blocking walk
of flow f is a directed walk, , such that all of the following properties hold:each edge, , , is unsaturated;
or there is an edge, , such that and ;
or there is an edge, , such that and .
A network flow is stable, if there is no blocking walk in the graph.
The network can be seen as a market situation, where the vertices are the traders and the edges connecting them are possible deals. All participants rank their partners for arbitrary reasons: e.g., quality, price or location. These rankings are the preference lists of our instance. Notice that edges do not necessarily correspond to deals involving the same product, and there may be cycles on the graph, even of a length of two. An unsaturated walk is a possible deal between vendors and . If they are suppliers or consumers (terminals) or can improve their situation using the unsaturated walk, then they will agree to send some flow along it and break the existing scheme.
It was shown by Fleiner [
6] that each instance,
, of the stable flow problem can be converted into an equivalent instance,
, of the stable allocation problem, such that every stable flow corresponds to a stable allocation and
vice versa. Since there always exists a stable allocation [
2], the existence of stable flows directly follows from the equivalence of stability on
and
. The construction shows that stable flows can be found in polynomial time.
Theorem 2.3 (Fleiner, 2010 [
6]).
There is a stable flow on every instance, .
Theorem 2.4 (Fleiner, 2010 [
6])
. For a fixed instance, each edge incident to a terminal vertex has the same value in every stable flow. The stable flow problem can be seen as a generalization of the stable allocation problem. We introduce two terminal vertices to G and connect s with all vertices representing jobs and t with all vertices representing a machine. The new edges get the quota of their non-terminal end vertex as capacity. Now, we orient all edges from s to the jobs, from the jobs to the machines and from the machines to t, in order to get a directed network. On this network, all stable flows induce a stable allocation on the original graph and vice versa.
2.2. Algorithms to Find Stable Flows
The stable allocation problem can be solved in polynomial time [
2,
4]. As mentioned in the introduction, the augmenting path algorithm is not always the most efficient way to find stable allocations; the Gale-Shapley algorithm terminates faster in some cases. It can be run on
in order to give a stable allocation, which yields a stable flow on
. Note that this holds for irrational data, as well. The fact that this method can be directly applied to instance
is briefly mentioned by Fleiner [
6]. In the following, we will show how to interpret the direct application of the Gale-Shapley algorithm on the network as a preflow-push-type algorithm and prove its correctness. We will provide two variants, a basic preflow-push variant that is easy to understand and one that resembles the alternating proposal/refusal scheme of the original Gale-Shapley algorithm.
Proposal and refusal pointers: For each vertex, , the algorithm maintains two pointers, and . The first pointer, , iterates through v’s list of outgoing edges from the highest to the lowest priority edge. It points to that edge along which v is currently willing to offer more flow. Likewise, iterates through v’s list of incoming edges from the lowest to the highest priority edge. It points to that edge that v is going to refuse next, if necessary. For technical reasons, we introduce one more element to each preference list: after passing through all neighbors, reaches a state encoded by . This means that v cannot submit any more offers. Likewise, initially, as v has no intention to refuse flow in the beginning.
Initialization: The algorithm starts by saturating all edges leaving the terminal set, i.e., for all with . We define the excess of a vertex, v, w.r.t. f, by , where denotes the set of incoming edges, while stands for the outgoing ones. Note that f initially is not a feasible flow, as for some non-terminal vertices, —we will call such vertices active.
