On Solving the Minimum Spanning Tree Problem with Conflicting Edge Pairs
Abstract
1. Introduction
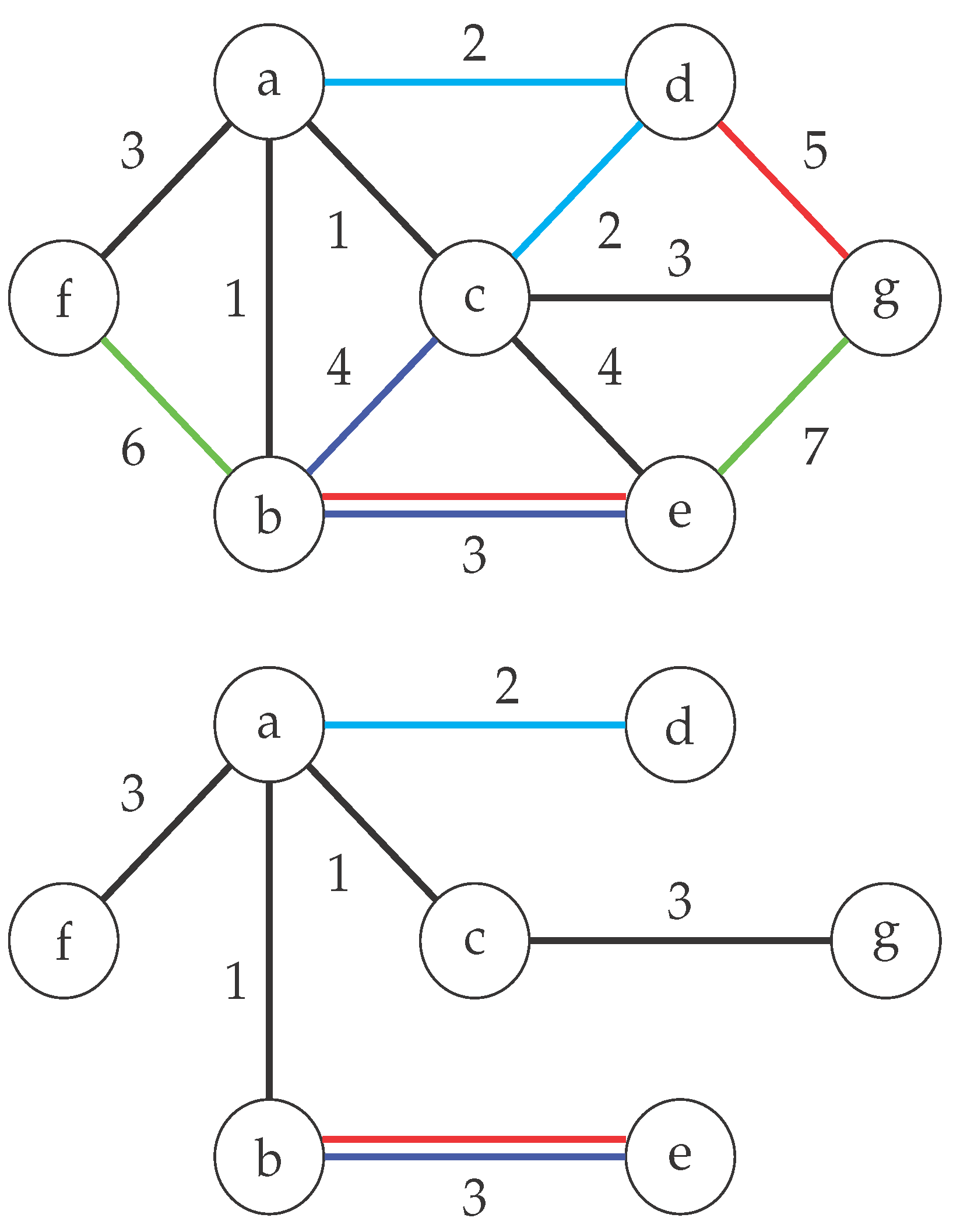
2. Problem Description
3. A Mixed-Integer Linear Programming Model
4. Computational Experiments
4.1. Benchmark Instances
4.2. Experimental Results
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Prim, R.C. Shortest connection networks and some generalizations. Bell Syst. Tech. J. 1957, 6, 1389–1401. [Google Scholar] [CrossRef]
- Darmann, A.; Pferschy, U.; Schauer, J.; Woeginger, G.J. Paths, trees and matchings under disjunctive constraints. Discret. Appl. Math. 2011, 16, 1726–1735. [Google Scholar] [CrossRef]
- Zhang, R.; Kabadi, S.; Punnen, A. The minimum spanning tree problem with conflict constraints and its variations. Discret. Optim. 2011, 2, 191–205. [Google Scholar] [CrossRef]
- Samer, P.; Urrutia, S. A branch and cut algorithm for minimum spanning trees under conflict constraints. Optim. Lett. 2014, 1, 41–55. [Google Scholar] [CrossRef]
- Carrabs, F.; Cerrone, C.; Pentangelo, R. A multi-ethnic genetic approach for the minimum conflict weighted spanning tree problem. Networks 2019, 2, 134–147. [Google Scholar] [CrossRef]
- Carrabs, F.; Gaudioso, M. A Lagrangian approach for the minimum spanning tree problem with conflicting edge pairs. Networks 2021, 1, 32–45. [Google Scholar] [CrossRef]
- Carrabs, F.; Cerulli, R.; Pentangelo, R.; Raiconi, A. Minimum spanning tree with conflicting edge pairs: A branch-and-cut approach. In Annals of Operations Research; Springer: Berlin/Heidelberg, Germany, 2019; pp. 65–78. [Google Scholar]
- Öncan, T.; Zhang, R.; Punnen, A.P. The minimum cost perfect matching problem with conflict pair constraints. Comput. Oper. Res. 2013, 40, 920–930. [Google Scholar] [CrossRef]
- Öncan, T.; Altınel, I.K. Iterated exact and heuristic algorithms for the minimum cost bipartite perfect matching problem with conflict constraints. In Proceedings of the 2017 IEEE International Conference on Industrial Engineering and Engineering Management (IEEM), Singapore, 10–13 December 2017; pp. 1032–1036. [Google Scholar]
- Öncan, T.; Altınel, I.K. A Branch-and-Bound Algorithm for the Minimum Cost Bipartite Perfect Matching Problem with Conflict Pair Constraints. Electron. Notes Discret. Math. 2018, 64, 5–14. [Google Scholar] [CrossRef]
- Öncan, T.; Şuvak, Z.; Akyüz, M.H.; Altınel, I.K. Assignment problem with conflicts. Comput. Oper. Res. 2019, 111, 214–229. [Google Scholar] [CrossRef]
- Yamada, T.; Kataoka, S.; Watanabe, K. Heuristic and exact algorithms for the disjunctively constrained knapsack problem. Informs J. Comput. 2002, 43, 2864–2870. [Google Scholar]
- Hifi, M.; Michrafy, M. Reduction strategies and exact algorithms for the disjunctively constrained knapsack problem. Comput. Oper. Res. 2007, 34, 2657–2673. [Google Scholar] [CrossRef]
- Hifi, M.; Michrafy, M. A reactive local search-based algorithm for the disjunctively constrained knapsack problem. J. Oper. Res. Soc. 2006, 57, 718–726. [Google Scholar] [CrossRef]
- Akeb, H.; Hifi, M.; Ould Ahmed Mounir, M.E. Local branching-based algorithms for the disjunctively constrained knapsack problem. Comput. Ind. Eng. 2011, 60, 811–820. [Google Scholar] [CrossRef]
- Hifi, M.; Omani, N. An algorithm for the disjunctively constrained knapsack problem. Int. J. Oper. Res. 2012, 13, 22–43. [Google Scholar] [CrossRef]
- Hifi, M. An iterative rounding search-based algorithm for the disjunctively constrained knapsack problem. Eng. Optim. 2014, 46, 1109–1122. [Google Scholar] [CrossRef]
- Bettinelli, A.; Cacchiani, V.; Malaguti, E. A Branch-and-Bound Algorithm for the Knapsack Problem with Conflict Graph. INFORMS J. Comput. 2017, 29, 457–473. [Google Scholar] [CrossRef]
- Coniglio, S.; Furini, F.; San Segundo, P. A new combinatorial branch-and-bound algorithm for the Knapsack Problem with Conflicts. Eur. J. Oper. Res. 2021, 289, 435–455. [Google Scholar] [CrossRef]
- Carrabs, F.; Cerulli, R.; Mansini, R.; Moreschini, L.; Serra, D. Solving the Set Covering Problem with Conflicts on Sets: A new parallel GRASP. Comput. Oper. Res. 2024, 166, 106620. [Google Scholar] [CrossRef]
- Jacob, A.; Majumdar, D.; Raman, V. Parameterized complexity of conflict-free set cover. Lect. Notes Comput. Sci. 2019, 11532, 191–202. [Google Scholar]
- Saffari, S.; Fathi, Y. Set covering problem with conflict constraints. Comput. Oper. Res. 2022, 143, 105763. [Google Scholar] [CrossRef]
- Banik, A.; Panolan, F.; Raman, V.; Sahlot, V.; Saurabh, S. Parameterized Complexity of Geometric Covering Problems Having Conflicts. Algorithmica 2020, 82, 1–19. [Google Scholar] [CrossRef]
- Gabow, H.; Maheshwari, S.; Osterweil, L. On Two Problems in the Generation of Program Test Paths. IEEE Trans. Softw. Eng. 1976, SE-2, 227–231. [Google Scholar] [CrossRef]
