Asynchronous Gathering in a Dangerous Ring †
Abstract
1. Introduction
1.1. Premise
1.2. Background
- Gathering. The gathering problem consists in having the agents meet at the same node and enter a terminal state within a finite amount of time; there is no a priori restriction on which node will become the gathering point. The gathering problem has been extensively investigated under a large variety of settings and communication mechanisms. In anonymous and symmetric settings, like the one considered here, the possibility (and difficulty) of a solution is related to the possibility (and difficulty) to deterministically find or create an asymmetry in the system, enabling the agents to agree on a meeting point.
- Black Hole Search. Among the severe security threats faced in systems supporting mobile agents, a particularly troublesome one is a harmful host; that is, the presence at a network site of harmful stationary processes. The problem posed by the presence of a harmful host has been intensively studied from a programming point of view (e.g., see [9,10,11]), and also from an algorithmic prospective [12]. Obviously, the first step in any solution to such a problem must be to identify, if possible, the harmful host determining its location. Depending on the nature of the danger, the task to identify the harmful host might be difficult, if not impossible, to perform.
1.3. Contributions
2. Definitions, Basic Properties, and Techniques
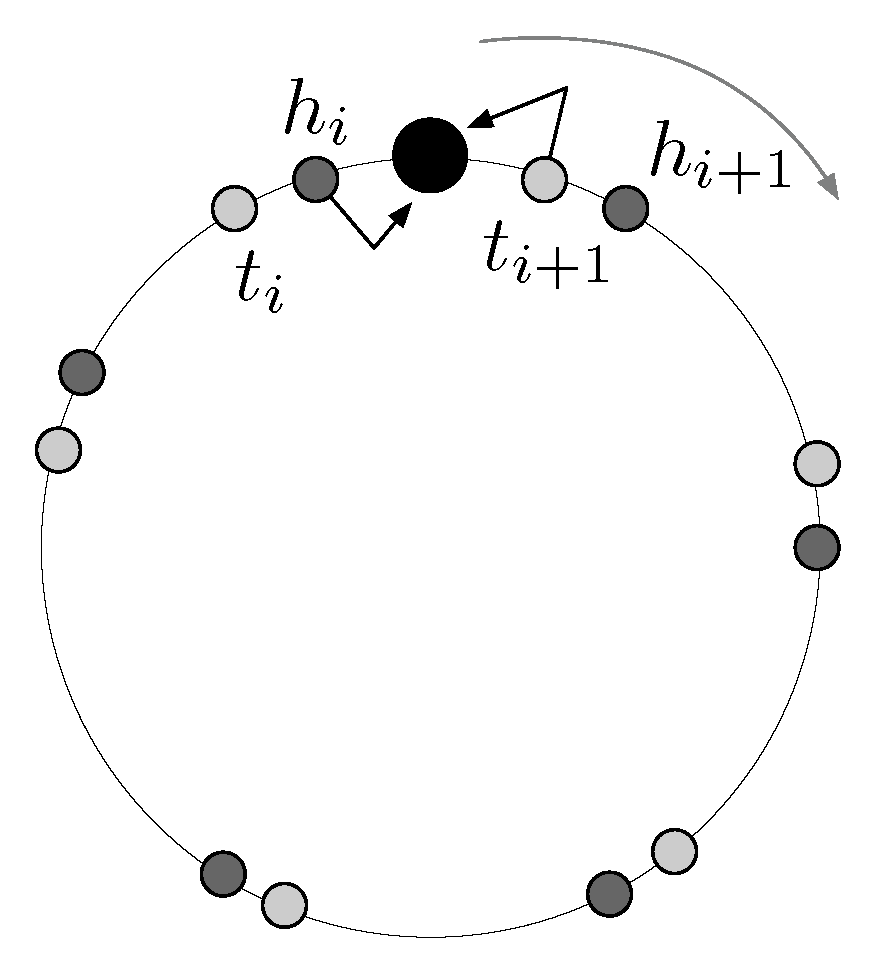
2.1. Model
- In the oriented case, there is a single extremal agent—the leftmost one, measured from the Bh.
