A Lightweight Deep Learning Approach for Detecting External Intrusion Signals from Optical Fiber Sensing System Based on Temporal Efficient Residual Network
Abstract
1. Introduction
- A novel lightweight architecture—TEResNet—is proposed. All low-level features are incorporated into the formation of high-level features in subsequent layers, thus eliminating the need to stack multiple layers in order to generate high-level features.
- A new dataset comprising 6948 signal segments was collected in the construction environment of the Guangzhou Metro, which has been made publicly available to facilitate further research.
- Experiments show that with only 48,009 learnable parameters, TEResNet achieves an accuracy of 97.12% and an F1 score of 96.15%, which is a superior performance compared to existing methods and advanced neural networks.
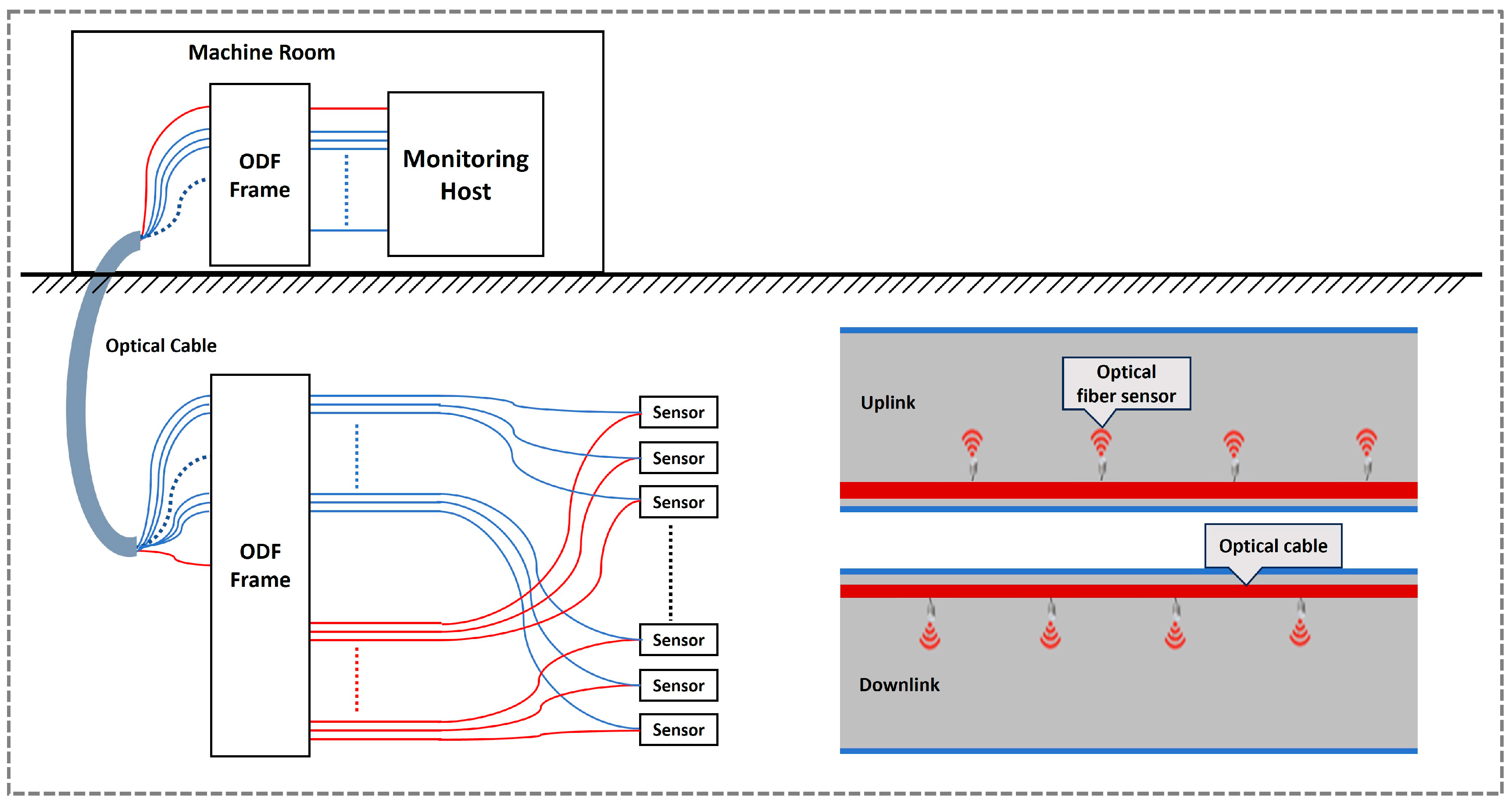
2. Dataset
2.1. Data Acquisition and Analysis
2.2. Dataset Preprocessing
3. Proposed Lightweight Deep Learning Approach
3.1. Characteristic Analysis
3.2. Temporal Efficient Residual Network
3.2.1. Overview of the Proposed TEResNet
3.2.2. Temporal Convolution
3.2.3. Dilated Convolution
3.2.4. Basic Block of ResNet Style
4. Results
4.1. Evaluation Indicators
- (1)
- Accuracy: the proportion of the number of samples correctly categorized out of all samples to the total number of samples, calculated using the following formula:
- (2)
- Precision: the proportion of samples predicted by the model to be positive that are actually positive, calculated using the following formula:
- (3)
- Recall: the proportion of the number of samples accurately predicted as positive by the model to the number of all positive samples, calculated using the following formula:
- (4)
- F1 score: a reconciled mean evaluation metric of precision and recall, calculated using the following formula:
4.2. Experiments and Analysis
4.2.1. Ablation Experiments and Parameter Selection
4.2.2. Comparative Experiments
4.2.3. Complete Signal Testing
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nasrollahi, K.; Dijkstra, J.; Nielsen, J.C.O. Towards real-time condition monitoring of a transition zone in a railway structure using fibre Bragg grating sensors. Transp. Geotech. 2024, 44, 101166. [Google Scholar] [CrossRef]
- Abbas, N.; Umar, T.; Salih, R.; Akbar, M.; Hussain, Z.; Haibei, X. Structural Health Monitoring of Underground Metro Tunnel by Identifying Damage Using ANN Deep Learning Auto-Encoder. Appl. Sci. 2023, 13, 1332. [Google Scholar] [CrossRef]
