Sustainable Risk Identification Using Formal Ontologies †
Abstract
:1. Introduction
2. Materials and Methods
- formally define concepts associated with a specific risk type, as well as their relations, by authoring an ontology;
- formally define the risk type in the ontology, using the predefined concepts and relations. This definition of a risk type aims to promote the automatic identification of its instantiations;
- capture the organisational situation by instantiating the existing ontology definitions. This is achieved by incorporating “individual” definitions into the ontology;
- apply automated, ontology-based reasoners to the ontology to derive new, inferred insights about the situation.
3. Results
3.1. Concepts and Relations (Meta Levels Definitions)
- Application, representing a software application by the enterprise;
- Component, representing any software component;
- Business Function, representing any function that relates to the enterprise’s business operation;
- Sensitive Information, representing any sensitive information item owned by the enterprise;
- Vulnerability, representing any vulnerability of software components;
- Risk, representing the enterprise’s risk definitions;
- Cybersecurity Risk, representing a specific subclass of risk definitions relating to cybersecurity issues;
- Vulnerability-Induced Risk, representing any risk to the business emerging from the existence of a vulnerability. Being a risk definition relating to a cybersecurity issue, it is a specific subclass of Cybersecurity Risk.
- accessInfo—represents an ability of an application (Domain) to access a sensitive information item (Range);
- supportsFunction—represents that an application (Domain) supports a business function (Range);
- includesComponent—represents a software application composition, linking the application (Domain) with its components (Range);
- foundIn—represents a vulnerability (Domain) found in a software component (Range);
- susceptible2Vulnerability—marks an application (Domain) as being susceptible to a vulnerability (Range) due to one of its software components. This object property is formally defined as a composite property using other object properties:
- 6.
- risksInfo—indicates that a vulnerability (Domain) may risk sensitive information (Range). This object property is formally defined as a composite property using other object properties:
- 7.
- risksFunction—indicates that a vulnerability (Domain) may risk a business function (Range). This object property is formally defined as a composite property using other object properties:
- 8.
- risksVia—identifies the application (Range) through which a specific Vulnerability-Induced Risk (Domain) can be realised. This object property is formally defined as a composite property using other object properties:
inverse(supportsFunction) ◦ risksFunction
3.2. Risk Definition
((risksFunction some BusinessFunction) or
(risksInfo some SensitiveInformation))
3.3. Situation
- App1, which does not include Log4j as one of its software components;
- App2, which includes Log4j as one of its software components;
- App3, which includes Log4j as one of its software components and has access to the sensitive information item named ClientIDsList;
- App4, which includes Log4j as one of its software components and supports the business function named OpenAccount.
3.4. Ontology-Based Inferrence
- The “susceptible2Vulnerability” object property is attributed to App2, App3 and App4. This suggests that each of these applications is susceptible to the vulnerability.
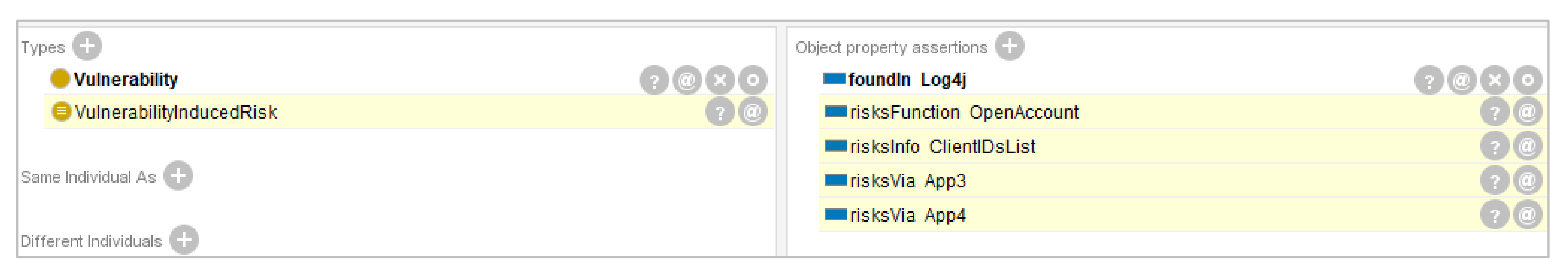
- The Log4shell vulnerability is categorized—automatically—as a VulnerabilityInducedRisk. This indicates that this specific vulnerability introduces new risk/s to the enterprise, as Figure 2 shows. This is the automatic identification of new risks.