- Krause, K.W.; Goodwin, M.A.; Smith, R.W. Optimal Software Test Planning Through Automated Network Analysis; TRW Systems Group: Redondo Beach, CA, USA, 1973; pp. 18–22. [Google Scholar]
- Srimani, P.K.; Sinha, B.P. Impossible pair constrained test path generation in a program. Inf. Sci. 1982, 28, 87–103. [Google Scholar] [CrossRef]
- Blanco, M.; Borndörfer, R.; Brückner, M.; Hoàng, N.D.; Schlechte, T. On the Path Avoiding Forbidden Pairs Polytope. Electron. Notes Discret. Math. 2015, 50, 343–348. [Google Scholar] [CrossRef]
- Ferone, D.; Festa, P.; Salani, M. Branch and Bound and Dynamic Programming Approaches for the Path Avoiding Forbidden Pairs Problem. In Optimization and Decision Science: ODS, Virtual Conference, November 19, 2020; Cerulli, R., Dell’Amico, M., Guerriero, F., Pacciarelli, D., Sforza, A., Eds.; Springer International Publishing: Cham, Switzerland, 2021; pp. 227–235. [Google Scholar]
- Cerulli, R.; Guerriero, G.; Scalzo, E.; Sorgente, C. Shortest paths with exclusive-disjunction arc pairs conflicts. Comput. Oper. Res. 2023, 152, 106158. [Google Scholar] [CrossRef]
- Pferschy, U.; Schauer, J. The maximum flow problem with disjunctive constraints. J. Comb. Optim. 2013, 26, 109–119. [Google Scholar] [CrossRef]
- Şuvak, Z.; Altınel, I.K.; Aras, N. Exact solution algorithms for the maximum flow problem with additional conflict constraints. Eur. J. Oper. Res. 2020, 287, 410–437. [Google Scholar] [CrossRef]
- Carrabs, F.; Cerulli, R.; Mansini, R.; Serra, D.; Sorgente, C. Hybridizing Carousel Greedy and Kernel Search: A new approach for the maximum flow problem with conflict constraints. Eur. J. Oper. Res. 2025, 324, 414–435. [Google Scholar] [CrossRef]
- Cerrone, C.; Cerulli, R.; Golden, B. Carousel greedy: A generalized greedy algorithm with applications in optimization. Comput. Oper. Res. 2017, 85, 97–112. [Google Scholar] [CrossRef]
- Angelelli, E.; Mansini, R.; Speranza, M.G. Kernel search: A new heuristic framework for portfolio selection. Comput. Optim. Appl. 2012, 51, 345–361. [Google Scholar] [CrossRef]
- Klein, A.; Haugland, D.; Bauer, J.; Mommer, M. An integer programming model for branching cable layouts in offshore wind farms. In Advances in Intelligent Systems and Computing; Springer: Berlin/Heidelberg, Germany, 2015; pp. 27–36. [Google Scholar]
- Darmann, A.; Pferschy, U.; Schauer, J. Determining a minimum spanning tree with disjunctive constraints. In Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; pp. 414–423. [Google Scholar]
- Magnanti, T.L.; Wolsey, L. Optimal trees. In Handbook in Operations Research and Management Science; Ball, M.O., Magnanti, T.L., Monma, C.L., Nemhauser, G.L., Eds.; North Holland Publishing: Amsterdam, The Netherlands, 1995; pp. 503–615. [Google Scholar]
- Abdelmaguid, T.F. An Efficient Mixed Integer Linear Programming Model for the Minimum Spanning Tree Problem. Mathematics 2018, 6, 183. [Google Scholar] [CrossRef]
- de Almeida, A.M.; Martins, P.; de Souza, M.C. Min-degree constrained minimum spanning tree problem: complexity, properties, and formulations. Int. Trans. Oper. Res. 2012, 19, 323–352. [Google Scholar] [CrossRef]
- Gouveia, L.; Magnanti, T.L. Network flow models for designing diameter-constrained minimum-spanning and Steiner trees. Networks 2003, 41, 159–173. [Google Scholar] [CrossRef]
- Perron, L.; Didier, F. Google OR-Tools-CP-SAT. 2025. Available online: https://developers.google.com/optimization/cp/cp_solver/ (accessed on 9 July 2025).
- Montemanni, R.; Dell’Amico, M. Solving the parallel drone scheduling traveling salesman problem via constraint programming. Algorithms 2023, 16, 40. [Google Scholar] [CrossRef]
- Montemanni, R.; Dell’Amico, M.; Corsini, A. Parallel drone scheduling vehicle routing problems with collective drones. Comput. Oper. Res. 2024, 163, 106514. [Google Scholar] [CrossRef]
- Montemanni, R.; Smith, D.H. On Solving the Maximum Flow Problem with Conflict Constraints. In Proceedings of the 2025 Industrial Electronics and Applications Conference, Sabah, Malaysia, 8–9 September 2025. [Google Scholar]
- Montemanni, R. Solving a Home Healthcare Routing and Scheduling Problem with Real-World Features. In Machine Learning and Soft Computing, Proceedings of International Conference on Machine Learning and Soft Computing, Tokyo, Japan, 24–26 January 2025; Springer: Singapore, 2025; pp. 111–119. [Google Scholar]
- Stuckey, P.J. Lazy Clause Generation: Combining the Power of SAT and CP (and MIP?) Solving. In Proceedings of the International Conference on Integration of Artificial Intelligence and Operations Research Techniques in Constraint Programming (CPAIOR), Bologna, Italy, 14–18 June 2010; pp. 5–9. [Google Scholar]
- GEne Network Expansion. CPU Performance. 2025. Available online: https://gene.disi.unitn.it/test/cpu_list.php (accessed on 9 July 2025).