- In the unoriented case, there are two extremal agents—the leftmost agent within each group of agents with the same understanding of left and right (note that `leftmost’ is evaluated using the orientation of the group).
2.2. Cautious Walk
- unexplored—if no agent has moved across this port,
- safe—if an agent arrived via this port, or
- active—if an agent departed via this port, but no agent has arrived via it.
- Rule 1. When an agent moves from node u to v via an unexplored port, this marks the port as active; arriving at v, if there is no black hole there, it immediately returns to u, which marks the port as safe, and then continues the execution of the algorithm.
- Rule 2. An agent never leaves via an active port.
- Rule 3. An agent can always leave via a safe port.
2.3. Basic Results and Lower Bounds
- 1.
- is unsolvable;
- 2.
- If the ring is unoriented, then is unsolvable.
- (1) It suffices for the adversary to choose as the location of the black hole the node where the first moving agent goes to: it disappears in the black hole, hence it will never be able to gather.
- (2) By contradiction, let be a deterministic solution algorithm, let the ring be unoriented, and let be the first moving agent. Let us assume, without loss of generality, that (according to the algorithm) moves to its left. The adversary chooses as the location of the black hole the node to the left of . Then, it places another agent to the immediate left of the black hole, and assigns to a sense of orientation opposite to the one of . Moreover, the adversary does not activate any other agents until both and make their move. This implies that, since is deterministic, will choose right as its moving direction. Therefore, both and will eventually disappear into the black hole, a contradiction. □
3. Gathering When Is Known and Is Unknown
3.1. In Oriented Rings
- An explorer at node u moves to the using cautious walk. if it enters the black hole, it dies; if it enters a node visited by another agent, it becomes a follower, returns to u, making the link safe; if it enters an unvisited node, it returns to u (maintaining the state explorer), it renders the right link safe and goes again to to continue the cautious walk.
- A follower at node u: if the right link is safe, it moves to the ; if the link is active and there are at least agents at u, it terminates the execution of the algorithm; else, it waits until the condition changes.
3.2. Unoriented Rings
3.2.1. k Odd
- 1.
- A red (resp. blue) explorer at node u moves to its right using cautious walk.
- (a)
- if it enters the black hole, it dies;
- (b)
- if it enters a node visited by another red (resp. blue) agent, it becomes a red (resp. blue) follower, returns to u, making the link safe;
- (c)
- if it enters a node that is a blue (resp. red) collection point, it becomes a blue (resp. red) follower;
- (d)
- if it enters a node where on the whiteboard there is a message indicating the direction of the collection point, it becomes notified;
- (e)
- if it enters a node where on the whiteboard there is a message to become a left-collector, it cancels the message, and it becomes a left-collector;
- (f)
- if it enters an unvisited node, it returns to u. If there are less than red (resp. blue) followers at u, it renders the right link safe and goes again to the to continue the cautious walk. If there are at least red (resp. blue) followers at u, it becomes a right-collector; moreover, if u is not a collection point, it registers this node as the red (resp. blue) collection point on the whiteboard.
- 2.
- A red (resp. blue) follower at node u:
- (a)
- if u is not a collection point and there are less than red (resp. blue) followers, it moves to its right if its right link is safe;
- (b)
- if u is not a collection point and there are at least red (resp. blue) followers at u, it registers u as a collection point; if its right link is safe, it becomes a right-collector, otherwise, it becomes a left-collector;
- (c)
- if u is a collection point and there is no left-collector, then it becomes a left-collector;
- (d)
- if it enters a node where on the whiteboard there is a message indicating the direction of the collection point, it becomes notified.
- 3.
- The left-collector x travels (using cautious walk when necessary) left, writing on the whiteboards of every visiting node the instruction to reach the collection point; it does so until it either dies in the black hole or reaches the last safe node explored by a blue explorer. In the latter case, the left-collector leaves a message for the blue explorer y, informing it of the collection point and instructing it to become a left-collector; it then becomes notified.
- 4.
- The rules for the right-collector are exactly those for the left-collector, where “left” and “right” are switched and so are “blue” and “red”.