Preflow-push variant:
The algorithm iteratively selects an active vertex, , and pushes as much flow as possible along , advancing the proposal pointer whenever the edge is saturated or an already refused edge is encountered. If reaches the zero-state before all excessive flow has been pushed out of the vertex, it continues by decreasing the flow on the incoming edge, , advancing the refusal pointer whenever the flow on the edge reaches zero. After a push operation, the excess of the vertex is zero, and another active vertex is selected. The algorithm terminates once there is no active vertex left. For a pseudo-code listing of this preflow-push approach, see Algorithm 1.
| Algorithm 1 Preflow-push algorithm. |
Initialize . Saturate all edges, leaving S. while do while do if then propose() else refuse() end if end while end while
|
Simultaneous variant: An alternative variant that resembles the Gale-Shapley algorithm more closely can be obtained by performing alternating rounds of proposal and refusal steps, respectively, on all active vertices simultaneously (cf., Algorithm 2). This variant of the algorithm will prove useful when analyzing stable flows in a time-expanded network later in this paper.
| Algorithm 2 Simultaneous push algorithm. |
Initialize . Saturate all edges, leaving S. while do for all do propose() end for for all do refuse() end for endwhile
|
procedurepropose() if ( or ) and then else advance(p[v]) end if end procedure
| procedure refuse() if and then else advance(r[w]) end if end procedure
|
A special execution of Algorithm 1 gives the McVitie-Wilson algorithm [
9] for the stable marriage problem. We can determine the choice of active vertices, while running Algorithm 1 on the flow instance defined by the stable matching instance. At initialization, the source sends one unit of flow to each vertex, symbolizing a man. The active vertex chosen arbitrarily in the first step is one of them. He proposes along his best edge, and the asked woman accepts the offer and sends the flow further to the sink. Now, the second man will be chosen arbitrarily; he proposes along his best edge. If any woman gets more than one offer, her vertex enters the active set, and she needs to be chosen next. Afterwards, the refused man must play the role of the selected vertex, and so on. This way, we run the deferred-acceptance algorithm by taking the men one by one to the instance, always setting up a current stable matching.
Theorem 2.5. If c is integral, both algorithms return an integral stable flow in at most iterations.
The proof is split into three parts:
Claim 1. Throughout the course of the algorithms, f is integral.
Proof. We prove this by induction. The claim is true after initialization, as the capacities of all edges are integral. Thus, before a call of refuse or propose, the excess of the corresponding vertex is integral, as well. This implies that the flow value of the corresponding edge is changed by an integral amount. ☐
Claim 2. Both algorithms terminate after steps.
Proof. In each call of propose, the flow value of the corresponding edge is increased by an integral amount (by claim 1), or the pointer p is advanced. Likewise, in each call of refuse, the flow value of the corresponding edge is decreased by an integral amount, or the pointer r is advanced. Once refuse is called for some edge, , the flow value cannot be increased by a propose call anymore. Thus, there can be only at most calls of propose and refuse. ☐
Claim 3. The algorithms return a stable flow.
Proof. After termination, f is a feasible flow, as the excess of every non-terminal vertex is zero. Now, suppose there is a blocking walk in the network. There are two reasons for leaving unsaturated edges in the network: either the edge was refused or there was no proposal along it using all its capacity; it stayed at least partly unexamined. We will study which case can come up at which position in the blocking walk.
If an unsaturated walk starts at a terminal vertex, then the first edge of it has been refused, since must try to fill all its adjacent edges with maximum capacity. If the walk ends at a terminal vertex, there was no full proposal along that edge in the algorithm, since terminal vertices do not refuse any flow. If the blocking walk starts at a non-terminal vertex, then there must be a dominated edge starting at the same vertex and having nonzero value. This proves that the unsaturated edge has been refused, because vertices submit offers along edges in their order in the preference list of the start vertex. A similar argument can applied to the end vertex of the blocking walk: there must be a dominated edge ending at the same vertex and having nonzero value. The unsaturated edge can not be a refused one, since we always refuse the worst edges.
The argument above shows that the blocking walk must start with a refused edge and end with a not fully proposed one. This means that along the walk, there has to be at least one refused edge, , and an at least partly unexamined one, . This implies that vertex v refused flow, although it has not filled up its outgoing quota, a contradiction. ☐
Corollary 2.6. If c is rational, both algorithms return a rational stable flow.