| Instances | MILP | LB-MST | LB-MI | HDA | Mega | HDA+ | BC | BC | CP-SAT | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [3] | [3] | [3] | [6] | [5] | [6] | [4] | [7] | Dev% | |||||||||||||
| n | m | p | UB | LB | LB | LB | Sec | UB | Sec | UB | Sec | LB | UB | LB | UB | Sec | LB | UB | Sec | LB | UB |
| 50 | 200 | 199 | 708 | 701.1 | 702.8 | 705.5 | 0.3 | 708 | 0.7 | 726 | 0.4 | 708.0 | 708 | 708.0 | 708 | 0.2 | 708 | 708 | 5.1 | 0.0 | 0.0 |
| 50 | 200 | 398 | 770 | 739.8 | 757.8 | 761.0 | 0.3 | 770 | 0.7 | 780 | 0.5 | 770.0 | 770 | 770.0 | 770 | 0.5 | 770 | 770 | 9.2 | 0.0 | 0.0 |
| 50 | 200 | 597 | 917 | 782.7 | 807.8 | 867.7 | 0.4 | 917 | 0.6 | 1176 | 0.6 | 917.0 | 917 | 917.0 | 917 | 1.8 | 917 | 917 | 46.0 | 0.0 | 0.0 |
| 50 | 200 | 995 | 1324 | 835.7 | 877.5 | 961.9 | 0.4 | 1365.4 | 0.6 | 1587 | 0.8 | 1324.0 | 1324 | 1324.0 | 1324 | 7.4 | 1324 | 1324 | 199.6 | 0.0 | 0.0 |
| 50 | 200 | 3903 | 1636 | 775.1 | 877.5 | 1042.8 | 1.2 | 1636 | 0.5 | 1653 | 2.2 | - | - | - | - | - | 1636 | 1636 | 0.1 | 0.0 | 0.0 |
| 50 | 200 | 4877 | 2043 | 698.7 | 887.5 | 1116.3 | 1.6 | 2043 | 0.5 | 2043 | 2.5 | - | - | - | - | - | 2043 | 2043 | 0.2 | 0.0 | 0.0 |
| 50 | 200 | 5864 | 2338 | 626.9 | 1030.3 | 2338.0 | 0.8 | 2338 | 0.6 | 2338 | 0.8 | - | - | - | - | - | 2338 | 2338 | 0.1 | 0.0 | 0.0 |
| 100 | 300 | 448 | 4041 | 3893.5 | 3991.2 | 4036.6 | 0.9 | 4099.2 | 0.6 | 4099 | 1.2 | 4041.0 | 4041 | 4041.0 | 4041 | 4.6 | 4041 | 4041 | 232.0 | 0.0 | 0.0 |
| 100 | 300 | 897 | 5658 | 4508.2 | 4624.2 | 4982.0 | 1.4 | - | 1.9 | - | 2.1 | 5658.0 | 5658 | 5658.0 | 5658 | 178.5 | 5658 | 5658 | 2758.6 | 0.0 | 0.0 |
| 100 | 300 | 1344 | - | - | 4681.3 | - | - | - | 2.9 | - | - | 6621.2 | - | 6635.4 | - | 5010.0 | Infeas | Infeas | 104.6 | −100.0 | −100.0 |
| 100 | 300 | 8609 | 7434 | 4043.4 | 5754.9 | 7434.0 | 0.6 | 7434 | 1.9 | 7434 | 0.6 | - | - | - | - | - | 7434 | 7434 | 0.1 | 0.0 | 0.0 |
| 100 | 300 | 10,686 | 7968 | 3970.5 | 6192.3 | 7968.0 | 0.6 | 7968 | 1.8 | 7968 | 0.5 | - | - | - | - | - | 7968 | 7968 | 0.2 | 0.0 | 0.0 |
| 100 | 300 | 12,761 | 8166 | 3936.3 | 6758.6 | 8166.0 | 0.5 | 8166 | 1.9 | 8166 | 0.5 | - | - | - | - | - | 8166 | 8166 | 0.1 | 0.0 | 0.0 |
| 100 | 500 | 1247 | 4275 | 4124.5 | 4165.7 | 4268.6 | 2.3 | 4291.2 | 5.3 | 4301 | 3.0 | 4275.0 | 4275 | 4275.0 | 4275 | 11.5 | 4275 | 4275 | 86.6 | 0.0 | 0.0 |
| 100 | 500 | 2495 | 5997 | 4701.9 | 4805.4 | 5238.2 | 2.5 | 6325 | 5.0 | 8214 | 5.5 | 5951.4 | 6006 | 5997.0 | 5997 | 1239.4 | 5676 | 6005 | 5010.0 | 5.4 | 0.1 |
| 100 | 500 | 3741 | 7665 | 4743.8 | 4871.3 | 5418.8 | 2.6 | 7788 | 3.2 | - | 6.8 | 6510.8 | 9440 | 6707.8 | 8049 | 5010.1 | 6267 | 7787 | 5010.0 | 6.6 | −0.013 |
| 100 | 500 | 6237 | - | - | 4969.0 | - | - | - | 5.0 | - | - | 7568.7 | - | 7729.3 | - | 5010.0 | 7259 | - | 5010.0 | 6.1 | 0.0 |
| 100 | 500 | 12,474 | - | - | 5194.7 | - | - | - | 6.9 | - | - | 9816.9 | - | 10,560.2 | - | 5010.0 | Infeas | Infeas | 15.1 | −100.0 | −100.0 |
| 100 | 500 | 24,740 | 12,652 | 4289.9 | 5104.9 | 5565.2 | 9.0 | 12,652 | 3.4 | 12,681 | 20.8 | - | - | - | - | - | 12,652 | 12,652 | 0.1 | 0.0 | 0.0 |
| 100 | 500 | 30,886 | 11,232 | 3972.7 | 5078.8 | 5672.7 | 15.5 | 11,232 | 3.6 | 11,287 | 26.4 | - | - | - | - | - | 11,232 | 11,232 | 0.1 | 0.0 | 0.0 |
| 100 | 500 | 36,827 | 11,481 | 3918.1 | 5710.8 | 11,481.0 | 22.9 | 11,481 | 3.6 | 11,481 | 24.4 | - | - | - | - | - | 11,481 | 11,481 | 0.2 | 0.0 | 0.0 |
| 200 | 400 | 13,660 | 17,728 | 14,085.8 | 17,245.9 | 17,728.0 | 1.3 | 17,728 | 7.7 | 17,728 | 1.4 | - | - | - | - | - | 17,728 | 17,728 | 0.1 | 0.0 | 0.0 |
| 200 | 400 | 17,089 | 18,617 | 14,067.3 | 18,048.2 | 18,617.0 | 1.5 | 18,617 | 7.7 | 18,617 | 1.4 | - | - | - | - | - | 18,617 | 18,617 | 0.1 | 0.0 | 0.0 |
| 200 | 400 | 20,470 | 19,140 | 13,998.7 | 18,646.2 | 19,140.0 | 1.4 | 19,140 | 7.6 | 19,140 | 1.4 | - | - | - | - | - | 19,140 | 19,140 | 0.1 | 0.0 | 0.0 |
| 200 | 600 | 1797 | 15,029 | 1111.6 | 11,425.8 | 12,451.6 | 4.9 | - | 12.6 | - | 8.6 | 13,072.9 | 14,707 | 13,171.2 | 14,086 | 5010.0 | 12,841 | 14,405 | 5010.0 | 2.5 | 2.3 |
| 200 | 600 | 3594 | - | 12,487.0 | - | - | 24.0 | - | - | 17,532.7 | - | 17,595.0 | - | 5010.0 | 0 | 0 | 158.9 | −100.0 | −100.0 | ||
| 200 | 600 | 5391 | - | 12,873.2 | - | - | 31.6 | - | - | Infeas | Infeas | Infeas | Infeas | 16.4 | Infeas | Infeas | 0.0 | 0.0 | 0.0 | ||
| 200 | 600 | 34,504 | 20,716 | 9466.1 | 15,393.1 | 20,716.0 | 3.0 | 20,716 | 11.6 | 20,716 | 3.0 | - | - | - | - | - | 20,716 | 20,716 | 0.1 | 0.0 | 0.0 |
| 200 | 600 | 42,860 | 18,025 | 9100.6 | 13,971.5 | 18,025.0 | 2.1 | 18,025 | 12.0 | 18,025 | 2.2 | - | - | - | - | - | 18,025 | 18,025 | 0.2 | 0.0 | 0.0 |