- 5.
- A notified agent moves in the direction of the collection point.
- 6.
- If an agent is at the collection point, and there are both the left-collector and the right-collector, it enters a terminal state.
3.2.2. k Even
- 1.
- a collector computes and remembers the distance from its collection point. If passing the role of collector to an explorer, it passes also the distance information;
- 2.
- if a collector meets another collector (they must be from different collection points):
- (a)
- if they are of the same color, since they both agree on the same orientation of the ring, then they agree on a unique site (e.g., the rightmost of the two) as the final common collection point;
- (b)
- if they are of different colors, if the distance between the collection points is odd, they agree on the middle node as the final common collection point; otherwise, each chooses the closest site incident on the middle edge as the final collection point of its group;
- (c)
- each collector goes back to its group and notifies all the agents there of their final collection point.
- 1. If k is odd, can always be solved.
- 2. If k is even, cannot be solved for ; however, can always be solved.
- 3. can always be solved.
4. Gathering When Is Unknown and Is Known
4.1. Oriented Rings
- a two-agent block (i.e., created by merging two one-agent blocks) has one R-explorer and one L-explorer;
- a three-agent block has two explorers (one in each direction) and an R-shadow;
- a four-agent block has two explorers and two shadows (one in each direction);
- any additional agent (e.g., after merging two four-agent blocks) becomes passive.
- R-explorer: Move right using cautious walk as needed until a node v already visited by a different R-explorer is entered. Become L-explorer.
- L-explorer: Move left using cautious walk as needed until a node v already visited by an L-explorer is entered. Become R-shadow and set size to 0.
- R-shadow: Move right until the last safe node v is reached, decrementing size. If v has already been visited by an R-shadow, set size to 0 and become L-shadow. If the R-shadow is waiting at v, wake it up.If v has not been visited by an R-shadow, become R-shadow.
- R-shadow: (Starting at the rightmost safe node in its explored part.) If size (i.e., you left this node, traveled across the explored block and returned, and the R-explorer meanwhile did not explore a new node), wait until woken up by an R-shadow or the R-explorer (which just explored the node to the right and returned to make the link safe).In the latter case, become R-shadow, otherwise, set size and move left until the last safe node is reached, counting in size the number of nodes traversed.If size, then become collector, else become R-shadow.
- L-shadow: Move left until the last safe node v is reached, decrementing size. If v has already been visited by an L-shadow, become passive (but if the L-shadow is waiting at v, wake it up before becoming passive).If v has not been visited by an L-shadow, become L-shadow.
- L-shadow: Analogous to R-shadow, but with reversed directions.
- collector: A collector agent traverses the explored part and collects all the agents on the way (if an agent meets a collector, it stops its activity and follows the collector). Once the whole explored part has been traversed (collector counts links), agents have been collected and have gathered at the same place. There is a technical detail: it can happen that both shadows can become collectors. In that case, the gathering point is the node where they meet (or, if they crossed each other on a link, the right endpoint of that link).
- passive: Wait to be collected by a collector.
4.2. Unoriented Rings
- when an R-explorer comes to a node already visited by an L-explorer of the opposite color, it becomes an R-shadow;
- when an L-explorer comes to a node already visited by an R-explorer of the opposite color, it becomes an R-shadow;
- the L- and R- for shadows are used only for aging purposes. The tests are made against the shadows working in the same direction. For example, when a red R-shadowa arrives to the last explored node v in its direction, it checks whether v has been visited by a red R-shadow or blue L-shadow. If yes, a becomes an L-shadow (and possibly awakens the shadow at v, regardless of its color), otherwise a becomes an R-shadow;
- when (if) two collectors cross each other on an edge, they may not agree on which endpoint to meet (if the situation is symmetric), therefore, only is guaranteed, not .
- 1. If k is odd or n is even, can always be solved
- 2. If k is even and n is odd, cannot be solved for ; however, can always be solved.