- The object property “risksInfo ClientIDsList” emerges with respect to the Log4shell vulnerability (Figure 2). This suggests that ClientIDsList, which is one of the enterprise’s sensitive information items, is at risk.
- The object property “risksFunction OpenAccount” emerges with respect to the Log4shell vulnerability (Figure 2). This suggests that OpenAccount—one of the enterprise’s business functions—is at risk.
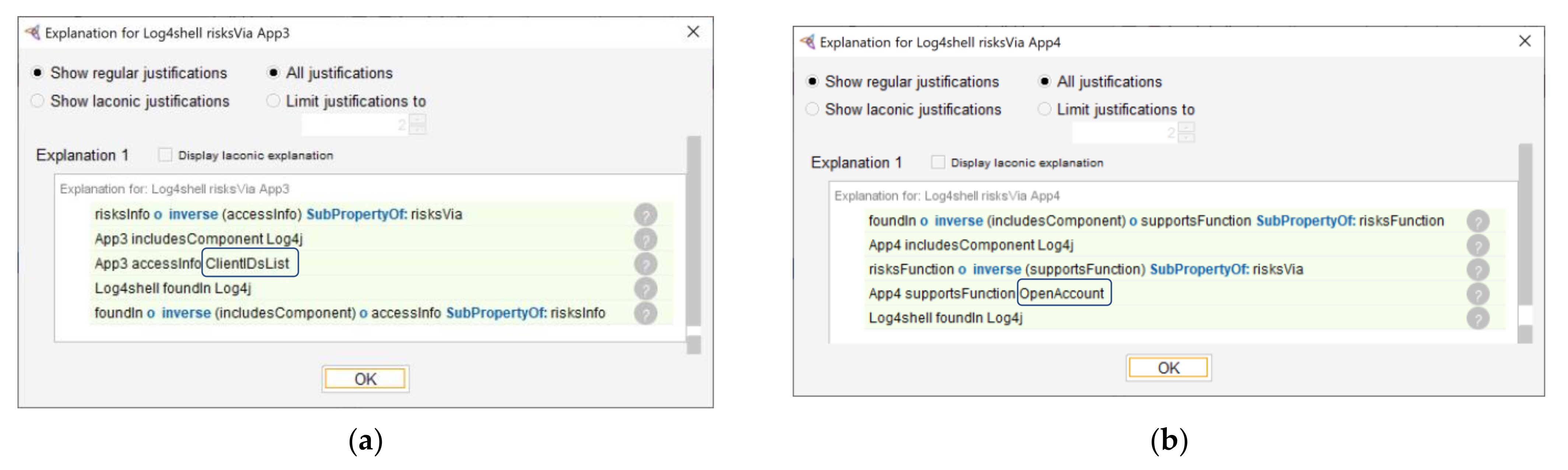
- Two new risksVia object property assertions emerge, with respect to the Log4shell vulnerability (Figure 2). Each of these suggests a possible attack surface through which the risk can realise. In the specific case, App3 is the attack surface for the risk on ClientIDsList and App4 is the attack surface for the risk on the OpenAccount. While this is not captured explicitly in the inferred assertions, the reasoner explanation mechanism provides this traceability, as Figure 3 shows.
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A. The Case Study Formal Ontology (OWL Format)
Appendix B. Inferred Assertions by the Reasoner (OWL Format)
References
- ISO 31073:2022; Risk Management—Vocabulary. International Standardization Organization (ISO): Geneva, Switzerland, 2022.
- Atkinson, C.; Cuske, C.; Dickopp, T. Concepts for an Ontology-Centric Technology Risk Management Architecture in the Banking Industry. In Proceedings of the 2006 10th IEEE International Enterprise Distributed Object Computing Conference Workshops (EDOCW’06), Hong Kong, China, 16–20 October 2006; p. 21. [Google Scholar] [CrossRef]
- Refsdal, A.; Solhaug, B.; Stølen, K. Cyber-Risk Management; SpringerBriefs in Computer Science; Springer International Publishing: Cham, Switzerland, 2015; ISBN 978-3-319-23569-1. [Google Scholar]
- Strupczewski, G. Defining Cyber Risk. Saf. Sci. 2021, 135, 105143. [Google Scholar] [CrossRef]
- ISO 31000:2018; Risk Management—Guidelines. International Standardization Organization (ISO): Geneva, Switzerland, 2018.