| 200 | 600 | 50,984 | 20,864 | 8734.5 | 16,708.1 | 20,864.0 | 1.9 | 20,864 | 12.5 | 20,864 | 2.0 | - | - | - | - | - | 20,864 | 20,864 | 0.1 | 0.0 | 0.0 |
| 200 | 800 | 3196 | 22,110 | 17,428.8 | 17,922.6 | 19,685.1 | 8.6 | 22,350.8 | 22.2 | - | 18.9 | 20,744.2 | 21,852 | 20,941.5 | 21,553 | 5010.1 | 20,030 | 22,722 | 5010.0 | 4.4 | 5.4 |
| 200 | 800 | 6392 | - | - | 19,705.7 | - | - | 28.4 | - | - | 26,361.3 | - | 26,526.7 | - | 5010.1 | 24,259 | - | 5010.0 | 8.5 | 0.0 | |
| 200 | 800 | 9588 | - | - | 20,684.8 | - | - | 38.3 | - | - | 29,443.6 | - | 30,634.2 | - | 5010.0 | 28,351 | - | 5010.0 | 7.5 | 0.0 | |
| 200 | 800 | 15,980 | - | - | 20,226.9 | - | - | 48.0 | - | - | 33,345.1 | - | 36,900.2 | - | 5010.0 | 0 | 0 | 35.4 | −100.0 | −100.0 | |
| 200 | 800 | 62,625 | 39,895 | 16,806.5 | 23,792.3 | 39,895.0 | 43.3 | 39,895 | 16.7 | 39,895 | 45.8 | - | - | - | - | - | 39,895 | 39,895 | 0.2 | 0.0 | 0.0 |
| 200 | 800 | 78,387 | 37,671 | 15,803.1 | 22,174.2 | 37,671.0 | 7.7 | 37,671 | 15.9 | 37,671 | 8.2 | - | - | - | - | - | 37,671 | 37,671 | 0.2 | 0.0 | 0.0 |
| 200 | 800 | 93,978 | 38,798 | 15,470.1 | 24,907.0 | 38,798.0 | 4.5 | 38,798 | 17.3 | 38,798 | 4.7 | - | - | - | - | - | 38,798 | 38,798 | 0.1 | 0.0 | 0.0 |
| 300 | 600 | 31,000 | 43,721 | 34,154.2 | 42,720.6 | 43,721.0 | 3.0 | 43,721 | 19.2 | 43,721 | 3.4 | - | - | - | - | - | 43,721 | 43,721 | 0.1 | 0.0 | 0.0 |
| 300 | 600 | 38,216 | 44,267 | 33,320.1 | 43,486.7 | 44,267.0 | 3.1 | 44,267 | 22.3 | 44,267 | 3.4 | - | - | - | - | - | 44,267 | 44,267 | 0.2 | 0.0 | 0.0 |
| 300 | 600 | 45,310 | 43,071 | 32,072.3 | 42,149.0 | 43,071.0 | 3.0 | 43,071 | 24.6 | 43,071 | 3.1 | - | - | - | - | - | 43,071 | 43,071 | 0.3 | 0.0 | 0.0 |
| 300 | 800 | 3196 | - | - | 30,190.1 | - | - | - | 62.8 | - | - | Infeas | Infeas | Infeas | Infeas | 2911.1 | Infeas | Infeas | 3.3 | 0.0 | 0.0 |
| 300 | 800 | 59,600 | 43,125 | 24,384.3 | 36,629.6 | 43,125.0 | 3.3 | 43,125 | 32.7 | 43,125 | 3.1 | - | - | - | - | - | 43,125 | 43,125 | 0.1 | 0.0 | 0.0 |
| 300 | 800 | 74,500 | 42,292 | 22,913.2 | 38,069.3 | 42,292.0 | 3.2 | 42,292 | 35.6 | 42,292 | 3.2 | - | - | - | - | - | 42,292 | 42,292 | 0.3 | 0.0 | 0.0 |
| 300 | 800 | 89,300 | 44,114 | 21,624.6 | 38,843.0 | 44,114.0 | 3.4 | 44,114 | 35.4 | 44,114 | 3.2 | - | - | - | - | - | 44,114 | 44,114 | 0.1 | 0.0 | 0.0 |
| 300 | 1000 | 4995 | - | - | 40,732.7 | - | - | - | 79.3 | - | - | 51,451.3 | - | 51,398.4 | - | 5010.0 | 48,180 | - | 5010.0 | 6.4 | 0.0 |
| 300 | 1000 | 9990 | - | - | 42,902.5 | - | - | - | 119.1 | - | - | 60,907.8 | - | 61,878.9 | - | 5010.0 | Infeas | Infeas | 181.3 | −100.0 | −100.0 |
| 300 | 1000 | 14,985 | - | - | 44,639.1 | - | - | - | 141.3 | - | - | Infeas | Infeas | Infeas | Infeas | 1820.0 | Infeas | Infeas | 9.7 | 0.0 | 0.0 |
| 300 | 1000 | 96,590 | 71,562 | 36,544.7 | 56,048.3 | 71,562.0 | 9.2 | 71,562 | 41.5 | 71,562 | 9.5 | - | - | - | - | - | 71,562 | 71,562 | 0.1 | 0.0 | 0.0 |
| 300 | 1000 | 120,500 | 76,345 | 34,380.8 | 58,780.1 | 76,345.0 | 6.6 | 76,345 | 33.4 | 76,345 | 6.7 | - | - | - | - | - | 76,345 | 76,345 | 0.2 | 0.0 | 0.0 |
| 300 | 1000 | 144,090 | 78,880 | 33,481.2 | 60,810.8 | 78,880.0 | 5.2 | 78,880 | 36.9 | 78,880 | 5.4 | - | - | - | - | - | 78,880 | 78,880 | 0.1 | 0.0 | 0.0 |
| Averages | −9.1 | −9.8 | |||||||||||||||||||
| Instances | HDA | HDA+ | BC | CP-SAT | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [6] | [6] | [7] | Dev% | ||||||||||||
| LB | Sec | UB | Sec | LB | UB | Sec | LB | UB | Sec | LB | UB | ||||
| 25 | 60 | 18 | 1 | 347.0 | 0.04 | 347 | 0.05 | 347.0 | 347 | 0.0 | 347 | 347 | 0.23 | 0.0 | 0.0 |
| 25 | 60 | 18 | 7 | 389.0 | 0.04 | 389 | 0.04 | 389.0 | 389 | 0.0 | 389 | 389 | 0.18 | 0.0 | 0.0 |
| 25 | 60 | 18 | 13 | 353.0 | 0.04 | 353 | 0.04 | 353.0 | 353 | 0.0 | 353 | 353 | 0.19 | 0.0 | 0.0 |
| 25 | 60 | 18 | 19 | 346.0 | 0.04 | 346 | 0.05 | 346.0 | 346 | 0.0 | 346 | 346 | 0.19 | 0.0 | 0.0 |
| 25 | 60 | 18 | 25 | 336.0 | 0.04 | 336 | 0.04 | 336.0 | 336 | 0.0 | 336 | 336 | 0.18 | 0.0 | 0.0 |
| 25 | 90 | 71 | 31 | 379.6 | 0.09 | 381 | 0.07 | 381.0 | 381 | 0.0 | 381 | 381 | 0.45 | 0.0 | 0.0 |
| 25 | 60 | 71 | 37 | 381.5 | 0.05 | 390 | 0.07 | 390.0 | 390 | 0.1 | 390 | 390 | 0.32 | 0.0 | 0.0 |
| 25 | 60 | 71 | 43 | 372.0 | 0.05 | 372 | 0.06 | 372.0 | 372 | 0.0 | 372 | 372 | 0.44 | 0.0 | 0.0 |
| 25 | 60 | 71 | 49 | 357.0 | 0.05 | 357 | 0.06 | 357.0 | 357 | 0.0 | 357 | 357 | 0.24 | 0.0 | 0.0 |
| 25 | 60 | 71 | 55 | 406.0 | 0.05 | 406 | 0.06 | 406.0 | 406 | 0.0 | 406 | 406 | 0.38 | 0.0 | 0.0 |
| 25 | 60 | 124 | 61 | 385.0 | 0.06 | 385 | 0.07 | 385.0 | 385 | 0.0 | 385 | 385 | 0.18 | 0.0 | 0.0 |
| 25 | 60 | 124 | 67 | 432.0 | 0.06 | 432 | 0.07 | 432.0 | 432 | 0.0 | 432 | 432 | 0.20 | 0.0 | 0.0 |