- 3. can always be solved.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Cao, J.; Das, S. Mobile Agents in Networking and Distributed Computing; Wiley: Hoboken, NJ, USA, 2012. [Google Scholar]
- Flocchini, P.; Prencipe, G.; Santoro, N. Distributed Computing by Mobile Entities; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Peng, M.; Shi, W.; Corriveau, J.P.; Pazzi, R.; Wang, Y. Black hole search in computer networks: State-of-the-art, challenges and future directions. J. Parallel Distrib. Comput. 2016, 88, 1–15. [Google Scholar] [CrossRef]
- Pelc, A. Deterministic Rendezvous Algorithms. In Distributed Computing by Mobile Entities; Flocchini, P., Prencipe, G., Santoro, N., Eds.; Springer: Berlin/Heidelberg, Germany, 2019; Chapter 17. [Google Scholar]
- Barrière, L.; Flocchini, P.; Fraigniaud, P.; Santoro, N. Rendezvous and election of mobile agents: Impact of sense of direction. Theory Comput. Syst. 2007, 40, 143–162. [Google Scholar] [CrossRef]
- Bampas, E.; Blin, L.; Czyzowicz, J.; Ilcinkas, D.; Labourel, A.; Potop-Butucaru, M.; Tixeuil, S. On asynchronous rendezvous in general graphs. Theor. Comput. Sci. 2019, 753, 80–90. [Google Scholar] [CrossRef]
- Czyzowicz, J.; Pelc, A.; Labourel, A. How to meet asynchronously (almost) everywhere. Acm. Trans. Algorithms 2012, 8, 37:1–37:14. [Google Scholar] [CrossRef]
- Dieudonné, Y.; Pelc, A.; Villain, V. How to meet asynchronously at polynomial cost. Siam J. Comput. 2015, 44, 844–867. [Google Scholar] [CrossRef]
- Chattopadhyay, T.; Prasad, G. Mobile agent security against malicious hosts: A survey. Comput. Sci. 2022, 3, 160. [Google Scholar] [CrossRef]
- Sander, T.; Tschudin, C.F. Protecting mobile agents against malicious hosts. In Mobile Agent Security; Vigna, G., Ed.; Springer: Berlin/Heidelberg, Germany, 1998; pp. 44–60. [Google Scholar]
- Vitek, J.; Castagna, G. Mobile computations and hostile hosts. In Mobile Objects; Tsichritzis, D., Ed.; University of Geneva: Geneva, Switzerland, 1999; pp. 241–261. [Google Scholar]
- Flocchini, P.; Santoro, N. Distributed Security Algorithms for Mobile Agents. In Mobile Agents in Networking and Distributed Computing; Cao, J., Das, S., Eds.; Wiley: Hoboken, NJ, USA, 2012; Chapter 3. [Google Scholar]
- Dobrev, S.; Flocchini, P.; Prencipe, G.; Santoro, N. Mobile search for a black hole in an anonymous ring. Algorithmica 2007, 48, 67–90. [Google Scholar] [CrossRef]
- Chalopin, J.; Das, S.; Labourel, A.; Markou, E. Black hole search with finite automata scattered in a synchronous torus. In Proceedings of the 25th International Symposium on Distributed Computing, Rome, Italy, 20–22 September 2011; pp. 432–446. [Google Scholar]
- Chalopin, J.; Das, S.; Labourel, A.; Markou, E. Tight bounds for Black Hole Search with scattered agents in a synchronous ring. Theor. Comput. Sci. 2013, 509, 70–85. [Google Scholar] [CrossRef]
- Czyzowicz, J.; Kowalski, D.; Markou, E.; Pelc, A. Complexity of searching for a Black Hole. Fundam. Inform. 2006, 71, 229–242. [Google Scholar]
- D’Emidio, M.; Frigioni, D.; Navarra, A. Explore and repair graphs with black holes using mobile entities. Theor. Comput. Sci. 2015, 605, 129–145. [Google Scholar] [CrossRef]
- Dobrev, S.; Flocchini, P.; Kralovic, R.; Prencipe, G.; Ruzicka, P.; Santoro, N. Optimal search for a black hole in common interconnection networks. Networks 2006, 47, 61–71. [Google Scholar] [CrossRef]