Proof. Any instance with a rational capacity vector can be transformed to an instance with an integral capacity vector by multiplying all capacities with their smallest common denominator. ☐
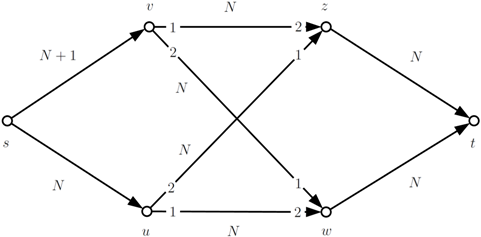
A simple network setting can illustrate how large capacities may cause a long running time. Note that this example is the flow extension of the allocation problem described by Baïou and Balinski [
2].
In the example above, , and N is an arbitrary large number. After saturating and , the simultaneous push algorithm saturates and and proposes along with one unit. This offer will be accepted by w, forcing it to refuse one flow unit along . Thus, u has to submit an offer to z, which needs to accept it and reject a flow unit from v. An alternating cycle of new offers and refusals will be made along , as long as there is any flow to refuse along and . This means, in total, N augmentations are along the cycle.
3. Flows over Time
3.1. Basic Notions
We are given a network, , consisting of a directed graph, D, some terminal vertices, , and a capacity function, , on the edges. The last element is the transit time function: . Besides these, an instance contains a time horizon, , as well. Loops and multiple edges are allowed in D.
Definition 3.1 (flow over time).
Functions, , for each edge form a flow over time
or dynamic flow
with time horizon, T, if they fulfill all of the following requirements: for
—this ensures that flow can be sent from u along an edge, , only if there is enough time left for it to reach v.
for all and
—capacity constraints hold all the time.
for all and
—flow conservation is fulfilled at every point in time.
Any dynamic flow problem can be converted into an ordinary flow problem with the help of the
time-expanded network,
. We create
T copies of
, with
denoting the
th copy of vertex
i. For every edge,
, and every
, we connect
with
. The vertices of
with a fixed index,
i, form a
timeslot. Though this construction reduces the flow over time concept to the static setting without transit times, the price of this simplification is a considerably larger time-expanded network,
, having a size linear in
T and, thus, exponential in the input size. This does not always cause a problem: in the maximum dynamic flow problem, there is always a temporally repeated maximum flow that can be found in polynomial time [
7,
8].
We extend the flow over a time instance to stable flows over time, by introducing preference lists. They have the same behavior as in the stable flow problem, and they do not change in time. The notion of stability can be extended to this instance the following way:
Definition 3.2 (stable flow over time).
A directed walk, ,
is a blocking walk
of flow over time, f, if there is a certain point in time, , such that all the following properties hold:each edge, , is unsaturated at time
or there is an edge, , such that and
or there is an edge, , such that and
A blocking walk, W, can be interpreted in a similar way as in the static case: if the two participants symbolized by the end vertices agree that sending some flow along W would improve their situation, then the scheme will be broken by them.
Note that a flow over time is stable, if and only if the corresponding flow in the time-expanded network is stable in the classical sense.
Theorem 3.3. For every and time horizon, , there is a stable flow over time.
Proof. A stable static flow exists in the time-expanded network. ☐
Corollary 3.4. In every stable flow over time with , the terminal vertices send and receive the same amount of flow in a fixed timeslot on all edges incident to them.
Proof. This follows from Theorem 2.4. ☐
Note that these two statements hold, even if the preference lists may change in time.
Remark 3.5. Without loss of generality, we can assume the graph to be simple and free of loops. If an edge, e, is a loop or parallel to another edge, we simply split this edge into two edges, , introducing a new vertex, . We assign capacities, , and transit times, and , to the new edges. As is a non-terminal and has only one incoming and one outgoing edge, it will never be the start or end vertex of a blocking walk. Furthermore, any blocking walk visiting corresponds to a blocking walk in the original graph using the edge, e, and vice versa.