| 25 | 60 | 124 | 73 | 424.5 | 0.07 | 474 | 0.1 | 458.0 | 458 | 0.3 | 458 | 458 | 0.48 | 0.0 | 0.0 |
| 25 | 60 | 124 | 79 | 398.0 | 0.07 | 400 | 0.08 | 400.0 | 400 | 0.0 | 400 | 400 | 0.45 | 0.0 | 0.0 |
| 25 | 60 | 124 | 85 | 406.8 | 0.08 | 421 | 0.12 | 420.0 | 420 | 0.0 | 420 | 420 | 0.42 | 0.0 | 0.0 |
| 25 | 90 | 41 | 91 | 310.1 | 0.05 | 311 | 0.05 | 311.0 | 311 | 0.0 | 311 | 311 | 0.54 | 0.0 | 0.0 |
| 25 | 90 | 41 | 97 | 306.0 | 0.05 | 306 | 0.06 | 306.0 | 306 | 0.0 | 306 | 306 | 0.36 | 0.0 | 0.0 |
| 25 | 90 | 41 | 103 | 299.0 | 0.05 | 299 | 0.05 | 299.0 | 299 | 0.0 | 299 | 299 | 0.31 | 0.0 | 0.0 |
| 25 | 90 | 41 | 109 | 297.0 | 0.05 | 297 | 0.05 | 297.0 | 297 | 0.0 | 297 | 297 | 0.30 | 0.0 | 0.0 |
| 25 | 90 | 41 | 115 | 318.0 | 0.05 | 318 | 0.05 | 318.0 | 318 | 0.0 | 318 | 318 | 0.25 | 0.0 | 0.0 |
| 25 | 90 | 161 | 121 | 305.0 | 0.08 | 305 | 0.09 | 305.0 | 305 | 0.0 | 305 | 305 | 0.54 | 0.0 | 0.0 |
| 25 | 90 | 161 | 127 | 339.0 | 0.12 | 339 | 0.11 | 339.0 | 339 | 0.0 | 339 | 339 | 0.29 | 0.0 | 0.0 |
| 25 | 90 | 161 | 133 | 344.0 | 0.08 | 344 | 0.09 | 344.0 | 344 | 0.0 | 344 | 344 | 0.23 | 0.0 | 0.0 |
| 25 | 90 | 161 | 139 | 328.0 | 0.09 | 331 | 0.11 | 329.0 | 329 | 0.0 | 329 | 329 | 0.61 | 0.0 | 0.0 |
| 25 | 90 | 161 | 145 | 325.0 | 0.08 | 327 | 0.11 | 326.0 | 326 | 0.0 | 326 | 326 | 0.89 | 0.0 | 0.0 |
| 25 | 90 | 281 | 151 | 347.9 | 0.1 | 349 | 0.13 | 349.0 | 349 | 0.0 | 349 | 349 | 0.56 | 0.0 | 0.0 |
| 25 | 90 | 281 | 157 | 370.6 | 0.1 | 385 | 0.16 | 385.0 | 385 | 0.5 | 385 | 385 | 2.67 | 0.0 | 0.0 |
| 25 | 90 | 281 | 163 | 330.8 | 0.11 | 335 | 0.14 | 335.0 | 335 | 0.0 | 335 | 335 | 0.66 | 0.0 | 0.0 |
| 25 | 90 | 281 | 169 | 334.7 | 0.1 | 358 | 0.18 | 348.0 | 348 | 0.1 | 348 | 348 | 1.91 | 0.0 | 0.0 |
| 25 | 90 | 281 | 175 | 350.1 | 0.1 | 359 | 0.17 | 357.0 | 357 | 0.0 | 357 | 357 | 0.98 | 0.0 | 0.0 |
| 25 | 120 | 72 | 181 | 282.0 | 0.07 | 282 | 0.06 | 282.0 | 282 | 0.0 | 282 | 282 | 0.24 | 0.0 | 0.0 |
| 25 | 120 | 72 | 187 | 294.0 | 0.06 | 294 | 0.06 | 294.0 | 294 | 0.0 | 294 | 294 | 0.90 | 0.0 | 0.0 |
| 25 | 120 | 72 | 193 | 284.0 | 0.06 | 284 | 0.08 | 284.0 | 284 | 0.0 | 284 | 284 | 0.48 | 0.0 | 0.0 |
| 25 | 120 | 72 | 199 | 281.0 | 0.06 | 281 | 0.07 | 281.0 | 281 | 0.0 | 281 | 281 | 0.53 | 0.0 | 0.0 |
| 25 | 120 | 72 | 205 | 292.0 | 0.06 | 292 | 0.06 | 292.0 | 292 | 0.0 | 292 | 292 | 0.30 | 0.0 | 0.0 |
| 25 | 120 | 286 | 211 | 320.3 | 0.12 | 321 | 0.16 | 321.0 | 321 | 0.0 | 321 | 321 | 1.06 | 0.0 | 0.0 |
| 25 | 120 | 286 | 217 | 317.0 | 0.12 | 317 | 0.17 | 317.0 | 317 | 0.0 | 317 | 317 | 0.64 | 0.0 | 0.0 |
| 25 | 120 | 286 | 223 | 284.0 | 0.56 | 284 | 0.12 | 284.0 | 284 | 0.0 | 284 | 284 | 0.31 | 0.0 | 0.0 |
| 25 | 120 | 286 | 229 | 311.0 | 0.12 | 312 | 0.17 | 311.0 | 311 | 0.0 | 311 | 311 | 0.58 | 0.0 | 0.0 |
| 25 | 120 | 286 | 235 | 290.0 | 0.13 | 290 | 0.13 | 290.0 | 290 | 0.0 | 290 | 290 | 0.36 | 0.0 | 0.0 |
| 25 | 120 | 500 | 241 | 319.2 | 0.16 | 341 | 0.26 | 329.0 | 329 | 0.1 | 329 | 329 | 4.72 | 0.0 | 0.0 |
| 25 | 120 | 500 | 247 | 326.1 | 0.16 | 347 | 0.25 | 339.0 | 339 | 0.5 | 339 | 339 | 1.84 | 0.0 | 0.0 |
| 25 | 120 | 500 | 253 | 354.5 | 0.16 | 383 | 0.3 | 368.0 | 368 | 0.4 | 368 | 368 | 1.55 | 0.0 | 0.0 |
| 25 | 120 | 500 | 259 | 306.5 | 0.16 | 314 | 0.22 | 311.0 | 311 | 0.0 | 311 | 311 | 0.65 | 0.0 | 0.0 |
| 25 | 120 | 500 | 265 | 318.0 | 0.16 | 325 | 0.25 | 321.0 | 321 | 0.0 | 321 | 321 | 0.74 | 0.0 | 0.0 |
| 50 | 245 | 299 | 271 | 619.0 | 0.34 | 619 | 0.37 | 619.0 | 619 | 0.0 | 619 | 619 | 2.75 | 0.0 | 0.0 |
| 50 | 245 | 299 | 277 | 604.0 | 0.36 | 604 | 0.38 | 604.0 | 604 | 0.0 | 604 | 604 | 1.49 | 0.0 | 0.0 |
| 50 | 245 | 299 | 283 | 634.0 | 0.34 | 634 | 0.35 | 634.0 | 634 | 0.0 | 634 | 634 | 0.72 | 0.0 | 0.0 |
| 50 | 245 | 299 | 289 | 615.5 | 0.34 | 616 | 0.4 | 616.0 | 616 | 0.1 | 616 | 616 | 1.49 | 0.0 | 0.0 |
| 50 | 245 | 299 | 295 | 595.0 | 0.34 | 595 | 0.44 | 595.0 | 595 | 0.0 | 595 | 595 | 7.28 | 0.0 | 0.0 |
| 50 | 245 | 1196 | 301 | 668.5 | 0.57 | 698 | 0.96 | 678.0 | 678 | 1.4 | 678 | 678 | 27.19 | 0.0 | 0.0 |
| 50 | 245 | 1196 | 307 | 655.5 | 0.56 | 721 | 0.99 | 681.0 | 681 | 3.2 | 681 | 681 | 51.96 | 0.0 | 0.0 |
| 50 | 245 | 1196 | 313 | 678.2 | 0.59 | 725 | 1 | 709.0 | 709 | 6.3 | 709 | 709 | 612.25 | 0.0 | 0.0 |
| 50 | 245 | 1196 | 319 | 634.0 | 1.26 | 656 | 0.86 | 639.0 | 639 | 1.5 | 639 | 639 | 16.54 | 0.0 | 0.0 |
| 50 | 245 | 1196 | 325 | 658.8 | 0.56 | 748 | 1.01 | 681.0 | 681 | 3.8 | 681 | 681 | 57.54 | 0.0 | 0.0 |
| 50 | 245 | 2093 | 331 | 661.3 | 0.76 | - | - | 791.2 | 820 | 5010.0 | 778 | 816 | 5010.00 | 1.7 | −0.5 |
| 50 | 245 | 2093 | 337 | 706.0 | 0.75 | - | - | 835.0 | 835 | 1938.7 | 835 | 835 | 4603.22 | 0.0 | 0.0 |
| 50 | 245 | 2093 | 343 | 666.5 | 0.74 | - | - | 773.2 | 811 | 5010.1 | 760 | 822 | 5010.00 | 1.7 | 1.4 |