- Eling, M.; Schnell, W. What Do We Know about Cyber Risk and Cyber Risk Insurance? J. Risk Financ. 2016, 17, 474–491. [Google Scholar] [CrossRef]
- Kosub, T. Components and Challenges of Integrated Cyber Risk Management. Z. Für Die Gesamte Versicher. 2015, 104, 615–634. [Google Scholar] [CrossRef]
- Jackson, G. Contingency for Cost Control in Project Management: A Case Study. Constr. Econ. Build. 2003, 3, 1–12. [Google Scholar] [CrossRef]
- Radanliev, P.; Charles, D.; Roure, D.; Nicolescu, R.; Huth, M.; Mantilla, R.; Cannady, S.; Burnap, P. Computers in Industry Future Developments in Cyber Risk Assessment for the Internet of Things. Comput. Ind. 2018, 102, 14–22. [Google Scholar] [CrossRef]
- Shin, B.; Lowry, P.B. A Review and Theoretical Explanation of the ‘Cyberthreat-Intelligence (CTI) Capability’ That Needs to Be Fostered in Information Security Practitioners and How This Can Be Accomplished. Comput. Secur. 2020, 92, 101761. [Google Scholar] [CrossRef]
- Kotsias, J.; Ahmad, A.; Scheepers, R. Adopting and Integrating Cyber-Threat Intelligence in a Commercial Organisation. Eur. J. Inf. Syst. 2022, 1–17. [Google Scholar] [CrossRef]
- Risk Registers (ENISA). Available online: https://www.enisa.europa.eu/topics/threat-risk-management/risk-management/current-risk/bcm-resilience/bc-plan/supporting-documents/risk-registers (accessed on 24 August 2022).
- Chen, Y.; Boehm, B.; Sheppard, L. Value Driven Security Threat Modeling Based on Attack Path Analysis. In Proceedings of the Annual Hawaii International Conference on System Sciences, Waikoloa, HI, USA, 3–6 January 2007. [Google Scholar]
- Zhao, J.; Yan, Q.; Li, J.; Shao, M.; He, Z.; Li, B. TIMiner: Automatically Extracting and Analyzing Categorized Cyber Threat Intelligence from Social Data. Comput. Secur. 2020, 95, 101867. [Google Scholar] [CrossRef]
- Schauer, S.; Polemi, N.; Mouratidis, H. MITIGATE: A Dynamic Supply Chain Cyber Risk Assessment Methodology. J. Transp. Secur. 2019, 12, 1–35. [Google Scholar] [CrossRef]
- Shaked, A.; Margalit, O. OnToRisk–A Formal Ontology Approach to Automate Cyber Security Risk Identification. In Proceedings of the 2022 17th Annual System of Systems Engineering Conference (SOSE), Rochester, NY, USA, 7–11 June 2022; pp. 74–79. [Google Scholar]
- Gruber, T.R. Towards Principles for Design of Ontologies Used for Knowledge Sharing. Int. J. Hum.-Comput. Stud. 1995, 43, 907–928. [Google Scholar] [CrossRef]
- Benjamins, V.R.; Davies, J.; Baeza-Yates, R.; Mika, P.; Zaragoza, H.; Greaves, M.; Gomez-Perez, J.M.; Contreras, J.; Domingue, J.; Fensel, D. Near-Term Prospects for Semantic Technologies. IEEE Intell. Syst. 2008, 23, 76–88. [Google Scholar] [CrossRef]
- Chandrasekaran, B.; Josephson, J.R.; Benjamins, V.R. What Aro Ontologies, and Why Do We Need Them? IEEE Intell. Syst. Appl. 1999, 14, 20–26. [Google Scholar] [CrossRef]
- Poole, D.L.; Mackworth, A.K. Artificial Intelligence; Cambridge University Press: Cambridge, UK, 2017; ISBN 9781107195394. [Google Scholar]
- Wang, J.A.; Guo, M. Security Data Mining in an Ontology for Vulnerability Management. In Proceedings of the 2009 International Joint Conference on Bioinformatics, Systems Biology and Intelligent Computing (IJCBS 2009), Shanghai, China, 3–5 August 2009; pp. 597–603. [Google Scholar]
- Gailly, F.; Alkhaldi, N.; Casteleyn, S.; Verbeke, W. Recommendation-Based Conceptual Modeling and Ontology Evolution Framework (CMOE+). Bus. Inf. Syst. Eng. 2017, 59, 235–250. [Google Scholar] [CrossRef]