As a result of this assumption, any propose or refuse operation on a vertex, , in the time-expanded network does not effect the state of any other copy, , of the same vertex.
Time-expanded variant of the preflow-push algorithm: In order to obtain structural insights on stable flows over time, we will apply Algorithm 1 in the time expanded network using a special order of the vertices: it picks a vertex, , from the underlying static network and handles all copies of v, starting at and ending at , processing each of them as long as it has excessive flow. We will call such a traversal of all copies of a vertex, v, by the algorithm a v-phase.
The following lemma gives important structural insights on the stable flow computed by Algorithm 3, which will prove useful in the following sections.
| Algorithm 3 Time-expanded variant of the preflow-push algorithm. |
Initialize . Saturate all edges, leaving S. while do for to do while do if then propose() else refuse() end if end while end for end while
|
Lemma 3.6. Let .
After every u-phase for any vertex, ,
in Algorithm 3, the following statements hold for all :
- (a)
- (b)
If and (or ), then .
- (c)
- (d)
If , then .
Proof. We prove the lemma by induction on the algorithm. Clearly, all statements are true after initialization. We show that they also stay true after the end of each phase.
First, observe that during a u-phase, statements (a) to (d) cannot be invalidated for any vertex, : The pointers of v are not changed, so (a) and (c) remain valid for v. The flow on any edge, , for any i cannot be changed, so (d) remains valid. Finally can only change if for some index, ℓ, but in this case, (b) is always true. We thus can assume that after a phase of vertex v, statements (a) to (d) are true for all vertices other than v and use this fact to show that they also hold for v.
Let
, and consider the pointers of copies of vertex
u and the flow on their incident edges after a
u-phase. As there are no loops in the underlying graph, the algorithm ensures
. Furthermore:
(if
exists) because (c) and (d) hold for vertex
w. Likewise,
(if
exists) because (a) and (b) hold for
w.
Assume, by contradiction, that (a) or (b) is not valid after the phase. This implies
and, thus,
by Equation (
2), where
. Let
. If (a) is not valid, then the pointer,
, must have been advanced during the phase, and thus,
. The inequality,
, is also true if (b) is not valid. In both cases,
. Thus, by Equation (
1),
. This yields
, a contradiction.
Now, assume, by contradiction, that (c) or (d) is not valid after the phase. This implies
and, thus,
by Equation (
1). Let
. If (c) is not valid, then the pointer,
, must have been advanced during the phase, and thus,
, where
denotes the flow before execution of the phase. The inequality,
, is also true, if (d) is not valid. In both cases,
. Thus, by Equation (
2),
. This again yields
, a contradiction.
☐
3.2. Infinite Time
In this section, we will prove the existence of a stable flow, even if the time horizon is infinite. This flow can be constructed by applying the time-expanded preflow-push algorithm on (under the assumption that it can apply the propose and refuse steps on all copies of a vertex in finite time). Even more, after a certain point in time, the stable flow is identical to a temporal repetition of the stable flow computed by the same algorithm in the static network, D.
We define to be the subgraph induced by the vertices, with . We will run Algorithm 1 on D and Algorithm 3 on in parallel, executing a u-phase in whenever vertex u is processed in D. (Note that the state of vertex does not, in particular, depend on any other vertex copy, , with . Therefore, the state of and its adjacent edges after the u-phase is well defined, although infinitely many copies of u are processed during the u-phase.) Let f be the flow values in D and be the flow values in that occur throughout the run of the algorithm, and let and be the corresponding pointers, respectively.
Our main theorem in this section states that there is a point in time from which on all computations in the infinite time expanded network correspond one-to-one to those in the static network.
Theorem 3.7. There is a point in time, , such that at the end of every u-phase for any vertex, u, throughout the course of the algorithm, for every , for all edges , and and for all .
Proof. Let . We will first prove by induction that until phase K, the statement of the theorem is true for . Clearly, this is true after initialization, as all edges leaving the terminal set are saturated, and all pointers are at their initial state.