- He, R.; Zhang, X.; Wang, X.; Zhao, Z.; An, S. Analysis and Prediction Method for Metro Tunnel Monitoring Data Based on Deep Learning. Tunn. Constr. 2021, 41, 584. [Google Scholar]
- Yang, L.; Li, S.M.; Chen, D.H.; Wu, Z.M. Impact dynamics analysis of shed tunnel structure hit by collapse rock-fall. Appl. Mech. Mater. 2011, 99–100, 1023–1026. [Google Scholar] [CrossRef]
- Liu, F.; Ma, D.; Li, S.; Gan, W.; Li, Z. Classifying Tunnel Anomalies Based on Ultraweak FBGs Signal and Transductive RVM Combined with Gaussian Mixture Model. IEEE Sens. J. 2020, 20, 6012–6019. [Google Scholar] [CrossRef]
- Prisutova, J.; Krynkin, A.; Tait, S.; Horoshenkov, K. Use of Fibre-Optic Sensors for Pipe Condition and Hydraulics Measurements: A Review. CivilEng 2022, 3, 85–113. [Google Scholar] [CrossRef]
- Li, S.; Jin, L.; Jiang, J.; Wang, H.; Nan, Q.; Sun, L. Looseness Identification of Track Fasteners Based on Ultra-Weak FBG Sensing Technology and Convolutional Autoencoder Network. Sensors 2022, 22, 5653. [Google Scholar] [CrossRef]
- Xie, Y.; Wang, M.; Zhong, Y.; Deng, L.; Zhang, J. Label-Free Anomaly Detection Using Distributed Optical Fiber Acoustic Sensing. Sensors 2023, 23, 4094. [Google Scholar] [CrossRef] [PubMed]
- Moffat, R.; Sotomayor, J.; Beltrán, J.F. Estimating tunnel wall displacements using a simple sensor based on a Brillouin optical time domain reflectometer apparatus. Int. J. Rock Mech. Min. Sci. 2015, 75, 233–243. [Google Scholar] [CrossRef]
- Braunfelds, J.; Senkans, U.; Skels, P.; Janeliukstis, R.; Porins, J.; Spolitis, S.; Bobrovs, V. Road Pavement Structural Health Monitoring by Embedded Fiber-Bragg-Grating-Based Optical Sensors. Sensors 2022, 22, 4581. [Google Scholar] [CrossRef] [PubMed]
- Huang, W.; Zhang, W.; Huang, J.; Li, F. Demonstration of multi-channel fiber optic interrogator based on time-division locking technique in subway intrusion detection. Opt. Express 2020, 28, 11472–11481. [Google Scholar] [CrossRef] [PubMed]
- Wang, J.; Peng, H.; Zhou, P.; Guo, J.; Jia, B.; Wu, H. Sound source localization based on Michelson fiber optic interferometer array. Opt. Fiber Technol. 2019, 51, 112–117. [Google Scholar] [CrossRef]
- Li, J.; Wang, Y.; Wang, P.; Bai, Q.; Gao, Y.; Zhang, H.; Jin, B. Pattern Recognition for Distributed Optical Fiber Vibration Sensing: A Review. IEEE Sens. J. 2021, 21, 11983–11998. [Google Scholar] [CrossRef]
- Luo, L.; Wang, W.; Yu, H.; Chen, X.; Bao, S. Abnormal event monitoring of underground pipelines using a distributed fiber-optic vibration sensing system. Meas. J. Int. Meas. Confed. 2023, 221, 113488. [Google Scholar] [CrossRef]