| 50 | 245 | 2093 | 349 | 680.8 | 0.76 | - | - | 820.0 | 836 | 5010.1 | 832 | 832 | 2874.48 | −1.5 | −0.5 |
| 50 | 245 | 2093 | 355 | 693.9 | 0.74 | - | - | 769.0 | 769 | 25.7 | 769 | 769 | 266.66 | 0.0 | 0.0 |
| 50 | 367 | 672 | 361 | 570.0 | 0.82 | 570 | 0.88 | 570.0 | 570 | 0.1 | 570 | 570 | 8.05 | 0.0 | 0.0 |
| 50 | 367 | 672 | 367 | 561.0 | 0.86 | 561 | 0.98 | 561.0 | 561 | 1.4 | 561 | 561 | 10.48 | 0.0 | 0.0 |
| 50 | 367 | 672 | 373 | 573.0 | 0.86 | 573 | 1.06 | 573.0 | 573 | 0.0 | 573 | 573 | 2.98 | 0.0 | 0.0 |
| 50 | 367 | 672 | 379 | 560.0 | 0.86 | 560 | 0.87 | 560.0 | 560 | 0.0 | 560 | 560 | 1.61 | 0.0 | 0.0 |
| 50 | 367 | 672 | 385 | 549.0 | 0.83 | 551 | 0.99 | 549.0 | 549 | 0.5 | 549 | 549 | 17.12 | 0.0 | 0.0 |
| 50 | 367 | 2687 | 391 | 596.4 | 1.26 | 657 | 2.37 | 612.0 | 612 | 7.5 | 612 | 612 | 230.76 | 0.0 | 0.0 |
| 50 | 367 | 2687 | 397 | 596.7 | 1.27 | 663 | 2.24 | 615.0 | 615 | 6.6 | 615 | 615 | 154.67 | 0.0 | 0.0 |
| 50 | 367 | 2687 | 403 | 577.1 | 1.26 | 635 | 2.33 | 587.0 | 587 | 3.0 | 587 | 587 | 35.79 | 0.0 | 0.0 |
| 50 | 367 | 2687 | 409 | 608.5 | 1.26 | 721 | 2.4 | 634.0 | 634 | 7.3 | 634 | 634 | 508.17 | 0.0 | 0.0 |
| 50 | 367 | 2687 | 415 | 636.1 | 3.08 | 688 | 2.45 | 643.0 | 643 | 3.2 | 643 | 643 | 72.48 | 0.0 | 0.0 |
| 50 | 367 | 4702 | 421 | 624.4 | 1.66 | - | - | 701.3 | 726 | 5010.1 | 689 | 735 | 5010.00 | 1.7 | 1.2 |
| 50 | 367 | 4702 | 427 | 635.4 | 1.65 | - | - | 719.5 | 753 | 5010.0 | 712 | 762 | 5010.00 | 1.0 | 1.2 |
| 50 | 367 | 4702 | 433 | 646.9 | 1.64 | - | - | 723.9 | 786 | 5010.0 | 719 | 784 | 5010.00 | 0.7 | −0.3 |
| 50 | 367 | 4702 | 439 | 597.5 | 1.72 | - | - | 669.8 | 711 | 5010.0 | 666 | 702 | 5010.00 | 0.6 | −1.3 |
| 50 | 367 | 4702 | 445 | 665.1 | 1.71 | 868 | 3.36 | 737.3 | 764 | 5010.0 | 727 | 775 | 5010.00 | 1.4 | 1.4 |
| 50 | 490 | 1199 | 451 | 548.0 | 1.68 | 552 | 2.03 | 548.0 | 548 | 0.1 | 548 | 548 | 8.41 | 0.0 | 0.0 |
| 50 | 490 | 1199 | 457 | 530.0 | 1.66 | 531 | 1.88 | 530.0 | 530 | 0.5 | 530 | 530 | 11.77 | 0.0 | 0.0 |
| 50 | 490 | 1199 | 463 | 549.0 | 1.65 | 549 | 1.76 | 549.0 | 549 | 0.0 | 549 | 549 | 3.08 | 0.0 | 0.0 |
| 50 | 490 | 1199 | 469 | 540.0 | 1.67 | 541 | 2.01 | 540.0 | 540 | 0.2 | 540 | 540 | 46.21 | 0.0 | 0.0 |
| 50 | 490 | 1199 | 475 | 540.0 | 1.65 | 540 | 1.71 | 540.0 | 540 | 0.0 | 540 | 540 | 4.77 | 0.0 | 0.0 |
| 50 | 490 | 4793 | 481 | 584.3 | 2.38 | 629 | 4.63 | 594.0 | 594 | 7.8 | 594 | 594 | 109.31 | 0.0 | 0.0 |
| 50 | 490 | 4793 | 487 | 559.9 | 2.4 | 650 | 4.9 | 579.0 | 579 | 13.8 | 579 | 579 | 1473.29 | 0.0 | 0.0 |
| 50 | 490 | 4793 | 493 | 578.3 | 2.43 | 657 | 4.75 | 589.0 | 589 | 3.0 | 589 | 589 | 31.17 | 0.0 | 0.0 |
| 50 | 490 | 4793 | 499 | 565.4 | 2.39 | 643 | 4.74 | 577.0 | 577 | 7.5 | 577 | 577 | 118.57 | 0.0 | 0.0 |
| 50 | 490 | 4793 | 505 | 577.4 | 2.4 | 670 | 4.71 | 592.0 | 592 | 6.0 | 592 | 592 | 40.34 | 0.0 | 0.0 |
| 50 | 490 | 8387 | 511 | 575.0 | 2.4 | 812 | 6.54 | 632.2 | 666 | 5010.0 | 626 | 683 | 5010.00 | 1.0 | 2.6 |
| 50 | 490 | 8387 | 517 | 569.0 | 3.07 | - | - | 626.7 | 651 | 5010.0 | 618 | 646 | 5010.00 | 1.4 | −0.8 |
| 50 | 490 | 8387 | 523 | 592.2 | 3.08 | - | - | 658.4 | 678 | 5010.0 | 650 | 676 | 5010.00 | 1.3 | −0.3 |
| 50 | 490 | 8387 | 529 | 592.5 | 3.07 | - | - | 662.2 | 682 | 5010.1 | 654 | 692 | 5010.00 | 1.2 | 1.5 |
| 50 | 490 | 8387 | 535 | 587.5 | 3.09 | 828 | 6.95 | 644.2 | 657 | 5010.0 | 636 | 674 | 5010.00 | 1.3 | 2.6 |
| 75 | 555 | 1538 | 541 | 868.0 | 2.51 | - | - | 868.0 | 868 | 0.7 | 868 | 868 | 75.24 | 0.0 | 0.0 |
| 75 | 555 | 1538 | 547 | 870.9 | 2.49 | - | - | 871.0 | 871 | 3.0 | 871 | 871 | 58.57 | 0.0 | 0.0 |
| 75 | 555 | 1538 | 553 | 838.0 | 2.45 | - | - | 838.0 | 838 | 0.3 | 838 | 838 | 33.73 | 0.0 | 0.0 |
| 75 | 555 | 1538 | 559 | 855.0 | 2.47 | - | - | 855.0 | 855 | 4.4 | 855 | 855 | 44.64 | 0.0 | 0.0 |
| 75 | 555 | 1538 | 565 | 857.0 | 2.47 | - | - | 857.0 | 857 | 4.1 | 857 | 857 | 48.19 | 0.0 | 0.0 |
| 75 | 555 | 6150 | 571 | 942.3 | 3.49 | - | - | 1023.7 | 1047 | 5010.0 | 1011 | 1048 | 5010.00 | 1.2 | 0.1 |
| 75 | 555 | 6150 | 577 | 937.6 | 3.54 | - | - | 1008.8 | 1069 | 5010.2 | 996 | 1054 | 5010.00 | 1.3 | −1.4 |
| 75 | 555 | 6150 | 583 | 910.9 | 3.48 | - | - | 987.3 | 1040 | 5010.1 | 973 | 1044 | 5010.00 | 1.4 | 0.4 |
| 75 | 555 | 6150 | 589 | 913.0 | 3.53 | - | - | 985.6 | 998 | 5010.1 | 973 | 1004 | 5010.00 | 1.3 | 0.6 |
| 75 | 555 | 6150 | 595 | 897.9 | 3.54 | - | - | 962.6 | 994 | 5010.1 | 953 | 1009 | 5010.00 | 1.0 | 1.5 |
| 75 | 555 | 10,762 | 601 | 922.5 | 4.44 | - | - | 1054.5 | - | 4647.3 | 1048 | - | 5010.00 | 0.6 | 0.0 |
| 75 | 555 | 10,762 | 607 | 948.0 | 12.01 | - | - | 1070.9 | - | 3483.6 | 1066 | - | 5010.00 | 0.5 | 0.0 |