Now assume that after phase K, the state of all flow variables and pointers in is identical to that in D. Now, let be the vertex that is processed in the current phase and let . Note that before the execution of the u-phase, all edges incident to carry the same flow as all edges incident to u in D (as ), and and . Therefore, the u-phase modifies and its incident edges in exactly the same way as u is modified by Algorithm 1 in D. Accordingly, after the end of the u-phase, the statement of the theorem still holds for .
We now have shown that up to phase K, the statement of the theorem holds for . Now, let be the number of iterations performed by Algorithm 1 before f is a stable flow in D. After iteration , no flow values or pointers in D are changed. Let . We will show that after iteration , also, no flow values or pointers in are changed, which concludes the proof of the theorem.
After iteration , all vertices in are inactive. Thus, their state can only change if the flow value on an edge, , for and , is increased. This can only happen, if , as well as , and . Note that at the end of the phase, , we have , and , by choice of . Now, by Lemma 3.6, , and as is neither refused nor saturated, . Again, by Lemma 3.6, as long as neither nor are advanced. Therefore, cannot be increased before some vertex in becomes active. Thus, is never increased. ☐
Corollary 3.8. Algorithm 3 constructs a stable flow, , in , such that for all and all , where is the number of iterations performed by the Algorithm 1 to compute the stable flow, f, in D, using the same order of vertices.
3.3. Storing at Vertices
The third point in the definition of a flow over time requires flow conservation in every timeslot. A different model allows storing at vertices: a vendor may delay the shipment of goods at his convenience, as long as the flow arrives at the terminal vertices within the time horizon. More formally, we generalize the definition of the
excess of vertex
v at time
θ as the amount of stored goods at vertex
v at time
θ:
While strict flow conservation requires for all non-terminal vertices and times in , weak flow conservation allows , except for time , where must hold for all .
The time-expanded network can be adapted for weak flow conservation by introducing so-called holdover edges, , of infinite capacity for each and . Setting the ranks of these holdover edges in the preference lists allows the investigation of interesting variations. One intuitive view comes from the fact that storing goods is expensive and people are impatient, thus letting the edges, , be the last on ’s preference list and the first on ’s preference list. In the following, we will investigate the four main cases with weak flow conservation, given by varying first and last preferences on the end vertices of holdover edges. In each case, we study how the sets of stable flows obeying the different flow conservation rules are related to each other.
We adapt the definition of a blocking walk for the case of intermediate storing. Apart from a starting time, θ, we need the exact time, , when the walk in D leaves a vertex, . A walk in D together with a sequence, , uniquely determines a walk on .
Example 3.9. Introducing waiting at vertices, stable flows may lose their stability, independent from the rank of holdover edges.
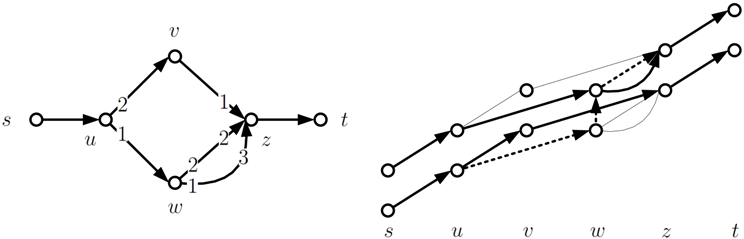
Proof. Consider the following example:
All edges in the static network have unit capacity and unit transit time; s and t are the non-terminal vertices. The unobvious preferences are shown on the edges. The time-expanded network with stands on the right side, showing only the vertices and edges that may be used in a feasible flow. On the static network above, there are three stable flows, each of them uses a different incoming edge of z. If waiting is not allowed, then the dynamic flow shown by the thick edges on the second network is stable, since all unsaturated paths are dominated by it at one end. Adding holdover edges to the time-expanded network breaks the scheme: the walk, (denoted by dashed lines), blocks the flow over time. Note that this is independent of the rank of the holdover edges, since we only need dominance at the ends of the blocking walk. ☐
Theorem 3.10. If T is sufficiently large and holdover edges always stand on the first place on preference lists, then there is no stable flow with value zero on all holdover edges.