- Sheng, L.I.; Yang, Q.I.U.; Qiuming, N.A.N.; Weibing, G.A.N.; Jinpeng, J. Identification and location method of illegal intrusion of drilling rig in subway line based on ultra-weak grating sensor array. J. Vib. Shock 2022, 41, 202–207. [Google Scholar]
- Guo, Y.; Chen, M.; Xiong, L.; Zhou, X.; Li, C. Fiber Bragg grating based acceleration sensors: A review. Sens. Rev. 2021, 41, 101–122. [Google Scholar] [CrossRef]
- Ma, C.; Liu, T.; Liu, K.; Jiang, J.; Ding, Z.; Pan, L.; Tian, M. Long-Range Distributed Fiber Vibration Sensor Using an Asymmetric Dual Mach-Zehnder Interferometers. J. Light. Technol. 2016, 34, 2235–2239. [Google Scholar] [CrossRef]
- Liu, K.; Jin, X.; Jiang, J.; Xu, T.; Ding, Z.; Huang, Y.; Sun, Z.; Xue, K.; Li, S.; Liu, T. Interferometer-Based Distributed Optical Fiber Sensors in Long-Distance Vibration Detection: A Review. IEEE Sens. J. 2022, 22, 21428–21444. [Google Scholar] [CrossRef]
- Chojnacki, M.; Pałka, N. Demodulation of output signals from unbalanced fibre optic Michelson interferometer. In Proceedings of the International Conference on Modern Problems of Radio Engineering, Telecommunications and Computer Science, TCSET 2002, Lviv-Slavsko, Ukraine, 18–23 February 2002. [Google Scholar]
- Jayawickrema, U.M.N.; Herath, H.M.C.M.; Hettiarachchi, N.K.; Sooriyaarachchi, H.P.; Epaarachchi, J.A. Fibre-optic sensor and deep learning-based structural health monitoring systems for civil structures: A review. Meas. J. Int. Meas. Confed. 2022, 199, 111543. [Google Scholar] [CrossRef]
- Tejedor, J.; Macias-Guarasa, J.; Martins, H.F.; Pastor-Graells, J.; Corredera, P.; Martin-Lopez, S. Machine learning methods for pipeline surveillance systems based on distributed acoustic sensing: A review. Appl. Sci. 2017, 7, 841. [Google Scholar] [CrossRef]
- Sidelnikov, O.; Redyuk, A.; Sygletos, S. Equalization performance and complexity analysis of dynamic deep neural networks in long haul transmission systems. Opt. Express 2018, 26, 32765–32776. [Google Scholar] [CrossRef]
- Hongquan, Q.; Tong, Z.; Fukun, B.; Liping, P. Vibration detection method for optical fibre pre-warning system. IET Signal Process. 2016, 10, 692–698. [Google Scholar] [CrossRef]
- Qiu, Z.; Zheng, T.; Qu, H.; Pang, L. A new detection method based on CFAR and DE for OFPS. Photonic Sens. 2016, 6, 261–267. [Google Scholar] [CrossRef][Green Version]
- Bai, Y.; Xing, J.; Xie, F.; Liu, S.; Li, J. Detection and identification of external intrusion signals from 33 km optical fiber sensing system based on deep learning. Opt. Fiber Technol. 2019, 53, 102060. [Google Scholar] [CrossRef]
- Jia, Z.; Ren, L.; Li, H.; Sun, W. Pipeline leak localization based on FBG hoop strain sensors combined with BP neural network. Appl. Sci. 2018, 8, 146. [Google Scholar] [CrossRef]