| 75 | 555 | 10,762 | 613 | 901.9 | 4.44 | - | - | 1041.0 | - | 5010.0 | 1034 | - | 5010.00 | 0.7 | 0.0 |
| 75 | 555 | 10,762 | 619 | 888.4 | 4.44 | - | - | 1006.4 | - | 5010.0 | 1005 | - | 5010.00 | 0.1 | 0.0 |
| 75 | 555 | 10,762 | 625 | 914.7 | 4.42 | - | - | 1048.1 | - | 3208.1 | 1043 | - | 5010.00 | 0.5 | 0.0 |
| 75 | 832 | 3457 | 631 | 797.8 | 6.86 | - | - | 798.0 | 798 | 4.8 | 798 | 798 | 78.24 | 0.0 | 0.0 |
| 75 | 832 | 3457 | 637 | 820.0 | 6.83 | - | - | 821.0 | 821 | 1.1 | 821 | 821 | 637.56 | 0.0 | 0.0 |
| 75 | 832 | 3457 | 643 | 815.3 | 6.87 | - | - | 816.0 | 816 | 4.0 | 816 | 816 | 262.59 | 0.0 | 0.0 |
| 75 | 832 | 3457 | 649 | 820.0 | 7.16 | - | - | 820.0 | 820 | 23.9 | 820 | 820 | 184.06 | 0.0 | 0.0 |
| 75 | 832 | 3457 | 655 | 815.0 | 7.23 | - | - | 815.0 | 815 | 1.4 | 815 | 815 | 84.81 | 0.0 | 0.0 |
| 75 | 832 | 13,828 | 661 | 830.9 | 9.08 | - | - | 875.7 | 891 | 5010.0 | 867 | 909 | 5010.00 | 1.0 | 2.0 |
| 75 | 832 | 13,828 | 667 | 859.5 | 9.05 | - | - | 901.8 | 947 | 5010.1 | 893 | 956 | 5010.00 | 1.0 | 1.0 |
| 75 | 832 | 13,828 | 673 | 829.0 | 9.04 | - | - | 873.7 | 892 | 5010.0 | 862 | 934 | 5010.00 | 1.3 | 4.7 |
| 75 | 832 | 13,828 | 679 | 842.2 | 8.98 | - | - | 885.6 | 915 | 4570.8 | 874 | 918 | 5010.00 | 1.3 | 0.3 |
| 75 | 832 | 13,828 | 685 | 846.7 | 9.05 | - | - | 886.9 | 896 | 5010.0 | 877 | 911 | 5010.00 | 1.1 | 1.7 |
| 75 | 832 | 24,199 | 691 | 870.0 | 12.24 | - | - | 955.8 | - | 1305.3 | 954 | - | 5010.00 | 0.2 | 0.0 |
| 75 | 832 | 24,199 | 697 | 837.7 | 12.33 | - | - | 913.0 | - | 1161.2 | 913 | - | 5010.00 | 0.0 | 0.0 |
| 75 | 832 | 24,199 | 703 | 842.0 | 27.17 | - | - | 915.0 | - | 953.0 | 913 | - | 5010.00 | 0.2 | 0.0 |
| 75 | 832 | 24,199 | 709 | 863.0 | 11.98 | - | - | 950.4 | - | 5010.1 | 954 | - | 5010.00 | −0.4 | 0.0 |
| 75 | 832 | 24,199 | 715 | 878.7 | 12.14 | - | - | 960.8 | - | 962.3 | 960 | - | 5010.00 | 0.1 | 0.0 |
| 75 | 1110 | 6155 | 721 | 787.0 | 14.88 | - | - | 787.0 | 787 | 2.1 | 787 | 787 | 237.82 | 0.0 | 0.0 |
| 75 | 1110 | 6155 | 727 | 785.0 | 14.82 | - | - | 785.0 | 785 | 5.4 | 785 | 785 | 214.71 | 0.0 | 0.0 |
| 75 | 1110 | 6155 | 733 | 783.0 | 14.78 | - | - | 783.0 | 783 | 0.0 | 783 | 783 | 102.86 | 0.0 | 0.0 |
| 75 | 1110 | 6155 | 739 | 783.9 | 14.94 | - | - | 784.0 | 784 | 3.3 | 784 | 784 | 128.21 | 0.0 | 0.0 |
| 75 | 1110 | 6155 | 745 | 796.5 | 14.86 | - | - | 797.0 | 797 | 5.7 | 797 | 797 | 479.97 | 0.0 | 0.0 |
| 75 | 1110 | 24,620 | 751 | 816.9 | 19.16 | - | - | 846.5 | 857 | 5010.0 | 840 | 871 | 5010.00 | 0.8 | 1.6 |
| 75 | 1110 | 24,620 | 757 | 798.0 | 19.28 | - | - | 829.2 | 851 | 4573.5 | 824 | 847 | 5010.00 | 0.6 | −0.5 |
| 75 | 1110 | 24,620 | 763 | 808.4 | 19.44 | - | - | 841.5 | 892 | 2189.8 | 837 | 917 | 5010.00 | 0.5 | 2.8 |
| 75 | 1110 | 24,620 | 769 | 808.0 | 19.31 | - | - | 841.6 | 864 | 2866.0 | 833 | 876 | 5010.00 | 1.0 | 1.4 |
| 75 | 1110 | 24,620 | 775 | 804.0 | 19.32 | - | - | 837.8 | 868 | 5010.1 | 829 | 868 | 5010.00 | 1.0 | 0.0 |
| 75 | 1110 | 43,085 | 781 | 817.0 | 27.33 | - | - | 873.5 | - | 2357.1 | 870 | - | 5010.00 | 0.4 | 0.0 |
| 75 | 1110 | 43,085 | 787 | 804.0 | 26.74 | - | - | 857.0 | - | 3106.8 | 859 | - | 5010.00 | −0.2 | 0.0 |
| 75 | 1110 | 43,085 | 793 | 827.3 | 26.9 | - | - | 885.9 | 1194 | 3443.8 | 884 | - | 5010.00 | 0.2 | 100.0 |
| 75 | 1110 | 43,085 | 799 | 799.0 | - | - | 856.70 | - | 3448.3 | 861 | - | 5010.00 | −0.5 | 0.0 | |
| 75 | 1110 | 43,085 | 805 | 806.0 | 27.14 | - | - | 859.1 | - | 3146.2 | 851 | - | 5010.00 | 0.9 | 0.0 |
| 100 | 990 | 4896 | 811 | 1118.5 | 11.59 | - | - | 1119.0 | 1119 | 43.7 | 1116 | 1121 | 5010.00 | 0.3 | 0.2 |
| 100 | 990 | 4896 | 817 | 1134.7 | 11.43 | - | - | 1137.0 | 1137 | 11.8 | 1137 | 1137 | 1091.57 | 0.0 | 0.0 |
| 100 | 990 | 4896 | 823 | 1112.5 | 11.71 | - | - | 1113.0 | 1113 | 71.8 | 1113 | 1113 | 493.89 | 0.0 | 0.0 |
| 100 | 990 | 4896 | 829 | 1109.6 | 11.48 | - | - | 1110.0 | 1110 | 48.6 | 1110 | 1110 | 942.31 | 0.0 | 0.0 |
| 100 | 990 | 4896 | 835 | 1088.7 | 11.99 | - | - | 1090.0 | 1090 | 35.8 | 1090 | 1090 | 357.10 | 0.0 | 0.0 |
| 100 | 990 | 19,583 | 841 | 1175.6 | 15.37 | - | - | 1249.4 | - | 5010.0 | 1239 | 1570 | 5010.00 | 0.8 | −100.0 |
| 100 | 990 | 19,583 | 847 | 1142.0 | 14.98 | - | - | 1225.8 | 1491 | 5010.0 | 1205 | 1650 | 5010.00 | 1.7 | 10.7 |
| 100 | 990 | 19,583 | 853 | 1140.7 | 14.8 | - | - | 1215.0 | 1510 | 5010.0 | 1203 | 1623 | 5010.00 | 1.0 | 7.5 |
| 100 | 990 | 19,583 | 859 | 1178.1 | 14.82 | - | - | 1264.2 | 1441 | 5010.2 | 1248 | 1632 | 5010.00 | 1.3 | 13.3 |
| 100 | 990 | 19,583 | 865 | 1176.4 | 15.36 | - | - | 1257.3 | 1560 | 5010.1 | 1244 | 1555 | 5010.00 | 1.1 | −0.3 |
| 100 | 990 | 34,269 | 871 | 1126.4 | 22.2 | - | - | 1264.8 | - | 5010.0 | 1251 | - | 5010.00 | 1.1 | 0.0 |