Proof. Suppose there is a stable flow on the time-expanded network that does not use any of the holdover edges. Consider all the copies of an arbitrary non-terminal vertex, v: if there are two of them that have a positive value on some incoming (and outgoing) edges, then holdover edges between them form a walk that blocks the flow. Thus, a stable flow over time passes through an arbitrary non-terminal vertex, at most, once. Regarding the maximal number of edges with positive flow value, this means two edges, at most, per non-terminal vertex, apart from the terminal-terminal edges that do not affect stability—a flow with this property has positive value on at most edges in the time-expanded network.
These maximum edges have to ensure that there is no unsaturated walk between terminal vertices. If the length (w.r.t. transit times) of the shortest walk is denoted by , then is a lower bound for the number of disjoint walks between terminal vertices. In order to saturate at least one edge along these walks, the inequality, , must hold; otherwise, at least one copy of the shortest walk is unsaturated—hence, it blocks the flow. ☐
Remark 3.11. Note that holdover edges can be simulated by introducing loops of unit transit time and sufficiently large capacity at every vertex of the underlying static network. By performing the modification explained in Remark 3.5 on these loops, we obtain an equivalent time-expanded network that fulfills the requirements of Lemma 3.6. We will use this observation in the following theorem.
Theorem 3.12. If and the holdover edges stand on the last place on preference lists, then there is a stable flow that has a value of zero on all holdover edges. It can be computed by applying Algorithm 3 on the time-expanded network, with all holdover edges being split according to Remark 3.11.
Proof. By contradiction, assume there is a holdover edge with positive flow value at some vertex, v. W.l.o.g., assume i to be minimal with . Since the time horizon is finite, there also is a latest point in time j, such that .
Since , the pointer, , must already have passed all outgoing non-holdover edges of , offering as much flow as the corresponding vertices are willing to accept. Therefore, by Lemma 3.6, the flow on each of these edges must be at least the flow on the corresponding edges of (if they exist). Thus, the total outflow of exceeds the total outflow of by at least . On the other hand, points either to zero or the incoming holdover edge, and thus, does not refuse any flow on the regular incoming edges. Again, by Lemma 3.6, the flow on those edges is at least the flow on the corresponding edges of . Thus, the total inflow of exceeds the total inflow of by at least . Putting this together yields , contradicting flow conservation. ☐
In the other two cases, when holdover edges are the best for one of the end vertices and the worst for the other one, storing can be used or avoided, depending on the network. There are even networks where all stable flows have positive value on some holdover edges.
4. Conclusions and Open Questions
We introduced stable flows over time, extending the concept of stability to network flows over time. As initial results, we proved the existence of stable flows, both for finite and infinite time horizons. In both cases, a stable flow can be computed in pseudo-polynomial time by applying a preflow-push algorithm operating directly on the flow network. We also showed that the possibility of storage at non-terminal vertices has an effect on the set of stable flows, depending on the preference given to holdover edges in the time-expanded network.
Although this paper provides first structural insights, many questions brought up by the definition of stable flows over time remain open, most prominently, the complexity of the stable flow problem: Is there a polynomial time algorithm for finding a stable flow? As of today, it is not even clear whether a stable flow over time can be encoded in polynomial space. First, research in this direction indicates that at least the concept of (generalized) temporally repeated flows cannot be applied directly.
Additionally, further extension of stability can be studied on a new setting, e.g., special edges or ties on preference lists, as can be extensions of the flow over the time model, e.g., connections to earliest arrival flows. Finally, we conjecture a stronger form of Theorem 3.12: if holdover edges have lowest priority at both the start and end vertex, no stable flow uses storage at non-terminal vertices.