- Li, S.; Peng, R.; Liu, Z. A surveillance system for urban buried pipeline subject to third-party threats based on fiber optic sensing and convolutional neural network. Struct. Health Monit. 2021, 20, 1704–1715. [Google Scholar] [CrossRef]
- Wu, H.; Chen, J.; Liu, X.; Xiao, Y.; Wang, M.; Zheng, Y.; Rao, Y. One-Dimensional CNN-Based Intelligent Recognition of Vibrations in Pipeline Monitoring With DAS. J. Light. Technol. 2019, 37, 4359–4366. [Google Scholar] [CrossRef]
- Tian, W.; Meng, J.; Zhong, X.J.; Tan, X. Intelligent Early Warning System for Construction Safety of Excavations Adjacent to Existing Metro Tunnels. Adv. Civ. Eng. 2021, 2021, 6690610. [Google Scholar] [CrossRef]
- Liu, W.; Liang, R.; Zhang, H.; Wu, Z.; Jiang, B. Deep learning based identification and uncertainty analysis of metro train induced ground-borne vibration. Mech. Syst. Signal Process. 2023, 189, 110062. [Google Scholar] [CrossRef]
- Huang, H.; Li, Q. Image recognition for water leakage in shield tunnel based on deep learning. Yanshilixue Yu Gongcheng Xuebao/Chin. J. Rock Mech. Eng. 2017, 36, 2861–2871. [Google Scholar] [CrossRef]
- Lyu, C.; Hu, X.; Niu, Z.; Yang, B.; Jin, J.; Ge, C. A light-weight neural network for marine acoustic signal recognition suitable for fiber-optic hydrophones. Expert Syst. Appl. 2024, 235, 121235. [Google Scholar] [CrossRef]
- Ma, J.; Hu, M.; Yang, Z.; Yang, H.; Ma, S.; Xu, H.; Yang, L.; Wu, Z. An Efficient Lightweight Deep-Learning Approach for Guided Lamb Wave-Based Damage Detection in Composite Structures. Appl. Sci. 2023, 13, 5022. [Google Scholar] [CrossRef]
- Liu, J.; Member, S.; Wen, Z.; Member, G.S. Online Pipeline Weld Defect Detection for Magnetic Flux Leakage Inspection System via Lightweight Rotated Network. IEEE Trans. Ind. Electron. 2024, 1–12. [Google Scholar] [CrossRef]
- Kong, Y.; Liu, Y.; Shi, Y.; Ansari, F.; Taylor, T. Research on the ϕ-OTDR fiber sensor sensitive for all of the distance. Opt. Commun. 2018, 407, 148–152. [Google Scholar] [CrossRef]
- Zhu, W.; Li, X.; Liu, C.; Xue, F.; Han, Y. An STFT-LSTM System for P-Wave Identification. IEEE Geosci. Remote Sens. Lett. 2020, 17, 519–523. [Google Scholar] [CrossRef]
- Choi, S.; Seo, S.; Shin, B.; Byun, H.; Kersner, M.; Kim, B.; Kim, D.; Ha, S. Temporal convolution for real-time keyword spotting on mobile devices. In Proceedings of the Annual Conference of the International Speech Communication Association (INTERSPEECH 2019), Graz, Austria, 15–19 September 2019; pp. 3372–3376. [Google Scholar] [CrossRef]