| 100 | 990 | 34,269 | 877 | 1148.9 | 24.59 | - | - | 1295.6 | - | 5010.0 | 1285 | - | 5010.00 | 0.8 | 0.0 |
| 100 | 990 | 34,269 | 883 | 1179.9 | 21.17 | - | - | 1323.7 | - | 5010.0 | 1305 | - | 5010.00 | 1.4 | 0.0 |
| 100 | 990 | 34,269 | 889 | 1146.7 | 20.3 | - | - | 1283.6 | - | 5010.0 | 1268 | - | 5010.00 | 1.2 | 0.0 |
| 100 | 990 | 34,269 | 895 | 1155.0 | 20.42 | - | - | 1309.1 | - | 5010.0 | 1297 | - | 5010.00 | 0.9 | 0.0 |
| 100 | 1485 | 11,019 | 901 | 1077.9 | 34.81 | - | - | 1079.0 | 1079 | 248.6 | 1077 | 1081 | 5010.00 | 0.2 | 0.2 |
| 100 | 1485 | 11,019 | 907 | 1054.9 | 34.46 | - | - | 1056.0 | 1056 | 113.4 | 1056 | 1056 | 757.17 | 0.0 | 0.0 |
| 100 | 1485 | 11,019 | 913 | 1059.0 | 34.29 | - | - | 1059.0 | 1059 | 47.9 | 1059 | 1059 | 503.94 | 0.0 | 0.0 |
| 100 | 1485 | 11,019 | 919 | 1046.0 | 34.09 | - | - | 1046.0 | 1046 | 195.2 | 1046 | 1046 | 1206.51 | 0.0 | 0.0 |
| 100 | 1485 | 11,019 | 925 | 1071.2 | 34.17 | - | - | 1072.0 | 1072 | 249.6 | 1071 | 1072 | 5010.00 | 0.1 | 0.0 |
| 100 | 1485 | 44,075 | 931 | 1096.9 | 46.07 | - | - | 1144.0 | 1374 | 3018.3 | 1130 | 1444 | 5010.00 | 1.2 | 5.1 |
| 100 | 1485 | 44,075 | 937 | 1091.0 | 45.6 | - | - | 1143.6 | 1291 | 2144.6 | 1134 | 1511 | 5010.00 | 0.8 | 17.0 |
| 100 | 1485 | 44,075 | 943 | 1084.4 | 46.54 | - | - | 1137.6 | 1344 | 3075.6 | 1125 | 1390 | 5010.00 | 1.1 | 3.4 |
| 100 | 1485 | 44,075 | 949 | 1089.4 | 46.01 | - | - | 1136.9 | 1286 | 3523.3 | 1131 | 1417 | 5010.00 | 0.5 | 10.2 |
| 100 | 1485 | 44,075 | 955 | 1088.4 | 45.84 | - | - | 1134.6 | 1370 | 2954.2 | 1127 | 1524 | 5010.00 | 0.7 | 11.2 |
| 100 | 1485 | 77,131 | 961 | 1083.5 | 60.68 | - | - | 1164.4 | - | 4773.8 | 1156 | - | 5010.00 | 0.7 | 0.0 |
| 100 | 1485 | 77,131 | 967 | 1086.0 | 60.29 | - | - | 1168.2 | - | 5010.0 | 1160 | - | 5010.00 | 0.7 | 0.0 |
| 100 | 1485 | 77,131 | 973 | 1094.0 | 60.69 | - | - | 1187.8 | - | 5010.0 | 1175 | - | 5010.00 | 1.1 | 0.0 |
| 100 | 1485 | 77,131 | 979 | 1105.9 | 60.83 | - | - | 1183.7 | - | 5010.0 | 1175 | - | 5010.00 | 0.7 | 0.0 |
| 100 | 1485 | 77,131 | 985 | 1090.9 | 60.63 | - | - | 1164.5 | - | 5010.0 | 1155 | - | 5010.00 | 0.8 | 0.0 |
| 100 | 1980 | 19,593 | 991 | 1030.9 | 76.15 | - | - | 1031.0 | 1031 | 214.4 | 1031 | 1031 | 919.88 | 0.0 | 0.0 |
| 100 | 1980 | 19,593 | 997 | 1034.9 | 76.02 | - | - | 1036.0 | 1036 | 42.8 | 1036 | 1036 | 1298.69 | 0.0 | 0.0 |
| 100 | 1980 | 19,593 | 1003 | 1024.0 | 76.43 | - | - | 1024.0 | 1024 | 21.8 | 1024 | 1024 | 622.64 | 0.0 | 0.0 |
| 100 | 1980 | 19,593 | 1009 | 1025.0 | 76.67 | - | - | 1025.0 | 1025 | 27.4 | 1025 | 1025 | 546.97 | 0.0 | 0.0 |
| 100 | 1980 | 19,593 | 1015 | 1027.5 | 77.49 | - | - | 1028.0 | 1028 | 151.0 | 1028 | 1028 | 1964.48 | 0.0 | 0.0 |
| 100 | 1980 | 78,369 | 1021 | 1060.5 | 106.68 | - | - | 1097.0 | 1234 | 5010.1 | 1091 | 1358 | 5010.00 | 0.5 | 10.0 |
| 100 | 1980 | 78,369 | 1027 | 1034.0 | 106.82 | - | - | 1065.6 | 1187 | 5010.1 | 1064 | 1305 | 5010.00 | 0.2 | 9.9 |
| 100 | 1980 | 78,369 | 1033 | 1050.5 | 104.96 | - | - | 1087.4 | 1213 | 5010.1 | 1076 | 1314 | 5010.00 | 1.0 | 8.3 |
| 100 | 1980 | 78,369 | 1039 | 1048.1 | 103.83 | - | - | 1083.5 | 1221 | 5010.1 | 1076 | 1320 | 5010.00 | 0.7 | 8.1 |
| 100 | 1980 | 78,369 | 1045 | 1048.9 | 103.99 | - | - | 1084.1 | 1245 | 5010.1 | 1079 | 1353 | 5010.00 | 0.5 | 8.7 |
| 100 | 1980 | 137,145 | 1051 | 1041.8 | 129.47 | - | - | 1100.6 | - | 5010.1 | 1086 | - | 5010.00 | 1.3 | 0.0 |
| 100 | 1980 | 137,145 | 1057 | 1066.5 | 129.26 | - | - | 1126.3 | - | 5010.1 | 1114 | - | 5010.00 | 1.1 | 0.0 |
| 100 | 1980 | 137,145 | 1063 | 1052.4 | 130.38 | - | - | 1111.3 | - | 5010.1 | 1087 | - | 5010.00 | 2.2 | 0.0 |
| 100 | 1980 | 137,145 | 1069 | 1062.9 | 130.01 | - | - | 1118.7 | - | 5010.1 | 1100 | - | 5010.00 | 1.7 | 0.0 |
| 100 | 1980 | 137,145 | 1075 | 1055.5 | 130.01 | - | - | 1114.1 | - | 5010.1 | 1105 | - | 5010.00 | 0.8 | 0.0 |
| Averages | 0.4 | 0.8 | |||||||||||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Montemanni, R.; Smith, D.H. On Solving the Minimum Spanning Tree Problem with Conflicting Edge Pairs. Algorithms 2025, 18, 526. https://doi.org/10.3390/a18080526
Montemanni R, Smith DH. On Solving the Minimum Spanning Tree Problem with Conflicting Edge Pairs. Algorithms. 2025; 18(8):526. https://doi.org/10.3390/a18080526
Chicago/Turabian StyleMontemanni, Roberto, and Derek H. Smith. 2025. "On Solving the Minimum Spanning Tree Problem with Conflicting Edge Pairs" Algorithms 18, no. 8: 526. https://doi.org/10.3390/a18080526
APA StyleMontemanni, R., & Smith, D. H. (2025). On Solving the Minimum Spanning Tree Problem with Conflicting Edge Pairs. Algorithms, 18(8), 526. https://doi.org/10.3390/a18080526