- Dobrev, S.; Flocchini, P.; Královič, R.; Santoro, N. Exploring an unknown dangerous graph using tokens. Theor. Comput. Sci. 2013, 472, 28–45. [Google Scholar] [CrossRef]
- Dobrev, S.; Flocchini, P.; Prencipe, G.; Santoro, N. Searching for a black hole in arbitrary networks: Optimal mobile agents protocols. Distrib. Comput. 2006, 19, 1–35. [Google Scholar] [CrossRef]
- Flocchini, P.; Kellett, M.; Mason, P.; Santoro, N. Map construction and exploration by mobile agents scattered in a dangerous network. In Proceedings of the 28th IEEE International Parallel and Distributed Processing Symposium, Rome, Italy, 23–29 May 2009; pp. 1–10. [Google Scholar]
- Flocchini, P.; Kellett, M.; Mason, P.; Santoro, N. Fault-tolerant exploration of an unknown dangerous graph by scattered agents. In Proceedings of the 14th International Symposium on Stabilization, Safety, and Security of Distributed Systems (SSS), Toronto, ON, Canada, 1–4 October 2012; pp. 299–313. [Google Scholar]
- Klasing, R.; Markou, E.; Radzik, T.; Sarracco, F. Approximation bounds for Black Hole Search problems. Networks 2008, 52, 216–226. [Google Scholar] [CrossRef]
- Kosowski, A.; Navarra, A.; Pinotti, M. Synchronous black hole search in directed graphs. Theor. Comput. Sci. 2011, 412, 5752–5759. [Google Scholar] [CrossRef]
- Markou, E.; Paquette, M. Black hole search and exploration in unoriented tori with synchronous scattered finite automata. In Proceedings of the 14th International Conference on Principles of Distributed Systems, Rome, Italy, 18–20 December 2012; pp. 239–253. [Google Scholar]
- Markou, E.; Shi, W. Dangerous Graphs. In Distributed Computing by Mobile Entities; Flocchini, P., Prencipe, G., Santoro, N., Eds.; Springer: Berlin/Heidelberg, Germany, 2019; Chapter 18. [Google Scholar]
- Balamohan, B.; Flocchini, P.; Miri, A.; Santoro, N. Time optimal algorithms for black hole search in rings. Discret. Math. Algorithms Appl. 2011, 3, 1–15. [Google Scholar] [CrossRef]
- Dobrev, S.; Santoro, N.; Shi, W. Using scattered mobile agents to locate a black hole in a unoriented ring with tokens. Int. J. Found. Comput. Sci. 2008, 19, 1355–1372. [Google Scholar] [CrossRef]
- Dobrev, S.; Flocchini, P.; Prencipe, G.; Santoro, N. Multiple agents rendezvous in a ring in spite of a black hole. In Proceedings of the 7th International Conference on Principles of Distributed Systems, La Martinique, France, 10–13 December 2003; pp. 34–46. [Google Scholar]



| n Unknown, k Known | n Known, k Unknown | |||
|---|---|---|---|---|
| ORIENTED | ||||
| k odd | k odd or n even | |||
| UNORIENTED | k even | k even and n odd | ||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dobrev, S.; Flocchini, P.; Prencipe, G.; Santoro, N. Asynchronous Gathering in a Dangerous Ring. Algorithms 2023, 16, 222. https://doi.org/10.3390/a16050222
Dobrev S, Flocchini P, Prencipe G, Santoro N. Asynchronous Gathering in a Dangerous Ring. Algorithms. 2023; 16(5):222. https://doi.org/10.3390/a16050222
Chicago/Turabian StyleDobrev, Stefan, Paola Flocchini, Giuseppe Prencipe, and Nicola Santoro. 2023. "Asynchronous Gathering in a Dangerous Ring" Algorithms 16, no. 5: 222. https://doi.org/10.3390/a16050222
APA StyleDobrev, S., Flocchini, P., Prencipe, G., & Santoro, N. (2023). Asynchronous Gathering in a Dangerous Ring. Algorithms, 16(5), 222. https://doi.org/10.3390/a16050222