- Li, X.; Wei, X.; Qin, X. Small-footprint keyword spotting with multi-scale temporal convolution. In Proceedings of the Proceedings of the Annual Conference of the International Speech Communication Association, INTERSPEECH 2020, Shanghai, China, 25–29 October 2020, Shanghai, China, 25–29 October 2020; pp. 1987–1991. [Google Scholar] [CrossRef]
- Hou, J.; Xie, L.; Zhang, S. Two-stage streaming keyword detection and localization with multi-scale depthwise temporal convolution. Neural Netw. 2022, 150, 28–42. [Google Scholar] [CrossRef] [PubMed]
- Coucke, A.; Chlieh, M.; Gisselbrecht, T.; Leroy, D.; Poumeyrol, M.; Lavril, T. Efficient Keyword Spotting Using Dilated Convolutions and Gating. In Proceedings of the 2019 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP 2019), Brighton, UK, 12–17 May 2019; pp. 6351–6355. [Google Scholar] [CrossRef]
- Yu, F.; Koltun, V. Multi-scale context aggregation by dilated convolutions. In Proceedings of the 4th International Conference on Learning Representations, ICLR 2016—Conference Track Proceedings, San Juan, Puerto Rico, 2–4 May 2016. [Google Scholar]
- He, K.; Zhang, X.; Ren, S.; Sun, J. Deep residual learning for image recognition. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Las Vegas, NV, USA, 27–30 June 2016; pp. 770–778. [Google Scholar] [CrossRef]
- Kingma, D.P.; Ba, J.L. Adam: A method for stochastic optimization. In Proceedings of the 3rd International Conference on Learning Representations, ICLR 2015—Conference Track Proceedings, San Diego, CA, USA, 7–9 May 2015. [Google Scholar]
- Staudemeyer, R.C.; Morris, E.R. Understanding LSTM—A tutorial into Long Short-Term Memory Recurrent Neural Networks. arXiv 2019, arXiv:1909.09586. [Google Scholar]
- Cho, K.; Van Merriënboer, B.; Gulcehre, C.; Bahdanau, D.; Bougares, F.; Schwenk, H.; Bengio, Y. Learning phrase representations using RNN encoder-decoder for statistical machine translation. In Proceedings of the 2014 Conference on Empirical Methods in Natural Language Processing (EMNLP), Doha, Qatar, 25–29 October 2014; pp. 1724–1734. [Google Scholar] [CrossRef]
- Li, S.; Qiu, Y.; Jiang, J.; Wang, H.; Nan, Q.; Sun, L. Identification of Abnormal Vibration Signal of Subway Track Bed Based on Ultra-Weak FBG Sensing Array Combined with Unsupervised Learning Network. Symmetry 2022, 14, 1100. [Google Scholar] [CrossRef]
- Vaswani, A.; Shazeer, N.; Parmar, N.; Uszkoreit, J.; Jones, L.; Gomez, A.N.; Kaiser, Ł.; Polosukhin, I. Attention is all you need. In Proceedings of the Advances in Neural Information Processing Systems, Long Beach, CA, USA, 4–9 December 2017; Volume 2017. [Google Scholar]


