- Thomas, O.; Michael Fellmann, M.A. Semantic Process Modeling—Design and Implementation of an Ontology-Based Representation of Business Processes. Bus. Inf. Syst. Eng. 2009, 1, 438–451. [Google Scholar] [CrossRef]
- Meng, X.; Wang, F.; Xie, Y.; Song, G.; Ma, S.; Hu, S.; Bai, J.; Yang, Y. An Ontology-Driven Approach for Integrating Intelligence to Manage Human and Ecological Health Risks in the Geospatial Sensor Web. Sensors 2018, 18, 3619. [Google Scholar] [CrossRef]
- Shen, Y.; Xu, M.; Lin, Y.; Cui, C.; Shi, X.; Liu, Y. Safety Risk Management of Prefabricated Building Construction Based on Ontology Technology in the BIM Environment. Buildings 2022, 12, 765. [Google Scholar] [CrossRef]
- Välja, M.; Heiding, F.; Franke, U.; Lagerström, R. Automating Threat Modeling Using an Ontology Framework: Validated with Data from Critical Infrastructures. Cybersecurity 2020, 3, 19. [Google Scholar] [CrossRef]
- Aranovich, R.; Wu, M.; Yu, D.; Katsy, K.; Ahmadnia, B.; Bishop, M.; Filkov, V.; Sagae, K. Beyond NVD: Cybersecurity Meets the Semantic Web. In ACM International Conference Proceeding Series; Association for Computing Machinery: New York, NY, USA, 2021; pp. 59–69. [Google Scholar]
- Mozzaquatro, B.; Agostinho, C.; Goncalves, D.; Martins, J.; Jardim-Goncalves, R. An Ontology-Based Cybersecurity Framework for the Internet of Things. Sensors 2018, 18, 3053. [Google Scholar] [CrossRef]
- Vega-Barbas, M.; Villagrá, V.A.; Monje, F.; Riesco, R.; Larriva-Novo, X.; Berrocal, J. Ontology-Based System for Dynamic Risk Management in Administrative Domains. Appl. Sci. 2019, 9, 4547. [Google Scholar] [CrossRef] [Green Version]
- Eckhart, M.; Ekelhart, A.; Weippl, E. Automated Security Risk Identification Using AutomationML-Based Engineering Data. IEEE Trans. Dependable Secur. Comput. 2022, 19, 1655–1672. [Google Scholar] [CrossRef]
- Ghaffarian, S.M.; Shahriari, H.R. Software Vulnerability Analysis and Discovery Using Machine-Learning and Data-Mining Techniques: A Survey. ACM Comput. Surv. 2017, 50, 1–36. [Google Scholar] [CrossRef]
- Yin, R.K. Case Study Research: Design and Methods; SAGE: New York, NY, USA, 2009; ISBN 9781412960991. [Google Scholar]
- Adkins, H. Review of the December 2021 Log4j Event; Cybersecurity and Infrastructure Security Agency: Rosslyn, VA, USA, 2022. [Google Scholar]
- Tuttle, H. 2022 Cyber Landscape. Risk Manag. 2022, 69, 18–23. [Google Scholar]
- Protégé. Available online: http://protege.stanford.edu (accessed on 14 March 2022).
- The CoModIDE Plugin for Protégé Repository. Available online: https://github.com/comodide/CoModIDE (accessed on 21 March 2022).
- MITRE CVE Website. Available online: https://cve.mitre.org/ (accessed on 17 August 2022).

Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shaked, A.; Margalit, O. Sustainable Risk Identification Using Formal Ontologies. Algorithms 2022, 15, 316. https://doi.org/10.3390/a15090316
Shaked A, Margalit O. Sustainable Risk Identification Using Formal Ontologies. Algorithms. 2022; 15(9):316. https://doi.org/10.3390/a15090316
Chicago/Turabian StyleShaked, Avi, and Oded Margalit. 2022. "Sustainable Risk Identification Using Formal Ontologies" Algorithms 15, no. 9: 316. https://doi.org/10.3390/a15090316
APA StyleShaked, A., & Margalit, O. (2022). Sustainable Risk Identification Using Formal Ontologies. Algorithms, 15(9), 316. https://doi.org/10.3390/a15090316