| Train | Test | |
|---|---|---|
| Normal | 4650 | 255 |
| Abnormal | 1898 | 162 |
| Total | 6548 | 417 |
| True | Predicted | |
|---|---|---|
| Negative | Positive | |
| Negative | TN (True Negative) | FP (False Positive) |
| Positive | FN (False Negative) | TP (True Positive) |
| M | N | P | Q | |
|---|---|---|---|---|
| Parameter 1 | 8 | 8 | 8 | 16 |
| Parameter 2 | 8 | 8 | 16 | 24 |
| Parameter 3 | 8 | 16 | 24 | 32 |
| Parameter 4 | 8 | 24 | 32 | 48 |
| Methods | Accuracy (%)/Precision (%)/Recall (%) | F1 Score (%) | Parameters | Inference Time (ms/Sample) |
|---|---|---|---|---|
| CNN | 75.54/65.63/77.78 | 71.19 | 395,681 | 0.0544 |
| LSTM | 76.50/64.95/85.80 | 73.94 | 3,289,601 | 0.0180 |
| GRU | 75.30/63.98/83.33 | 72.39 | 2,500,097 | 0.0095 |
| CNN-LSTM-AM | 86.57/100/65.43 | 79.10 | 4,316,293 | 1.1912 |
| Transformer | 88.73/89.12/80.86 | 84.79 | 530,434 | 24.30 |
| 1DResNet | 88.49/100/70.37 | 82.61 | 3,844,930 | 0.0800 |
| LCANet | 90.41/100/75.31 | 85.92 | 87,105 | 0.1269 |
| STFT+2DResNet | 95.68/100/88.89 | 94.12 | 11,168,193 | 0.3196 |
| CLDNN | 96.40/100/90.74 | 95.15 | 4,742,081 | 0.0626 |
| TEResNet (our) | 97.12/100/92.59 | 96.15 | 48,009 | 0.0480 |
| Methods | Accuracy (%) | F1 Score (%) | Parameters | Inference Time (ms/Sample) |
|---|---|---|---|---|
| LCANet | 90.41 | 85.92 | 87,105 | 0.1269 |
| TEResNet (our) | 97.12 (+7.4%) | 96.15 (+11.9%) | 48,009 (−44.9%) | 0.0480 (−62.2%) |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Y.; Guo, Z.; Luo, H.; Liu, J.; Zhou, R. A Lightweight Deep Learning Approach for Detecting External Intrusion Signals from Optical Fiber Sensing System Based on Temporal Efficient Residual Network. Algorithms 2025, 18, 101. https://doi.org/10.3390/a18020101
Wang Y, Guo Z, Luo H, Liu J, Zhou R. A Lightweight Deep Learning Approach for Detecting External Intrusion Signals from Optical Fiber Sensing System Based on Temporal Efficient Residual Network. Algorithms. 2025; 18(2):101. https://doi.org/10.3390/a18020101
Chicago/Turabian StyleWang, Yizhao, Ziye Guo, Haitao Luo, Jing Liu, and Ruohua Zhou. 2025. "A Lightweight Deep Learning Approach for Detecting External Intrusion Signals from Optical Fiber Sensing System Based on Temporal Efficient Residual Network" Algorithms 18, no. 2: 101. https://doi.org/10.3390/a18020101
APA StyleWang, Y., Guo, Z., Luo, H., Liu, J., & Zhou, R. (2025). A Lightweight Deep Learning Approach for Detecting External Intrusion Signals from Optical Fiber Sensing System Based on Temporal Efficient Residual Network. Algorithms, 18(2), 101. https://doi.org/10.3390/a18020101









